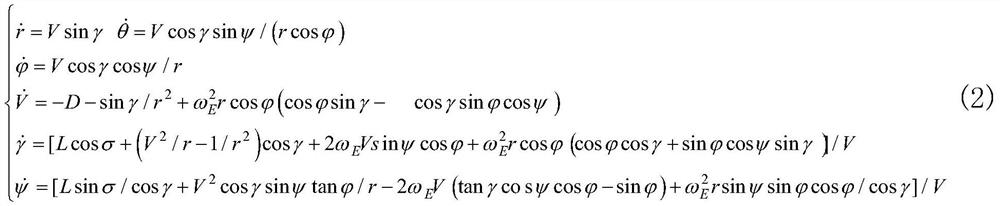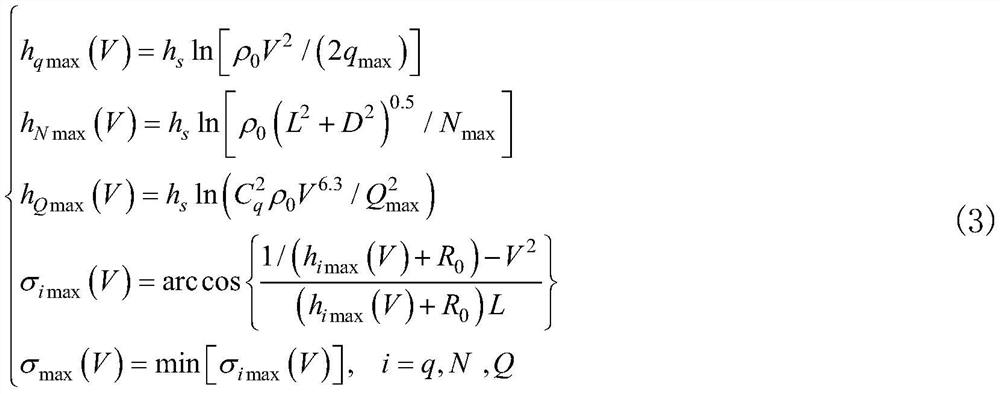Patents
Literature
69results about How to "Increase unpredictability" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
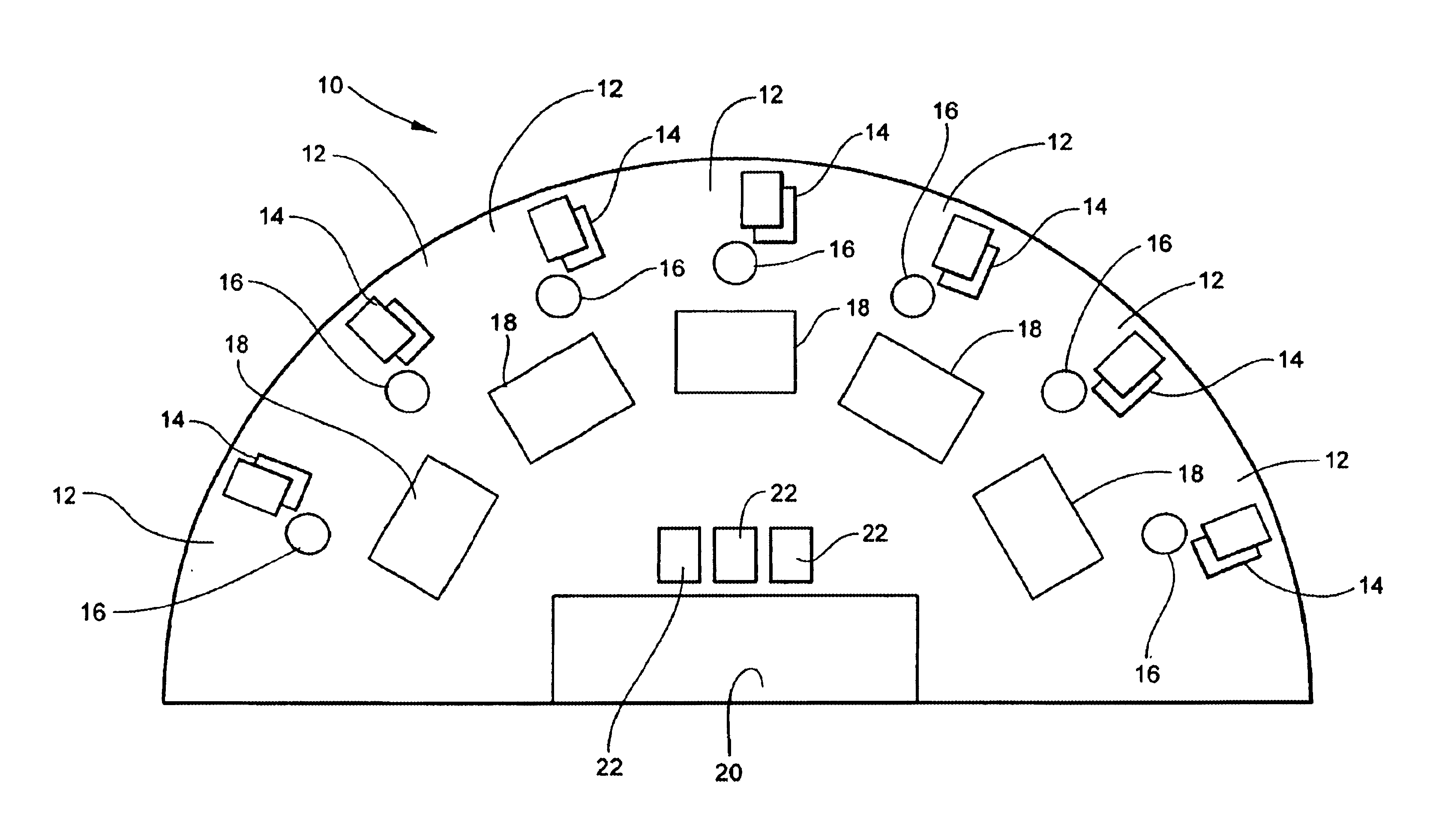
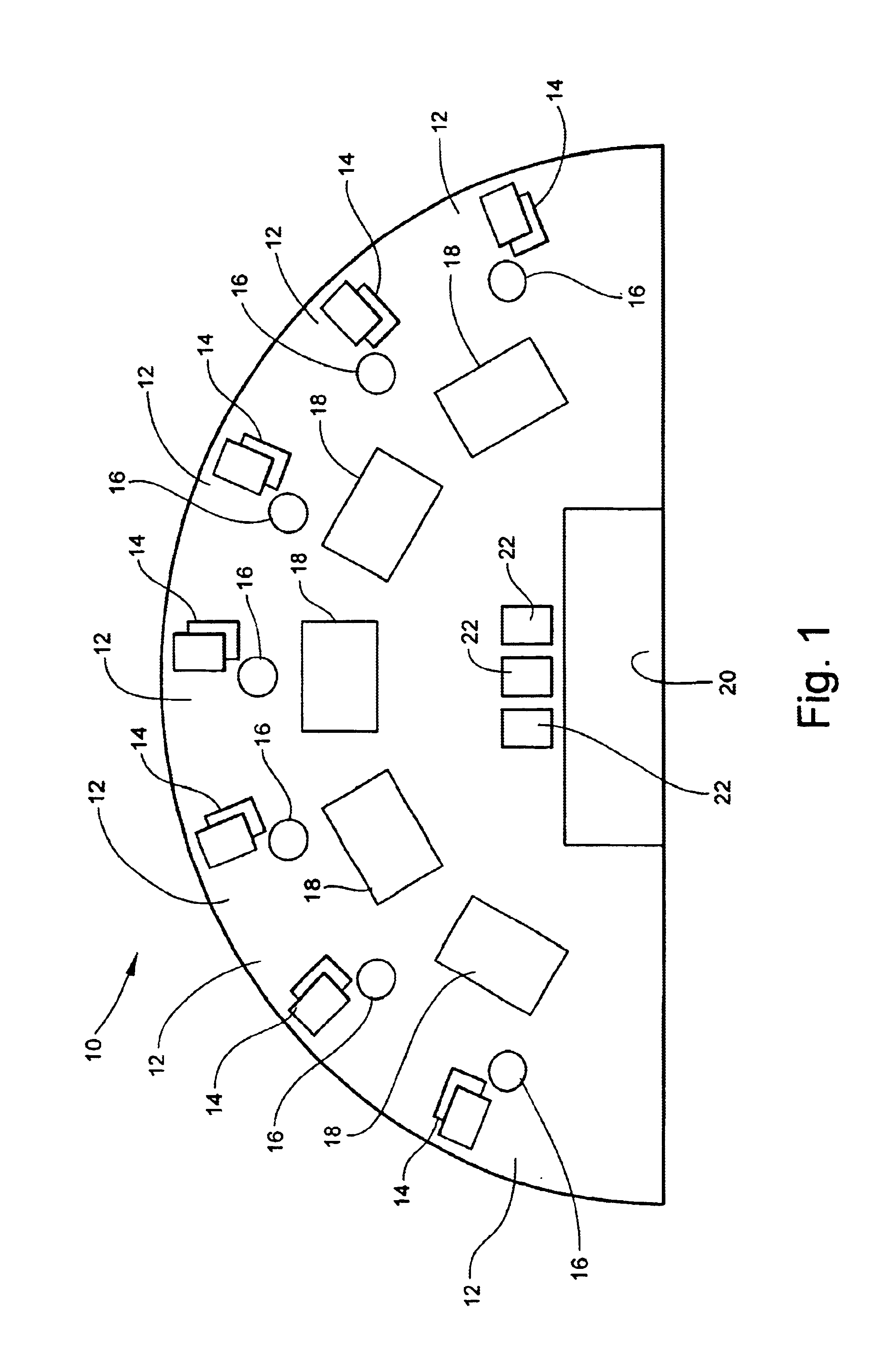
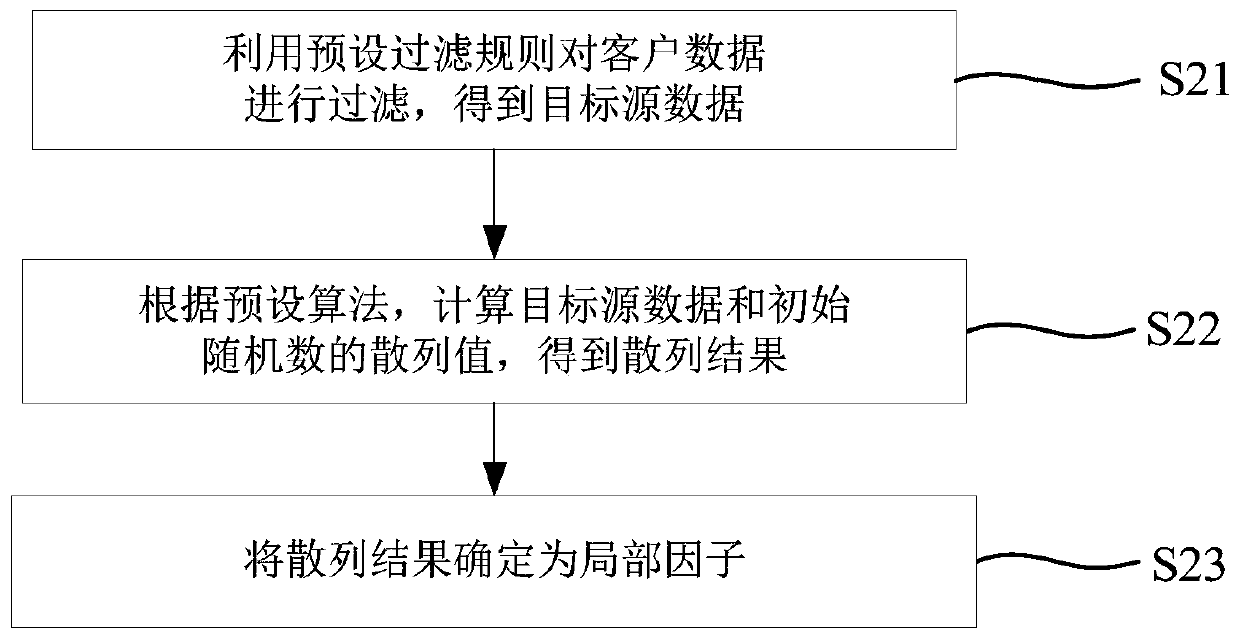
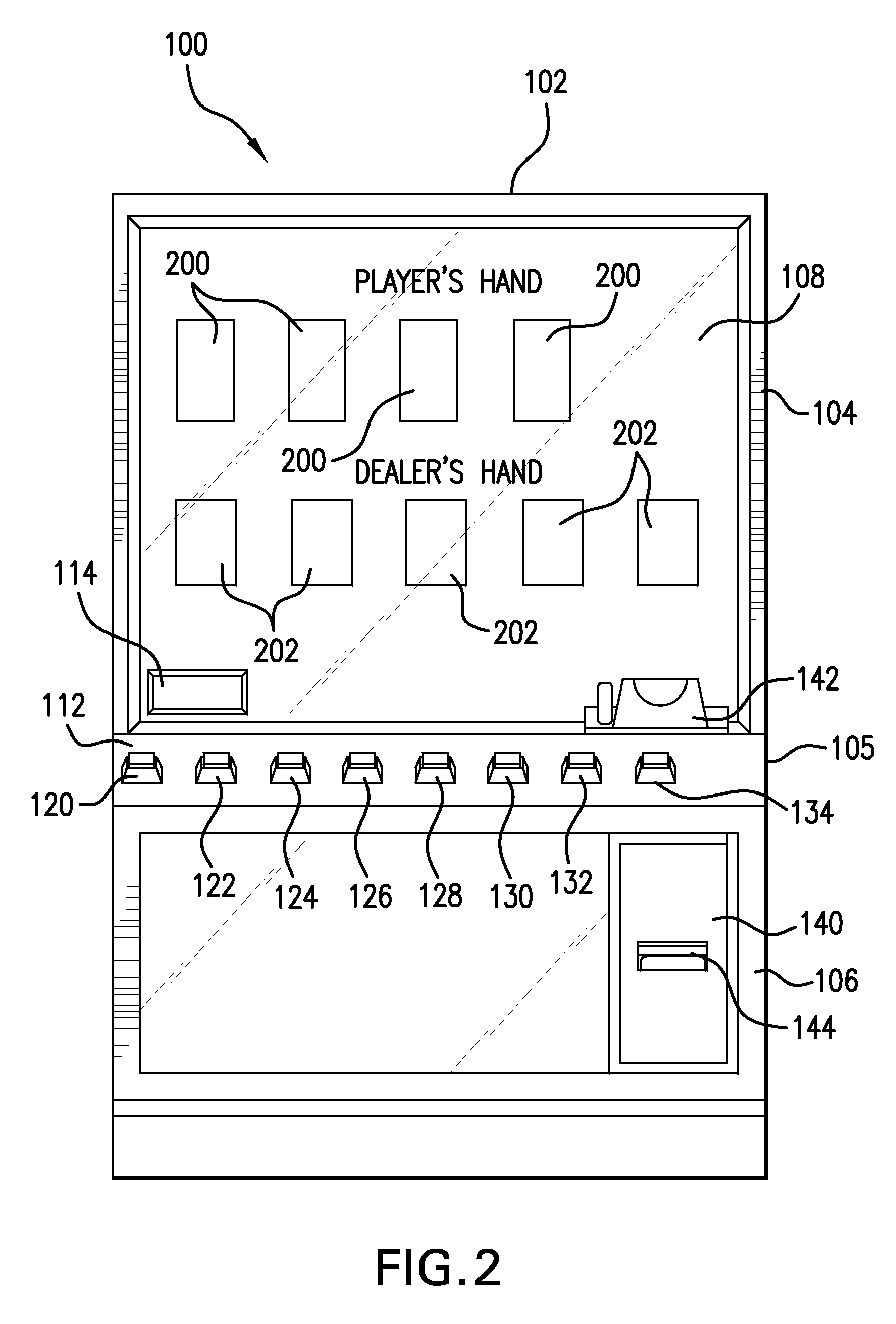
Method for playing modified blackjack with poker option
Owner:PATRONI ANTHONY F +1
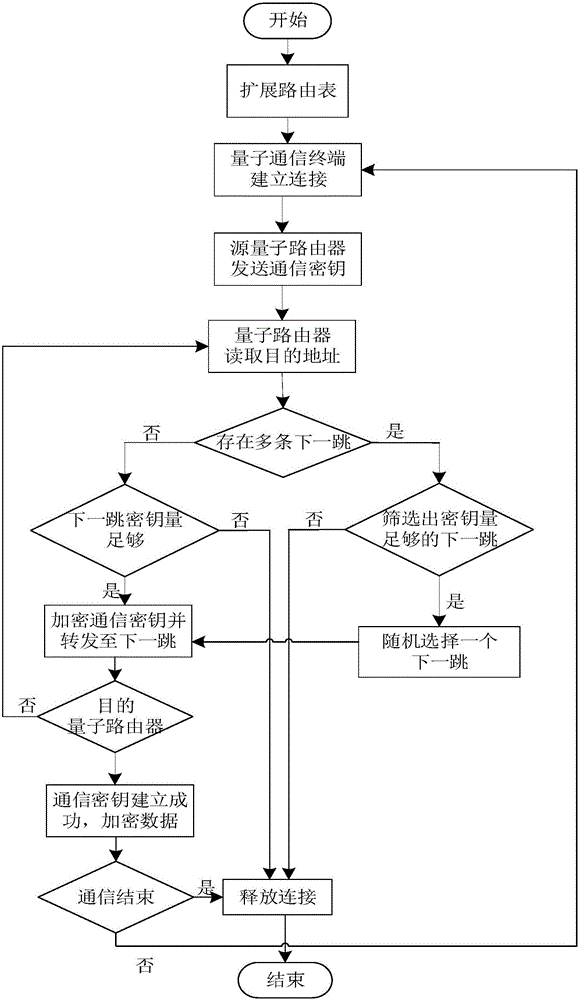
Random routing method in quantum secret communication network
ActiveCN106230582AReduce consumptionImprove service efficiencyKey distribution for secure communicationData switching networksComputer hardwarePredictability
The invention discloses a random routing method in a quantum secret communication network and mainly aims to solve the problem of low safety of a secret key caused by a unique negotiation path and high predictability of the path of a communication secret key in the prior art. The technical scheme of the random routing method are that by improving a distance vector-based routing algorithm expansion routing list, multiple next-hops are added to a quantum router arriving at a certain target address, and thus, multiple shortest paths from a source quantum router to a target quantum router are obtained; and by considering the secret key quantity on a link, on the condition that multiple next-hop routing nodes with enough secret key quantity exists, a next-hop is randomly selected from the next-hop routing nodes and the communication secret key is transmitted hop by hop until the communication secret key is transmitted to the target quantum router, thereby achieving random performing of secret key negotiation on multiple paths. According to the invention, secret key consumption is reduced, safety of the secret key during the secret key negotiation process is improved; and the random routing method can be used for the quantum secret communication network.
Owner:XIDIAN UNIV
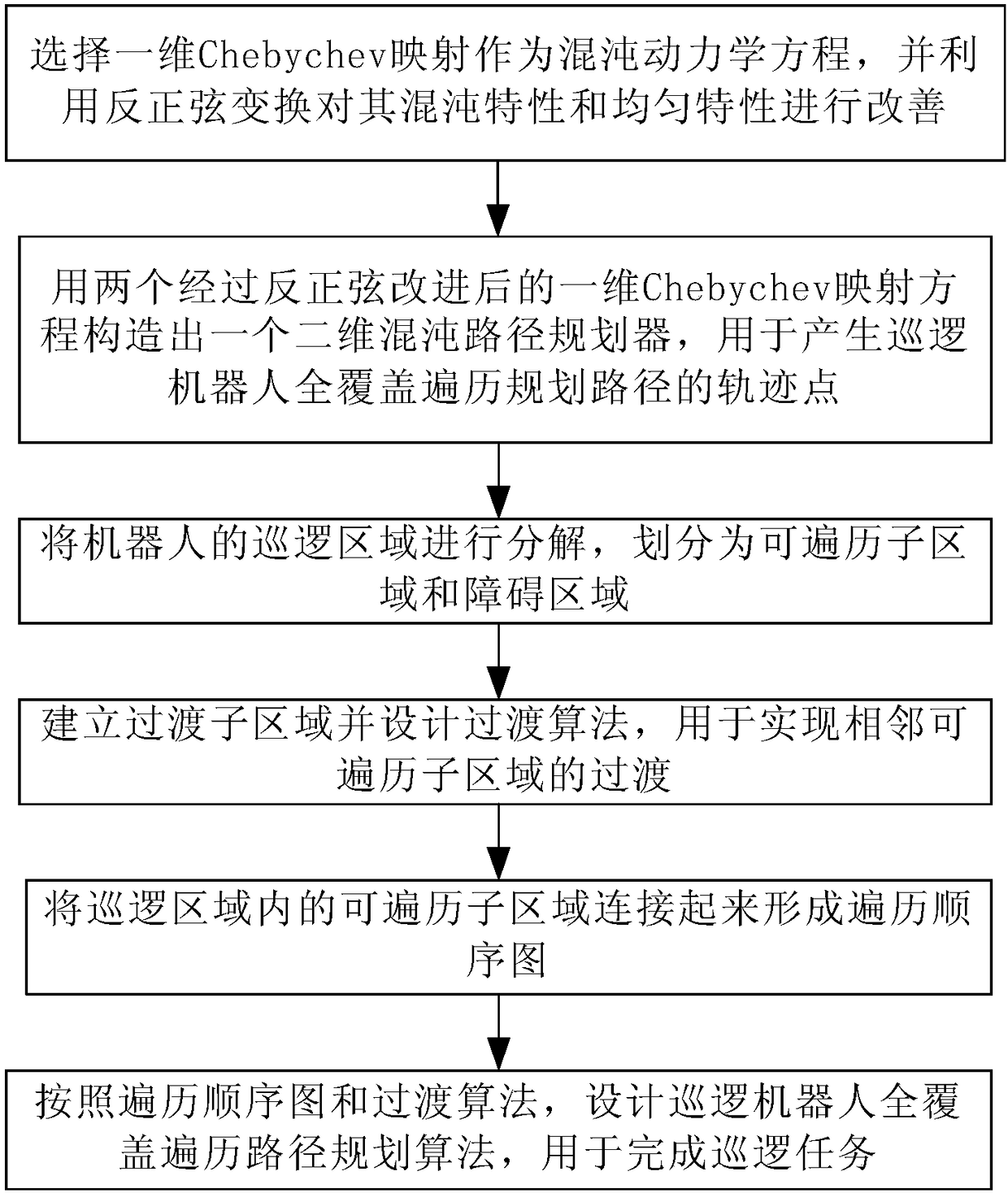
Design method of patrol robot full-coverage traversal path planning algorithm
InactiveCN108255178AIncrease coverageImprove work efficiencyPosition/course control in two dimensionsDynamic equationSequence diagram
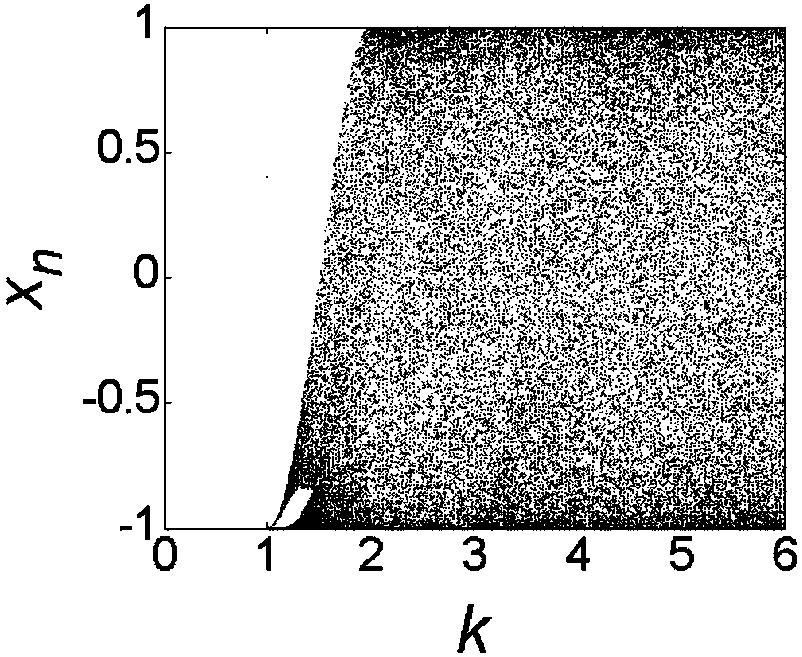
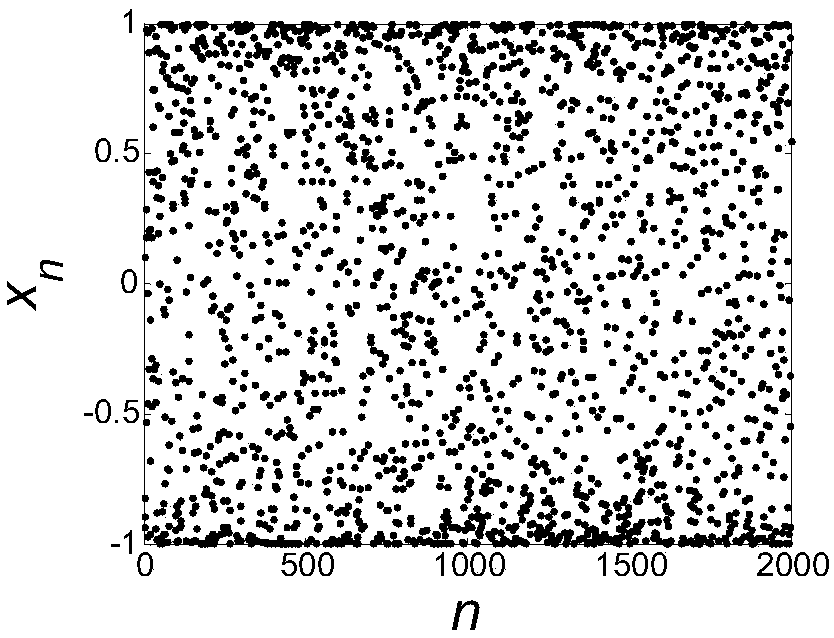
The invention discloses a design method of a patrol robot full-coverage traversal path planning algorithm. The method includes the following steps that: a one-dimensional Chebychev mapping is selectedas a chaotic dynamic equation, and inverse sine transformation is utilized to improve the chaotic characteristic and uniform characteristic of the chaotic dynamic equation; two inverse sine-improvedone-dimensional Chebychev mapping equations are adopted to construct a two-dimensional chaotic path planner; the patrol area of a robot is decomposed into traversable sub-regions and obstacle regions;transition sub-regions re established, and a transition algorithm is designed; the traversable sub-regions in the patrol area are connected to form a traversal sequence diagram; the patrol robot full-coverage traversal path planning algorithm is designed according to the traversal sequence diagram and the transition algorithm, and the patrol robot full-coverage traversal path planning algorithm can be used for completing a patrol task. The algorithm of the invention has the advantages of simplicity, low repetition rate and high coverage rate, and can ensure the randomness and unpredictabilityof the patrol task while ensuring full coverage of the patrol area.
