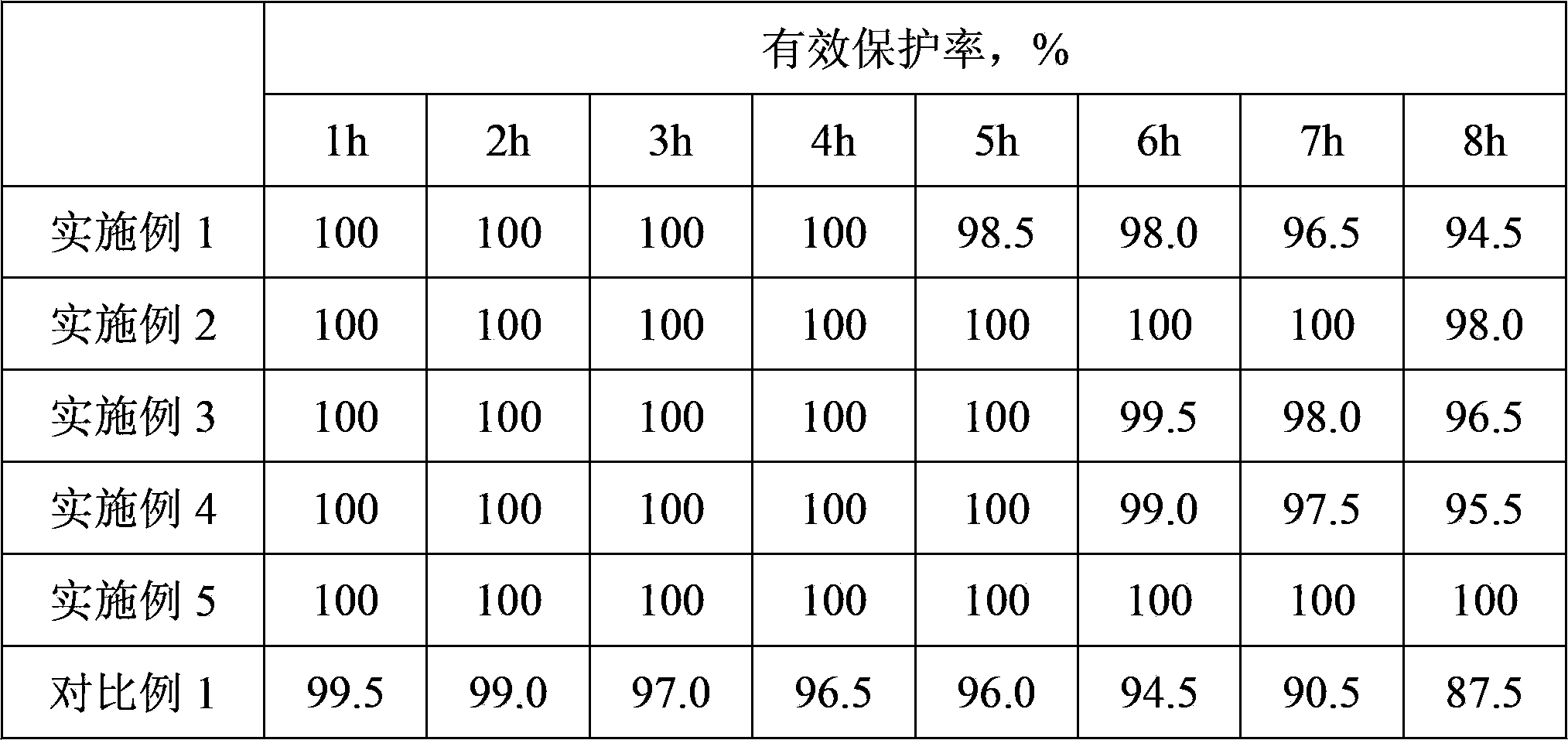
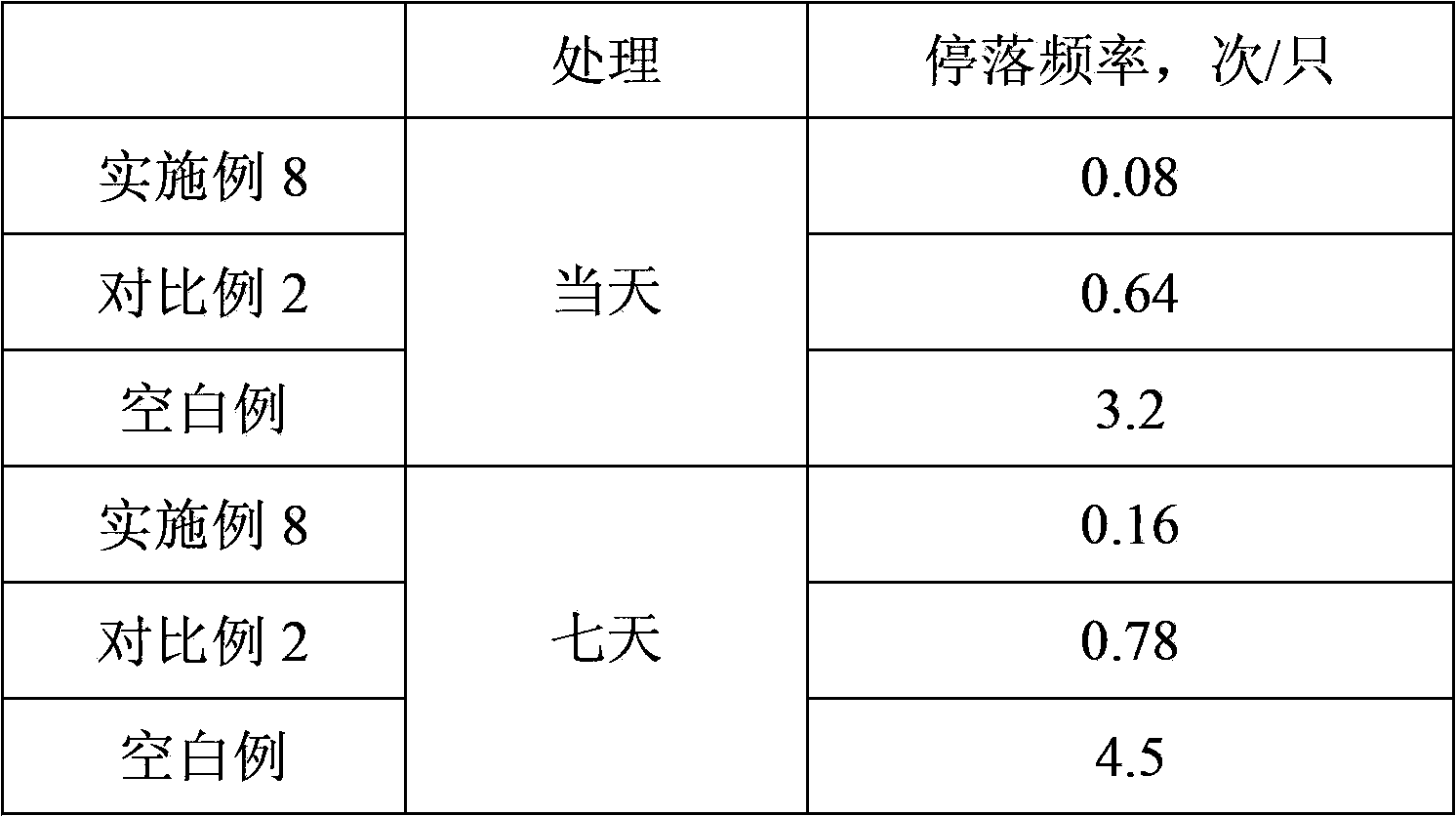
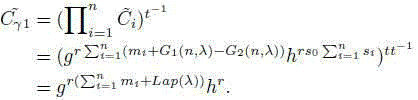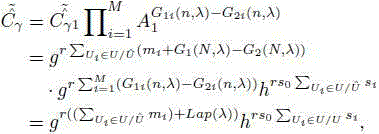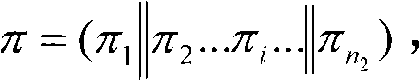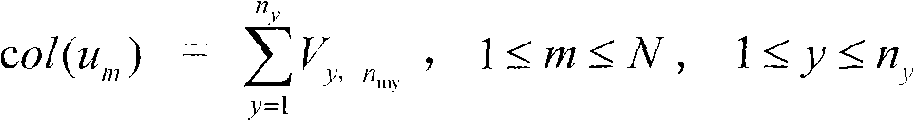Patents
Literature
87results about How to "Improve attack ability" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
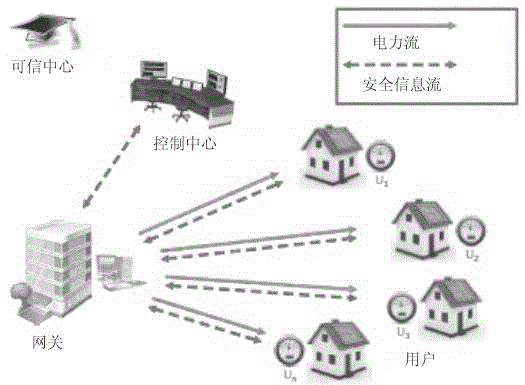
Smart power grid aggregation method and system for differential privacy security and fault tolerance
ActiveCN104579781AEfficient and flexible fault toleranceResistance to Differential Privacy AttacksPower network operation systems integrationCircuit arrangementsFault toleranceTelecommunications link
The invention discloses a smart power grid aggregation method and system for differential privacy security and fault tolerance. The method comprises the steps that a smart electric meter records and reports the electricity consumption of users in real time; a control center is responsible for collecting, processing and analyzing real-time electricity consumption data; a gateway is responsible for instruction delivery, data aggregation and security transmission between the control center and the users; a credible center is responsible for managing the whole system, and main function modules include a system initialization function module, a data aggregation request function module, a data aggregation request relay function module, a user data report function module, a security data aggregation function module and an aggregated data recovery module. According to the smart power grid aggregation method and system, the common fault tolerant function is supported, a difference privacy attack can be resisted, and the phenomenon that a hostile attacker exposes and obtains privacy information of the users by eavesdropping user communication links can be resisted; when some user data are not reported successfully, the electricity consumption of all the users with normal data reporting can still be aggregated; the smart power grid aggregation method and system have the high elastic expandability and can support efficient million-scale smart power grid electricity consumption data aggregation.
Owner:ZHEJIANG GONGSHANG UNIVERSITY
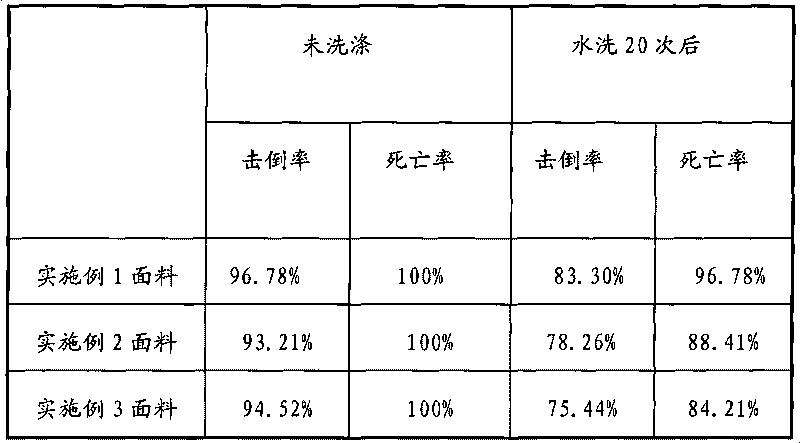
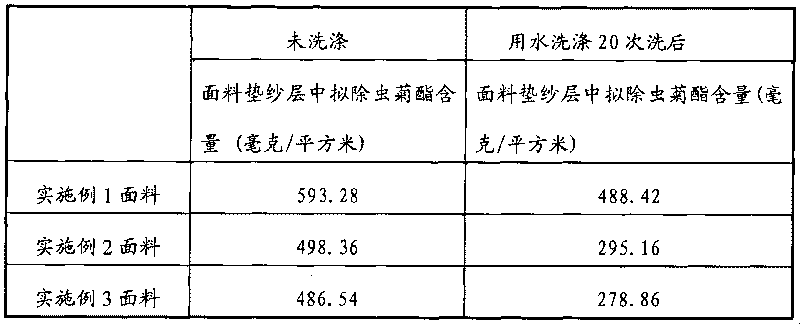
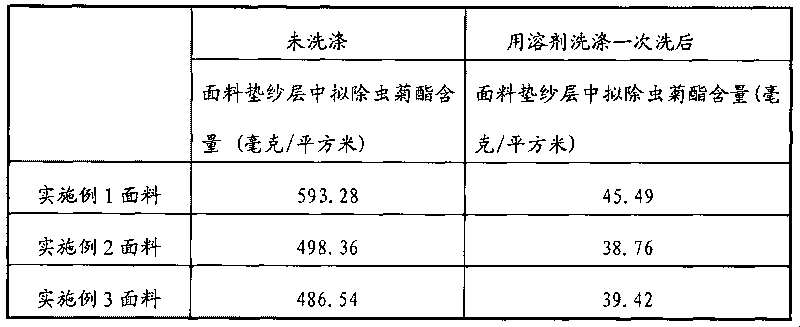
Mothproof fabric and preparation method thereof
The invention discloses a mothproof fabric and a preparation method thereof. The preparation method of the mothproof fabric comprises the following steps: weaving natural fibers into an inner layer, synthetic multifilament yarn into a surface course, and polypropylene fiber filament or polyethylene fiber filament fabric into a lapping layer, wherein the inner layer and the surface course are in grid shape; dying in dying liquid at a temperature of 60-105 DEG C for 10-120 minutes; washing with water; drying; and forming, wherein the dying liquid is a missible-oil aqueous solution, missible oil is formed by mixing pyrethroid and ether solvent in a mass ratio of 1:5 to 1:20; the mass ratio of the fabric to the dying liquid is 1:7 to 1:20; and the amount of the missible oil is 5-10% of the fabric weight. The method has short production flows, convenient operation, small consumption of a pyrethroid pesticide and low requirements for fiber material by adopting dying and the additional pyrethroid pesticide; and the fabric prepared by the method has favorable permeability, strong capability of resisting insect invasion and long anti-mosquito effect.
