System and method for realizing single-point login
A single sign-on and website technology, applied in the Internet field, can solve the problems of legal identity login failure, complex encryption algorithm, defrauding legal identity, etc., and achieve the effect of small software modification, simple processing logic, and saving processing time and investment
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
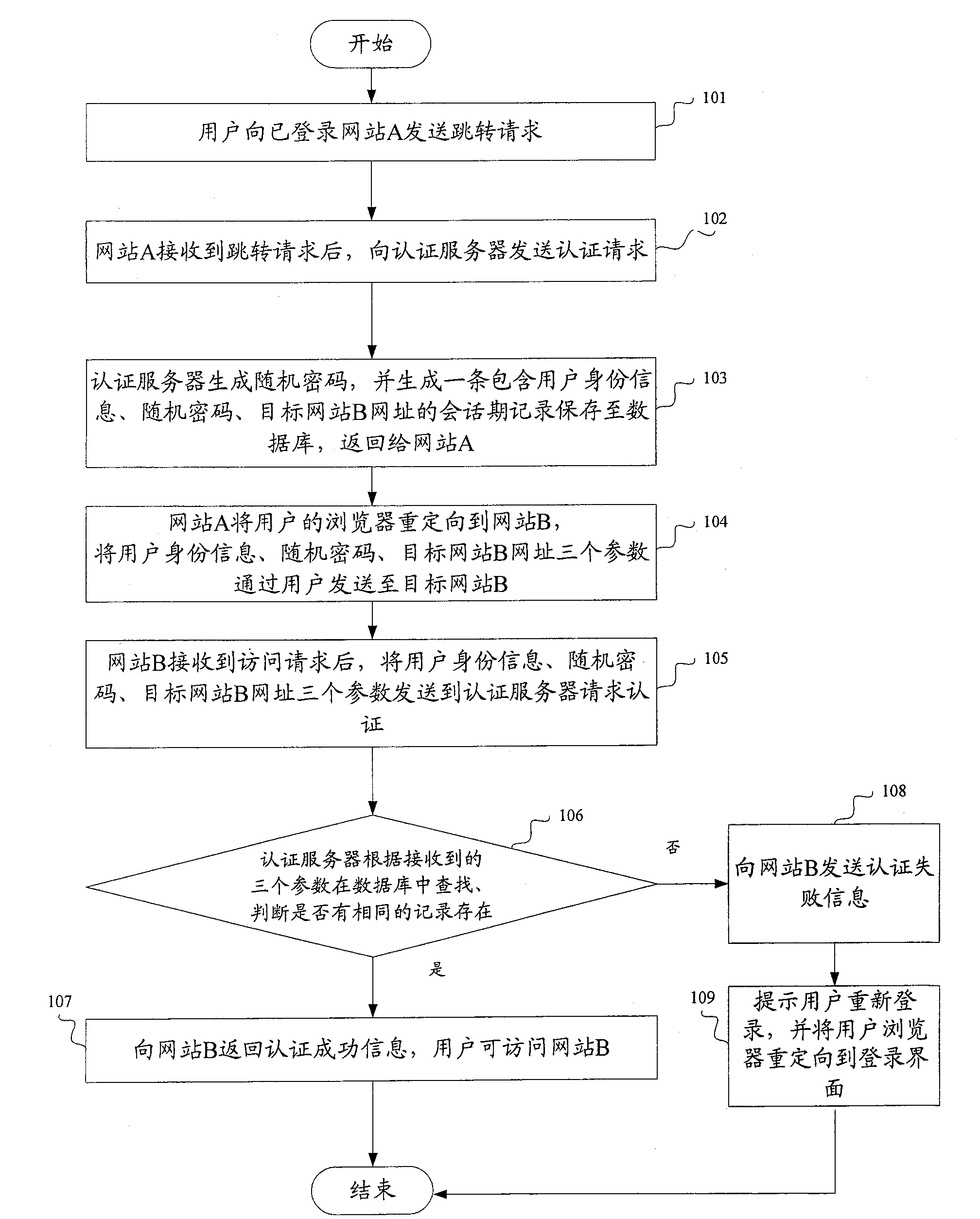
[0038] The invention provides a single sign-on method, which is used to realize simple, safe, low-coupling and low-cost single sign-on.
[0039] refer to figure 1 , to illustrate the implementation method of the present invention.
[0040] Step 101: The user sends a jump request to the website A that has logged in to the website B;
[0041] Step 102: After website A receives the redirection request, it sends an authentication request to the authentication server with user identity information and the URL of website B to be logged in;
[0042] Step 103: The authentication server generates a random password after receiving the authentication request, and generates a session record including user identity information, random password, and URL of the target website B, saves it to the database, and returns it to the website A;
[0043] Step 104: website A redirects the user's browser to website B, and sends the three parameters of user identity information, random password, and URL...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com