Service access method and system, authentication method and system, client and authentication server
An authentication server and business access technology, which is applied in client, business access, authentication server, authentication method and corresponding system fields, can solve the problem of low security of business access
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
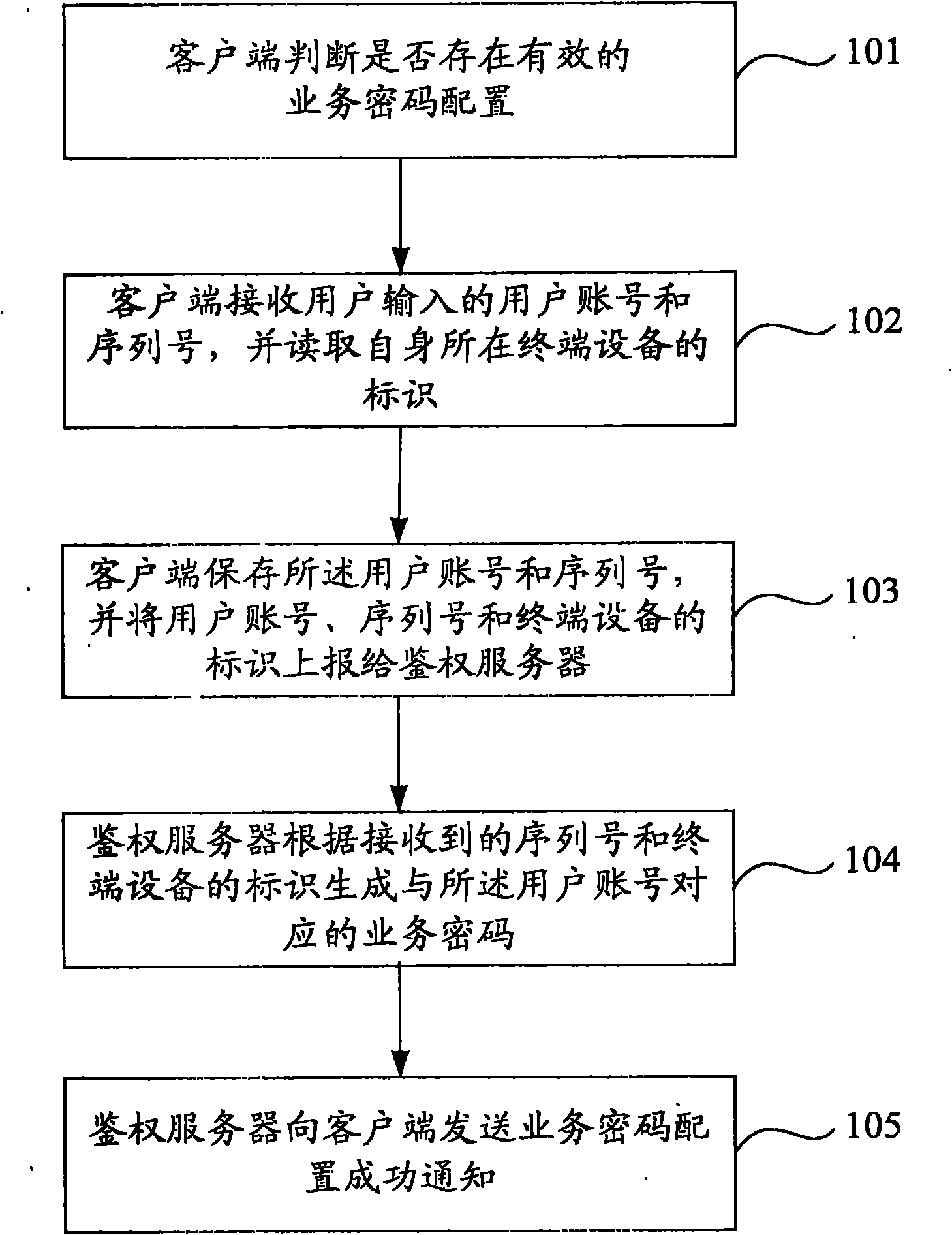
[0044] Such as figure 1 As shown, it is the configuration process of the service password provided by Embodiment 1 of the present invention, and the specific content includes:
[0045] Step 101, the client terminal judges whether there is a valid service password configuration.
[0046] There may be various trigger conditions for this step, including but not limited to: periodically judging whether there is a valid service password configuration, and judging whether there is a valid business password configuration when receiving a service access request.
[0047] The specific judgment method can be as follows: set the business password configuration success flag in the client, if there is currently a valid business password configuration, set the business password configuration success flag to 1; otherwise, the business password configuration success flag position 0.