Owner:SHANDONG UNIV OF TECH
Mimicry tamper-proof method of distributed file system
InactiveCN104766025ATampering smallIncrease randomnessDigital data protectionSpecial data processing applicationsTamper resistanceDistributed File System
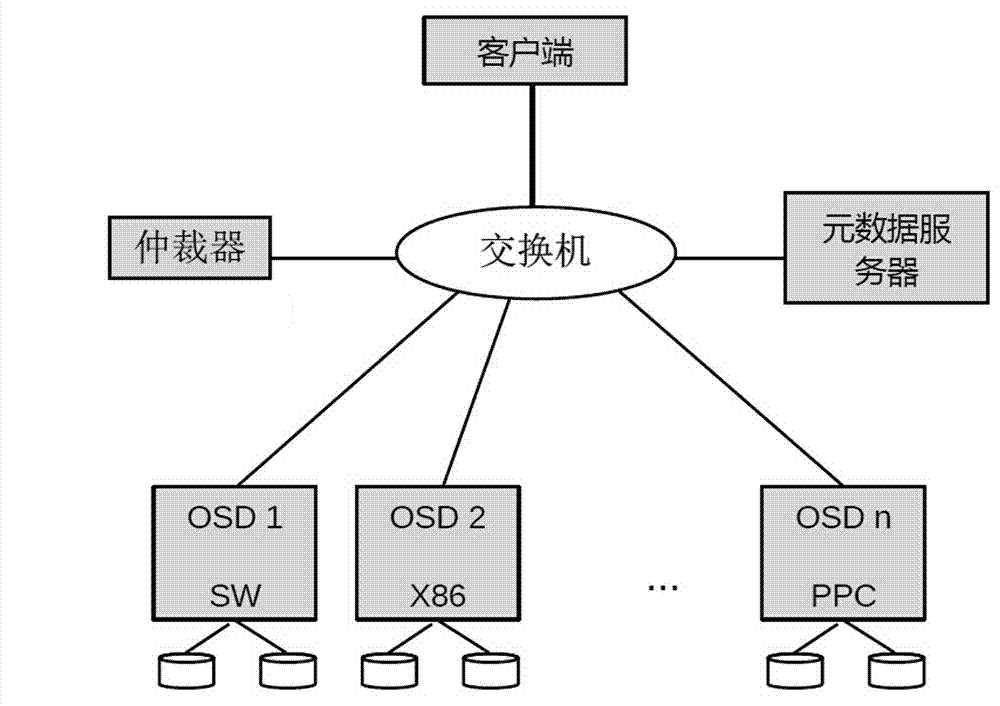
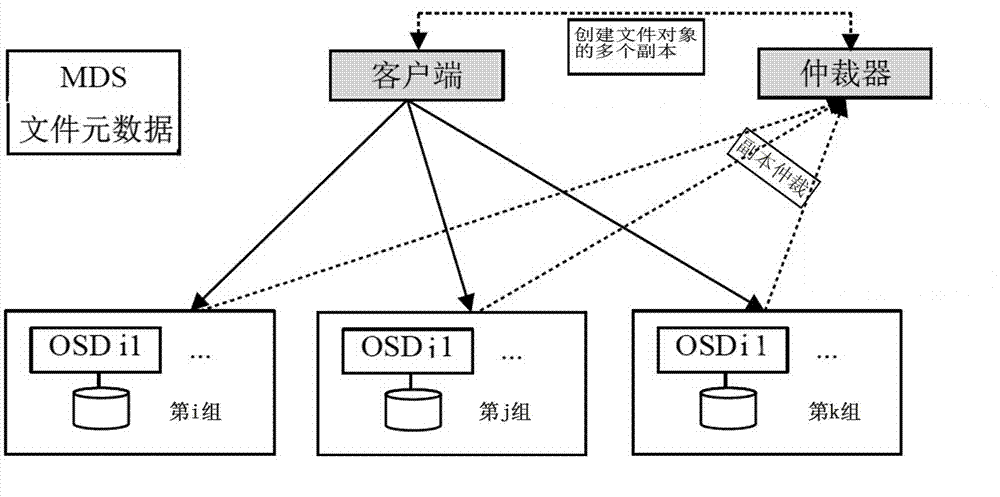
The invention discloses a mimicry tamper-proof method of a distributed file system and accordingly the problem that files are tampered with in the distributed file system in the prior art is solved. The mimicry tamper-proof method comprises the following steps of step 1, creating a plurality of copies for every file object to be written in different types of data nodes respectively and step 2, adding an arbitrator to evaluate every copy, selecting reserved copies according to different purposes respectively and deleting the other copies. According to the mimicry tamper-proof method of the distributed file system, a hijacker can only obtain file objects in a certain data node even if the data node is hijacked; every file object is only a fragment of an actual file and accordingly the hijacker is difficult to determine a file to which the object belongs and the position of the object in the file and accordingly the hijacker is difficult to accurately tamper with the file; the modification on the file objects by the hijacker does not necessarily adopted by the arbitrator and accordingly the security of the file system is greatly improved.
Owner:THE PLA INFORMATION ENG UNIV
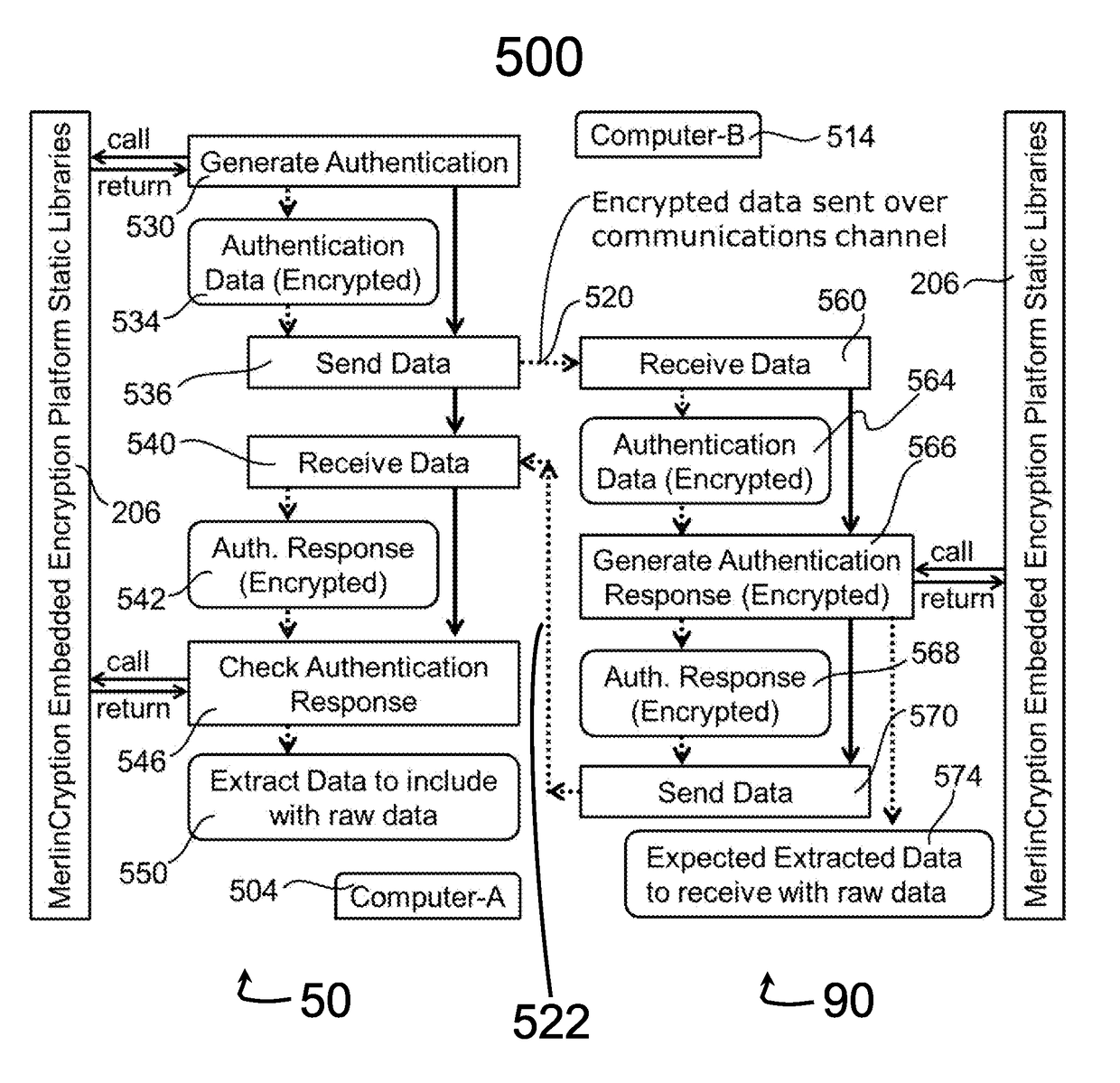
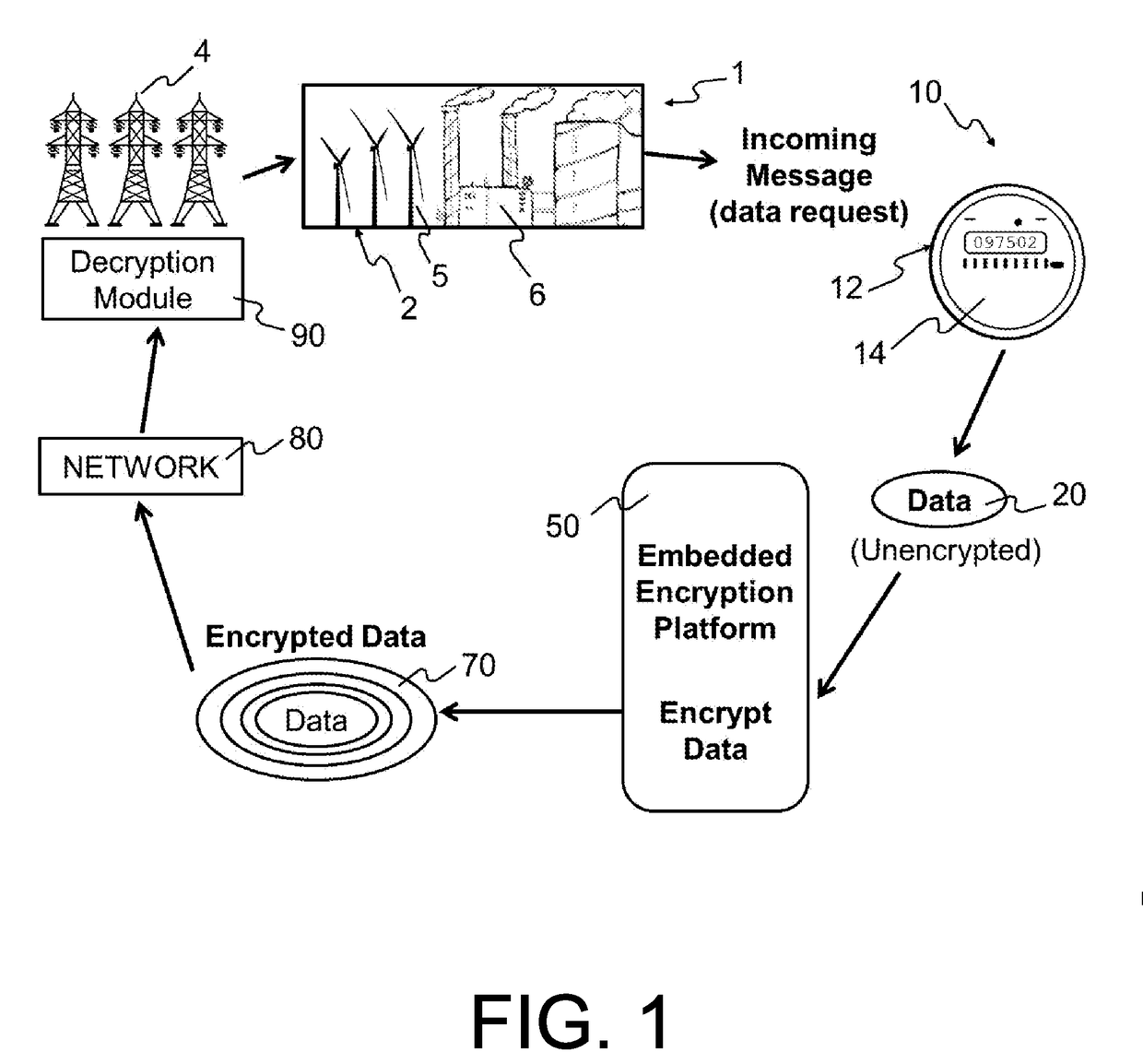
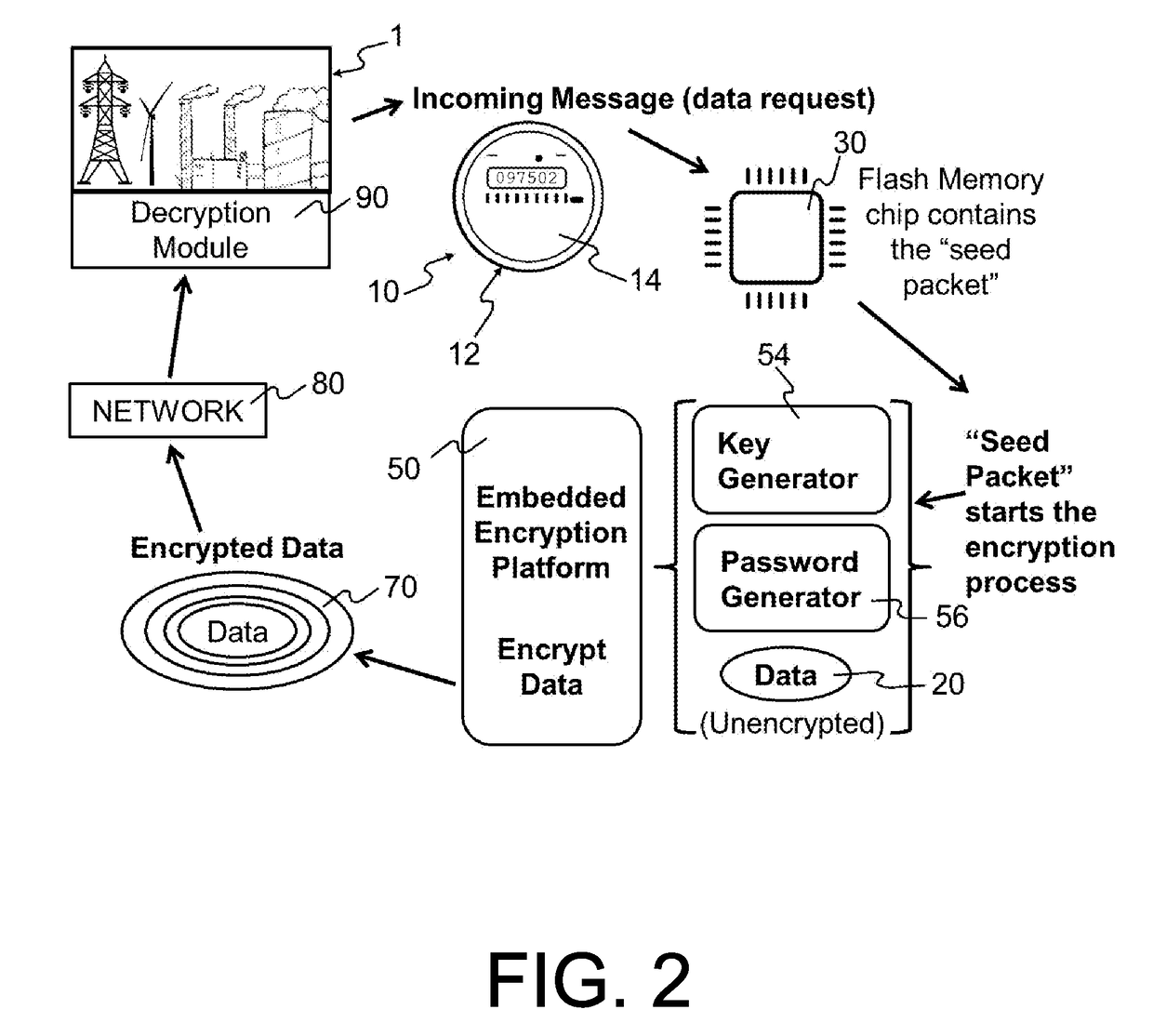
Embedded encryption platform comprising an algorithmically flexible multiple parameter encryption system
InactiveUS20170099144A1Improves unpredictabilityIncrease unpredictabilityKey distribution for secure communicationUser identity/authority verificationDisk encryptionEncryption system
A machine-to-machine (M2M) partner automates all program parameter calculations through scripting or programming during an end-to-end encryption and decryption process. A platform dynamically scripts or programs the calculation of the encryption parameters and automatic response to alarms and alerts or to protect data transfers. The dynamic scripting effectively causes the same platform to be a different custom version for each value of parameters. Different custom versions of the platform encryption engines are not interoperable with each other or with a standard version. Variable and flexible multi-faceted unpredictable authentication methods authorize communication nodes. The platform performs multiple-stage checking of version, key, and password. The platform controller scrubs memory before exiting. A “Seed Packet” of data is used algorithmically to generate a sequence of random data to both generate and make use of an encryption key and password. The algorithmic process steps are themselves subject to change.