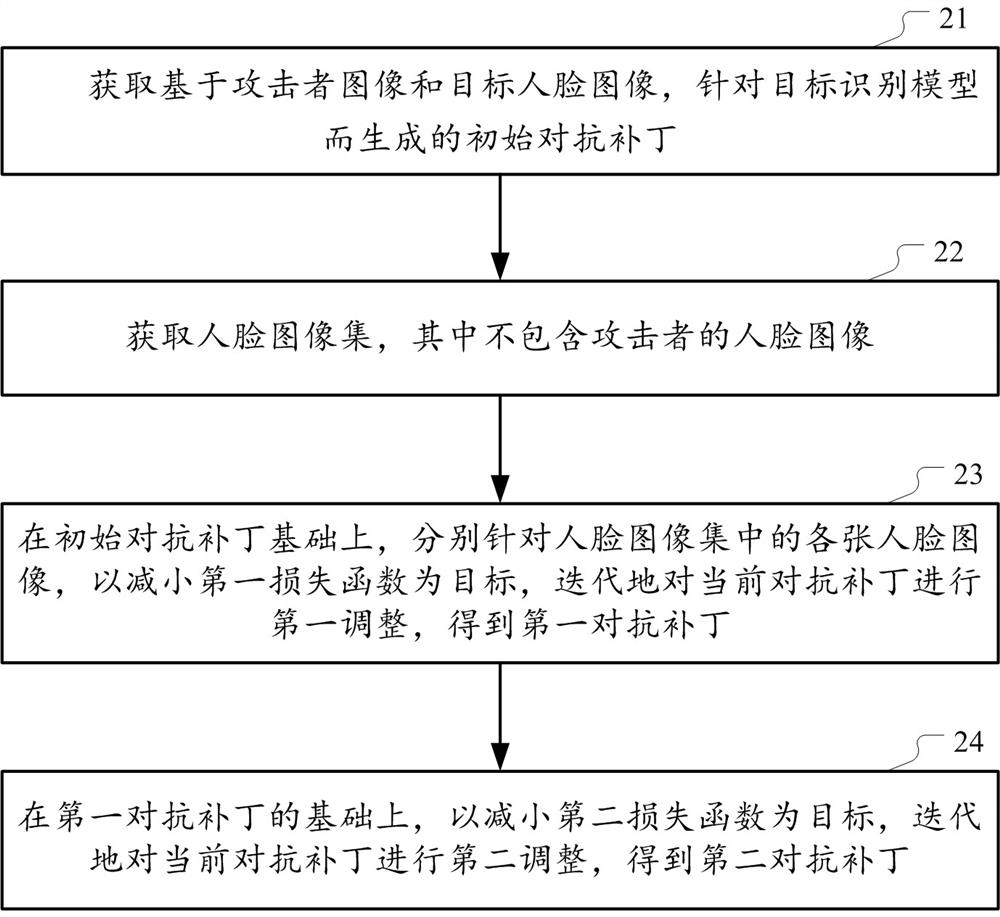
Owner:SHANGHAI GONGTAI TEXTILE PROD +1
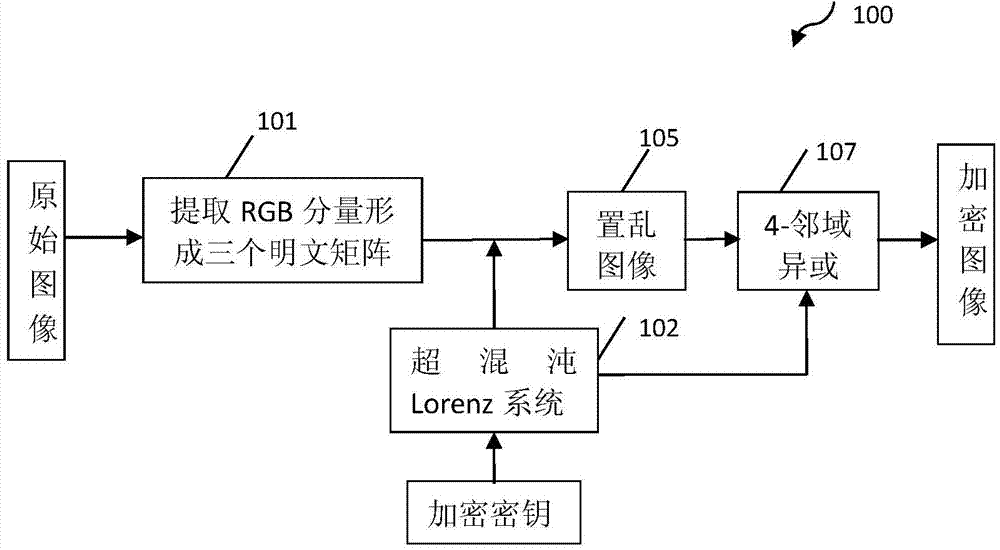
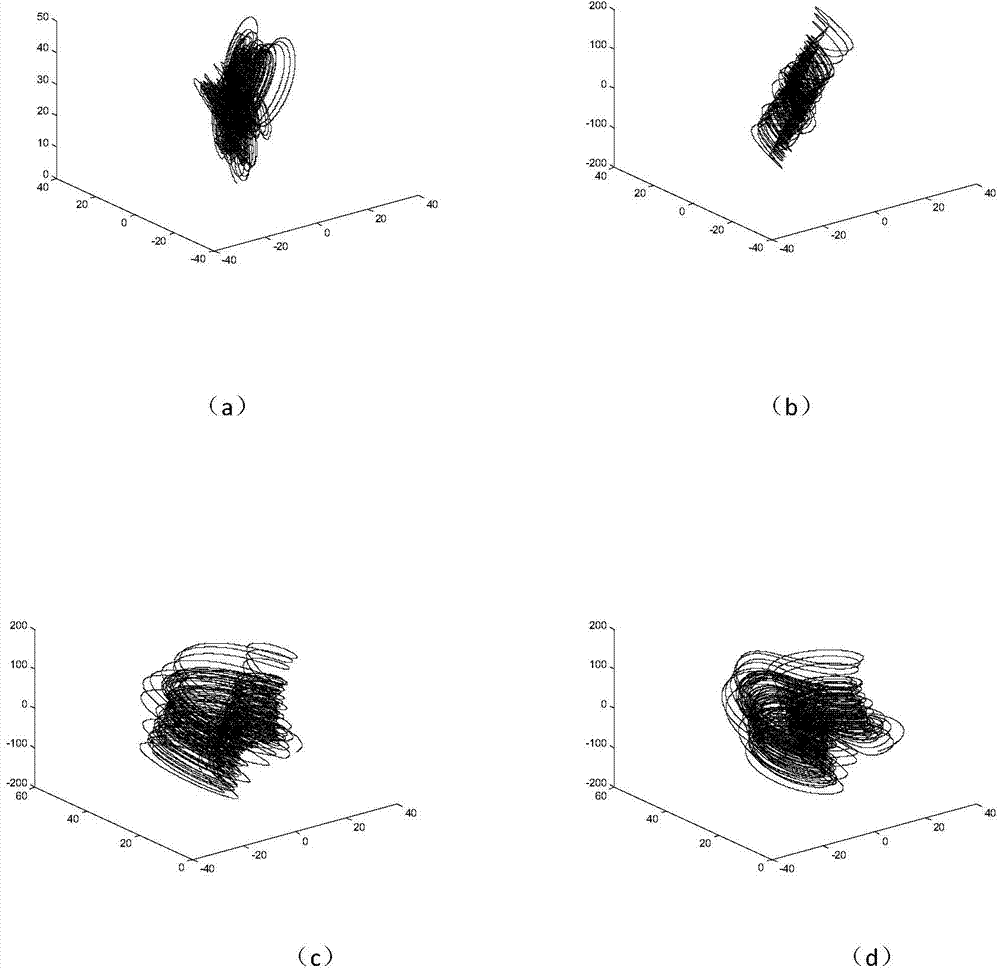
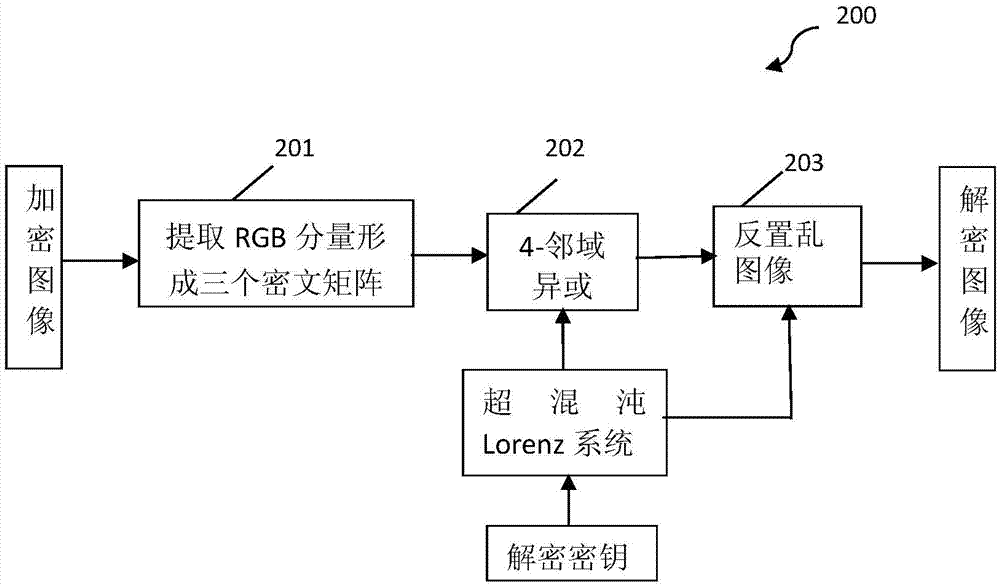
4-neighborhood exclusive or image encryption method based on hyper-chaos lorenz system
InactiveCN103491279ALarge key spaceImprove securitySecuring communicationPictoral communicationPattern recognitionColor image
The invention relates to a 4-neighborhood exclusive or image encryption method based on a hyper-chaos Lorenz system. The method is characterized in that RGE three components of an original color image are extracted, the grey levels of all pixel points in the RGE three components are recorded as a two-dimensional matrix PR, a two-dimensional matrix PG and a two-dimensional matrix PB, scrambling is carried out on the matrix PR, the matrix PG and the matrix PB respectively by means of chaos sequences generated by the hyper-chaos Lorenz to obtain an image pixel matrix PR1, an image pixel matrix PG1 and an image pixel matrix PB1 after scrambling, and 4-neighborhood exclusive or encryption is carried out on the matrix PR1 through reusing of the processed chaos sequences of the Lorenz, the matrix PG1 and the matrix PB1 respectively, so the encryption process is completed. The scrambling and 4-neighborhood exclusive or encryption are carried out on the color image through the hyper-chaos Lorenz system, so the method has the advantages of being large in secret key space, good in safety and strong in plaintext attack resistance and is suitable for image secret communication.
Owner:UNIV OF SHANGHAI FOR SCI & TECH
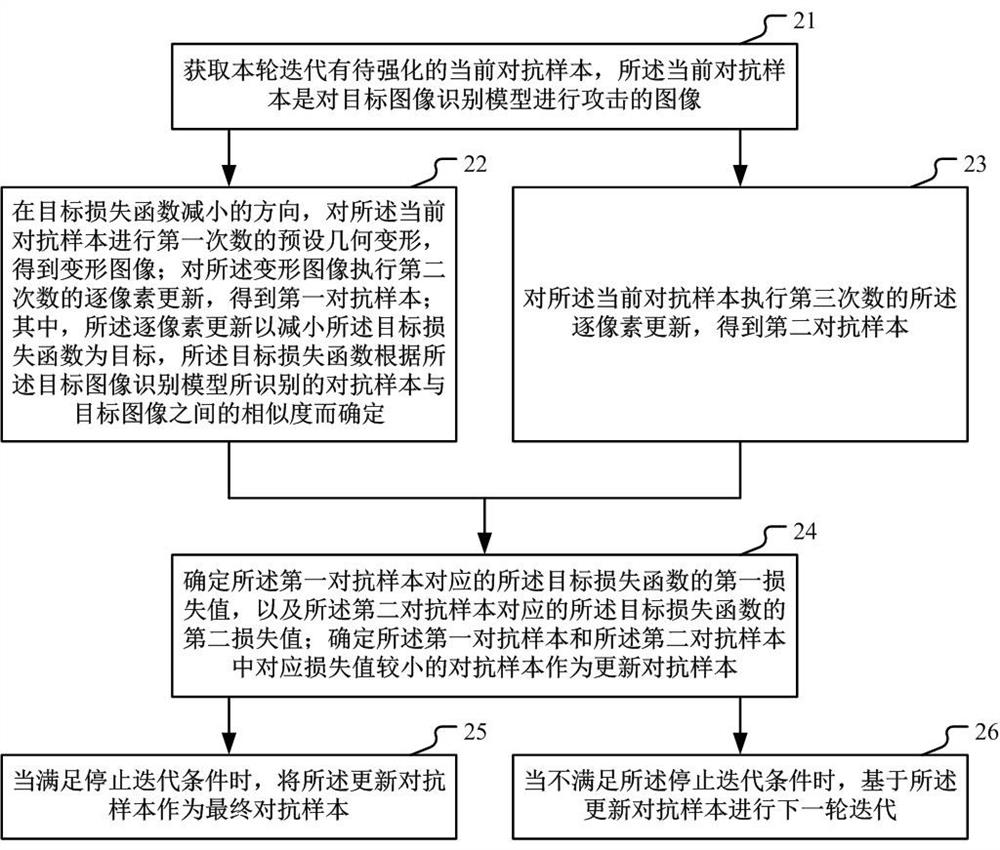
Adversarial sample generation method and device
ActiveCN111737691AGood attack effectAggressiveCharacter and pattern recognitionPlatform integrity maintainanceComputational physicsMorphing
Embodiments of the invention provide an adversarial sample generation method and device. The method comprises the steps of obtaining a to-be-enhanced current adversarial sample in the current iteration; in the decreasing direction of the target loss function, performing preset geometric deformation on the current adversarial sample for a first time to obtain a deformed image; executing second-timepixel-by-pixel updating on the deformed image to obtain a first adversarial sample; performing third pixel-by-pixel updating on the current adversarial sample to obtain a second adversarial sample; determining an adversarial sample with a smaller corresponding loss value in the first adversarial sample and the second adversarial sample as an updated adversarial sample; when the iteration stoppingcondition is met, taking the updated adversarial sample as a final adversarial sample; and when the iteration stopping condition is not met, performing the next round of iteration based on the updated adversarial sample. The generated adversarial sample can have stronger aggressivity, so that targeted defense is realized.
Owner:ALIPAY (HANGZHOU) INFORMATION TECH CO LTD
Generating method of variable-parameter multistage chaotic pseudorandom sequence
ActiveCN102708534AThe generation method is flexible and convenientImprove securityImage data processing detailsPseudorandom sequenceEncryption
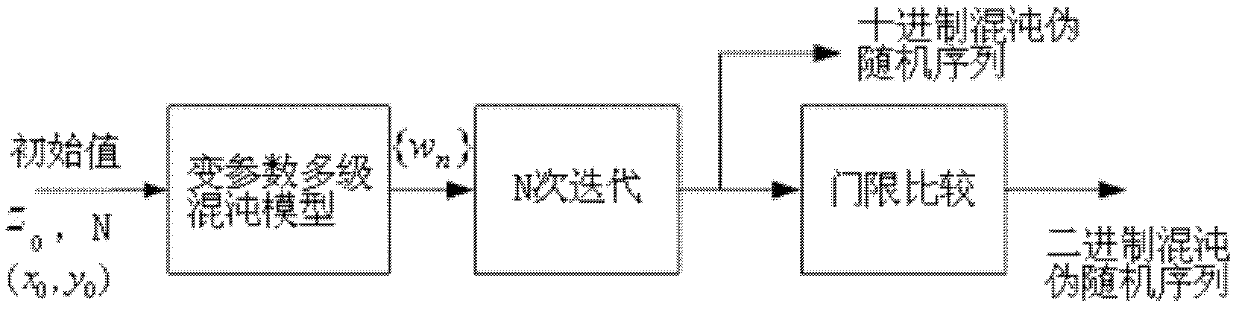
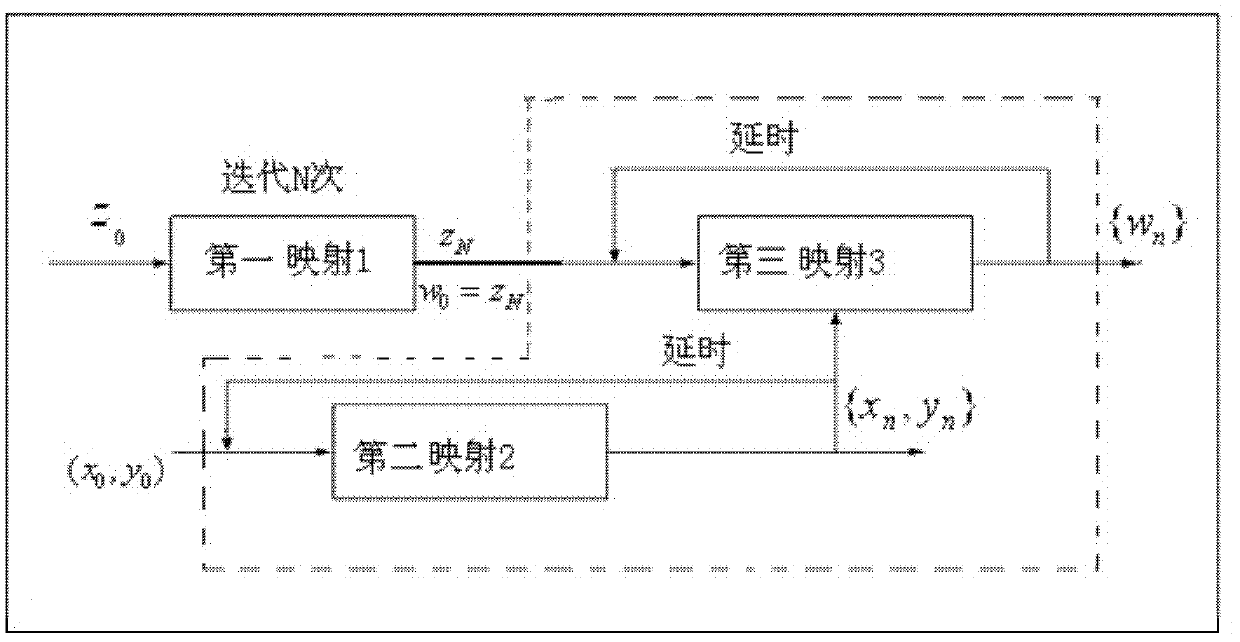
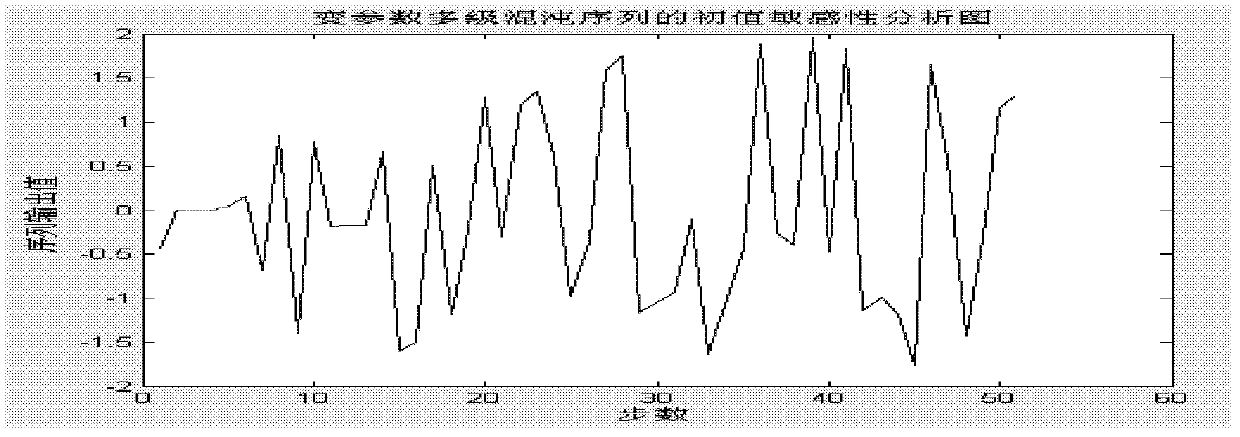
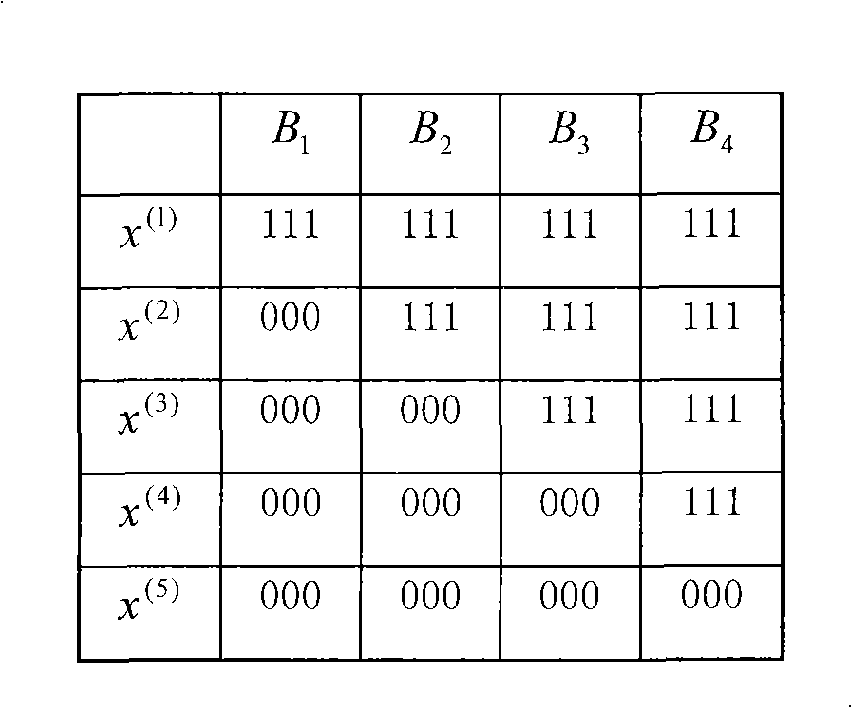
The invention provides a generating method of a variable-parameter multistage chaotic pseudorandom sequence, comprising the following steps of: selecting chaotic mapping 1, setting an initial value z0and iterating for N times according to the operation relationship of the mapping 1 to output ZN; selecting chaotic mapping 2, setting an initial value (x0, y0), and iterating for N times according to the operation relationship of the mapping 2 to output (xn, yn); selecting chaotic mapping 3, setting an initial value of the mapping 3 w0 to be equal to ZN, dynamically controlling the order of the mapping 3 by the output of the mapping 2, wherein when the iteration is carried out for even times, the order is controlled by xn, and when the iteration is carried out for odd times, the order is controlled by yn; iterating and outputting wn by virtue of the initial value and the order according to the operation relationship of the mapping 3; forming a variable-parameter multistage chaotic model by the mapping 1, 2, 3, and iterating for N times to generate a decimal chaotic pseudorandom sequence wN with the length of N; and outputting a binary chaotic pseudorandom sequence through a threshold comparison. By adopting the generating method of the variable-parameter multistage chaotic pseudorandom sequence, the chaotic pseudorandom sequence of which the related function is approximate to impact, the mutual related function is approximate to 0 and the power spectrum is approximate to a constant can be generated flexibly and conveniently; and the requirement of users on the image encryption can be satisfied.