[0048] If there is currently a valid service password configuration, then end the service password configur...
Embodiment 2
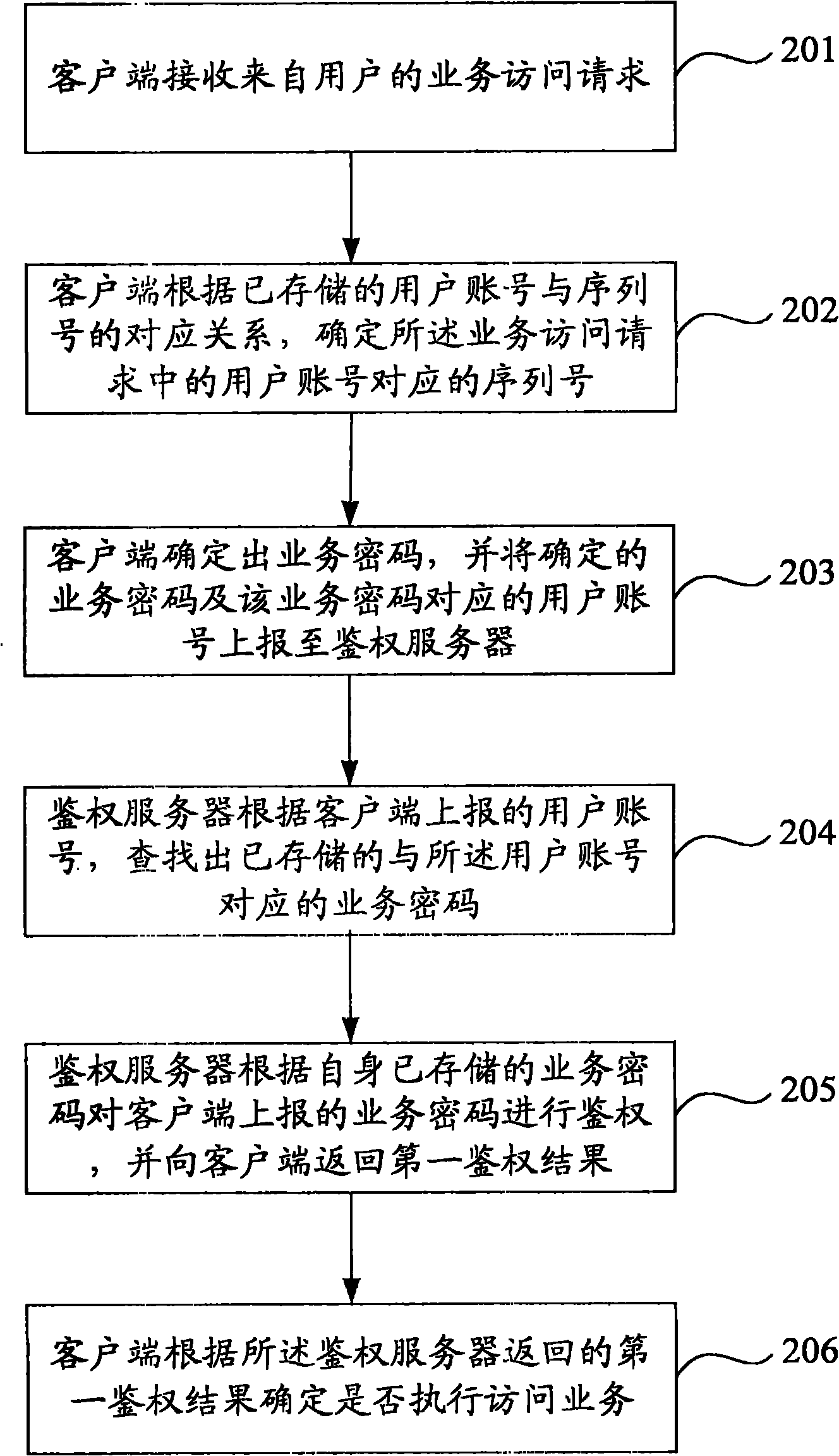
[0061] Such as figure 2 As shown, it is a schematic flow diagram of the service access method provided in Embodiment 2 of the present invention, and the specific content includes:
[0062] Step 201, the client receives a service access request from a user.
[0063] When the user logs in to the client, a service access request is initiated to the client, and the service access request carries a user account representing the user's identity.
[0064] This step can be used as the trigger condition of step 101 in Embodiment 1. When the client receives the service access request, it judges whether there is a valid service password configuration corresponding to the user account. If there is no valid service password configuration, enter the The service password configuration process recorded in Embodiment 1, otherwise, directly enter the service access process.
