Patents
Literature
117 results about "Network traffic management" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
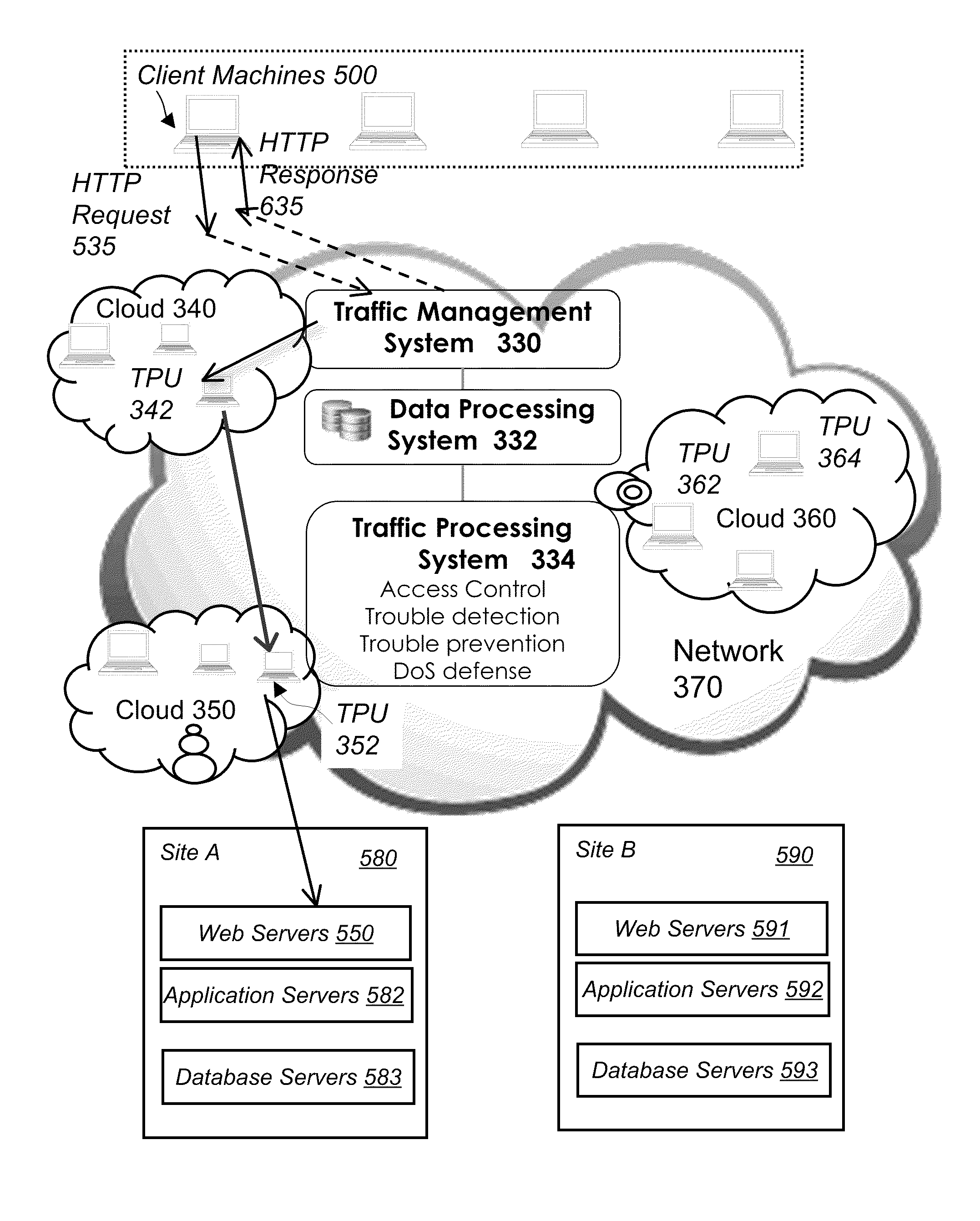
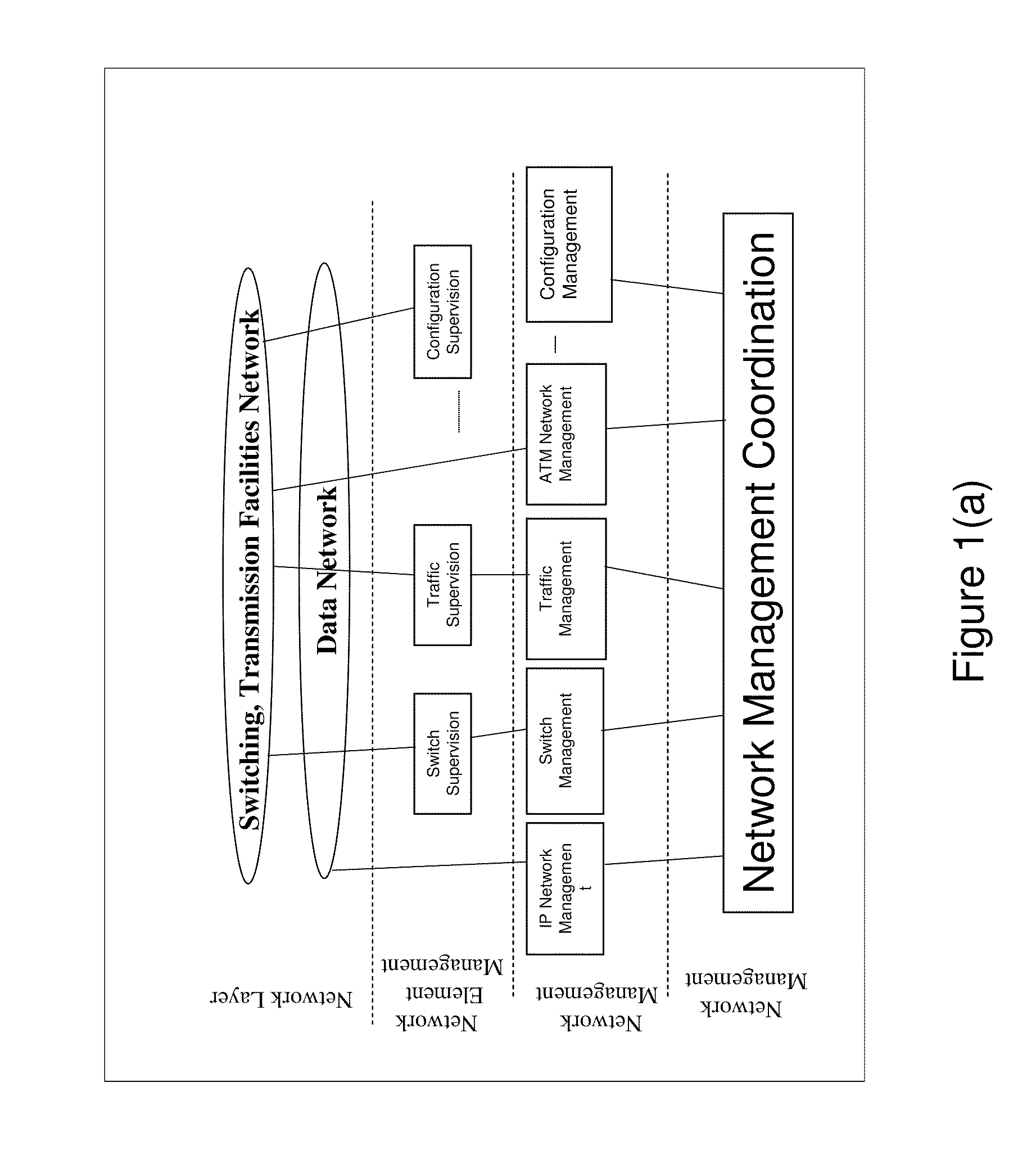
Network Traffic Management. Network traffic management, also known as application traffic management, refers to a methodology that F5 pioneered for intercepting, inspecting, and translating network traffic, directing it to the optimum resource based on specific business policies. This allows network administrators to apply availability, scalability,...
System and method for network traffic management and load balancing
InactiveUS20100223364A1Improve application performanceImprove availabilityMultiple digital computer combinationsLocation information based serviceTraffic capacityFailover
A method for providing load balancing and failover among a set of computing nodes running a network accessible computer service includes providing a computer service that is hosted at one or more servers comprised in a set of computing nodes and is accessible to clients via a first network. Providing a second network including a plurality of traffic processing nodes and load balancing means. The load balancing means is configured to provide load balancing among the set of computing nodes running the computer service. Providing means for redirecting network traffic comprising client requests to access the computer service from the first network to the second network. Providing means for selecting a traffic processing node of the second network for receiving the redirected network traffic comprising the client requests to access the computer service and redirecting the network traffic to the traffic processing node via the means for redirecting network traffic. For every client request for access to the computer service, determining an optimal computing node among the set of computing nodes running the computer service by the traffic processing node via the load balancing means, and then routing the client request to the optimal computing node by the traffic processing node via the second network.
Owner:YOTTAA
Method, apparatus and sofware for network traffic management
A network traffic evaluation device is provided that may be used to warn of or prevent trafficabnormalities such as denial of service attacks. The device includes a data interface to receive one or both of network traffic and data indicative of characteristics f network traffic. The network traffic and / or data received by the data interface is processed for predeterminedcharacteristics that indicate that the network traffic contains a subset of attack traffic. Upon detection of the predetermined characteristics information defining a superset is provided. The superset is a portion of the network traffic that contains the subset and defines network traffic that may be redirected and / or blocked by a network device.