Owner:SOBEL PREM
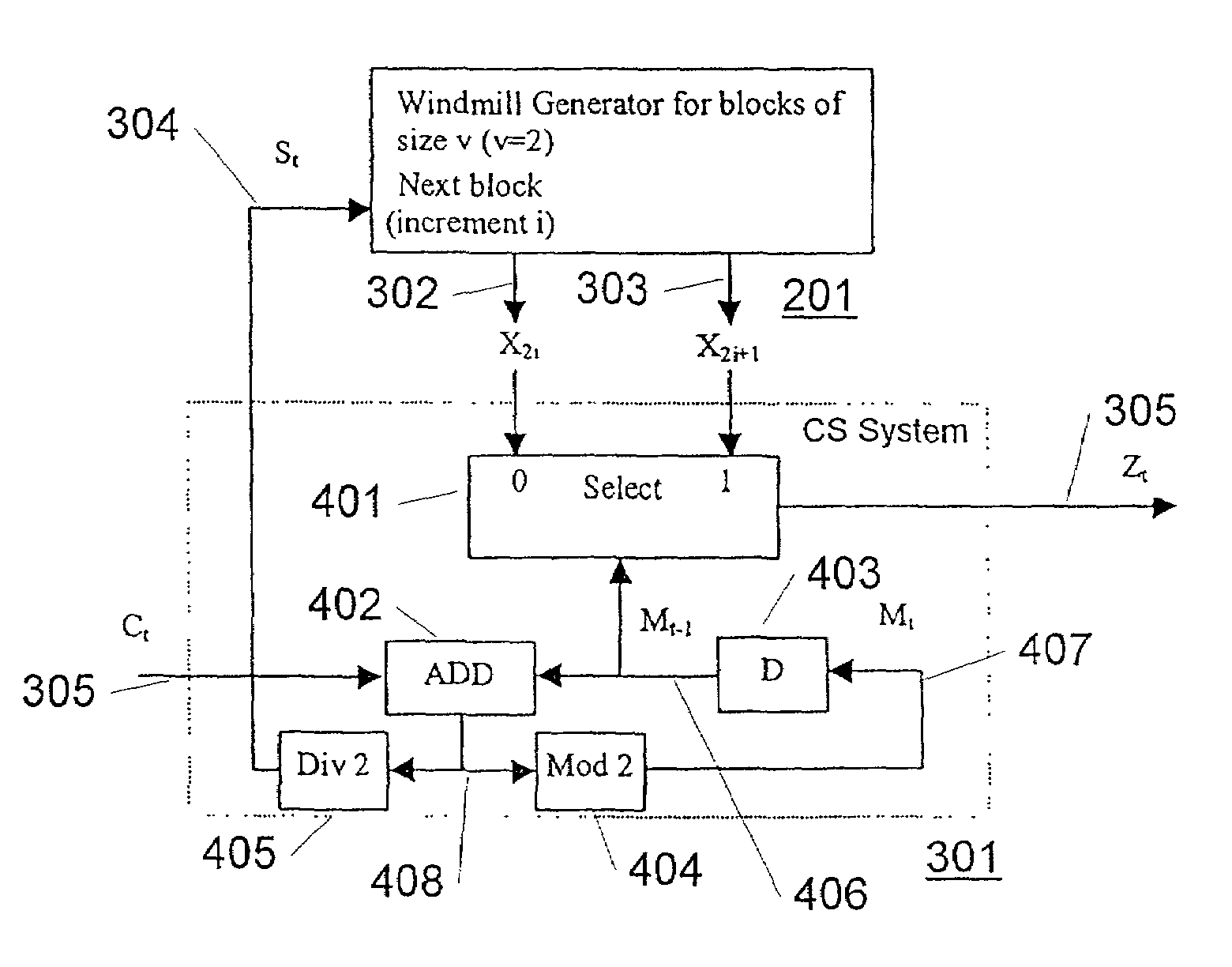
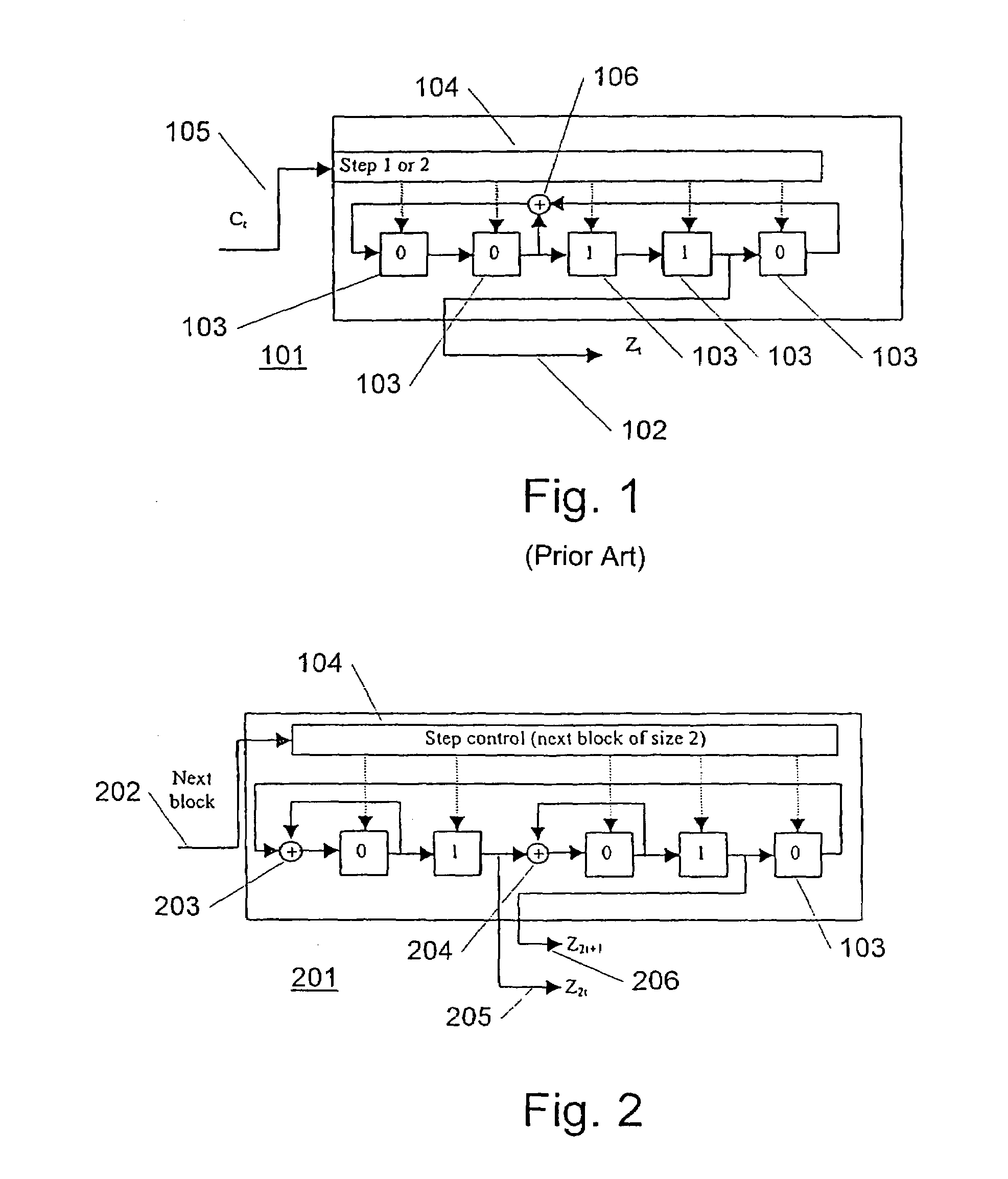
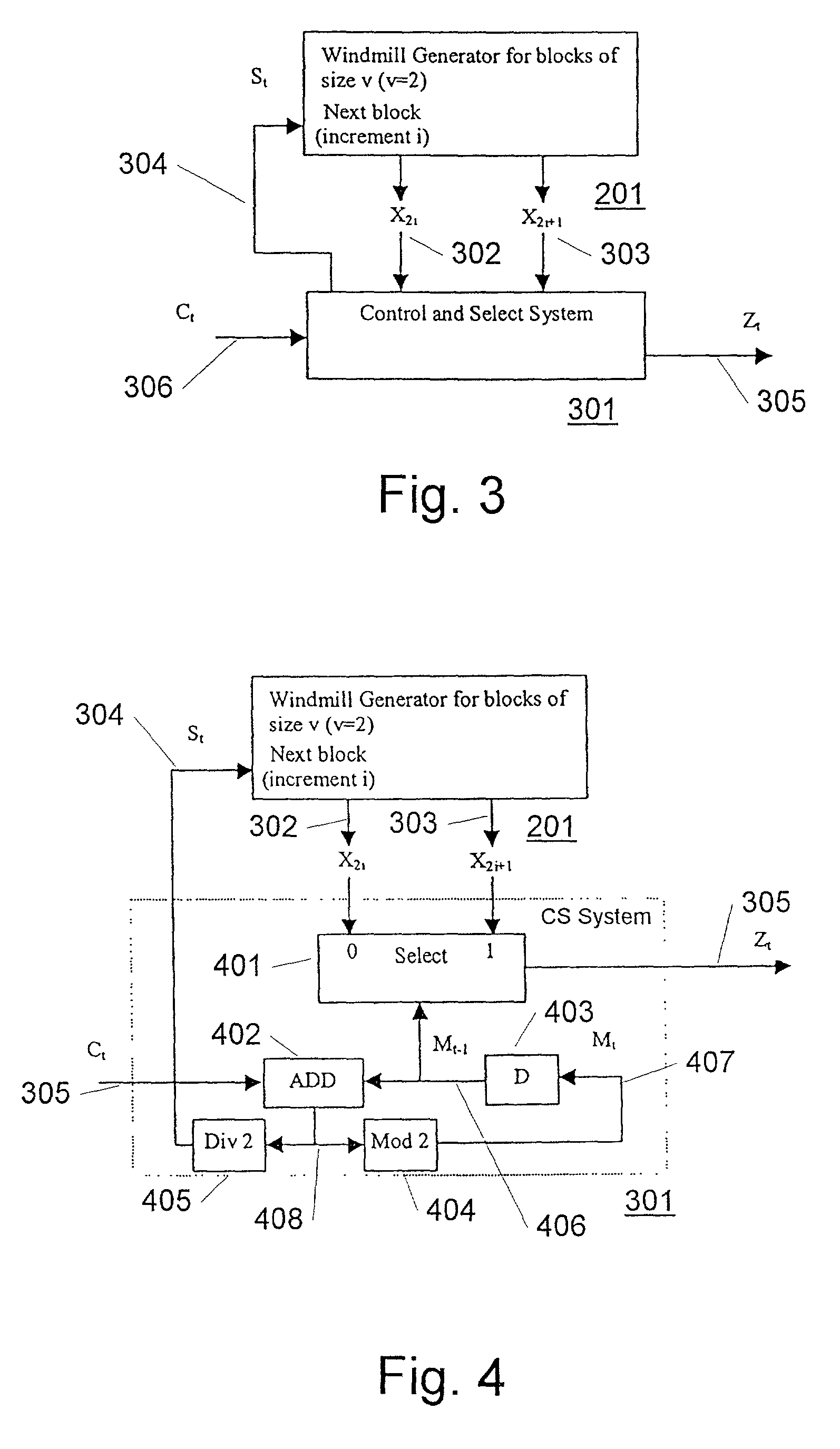
Method and an electrical device for efficient generation of multi-rate pseudo random noise (PN) sequence
InactiveUS7089274B2Easy constructionFlexible, efficient and cryptographically more secureRandom number generatorsMultiplex code generationEngineeringRandom noise
An electrical device for generating a multi-rate pseudo random noise (PN) sequence. A sequence generator is adapted to output a plurality of sequence values based on a step control signal (St). A selection system is adapted to select one of a plurality of sequence values based on a select value (Mt). A step control is adapted to provide the step control signal (St). Also disclosed is a method of generating a multi-rate PN sequence.
Owner:UNWIRED PLANET
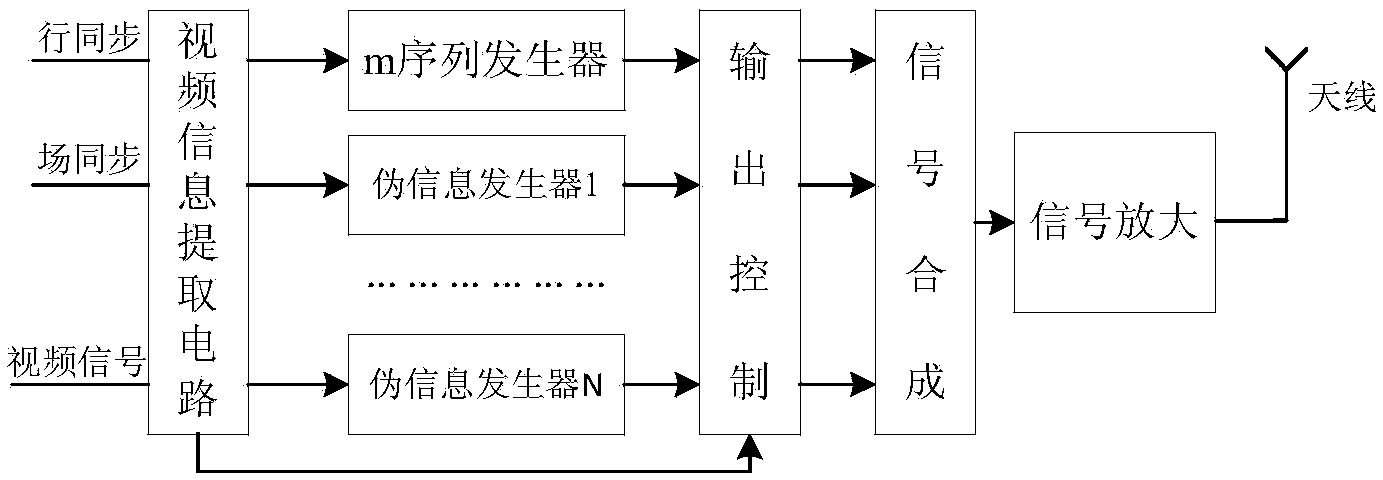
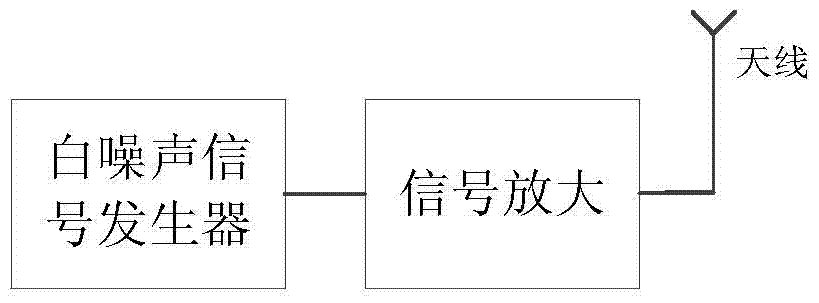
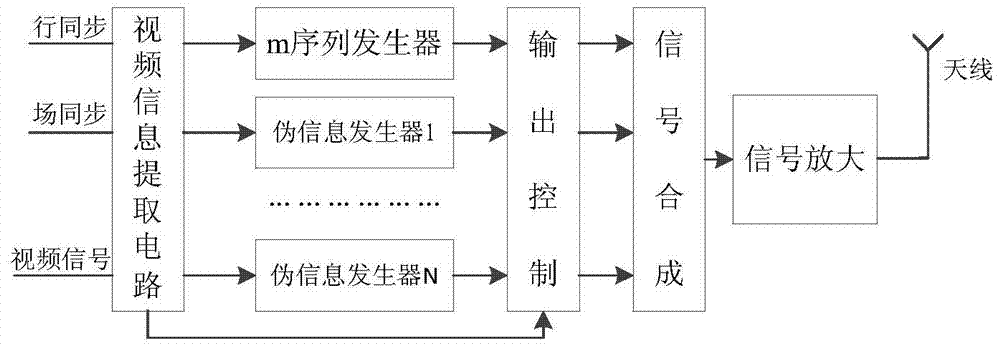
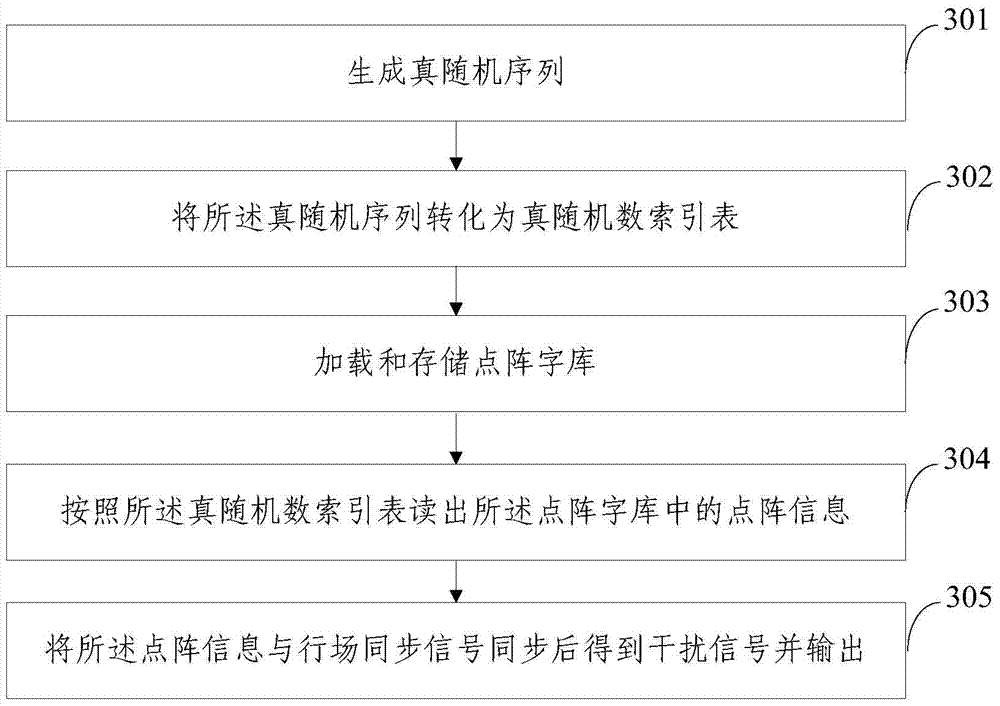
Video information electromagnetic leakage interference defending method and device
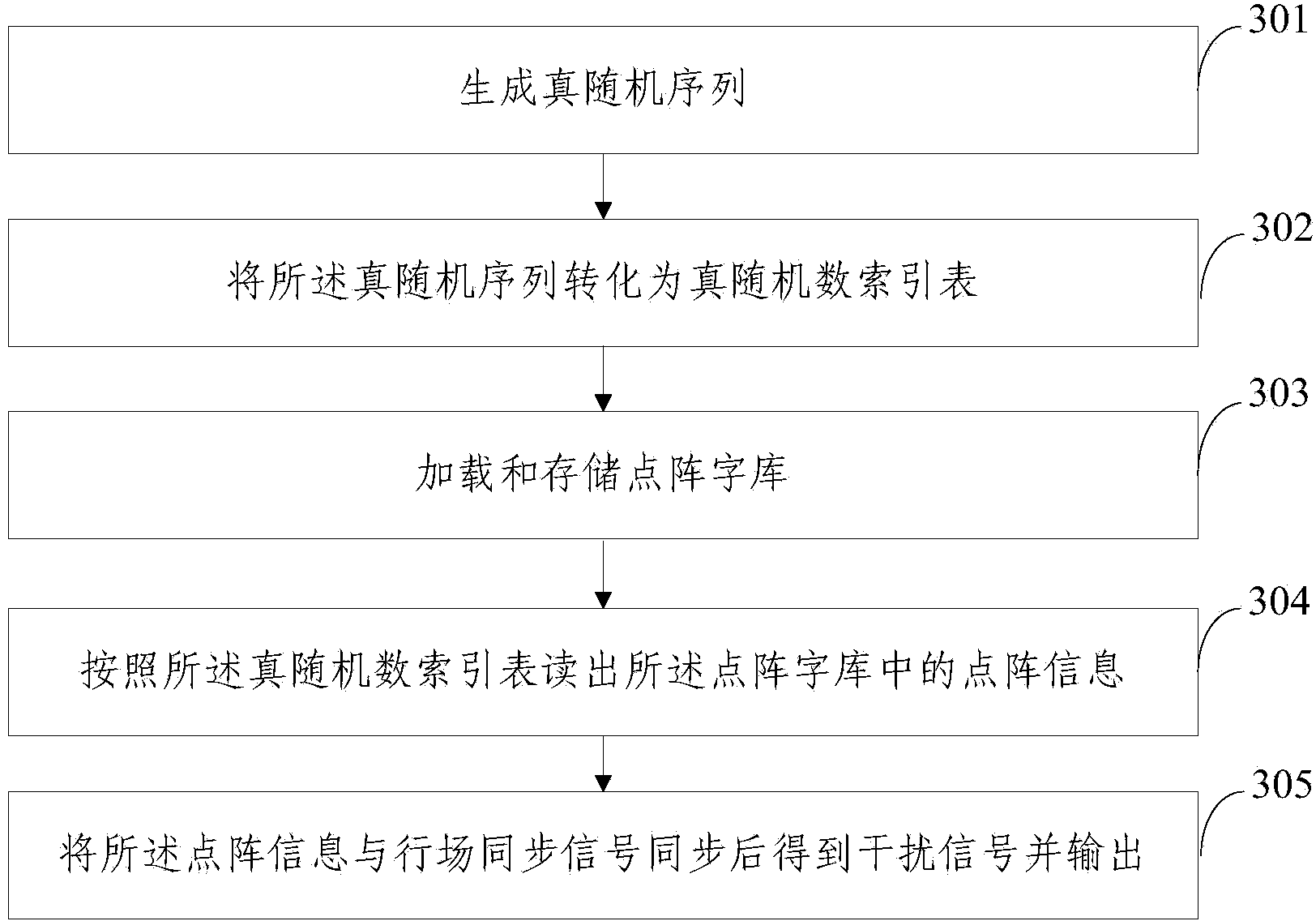
ActiveCN103886269AIncrease randomnessIncrease unpredictabilityInternal/peripheral component protectionDigital signal processingDot matrix
The invention provides a video information electromagnetic leakage interference defending method and device. The method comprises the steps that a true random sequence is generated; the true random sequence is converted into a true random number index table; a dot matrix word stock is loaded and stored; dot matrix information in the dot matrix work stock is read according to the true random number index table; and the dot matrix information and traveling field synchronizing signals are subjected to synchronization, and then interference signals are obtained and output. A related interference mode based on the true random number is provided for modulation of the interference signals, the randomness and the unpredictability of the interference signals are improved, the interference signals cannot be tracked or demodulated, the problem that a stealing side uses various digital signal processing methods for restoring useful information from the interference signals can be effectively avoided, and accordingly the purpose of sensitive information protecting is achieved.
Owner:INST OF INFORMATION ENG CHINESE ACAD OF SCI
Image encryption and decryption method based on fractional order translation chaotic system
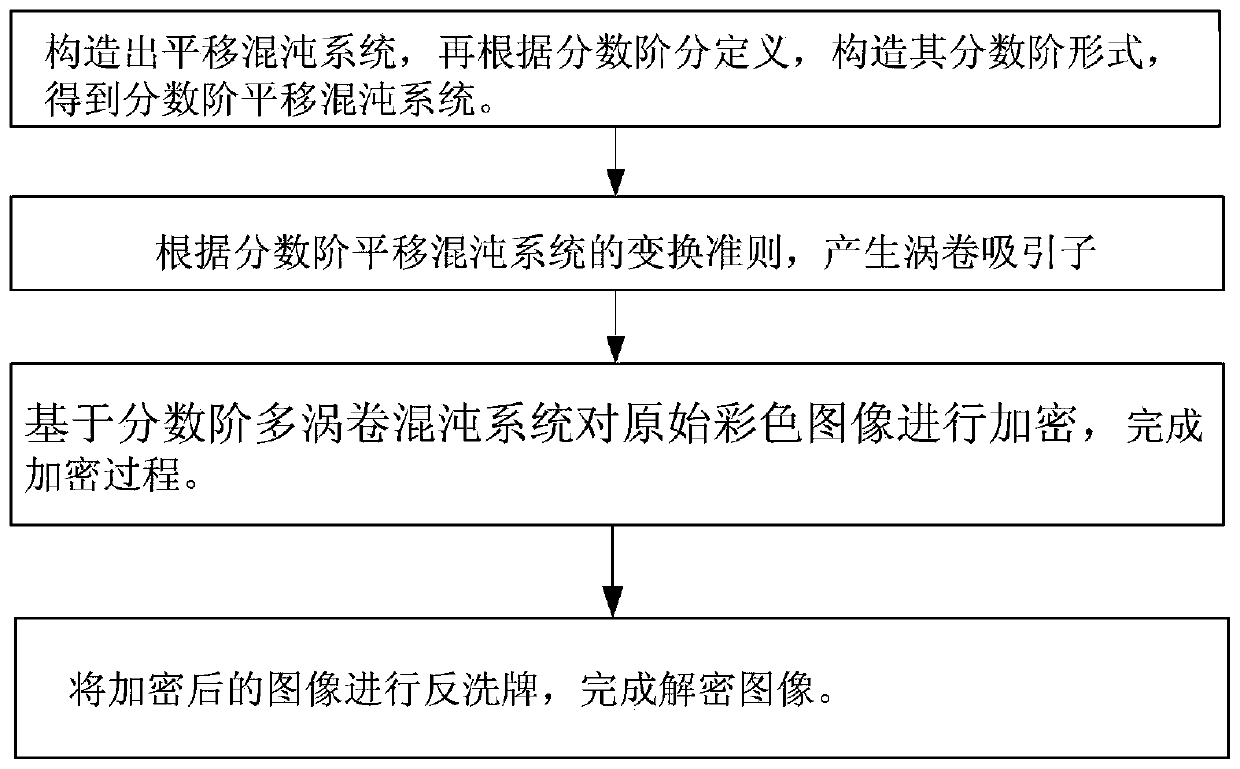
PendingCN110572252AHigh dimensional spaceStrong initial value sensitivityDigital data protectionSecuring communication by chaotic signalsComputer hardwarePlaintext
The invention discloses an image encryption and decryption method based on a fractional order translation chaotic system, and relates to the fields of computer cryptography, image encryption processing and communication and network engineering, which can solve the problems that initial conditions of an existing chaotic system are not associated with plaintexts, plaintext attacks cannot be resisted, and the safety is poor. According to themethod, translation transformation is conducted on the fractional order chaotic system by introducing a piecewise function, parameters are set, different numbers of scroll attractors can be generated, and the fractional order translation chaotic system perfects the field of fractional order chaotic systems composed of three-dimensional one-time autonomousconstant differential. Meanwhile, the fractional order multi-scroll chaotic system has higher dimension space and higher initial value sensitivity, the image encryption and decryption algorithm basedon the system is high in randomness and multiple in secret key parameters, a multi-iteration mode is adopted in the encryption process, an encrypted ciphertext matrix becomes very uniform, and therefore the purpose of effectively hiding original image information is achieved.
