Secure access method and device, storage medium and terminal equipment
A security access and risk technology, applied in the computer field, can solve the problems of difficult judgment, poor reusability, and high labor cost
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0093] In the following, only some exemplary embodiments are briefly described. As those skilled in the art would realize, the described embodiments may be modified in various different ways, all without departing from the spirit or scope of the present invention. Accordingly, the drawings and descriptions are to be regarded as illustrative in nature and not restrictive.
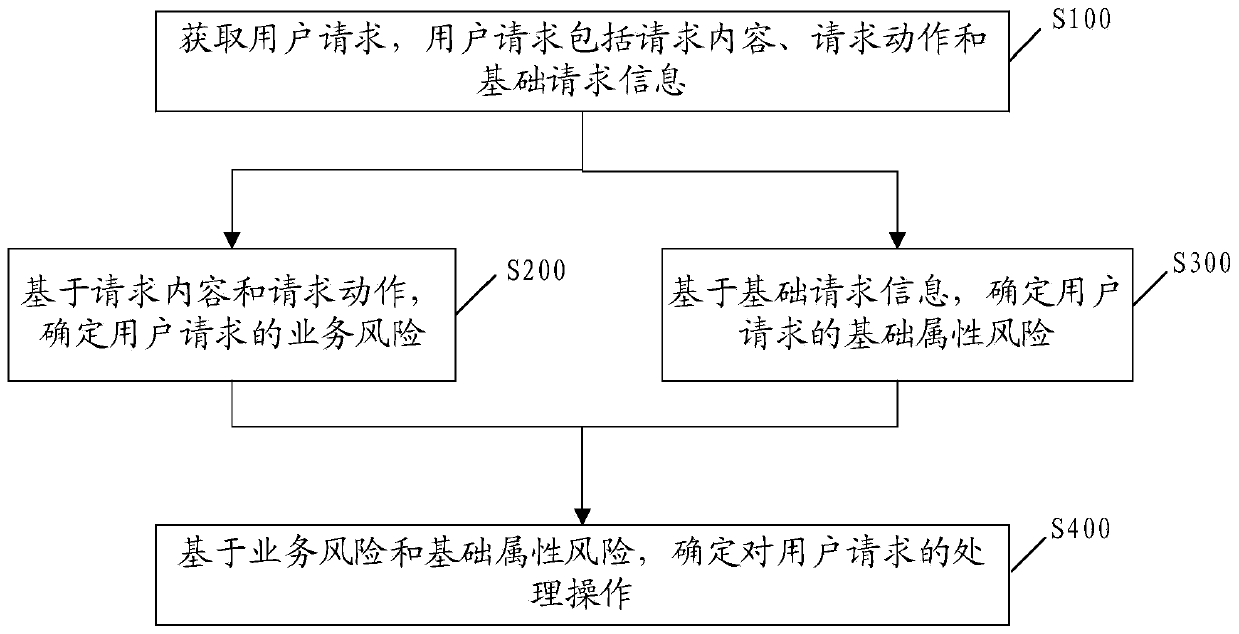
[0094] see figure 1 , the embodiment of the present invention provides a secure access method. This embodiment can be applied to scenarios such as financial transactions, online comments, logging in or registering on a certain website or platform. This embodiment may include steps S100 to S400, as follows:
[0095] S100. Obtain a user request, where the user request includes request content, request action and basic request information.
[0096] In some embodiments, when the service-providing system receives a user request, it can split the user request, and extract request content, request action, and b...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com