Owner:ESPHION
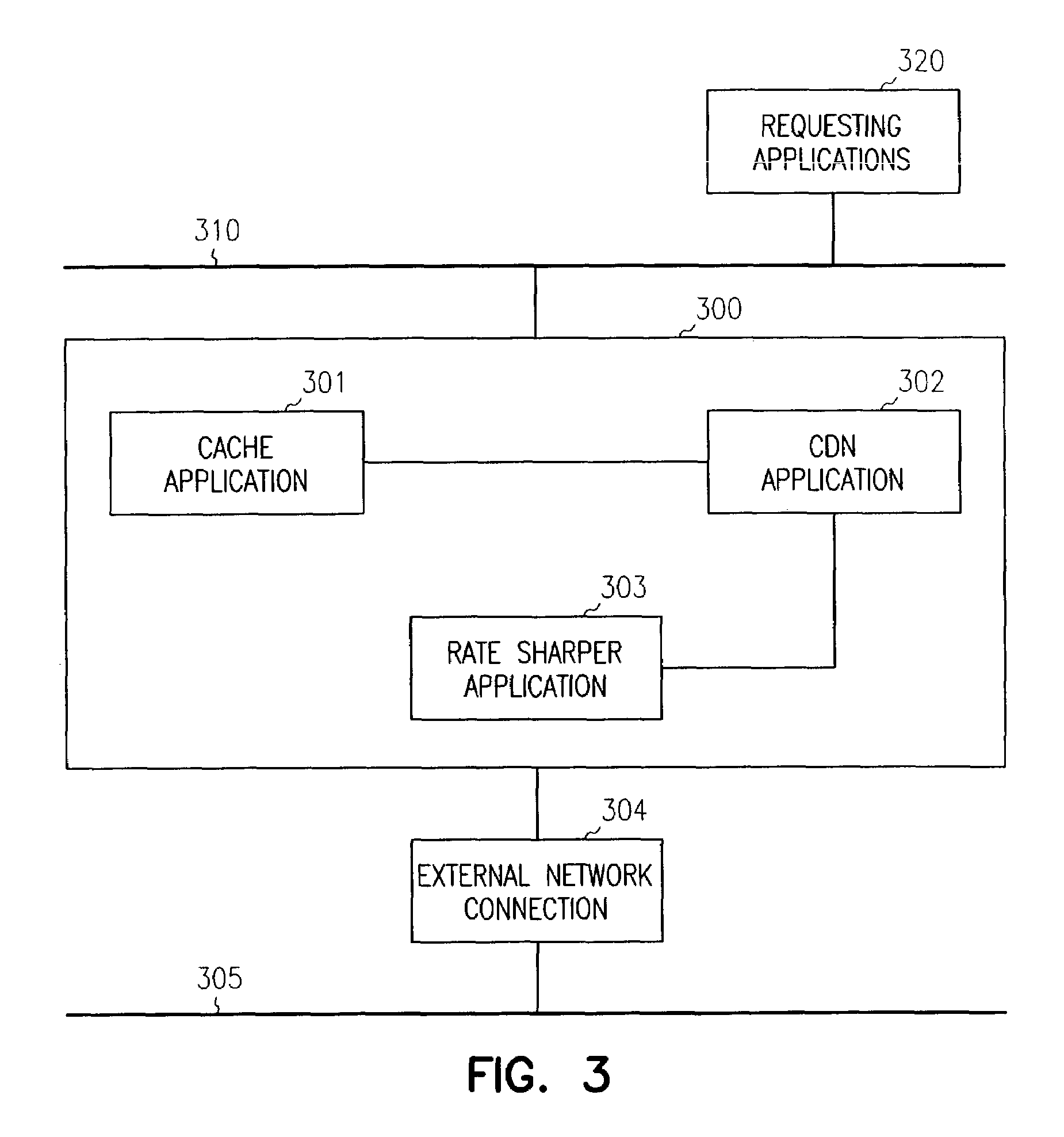
Methods and systems for managing network traffic
InactiveUS7680897B1Improve utilizationImprove in instanceMultiple digital computer combinationsData switching networksContent distributionTraffic capacity
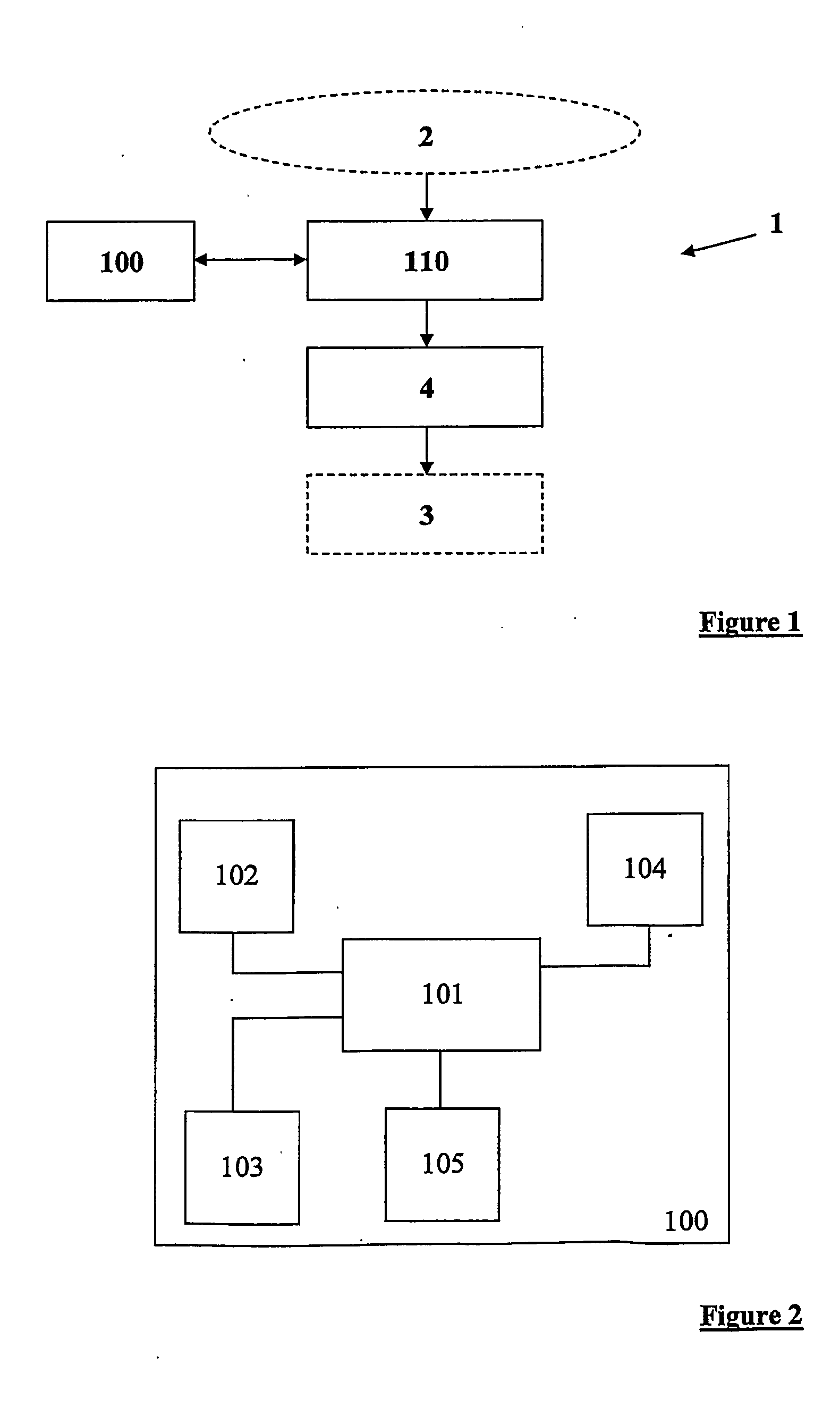
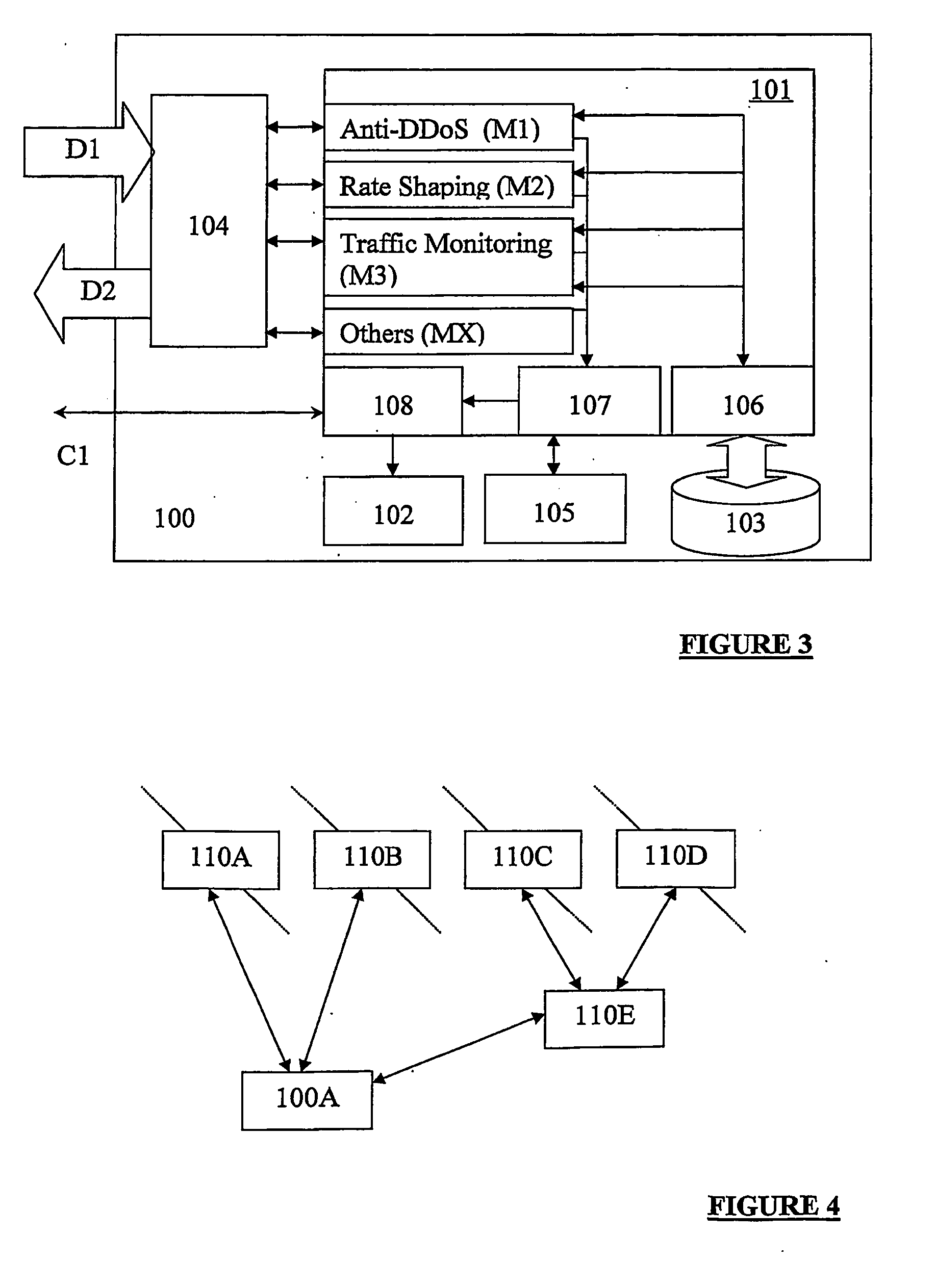
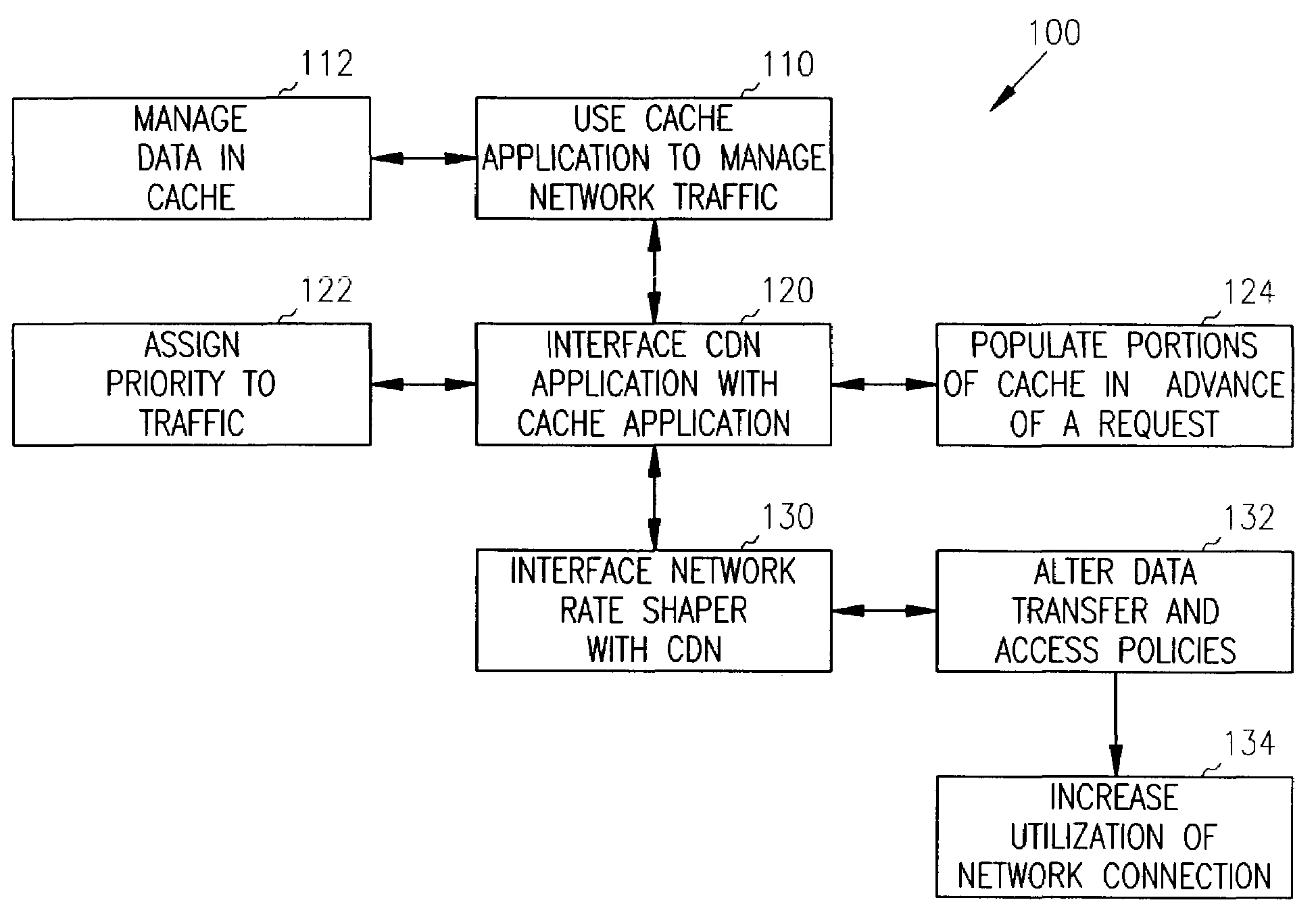
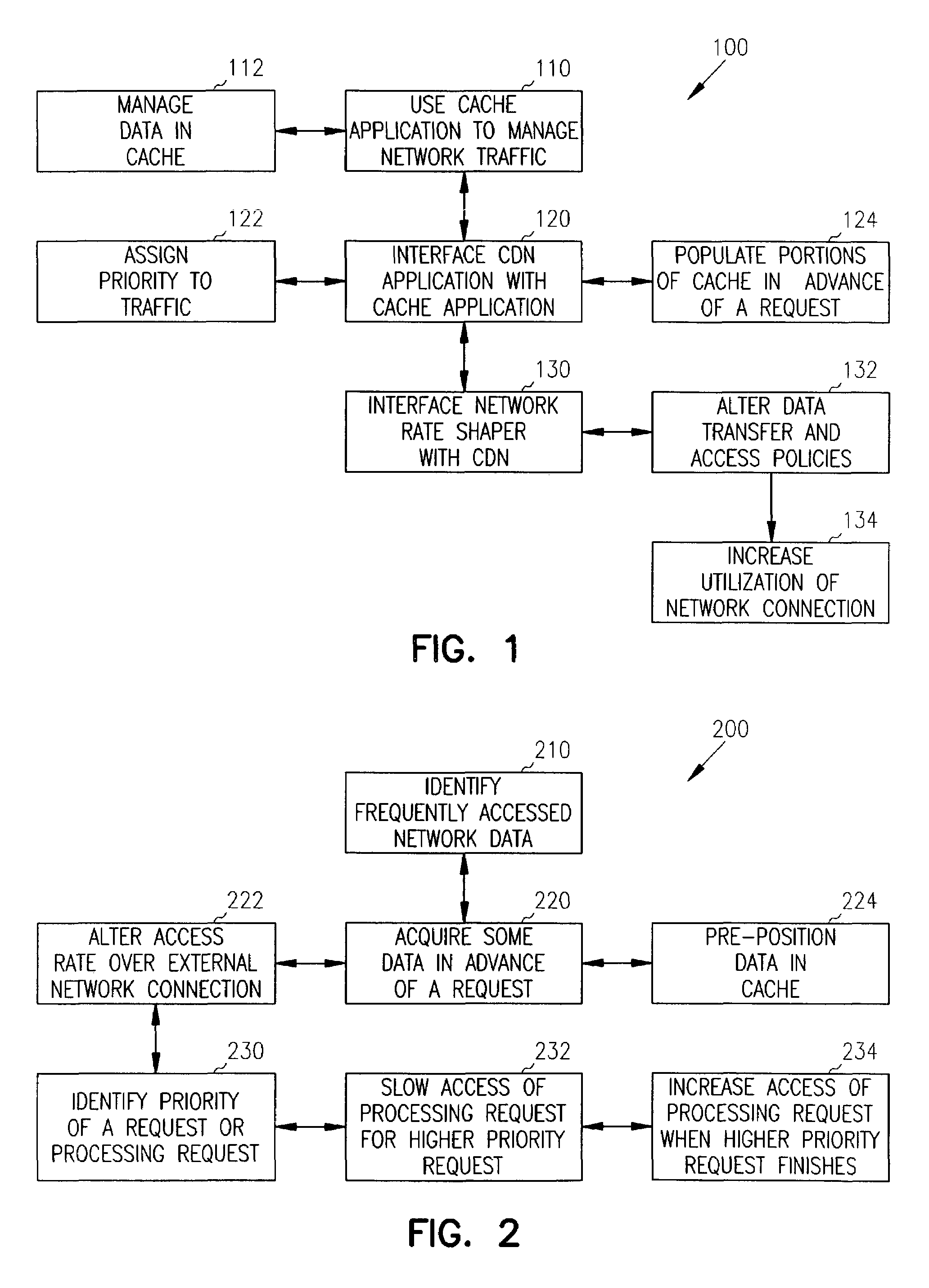
Methods and systems for network traffic management are provided. A content distribution network application manages data in a cache. A network rate shaper application controls and manages requests for access to an external network connection. The content distribution network application determines priorities associated with requests and communicates these priorities to the rate shaper application. The rate shaper application adjusts access levels or data transfer rates for the requests based on the received priorities.
