Patents
Literature
647 results about "Temporary file" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Temporary files, or foo files (.TMP), are files created to temporarily contain information while a new file is being made. It may be created by computer programs for a variety of purposes; principally when a program cannot allocate enough memory for its tasks, when the program is working on data bigger than the architecture's address space, or as a primitive form of inter-process communication.
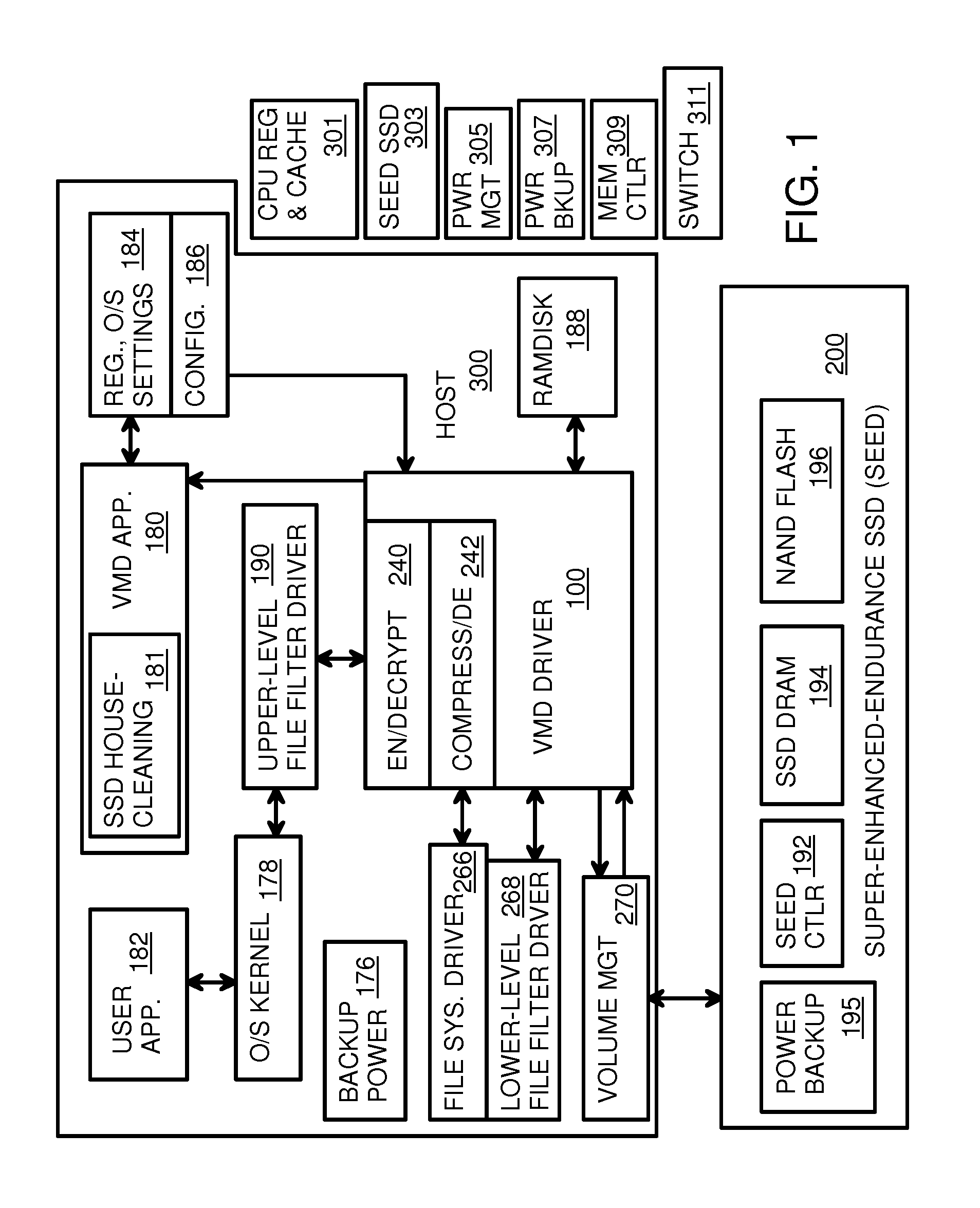
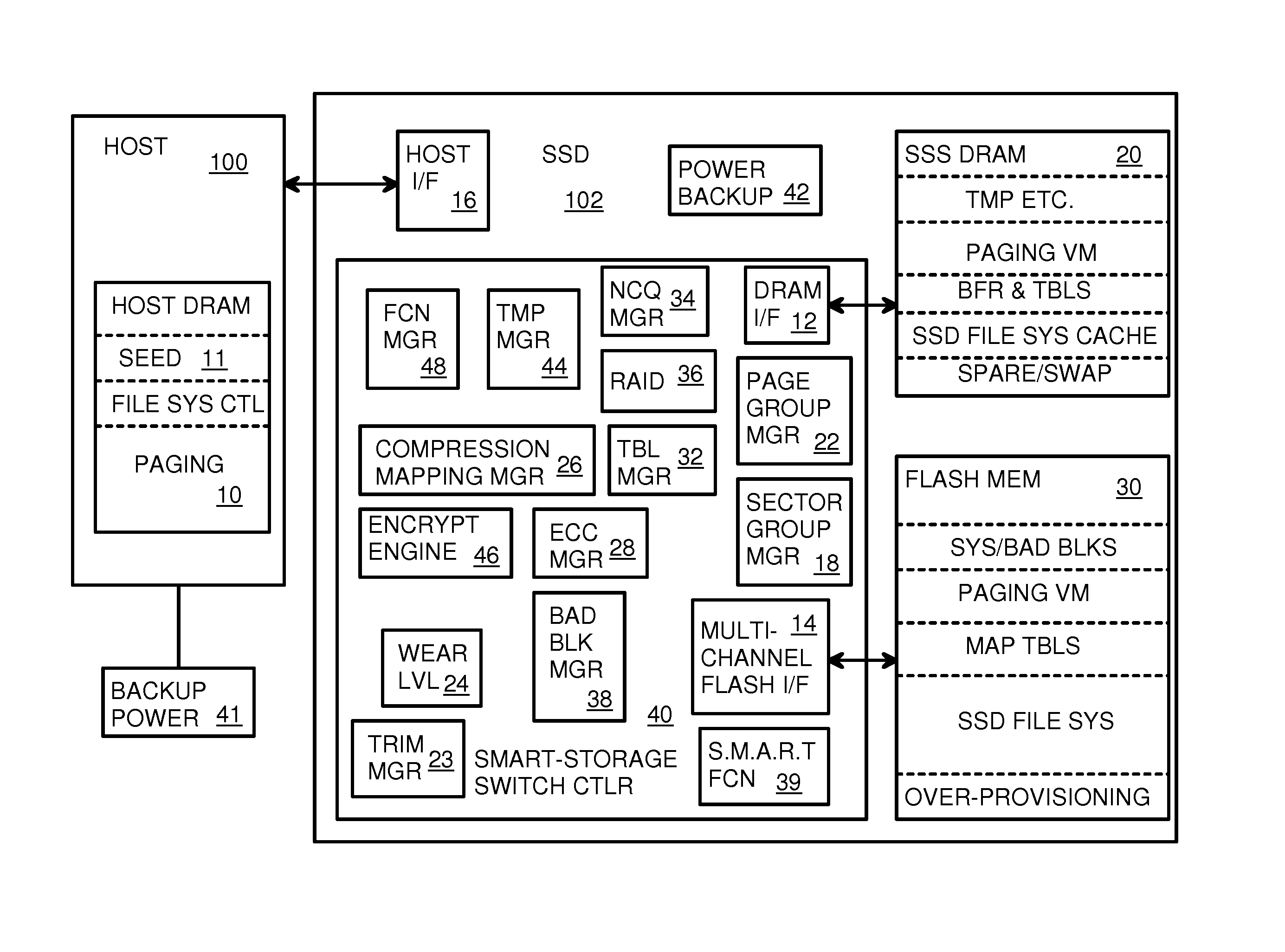
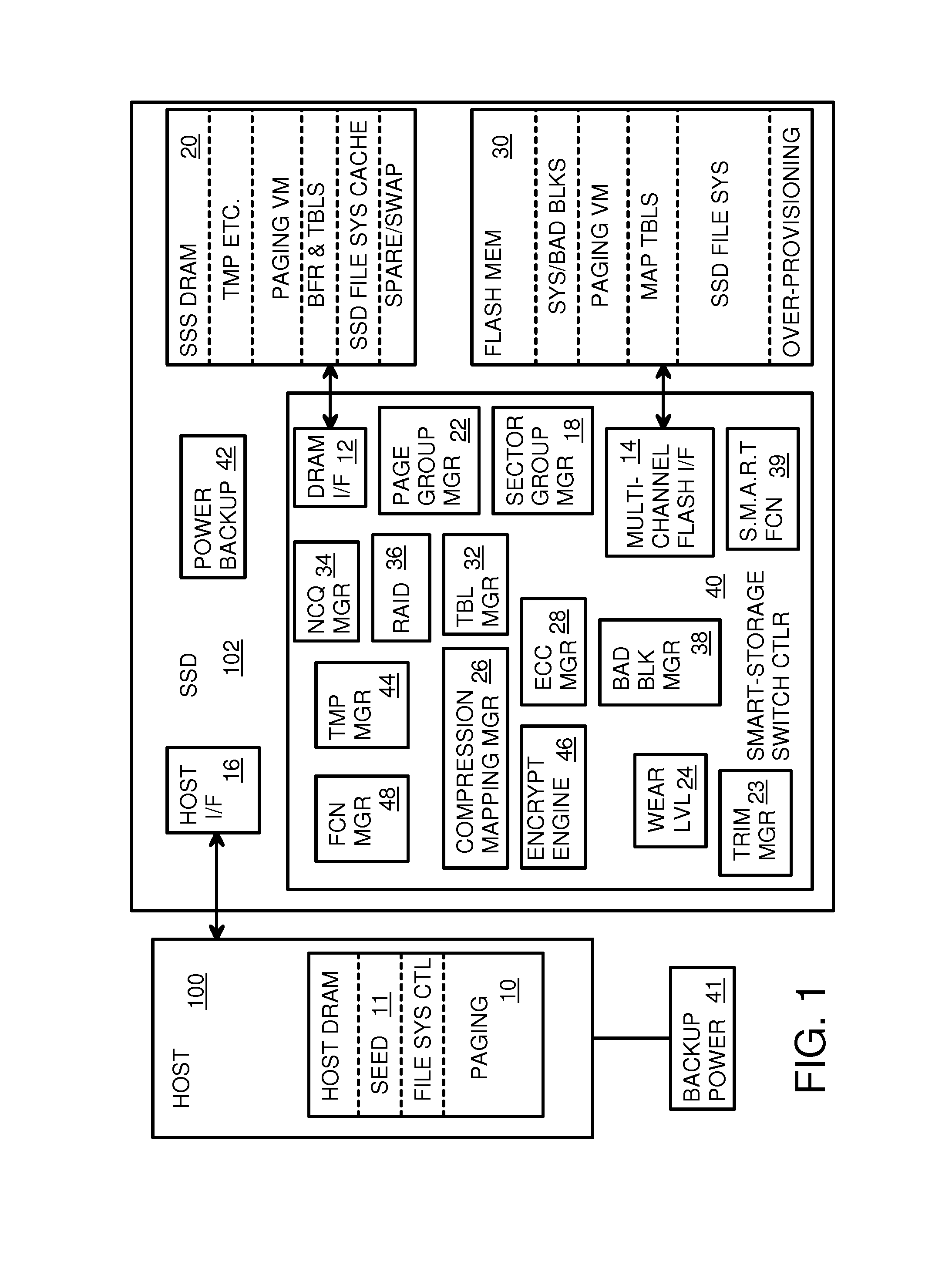
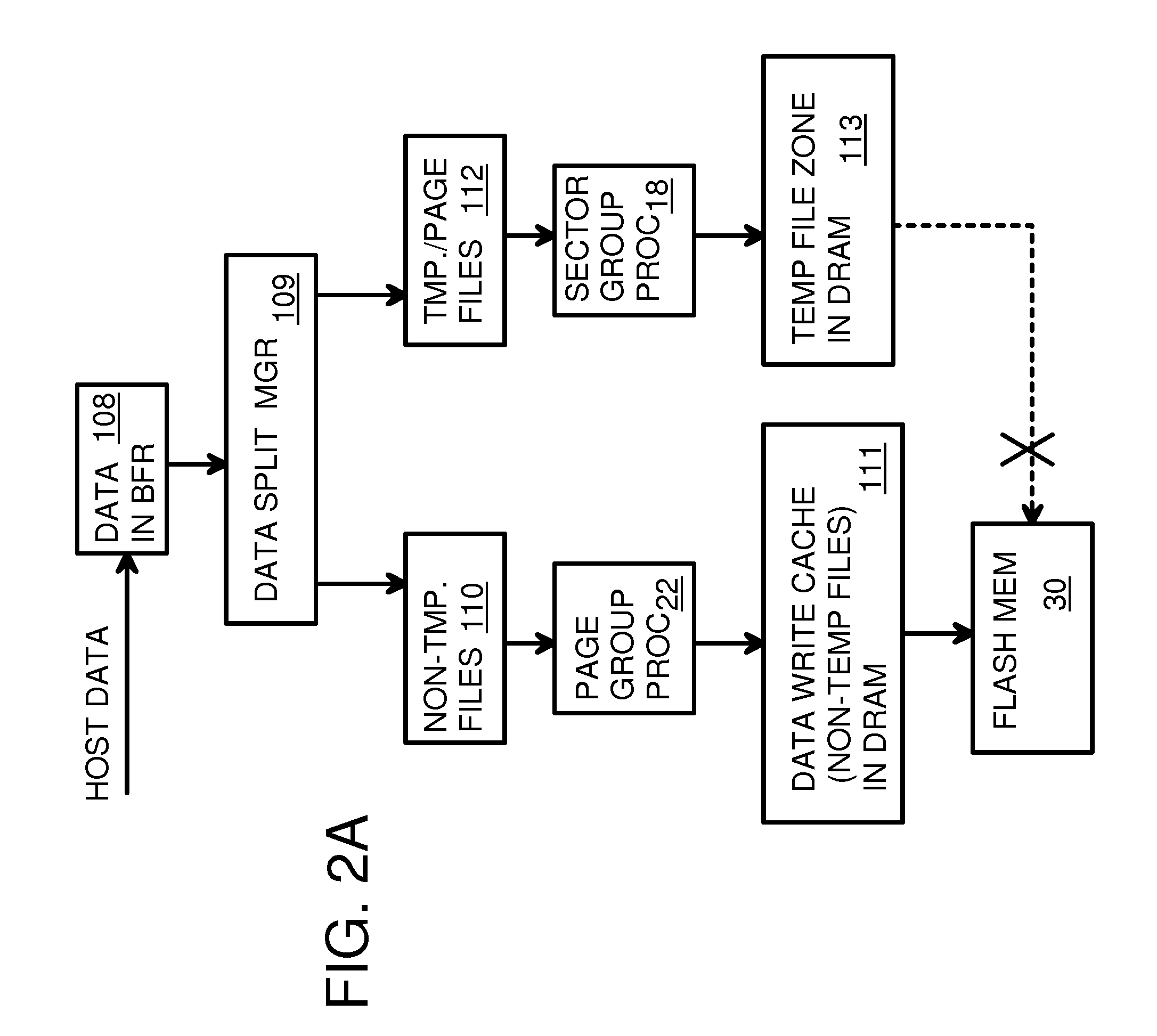
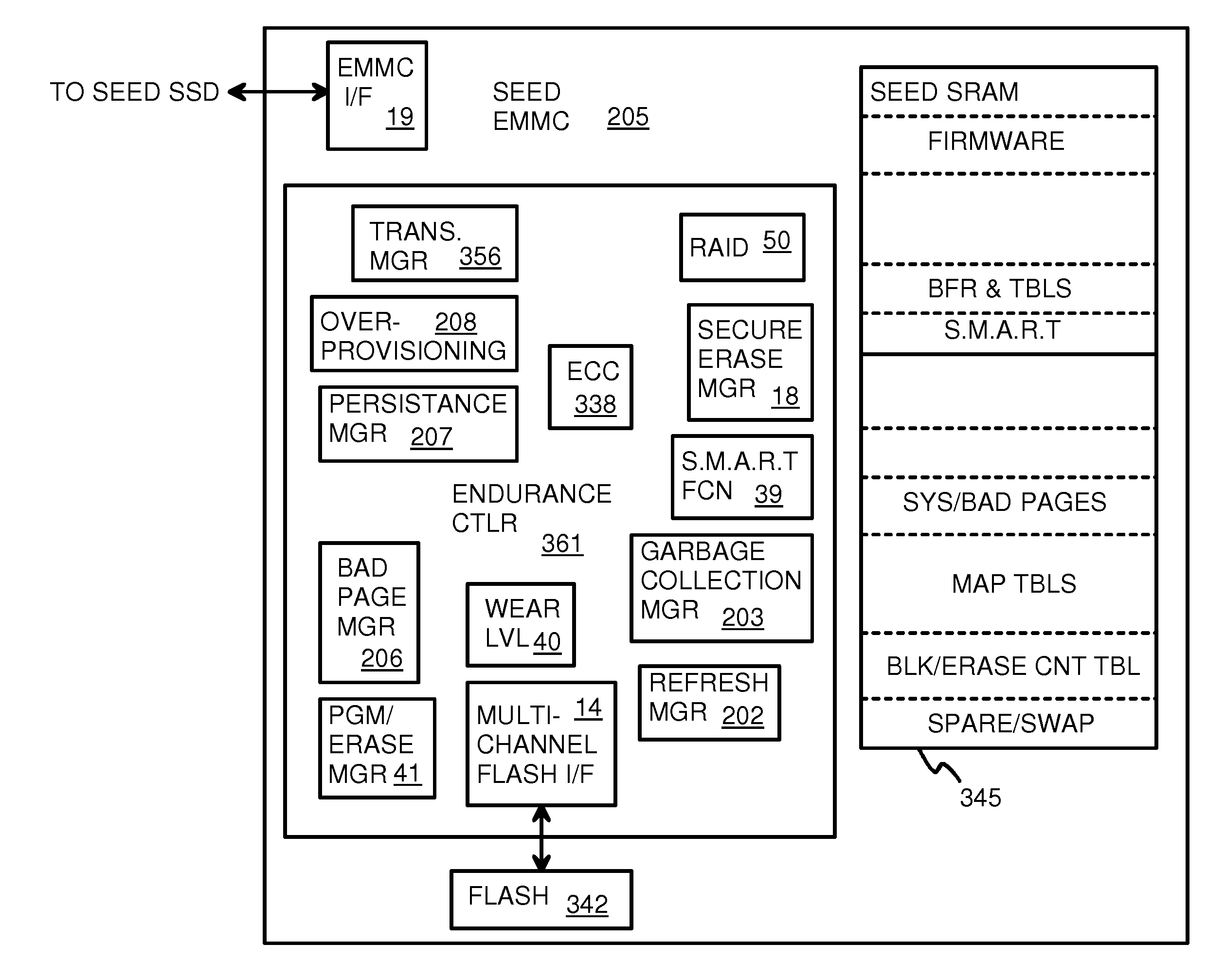
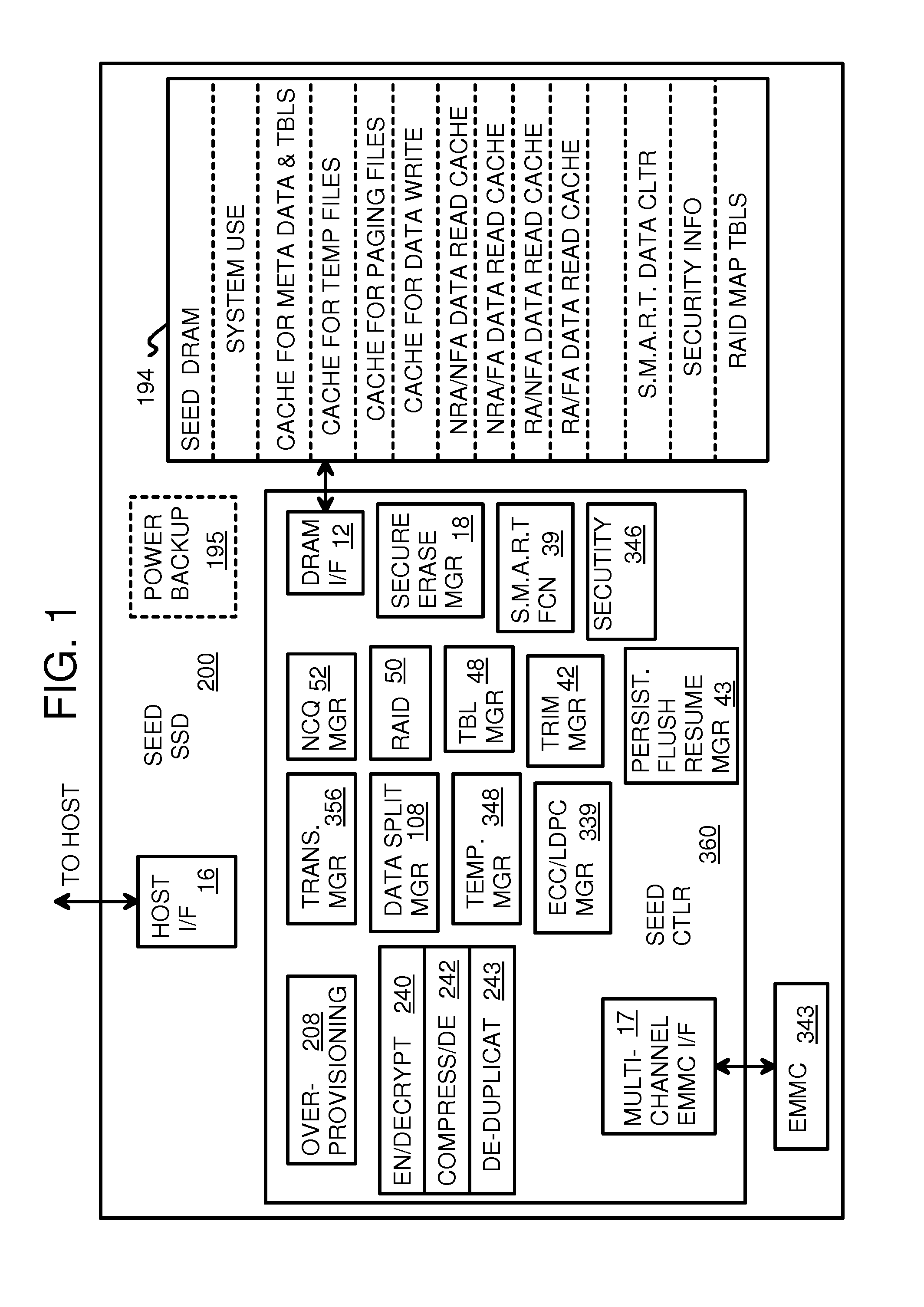
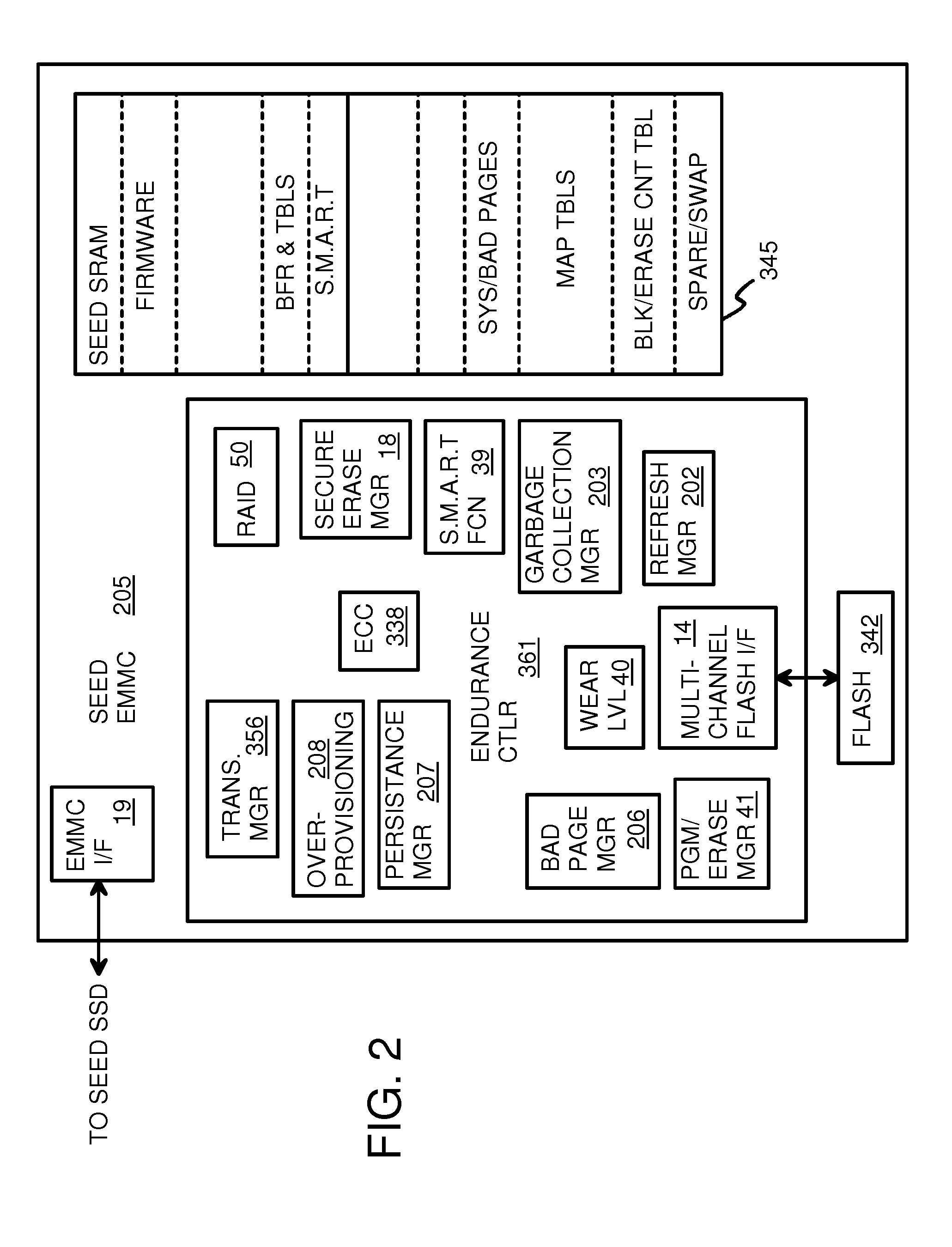
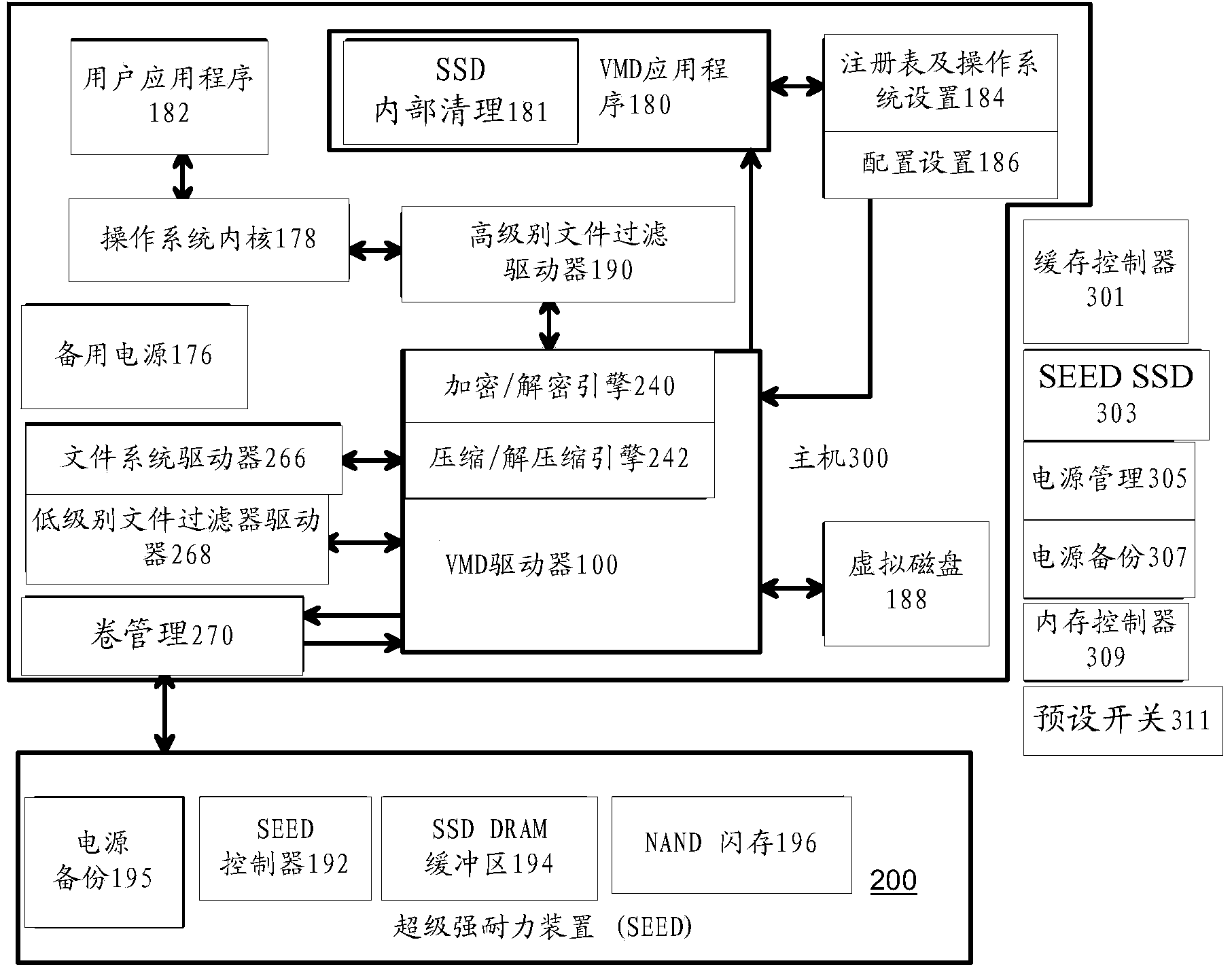
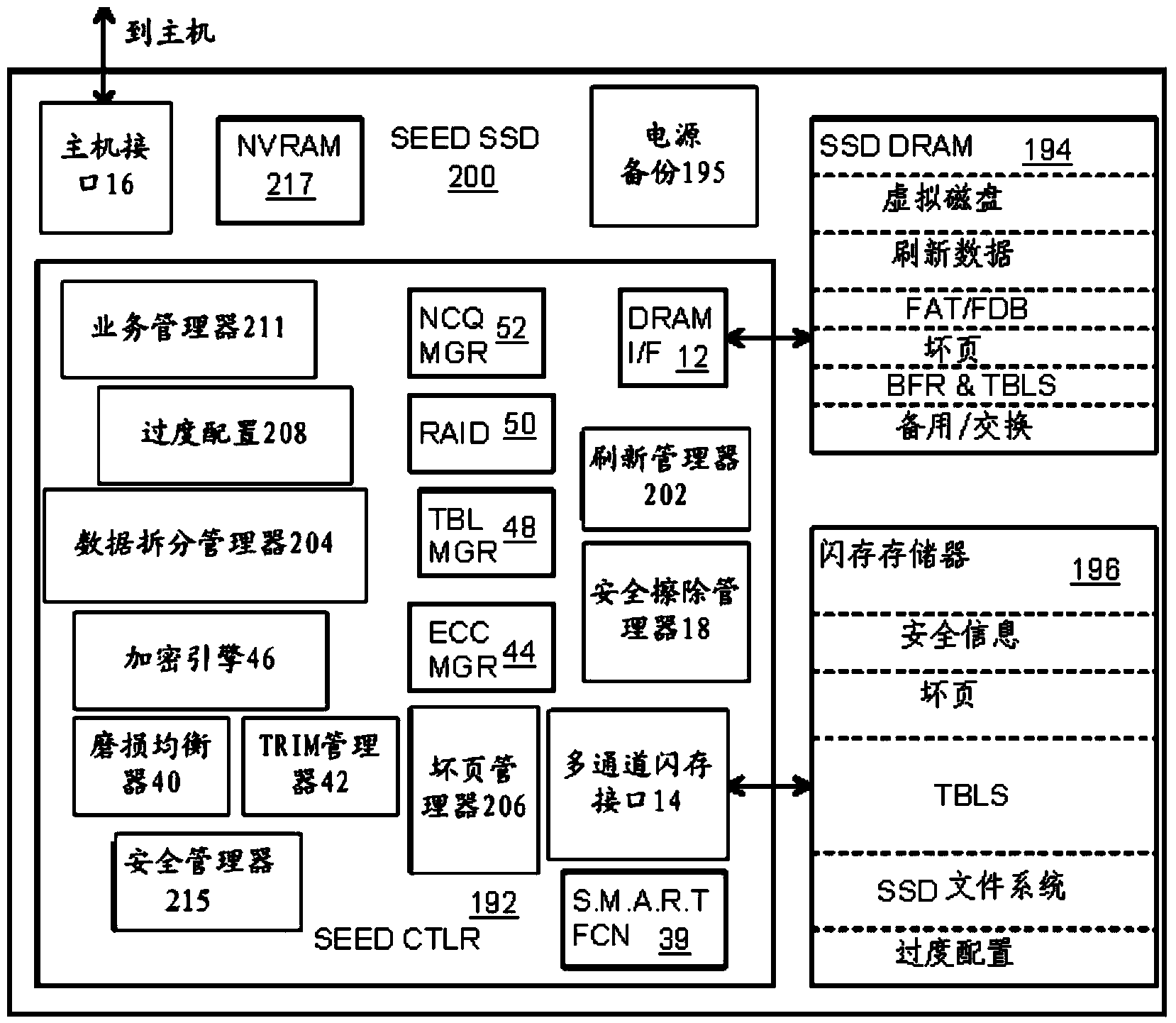
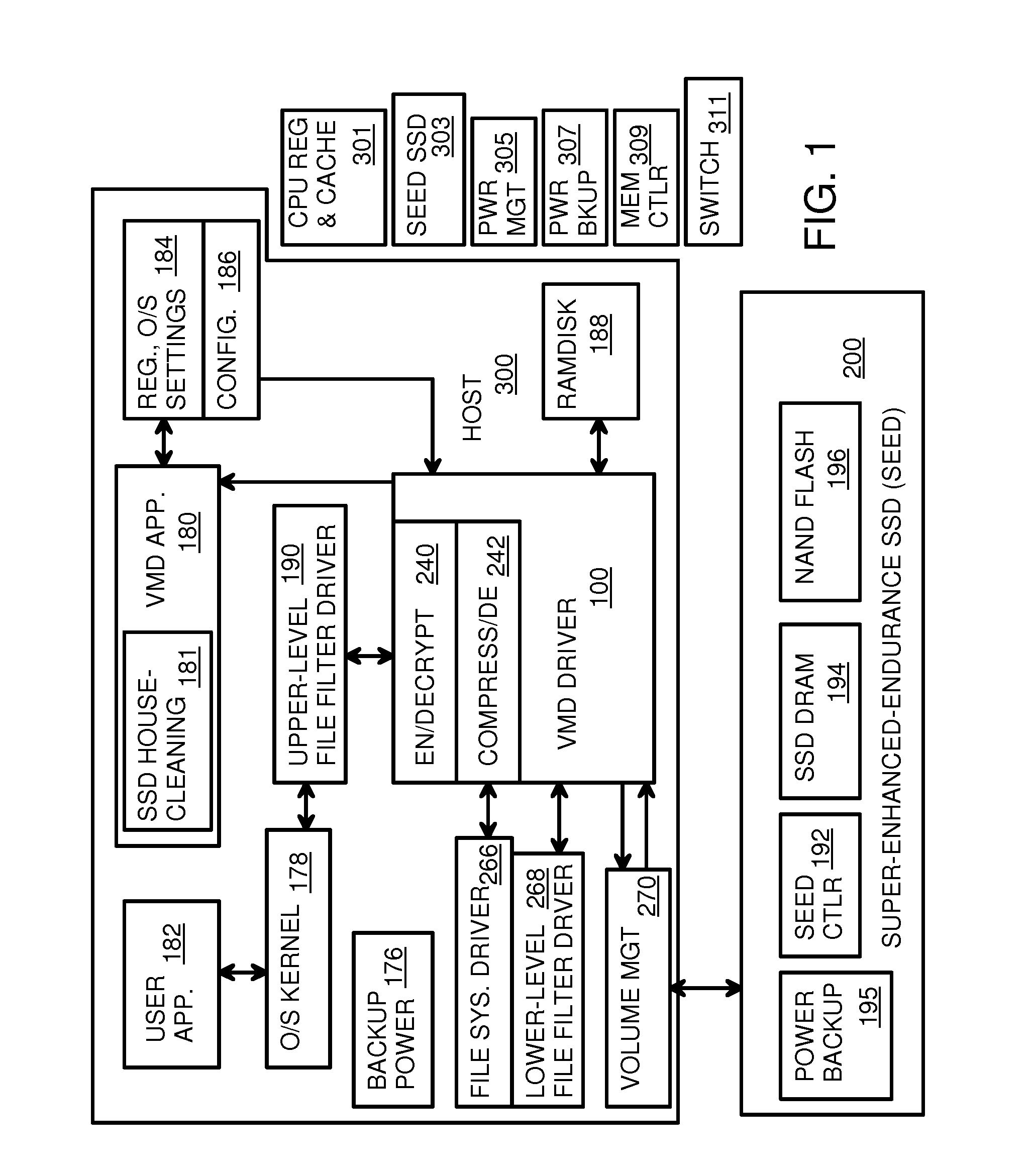
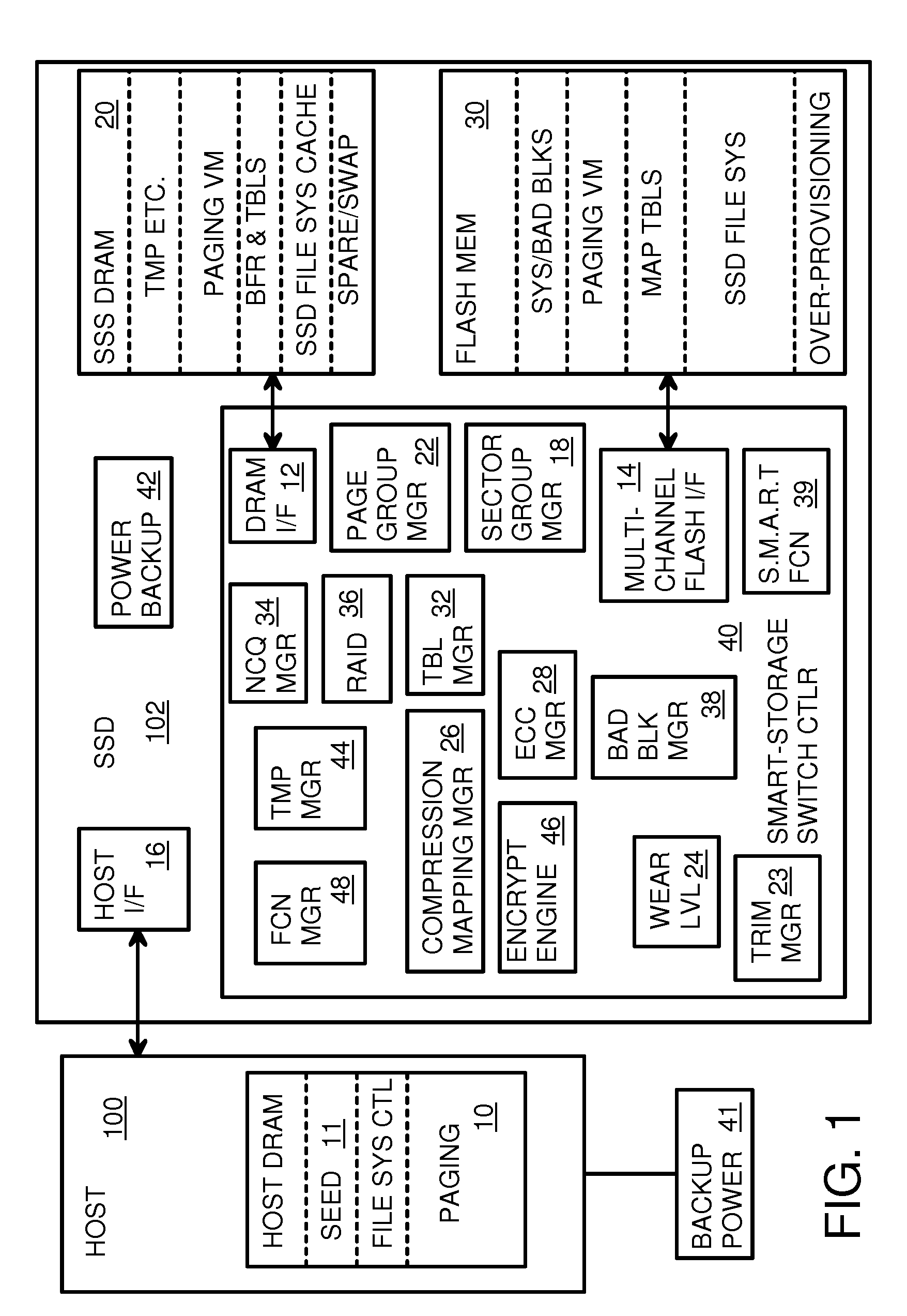
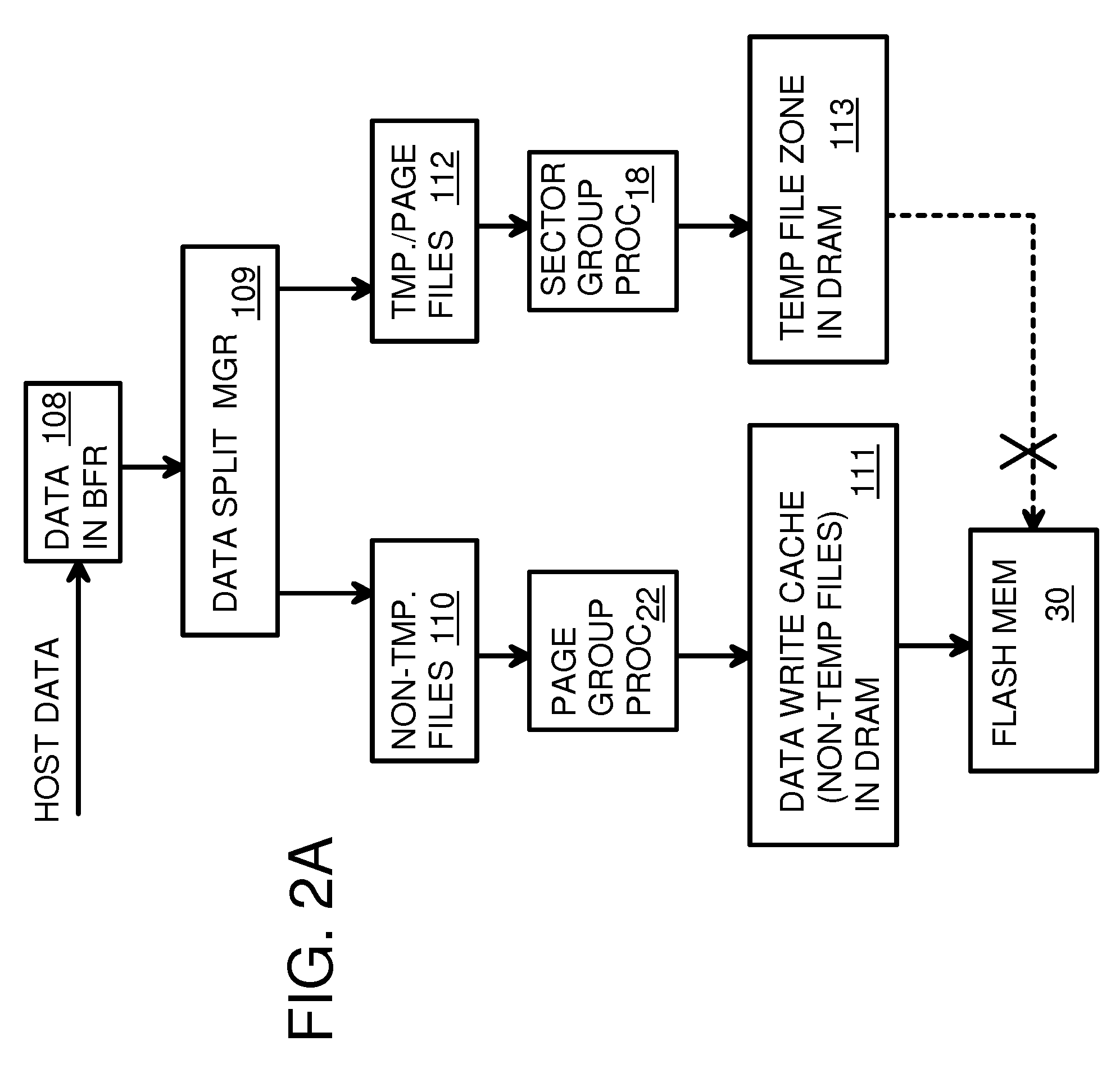
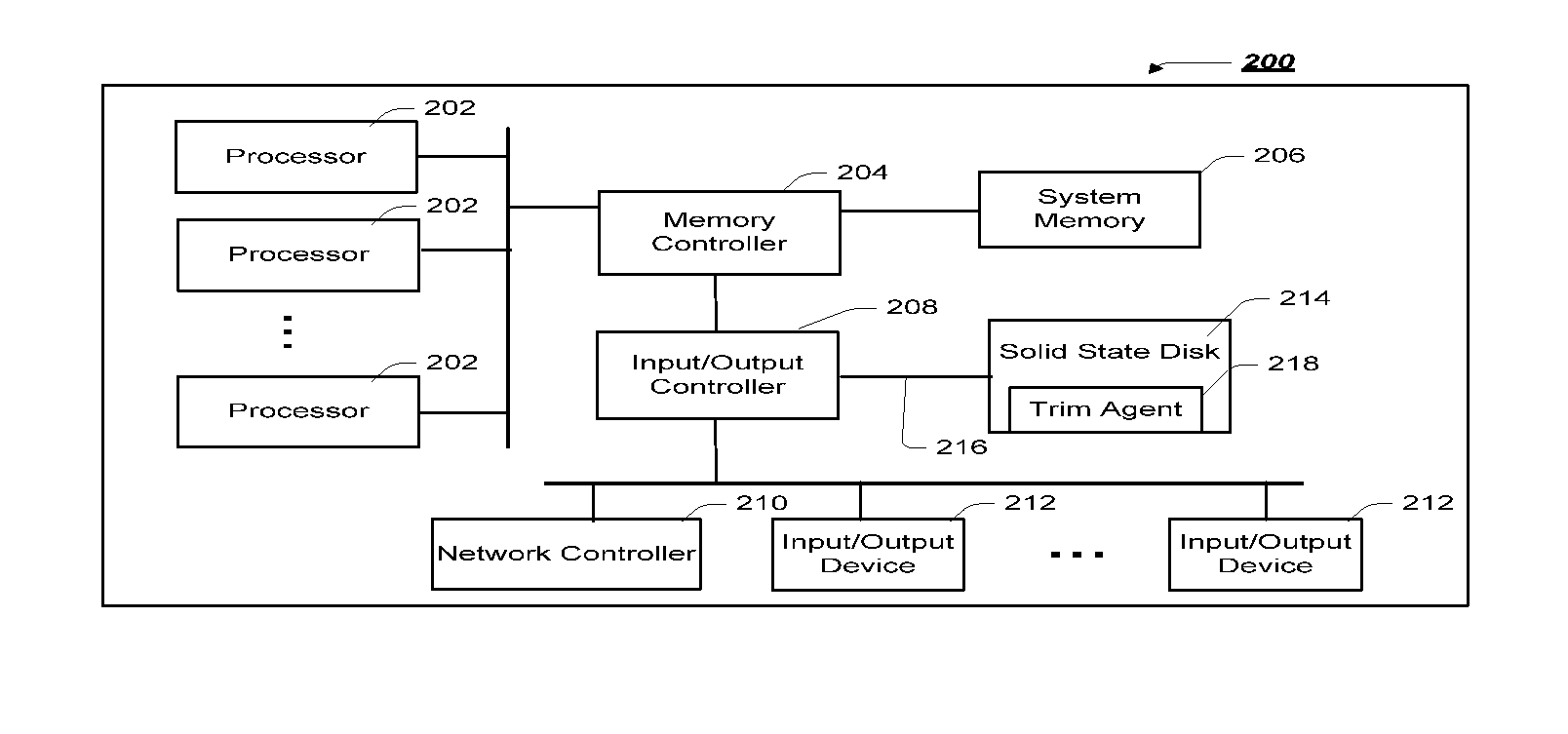
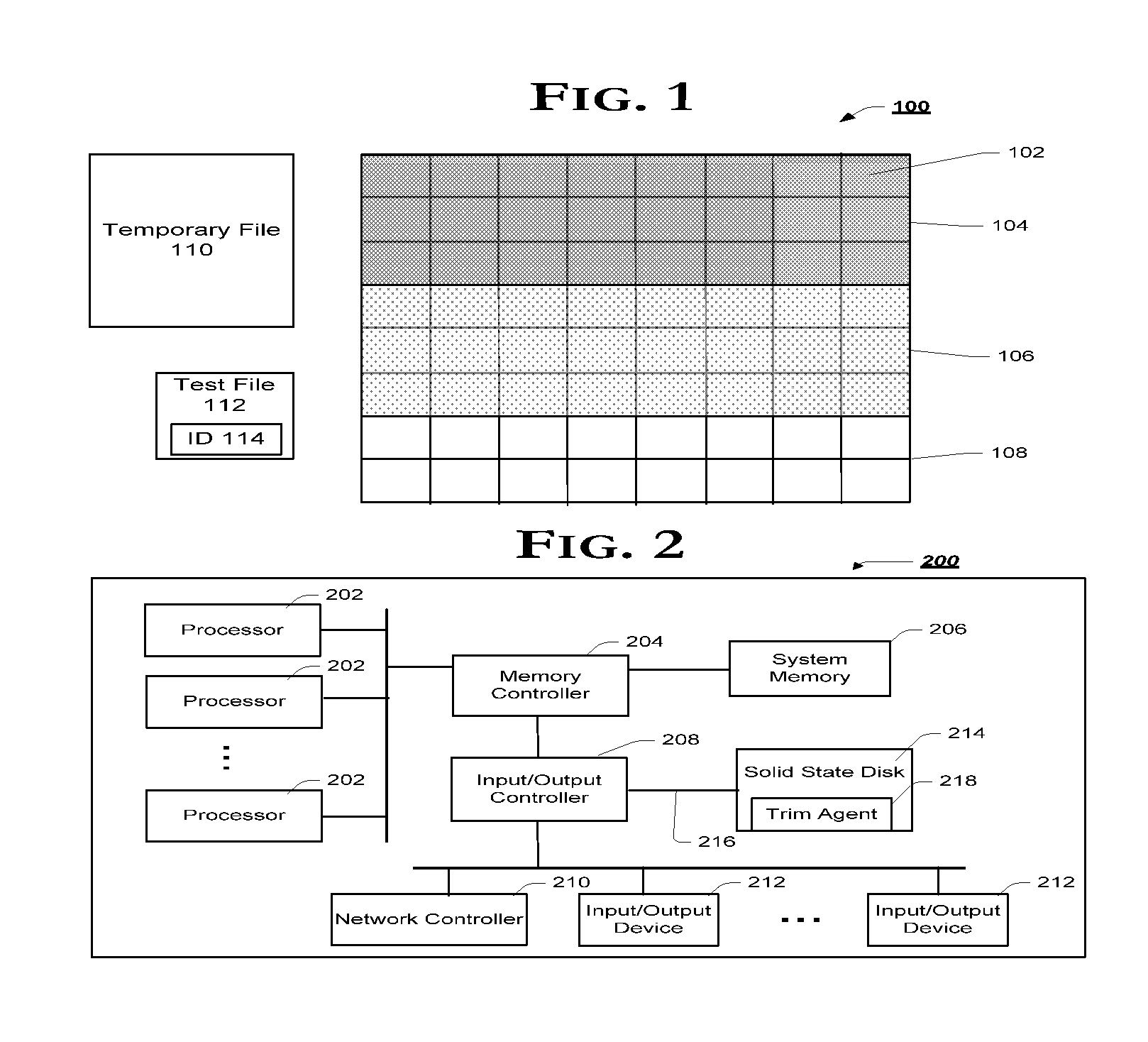
Super-Endurance Solid-State Drive with Endurance Translation Layer (ETL) and Diversion of Temp Files for Reduced Flash Wear