Owner:CHANGCHUN UNIV OF TECH
Physical unclonable function circuit utilizing monostable timing offset
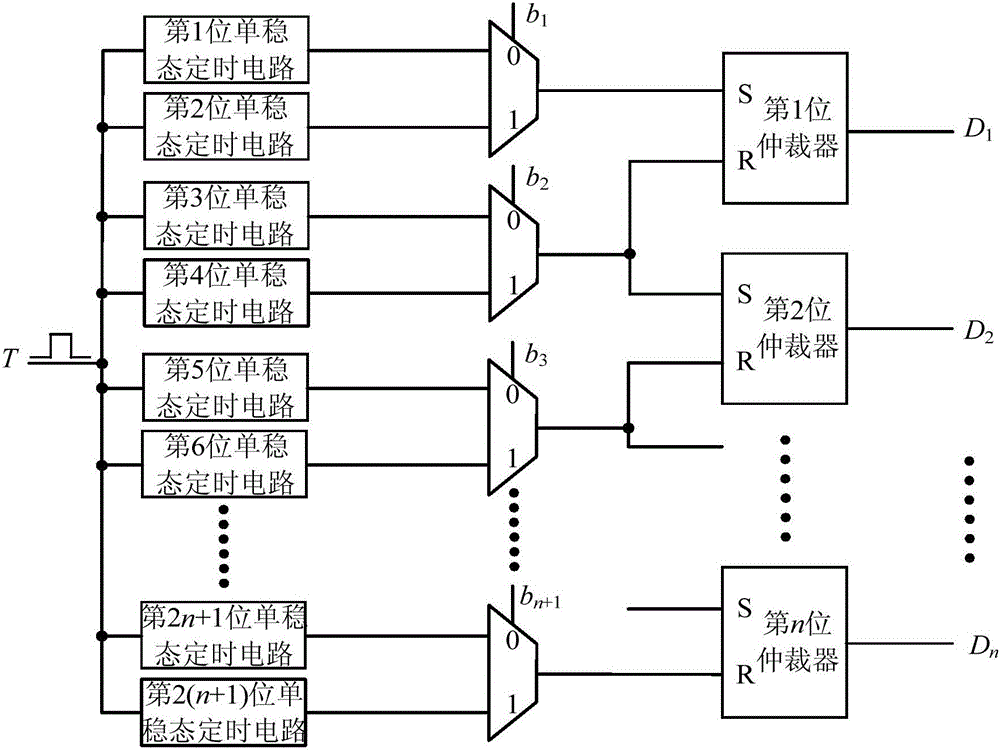
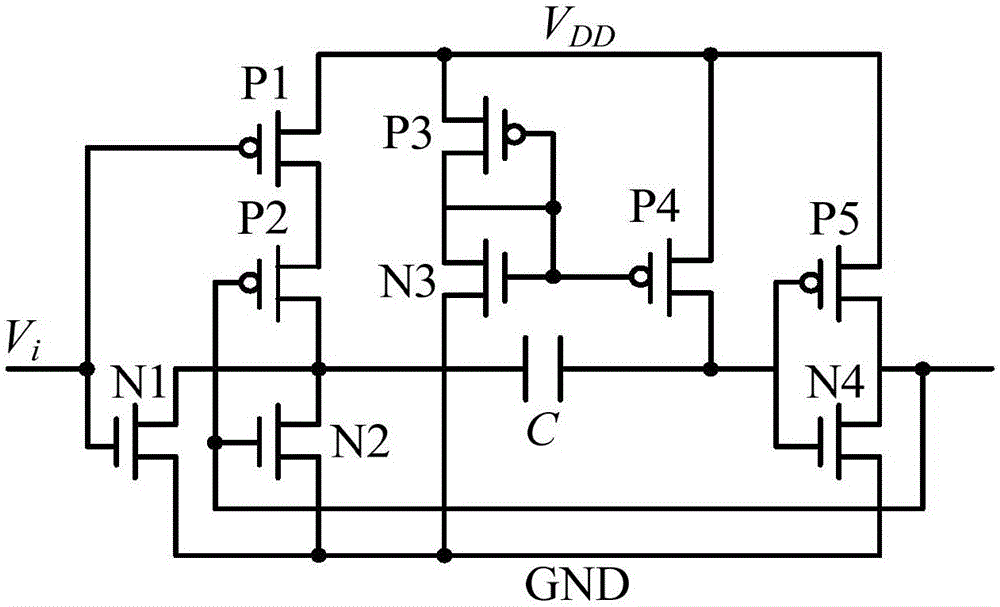
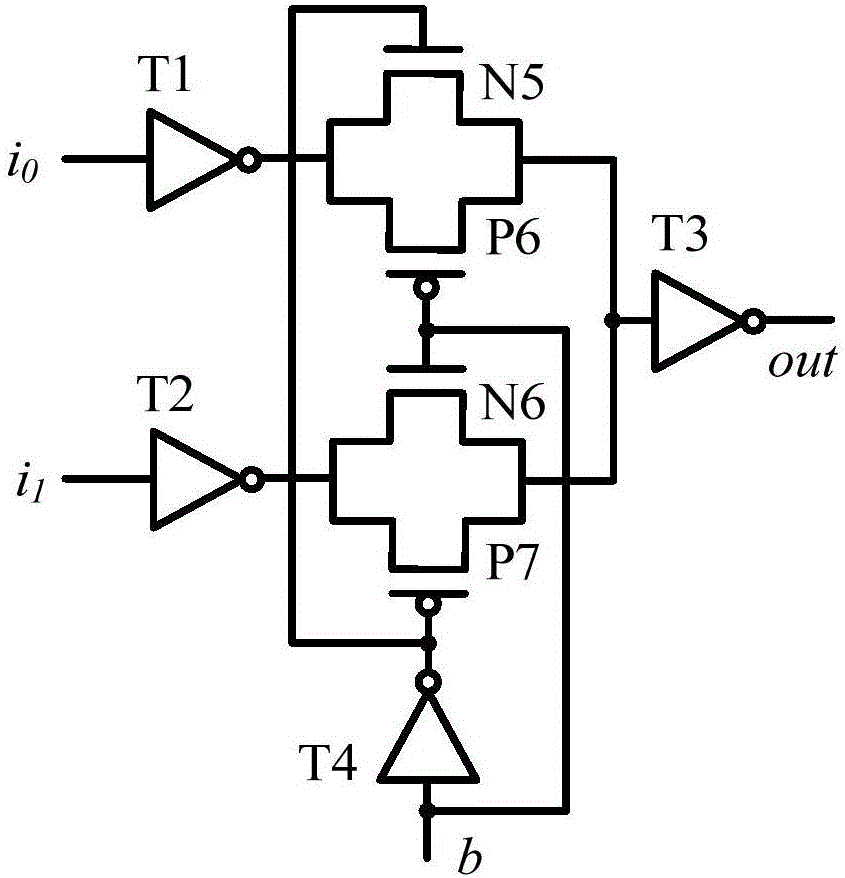
ActiveCN106548094AIncrease unpredictabilityEasy to identifyInternal/peripheral component protectionInput selectionPhysical unclonable function
The invention discloses a physical unclonable function circuit utilizing monostable timing offset. The circuit comprises 2(n+1) monostable timing circuits, n+1 two-input selection circuits and n arbiters, wherein n is an integer larger than or equal to 1. An output end of a 2j+1 th monostable timing circuit is connected with a first input end of a j+1 two-input selection circuit. An output end of the 2j+1 th monostable timing circuit is connected with a second input end of the j+1 two-input selection circuit. j is equal to 0,1,2...,n. An output end of a first two-input selection circuit is connected with a first input end of a first arbiter. An output end of a k two-input selection circuit is connected with a second input end of a k-1 arbiter and a first input end of a k arbiter. K is equal to 2, 3...,n. An output end of a n+1 two-input selection circuit is connected with a second input end of a n arbiter. The physical unclonable function circuit utilizing monostable timing offset has following advantages: on the basis of higher reliability and uniqueness, high identifiability is obtained.
Owner:NINGBO UNIV
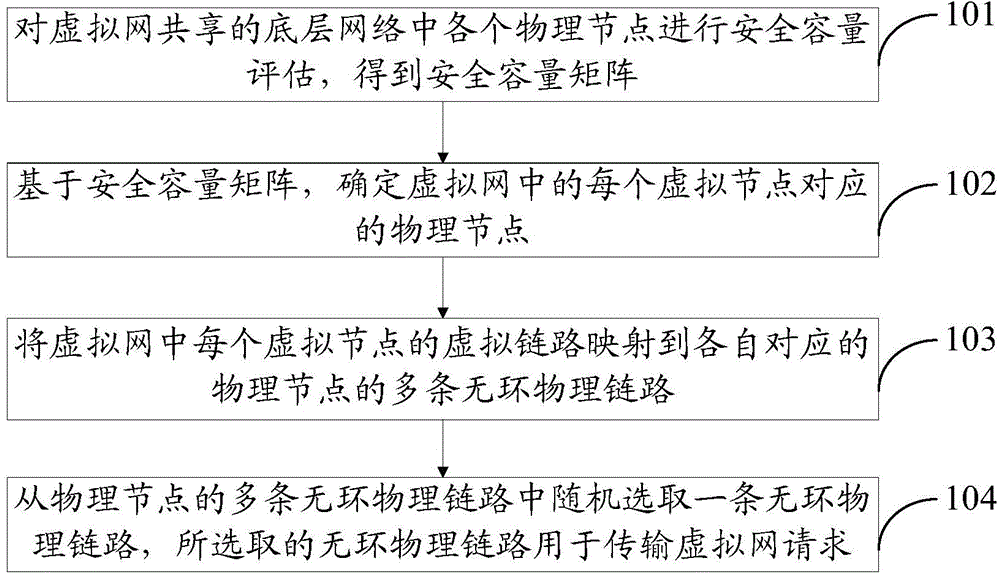
Mapping method and mapping device for virtual network
The invention provides a mapping method and a mapping device for a virtual network. The mapping method comprises the following steps: performing safety capacity assessment on physical nodes in a bottom network shared by the virtual network to obtain a safety capacity matrix; based on the safety capacity matrix, determining the physical node corresponding to each virtual node in the virtual network; mapping the virtual link of each virtual node in the virtual network to a plurality of loop-free physical links corresponding to each physical node; randomly selecting one loop-free physical link from the loop-free physical links of the physical nodes, wherein the selected physical link is used for transmitting a virtual network request, that is, according to the mapping method provided by the scheme of the invention, one loop-free physical link can be randomly selected for transmitting the virtual network request during transmission of the virtual network request, the manner of randomly selecting the physical link can improve the unpredictability of link transmission, so as to improve the data transmission safety.
Owner:THE PLA INFORMATION ENG UNIV
Method for playing a wagering game
InactiveUS8096556B2Improve overall revenueIncrease unpredictabilityCard gamesApparatus for meter-controlled dispensingComputer hardware
Owner:VEGAS GAMING GROUP
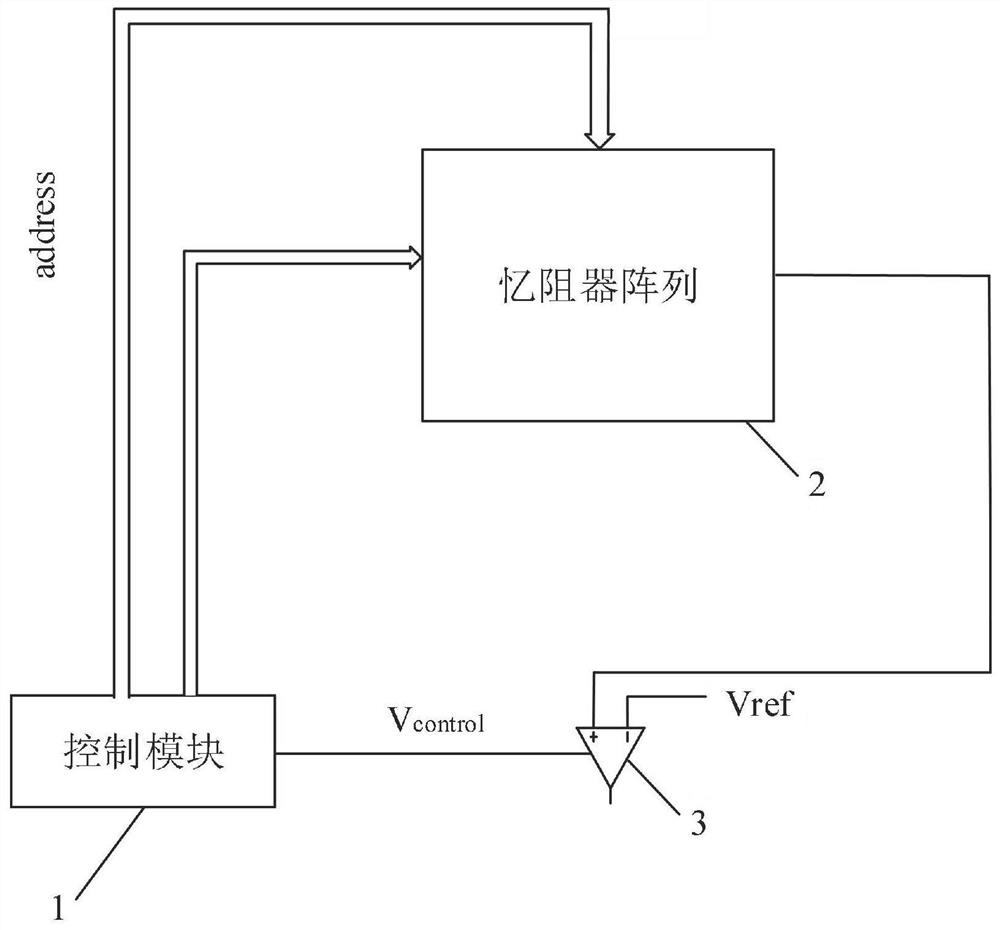
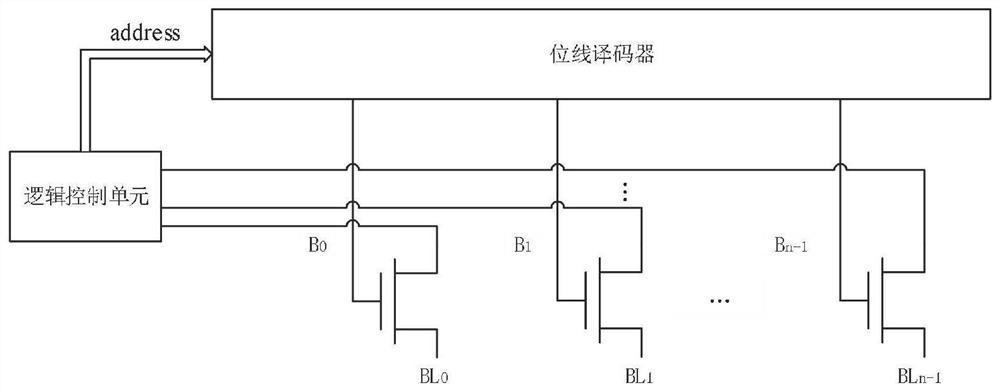
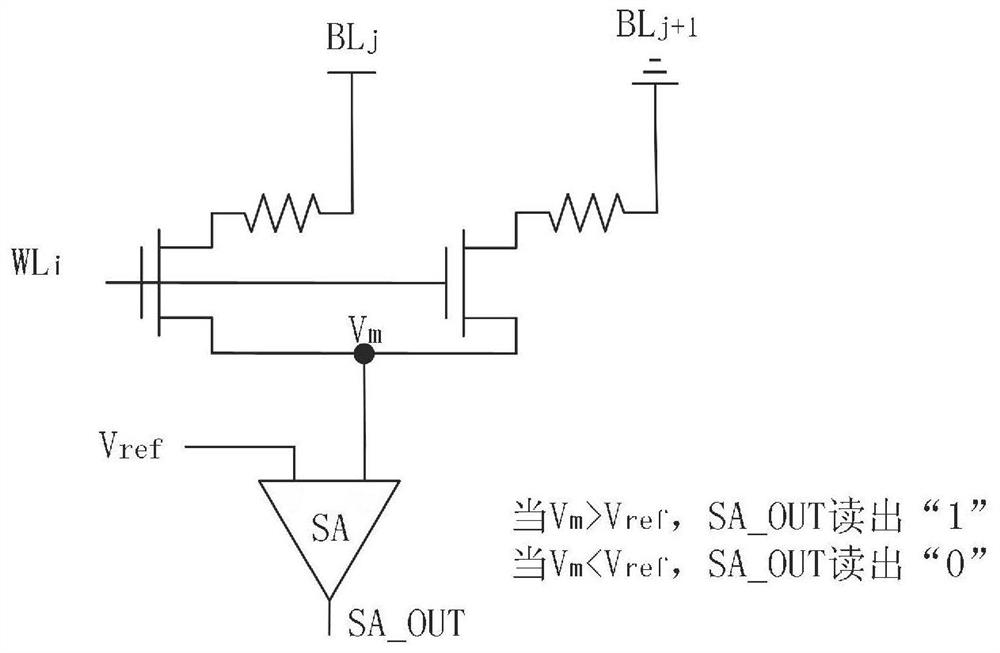
Physical unclonable function circuit and operation method thereof
The invention discloses a physical unclonable function circuit and an operation method thereof, and belongs to the field of circuit design. The physical unclonable function circuit comprises a control module, a memristor array and a comparison amplification circuit, wherein the control module is used for selecting memristor units in the ith row and the jth column and memristor units in the ith row and the (j+1)th column in the memristor array based on an externally input excitation signal, conducting the ith row of the memristor array, applying a high level signal to the jth column of the memristor array, applying a low level signal to the (j+1)th column of the memristor array, and enabling the rest columns to be in a suspended state, so that the selected memristor units form a series circuit to perform voltage division operation. The source line output of the ith row of the memristor array is a voltage division signal at the middle voltage division point of the series circuit; the comparison amplification circuit is used for comparing the voltage division signal with the reference voltage to obtain a response signal. The circuit is not affected by crosstalk current, the accuracy of the response result is high, and the bit error rate is greatly reduced.