Owner:JIANGSU XINGHUA RUBBER BELT
Roselle beverage
InactiveCN102599592AGood for healthLong retention periodFood preparationSmoked PlumGLYCYRRHIZA EXTRACT
The invention relates to roselle beverage which comprises the following components in percentage by weight: 50-55% of roselle juice, 0.4-0.5% of fructo-oligosaccharide, 5-6% of high fructose corn syrup, 0.7-0.8% of xylitol, 0.2-0.3% of citric acid, 0.01-0.05% of stevia rebaudiana, 0.02% of nisin and the balance of water, wherein the roselle juice is prepared by extracting a roselle mixture composed of dried roselle, dried smoked plum, dried hawthorn and dried liquorice; the roselle mixture comprises the components in percentage by weight: 96-99% of dried roselle, 0.4-1% of dried smoked plum, 0.05-0.5% of dried hawthorn and 0.05-0.5% of dried liquorice. The roselle beverage is prepared through the following processes of: mixing, boiling, filtering, sterilizing, canning and sealing. The roselle of the invention contains more hibiscus acid and roselle saponins which not only have antioxidant and health care effects for eliminating free radicals and keeping youth, but also have physiological functions of lipid-lowering and anti-aging or the like. By utilizingthe roselle beverage disclosed by the invention, the medicinal effects of roselle are given into full play, and the effects of the roselle for removing radicals, skin care and keeping youth are enhanced. The roselle beverage has the advantages of easily available raw materials, simple process, convenience in drinking, no toxic or side effect, and the like.
Owner:NANCHANG UNIV
Digital finger print generating and tracking method
InactiveCN101276407AShorten the lengthResistance to sudden errorsCharacter and pattern recognitionThree levelComputer hardware
The invention discloses a digital fingerprint generating and tracking algorithm. The digital fingerprint generating method comprises constructing fingerprint codeword via three-level cascaded encoding means, namely using anti-collusion code as inner code to construct characteristic fingerprint code at first, then using error-correcting code as outer code to construct unit fingerprint code, finally serially connecting a plurality of unit fingerprint codes to construct joint fingerprint code; the digital fingerprint tracking method comprises using soft-judge tracking means to judge whether the user participates the collusion, namely carrying out quantization calculation on the user collusion-participating degree, and judging the collusion user according to the user collusion-participating degree. The invention is suitable for being embedded in digital copyright protection of digital works with small capacity, also capable of being applied in protection of pay-data under circumstances such as digital TV, digital broadcast, VOD, DVB, etc.
Owner:WUHAN UNIV
Citionella oil mosquito-repelling liquid as well as mosquito-repelling summer sleeping mat and preparation method thereof
ActiveCN103651634AMosquito repellent quicklyStrong attack abilityBiocidePest repellentsOrganic solventDEET
The invention discloses citionella oil mosquito-repelling liquid as well as a mosquito-repelling summer sleeping mat and a preparation method of the mosquito-repelling summer sleeping mat. The citionella oil mosquito-repelling liquid is composed of following components in parts by weight: 8-16 parts of deet, 3-5 parts of pyriproxyfen, 2-4 parts of citionella oil, 10-20 parts of an emulsifying agent and 60-90 parts of an organic solvent. The mosquito-repelling summer sleeping mat is prepared by a method comprising the following steps: (1) diluting the citionella oil mosquito-repelling liquid for 20-60 times to form a dip dyeing solution; and (2) immersing a summer sleeping mat into the dip dyeing solution and drying to prepare the mosquito-repelling summer sleeping mat. The citionella oil mosquito-repelling liquid provided by the invention is safe to human and livestock, is less prone to generate drug resistance and is easy to degrade in a natural environment; the prepared mosquito-repelling summer sleeping mat has strong capability of repelling the invasion of insects including mosquitoes and the like, and has a lasting mosquito-repelling effect.
Owner:阜阳创启工艺品有限公司
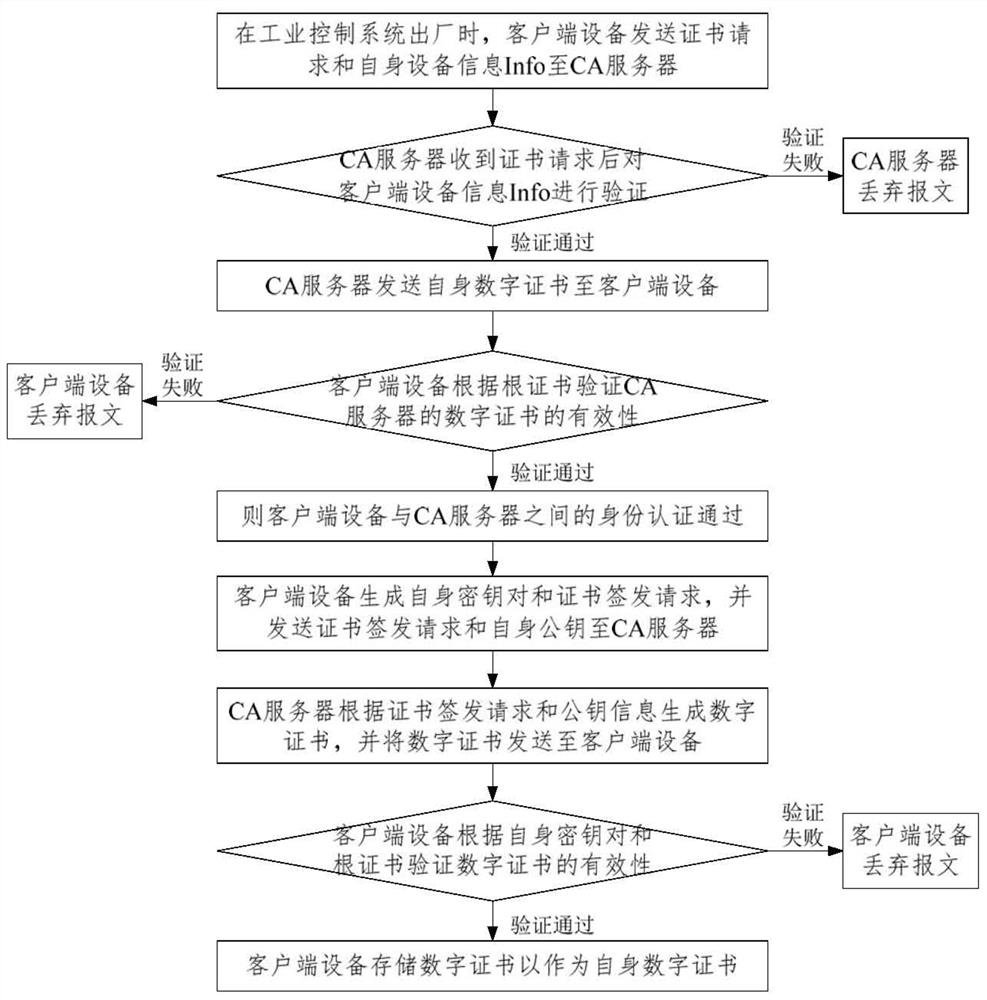
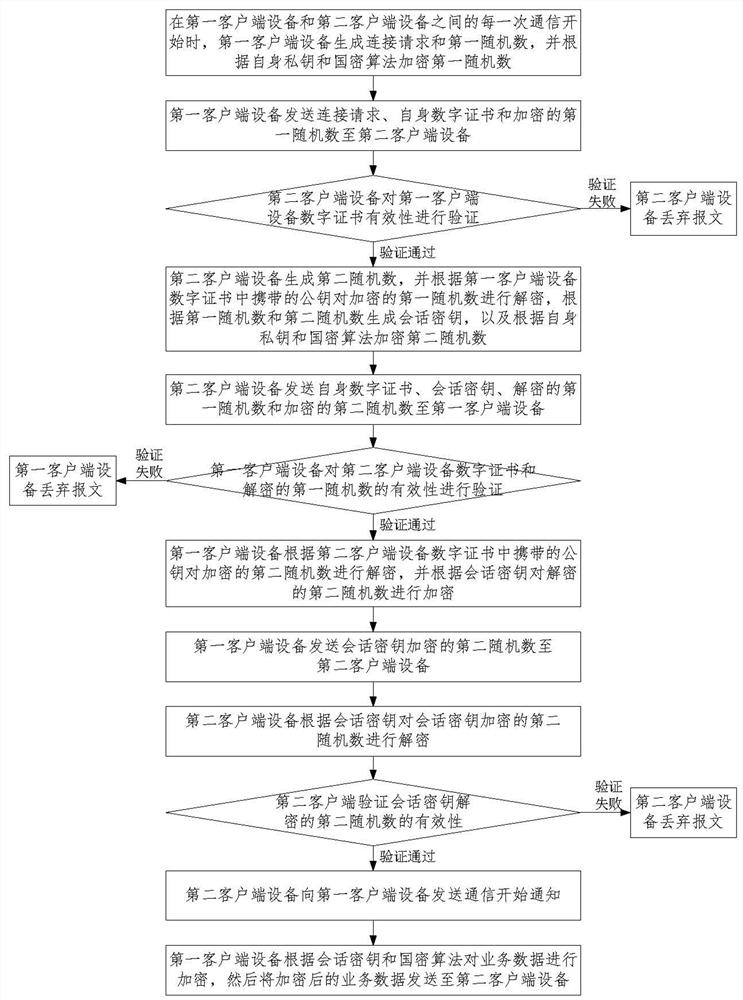
Digital certificate issuing management method for industrial control system and encryption communication method for industrial control system
InactiveCN112350826AImprove communication securityEfficient managementKey distribution for secure communicationUser identity/authority verificationCommunications securityRoot certificate
The invention provides a digital certificate issuing management method for an industrial control system, which realizes digital certificate issuing and management of an engineer station, a controllerand an operator station in the industrial control system on the basis of a certificate management system of public key infrastructure (PKI) in combination with network environment characteristics of the industrial control system. The invention also provides an encryption communication method for the industrial control system and the method comprises the steps: carrying out identity authenticationand dynamic secret key negotiation between first client equipment and second client equipment based on the digital certificates of the two communication sides, a root certificate of a CA server and acryptographic algorithm when each communication between first client equipment and second client equipment starts; and if identity authentication is passed, performing encrypted communication betweenthe first client equipment and the second client equipment according to the session key obtained after the national cryptographic algorithm and the key negotiation. The communication security of the whole industrial control system is improved, and the risk that the communication is hijacked or maliciously tampered is effectively reduced.
Owner:ZHEJIANG SUPCON TECH
Image encryption method for hyper-chaotic pseudo-random sequence
ActiveCN110519037AGenerating method is simple and flexibleBig spaceEncryption apparatus with shift registers/memoriesSecuring communication by chaotic signalsPattern recognitionChaotic
The invention discloses an image encryption method for a hyper-chaotic pseudo-random sequence, and the method comprises the steps: firstly selecting a fourth-order hyper-chaotic Chen system, generating the hyper-chaotic pseudo-random sequence, and enabling an initial value of the hyper-chaotic pseudo-random sequence to serve as a secret key; secondly, preprocessing the image, defining the row-column transformation relation of the image, further disturbing the row and column of the image, and determining parameters of the row-column transformation relation dynamically by a hyperchaotic pseudo-random sequence; defining the transformation relation of the image pixel values again, wherein the parameters of the transformation relation are dynamically determined by the hyper-chaotic pseudo-random sequence; and finally, encrypting the transformed image to obtain an encrypted image. According to the invention, a pseudorandom sequence with better initial sensitivity, randomness, stability, autocorrelation and other characteristics can be flexibly and conveniently generated, so that a better secret key is obtained; and the positions and pixel values of the image pixels are dynamically disturbed, so that the correlation of the image is further reduced, the secrecy effect is further improved, the higher requirement of a user on image encryption can be met, and the practicability is higher.
Owner:JIANGSU UNIV OF TECH
Composite drill bit
InactiveCN106121541AWide operating parameter spaceEasy to controlDrill bitsConstructionsTorsional vibrationIgneous rock
The invention relates to the technical field of petroleum drilling and well cementation, in particular to a composite drill bit which comprises a PDC drill bit body and roller cones. The roller cones are installed on the PDC drill bit body. The roller cone and PDC composite drill bit is composed of the roller cones and PDC, the advantages of roller cone drill bits and PDC drill bits are combined, the aggressivity is high, the cutting efficiency is high, the mechanical drilling speed of the composite drill bit is 2-4 times higher than the roller cone drill bits when the composite drill bit operates on poor-drillability stratums (such as igneous rock and mud and sand interbeddings containing gravels), and the mechanical drilling speed and the rotation speed are in direct proportion. When a motor is adopted by the roller cone and PDC composite drill bit for drilling, the mechanical drilling speed is increased remarkably. Another advantage is reflected in the influences of the roller cones on drill bit dynamics, compared with the conventional PDC drill bits, the torque fluctuation degree can be reduced by as much as 50%, the torsional vibration degree is lowered under the low rotation speed condition, and the whirling vibration degree is lowered under the high rotation speed condition.
Owner:TIANJIN LILIN BIT
Intelligent confrontation sample generation method and system based on optimization algorithm and invariance
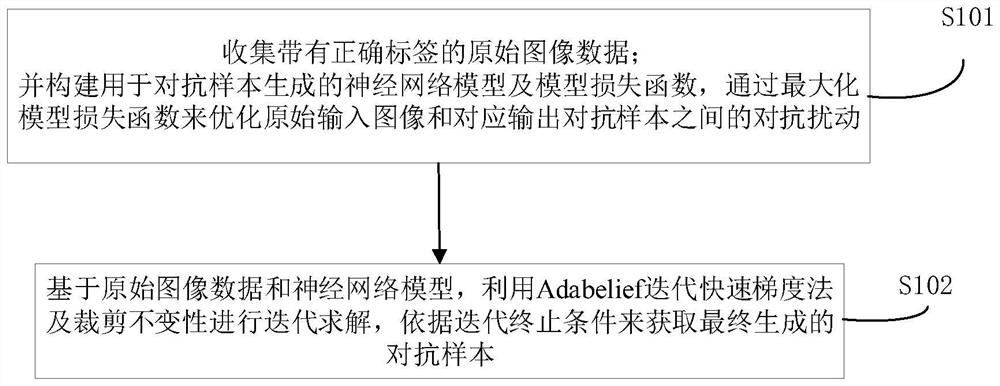
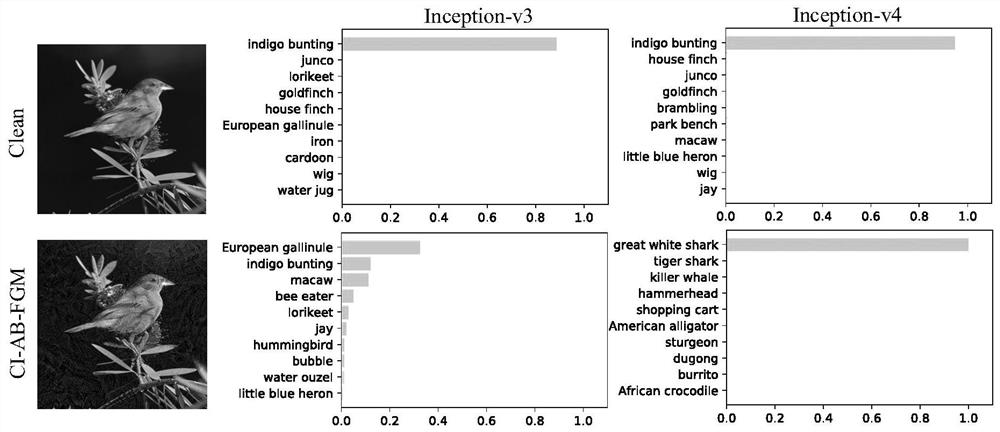
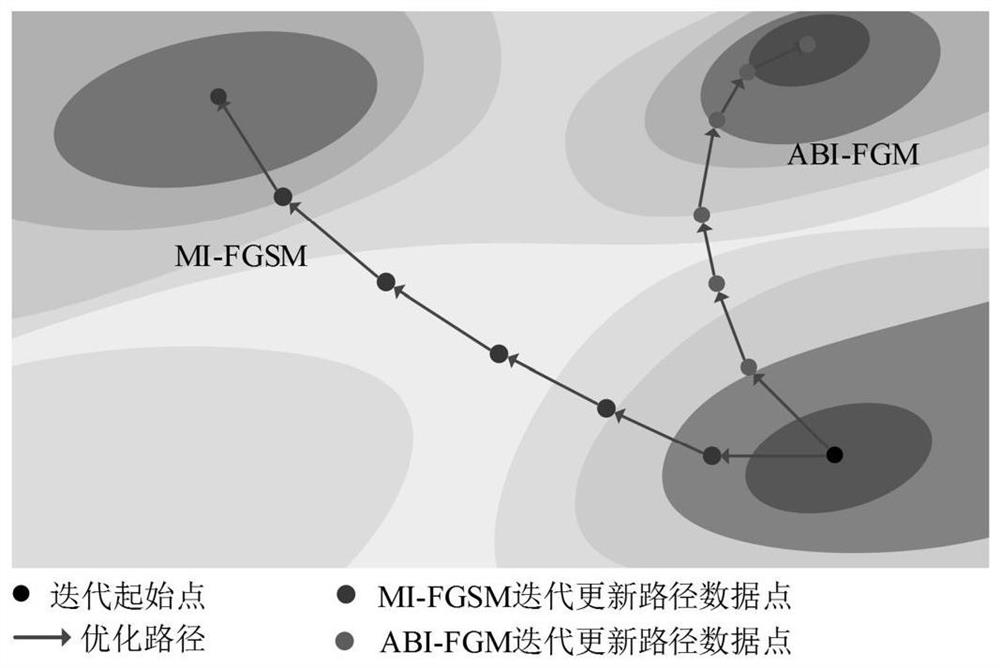
PendingCN114066912AImprove portabilityImprove the build processImage enhancementImage analysisNetwork modelEngineering
The invention belongs to the technical field of image recognition data processing, and particularly relates to an intelligent adversarial sample generation method and system based on an optimization algorithm and invariance. The method comprises the steps: collecting original image data with a correct label; constructing a neural network model for adversarial sample generation and a model loss function, and optimizing adversarial disturbance between an original input image and a corresponding output adversarial sample by maximizing the model loss function; based on original image data and a neural network model, an Adazief iterative quick gradient method and a cutting invariance method are used for iterative solution, and a finally generated adversarial sample is obtained according to an iteration termination condition. From the perspective that the generation process of the adversarial sample is similar to the neural network training process, the convergence process is optimized through the Adazief iteration quick gradient method, the over-fitting phenomenon in the adversarial attack is avoided by using the cutting invariance, the adversarial sample with better mobility can be generated, the robustness of the network model is improved, and the practical scene application is facilitated.
