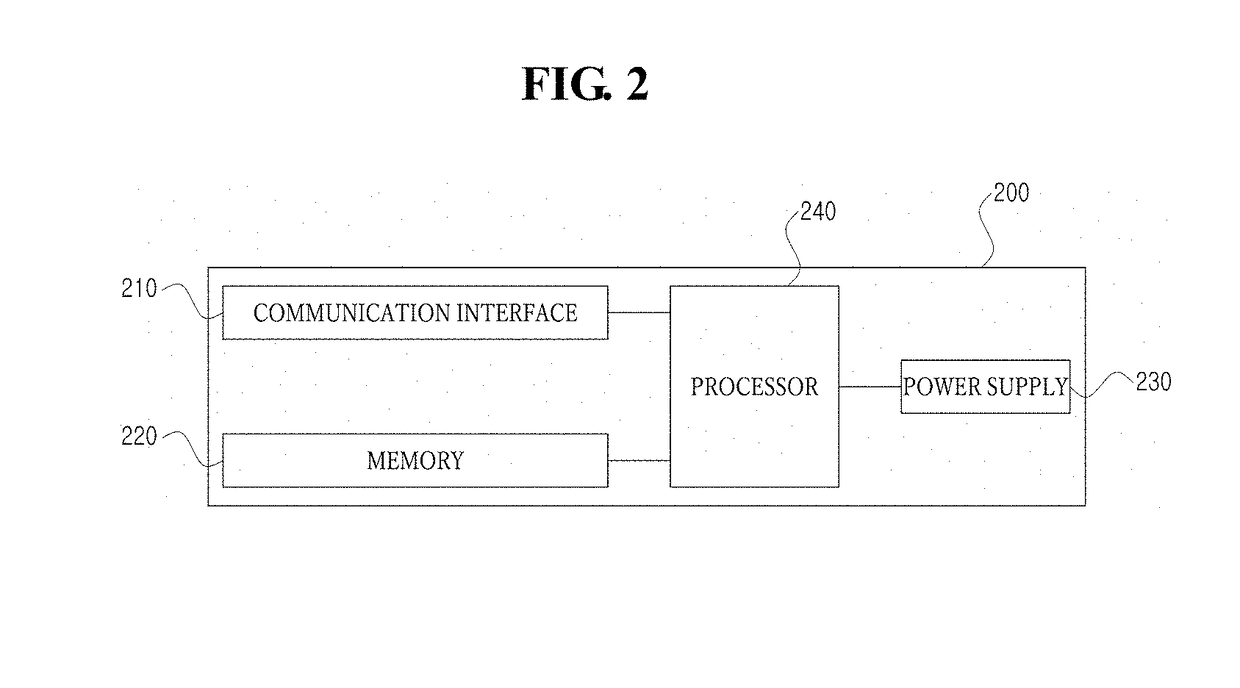
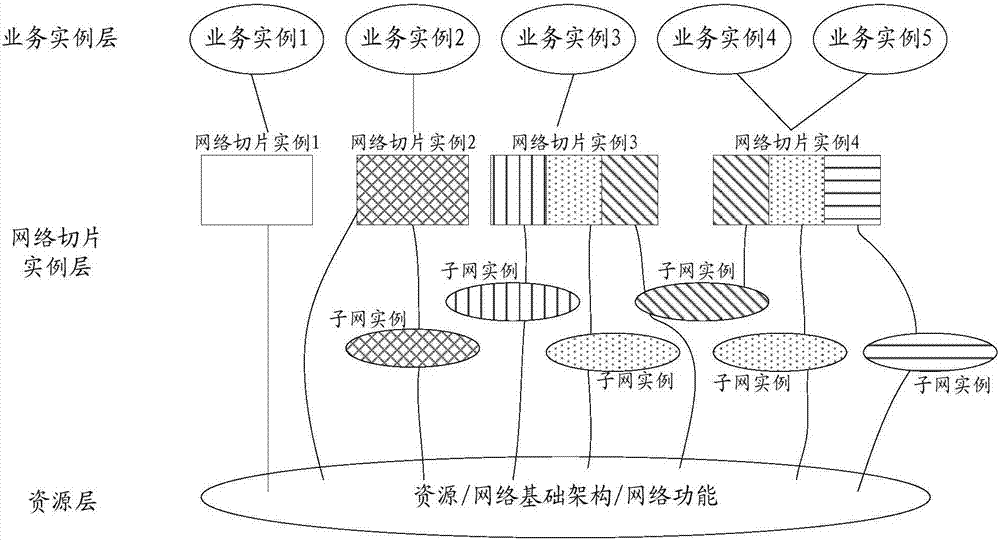
Patents
Literature
156results about How to "Improve access security" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
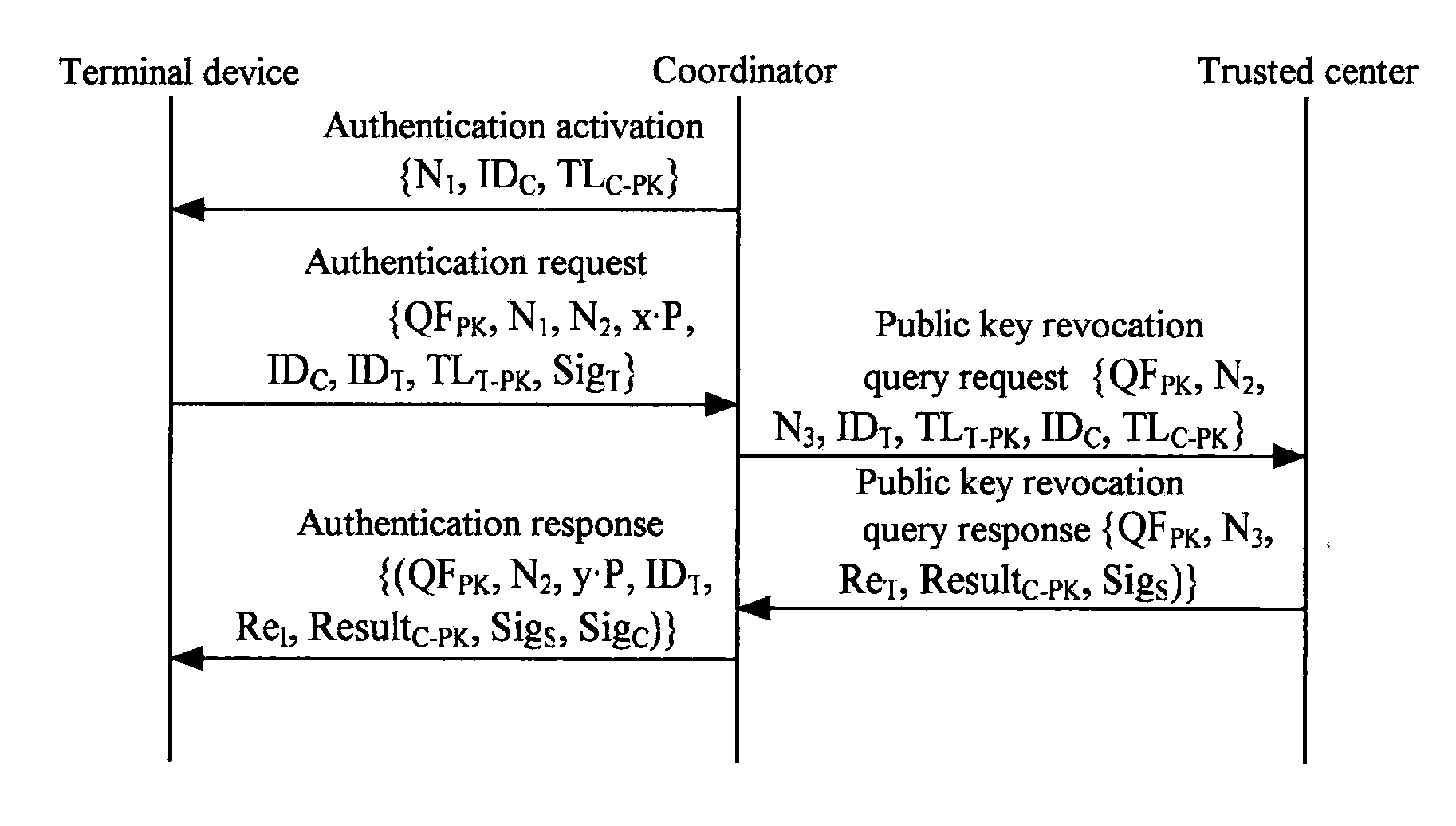
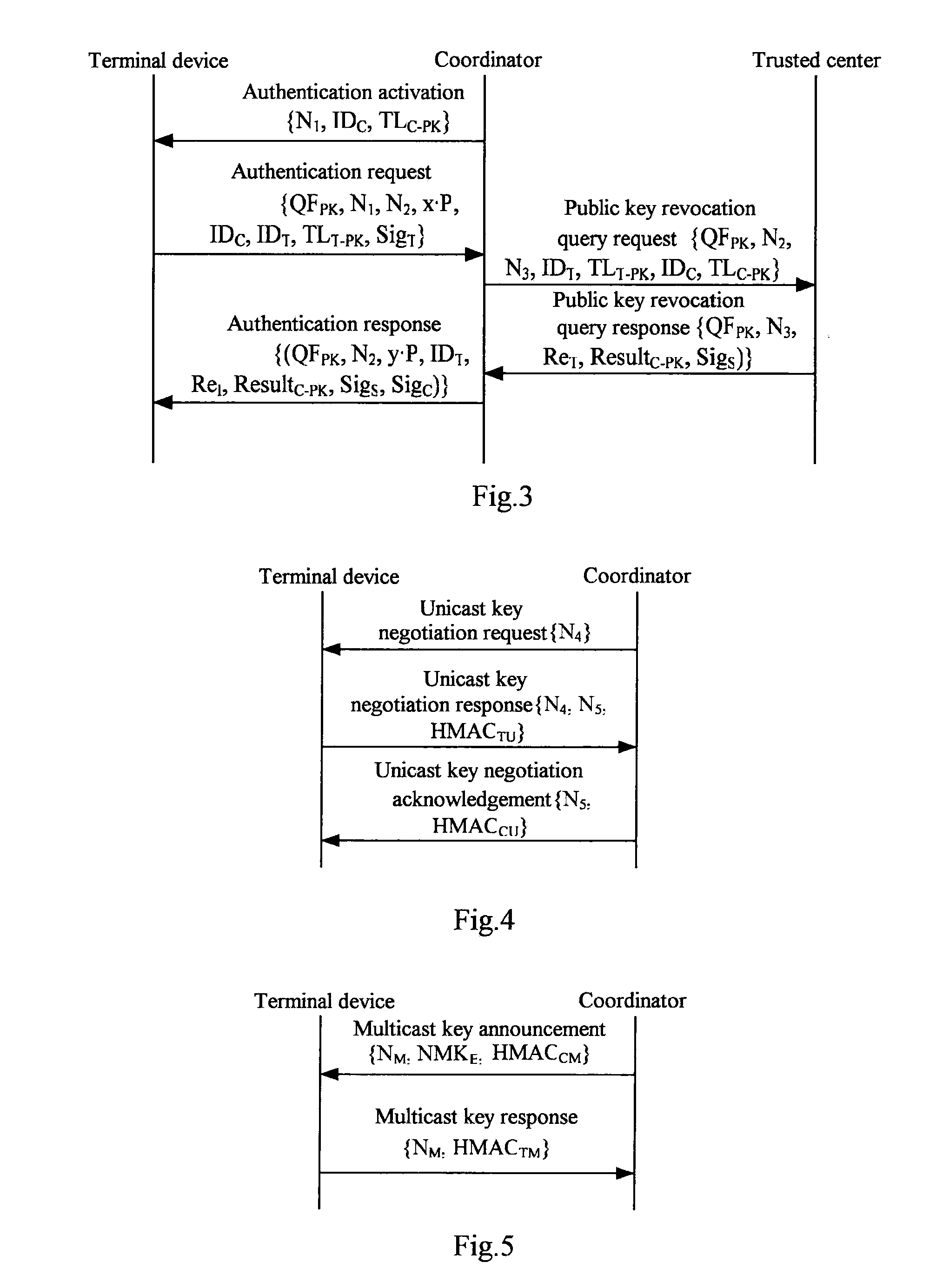
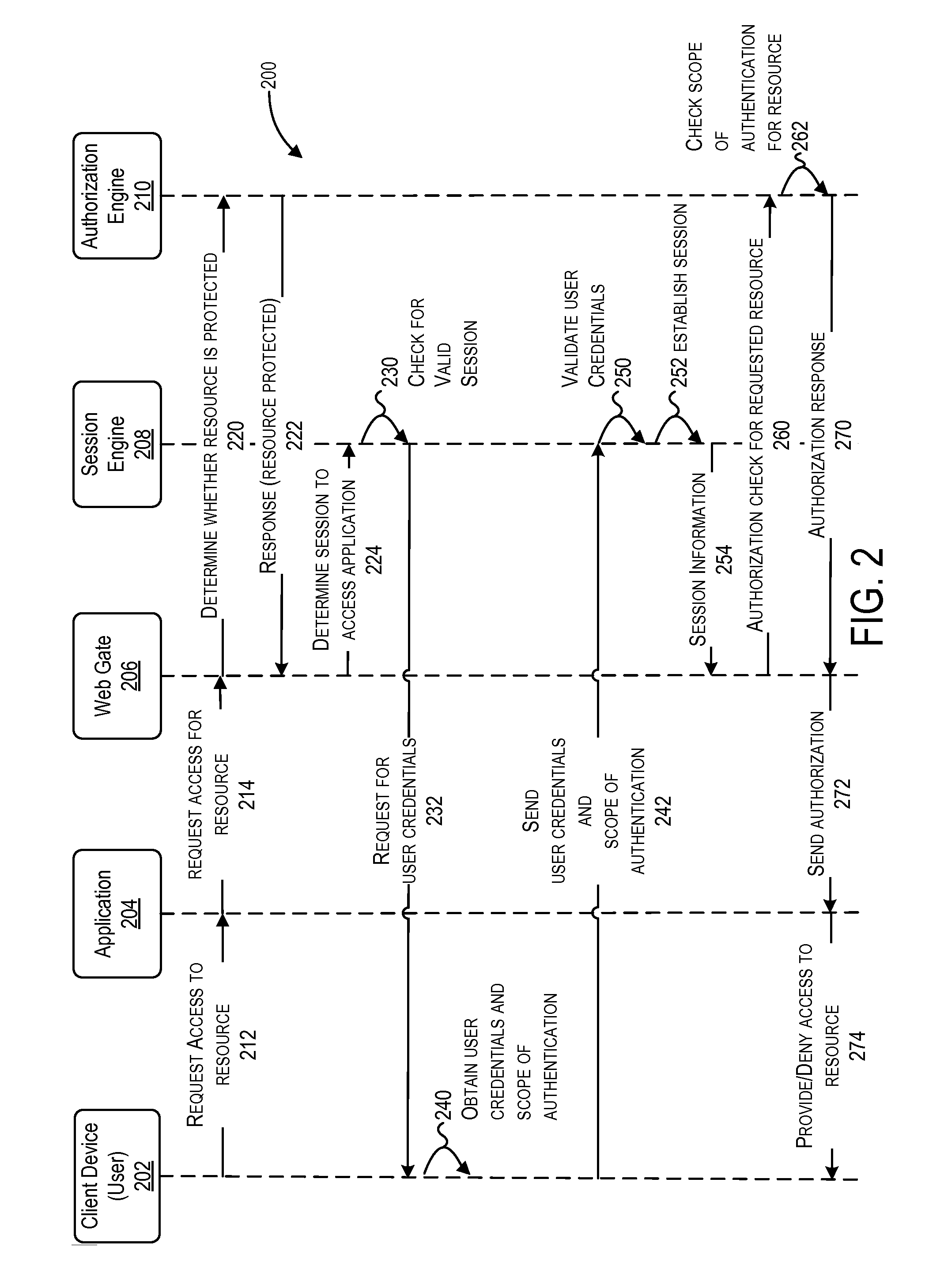
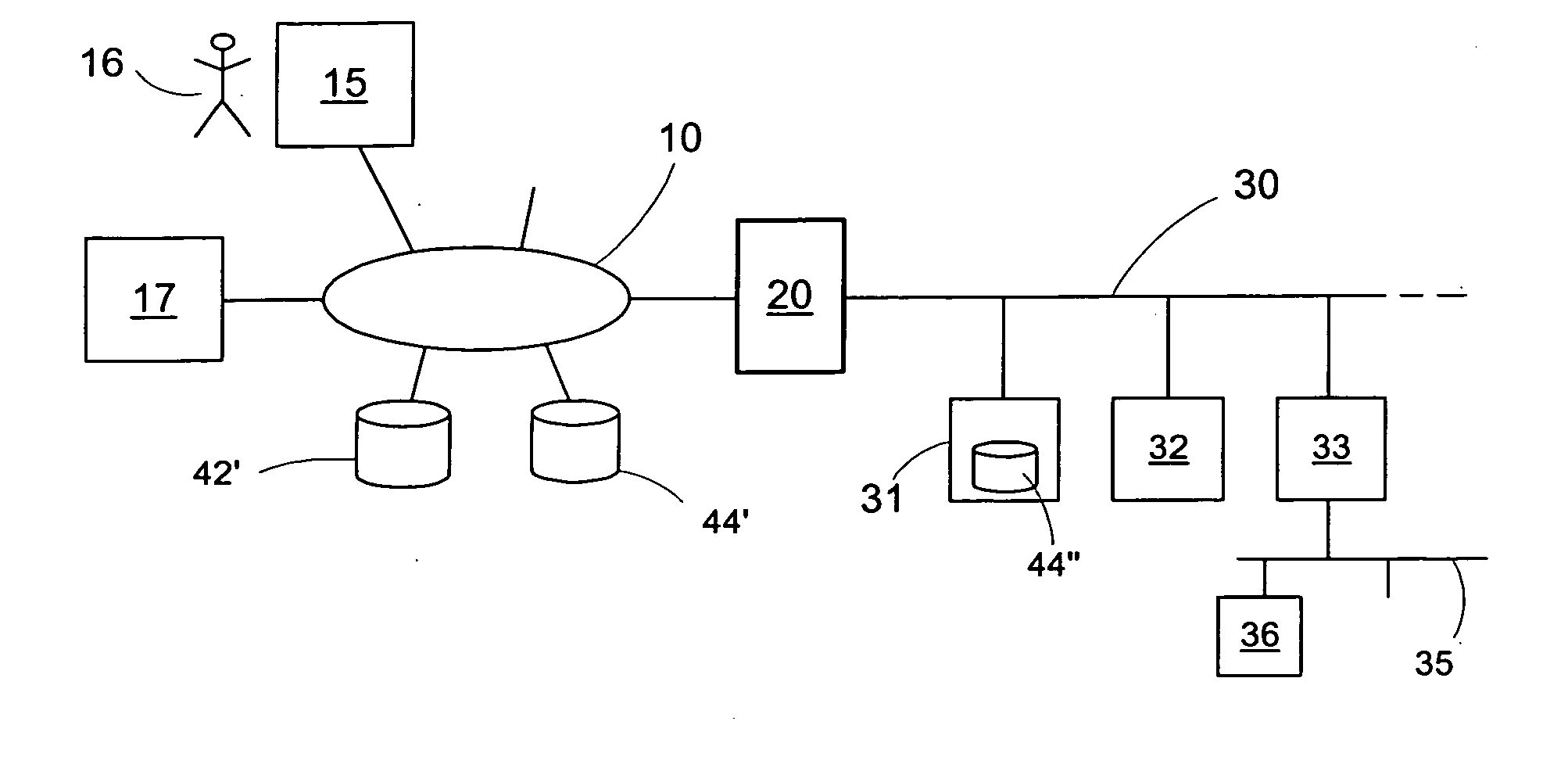
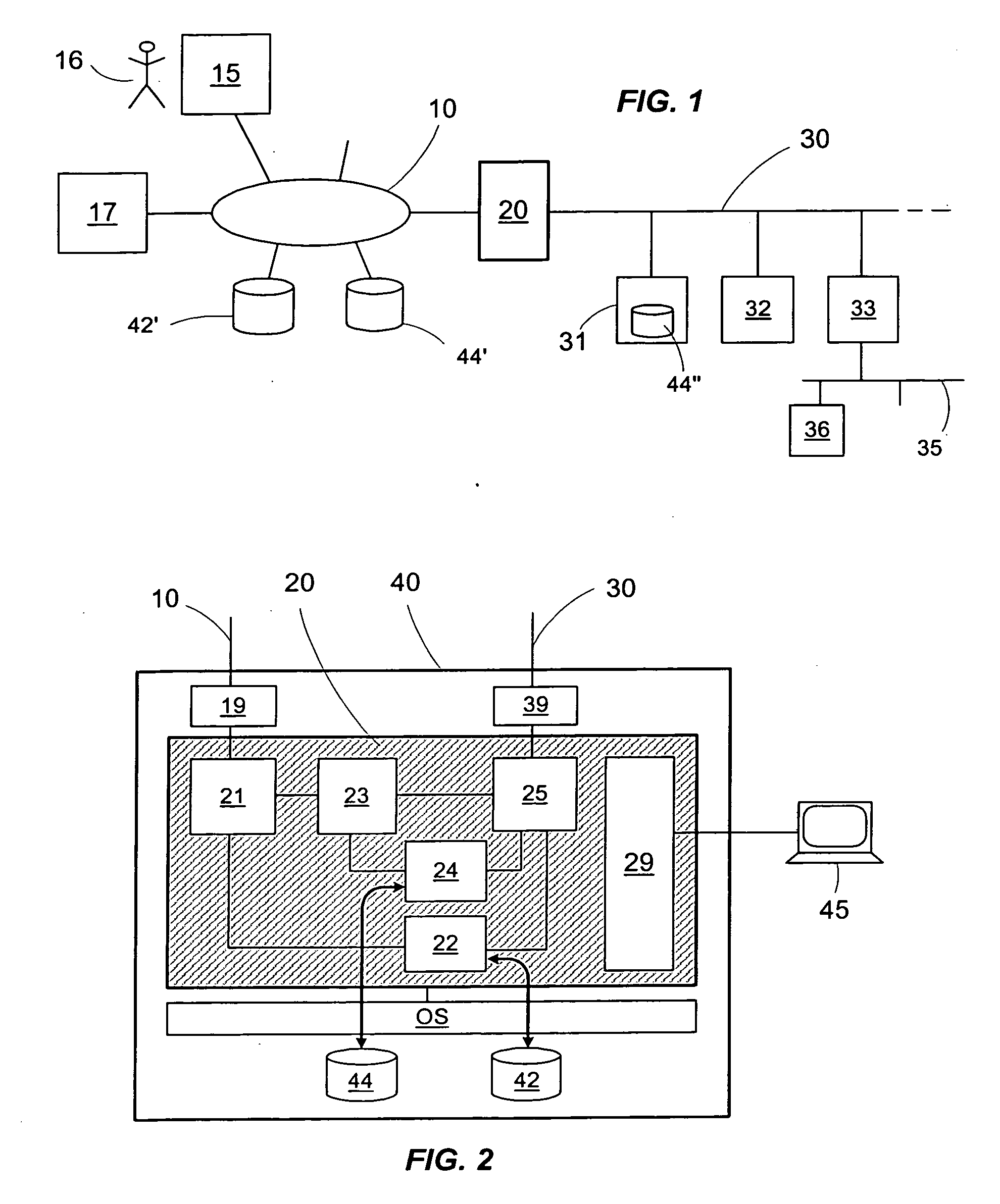
Authentication access method and authentication access system for wireless multi-hop network
InactiveUS20100293370A1Improve access securityImprove access performanceUser identity/authority verificationSecret communicationWeb authenticationAccess method
Authentication access method and authentication access system for wireless multi-hop network. Terminal equipment and coordinator have the capability of port control, the coordinator broadcasts a beacon frame, and the terminal equipment selects an authentication and key management suite and transmits a connecting request command to the coordinator. The coordinator performs authentication with the terminal equipment according to the authentication and key management suite which is selected by the terminal equipment, after authenticated, transmits a connecting response command to the terminal equipment. The terminal equipment and the coordinator control the port according to the authentication result, therefore the authenticated access for the wireless multi-hop network is realized. The invention solves the security problem of the wireless multi-hop network authentication method.
Owner:CHINA IWNCOMM
Communications Device Authentication
ActiveUS20140057599A1Authentication is efficient and rapidThe certification process is reliableUnauthorised/fraudulent call preventionEavesdropping prevention circuitsRadio access technologyCommunication device
There is described a method of accessing a resource requiring identity authentication, the method comprising: receiving at a communications device an encrypted token in response to an identity of the communications device being authenticated over a first radio access technology; decrypting the encrypted token using the identity of the communications device; and using the decrypted token over a second radio access technology to authenticate the identity of the communications device so as to allow access to the resource via the second radio access technology.
Owner:VODAFONE IP LICENSING
Restricting access for a single sign-on (SSO) session
ActiveUS20170034152A1Easy to controlImprove access securityTransmissionInternet privacyAccess management
Techniques are disclosed for restricting access to resources accessible in a SSO session. An access management system may provide access one or more resources by implementing an SSO system to provide a SSO session. An SSO session may provide an authenticated user with access to protected resources to which the user is entitled to access. In some instances, a user sharing a computer with other users may want to access a particular protected resource so as to restrict other users sharing the computer from accessing other protected resources accessible to the user in an SSO session. The access management system may enable the user to dynamically choose, such as during login, the protected resources which to restrict and / or permit. Upon successful authentication, a session may be established for only those protected resources that are permitted based on the user's selection, while the other resources are restricted.
