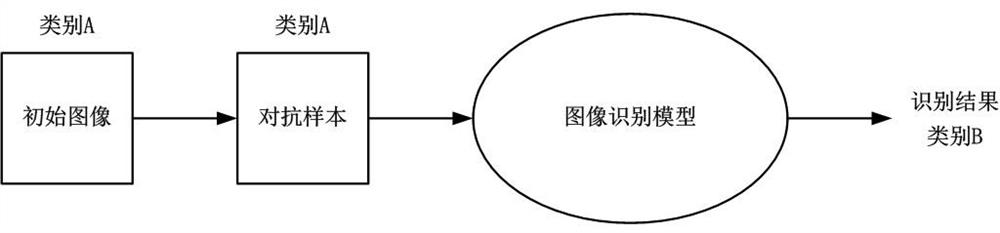
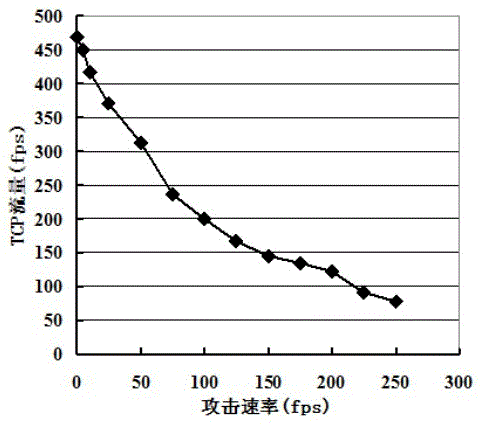
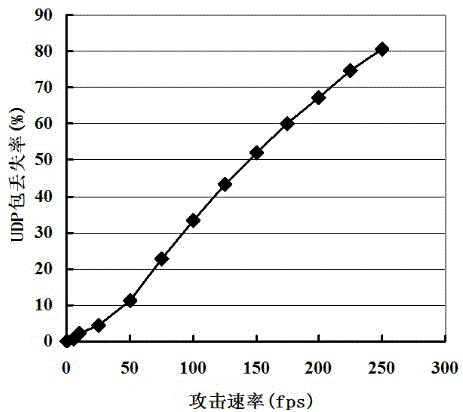
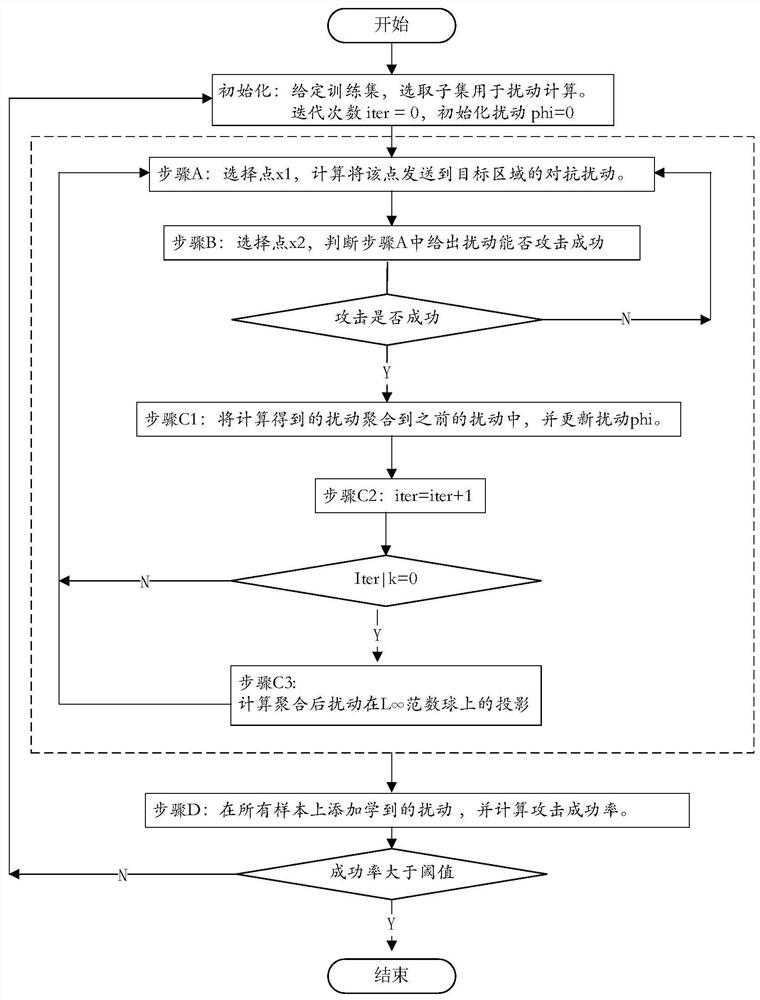
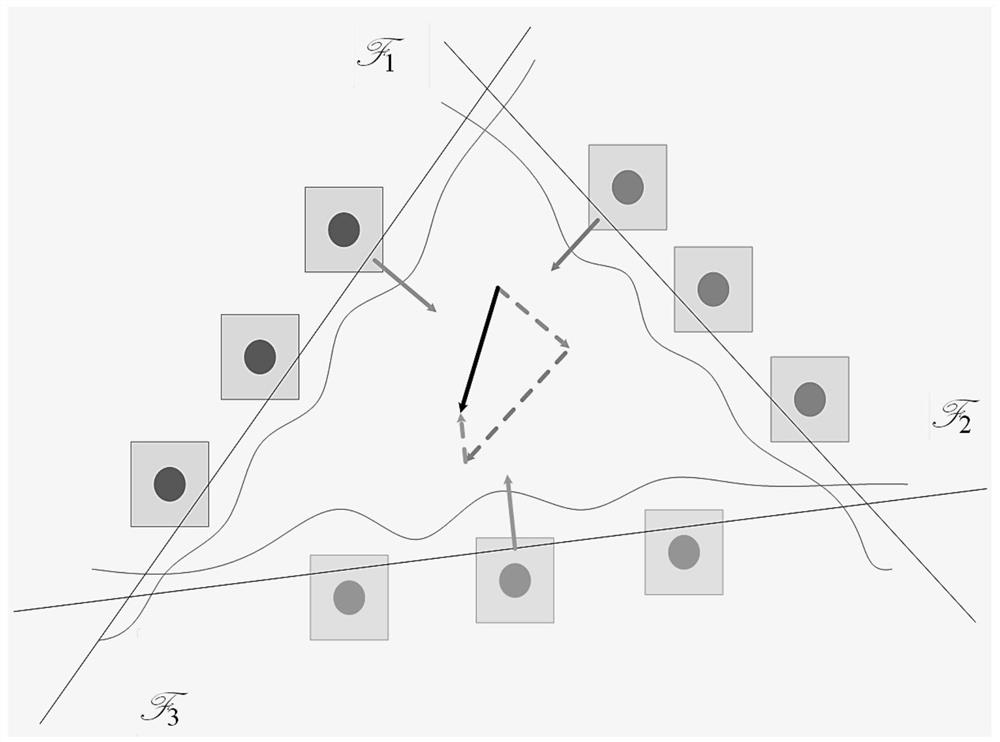
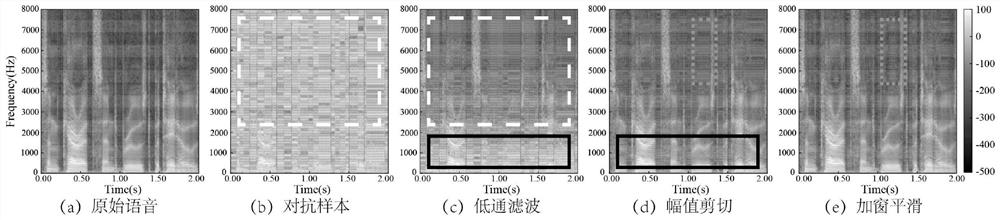
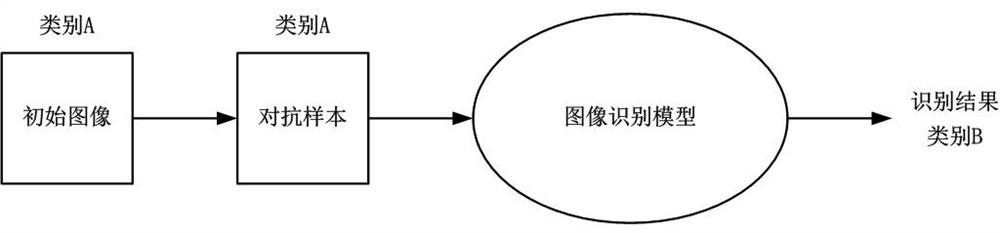
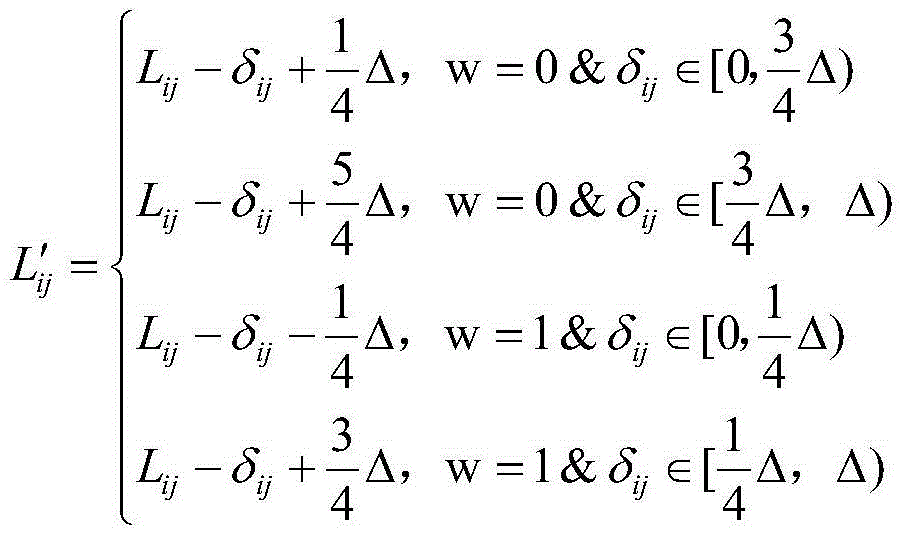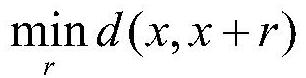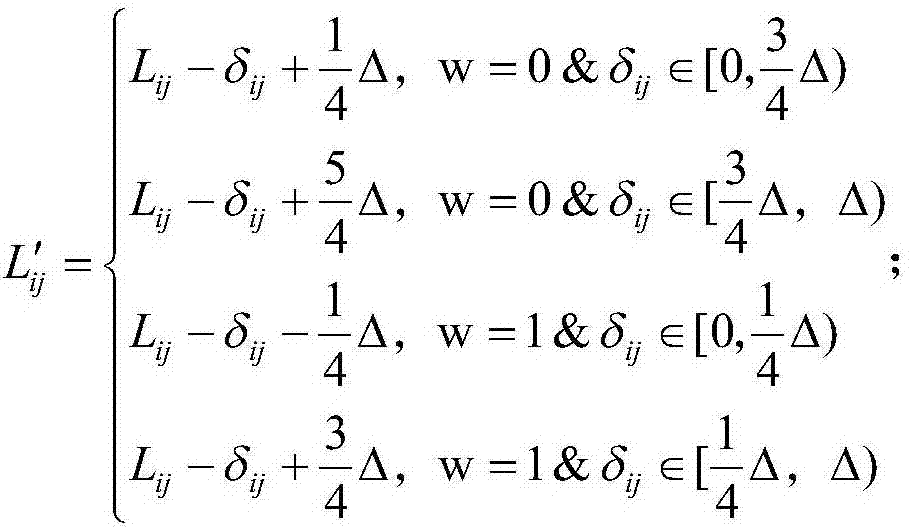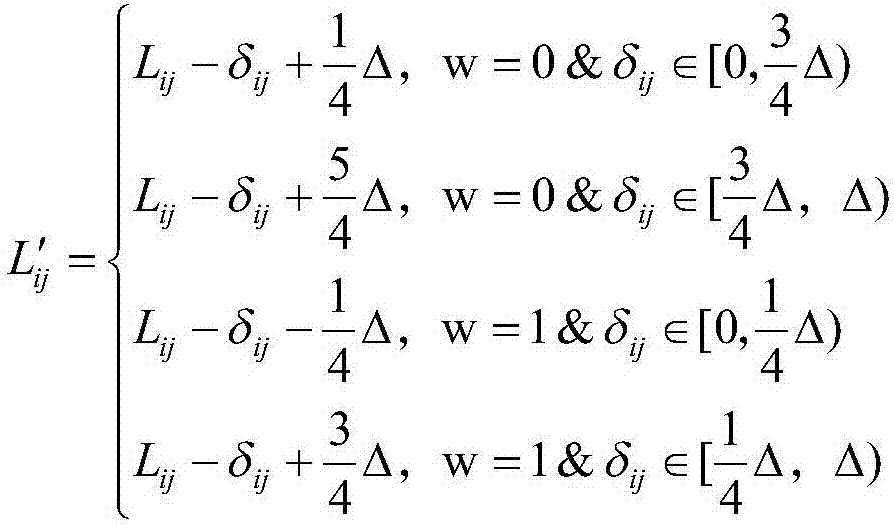Patents
Literature
54results about How to "Good attack performance" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
A step size self-adaptive attack resisting method based on model extraction
ActiveCN109948663AGood attack performanceStrong non-black box attack capabilityCharacter and pattern recognitionNeural architecturesModel extractionData set
The invention discloses a step size self-adaptive attack resisting method based on model extraction. The step size self-adaptive attack resisting method comprises the following steps: step 1, constructing an image data set; Step 2, training a convolutional neural network for the image set IMG to serve as a to-be-attacked target model, step 3, calculating a cross entropy loss function, realizing model extraction of the convolutional neural network, and initializing a gradient value and a step length g1 of an iterative attack; Step 4, forming a new adversarial sample x1; 5, recalculating the cross entropy loss function, and updating the step length of adding the confrontation noise in the next step by using the new gradient value; Step 6, repeatedly the process of inputting images, calculating cross entropy loss function, computing the step size, updating the adversarial sample; repeatedly operating the step 5 for T-1 timeS, obtaining a final iteration attack confrontation sample x'i, and inputting the confrontation sample into the target model for classification to obtain a classification result N (x'i). Compared with the prior art, the method has the advantages that a better attackeffect can be achieved, and compared with a current iteration method, the method has higher non-black box attack capability.