ActiveUS20120284587A1Memory architecture accessing/allocationDigital storageFilename extensionData file
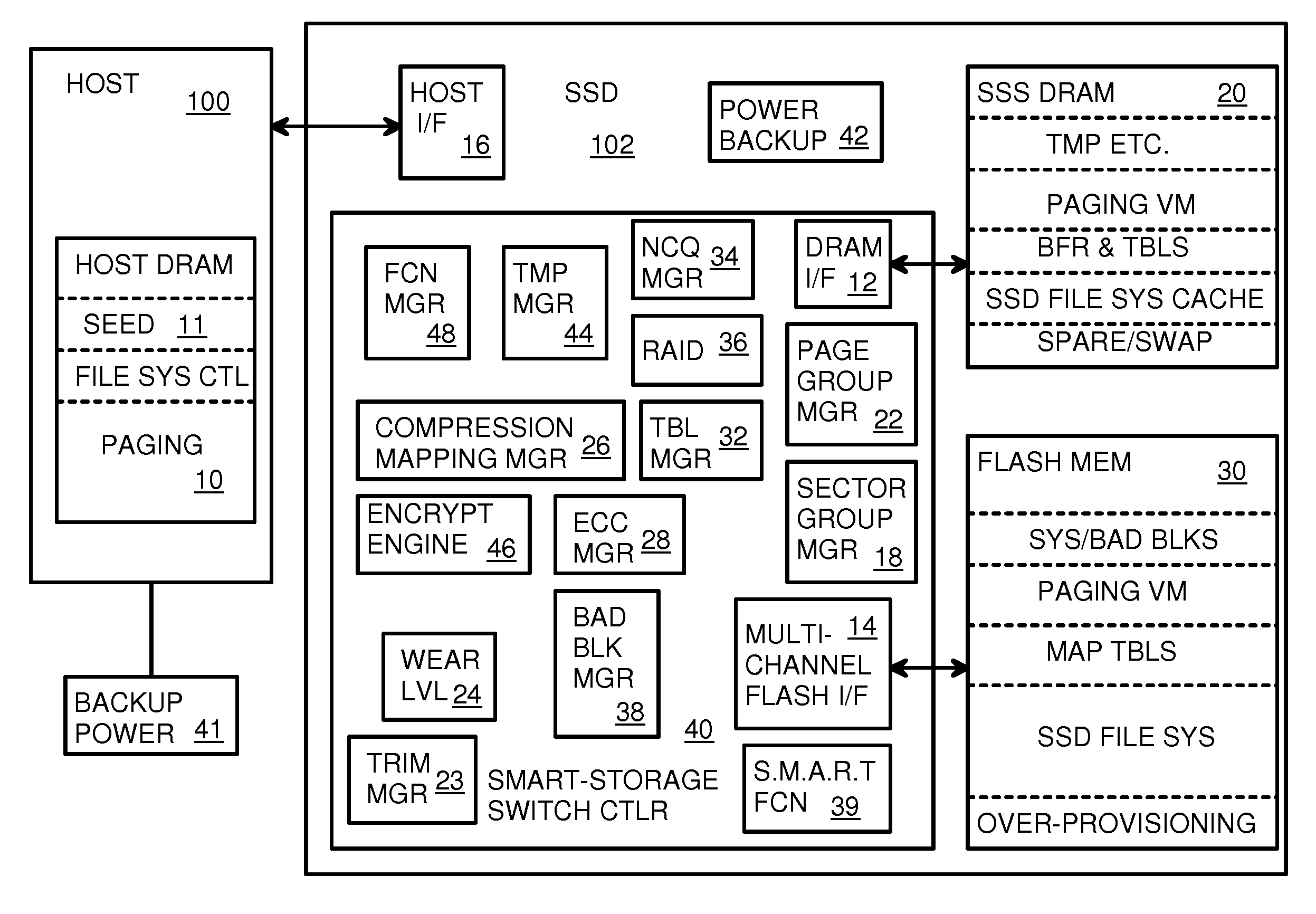
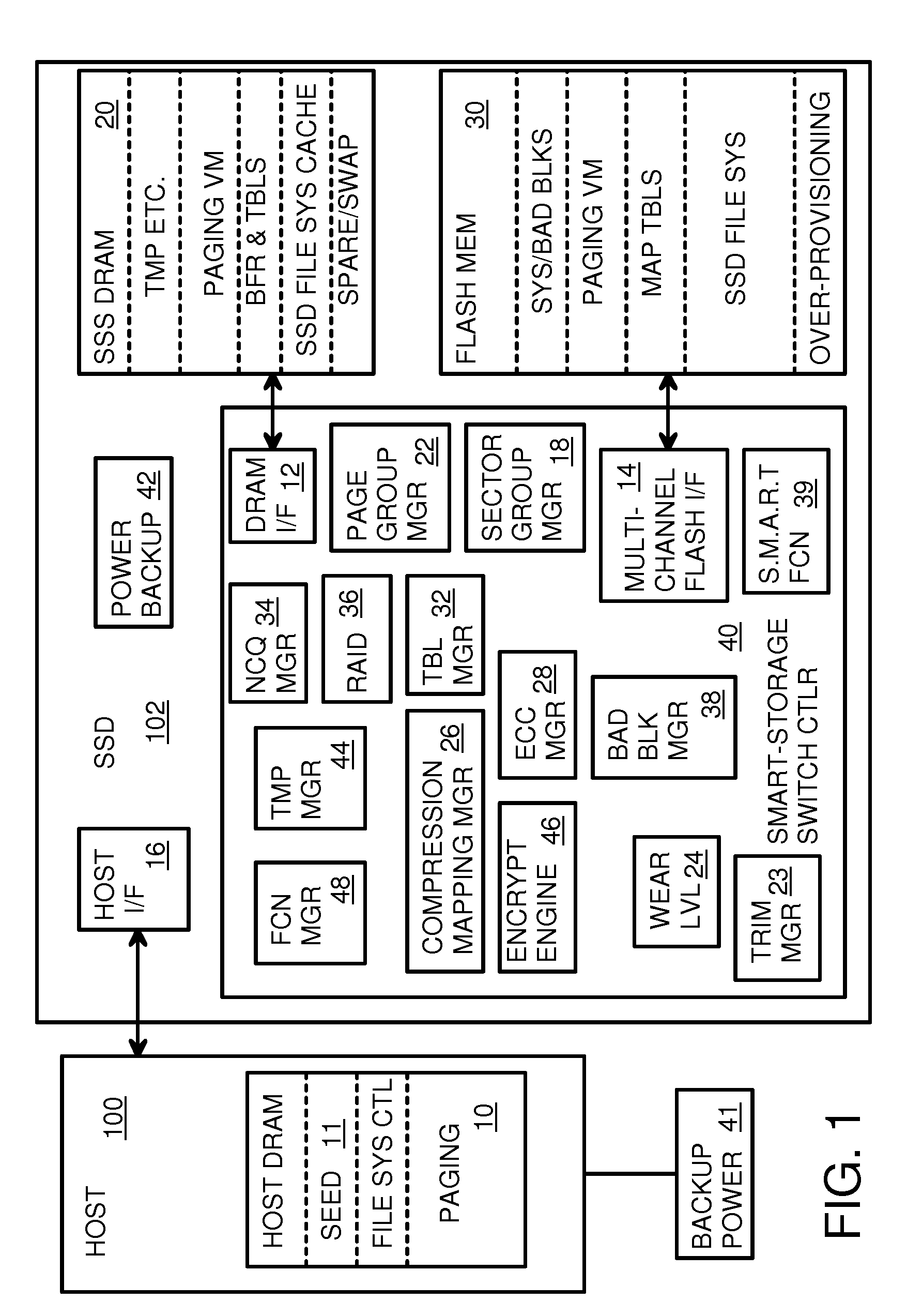
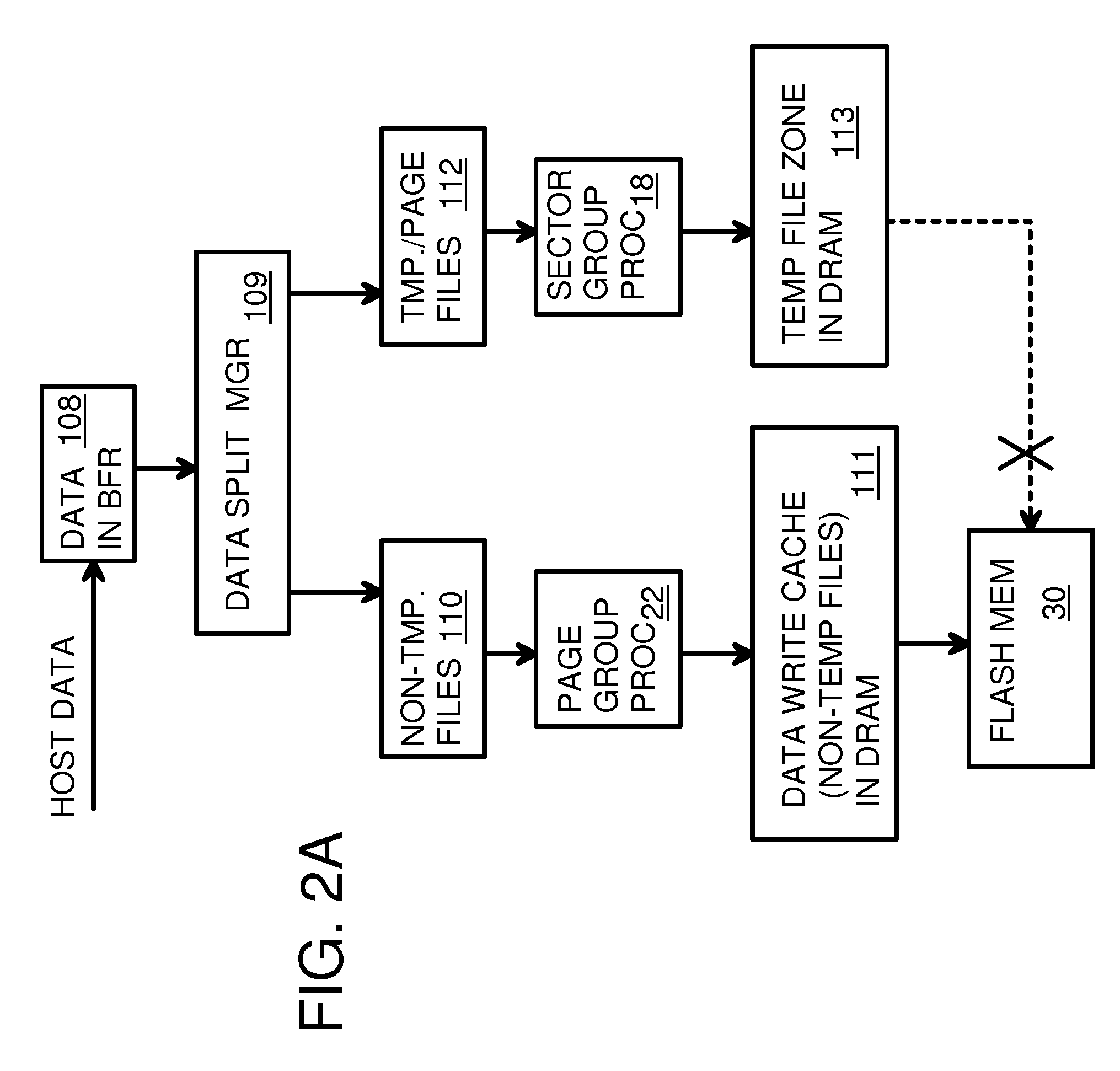
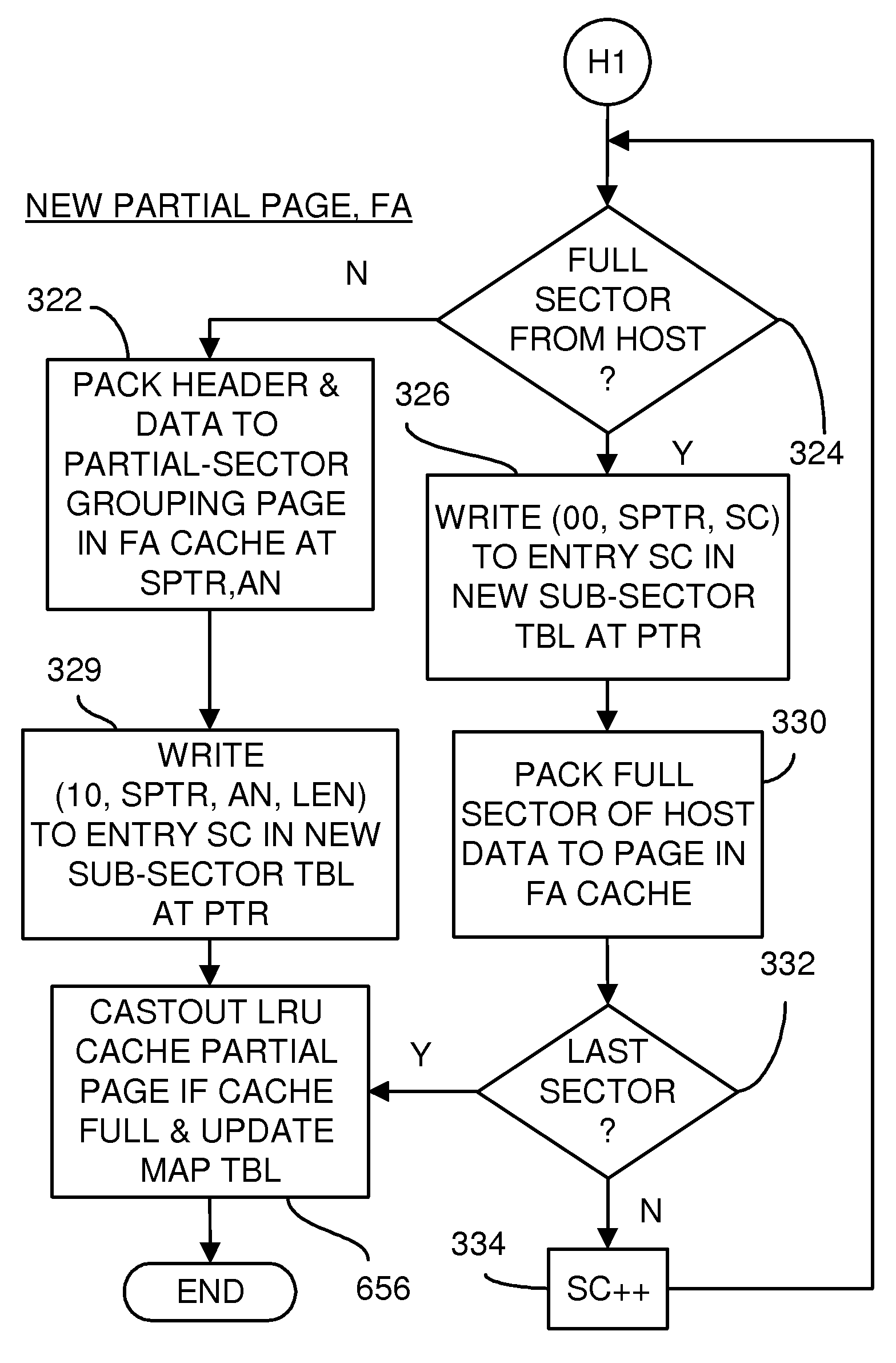
A flash drive has increased endurance and longevity by reducing writes to flash. An Endurance Translation Layer (ETL) is created in a DRAM buffer and provides temporary storage to reduce flash wear. A Smart Storage Switch (SSS) controller assigns data-type bits when categorizing host accesses as paging files used by memory management, temporary files, File Allocation Table (FAT) and File Descriptor Block (FDB) entries, and user data files, using address ranges and file extensions read from FAT. Paging files and temporary files are never written to flash. Partial-page data is packed and sector mapped by sub-sector mapping tables that are pointed to by a unified mapping table that stores the data-type bits and pointers to data or tables in DRAM. Partial sectors are packed together to reduce DRAM usage and flash wear. A spare / swap area in DRAM reduces flash wear. Reference voltages are adjusted when error correction fails.