[0065] Step 202: The client determines the serial number corresponding to the user account in the service access requ...
Embodiment 3
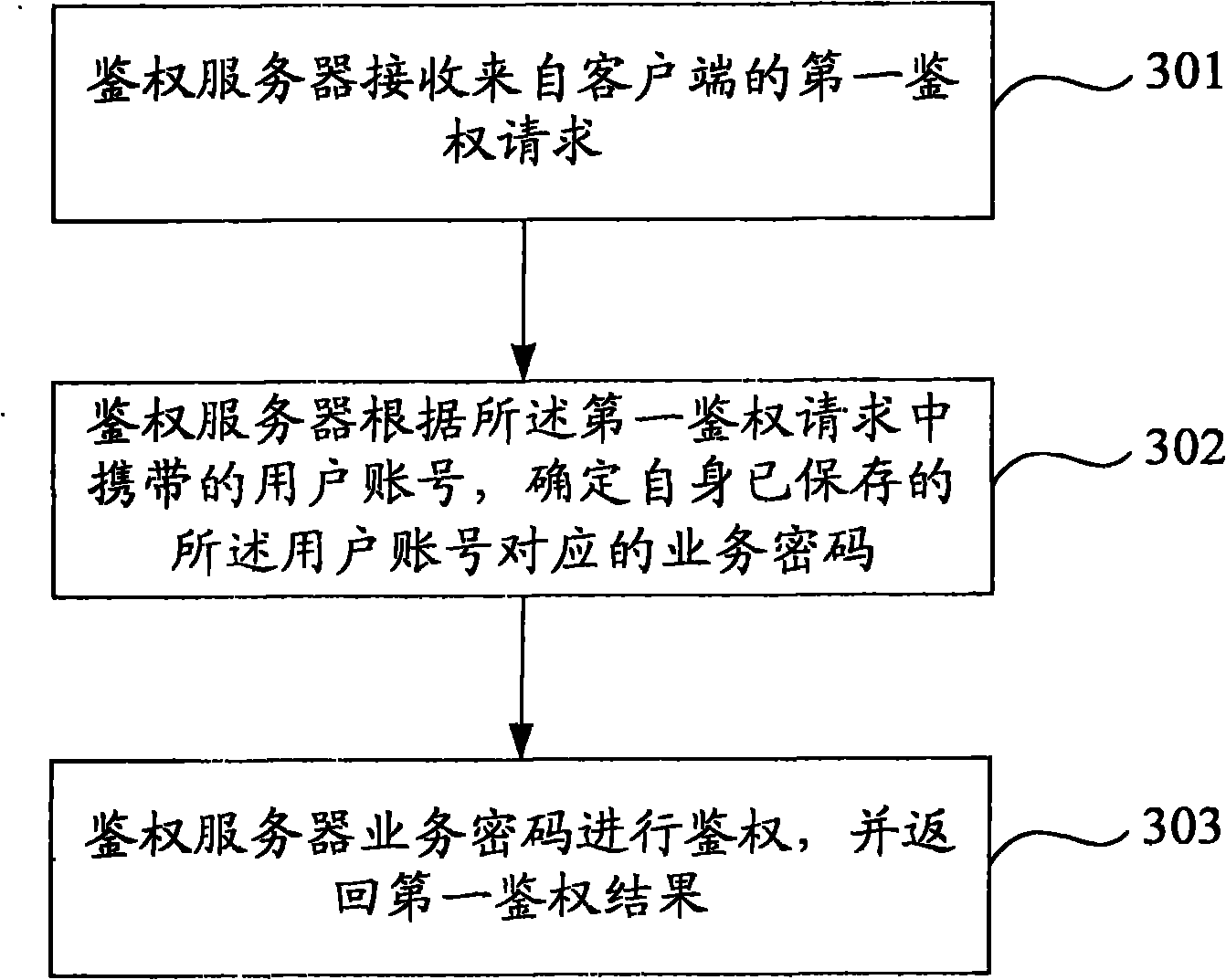
[0080] Embodiment 3 of the present invention also provides an authentication method under the same inventive concept as Embodiment 2, such as image 3 As shown, the method includes the following steps:
[0081] Step 301: the authentication server receives a first authentication request from a client.
[0082] The first authentication request includes a user account.
[0083] Before this step is performed, the authentication server and the client have performed a configuration process for the service password of the user account.
[0084] Step 302: According to the user account carried in the first authentication request, the authentication server determines the service password corresponding to the user account which has been saved by itself.
[0085] In this step, the authentication server determines the service password corresponding to the user account carried in the first authentication request according to the correspondence between the user account and the service pass...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com