Owner:TIANJIN UNIV
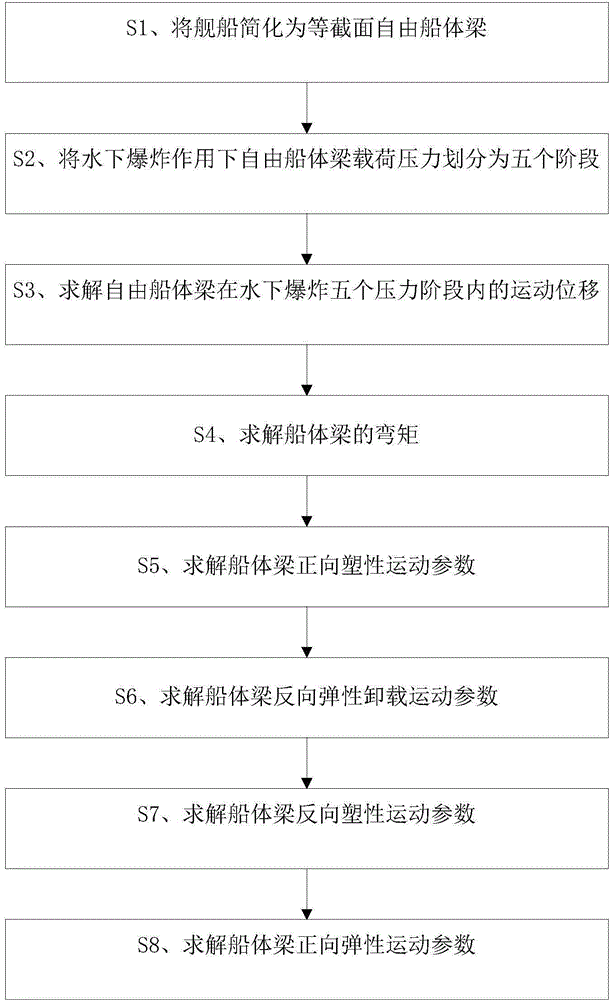
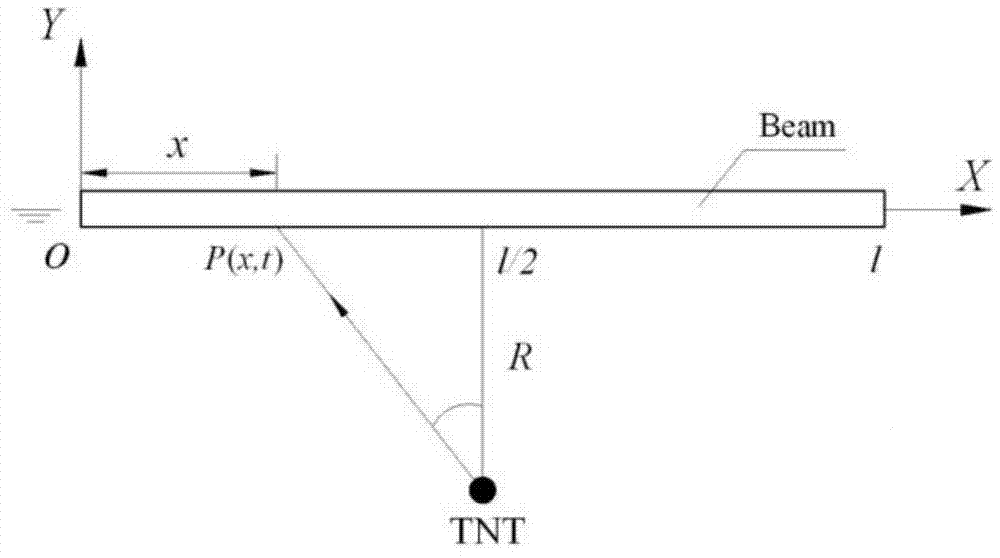
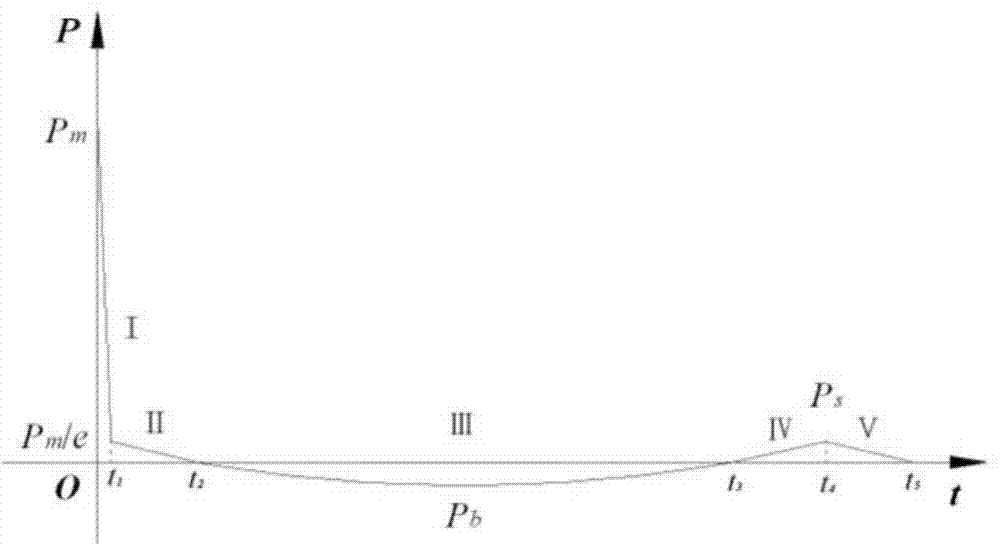
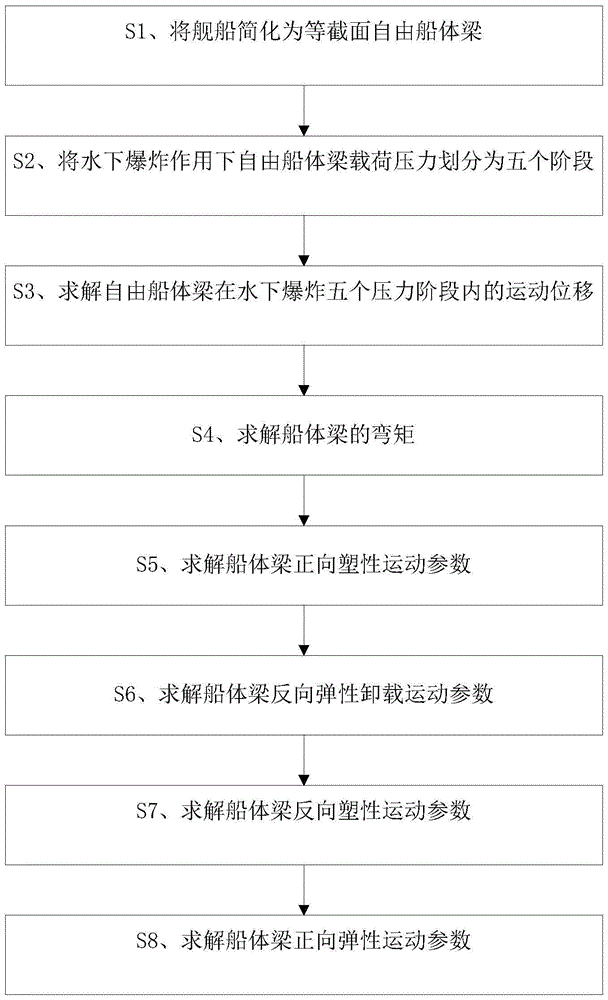
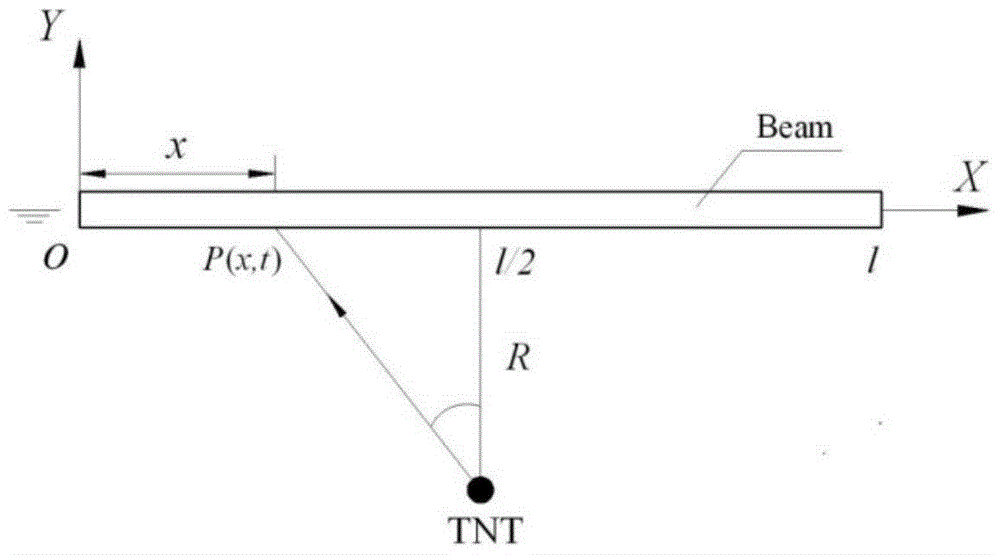
Ship whole elastic-plastic movement response predication method and system under action of underwater explosion
InactiveCN104657611AImprove the design levelGood attack performanceSpecial data processing applicationsUnderwater explosionMarine engineering
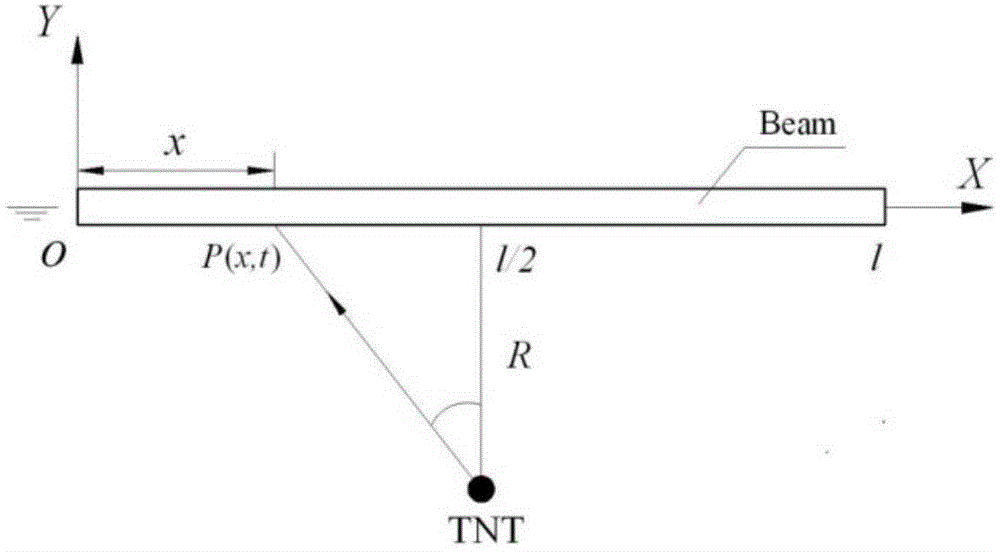
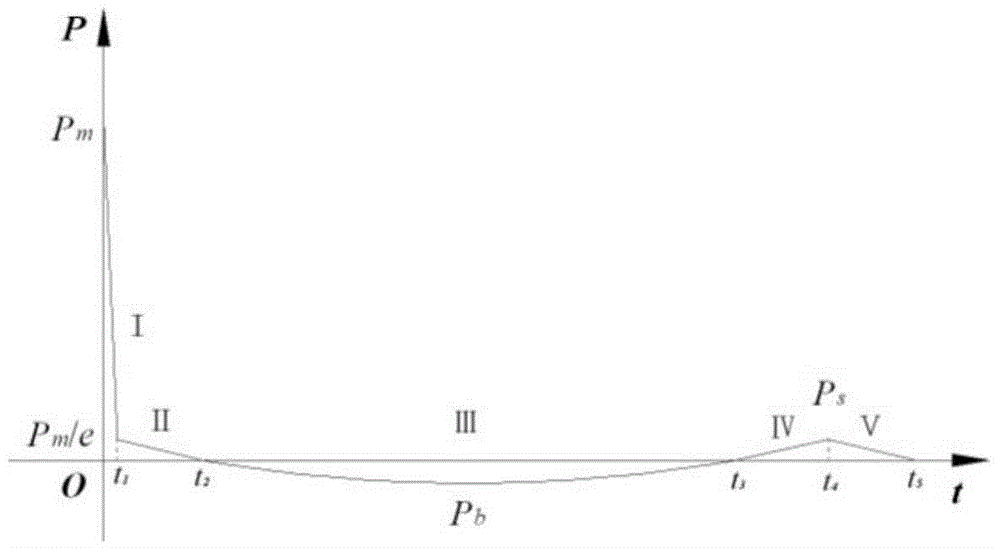
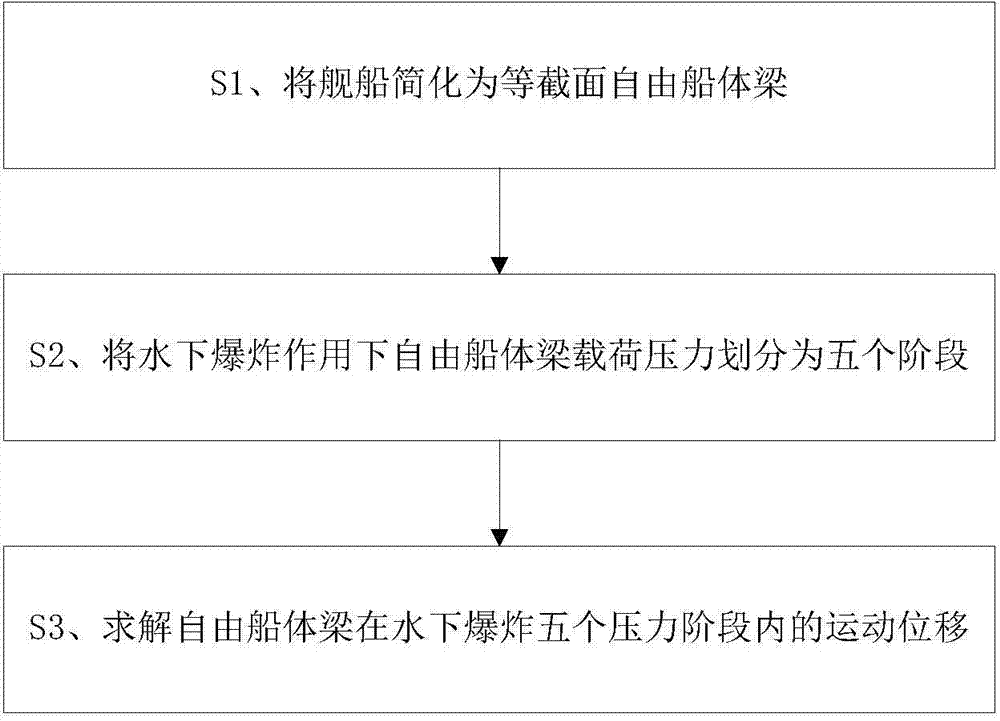
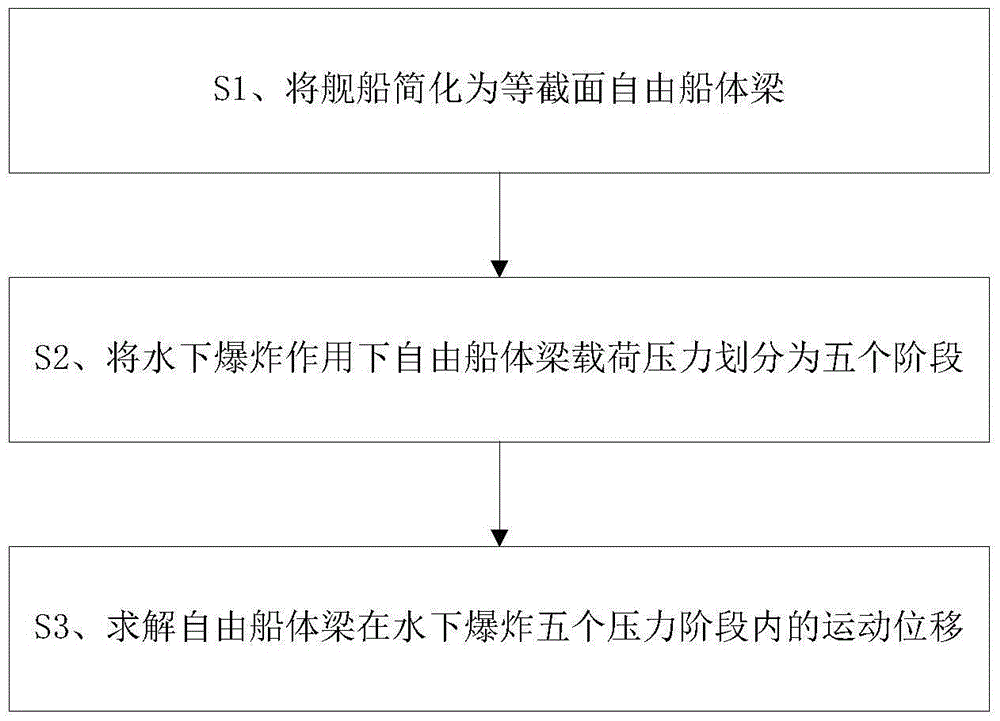
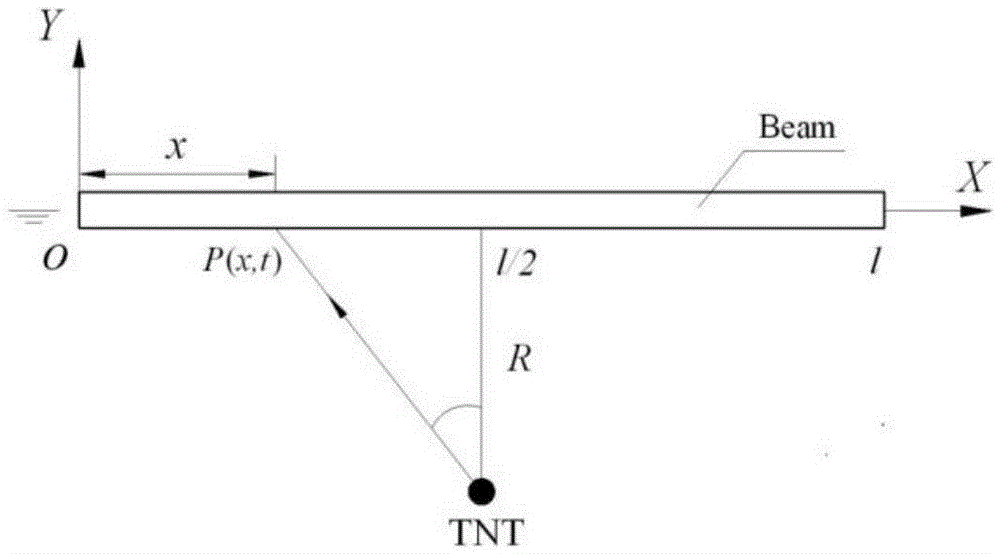
The invention discloses a ship whole elastic-plastic movement response predication method and system under the action of underwater explosion. The method comprises the following steps: S1, simplifying a ship into a free ship body beam with an equal section; S2, dividing load pressure of the free ship body beam into five time phases under the action of the underwater explosion; S3, solving movement displacement of the free ship body beam in the five time phases under the action of the underwater explosion; S4, solving a bending moment of the ship body beam; S5, solving forward plastic movement parameters of the ship body beam; S6, solving backward elastic unloading movement parameters of the ship body beam; S7, solving backward plastic movement parameters of the ship body beam; S8, solving forward plastic movement parameters of the ship body beam. The invention further provides a system for realizing the method. According to the method and the system disclosed by the invention, the ship plastic movement process is analyzed on the basis of comprehensively considering the impact effect on the whole ship body by impact waves and air bubble loads, and engineering predication of ship whole elastic-plastic movement deformation under the action of the underwater explosion can be accurately and conveniently realized.