Owner:SUPER TALENT TECH CORP
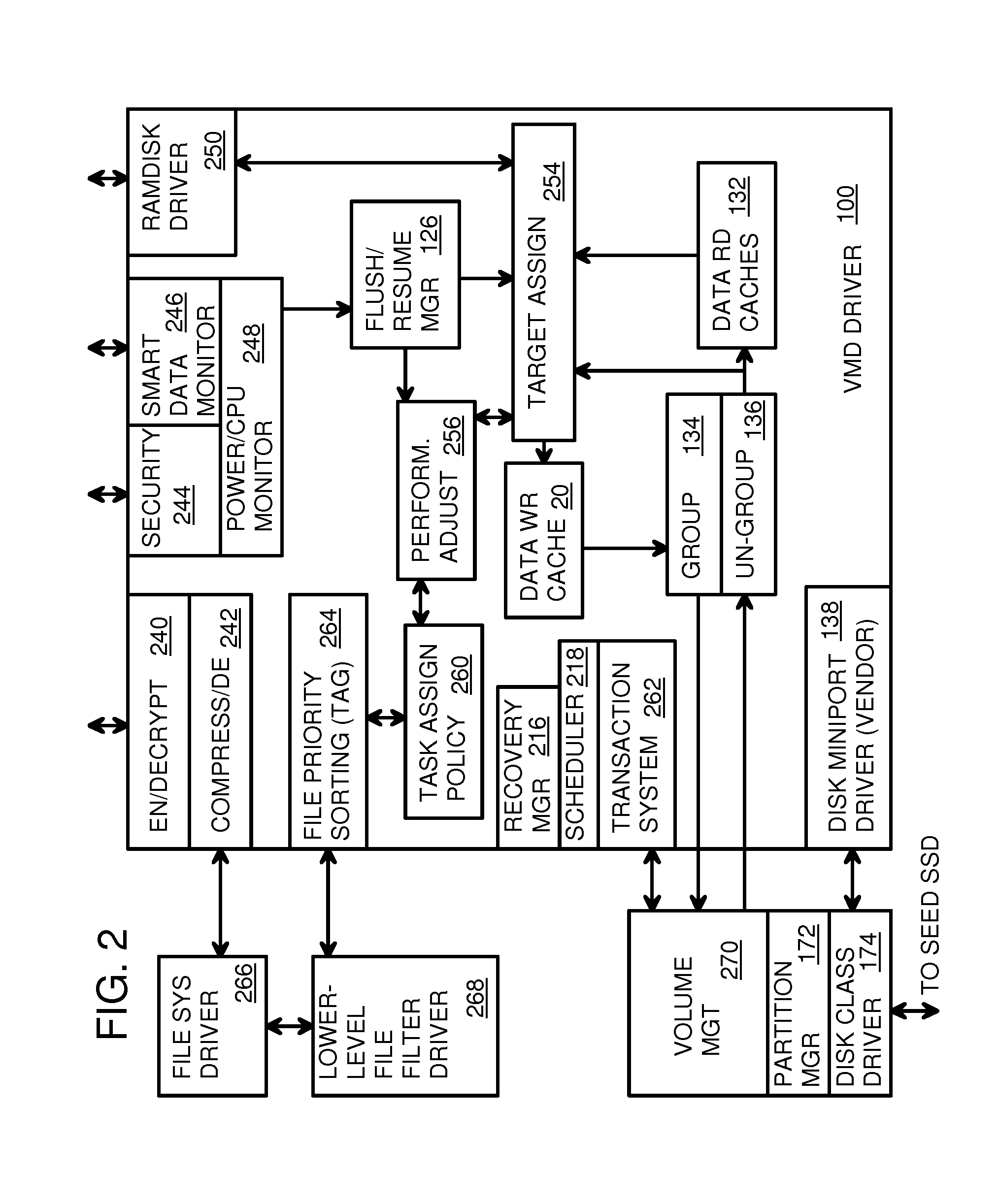
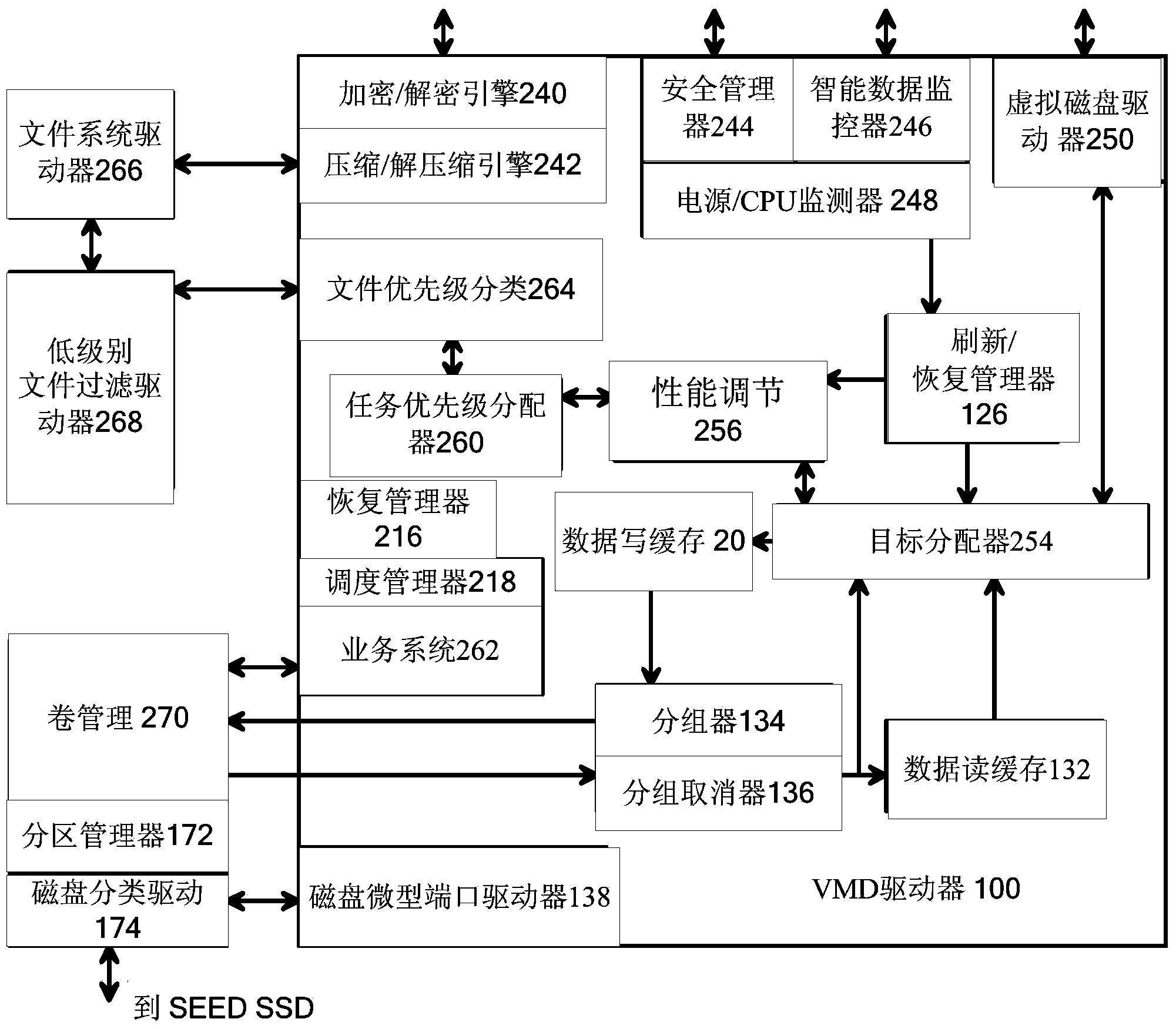
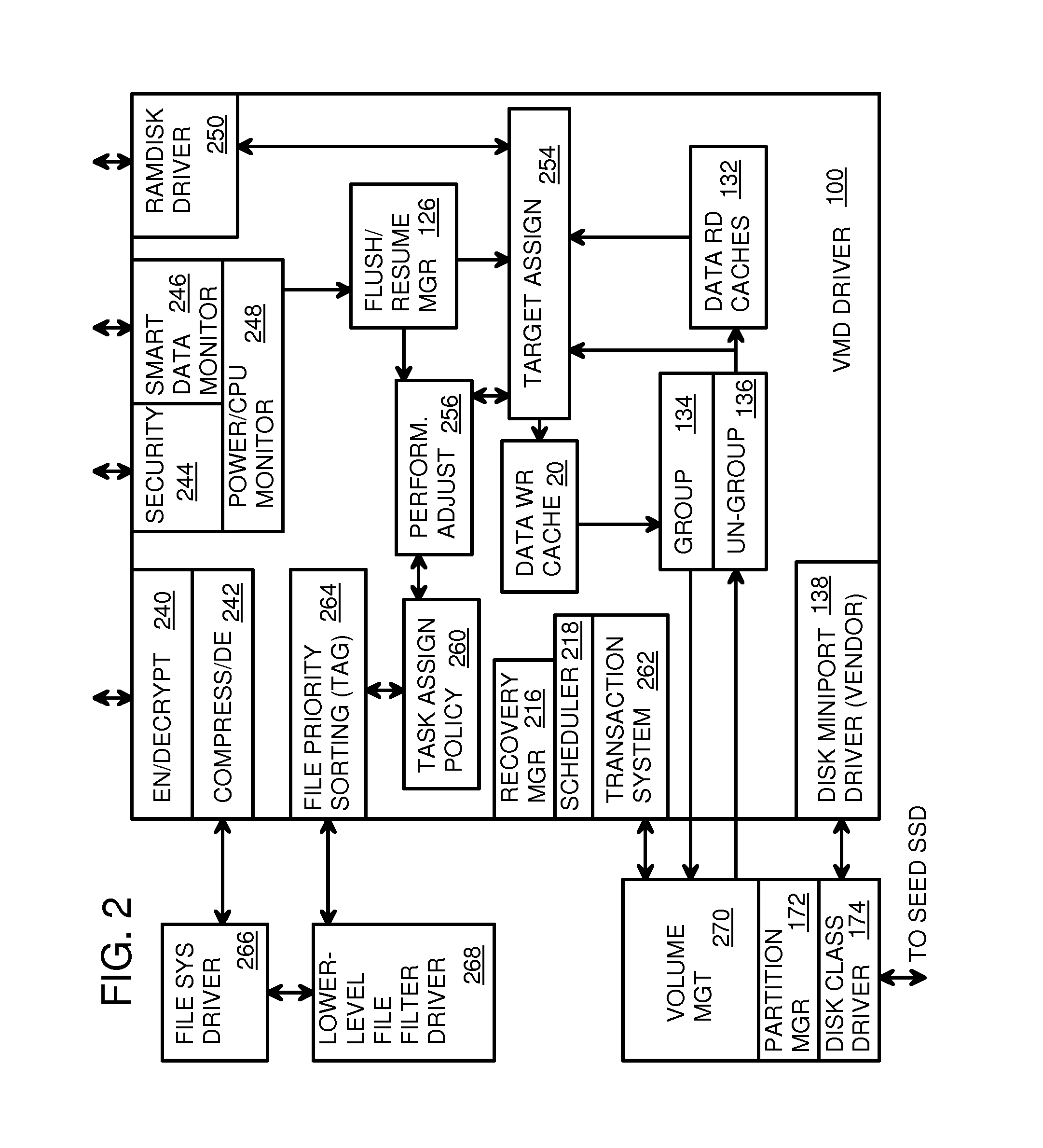
Virtual Memory Device (VMD) Application/Driver with Dual-Level Interception for Data-Type Splitting, Meta-Page Grouping, and Diversion of Temp Files to Ramdisks for Enhanced Flash Endurance
ActiveUS20130145085A1Memory architecture accessing/allocationMemory adressing/allocation/relocationFilename extensionData file
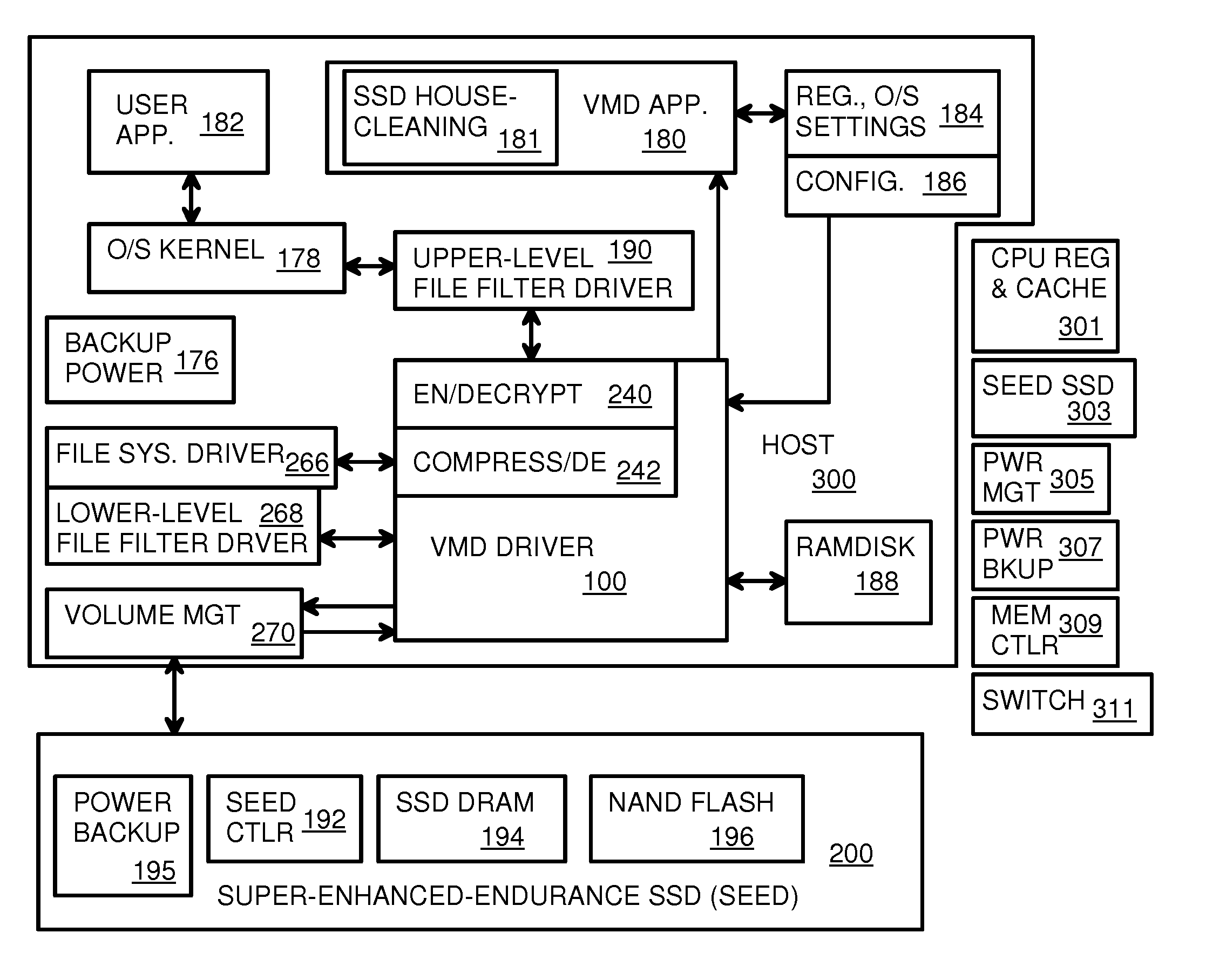
A Virtual-Memory Device (VMD) driver and application execute on a host to increase endurance of flash memory attached to a Super Enhanced Endurance Device (SEED) or Solid-State Drive (SSD). Host accesses to flash are intercepted by the VMD driver using upper and lower-level filter drivers and categorized as data types of paging files, temporary files, meta-data, and user data files, using address ranges and file extensions read from meta-data tables. Paging files and temporary files are optionally written to flash. Full-page and partial-page data are grouped into multi-page meta-pages by data type before storage by the SSD. ramdisks and caches for storing each data type in the host DRAM are managed and flushed to the SSD by the VMD driver. Write dates are stored for pages or blocks for management functions. A spare / swap area in DRAM reduces flash wear. Reference voltages are adjusted when error correction fails.
Owner:SUPER TALENT TECH CORP
Endurance Translation Layer (ETL) and Diversion of Temp Files for Reduced Flash Wear of a Super-Endurance Solid-State Drive
ActiveUS20150106556A1Memory architecture accessing/allocationMemory adressing/allocation/relocationFilename extensionData file
A flash drive has increased endurance and longevity by reducing writes to flash. An Endurance Translation Layer (ETL) is created in a DRAM buffer and provides temporary storage to reduce flash wear. A Smart Storage Switch (SSS) controller assigns data-type bits when categorizing host accesses as paging files used by memory management, temporary files, File Allocation Table (FAT) and File Descriptor Block (FDB) entries, and user data files, using address ranges and file extensions read from FAT. Paging files and temporary files are never written to flash. Partial-page data is packed and sector mapped by sub-sector mapping tables that are pointed to by a unified mapping table that stores the data-type bits and pointers to data or tables in DRAM. Partial sectors are packed together to reduce DRAM usage and flash wear. A spare / swap area in DRAM reduces flash wear. Reference voltages are adjusted when error correction fails.
Owner:SUPER TALENT TECH CORP
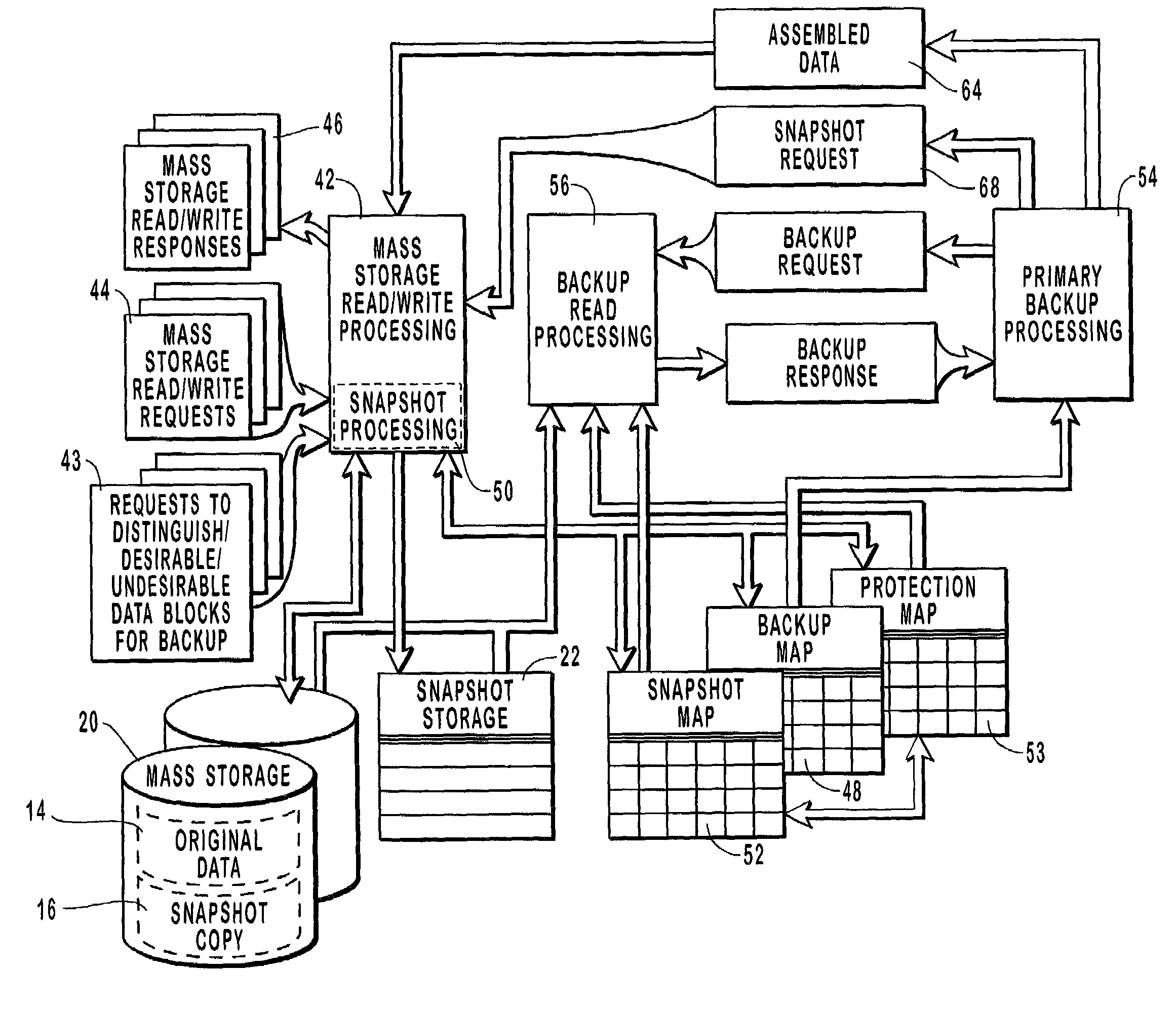
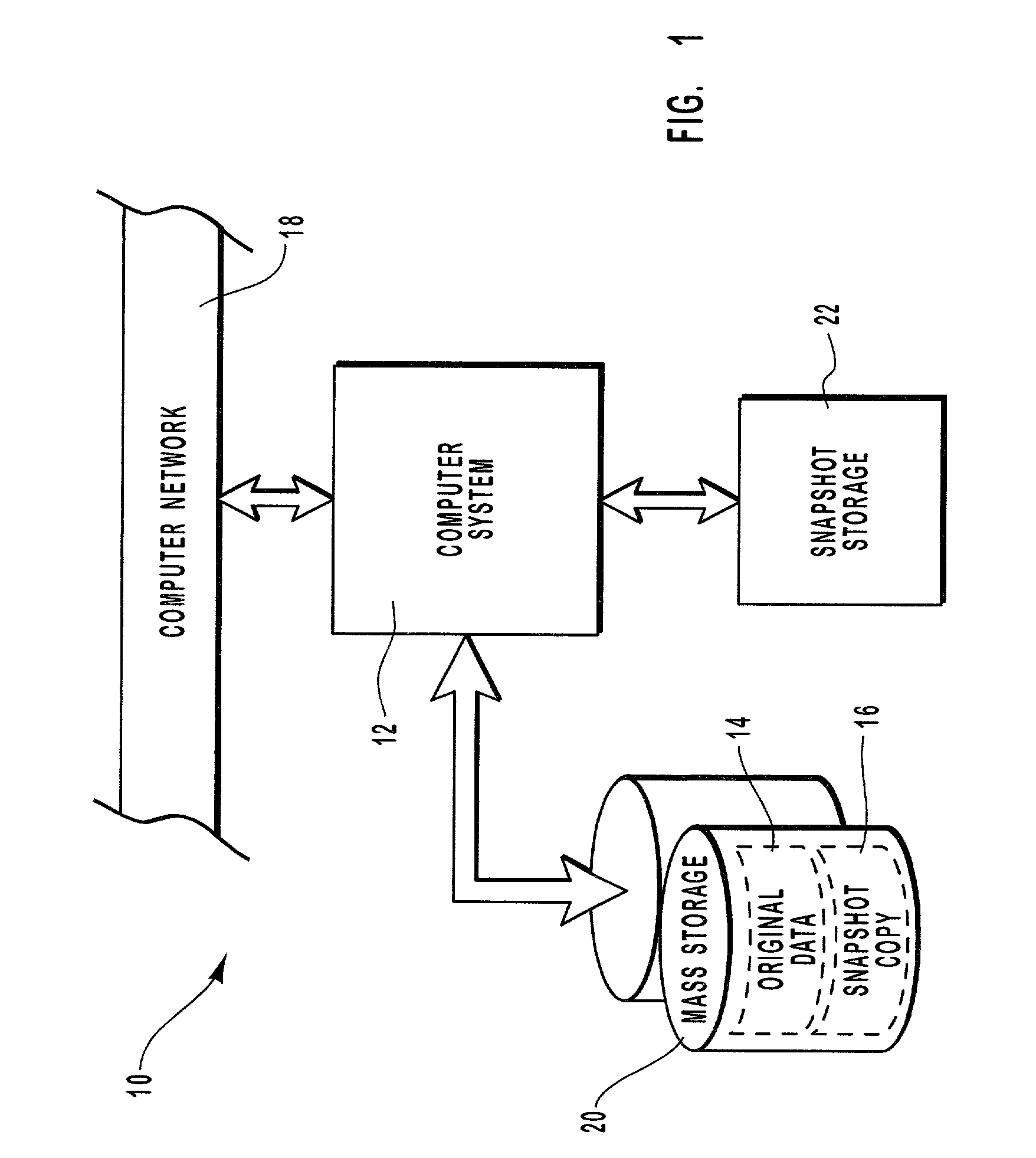
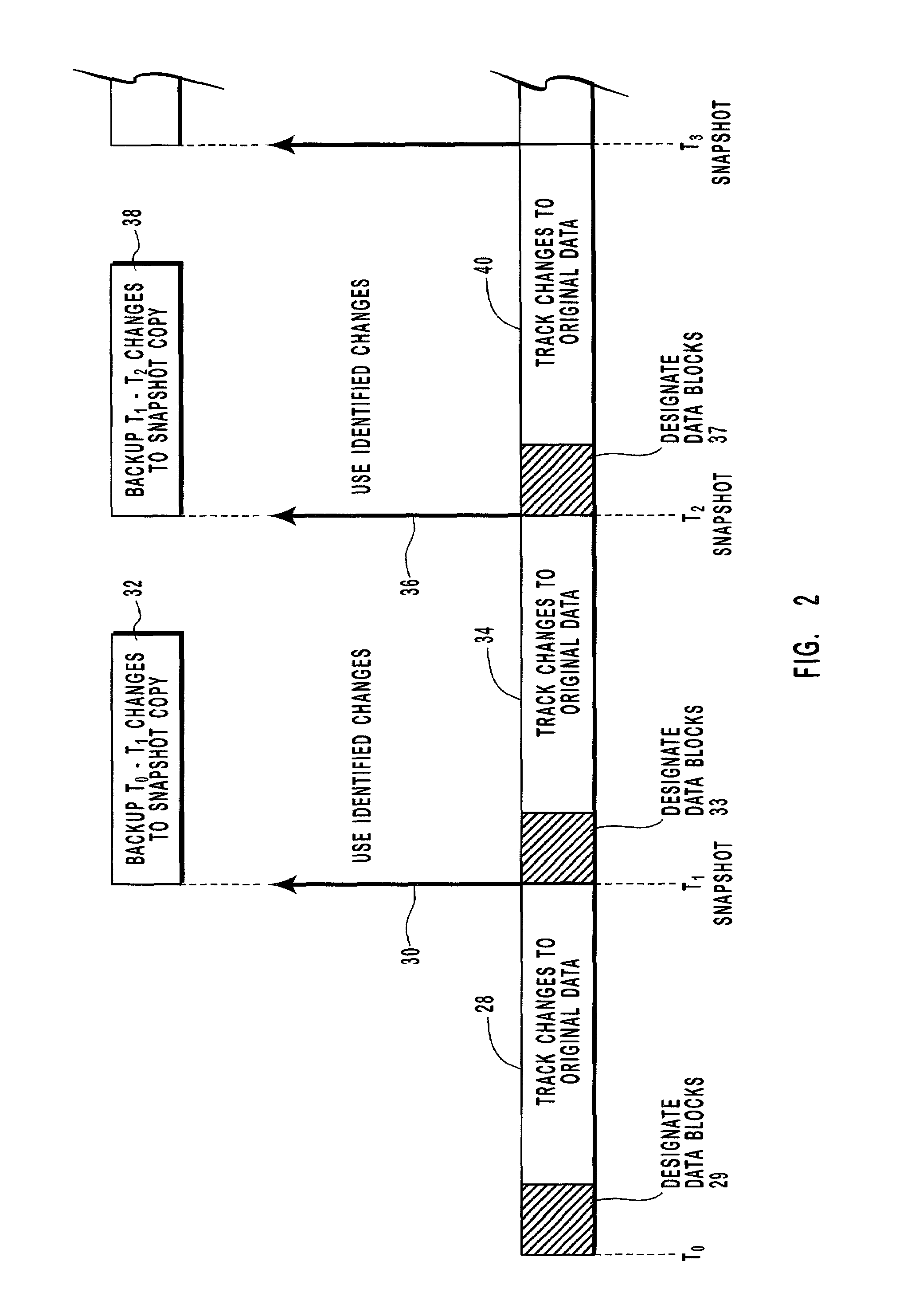
Preserving a snapshot of selected data of a mass storage system
ActiveUS7296125B2Reduce data volumeEasy to useInput/output to record carriersData processing applicationsOriginal dataCommunication bandwidth
Owner:EMC IP HLDG CO LLC
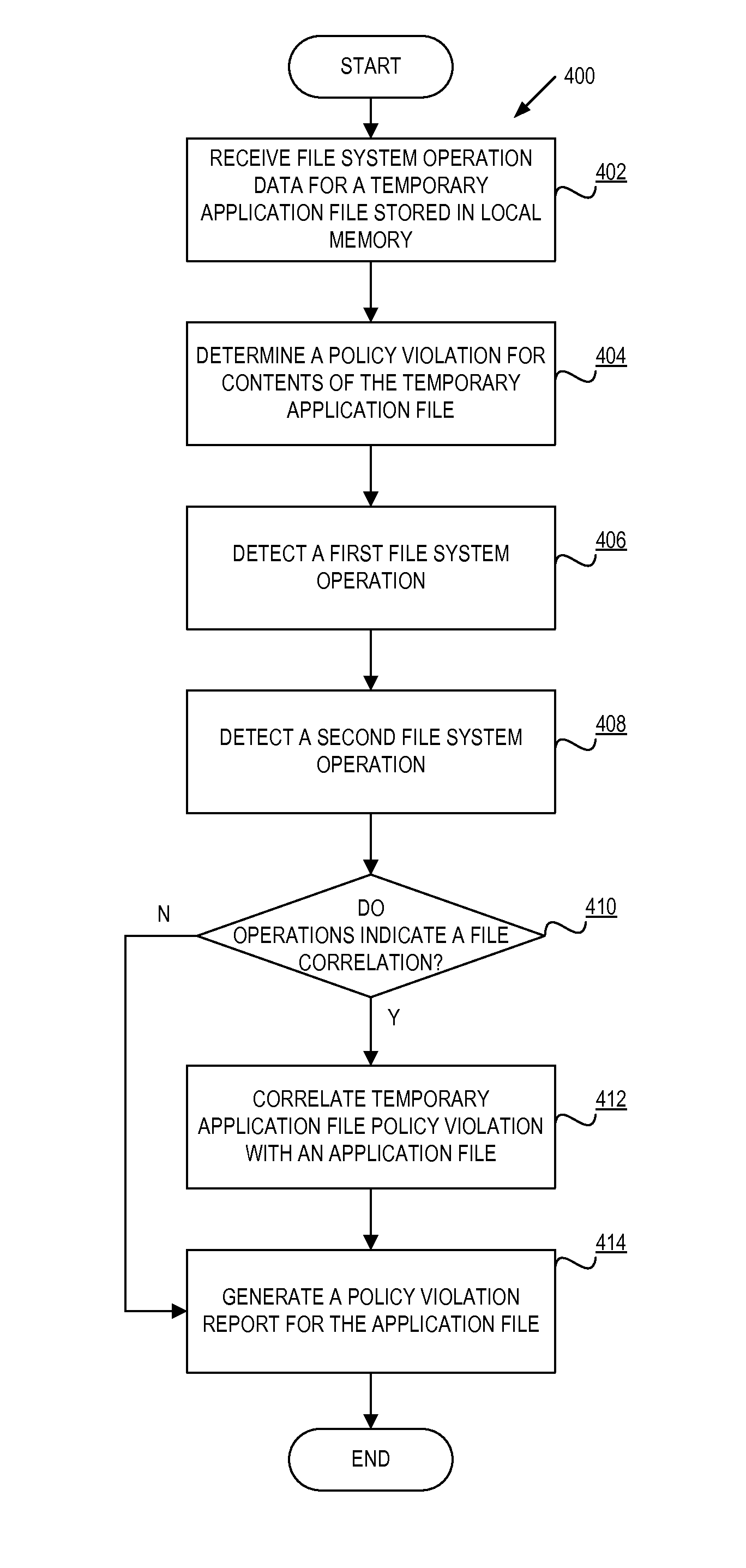
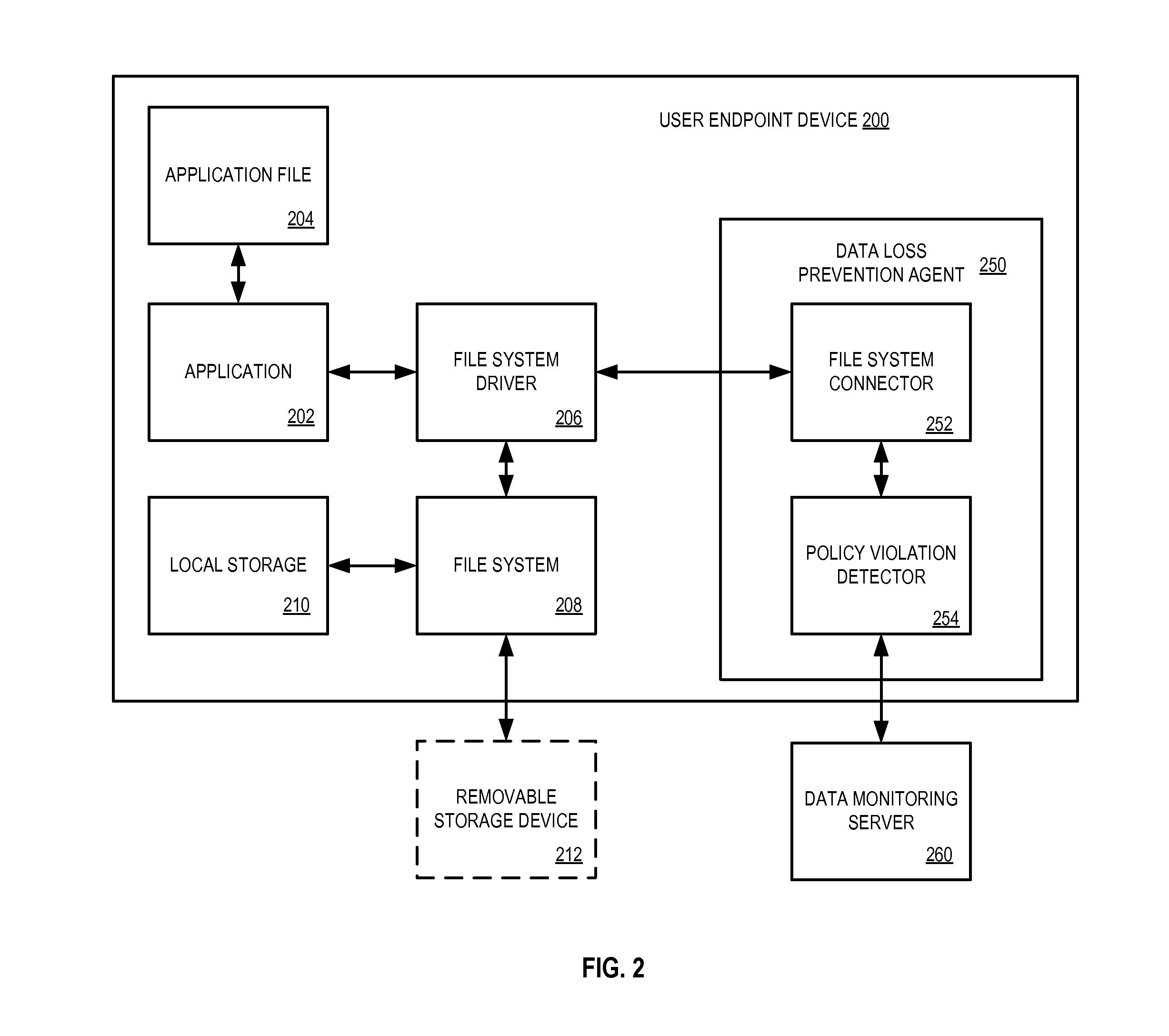
System and method for managing data loss due to policy violations in temporary files
InactiveUS7991747B1Memory loss protectionDigital data processing detailsClient agentApplication software
A method and apparatus for managing data loss due to policy violations in temporary files is described. In one embodiment, the method includes monitoring, by a client agent, information content on a client for violations of a policy. The method further includes determining, by the client agent, that a violation of the policy has occurred for content of a temporary file of an application. In one embodiment, the policy violation of the temporary file is correlated, by the client agent, with an original file of the application.
Owner:CA TECH INC
Green eMMC Device (GeD) Controller with DRAM Data Persistence, Data-Type Splitting, Meta-Page Grouping, and Diversion of Temp Files for Enhanced Flash Endurance
ActiveUS20140310574A1Memory architecture accessing/allocationInput/output to record carriersFilename extensionData file
A controller for a Super Enhanced Endurance Device (SEED) or Solid-State Drive (SSD) increases flash endurance using a DRAM buffer. Host accesses to flash are intercepted by the controller and categorized as data types of paging files, temporary files, meta-data, and user data files, using address ranges and file extensions read from meta-data tables. Paging files and temporary files are optionally written to flash. Full-page and partial-page data are grouped into multi-page meta-pages by data type in the DRAM before storage by lower-level flash devices such as eMMC, UFS, or iSSD. Caches in the DRAM buffer for storing each data type are managed and flushed to the flash devices by the controller. Write dates are stored for pages or blocks for management functions. A spare / swap area in DRAM reduces flash wear. Reference voltages are adjusted when error correction fails.
