Patents
Literature
76 results about "File Control Block" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
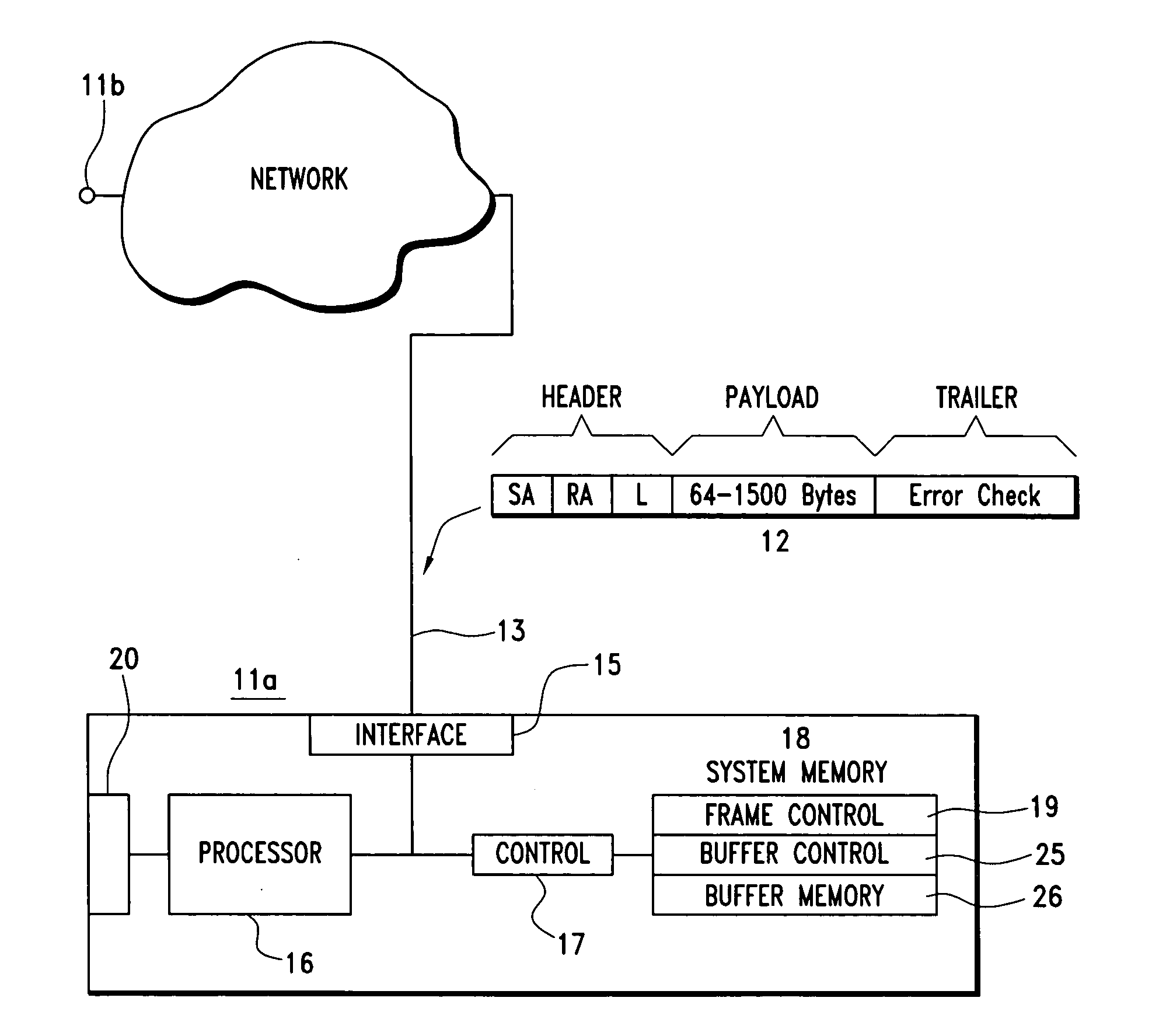
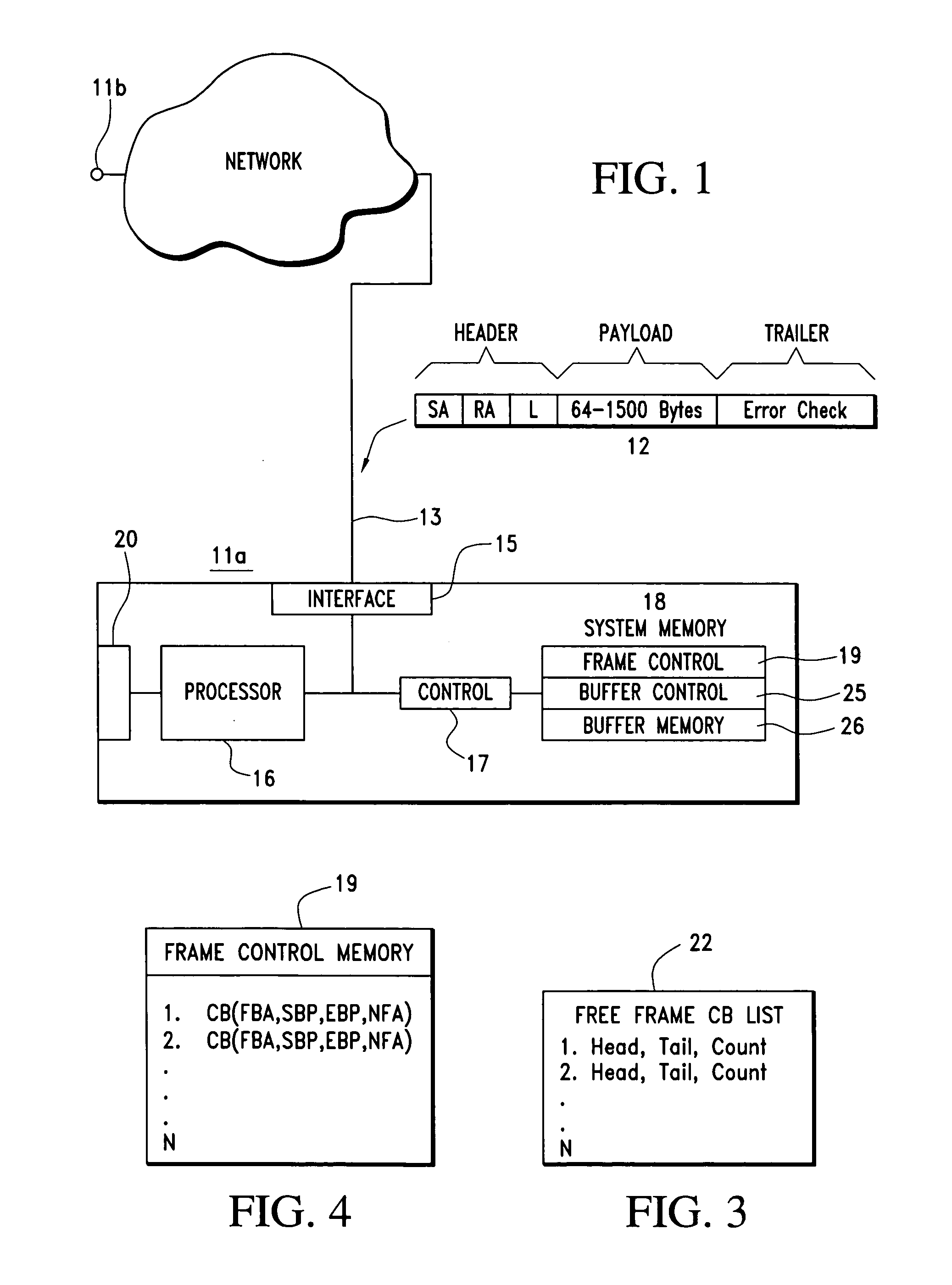
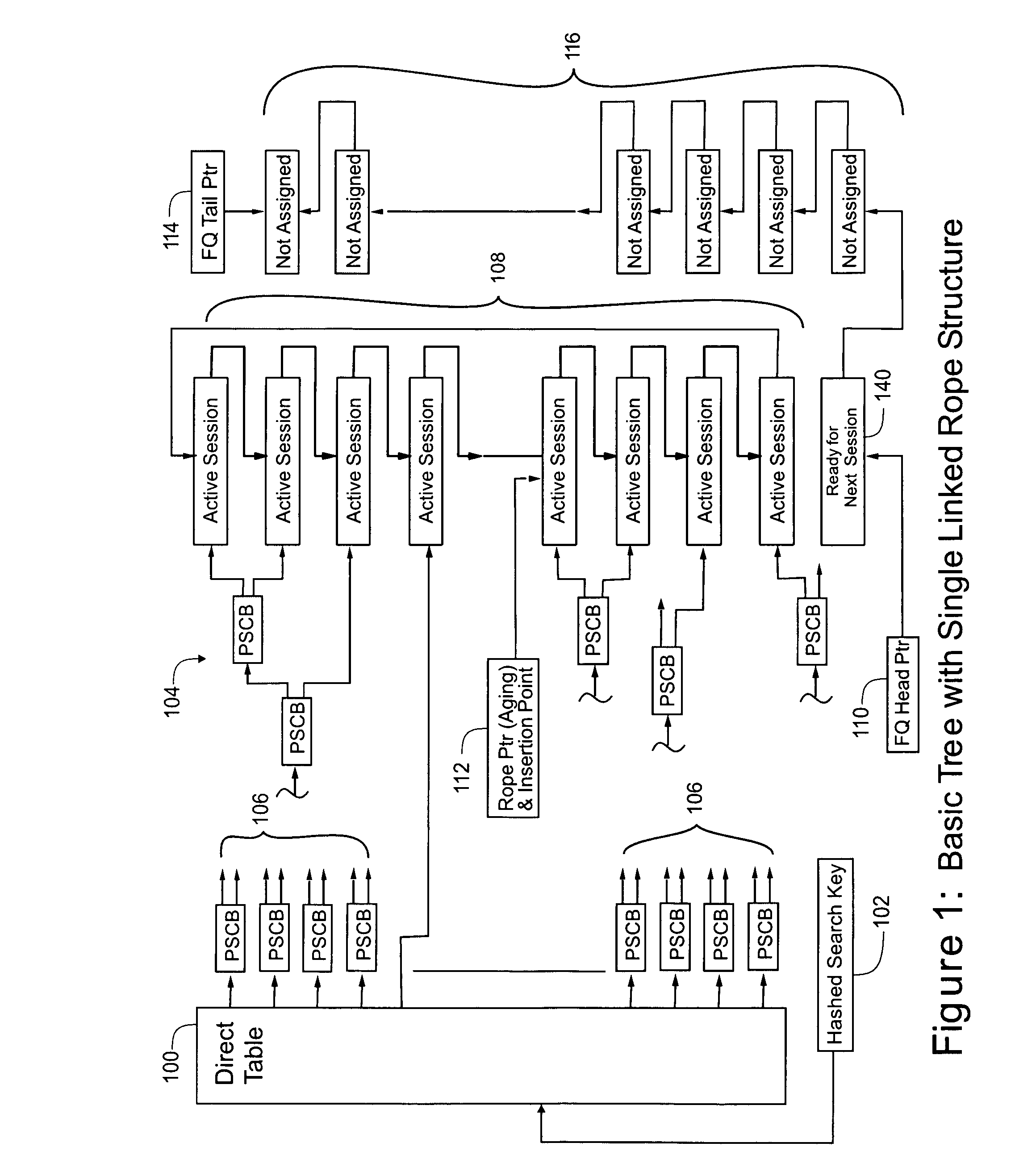
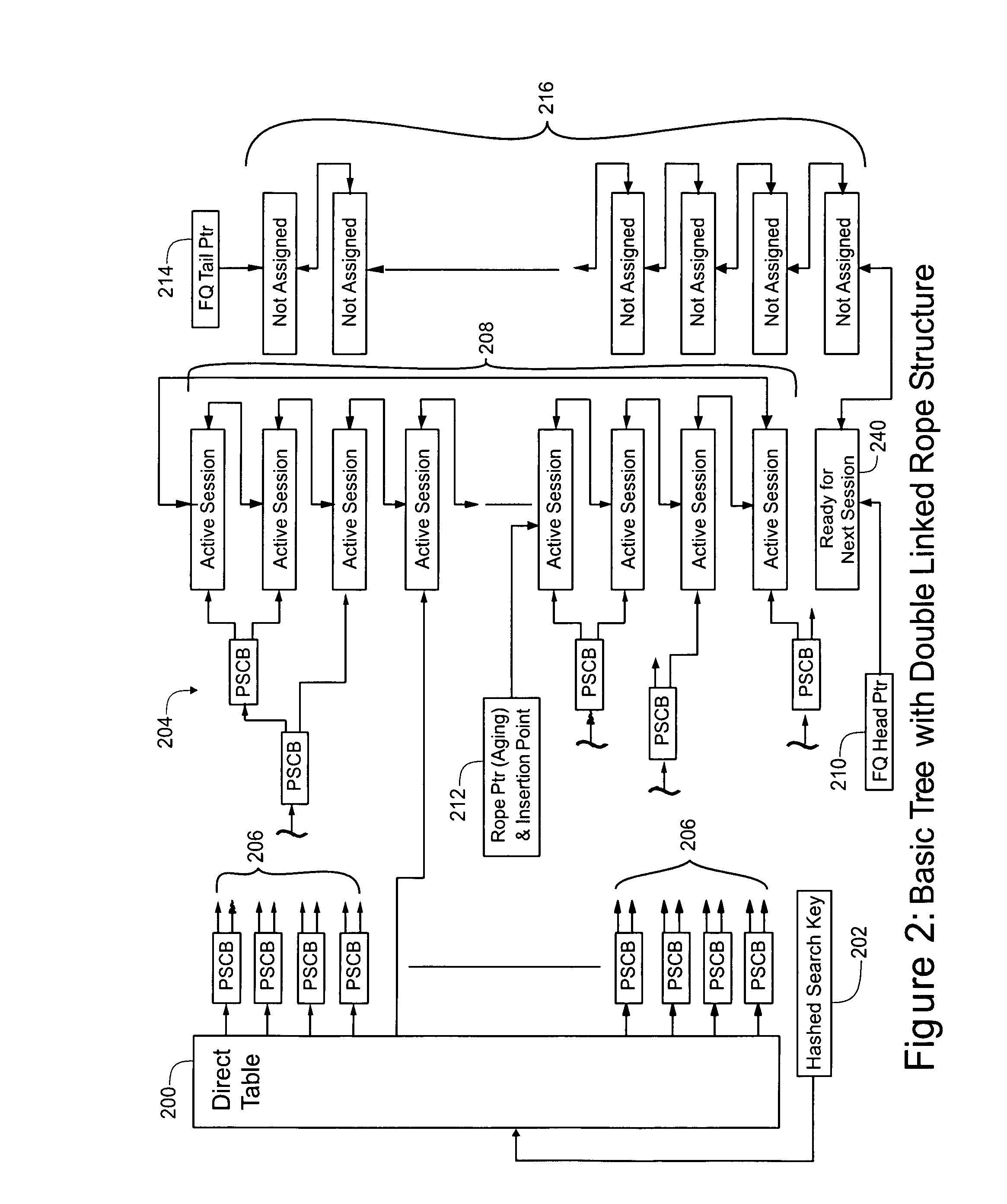
A File Control Block (FCB) is a file system structure in which the state of an open file is maintained. A FCB is managed by the operating system, but it resides in the memory of the program that uses the file, not in operating system memory. This allows a process to have as many files open at one time as it wants to, provided it can spare enough memory for an FCB per file.
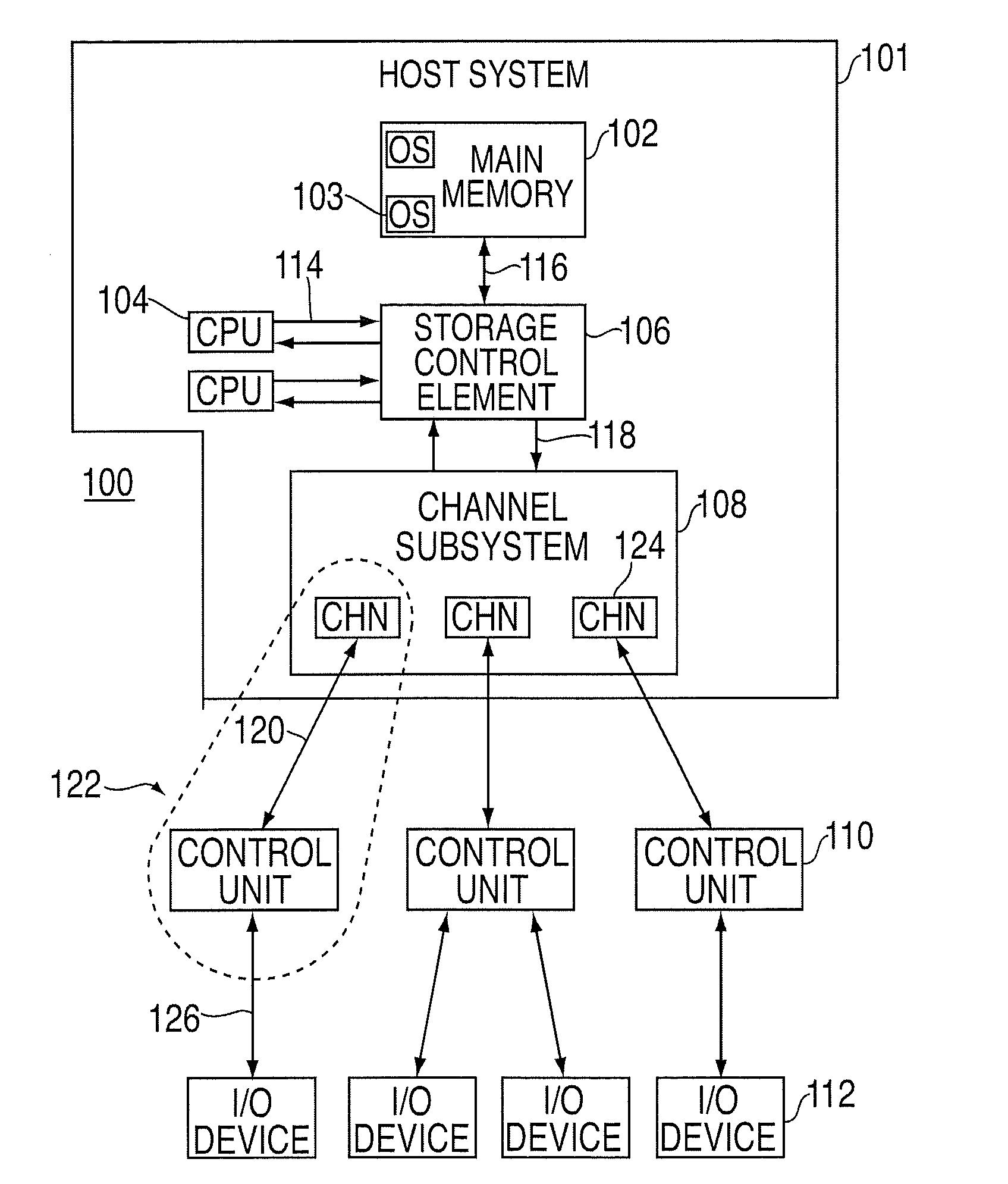
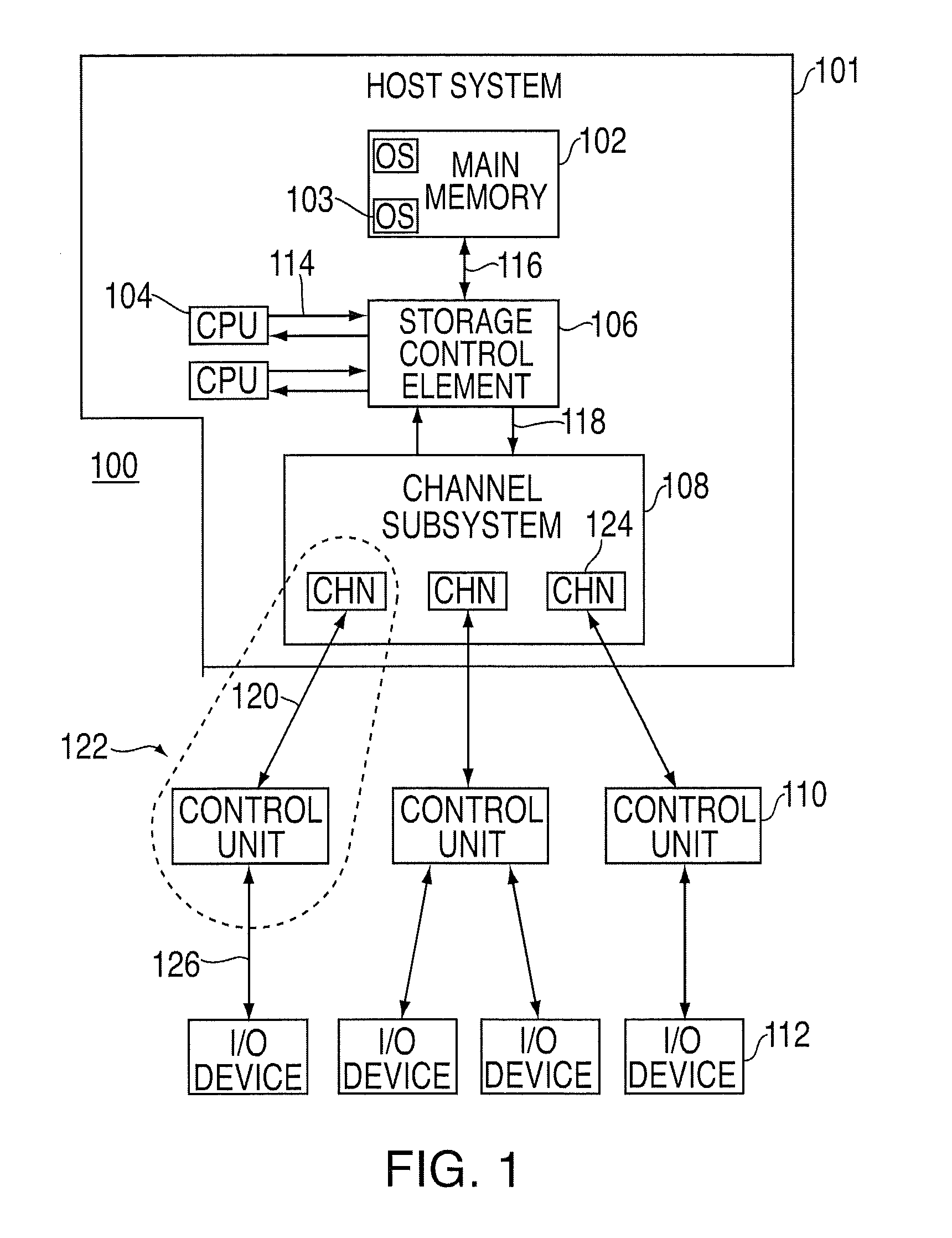
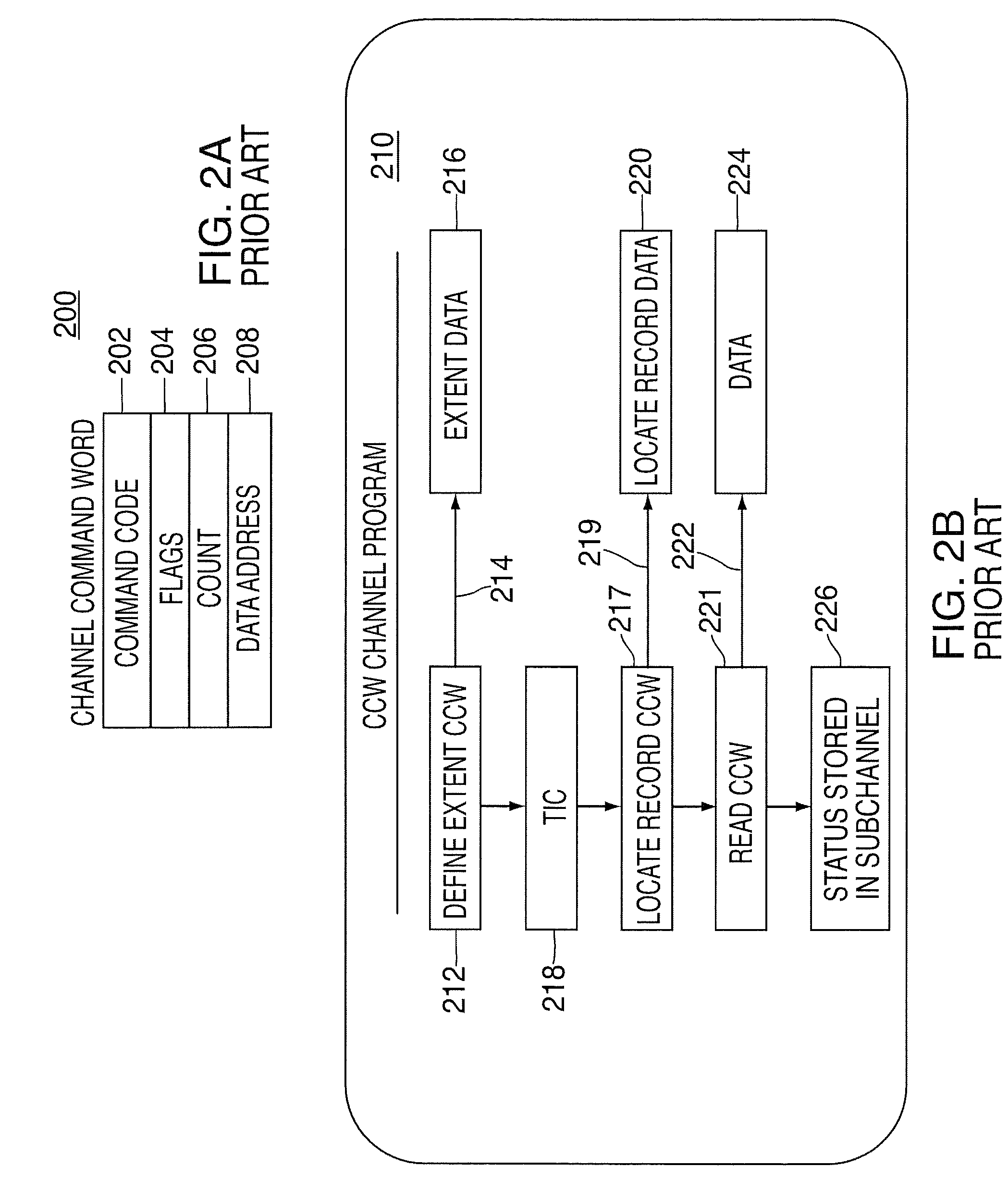
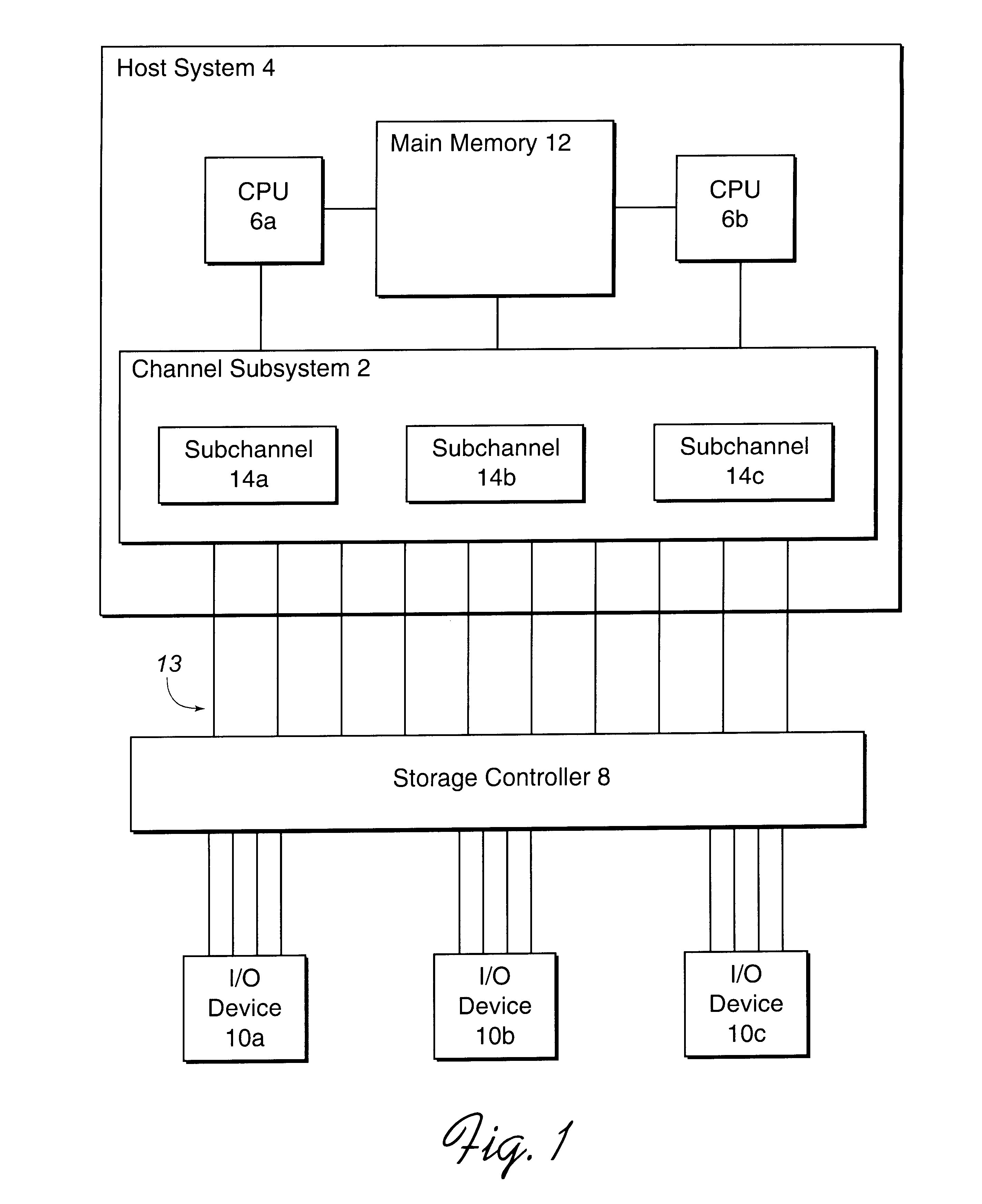
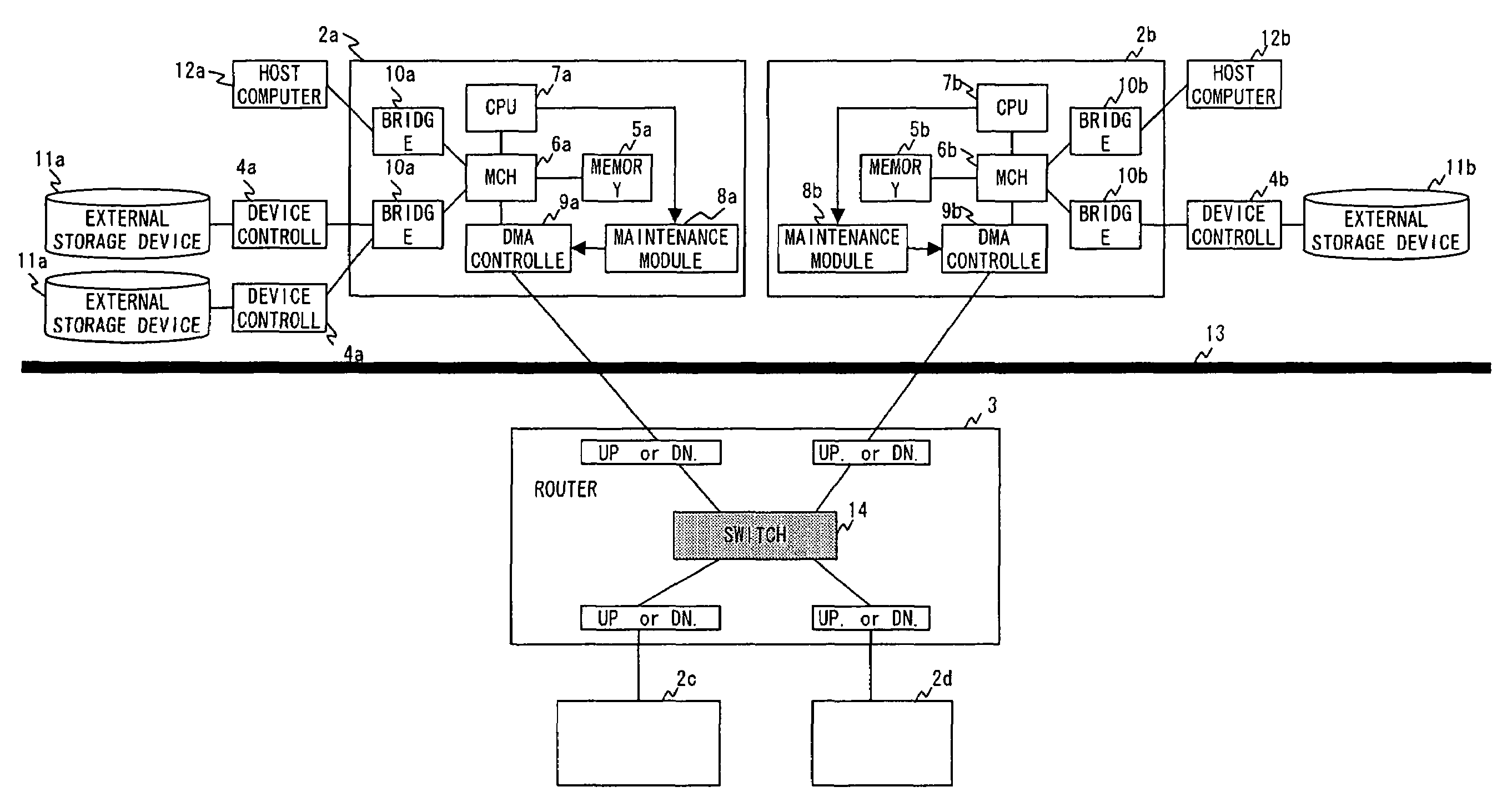
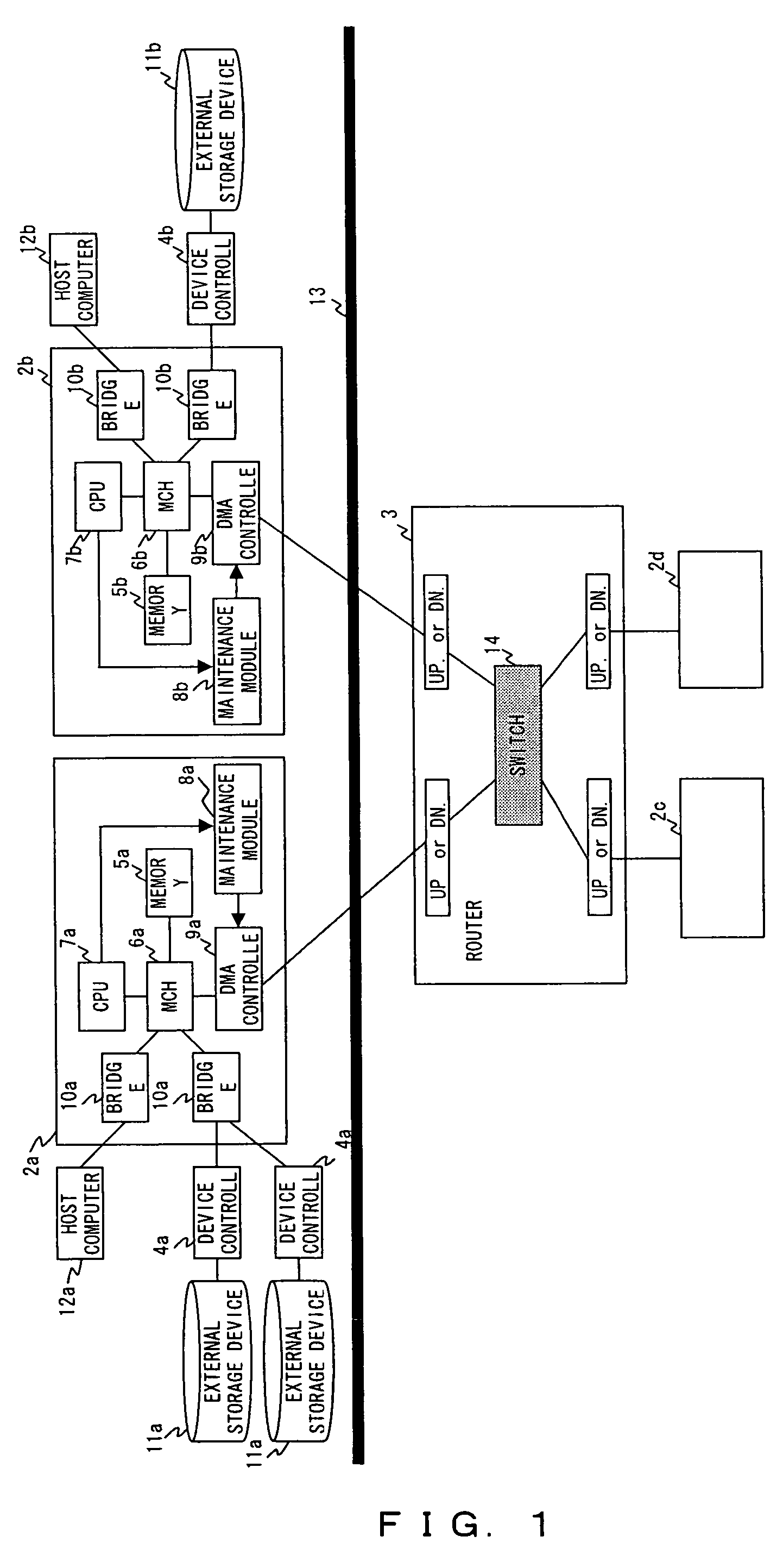
Providing indirect data addressing for a control block at a channel subsystem of an I/O processing system
ActiveUS20090210563A1Input/output processes for data processingComputerized systemFile Control Block
An computer program product, apparatus, and method for facilitating input / output (I / O) processing for an I / O operation at a host computer system configured for communication with a control unit. The computer program product includes a tangible storage medium readable by a processing circuit and storing instructions for execution by the processing circuit for performing a method. The method includes the host computer system obtaining a transport command word (TCW) for an I / O operation. The TCW specifies a location of one or more I / O commands and a flag. The flag is set to indicate that the location is an indirect address. The host computer system extracts the location of the one or more I / O commands and the flag from the TCW. The host computer system gathers the one or more I / O commands responsive to the location specified by the TCW and the flag, and then forwards the one or more I / O commands to the control unit for execution.