Owner:HUAZHONG UNIV OF SCI & TECH
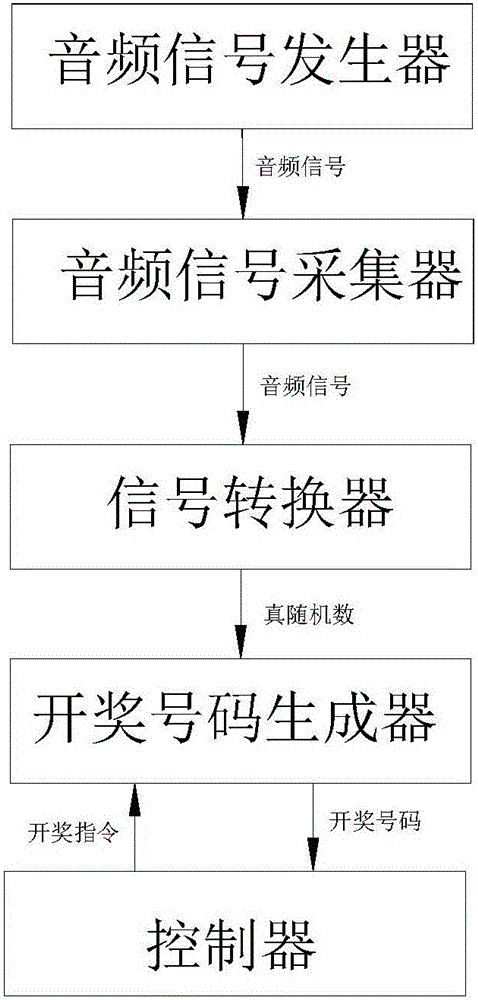
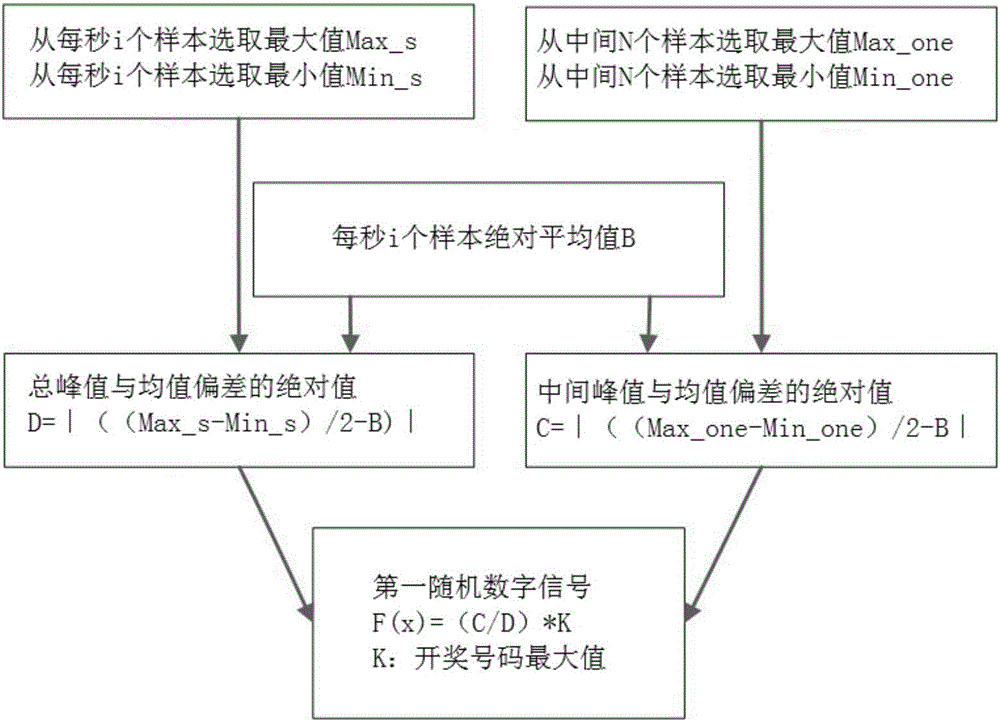
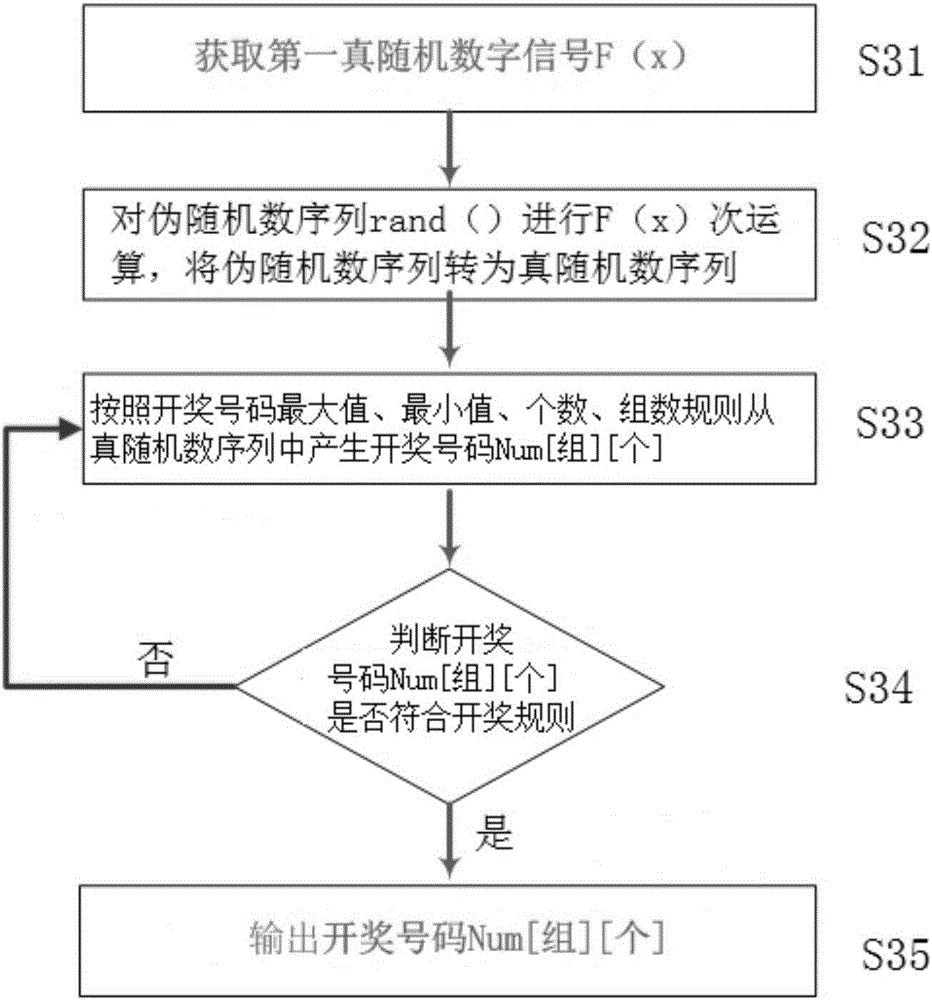
Automatic music lottery drawing machine and lottery drawing method
InactiveCN105913536AIncrease randomnessStrong randomnessLottery apparatusNumber generatorBase sequence
The invention discloses an automatic music lottery drawing machine and a lottery drawing method. The lottery drawing machine comprises an audio signal generator for sending a random audio signal, an audio signal acquisition unit for acquiring a random audio signal sent by the audio signal generator, a signal converter for converting the acquired random audio signal into a first random digital signal, a controller for sending a lottery drawing control instruction, and a lottery drawing number generator for putting the first random digital signal into a pseudorandom number base sequence to generate a real random number base sequence, and generating a lottery drawing number from the real random number base sequence according to the lottery drawing control instruction sent by the controller. The automatic music lottery drawing machine is high in automation degree, strong in randomness and high in unpredictability and requirements on modern rapid and automatic lottery drawing are met.
Owner:上海申彩信息系统有限公司
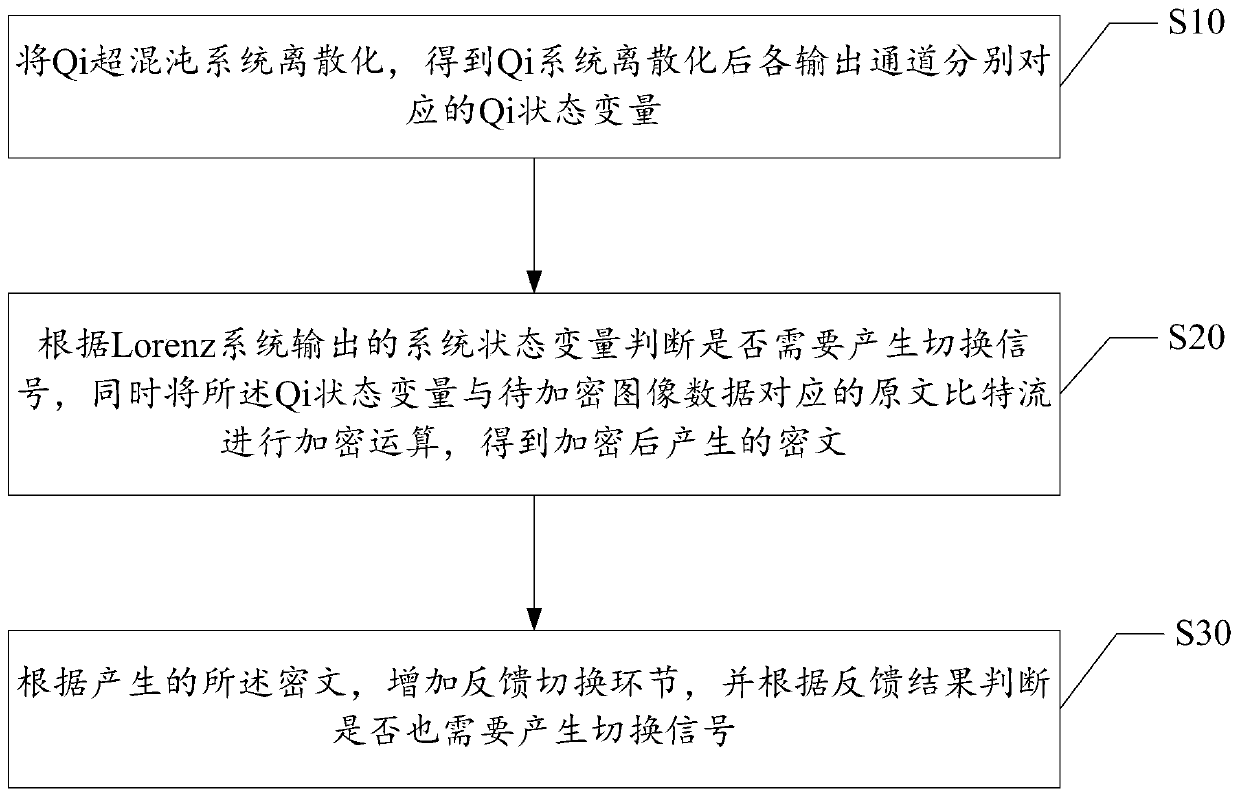
Feedback switching encryption method based on double-chaotic system
ActiveCN110012313AImprove securityIncrease unpredictabilitySecuring communication by chaotic signalsSelective content distributionComputer hardwareState variable
The invention discloses a feedback switching encryption method based on a double-chaotic system, comprising the following steps of: discretizing a Qi hyper-chaotic system to obtain Qi state variablesrespectively corresponding to output channels after discretization of the Qi system; judging whether a switching signal needs to be generated or not according to a system state variable output by theLorenz system, and performing encryption operation on the Qi state variable and an original text bit stream corresponding to the image data to be encrypted to obtain a ciphertext generated after encryption; according to the generated ciphertext, adding a feedback switching link, and judging whether a switching signal needs to be generated or not according to a feedback result; the purpose of improving switching signal unpredictability and encryption sequence randomness by using a pair of double chaotic systems of a Lorenz system and a Qi system is achieved, and the security of image data encryption is enhanced.
Owner:CIVIL AVIATION UNIV OF CHINA
System and methods for entropy and statistical quality metrics in physical unclonable function generated bitstrings
ActiveUS20190268170A1Increase diversityIncrease unpredictabilityUser identity/authority verificationDigital data authenticationStatistical qualityPhysical unclonable function
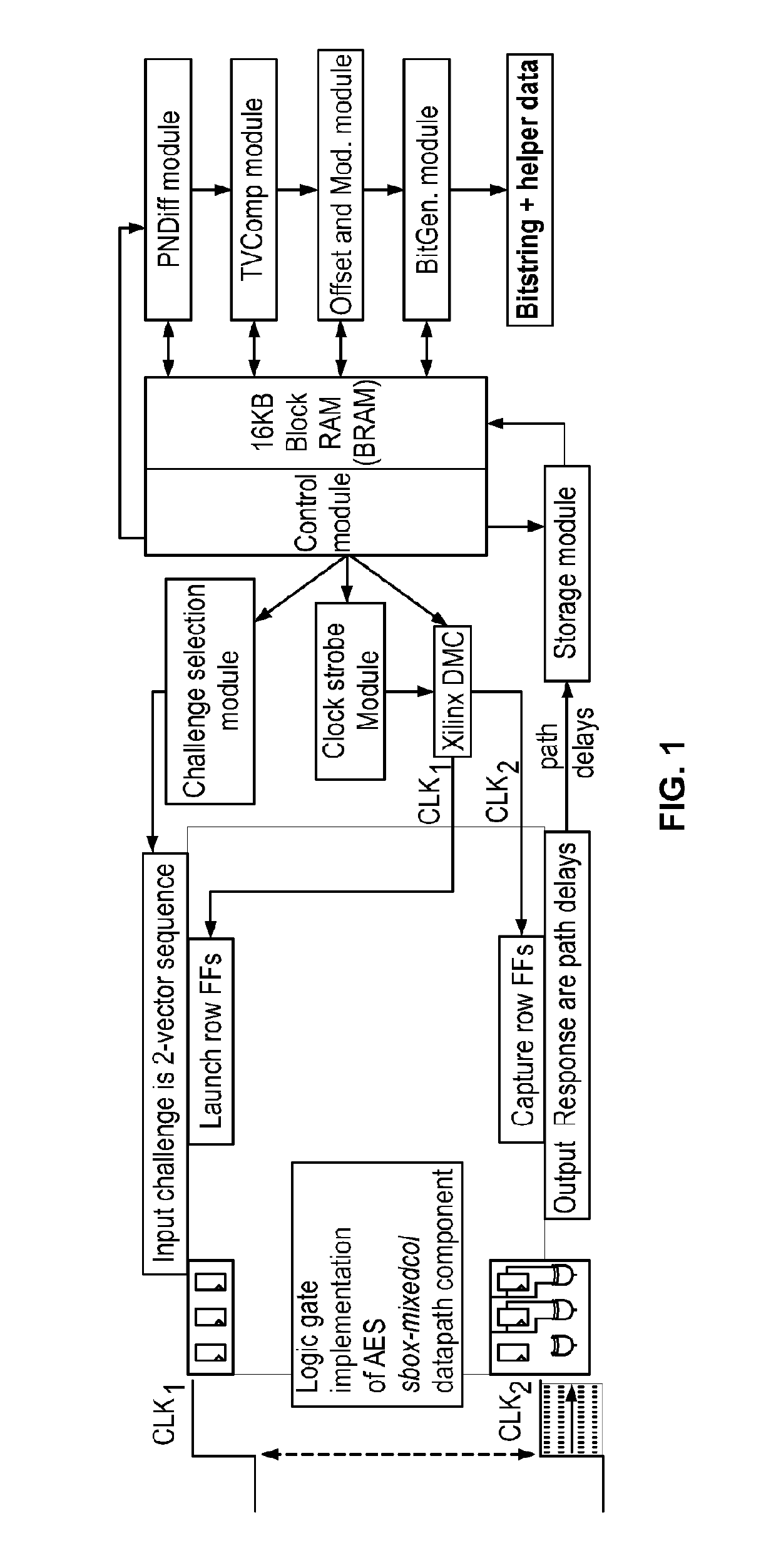
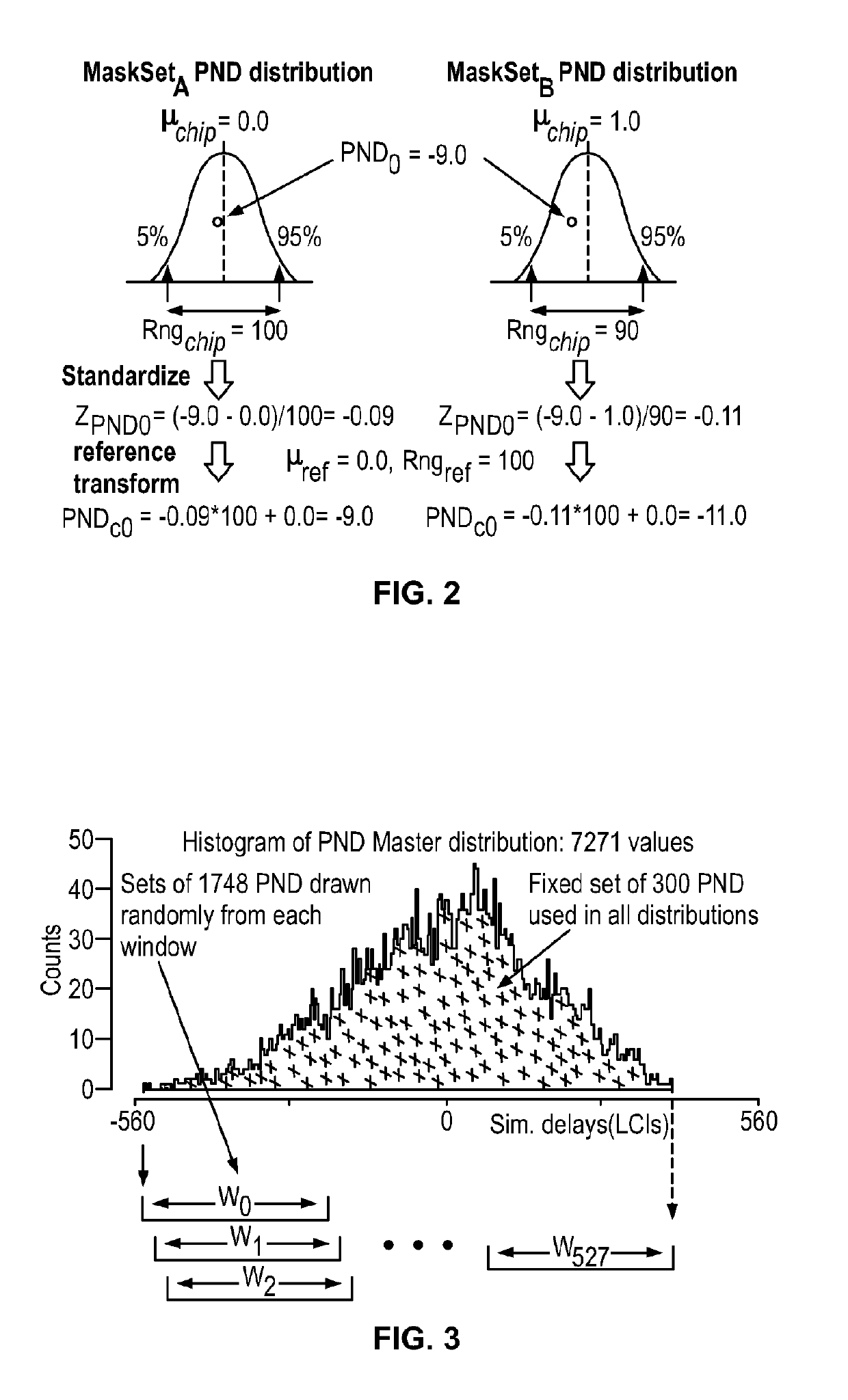
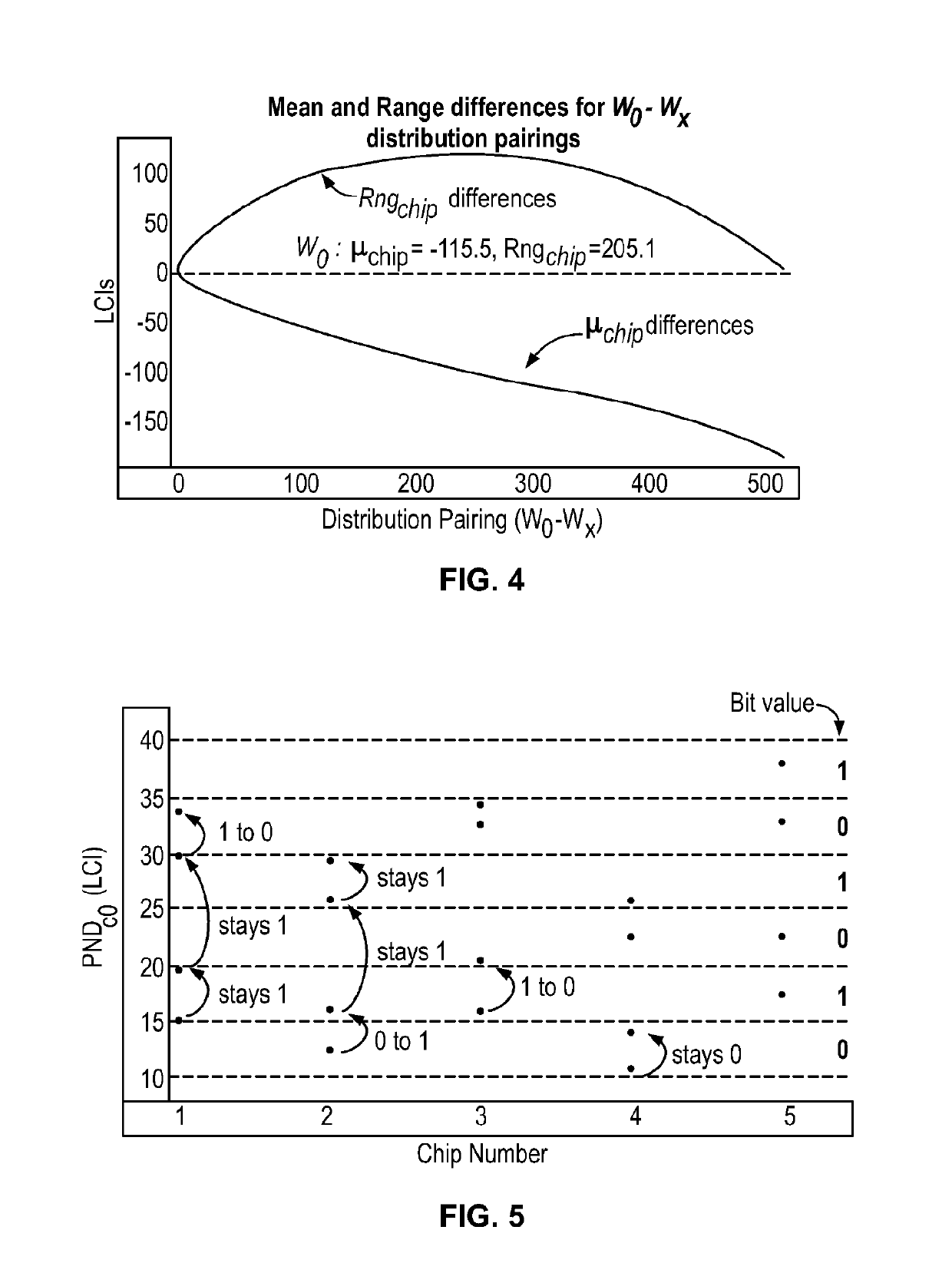
The Distribution Effect is proposed for the HELP PUF that is based on purposely introducing biases in the mean and range parameters of path delay distributions to enhance entropy. The biased distributions are then used in the bitstring construction process to introduce differences in the bit values associated with path delays that would normally remain fixed. Offsets are computed to fine tune a token's digitized path delays as a means of maximizing entropy and reproducibility in the generated bitstrings: a first population-based offset method computes median values using data from multiple tokens (i.e., the population) and a second chip-specific technique is proposed which fine tunes path delays using enrollment data from the authenticating token.
