Processing method and device as well as acquisition method and device for security information
A security information and processing method technology, applied in the field of security information processing method and device, acquisition method and device, can solve problems such as different security algorithms and keys, inability to achieve security isolation of different network slices, and inability to provide different network slices , to achieve security isolation and improve access security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
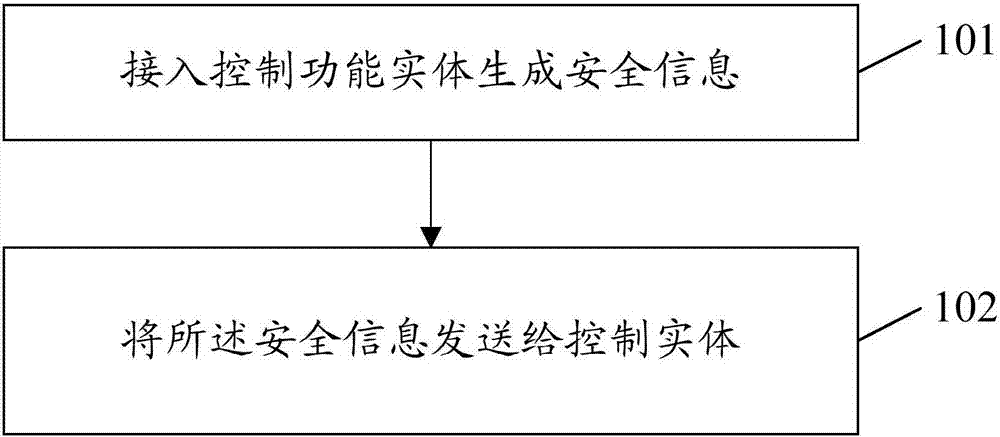
[0071] Such as figure 2 As shown, the first embodiment of the present invention provides a processing method for security information, the processing method comprising:
[0072] Step 101, the access control functional entity generates security information;
[0073] Step 102, sending the security information to a control entity.
[0074] It should be noted that the access control function entity provided by the embodiment of the present invention may be AAA or HSS. Among them, AAA is Authentication Authorization Accounting, authentication authorization accounting; HSS is Home Subscriber Server, belonging to the user server
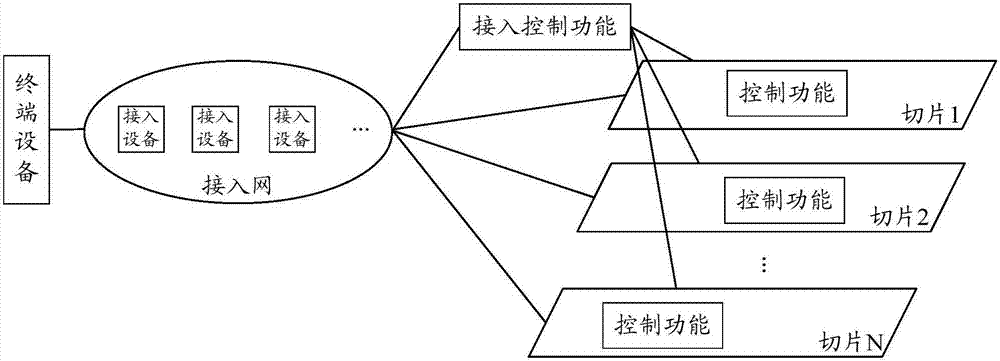
[0075] Such as image 3 Shown is the system architecture of the terminal access network slicing method provided by the embodiment of the present invention. The system architecture separates the authentication and authorization functions from each network slice to form an independent function, that is, image 3 In the access control function, the access...
no. 2 example
[0108] The second embodiment of the present invention provides a method for obtaining security information of a terminal, which is applied to network slicing, and the method for obtaining includes:
[0109] Step 201, receiving terminal security information sent by an access control functional entity; or,
[0110] Step 301: Send a first request message to the access control function entity, the first request message carries the identifier of the terminal requesting to access the network slice, and the first request message is used to request to obtain the terminal's security information;
[0111] Step 302, receiving the security information of the terminal sent by the access control function; or,
[0112] Step 401, receiving an access request message of a terminal sent by an access device, where the access request message carries security information of the terminal.
[0113] Specifically, in step 201, the access control entity actively provides terminal information to the ne...
no. 3 example
[0118] The third embodiment of the present invention provides a method for obtaining security information of network slicing, which is applied to a terminal, including:
[0119] Step 501, receiving the security information of each network slice subscribed by the terminal sent by the access control function entity; or,
[0120] Step 601: Send a second request message to the access control function entity, where the second request message carries information about the network slice accessed by the terminal, and the second request message is used to request to obtain the security information of the network slice. information;
[0121] Step 602: Receive the security information of the network slice sent by the access control function entity.
[0122] Specifically, step 501 is actively provided by the access control function, which means that it sends security information of each network slice subscribed by the terminal to the terminal during the authentication process (or after t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com