Owner:RPX CORP
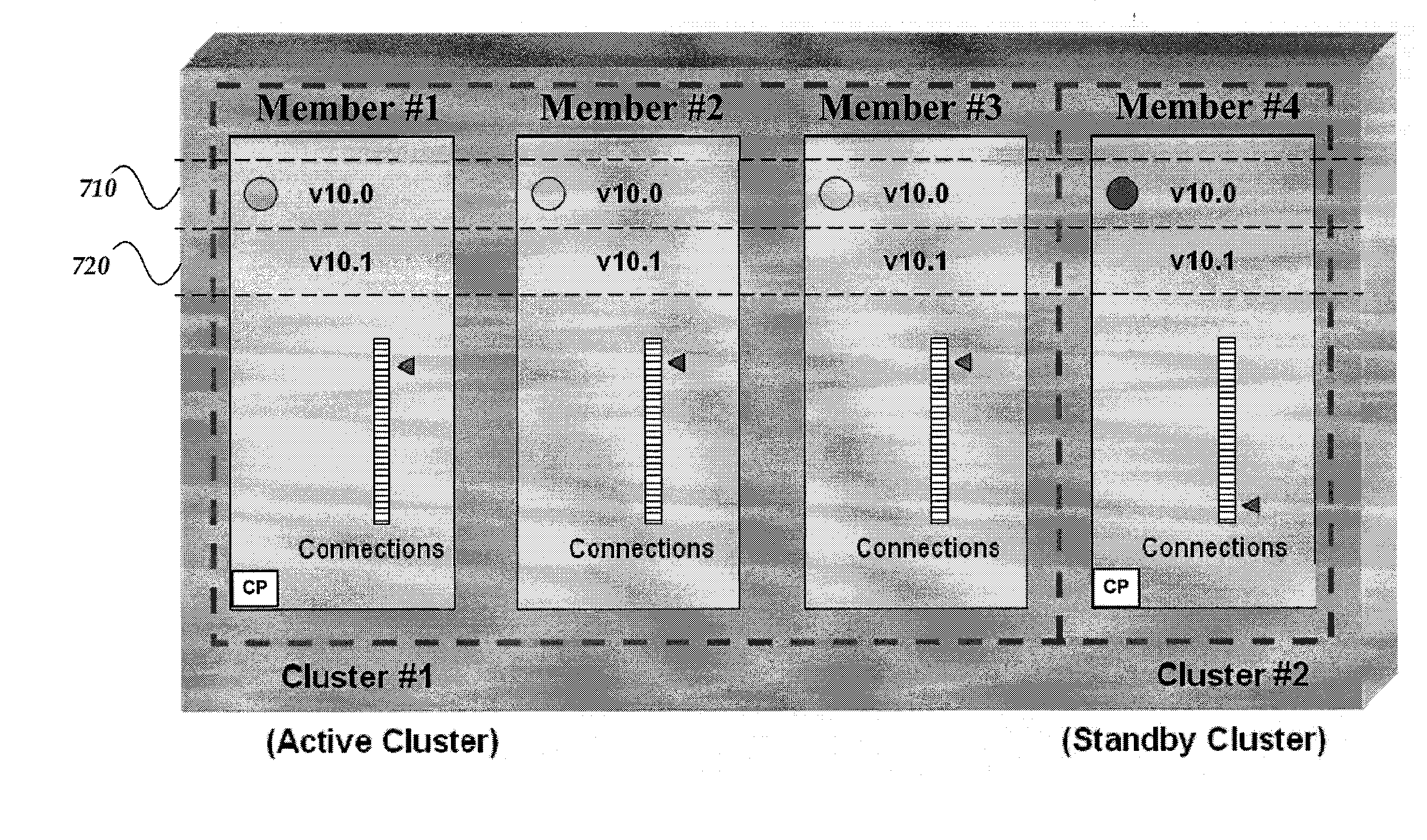
Upgrading network traffic management devices while maintaining availability
ActiveUS20100042869A1Software engineeringMultiple digital computer combinationsTraffic capacityVirtual cluster
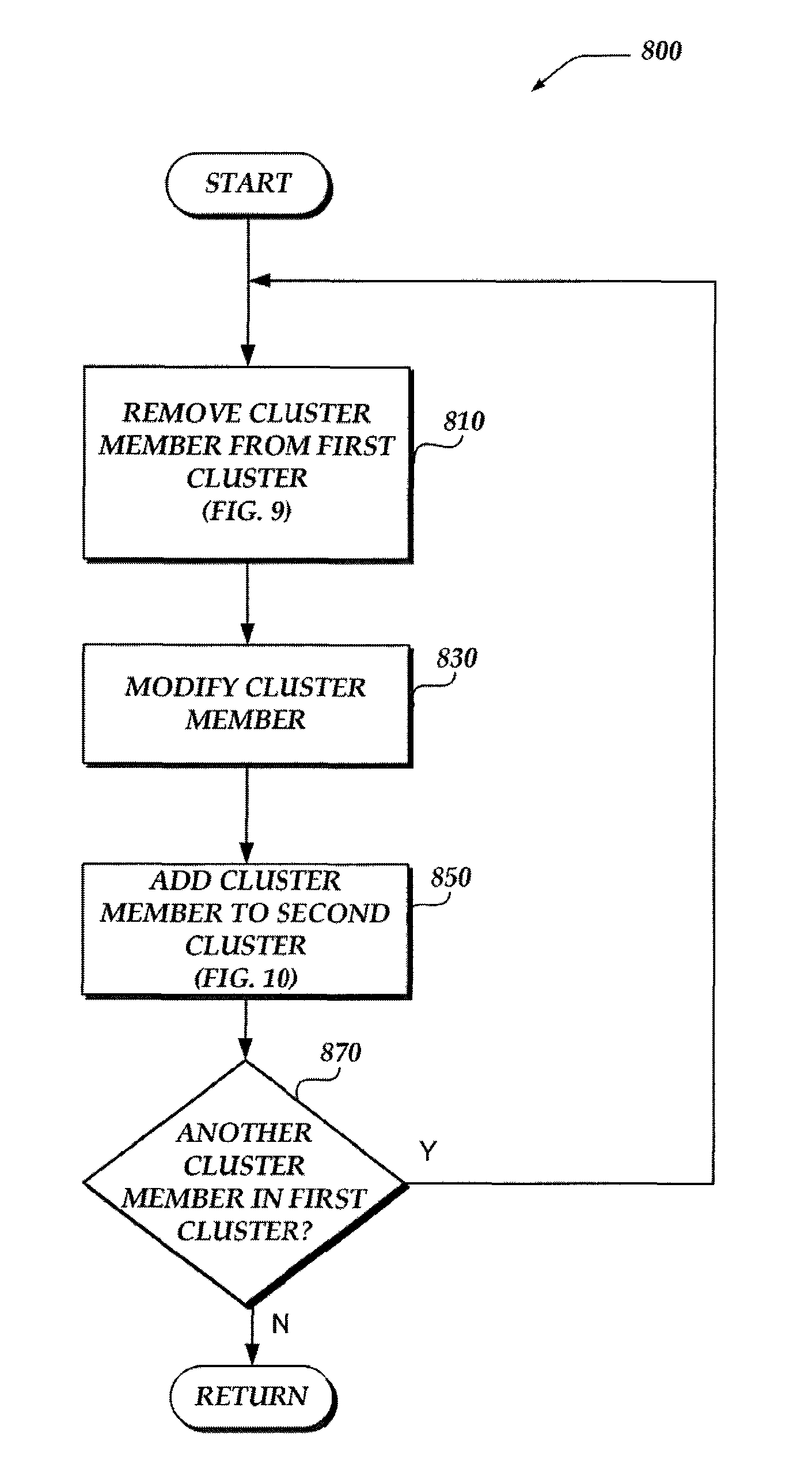
A method, system, machine-readable storage medium, and apparatus are directed towards upgrading a cluster by bifurcating the cluster into two virtual clusters, an “old” virtual cluster (old active cluster) and a “new” virtual cluster (new standby cluster), and iteratively upgrading members of the old cluster while moving them into the new cluster. While members are added to the new cluster, existing connections and new connections are seamlessly processed by the old cluster. Optionally, state mirroring occurs between the old cluster and the new cluster once the number of members of the old and new clusters are approximately equal. Once a threshold number of members have been transferred to the new cluster, control and processing may be taken over by the new cluster. Transfer of control from the old cluster to the new cluster may be performed by failing over connectivity from the old cluster to the new cluster.