Owner:UNM RAINFOREST INNOVATIONS
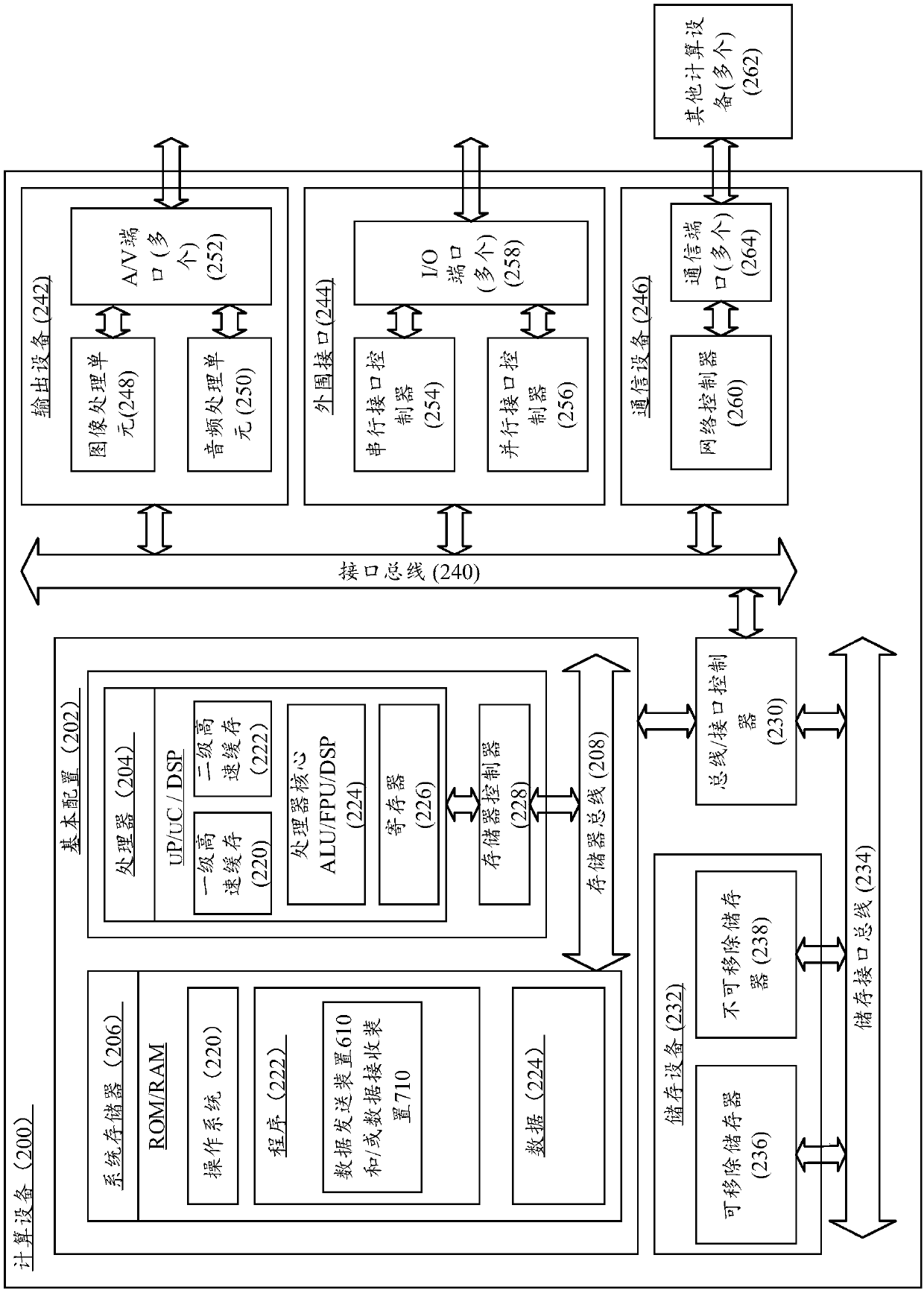
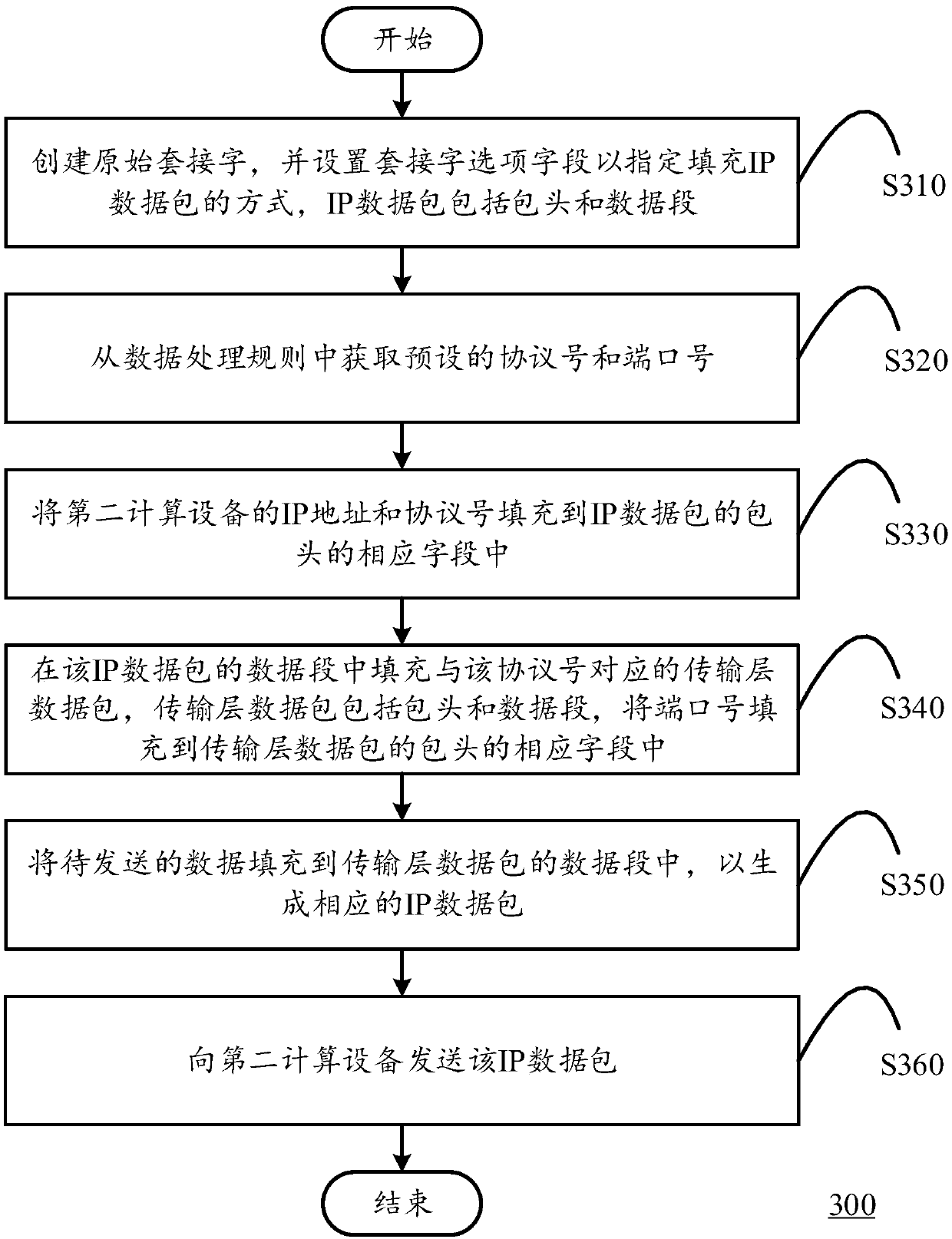
Data sending method, data receiving method and data communication system
InactiveCN107743122AReduce riskIncrease unpredictabilityTransmission format adaptationCommunications systemData segment
The invention discloses a data sending method, a data receiving method and a data communication system. The data receiving method is suitable for being performed in a first computing device. The firstcomputing device and a second computing device are in communication connection and store data processing rules. The method comprises the steps of establishing an original socket and setting a socketoption field to appoint a mode of filling an IP data packet, wherein the IP data packet comprises a packet header and a data field; obtaining a preset protocol number and port number from the data processing rules; filling the corresponding field of the packet header of the IP data packet with an IP address and the protocol number of the second computing device; filling the data field of the IP data packet with a transmission layer data packet corresponding to the protocol number, wherein the transmission layer data packet comprises the packet header and the data field, and filling the corresponding field of the packet header of the transmission layer data packet with the port number; and filling the data field of the transmission layer data packet with to-be-sent data, thereby generatingthe corresponding IP data packet; and sending the IP data packet to the second computing device.
Owner:BEIJING KNOWNSEC INFORMATION TECH
Game machine
InactiveUS7780171B2Enhancing its appealIncrease unpredictabilityIndoor gamesBall sportsEngineeringMechanical engineering
A game machine (1) includes a game board (3) having a housing section opened on a game surface, a target which is provided to the housing section so as to freely appear and disappear, and a target driving mechanism which is provided into the game board and allows the target (9) to appear and disappear from and into the housing section. The game machine is provided with a supporting pedestal (2) which supports the game board, a rotation driving device (20) which rotates the game board supported to the supporting pedestal about a pivot axis line RC extending to a direction where the line crosses the board surface in a reciprocating manner, and a tilt giving mechanism which is provided between the supporting pedestal and the game board and gives a motion to the game board according to the rotating motion of the game board about the pivot axis line RC so that the game board tilts with respect to the pivot axis line.
Owner:KONAMI DIGITAL ENTERTAINMENT CO LTD
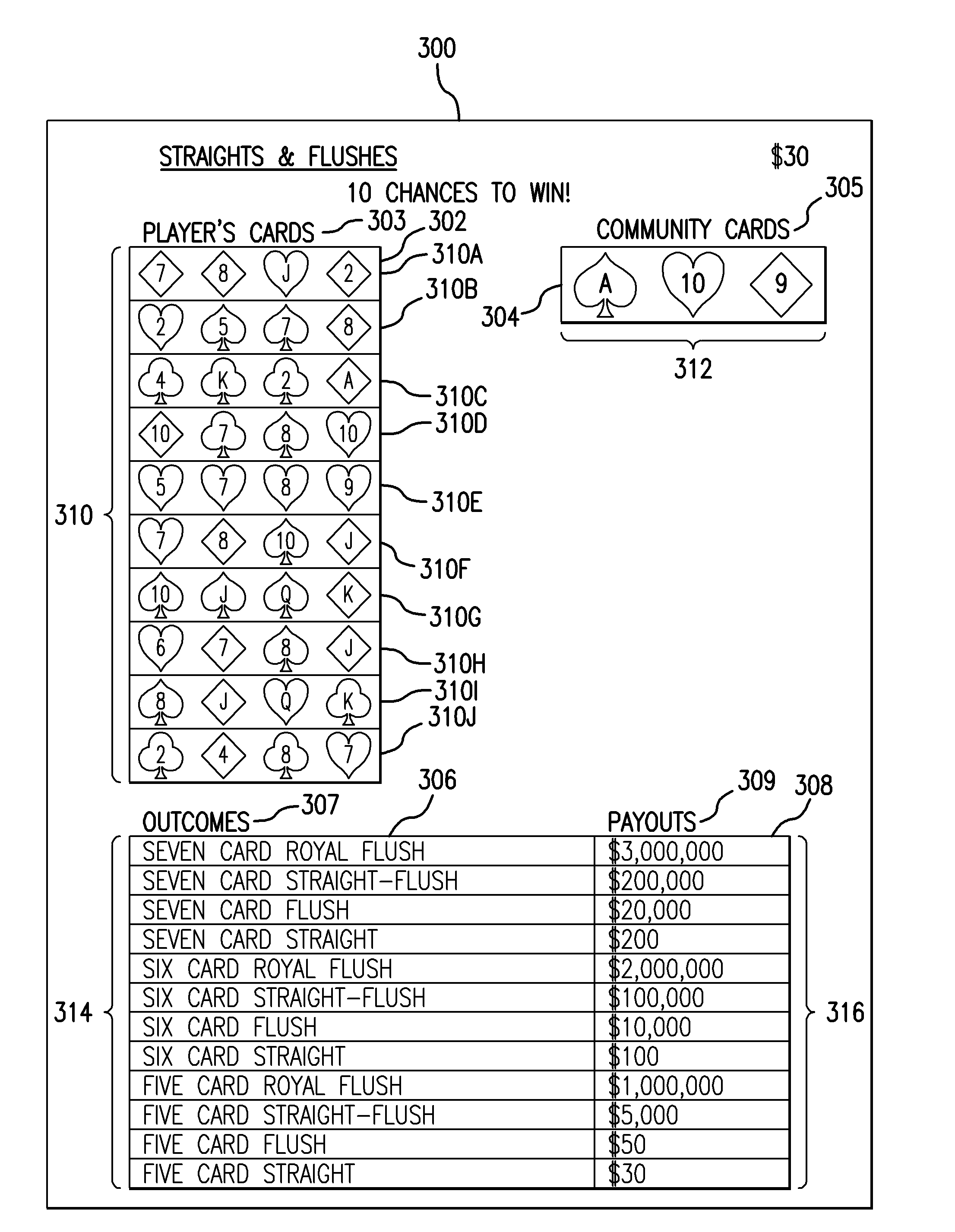
Method For Playing A Wagering Game
InactiveUS20130043651A1Improve overall revenueIncrease unpredictabilityBoard gamesCard gamesGame playLottery ticket
An instant lottery ticket game includes the steps of removing a first opaque covering surface to reveal a first set of indicia indicative of a plurality of player's hands of cards wherein each player's hand of cards has four cards, removing a second opaque covering surface to reveal a second set of indicia indicating a set of community cards wherein the set of community cards has three cards, removing a third opaque covering surface to reveal a third set of indicia indicative of a plurality of winning hands, removing a third opaque covering surface to reveal a fourth set of indicia indicative of a plurality of payouts wherein each payout corresponds to a one of the plurality of winning hands, and determining, for each player's hand of cards, if the combination of the player's hand of cards with one or more of the community cards yields a winning hand.
Owner:CHAMBERLAIN RONALD
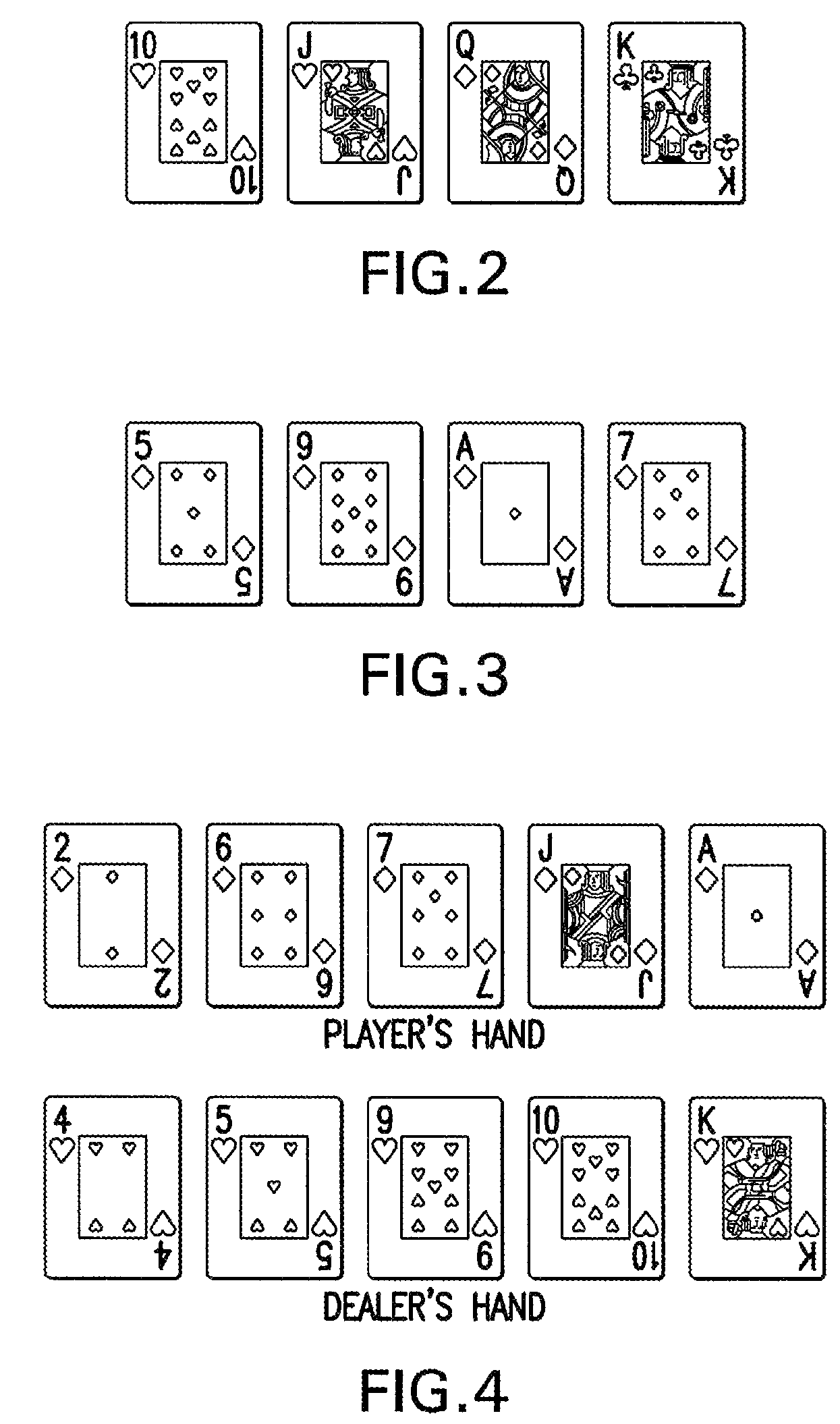
Method For Playing Modified Blackjack
InactiveUS20090102128A1Improve overall revenueIncrease unpredictabilityCard gamesPlaying cardComputer science
A method of playing modified blackjack wherein, in one embodiment, a plurality of decks of cards is provided wherein each playing card has a specific numeric value. An ante or initial wager is placed by at least one player. Next, the dealer preferably deals an initial two card hand in a left-to-right motion starting from the dealer's left. The cards are dealt face down. The dealer also deals himself an initial two card hand. The player then views his or her cards and then decides whether to stay, fold or place a second wager to obtain additional cards. If the player wants additional cards, the player places the second wager. The player may request only one additional card, or he may request two more additional cards to achieve a four card hand. These additional cards are dealt face up. The maximum number of cards a player may have is four cards. However, the dealer may deal himself more than four cards. If the player's cards have a total point value that exceeds 25, the player “busts” and is out. The dealer must stand on 21. This means that the dealer must continue to deal himself additional cards until the point value of the dealer's hand is greater than or equal to 21. If the point value of the dealer's hand is greater than 25, the dealer busts and is out. If the player's hand has a point value of 25 and the dealer's hand does not have a point value of 25, the player wins and his or her winnings are determined by a predetermined pay-table set by the house. If the dealer's hand has a point value that is 21 and the player's hand has a point value that is greater than 21 but less than or equal to 25, the player wins and his or her winnings are determined by a predetermined pay-table set by the house. Other aspects of the method of playing modified blackjack are disclosed herein.
Owner:CHAMBERLAIN RONALD
Method and device for preventing electromagnetic leakage interference of video information
ActiveCN103886269BIncrease randomnessIncrease unpredictabilityInternal/peripheral component protectionDigital signal processingDot matrix
The invention provides a video information electromagnetic leakage interference defending method and device. The method comprises the steps that a true random sequence is generated; the true random sequence is converted into a true random number index table; a dot matrix word stock is loaded and stored; dot matrix information in the dot matrix work stock is read according to the true random number index table; and the dot matrix information and traveling field synchronizing signals are subjected to synchronization, and then interference signals are obtained and output. A related interference mode based on the true random number is provided for modulation of the interference signals, the randomness and the unpredictability of the interference signals are improved, the interference signals cannot be tracked or demodulated, the problem that a stealing side uses various digital signal processing methods for restoring useful information from the interference signals can be effectively avoided, and accordingly the purpose of sensitive information protecting is achieved.
Owner:INST OF INFORMATION ENG CHINESE ACAD OF SCI
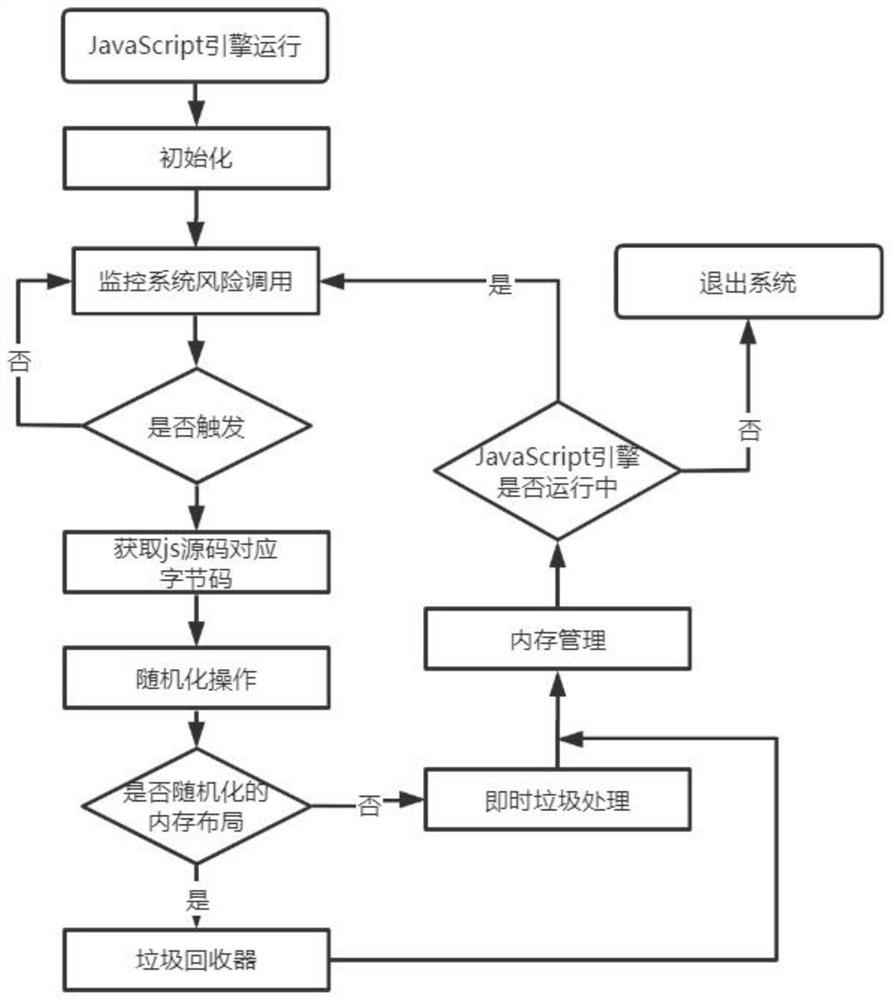
JavaScript engine memory information leakage defense method and system based on runtime randomization
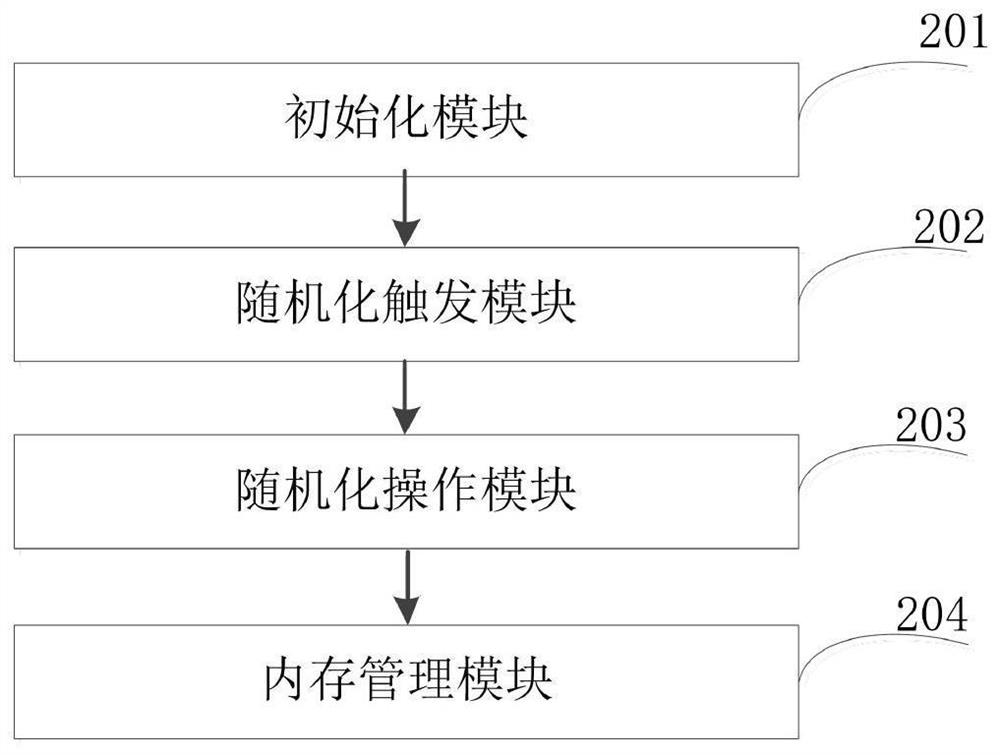
PendingCN111797388AIncrease unpredictabilityAchieve defensePlatform integrity maintainanceSoftware simulation/interpretation/emulationAttackInit
The invention discloses a JavaScript engine memory information leakage prevention method and system based on runtime randomization. The method comprises the following steps of step 1), initializing the system, carrying out initialization setting on a JavaScript engine-based runtime randomization system; 2) monitoring a risk behavior causing memory information leakage in a JavaScript engine runningprocess, and triggering a randomized system to execute during running; 3) realizing randomized operation of the JS engine; and 4) managing the memory in the operation process of the randomized systemduring operation, thereby realizing recovery management of memory garbage generated during operation of the randomized system during operation. The method is advantaged in that a security protectionproblem of dynamically generating the code by the JavaScript engine can be solved, and the capacity of the JS engine for coping with attacks based on memory information leakage is effectively improved.