Owner:NAVAL UNIV OF ENG PLA
DWT-SVD geometric attack prevention blind watermark method based on SIFT
ActiveCN103955878AGood resistance to attackGood attackImage data processing detailsSingular value decompositionWatermark method
The invention relates to a DWT-SVD geometric attack prevention blind watermark method based on SIFT. The method comprises a watermark embedding method and a watermark extraction method. The watermark embedding method includes the steps that discrete waterlet transformation is conducted on an original image, a low-frequency sub-band of the original image is divided into small blocks, singular value decomposition is conducted on each small block, chaotic encryption is conducted on watermarks to be embedded, and the watermarks are embedded into the maximum singular value of each small block through an optimal quantitative method, the SIFT feature points of a watermark image are stored as secret keys, the types of geometric attacks are judged according to the secret keys, and correction is conducted. The watermark extraction method is the inverse process of the watermark embedding method and includes the steps of correction of attacked images, watermark extraction and watermark decryption and restoration. According to the method, by the utilization of the rotation, zoom and translation invariance of the SIFT feature points and the combination of the advantages of DWT and SVD in the digital watermark aspect, robustness on geometric attacks is remarkably improved.
Owner:HANGZHOU DIANZI UNIV
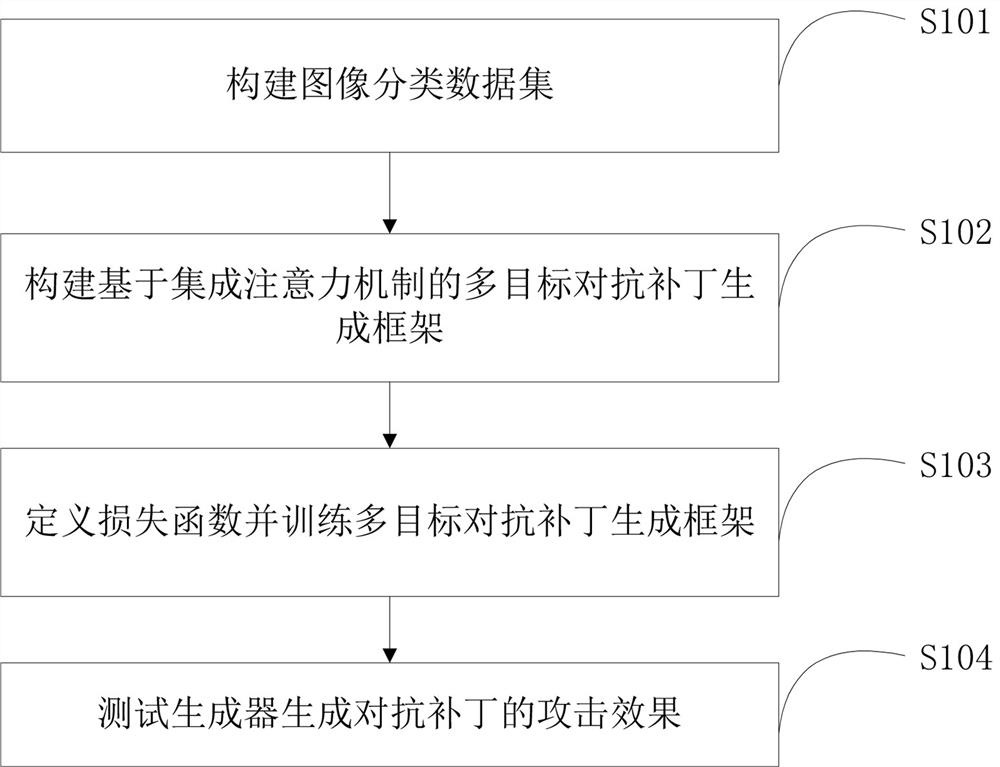
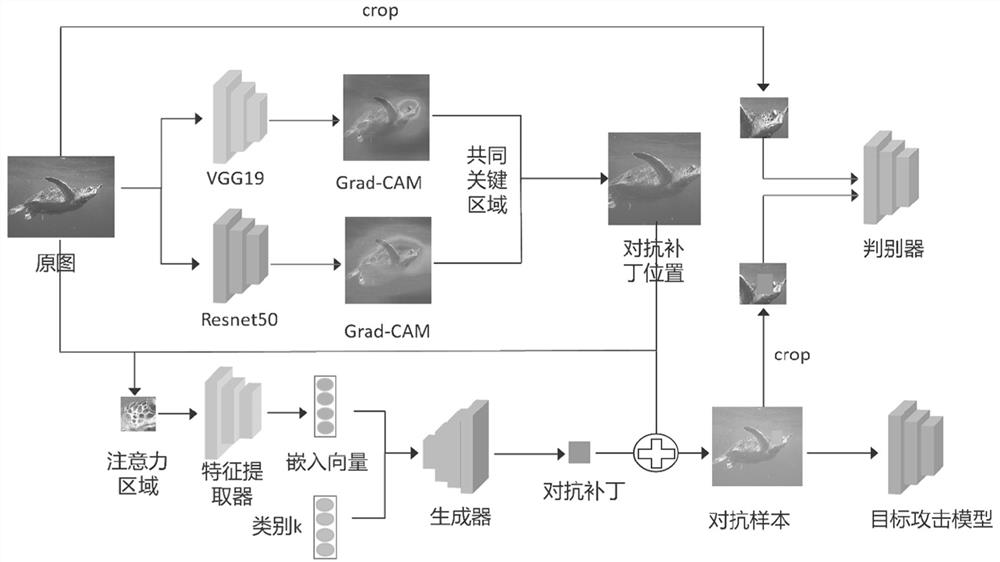
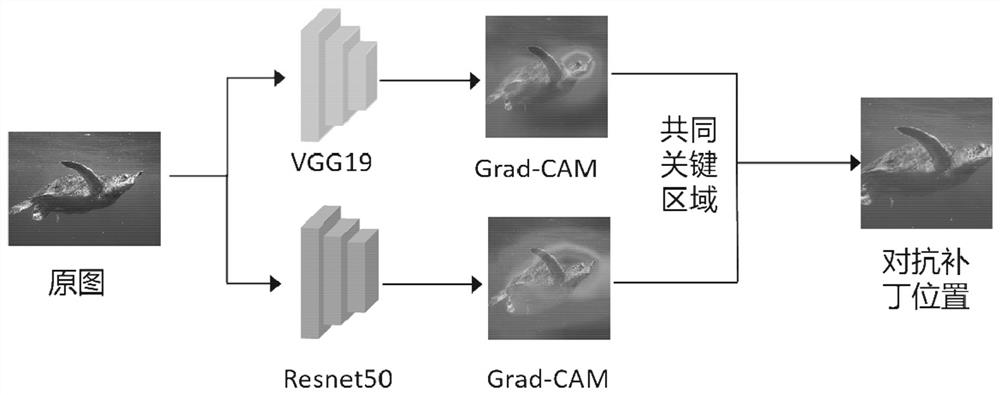
Multi-target adversarial patch generation method and device based on integrated attention mechanism
ActiveCN112085069AImprove visual effectsGood attack performanceInternal combustion piston enginesCharacter and pattern recognitionDiscriminatorData set
The invention belongs to the technical field of artificial intelligence security, and particularly relates to a multi-target adversarial patch generation method and device based on an integrated attention mechanism, and the method comprises the steps: constructing an image classification data set; constructing a multi-target adversarial patch generation framework based on an integrated attention mechanism; defining a loss function and training a multi-target adversarial patch generation framework; and testing the attack effect of the generated countermeasure patch. According to the method, thekey classification area of the input image is positioned by integrating the attention mechanism, so that the better attack performance and mobility of the countermeasure patch are ensured; the inputof the generator makes full use of the original image information, so that the anti-patching effect generated by the generator is better; the input of the generator is also fused with multi-target category information, so that any specified category of the target model can be attacked, and multi-target category attacks can be realized; and the input of the discriminator is cut to ensure that the discriminator learns more context information and improve the visual effect of the adversarial patch.
Owner:PLA STRATEGIC SUPPORT FORCE INFORMATION ENG UNIV PLA SSF IEU
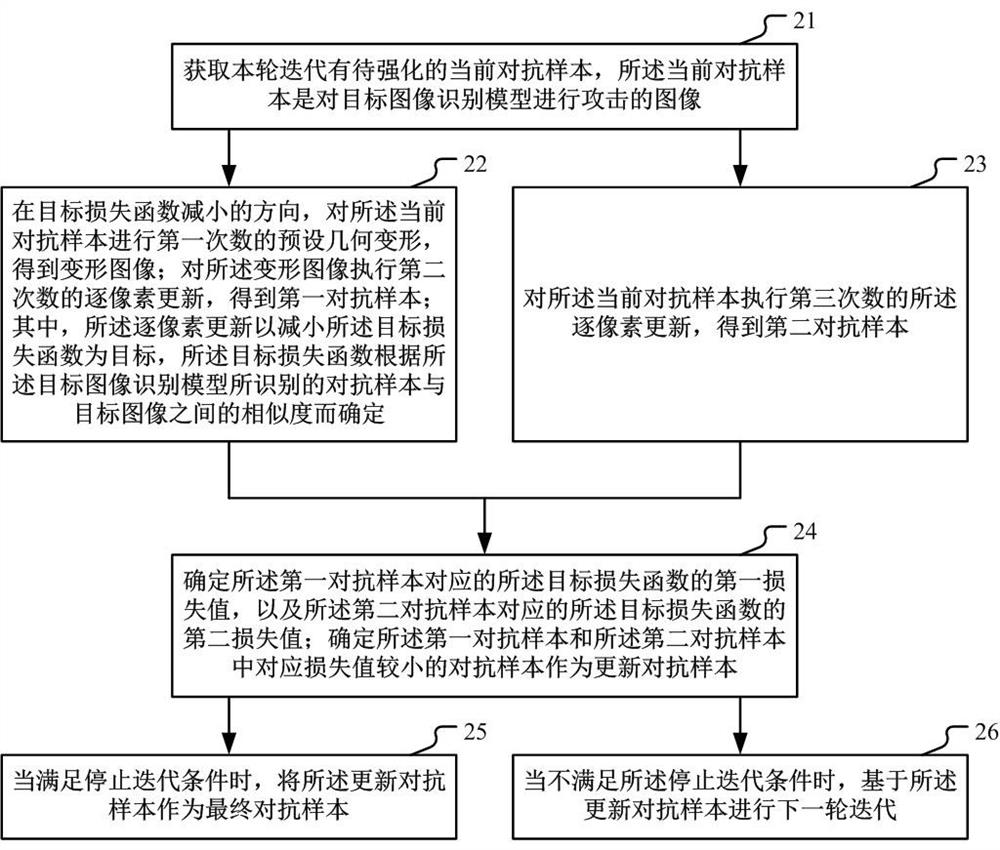
Adversarial sample generation method and device
ActiveCN111737691AGood attack effectAggressiveCharacter and pattern recognitionPlatform integrity maintainanceComputational physicsMorphing
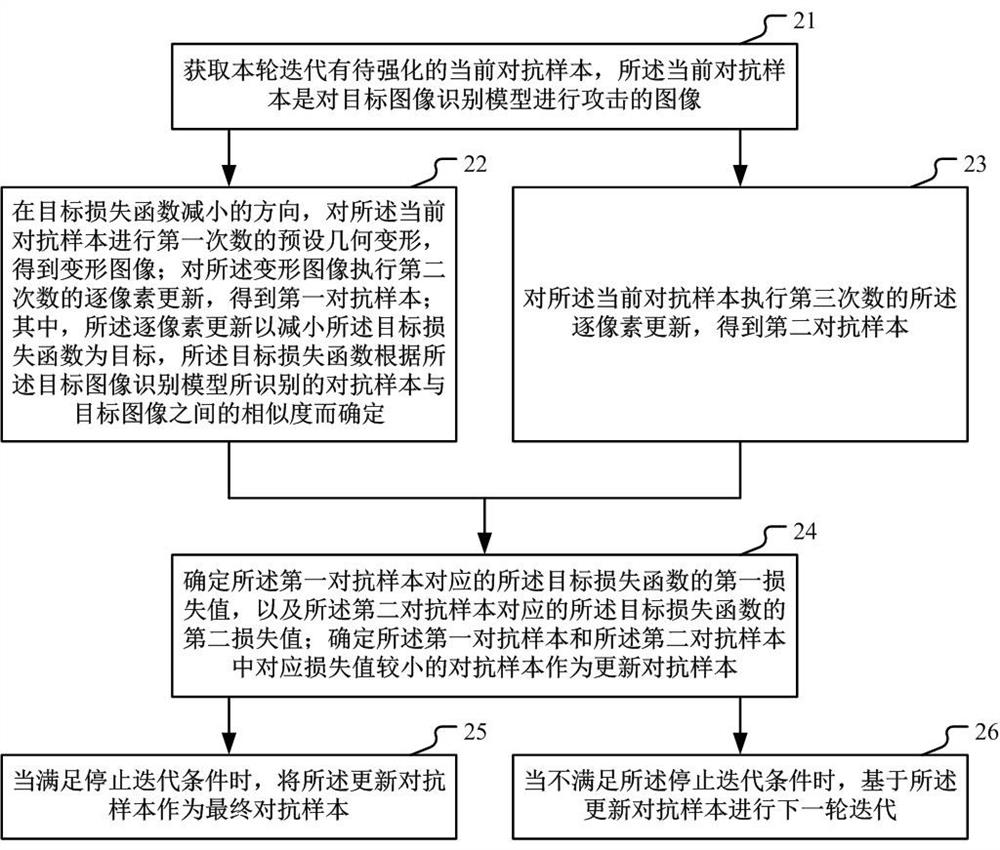
Embodiments of the invention provide an adversarial sample generation method and device. The method comprises the steps of obtaining a to-be-enhanced current adversarial sample in the current iteration; in the decreasing direction of the target loss function, performing preset geometric deformation on the current adversarial sample for a first time to obtain a deformed image; executing second-timepixel-by-pixel updating on the deformed image to obtain a first adversarial sample; performing third pixel-by-pixel updating on the current adversarial sample to obtain a second adversarial sample; determining an adversarial sample with a smaller corresponding loss value in the first adversarial sample and the second adversarial sample as an updated adversarial sample; when the iteration stoppingcondition is met, taking the updated adversarial sample as a final adversarial sample; and when the iteration stopping condition is not met, performing the next round of iteration based on the updated adversarial sample. The generated adversarial sample can have stronger aggressivity, so that targeted defense is realized.