Owner:SUPER TALENT TECH CORP
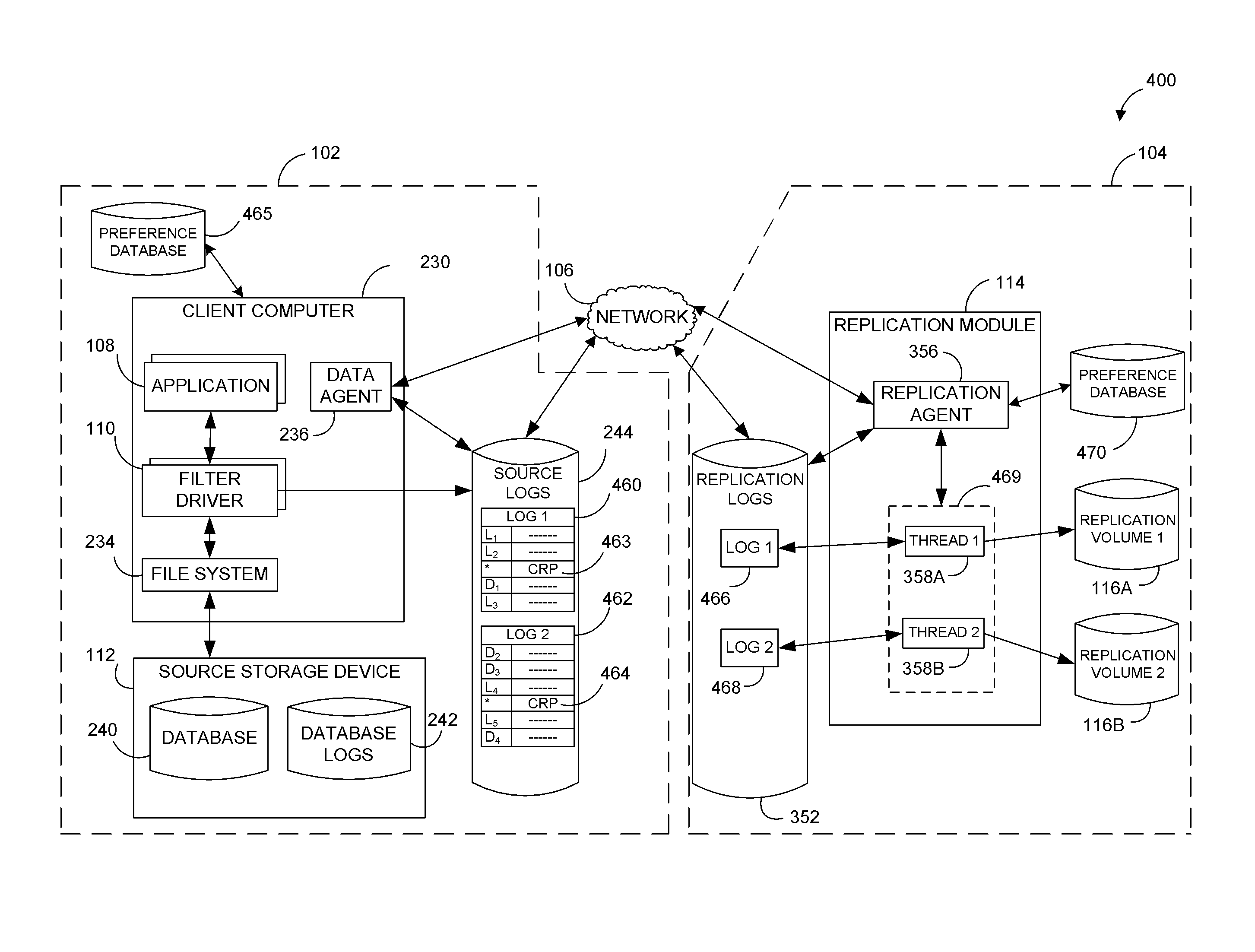
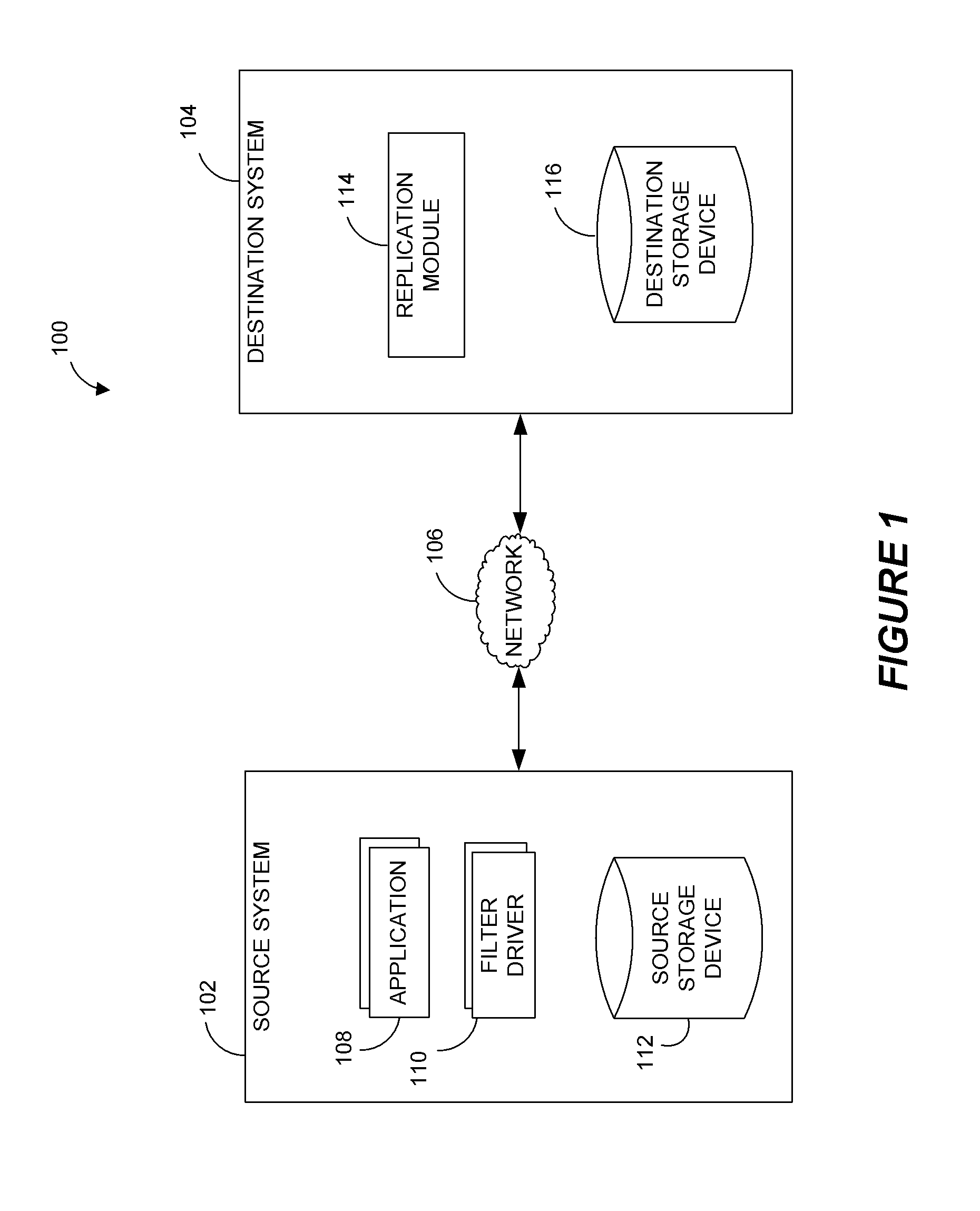
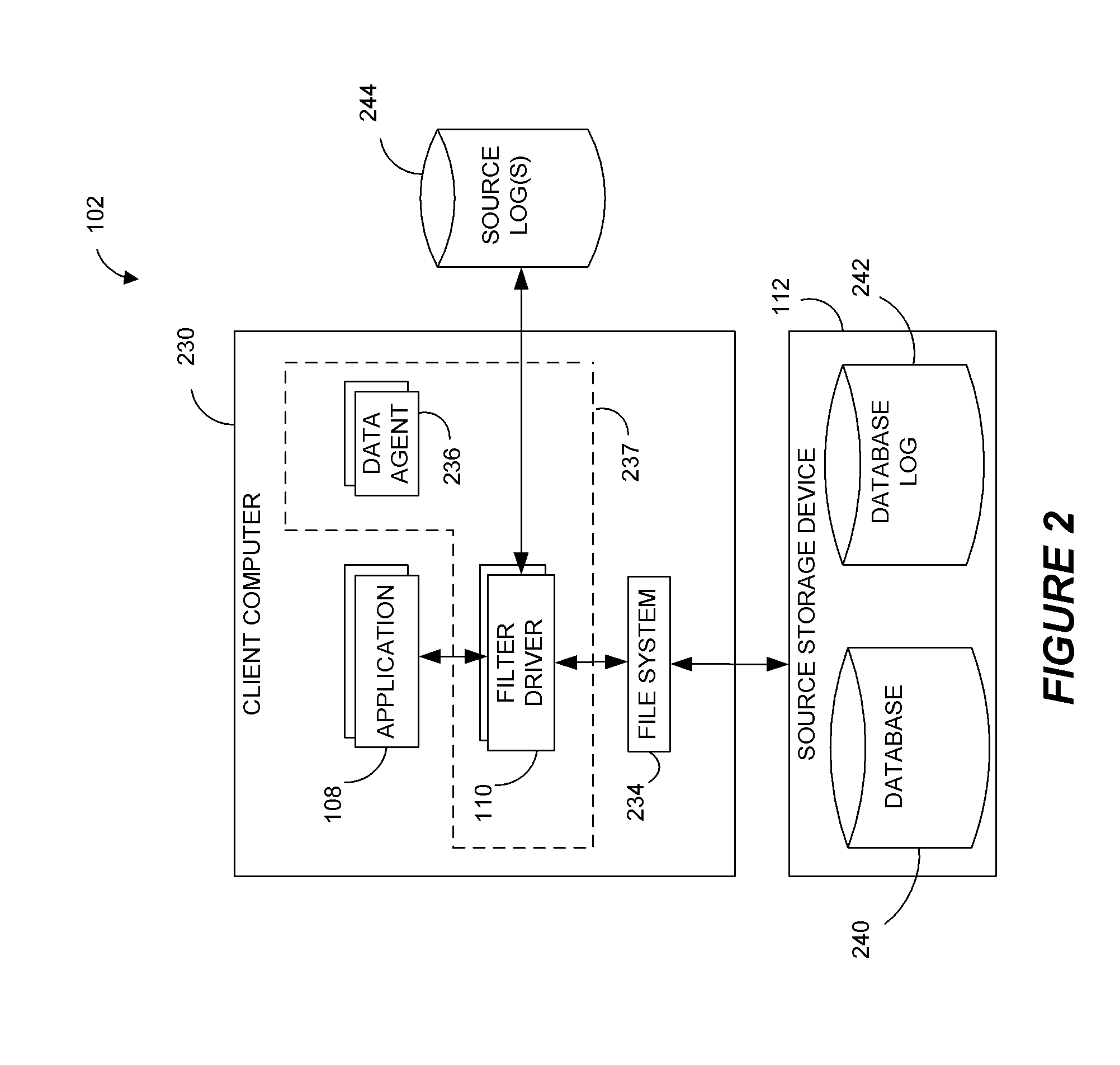
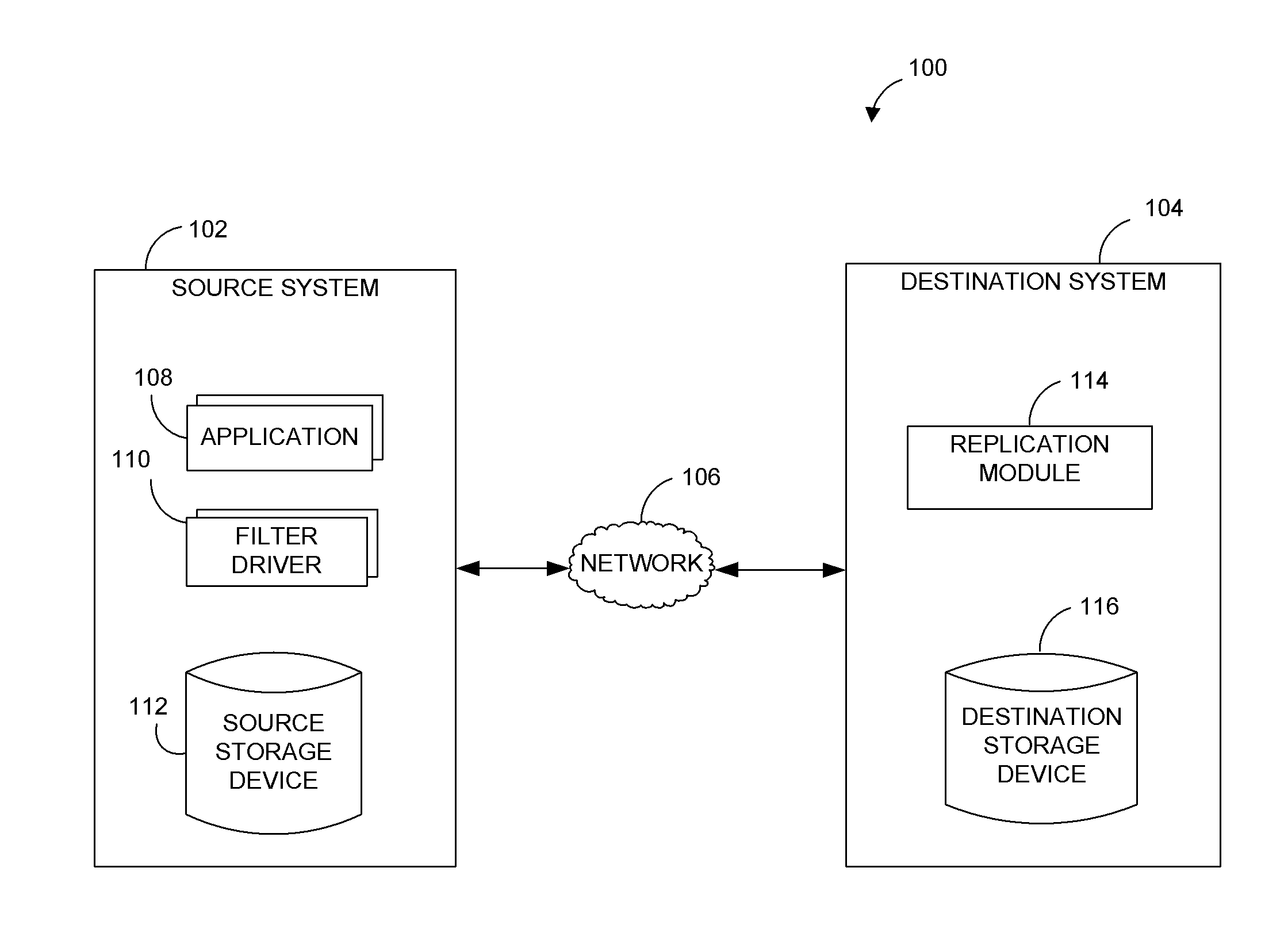
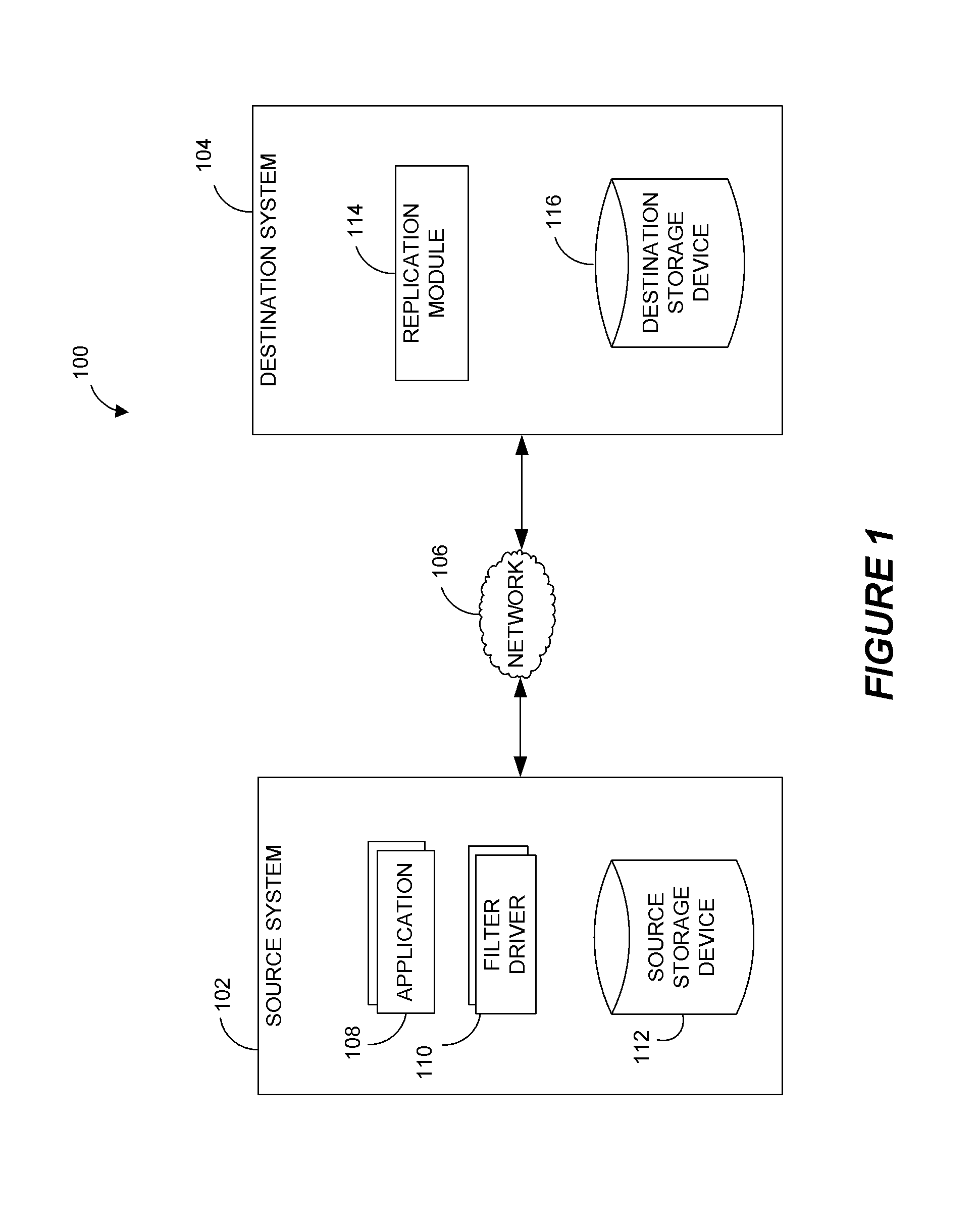
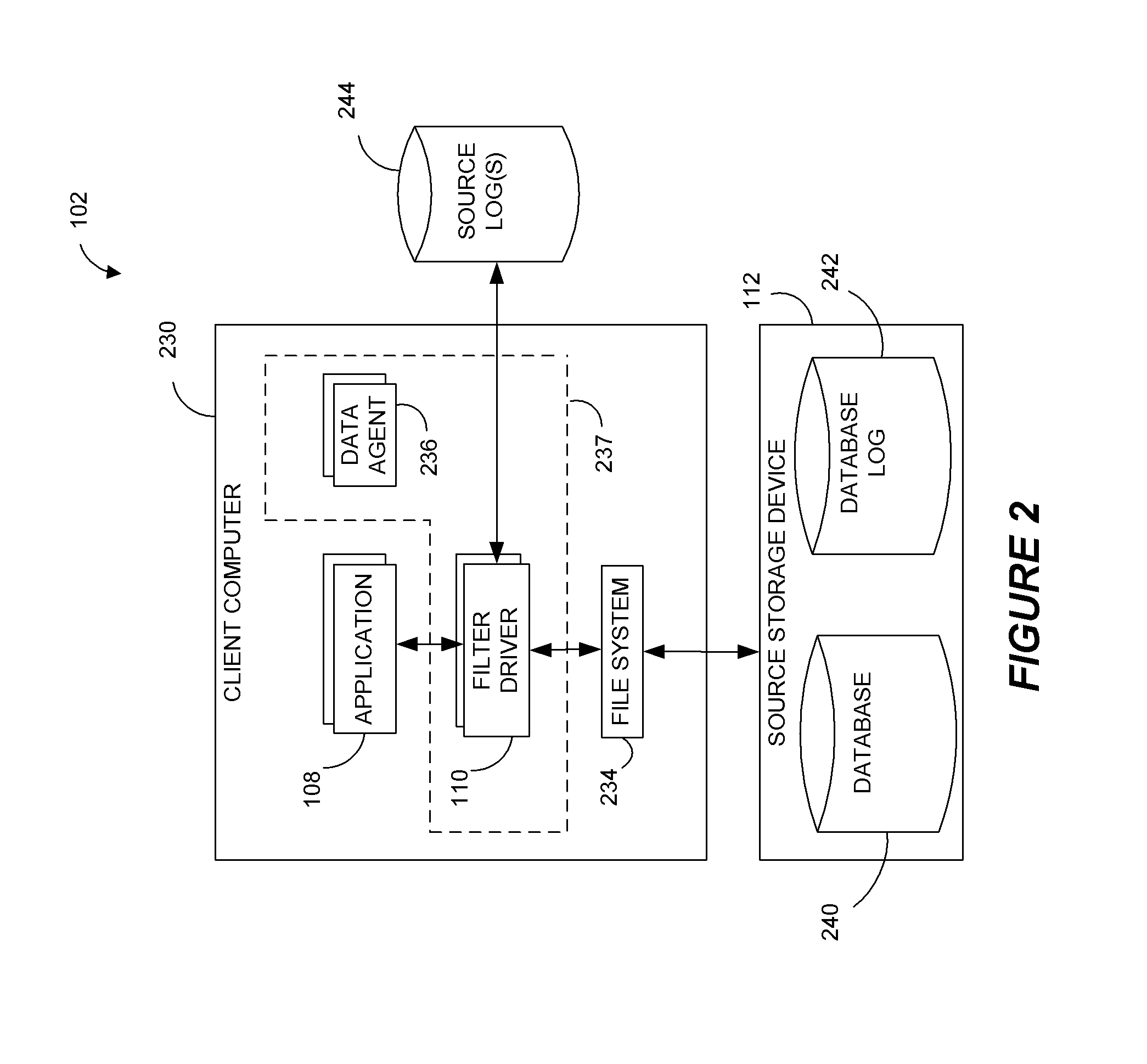
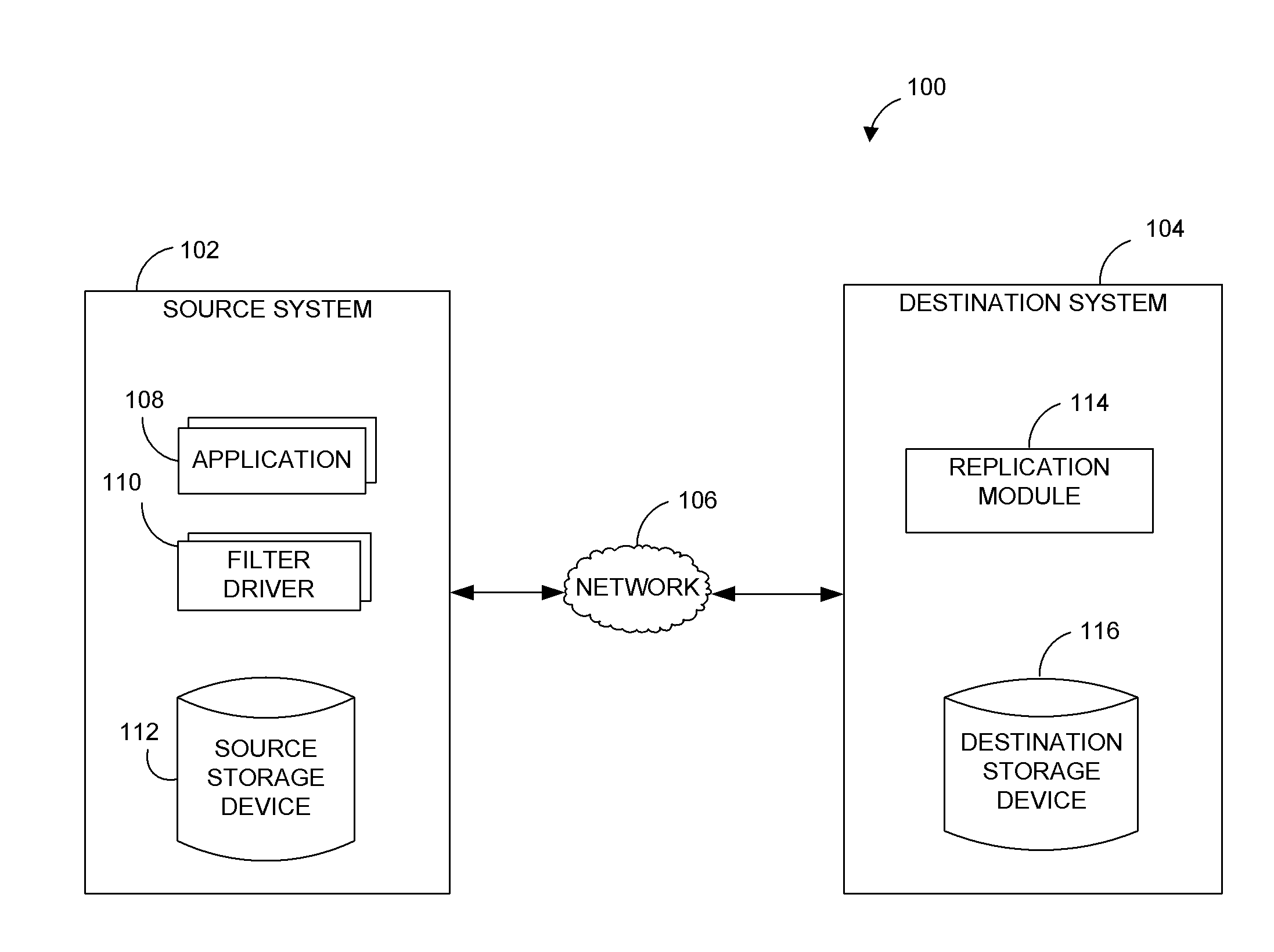
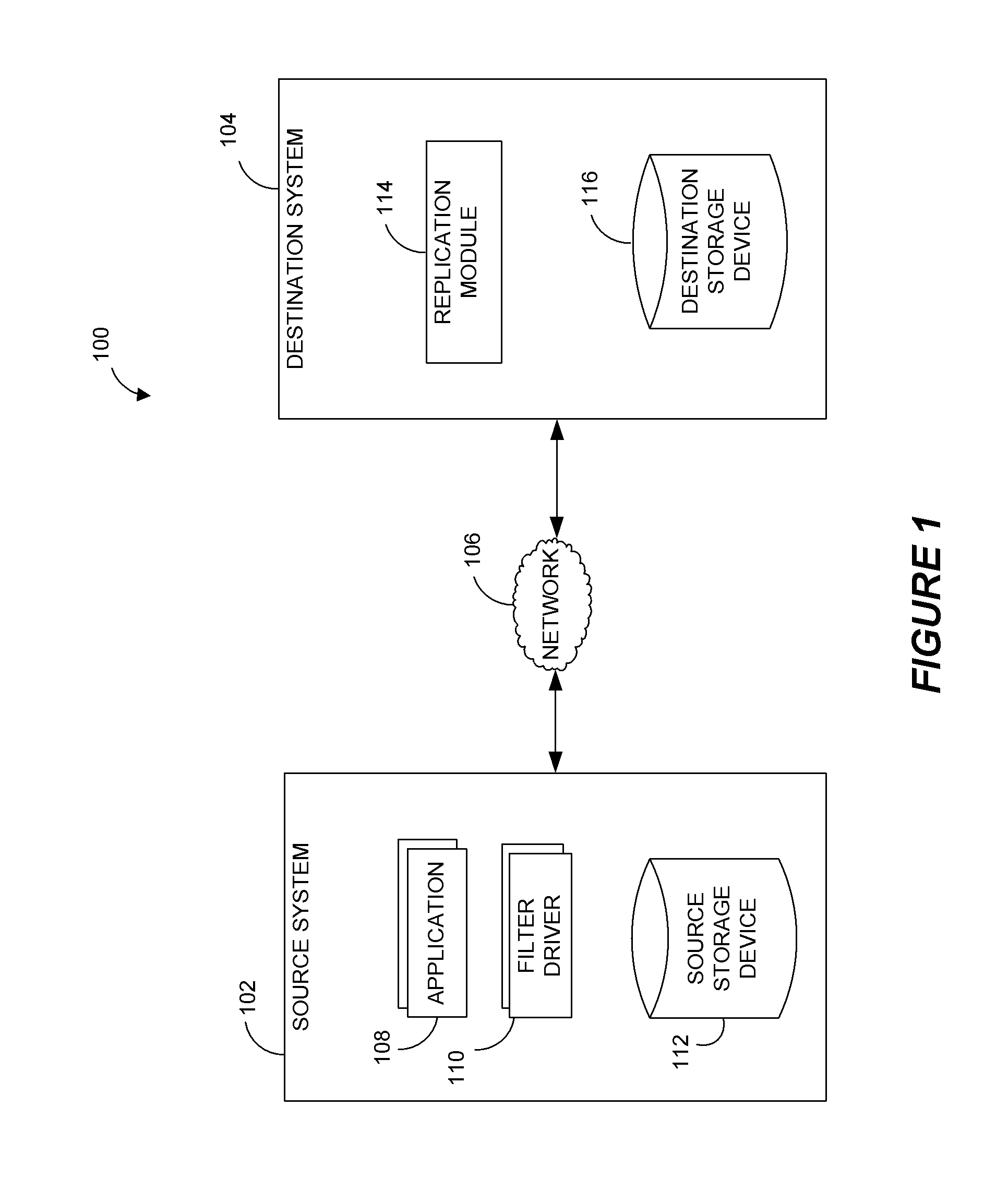
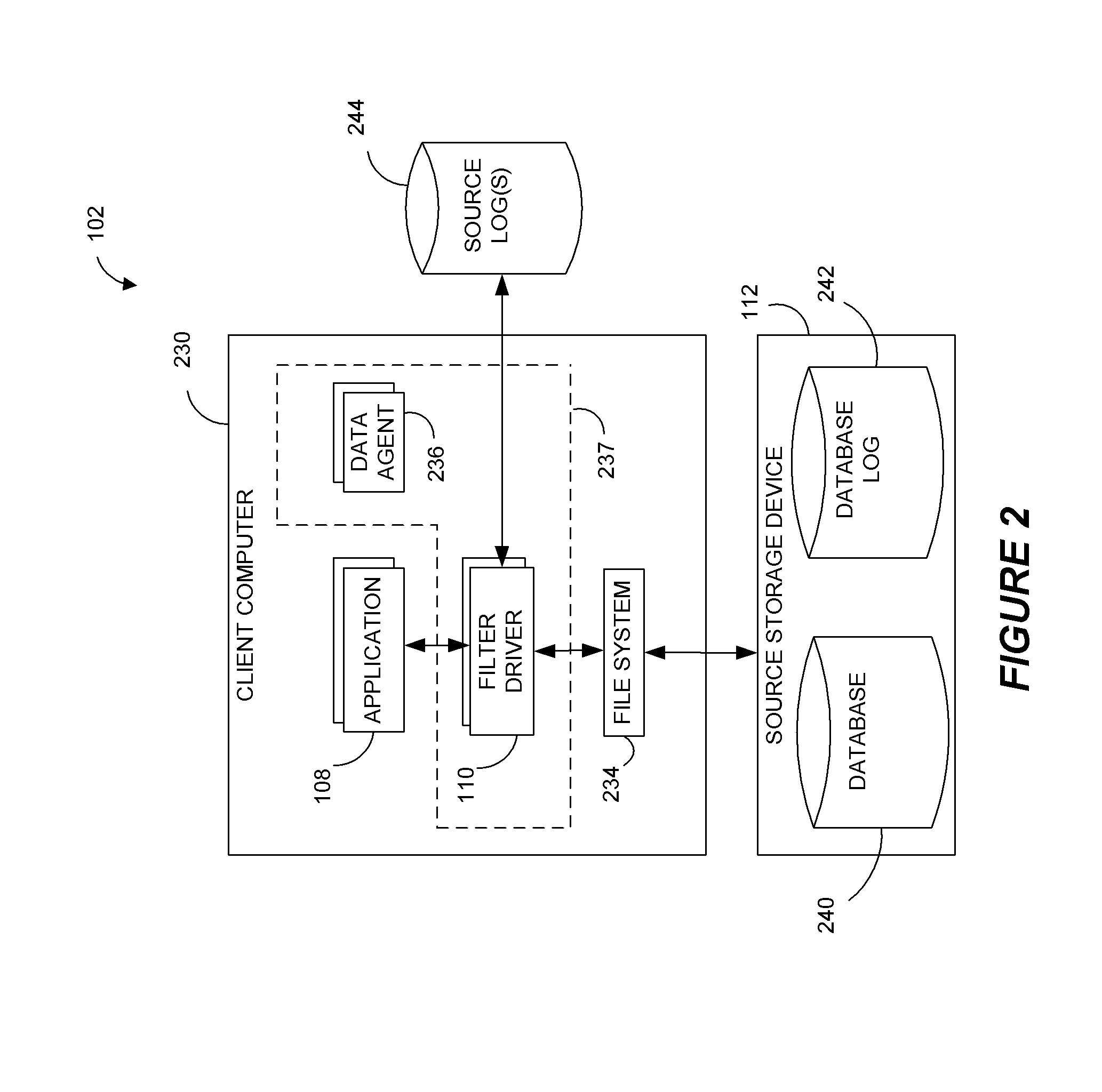
Systems and methods for performing data replication
ActiveUS8489656B2Easy to operateDigital data information retrievalDigital data processing detailsFile systemData operations
Preparing source data to be replicated in a continuous data replication environment. Certain systems and methods populate a file name database with entries having a unique file identifier descriptor (FID), short name and a FID of the parent directory of each directory or file on a source storage device. Such information is advantageously gathered during scanning of a live file system without requiring a snapshot of the source storage device. The database can be further used to generate absolute file names associated with data operations to be replayed on a destination storage device. Based on the obtained FIDs, certain embodiments can further combine write operations to be replayed on the destination storage device and / or avoid replicating temporary files to the destination system.
Owner:COMMVAULT SYST INC
Systems and methods for performing data replication
InactiveUS20110295804A1Easy to operateDigital data information retrievalError detection/correctionFile systemData operations
Preparing source data to be replicated in a continuous data replication environment. Certain systems and methods populate a file name database with entries having a unique file identifier descriptor (FID), short name and a FID of the parent directory of each directory or file on a source storage device. Such information is advantageously gathered during scanning of a live file system without requiring a snapshot of the source storage device. The database can be further used to generate absolute file names associated with data operations to be replayed on a destination storage device. Based on the obtained FIDs, certain embodiments can further combine write operations to be replayed on the destination storage device and / or avoid replicating temporary files to the destination system.
Owner:COMMVAULT SYST INC
Systems and methods for performing data replication
ActiveUS20110295806A1Easy to operateDigital data information retrievalDigital data processing detailsFile systemData operations
Preparing source data to be replicated in a continuous data replication environment. Certain systems and methods populate a file name database with entries having a unique file identifier descriptor (FID), short name and a FID of the parent directory of each directory or file on a source storage device. Such information is advantageously gathered during scanning of a live file system without requiring a snapshot of the source storage device. The database can be further used to generate absolute file names associated with data operations to be replayed on a destination storage device. Based on the obtained FIDs, certain embodiments can further combine write operations to be replayed on the destination storage device and / or avoid replicating temporary files to the destination system.
