Mimicry tamper-proof method of distributed file system
A distributed file and file system technology, applied in special data processing applications, instruments, electrical digital data processing, etc., and can solve problems such as data node failures
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
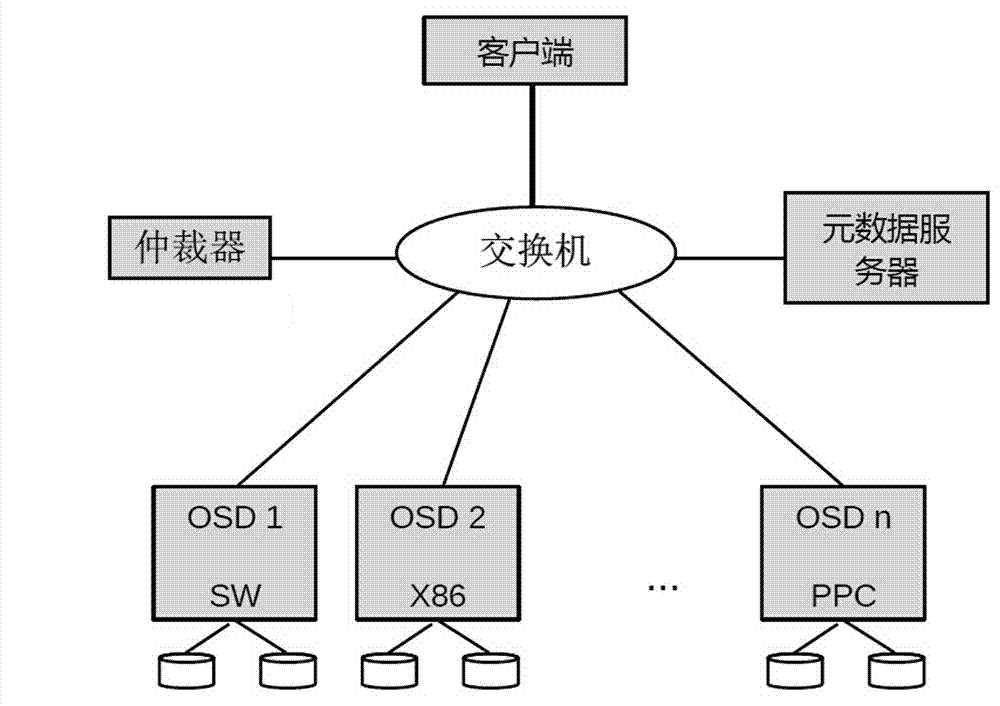
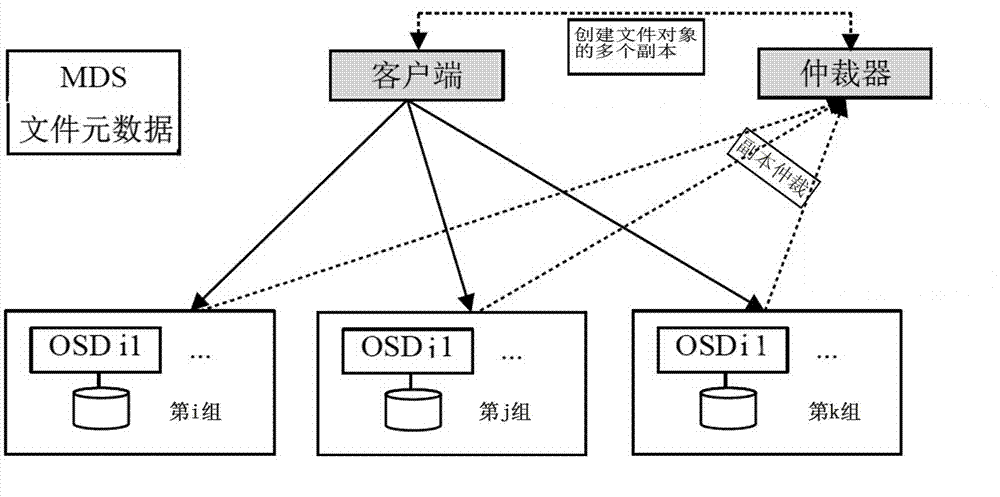
[0018] Below in conjunction with accompanying drawing and specific implementation mode, the mimetic anti-tampering method of the distributed file system of the present invention is further described: As shown in the figure, the present embodiment contains the following process: 1. For each file object to be written, in different Create multiple copies in the data nodes of the type; 2. Add an arbitrator to evaluate each copy, select the reserved copy according to different purposes, and delete the rest.
[0019] The arbitrator runs in an independent computer system and understands the information of newly written and unarbitrated copies, such as the identification, location and relationship of the copies; the arbiter compares the consistency of each copy, and obtains Select the copy to be deleted; the number of copies to keep depends on the agreement of the system, and at least one copy should be kept; if the contents of the copies of the same file object are completely consiste...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com