Owner:ALIPAY (HANGZHOU) INFORMATION TECH CO LTD
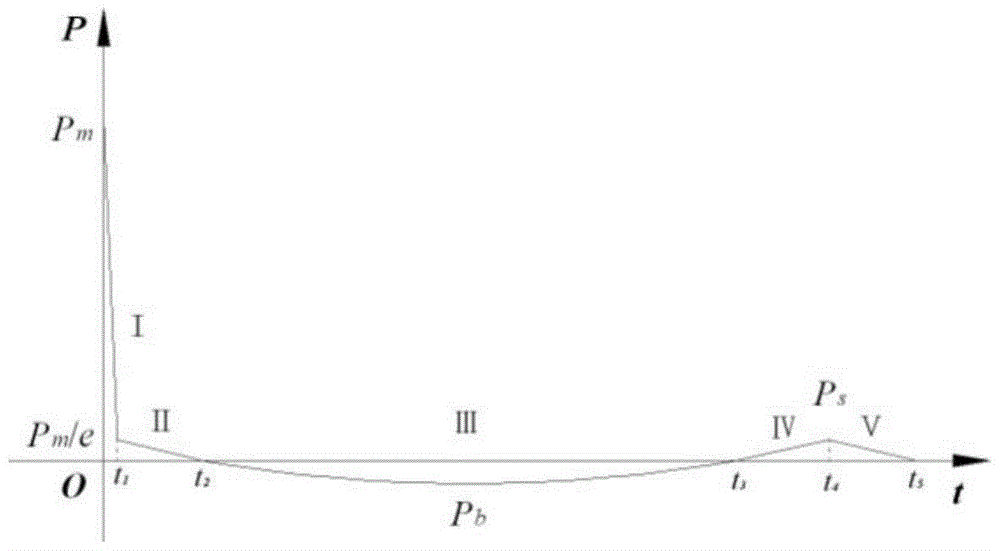
Ship whipping motion response prediction method and system under underwater explosion situation
InactiveCN104743086AImprove the design levelGood attack performanceDefensive equipmentOffensive equipmentUnderwater explosionEngineering
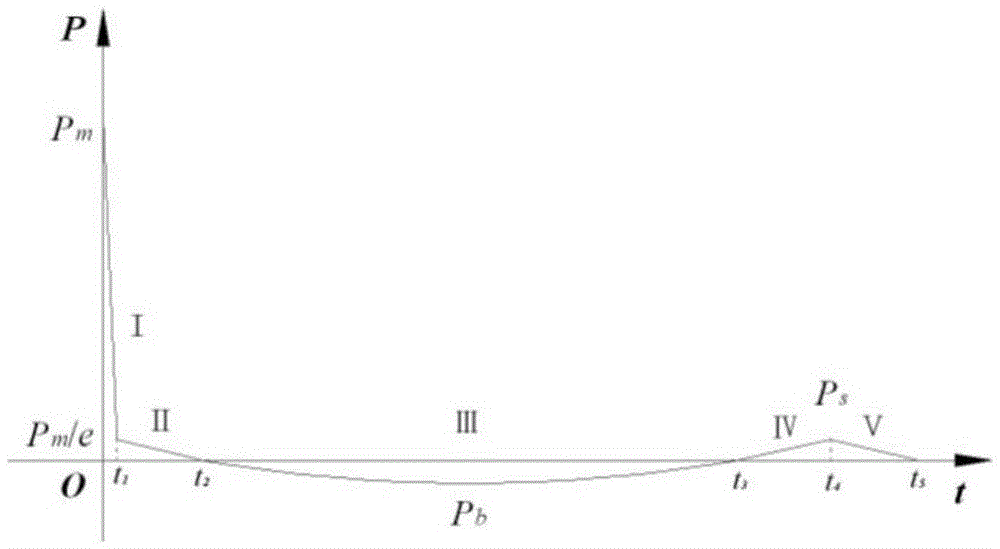
The invention discloses a ship whipping motion response prediction method and system under a combined effect of underwater explosive shock waves and bubbles. The ship whipping motion response prediction method comprises the steps that step 1, a ship is equivalent to a uniform cross section free ship body girder, and therefore the prediction of ship motion responses are equivalent to the predication of free ship body girder motion responses; step 2, the load pressure process of the free ship body girder under the underwater explosion effect is divided into five time phases, and a shock wave pressure peak value, a bubble pulsation phase negative pressure peak value and a bubble first time pulsation pressure peak value are collected; step 3, motion displacements in the five time phases of underwater explosion of the free ship body girder are solved. The invention further provides a ship whipping motion response prediction system. The ship whipping motion response prediction method and system comprehensively consider the shock effect of the shock wave and the bubble load on the whole ship, the underwater explosion load pressure is simplified to be five phases, the motion displacements of a ship in different phases are calculated, and therefore project prediction of ship elastic motion or whipping motion responses under medium and distal field explosion effect is achieved accurately, simply and conveniently.
Owner:NAVAL UNIV OF ENG PLA
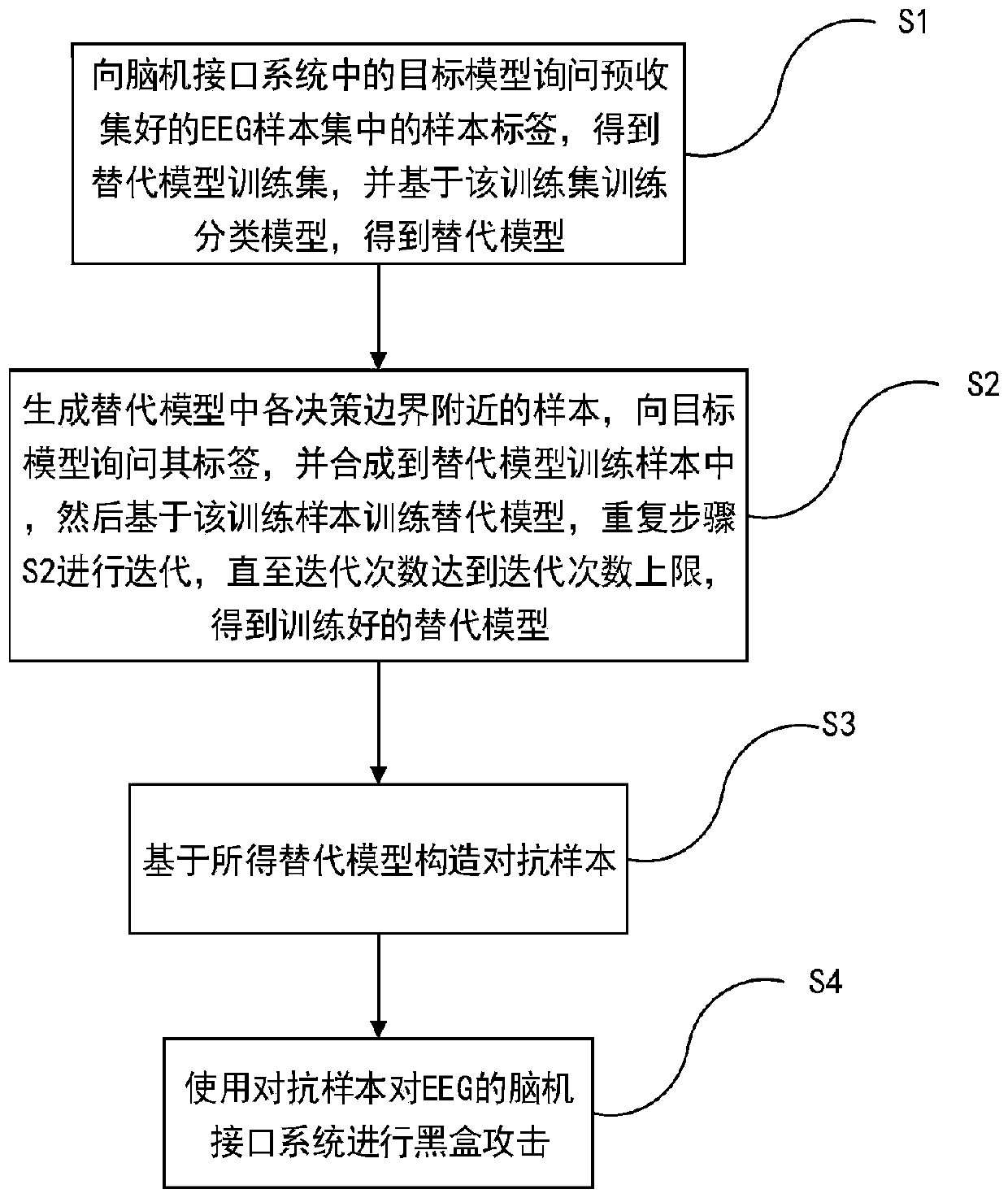
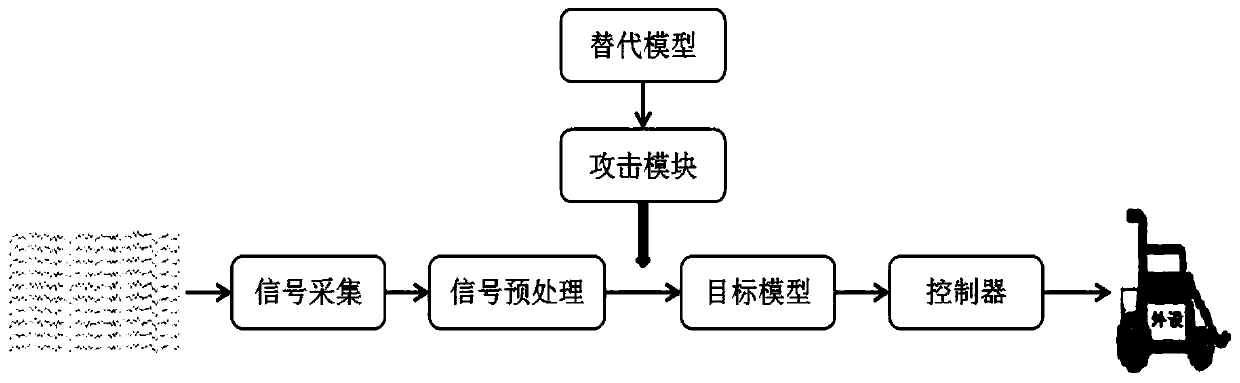
Black box attack method for brain-computer interface system
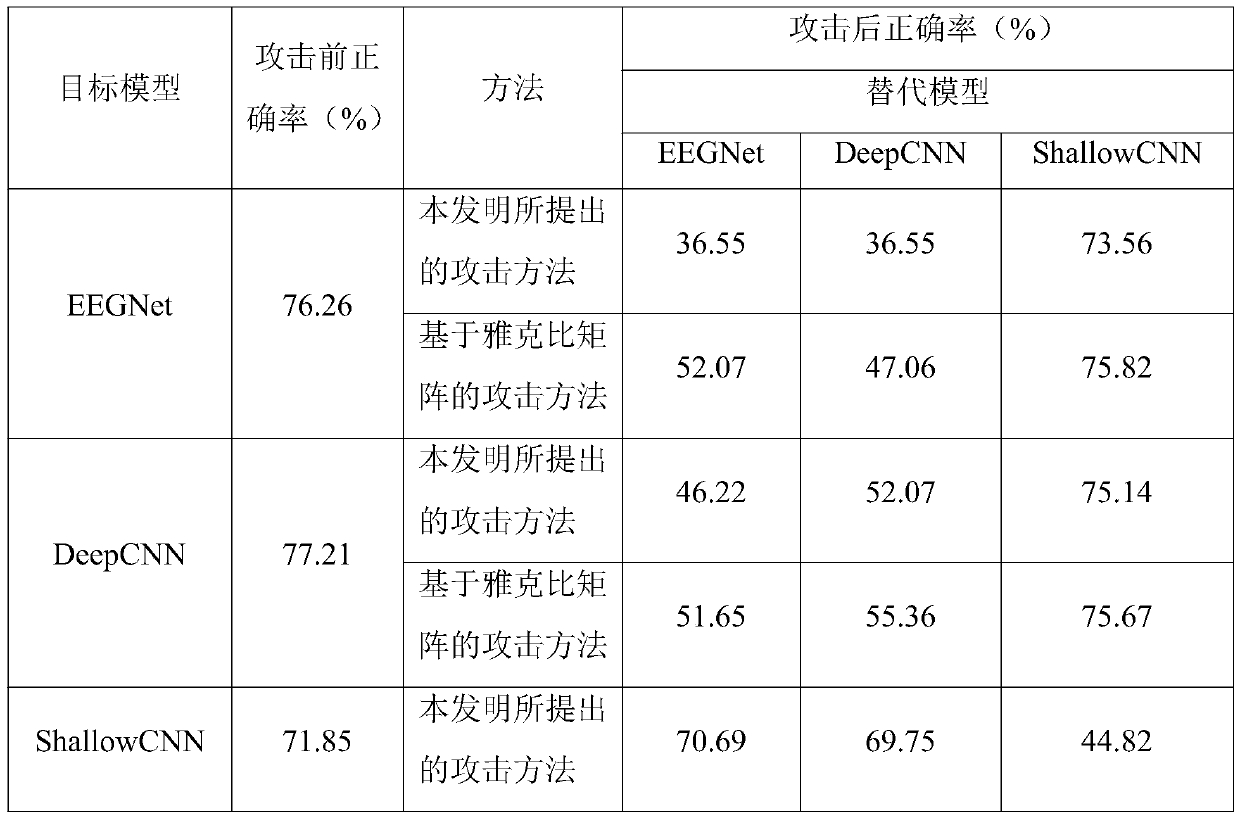
ActiveCN110837637ALarge amount of informationIncrease diversityCharacter and pattern recognitionPlatform integrity maintainanceLow noiseTime domain
The invention discloses a black box attack method for a brain-computer interface system. Firstly, generating EEG samples with more information amount and diversity based on inquiry synthesis active learning to substitute model training samples, then training an alternative model based on the training sample, so that the alternative model can better approximate a target model, and finally, generating an adversarial sample on the trained alternative model, and performing black box attack on a brain-computer interface system of the EEG by using the adversarial sample, so that the brain-computer interface system can be wrongly classified on the target model. Compared with a traditional black box attack method based on a Jacobian matrix, the method has a better attack effect. The same or betterattack performance can be obtained under the condition of fewer inquiry times, the generated countermeasure sample has very low noise, is almost not different from the original EEG signal in time domain and frequency domain and cannot be easily found, and the attack efficiency of the black box attack in the brain-computer interface system is greatly improved.
Owner:HUAZHONG UNIV OF SCI & TECH
Matt-white immersion-gold-resistant, anti-cracking and light-sensing solder mask material and preparation method thereof
ActiveCN105137716AImprove heat resistanceGood chemical resistancePhotosensitive materials for photomechanical apparatusAcrylic resinFirming agent
The invention discloses a matt-white immersion-gold-resistant, anti-cracking and light-sensing solder mask material and a preparation method thereof. The matt-white immersion-gold-resistant, anti-cracking and light-sensing solder mask material mainly comprises a main agent and a curing agent, wherein the main agent comprises acrylic resin with a special function, acrylic resin, a photoinitiator, a dispersing agent, dibasic ester, fumed silica, barium sulfate, titanium dioxide and an antifoaming agent; the curing agent comprises thermocuring resin, a curing additive, melamine, a photocuring monomer, triglycidyl isocyanurate, titanium dioxide and dibasic ester. The prepared matt-white light-sensing solder mask material has high immersion gold resistance and yellowing resistance, and is more stable and reliable during normal technology use of a PCB (printed circuit board).