Owner:PLA STRATEGIC SUPPORT FORCE INFORMATION ENG UNIV PLA SSF IEU
Sophoramine insect-preventing missible oil, sophoramine insect-preventing fabric and preparation method of fabric
The invention discloses sophoramine insect-preventing missible oil, a sophoramine insect-preventing fabric and a preparation method of the sophoramine insect-preventing fabric. The sophoramine insect-preventing missible oil comprises the following components in percentage by weight: 5%-15% of pyrethroid, 2%-4% of sophoramine, 8%-15% of an emulsifying agent, and the balance of an organic solvent. The preparation method of the sophoramine insect-preventing fabric comprises the following steps of: (1) diluting the sophoramine insect-preventing missible oil for 50-100 times by water so as to form dip dyeing liquor; and (2) dip-dyeing a fabric in the dip dyeing liquor, spin-drying, washing by water, spin-drying for the second time, and setting, thus obtaining the insect-preventing fabric. A biological source is added to the sophoramine insect-preventing missible oil for achieving the synergistic interaction with pyrethroid, and the sophoramine insect-preventing fabric prepared by the preparation method has strong capacity of resisting invasion of insects such as mosquitoes and has a lasting mosquito preventing effect.
Owner:SHANGHAI GONGTAI TEXTILE PROD
Countermeasure defense method for countermeasure attacks based on artificial immune algorithm
ActiveCN111598210AIncrease diversityEasy to adjustInternal combustion piston enginesCharacter and pattern recognitionAlgorithmArtificial immune algorithm
The invention discloses a confrontation defense method for confrontation attack based on an artificial immune algorithm. The method comprises the following steps: (1) obtaining an original picture sample set; based on the original picture sample, generating an adversarial sample based on an artificial immune algorithm; merging the original picture sample and the adversarial sample, and dividing into a training set and a test set; (2) training a picture classifier by using the training set and the test set to obtain a picture recognition model; and (3) identifying the to-be-identified picture by utilizing the picture identification model to realize confrontation and defense of picture identification. According to the invention, the technical problems of poor defense effect and low classifier identification accuracy in the prior art when attacks are resisted based on an artificial immune algorithm can be solved.
Owner:ZHEJIANG UNIV OF TECH
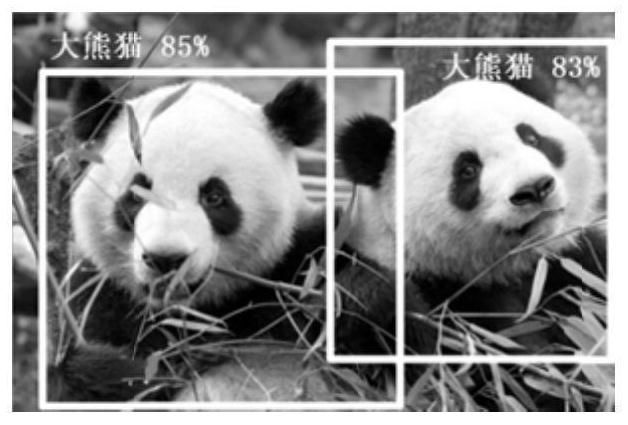
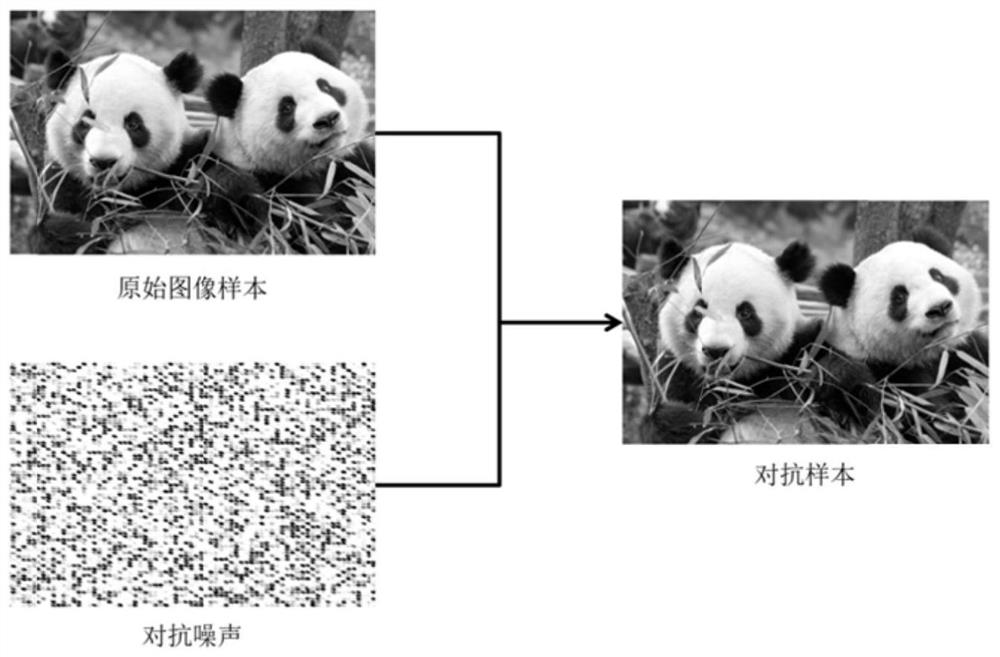
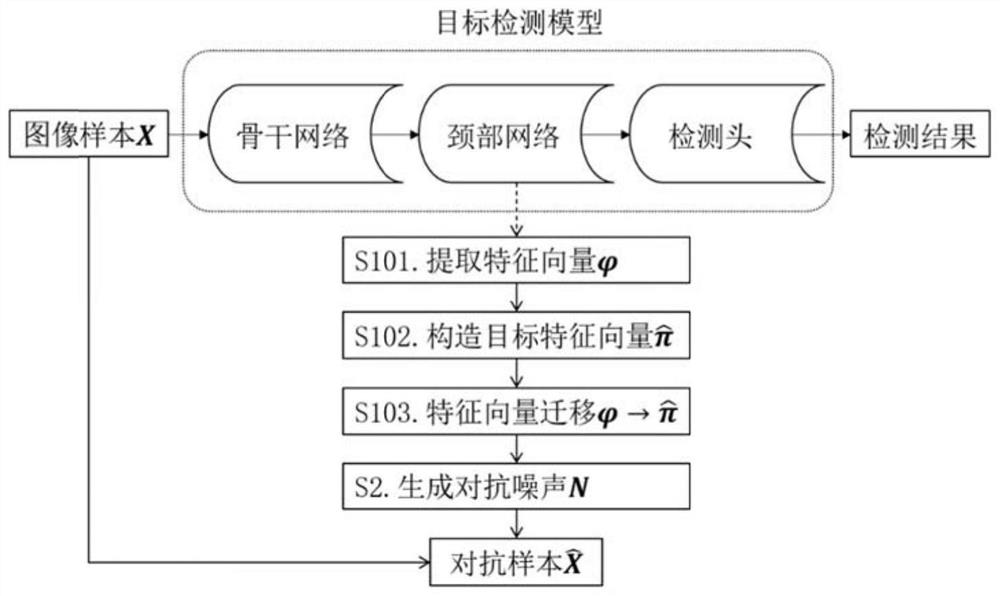
Adversarial sample generation method based on target detection model feature vector migration
PendingCN114549933AImprove attack abilityImprove portabilityCharacter and pattern recognitionNeural architecturesFeature vectorAlgorithm
The invention discloses an adversarial sample generation method based on target detection model feature vector migration. The adversarial sample generation method comprises the following steps of S1, convolutional neural network feature vector migration; step S2, generating adversarial noise; and step S3, evaluating an adversarial sample attack effect. According to the method, the attack effect of the confrontation sample in deep learning models such as target detection is stronger, and better mobility is achieved on the premise that attack concealment is considered. The adversarial sample generation method disclosed by the invention reveals the important role of the feature vector in the adversarial mechanism of the target detection model, verifies the attack threat of the adversarial sample disclosed by the invention, and can heuristically explore the research in the field of a robust target detection algorithm, so that a new defense mechanism is designed; and the method is of great significance to application of the target detection model in actual life.
Owner:NANJING UNIV
Anti-insect fabric
InactiveCN102476486AFeel goodImprove breathabilitySynthetic resin layered productsHigh resistanceEngineering
The invention discloses an anti-insect fabric, which consists of a lining layer made of natural fibers or artificial fibers, a face layer made of synthetic fiber multifilaments, and a lapping layer arranged between the lining layer and the face layer and made of polypropylene or polyethylene fiber monofilaments. The lining layer, the face layer and the lapping layer all contain pesticide components. The fibers adopted in the invention all can be recycled for jet-spinning again at low cost, and the processed fabric has good hand-feeling. The inventive anti-insect fabric has good air permeability, high resistance against insects such as mosquito, and long lasting anti-insect effects.
Owner:WUJIANG HUAHUANG PRINTING PROD
Quick enciphering method and device for wavelet image
InactiveCN1527249AStrong attack abilitySmall amount of calculation2D-image generationImage codingInformation transmissionHigh frequency
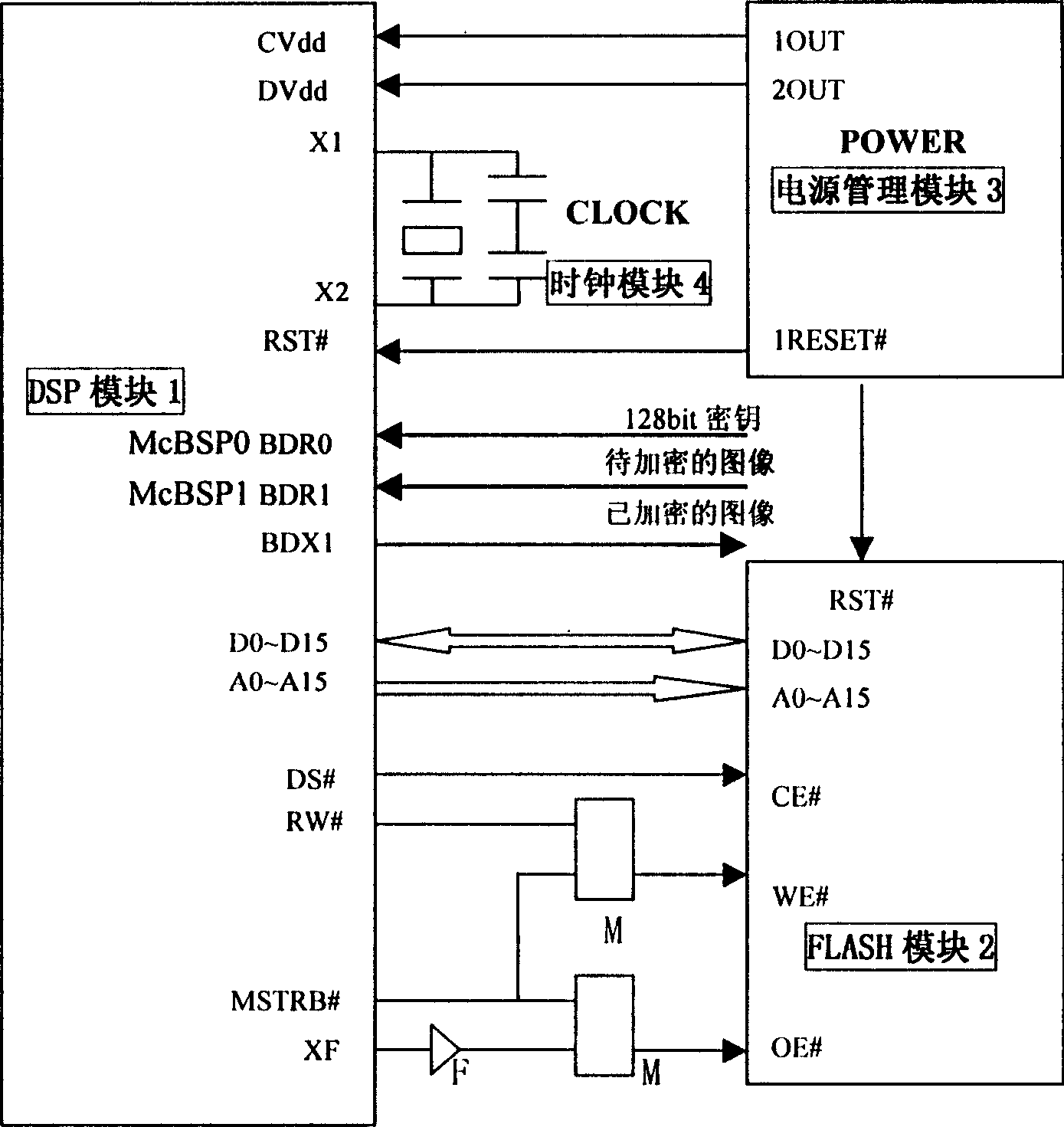
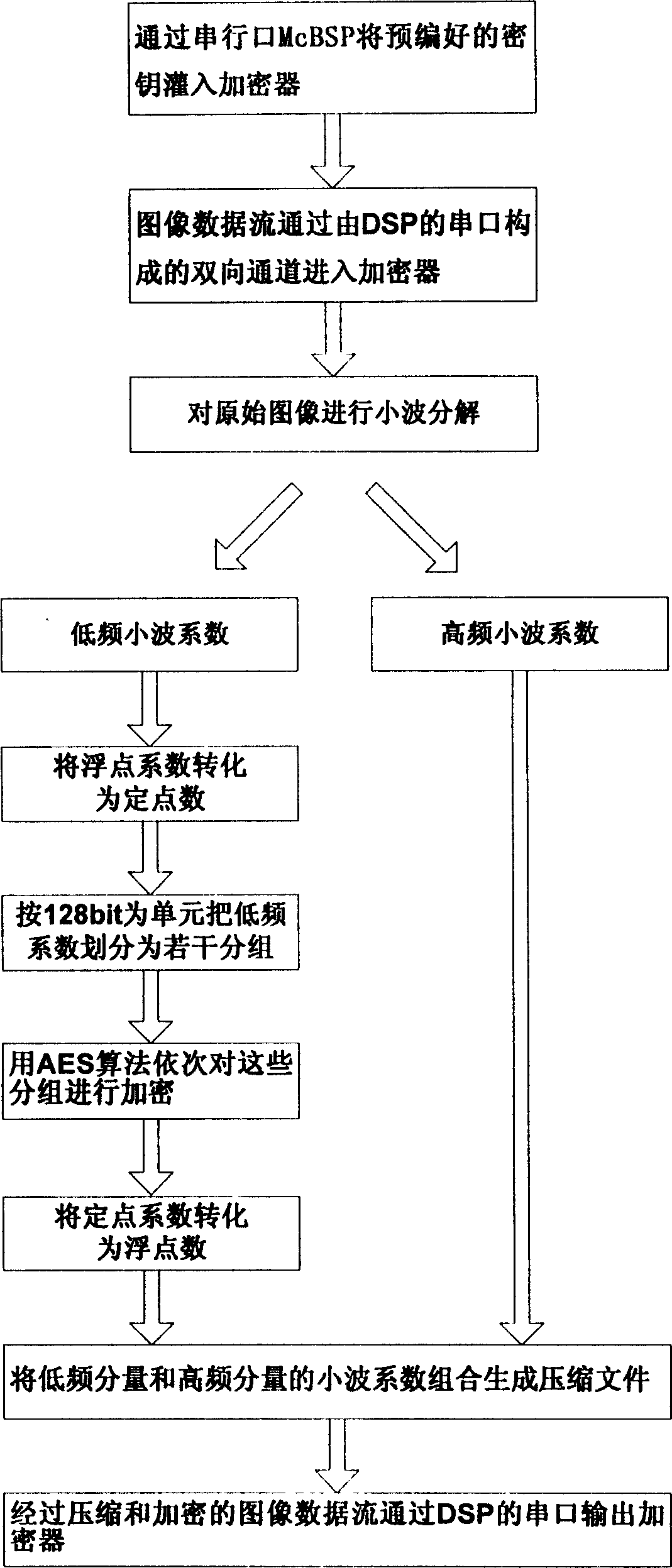
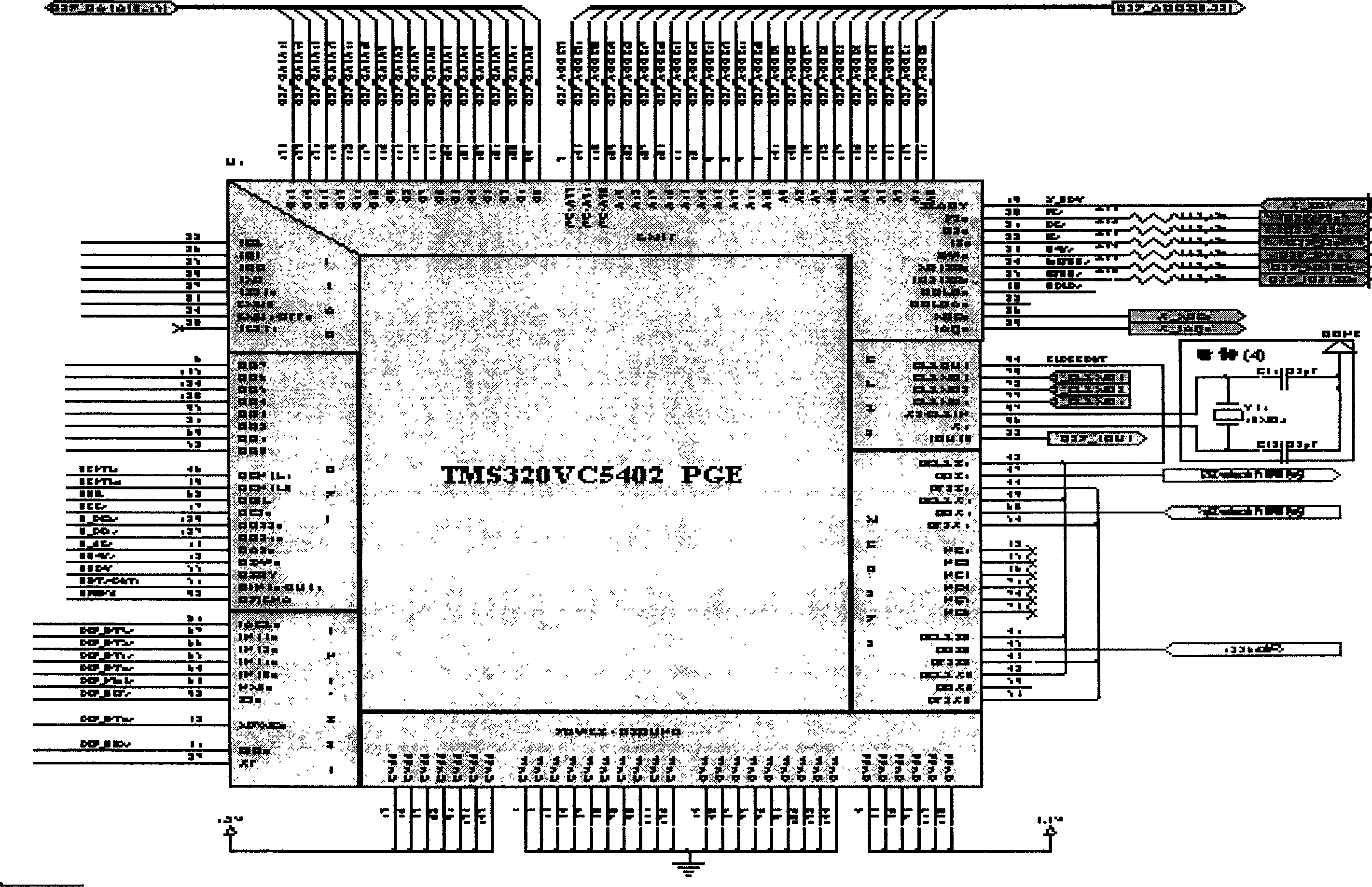
The present invention relates to method and device for safe information transmission. The quick enciphering device consists of DSP module, FLASH module, power supply managing module and clock module. The enciphering method includes: feeding pre-programmed cipher key via serial port to the enciphering device; feeding the image data flow to the enciphering device via the two-way channel comprising DSP serial port; analyzing the image into LF component and HF detail component; converting the wavelet coefficient of the LF component from floating point number into fixed point number; dividing the wavelet coefficient of the LF component into sub-groups of 128 bit; enciphering the sub-groups successively in AES algorithm; converting the wavelet coefficient of the LF component from fixed point number to floating point number; combining the wavelet coefficient of LF component and HF component to form compressed image file; and outputting the image data flow via the DSP serial port.