Owner:ORACLE INT CORP
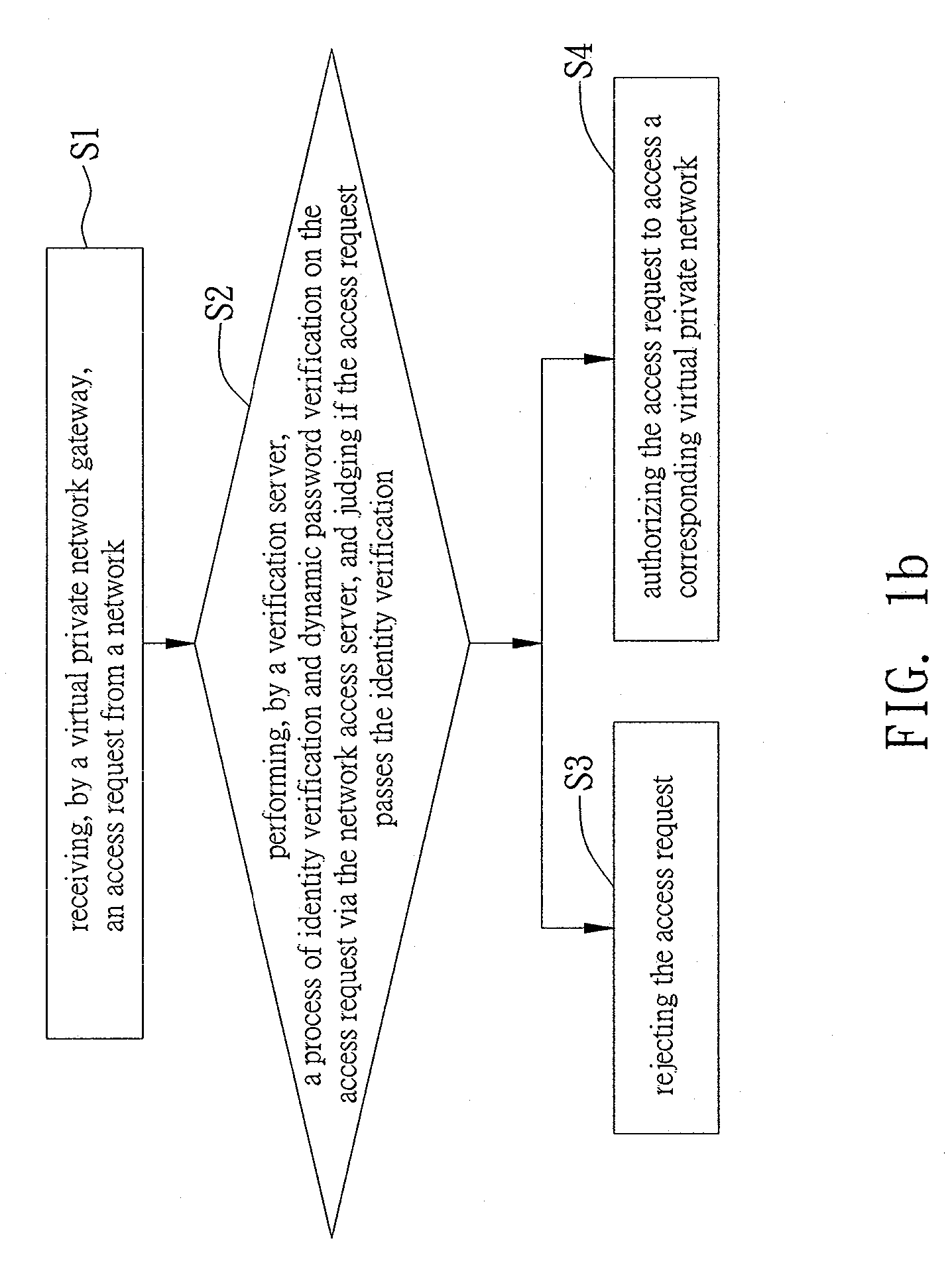
Identity verification system applicable to virtual private network architecture and method of the same
InactiveUS20090313691A1Improve access securityProvide convenienceMultiple digital computer combinationsProgram controlNetwork access serverPrivate network
An identity verification system applicable to a virtual private network architecture and method of the same are provided. The system is provided and connected to a virtual private network gateway. The virtual private network gateway is connected to a verification server via a network access server. The method comprises receiving an access request from a network via the virtual private network gateway, performing a process of identify verification and dynamic password verification on the access request by the verification server and via the network access server, rejecting the access request if the access request does not pass the identity verification, and authorizing the access request to access a corresponding virtual private network if the access request passes the identity verification, thereby enhancing security in accessing the virtual private network.
Owner:CHUNGHWA TELECOM CO LTD
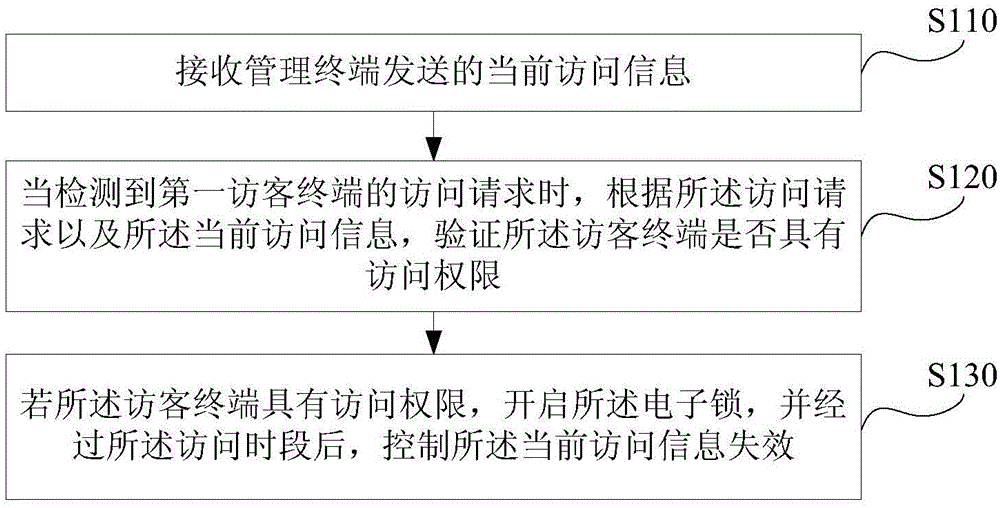
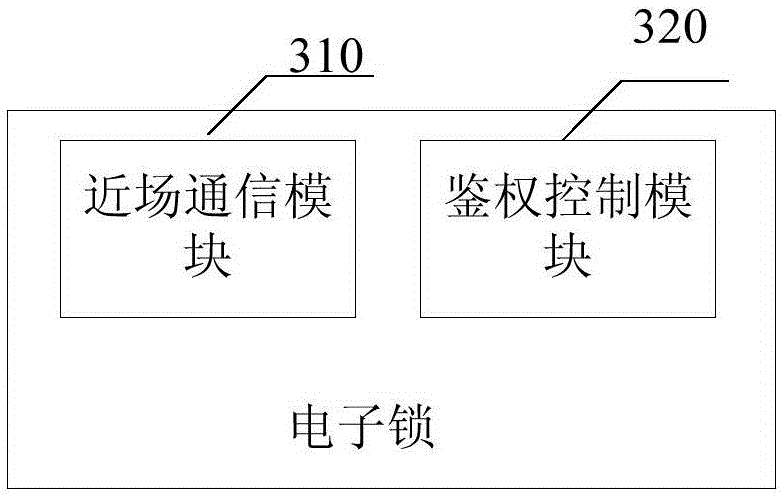
Access control method and system, electronic lock, and management and visitor terminal
ActiveCN105654580AImprove access securityLow costIndividual entry/exit registersTransmissionAccess timeComputer terminal
The invention discloses an access control method and system, an electronic lock, and a management and visitor terminal. A management terminal authorizes the access of a legal visitor terminal to an electronic lock. Then the management terminal will send the identification number of the visitor terminal, access time, and access secret key to the electronic lock. When the electronic lock detects the access request from the visitor terminal, the access request carries with the identification number of the visitor terminal and current access secrete key, the electronic lock will judge whether the visitor terminal is a legal visitor terminal that has been authorized by the management terminal or not according to the identification number, thus the access secret key will not be stolen and used by other visitor terminals, the happening of illegal access to the electronic lock is avoided; moreover, the management only authorize a certain time period during which the visitor terminal can access the electronic lock, after the period, the secret key expires, and thus the access safety of the electronic lock is further improved.
Owner:YULONG COMPUTER TELECOMM SCI (SHENZHEN) CO LTD
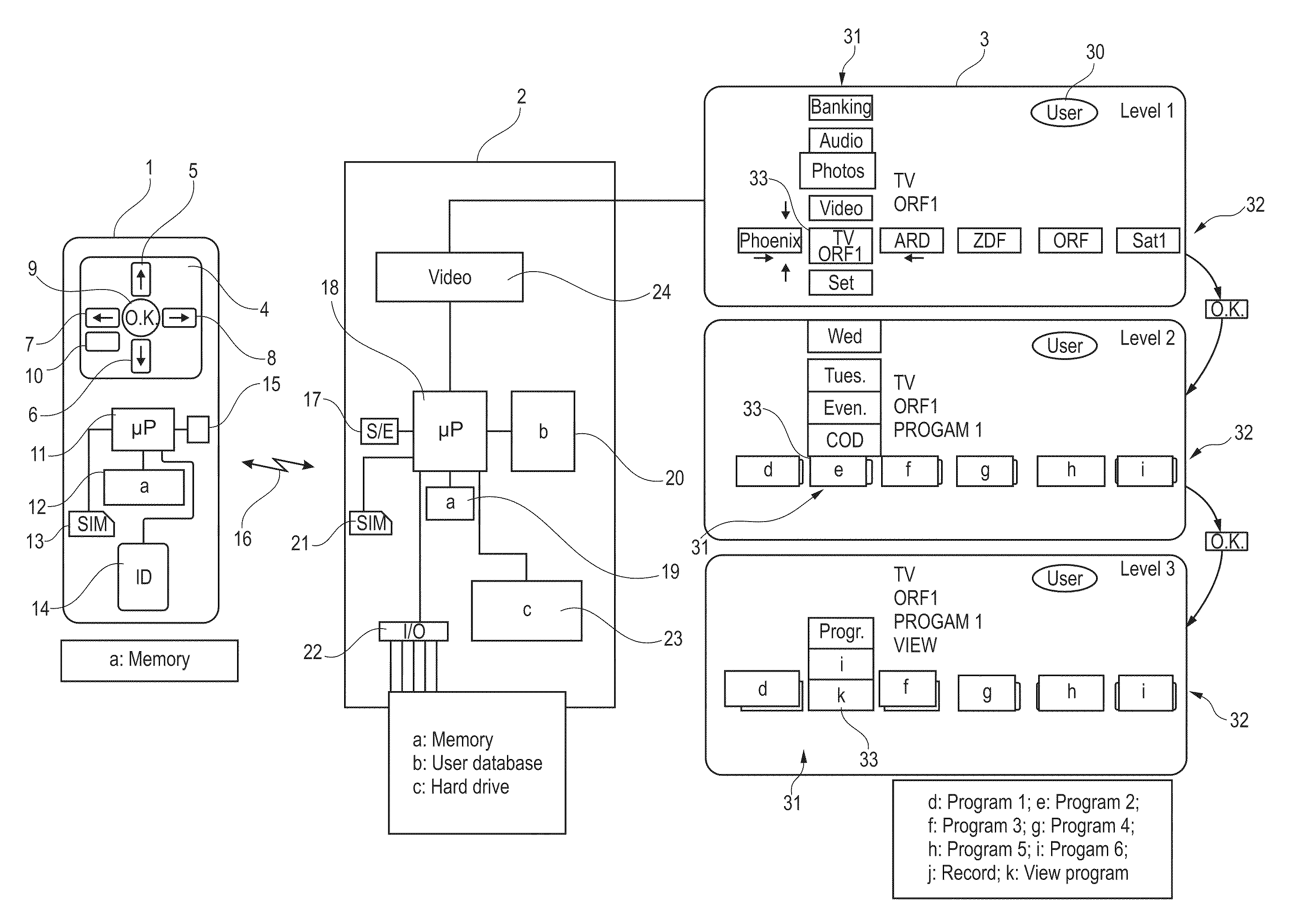
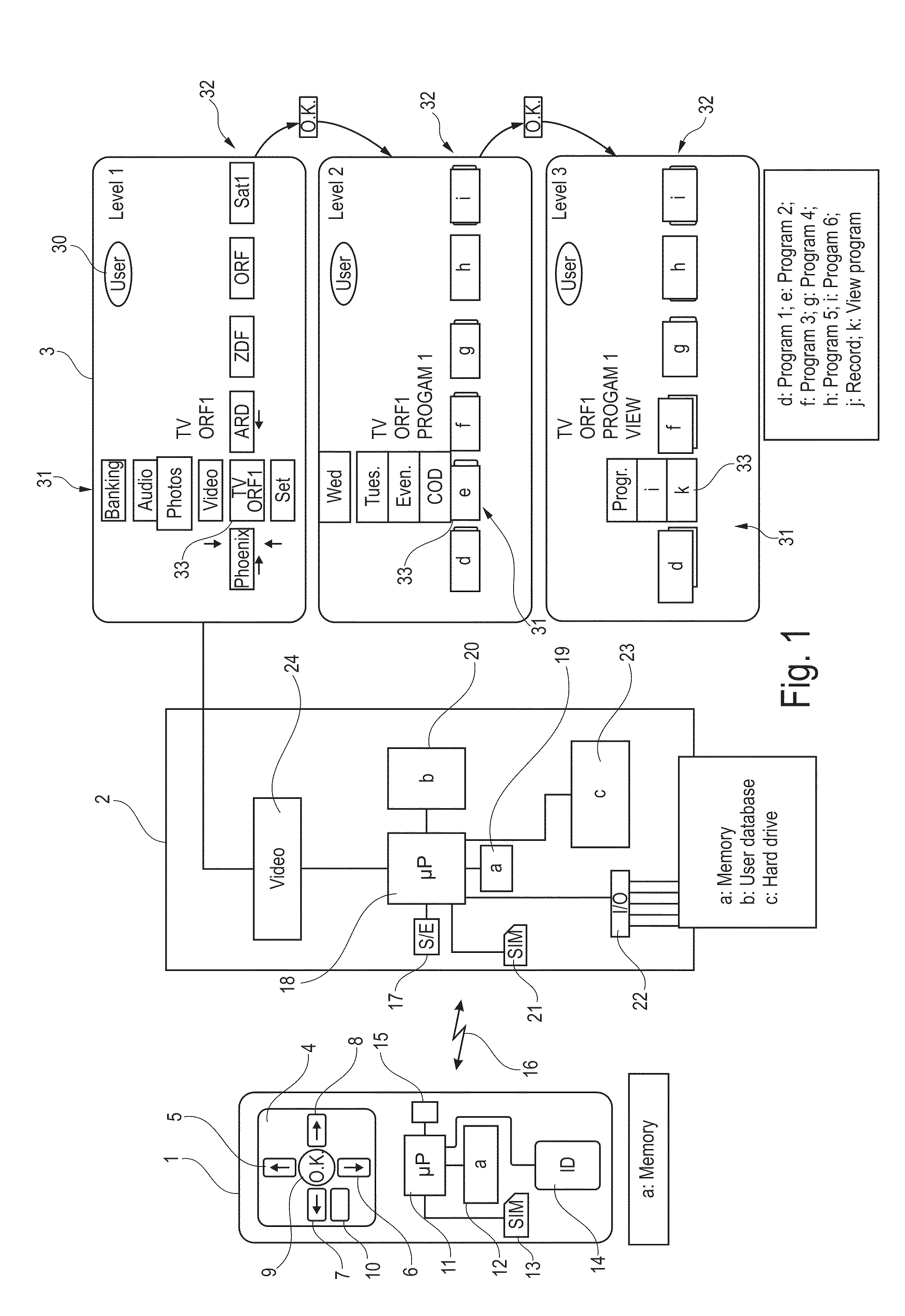
Multimedia arrangement
InactiveUS20100146278A1Easy to operateImprove remote controlTelevision system detailsDigital data processing detailsRemote controlDisplay device
The invention relates to a multimedia arrangement comprising a remote control (1) having a keypad (4) with only six control buttons (5-10). All functions of the multimedia device (2) can be controlled via three menu levels, an object group being selectable in the first menu level, an object being selectable in the second menu level, and an action to be performed with the object being selectable in the third. Elements of the object groups, objects, and actions are displayed in fields on the display device in a vertical column (31) and a horizontal line (32), the column (31) and the line (32) intersecting in a focus field (33). The elements of the fields can be moved by the control buttons (5-8) in the fixed focus field, and can be activated there by a selection button (9). Selection and arrangement of the elements is done by a user database (20) in the multimedia device depending on data determined by an identification device of the remote control.
Owner:FM MARKETING
Access control system for automation equipment
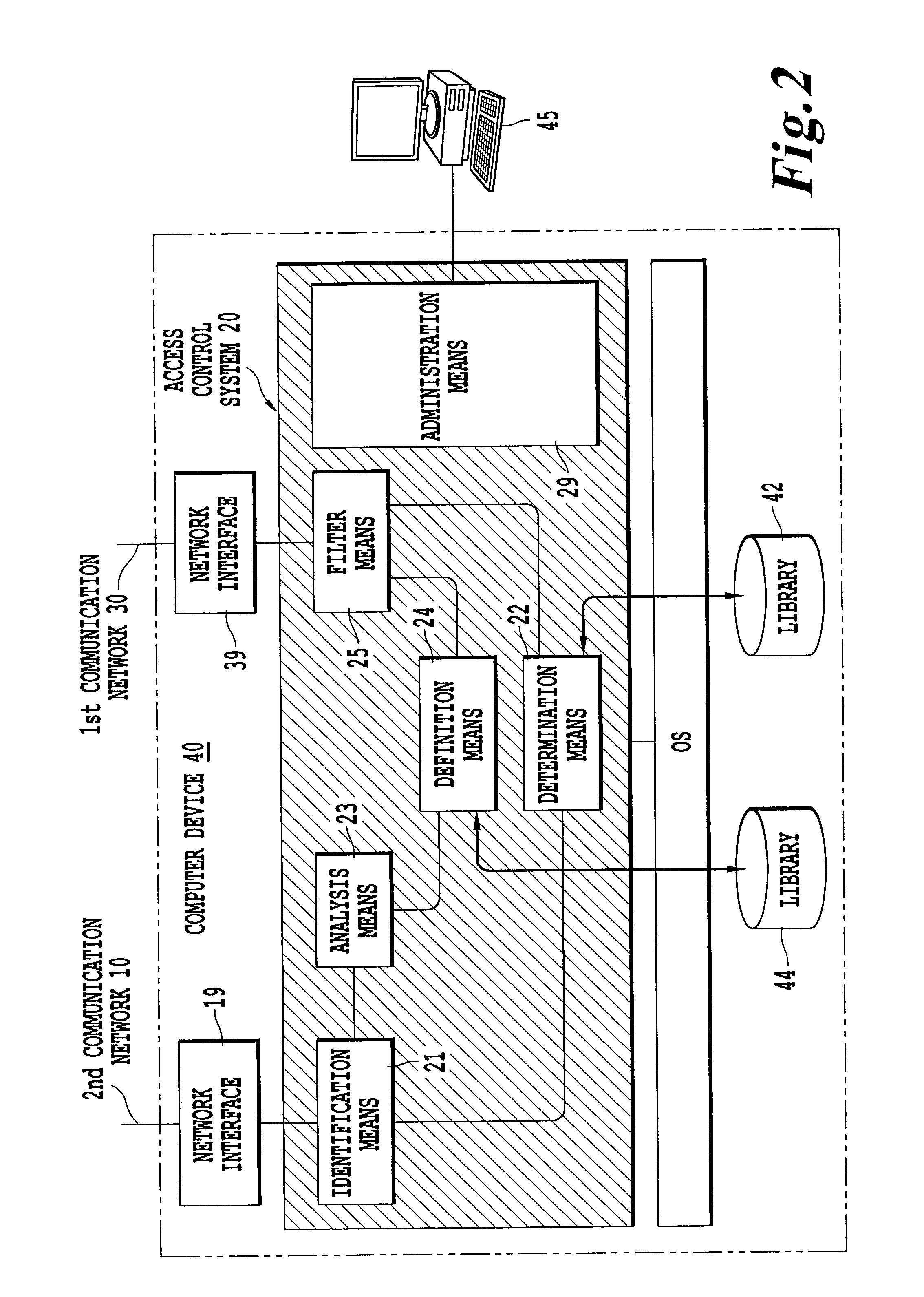
ActiveUS20070112961A1Improve securityEasy maintenanceError preventionFrequency-division multiplex detailsClient-sideBusiness function
System for controlling access to automation equipments connected to a first network, from at least one client station connected to a second network. The system includes determination means of a functional profile containing a list of business functions that a user of the client station is authorized to carry out on the equipment, analysing means of a frame sent on the second network by the user, in order to determine a request and a destination equipment, definition means of a filter profile for the destination equipment, containing, for each business function and for each protocol, a list of requests that the destination equipment is capable of receiving, and filter means capable of authorizing or prohibiting transmission of the sent frame on the first network, according to the frame, the functional profile of the identified user and the filter profile of the destination equipment.
Owner:SCHNEIDER ELECTRIC IND SAS
Method for managing wireless multi-hop network key
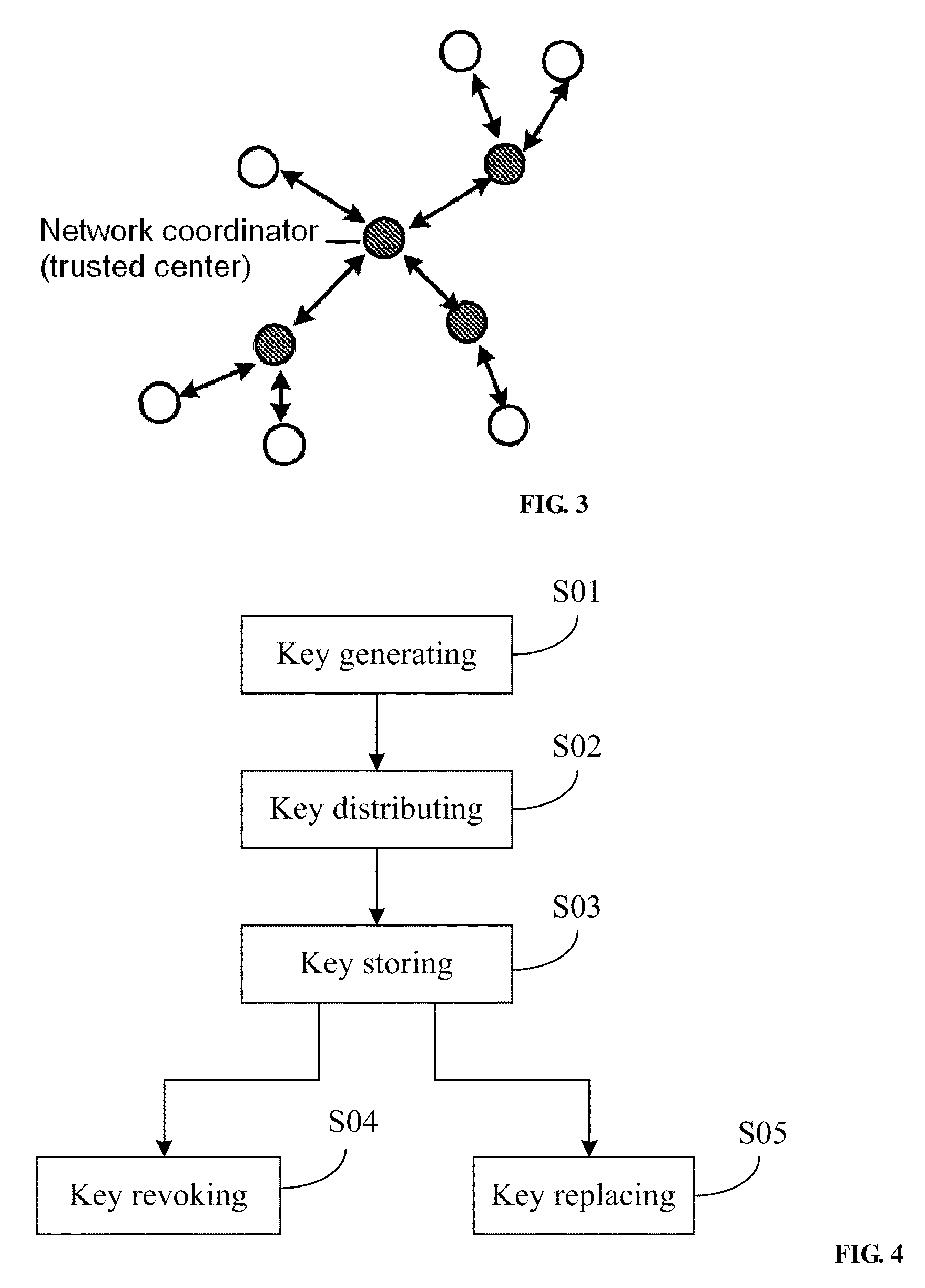
InactiveUS20100299519A1Improve securityImprove performancePublic key for secure communicationNetwork topologiesNetwork keyLarge networks
A method for managing wireless multi-hop network key is applicable to a security application protocol when a WAPI frame method (TePA, an access control method based on the ternary peer-to-peer identification) is applied in a concrete network containing a Wireless Local Area Network, a Wireless Metropolitan Area Network AN and a Wireless Personal Area Network. The key management method of the present invention includes the steps of key generation, key distribution, key storage, key modification and key revocation. The present invention solves the technical problems that the prior pre-share-key based key management method is not suitable for larger networks and the PKI-based key management method is not suitable for wireless multi-hop networks; the public-key system and the ternary structure are adopted, thereby the security and the performance of the wireless multi-hop networks are improved.