Owner:江门市阪桥电子材料有限公司
A method for preventing a community structure in a complex network from being deeply mined
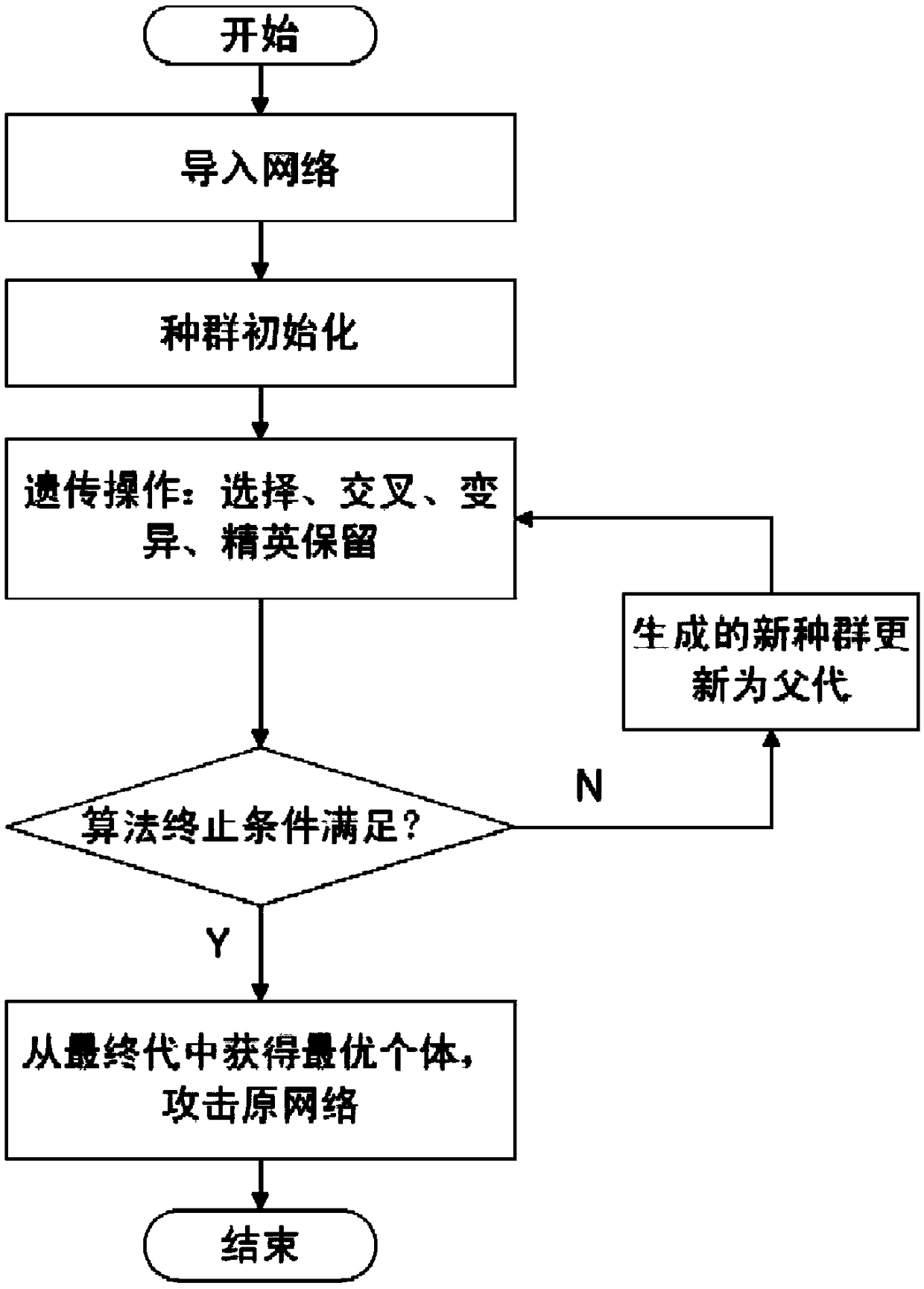
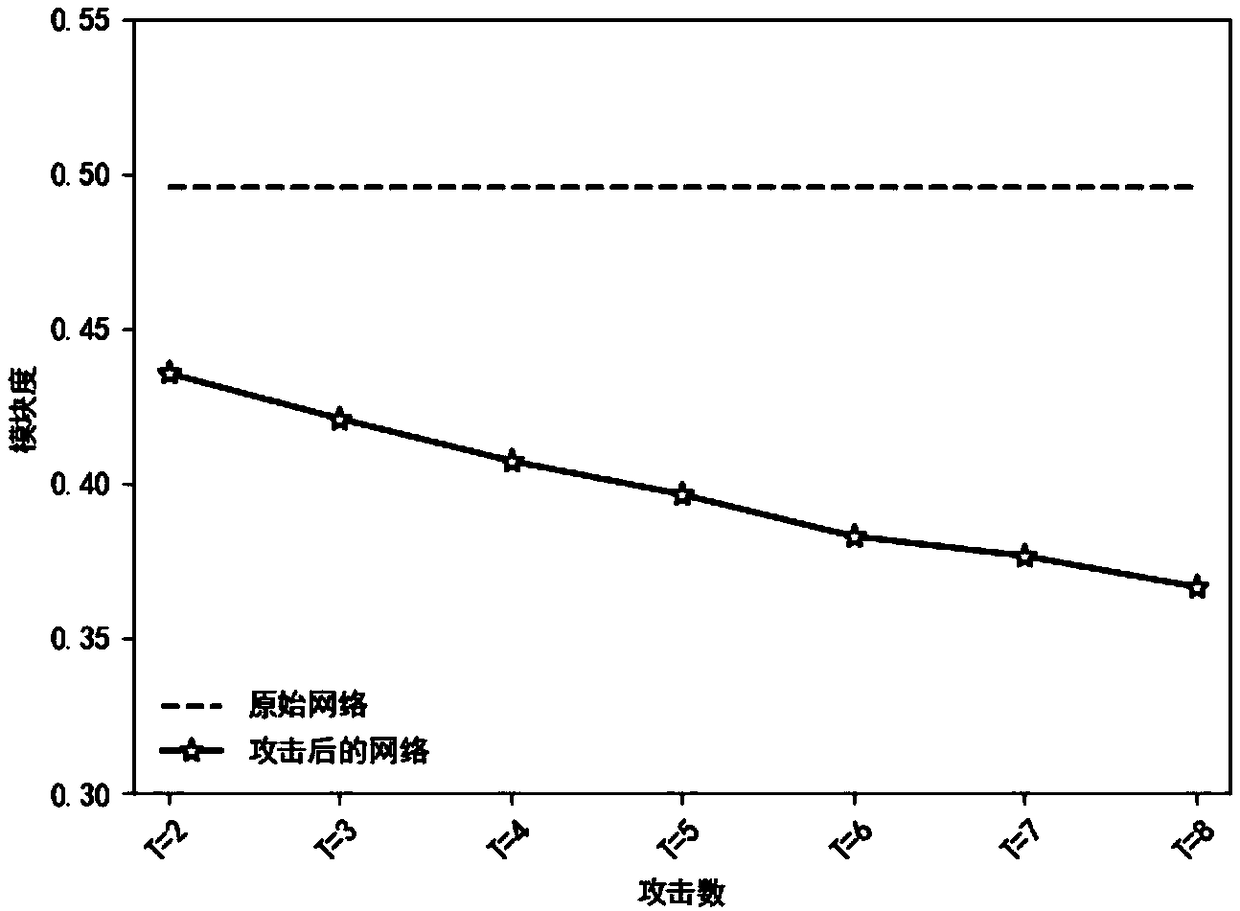
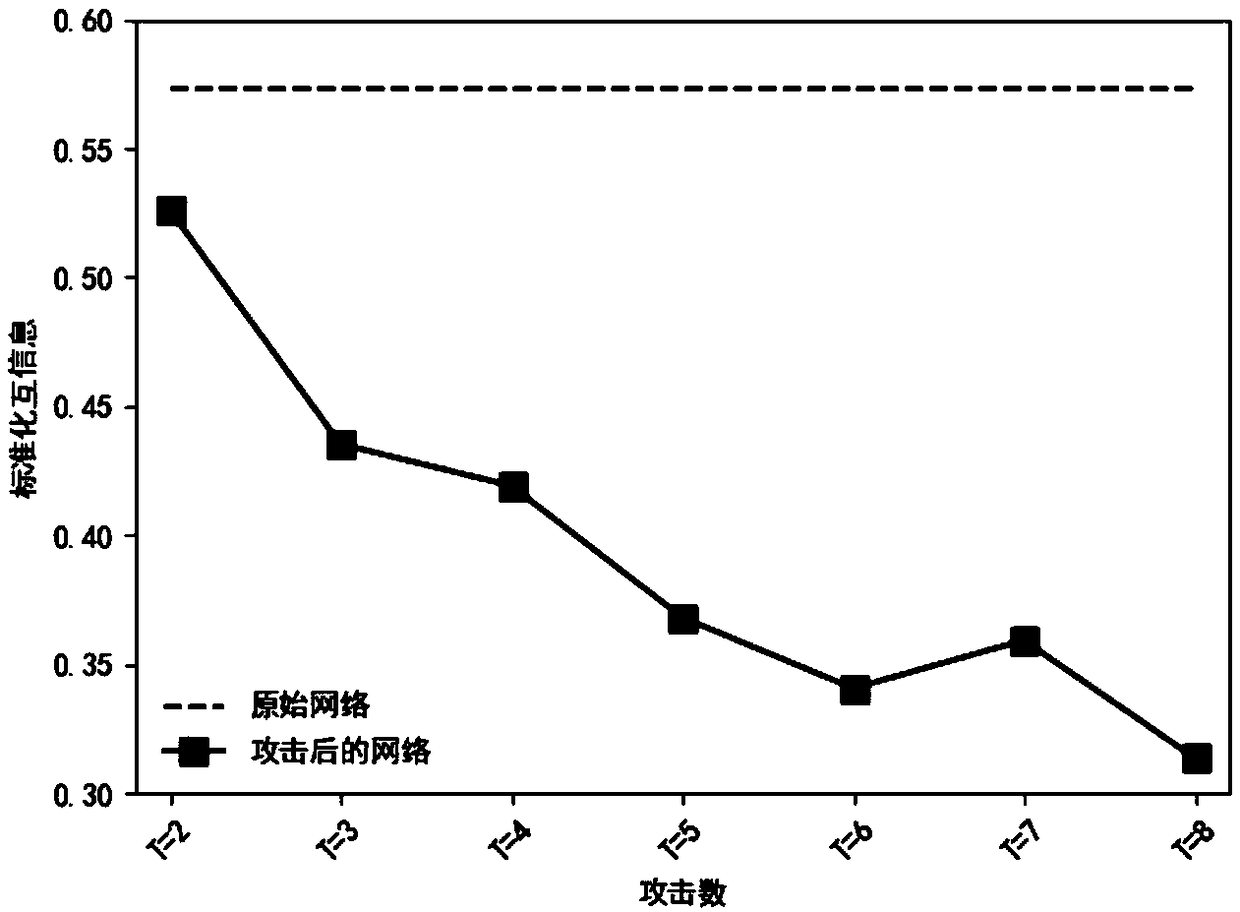
ActiveCN109376544AAvoid over diggingGood attack performanceDigital data information retrievalData processing applicationsCluster algorithmComputer network
The invention provides a method for preventing a community structure in a complex network from being deeply mined. The method comprises the following steps: (1) for a given network, initializing a population according to a set coding mode, sequentially selecting an initial population, crossing, mutating and reserving an elite to obtain an optimal individual, namely, an optimal attack strategy of acomplex network clustering algorithm; (2) according to the optimal individuals, adding or deleting the corresponding edges in the network to obtain the new network after camouflage so as to prevent the community structure in the complex network from being accurately mined. The method for preventing the community structure in the complex network from being excavated in depth provided by the invention effectively reduces the performance of the complex network clustering algorithm and guarantees the privacy safety of the community in the network.
Owner:ZHEJIANG UNIV OF TECH
Martial art arena robot going onto stage in tail slope mode
InactiveCN109966754AFlexible movementHigh-precision detectionSelf-moving toy figuresRemote-control toysEngineeringLaser sensor
The invention relates to a martial art arena robot going onto a stage in a tail slope mode. The martial art arena robot comprises a base plate part, a slope stage going part, an upper layer structure,a shovel attacking device, a sensor module layout, a battery part and a control circuit part. The martial art arena robot goes onto an arena with a certain height by using the tail slope; the stage going speed is high; and the success rate is high. A plurality of laser sensors and grayscale sensors are installed, so that the arena robot accurately detects the edge of the arena, fast recognizes anopponent, and sensitively gives a response. In a control aspect, a serial bus connection mode is used. In a structure aspect, the martial art arena robot has the advantages that materials are saved;the processing is easy; the production period is short; and the transformation is easy, and the like.
Owner:NORTHWESTERN POLYTECHNICAL UNIV
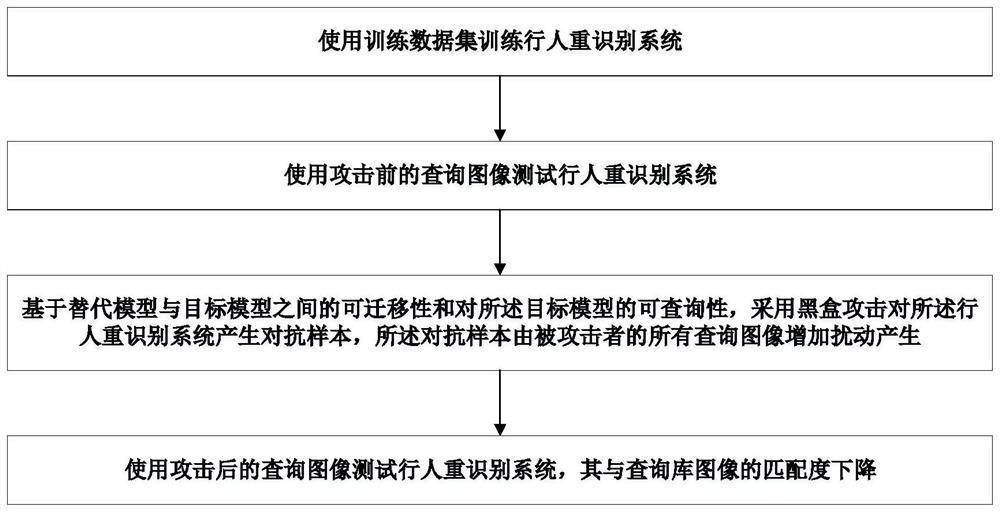
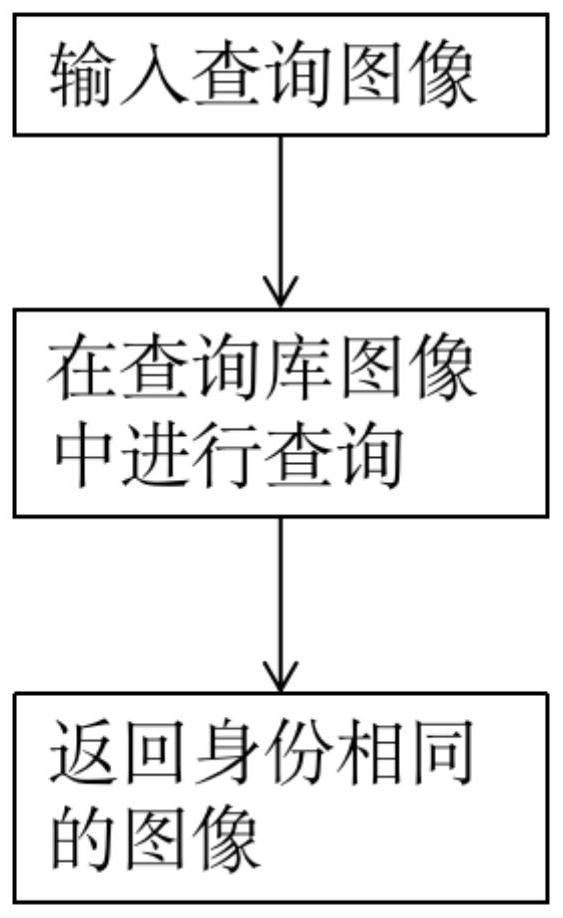
Method for black box attack of pedestrian re-identification system
PendingCN113111963ARealisticReduce cumbersome stepsCharacter and pattern recognitionNeural architecturesTraining data setsEngineering
The invention provides a method for attacking a pedestrian re-identification system. The method comprises the following steps: training the pedestrian re-identification system by using a training data set; testing a pedestrian re-recognition system by using the query image before the attack; based on the mobility between the substitution model and a target model and the inquirability of the target model, black box attack is adopted to generate an adversarial sample for the pedestrian re-recognition system, and the adversarial sample is generated by adding disturbance to all query images of an attacked person; when the attacked query image is used for testing the pedestrian re-recognition system, the matching degree of the pedestrian re-recognition system and the query library image is reduced. The same disturbance is added to all images of an attacked person, so that a corresponding adversarial sample is generated, a new black box attack mode is formed, and the black box attack mode is more practical; time and labor are saved, and the attack effect is good.