Owner:IBM CORP
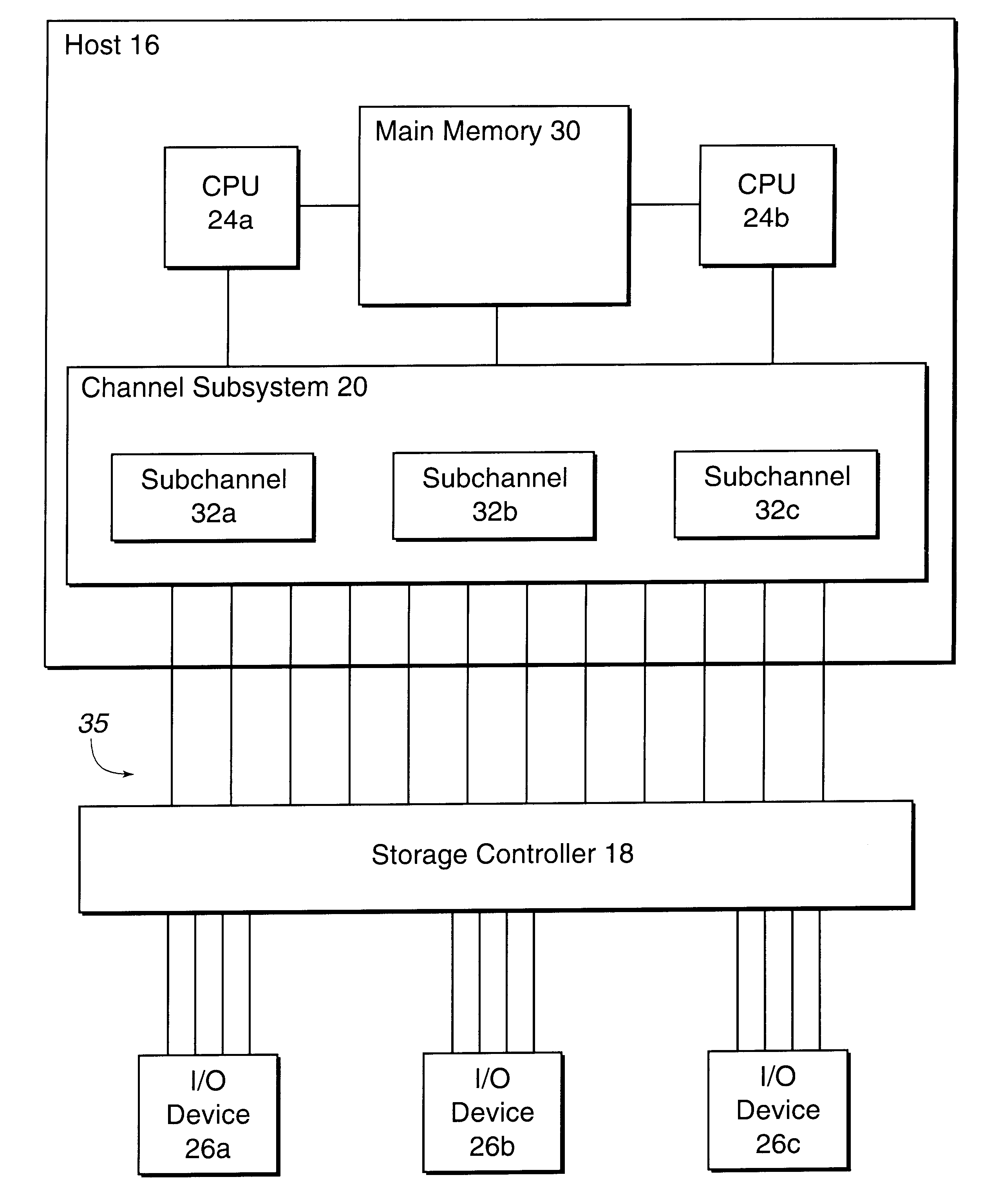
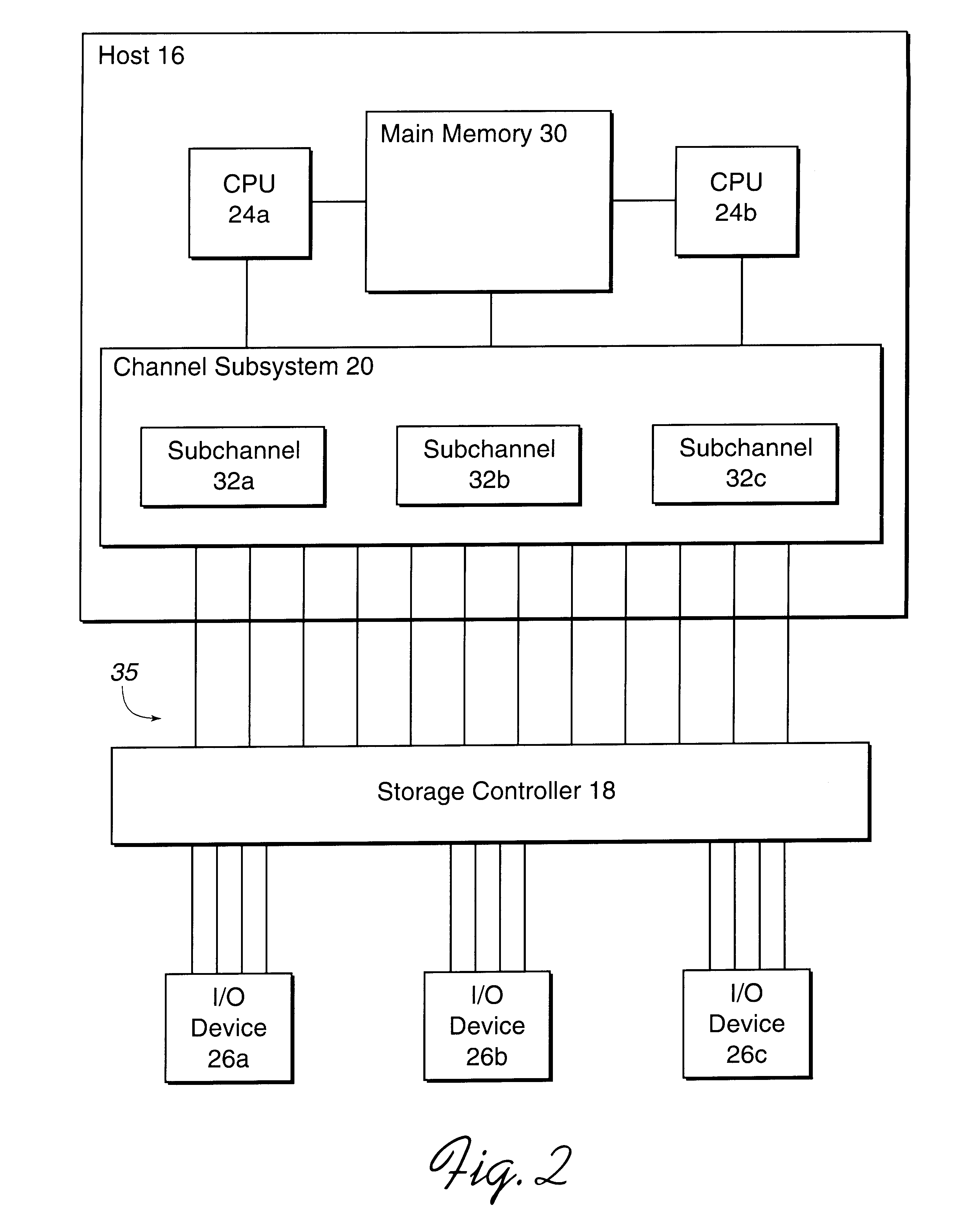
Method and system for dynamically assigning addresses to an input/output device
InactiveUS6185638B1Memory systemsInput/output processes for data processingDirect-access storage deviceComputerized system
Disclosed is a system for dynamically assigning alias addresses to base addresses referencing an I / O device, such as a direct access storage device (DASD). In the system, at least one base control block indicates a base address and a plurality of alias control blocks indicate a plurality of alias addresses. Each control block is associated with an address for addressing an I / O device. A processing unit, such as a host computer system, processes at least one alias control block associated with the I / O device and determines a base control block associated with the I / O device with which the alias control blocks are associated. The processing unit then binds at least one alias control block to the determined base control block. The bound base and alias control blocks provide different addresses to address the same I / O device. Further, the bound base and alias addresses address the same I / O device for subsequent I / O operations until the processing unit detects a reassignment of the association of base and alias addresses.
Owner:IBM CORP
Secure multi-party protocol
A requestor and a responder may conduct secure communication by making API calls based on a secure multi-party protocol. The requestor may send a request data packet sent in a API request to the responder, where the request data packet can include at least a control block that is asymmetrically encrypted and a data block that is symmetrically encrypted. The responder may return a response data packet to the requestor, where the response data packet can include at least a control block and a data block that are both symmetrically encrypted. The requestor and the responder may derive the keys for decrypting the encrypted portions of the request and response data packets based on some information only known to the requestor and the responder. The secure multi-party protocol forgoes the need to store and manage keys in a hardware security module.
Owner:VISA INT SERVICE ASSOC
Method for controlling access to encrypted content using multiple broadcast encryption based control blocks
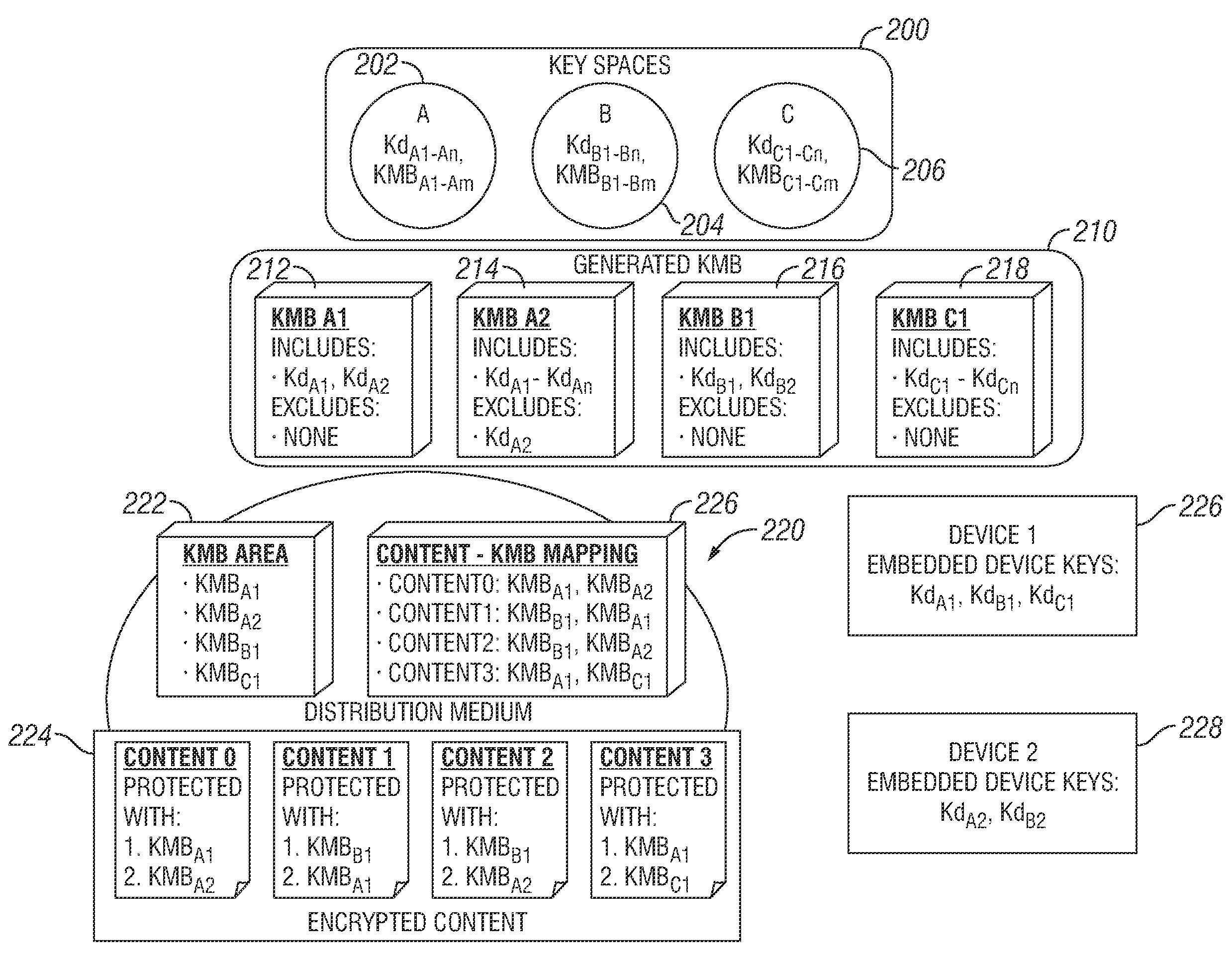
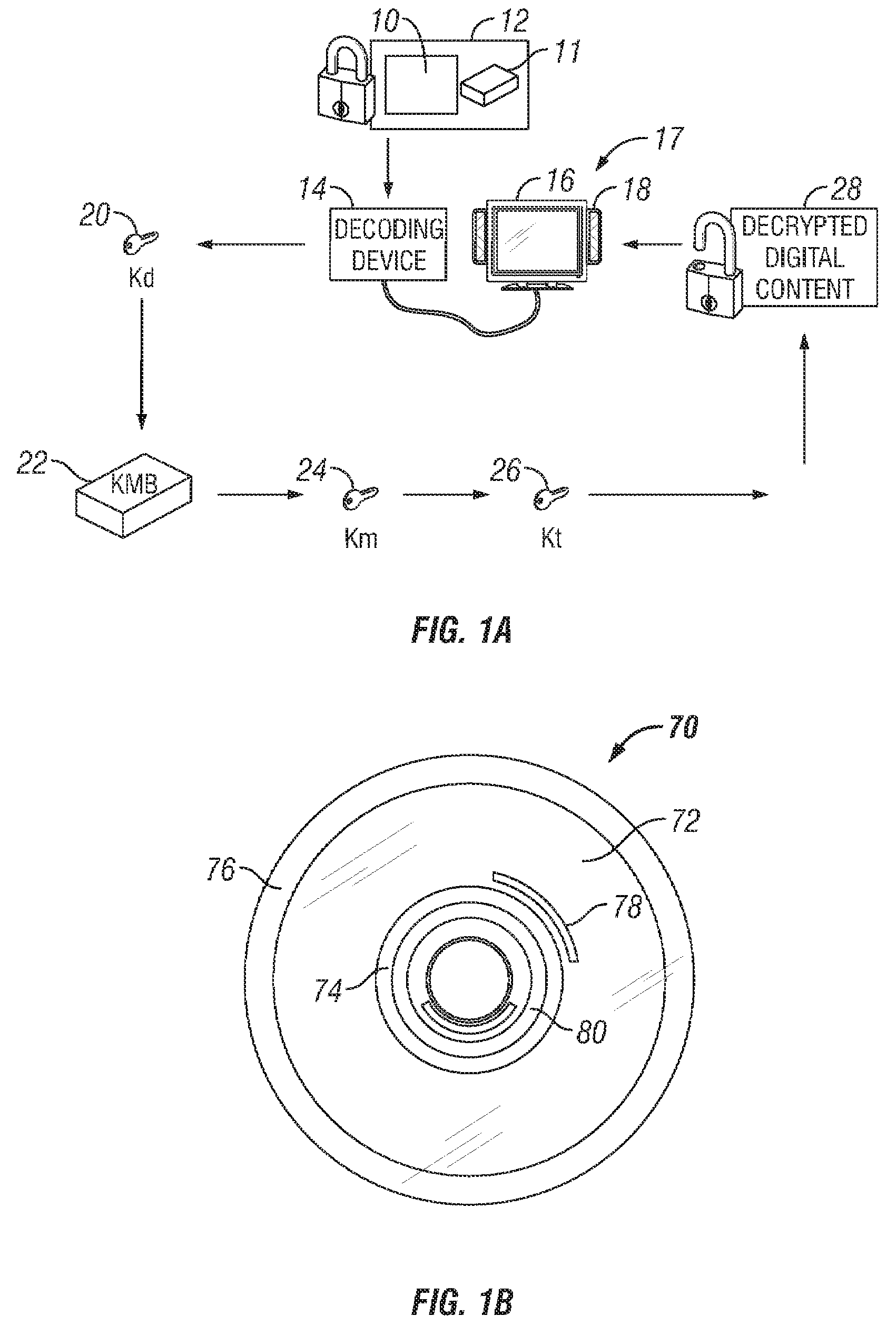
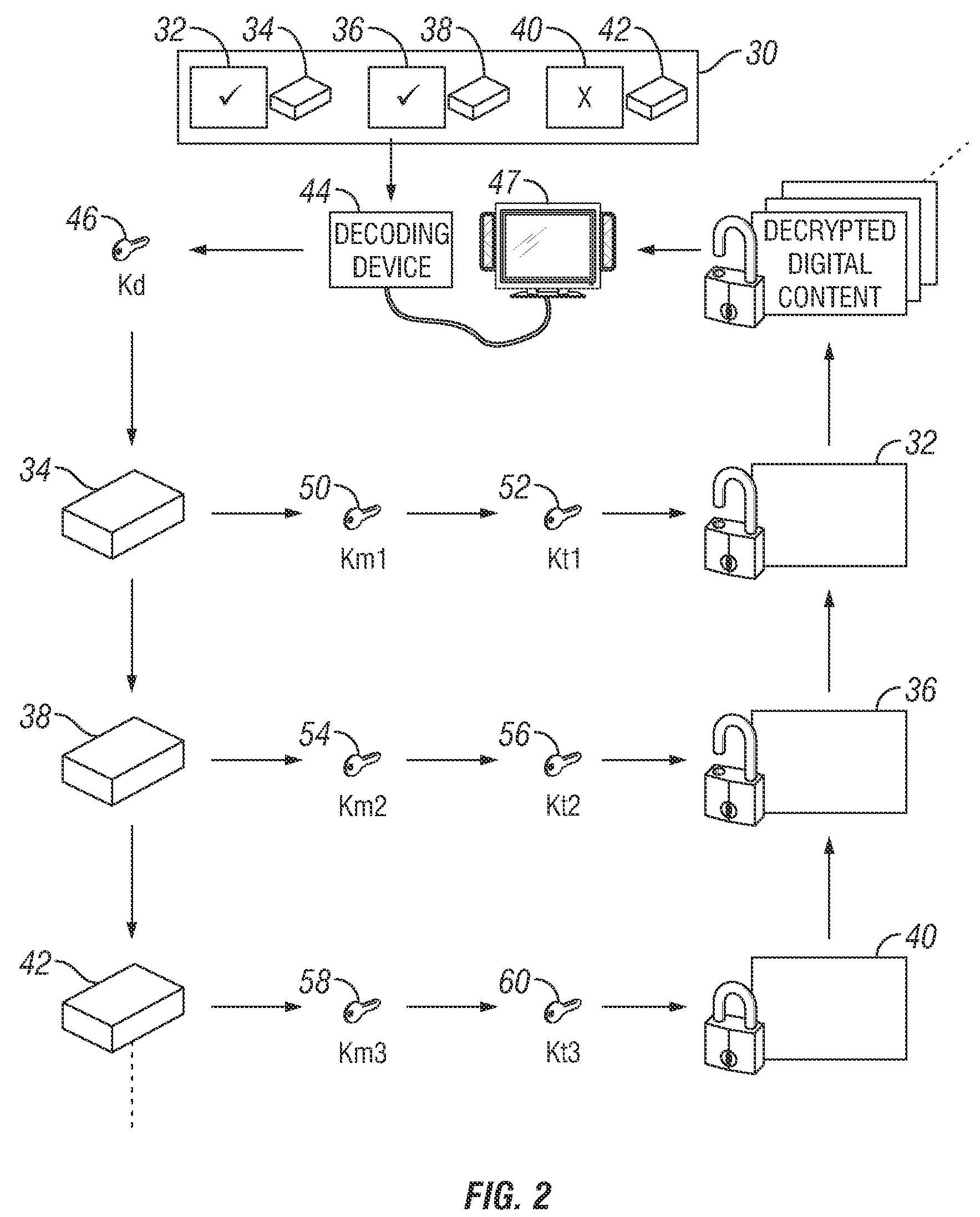
An apparatus and a method are provided for selectively accessing digital content carried on a distribution medium such as a physical medium or a broadcast medium. In one embodiment, a plurality of digital content items are encrypted under a plurality of different key management blocks, wherein each key management block is associated with a different set of device keys. The plurality of content items may be provided together on a single distribution medium to devices having assigned device keys, so that devices may selectively access content as determined by the different key management block used to encrypt the various content items and by the device keys assigned to the devices. Depending on the association between the device key and the key management blocks, the decoding device may decode all of the content items, some of the content items, or none of the content items. To provide greater security, each content item may be multiple encrypted using multiple key management blocks per content item.