Owner:COMMVAULT SYST INC
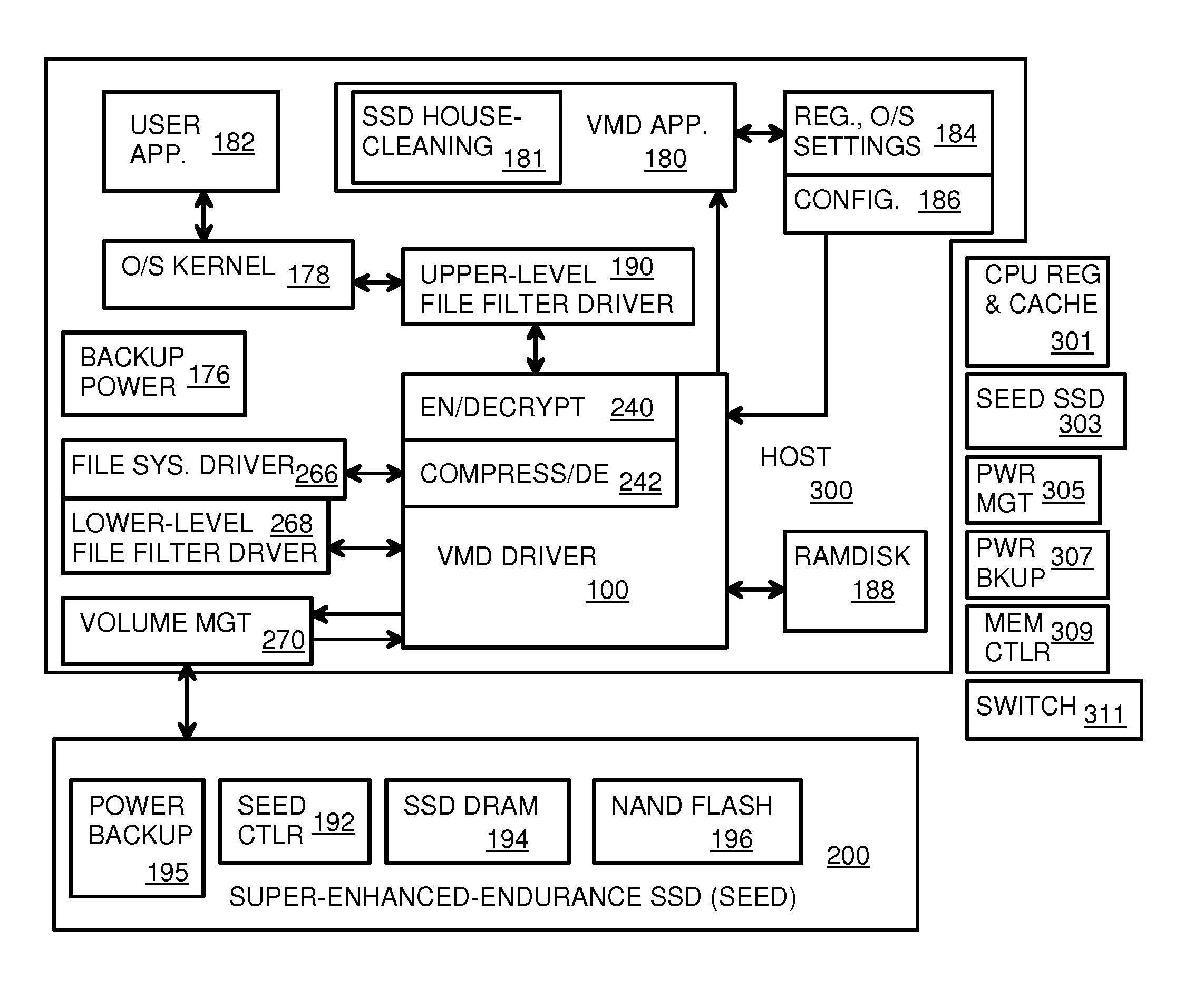
Vmd application/driver
The invention provides a VMD (Virtual-Memory Device) executed on a host and application thereof for enhancing flash memory endurance of an SEED (Super Enhanced Endurance Device) or an SSD (Solid-State Drive). The VMD driver utilizes a high-level or a low-level filtering driver to intercept and capture access to flash memory of the host and to sort access to the flash memory of the host into paging file data type, temporary files, meta data and user data files by using address range and file extensions read by the meta data. Optionally, the paging files and the temporary files are written in the flash memory. Full pages and local pages are grouped into multi-page metapage according to data type before SSD storage data passes. A virtual RAM disk and cache storing the data type in the host DRAM are managed and refreshed to SSD through the VMD driver. Write data is stored for blocks or pages managing functions. Flash memory abrasion is reduced in a backup / exchange area in the DRAM. The reference voltage is adjusted when error correction fails.
Owner:武汉网上网科技有限公司
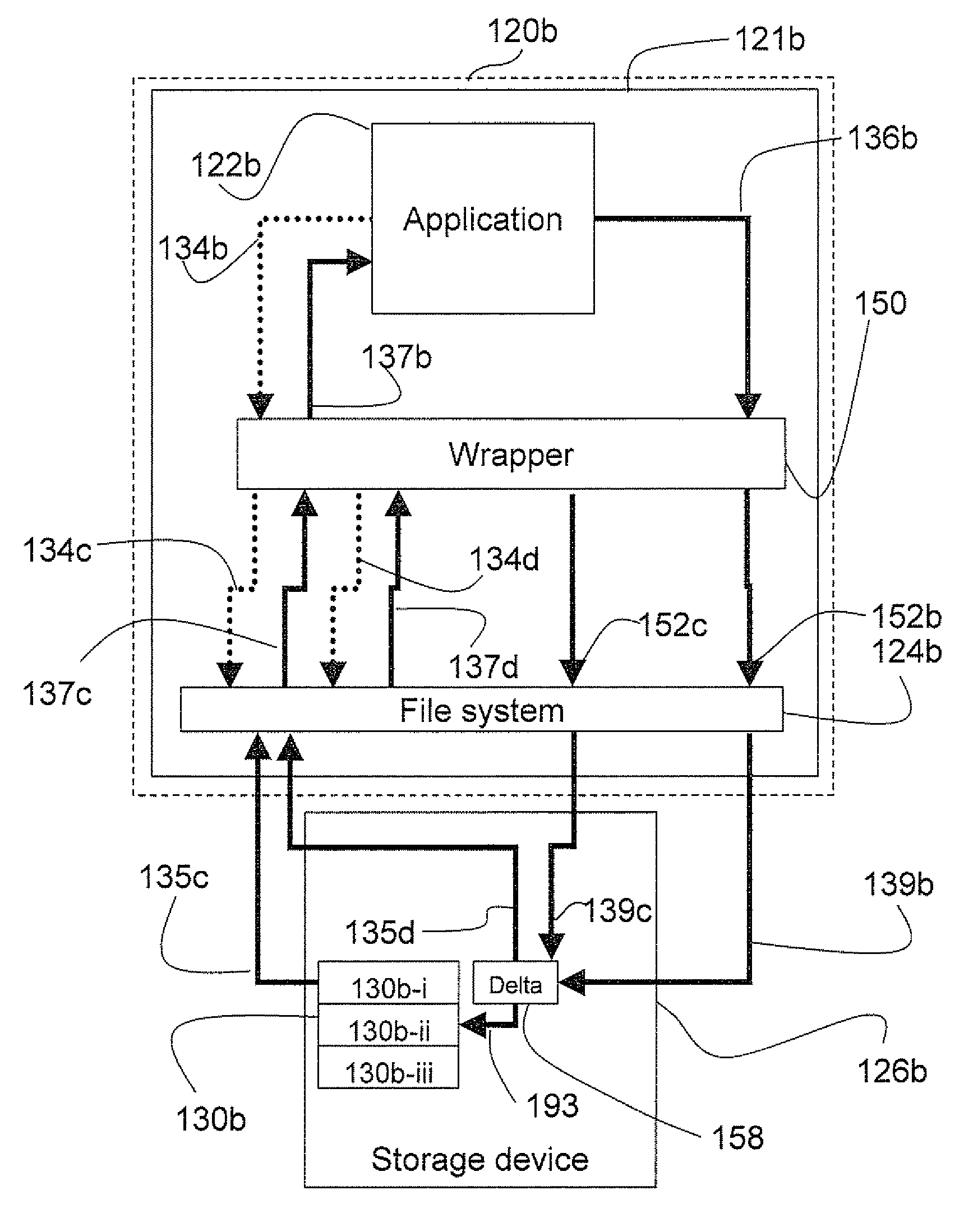
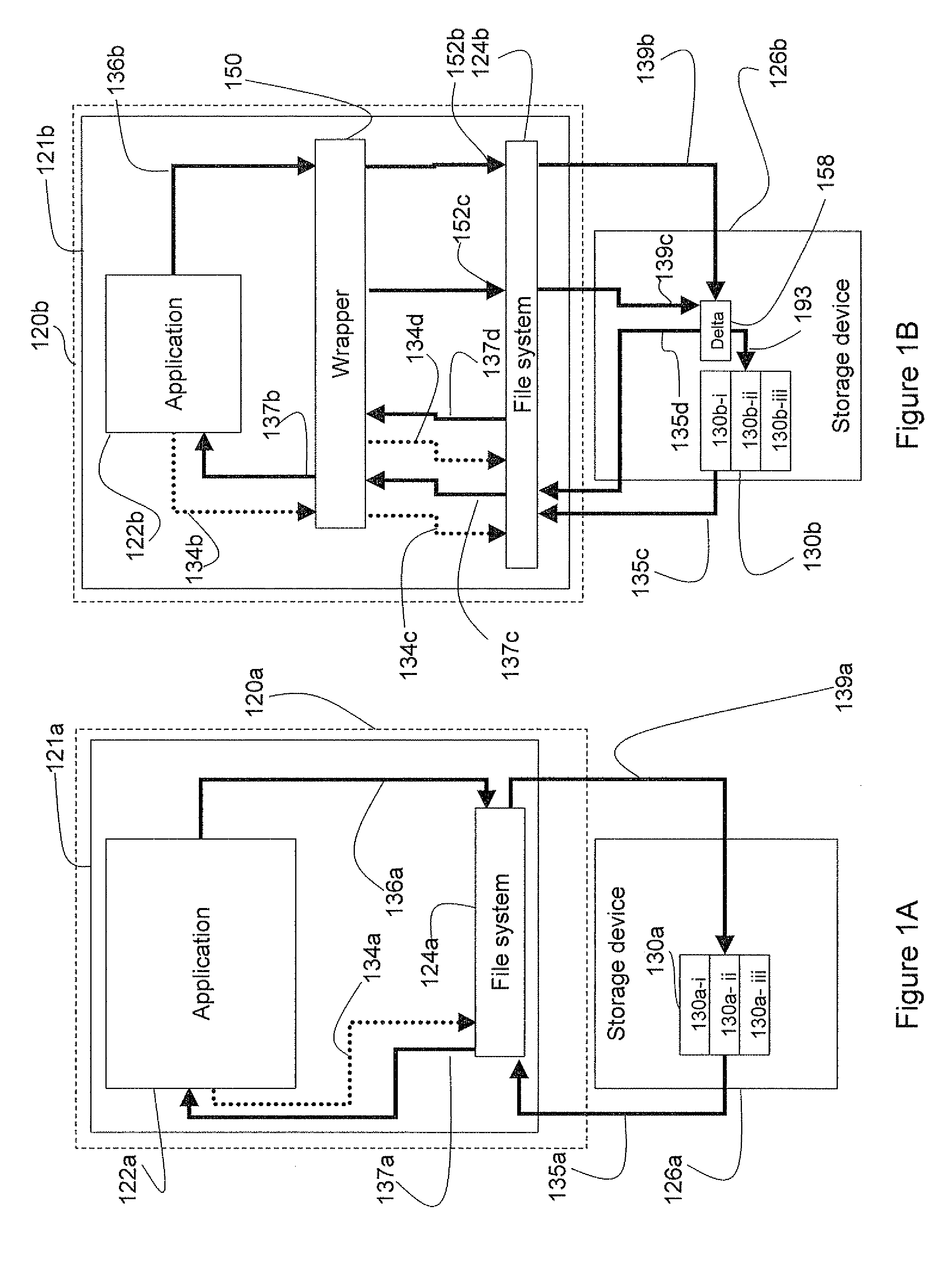
Incremental transparent file updating
InactiveUS20080134163A1Protection from damageEfficient updateMemory loss protectionDigital data processing detailsData CorruptionApplication software
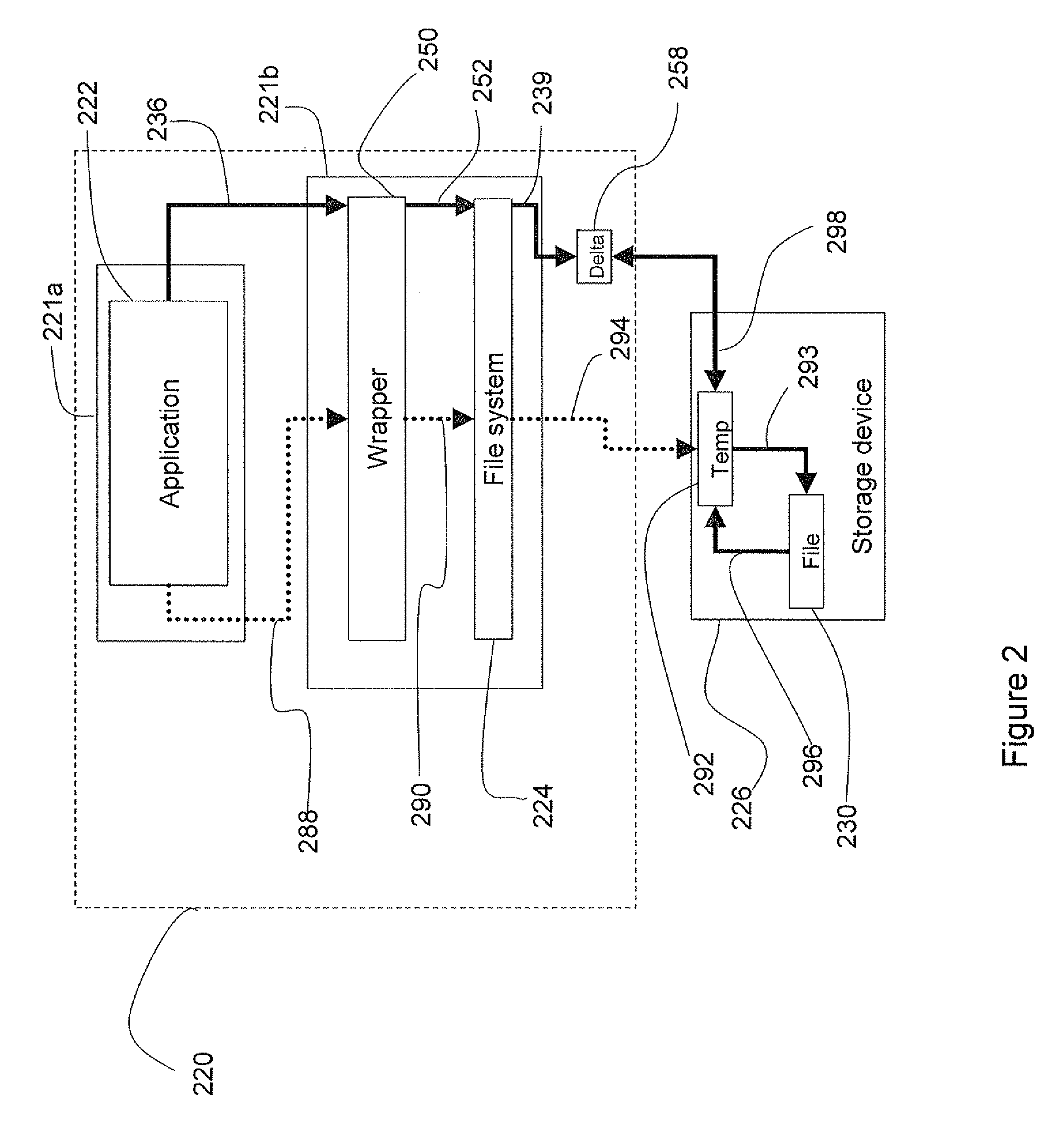
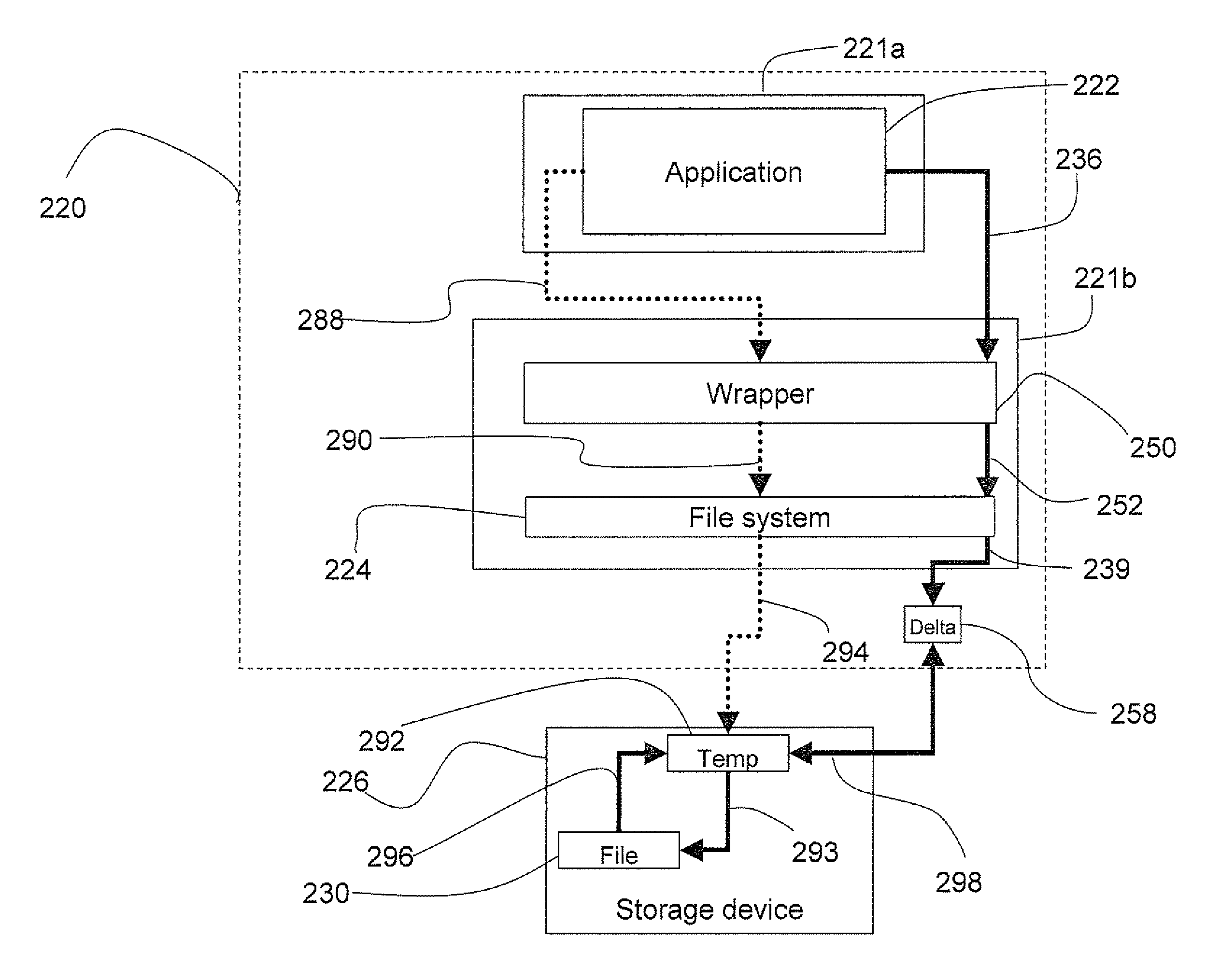
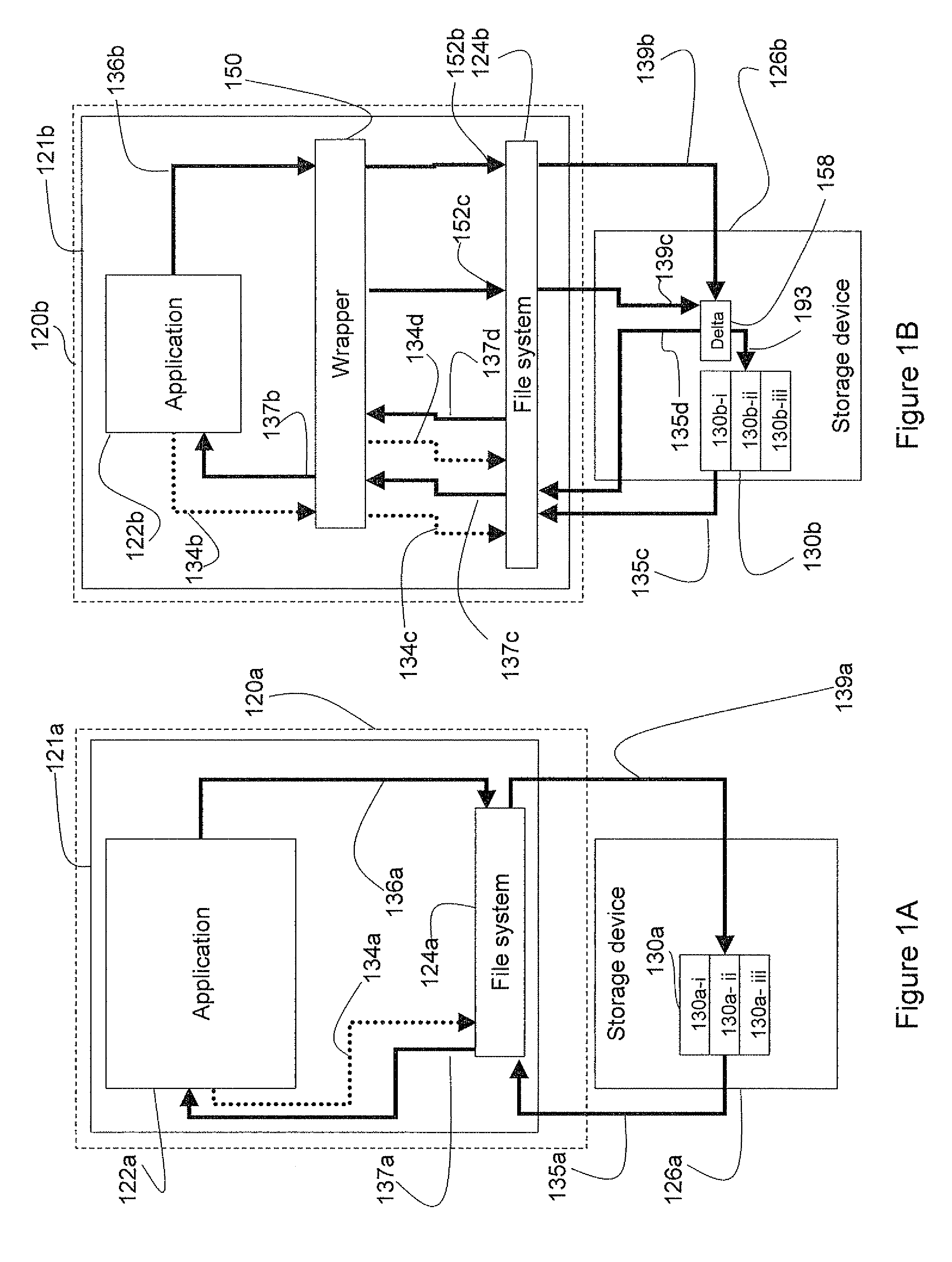
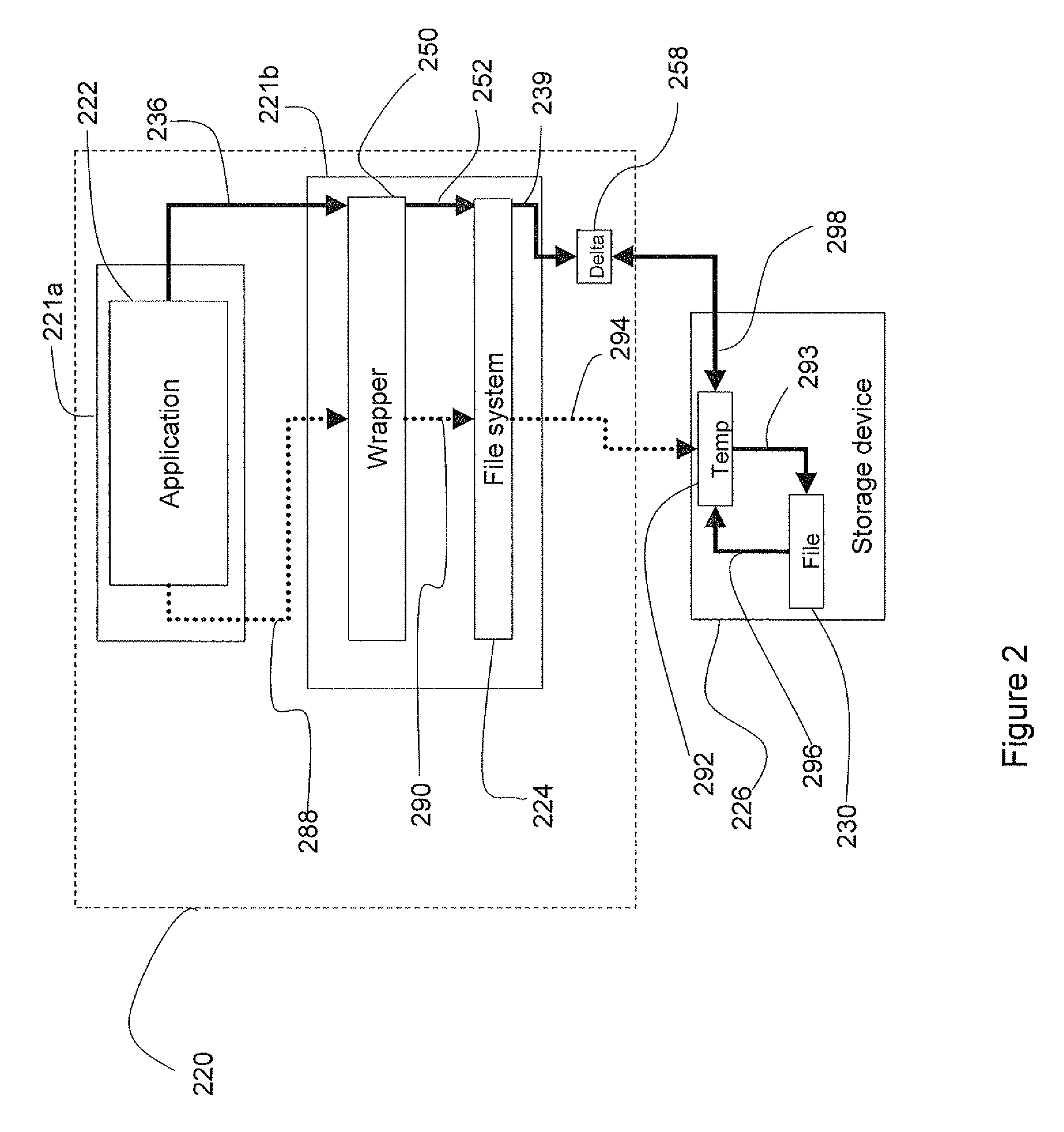
A system and method to protect a target file from data damage wherein a wrapper application transparently intercepts a write call operative to affect the target file and stores the pertinent data in a delta file. Occasionally the target file is backed up in a temporary file and then updated. The wrapper application also intercepts a read call operative to access the target file and merges the update information with data from the target file in a temporary file. The resulting merged data is returned as read results data.
Owner:WESTERN DIGITAL ISRAEL LTD
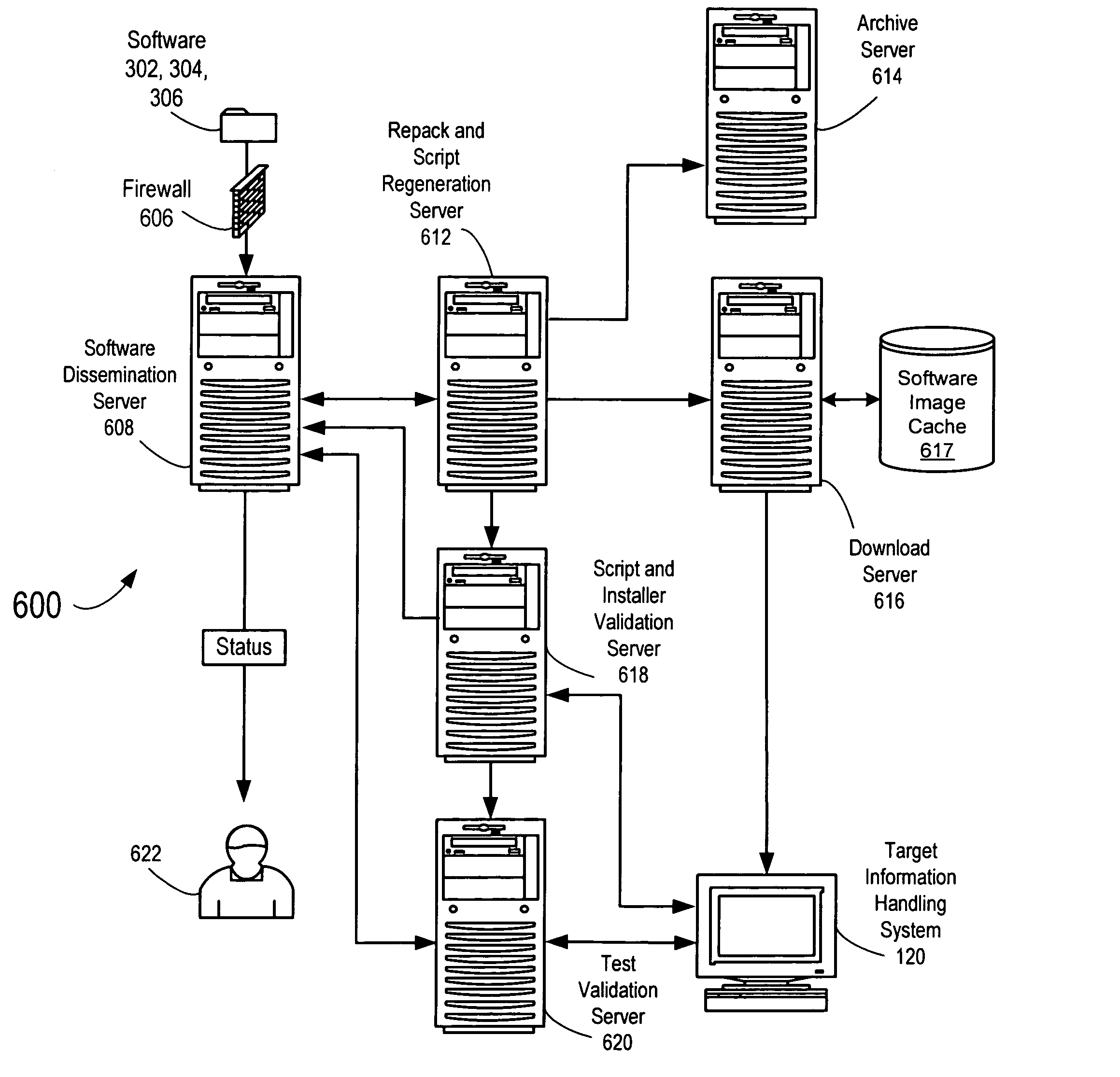
Method and system for automated generation of customized factory installable software
InactiveUS20050172284A1Reduce errorsShorten the timeProgram loading/initiatingMemory systemsInformation processingHandling system
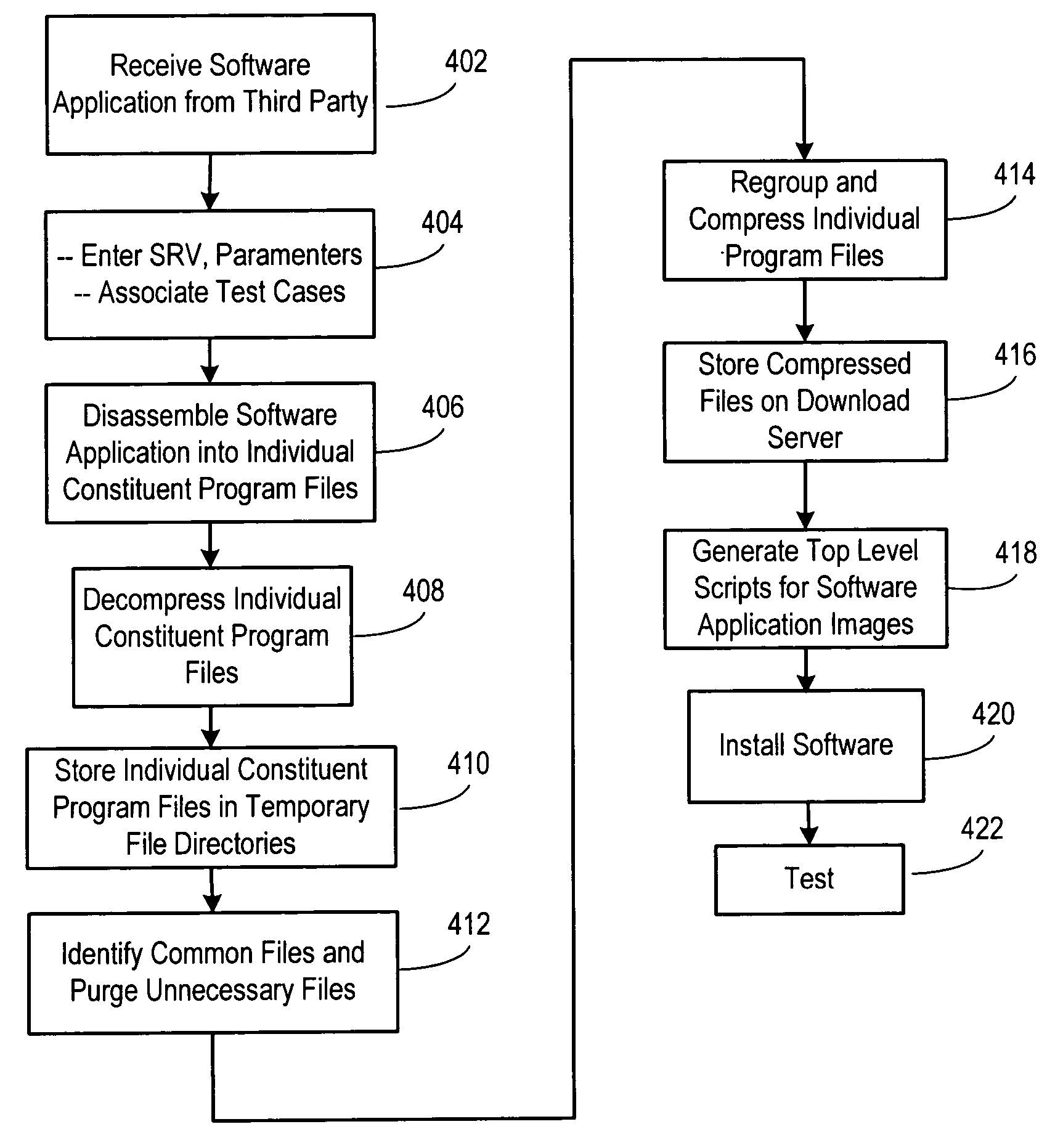
An automated system for software installation in a build-to-order information handling system. In one embodiment of the invention, a plurality of software applications are received and are disassembled to separate the individual constituent program files. These program files are decompressed and are stored in temporary file directories. Program files that are common to each of the software applications are identified and indexed. After the file analysis, the files are regrouped and a stored as a new set of compressed files. Once the new set of compressed files has been created, the top level scripts for the software application images are updated for use with the new compressed files to allow the desired combinations of software applications to be regenerated. The regenerated compressed files are then loaded into the factory servers for use in manufacturing information handling systems.