Owner:CHINA IWNCOMM
Service access method and system, authentication method and system, client and authentication server
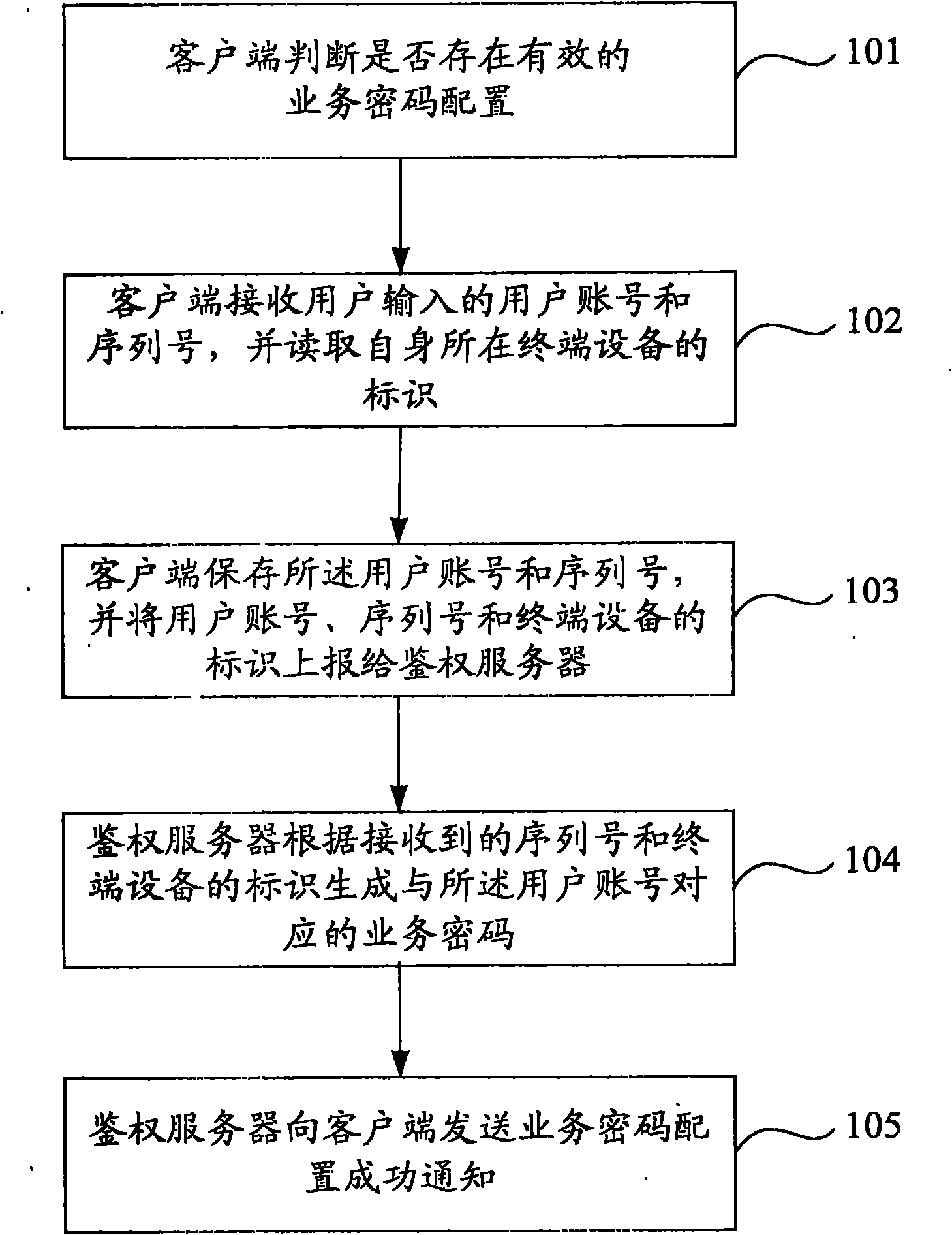
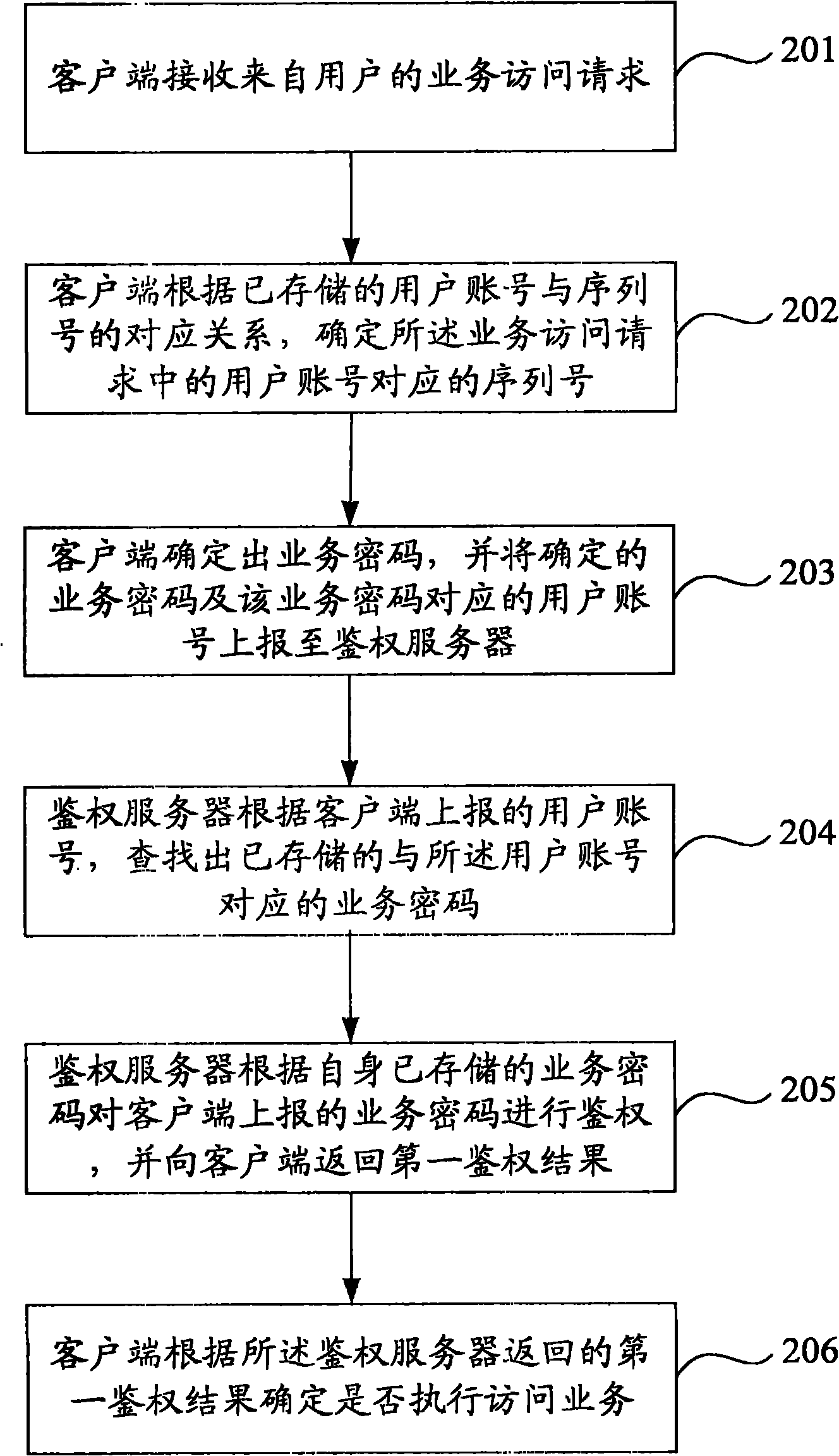
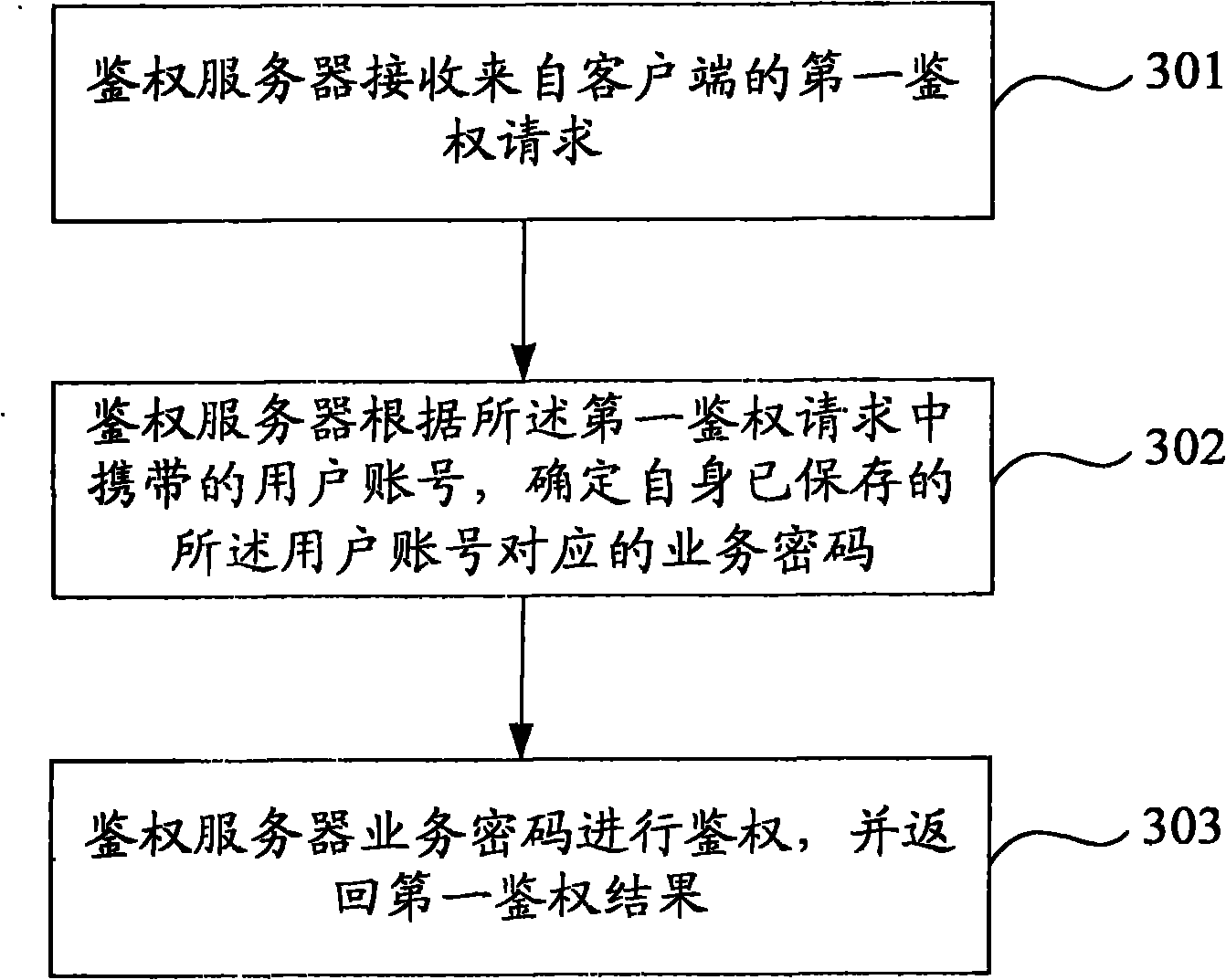
The invention provides a service access method, a service access system, an authentication method, an authentication system, a client and an authentication server. The specific content is that: the authentication server generates and stores a service password corresponding to a user account according to the user account, a sequence number and an identifier of terminal equipment which are submitted by the client; when a subsequent user requests for service access, the client generates a service password corresponding to the user account according to the user account, the sequence number and the identifier of the terminal equipment, and indicates the authentication server to authenticate according to the pre-stored service password and the service password generated by the client; the service password is relevant to the identifier of the terminal equipment in which the client is positioned and relevant to the sequence number, the identifier of the terminal equipment is difficult to steal maliciously and the sequence number has longer bits from 64 to 128 and is difficult to peep, so the safety of accessed service can be improved by adopting the scheme of the embodiment of the invention.
Owner:CHINA MOBILE COMM CO LTD
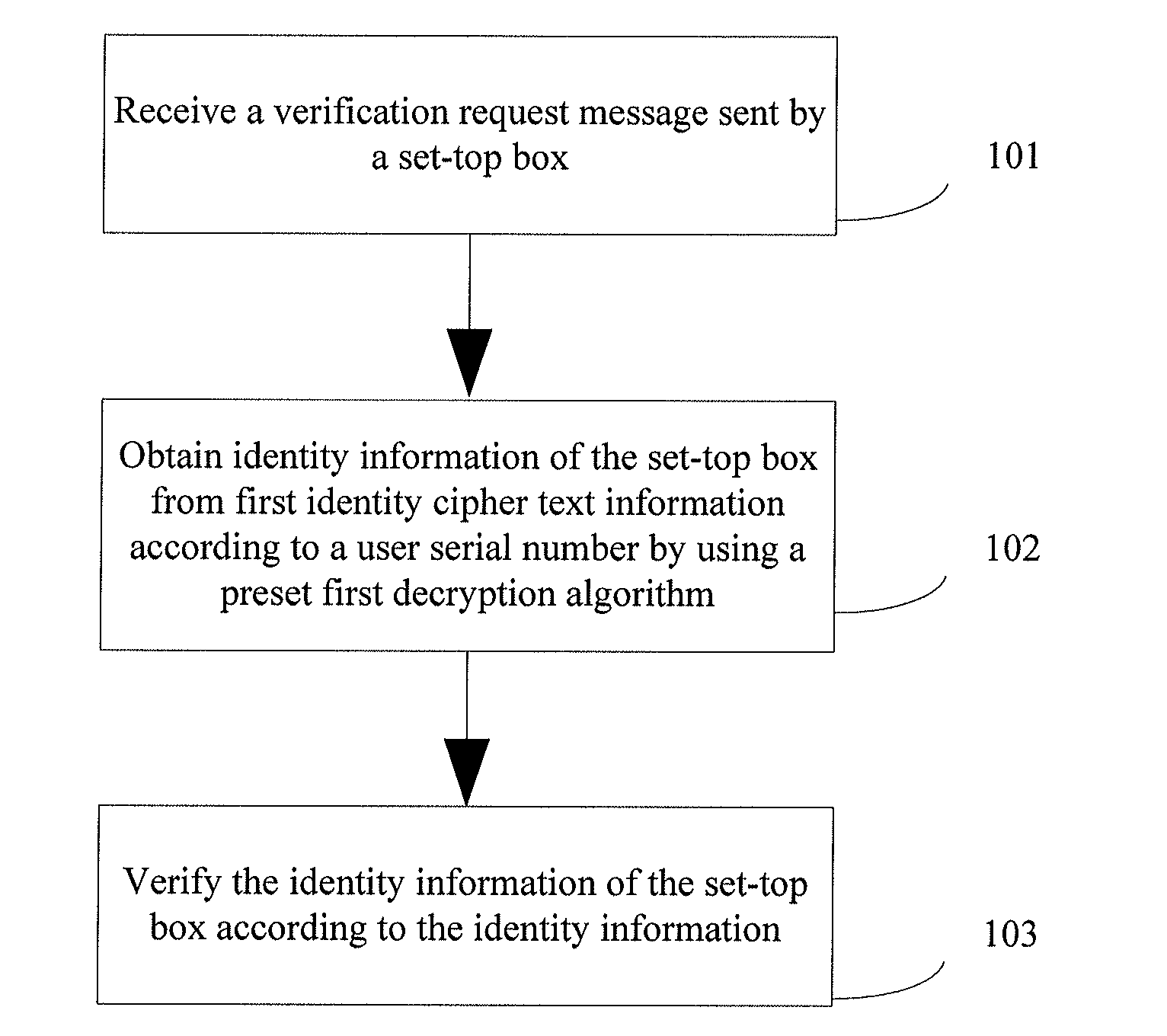
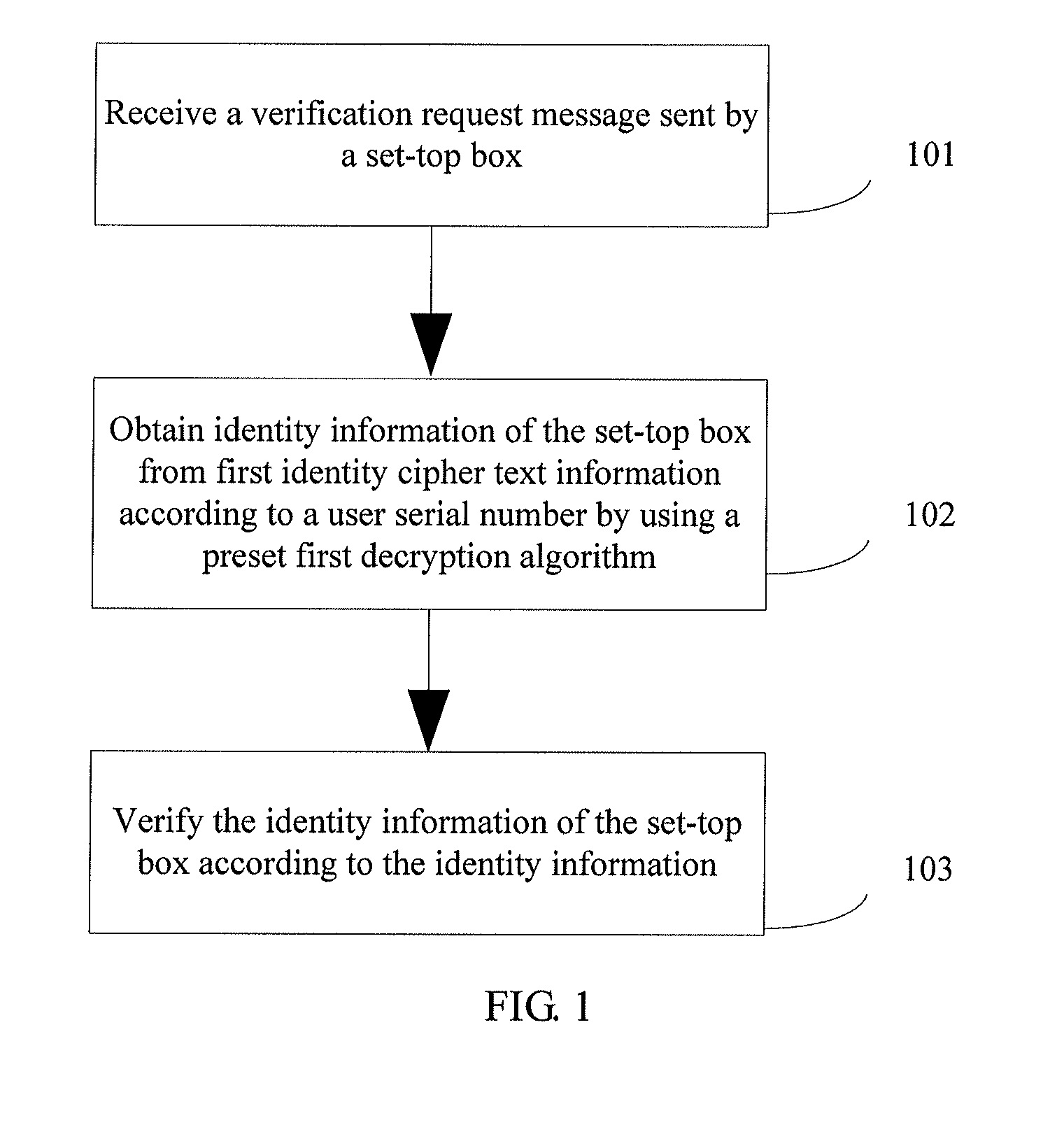
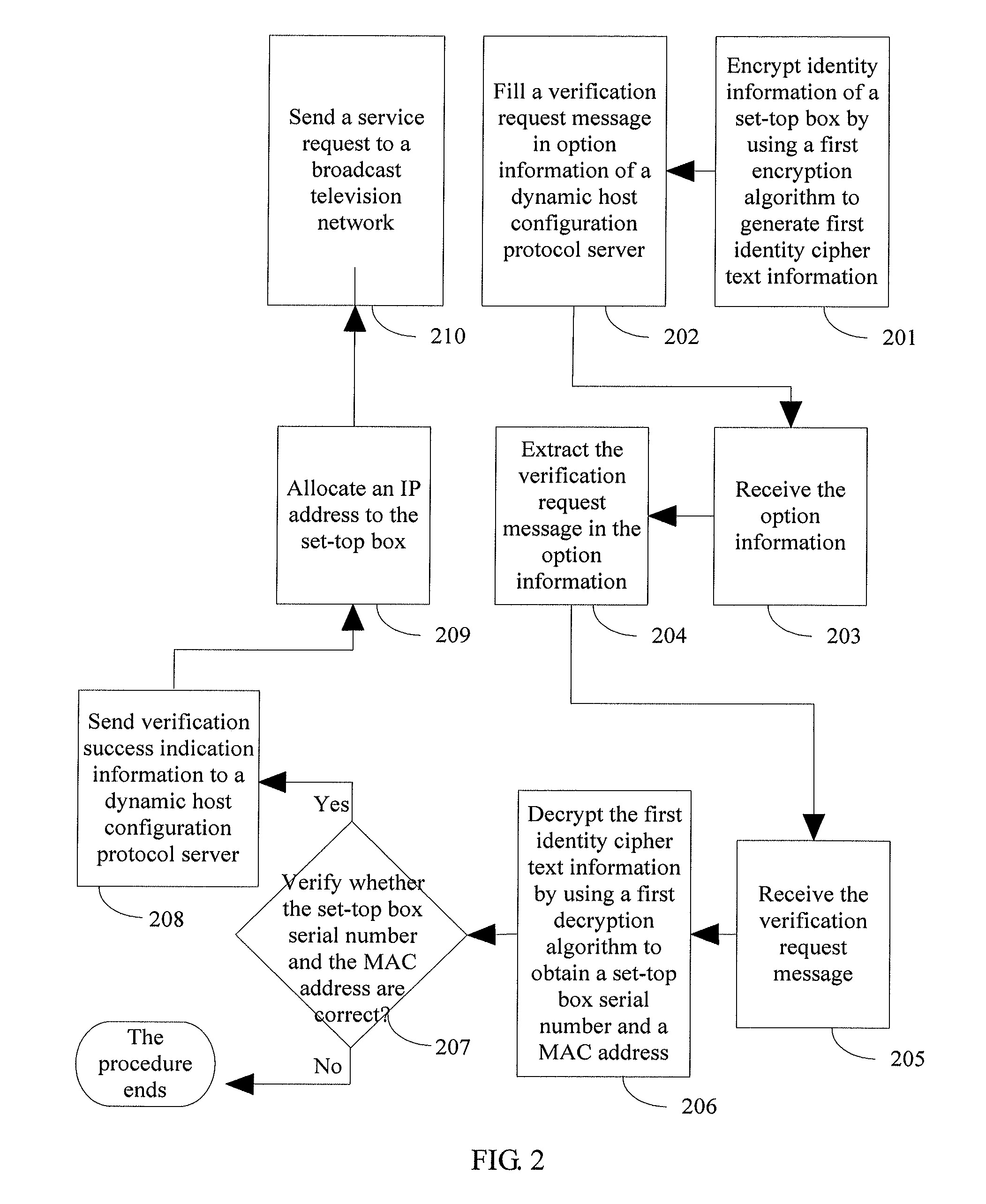
Method and authentication server for verifying access identity of set-top box
ActiveUS20130276019A1Improve access accuracyImprove access securityDigital data authenticationTelevision systemsEngineeringSet top box
Embodiments of the present invention disclose a method and an authentication server for verifying an access identity of a set-top box, and relate to the field of communication technologies The method of the present invention includes: receiving a verification request message sent by a set-top box, where the verification request message carries first identity cipher text information of the set-top box, software version information of the set-top box, and a user serial number, and the first identity cipher text information is generated by the set-top box according to identity information of the set-top box by using a first encryption algorithm; obtaining the identity information of the set-top box from the first identity cipher text information according to the user serial number by using a preset first decryption algorithm; and verifying the identity information of the set-top box according to the software version information.
Owner:HUAWEI DEVICE CO LTD
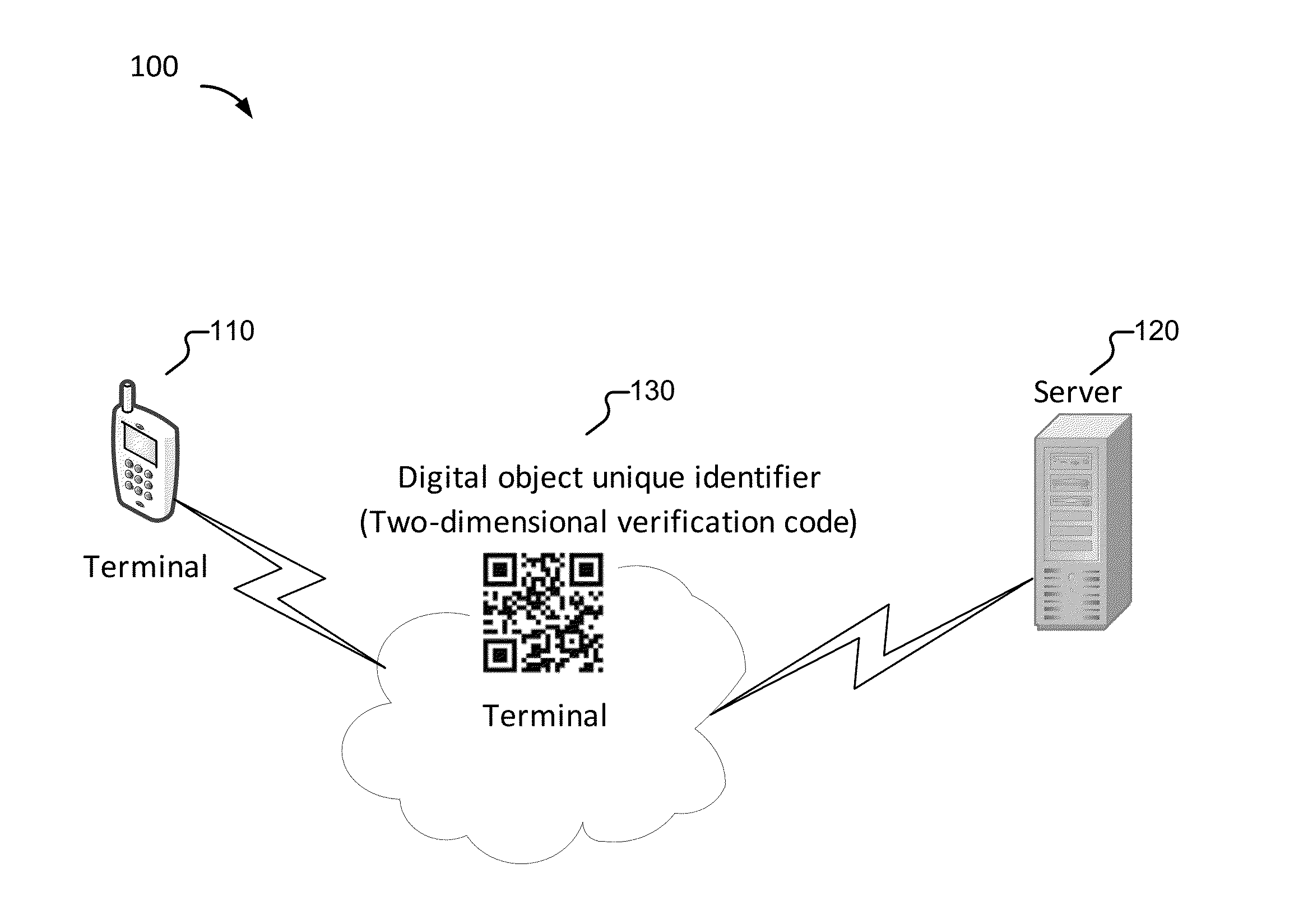
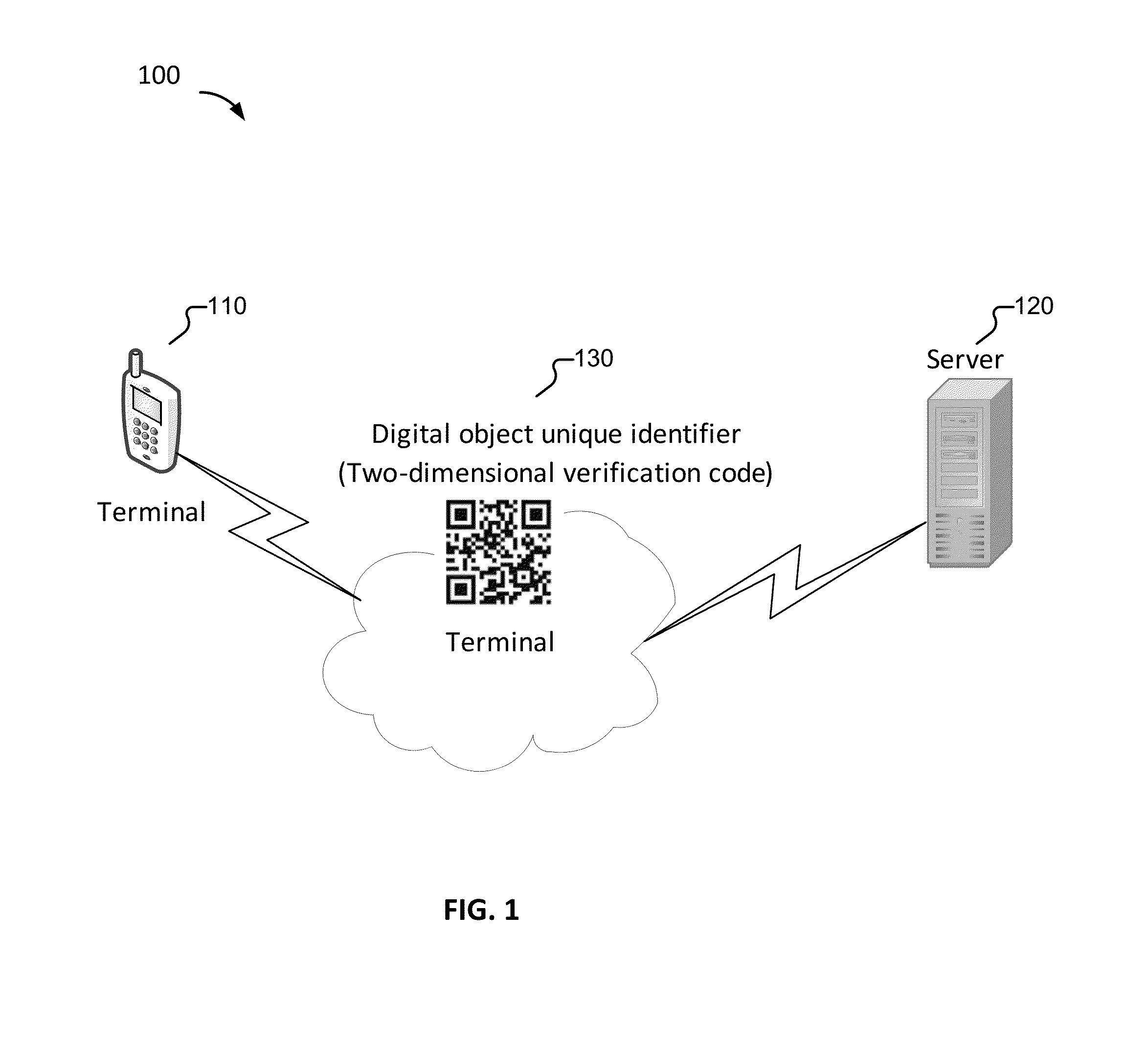
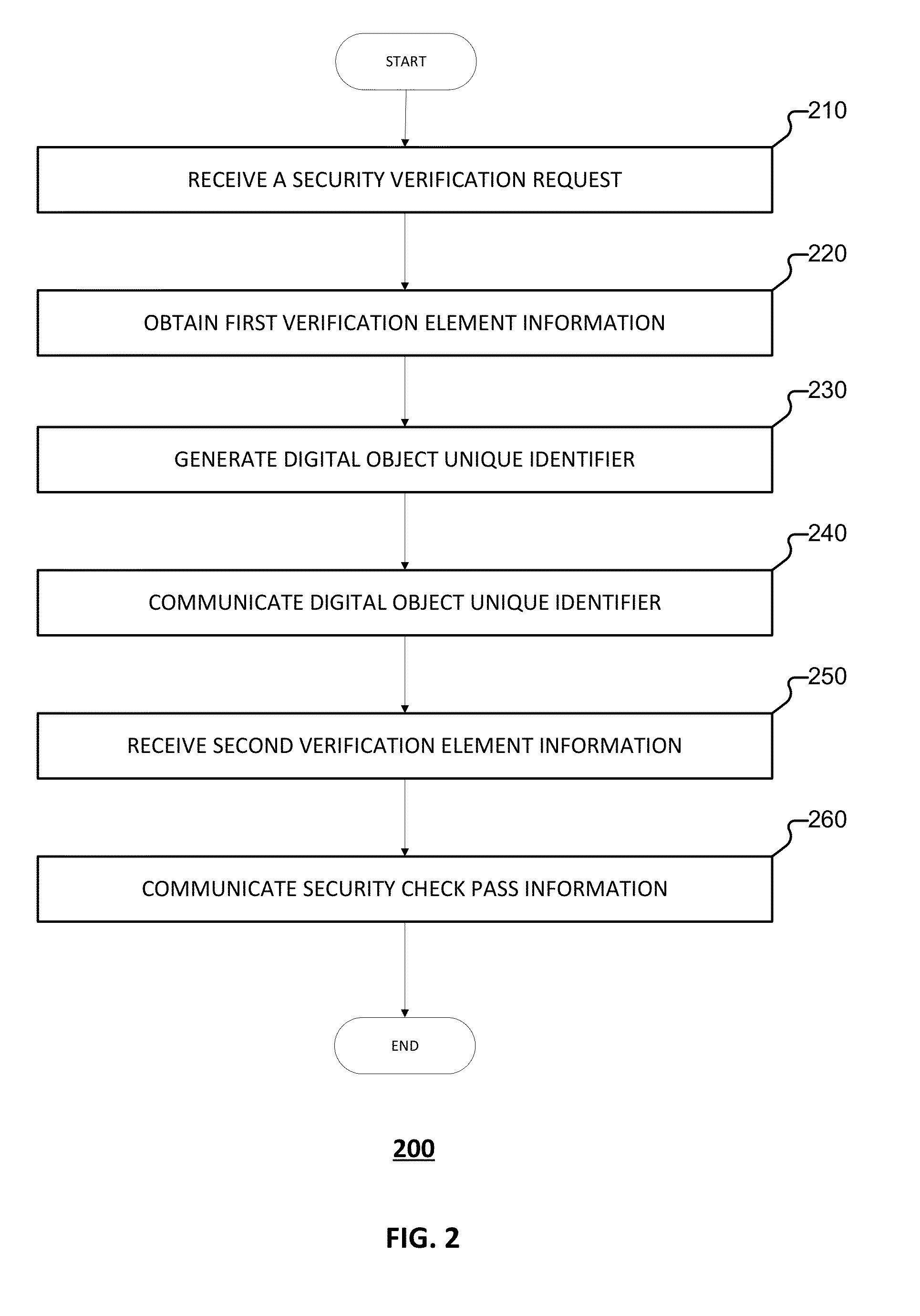
Method, apparatus, and system for providing a security check
ActiveUS20150341333A1Not easy to be stolenAvoid possibilityDigital data processing detailsUser identity/authority verificationUnique identifierSecurity check
Embodiments of the present application relate to a method, apparatus, and system for providing a security check. The method includes receiving a security verification request sent from a terminal, obtaining first verification element information based at least in part on the security verification request, generating a digital object unique identifier based at least in part on the first verification element information, sending the digital object unique identifier to the terminal, receiving second verification element information from the terminal, and in the event that the first verification element information and the second verification element information are consistent, sending security check pass information to the terminal.