Owner:IBM CORP
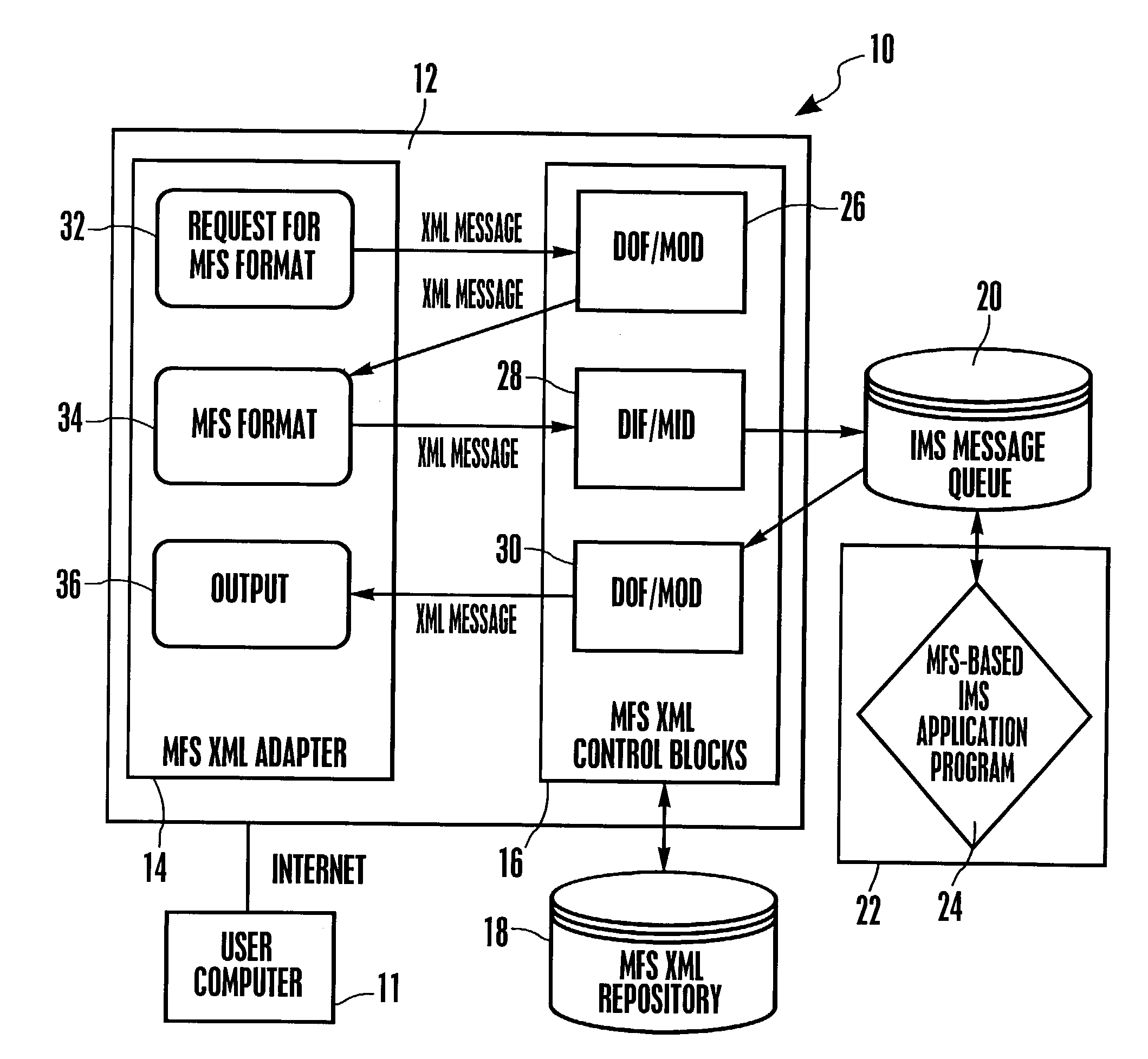
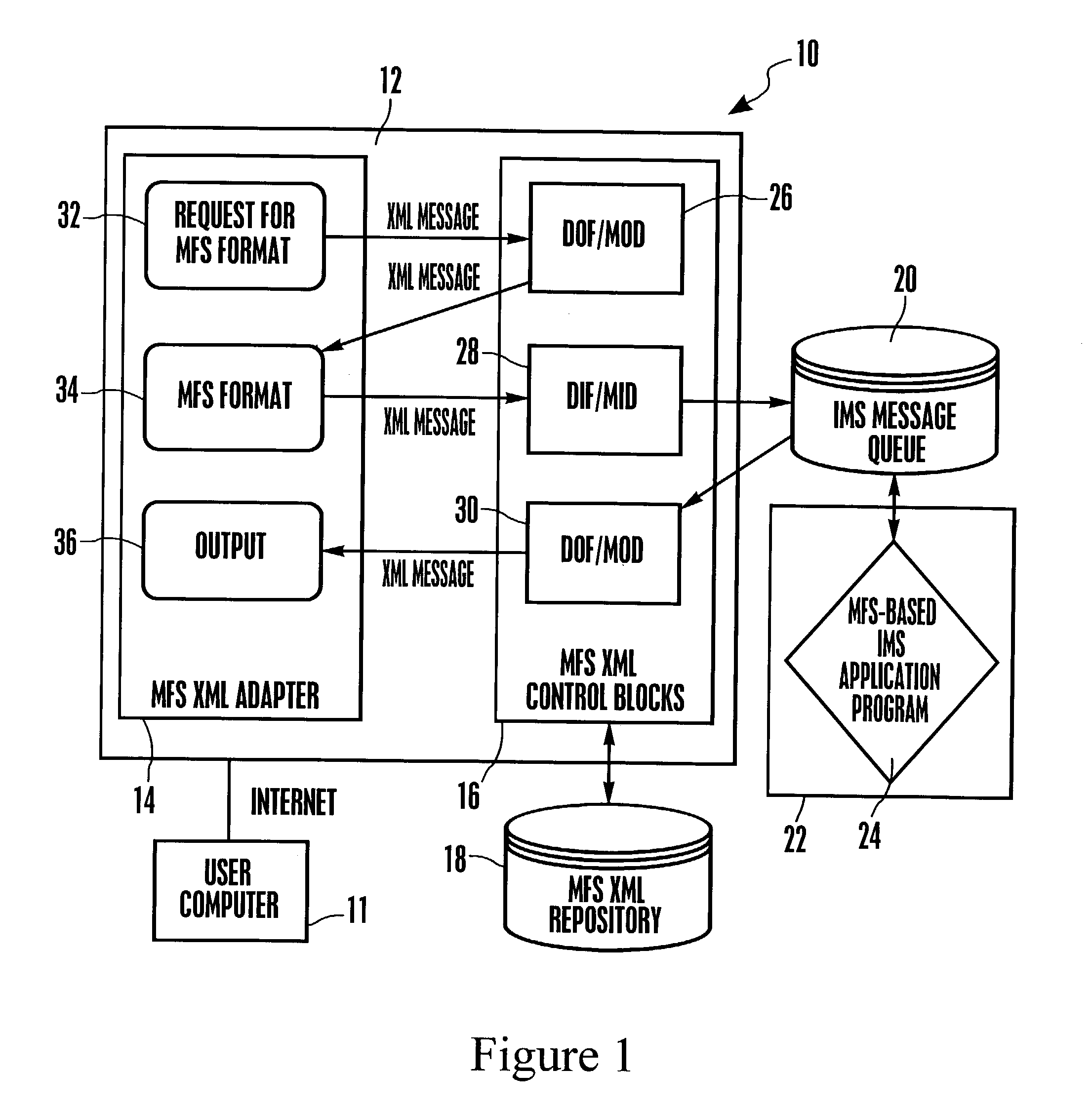
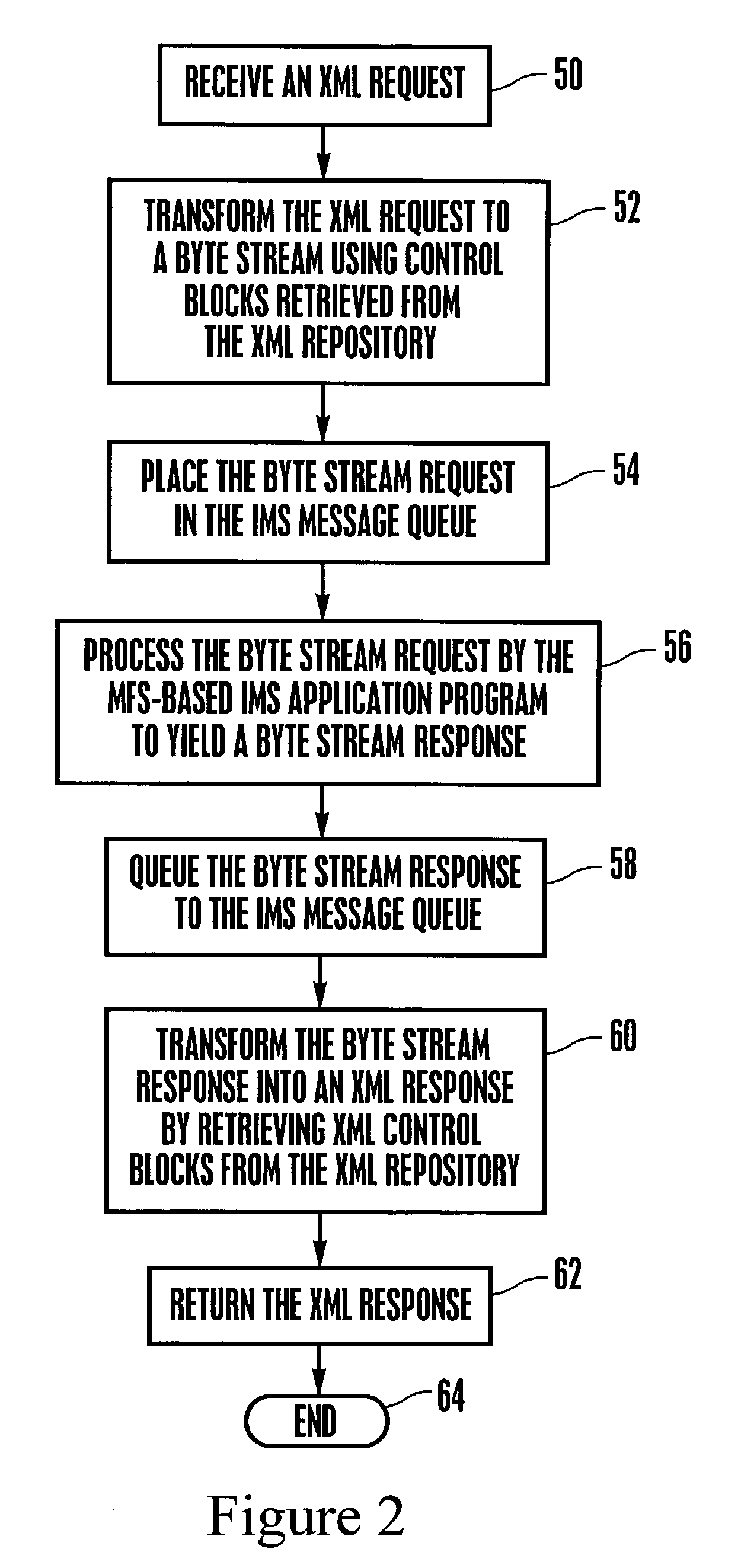
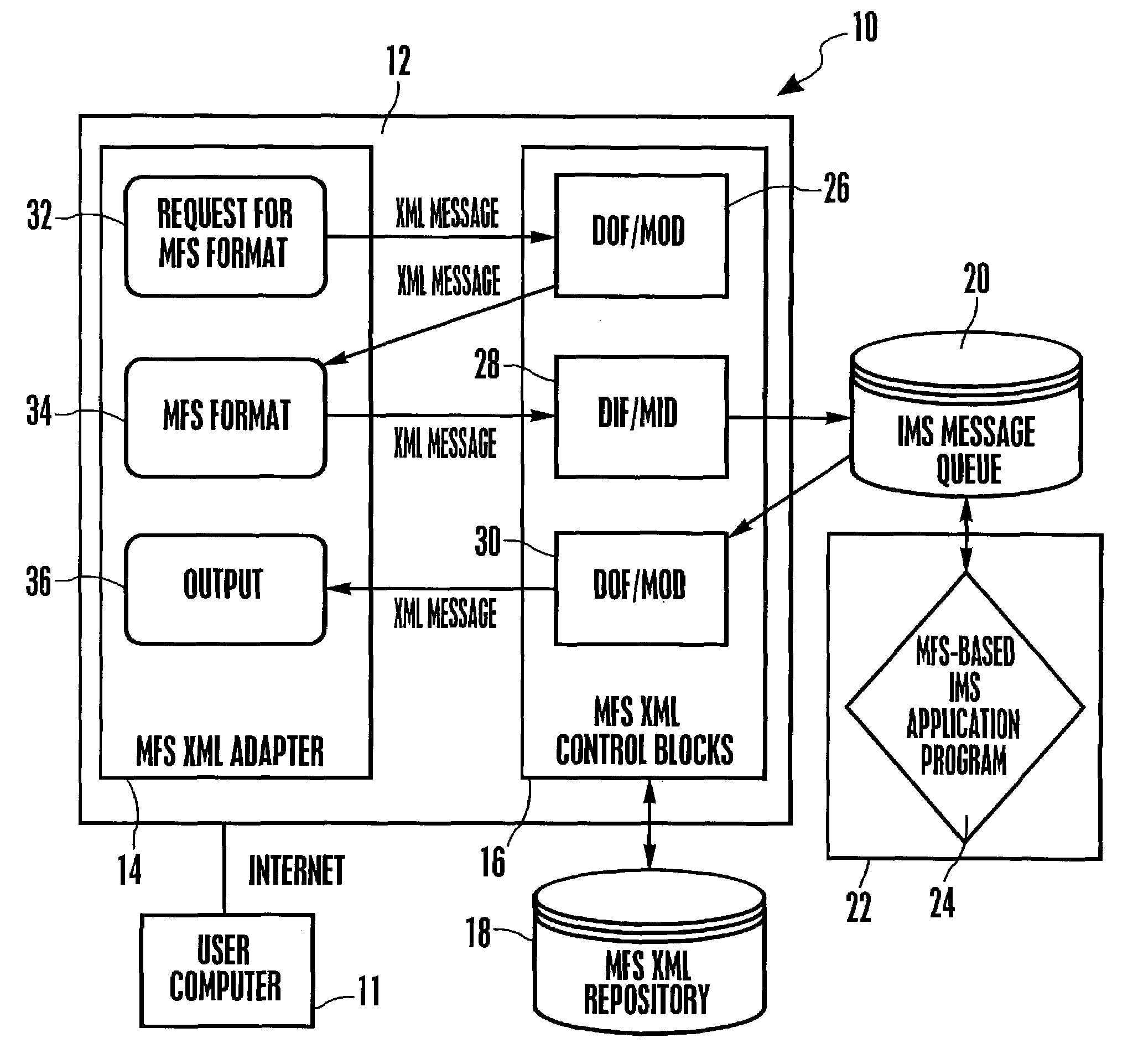
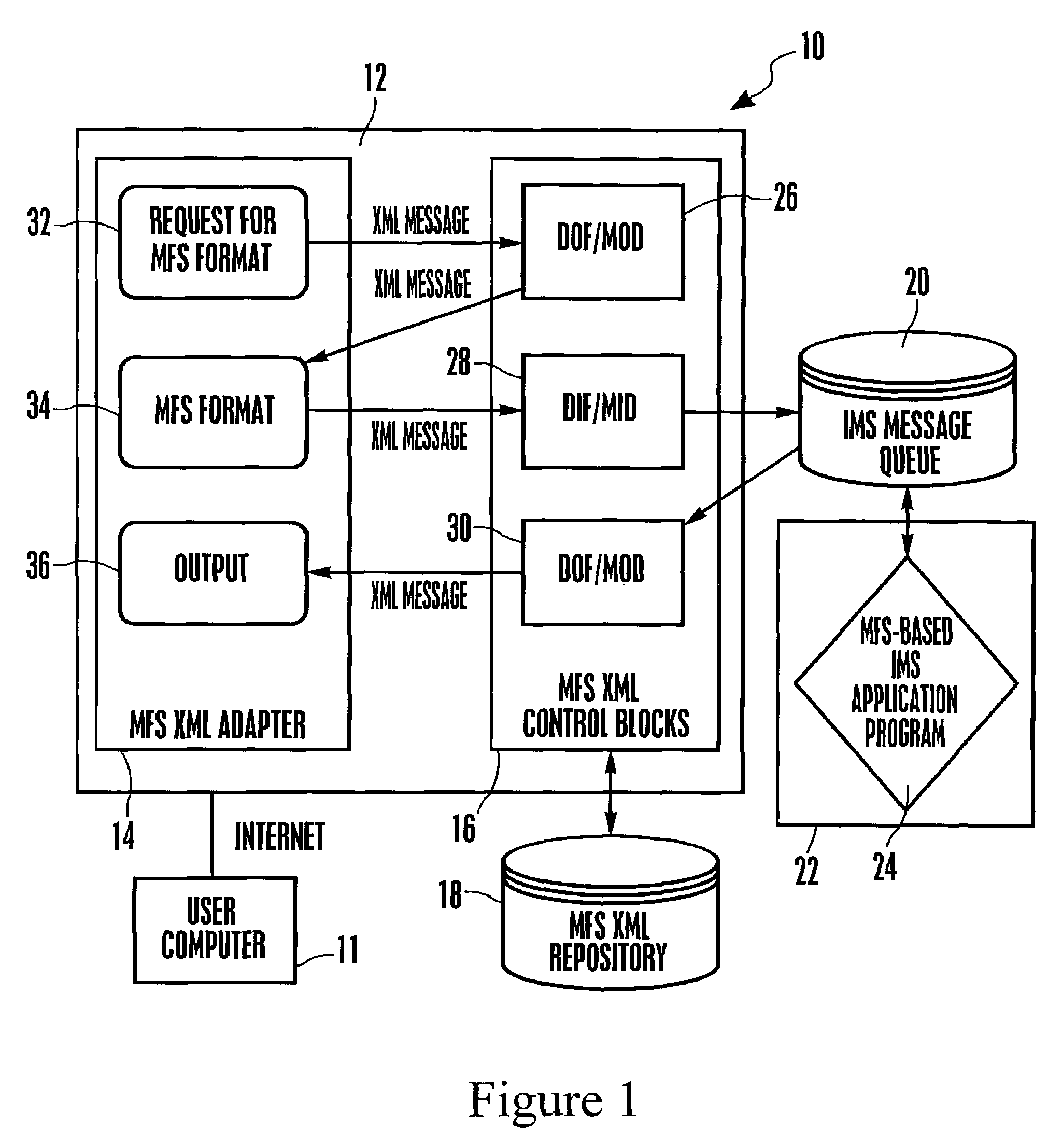
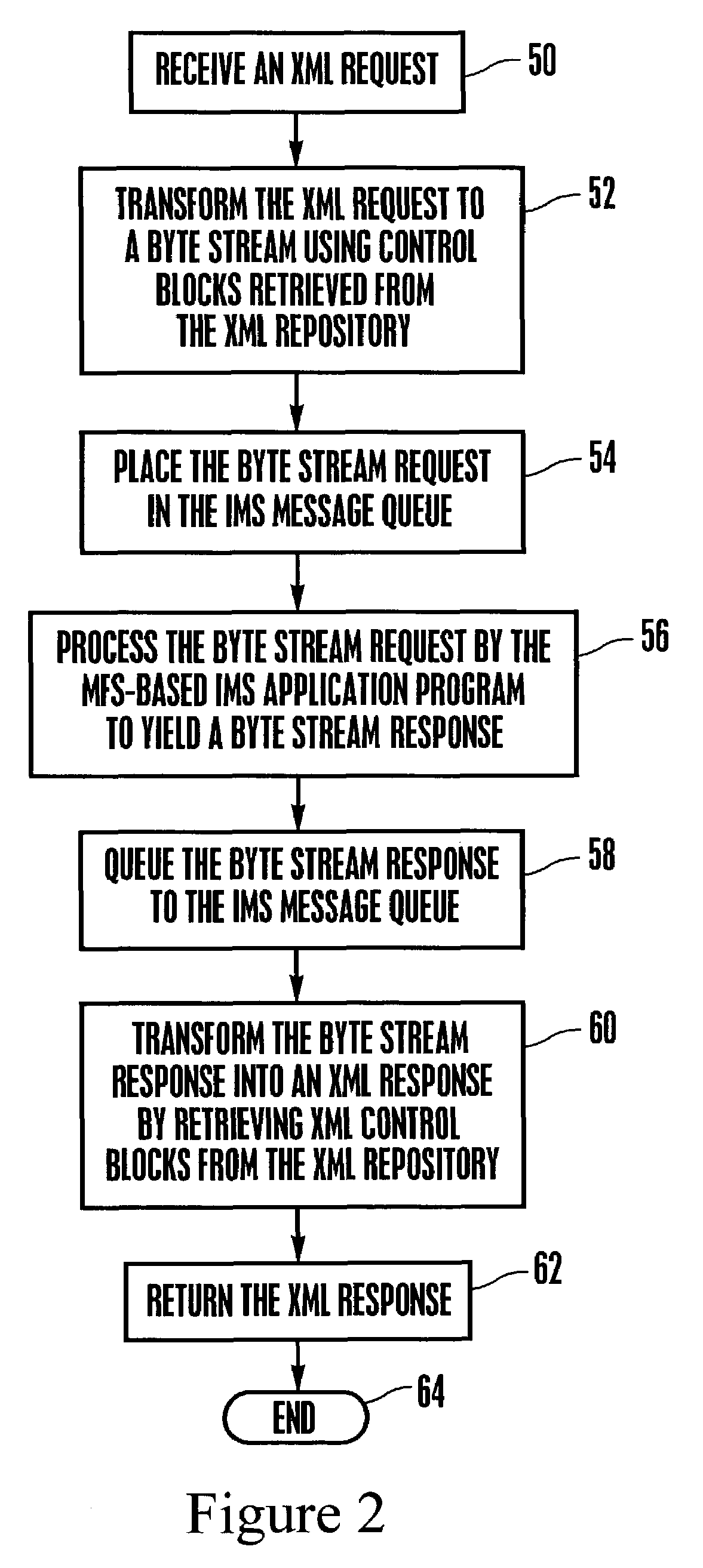
System and method for representing MFS control blocks in XML for MFS-based IMS applications
InactiveUS20040237034A1Digital computer detailsNatural language data processingMessage queueRelevant information
A system and method for representing MFS control blocks in XML for MFS-based IMS applications utilizes an MFS XML adapter and an MFS XML repository to translate between XML and MFS. The repository contains XML files for DOF / MOD and XML files for DIF / MID. When an XML request is received, the XML request is transformed to a byte stream by retrieving the relevant information from the MFS XML repository. The byte stream can then be placed in an IMS message queue to await processing by an MFS-based IMS application program. A byte stream response is generated by the MFS-based IMS application and is transformed into an XML response, again, by retrieving the relevant information from the MFS XML repository.
Owner:IBM CORP
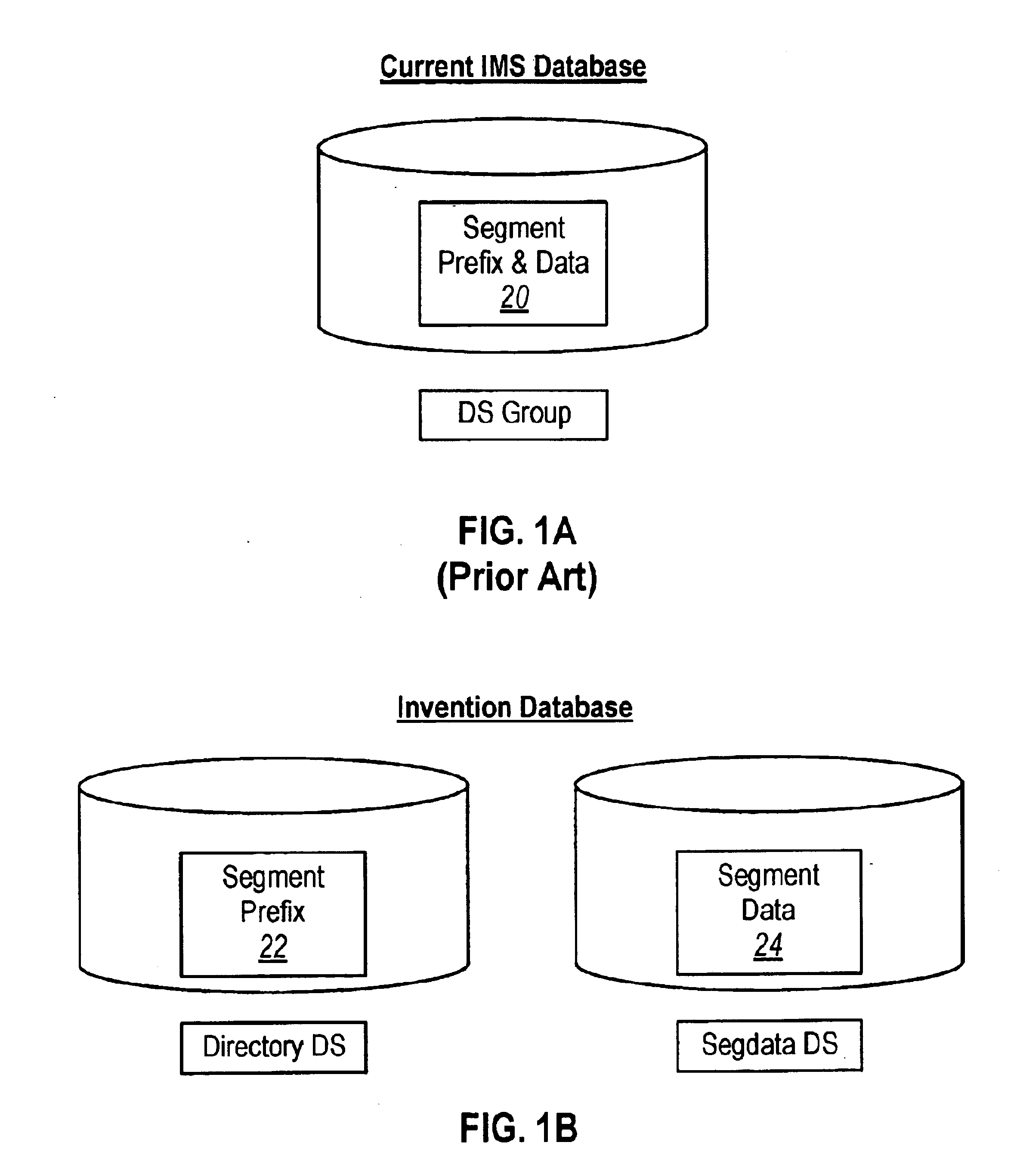
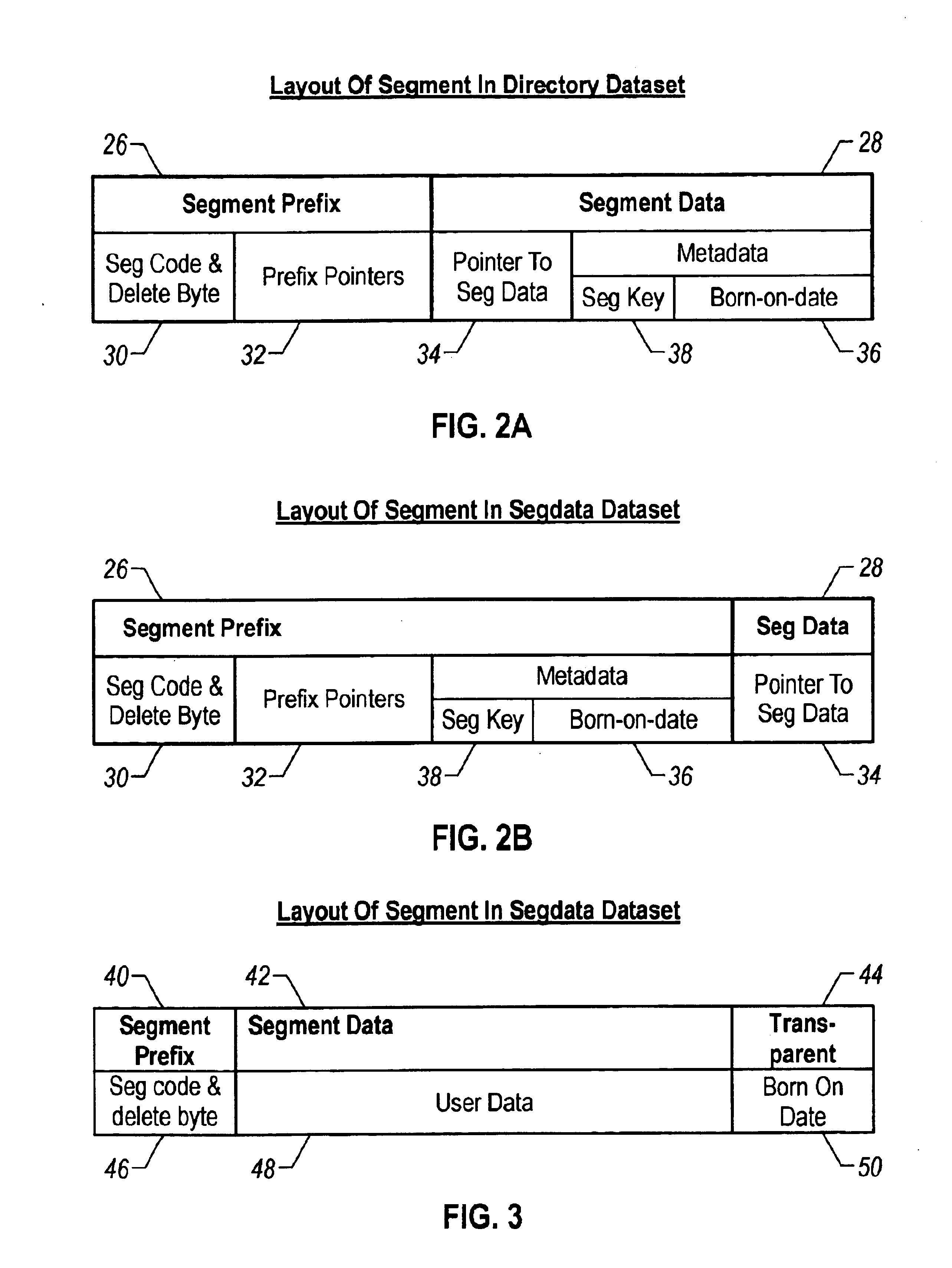
Space management of an IMS database
InactiveUS6879986B1Easy maintenanceExpand databaseData processing applicationsDigital data information retrievalMemory addressUnit Control Block
Space within an IMS database can be managed during loading or updating of the database. After an IMS database is loaded, a space management program can assume control from the IMS program for a period of time. During this period of time, the space management program obtains memory addresses of IMS control blocks built by the IMS program and further obtains information about the IMS database. When the IMS program attempts to insert data into the IMS database, either during loading or updating of the database, the space management program reassumes control from the IMS program. The space management program selects a storage location for the data to be stored, and modifies the IMS control blocks to indicate the storage location selected. The space management program may also insert the data into the storage locations selected. Control is then passed back to the IMS program. If segments are to be inserted into the IMS database, and such segments are to be split, then the space management program selects two storage locations for the components of the split segment to be stored. The storage locations selected by the space management program are selected based on IMS database user preferences.
Owner:NEON ENTERPRISE SOFTWARE
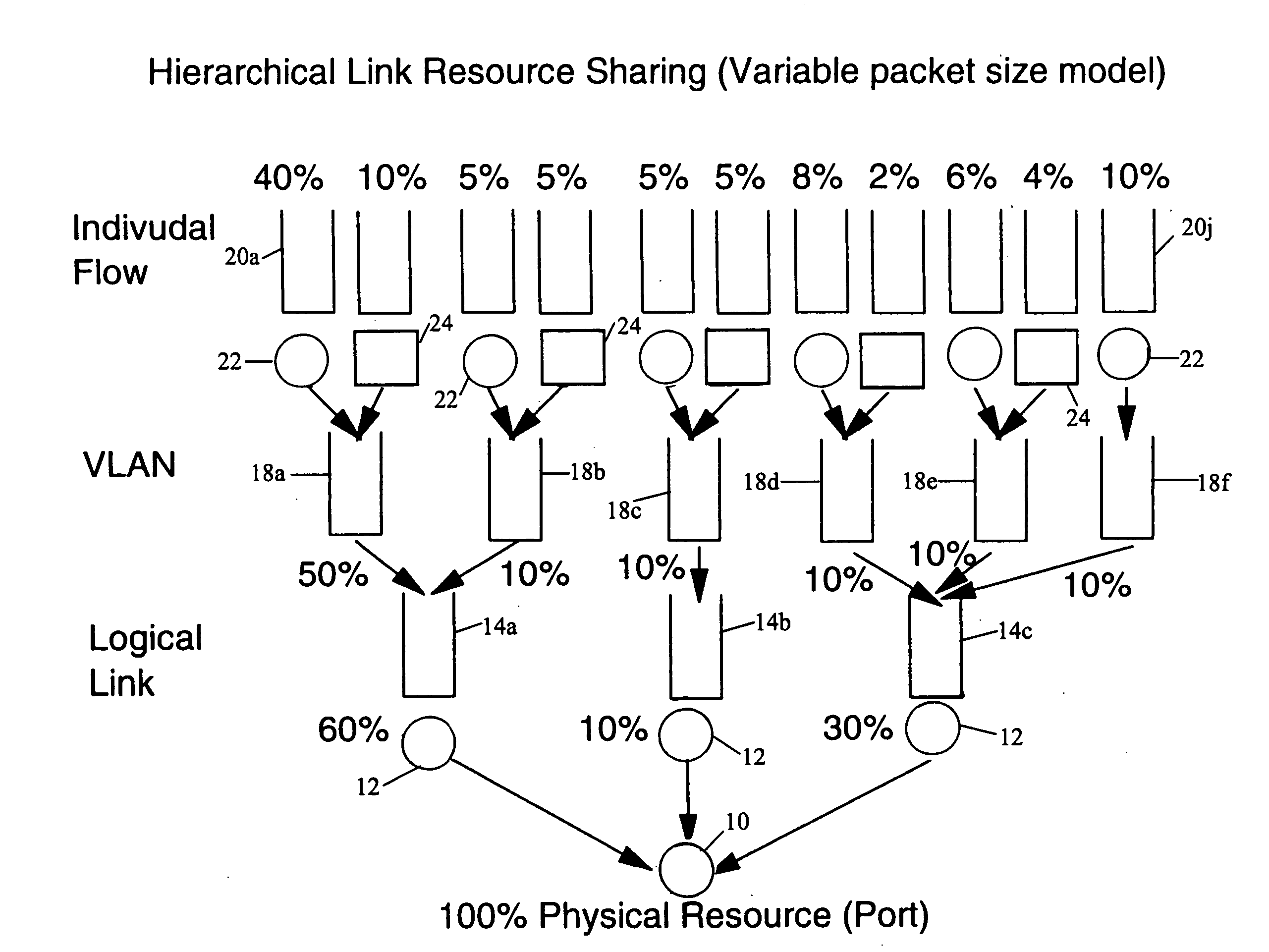
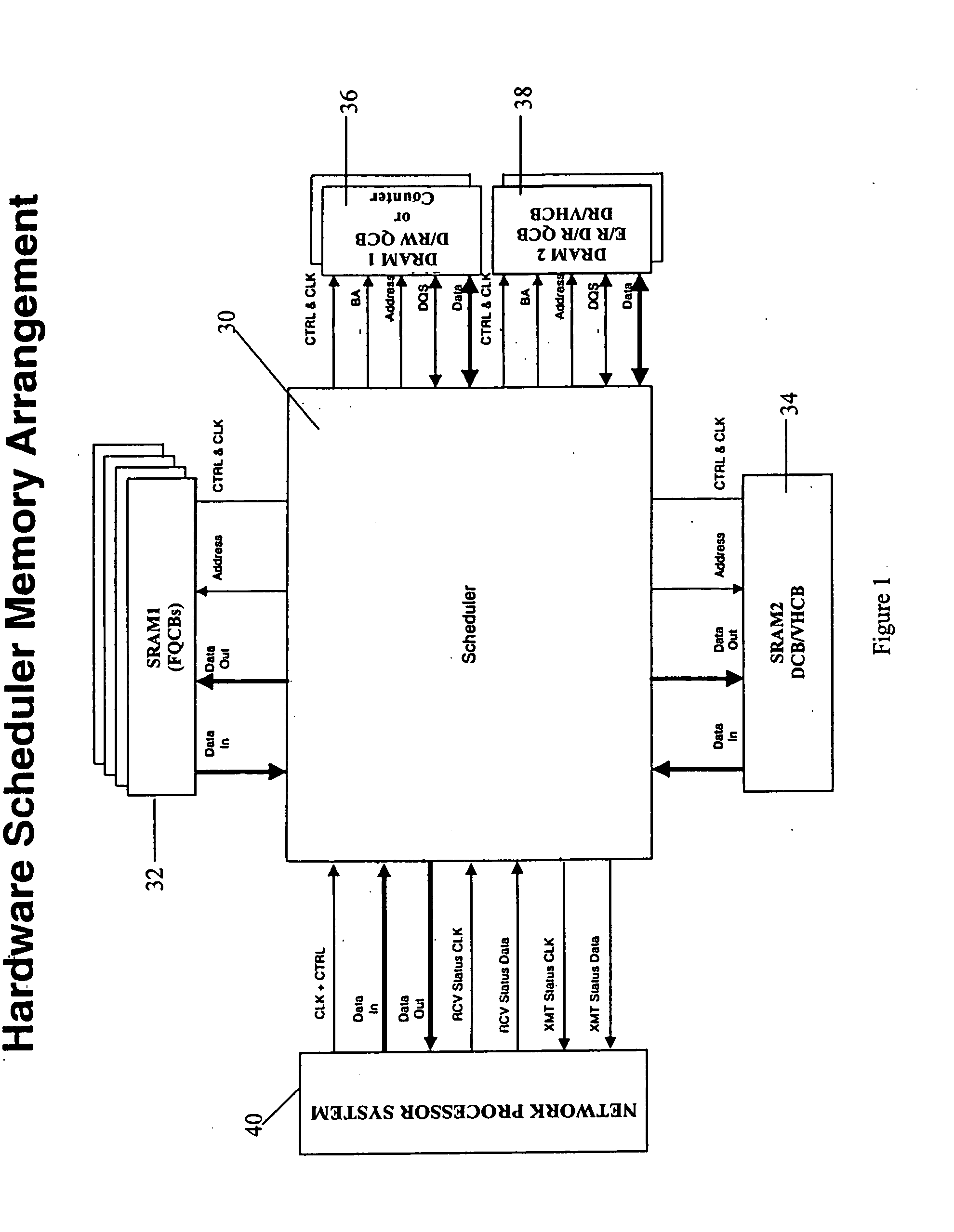
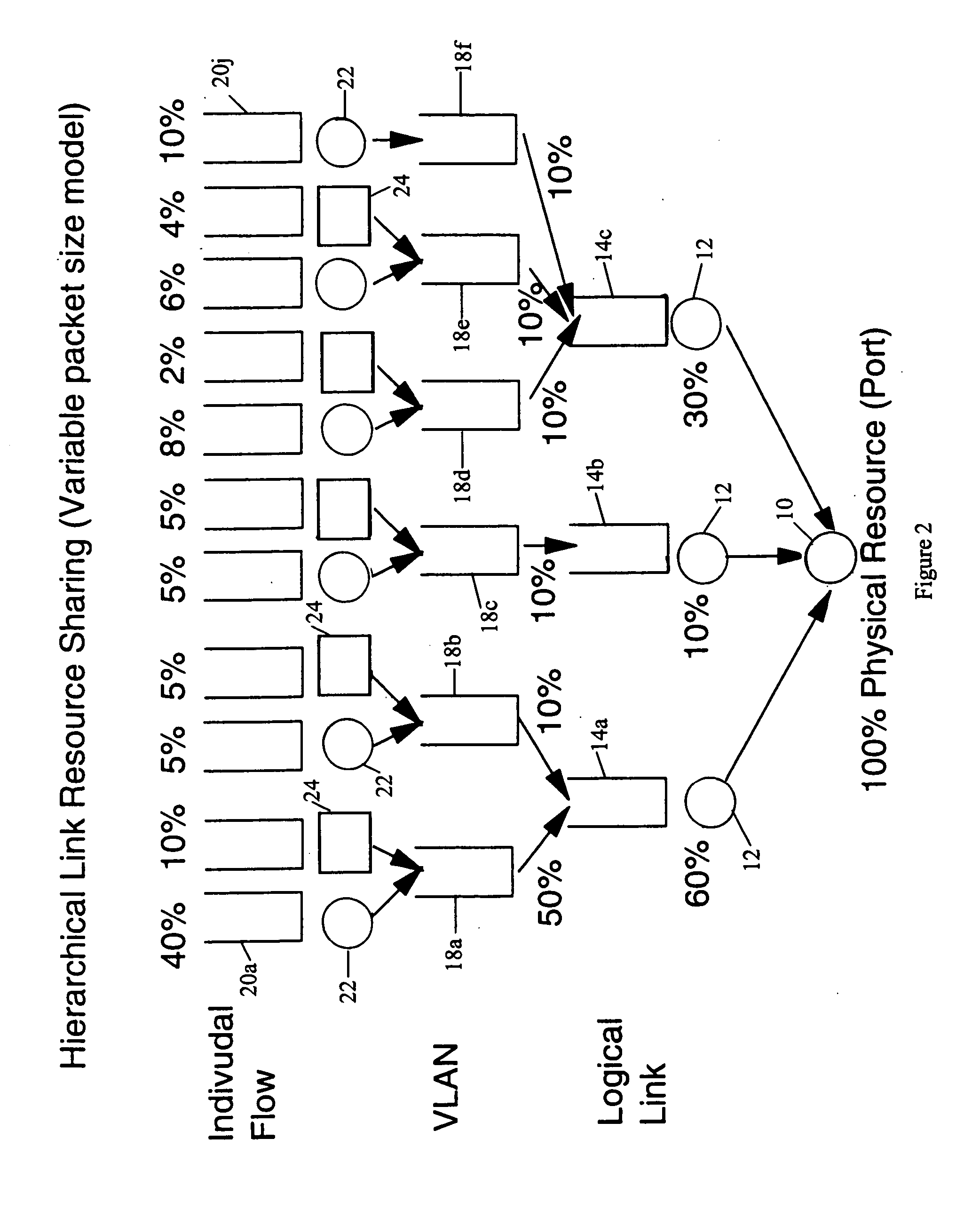
Structure and method for scheduler pipeline design for hierarchical link sharing
InactiveUS20050177644A1Reduce in quantityMultiple digital computer combinationsData switching networksTraffic capacityExternal storage
A pipeline configuration is described for use in network traffic management for the hardware scheduling of events arranged in a hierarchical linkage. The configuration reduces costs by minimizing the use of external SRAM memory devices. This results in some external memory devices being shared by different types of control blocks, such as flow queue control blocks, frame control blocks and hierarchy control blocks. Both SRAM and DRAM memory devices are used, depending on the content of the control block (Read-Modify-Write or ‘read’ only) at enqueue and dequeue, or Read-Modify-Write solely at dequeue. The scheduler utilizes time-based calendars and weighted fair queueing calendars in the egress calendar design. Control blocks that are accessed infrequently are stored in DRAM memory while those accessed frequently are stored in SRAM.