Owner:DELL PROD LP
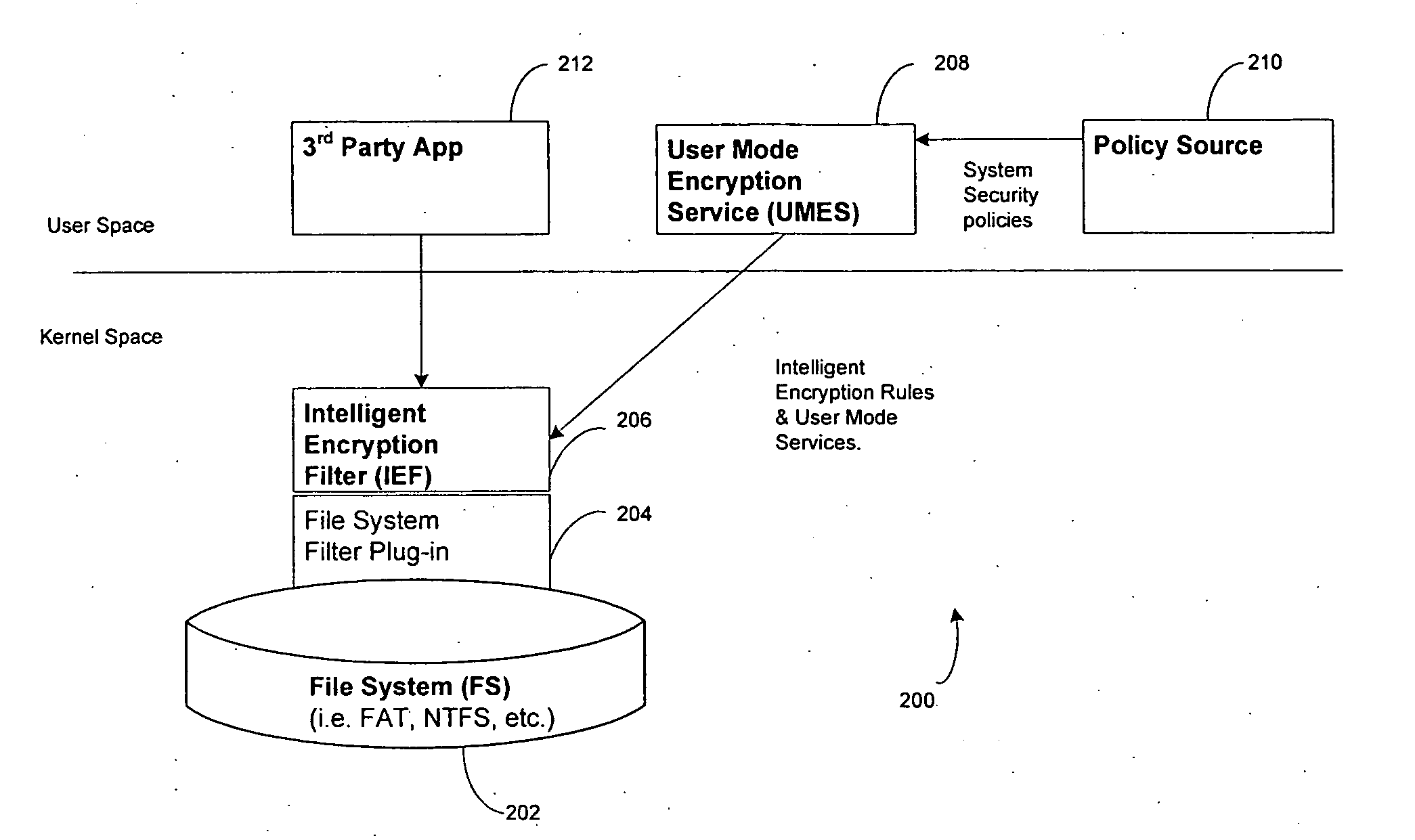
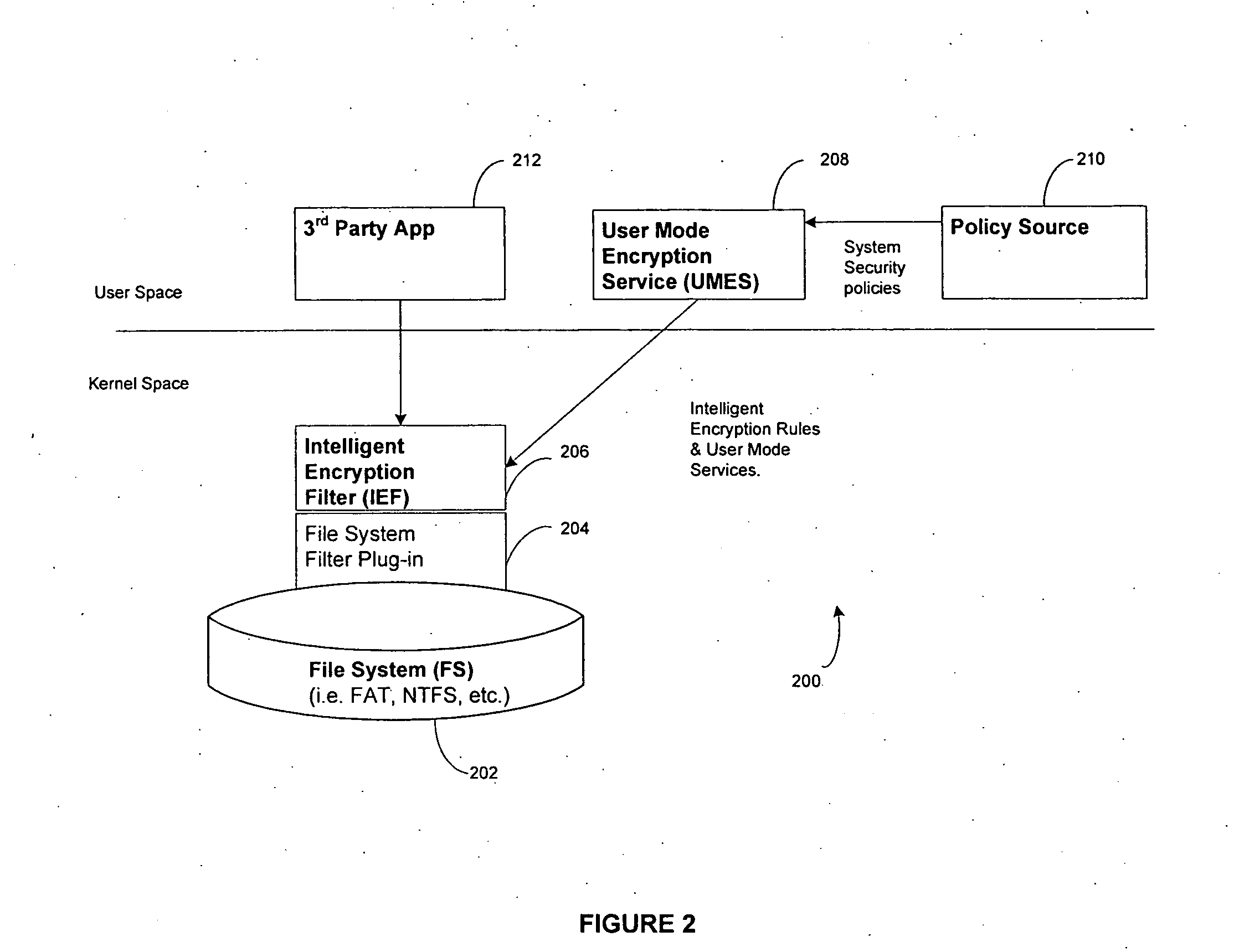
System and method for intelligence based security
ActiveUS20070174909A1Safe storageSlow performanceRandom number generatorsUser identity/authority verificationInformation processingOperational system
Included in the present disclosure are a system, method and program of instructions operable to protect vital information by combining information about a user and what they are allowed to see with information about essential files that need to be protected on an information handling system. Using intelligent security rules, essential information may be encrypted without encrypting the entire operating system or application files. According to aspects of the present disclosure, shared data, user data, temporary files, paging files, the password hash that is stored in the registry, and data stored on removable media may be protected.
Owner:DELL MARKETING
Virtual Memory Device (VMD) Application/Driver for Enhanced Flash Endurance
ActiveUS20150106557A1Memory architecture accessing/allocationInput/output to record carriersVirtual memoryFilename extension
A Virtual-Memory Device (VMD) driver and application execute on a host to increase endurance of flash memory attached to a Super Enhanced Endurance Device (SEED) or Solid-State Drive (SSD). Host accesses to flash are intercepted by the VMD driver using upper and lower-level filter drivers and categorized as data types of paging files, temporary files, meta-data, and user data files, using address ranges and file extensions read from meta-data tables. Paging files and temporary files are optionally written to flash. Full-page and partial-page data are grouped into multi-page meta-pages by data type before storage by the SSD. Ramdisks and caches for storing each data type in the host DRAM are managed and flushed to the SSD by the VMD driver. Write dates are stored for pages or blocks for management functions. A spare / swap area in DRAM reduces flash wear. Reference voltages are adjusted when error correction fails.
Owner:SUPER TALENT TECH CORP
Cache system in factory server for software dissemination
InactiveUS20050125524A1Minimizing size of cacheReduce the amount requiredCode conversionDigital computer detailsInformation processingFile comparison
A method and apparatus for minimizing the size of the cache that is required to store software packages for installation on an information handling system. An analysis is conducted on the individual program files contained in a software application file. In the analysis, the software application file is disassembled into the individual program files and each of the program files is decompressed and stored in temporary file directories. Files that are common to each of the software packages are identified. After the file comparison, the method and apparatus of the present invention is used to re-group the files to generate a composite program file library that contains all of the program files needed to regenerate the software application files. This composite program file library is then stored on a cache in a factory server used to manufacture information handling systems in a build to order process.
Owner:DELL PROD LP
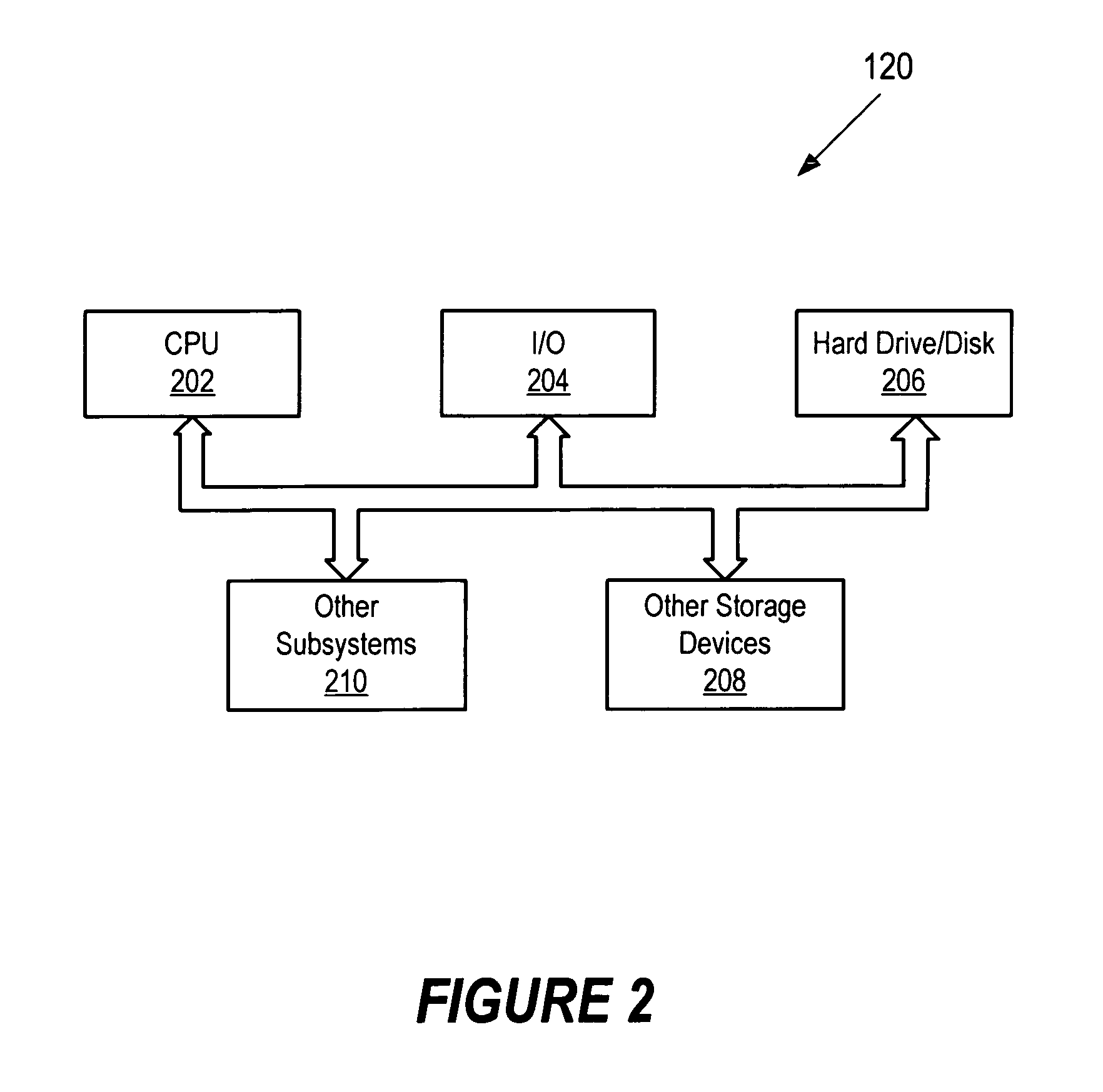
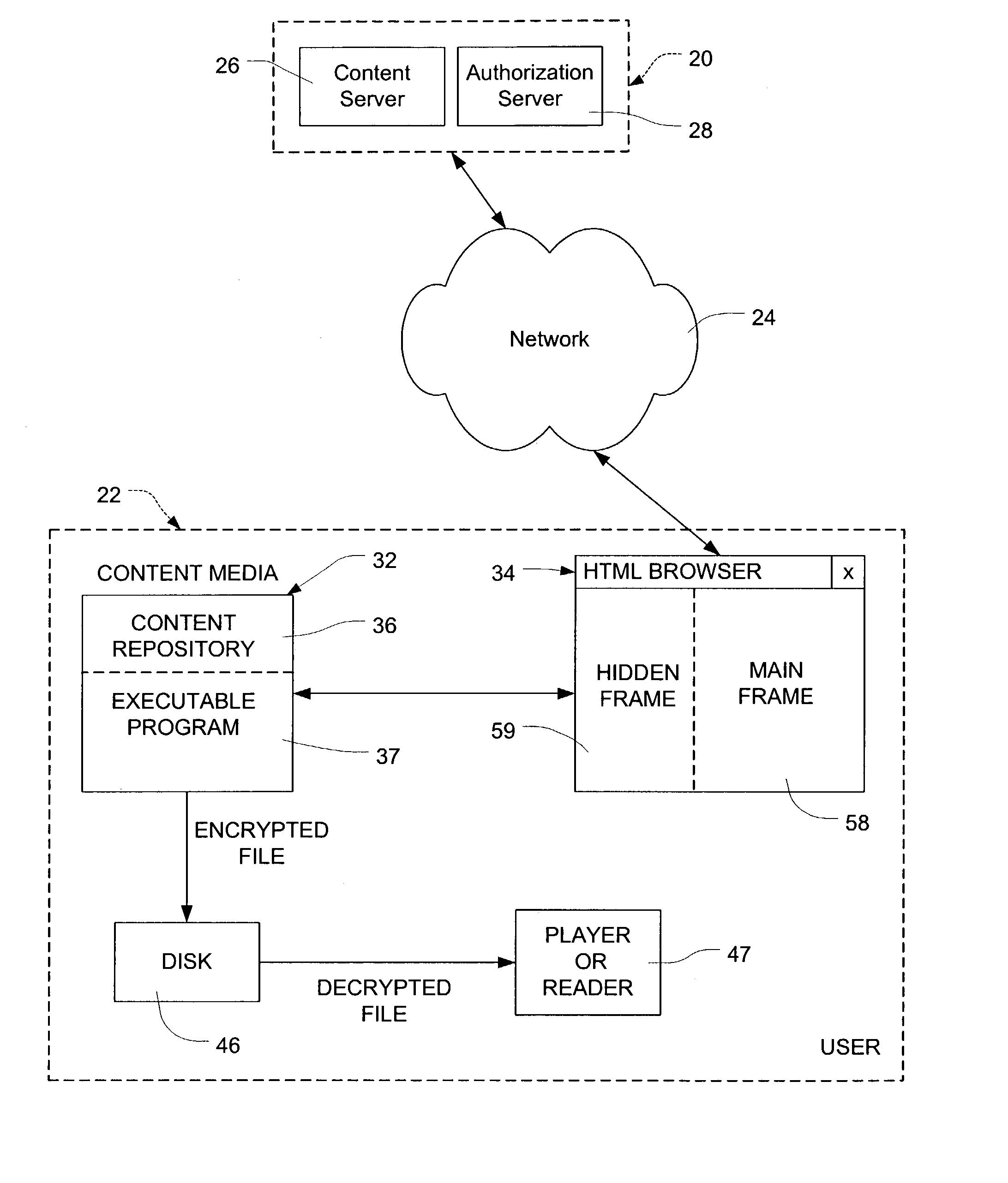
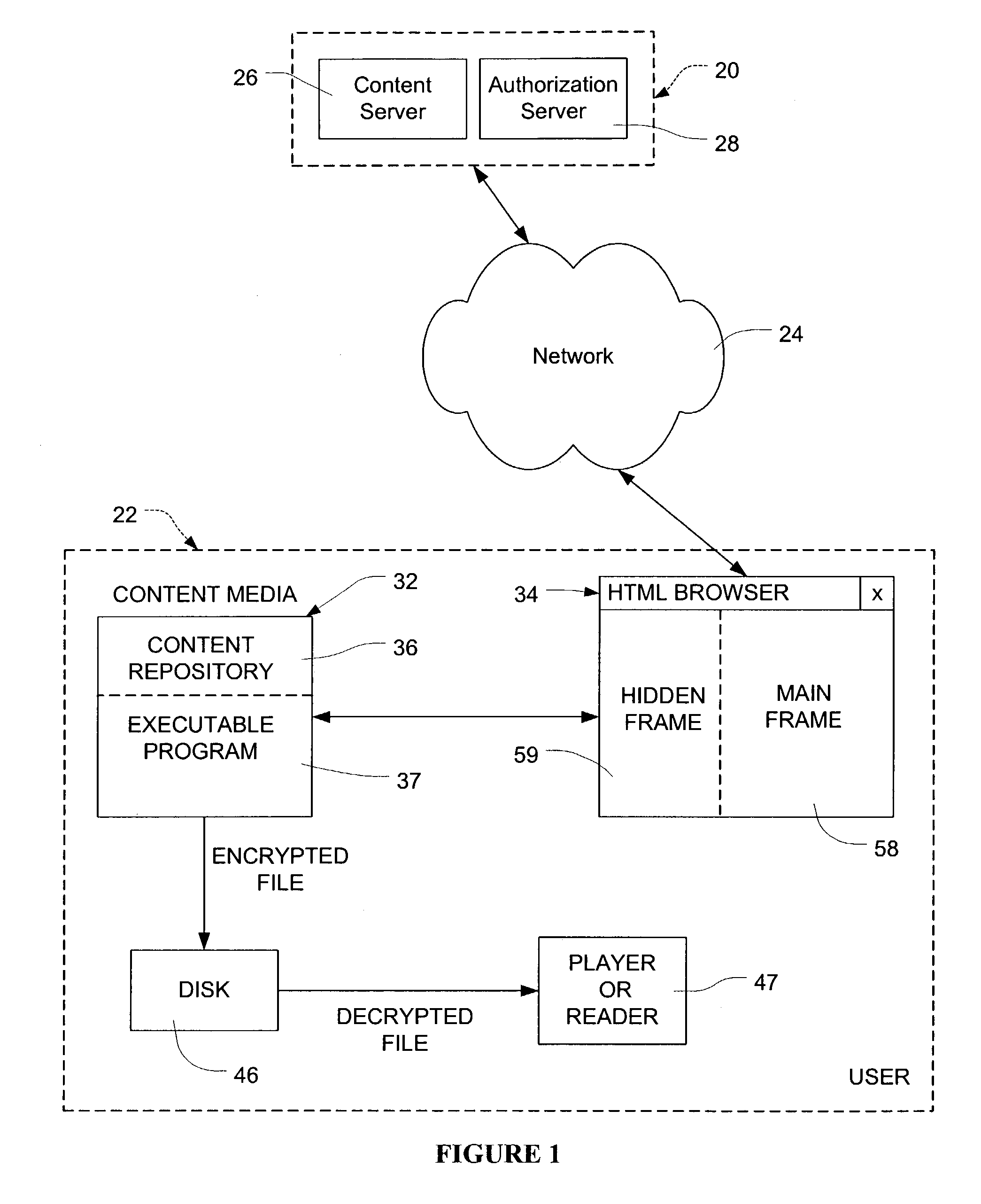
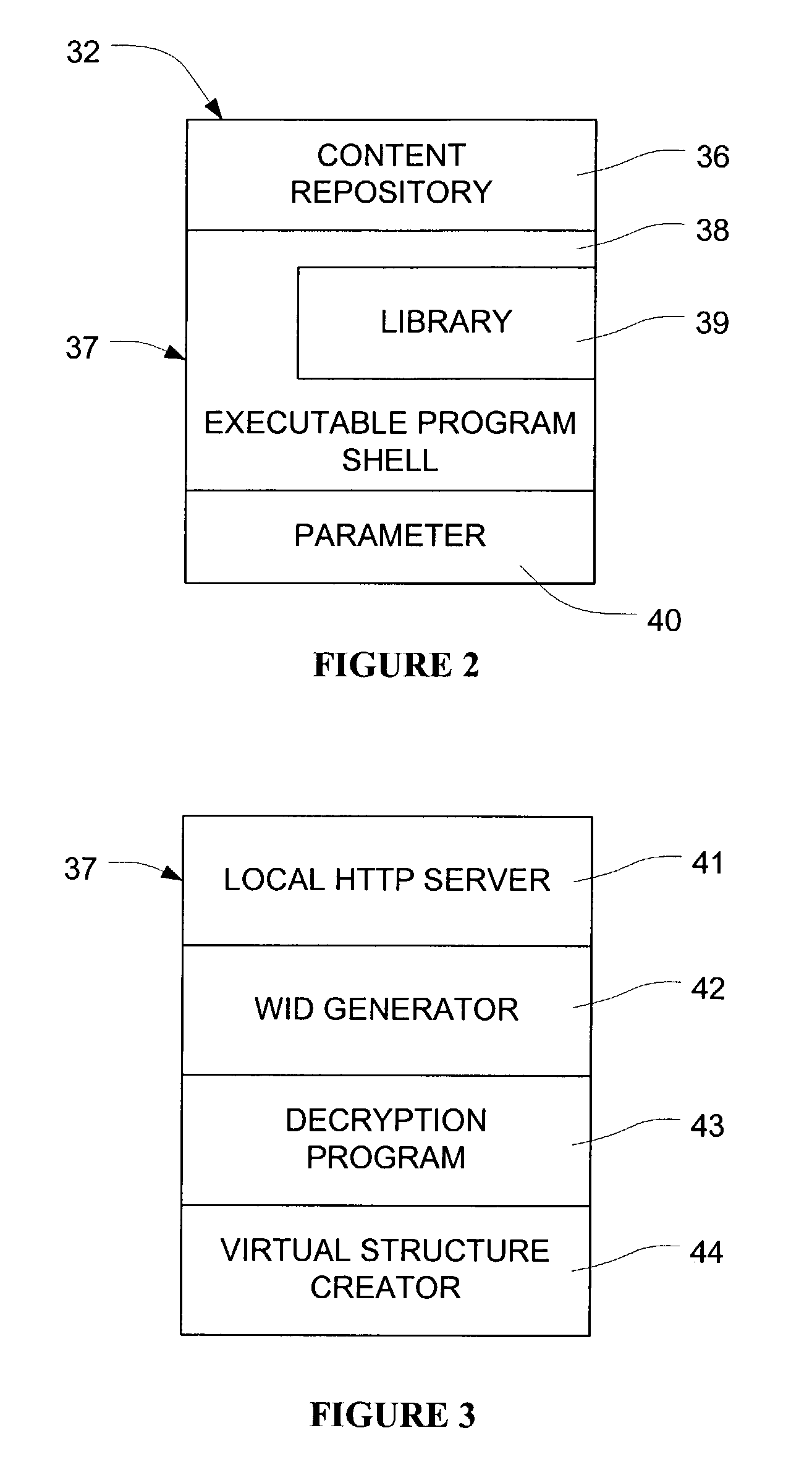
Remote access authorization of local content
InactiveUS7089425B2Digital data processing detailsUser identity/authority verificationPersonalizationLogin session
Network users are authorized individual access during a log-on session to encrypted content on content media at the user without the necessity of individualizing the content media for the particular user. The content may comprise multimedia data. The content media, which may be mass produced and distributed, includes a computer program which generates a unique configuration identifier upon instantiation of the program to begin a user access session. The program creates a virtual directory structure for the content that is uniquely determined for that session by the configuration identifier. The configuration identifier is uploaded to a remote server which uses the configuration identifier with other information identifying the content media and the user authorize user access. The remote server creates and downloads to a browser of the user an encrypted message containing URLs for accessing the content in the virtual directory structure and containing transformations of a decryption algorithm and decryption keys for the encrypted content. Encrypted multimedia content selected by the user is stored in a temporary file, decrypted in a moving time window, and rendered After rendering, the decrypted portion of the temporary file is scrambled to preclude further access.
Owner:C14 TECH
Method and system concurrently accessing a large amount of small documents in cluster storage
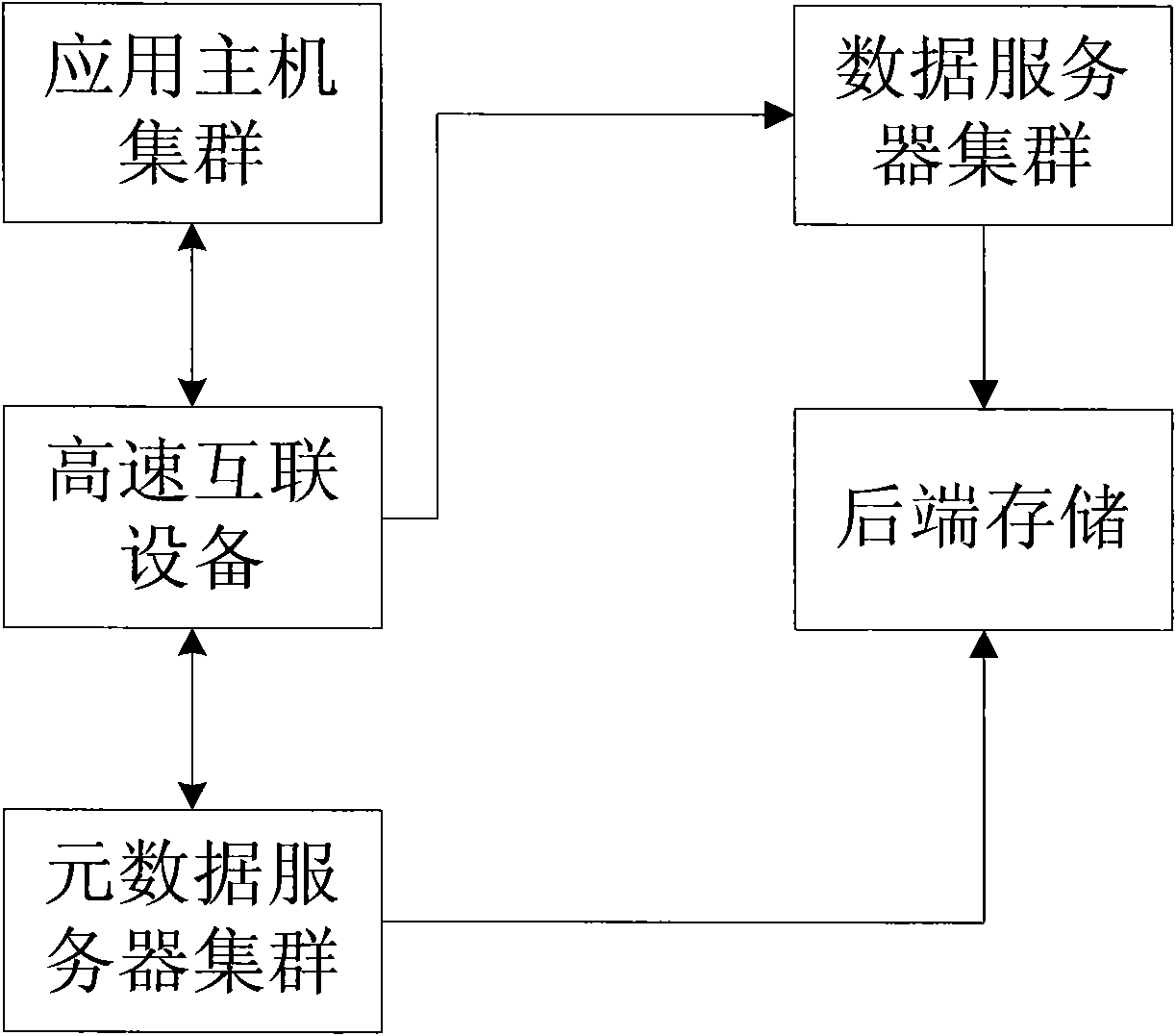
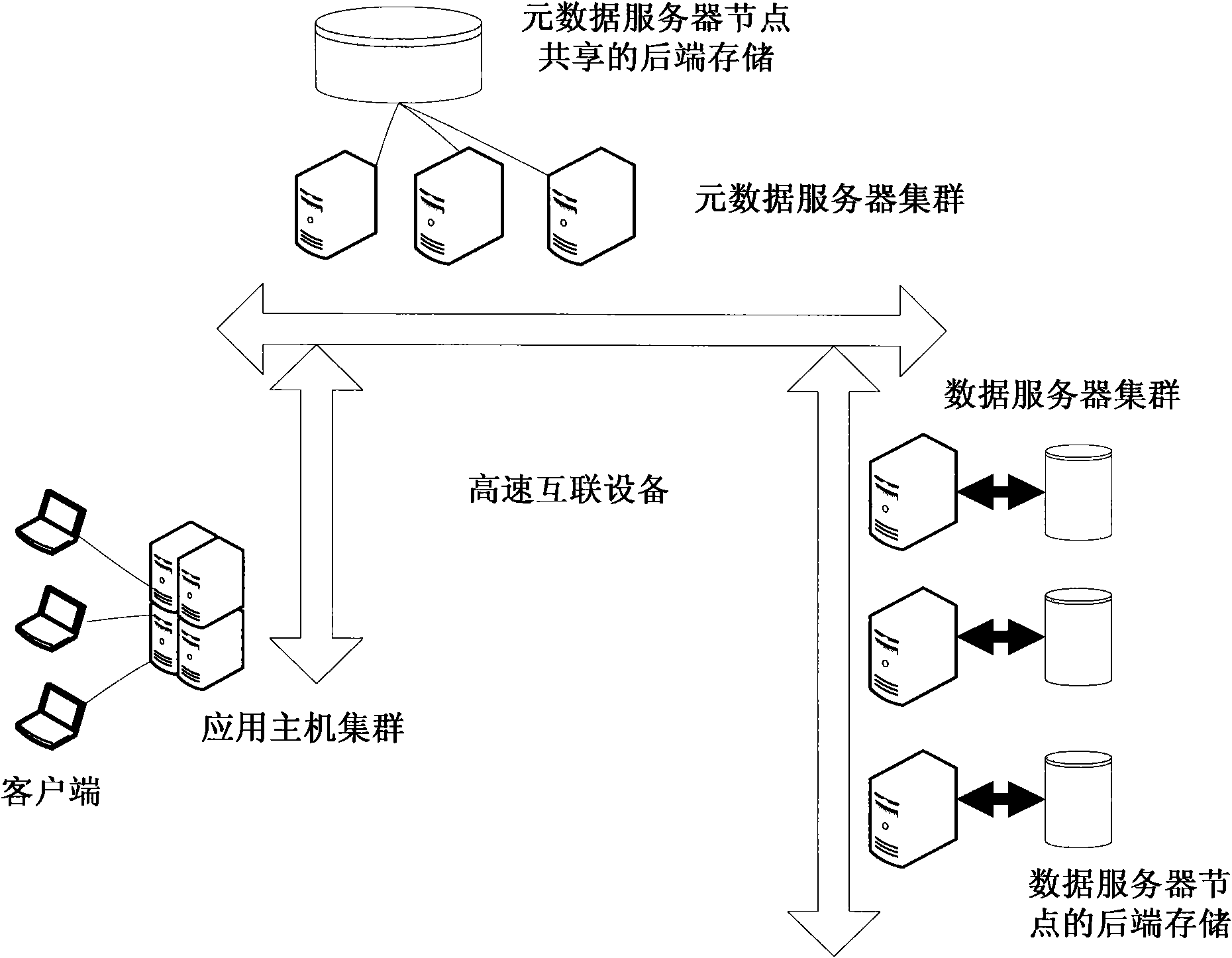
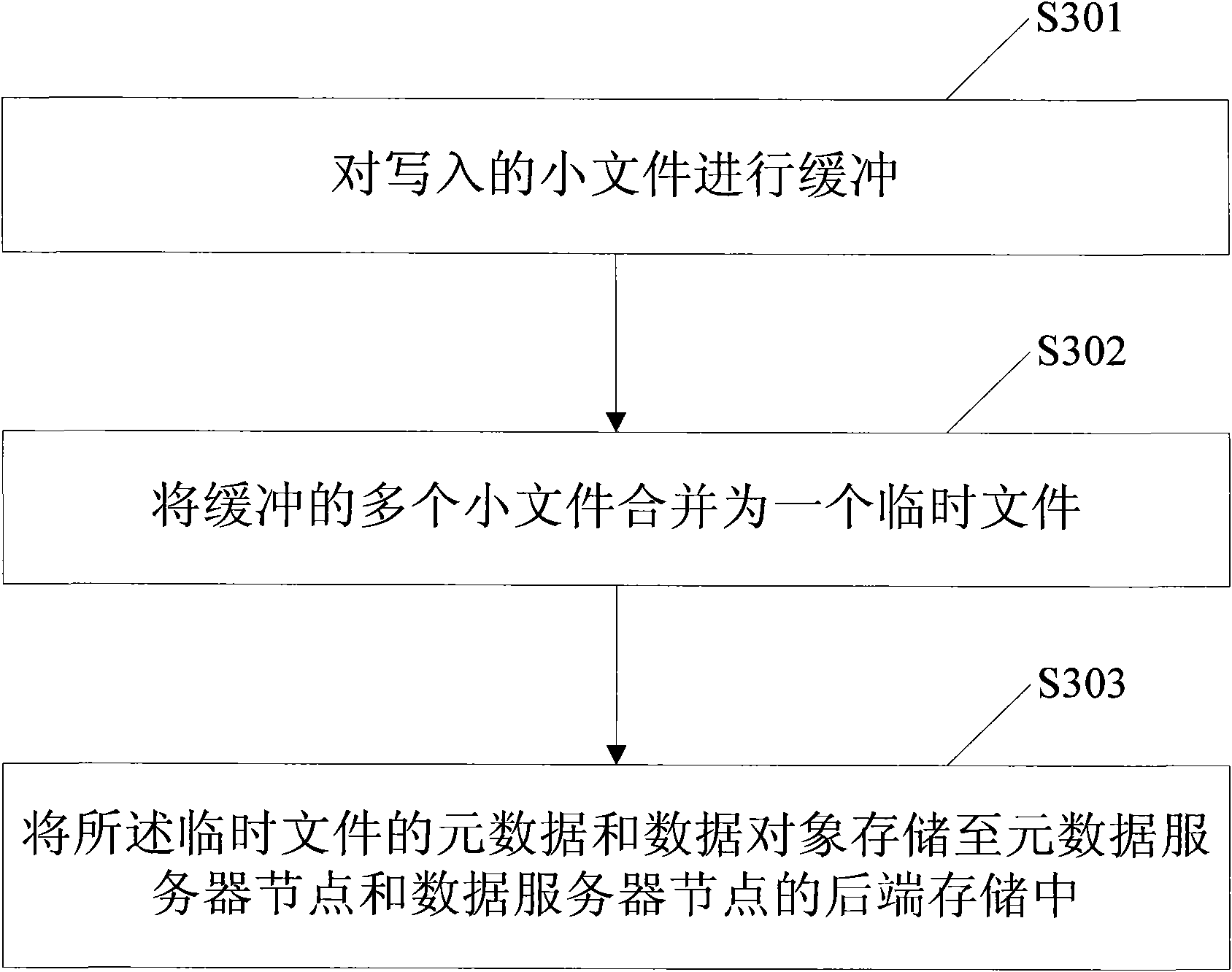
ActiveCN101854388AShort response timeImprove response speedTransmissionSpecial data processing applicationsClustered file systemPaper document
The invention provides a method and system concurrently accessing a large amount of small documents in cluster storage. The method comprises the following steps: the written small documents are buffered, a plurality of buffered small documents are merged into one temporary document, the metadata and the data object of the temporary document are stored into the backend storage of a metadata server node and a data server node. The method can effectively improve the response time and speed of the cluster document system service and the whole data read and write time and transaction capacity per unit time of the data.