Owner:SHENZHEN GRADUATE SCHOOL TSINGHUA UNIV
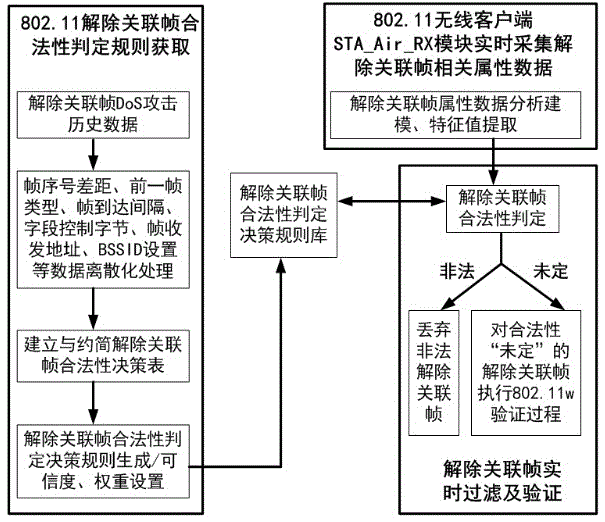
Novel method for preventing DoS attack of wireless disassociation frame based on rough set
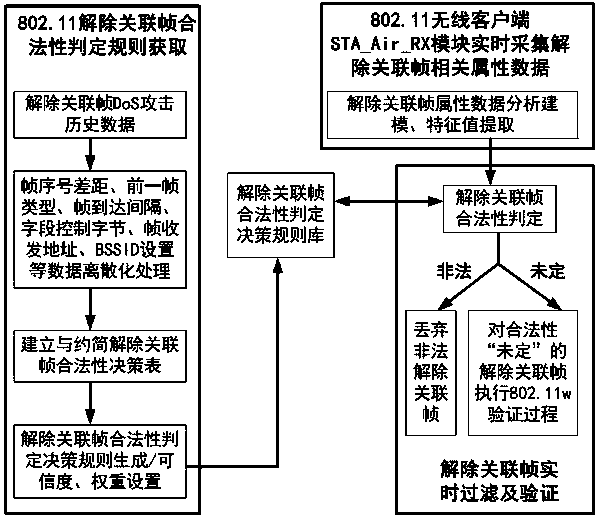
InactiveCN105471879ALegality, Convenient and EffectiveImprove accuracyTransmissionFrame basedDecision table
The invention relates to a novel method for preventing DoS attack of a wireless disassociation frame based on a rough set, and provides a disassociation frame validity decision rule based on various types of characteristic attributes of an 802.11 frame, wherein the characteristic attributes mainly comprises nine parts: frame number difference, the type of a previous frame, a time interval between a frame and the previous frame, field control byte configuration, frame receiver address setting, frame sender address setting, BSSID setting, Reason Code setting, and Duration ID setting. The method comprises the steps: building a decision table for discriminating whether the disassociation frame is legal or not according to the research of WiFi wireless communication features and the attribute characteristics of the disassociation frame; carrying out the attribute reduction of a conventional method which employs nine condition attributes for discriminating whether the disassociation frame is legal based on the rough set theory, wherein the novel method just needs three condition attributes for judging the authenticity of the disassociation frame; and building a novel '802.11w-rough set filtering ' method, wherein the method can enable a WiFi LAN to effectively prevent the DoS attack of the wireless disassociation frame at low and high attack rates.
Owner:SANMING UNIV
Target attack adversarial sample generation method for deep learning model
InactiveCN112183671AConstrained perturbation sizeGuaranteed attack success rateEnsemble learningCharacter and pattern recognitionData setAlgorithm
The invention discloses a target attack adversarial sample generation method for a deep learning model, and belongs to the field of deep learning security. In order to detect blind spots of a deep learning model through a countermeasure attack method and focus on a specific area of the model, the invention designs a target attack countermeasure sample generation method for the deep learning model,which can extract a general mode which is suitable for most samples and contains semantic information missed by the model from a data set of a small number of samples. An adversarial sample capable of stably realizing high-success-rate adversarial attack can be quickly generated. A manifold represented by a polyhedral approximate deep learning model is used, an optimization technology is used tocalculate a minimum disturbance vector required for sending a certain point in a training set to a classification boundary of a region corresponding to a target class on the manifold, multi-point calculation is continuously aggregated, updated and projected, and the above steps are iteratively executed till the attacked target model reaches a preset attack success rate.
Owner:SICHUAN UNIV
Information processing method and device, medium and computing equipment
ActiveCN110020593AGood attack performanceReduce visitsCharacter and pattern recognitionNeural architecturesPattern recognitionInformation processing
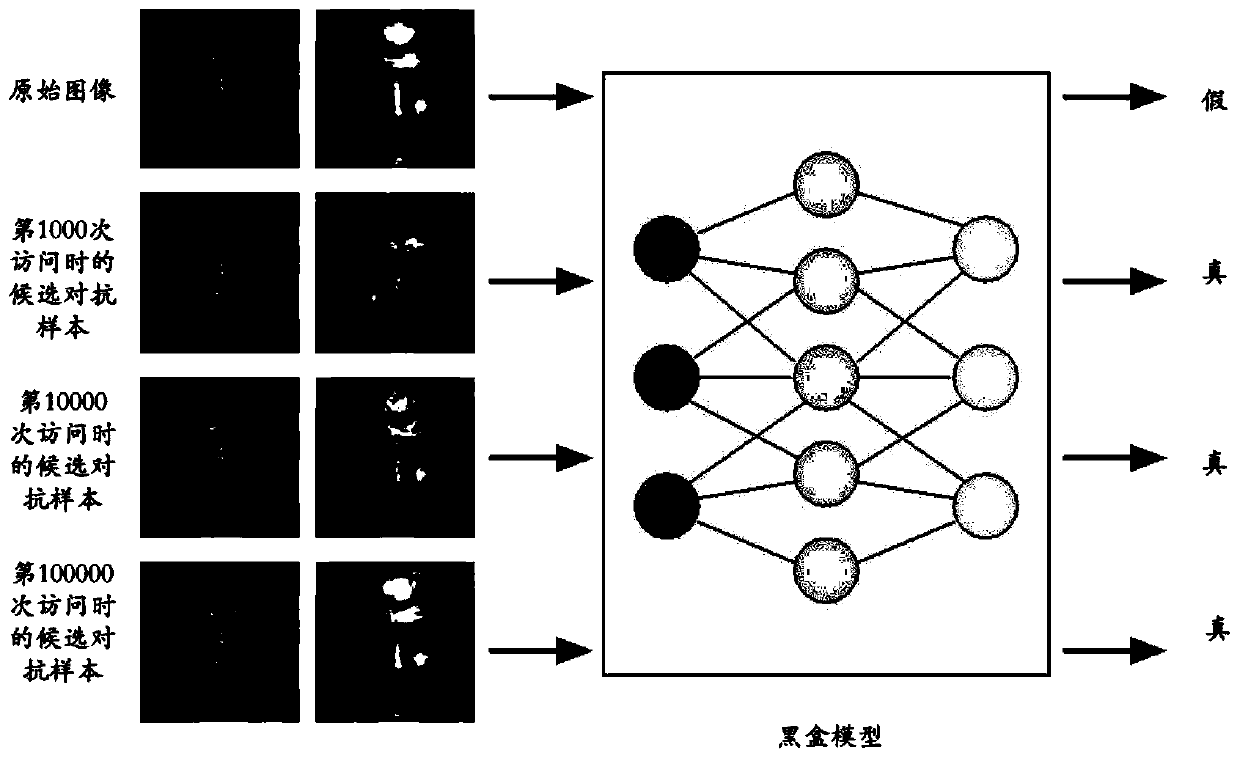
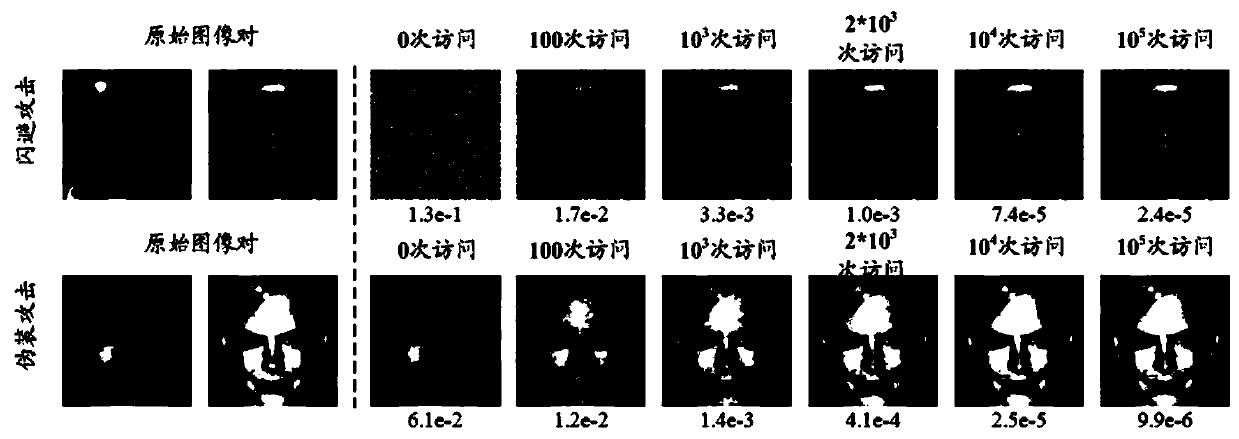
The embodiment of the invention provides an information processing method and device, a storage medium and computing equipment. The information processing method comprises the steps of obtaining a predetermined image recognition model; for the image recognition model, based on an input-output relationship obtained by accessing an image recognition model by using candidate confrontation samples searched in an input space each time, solving an optimal solution of a preset optimization problem through iterative calculation of gradually reducing the distance between the candidate confrontation sample and the original sample, wherein the preset optimization problem comprises the steps of obtaining the candidate confrontation sample with the minimum distance from the original sample in an inputspace; and enabling the candidate confrontation samples searched in each iteration to successfully attack the image recognition model. According to the technology provided by the invention, the imagerecognition model given for resisting the successful attack of the sample can be generated under the condition that the model structure and parameters are not obtained, the attack effect on the face recognition model is especially good, and compared with the prior art, the access frequency can be greatly reduced.
Owner:TSINGHUA UNIV
Chaos-based initial vector generation algorithm and IP core thereof
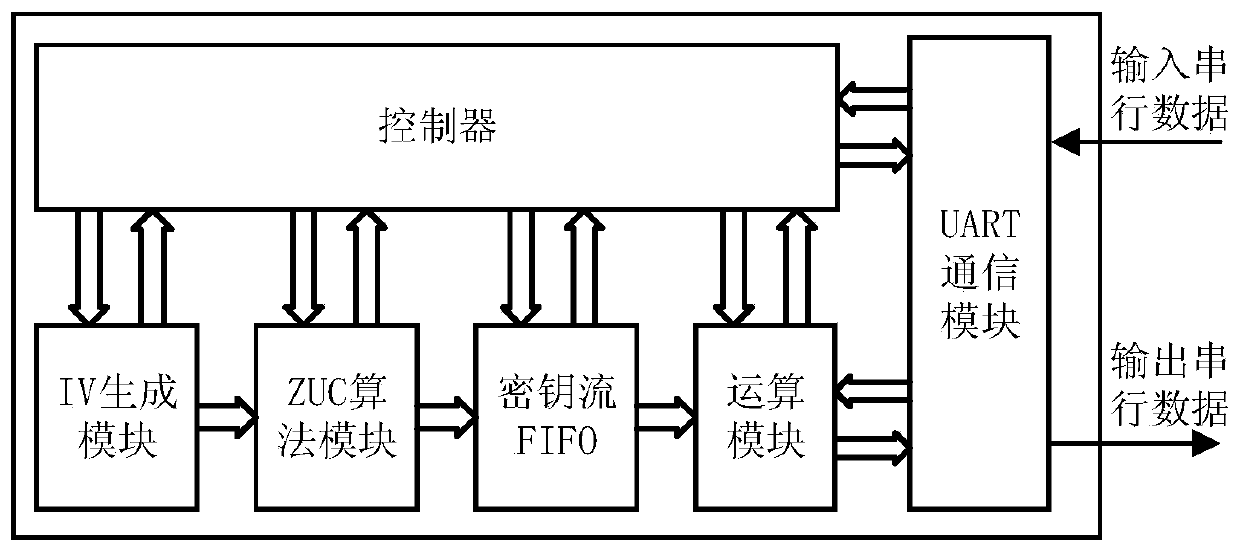
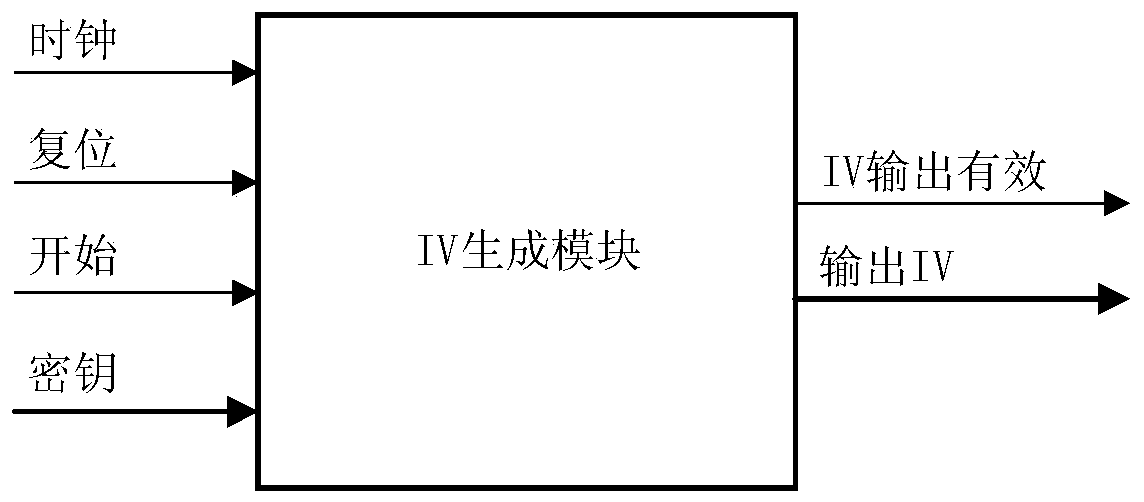
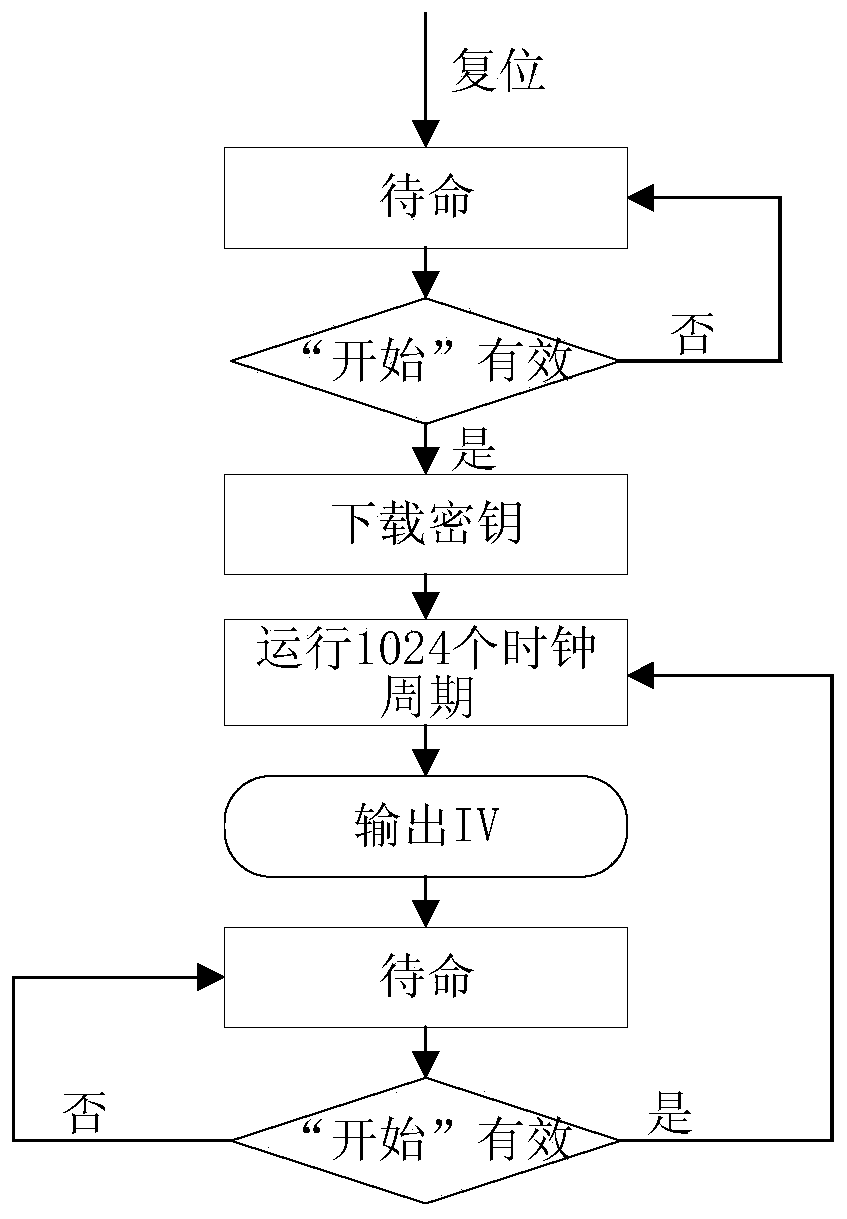
ActiveCN110995405AIncrease unpredictabilityGood attack performanceSecuring communication by chaotic signalsCryptographic attack countermeasuresKeystreamParallel computing
The invention provides a chaos-based initial vector generation algorithm and an IP core thereof, and the generation algorithm comprises the steps: inputting a 32-bit initial value x0 into a Logistic chaos-based sequence generator, and dividing a 128-bit initial key KEY of a ZUC encryption algorithm into 16 32-bit keys [i]; assigning the key [0] to 32 bits x0, and calculating x1 = 4 * 0 (1-x0); assigning the key [i] to the key [i-1], then assigning the x1 to the key [15], and intercepting a 128-bit sequence at the end of all x1 sequences generated in sequence every 1024 bits as an initial vector; the IP core for generating the algorithm comprises an initial vector generation module generated by the method, a ZUC encryption algorithm module, a key stream FIFO module, an operation module, a UART communication module and a controller module. According to the method, the good randomness of the chaotic pseudo-random sequence is utilized, so that the unpredictability of the initial vector isgreatly improved.