Owner:IBM CORP
System and method for representing MFS control blocks in XML for MFS-based IMS applications
InactiveUS7130893B2Natural language data processingMultiple digital computer combinationsMessage queueRelevant information
A system and method for representing MFS control blocks in XML for MFS-based IMS applications utilizes an MFS XML adapter and an MFS XML repository to translate between XML and MFS. The repository contains XML files for DOF / MOD and XML files for DIF / MID. When an XML request is received, the XML request is transformed to a byte stream by retrieving the relevant information from the MFS XML repository. The byte stream can then be placed in an IMS message queue to await processing by an MFS-based IMS application program. A byte stream response is generated by the MFS-based IMS application and is transformed into an XML response, again, by retrieving the relevant information from the MFS XML repository.
Owner:IBM CORP
Semiconductor device and multilayer semiconductor device
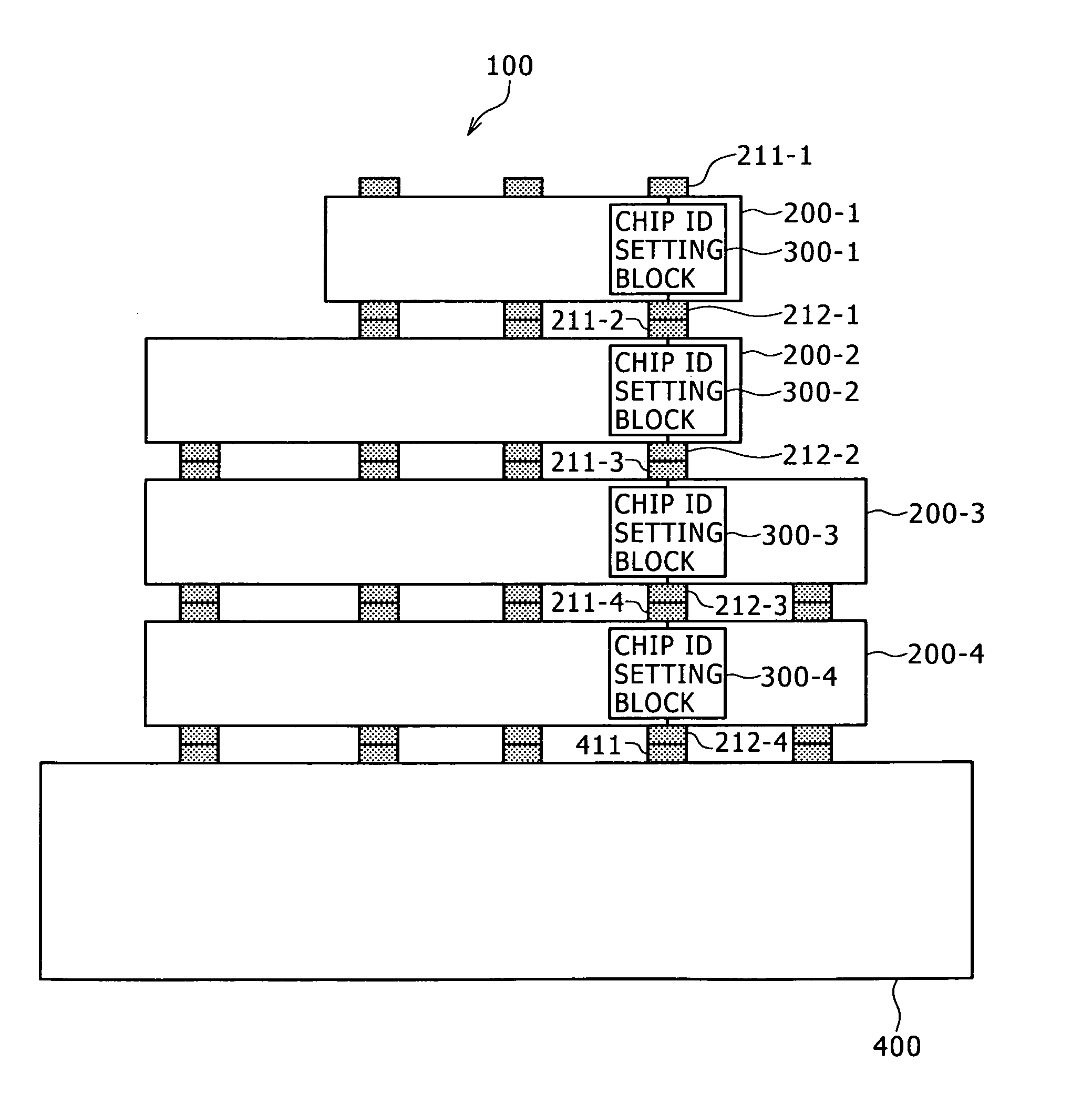
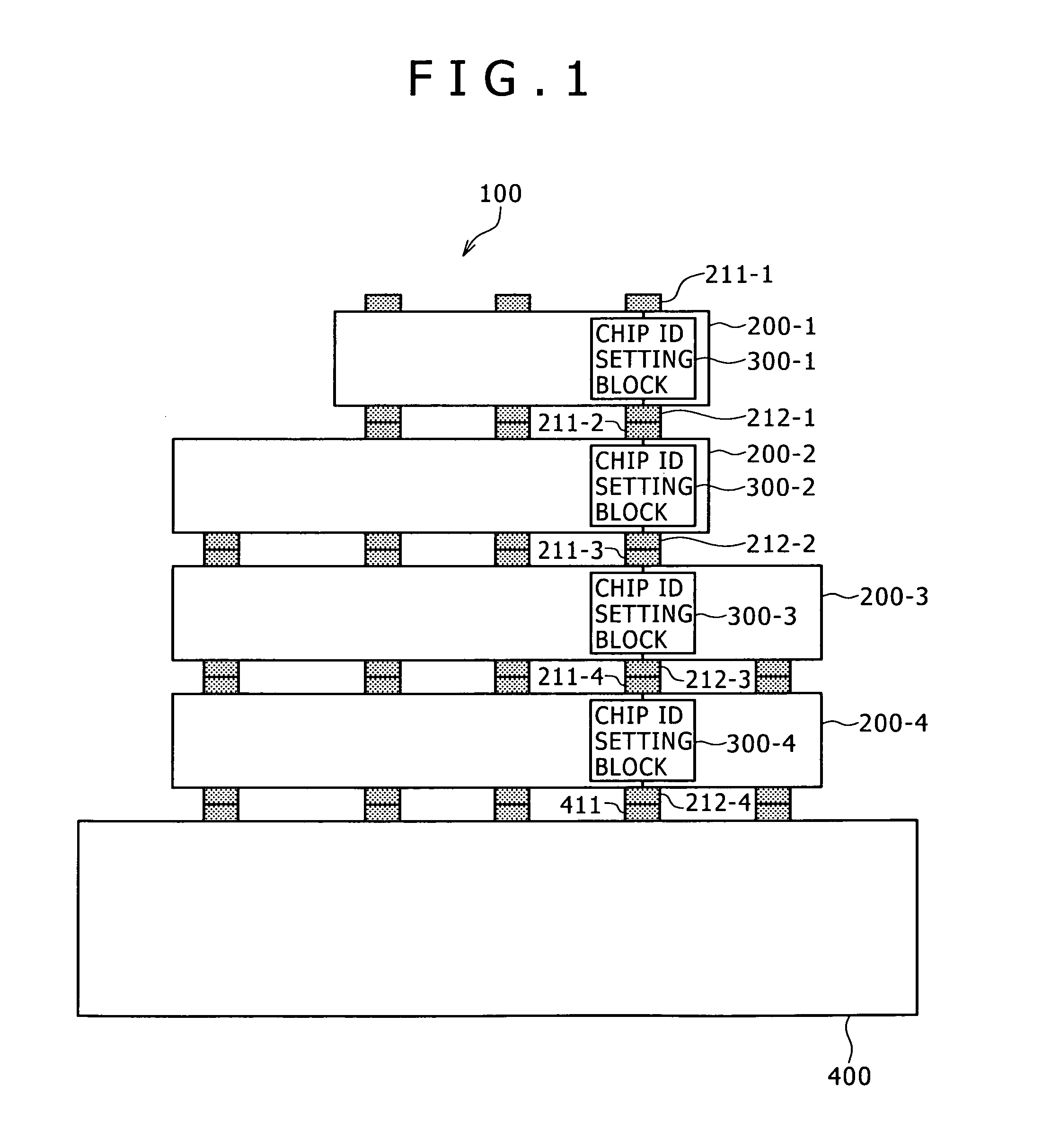
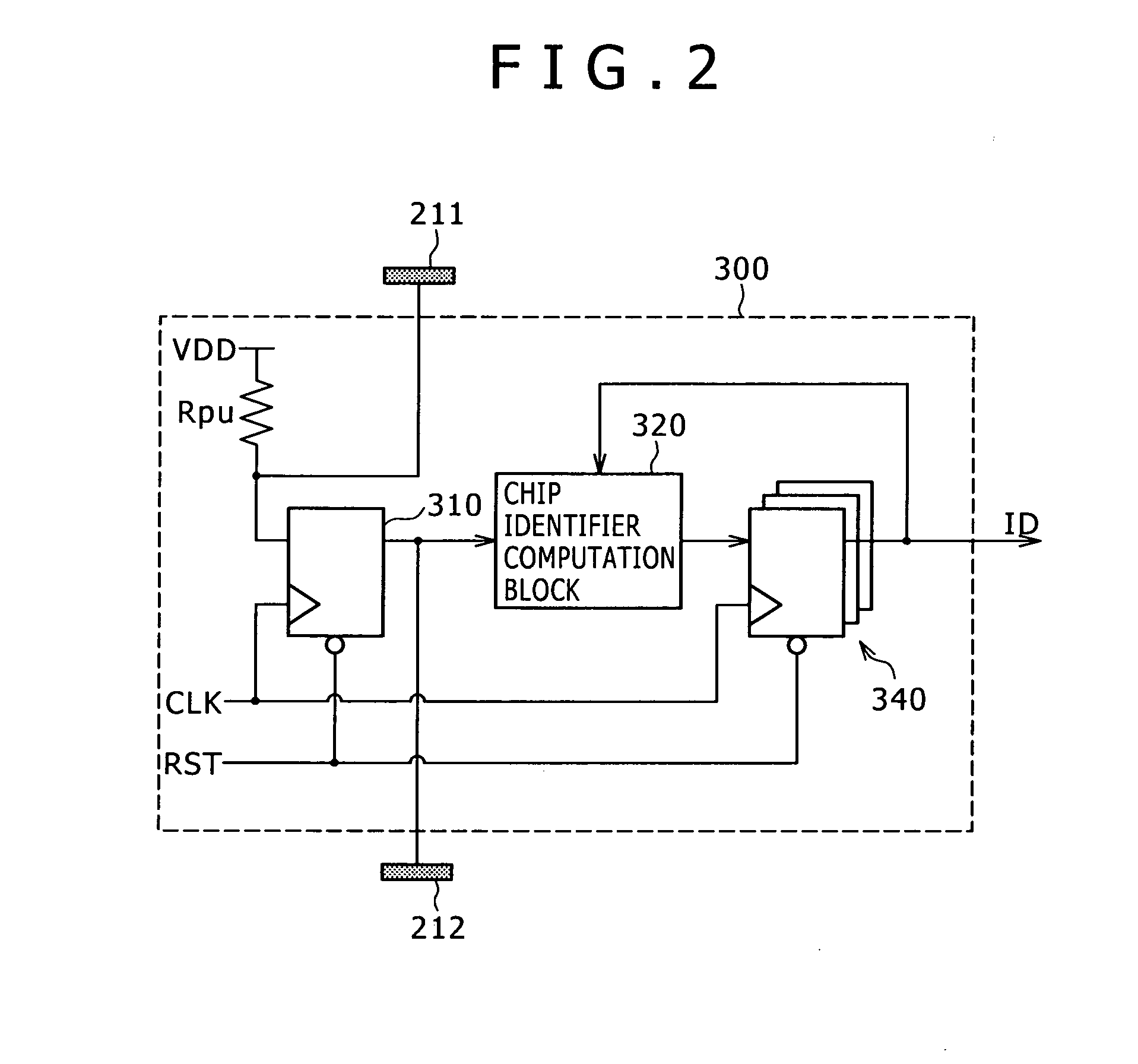
ActiveUS8405221B2Good effectCircuit configuration becomes complicatedSemiconductor/solid-state device detailsSolid-state devicesComputer hardwareFile Control Block
Disclosed herein is a semiconductor device including: an input terminal receiving, if a preceding-stage semiconductor device is layered on a predetermined one of an upper layer and a lower layer, a bit train outputted from the preceding-stage semiconductor device; a semiconductor device identifier hold block holding a semiconductor device identifier for uniquely identifying the semiconductor device; a semiconductor device identifier computation block executing computation by using the semiconductor device identifier to update the semiconductor device identifier held in the semiconductor device identifier hold block according to a result of the computation; a control block once holding data of a bit train entered from the input terminal to control updating of the semiconductor device identifier executed by the semiconductor device identifier computation block based on the held data; and an output terminal outputting the bit train held in the control block to a succeeding-stage semiconductor device layered on another layer.
Owner:TESSERA ADVANCED TECH
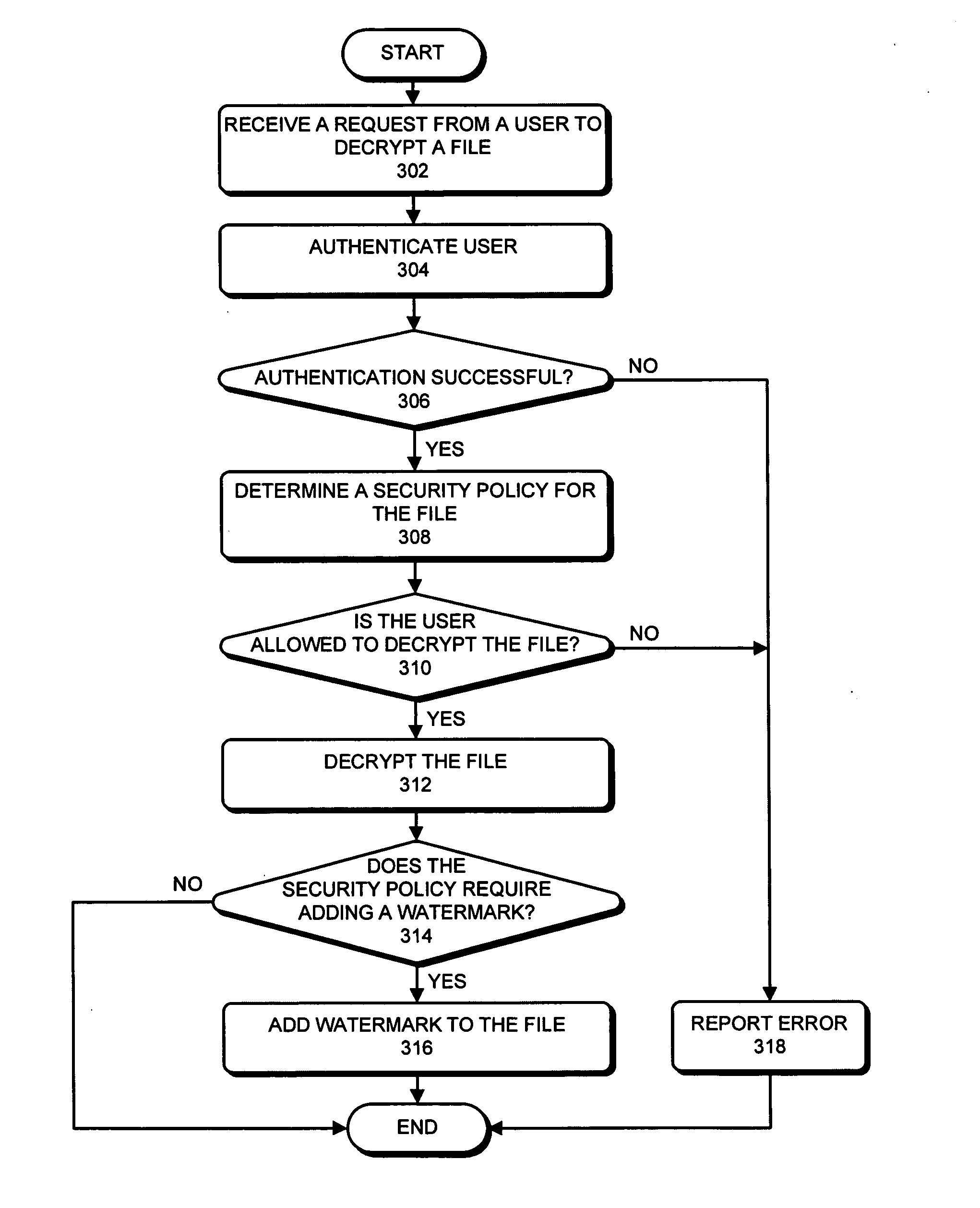
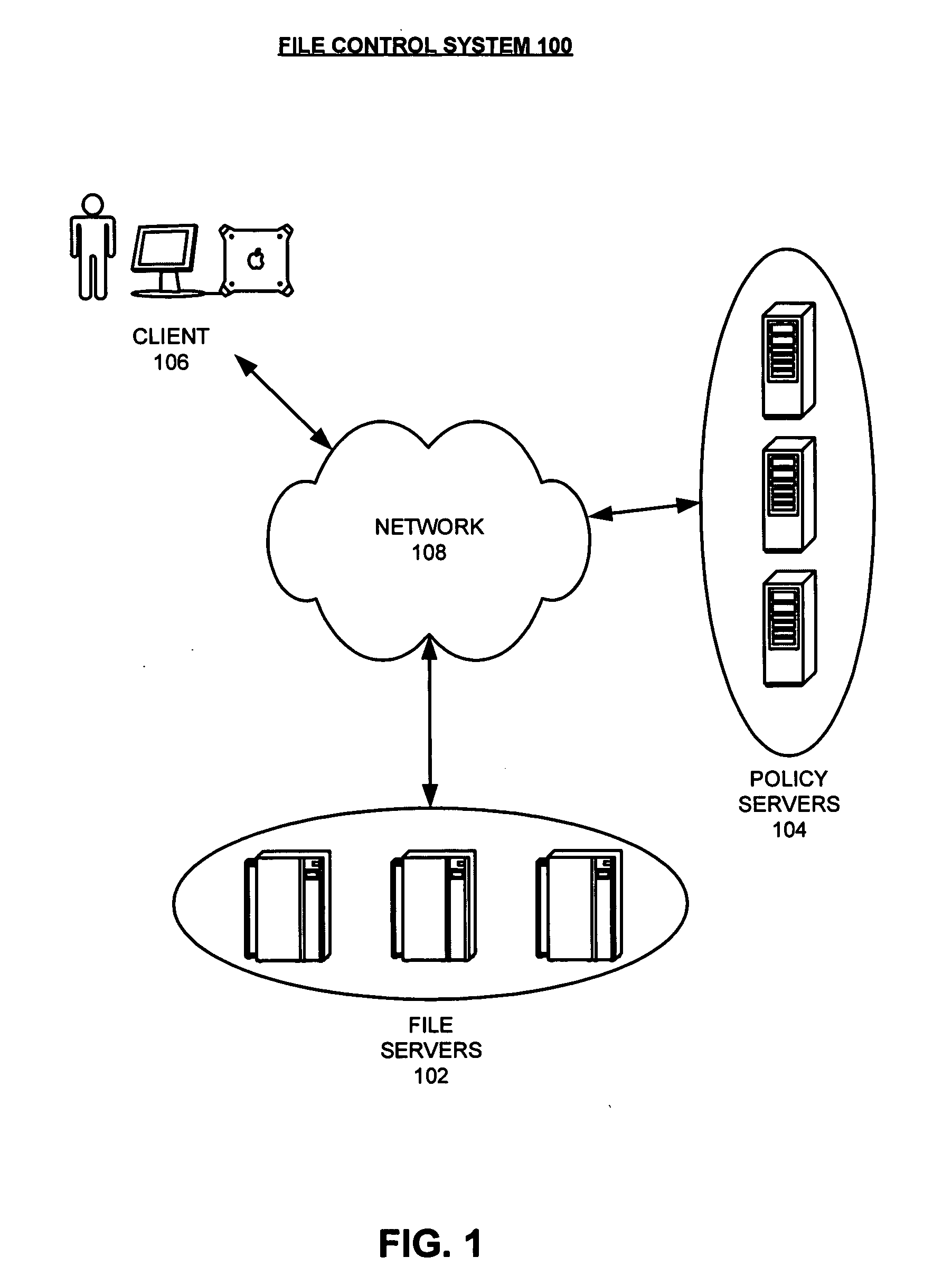
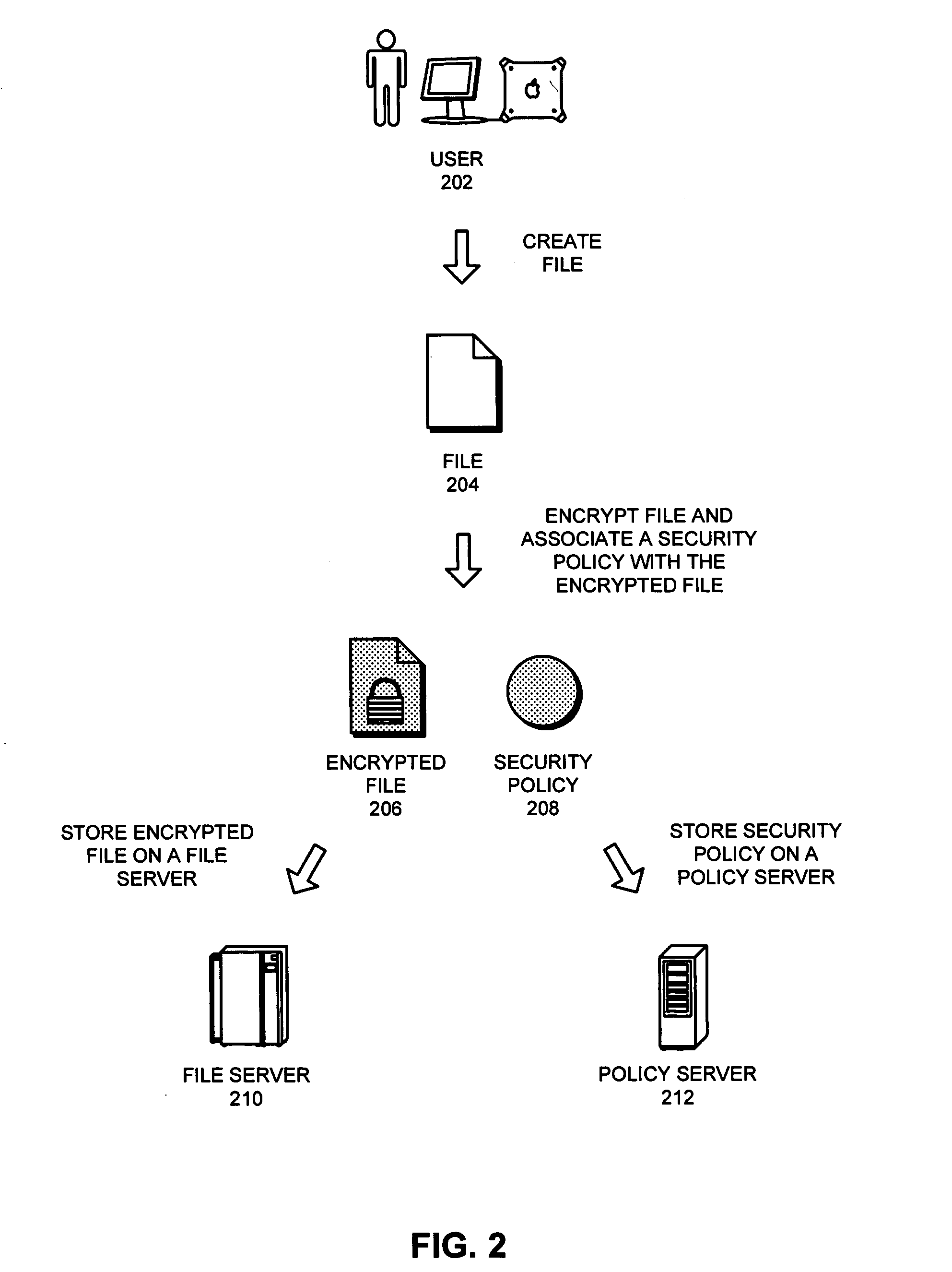
Method and apparatus for combining encryption and steganography in a file control system
One embodiment of the present invention provides a system that improves security of a file control system. During operation the system receives a request from a user to decrypt a file. The system then decrypts the file. Next, the system adds a watermark to the decrypted file which allows the decrypted file to be subsequently traced back to the origin of the decrypted file, thereby improving security of the file control system. Note that the watermark can include a user identifier, an Internet Protocol (IP) address associated with the user, a hardware address or identifier associated with the user, a timestamp, or any other information that can be used to identify the origin of the decrypted file.
Owner:ADOBE INC
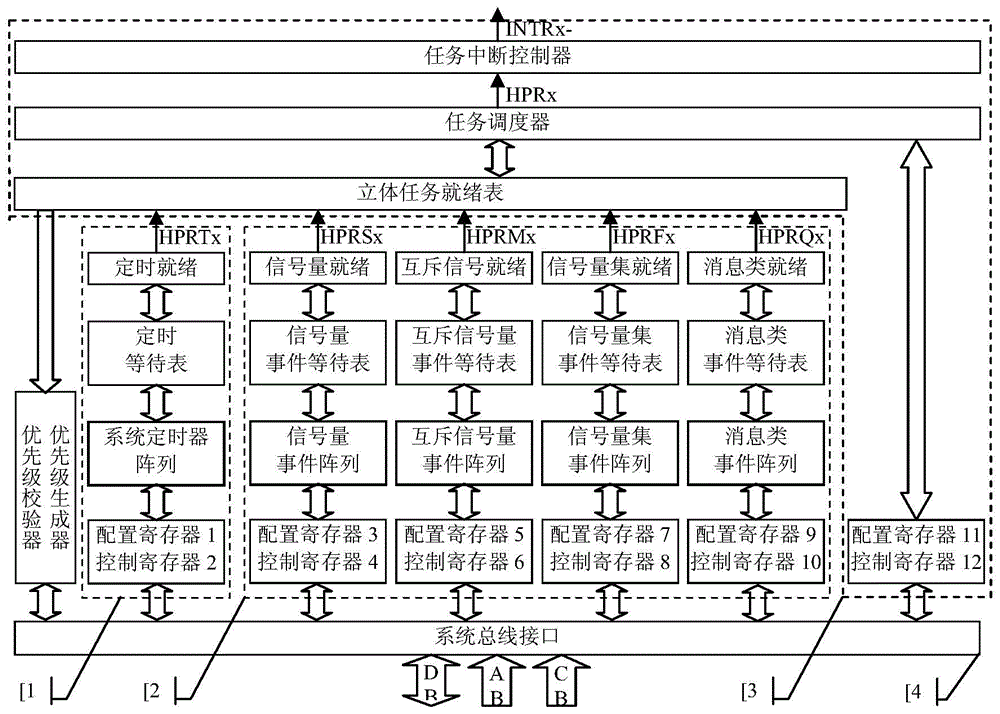
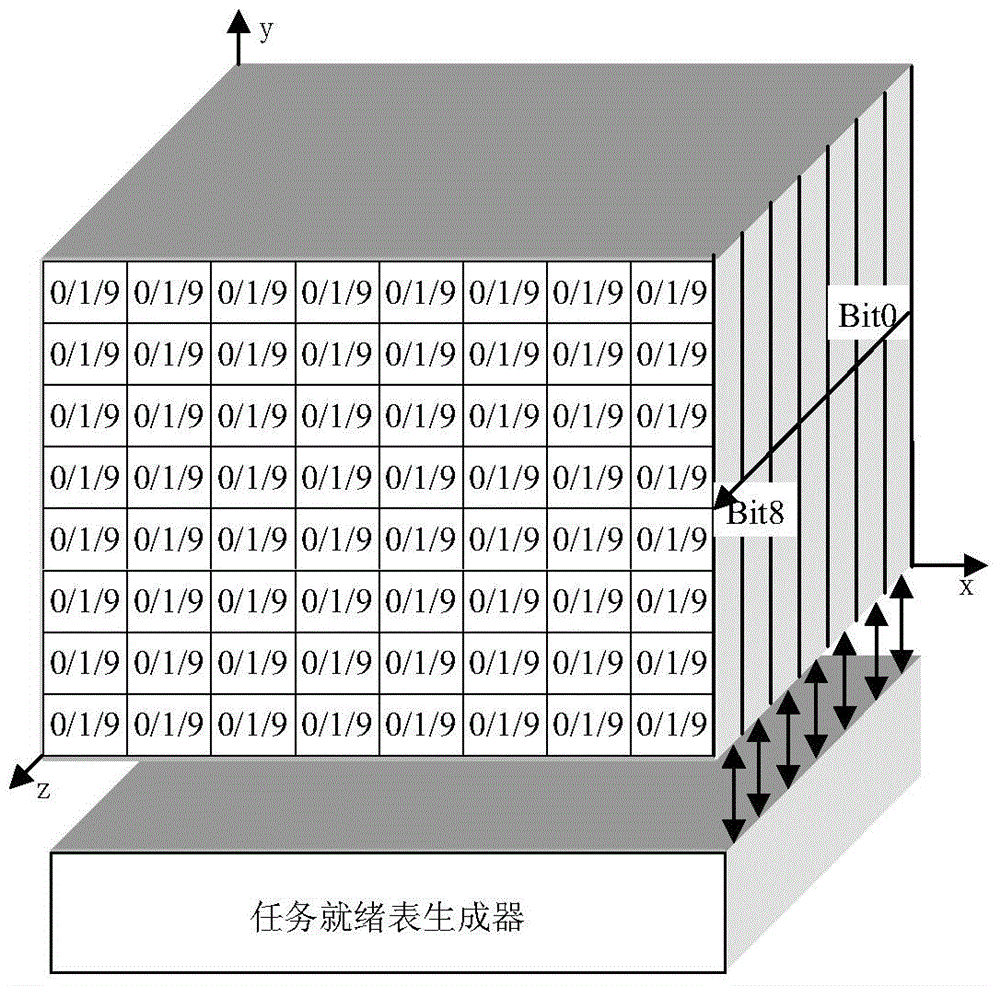
Hardware real-time operation system
InactiveCN103559045AImplement task switchingReduce couplingSpecific program execution arrangementsEmbedded technologyOperational system
The invention belongs to the technical field of computer equipment and relates to a hardware real-time operation system. A timing manager is used for realizing time delay and periodic execution of a task through a hardware timer; a task manager is used for realizing operation management of a task control block queue; an event manager is used for realizing operation and management of a semaphore control block, a mutually exclusive semaphore control block, a semaphore set control block, a message mailbox control block and an event control block of a message queue control block; and a bus interface manager is used for realizing data transmission and control between a processor and the real-time operation system. The hardware real-time operation system has a reliable design principle, an advanced design concept and a scientific contract technical means, adopts a cross embedded technology and an integrated circuit technology to achieve a hardware real-time operation system IC (integrated circuit), effectively improves real-time performance, reliability and stability of the real-time operation system, and has wide development and application values.
