Digital certificate issuing management method for industrial control system and encryption communication method for industrial control system
An industrial control system and digital certificate technology, applied in key distribution, can solve the problems that the controller configuration and business data are easily tampered with, hijacked and forged, unable to effectively verify the identity of the communication party, and the security strength of the password is limited, etc., to achieve Improving communication security, reducing the risk of hijacking or malicious tampering, and improving communication security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0047] In order to better explain the present invention and facilitate understanding, the present invention will be described in detail below through specific embodiments in conjunction with the accompanying drawings.
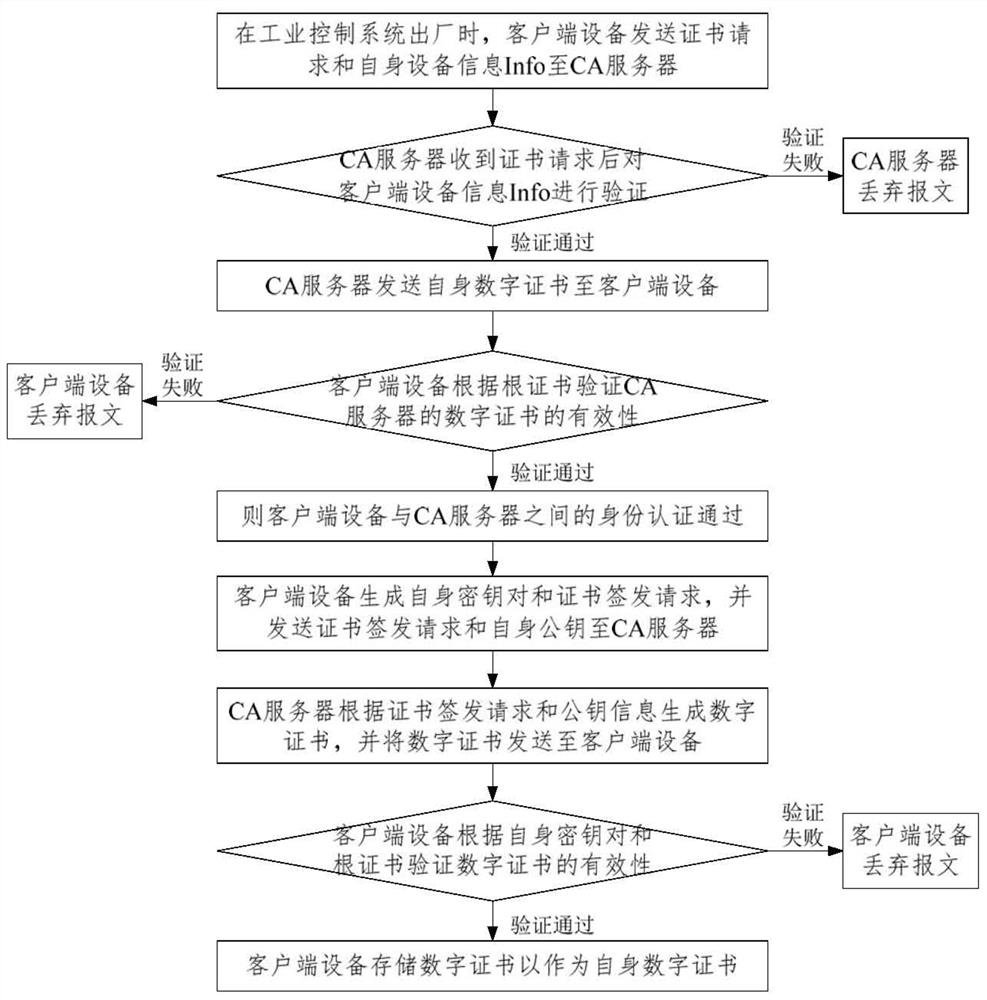
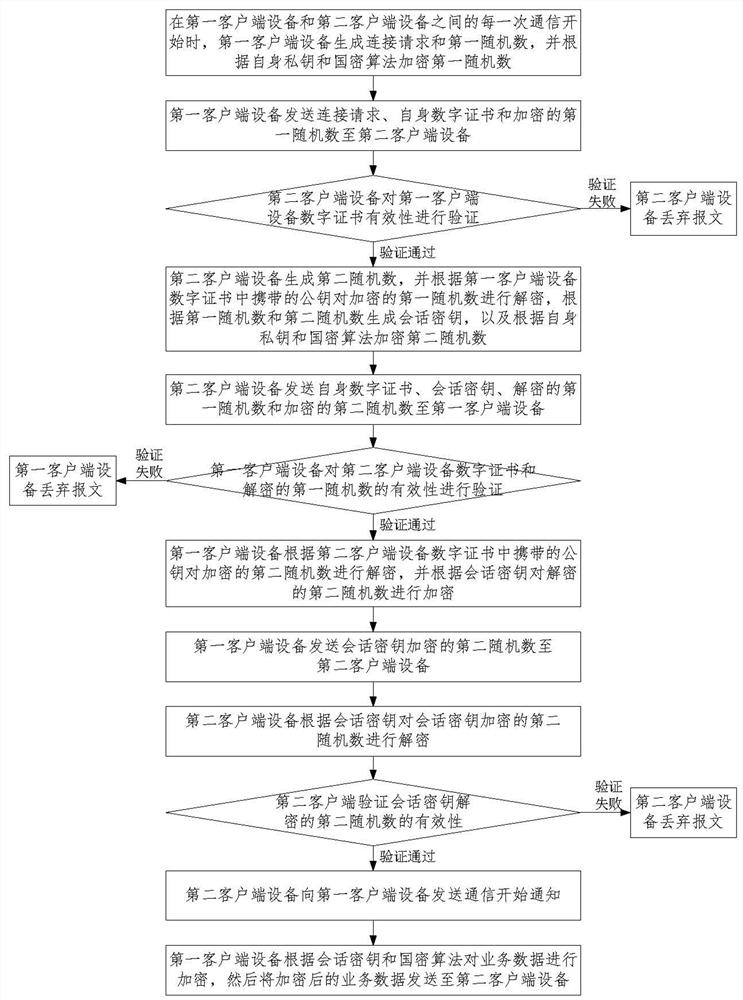
[0048] Public Key Infrastructure (PKI) is a set of infrastructure consisting of hardware, software, participants, management policies and processes, the purpose of which is to create, manage, distribute, use, store and revoke digital certificates uniformly . Digital certificate is the core of PKI architecture, and its data signature is similar to the encryption process. After the data is encrypted, only the receiver can open or change the data information, add his own signature and then transmit it to the sender, while the receiver's private The key is unique and private, which also ensures the authenticity and reliability of the signature, thereby ensuring the security of the information. Therefore, the digital certificate has the characteristics of unforgeabi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com