Owner:ADVANCED NEW TECH CO LTD
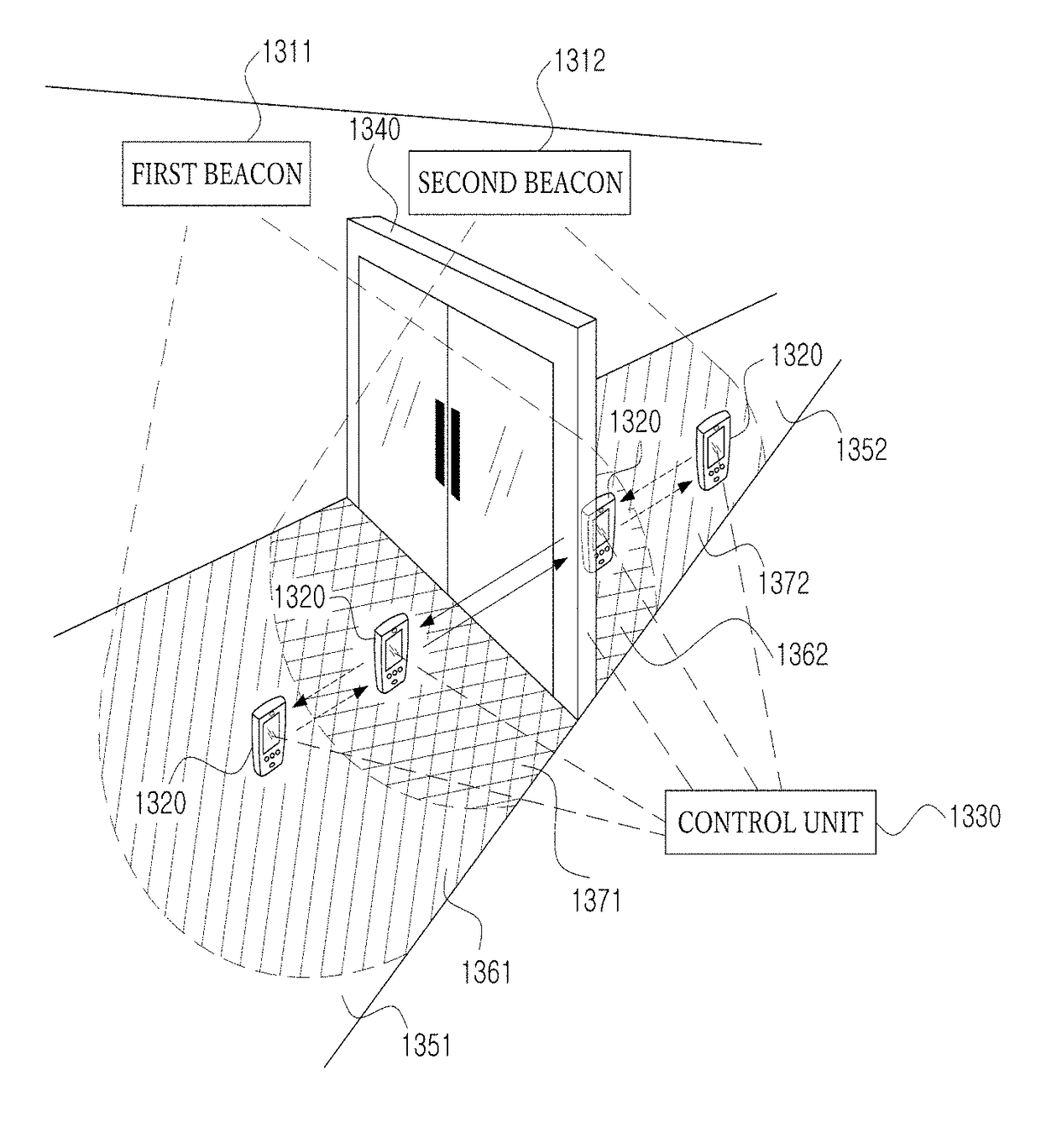
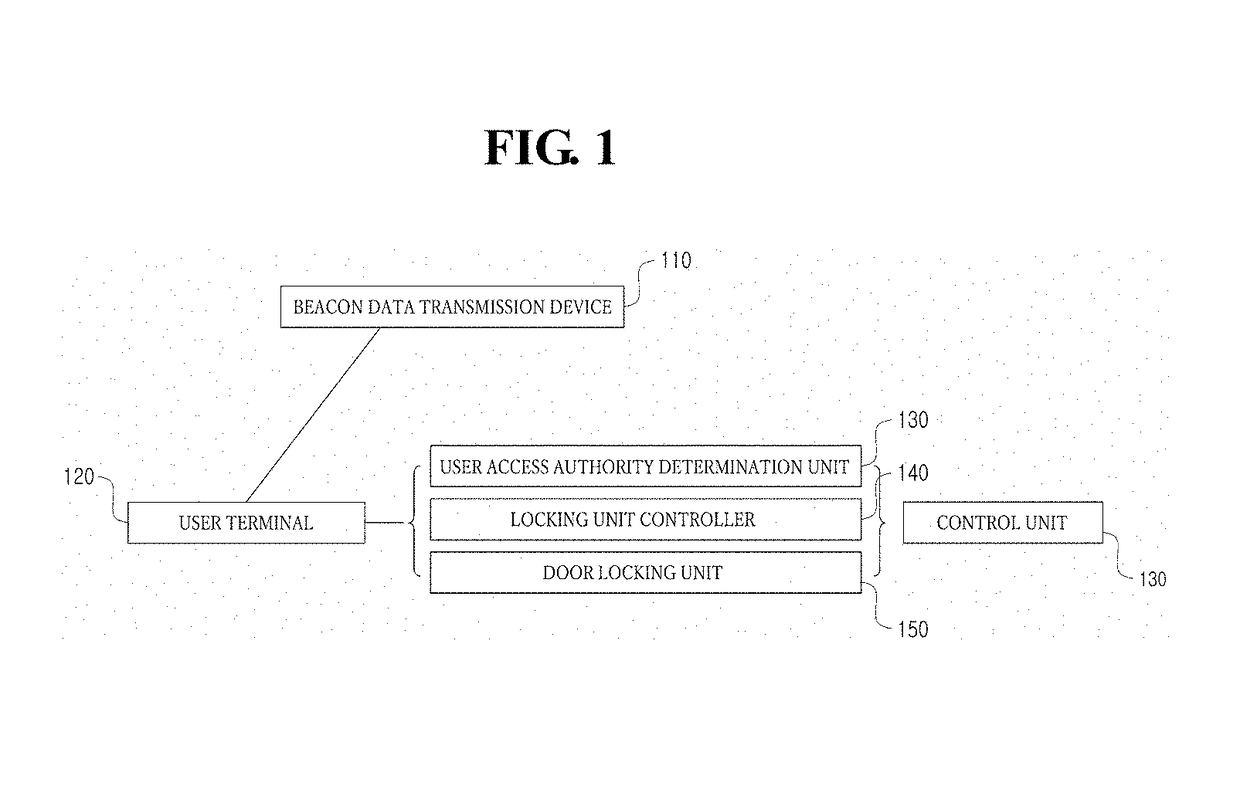
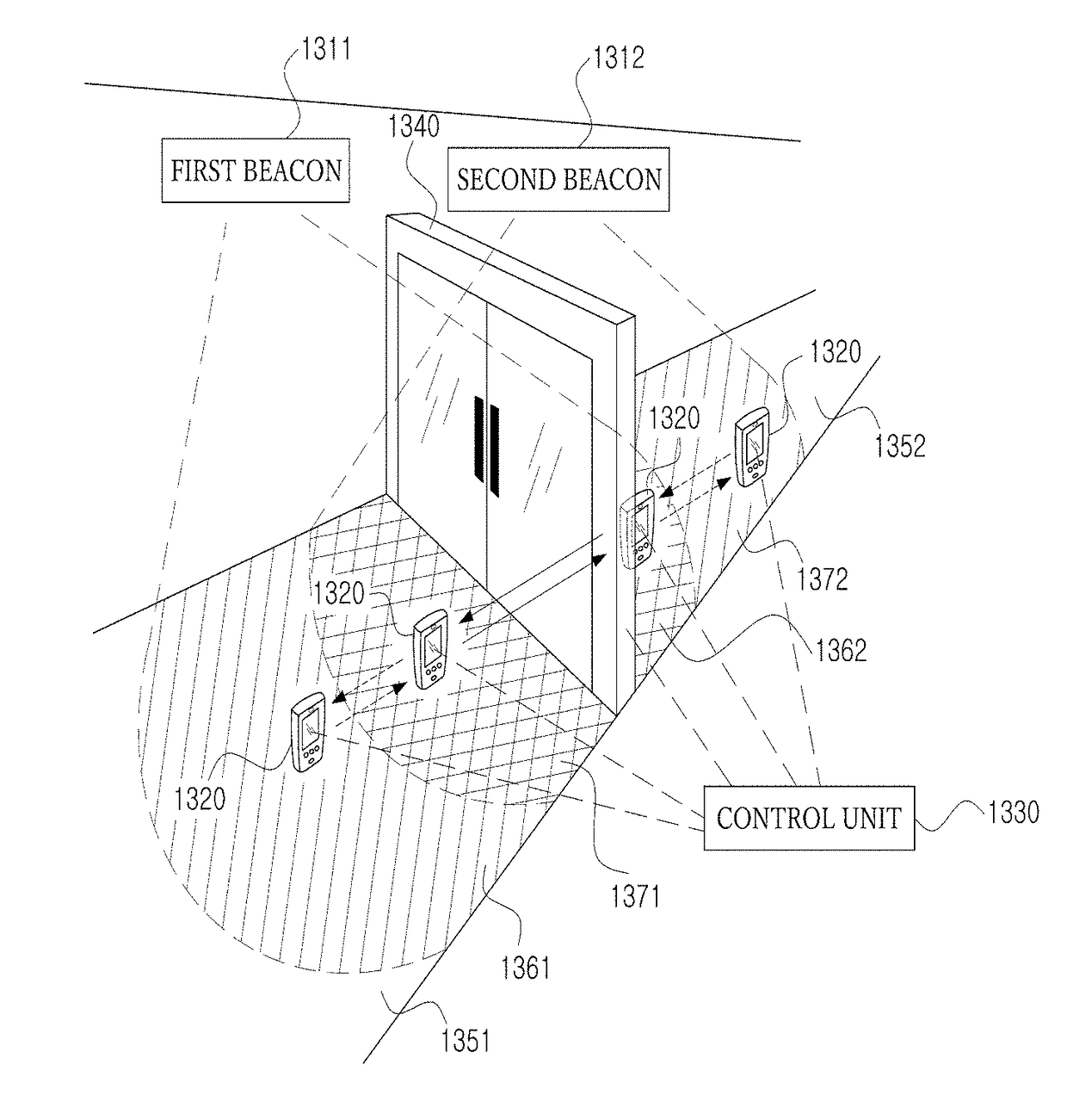
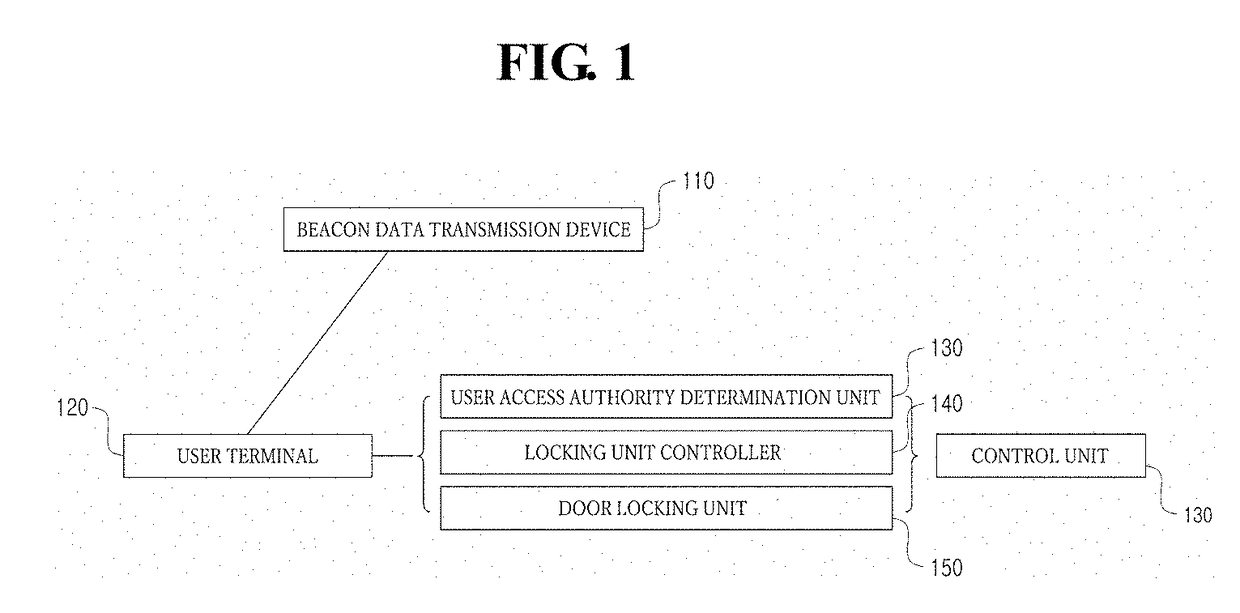
Method and system for managing door access using beacon signal
ActiveUS20180012432A1Improve access securityImprove user convenienceIndividual entry/exit registersComputer scienceAuthentication
A method and system allow management of access to a door using a beacon signal. A user access authority determination unit controls access of a user to a target door based beacon data from beacons installed near a door. The user carries a terminal that obtains the beacon data based on a proximity to the beacons. The method includes identifying the target door based on identification information of the beacons extracted from the beacon data. A type of user movement is determined. The type of user movement includes an entering movement that the user enters into an inner side from an outer side through the target door and an exiting movement that the user exits the inner side to the outer side through the target door. An access authentication process to be performed to unlock the target door is determined according to the determined type of user movement.
Owner:SUPREMA INC
Smart Internet of Things communication service system and smart Internet of Things communication service method
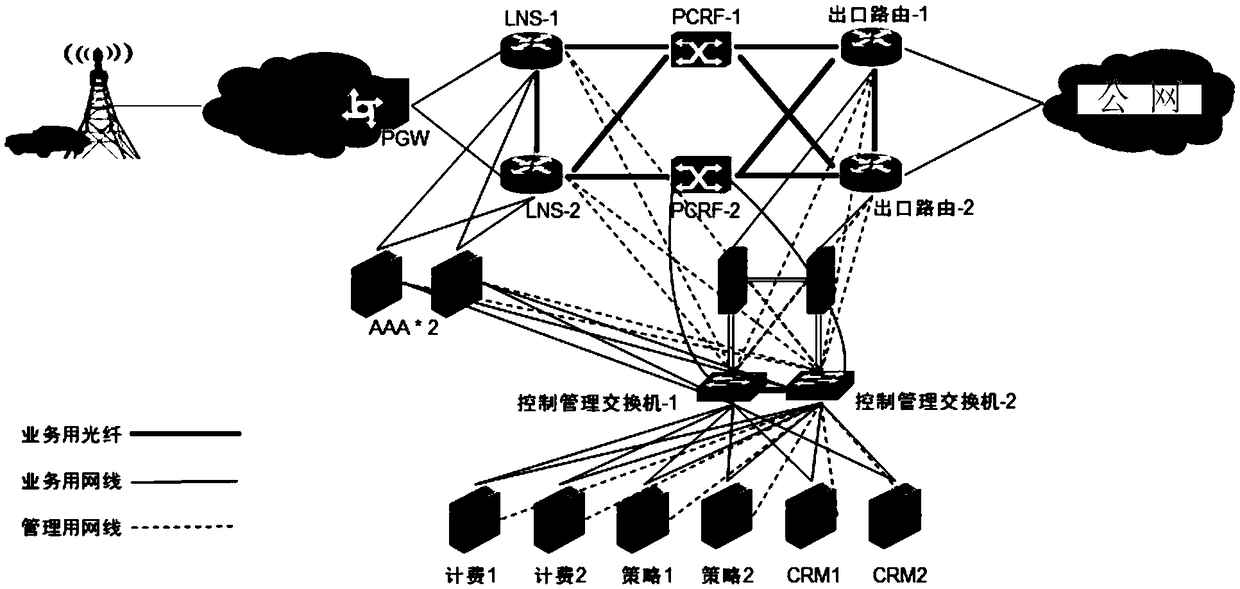
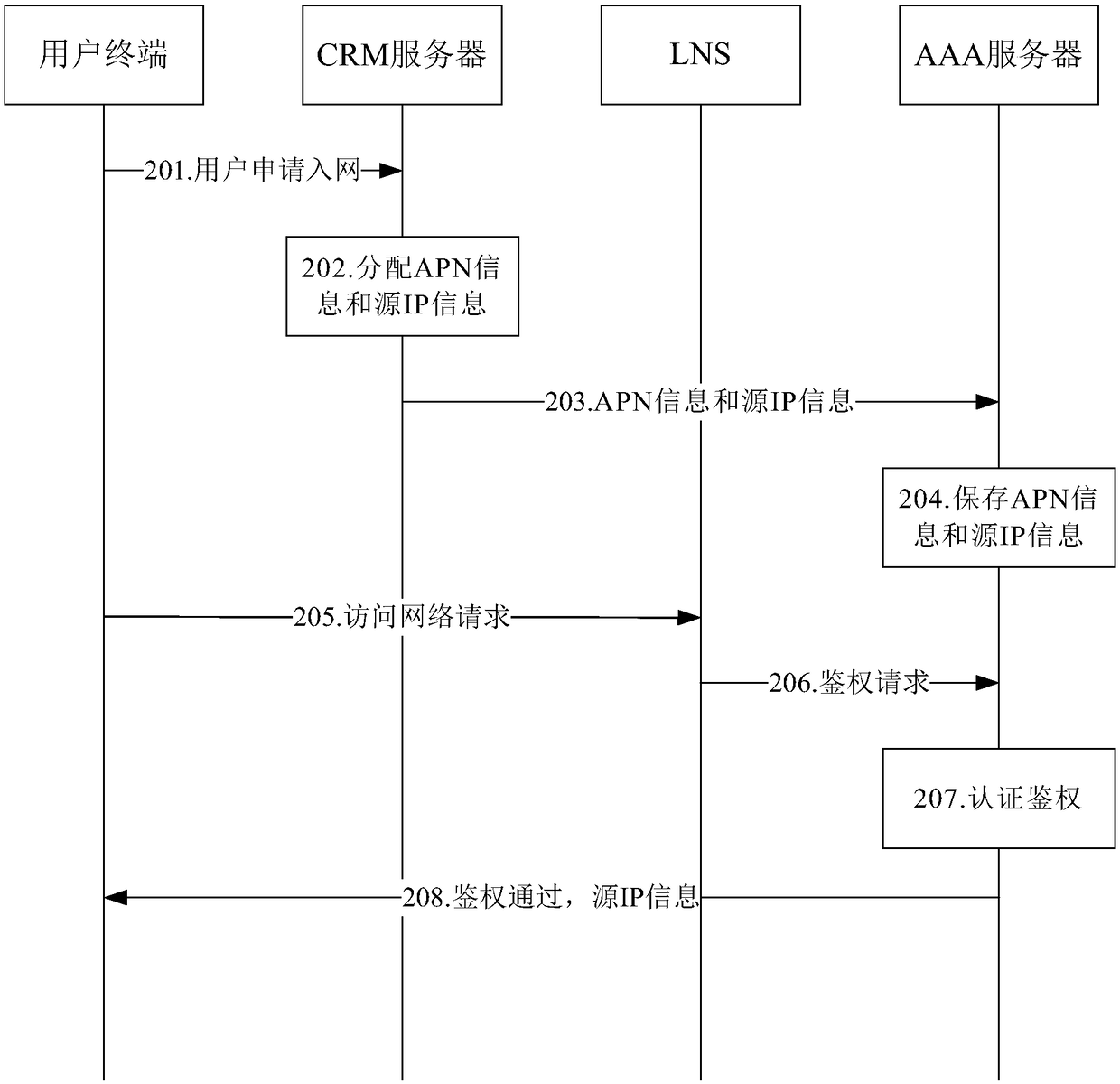
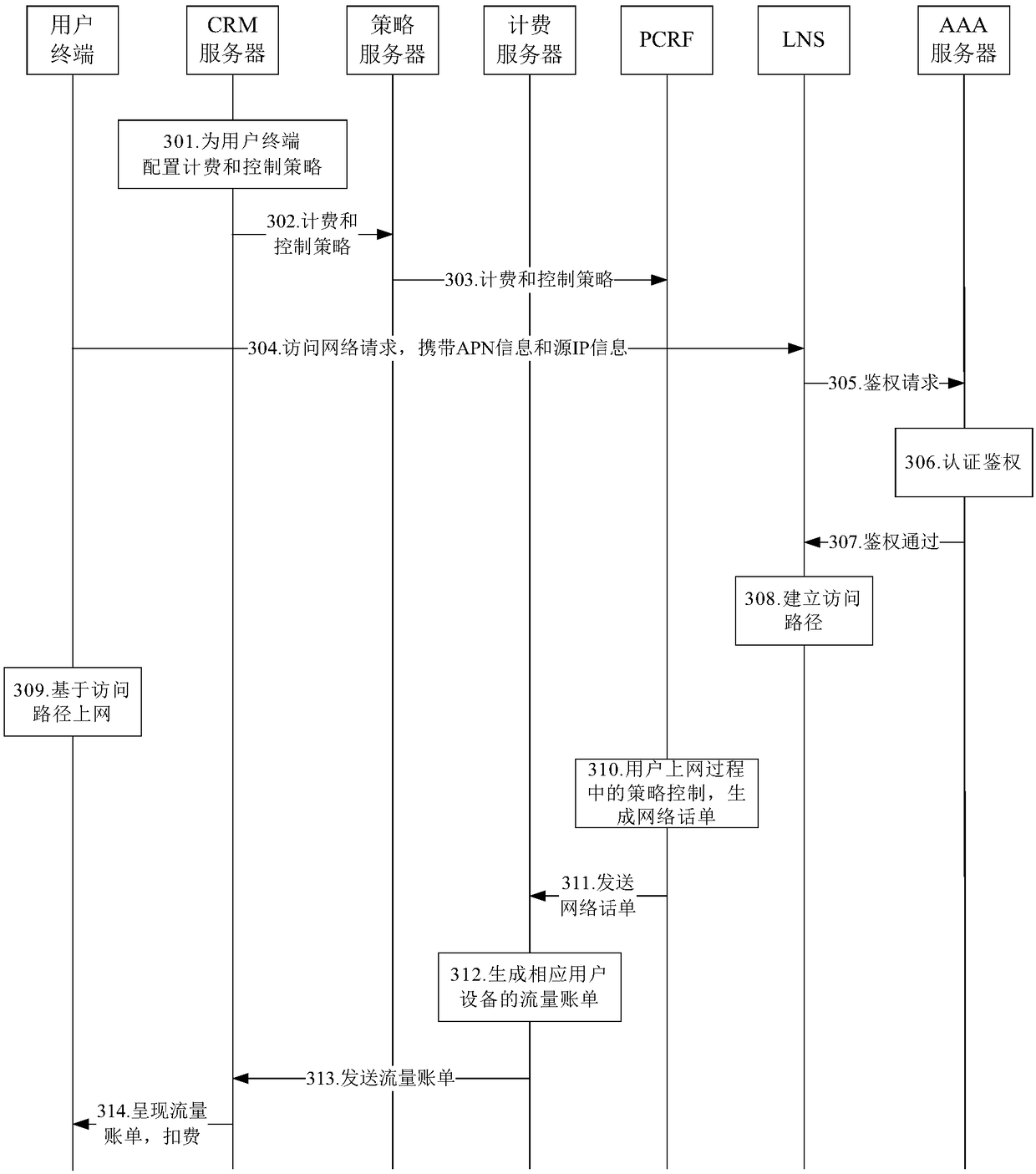
ActiveCN109450657AFull access authorizationFull securityMetering/charging/biilling arrangementsTraffic capacityCustomer relationship management
The invention discloses a smart Internet of Things communication service system and a smart Internet of Things communication service method. The system comprises: a forwarding layer device and a control layer device, wherein the forwarding layer device comprises: an LNS, a PCRF, and an egress routing device; the LNS accesses a PGW, and the LNS, the PCRF, and the egress routing device are connectedwith each other through a forwarding layer communication link; the control layer device comprises: an accounting server, a policy server, a CRM server, and a certification authentication server, which are in communication connection through the control layer link based on a control management switch; the policy server is in communication connection with the PCRF through the control layer link; the LNS establishes an L2TP VPN channel with the PGW; the CRM performs customer relationship management; the policy server synchronizes and controls the policy configuration of the PCRF; the PCRF records the network call bills of the user equipment based on the configured policy, and controls the network access behavior of the user equipment; the accounting server generates a corresponding traffic bill according to the network call bill recorded by the PCRF; and the certification authentication server performs certification authentication and log recording on the user equipment.