Owner:QINGDAO UNIV
Apparatus and method for efficiently modifying network data frames
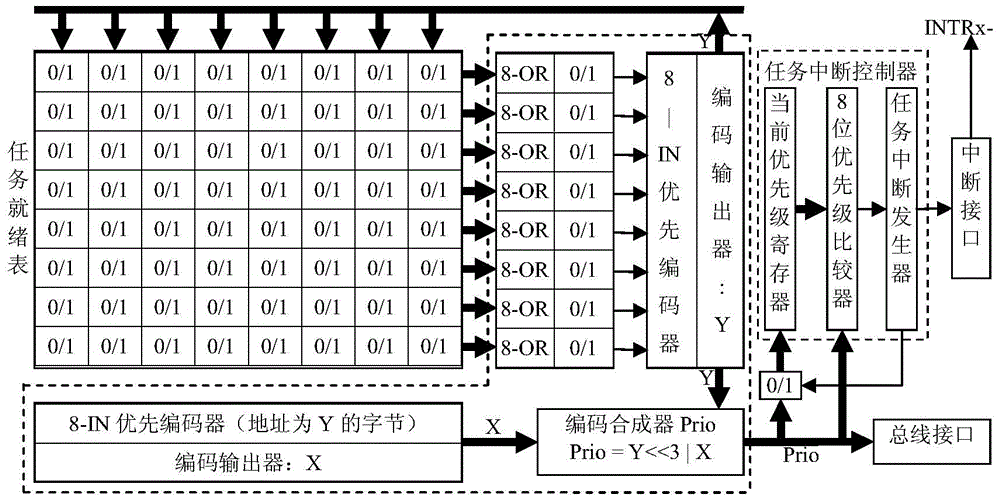
InactiveUS20060146881A1Reduce memory bandwidthTime-division multiplexTransmissionFile Control BlockNetwork data
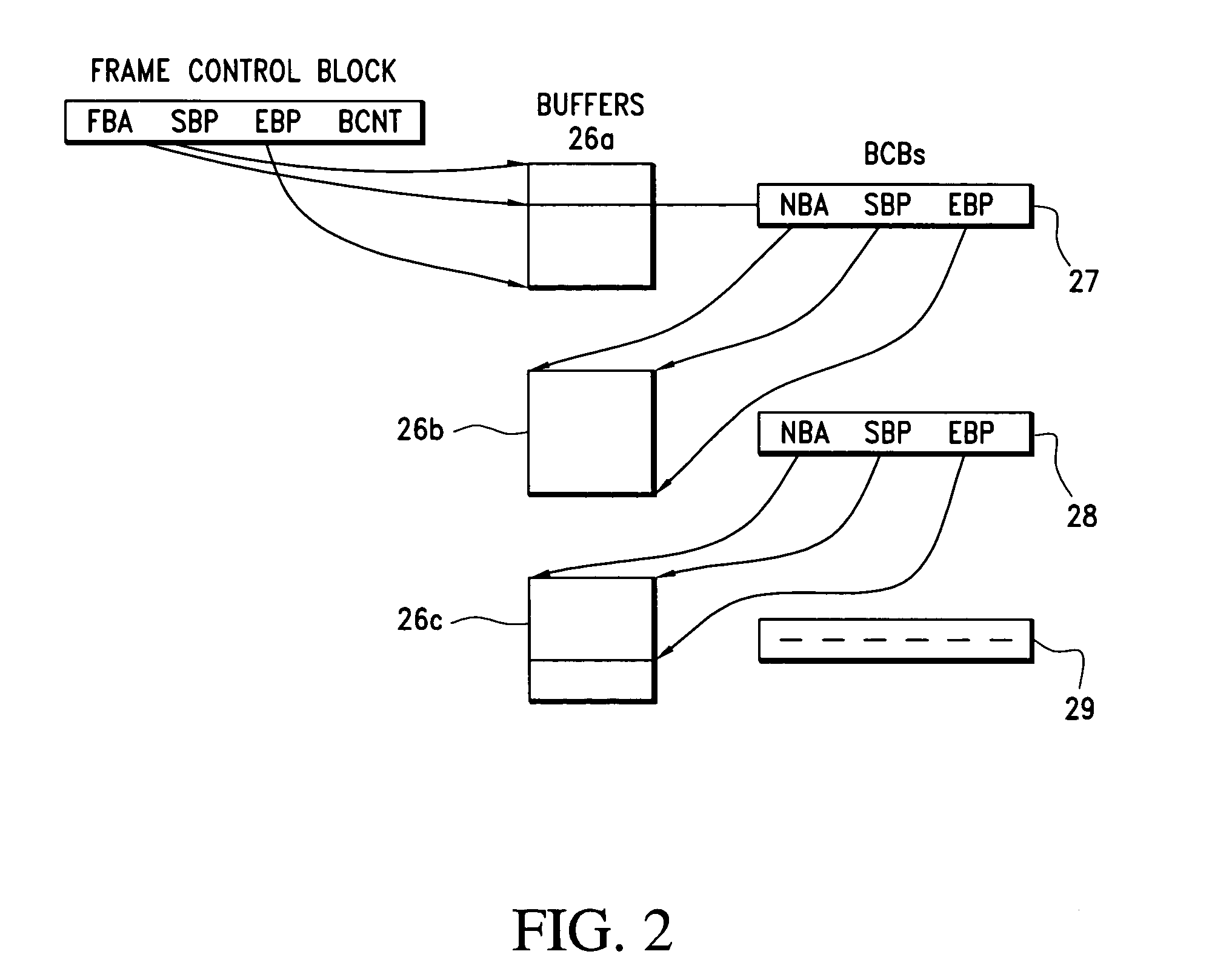
Apparatus and method for storing network frame data which is to be modified. A plurality of buffers stores the network data which is arranged in a data structure identified by a frame control block and buffer control block. A plurality of buffer control blocks associated with each buffer storing the frame data establishes a sequence of the buffers. Each buffer control block has data for identifying a subsequent buffer within the sequence. The first buffer is identified by a field of a frame control block as well as the beginning and ending address of the frame data. The frame data can be modified without rewriting the data to memory by altering the buffer control block and / or frame control block contents without having to copy or rewrite the data in order to modify it.
Owner:IBM CORP
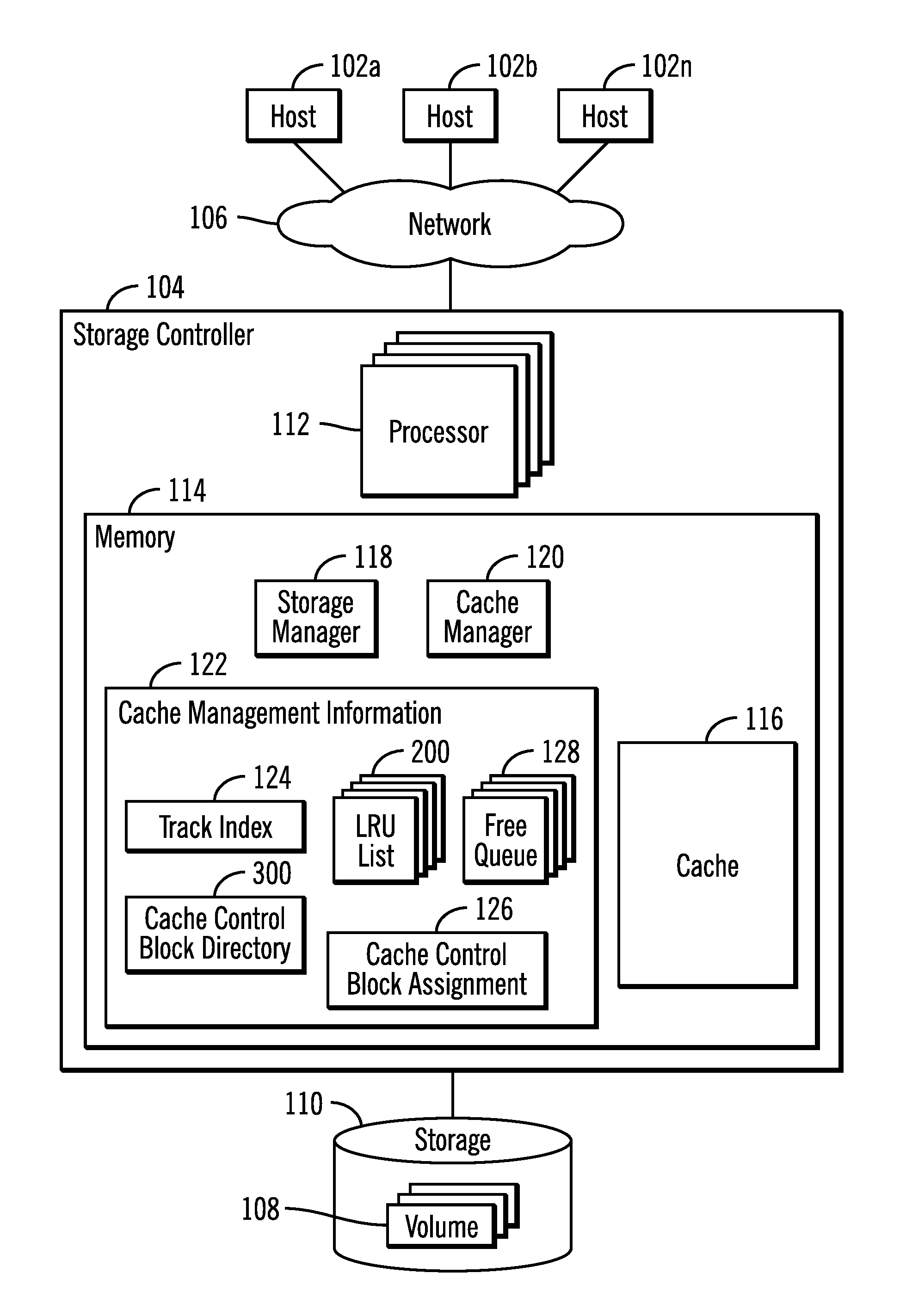
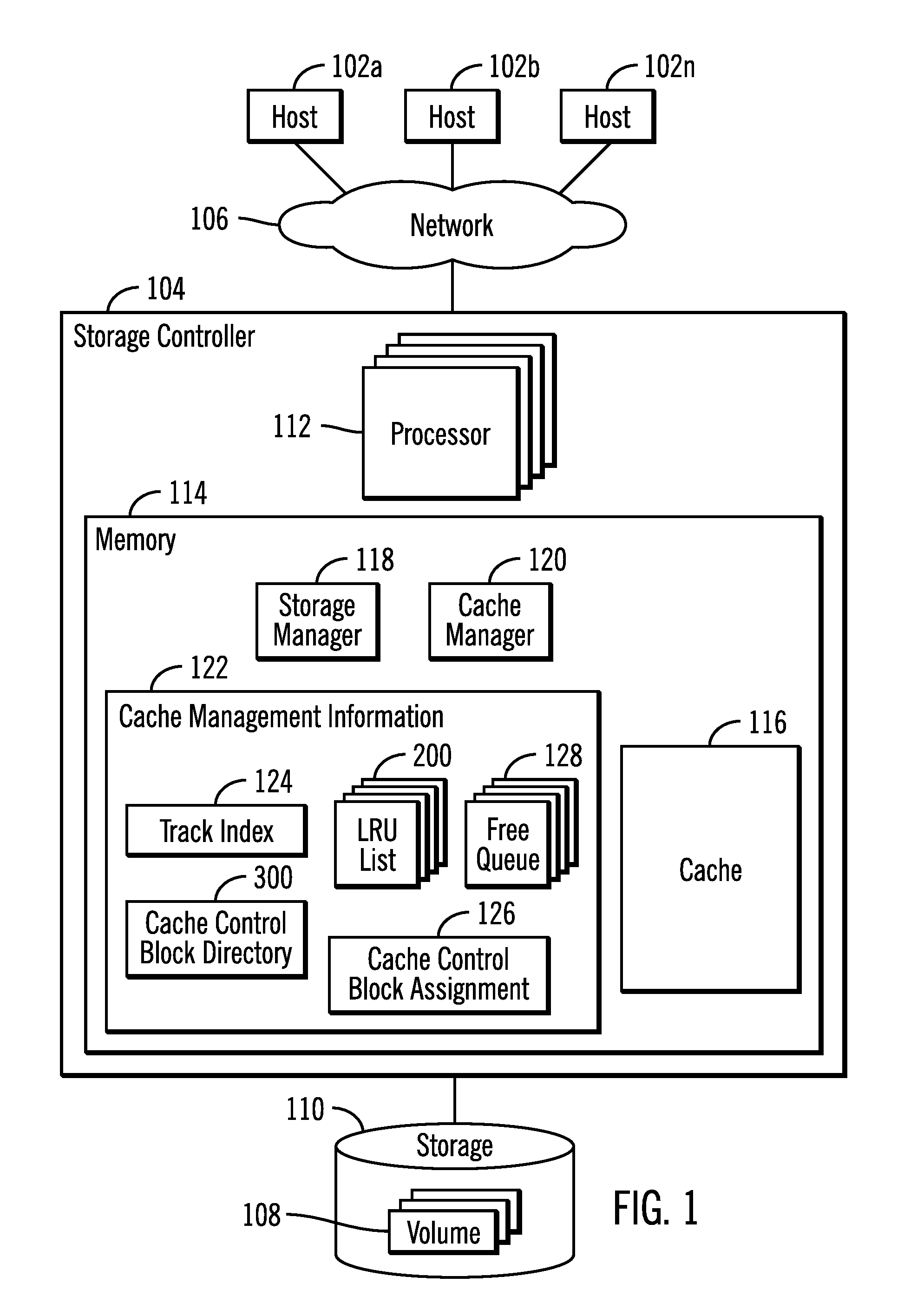
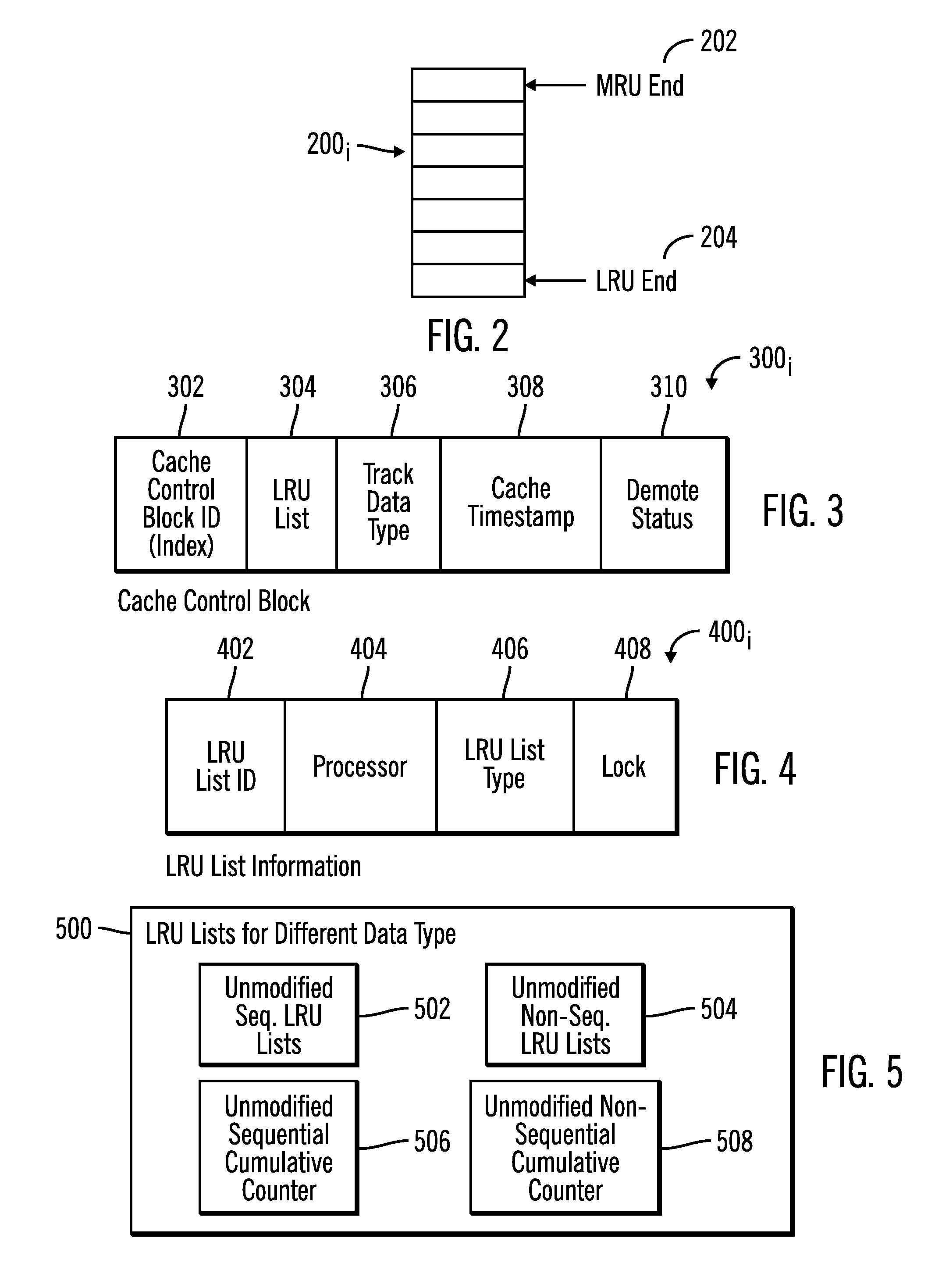
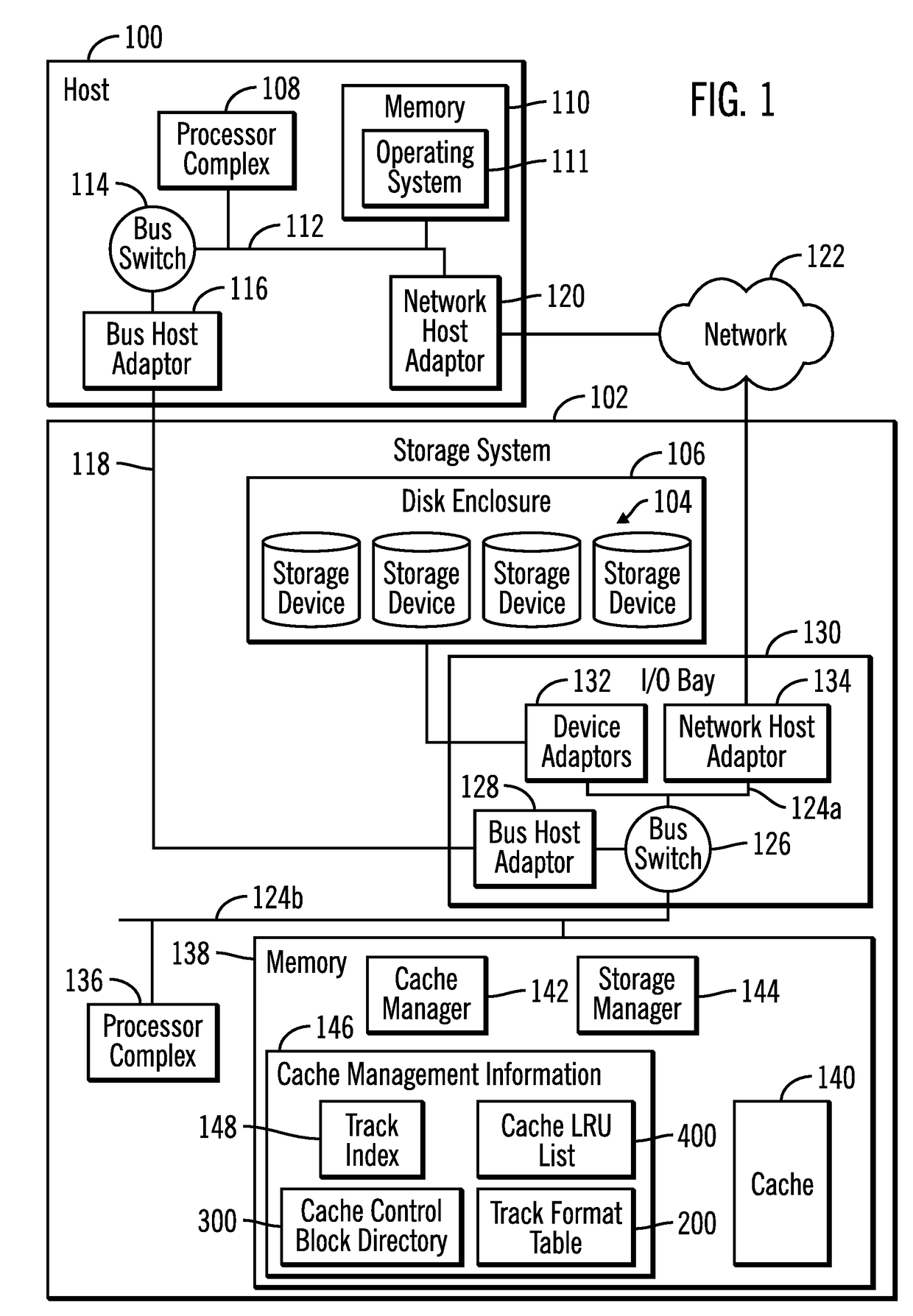
Assigning cache control blocks and cache lists to multiple processors to cache and demote tracks in a storage system
ActiveUS20170052902A1Memory architecture accessing/allocationMemory adressing/allocation/relocationParallel computingFile Control Block
Provided are a computer program product, system, and method for assigning cache control blocks and cache lists to multiple processors to cache and demote tracks in a storage system. Cache control blocks are assigned to processors. A track added to the cache for one of the processors is assigned one of the cache control blocks assigned to the processor. There are a plurality of lists one list for each of the processors and the cache control blocks assigned to the processor. A track to add to cache for a request is received from an initiating processor comprising one of the processors. One of the cache control blocks assigned to the initiating processor is allocated for the track to add to the cache. The track to add to the cache is indicated on the list for the initiating processor.
Owner:IBM CORP
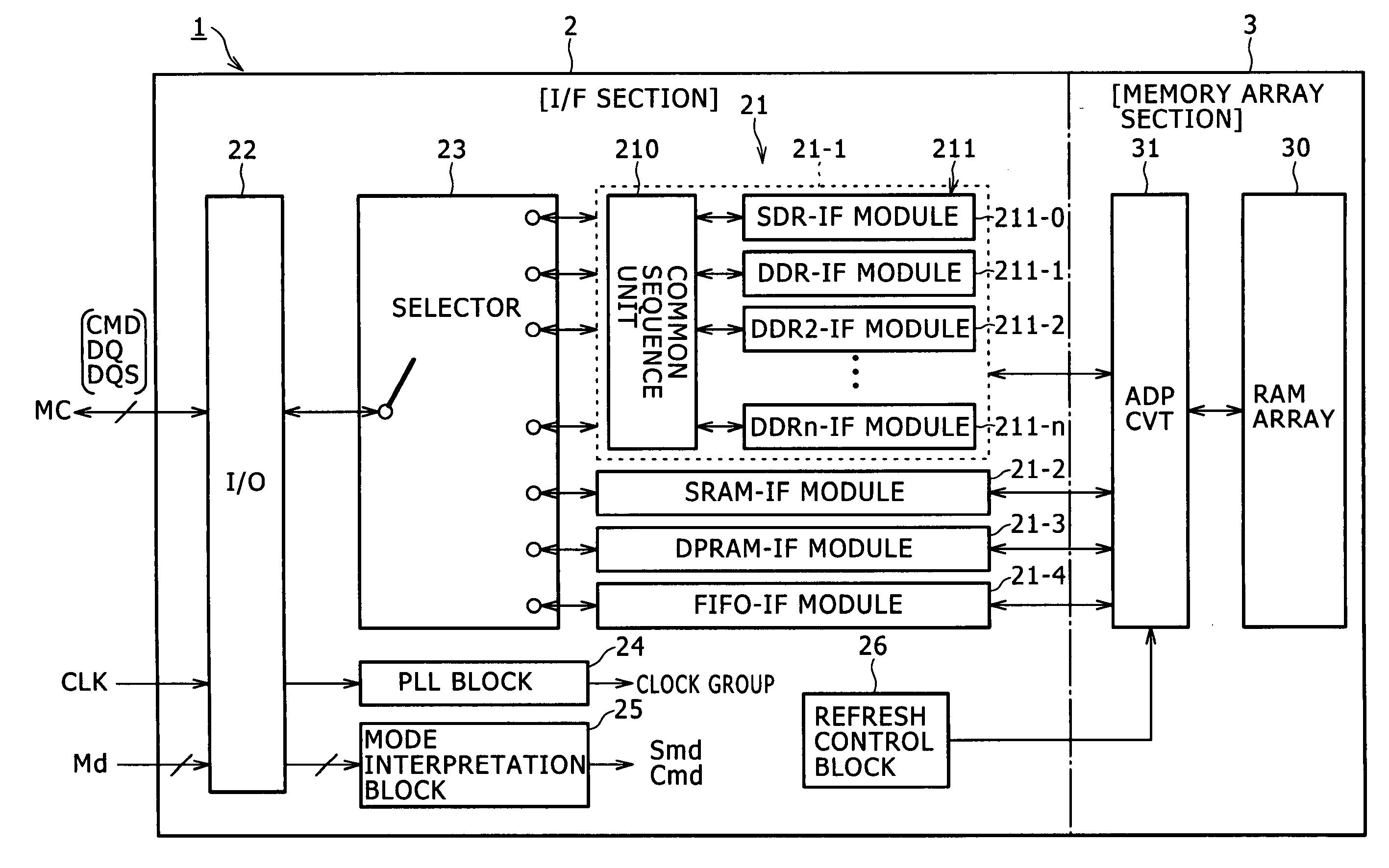
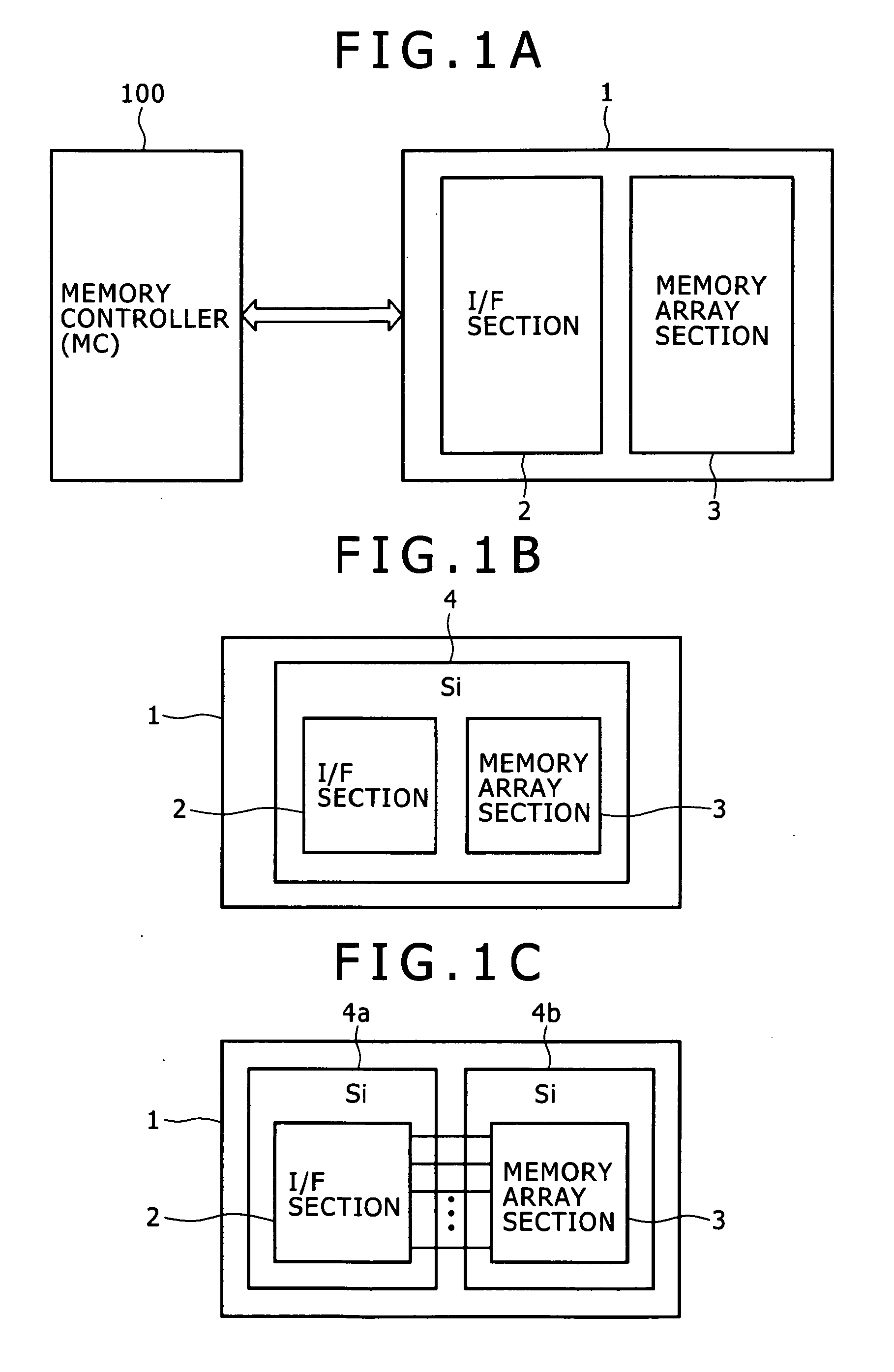
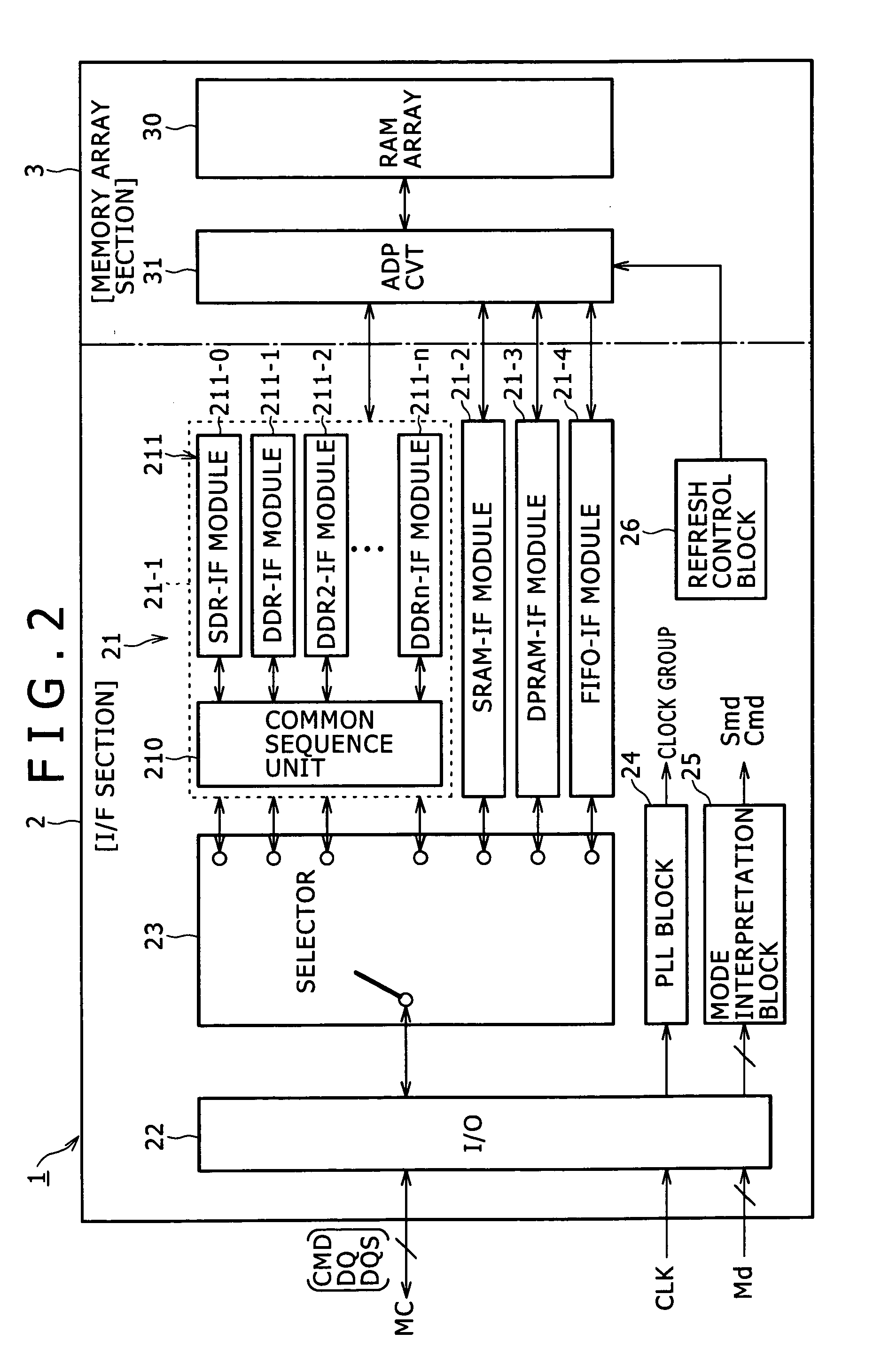
Semiconductor memory device and operation method therefor
Disclosed herein is a semiconductor memory device, including: a memory array section wherein a memory array which requires a refresh operation is formed; an interface section configured to carry out an interfacing process between an external apparatus and the memory array section; and a refresh control block for controlling the refresh operation; the interface section configured to include a plurality of interface modules individually corresponding to a plurality of memory types and selectively applied to the interfacing process between the external apparatus and the memory array section; the refresh control block having a function of issuing a refresh command within a refresh cycle and another function of preventing, if, upon issuance of the refresh command, an access command and the refresh command to the memory array are estimated to collide with each other, the collision.
