Method for encrypting files by adopting encryption sandbox
A file encryption and sandbox technology, applied in the direction of instruments, electronic digital data processing, platform integrity maintenance, etc., can solve the problems of transparent encryption, difficult to stabilize policy settings, complexity, etc., to achieve no risk of leakage, easy solution, simple policy configuration Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
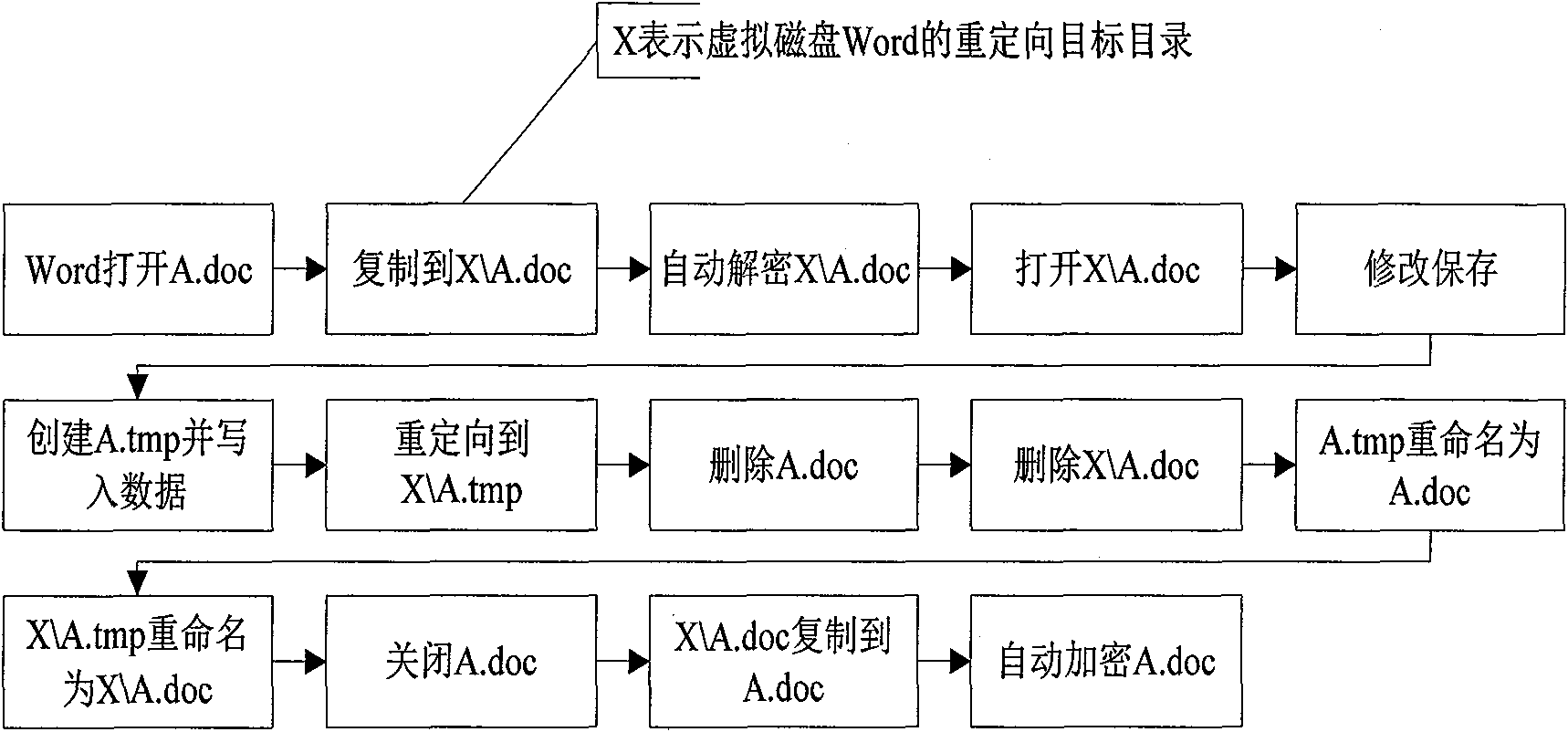
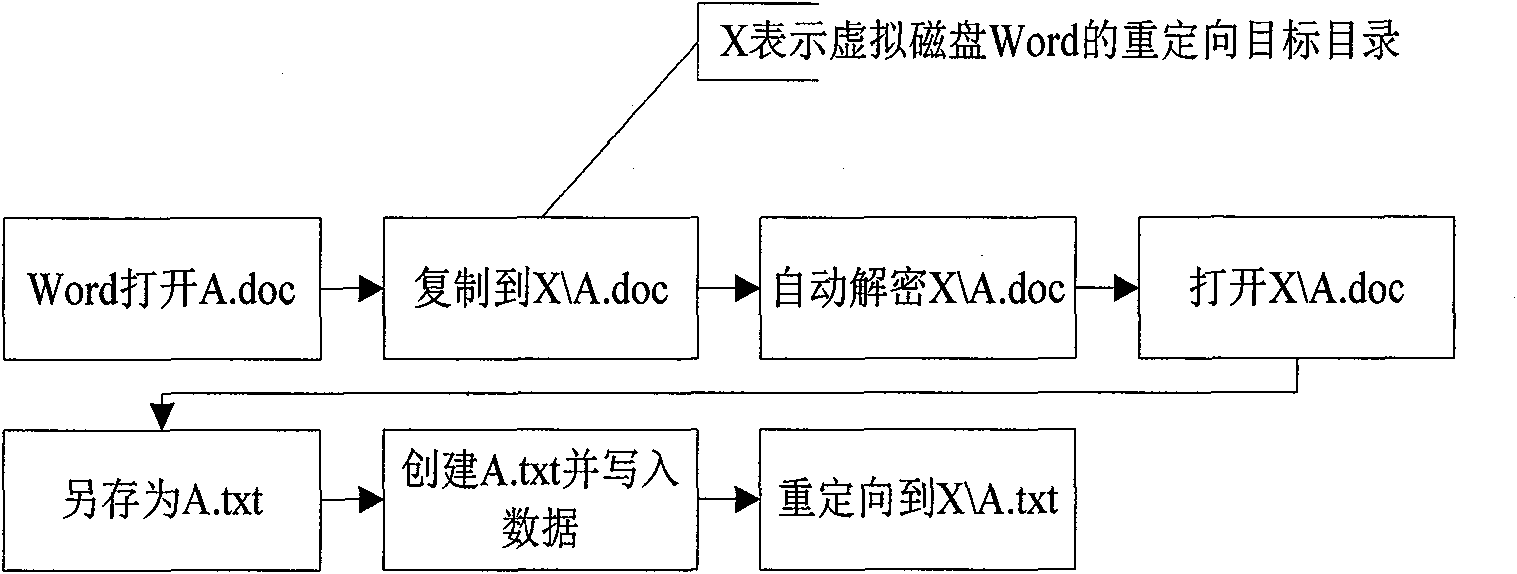
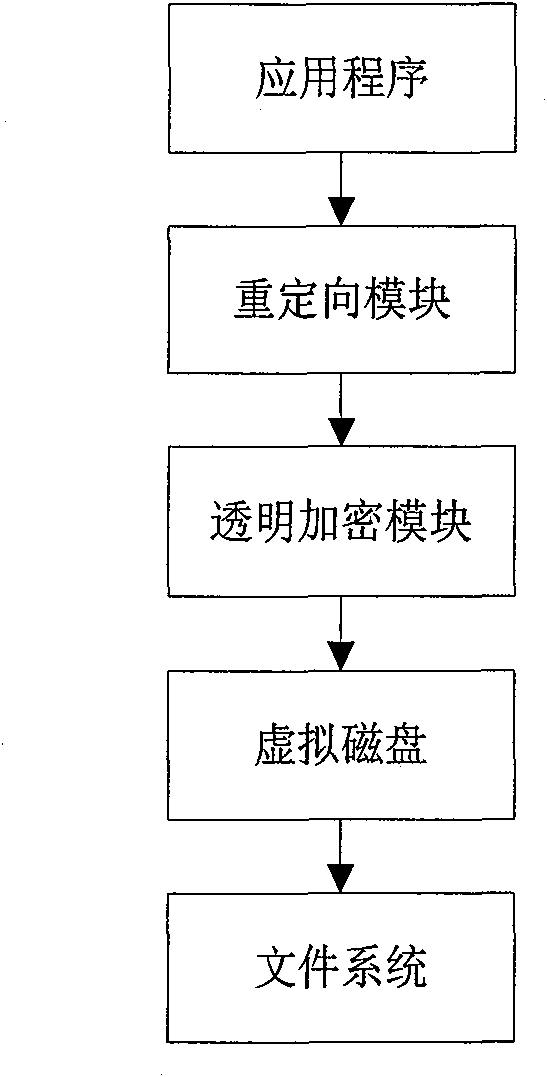
[0030] The virtual disk system described in the present invention, the redirection module and the transparent encryption module are all the underlying drivers of the system, and the relationship between them is as follows: image 3 As shown, the schematic diagram of the file encryption and decryption process, such as Figure 4 .
[0031] 1 virtual disk system
[0032] Virtual disks are used to store redirected file data, which can be implemented using file virtual disks and memory virtual disks. For file virtual disks, the operation process is as follows Figure 5 shown. First, the correct key must be set, otherwise the loading is refused; after the device object is created, in order to prevent application programs from accessing, no further symbolic links (that is, drive letters) are created. After the device is created, first clear the original data, and then mainly process the reading and writing of the virtual disk: encrypt according to the key when writing, and decryp...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com