Owner:WUHAN UNIV
Chaos-based initial vector generation algorithm and IP core thereof
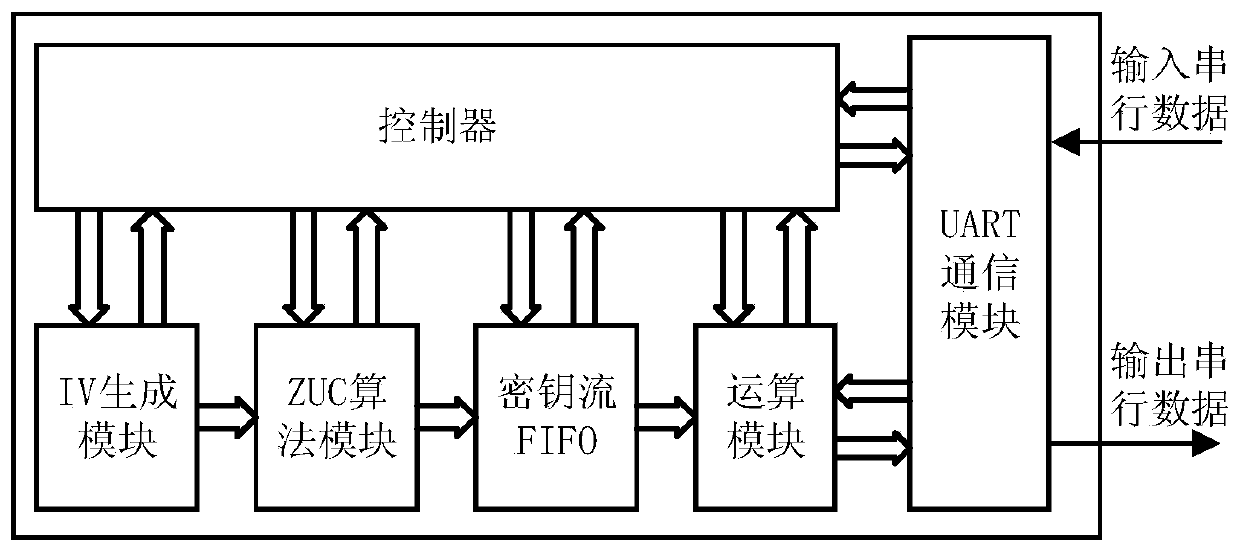
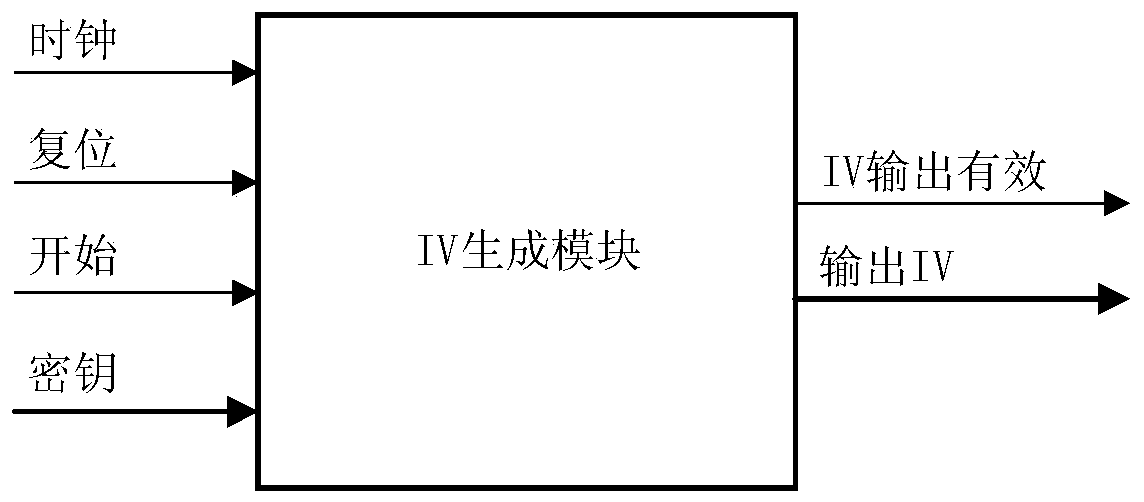
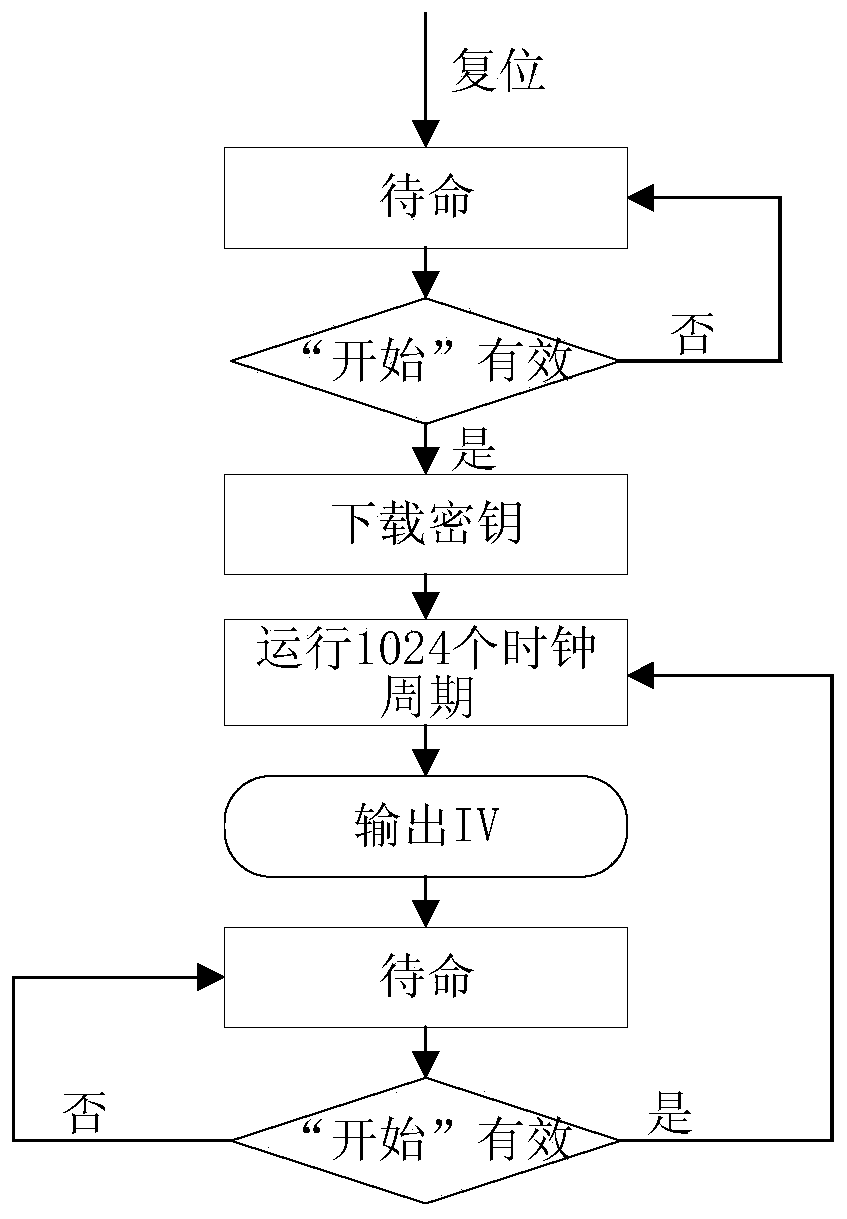
ActiveCN110995405AIncrease unpredictabilityGood attack performanceSecuring communication by chaotic signalsCryptographic attack countermeasuresKeystreamParallel computing
The invention provides a chaos-based initial vector generation algorithm and an IP core thereof, and the generation algorithm comprises the steps: inputting a 32-bit initial value x0 into a Logistic chaos-based sequence generator, and dividing a 128-bit initial key KEY of a ZUC encryption algorithm into 16 32-bit keys [i]; assigning the key [0] to 32 bits x0, and calculating x1 = 4 * 0 (1-x0); assigning the key [i] to the key [i-1], then assigning the x1 to the key [15], and intercepting a 128-bit sequence at the end of all x1 sequences generated in sequence every 1024 bits as an initial vector; the IP core for generating the algorithm comprises an initial vector generation module generated by the method, a ZUC encryption algorithm module, a key stream FIFO module, an operation module, a UART communication module and a controller module. According to the method, the good randomness of the chaotic pseudo-random sequence is utilized, so that the unpredictability of the initial vector isgreatly improved.
Owner:HEILONGJIANG UNIV
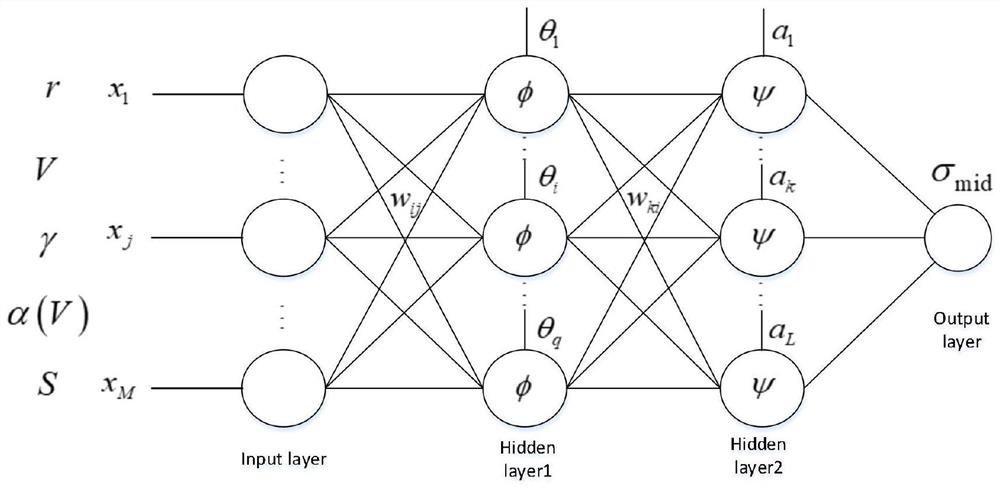
Aircraft intelligent trajectory planning method based on chaotic model and DNN
ActiveCN114442673AOvercome limitationsIncrease chaosSustainable transportationPosition/course control in three dimensionsFlight heightFlight vehicle
The invention discloses an aircraft intelligent trajectory planning method based on a chaos model and a DNN, and belongs to the technical field of aircraft trajectory planning. The method comprises the following steps: obtaining a network mapping relation between a flight state quantity and a flight control quantity; converting the process constraint into flight height and heeling angle constraint; generating a final chaotic signal in the guidance instruction; calculating a heeling angle section median meeting task constraints and a heeling angle required in real time; the size of the heeling angle after chaos processing is obtained; determining a heeling angle direction by adopting a sight angle error corridor; and restraining the amplitude of the heeling angle and the amplitude of the heeling rate. According to the method, the model limitation during the traditional flight path design is overcome, and the unpredictability of the guide instruction and the flight path is increased; and the influence of uncertainty on task reachability is limited. Therefore, the chaos of the flight path is increased on the premise of ensuring the feasibility of the predetermined task, the process constraint is met in the guidance instruction calculation, and the method has a certain engineering practical value.
Owner:哈尔滨逐宇航天科技有限责任公司
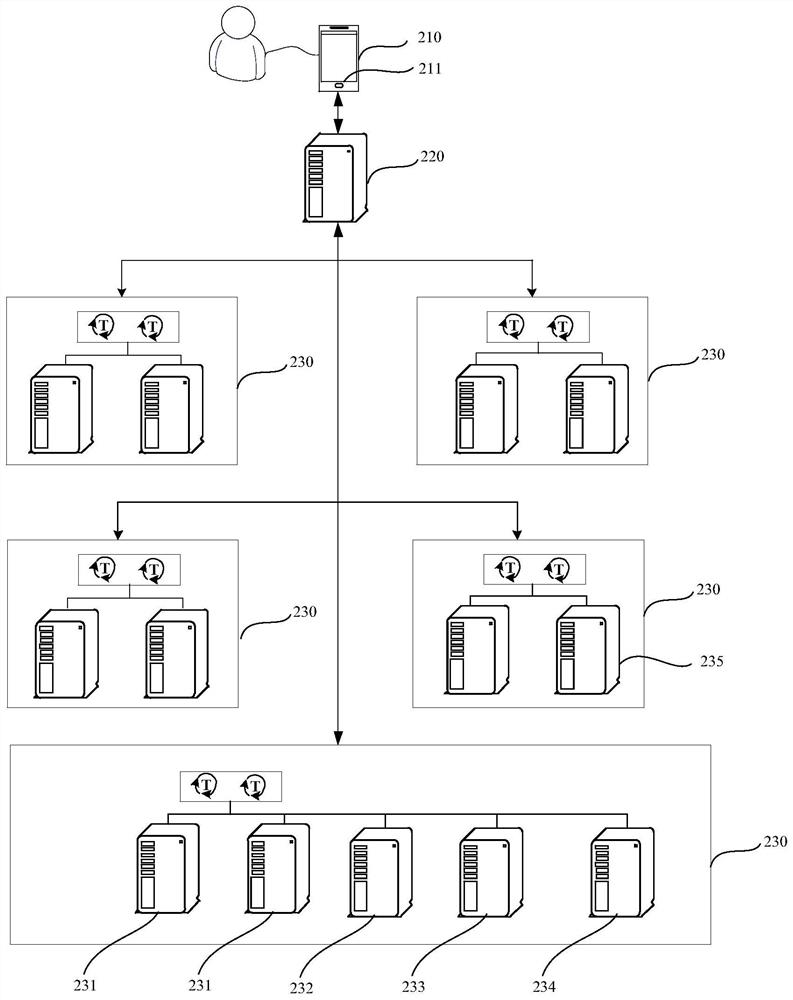
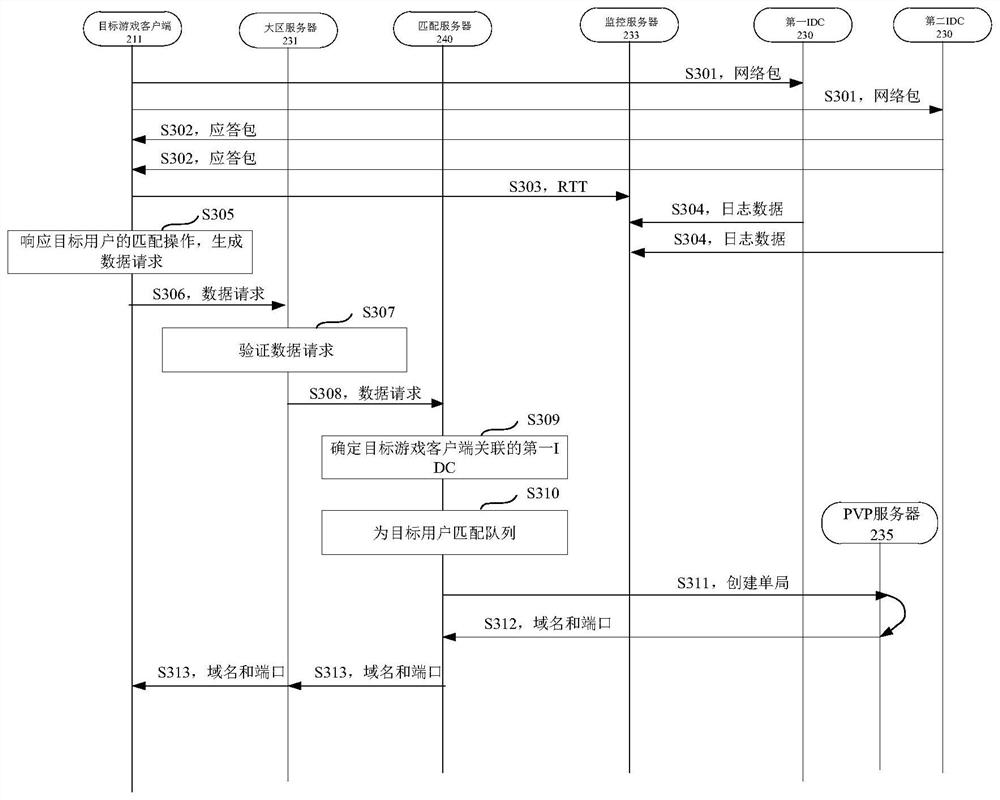
Game control method and device, computer equipment and storage medium
The invention relates to the technical field of cloud, and provides a game control method and a device, computer equipment and a storage medium, which are used for improving the game matching efficiency. The method comprises the steps of determining a first Internet data center IDC associated with a target game client according to a data request sent by the target client associated with a target account, wherein the data request is used for requesting to match a game queue; if the matching level of the first IDC is a first level and the state information in a first matching pool correspondingto the first IDC does not meet a set condition, adding the target account into a second matching pool of a second IDC of which the matching level is a second level for matching; wherein the matching level is divided according to the matching efficiency of the IDC, the higher the matching level is, the higher the matching efficiency of the IDC is, and the matching efficiency is determined accordingto the state information of the matching pool.
Owner:TENCENT TECH SHANGHAI
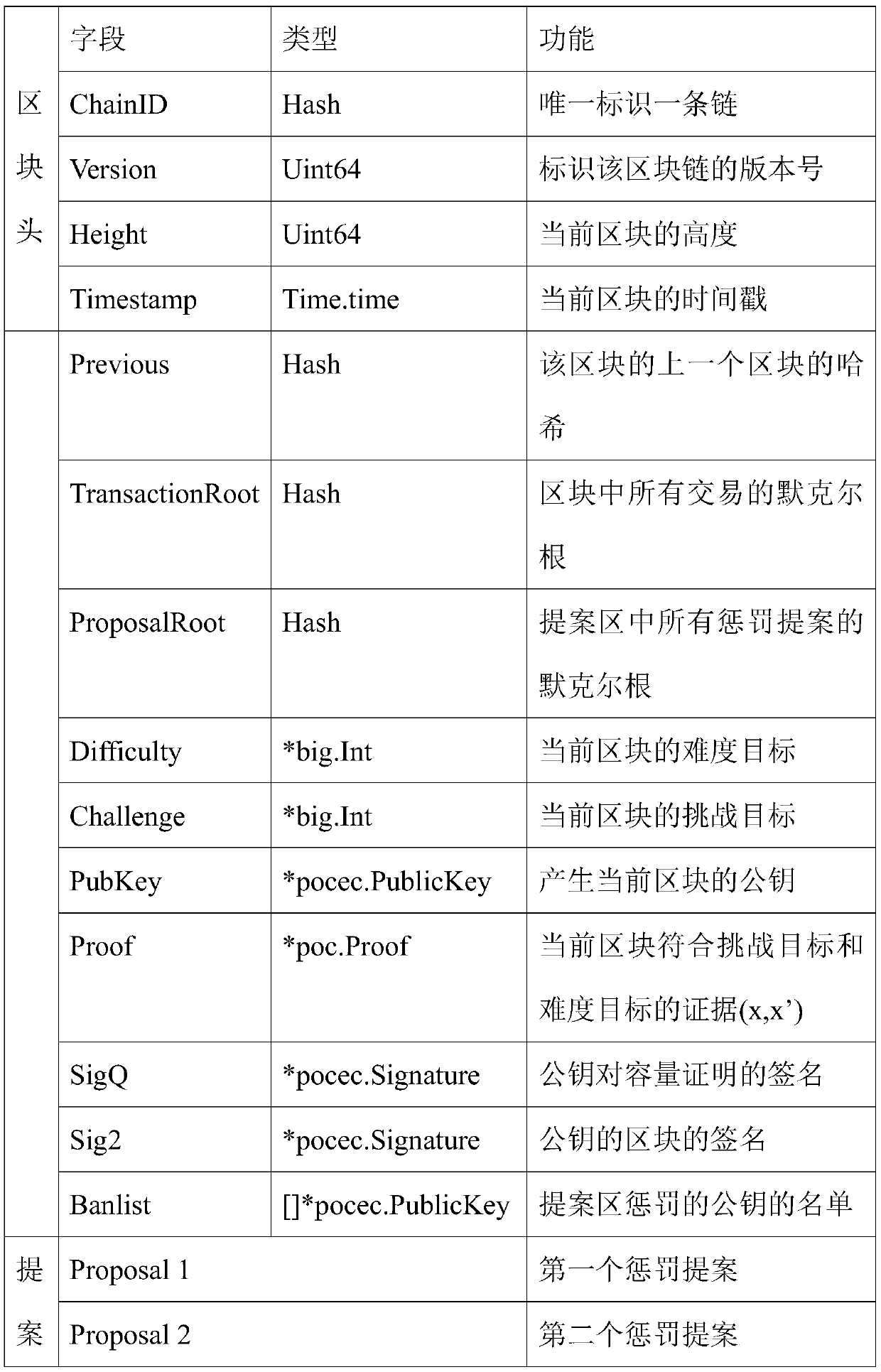
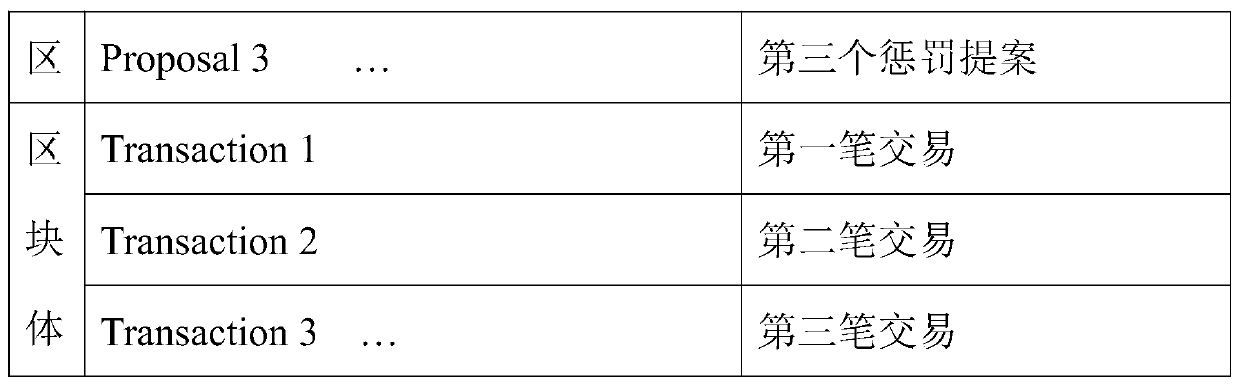
Block chain system construction method based on capacity certification
ActiveCN110609867AConsensus ConfirmationIncrease unpredictabilityKey distribution for secure communicationPublic key for secure communicationPredictabilityChain system
The invention relates to a block chain system construction method based on capacity certification. The method mainly comprises initialization and block construction. According to the method, a new consensus model is adopted, the pseudonym attack is resisted by using the storage capacity, the unpredictability of accounting right transfer is improved by using a verifiable random function, and the consensus of the block is realized through a capacity certification process, so that a complete block chain system is constructed.