Owner:广东联想懂的通信有限公司
Processing method and device as well as acquisition method and device for security information
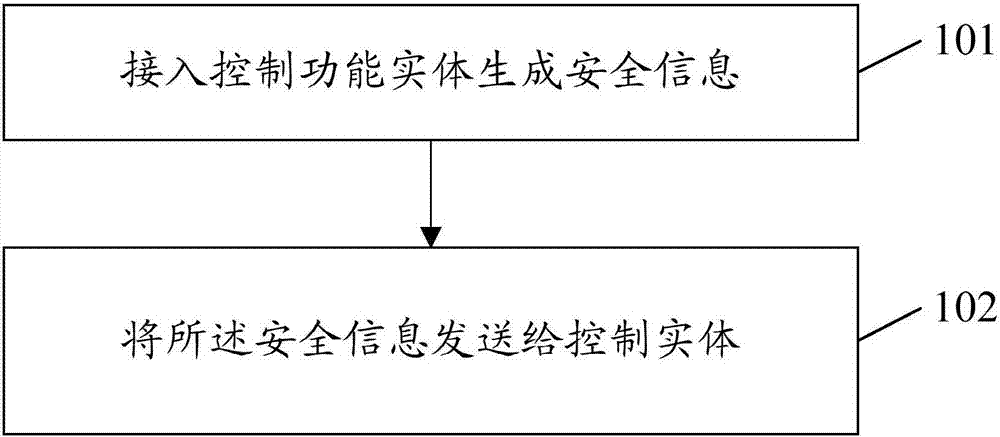
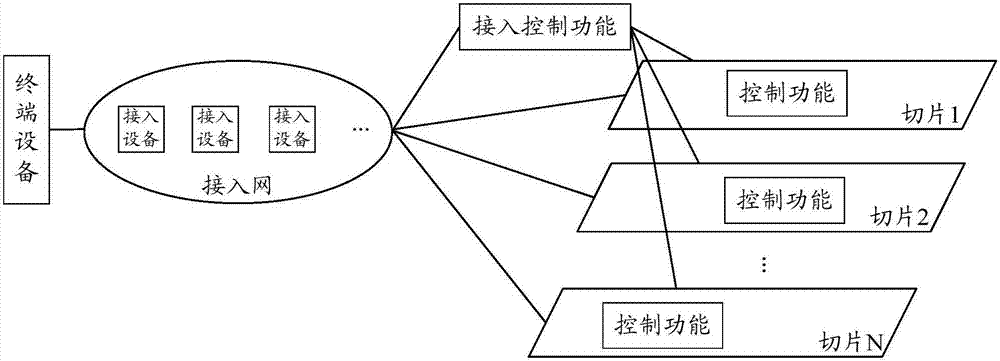
ActiveCN107094127AAchieve security isolationImprove access securityTransmissionSecurity arrangementControl functionSecurity information
The invention provides a processing method and device as well as acquisition method and device for security information. The processing method for the security information comprises the following steps: enabling an access control functional entity to generate security information; and sending the security information to a control entity. According to the embodiment of the invention, the access control functional entity authenticates and authorizes the terminal and is responsible for generating different security information for different network slices signed with the terminal, the network slices process high layer information sent by the terminal by using the generated security information to ensure that the terminal is accessed to the network slices, and thus the security isolation among the different network slices can be achieved, the access security can be improved, and the security isolation among the different network slices can be achieved.
Owner:DATANG MOBILE COMM EQUIP CO LTD
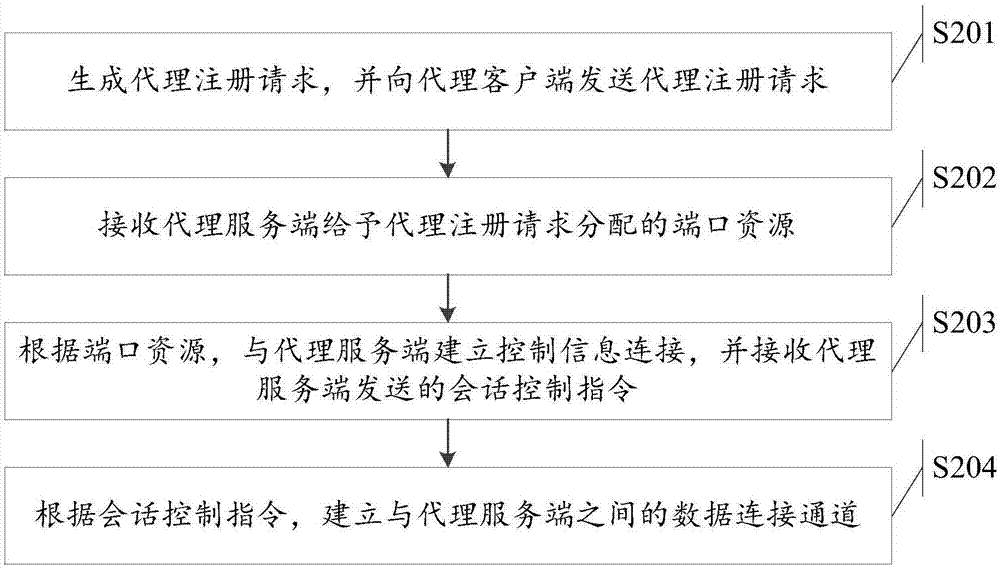
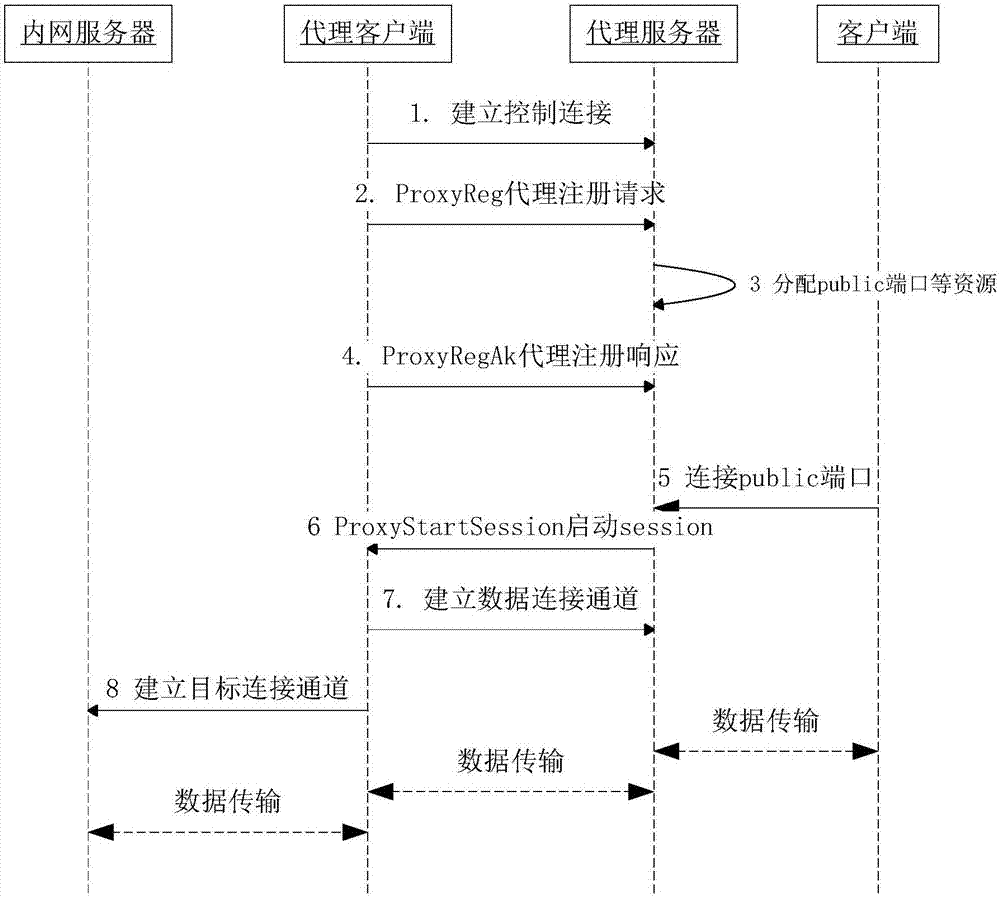
Access method, apparatus and system of data connection channel
ActiveCN107426339AImprove access securityGuaranteed not to be interceptedKey distribution for secure communicationUser identity/authority verificationData connectionAccess method
The invention discloses an access method, apparatus and system of a data connection channel. The method comprises the following steps: generating a proxy registration request, and sending the proxy registration request to a proxy server; receiving a port resource allocated by the proxy server based on the proxy registration request; according to the port resource, establishing control information connection with the proxy server, and receiving a session control instruction sent by the proxy server; and establishing the data connection channel with the proxy server according to the session control instruction. Through the method, in the connection process of the data connection channel between a proxy client and the proxy server, a unique session ID and a random number value are added to the session control instruction, verification is performed through the session ID and the random number value, and after the proxy server is successfully verified, the data connection channel is established between the proxy client and the proxy server, such that the access security of the data connection channel between the proxy client and the proxy server is improved.
Owner:ZHUHAI MAIYUE INFORMATION TECH
Access control system for automation equipment
ActiveUS7502323B2Easy to configureEasy maintenanceError preventionFrequency-division multiplex detailsMedia access controlBusiness function
System for controlling access to automation equipments connected to a first network, from at least one client station connected to a second network. The system includes determination means of a functional profile containing a list of business functions that a user of the client station is authorized to carry out on the equipment, analysing means of a frame sent on the second network by the user, in order to determine a request and a destination equipment, definition means of a filter profile for the destination equipment, containing, for each business function and for each protocol, a list of requests that the destination equipment is capable of receiving, and filter means capable of authorizing or prohibiting transmission of the sent frame on the first network, according to the frame, the functional profile of the identified user and the filter profile of the destination equipment.
Owner:SCHNEIDER ELECTRIC IND SAS
Configuration method and configuration system of virtual machine and SDN controller
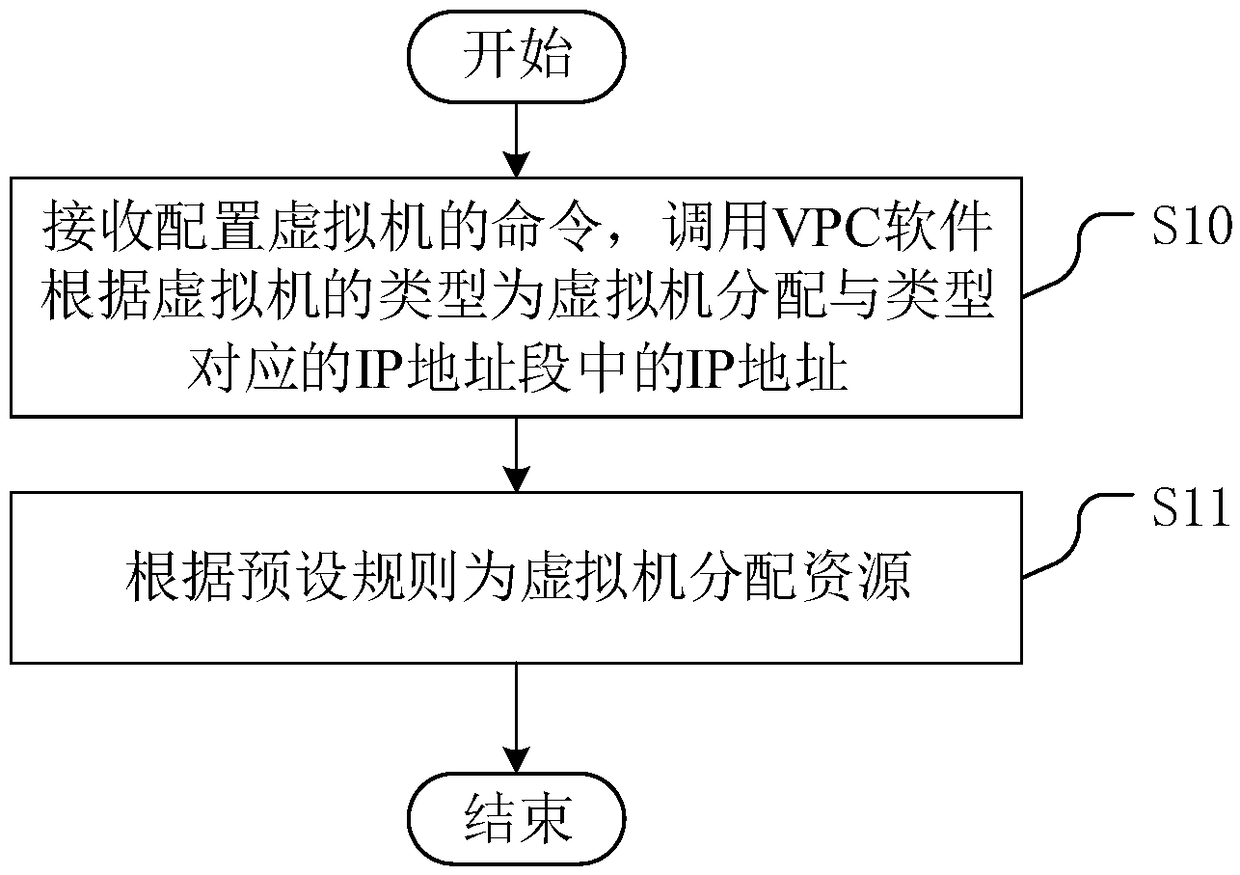
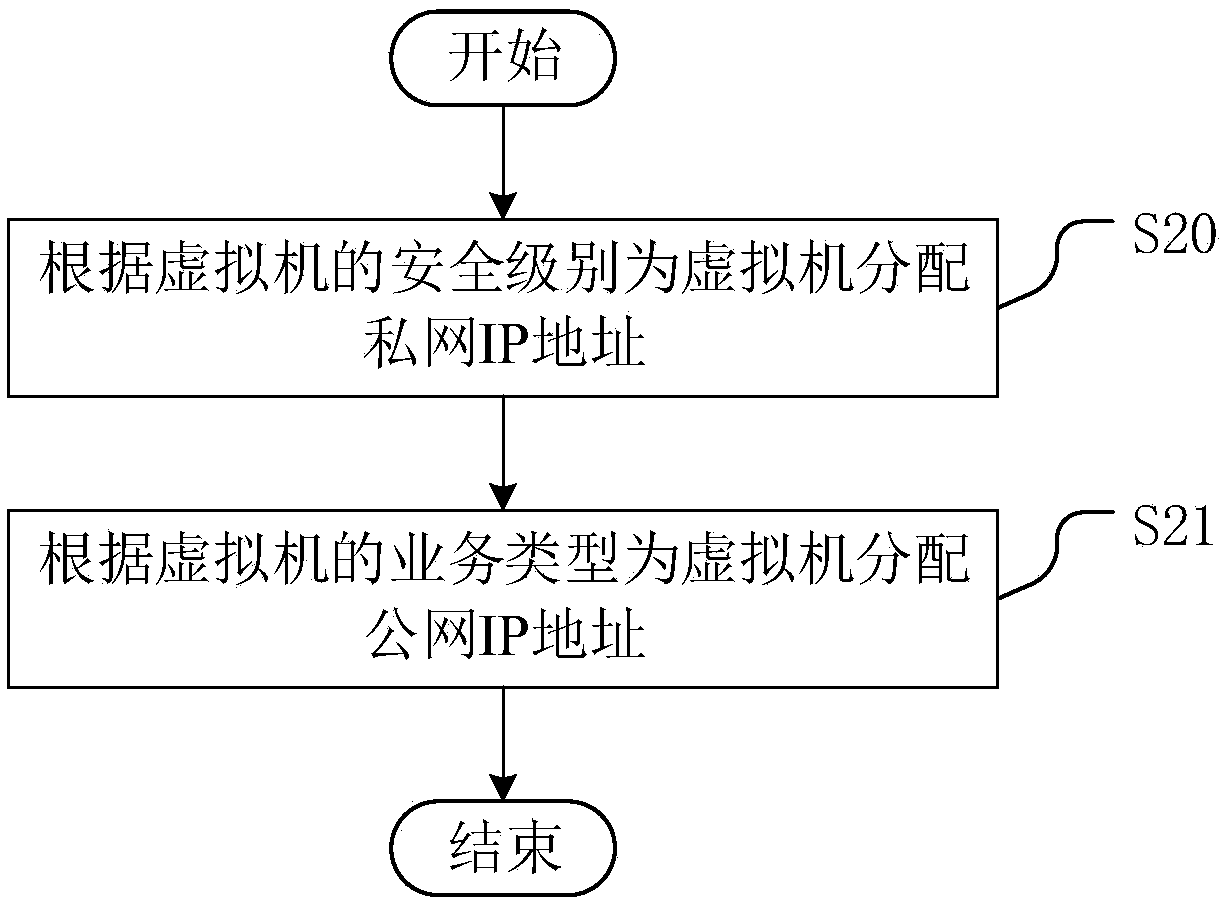
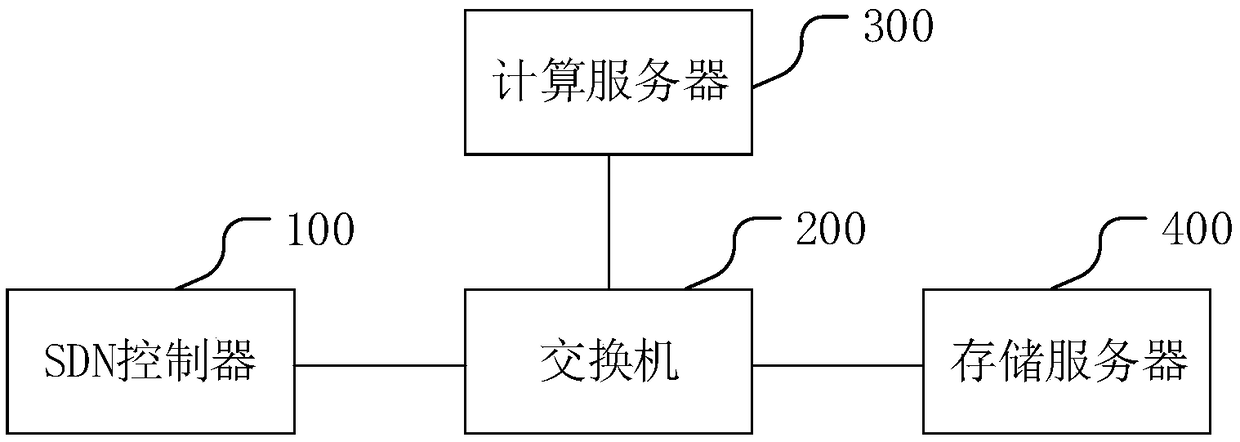
InactiveCN109445912ARealize self-configurationAchieve security isolationNetworks interconnectionSoftware simulation/interpretation/emulationDisk controllerVideo transmission
The invention discloses a configuration method of a virtual machine. A mobile video transmission system is improved by an SDN technology, so that a controller and a switch are separated, and an algorithm is compiled and realized based on an SDN controller. The method comprises the following steps of receiving a command for configuring a virtual machine; and then calling VPC software, allocating anIP address in the IP address field corresponding to the type to the virtual machine according to the type of the virtual machine, wherein the IP address fields corresponding to the types are not overlapped; and allocating the resources to the virtual machines according to the preset rules, so that the virtual machines with different services or different security levels are allocated in differentIP address fields, the autonomous configuration of the virtual machines is realized, the security isolation among the virtual machines is realized, and the access security among the virtual machinesis improved. The invention also discloses a virtual machine configuration system and an SDN controller, which have the above beneficial effects.
Owner:国网新疆电力有限公司信息通信公司 +1
Intelligent balance payment box system and working method thereof
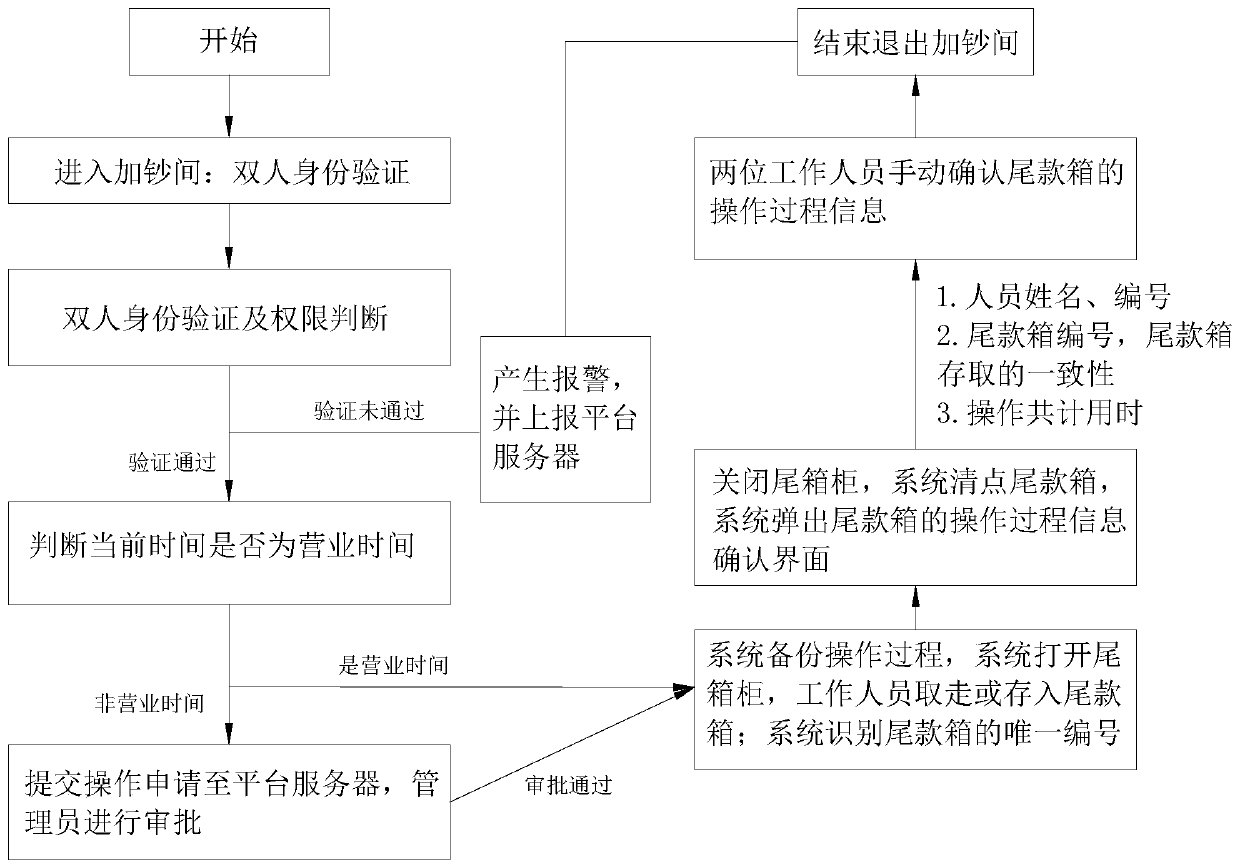
InactiveCN110223431AImprove access securityUse process standardizationIndividual entry/exit registersPaymentWorking set
The invention belongs to the technical field of intelligent storage, and discloses an intelligent balance payment box system and a working method thereof. The system comprises an identity verificationmodule, a permission management module, a time judgment module, a communication module, a balance payment box detection module and a balance payment box control module, wherein the identity verification module is used for obtaining the identity information of a user, and verifying the identity of the user; the permission management module is used for judging the operation permission of the user;the time judgment module is used for judging whether current time is business hours or not; the communication module is used for communicating with a platform server; the balance payment box detectionmodule is used for detecting the in-place state of the balance payment box; and the balance payment box control module is used for controlling the box door of the balance payment box to be opened andclosed and is independently connected with the identity verification module, the permission management module, the time judgment module, the communication module and the balance payment box detectionmodule. The system has a high balance payment box safety management mechanism, and situations that employees embezzle and exchange the balance payment box and the like can be avoided.
Owner:浙江北泰智能科技股份有限公司
Micro-service access proxy method and device thereof and storage medium
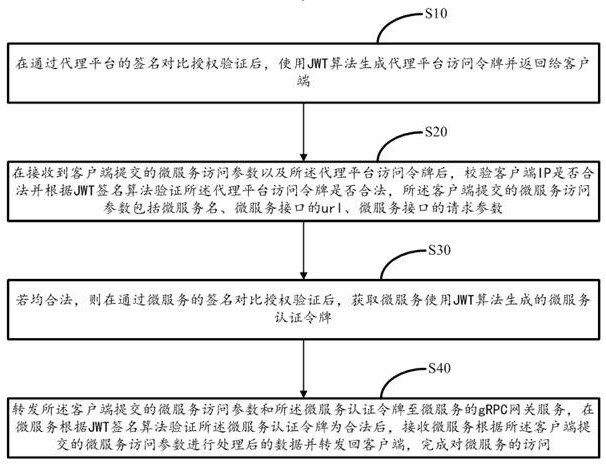
ActiveCN113676336AReduce learning costsImprove test efficiencyUser identity/authority verificationEngineeringAccess token
The invention discloses a micro-service access proxy method and a storage medium and a device thereof, and the method comprises the steps: generating a proxy platform access token after the signature verification of a proxy platform is passed, and returning the proxy platform access token to a client; after micro-service access parameters and a proxy platform access token submitted by the client are received, verifying whether the client IP and the proxy platform access token are legal or not, wherein the micro-service access parameters submitted by the client comprise a micro-service name, a url of a micro-service interface and a request parameter of the micro-service interface; if yes, obtaining a micro-service authentication token after the signature verification of the micro-service is passed; and forwarding the micro-service access parameter and the micro-service authentication token submitted by the client to the gRPC gateway service of the micro-service, after the micro-service authentication token is verified to be legal, receiving data processed by the micro-service according to the micro-service access parameter submitted by the client, and forwarding the data back to the client to complete access to the micro-service. Therefore, the safety is higher, and the test efficiency is higher.