Owner:F5 NETWORKS INC
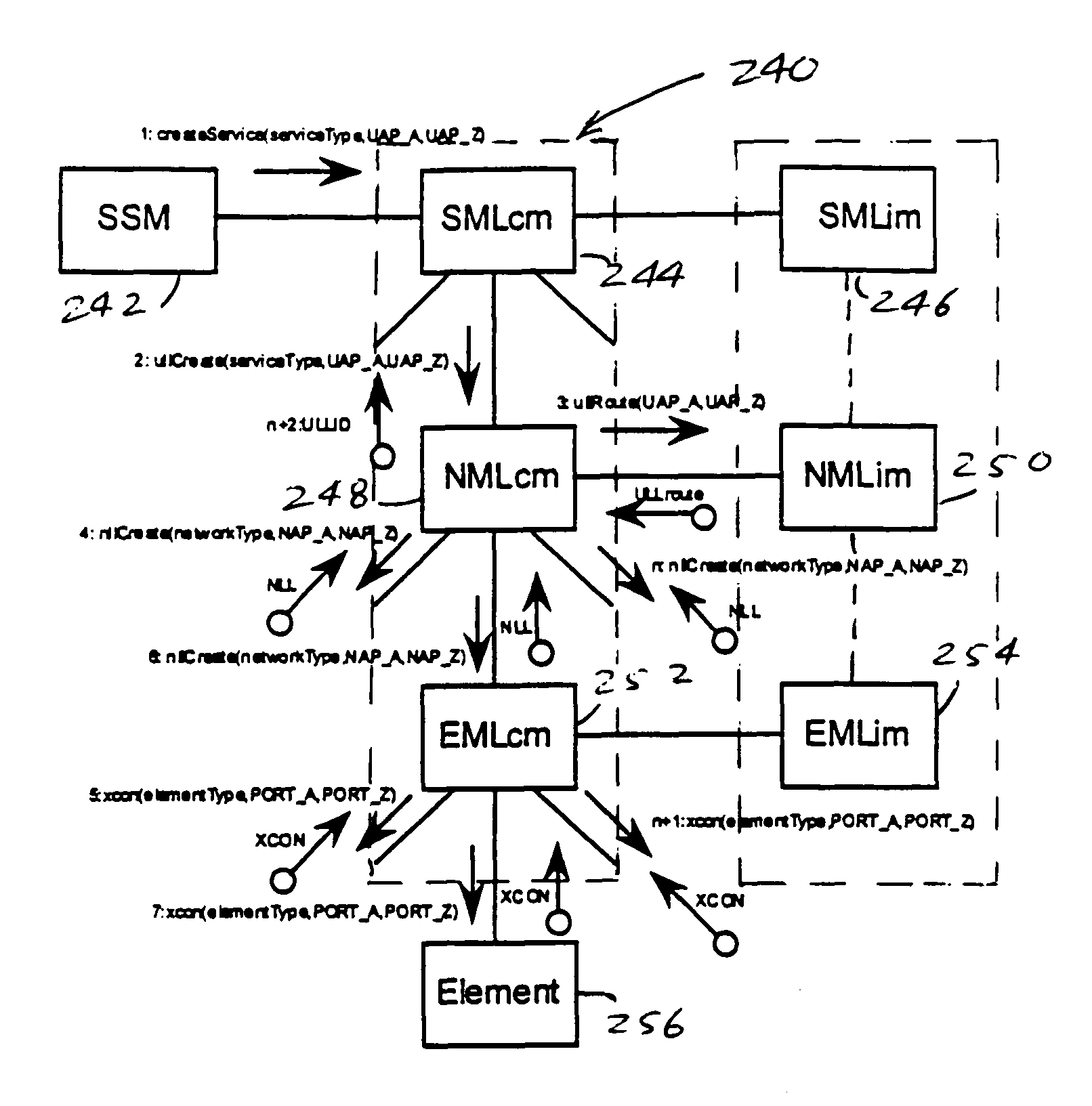
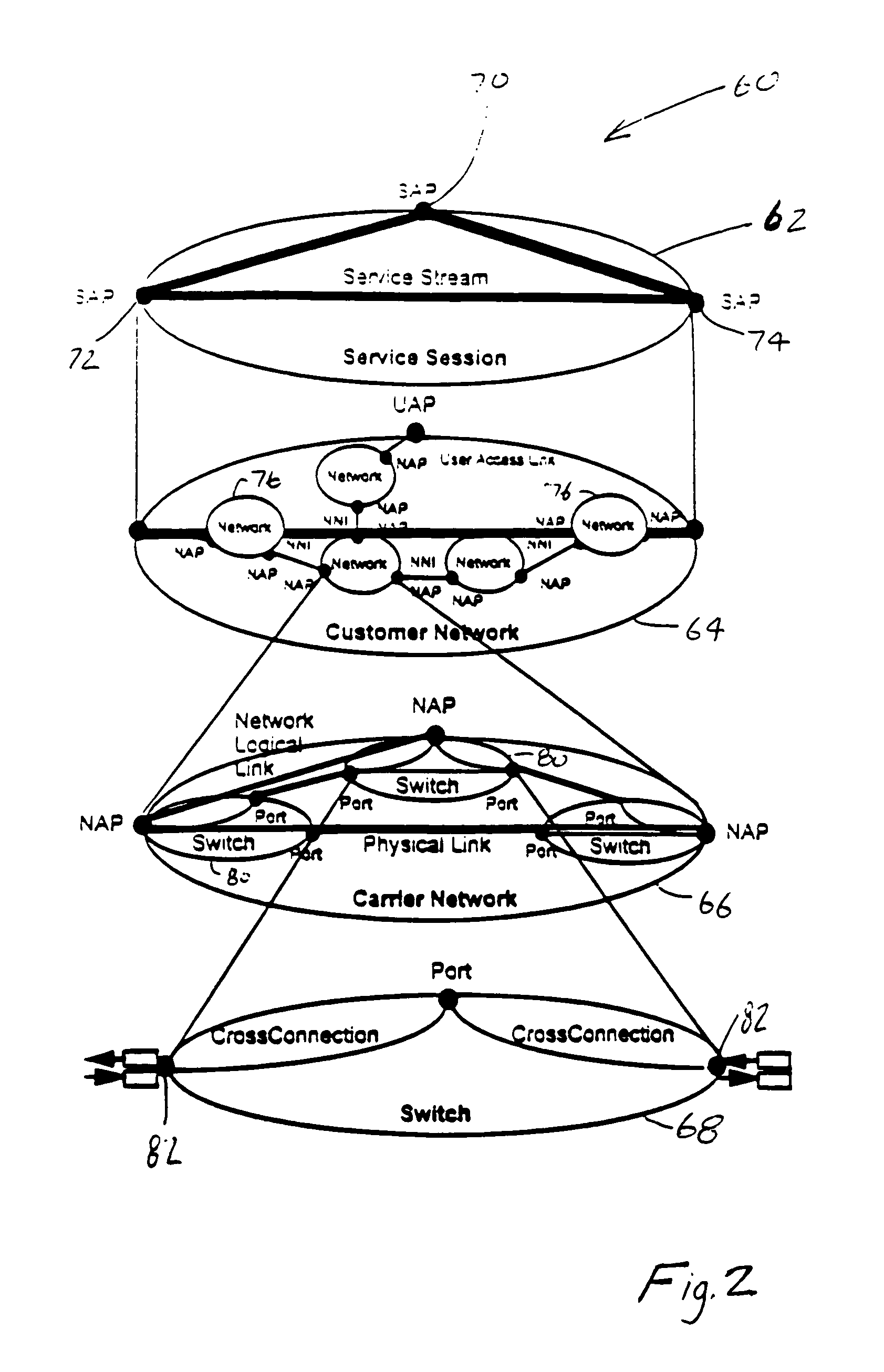
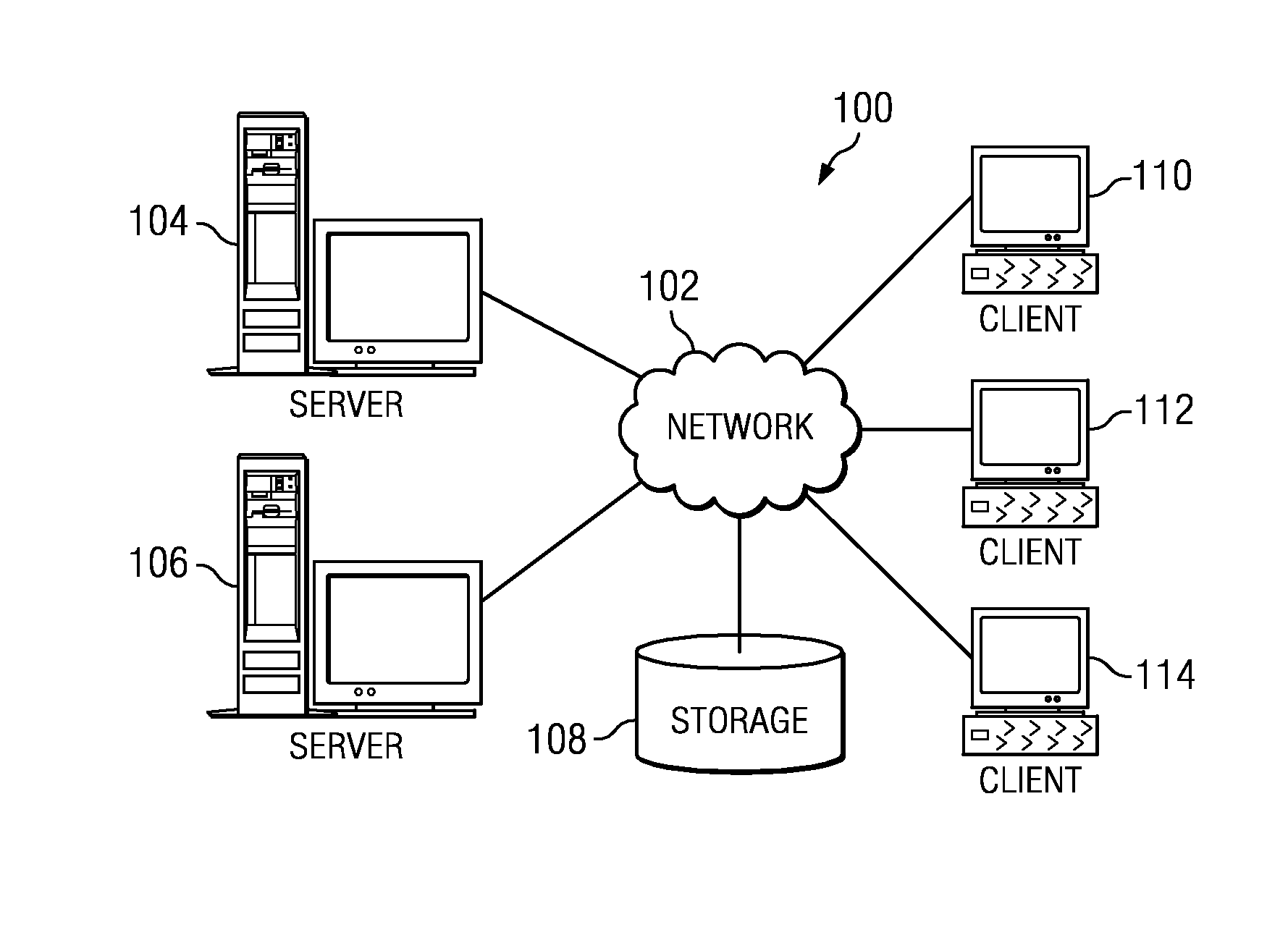
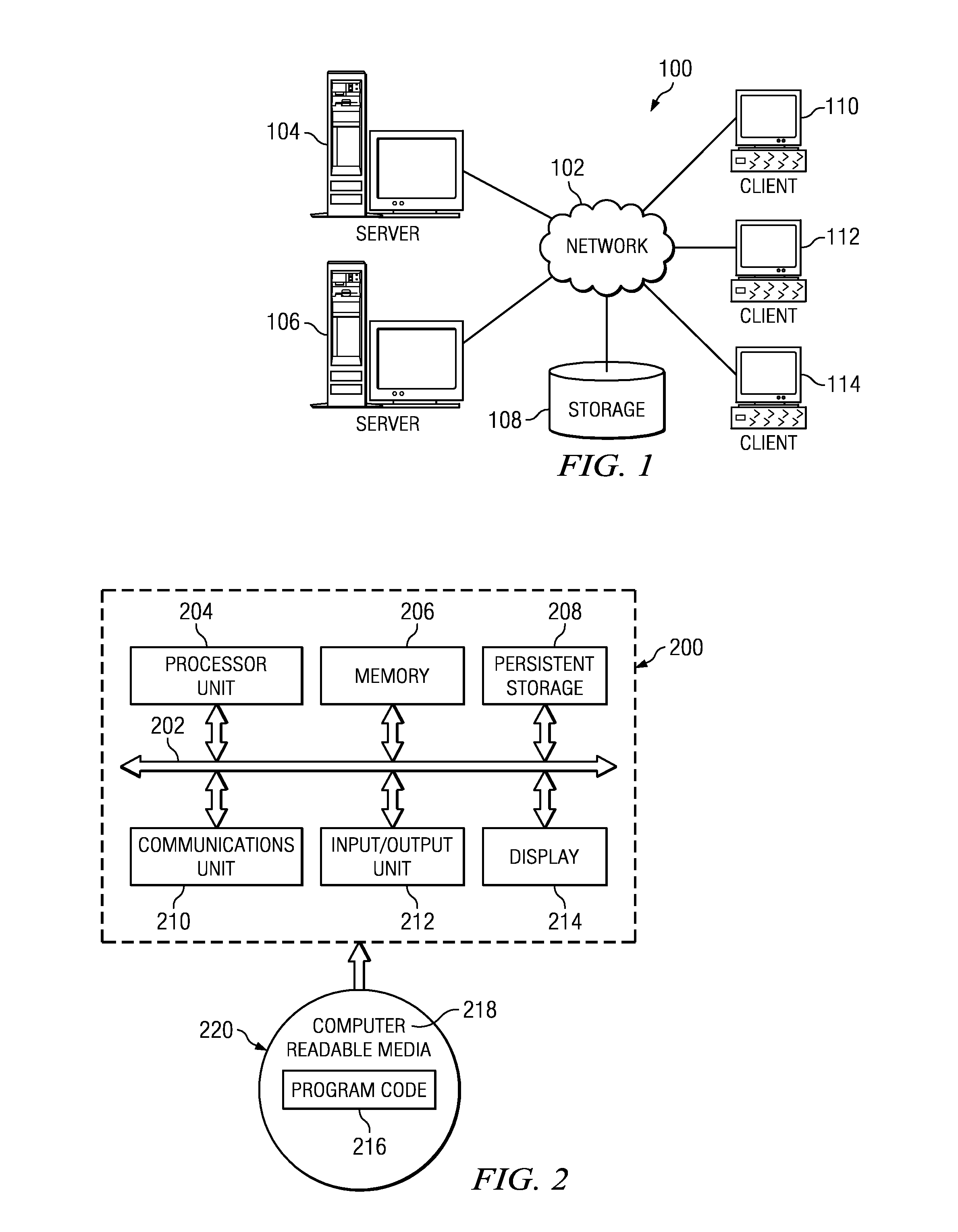
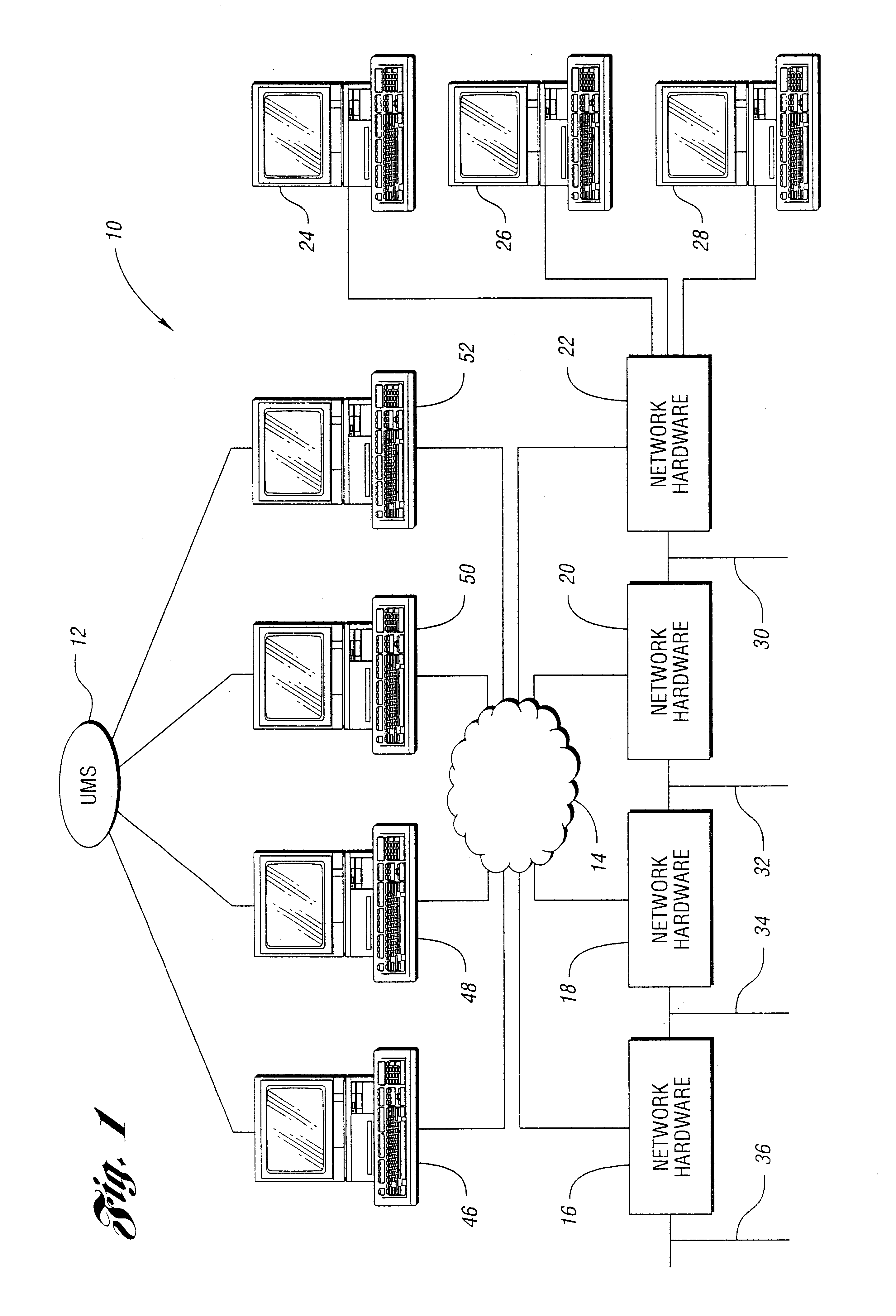
Network management system and graphical user interface
InactiveUS7966388B1Change is minimalError preventionTransmission systemsNetwork connectionNetworking hardware
A network management system and graphical user interface for configuring a network connection between first and second service access points utilizes a configuration manager and information manager to provide a generic set of models so that different manufacturer's nodal processors and other network hardware can be inserted into the network with minimal changes to the software which controls the device. The system comprises an information manager including routing information for the network. The configuration manager operates to establish a connection across each subnet on the route by sending requests to element managers to program the subnet elements.
