Communication method and device
A communication method and technology of the communication party, applied in the field of communication methods and devices, can solve problems such as losses, achieve the effect of protecting interests and improving communication security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0035] To further illustrate the application, the following examples are provided:
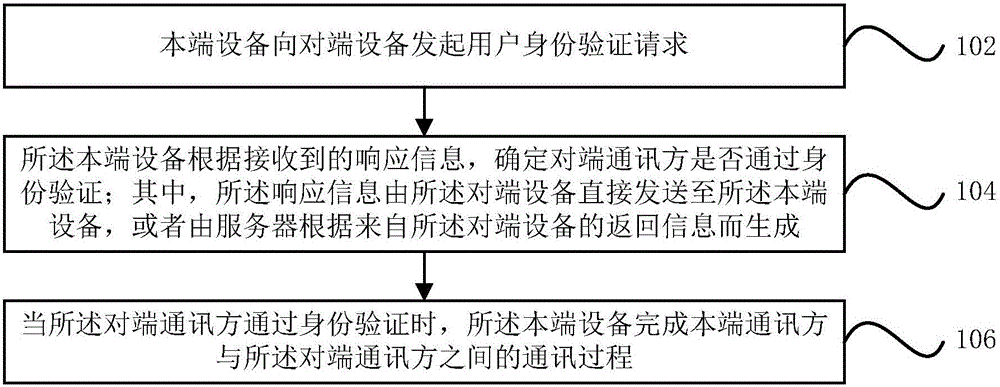
[0036] figure 1 It is a flow chart of a communication method based on verifying the initiator in an exemplary embodiment of the present application, such as figure 1 As shown, the method is applied to the electronic device of the verification initiator, and may include the following steps:
[0037] Step 102, the local device initiates a user identity verification request to the peer device.
[0038] Step 104, the local device determines whether the peer communication party has passed the identity verification according to the received response information; wherein, the response information is directly sent by the peer device to the local device, or is sent by the server according to Generated based on the return information from the peer device.
[0039] Step 106 , when the peer communication party passes the identity verification, the local device completes the communication process betwee...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com