Owner:SONY CORP
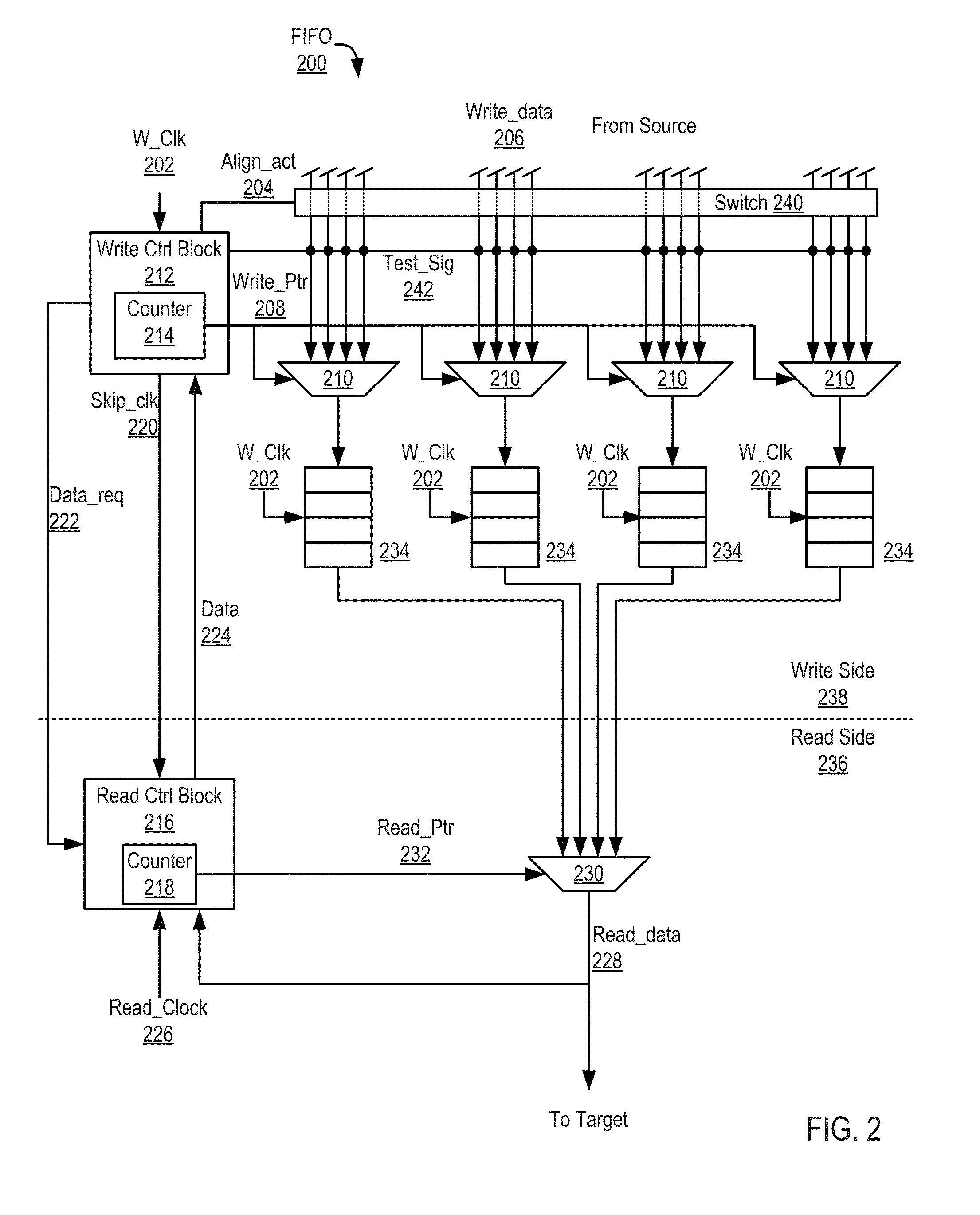
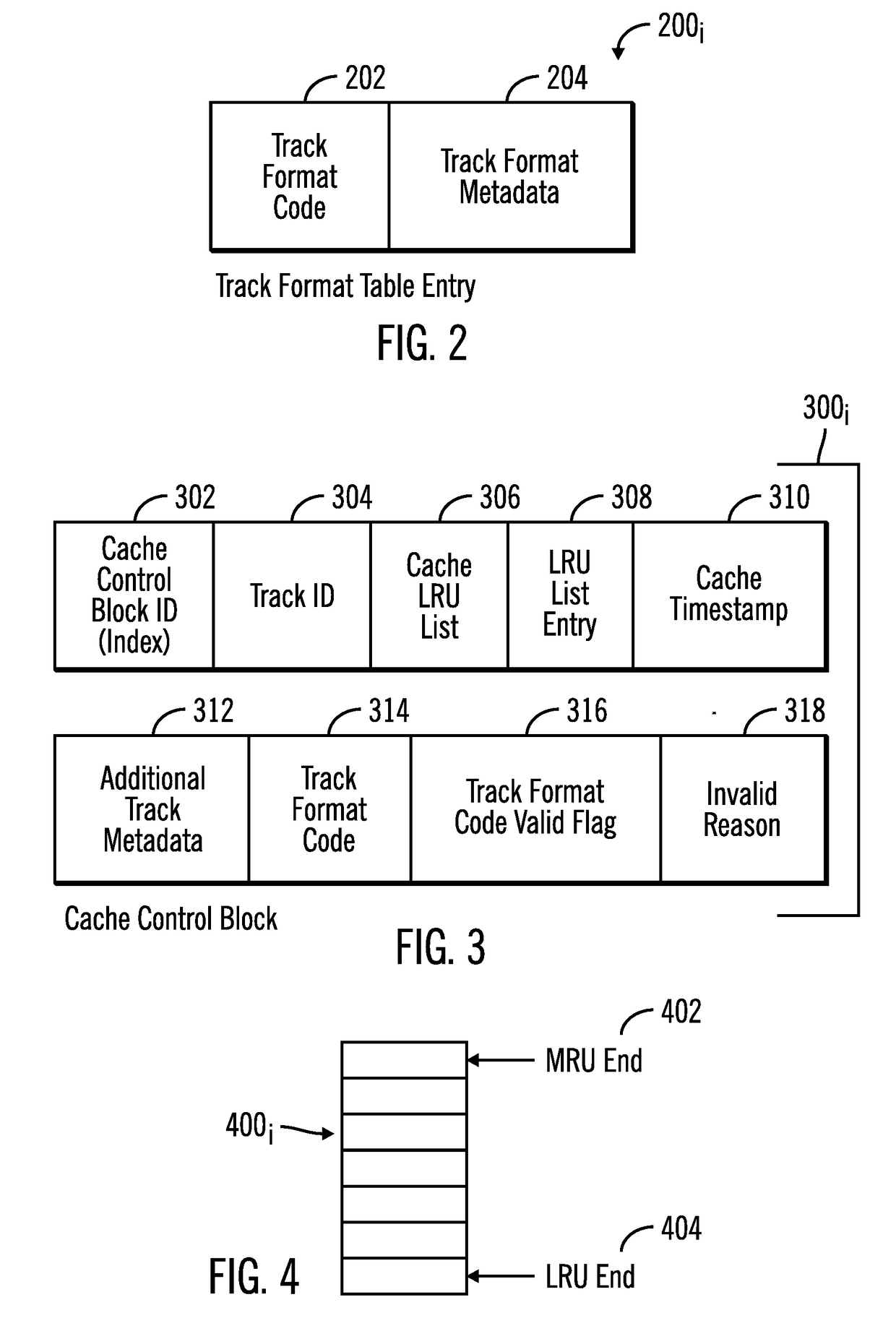
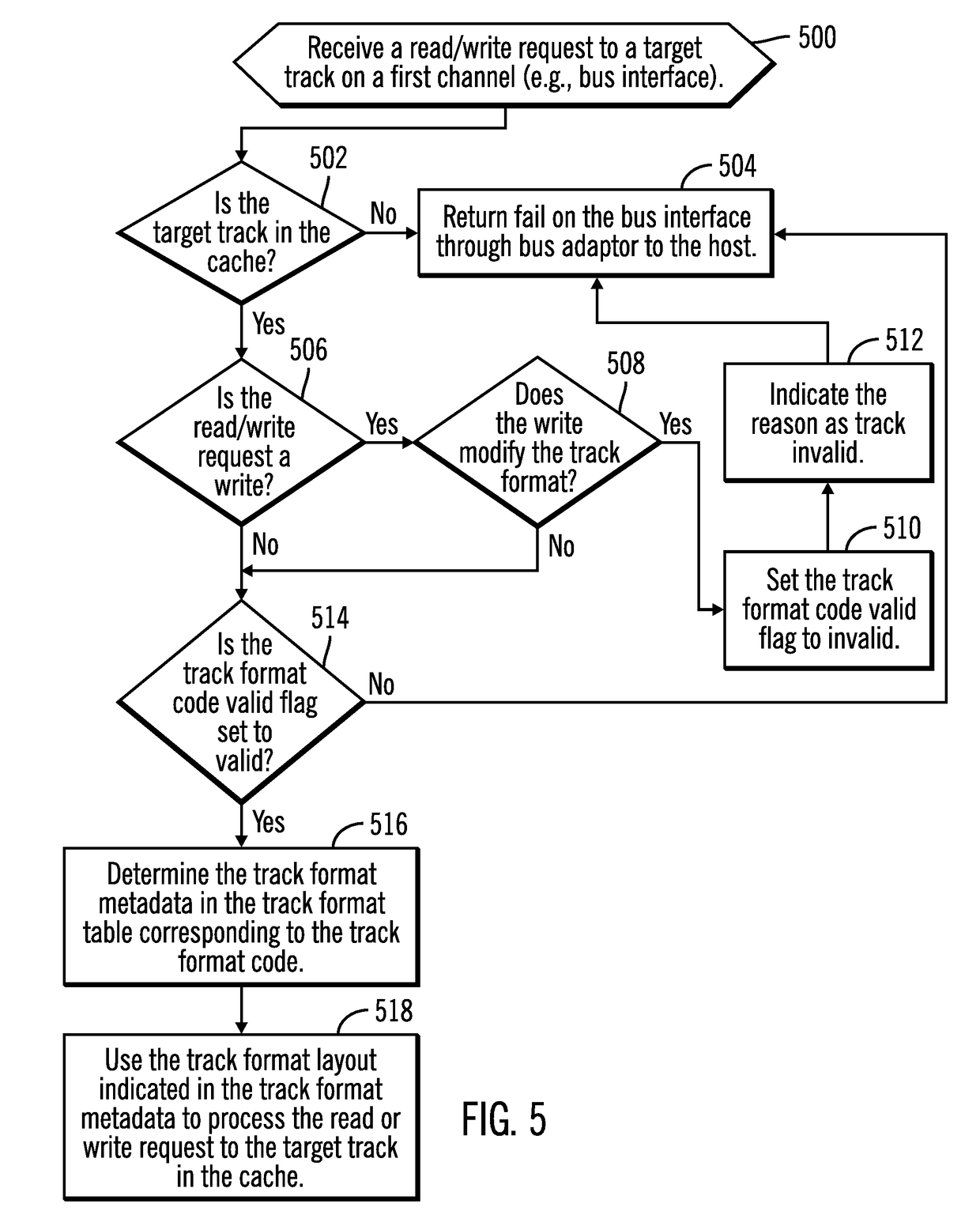
Using a track format code in a cache control block for a track in a cache to process read and write requests to the track in the cache
ActiveUS20190034304A1Minimum delayEasy to handleMemory architecture accessing/allocationMemory systemsData matchingParallel computing
Provided are a computer program product, system, and method for using a track format code in a cache control block for a track in a cache to process read and write requests to the track in the cache. A track format table associates track format codes with track format metadata. A determination is made as to whether the track format table has track format metadata matching track format metadata of a track staged into the cache. A determination is made as to whether a track format code from the track format table for the track format metadata in the track format table matches the track format metadata of the track staged. A cache control block for the track being added to the cache is generated including the determined track format code when the track format table has the matching track format metadata.
Owner:IBM CORP
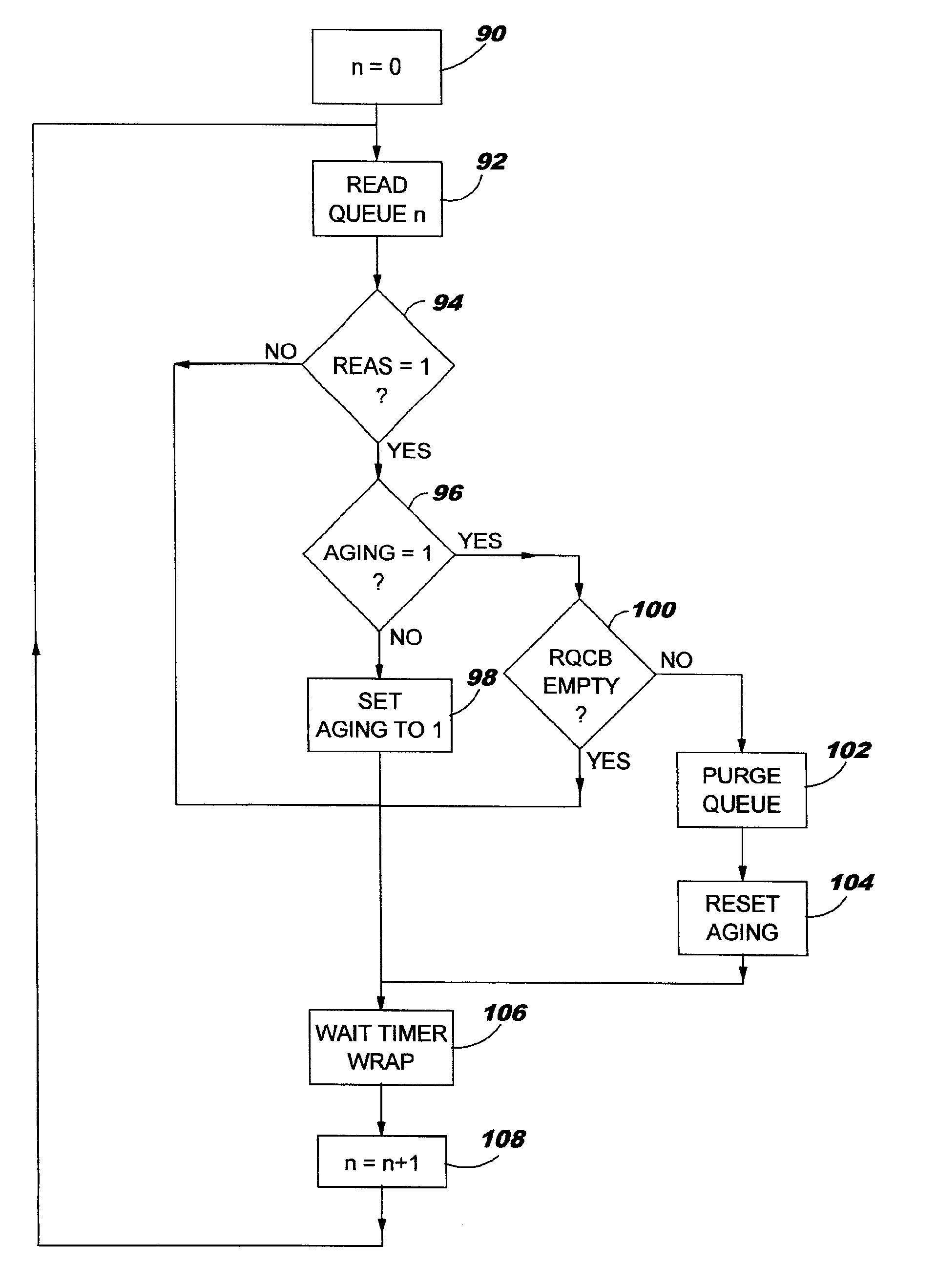
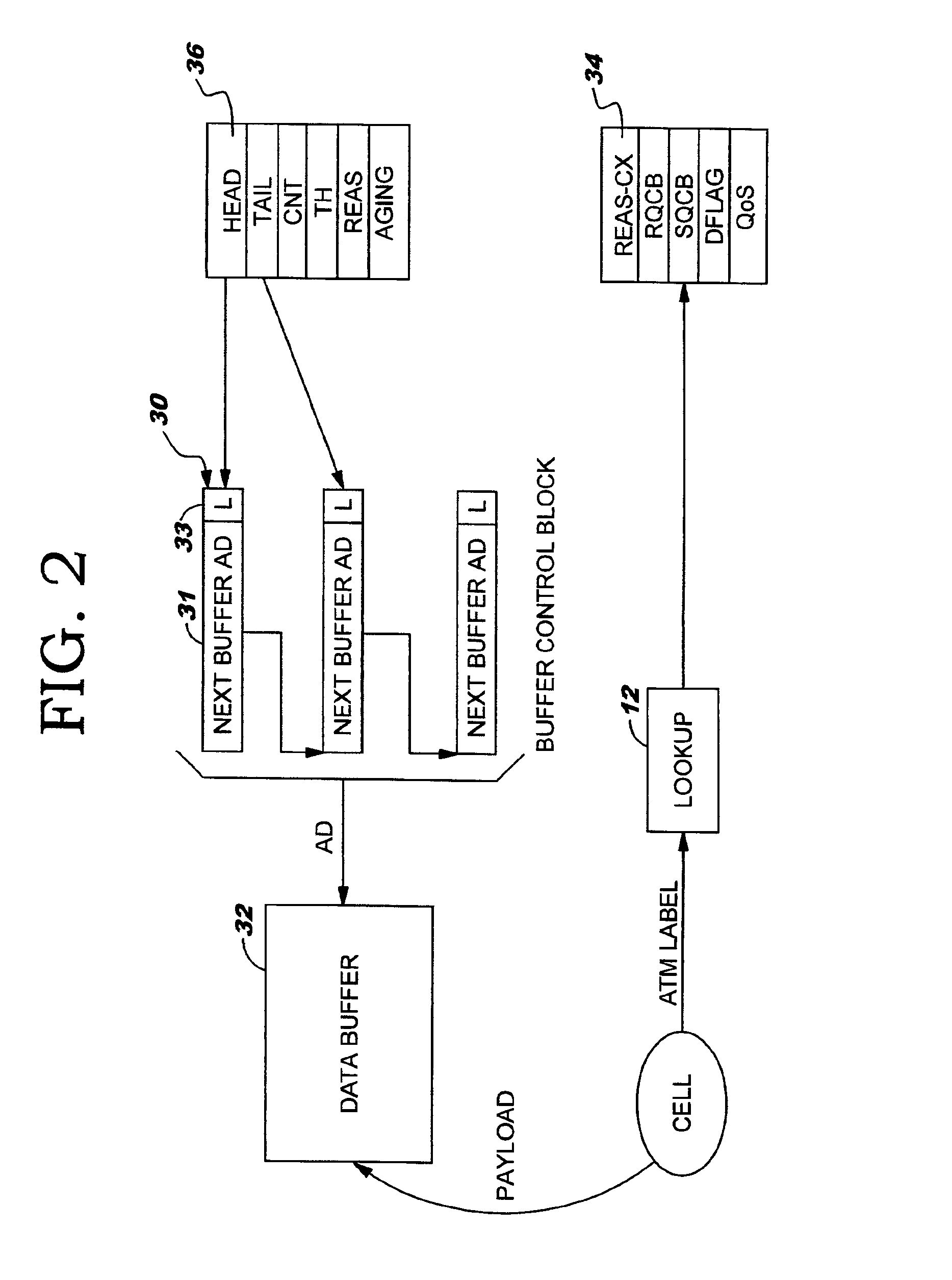
Enqueuing apparatus for asynchronous transfer mode (ATM) virtual circuit merging
A system and method for merging multiple connections that share a same class of service into a single virtual circuit (VC) in an Asynchronous Transfer Mode (ATM) network. A queuing apparatus includes multiple connection queues for each of the connections, and further includes a scheduled queue corresponding to a particular class of service, wherein contents of the connection queues are transferred into the scheduled queue before being transmitted on the VC. A reassembly queue control block (RQCB) defines a chain of buffer control blocks for the connection queues. Each buffer control block corresponds to a cell belonging to a packet of a particular connection and includes a next buffer address and a lock bit. The chain of buffer control blocks is transferred to a scheduled queue control block (SQCB) in response the lock bit indicating a last packet cell.
Owner:IBM CORP
File encryption system based on shadow file
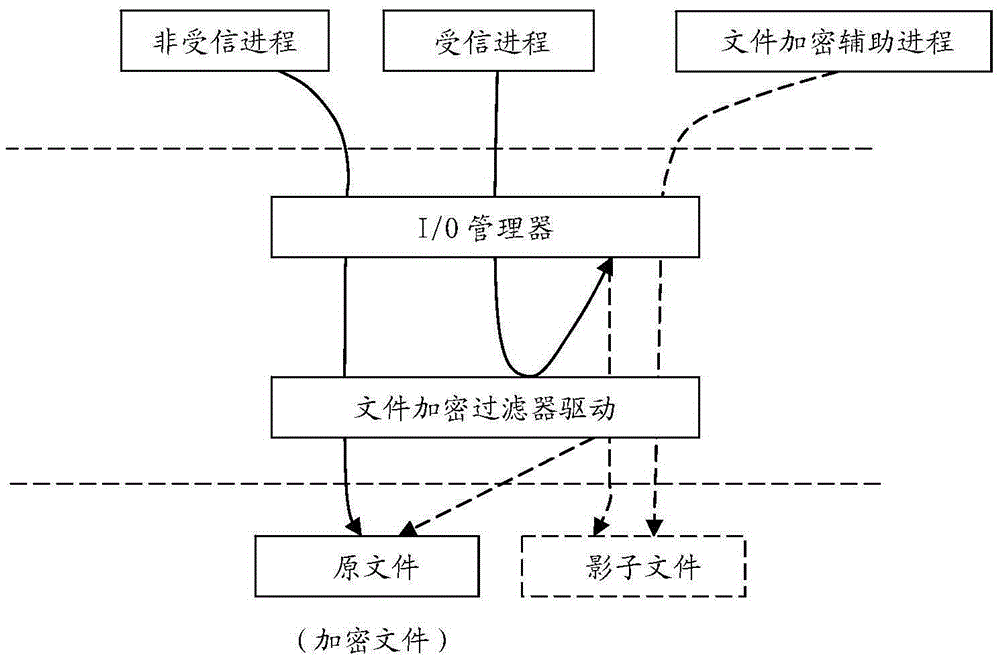
ActiveCN105426766AImprove access efficiencyAvoid the problem of frequently emptying the cacheDigital data protectionPlaintextXML Encryption
The invention relates to a file encryption system based on a shadow file. The system comprises: a file encryption filter driver. When a file is opened or created by a trusted process, if the file to open or create is an encryption file or a file located in a security file directory or a security file disk, the file encryption filter driver redirects a file opening or creating operation to a temporary file directory. Then the file encryption filter driver converts an I / O operation of the trusted process to the shadow file into an I / O operation to an original file of the shadow file, and during the operation, decrypts read encryption data and encrypts plain data to be written, and keeps file information and cache data of the shadow file in file control blocks to be consistent with the file information and cache data of the original file in file control blocks. However, an untrusted process directly performs the I / O operation on the encryption file. Because the trusted process and the untrusted process have respective data caches, the problem of frequent purging a cache is avoided.
Owner:嘉兴古奥基因科技有限公司
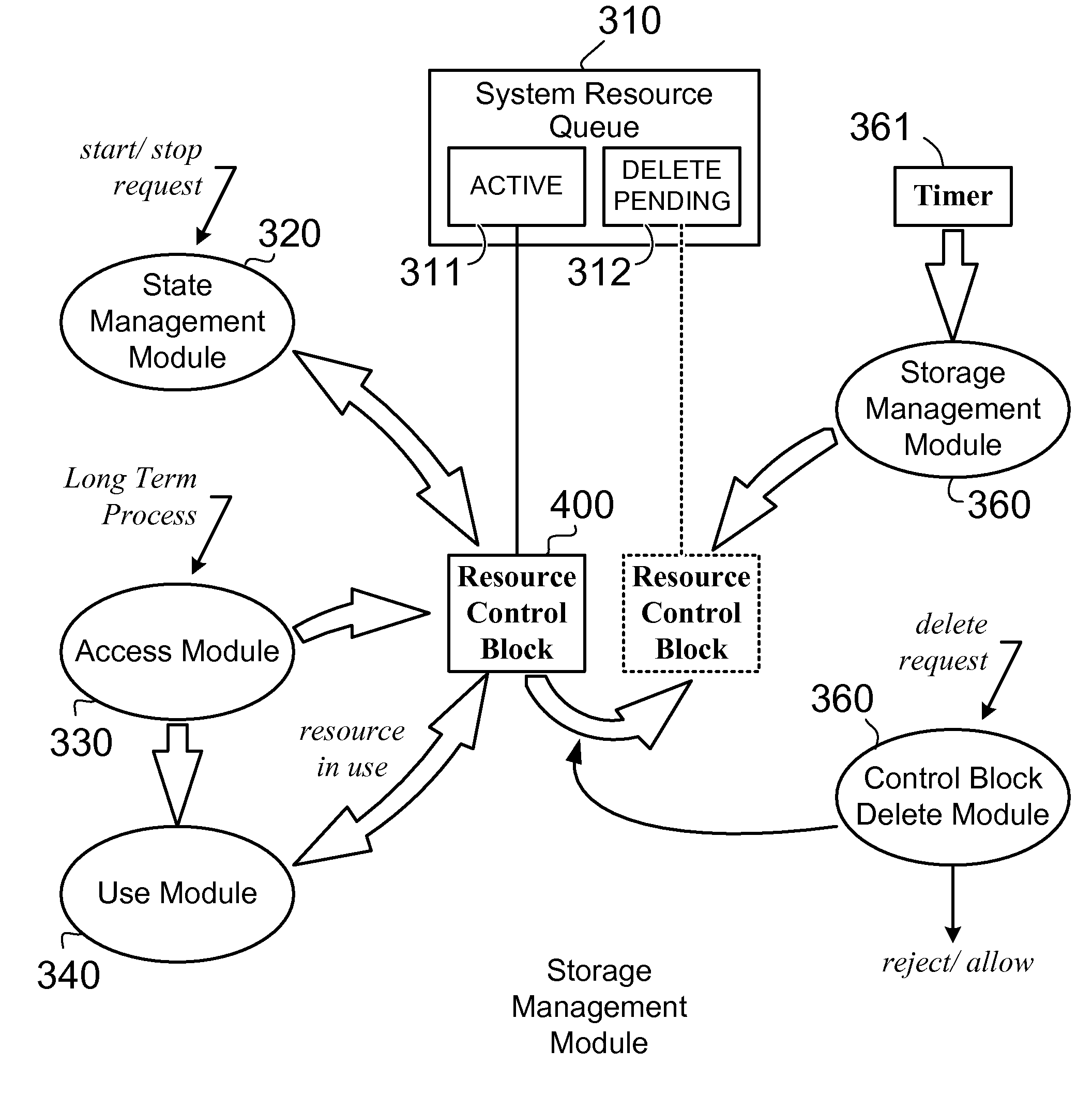
Computer program product and system for deferring the deletion of control blocks
ActiveUS20080244596A1Operate efficiently and effectivelyProgram synchronisationSpecial data processing applicationsFile Control BlockShort terms
A computer program product and system are disclosed for deferring the deletion of resource control blocks from a resource queue within an information management system that includes a plurality of short-term processes and a plurality of long-term processes when each of the long term processes has unset a ‘resource in use’ control flag for that long term process, a ‘request deletion’ flag has been set by the information management system, and a predetermined amount of time has elapsed.
Owner:SAP AG
Method for realizing balanced erase applicable to embedded Flash file system
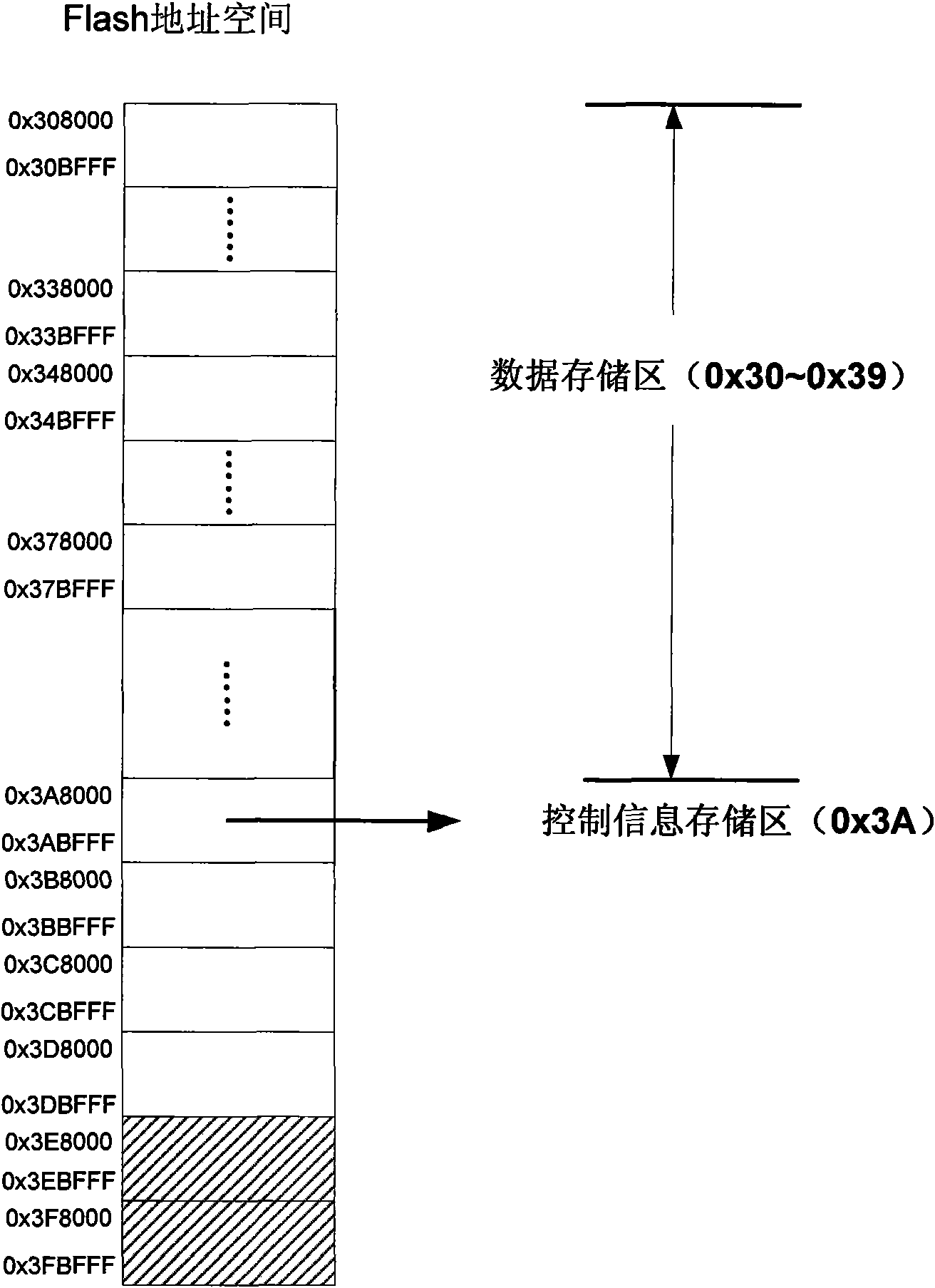
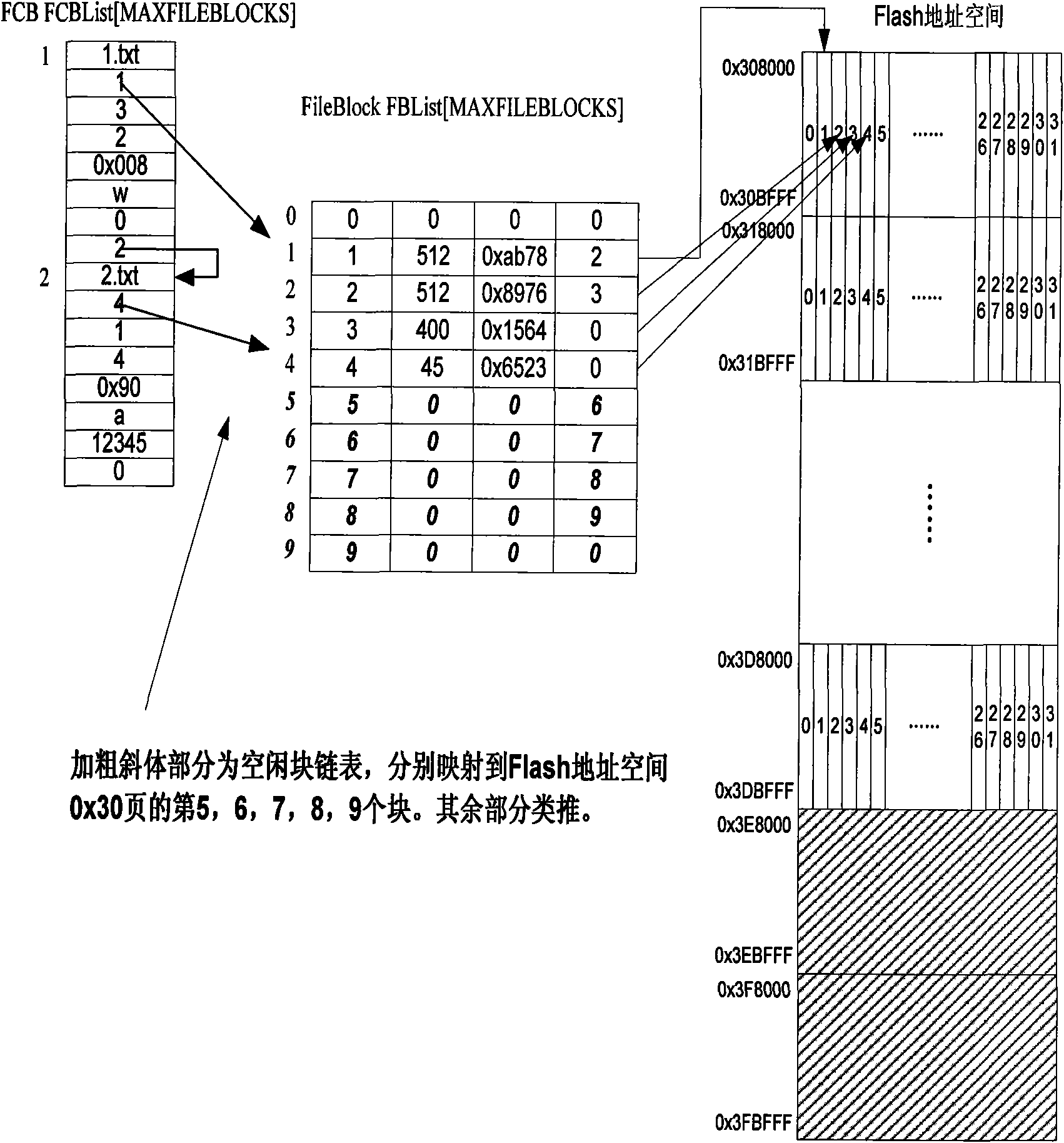
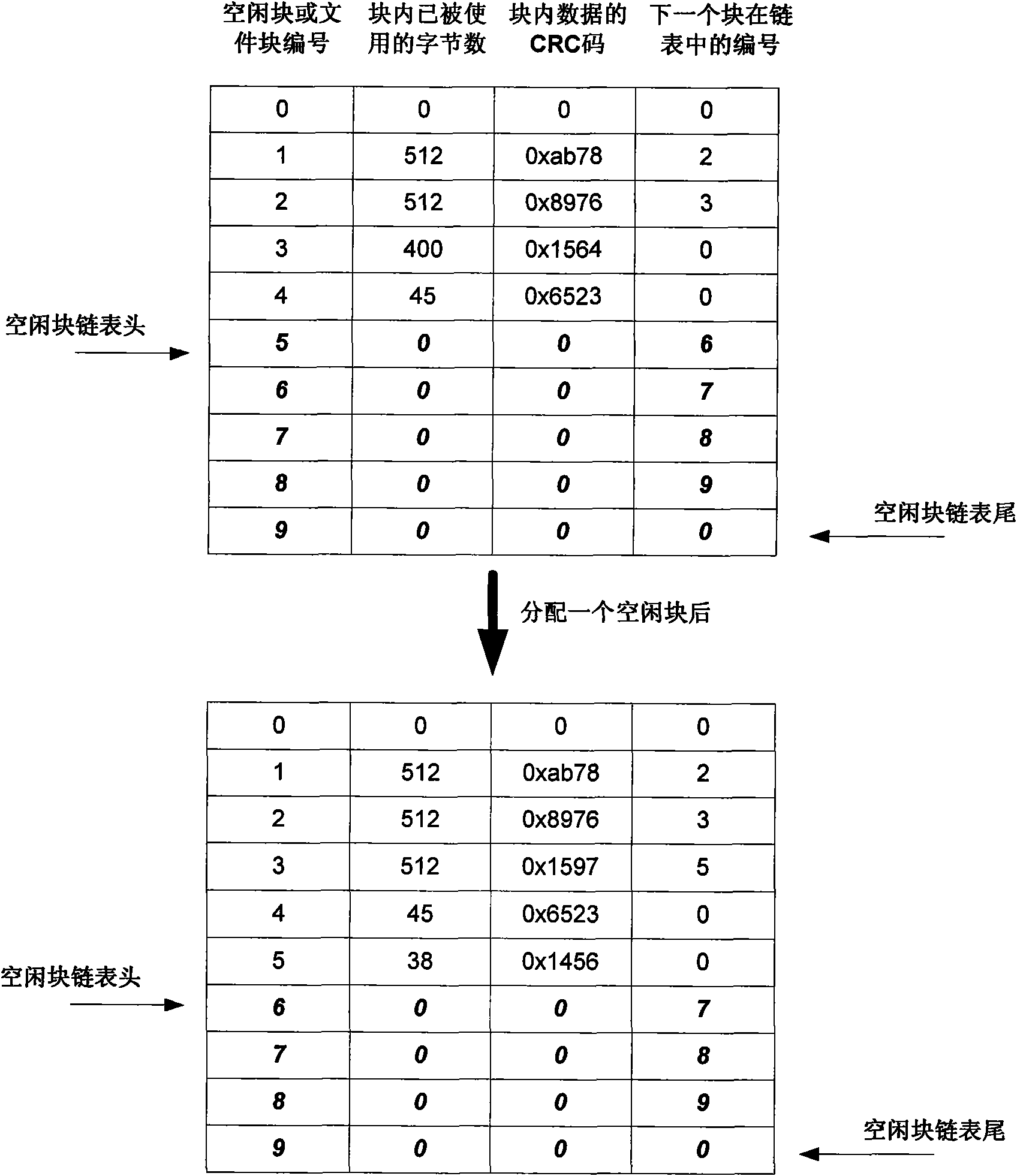
InactiveCN101609464AImprove the level ofReduce overheadMemory adressing/allocation/relocationSpecial data processing applicationsFlash file systemData information
The invention discloses a method for realizing balanced erase applicable to an embedded Flash file system. The method is to divide Flash memory space into a file control information region and a file data storage region, wherein, the file control information region is used for storing information of file control blocks and distribution information of file blocks as a basic distribution unit of a file system; the file data storage region is used for storing actual data information of the files; the file control information region stores the file control blocks of the file system and related control information of the file blocks, and the file data region is used for storing the actual data information of the files in the file system; the file system is to read control information of the Flash file control information region into a memory when the system is started, and write the control information of the file system in the memory into the Flash file control information region from the memory when the system is closed. Service life of Flash can be prolonged by adopting the method.