Owner:SUZHOU LANGCHAO INTELLIGENT TECH CO LTD
Super-endurance solid-state drive with endurance translation layer (ETL) and diversion of temp files for reduced flash wear
ActiveUS8959280B2Memory architecture accessing/allocationInput/output to record carriersFilename extensionData file
Owner:SUPER TALENT TECH CORP
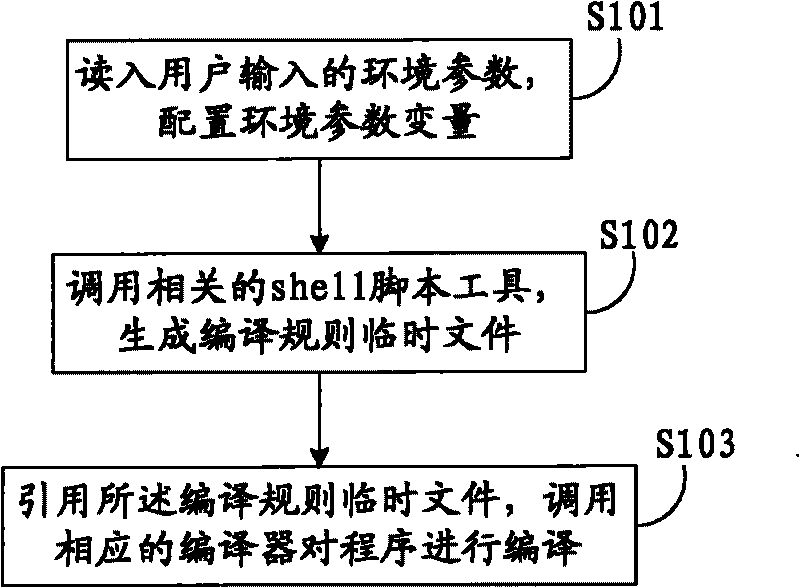
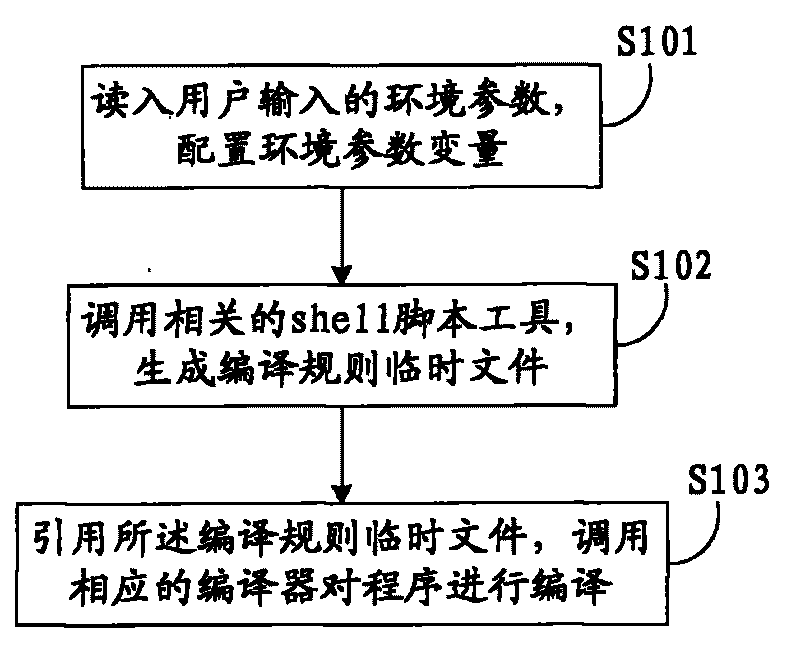
Method and device for compiling program
The invention discloses a method and a device for compiling a program. The method comprises the following steps: reading in environmental parameters input by a user and configuring variables of the environmental parameters; calling a related shell script tool to generate a compiling rule temporary file; and quoting the compiling rule temporary file, and calling a corresponding compiler to compile the program. The method and the device can conveniently and quickly finish compiling, are easy to maintain and transplant, and can improve the compiling speed.
Owner:NETPOSA TECH
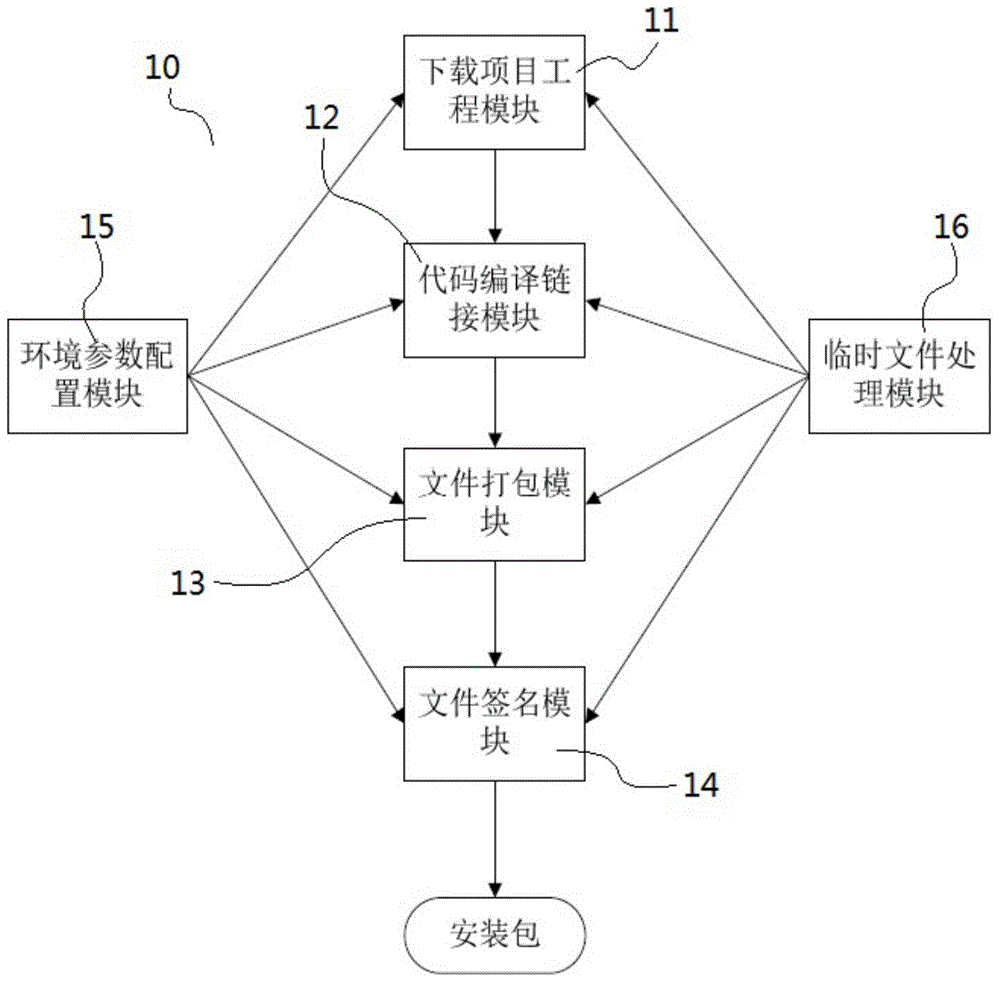
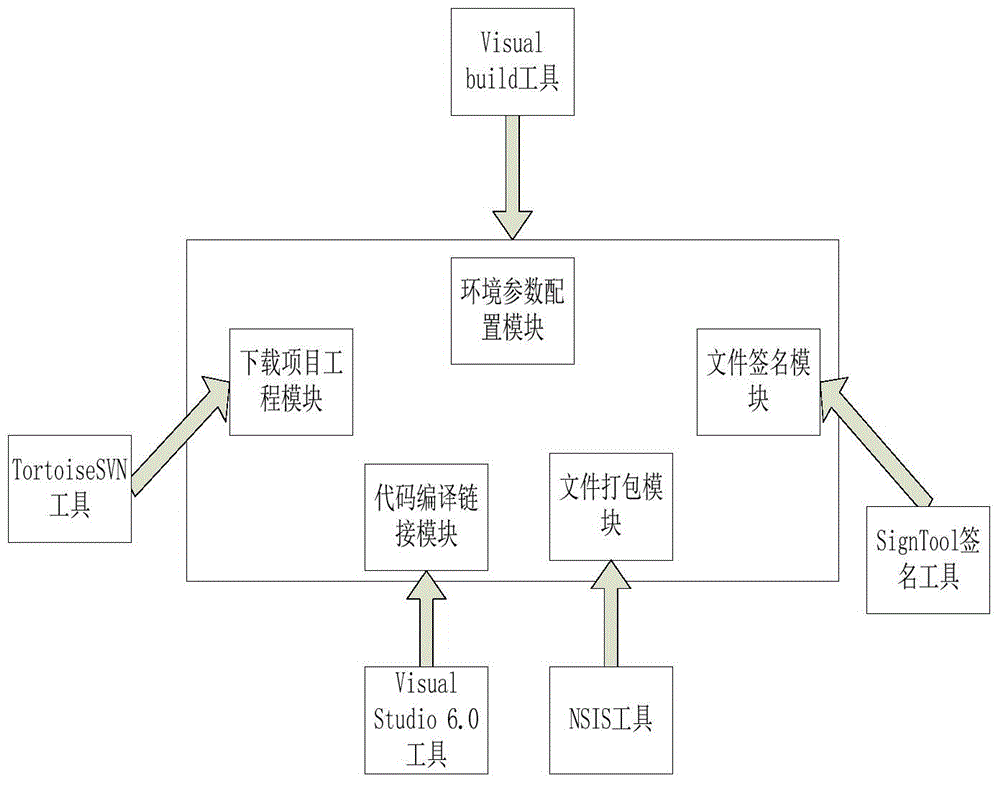
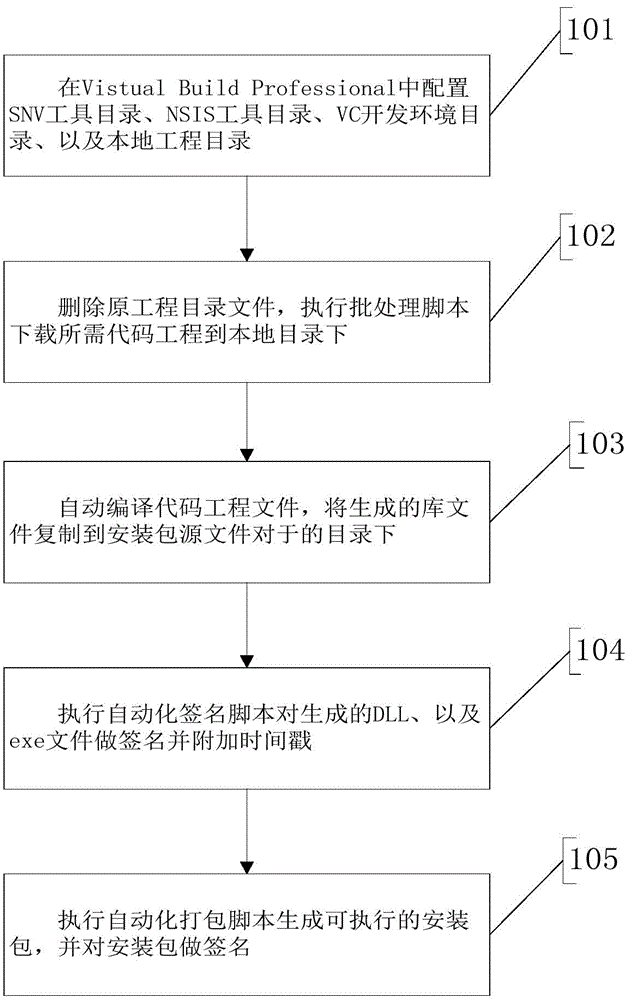
Automatic quick generation system and method for UKey installation package
ActiveCN104572237AAutomatic generatedQuick buildProgram controlMemory systemsSource code fileSoftware engineering
The invention discloses automatic quick generation system and method for a UKey installation package. The system comprises a download item project module, a code compiling and linking module, a file packaging module, a file signature module, an environmental parameter configuration module and a temporary file processing module which are matched with each other. The method comprises the installation package generation steps of (1) configuring and integrating a development environment directory, a SVN path, an NSIS path and a local directory; (2) creating a project folder in the local directory, and downloading a source code file of the project from a source code SVN sever; (3) automatically compiling a script, and compiling a program library as requirement; (4) preparing a signature time stamp for the generated library document; (5) packing the script through NSIS, and generating an installation package executable file. According to the scheme, the system and method have the advantages that the UKEY installation package can be automatically generated, thus the preparation process is greatly simplified, and the working efficiency of developers can be effectively increased.
Owner:DYNAMICODE
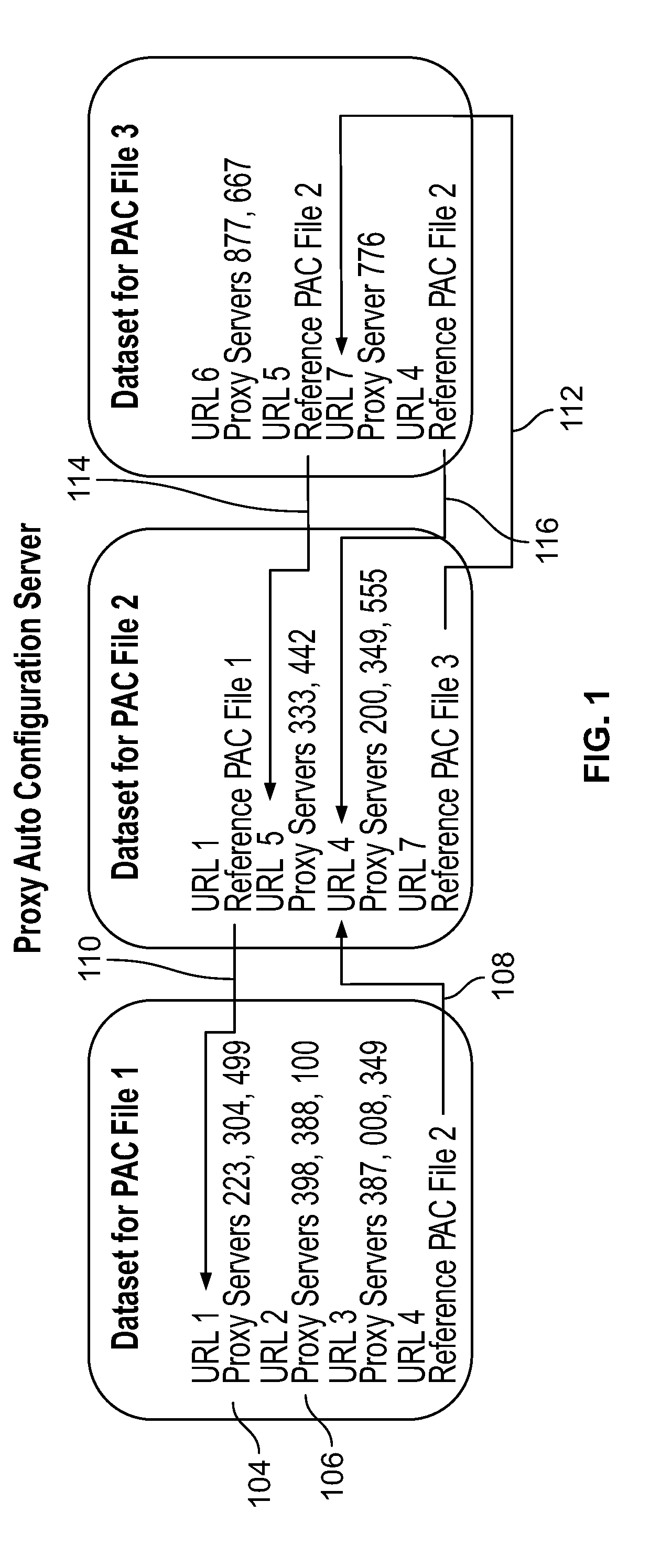
Proxy automatic configuration file manager
ActiveUS20190036777A1Minimize update anomalyMinimize update anomaliesData switching networksWeb browserUniform resource locator
A PAC file manager is provided. The PAC file manager may include PAC files. The PAC files may be generated by, and be resident on, a PAC server. The PAC file manager may include update processors. Each update processor may include a capability to transmit update information to the PAC server. The update information may be for updating URLs included in the PAC files. The PAC file manager may also include general processors and proxy servers. Each time a general processor launches a web browser, the general processor may download a PAC file from the PAC server. The PAC file may be stored in a temporary file associated with the general processor. Each PAC file may include instructions to be used to direct the associated general processor how to access the URL. The instructions may identify whether to use a proxy server and which specific proxy server to use.
Owner:BANK OF AMERICA CORP
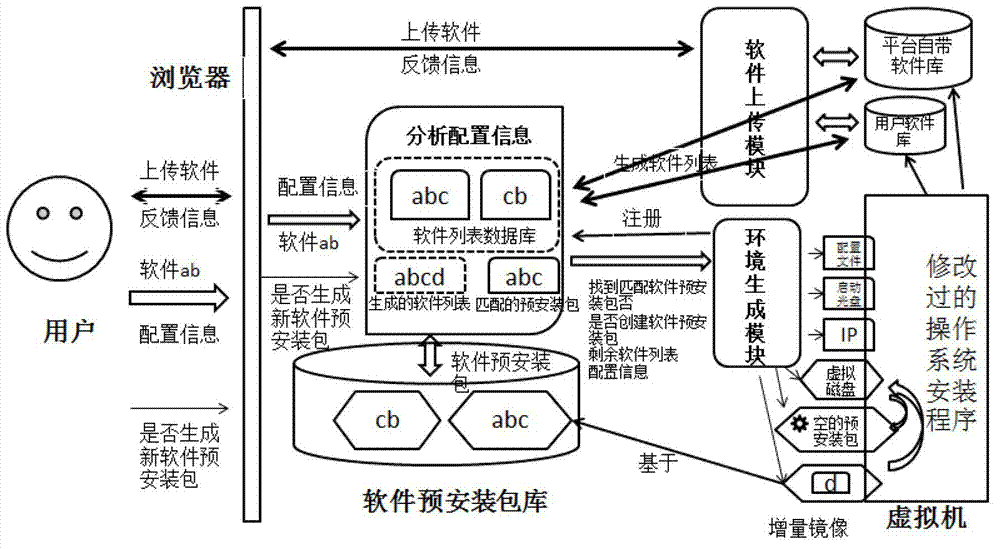
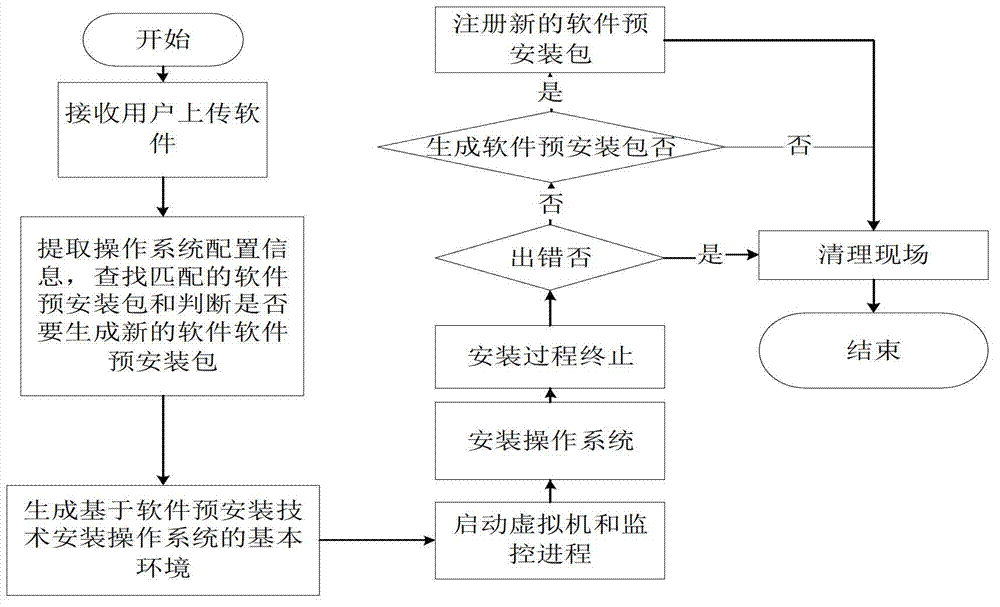
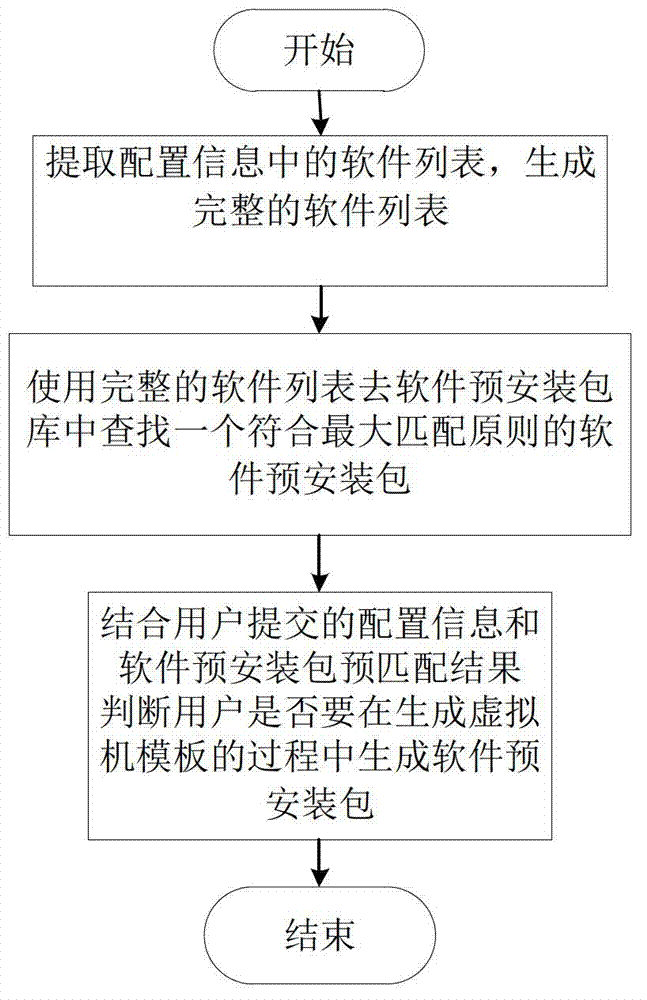
Virtual machine mirror image generating method and device based on software preinstallation in cloud environment
ActiveCN103092650AIncrease generation speedAvoid duplicate installationsProgram loading/initiatingIp addressSystem configuration
The invention discloses a virtual machine mirror image generating method and a device based on software preinstallation in cloud environment. The virtual machine mirror image generating method and the device based on the software preinstallation in the cloud environment comprise that softwares which are uploaded by users are received and dependency of the uploaded softwares are checked, operating system configuration information which is submitted by the users is received and analyzed to obtain analysis results of the operating system configuration information. Basic environment which is necessary to install an operating system based on the software preinstallation technology is generated according to the analysis results of the operating system configuration information. A virtual machine start is started by using a virtual machine start configuration file in the generated environment and a monitoring progress is started at the same time. An operating system installation program is operated in the virtual machine and the operating system is installed in a non-interactive mode. Meanwhile, the monitoring progress judges whether the installation of the operating system is wrong or accomplished or not. When the installation of the operating system is wrong, the virtual machine is closed and temporary files in the basic environment are cleaned and internet protocol (IP) address is returned to an IP address pool. The virtual machine mirror image generating method and the device based on the software preinstallation in the cloud environment can solve defects of an existing manner, wherein the defects of the existing manner are insufficient in flexibility, low in speed, serious in source consumption and the like.
Owner:HUAZHONG UNIV OF SCI & TECH
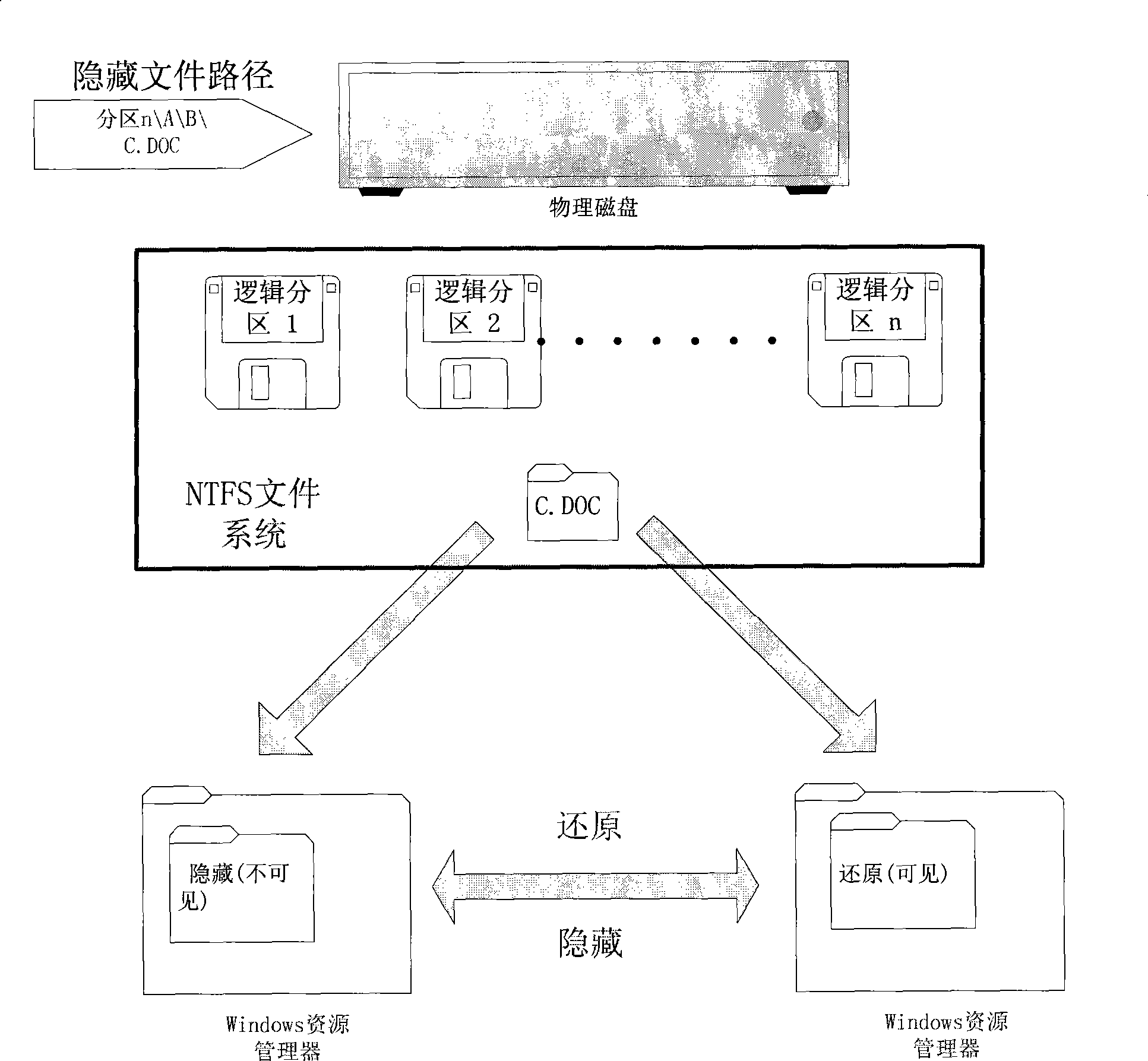
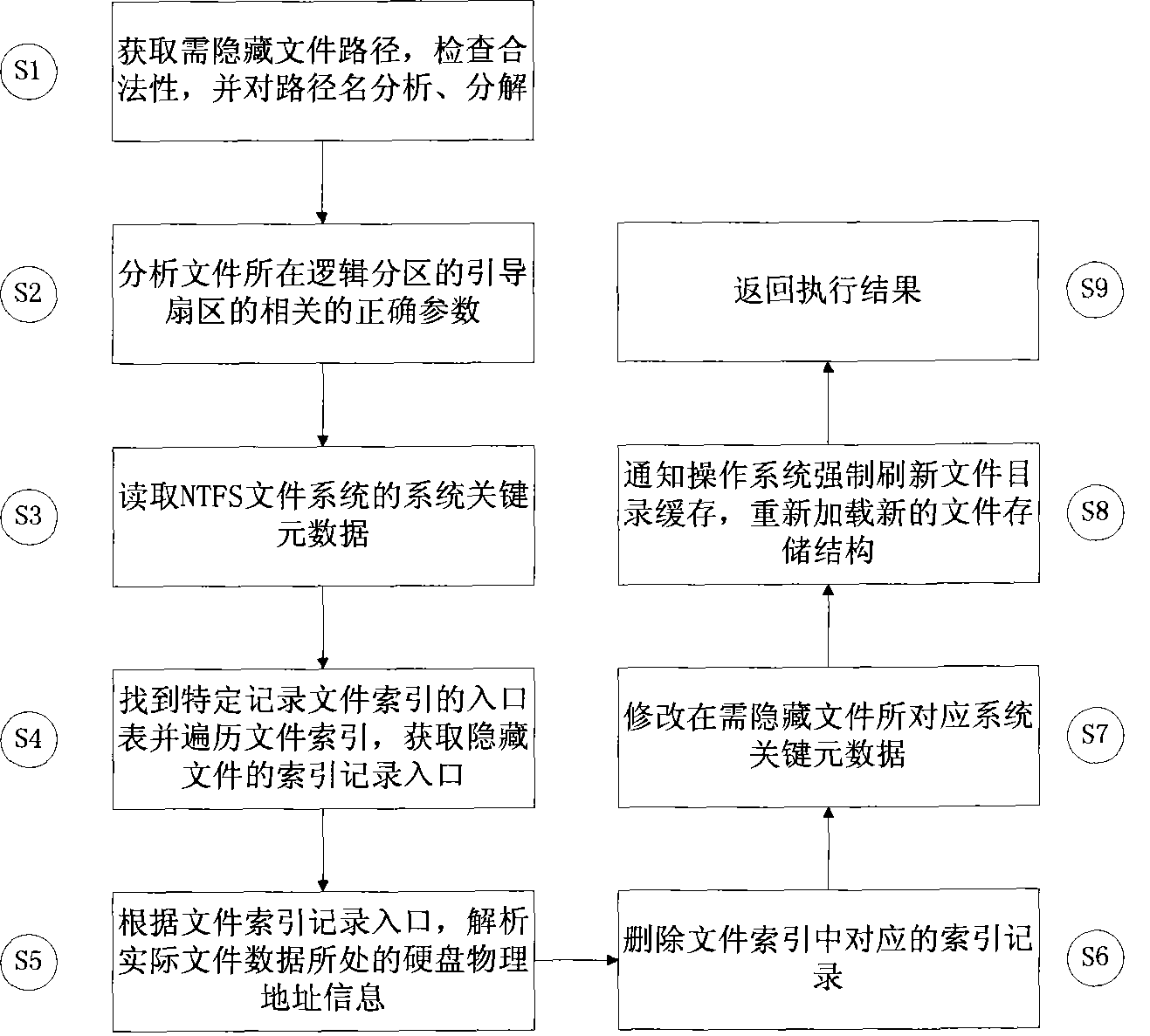
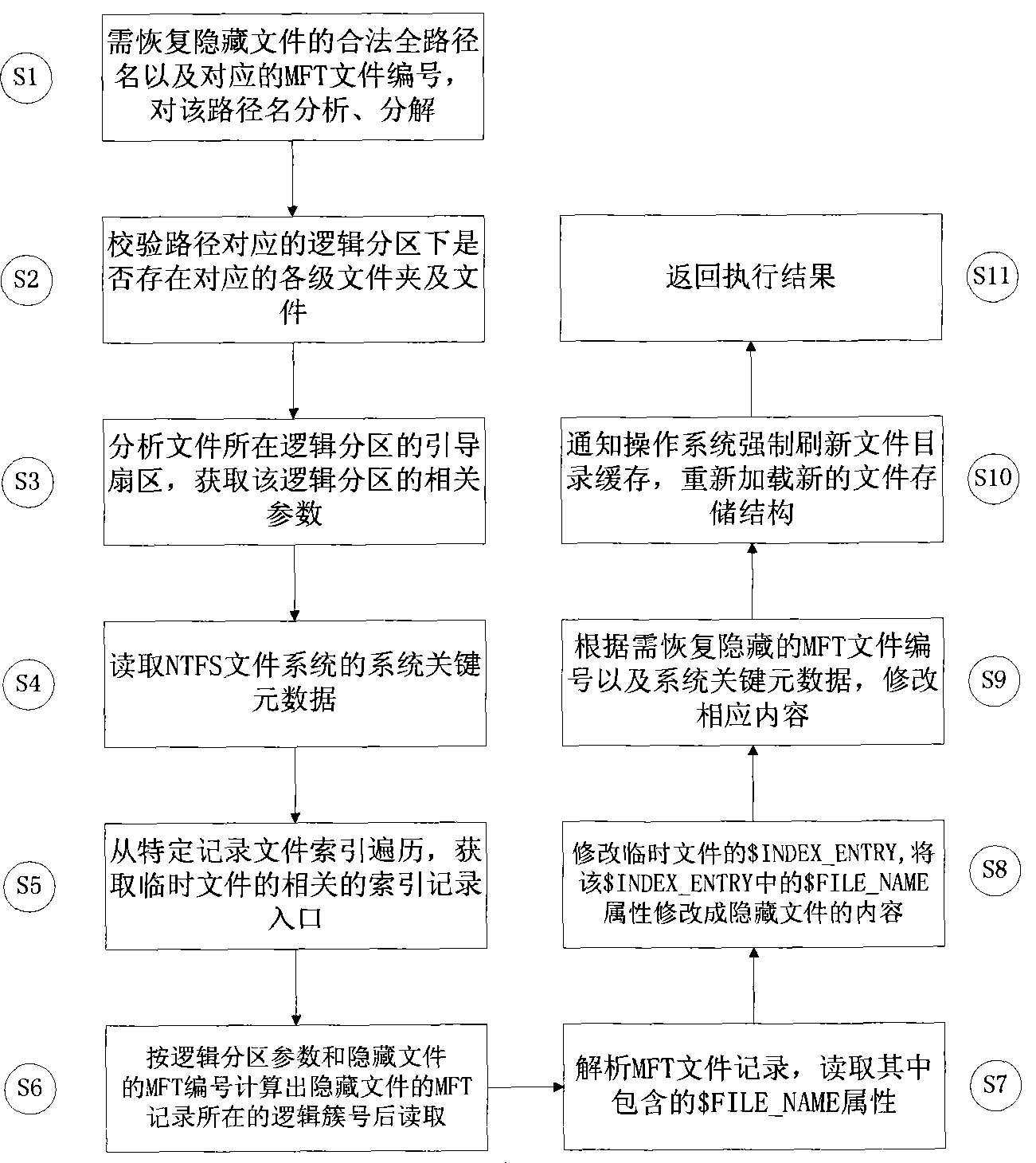
Light file hiding method in NTFS file system
InactiveCN101464900AWill not increase the waiting time for executionImprove integritySpecial data processing applicationsData integrityHidden data
The invention discloses a method for hiding light-weight files under an NTFS file system, which belongs to the technical field of computer network information. The method comprises a data hiding method and a hidden data recovering method, wherein, the data hiding method is characterized in that metadata of the file system referred according to the legal file path traverses index record entries of special files, thereby achieving the purpose of hiding file data. The hidden data recovering method is characterized in that the hidden data is redisplayed and added into the file system by altering the index record entry of a temporary file according to the legal file path and the record number of the hidden files, thereby achieving the purpose of recovering the hidden data. By adopting the invention, the confidentiality of confidential data and the transparency for other users can be realized through data hiding. Meanwhile, data exchange and operation expenditure during the execution process of hidden data are minimized, and data integrity and reliability are protected to the greatest extent.