Owner:NANJING UNIV OF POSTS & TELECOMM
Oral liquid for treating cancers and preparation method thereof
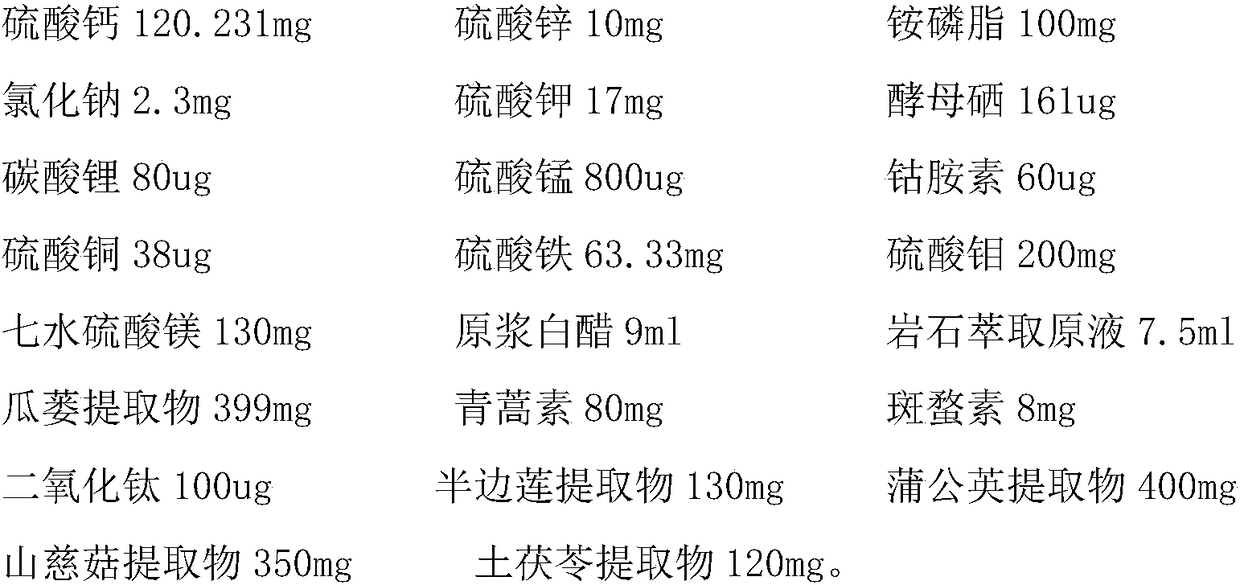
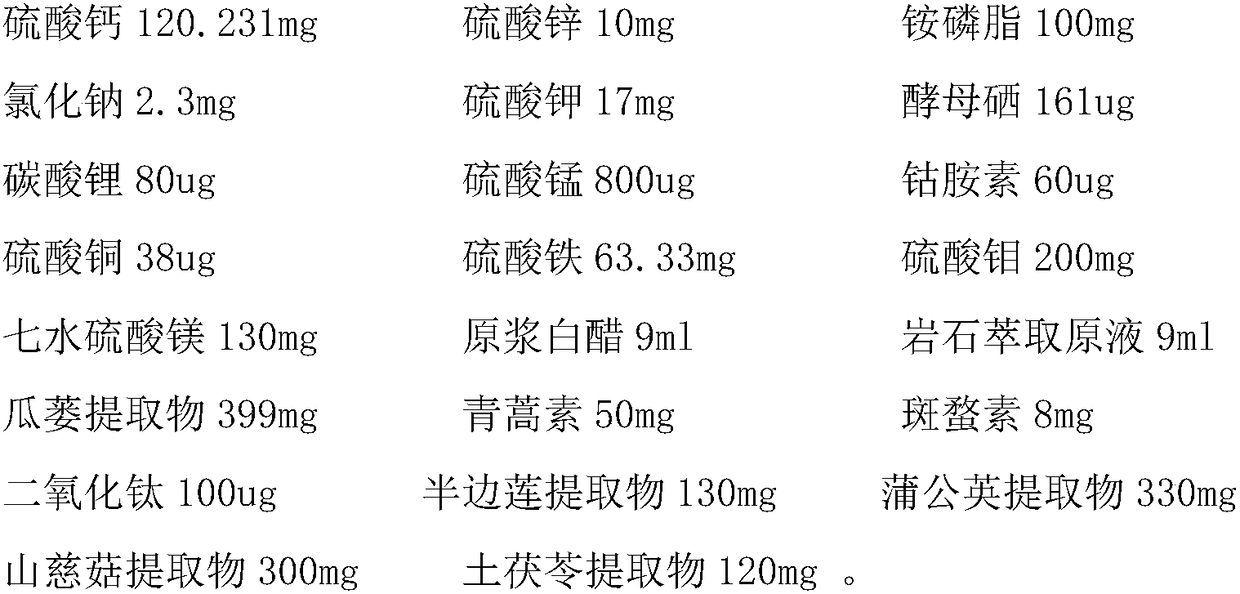
InactiveCN108310287AGreat tasteIncrease acidityHeavy metal active ingredientsInorganic boron active ingredientsCobalaminChemistry
The invention provides oral liquid for treating cancers and a preparation method thereof. The oral liquid is prepared from the raw materials in parts by weight: calcium sulfate, zinc sulfate, ammoniumphosphatide, sodium chloride, potassium sulfate, selenium yeast, lithium carbonate, manganese sulfate, cobalamin, copper sulfate, ferric sulfate, molybdenum trisulfate, magnesium sulfate heptahydrate, raw white vinegar, rock extraction original liquid, a fructus trichosanthis extract, artemisinin, cantharidin, titanium dioxide, a herba lobeliae chinensis extract, a herba taraxaci extract, a rhizoma pleionis extract, a rhizoma smilacis glabrae extract and the like. The oral liquid is mainly applied to the treatment of common tumors and cancers of digestive systems, respiratory systems, urogenital systems and the like, which have the highest pathogenesis rate, of human bodies.
Owner:深圳安轩堂生物科技有限公司
Fighting type top
ActiveCN104841135AImprove controllabilityImprove durabilityTopsToy gearsElectric machineryControl theory
The invention discloses a fighting type top. The fighting type top is characterized by comprising a top body, a motor and rolling wheels, wherein a rotating shaft of the motor and the rolling wheels are connected through a clutch transmission set; when the motor rotates in the first direction, the rolling wheels synchronously rotate in the opposite directions, so that rotation of the fighting type top is achieved; when the motor rotates in the second direction, the rolling wheels synchronously rotate in the same direction, so that movement of the fighting type top is achieved. Movement of the electric top can be achieved through control over rotation of the motor in the first direction or the second direction, a player can autonomously select to attack or avoid the opposite side in a fighting game, the interaction between the electric top and the player is effectively improved, and the technical level of the player can also be reflected; friction between the rolling wheels and the contact surface is rolling friction, the energy consumption of friction is lower, and therefore the persistence of rotation of the top is improved; in addition, due to the contact between the two rolling wheels and the contact surface, the stability of the top can be higher, the top can be more flexible, and the top cannot easily be inclined in a collision fighting process in the fighting game, and the fighting winning percentage is increased.
Owner:ALPHA GRP CO LTD +2
Biological source insect-preventing fabric and preparation method thereof
ActiveCN103374818AGood anti-mosquito effectStrong attack abilityBiocideFibre treatmentOrganic solventSpins
The invention discloses a biological source insect-preventing fabric and a preparation method thereof. The preparation method is characterized by comprising the following steps of: (1) diluting biological source insect-preventing missible oil for 50-100 times by water to form dip dyeing liquid; and (2) dip-dyeing a fabric in the dip dyeing liquid, spin-drying, washing by water, spin-drying for the second time, and setting, thus obtaining the insect-preventing fabric. The biological source insect-preventing missible oil comprises the following components in percentage by weight: 5%-15% of pyrethroid, 2%-4% of LeiTeng ketone, 8%-15% of an emulsifying agent, and the balance of an organic solvent. The biological source insect-preventing fabric prepared by the preparation method provided by the invention has strong capacity for resisting invasion of insects such as mosquitoes, and has a lasting effect for preventing mosquitoes.
Owner:广州市缔造亿百儿童用品有限公司
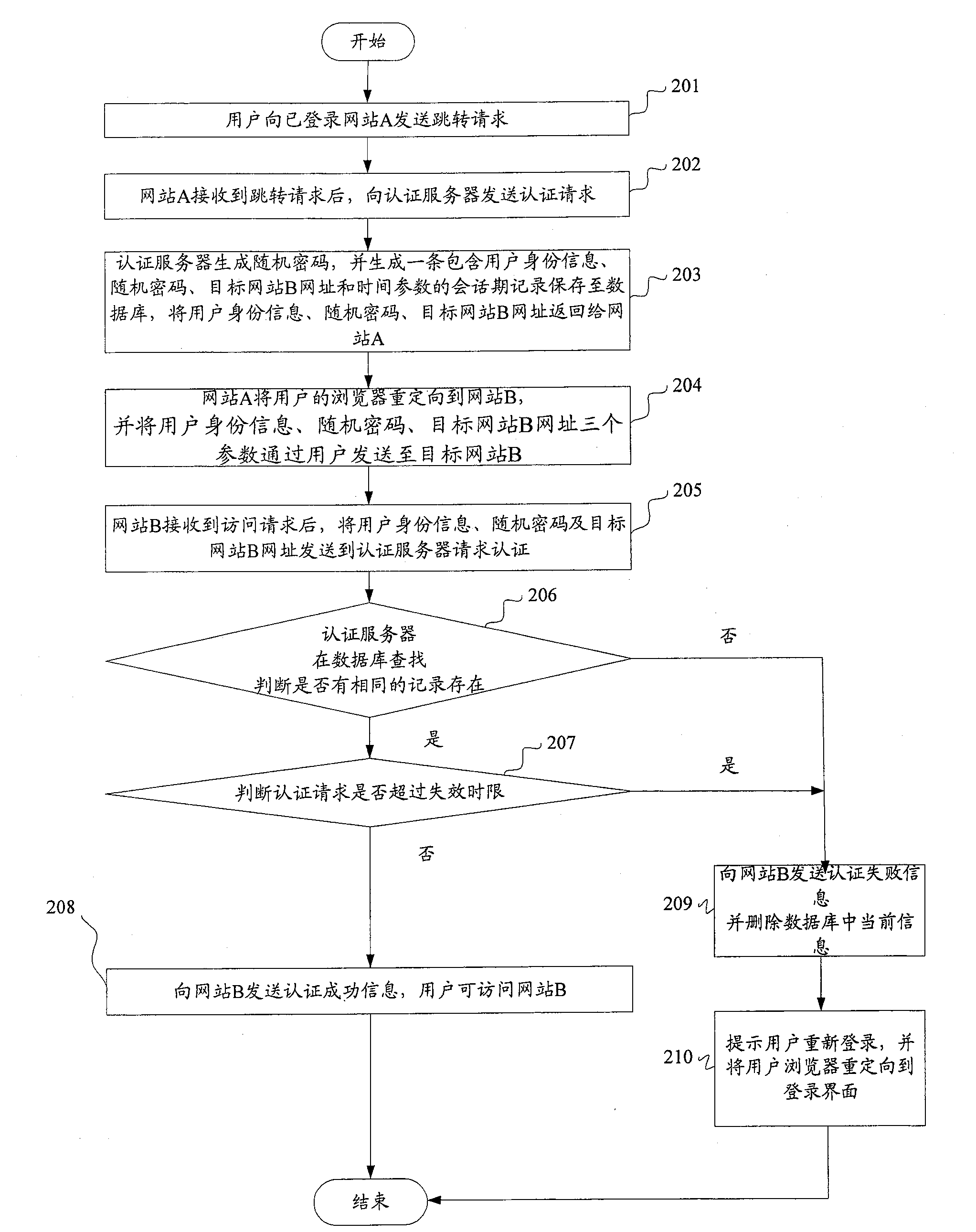
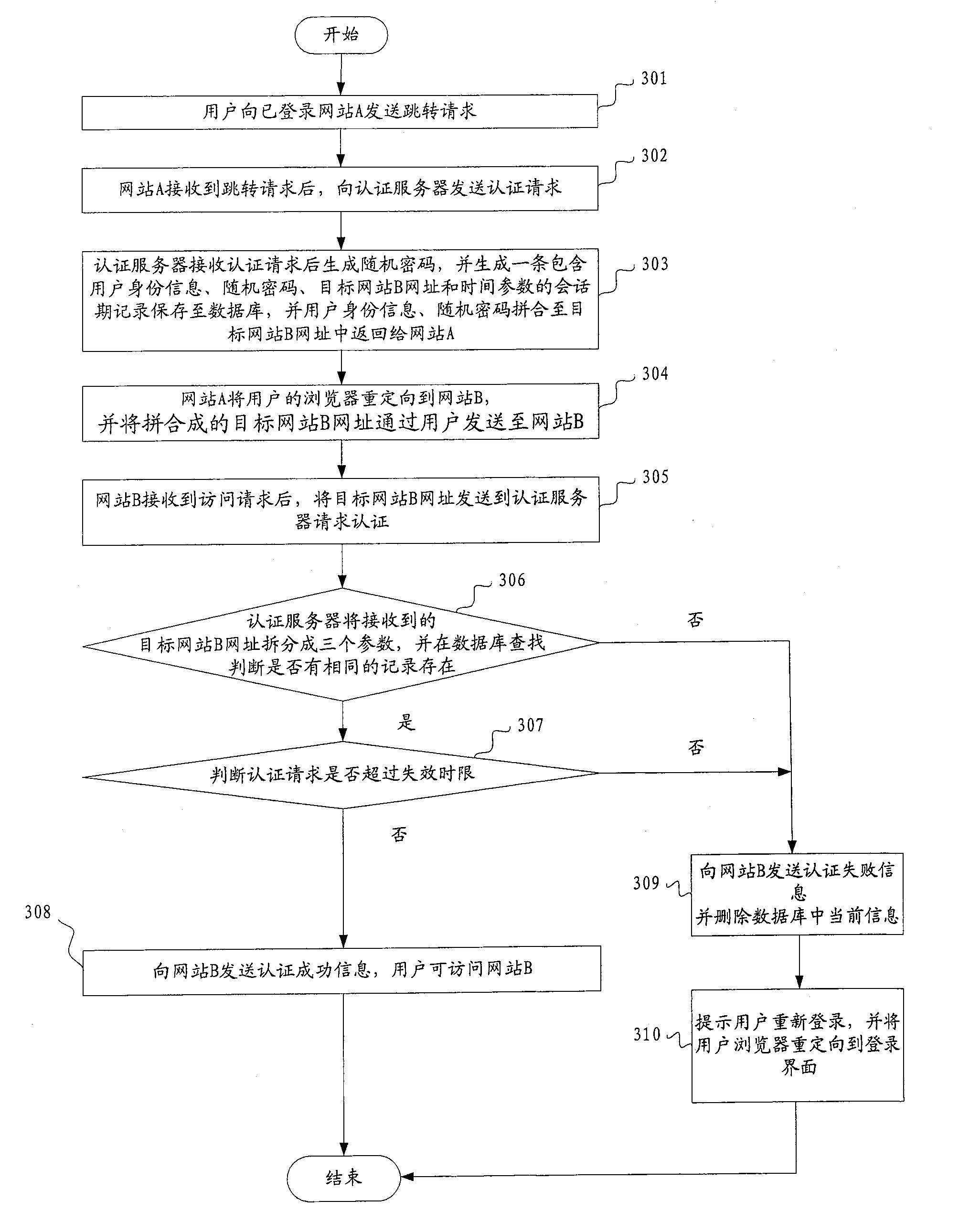
System and method for realizing single-point login
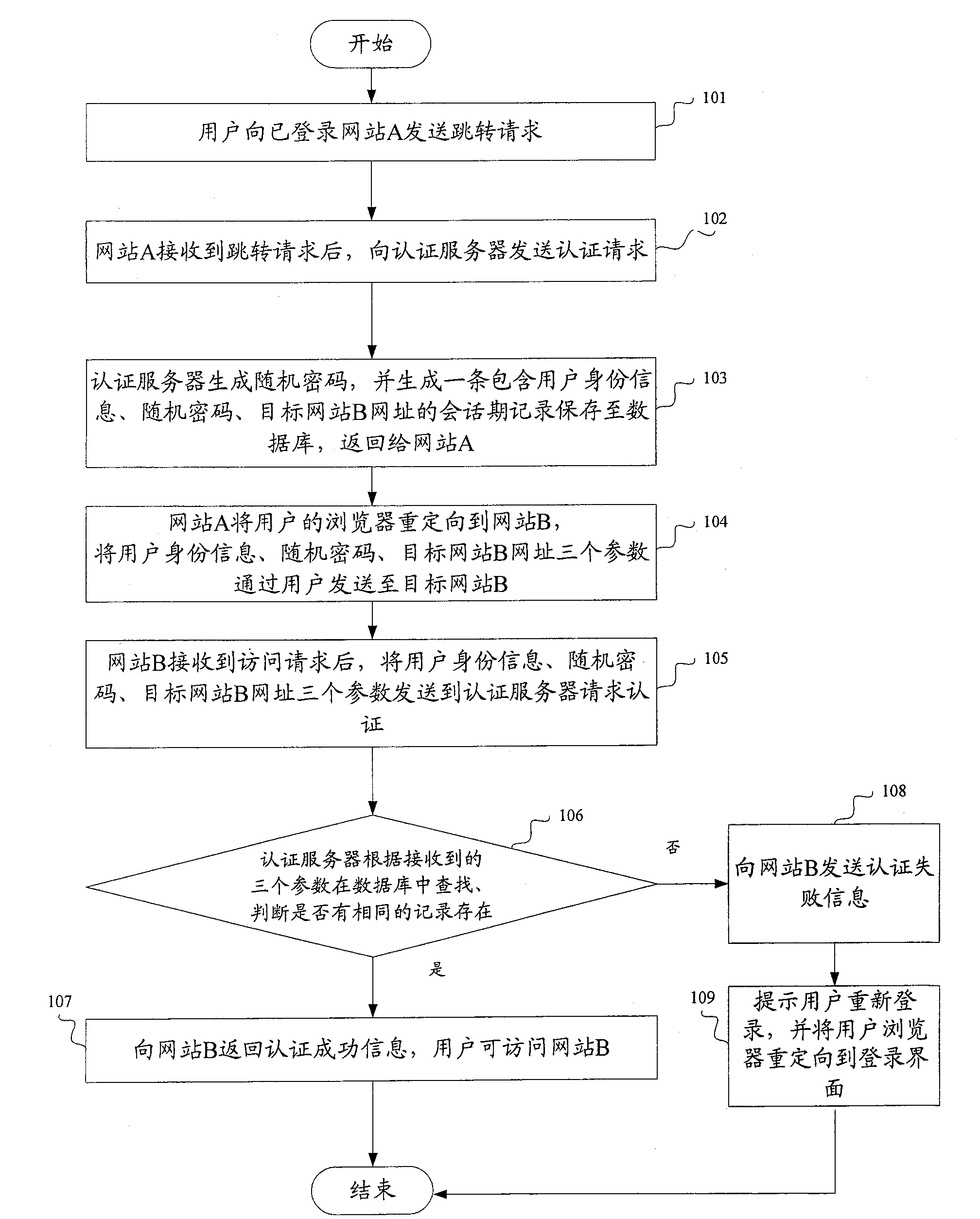
ActiveCN100586066CPrevent replaySmall modificationUser identity/authority verificationData switching by path configurationInternet privacyAuthentication server
The method comprises: user sends a jump request with its identification information and the website B address expected to login to the authentication server from a website A already logged in; the authentication server receives the jump request and generate a random cipher, and then generates the user ID information, random cipher and destination website B address, and then saves them; the user ID information, random cipher, destination website B address are returned to the website A; the website A redirects the user's browser to the destination website B, and transmits the user ID information, random cipher, and destination website B address to the authentication server through user and website B; the authentication server makes search to decide if there is a identical user's ID information, destination website B address and random cipher sent from the website B; if yes, then returning a successfully login sign to the website B, and permitting user login. The system thereof comprises: the website A already logged on and the website expected to log in.
