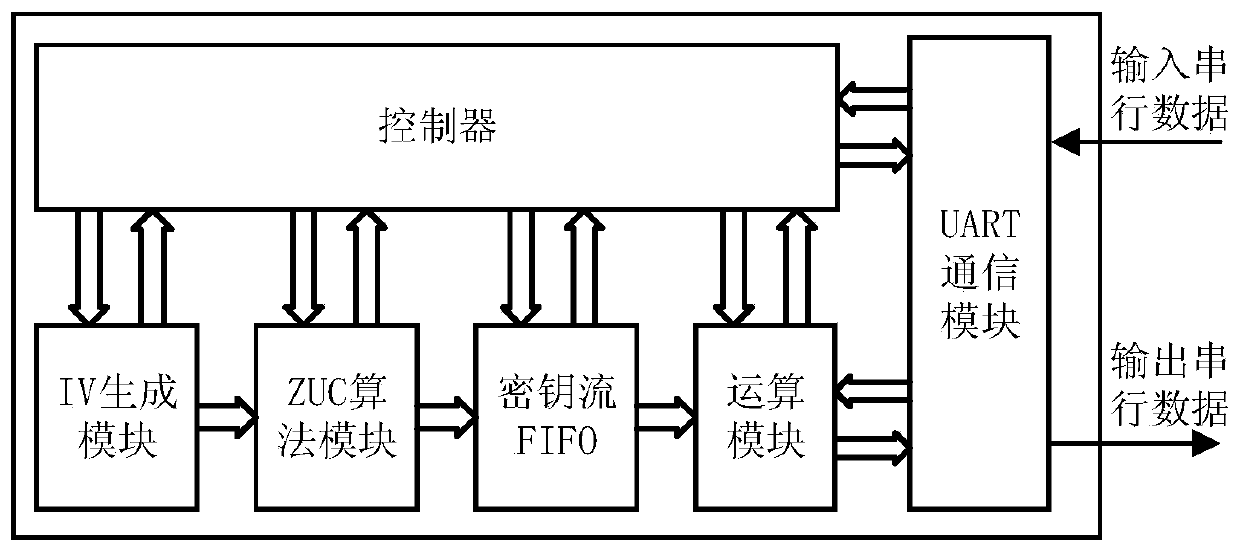
Chaos-based initial vector generation algorithm and IP core thereof
A technology of initial vector and generation algorithm, applied in secure communication through chaotic signals, countermeasures to attack encryption mechanisms, digital transmission systems, etc., can solve the problems of difficult application of the system, easy information loss, etc. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0036] A chaotic initial vector generation algorithm, the initial vector generation method is as follows:
[0037] Step 1. First, input a 32-bit initial value x into the sequence generator based on Logistic chaos 0 , the 128-bit initial key KEY of the ZUC encryption algorithm is divided into 16 32-bit key[i] (0≤i≤15), so that key[i] (0≤i≤15) are respectively used as the Logistic chaotic iterative mapping enter,
[0038] Among them, the expression of Logistic chaotic iterative mapping is as follows:
[0039] x n+1 =4x n (1-x n ) (1)
[0040] where x 0 is the initial value, n is the number of iterations, and x n Consists of 32-bit registers;
[0041] Step 2. Assign key[0] to 32-bit x 0 , and calculate x 1 =4x 0 (1-x 0 );
[0042] Step 3. Assign key[i] to key[i-1], and then assign x 1 Assigned to key[15], for all x generated in order 1 Intercept the 128-bit sequence at the end of the sequence at intervals of 1024 bits as an initial vector, and turn back to step 2. ...
Embodiment 2
[0050] FPGA of IP Core Based on Chaotic Initial Vector Generation Algorithm
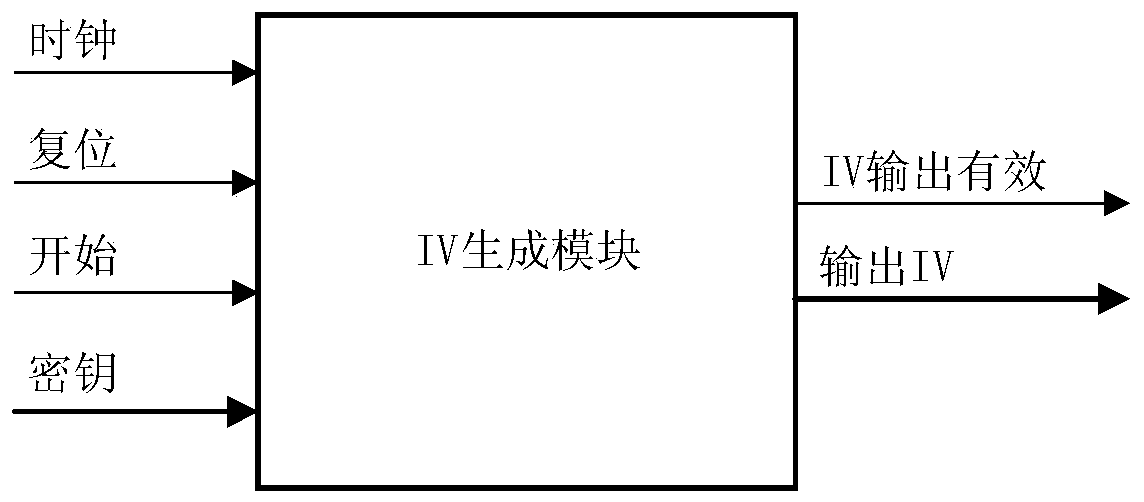
[0051] Such as figure 2 As shown, the initial vector generation module has 6 input and output signals, and its signal definitions are listed in Table 1.