Owner:ZHEJIANG UNIV
Network packet storage method and network packet transmitting apparatus using the same
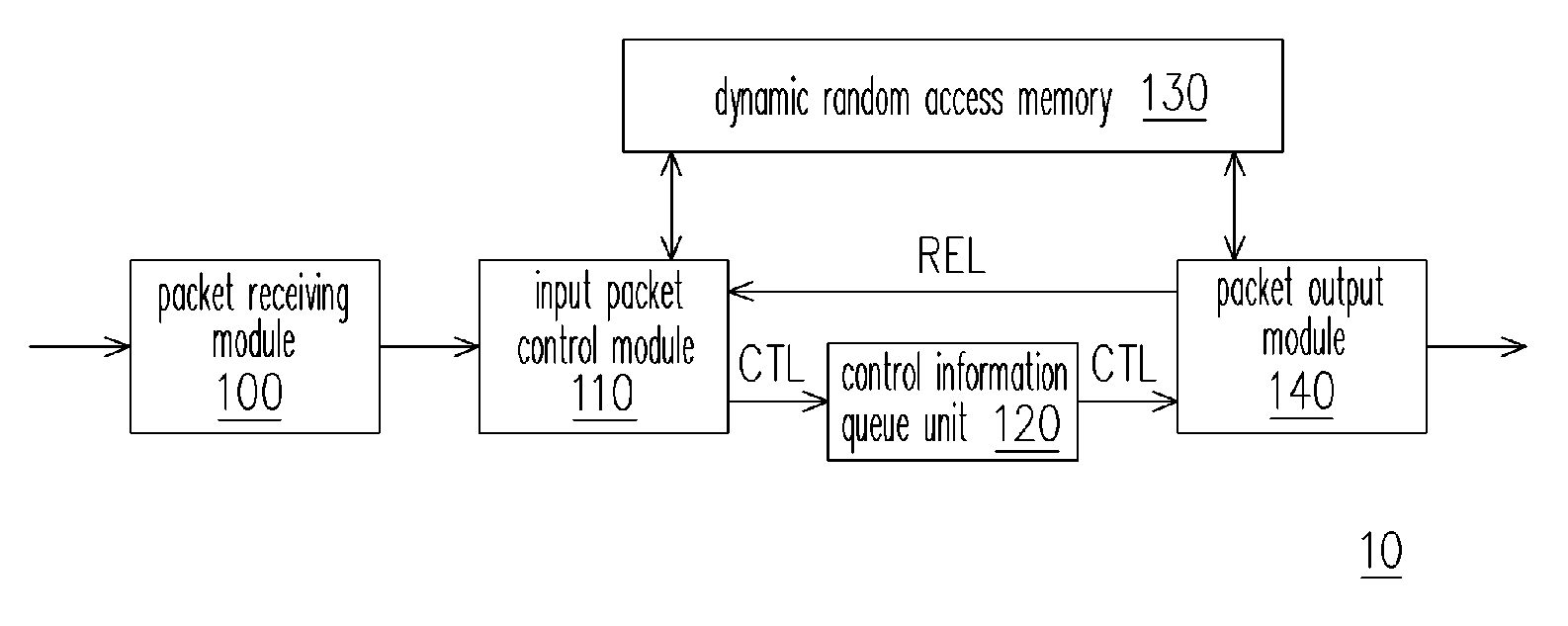
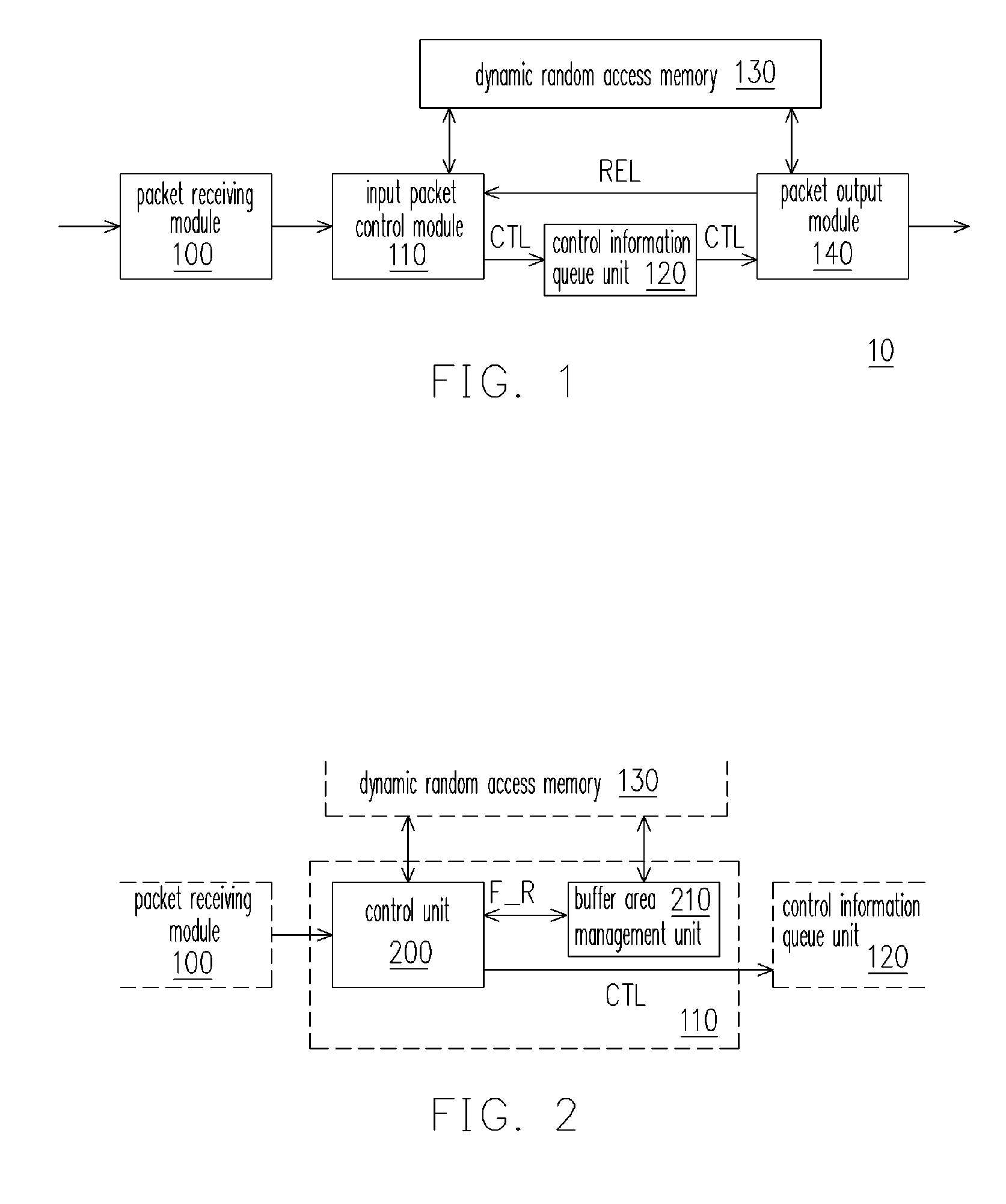
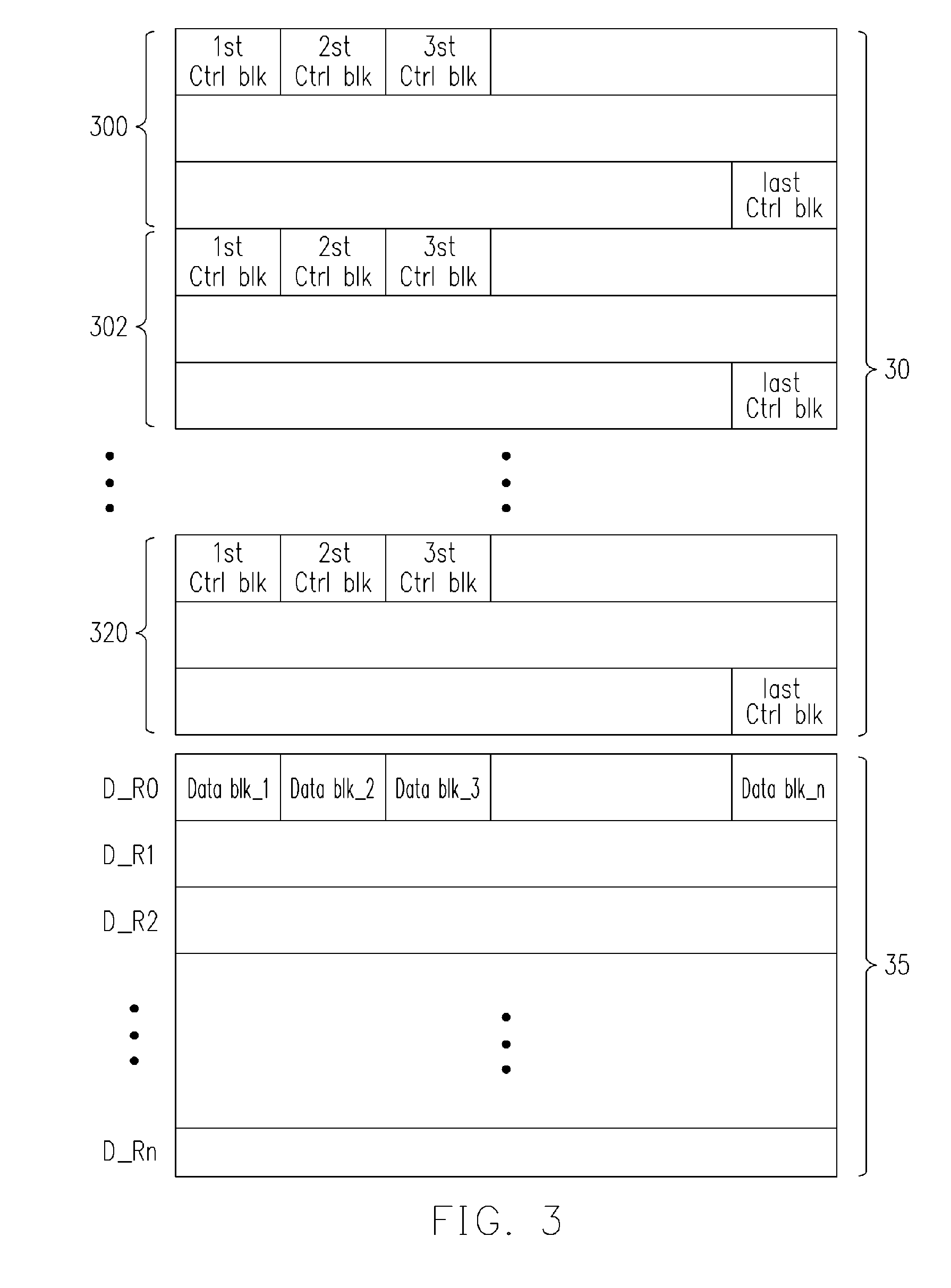
ActiveUS7627672B2Reduce accessReduce the burden onMultiplex system selection arrangementsData switching by path configurationComputer hardwareNetwork packet
A network packet storage method and network packet transmitting apparatus using the same is provided. A packet content and a path control information are obtained from a received packet, and a packet storage address of the packet content is determined according to a predetermined storage rule. The packet content is stored in a data block and packet storage addresses and path control information of packets output via the same output port are stored in a control block. The data block is output when its size reaches a predetermined data block size such that a dynamic random access memory receives the data block by using burst mode. Further, the control block is output when its size reaches a predetermined control block size.
Owner:A10 NETWORKS
Preventing at least in part control processors from being overloaded
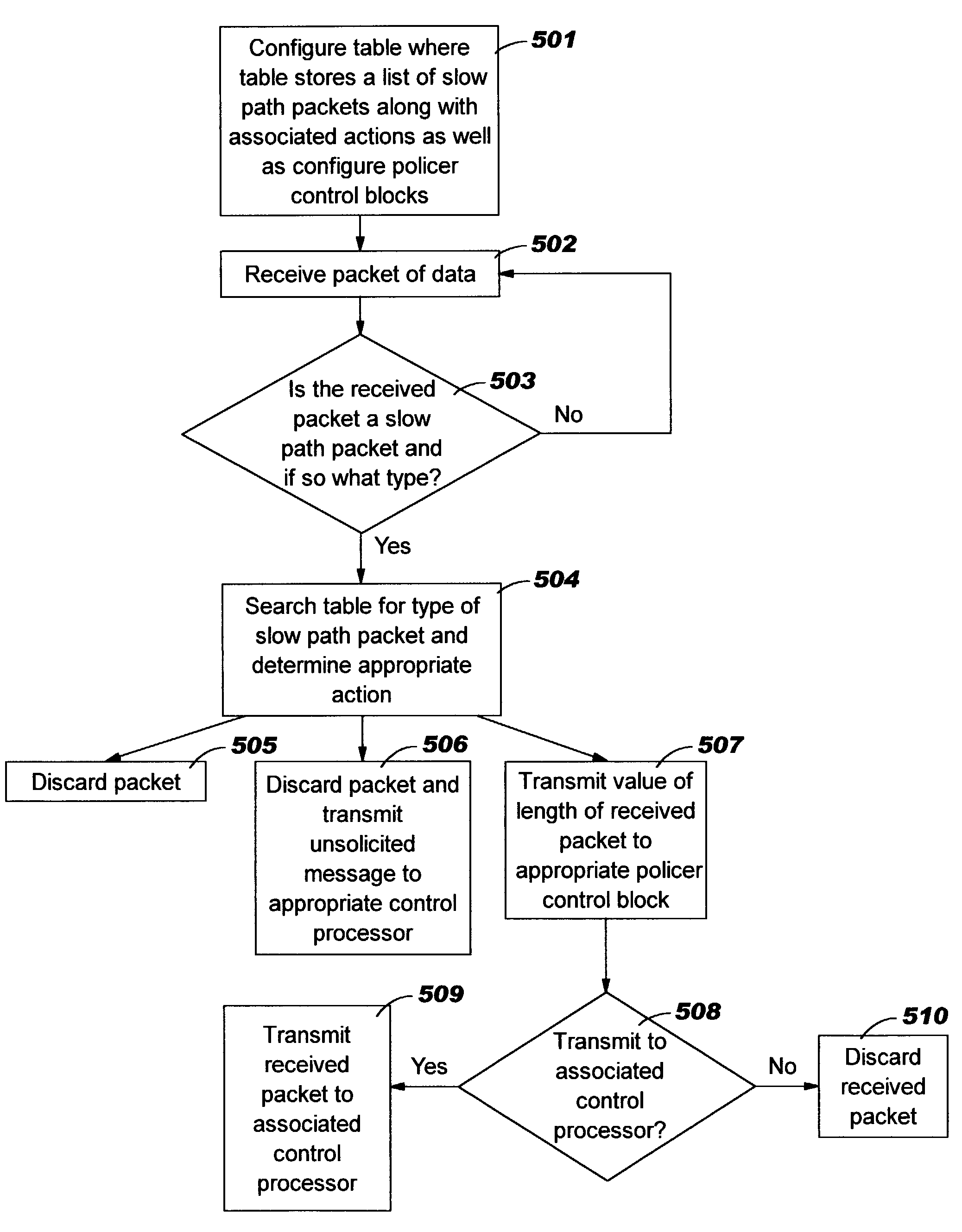
InactiveUS6973503B2Avoid controlExceed processing capacityError preventionTransmission systemsUnit Control BlockFile Control Block
A method, system and computer program product for preventing at least in part overloading of a control processor. A network device may comprise at least one network processor and at least one control processor. The control processor may be configured to process slow path packets that are redirected from a network processor to the control processor. The control processor may configure control blocks to determine if the bandwidth for the control processor will be exceeded by the network processor transferring another slow path packet to the control processor. If the control block determines that transmitting the slow path packet would exceed the processing capacity of the control processor, then the control block may generate a result indicating for the network processor to discard the received packet. By discarding packets that exceed the processing capacity of the control processor, overloading of the control processor may at least in part be prevented.
Owner:IBM CORP
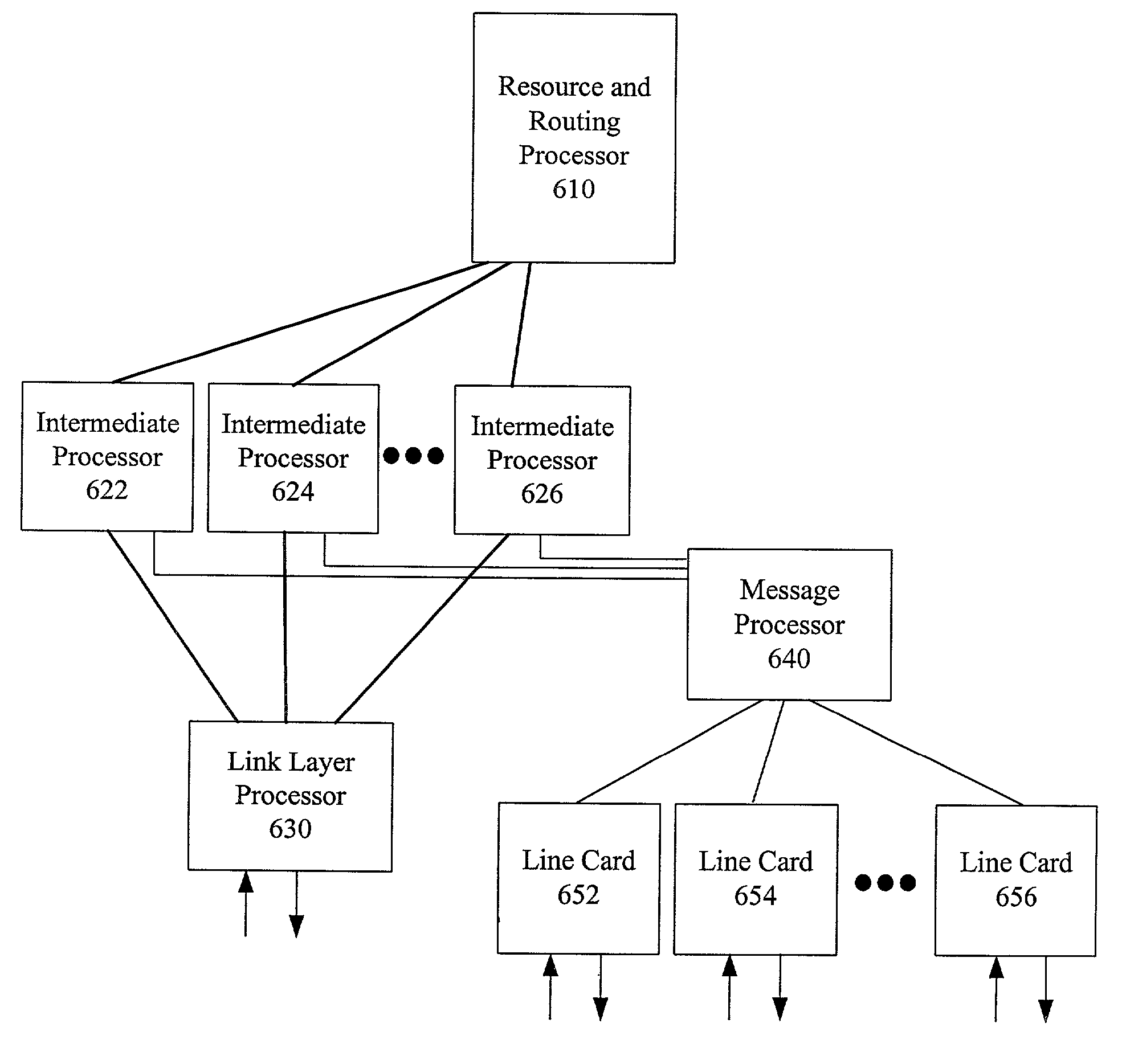
Multiprocessor control block for use in a communication switch and method therefore
InactiveUS7385965B2Time-division multiplexData switching by path configurationMulti processorParallel computing
A communication switch that includes a multiprocessor control block and a method therefore is presented. The multiprocessor control block includes a centralized resource and routing processor that controls resource allocation and routing functionality within the switch. A plurality of intermediate processors operably coupled to the resource and routing processor perform call processing for corresponding portions of the connections supported by the switch, where such call processing includes issuing resource allocation requests to the resource and routing processor. Each of the intermediate processors further performs functions associated with a signaling layer portion of the protocol stack. The multiprocessor control block also includes a link layer processor operably coupled to the plurality of intermediate processors, where the link layer processor also couples to a switching fabric of the communication switch. The link layer processor receives ingress data units from the switching fabric and selectively forwards these ingress data units to one or more of the plurality of intermediate processors for processing. The link layer processor also received egress data units from the plurality of intermediate processors that it forwards to the switching fabric.
Owner:ALCATEL CANADA
Data structure supporting random delete and timer function
InactiveUS20080133467A1Easy to handleOptimize data structureData processing applicationsDigital computer detailsHigh rateFile Control Block
A procedure is used to provide data structures that handle large numbers of active data entries and a high rate of additions and deletions of active entries. The procedure utilizes one or more of the following modifications. Timers are removed from individual session table entries and are linked via pointers. Bilateral links are established between the session table and the timer structure. Aging / timer checks are applied to the timer control block (TCB). A chain of TCBs, optionally including an excess of blocks, may be used along with packing of multiple TCBs into a single memory location. This excess of blocks permits a terminated session to continue to occupy a TCB until the timer process progresses to that block location in the chain of blocks.
Owner:IBM CORP
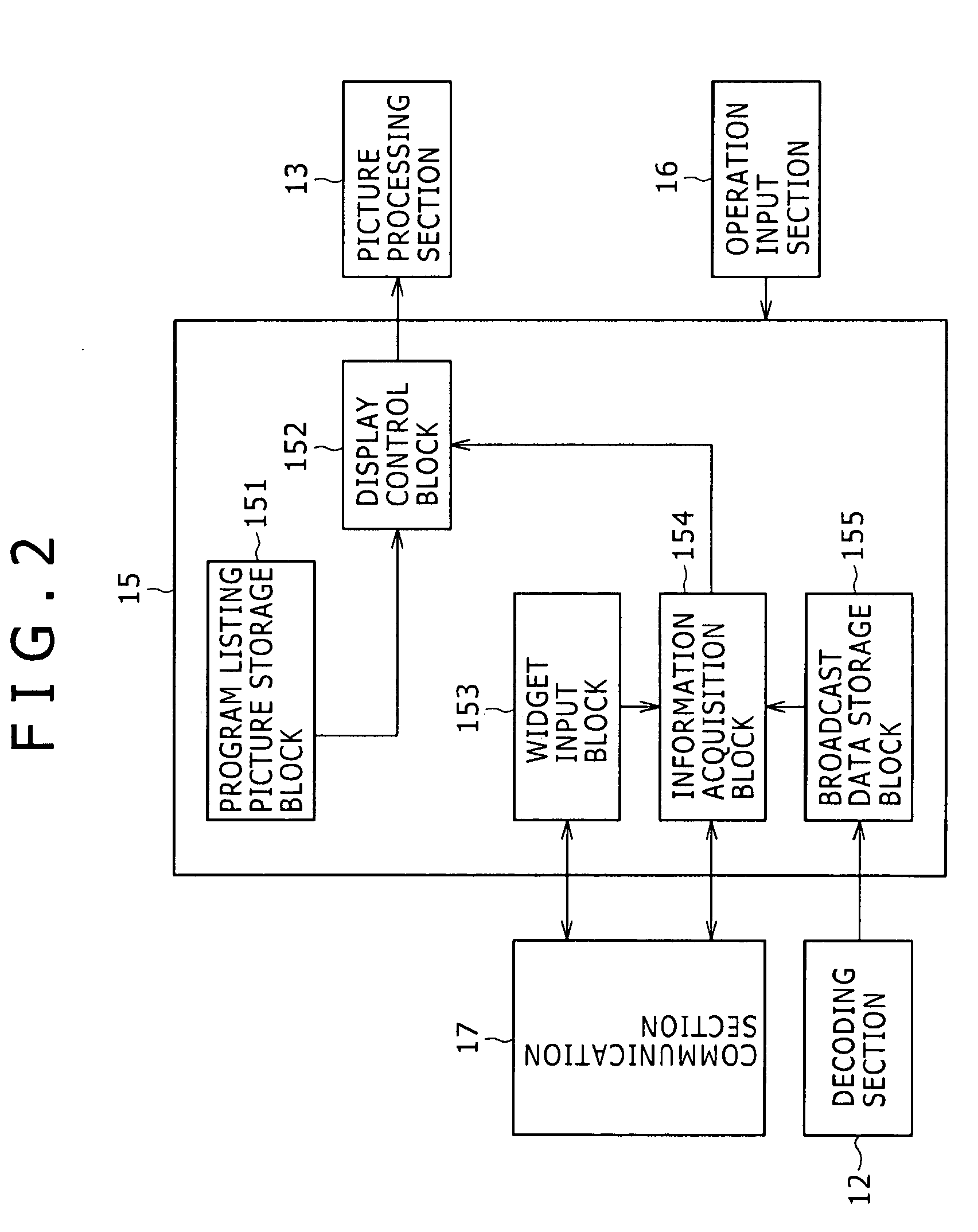
Program listing display control apparatus, program listing display apparatus, and program listing display control method
ActiveUS20100031293A1Guarantee bird's-eye visibilityReduce workloadTelevision system detailsColor television detailsInput controlFile Control Block
Disclosed herein is a program listing display control apparatus including: a program listing picture storage block configured to store a program listing picture in which are disposed program time slots to which a plurality of broadcast programs are allocated; a display control block configured to control a display apparatus to display the program listing picture; a control information input block configured to input control information for controlling the acquisition of additional information to be added to the program listing picture; and an information acquisition block configured to acquire program identification information for identifying the programs to which the additional information is added and the additional information regarding the programs identified by the program identification information, on the basis of the control information input through the control information input block.