Owner:BEIJING KINGSOFT SOFTWARE
Novel PDC drill bit with stable function
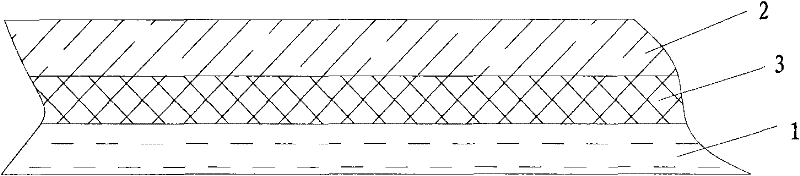
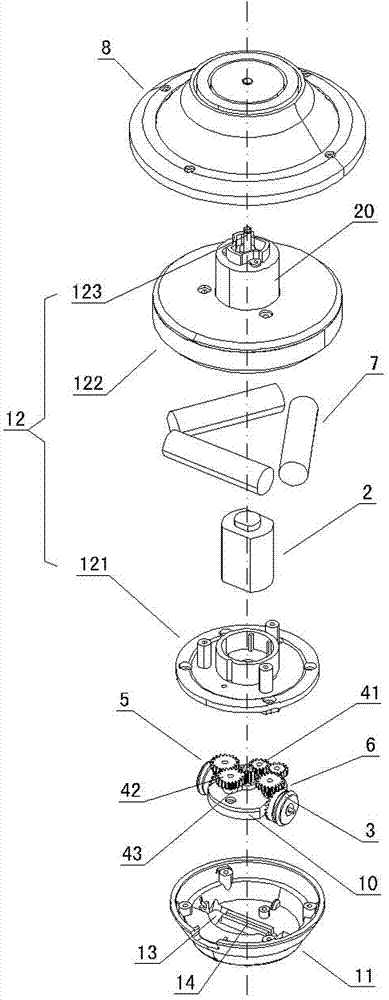
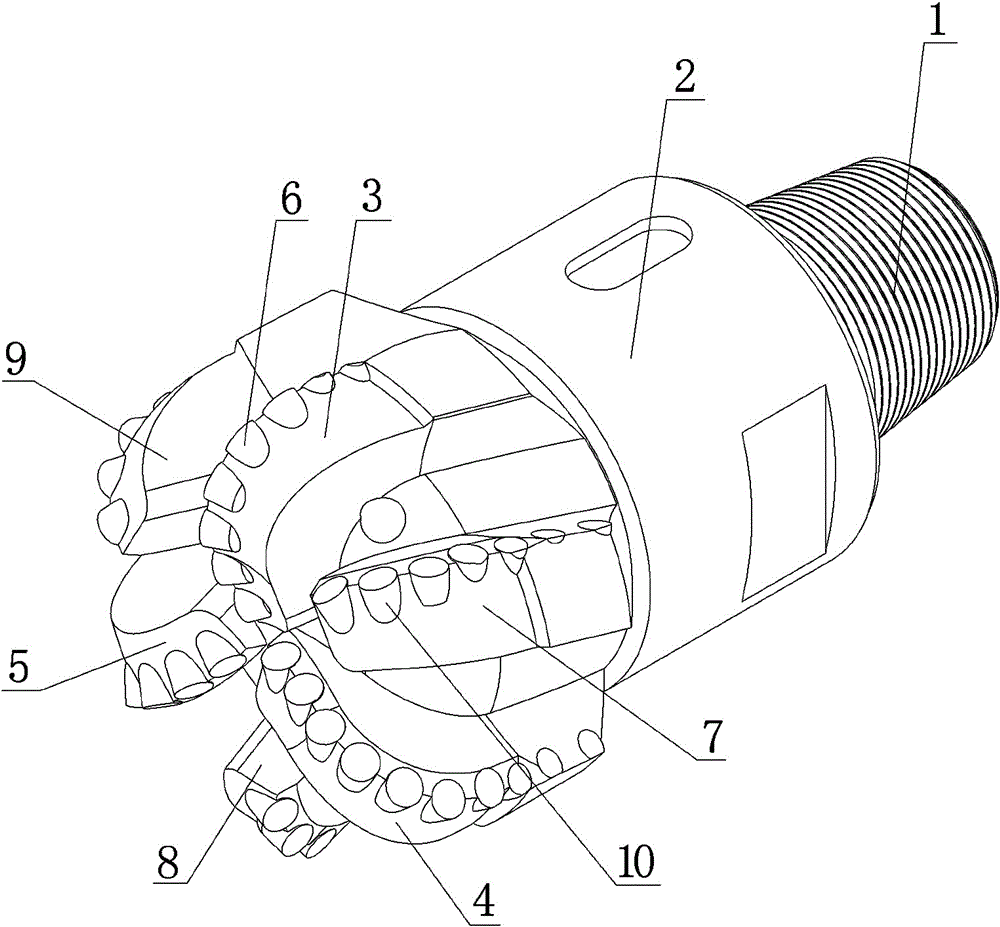
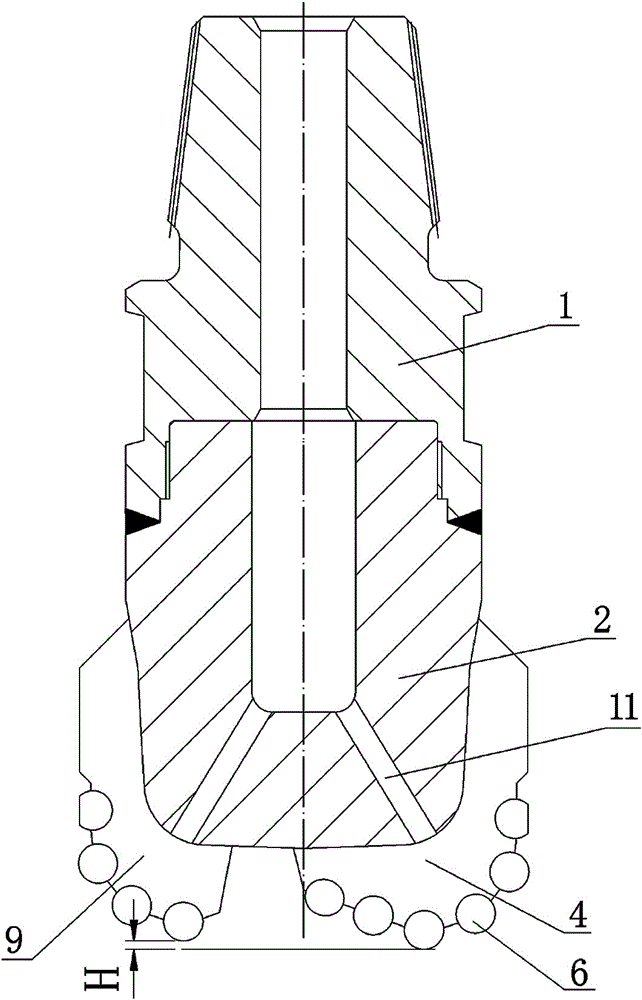
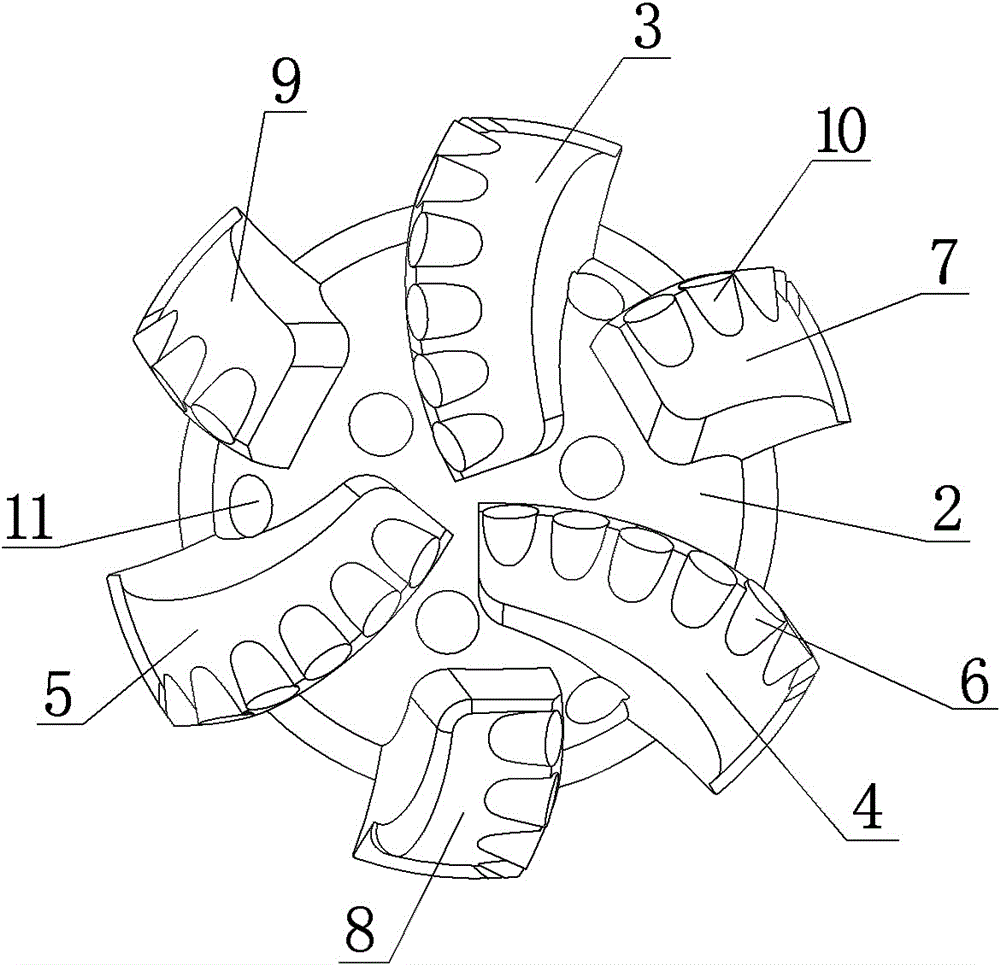
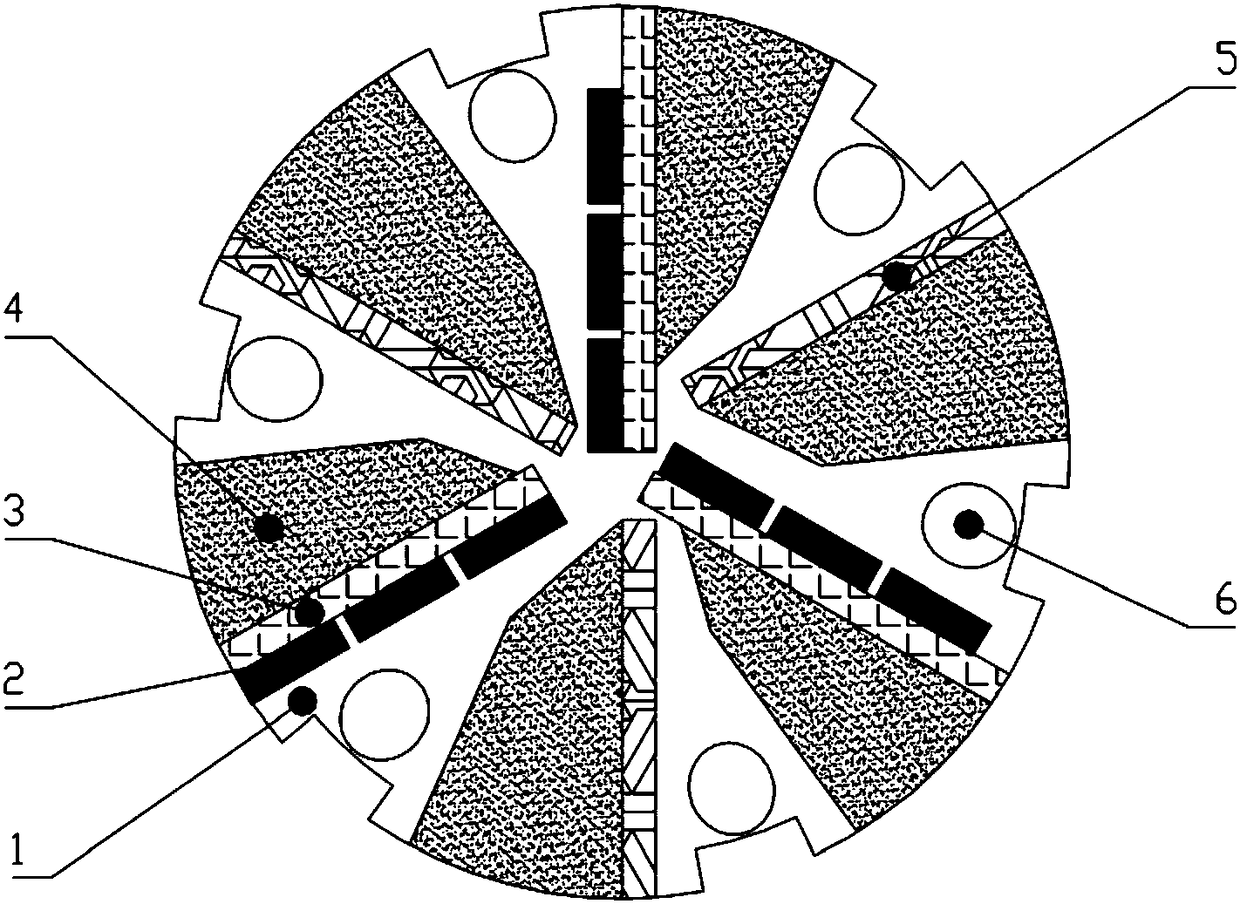
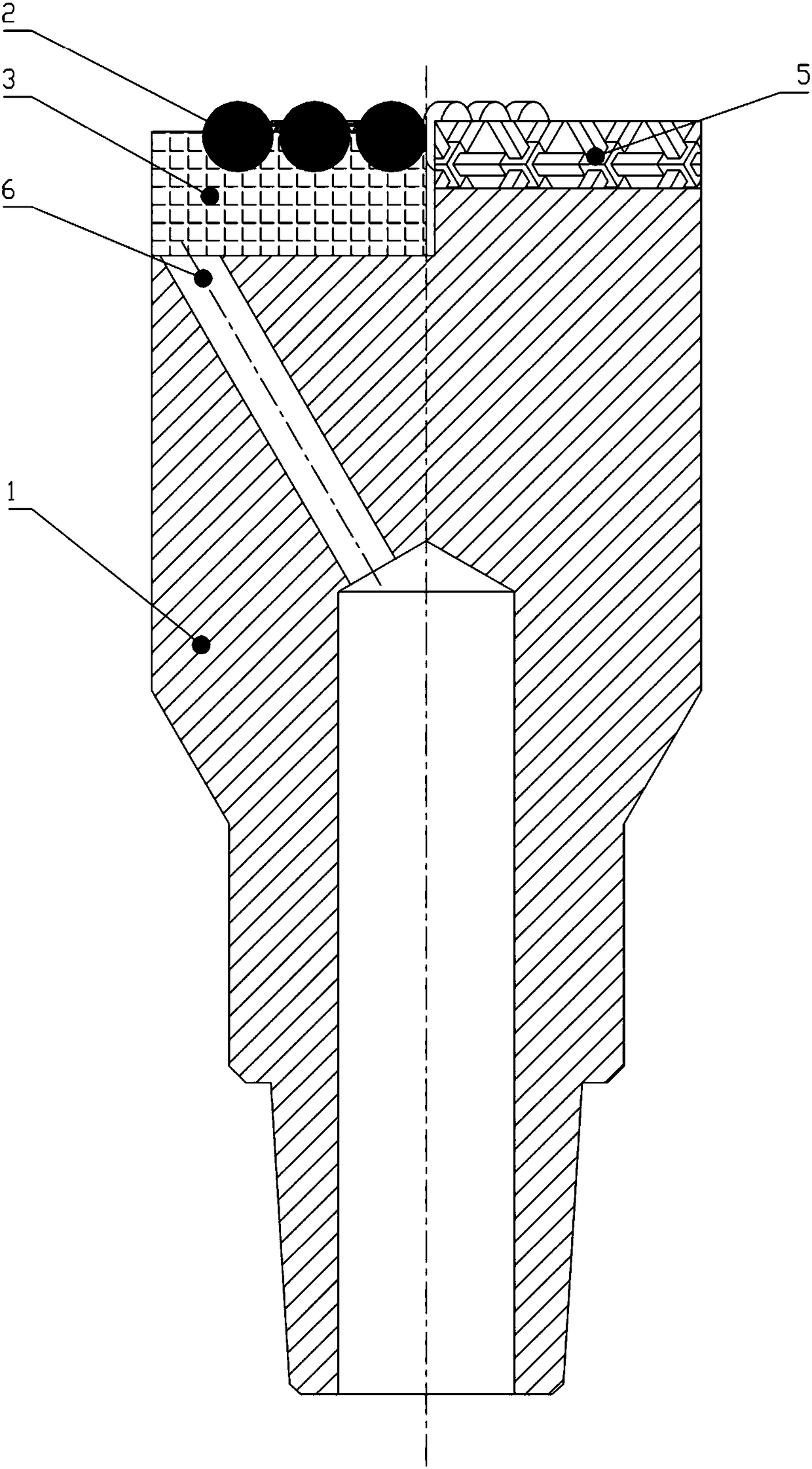
InactiveCN106050148AReduce sensitivityExtended service lifeDrill bitsConstructionsWell drillingPerpendicular distance
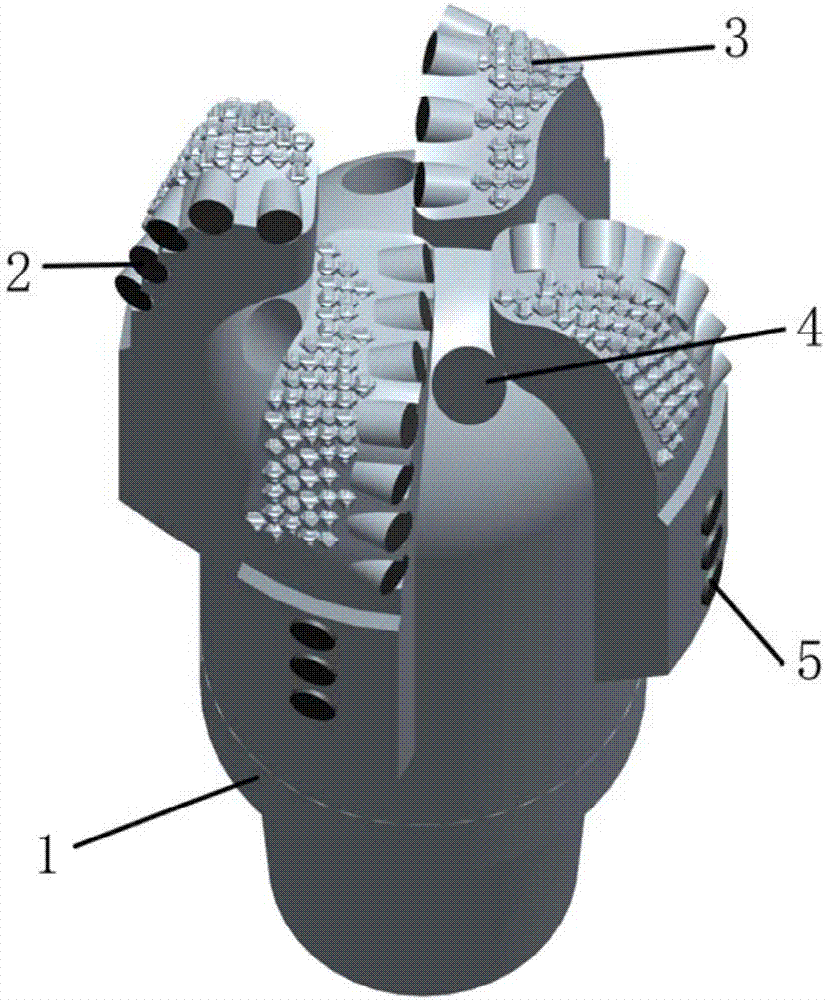
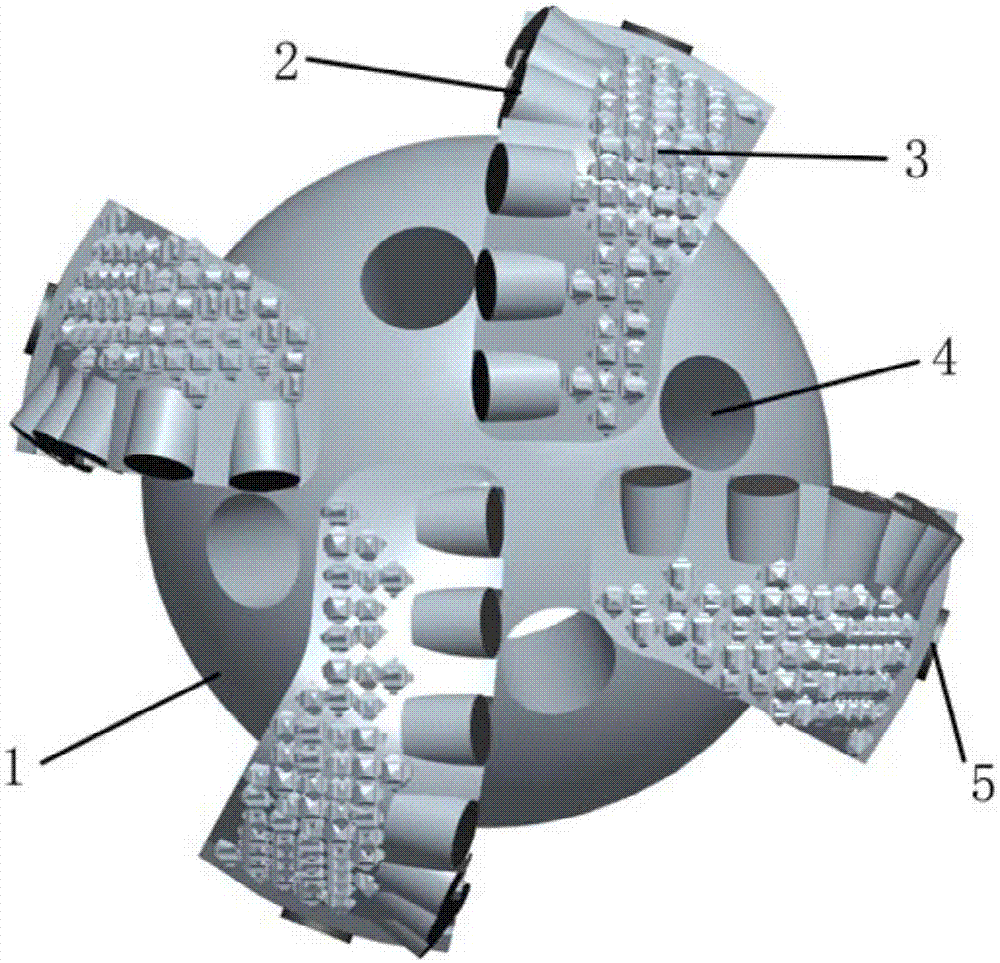
The invention discloses a novel ODC drill bit with a stale function. The novel ODC drill bit comprises a drill bit base body (1) and a drill bit crown (2) arranged on the drill bit base body (1). A main cutter wing A (3), a main cutter wing B (4) and a main cutter wing C (5) are arranged on the drill bit crown (2), a compound sheet is embedded in each cutting tooth I (6), cutting teeth II are distributed on an auxiliary cutter wing a (7), an auxiliary cutter wing b (8) and an auxiliary cutter wing c (9), the perpendicular distance between the cutter teeth I (6) at the lowermost ends of the main cutter wings and the cutting teeth II (10) at the lowermost ends of the auxiliary cutter wings is H, and H is smaller than 10 mm. The novel ODC drill bit has the advantages that the phenomena that when the requirements for a small number of cutter wings and a high mechanical drilling speed are met, insufficient support of a drill bit to the stratum occurs, the stability is poor, and deflection of a borehole and suppress jump in a soft and hard staggered stratum are likely to be caused are avoided; meanwhile, the rock breaking aggressiveness is improved, the rock braking speed is increased, the service life of the drill bit is prolonged, and the drilling cost is reduced.
Owner:四川保瑞特钻头有限公司
Mosquito-repelling emulsified oil as well as mosquito-repelling summer sleeping mat and preparation methods thereof
ActiveCN103651427AImprove mosquito repellent effectImprove attack abilityBiocidePest repellentsOrganic solventSophoramine
The invention discloses mosquito-repelling emulsified oil as well as a mosquito-repelling summer sleeping mat and preparation methods of the mosquito-repelling emulsified oil and the mosquito-repelling summer sleeping mat. The mosquito-repelling emulsified oil is composed of following components in percentage by weight: 5%-15% of deet, 2%-4% of sophoramine, 8%-15% of an emulsifying agent and the balance of an organic solvent. The mosquito-repelling summer sleeping mat is prepared by the following steps: (1) diluting the mosquito-repelling emulsified oil for 20-60 times to form a dip dyeing solution; and (2) immersing a summer sleeping mat into the dip dyeing solution and drying to prepare the mosquito-repelling summer sleeping mat. The mosquito-repelling emulsified oil provided by the invention is safe to human and livestock, is less prone to generate drug resistance and is easy to degrade in a natural environment; the prepared mosquito-repelling summer sleeping mat has strong capability of repelling the invasion of insects including mosquitoes and the like, and has a lasting mosquito-repelling effect.