Owner:HEILONGJIANG UNIV
Federal learning-oriented sample poisoning attack resisting method
PendingCN114764499ALow toxicityReduce aggressionCharacter and pattern recognitionPlatform integrity maintainanceAttackEngineering
A federated learning-oriented confrontation sample poisoning attack method comprises the following steps: defining the following scenes: assuming that m participants participate in training, mgt; the k-th participant is assumed to be an attacker, and the attack target is that the performance of the federal learning global model on the test set is as poor as possible after the local model parameters participate in aggregation; the method comprises the steps that firstly, an attacker adds certain adversarial disturbance which cannot be perceived by human eyes to local private training samples to generate toxic adversarial samples, and local training is carried out based on the samples; secondly, in order to dominate the training process of the global model, an attacker improves the training learning rate in the local training process so as to accelerate the generation of malicious model parameters; and finally, an attacker uploads local model parameters to a server side to participate in aggregation so as to influence a global model. Under the attack of the method, the performance of the federal global model is remarkably reduced, and the attack method shows good generalization performance.
Owner:DALIAN UNIV OF TECH
A multifunctional shield with guide slots
A multifunctional shield with guide grooves, relating to the field of police shields, comprising a shield body, a handle, a pad and an elbow locking fixture, the shield body includes a shield body front and a shield body back, the pad It is connected to the back of the shield body, the handle and the elbow locking fixture are connected to the shield body through the pad, the front of the shield body is convex, and the front of the shield body is provided with a left guide groove group and the right guide groove group, the left guide groove group is composed of a plurality of left guide grooves, the right guide groove group is composed of a plurality of right guide grooves, and the shield body also includes a longitudinal axis, so The left guide groove extends from the longitudinal axis to the left edge of the front of the shield body along the inclined downward direction of the outer convex surface, and the left guide groove group and the right guide groove group are arranged symmetrically along the longitudinal axis, The shield includes unloading mode and rebound attack mode when used.
Owner:BENGBU ZHIDA TECH CONSULTING CO LTD
SIFT-based blind watermarking method for dwt‑svd against geometric attacks
ActiveCN103955878BGood resistance to attackGood attackImage data processing detailsSingular value decompositionWatermark method
The invention relates to a DWT-SVD geometric attack prevention blind watermark method based on SIFT. The method comprises a watermark embedding method and a watermark extraction method. The watermark embedding method includes the steps that discrete waterlet transformation is conducted on an original image, a low-frequency sub-band of the original image is divided into small blocks, singular value decomposition is conducted on each small block, chaotic encryption is conducted on watermarks to be embedded, and the watermarks are embedded into the maximum singular value of each small block through an optimal quantitative method, the SIFT feature points of a watermark image are stored as secret keys, the types of geometric attacks are judged according to the secret keys, and correction is conducted. The watermark extraction method is the inverse process of the watermark embedding method and includes the steps of correction of attacked images, watermark extraction and watermark decryption and restoration. According to the method, by the utilization of the rotation, zoom and translation invariance of the SIFT feature points and the combination of the advantages of DWT and SVD in the digital watermark aspect, robustness on geometric attacks is remarkably improved.
Owner:HANGZHOU DIANZI UNIV
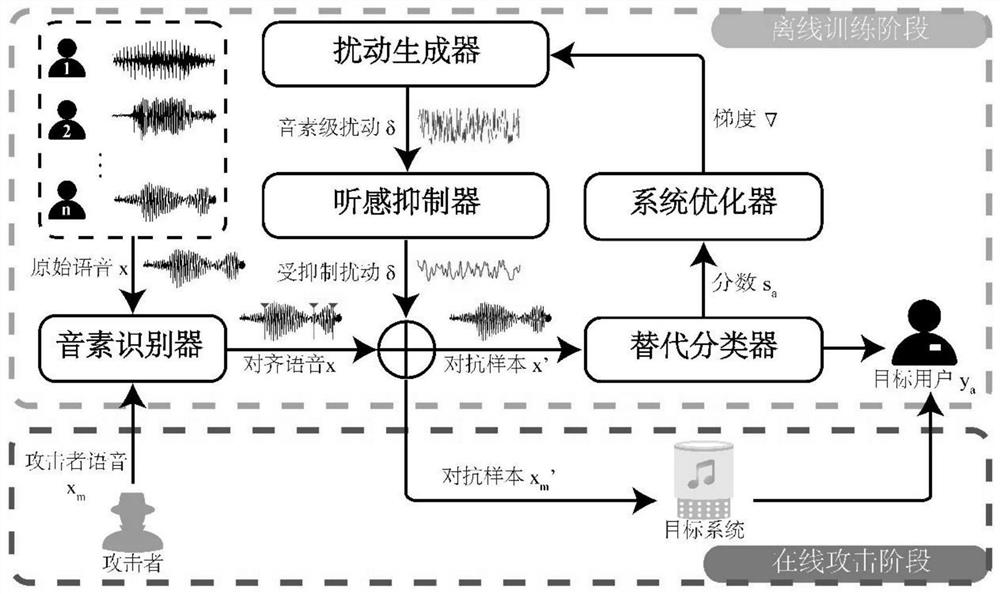
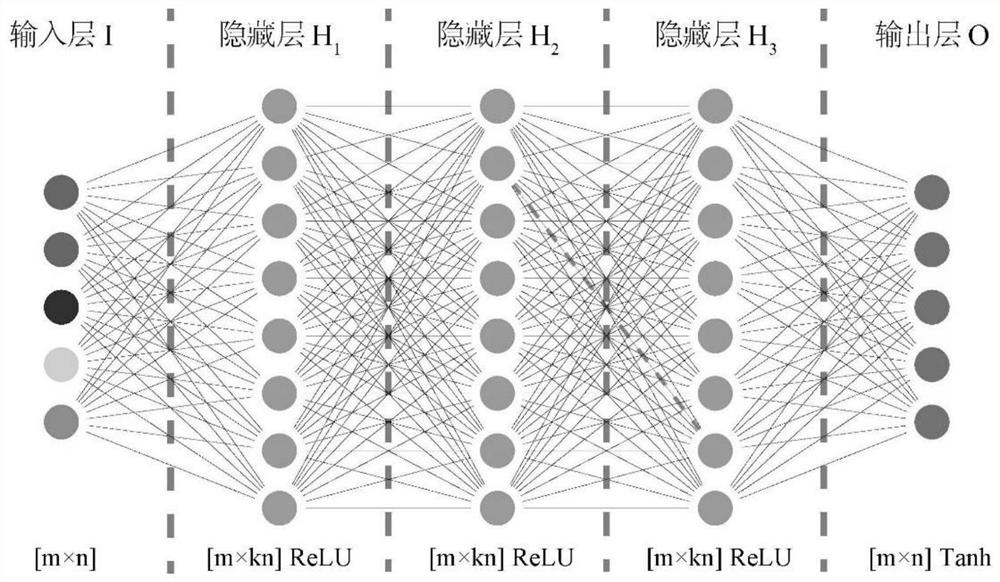
Phoneme-level voiceprint recognition confrontation sample construction system and method based on neural network generative model
PendingCN114093371AImprove production efficiencyMeet real-time needsSpeech analysisNeural architecturesPattern recognitionPhoneme recognition
The invention discloses a phoneme-level voiceprint recognition confrontation sample construction system and method based on a neural network generative model. The system comprises a phoneme recognizer, a disturbance generator, a hearing suppressor, an alternative classifier, and a system optimizer, the suppressed disturbance generated by the hearing suppressor and the aligned voice generated by the phoneme recognizer are superposed to generate an adversarial sample, the adversarial sample is classified by the substitution classifier, scores are sent to the system optimizer, gradients are reversely propagated to the disturbance generator for iterative updating, and a trained phoneme disturbance generator is obtained. According to the method, the phoneme information in the voice is creatively fused to carry out disturbance construction, the phonemes in the voice are recognized and positioned by using the phoneme recognizer, and the fine-grained general adversarial disturbance is generated at the phoneme level, so that the adversarial disturbance generated in one step can be reused for any voice text input, finally, text-independent and input-independent general adversarial sample generation is realized, and the generation efficiency of the adversarial sample is greatly improved.
Owner:ZHEJIANG UNIV
Method and system for predicting overall elastic-plastic motion response of ship under underwater explosion
InactiveCN104657611BImprove the design levelGood attack performanceSpecial data processing applicationsUnderwater explosionMotion parameter
The invention discloses a ship whole elastic-plastic movement response predication method and system under the action of underwater explosion. The method comprises the following steps: S1, simplifying a ship into a free ship body beam with an equal section; S2, dividing load pressure of the free ship body beam into five time phases under the action of the underwater explosion; S3, solving movement displacement of the free ship body beam in the five time phases under the action of the underwater explosion; S4, solving a bending moment of the ship body beam; S5, solving forward plastic movement parameters of the ship body beam; S6, solving backward elastic unloading movement parameters of the ship body beam; S7, solving backward plastic movement parameters of the ship body beam; S8, solving forward plastic movement parameters of the ship body beam. The invention further provides a system for realizing the method. According to the method and the system disclosed by the invention, the ship plastic movement process is analyzed on the basis of comprehensively considering the impact effect on the whole ship body by impact waves and air bubble loads, and engineering predication of ship whole elastic-plastic movement deformation under the action of the underwater explosion can be accurately and conveniently realized.
Owner:NAVAL UNIV OF ENG PLA
Method and device for generating an adversarial example
ActiveCN111737691BImprove attack abilityGood attack performanceCharacter and pattern recognitionPlatform integrity maintainanceMorphingComputational physics
The embodiment of this specification provides a method and device for generating an adversarial sample. The method includes: obtaining the current adversarial sample to be strengthened in the current round of iterations; and presetting the first number of current adversarial samples in the direction of reducing the target loss function Geometric deformation to obtain a deformed image; perform a second pixel-by-pixel update on the deformed image to obtain the first adversarial sample; perform a third pixel-by-pixel update on the current adversarial sample to obtain a second adversarial sample; determine the first adversarial sample and In the second adversarial example, the adversarial example with a smaller loss value is used as an updated adversarial example; when the stop iteration condition is met, the updated adversarial example is used as the final adversarial example; when the stop iteration condition is not met, the next round is performed based on the updated adversarial example iterate. It can make the generated adversarial samples more aggressive, so as to provide targeted defense.
Owner:ALIPAY (HANGZHOU) INFORMATION TECH CO LTD
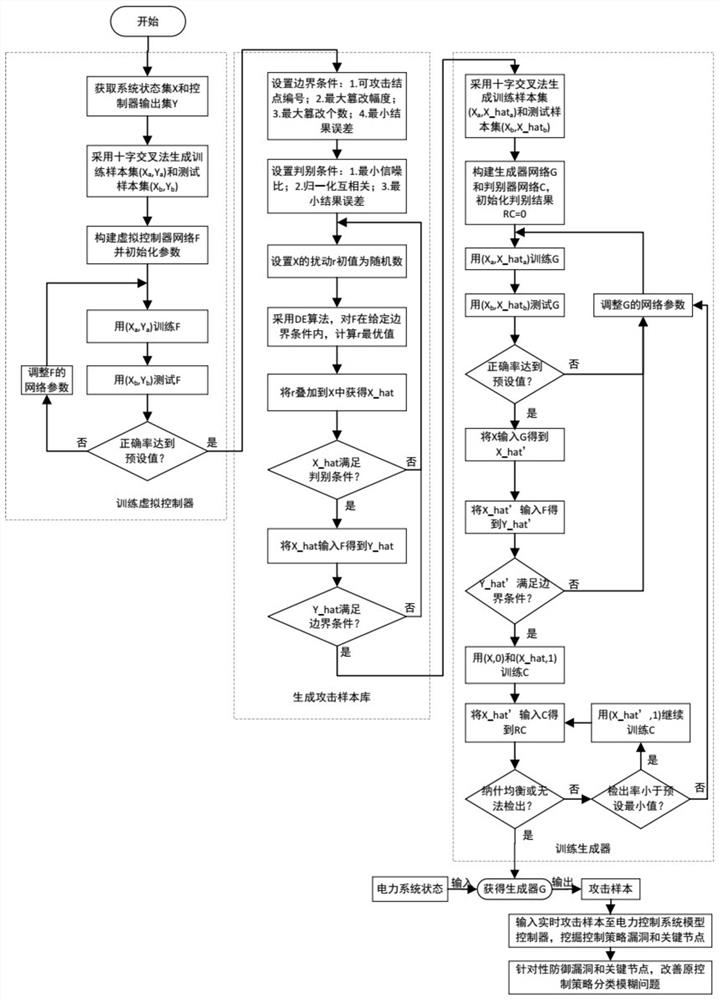
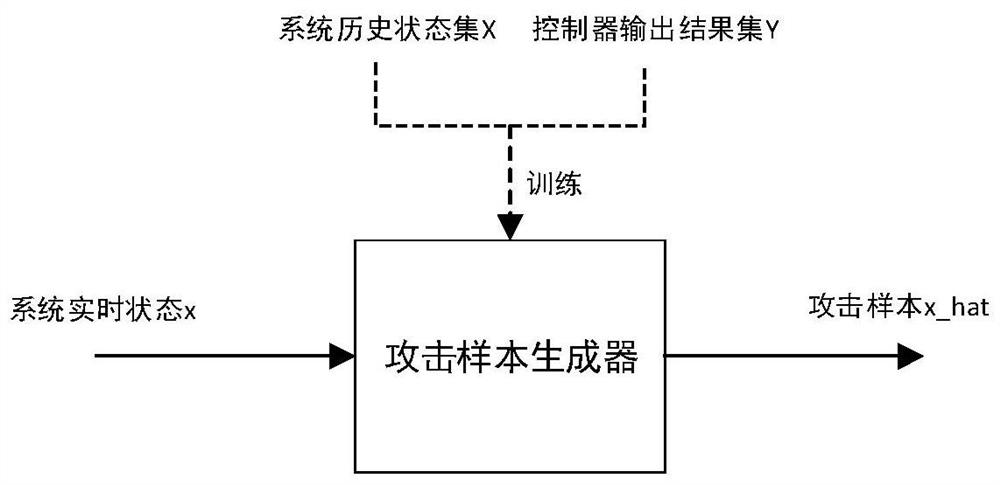
An active defense method applied to power control system network attack
ActiveCN112367291BAvoid defectsReduce disturbanceCharacter and pattern recognitionNeural architecturesPower control systemElectric power system
The invention discloses an active defense method applied to a network attack on an electric power control system. A virtual controller network, a virtual attack sample library and an attack sample generator are constructed through a black box method, and a virtual attack event is constructed, so as to investigate and repair the electric power system. , the active defense method of the present invention is easy to implement, easy to deploy in the power control system, so as to improve the stability of the system, and has a good effect on the investigation of concealed attacks.