Owner:SATURN LICENSING LLC
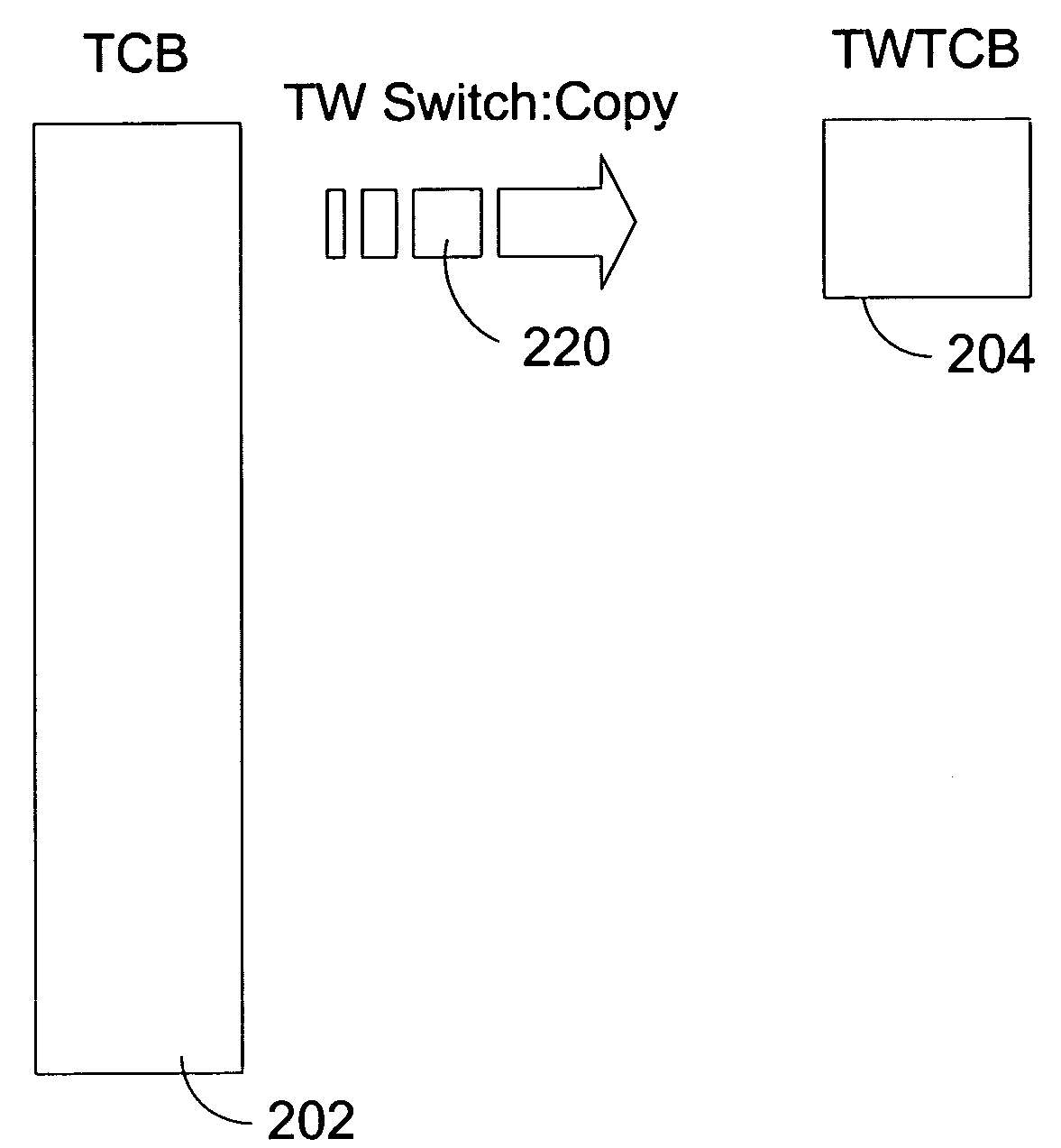
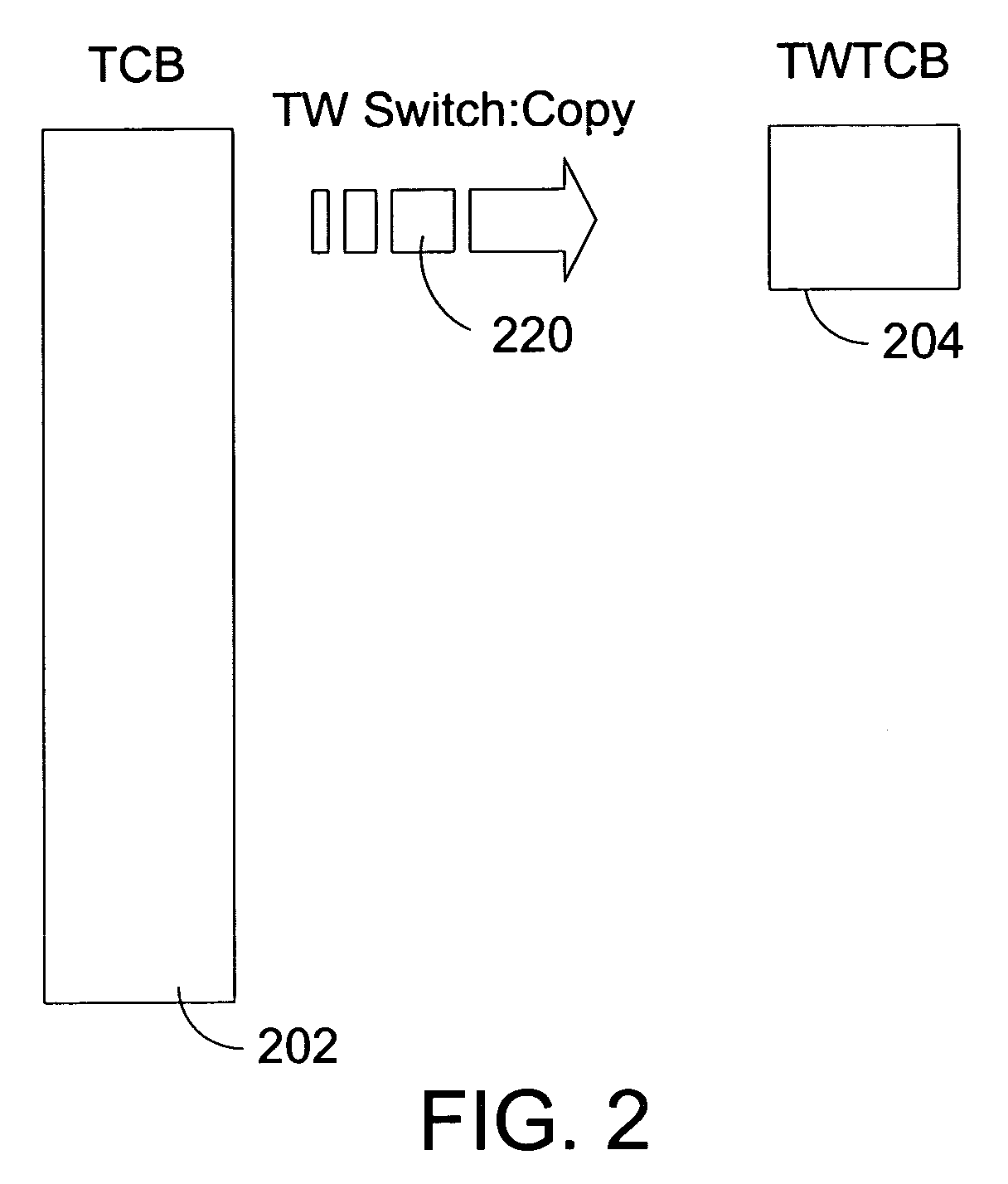
System and method of enhancing server throughput by minimizing timed-wait TCP control block (TWTCB) size
InactiveUS7263556B1Increase performance throughputReduce the amount of informationMultiple digital computer combinationsTransmissionNetwork packetFile Control Block
A system and method to improve server throughput is presented. This system and method stores only selected information from the server's TCP / IP Transmission Control Block (TCB) in the time-wait state. This allows for the release of a portion of the non-paged pool (NPP) memory that was used by the TCB to previously service the now closing connection. This newly released NPP memory may then be used by the server to service additional TCP / IP connections, thus improving the throughput of the server. This small time-wait TCB (TWTCB) stores only an amount of information necessary to uniquely identify the connection to which it relates. Information that was stored to allow servicing of an active connection, but that is not needed to merely identify the connection, is not kept in the TWTCB. By maintaining information that allows for a unique identification of a closing connection, late routed packets for that connection are prevented from establishing a new connection with the server. By minimizing the amount of information to accomplish this unique identification, additional connections to new client may be established without reaching a NPP memory limit.
Owner:MICROSOFT TECH LICENSING LLC
File control system and file control device
InactiveUS7624324B2Optimize dataImprove reliabilityInput/output to record carriersError preventionDirect memory accessExternal storage
A file control system performing DMA (direct memory access) transfer is provided. The file control system includes file control devices, and each of the file control devices is provided between a host computer and an external storage device. A first file control device among the file control devices checks for errors in the data read from a memory, changes the error detection code added to the read data from a first error detection code to a second error detection code, changes at least a part of the data when an error is detected, and executes DMA-transfer of the data, which is changed or is not changed, to a second file control device of the transfer destination.
Owner:FUJITSU LTD
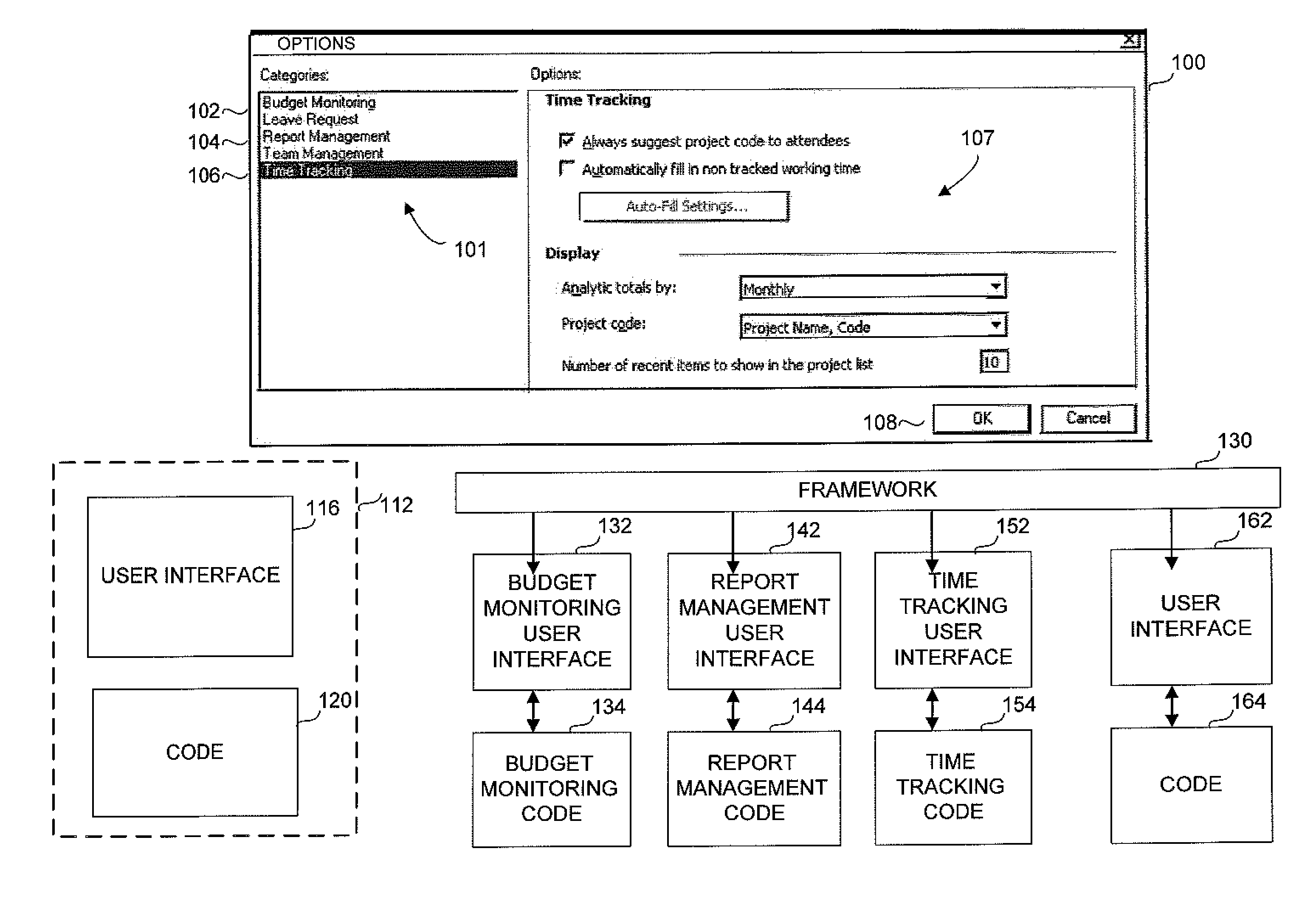
Method and apparatus for multi-file controls
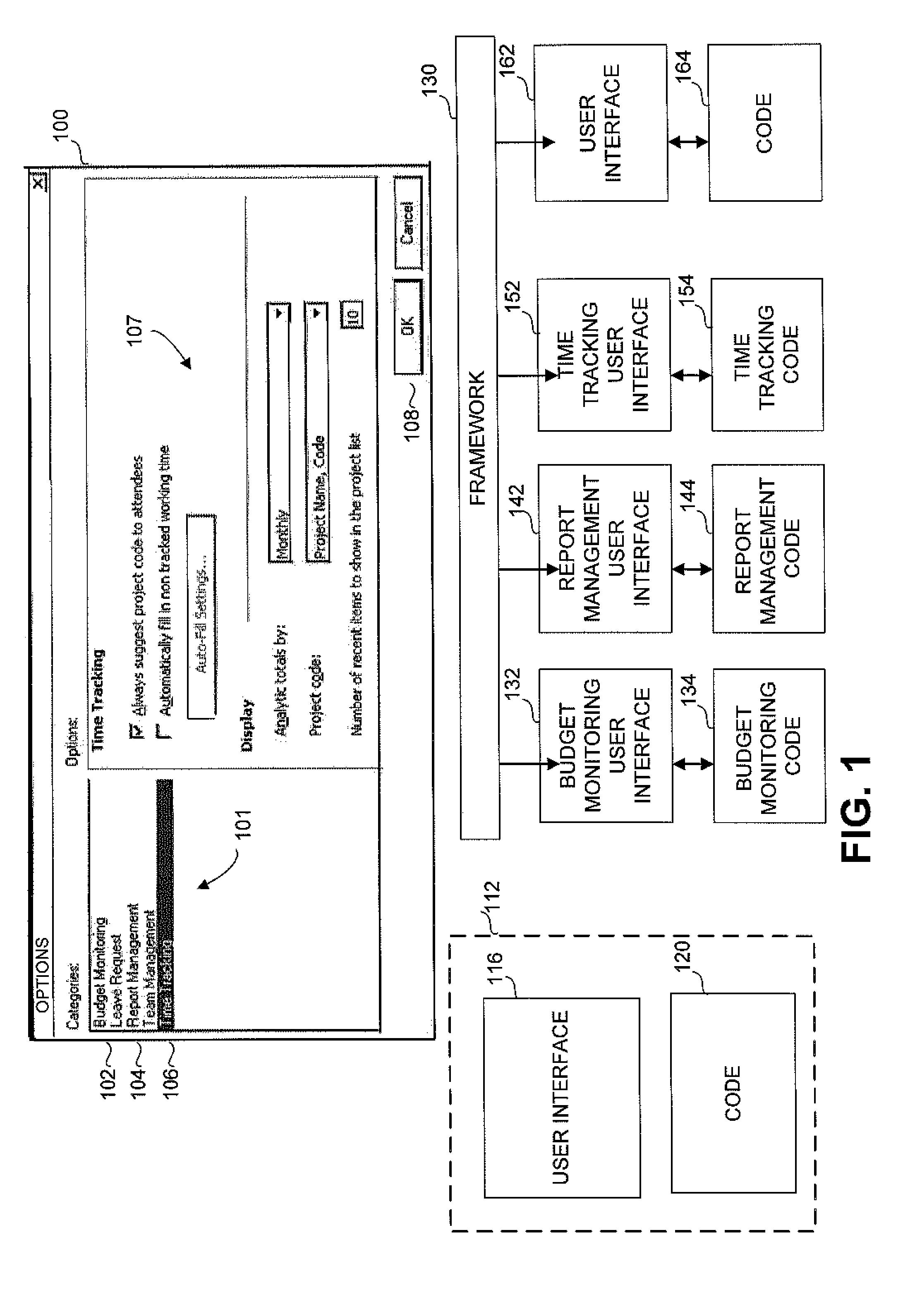
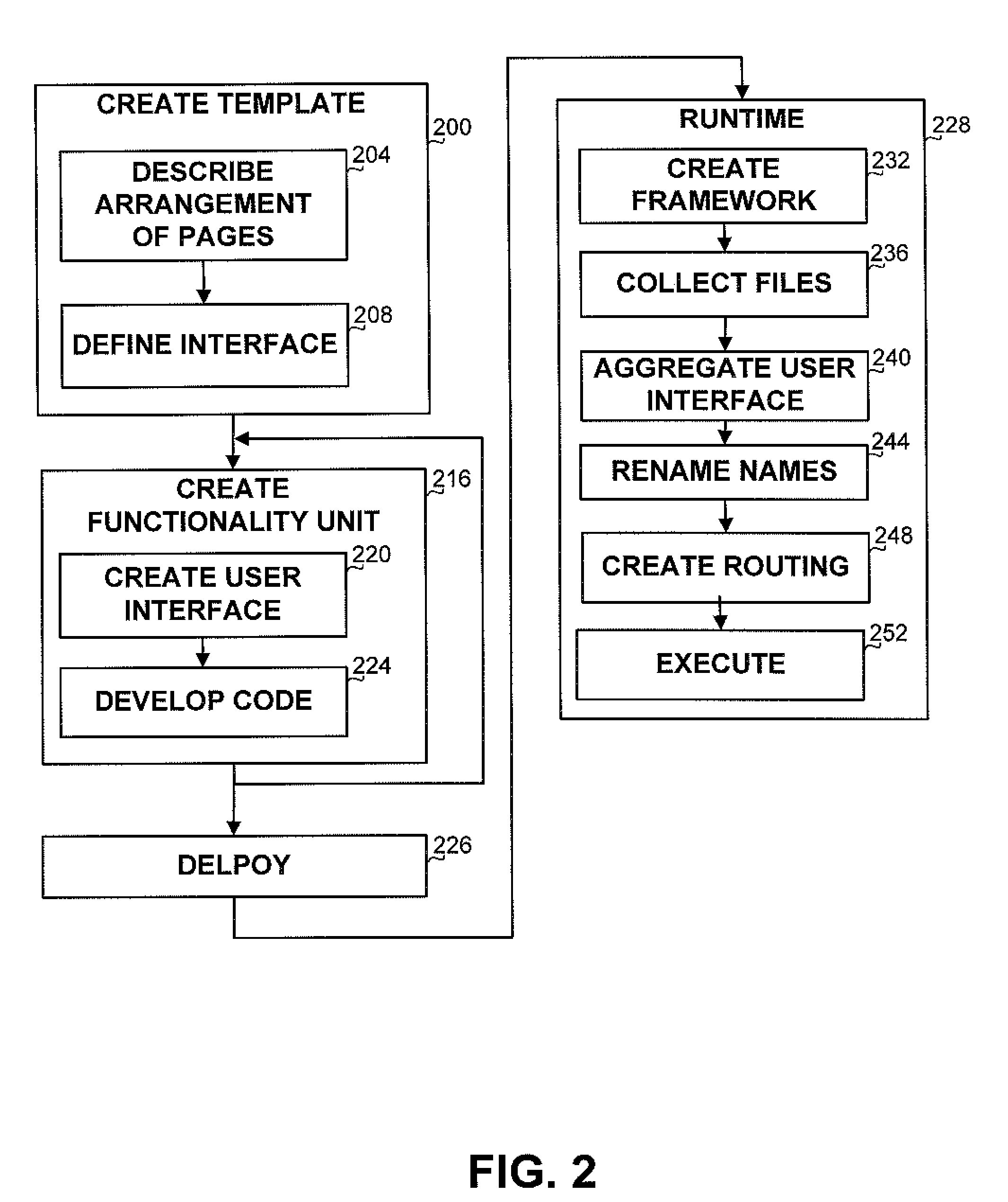
ActiveUS8423895B2Software designInput/output processes for data processingFile Control BlockSingle pair
A method and apparatus for enabling a unit such as a complex control comprising multiple pages, which should be implemented as a single pair of user interface file and code file, to be implemented in a multiplicity of files, to enable multiple developers to work concurrently on the control, and to enable dynamic addition, deletion or update of pages in a control. The method comprises constructing a template describing the complex control, generating separate pages according to the template, and in run time aggregating the separate pages, renaming elements within the separate pages and routing events to the event handlers implemented by the separate pages.
Owner:SAP AG
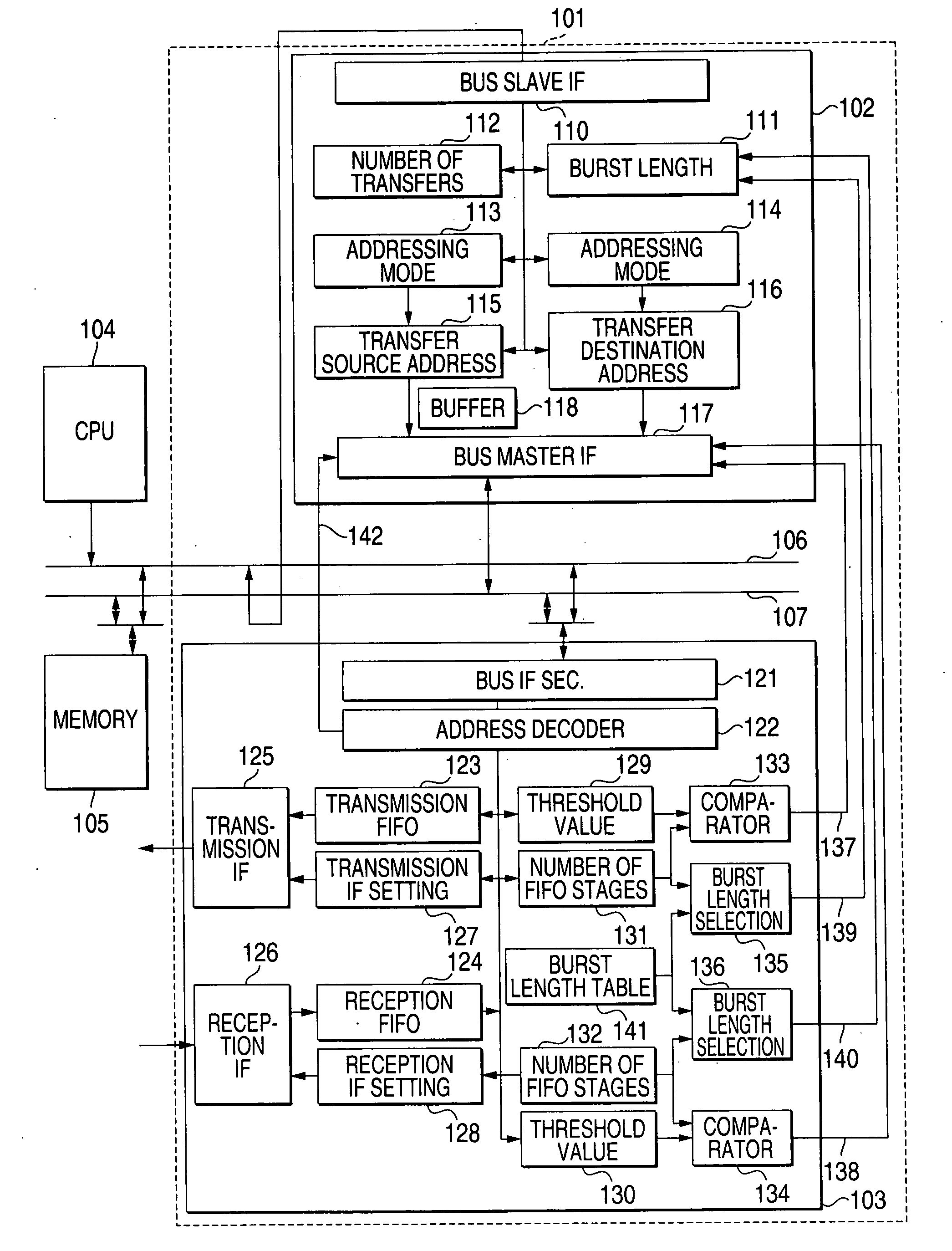
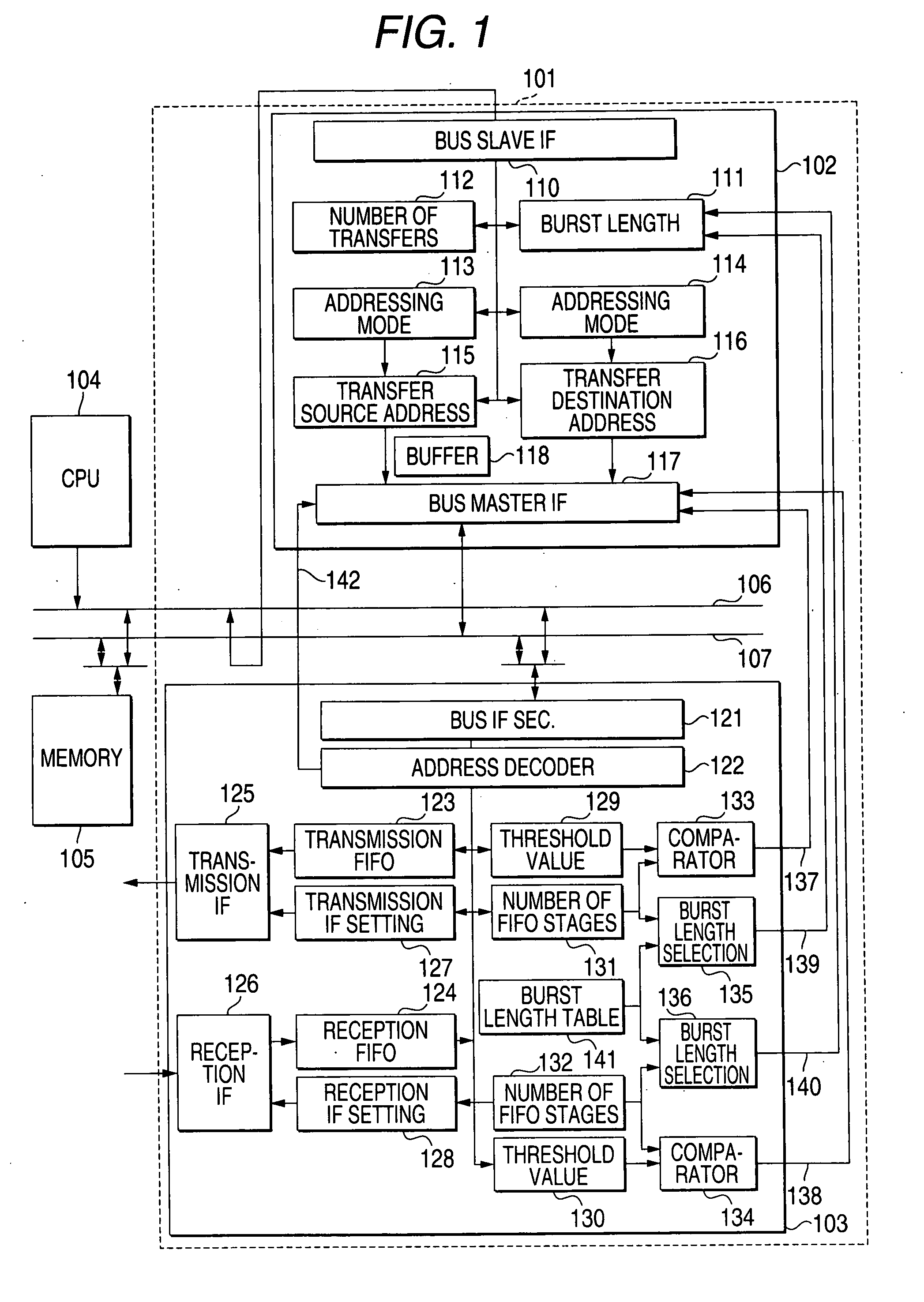
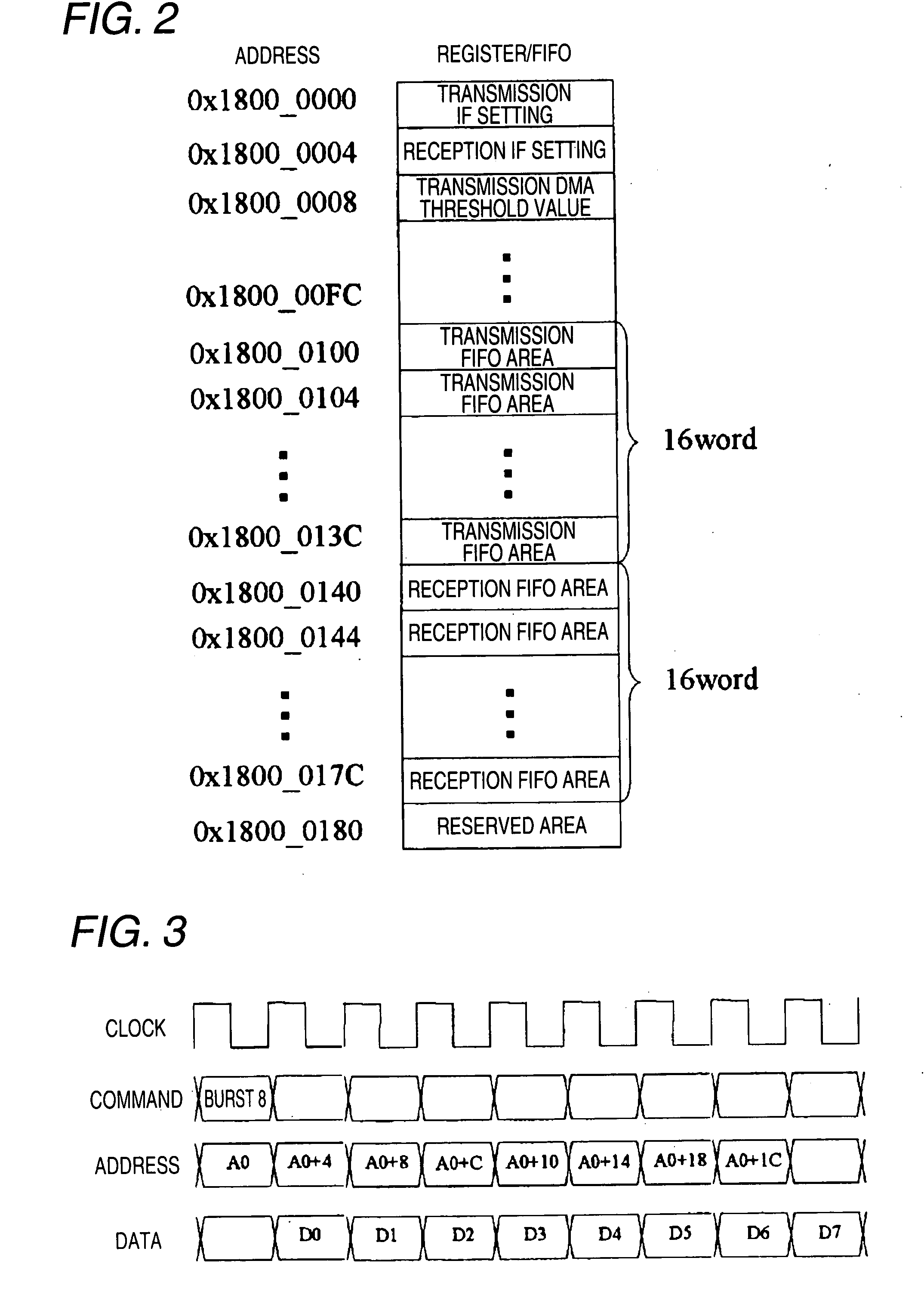
DMA transfer apparatus
InactiveUS20080320178A1Avoid a FIFO overflowMinimize timeElectric digital data processingBurst transmissionProcessor register
A DMA transfer apparatus 101 is equipped with a DMA control block 102 and a FIFO-incorporated block 103. The DMA control block 102 is connected, as a bus master, to a DMA bus capable of burst transfer and having a function of controlling a burst transfer by generating burst access for sending data consecutively a certain number of times while incrementing the address after sending a command. The FIFO-incorporated block 103 is connected the DMA bus as its slave and having a FIFO whose address is mapped to a continuous address space. An arrangement is provided so that a parameter dedicated to FIFO transfer can be set in an addressing mode setting register of a control register group of the DMA control block 102, whereby a burst transfer to or from the FIFO whose address is mapped to the continuous address space is controlled.
Owner:PANASONIC CORP
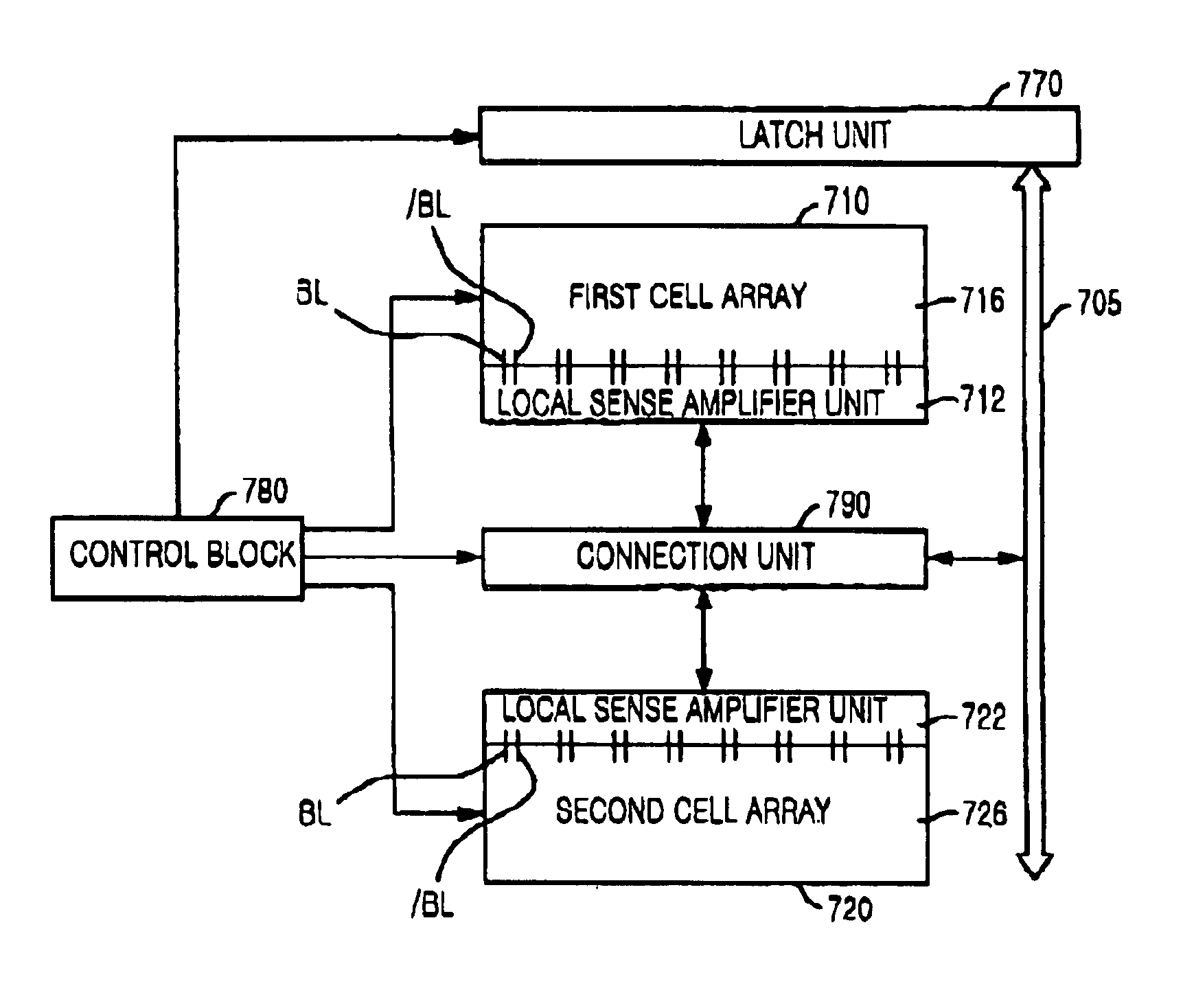
Semiconductor memory device with reduced data access time
A memory device includes at least two cell blocks connected to a global bit line for outputting data in response to an instruction; at least one global bit line connection unit for selectively connecting the global bit line to each cell block under control of a control block, one global bit line connection unit being allocated between the two cell blocks; and said control block for controlling output of data stored in each cell block to the global bit line and restoration of the outputted data of the global bit line to the original cell block or another cell block which is determined by depending upon whether data in response to a next instruction is outputted from the original cell block or another cell block.
Owner:SK HYNIX INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com