Owner:安徽徽一通讯科技有限公司
Big data tracing method and system based on digital watermarking
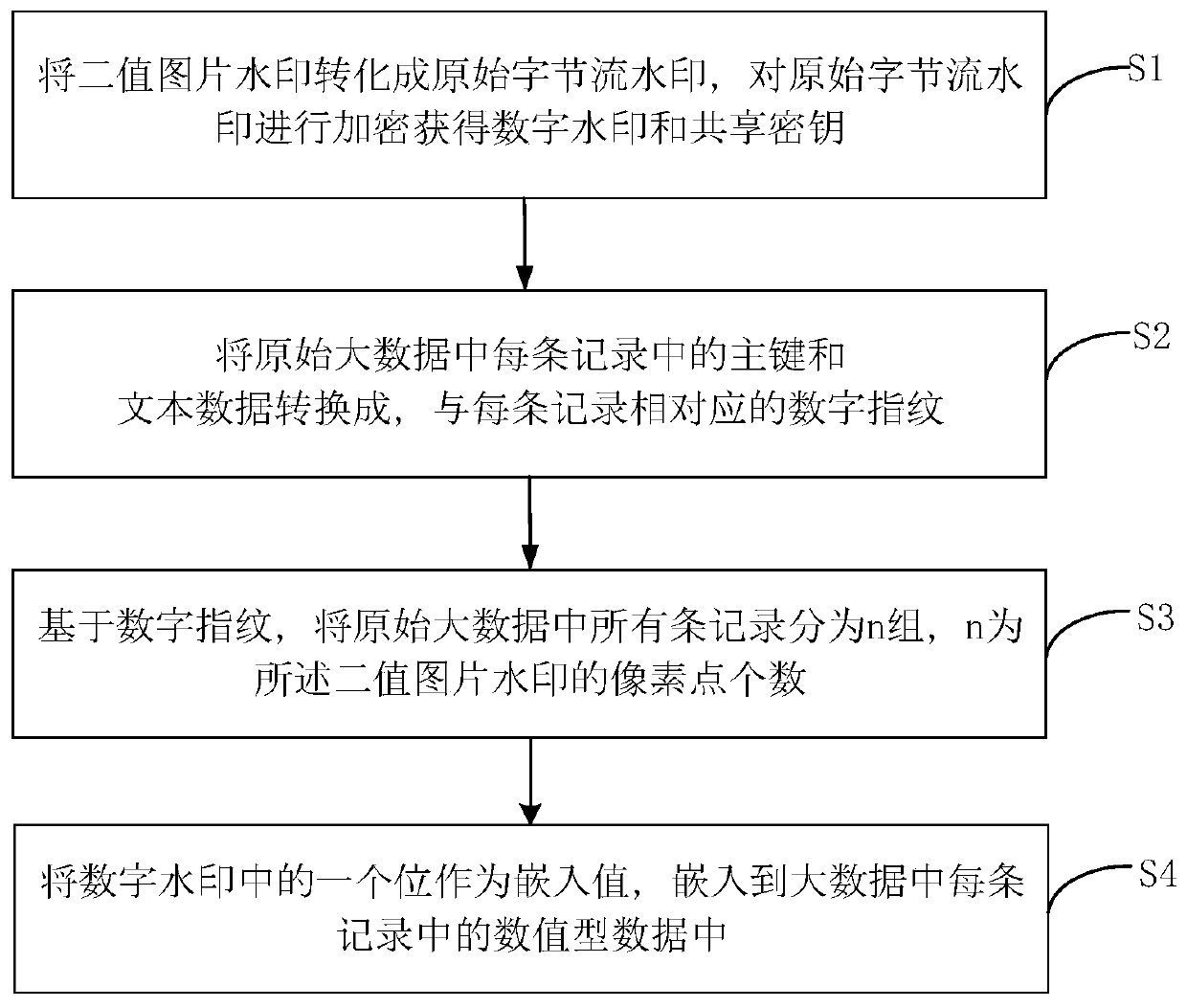
PendingCN110069907AImprove robustnessStrong anti-deletion attackDigital data protectionImage data processing detailsEmbedded valueNumeric data
The embodiment of the invention provides a big data tracing method and system, and the method comprises the steps: enabling a binary image watermark to be converted into an original byte flow watermark, and carrying out the encryption of the original byte flow watermark, and obtaining a digital watermark and a shared key; converting the primary key and the text data in each record in the originalbig data into digital fingerprints corresponding to each record; dividing all records in the original big data into n groups based on the digital fingerprint, n being the number of pixel points of thebinary image watermark, wherein each record and the digital fingerprint corresponding to each record correspond to one pixel in the binary image watermark, namely one bit in the digital watermark; and taking one bit in the digital watermark as an embedded value, and embedding the embedded value into numeric data in each record in the big data. The embodiment of the invention has the following advantages: the problems of poor algorithm robustness, poor deletion attack resistance, poor increase attack resistance and the like in the prior art are solved.
Owner:刘忠平 +2
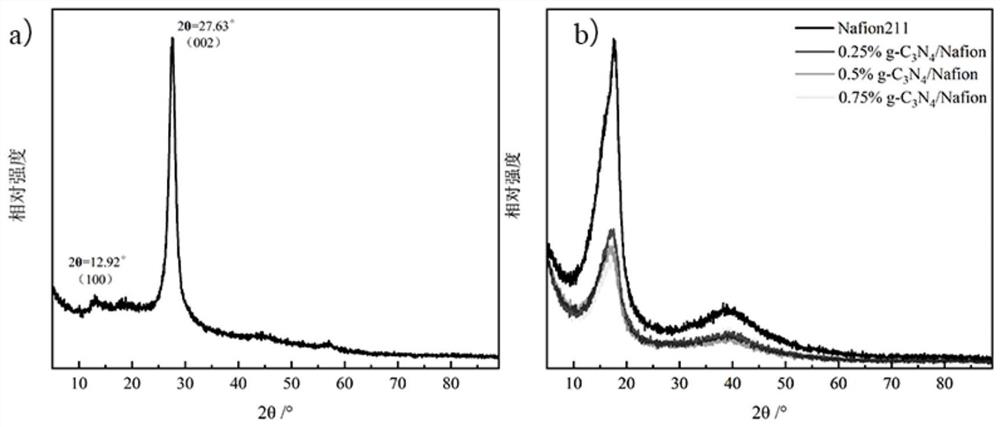
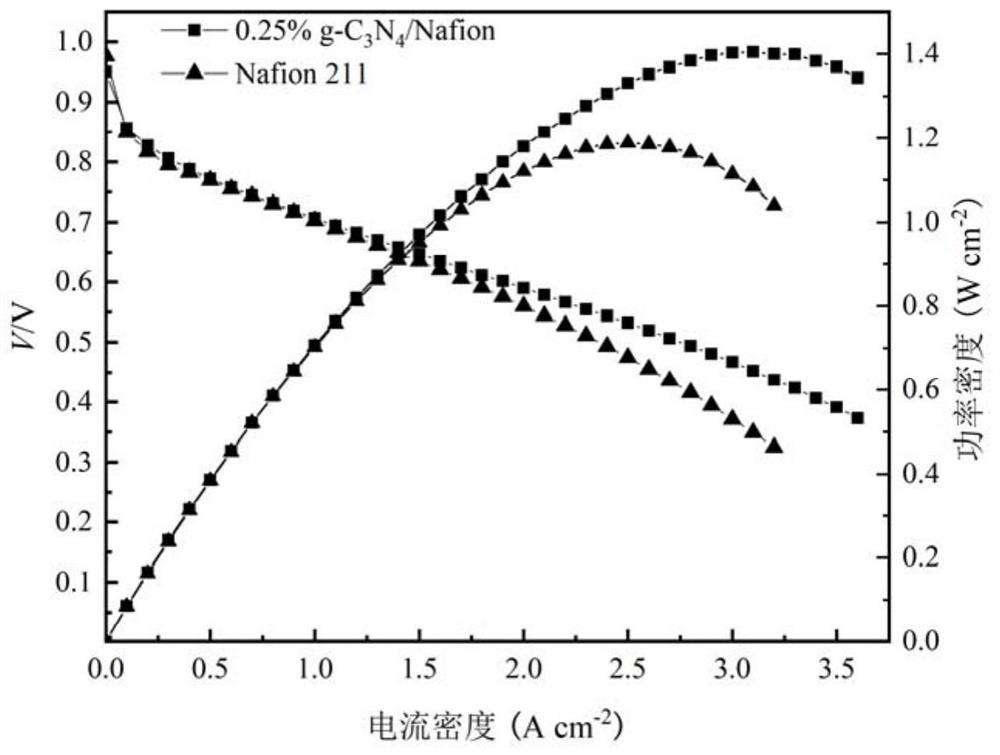
Nafion/g-C3N4 composite film as well as preparation method and application thereof
ActiveCN112820921AEasy to operateThe synthesis method is simpleFuel cellsCarbon nitrideProton exchange membrane fuel cell
The invention provides a Nafion / g-C3N4 composite membrane as well as a preparation method and application thereof, particularly relates to a composite membrane prepared by compounding protonated carbon nitride and Nafion resin, and belongs to the technical field of proton exchange membrane fuel cells. The preparation method comprises the following steps: firstly dissolving Nafion resin in a high-boiling-point solvent, then adding a dispersed g-C3N4 suspension into the Nafion solution, stirring, performing uniform ultrasonic treatment, pouring into a mold, and drying at a certain temperature to form a film, thereby obtaining the composite film. The conductivity of the composite film doped with g-C3N4 is obviously improved, and the polarization performance of a single cell is superior to that of a commercial Nafion 211 film.