Owner:深圳市明源云采购科技有限公司
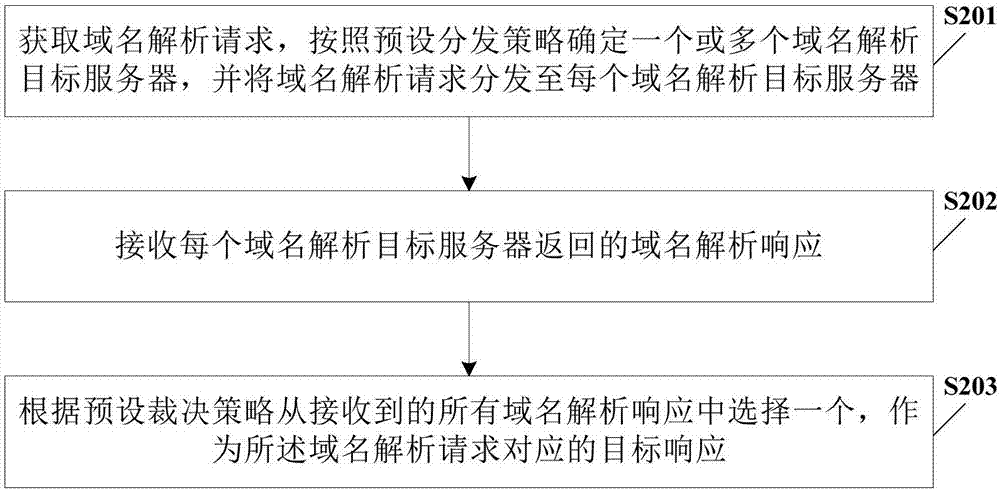
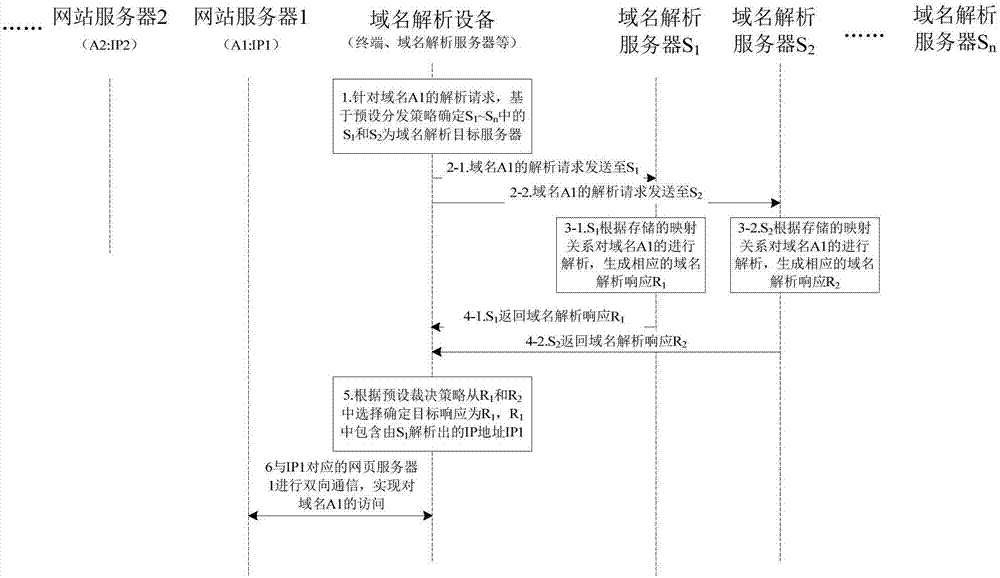
Domain name analysis method and device
The embodiment of the invention discloses a domain name analysis method and device. The domain name analysis method comprises the steps of: selecting one or more domain name analysis servers from multiple domain name analysis servers, taking one or more domain name analysis servers as target domain name analysis servers, respectively distributing the same domain name analysis request to each target domain name analysis server, analyzing the same domain name to be analyzed through the target domain name analysis servers, so that multiple domain name analysis responses are obtained, selecting one domain name analysis response from the multiple domain name analysis responses, and taking the domain name analysis response as the target response. Compared with the condition that domain name analysis is carried out by fixed adoption of a domain name analysis server for a long time in the prior art, the embodiment of the invention can avoid the condition that a large number of domain names are wrongly analyzed when a certain domain name analysis server has a security problem, increase the accuracy rate of the domain name analysis result, and improve the access security.
Owner:SHANGHAI HONGZHEN INFORMATION SCI & TECH CO LTD +1
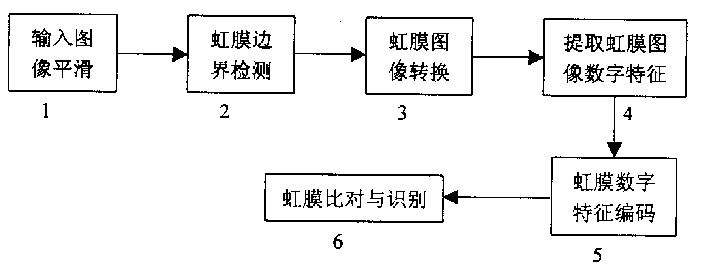
Iris recognizing method
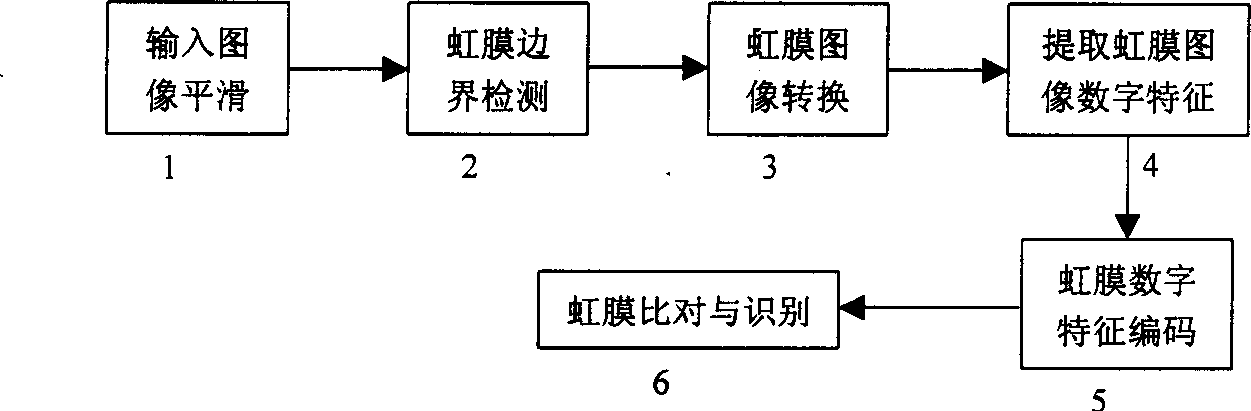
InactiveCN1092372CImprove access securityEye surgeryCharacter and pattern recognitionIris codeFeature coding
The present invention is a method of determining the position of the iris of the eyeball in the digital image obtained from the visible part of the user's eyeball, so as to establish a digital image file that fully expresses the texture information of the iris, and the digital image The file is processed to extract the digital texture features of the iris and perform feature encoding, i.e. the iris code, and compare the iris code with the iris codes of the iris of the same eyeball and / or other eyeballs stored in the database to compare the iris code of the iris The iris recognition method for user authentication is described. The method consists of iris image smoothing, iris boundary detection, iris image transformation, iris texture feature extraction, iris feature encoding and recognition methods. The invention can be used in public security systems, can be used on magnetic cards to replace personal identity codes, and can also be used in information systems to improve access security and the like.
Owner:KAIPINGAISEN IT TECH BEIJING
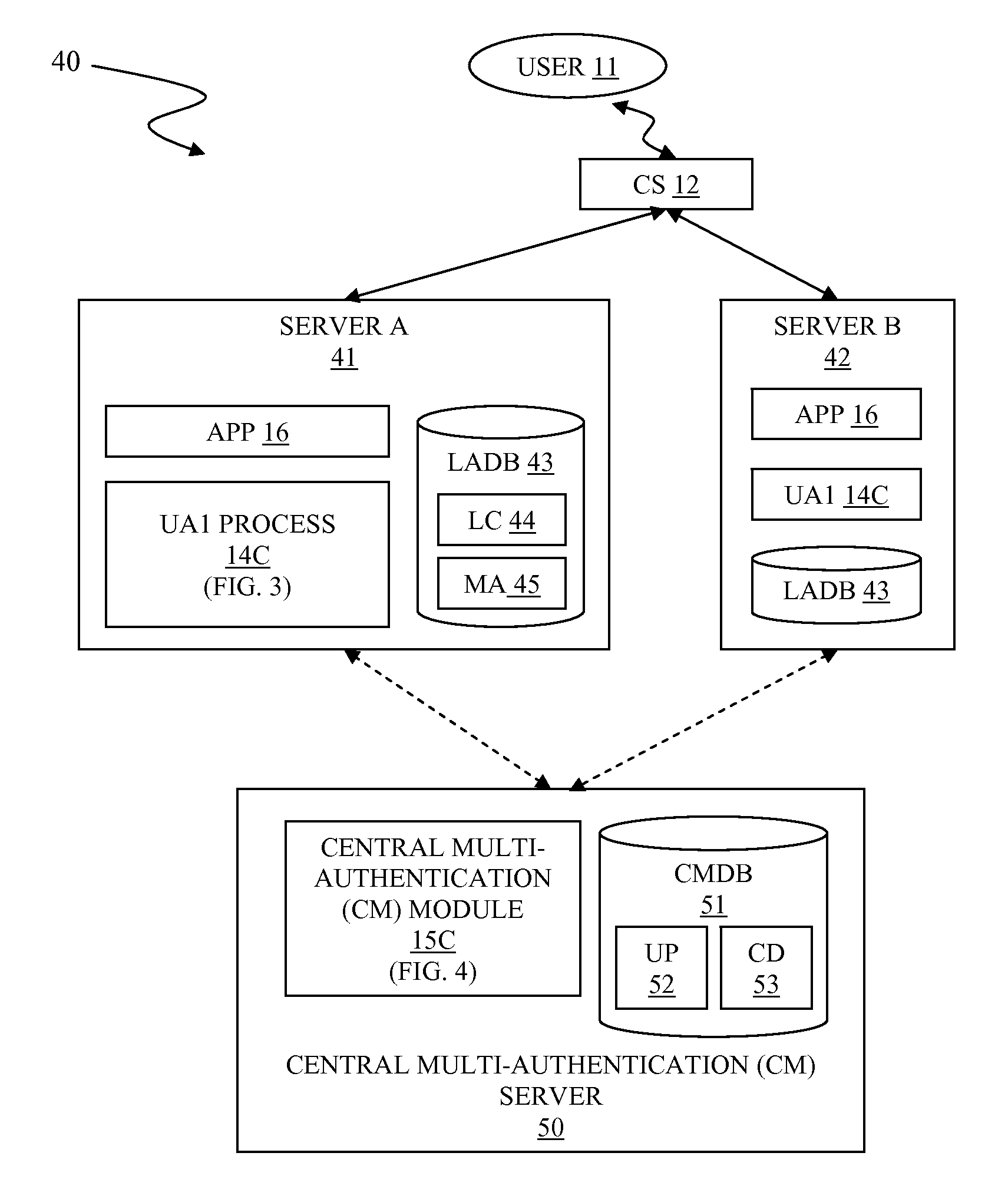
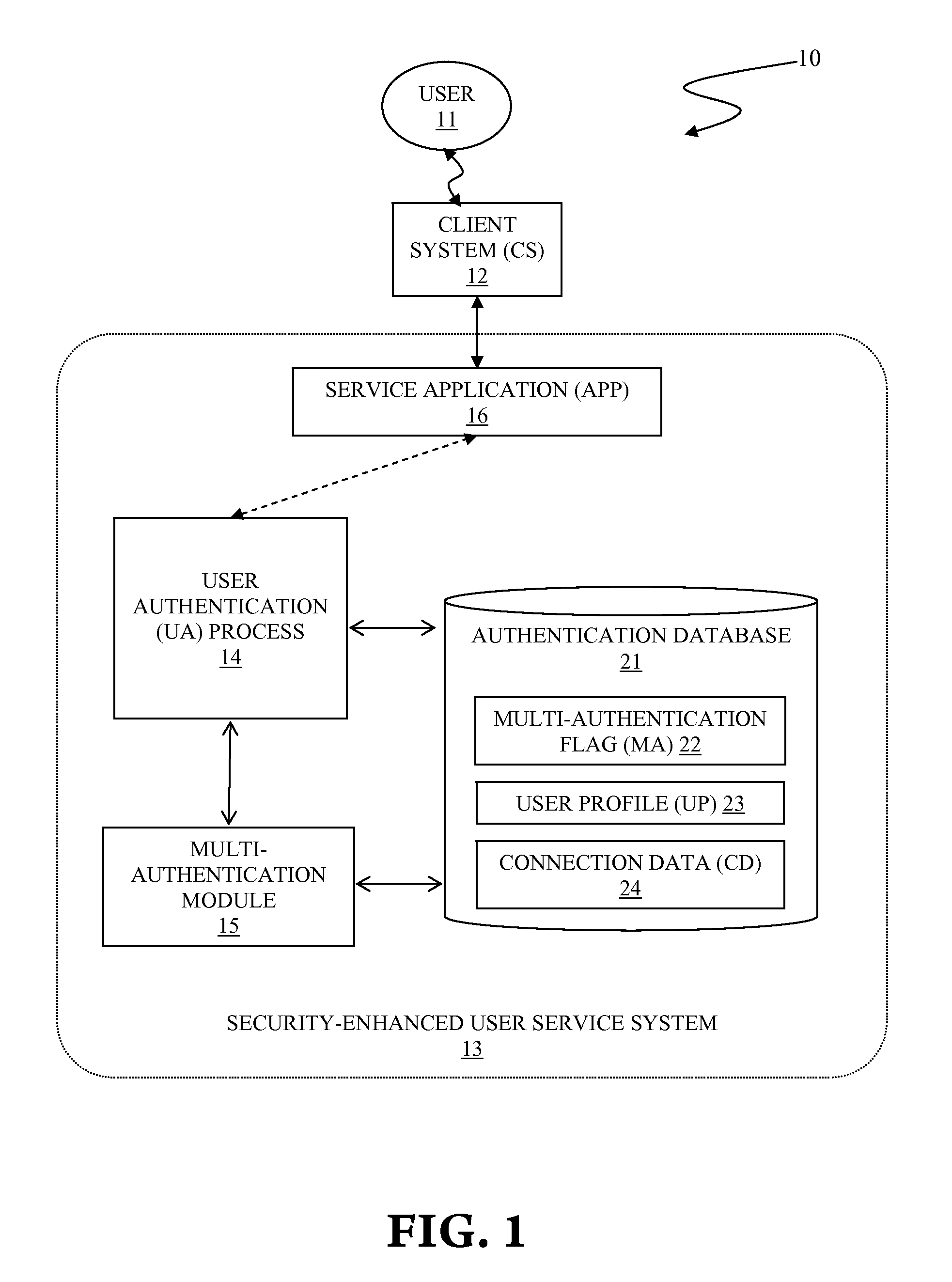
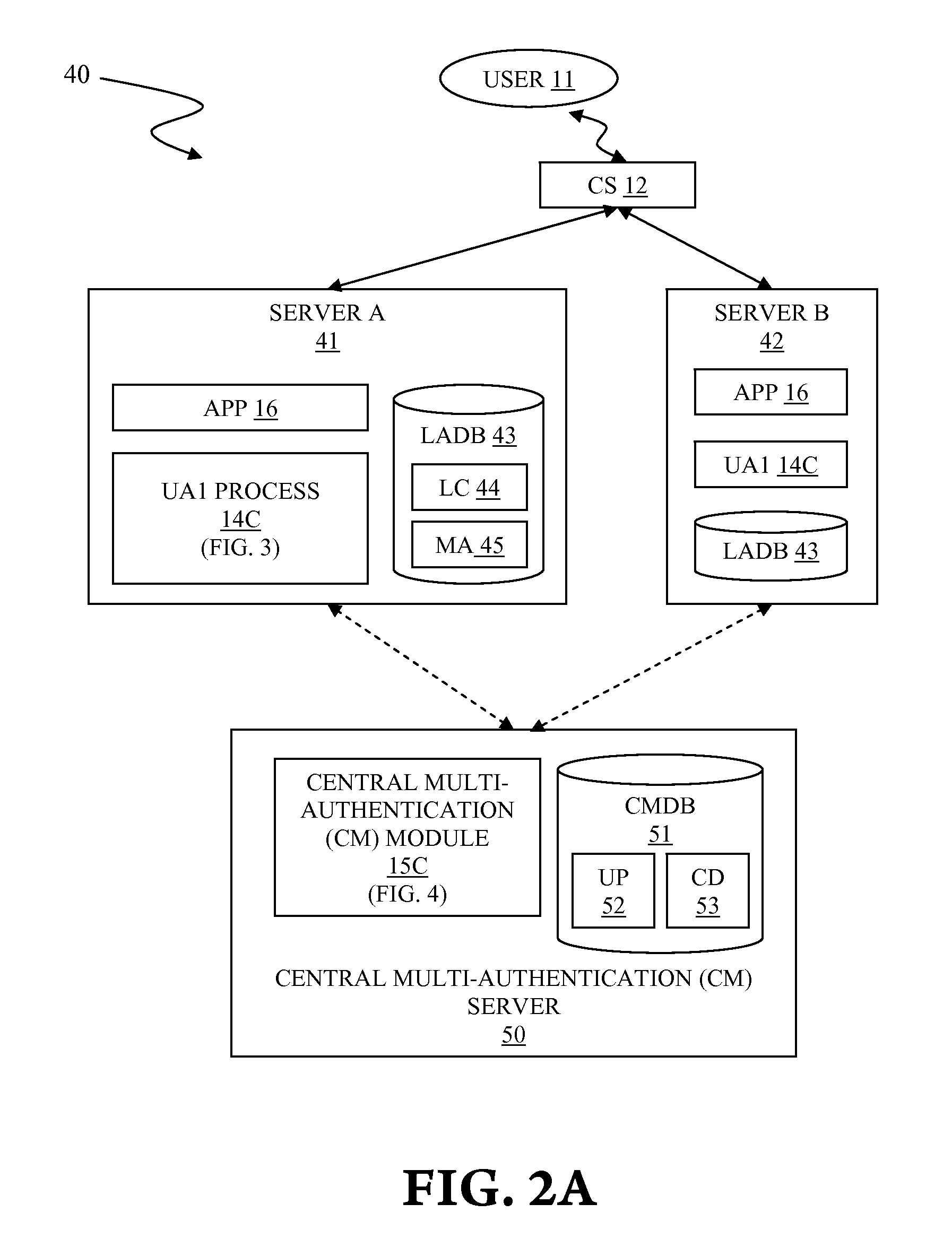
Multiple independent authentications for enhanced security
InactiveUS20120278870A1Improve access securityDigital data processing detailsUser identity/authority verificationClient-sideUser authentication
A system and associated method for providing enhanced site access security by use of multiple authentications from independent sources. A security enhanced user service system has components of a user authentication process, a service application, a multi-authentication module and an authentication database. A user attempting to use the service application accesses through a client system that is coupled to the security enhanced user service system. The user authentication process receives login information from the user, checks for validity, and sends to the multi-authentication module to further verify the login information. The multi-authentication module generates a grant or denial by use of predefined logical condition to satisfy for the grant response, data stored in the authentication database, another security enhanced user service system etc., pursuant to a specific configuration.
Owner:IBM CORP
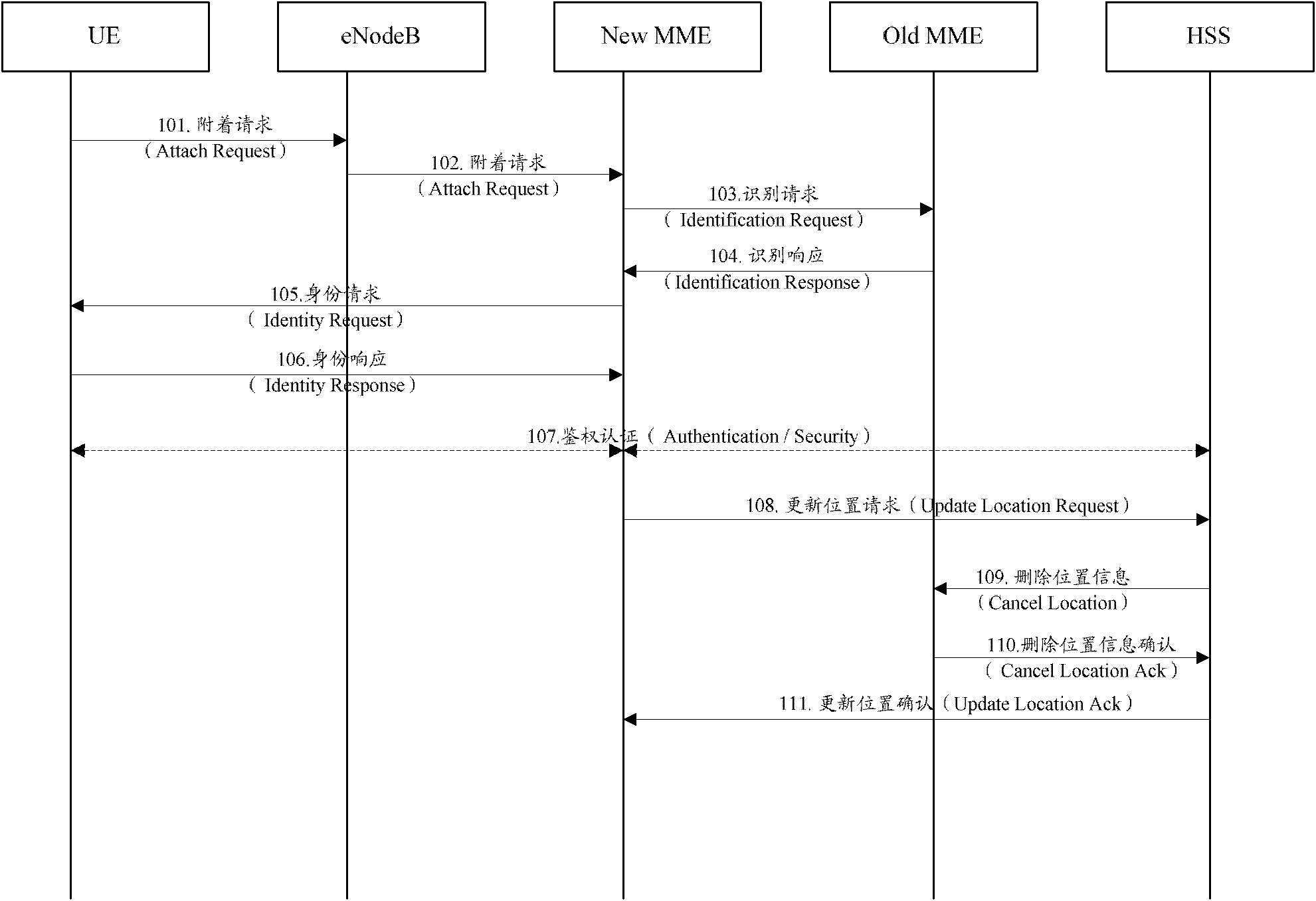
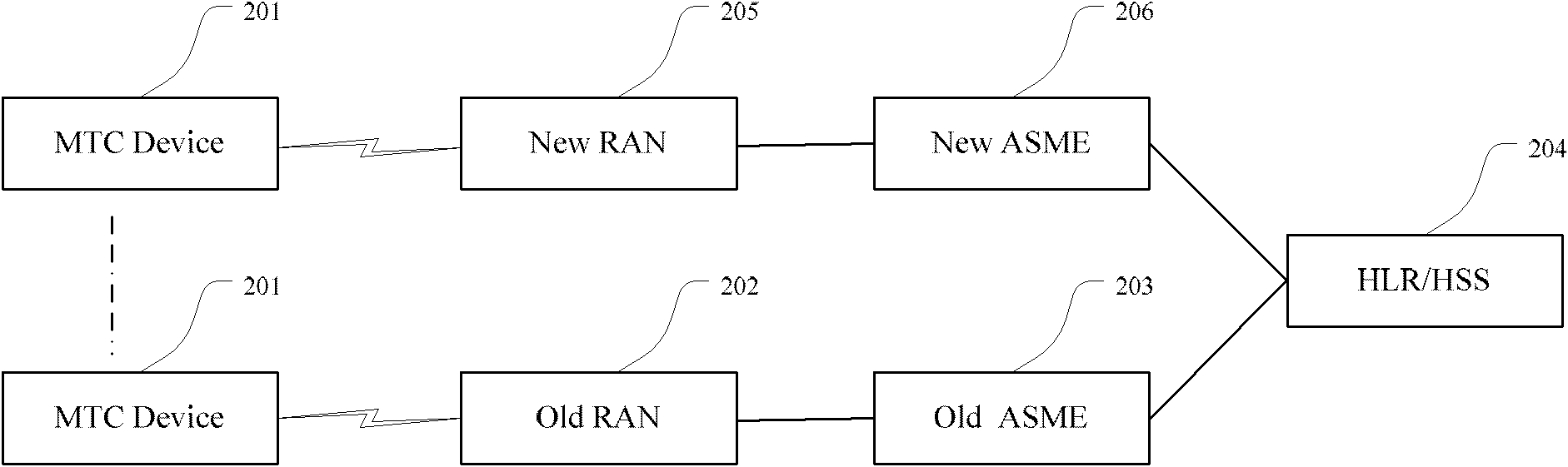
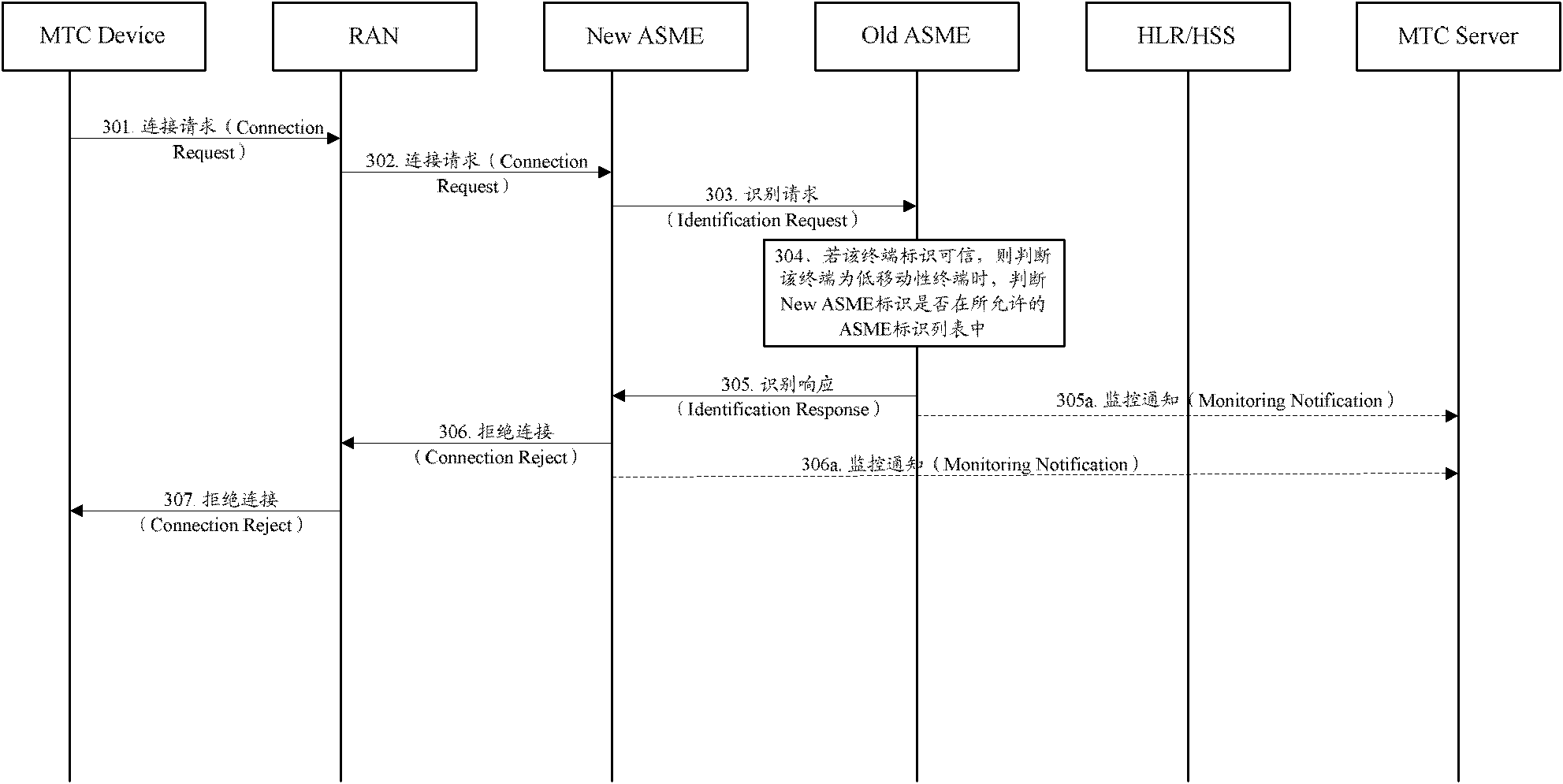
Method for monitoring position change of low mobility terminal and system thereof
InactiveCN102724649AImprove access securityReduce signaling loadNetwork data managementReal-time computingSecurity management
The invention discloses a method for monitoring the position change of a low mobility terminal. Position restriction information of the terminal is configured in a HSS / HLR as signed data and is downloaded to access security management equipment (ASME) in a process of inserting the signed data. The method also comprises that: in an Attach / RAU / TAU process, when ASME which the terminal accesses before checks that ASME which the terminal asks to access at present is not in the position restriction information, the Attach / RAU / TAU process is rejected, and alarm information is sent to an MTC server. The invention discloses a system for monitoring the position change of the low mobility terminal. According to the method and the system, access security of a low mobility MTC terminal and a network is raised, and a possibly generated signaling load in an invalid movement of this type of low mobility MTC terminal is significantly reduced.