Owner:ELECTRIC POWER RESEARCH INSTITUTE OF STATE GRID NINGXIA ELECTRIC POWER COMPANY +1
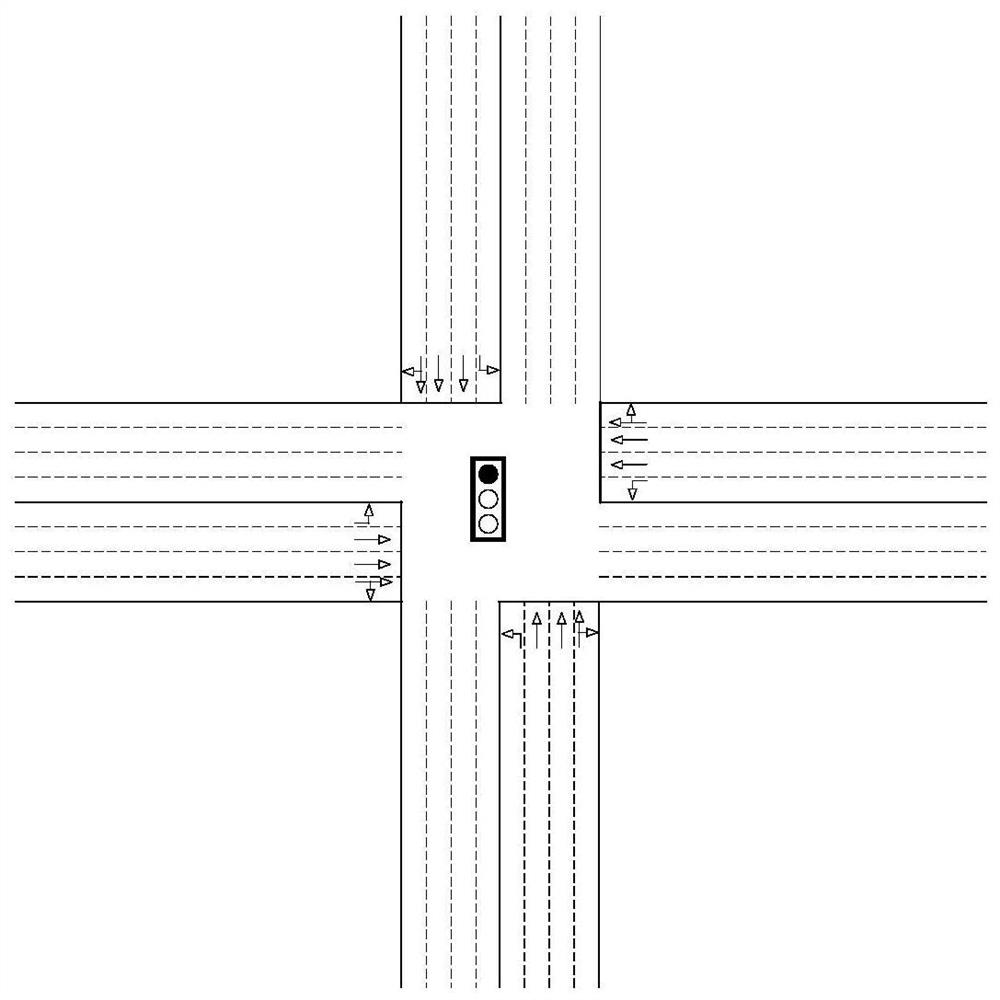
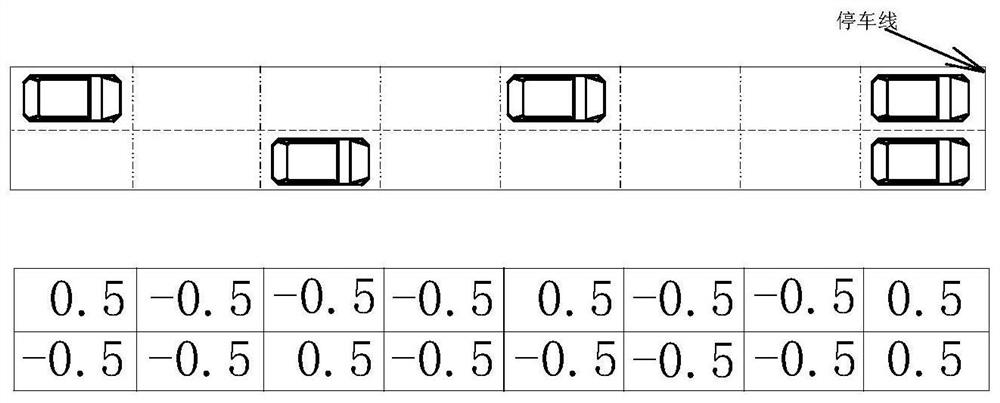
An Adversarial Perturbation Generation Method for Intelligent Single Intersection Based on CW Attack
ActiveCN113487870BImplement targeted attacksLess attacksControlling traffic signalsDetection of traffic movementSimulationEngineering
An adversarial disturbance generation method for intelligent single intersection based on CW attack. According to the existing DQN algorithm in deep reinforcement learning, an adaptive intelligent traffic light model for controlling single intersection is trained. The degree of preference judges whether the current state has attack value, and generates adversarial samples based on the CW attack combined with the optimal gradient sorting and the discreteness of the input state (ie, the spatial distribution of the vehicle in the corresponding road section). Finally, through the smoothness of the traffic flow in SUMO, the vehicle Changes in queue length and overall waiting time test the effect of the attack. The invention reduces the probability of an attack being discovered, and the attack effect is good.
Owner:ZHEJIANG UNIV OF TECH
A Step Size Adaptive Adversarial Attack Method Based on Model Extraction
ActiveCN109948663BGood attack performanceStrong non-black box attack capabilityCharacter and pattern recognitionNeural architecturesModel extractionData set
The invention discloses a step-size self-adaptive adversarial attack method based on model extraction, step 1, constructing an image data set; step 2, training a convolutional neural network on the image set IMG, as a target model to be attacked, and step 3, calculating The cross-entropy loss function realizes the model extraction of the convolutional neural network and initializes the gradient value and step size g of the iterative attack 1 ; Step 4, form a new adversarial sample x 1 ; Step 5, recalculate the cross-entropy loss function, and use the new gradient value to update the step size of adding anti-noise in the next step; Step 6, repeat the process of inputting the image-calculating the cross-entropy loss function-calculating the step size-updating the confrontation sample; Step 5 Repeat the operation T‑1 times to get the final iterative attack adversarial sample x′ i , and input the adversarial sample into the target model for classification, and obtain the classification result N(x′ i ). Compared with the prior art, the present invention can achieve better attack effect, and has stronger non-black-box attack capability than the current iterative method.
Owner:TIANJIN UNIV
Shield with guiding protective function
The invention discloses a shield with a guiding protective function. The shield comprises a shield body, handheld handles, a protective pad and elbow locking and fixing devices, wherein the shield body comprises a shield body front surface and a shield body back surface; the protective pad is connected with the shield body back surface; each handheld handle and the corresponding elbow locking and fixing device penetrate through the protective pad and are connected with the shield body; the shield body front surface is an outwardly convex arc surface, or an inverted-V-shaped surface or a circular-arc-shaped surface; each lateral side is provided with a wrinkle surface consisting of continuous guiding grooves; each guiding groove transversely extends from an apex intersecting line towards a lateral point intersecting line; the shield body front surface is provided with protective devices; each protective device is arranged in the manner that the protective device extends from the corresponding lateral point intersecting line towards the shield front surface; each protective device comprises a first bent edge; and each V-shaped protective device is formed by the corresponding V-shaped bent edge and the corresponding lateral edge. According to the shield disclosed by the invention, an attacking object can be guided and blocked through the guiding grooves, so that good protection is realized.
Owner:BENGBU ZHIDA TECH CONSULTING CO LTD
Multifunctional shield with capture devices
Owner:临沂高新自来水有限公司
Novel Anti-Wireless Disassociation Frame Dos Attack Method Based on Rough Sets
InactiveCN105471879BLegality, Convenient and EffectiveImprove accuracyTransmissionFrame basedDecision table
The invention relates to a novel method for preventing DoS attack of a wireless disassociation frame based on a rough set, and provides a disassociation frame validity decision rule based on various types of characteristic attributes of an 802.11 frame, wherein the characteristic attributes mainly comprises nine parts: frame number difference, the type of a previous frame, a time interval between a frame and the previous frame, field control byte configuration, frame receiver address setting, frame sender address setting, BSSID setting, Reason Code setting, and Duration ID setting. The method comprises the steps: building a decision table for discriminating whether the disassociation frame is legal or not according to the research of WiFi wireless communication features and the attribute characteristics of the disassociation frame; carrying out the attribute reduction of a conventional method which employs nine condition attributes for discriminating whether the disassociation frame is legal based on the rough set theory, wherein the novel method just needs three condition attributes for judging the authenticity of the disassociation frame; and building a novel '802.11w-rough set filtering ' method, wherein the method can enable a WiFi LAN to effectively prevent the DoS attack of the wireless disassociation frame at low and high attack rates.
Owner:SANMING UNIV
A method and system for predicting the whip motion response of a ship under the action of an underwater explosion
InactiveCN104743086BImprove the design levelGood attack performanceDefensive equipmentOffensive equipmentUnderwater explosionPeak value
The invention discloses a ship whipping motion response prediction method and system under a combined effect of underwater explosive shock waves and bubbles. The ship whipping motion response prediction method comprises the steps that step 1, a ship is equivalent to a uniform cross section free ship body girder, and therefore the prediction of ship motion responses are equivalent to the predication of free ship body girder motion responses; step 2, the load pressure process of the free ship body girder under the underwater explosion effect is divided into five time phases, and a shock wave pressure peak value, a bubble pulsation phase negative pressure peak value and a bubble first time pulsation pressure peak value are collected; step 3, motion displacements in the five time phases of underwater explosion of the free ship body girder are solved. The invention further provides a ship whipping motion response prediction system. The ship whipping motion response prediction method and system comprehensively consider the shock effect of the shock wave and the bubble load on the whole ship, the underwater explosion load pressure is simplified to be five phases, the motion displacements of a ship in different phases are calculated, and therefore project prediction of ship elastic motion or whipping motion responses under medium and distal field explosion effect is achieved accurately, simply and conveniently.
Owner:NAVAL UNIV OF ENG PLA
Special nano iron powder for damaging satellite through spraying
The invention relates to a nano metal powder material, in particular to a special nano iron powder for damaging satellite through spraying which can lead a satellite to lose reconnaissance function for ever. The preparation method includes the steps as follows: processing raw materials into nano iron powder under the temperature of 10-5 DEG C below zero and under the condition of setting the high frequency cutting times as 4,500-5,500 times / minute, then respectively sorting the powder materials on which the particles ( D3 is equal to 41nm D25 is equal to 62.1nm D50 is equal to 125nm, D75 is equal to 177.2nm, and D97 is equal to 230.3nm) are distributed, cladding for anti-oxidation and processing the surface. 75 percent of aggressive nano iron powder particles can be deeply embedded in the surface of the whole satellite to completely cause the satellite blind.
Owner:王惠民
Directed attack anti-patch generation method and device
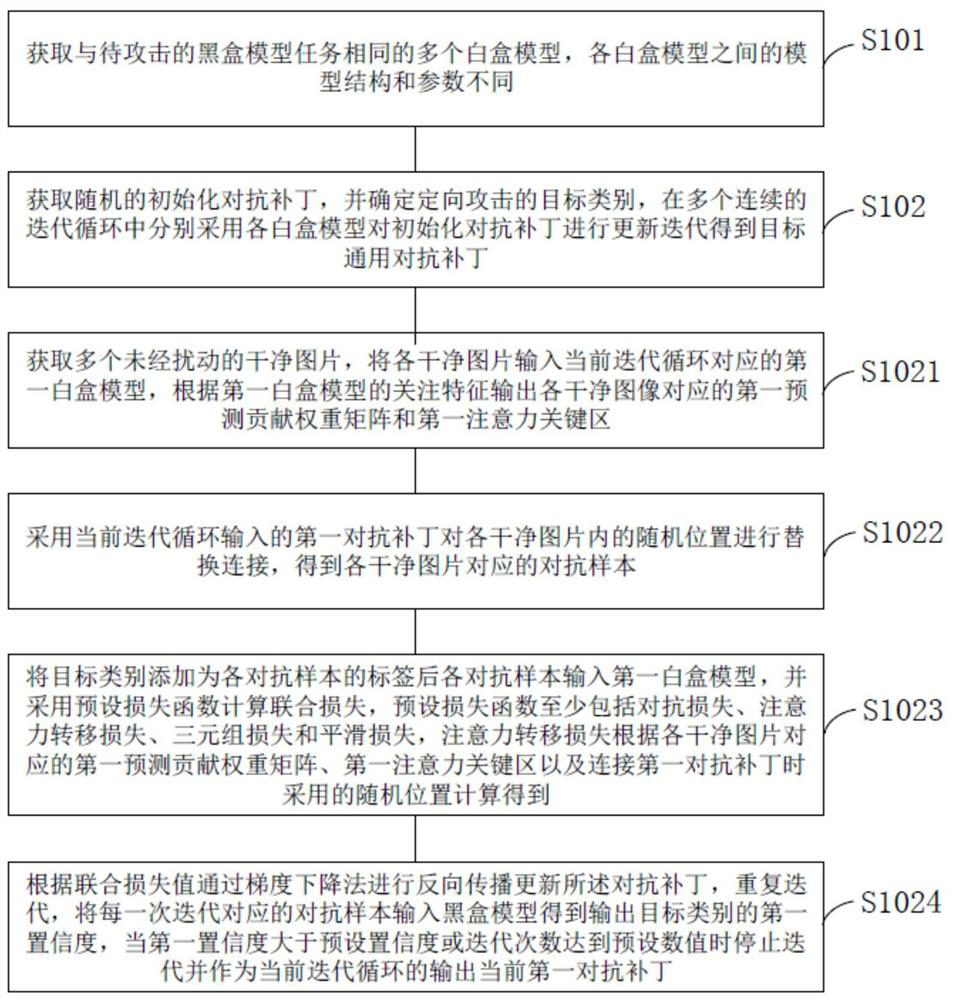
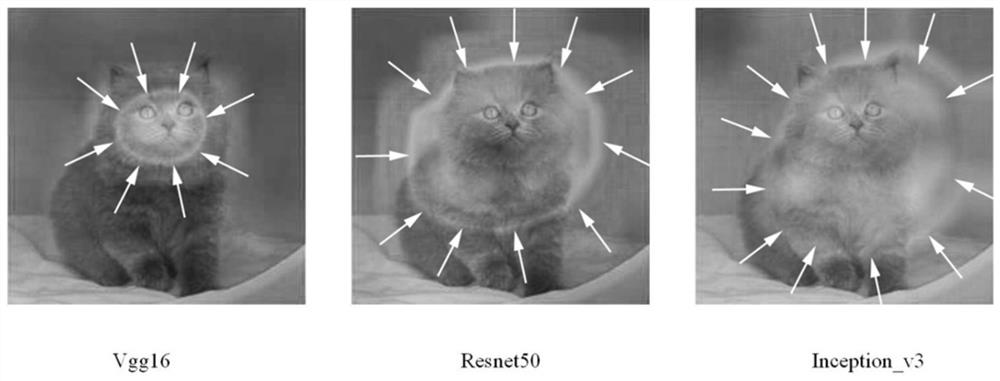
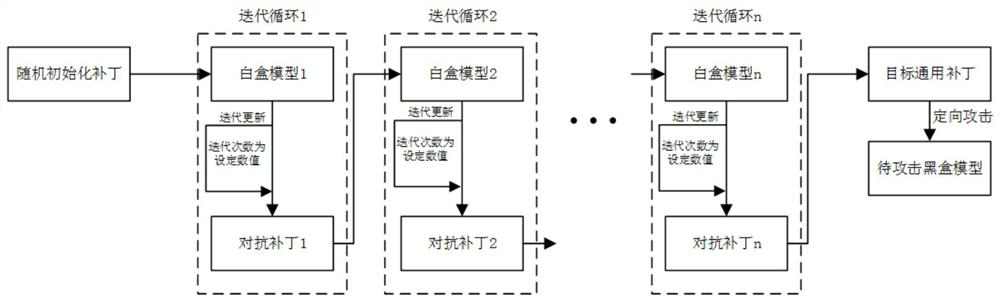
ActiveCN113255816BGood attack performanceIncrease success rateCharacter and pattern recognitionNeural architecturesAlgorithmBox model
The present invention provides a method and device for generating a directional attack adversarial patch. The method adopts a plurality of consecutive white-box models with different structures to iteratively update the adversarial patch, so that the obtained target general adversarial patch can be better for the black-box model with unknown structure. attack effect. By introducing the triplet loss, the success rate of the output target category can be improved during the directed attack. By introducing the attention shift loss, the migration effect of the target general adversarial patch to the model attention area can be improved, so as to greatly improve the directional attack effect of the target general adversarial patch. By introducing a smoothing loss, it is possible to reduce the gap between the pixel points of the target common adversarial patch, which is not easy to attract the attention of the human eye. Furthermore, by adding anti-patches, targeted attacks can be carried out at the physical and digital levels at the same time, which is easier to implement.
Owner:BEIJING UNIV OF POSTS & TELECOMM
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com