Owner:北京天云如川科技有限公司
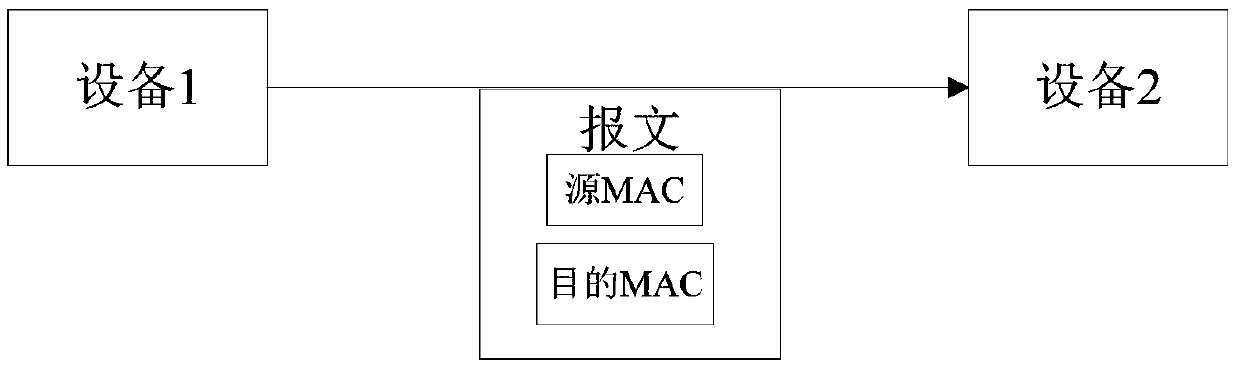
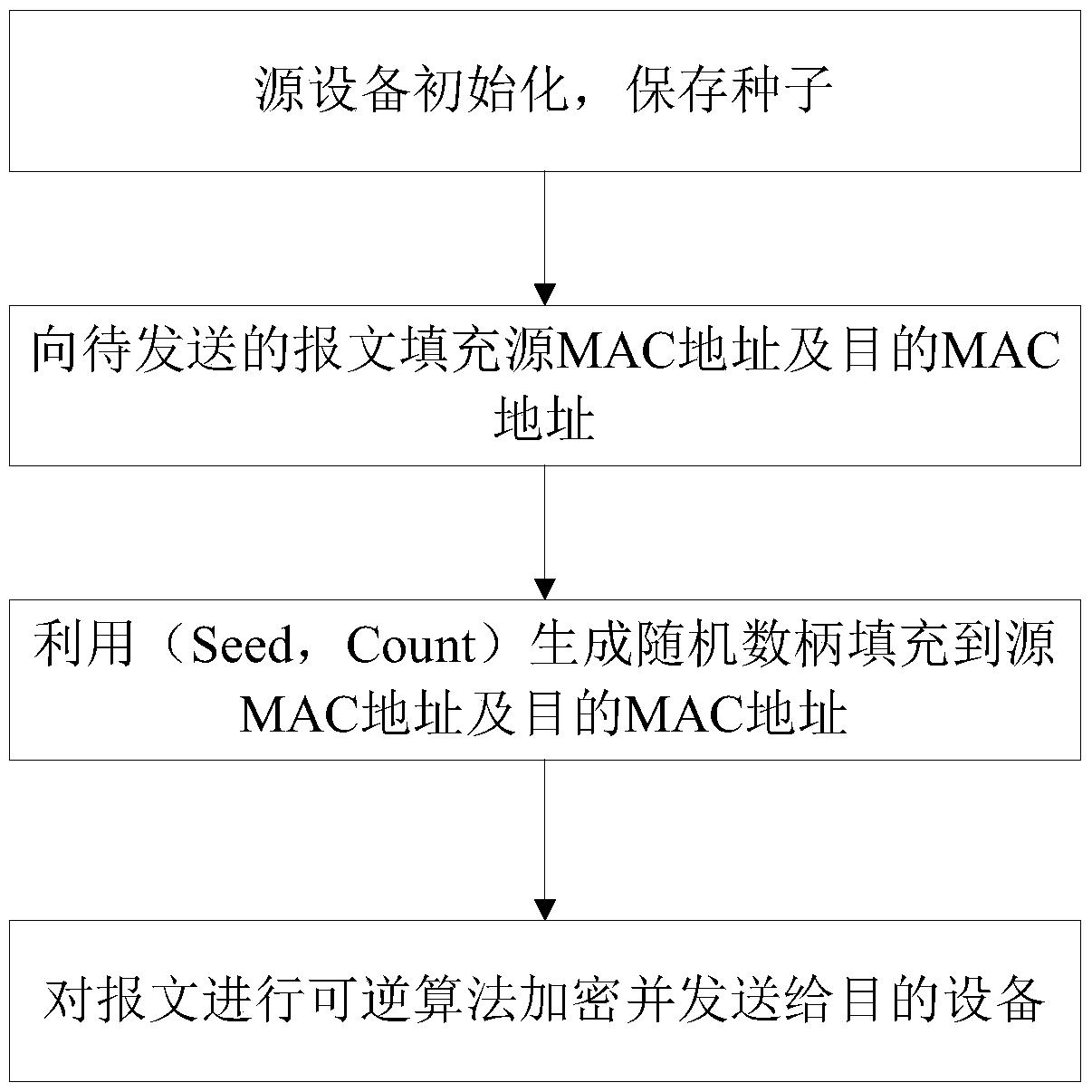
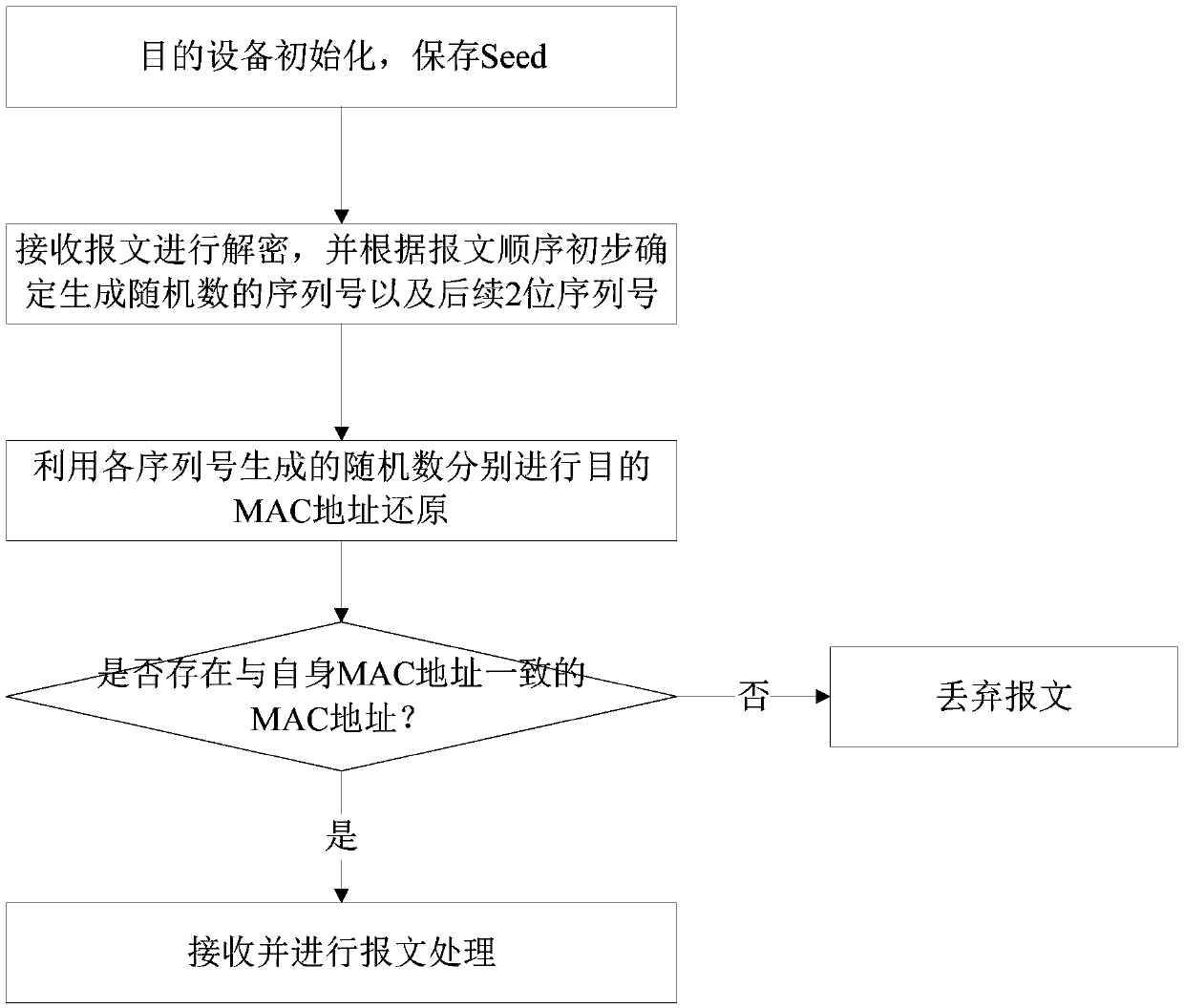
Method and system for safely accessing to target device by changing hardware identifiers
The invention discloses a method for safely accessing to a target device by changing hardware identifiers. The method is used for sending messages from a source device to the target device, comprising that: the source device obtains a corresponding first sequence number according to the sending sequence of the messages, generates random numbers based on the first sequence number and a first seed and adds the generated random numbers to the hardware identifiers of the target device of corresponding messages; after receiving the messages, the target device obtains a second sequence number according to the receiving sequence of the messages, generates corresponding random numbers based on the second sequence number and a second seed stored in the target device so as to reduce the hardware identifiers in the messages, compares the reduced hardware identifiers with own hardware identifiers, receives the messages when the reduced hardware identifiers are in accord with own hardware identifiers, and discards the messages when the reduced hardware identifiers are not in accord with own hardware identifiers. The invention also discloses a corresponding system for safety accessing to the target device. In application of the invention, the illegal monitoring difficulty is increased by adding random numbers to the hardware identifier so as to hidden the hardware identifiers; and the device accessing safety is ensured.
Owner:ZHEJIANG UNIVIEW TECH CO LTD
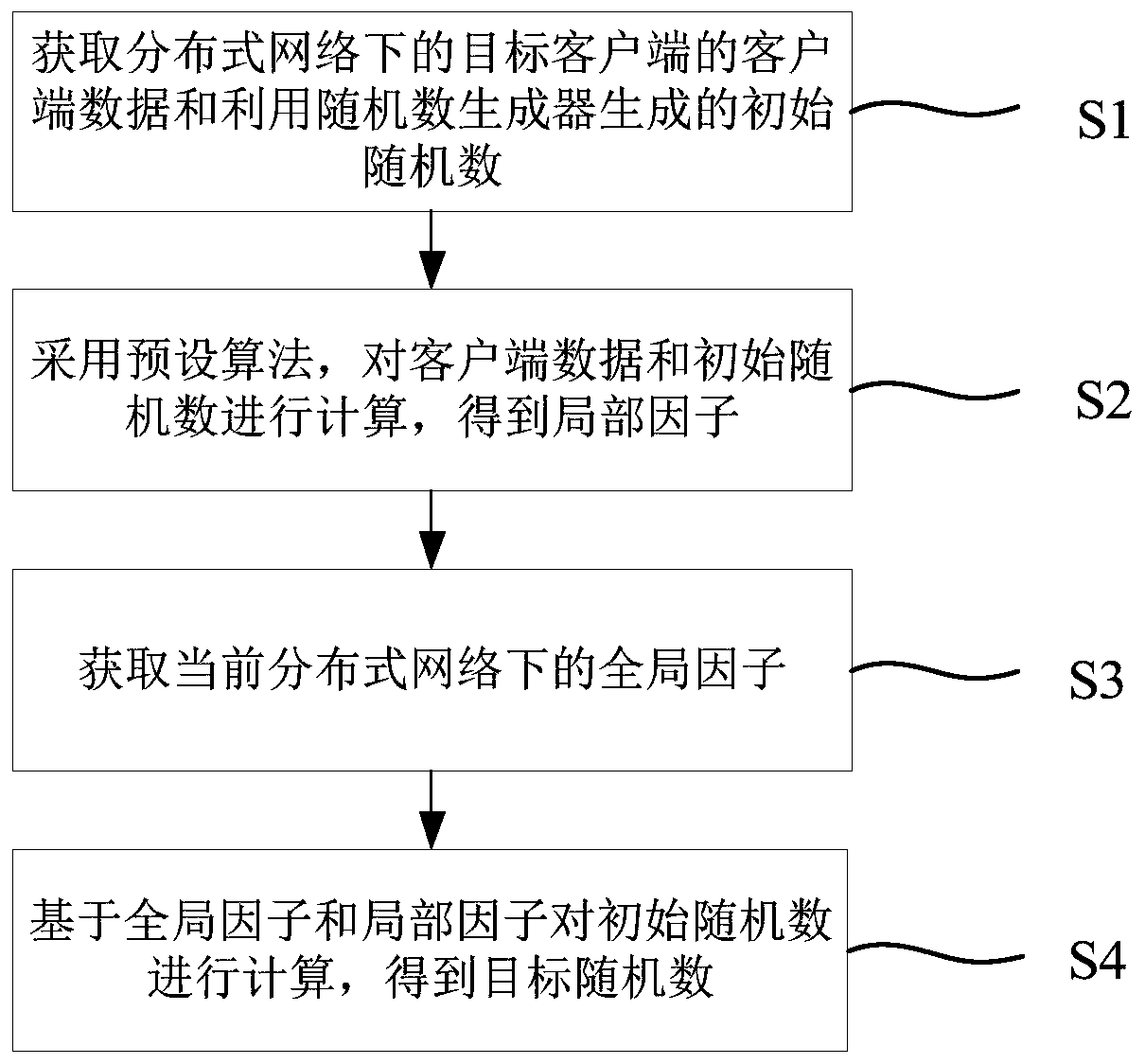
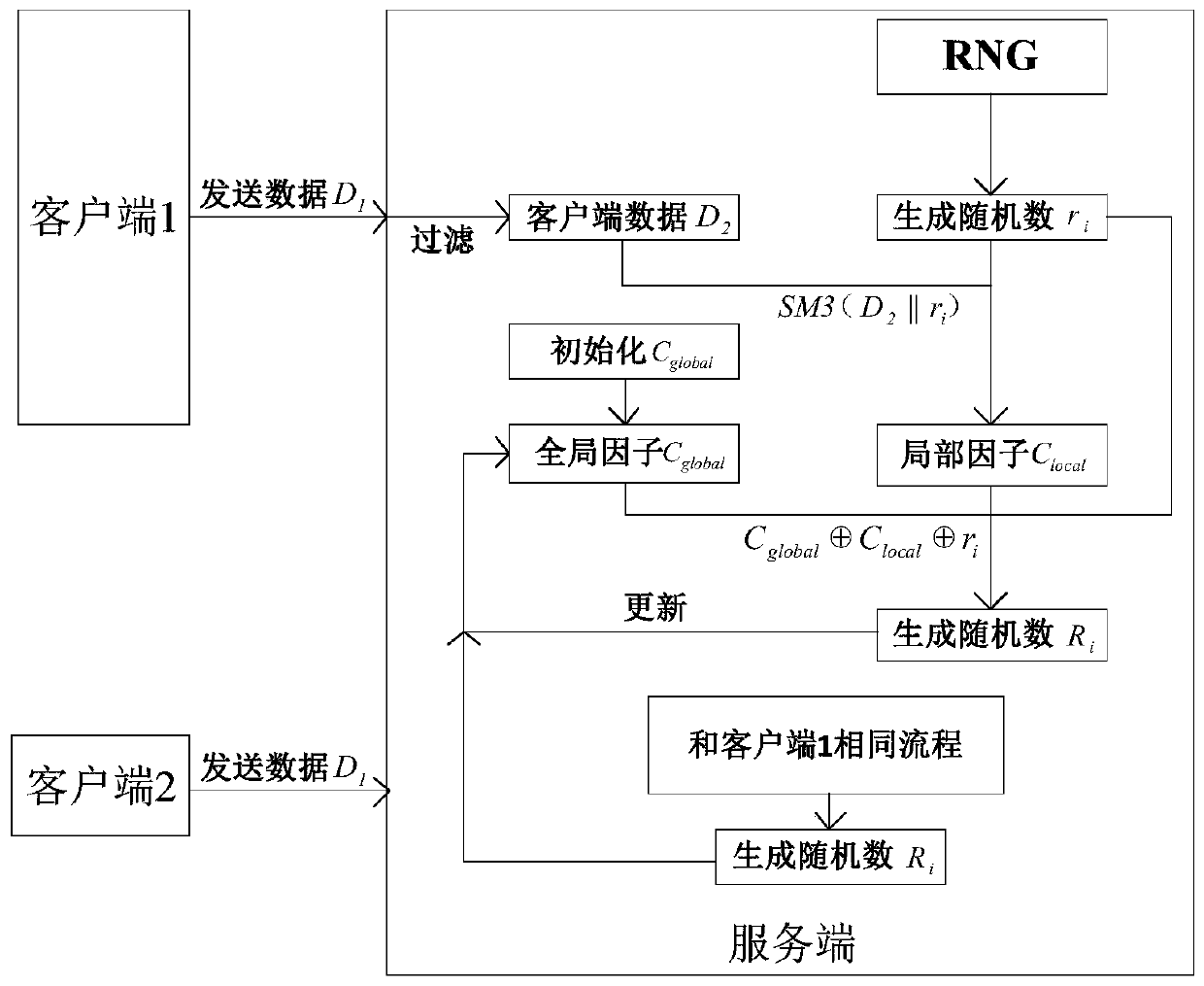
Random number generation method and system
ActiveCN111314061AIncrease production factorIncrease unpredictabilityKey distribution for secure communicationRandom number generatorsTheoretical computer scienceClient data
The invention provides a random number generation method and system, and the method comprises the steps: obtaining the client data of a target client under a distributed network and an initial randomnumber generated through a random number generator, and enabling the distributed network to comprise a plurality of distributed clients; calculating the client data and the initial random number by adopting a preset algorithm to obtain a local factor which is an influence factor provided by the target client and used for calculating the random number; obtaining a global factor under the current distributed network, wherein the global factor is an influence factor generated by utilizing random numbers corresponding to all clients under the distributed network; and calculating the initial randomnumber based on the global factor and the local factor to obtain a target random number. On the basis of the random number generated by the random number generator, the generation factors of the tworandom numbers are added, so that the generated random number rule is difficult to crack, and the unpredictability and randomness of the random number are improved.
Owner:SUZHOU KEDA TECH
Lightweight true random number generation method
PendingCN111142844AUnrestricted permissionsIncrease randomnessRandom number generatorsCharacter and pattern recognitionHash functionAccelerometer
The invention discloses a lightweight true random number generation method. The method comprises the following steps: (1) generating spatial motion trail characteristics of a mobile phone according tosignals of an accelerometer and a gyroscope; (2) taking the initial five-second spatial motion trail characteristics as reference values; (3) comparing the motion trail characteristic parameters acquired in real time with a reference value, wherein the output bit of forward deviation from the reference value is '1', and the output bit of reverse deviation from the reference value is '0'; and (4)when the length of the bit string output in the previous step reaches a specified value, hashing the bit string by using the selected hash function, and outputting the hash to obtain the generated random number sequence. The beneficial effects of the lightweight true random number generation method are that the data of the accelerometer and the gyroscope are fused to obtain the motion trail information of the mobile phone and generate random bits according to the trail range and amplitude; and an independent random number generation module can be formed, and randomness, unpredictability and non-reproducibility of data collected by an accelerometer and a gyroscope are improved.
Owner:杭州安司源科技有限公司
Method For Playing A Card Game
InactiveUS20120068409A1Improve overall revenueIncrease unpredictabilityCard gamesApparatus for meter-controlled dispensingPlaying cardComputer science
A method of playing a card game. The first step is to provide a deck of cards, wherein each playing card has a specific numeric value. A player places an Ante. The dealer then deals an initial hand of two cards face down to the dealer and to the player. The player views the initial hand of two cards in order to decide whether to stay or fold. The player forfeits his ante if the player decides to fold. Next, the player places a bet if the player decides to stay. The player then reveals his cards. The next step is to determine if the point value of the player's initial two-card hand is fourteen or fifteen. If the player's initial two-card hand has a point value of fourteen or fifteen, then the player is provided with an option to either (i) double down on the player's bet and take only one additional card, or (ii) not double down on the player's bet and take two additional cards. Thereafter, the dealer deals either the single additional card or the two additional cards face up to the player, depending upon the player's decision. If the player's initial two-card hand does not have a point value of fourteen or fifteen, then the player is required to take two additional cards. These additional two cards are dealt face up. The player's hand may never contain more than four cards. The dealer continues to deal cards to himself until the point value of the dealer's hand is greater than or equal to twenty one. The player loses if the point value of his hand exceeds twenty-five. The player wins if the player's hand has a point value of twenty-five and the dealer's hand has a point value that does not equal twenty-five, or if the point value of the player's hand is less than twenty-five and the point value of the dealer's hand is greater than twenty-five. There are other scenarios in which the player can win and there are scenarios in which the dealer can win.
Owner:CHAMBERLAIN RONALD
Method For Playing A Wagering Game
InactiveUS20100213672A1Improve overall revenueIncrease unpredictabilityCard gamesApparatus for meter-controlled dispensingRankingPlaying card
A method of playing a wagering game has the steps of providing at least one deck of playing cards, receiving an ante wager from each player in order to participate in the wagering game, dealing a first number of cards face down to each player who places the ante wager to form a player hand, dealing the first number of cards face down to the dealer to form a dealer hand, and providing an opportunity for a player to view the player's cards so that the player may decide whether to continue play or to surrender. Any player deciding to surrender shall fold and forfeit his ante wager. The method of playing the wagering game further includes receiving a call wager from each remaining player in order to continue to play the wagering game, dealing a second number of cards face down to each remaining player who places a call wager so that each player's hand is now formed by the combination of the first and second number of cards, dealing the second number of cards face down to the dealer so that the dealer's hand is now formed by the combination of the first and second number of cards, and determining if any player does not have at least a four card straight, a four card flush or a four card straight-flush. Any player that does not have at least a four card straight, a four card flush or a four card straight-flush immediately loses his ante wager and any jackpot wager. However, such a situation is a push with respect to the player's call wager and so the player's call wager is returned to him. Each player that has at least a four card straight-flush, a four card flush or a four card straight now plays against the dealer's hand. Next, the dealer's and player's hands are ranked in accordance with a predetermined ranking of hands. A player is paid on the player's ante and call wagers in accordance with a predetermined pay-table when the player's hand outranks the dealer's hand. Ante and call wagers are collected from the players whose hands do not outrank the dealer's hand.
Owner:VEGAS GAMING GROUP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com