Owner:QWEST
Apparatus and methods for real-time multimedia network traffic management & control in wireless networks
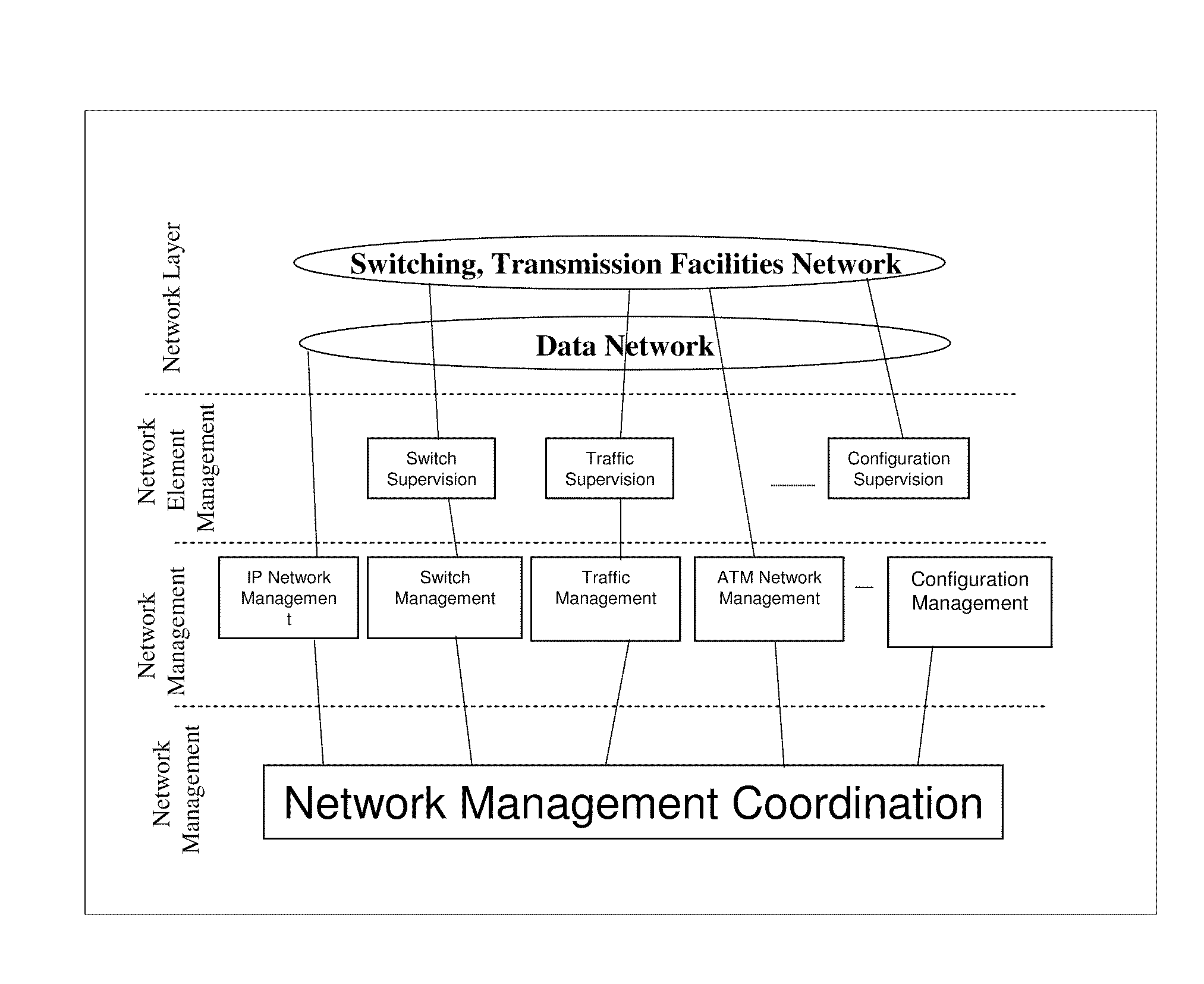
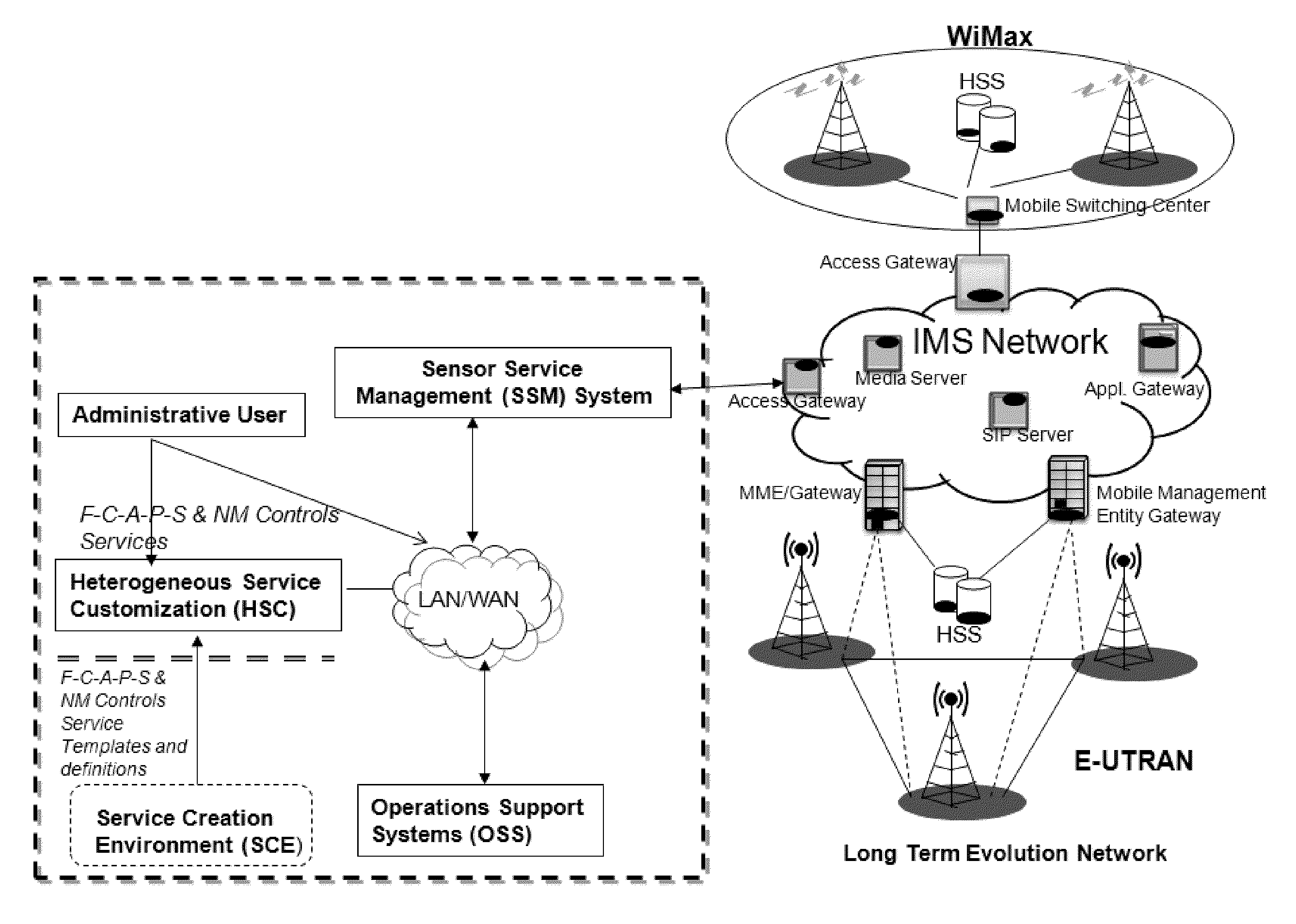
InactiveUS20100318652A1Facilitate real-time network managementEasy to manufactureMultiple digital computer combinationsTransmissionReal-time webNetwork management
The invention is directed to network management systems and methods that provide substantially real-time network management and control capabilities of multimedia streaming traffic in telecommunications networks. The invention provides pre-emptive and autonomous network management and control capabilities, and may include shared intelligence of embedded systems—Heterogeneous Sensor Entities (HSE) and the Sensor Service Management (SSM) system. HSEs are distributed real-time embedded systems provisioned in various network elements. HSEs performs fault, configuration, accounting, performance and security network management functions in real-time; and real-time network management control activations and removals. SSM facilitates automated decision making, rapid deployment of HSEs and real-time provisioning of network management and control services. The service communication framework amongst various HSEs and the SSM is provided by the Heterogeneous Service Creation system. The proposed network management procedure provides real-time network management and control capabilities of multimedia traffic in wireless networks and clusters of independent networks respectively.
Owner:KENT STATE UNIV
System and method for network traffic management
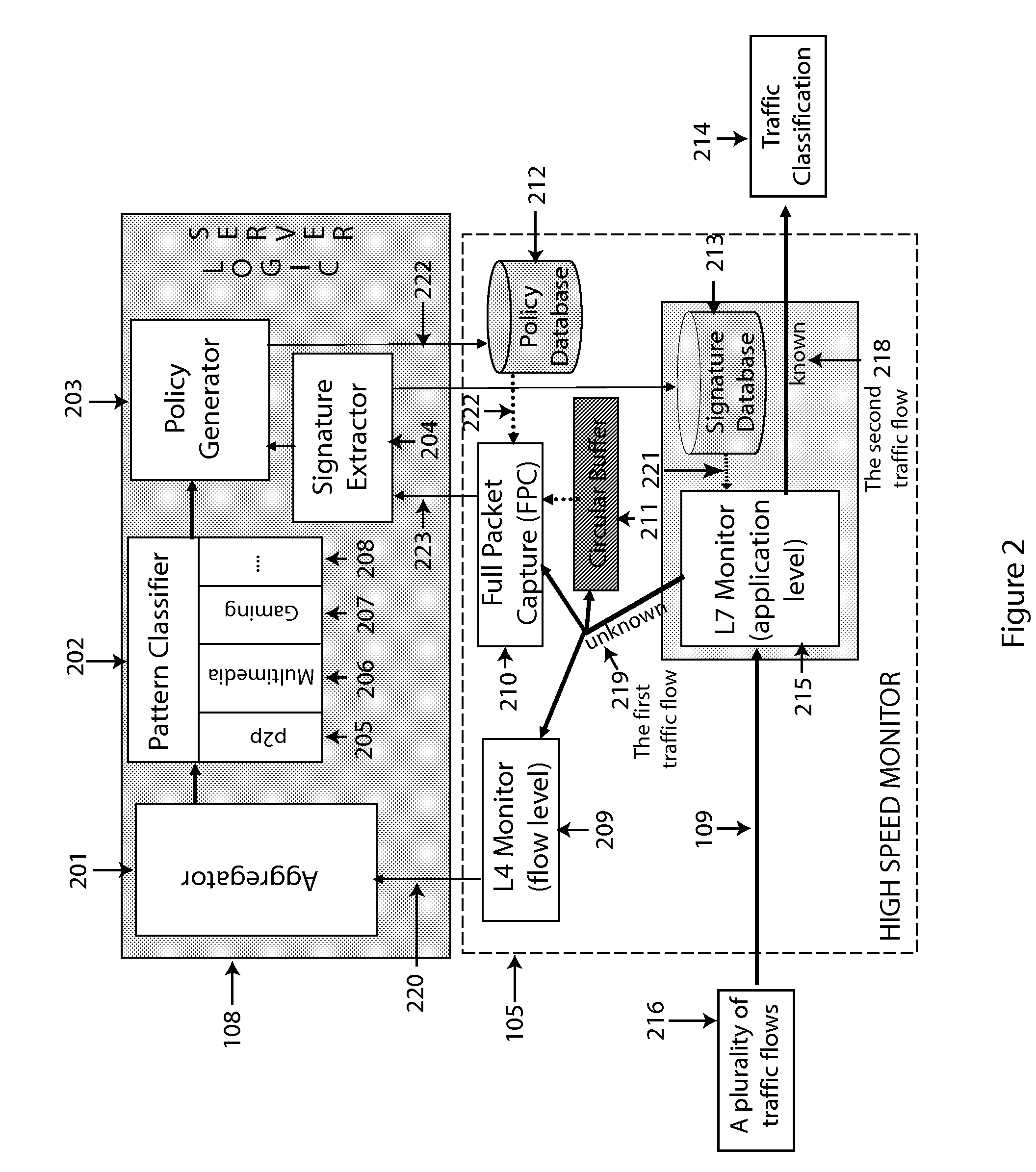
ActiveUS7644150B1Digital computer detailsBiological neural network modelsTraffic flowNetwork traffic management
The present invention relates to a method of managing a network. The method steps includes extracting a signature from a first traffic flow of a plurality of traffic flows on the network based on layer-3 / layer-4 information of the first traffic flow, storing the signature and an identification of a layer-7 application associated with the signature in a signature repository, identifying a second traffic flow of the plurality of traffic flows being associated with the layer-7 application by correlating the second traffic flow to the signature, and managing the network based on layer-7 application identification of the plurality of traffic flows.