Owner:ZTE CORP
Front access lan and timing (SATT)
ActiveUS7037143B2Reduce necessityImprove securityElectrically conductive connectionsCoupling device detailsMechanical engineeringElectronics
Owner:CIENA
Application programming interface access method and system, server and clients
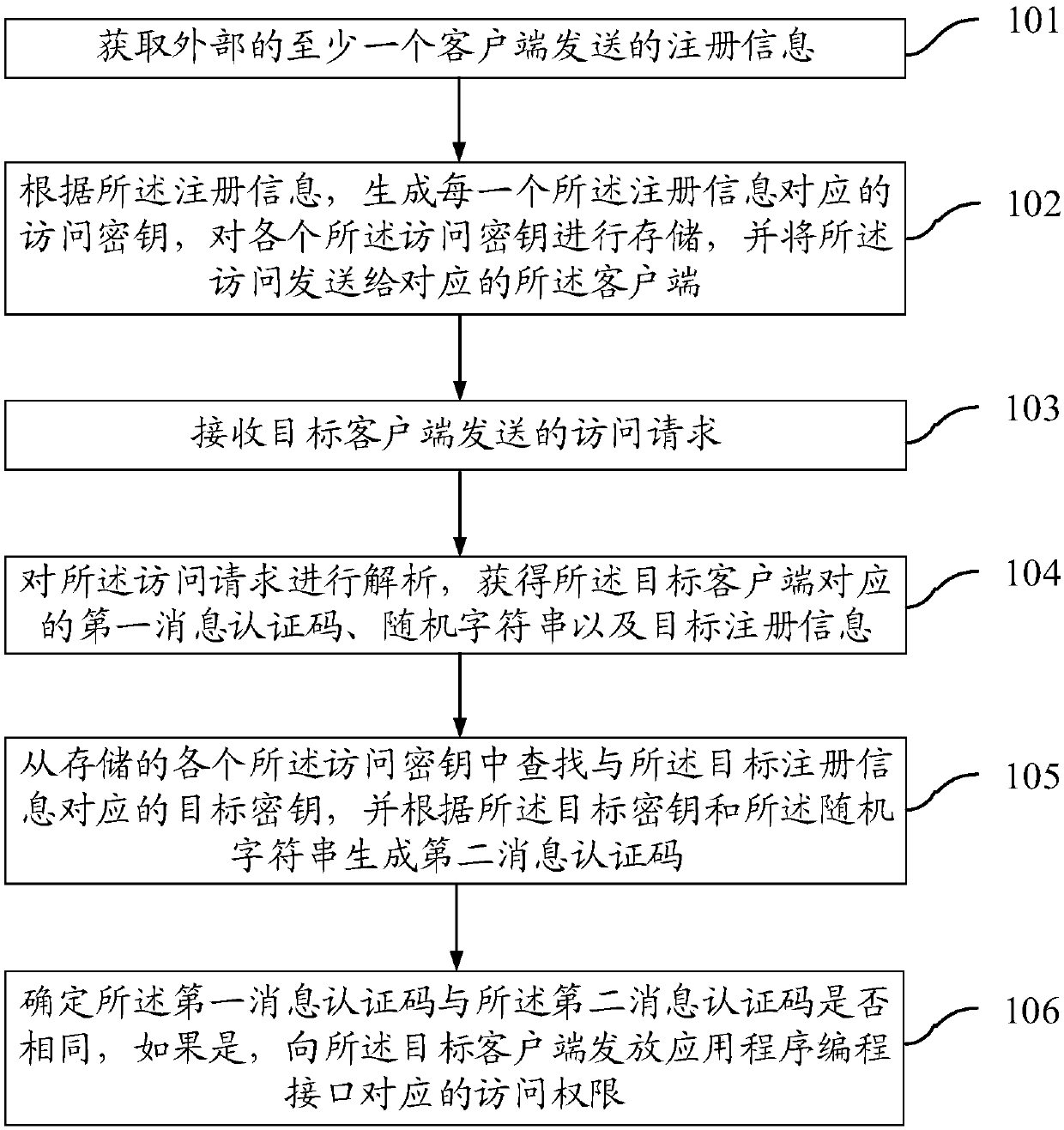
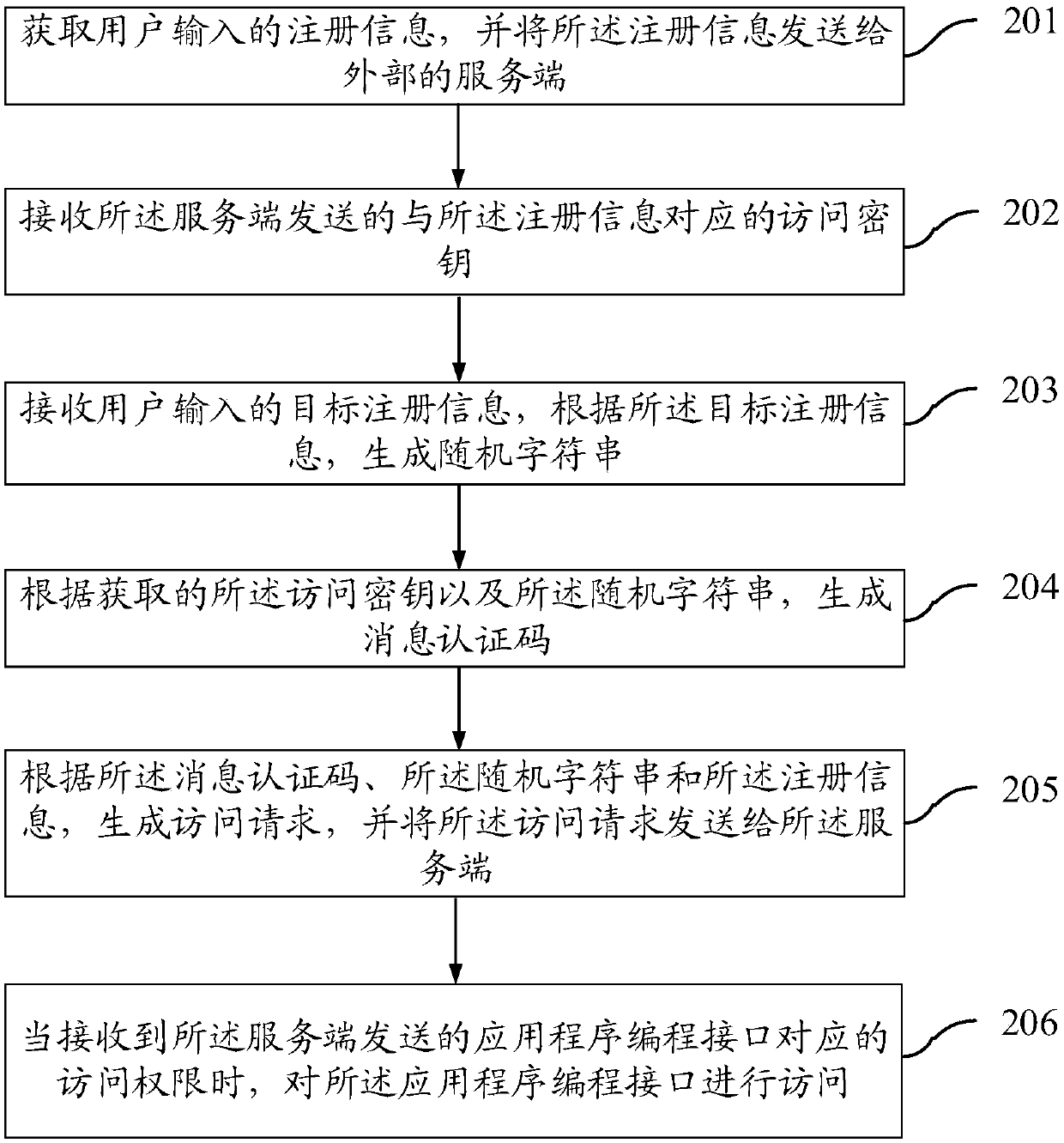
InactiveCN107911381AAvoid exposurePrevent leakageTransmissionAccess methodApplication programming interface
The invention provides an application programming interface access method and system, a server and clients. When the method is applied to the server, the method includes the following steps: acquiringregistration information sent by at least one external client; generating an access key corresponding to each piece of registration information according to the registration information, storing eachaccess key, and sending the access keys to the corresponding clients; receiving an access request sent by a target client; parsing the access request to obtain a first message authentication code, arandom character string and target registration information corresponding to the target client; searching a target key corresponding to the target registration information from each stored access key,and generating a second message authentication code according to the target key and the random character string; and determining whether the first message authentication code is the same as the second message authentication code, and if so, issuing an access authority corresponding to an application programming interface to the target client. According to the scheme, the security of API access can be improved.
Owner:JINAN INSPUR HIGH TECH TECH DEV CO LTD
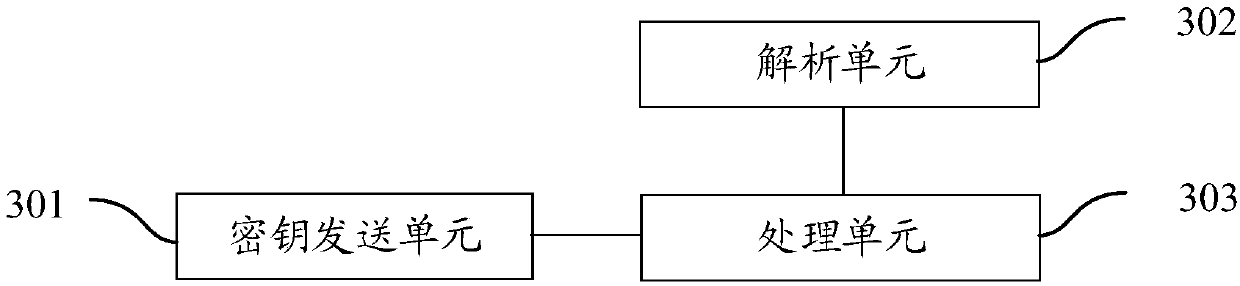
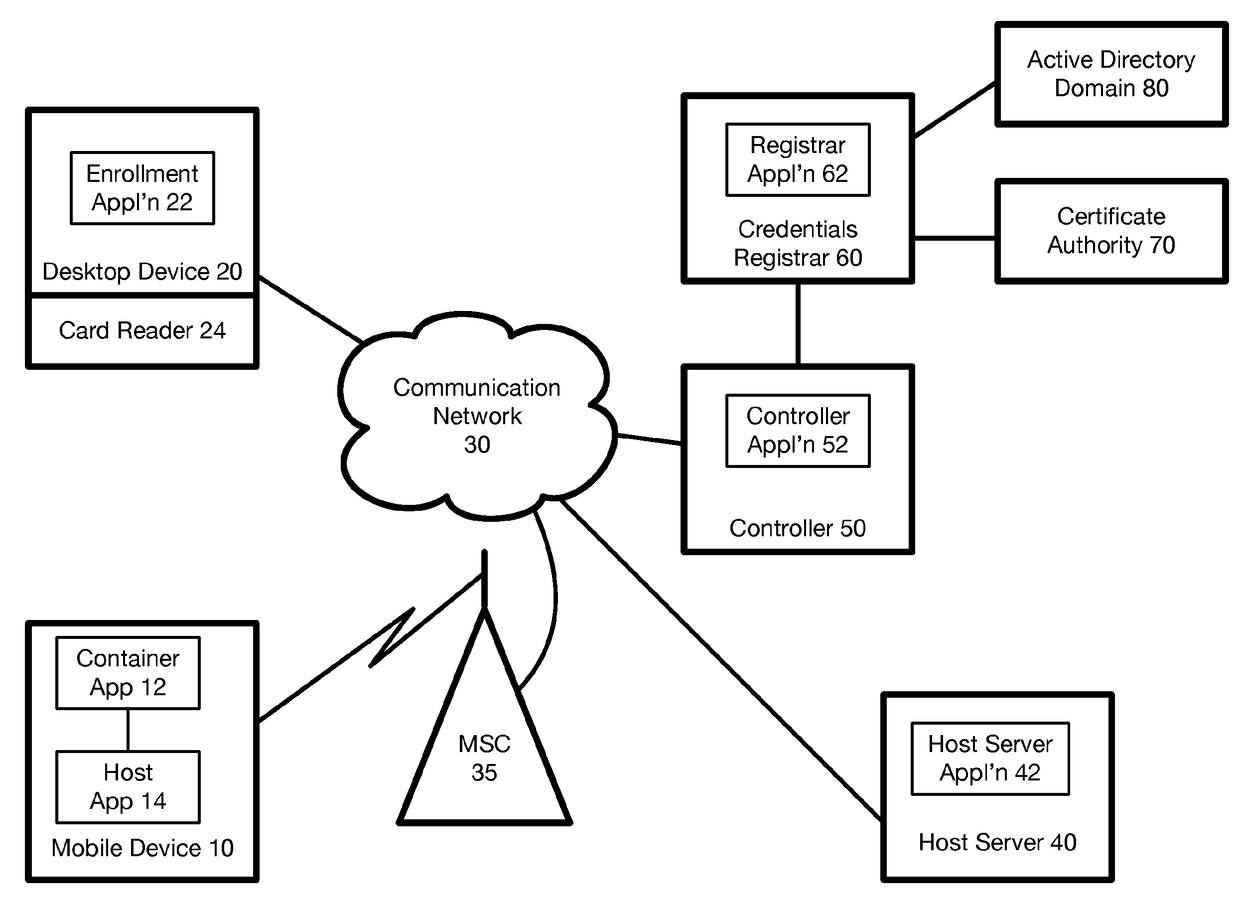
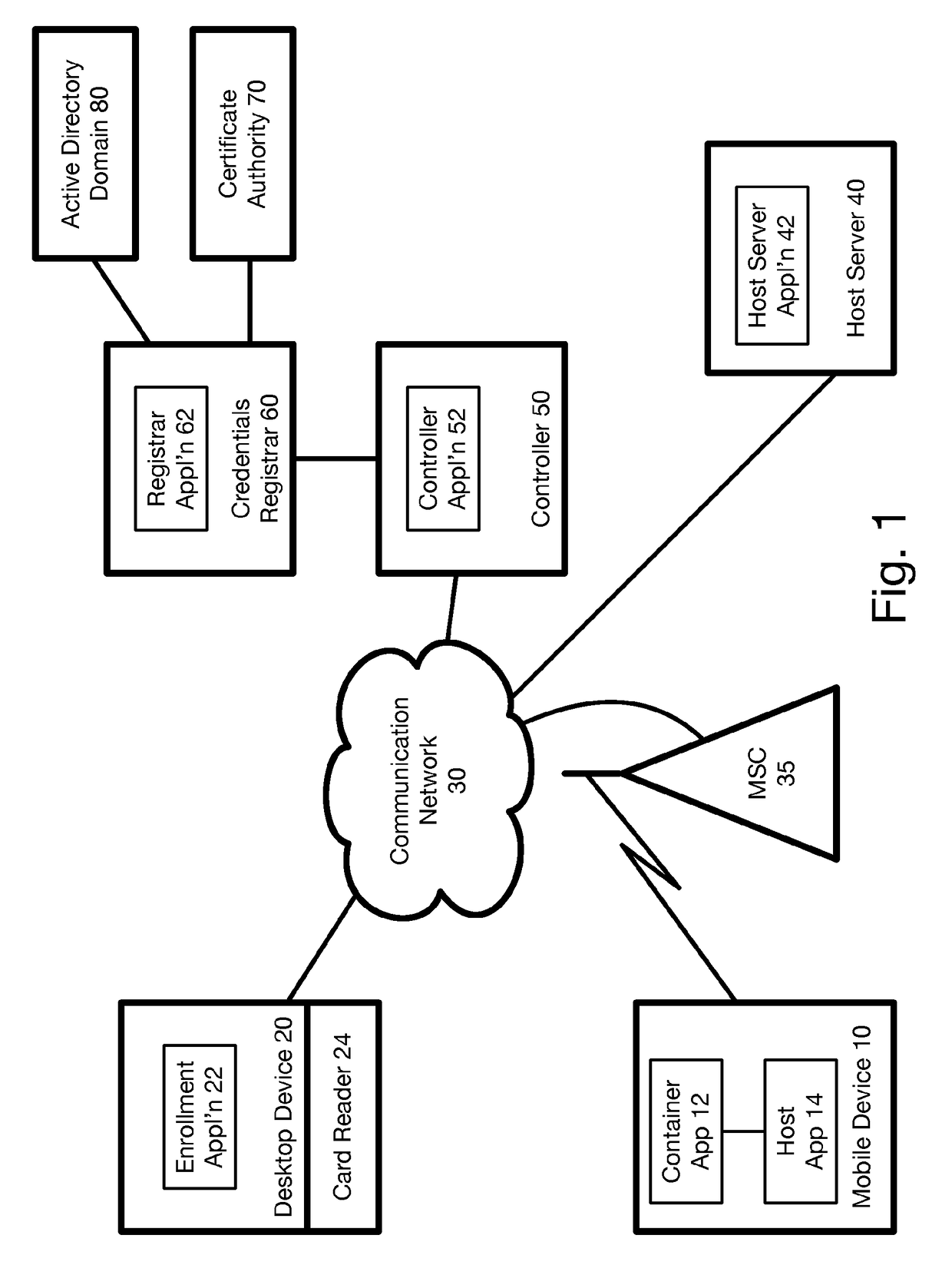
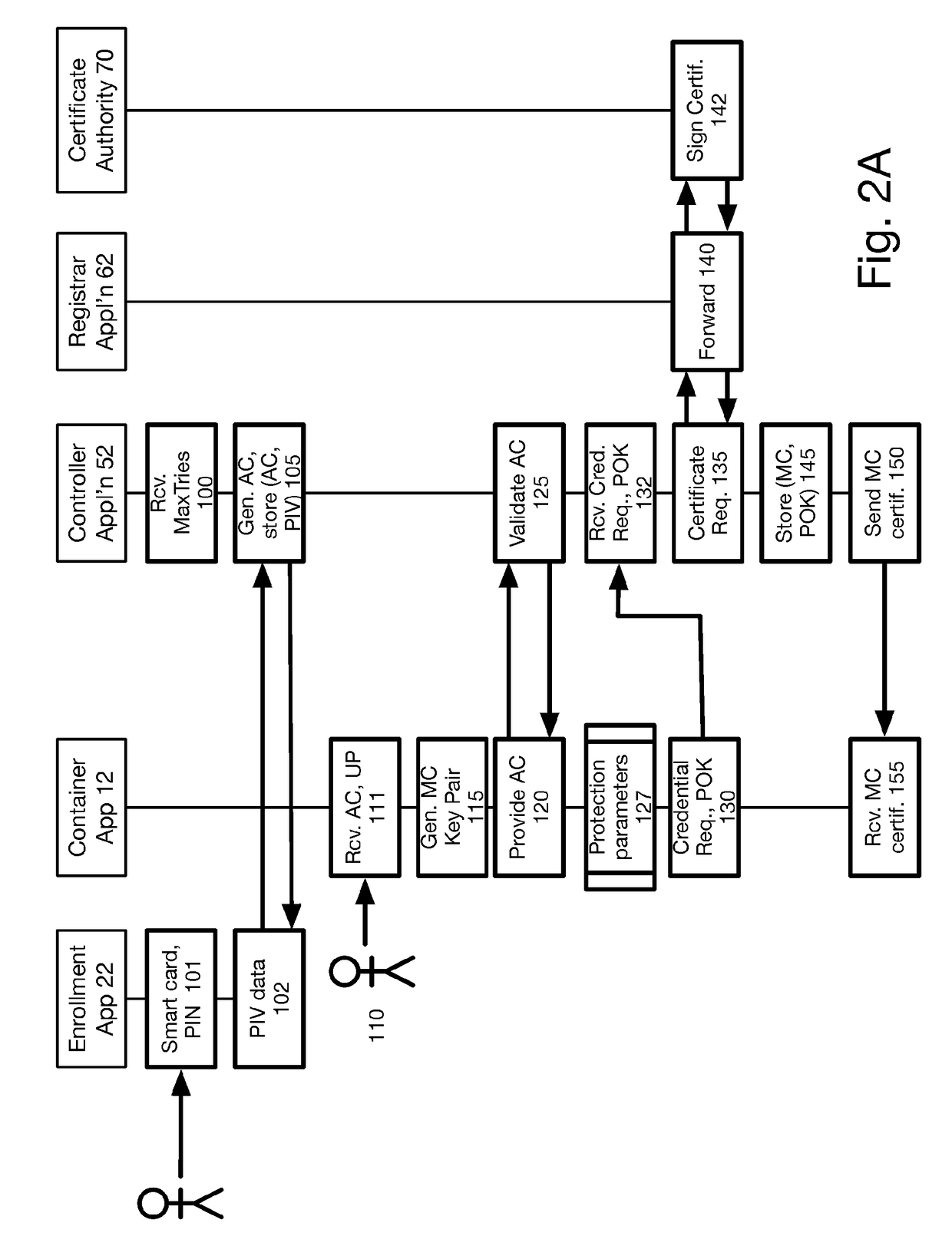
Method and system for issuing and using derived credentials
ActiveUS20180041494A1Improve access securityEncryption apparatus with shift registers/memoriesDigital data authenticationPasswordSmart card
At a mobile device, a password is used to create a proof of knowledge (POK). The POK is stored in a controller accessible via a communication network. The POK ensures that the controller can detect an incorrect password from the mobile device, and that the mobile device cannot be subject to a brute force attack to determine the DC stored in the mobile device. After a predetermined number of unsuccessful attempts to enter the password, the controller blocks further attempts, thereby restoring protection against a brute force attack that was lost going from a standalone smart card to mobile-device-based derived credentials. A portion of Derived Credentials, needed to authenticate the user of a mobile device, is stored in the controller, further increasing the difficulty of unauthorized use.