Owner:SHANGHAI JIAO TONG UNIV
Method for trimming data on non-volatile flash media
ActiveUS20110145306A1Memory architecture accessing/allocationSpecial data processing applicationsComputer scienceTemporary file
A method for trimming data on non-volatile flash media is generally presented. In this regard, in one embodiment, a method is introduced comprising allocating a temporary file that occupies free space on a flash memory, determining specific blocks of the flash memory that the temporary file occupies, generating TRIM commands for the specific blocks, and deleting the temporary file. Other embodiments are described and claimed.
Owner:SK HYNIX NAND PROD SOLUTIONS CORP
Self-Contained Application Disk for Automatically Launching Application Software or Starting Devices and Peripherals
InactiveUS20070214187A1Simplify useEasy to operateDigital data processing detailsDigital data protectionData fileRemovable media
A system and method for automatically executing a participating application upon insertion of a removable media into a computing device. When the computing device detects that the removable media containing has been inserted, a task disk control file is read from the removable media. The task disk control file contains all of the configuration information necessary to run the participating application from the removable media The participating application is then launched for use by a user. After the user is finished using the participating application, the removable disk is automatically ejected. In addition to monitoring for insertion of the removable media, events such as a completion of the self-contained application and a request to eject the media are monitored. When a completion event is encountered, all data files are saved, temporary files deleted and configuration information removed prior to the removable disk ejection. When an ejection event is encountered, the computing device is instructed to wait until the completion events are executed prior to actual ejection of the removable media.
Owner:EMC CORP
Incremental transparent file updating
InactiveUS8589341B2Protection from damageEfficient updateMemory loss protectionDigital data processing detailsData CorruptionApplication software
Owner:WESTERN DIGITAL ISRAEL LTD
Method for encrypting files by adopting encryption sandbox
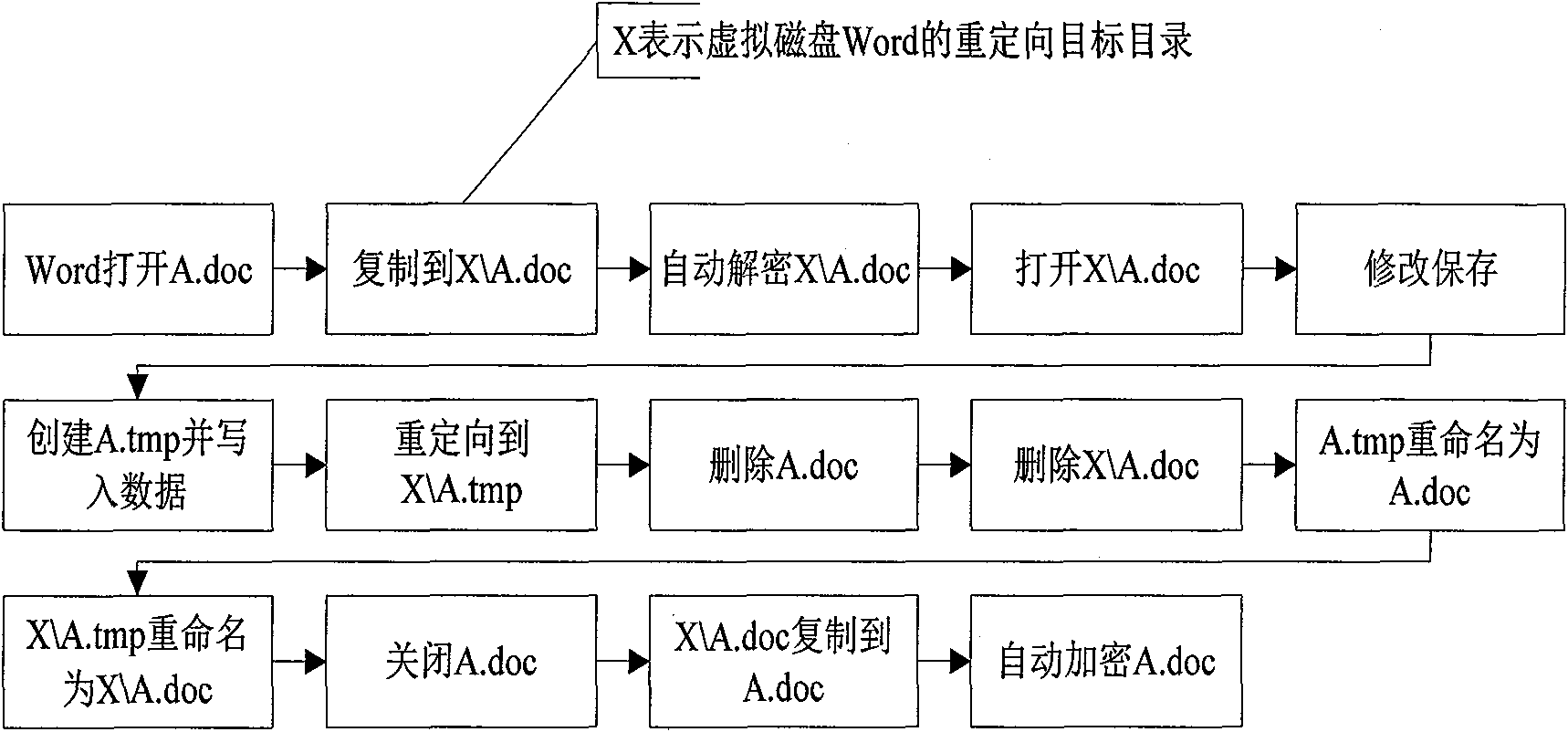
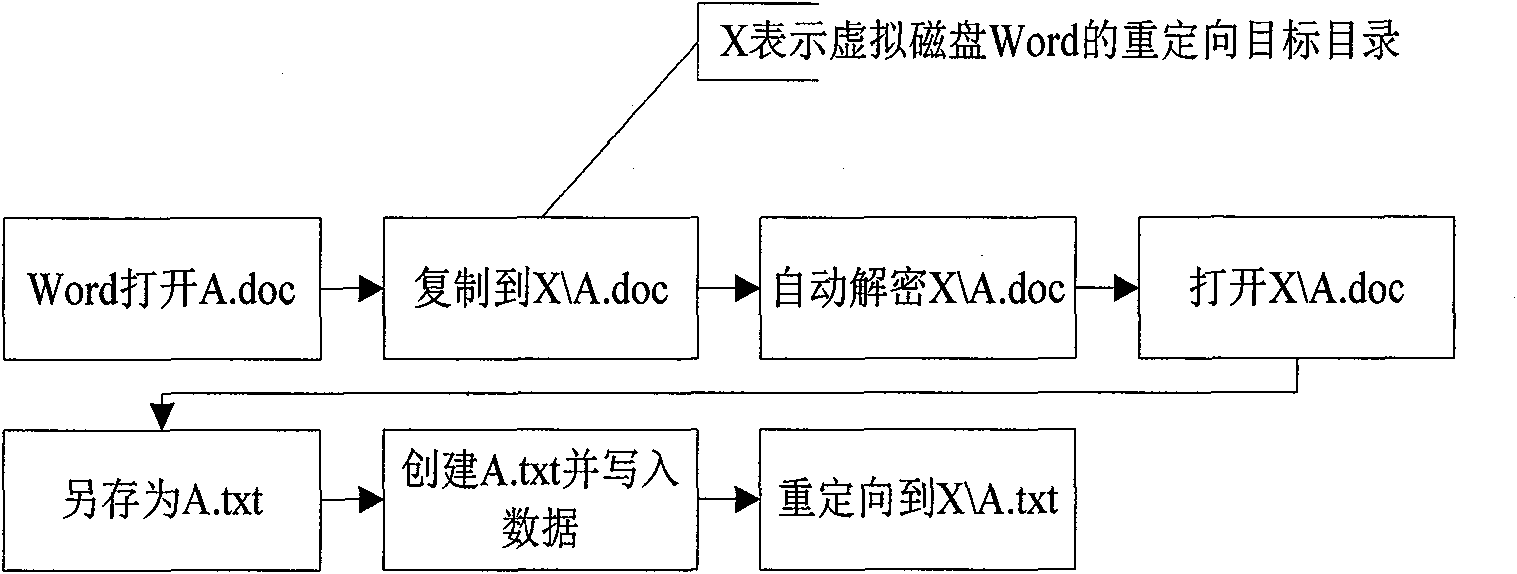
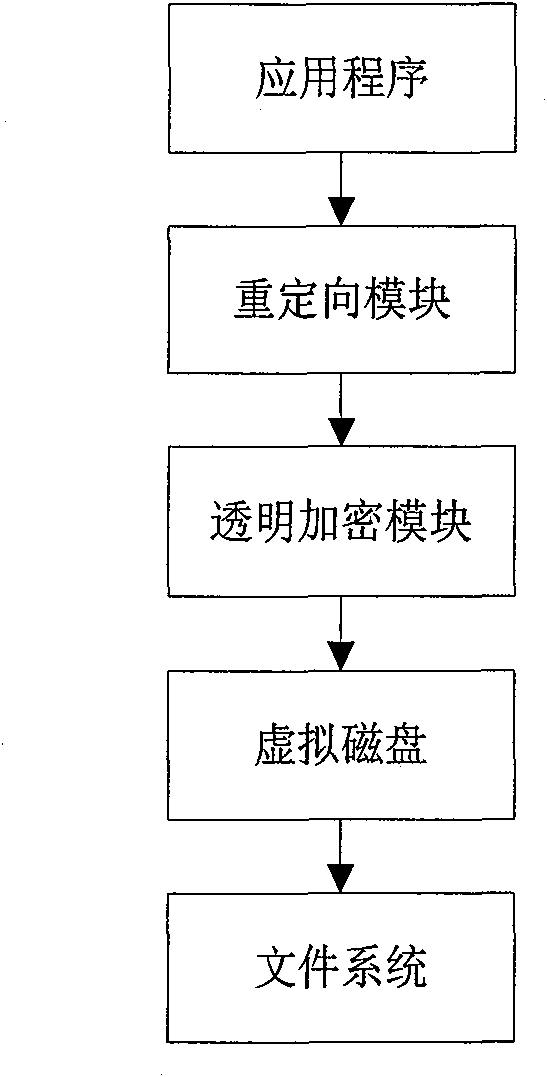
InactiveCN101847184AWill not cause leaksSolve the leakage problemDigital data protectionPlatform integrity maintainanceComputer hardwareFile copying
The invention discloses a method for encrypting files by adopting an encryption sandbox, which borrows ideas from the sandbox principle. When opened, a filed is copied and reoriented to a virtual disk, and all editing operations are performed in the virtual disk; when closed (or every once in a while), the file is encrypted and copied and covers the original file to achieve the effect of encryption. All files stored in the virtual disk are temporary files which can be deleted, but the deletion can not influence a system, which is just like a sandbox. With the method, the stability of encryption and decryption can be improved and the policy setting can be simplified.
Owner:深圳市虹安信息技术有限公司
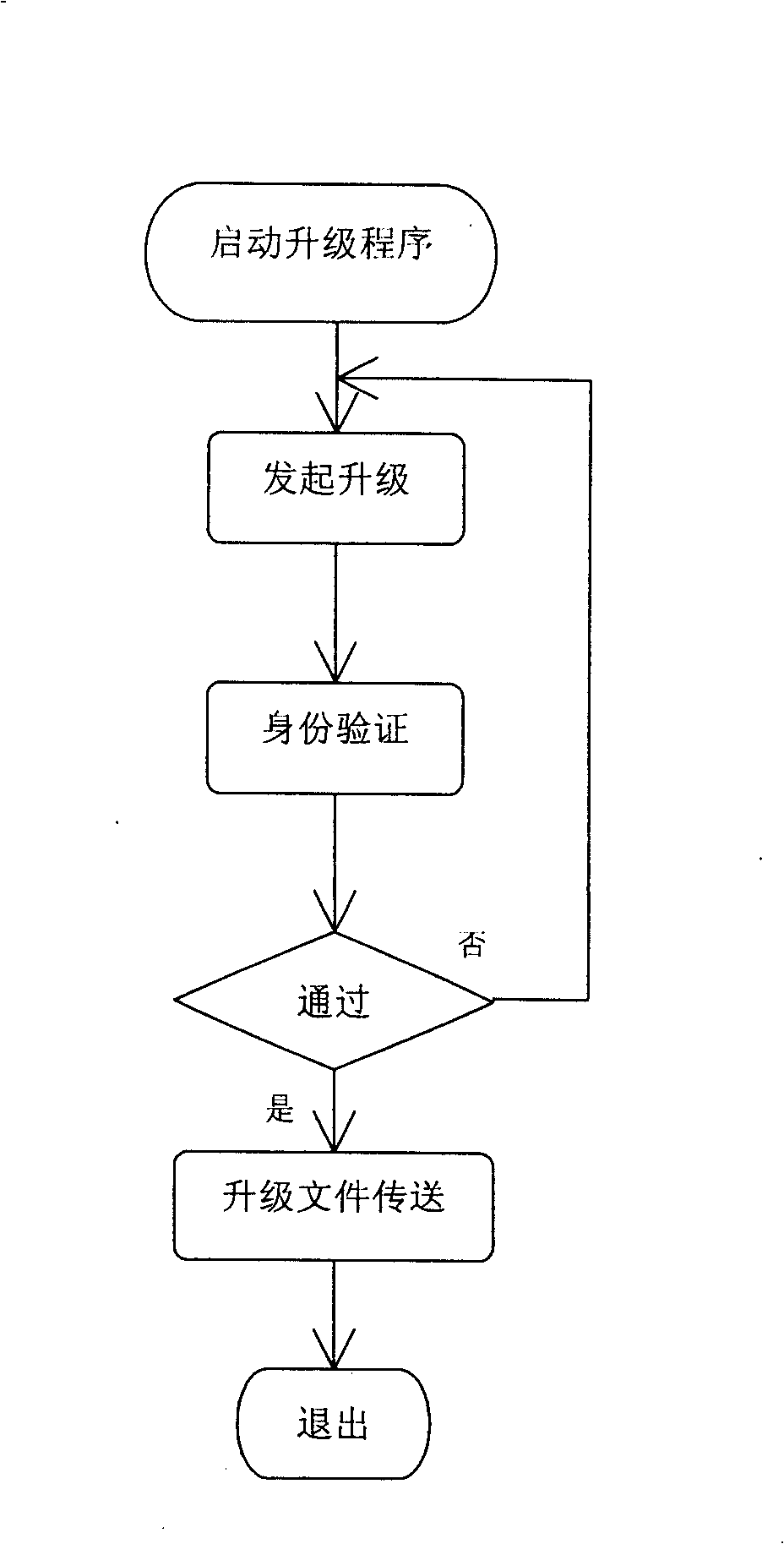
Method for upgrading built-in equipment
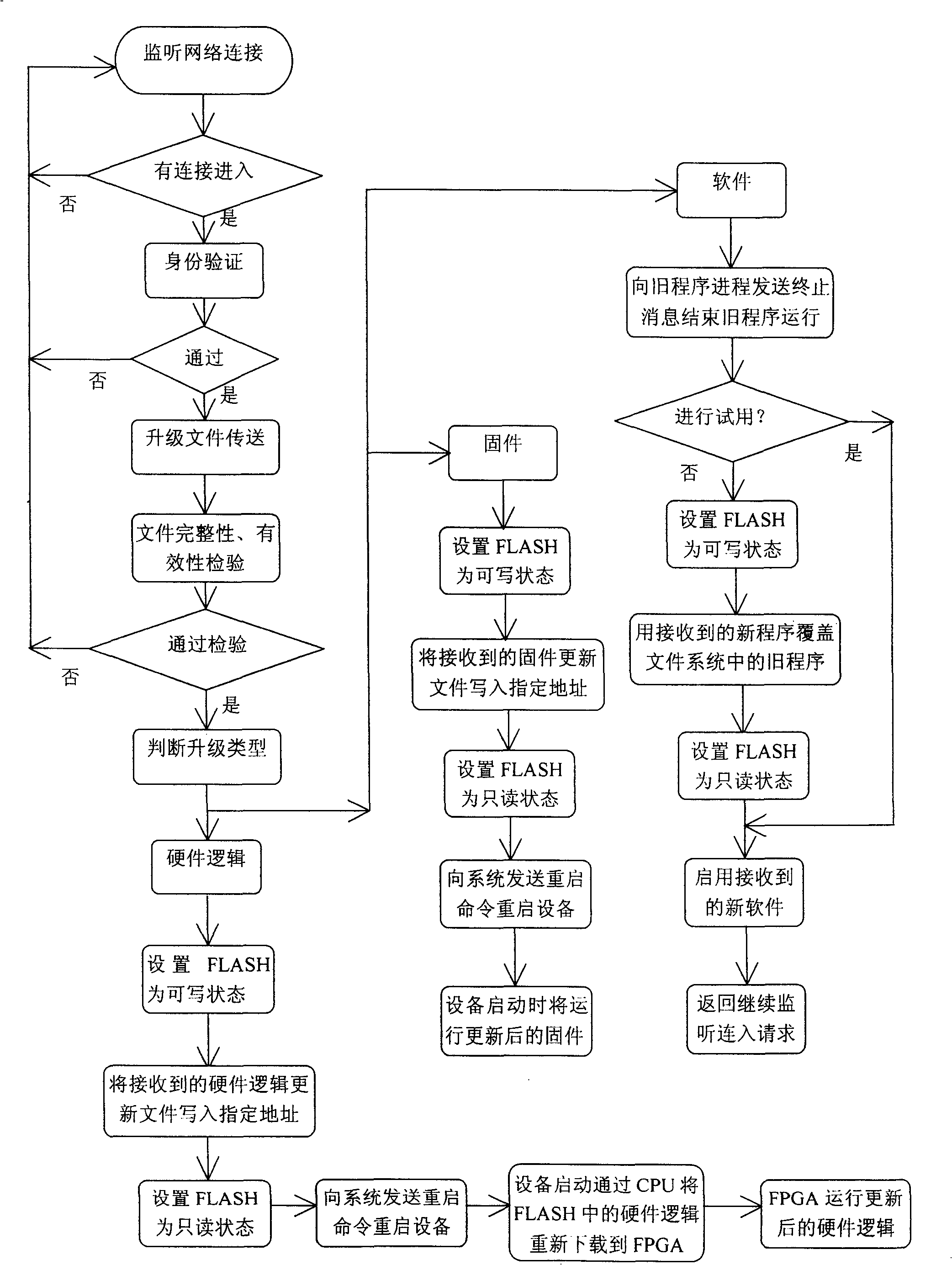
InactiveCN101330399AEasy to updateEliminate expensive specialized equipmentProgram loading/initiatingData switching networksSleep stateDEVS
The invention discloses an upgrading method for an embedded device. The method comprises the steps of running a back stage upgrading service program on the embedded device terminal, and judging whether a remote update is linked through monitoring a particular network interface; transmitting update files if an update is linked and the identity of a remoter regenerator is verified, wherein the back stage service is in sleep state in normal times; and updating hardware logic, firmware and software according to updating requirements after the files are transmitted and the files go through necessary detection (such as integrity, validness), wherein the files to be updated are written in a temporary files. The updating method enables a user or a developer to quickly update the hardware logic, the firmware and the software of the embedded device through the network, thereby eliminating expensive devices and complex operating processes.
Owner:上海风格信息技术股份有限公司
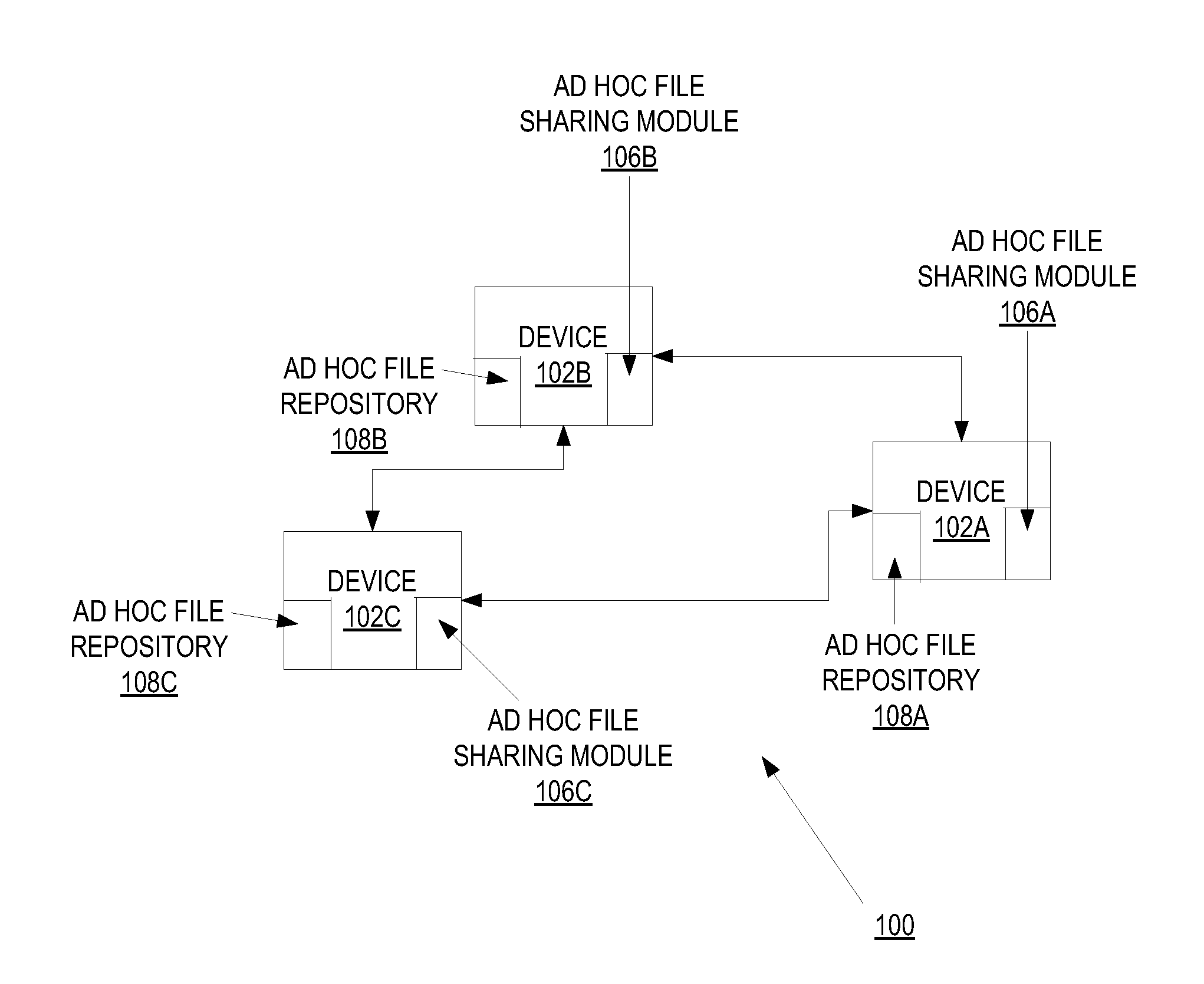
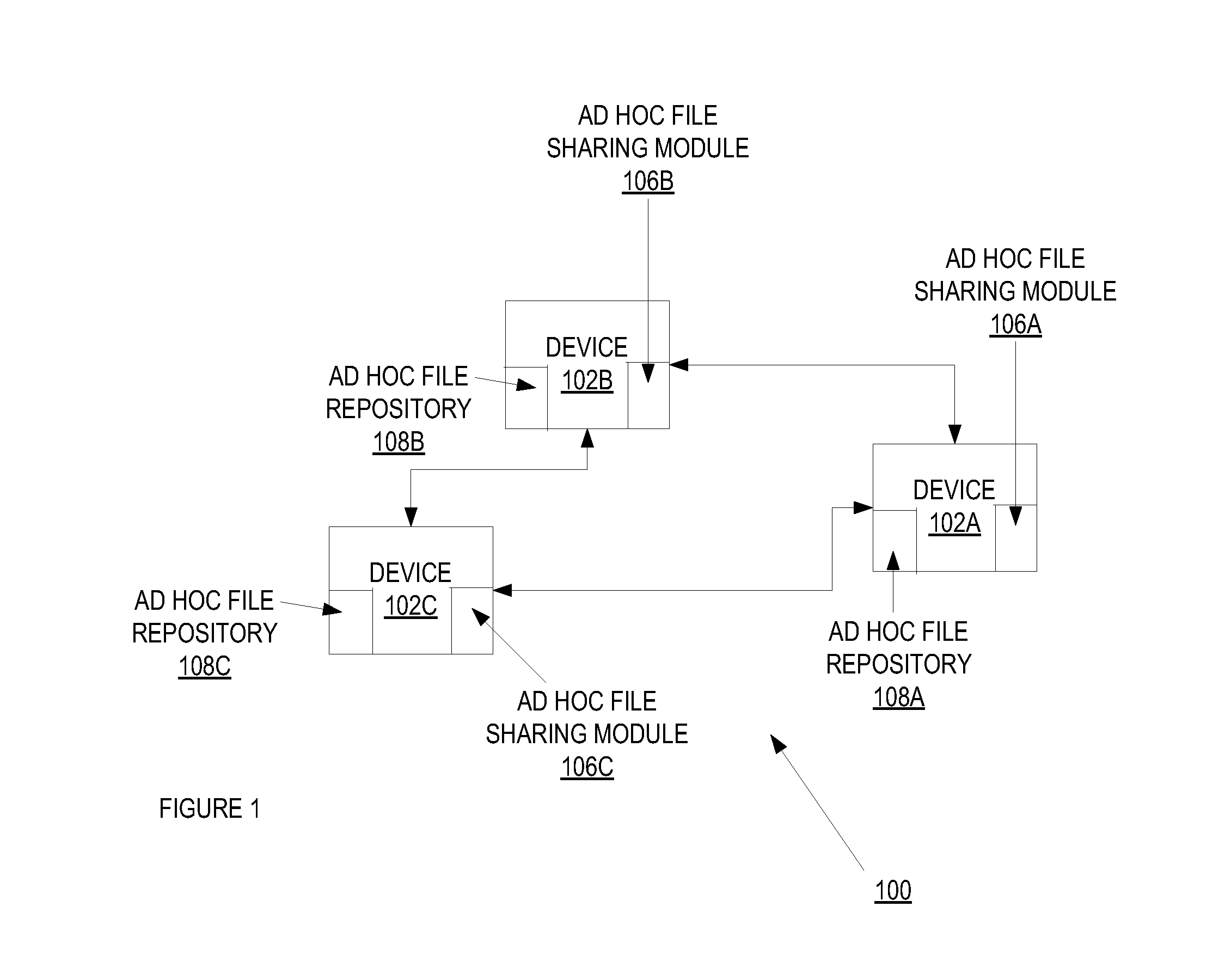
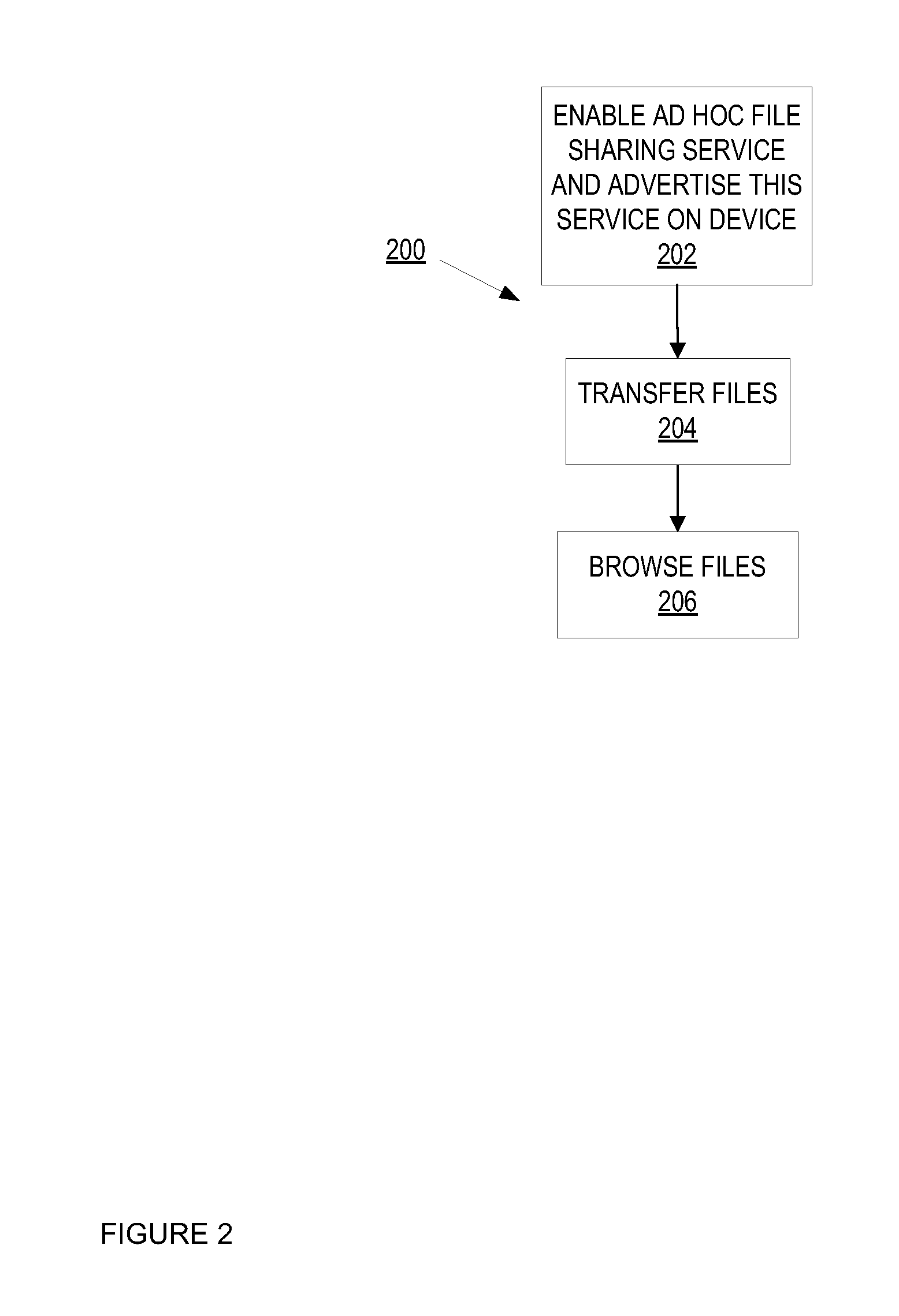
Ad hoc file sharing
A method and apparatus of a device that transfers files and performs file browsing using an ad hoc file sharing service is described. In an exemplary method, the device transmits an advertisement of the ad hoc file sharing service to each of one or more of other devices. The transmitted advertisements each include a user identity of the user associated with the first device. Furthermore, access to the ad hoc file sharing service is granted on a per-user basis. The device establishes a connection with each of the other devices and transfers files with each of the plurality of other devices.
Owner:APPLE INC
Method for caching local temporary files into embedded browser
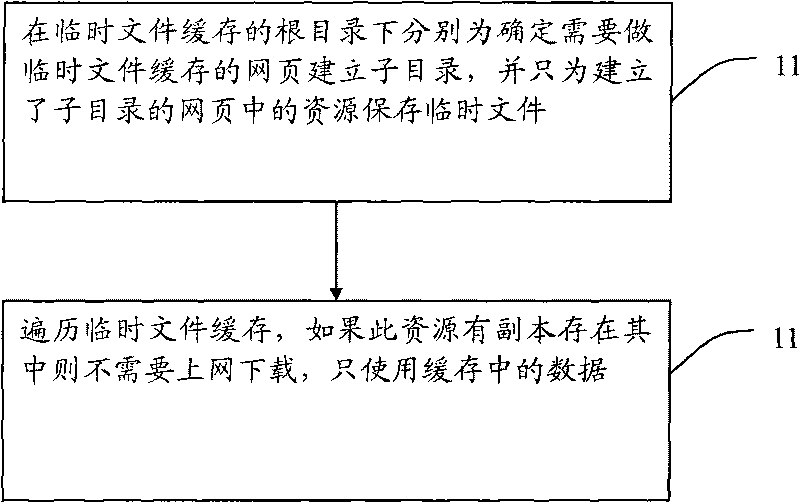
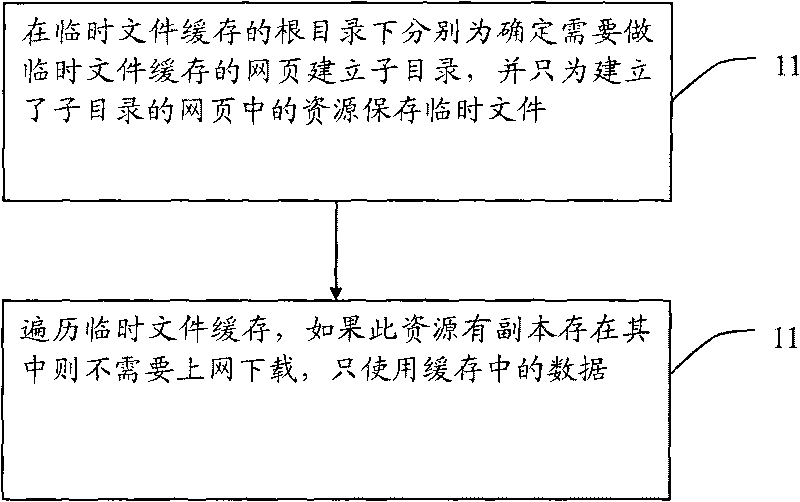
InactiveCN101710327APlay complementarityImprove the efficiency of visiting web pagesSpecial data processing applicationsWeb pageDatabase
The invention discloses a method for caching local temporary files into embedded browser, which comprises the steps: establishing a subdirectory for each webpage which needs to perform temporary file cache in a root directory of the temporary file cache, and saving temporary files only for resources in the webpages in which the subdirectory is established; and traversing the temporary file cache, and if transcripts exist in the resources, only using data in the cache without downloading other data on line. Through the technical scheme of the invention, the method can improve the efficiency of accessing the webpages by the embedded browser.
Owner:SHENZHEN SKYWORTH DIGITAL TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com