Access layer and non-access layer secret key safety isolation device and method thereof
A non-access layer key and access layer key technology, applied in the field of communication, can solve problems such as the inability of wireless communication network system to be implemented, and achieve the effect of realizing security isolation, ensuring security, and improving security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
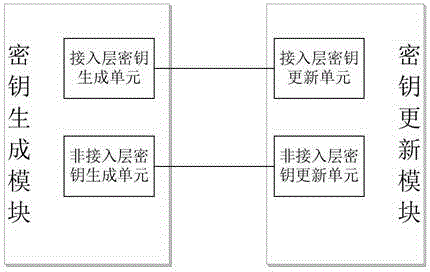
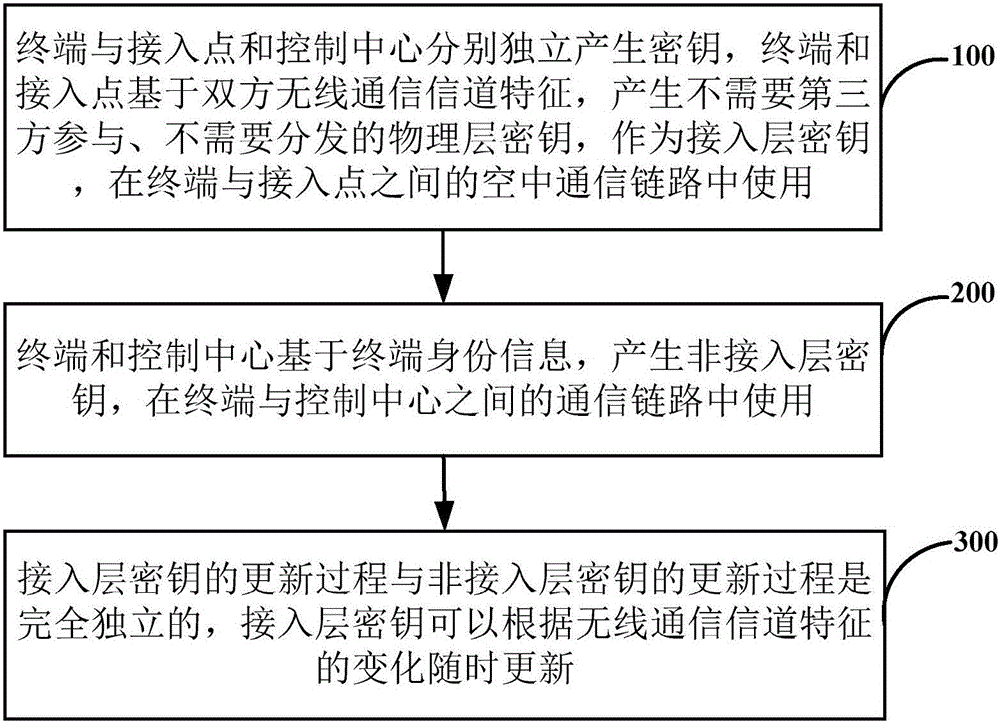
[0036] Embodiment one, see figure 1 As shown, an access layer and non-access layer key security isolation device includes a key generation module and a key update module, and the key generation module includes access layer keys that generate keys independently of each other A generation unit, a non-access stratum key generation unit, wherein, the access stratum key generation unit, the terminal and the access point generate the key used for the air communication link between the terminal and the access point based on the characteristics of the wireless communication channel of both parties The access stratum key; the non-access stratum key generation unit, the terminal and the control center generate the non-access stratum key for use in the communication link between the terminal and the control center based on the terminal identity information;
[0037] The key updating module includes an access stratum key updating unit and a non-access stratum key updating unit that comple...
Embodiment 2
[0040] Embodiment two, see Figure 1~2 As shown, a security isolation method for access layer and non-access layer keys includes the following steps:
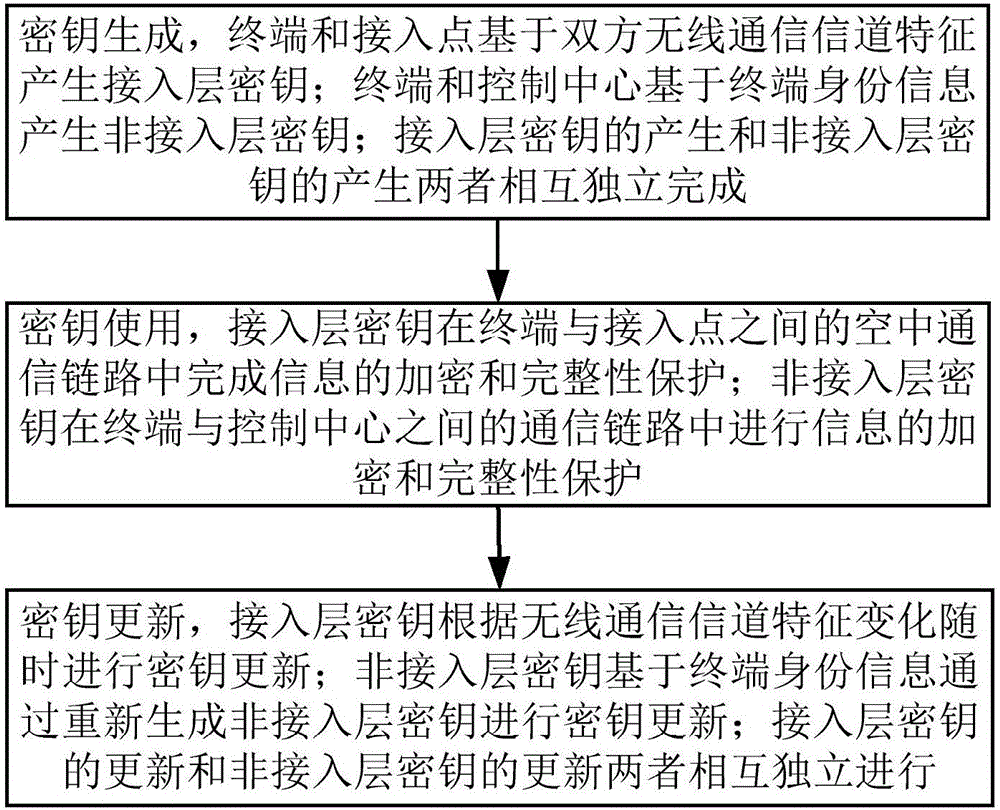
[0041] Step A, key generation, the terminal and the access point generate the access layer key based on the characteristics of the wireless communication channel of both parties; the terminal and the control center generate the non-access layer key based on the terminal identity information; the generation of the access layer key and the non-access layer key The generation of the access layer key is completed independently of each other;
[0042] Step B, key use, the access layer key completes information encryption and integrity protection in the air communication link between the terminal and the access point; the non-access layer key completes the information encryption and integrity protection in the communication link between the terminal and the control center Encryption and integrity protection of information on the roa...
Embodiment 3
[0045] Embodiment three, see Figure 1-7 As shown, a security isolation method for access layer and non-access layer keys includes the following content:
[0046] First, key generation, including: the generation of the access layer key and the generation of the non-access layer key are completed independently of each other, and the specific content is as follows:
[0047] 1) Access layer key generation: The terminal and the access point generate an access layer key based on the characteristics of the wireless communication channel between the two parties, including the following:
[0048] Step A1, the terminal and the access point respectively transmit pre-agreed transmission signals to each other in the same time slot;
[0049] Step A2: The terminal and the access point respectively obtain the first channel impulse response and the second channel impulse response according to the received signal and the pre-agreed transmission signal in step A1;
[0050] Step A3: The terminal...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com