Owner:DALIAN INST OF CHEM PHYSICS CHINESE ACAD OF SCI
Compound milling shoes with various cutting elements
InactiveCN108590558AHigh speedImprove efficiencyBorehole/well accessoriesPolycrystalline diamondCemented carbide
The invention discloses compound milling shoes with various cutting elements. The compound milling shoes with the various cutting elements comprise milling shoe bodies 1, polycrystalline diamond compact blades 3 and second-stage cutting blades 5 are distributed in the milling shoe bodies 1 at intervals, a plurality of polycrystalline diamond compacts 2 are arranged in front of the polycrystallinediamond compact blades 3 in the radial direction, and irregular cemented carbide cutting particles 4 are welded behind the polycrystalline diamond compact blades 3 and second-stage cutting blades 5 ina overlaying mode. The fluid cools the working milling shoes and brings the debris of drilling and milling out of the bottom of a well through water holes 6 formed between every two blades. The compound milling shoes with the various cutting elements have the advantages that the various cutting elements can improve the adaptability of the milling shoes to drill and mill various types of bridge plugs, the service life of the milling shoes is prolonged, the size of drill and grind debris particles is reduced, and the drilling milling speed and efficiency are improved.
Owner:四川安苏能源科技有限公司
Method for detecting proteome in rectal cancer
ActiveCN107860922AImprove reliabilityReflect content changesMaterial analysis by electric/magnetic meansDiseaseCell invasion
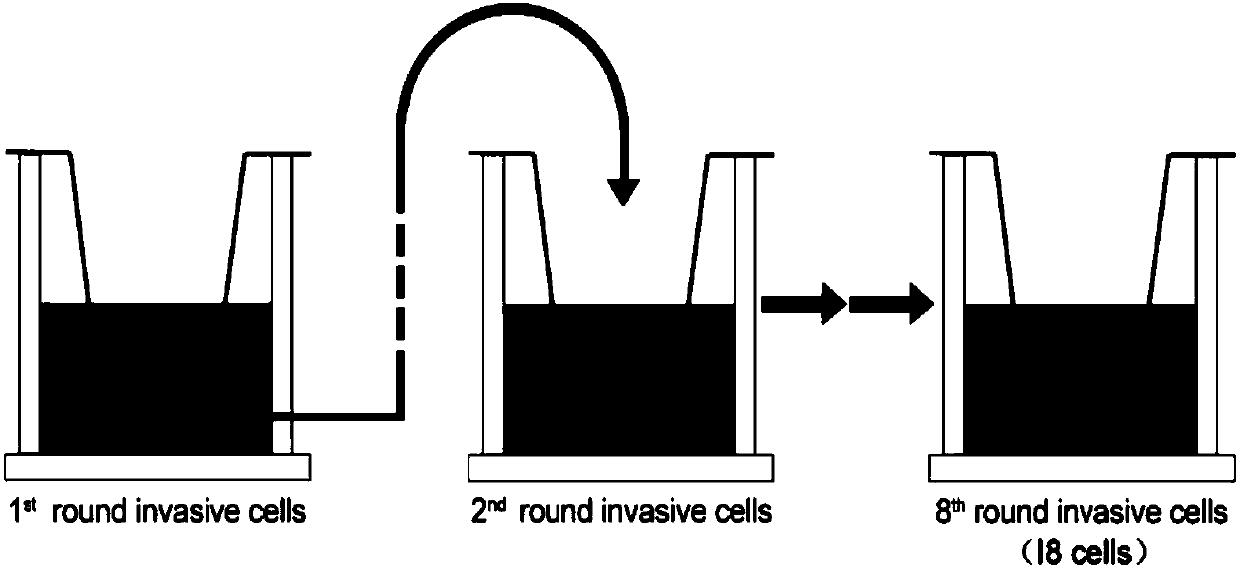
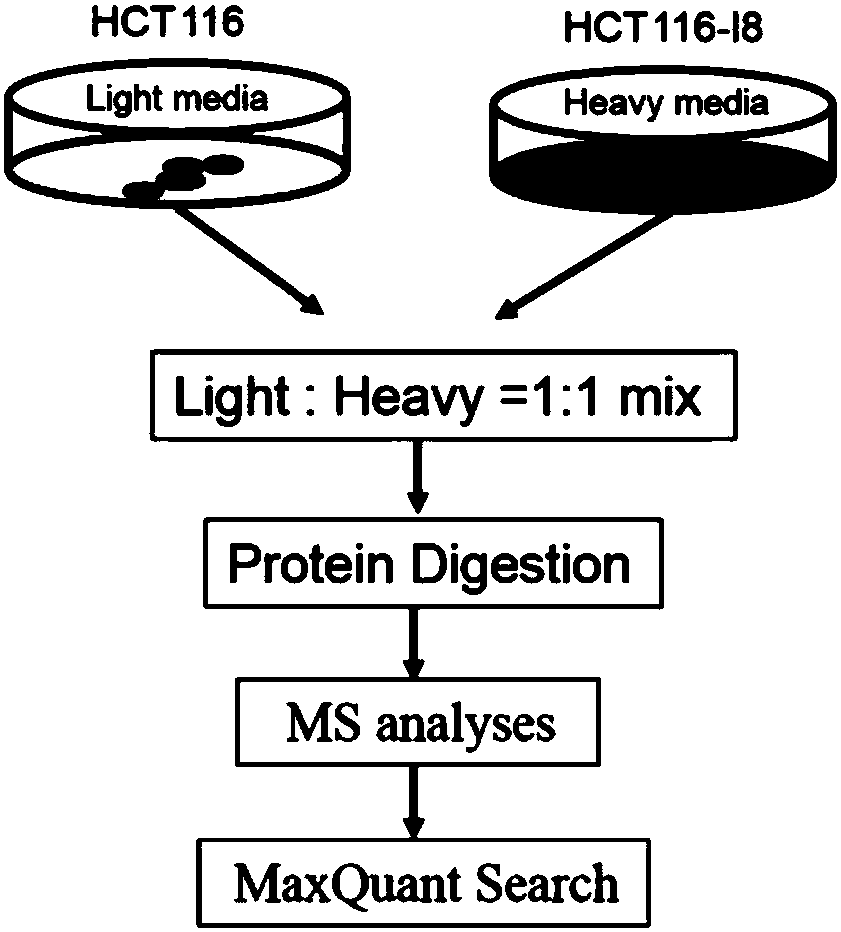
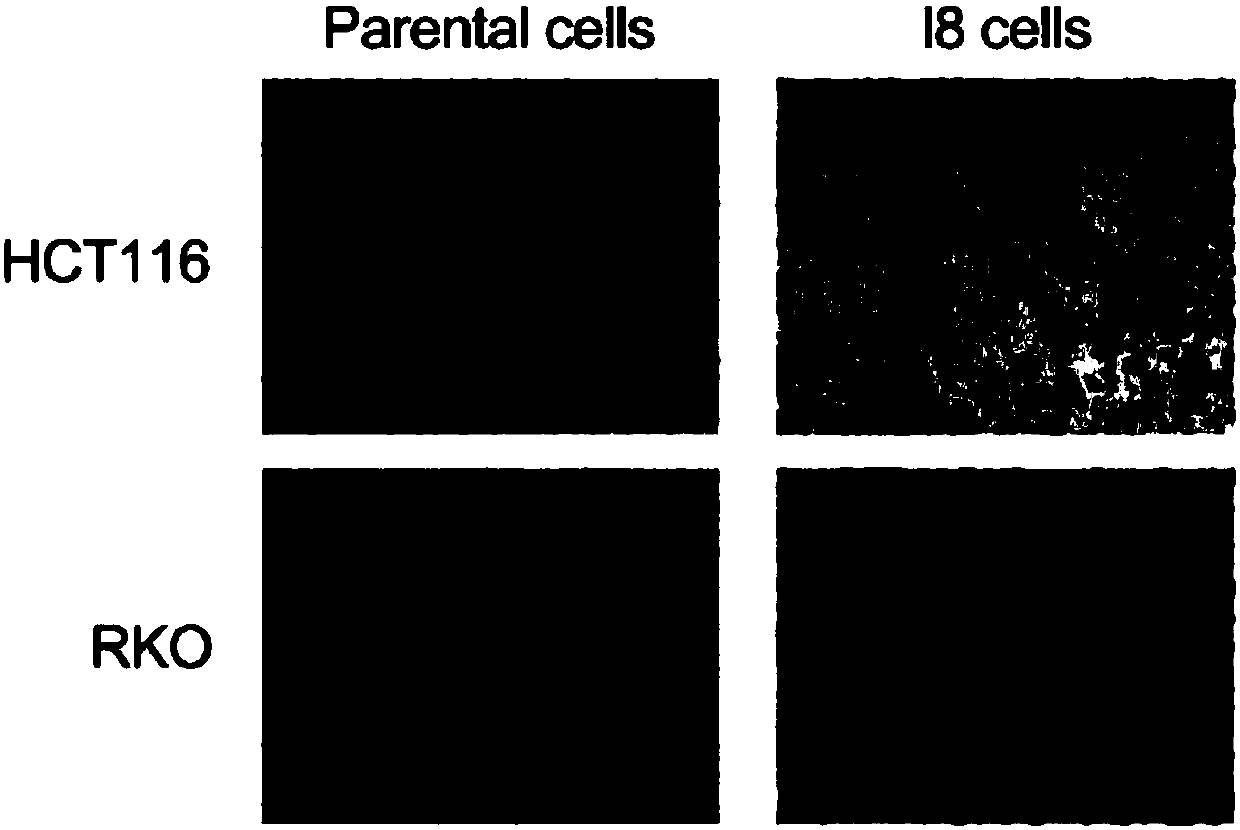
The invention relates to research on cancer cell metastasis, and particularly discloses a method for detecting a proteome in rectal cancer. According to the method, highly invasive rectal cancer cellsHCT116-I8 are screened by utilizing Transwell, and a protein or a pathway relating to cell invasion capacity is found by performing quantitative protein identification by combining an SILAC technology. Dynamic expression level of the protein in cells with high invasion capacity can be analyzed by a proteomic technology from an overall perspective, and a protein expression profile can be detectedpanoramically. The changes of proteomes in the cells with different invasion capacity in the rectal cancer can be detected in a high-throughput, high-precision and high-resolution manner by utilizinga highly invasive intestinal cancer model and a technology of screening invasion related functional protein by proteomics, and a protein pathway relating to invasion and metastasis can be found. The occurrence mechanism of diseases, such as cancer, can be explored efficiently by utilizing the technology, and a medicament acting target with high reliability is provided.
Owner:JINAN UNIVERSITY
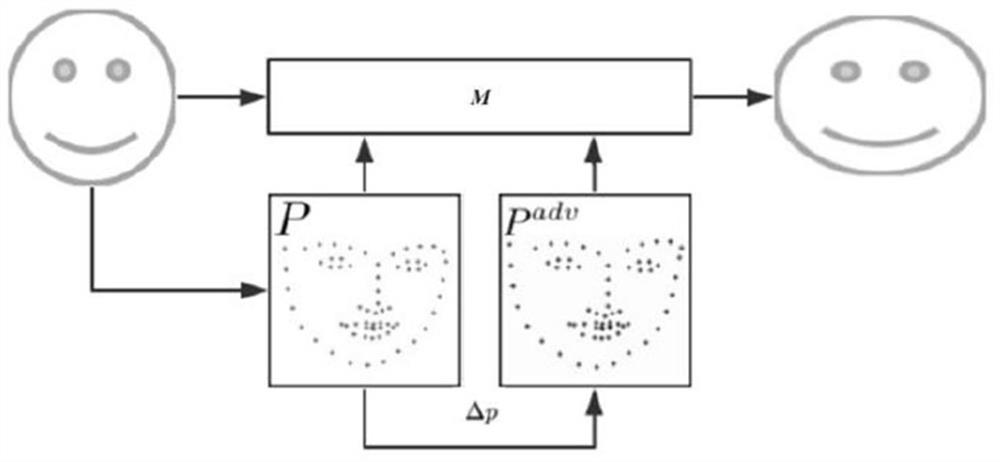
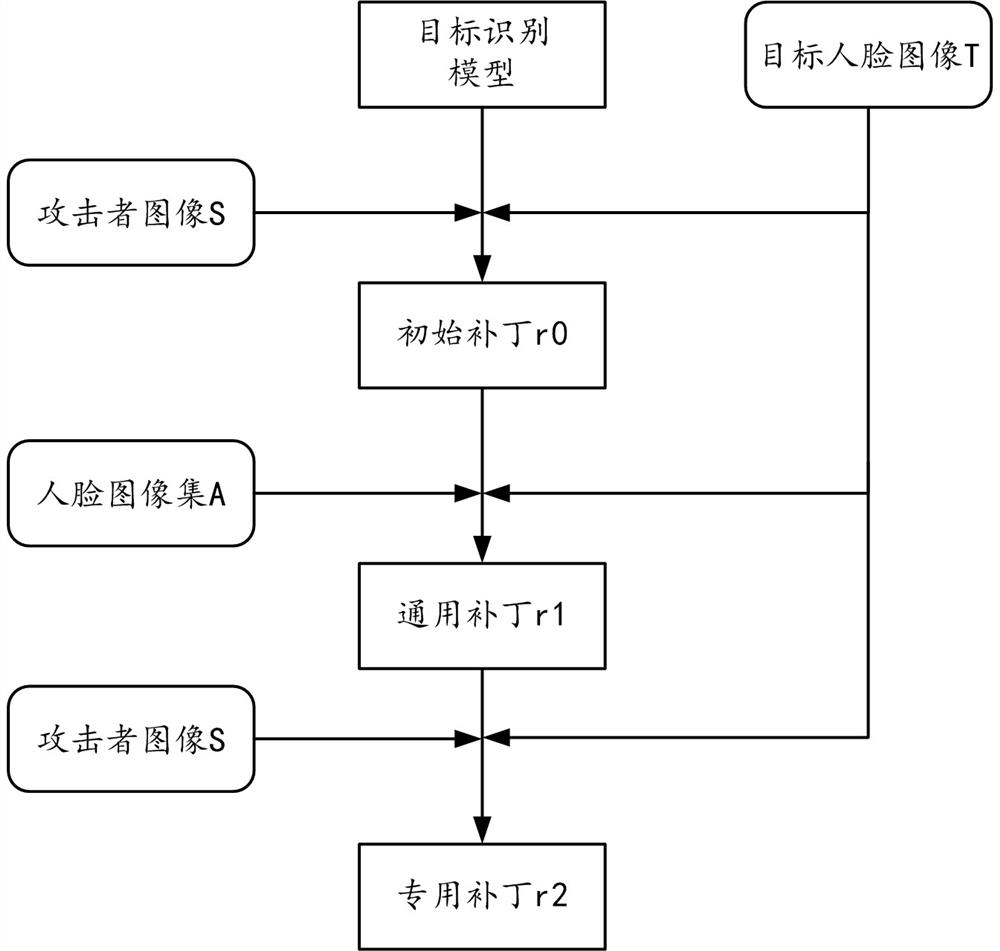
Method and device for generating face confrontation patches
ActiveCN111738217BImprove versatilityIncrease confusionImage enhancementCharacter and pattern recognitionPattern recognitionComputer graphics (images)
Owner:ALIPAY (HANGZHOU) INFORMATION TECH CO LTD
Peppermint oil mosquito repellent liquid, mosquito repellent summer sleeping mat and preparation method thereof
ActiveCN103651600AImprove attack abilityImprove mosquito repellent effectBiocidePest repellentsOrganic solventPeppermints
The invention discloses peppermint oil mosquito repellent liquid, a mosquito repellent summer sleeping mat and a preparation method thereof. The peppermint oil mosquito repellent liquid consists of the following components in parts by weight: 8-16 parts of diethylroluamide, 3-5 parts of pyriproxyfen, 2-4 parts of peppermint oil, 10-20 parts of emulsifier and 60-90 parts of organic solvent. The mosquito repellent summer sleeping mat is prepared by adopting the following method: (1), diluting the peppermint oil mosquito repellent liquid with water by 20-60 times to form a dip-dyeing liquid; (2), dyeing the summer sleeping mat into the dip-dyeing liquid, and drying to obtain the mosquito repellent summer sleeping mat. The peppermint oil mosquito repellent liquid disclosed by the invention is safe for people and livestock, less in possibility of generation of drug resistance, and easy to degrade in a natural environment. The mosquito repellent summer sleeping mat prepared by the method disclosed by the invention is strong in capability of repelling invasion of insects such as mosquitoes, and lasting in mosquito repellent effect.
Owner:安徽徽一通讯科技有限公司
Composite PDC milling shoe of drilling and milling bridge plug
PendingCN107965286AImprove adaptabilityEnhanced shoe lifeDrill bitsBorehole/well accessoriesCemented carbideEngineering
The invention discloses a composite PDC milling shoe of a drilling and milling bridge plug. The milling shoe comprises a milling shoe body 1. PDC composite sheet cutting elements 2 and hard alloy cutting elements 3 are arranged on the milling shoe body. A plurality of PDC composite sheets 2 are distributed on the front sides of cutting blades of the milling shoe. The irregular hard alloy cutting elements 3 with the normal height along the faces of blade bodies not higher than that of the PCD composite sheets are overlaid on the rear side of each PDC composite sheet 2. Fluid cools the working milling shoe and brings drilling and milling chippings out of a well bottom through water holes 4 between every two blades. Gauge protection teeth 5 of the PDC composite sheets take responsibility forthe gauge protection function of the milling shoe, and it is ensured that the milling shoe has strong gauge protection capacity. The composite PDC milling shoe has the advantages that by means of thecutting elements, the adaptability of the milling shoe for drilling and milling various bridge plugs can be improved, the service life of the milling shoe is prolonged, the size of drilling and milling chipping particles is reduced, and the drilling and milling speed and efficiency of well drilling are improved.
Owner:四川安苏能源科技有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com