Owner:ROUTE1
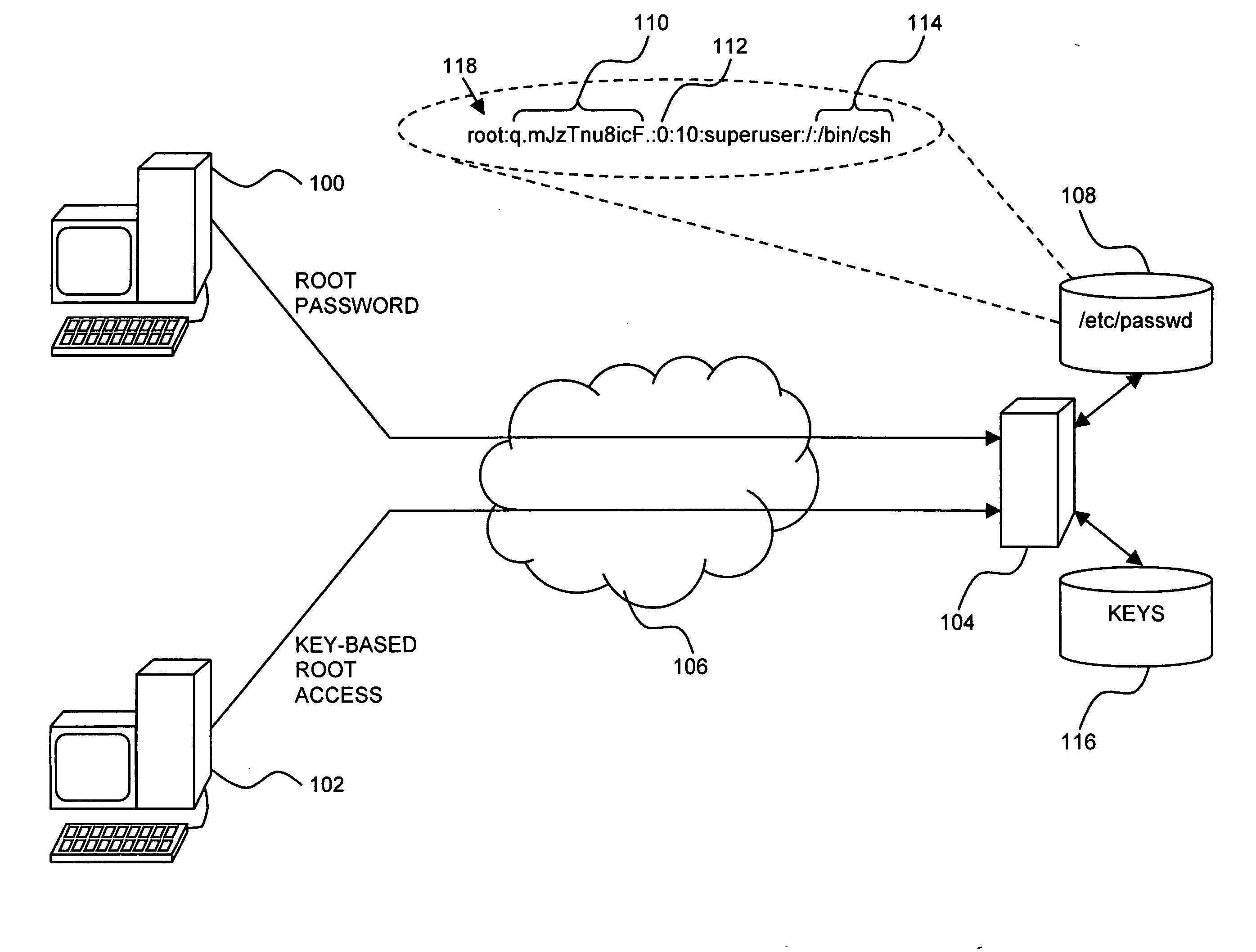
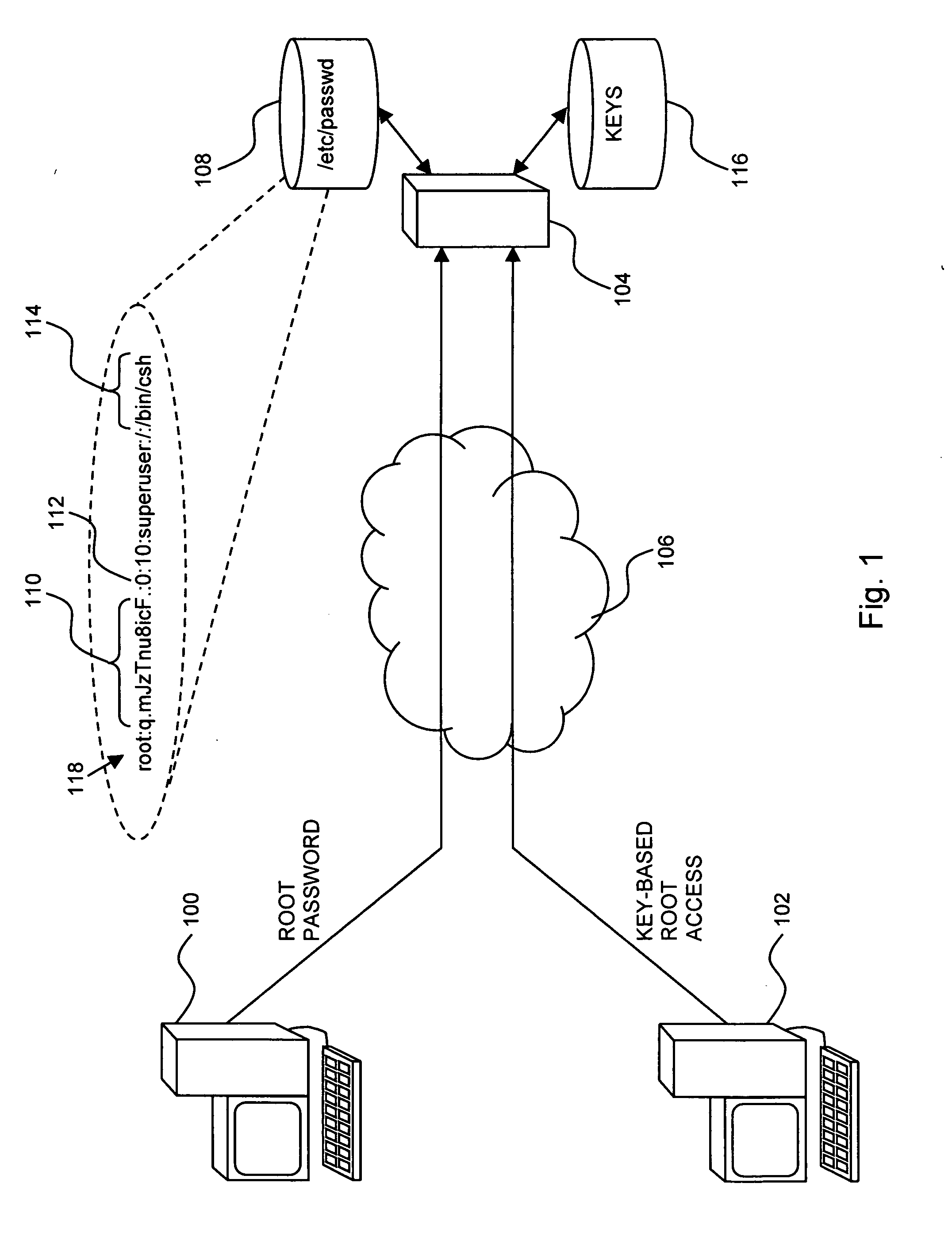
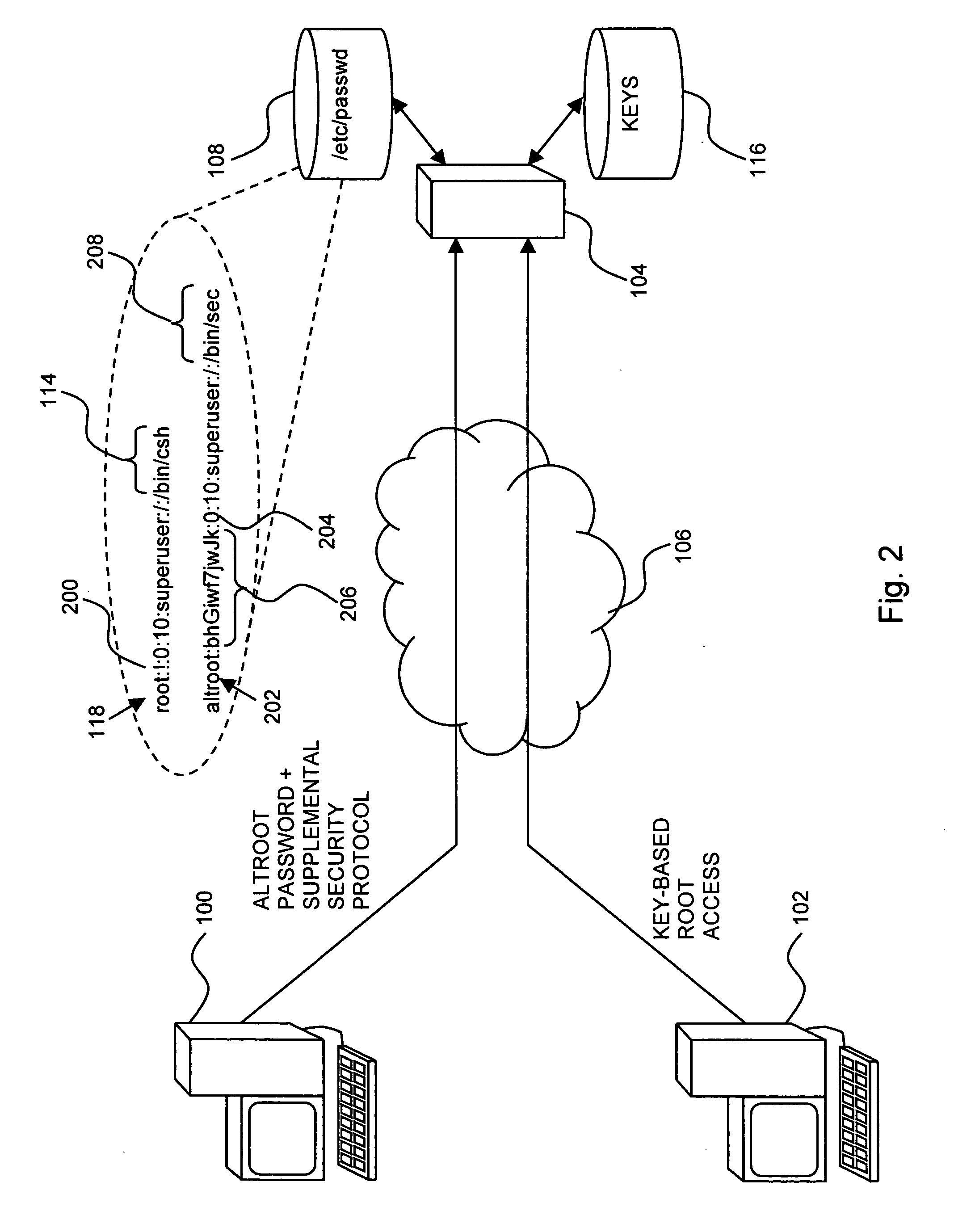
Computer access security
InactiveUS20060236118A1Improved computer access securityImprove access securityDigital data processing detailsUser identity/authority verificationPasswordComputer access
A method is provided for improved computer access security, the method including protecting an access record to prevent password access to a computer via the access record, creating an alternate access record corresponding to the protected record, enabling password access to the computer via the alternate record, providing the alternate record with the access level of the protected record, and configuring the alternate record to indicate a supplemental security program to be executed once a correct password for the alternate record is provided.
Owner:IBM CORP
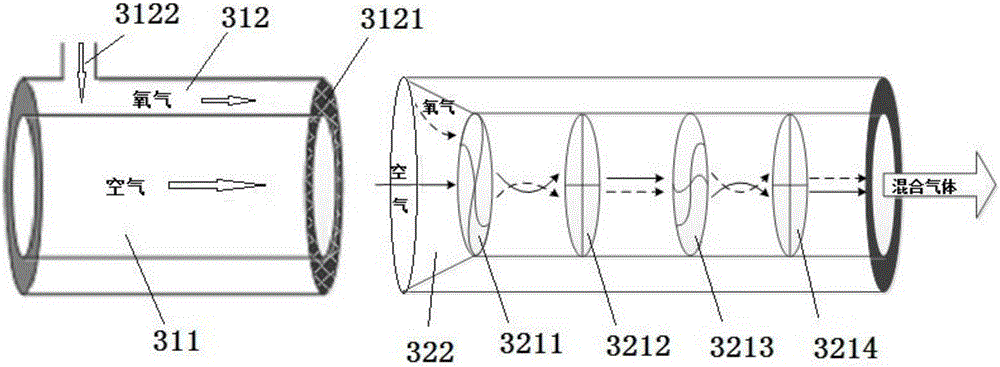
Air-oxygen mixing airway for respirator, respirator and method
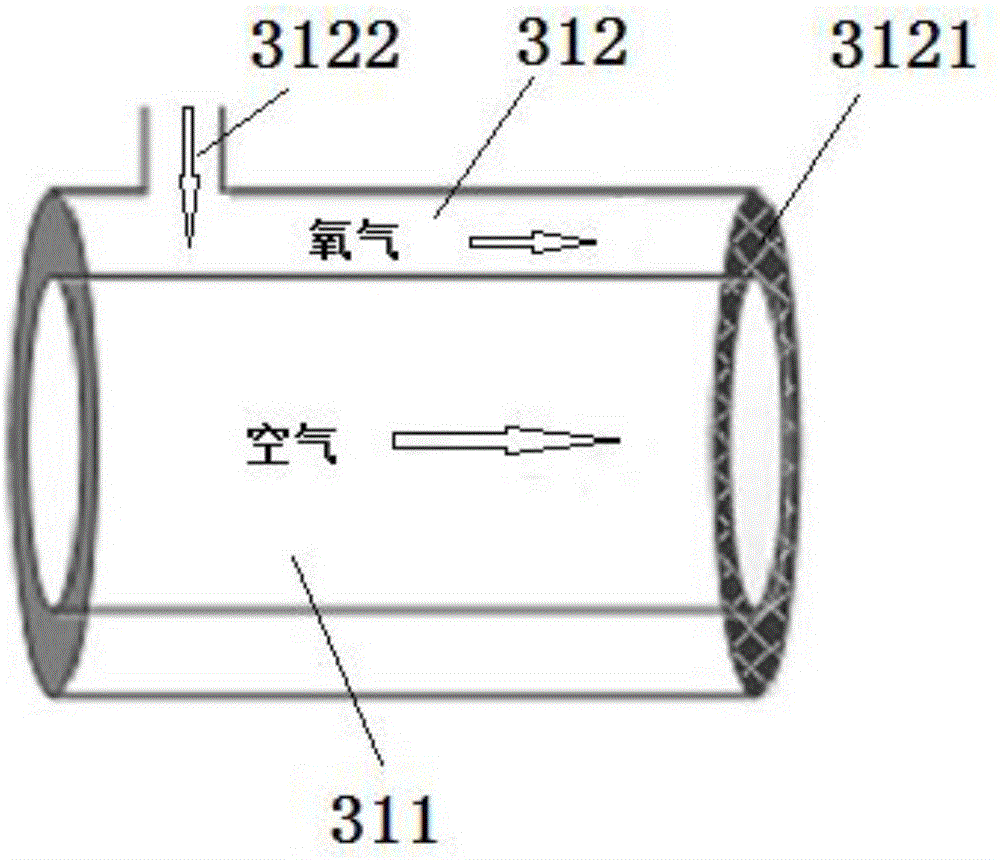
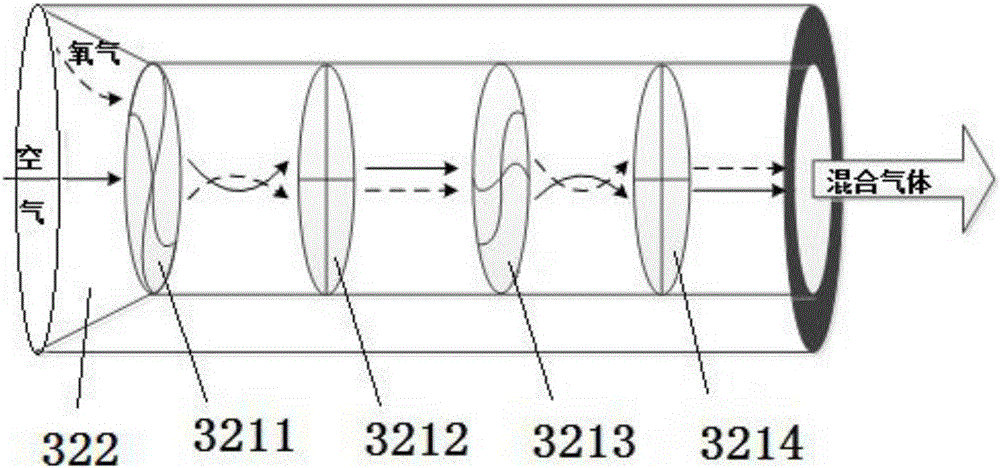
Disclosed are an air-oxygen mixing airway for a respirator, the respirator and a method. The air-oxygen mixing airway comprises an anti-turbulence member and an air-oxygen mixing cavity, the anti-turbulence member comprises an oxygen way and an air way, two ends of the air way are open, the left end of the oxygen way is closed while the right end of the same is provided with an oxygen barrier piece, and an oxygen inlet is arranged on the outer side of the oxygen barrier piece. The respirator comprises an oxygen way, an air way and an air-oxygen mixing chamber provided with the air-oxygen mixing airway, an oxygen miniature proportional valve, an oxygen flow sensor and an air intercepting member are arranged on the oxygen way, a fan, an air pressure adjusting valve, an air flow sensor and an air intercepting member are arranged on the air way, and opening degree of the oxygen valve is adjusted to adjust oxygen flowing speed according to oxygen concentration of mixed gas needing to be output and air flowing speed measured by the air flow sensor. The anti-turbulence member is adopted in the air-oxygen mixing airway, and can cooperate with the flow sensors which are high in accuracy and low in power consumption, and the oxygen barrier piece is utilized, so that accuracy of air-oxygen mixed gas can be improved.
Owner:HUNAN MICOME ZHONGJIN MEDICAL SCI & TECH DEV CO LTD
Method and system for managing door access using beacon signal
ActiveUS9805533B2Improve access securityImprove user convenienceIndividual entry/exit registersAuthenticationAccess control
Disclosed are a method and system for managing access to a door using a beacon signal. An access control method of a user access authority determination unit that controls access of a user to a target door based on a signal including beacon data from a plurality of beacons installed near a door, wherein the user carries a terminal and the terminal obtains the signal including the beacon data based on a proximity to the plurality of beacons may include identifying the target door based on an identification information of the plurality of beacons extracted from the beacon data, determining a type of user movement, wherein the type of user movement includes a entering movement that the user enters into an inner side from an outer side through the target door and a exiting movement that the user exits the inner side to the outer side through the target door, and determining an access authentication process to be performed to unlock the target door, wherein the access authentication process is determined according to the determined type of user movement.
Owner:SUPREMA INC
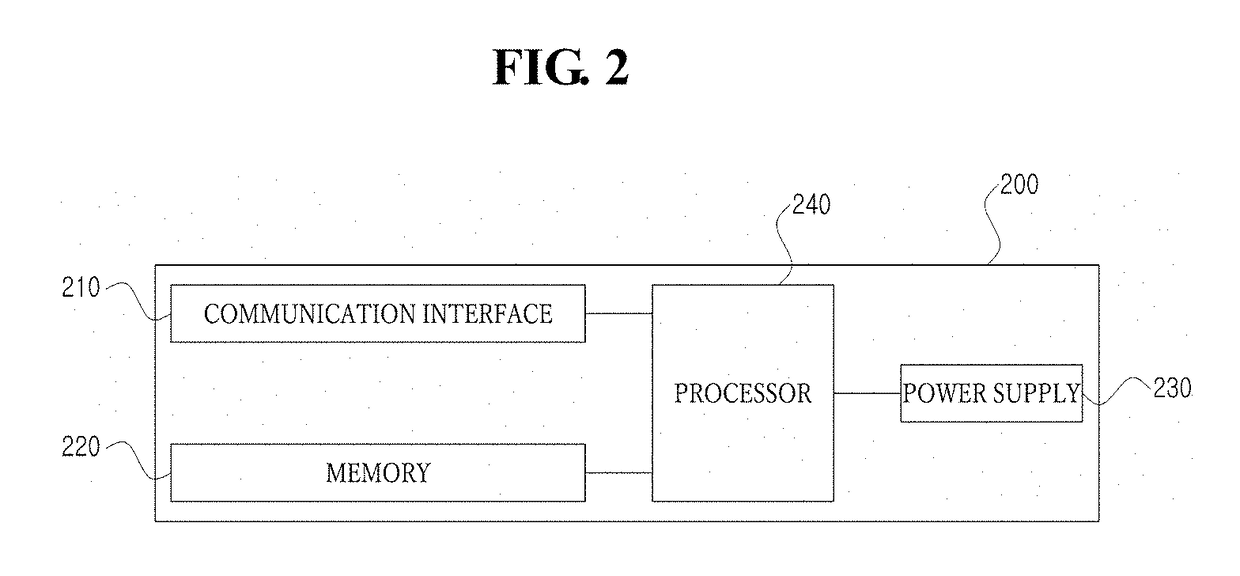
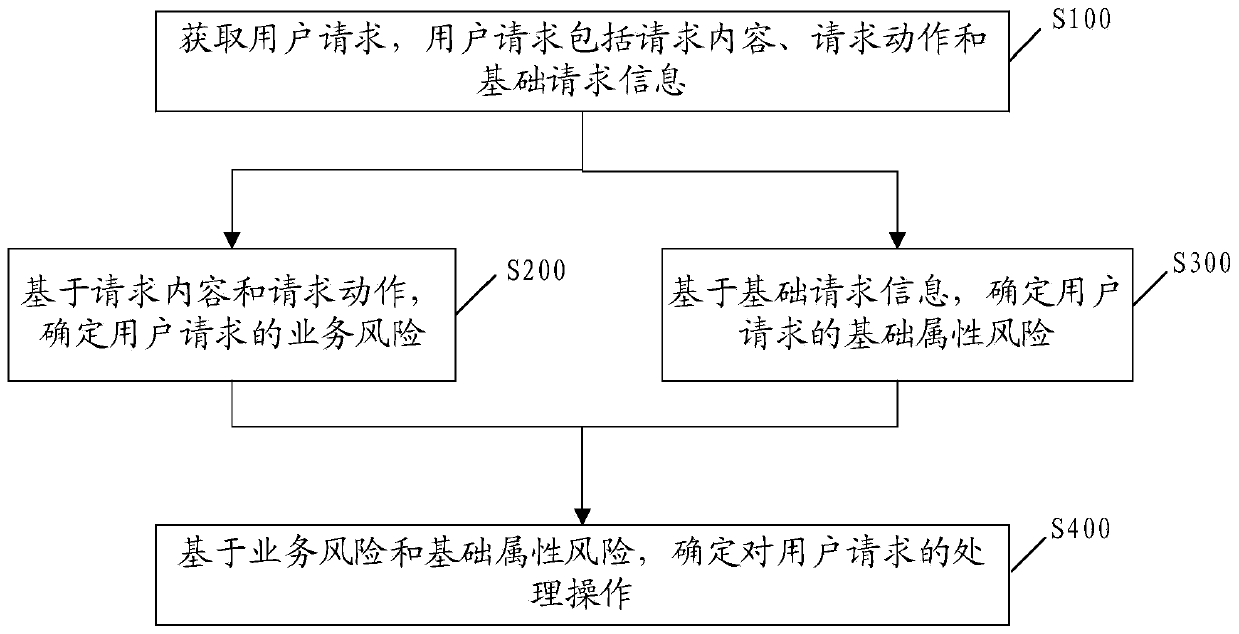
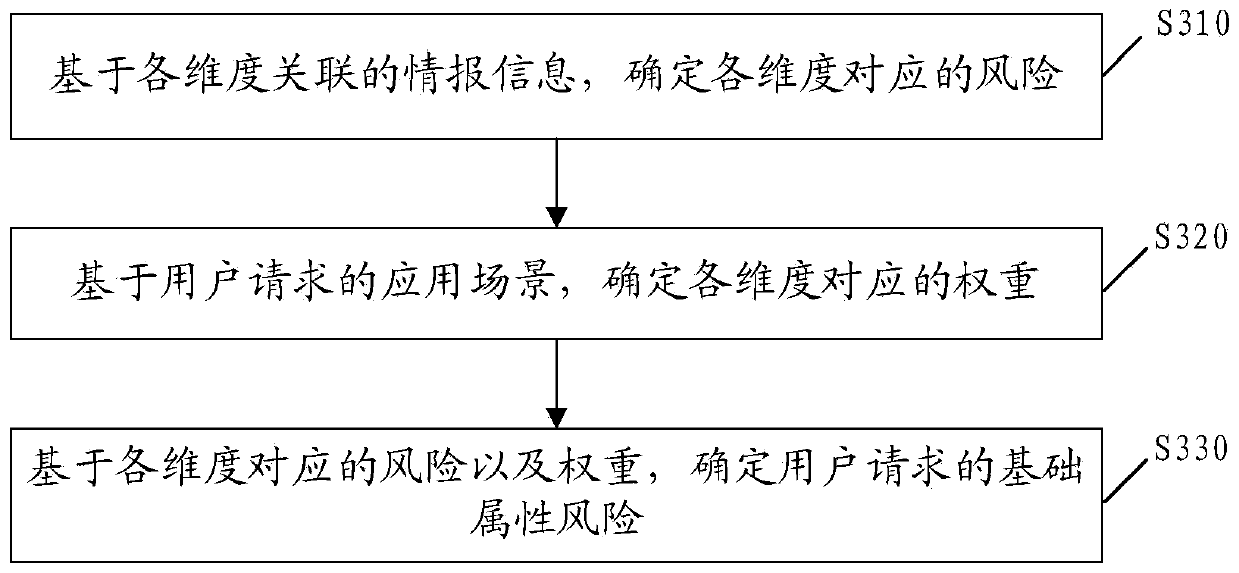
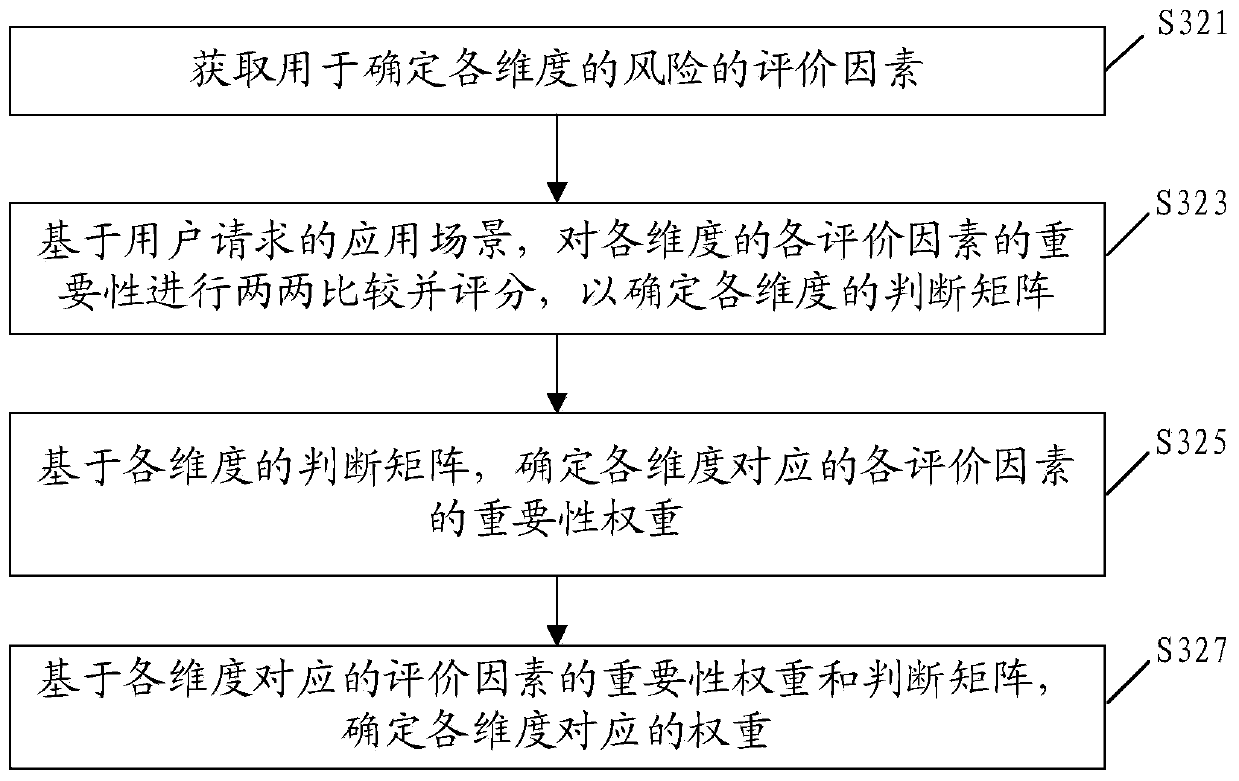
Secure access method and device, storage medium and terminal equipment
The invention provides a secure access method and device, a storage medium and terminal equipment, and the method comprises the steps: obtaining a user request which comprises request content, a request action and basic request information; determining a service risk requested by the user based on the request content and the request action; determining a basic attribute risk of the user request based on the basic request information; and determining a processing operation on the user request based on the business risk and the basic attribute risk. Compared with the prior art, the specific service scene and the basic information are integrated, and the service request risk is integrally judged. And moreover, the dependence of an enterprise on manual experience can be effectively reduced, and the method can be applied to different service scenes and has certain universality.
Owner:BAIDU ONLINE NETWORK TECH (BEIJIBG) CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com