[0052] Table 1 Top-level module signal list
[0053]
[0054]
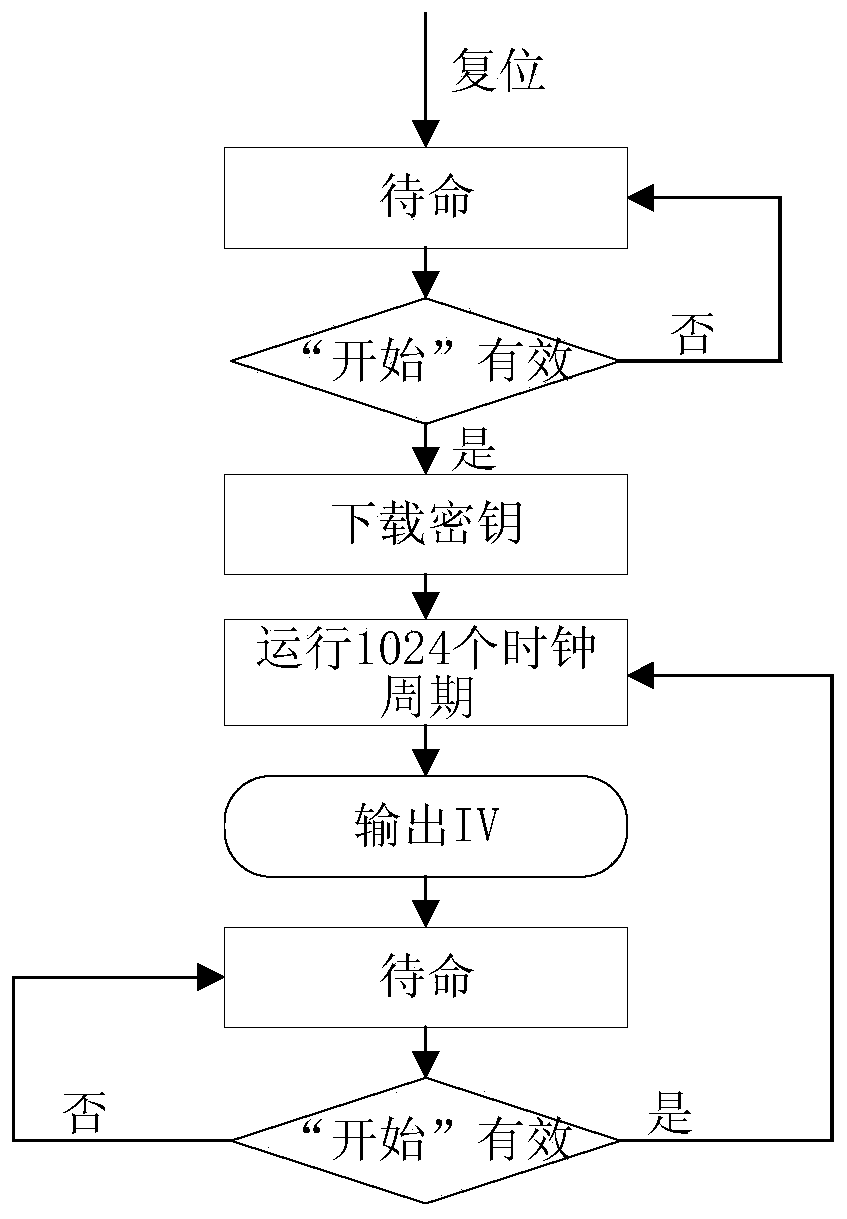
[0055] In addition to the clock signal and reset signal, the initial vector generation module also has a control signal "start". The main workflow of the initial vector generation module is explained here: when the initial vector generation module is powered on, it first performs a reset operation, and then The initial vector generation module enters the standby state. When the start signal is valid for the first time, the initial vector generation module will download the key and run for 1024 clock cycles, and then output an initial vector. At the same time, the initial vector valid flag signal "IV output is valid" pulls One beat higher means that the signal on the output sig...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com