Owner:THE BOEING CO
Apparatus and methods for real-time multimedia network traffic management and control in wireless networks
InactiveUS8868725B2Multiple digital computer combinationsData switching networksWireless mesh networkNetwork management
Owner:KENT STATE UNIV
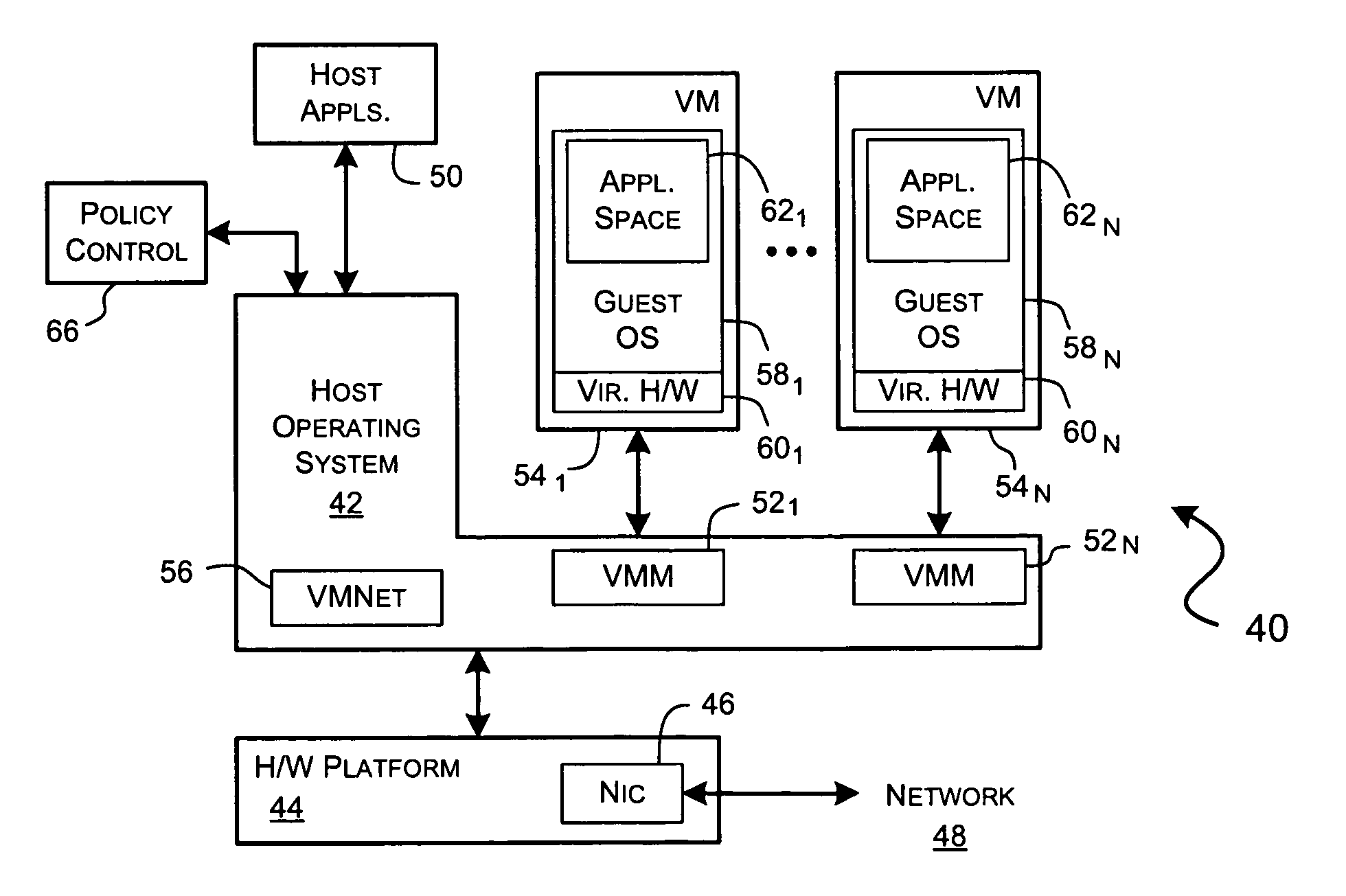
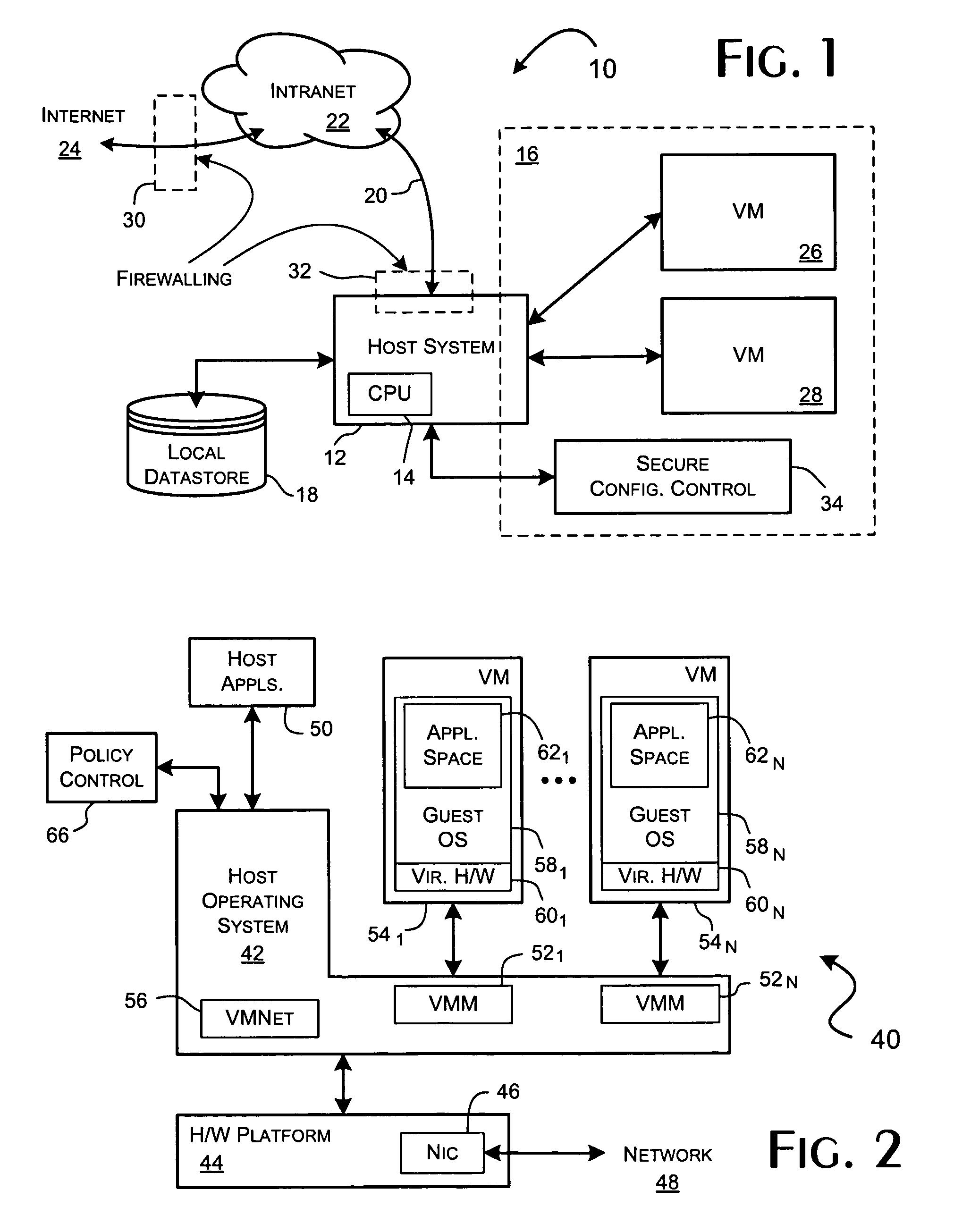
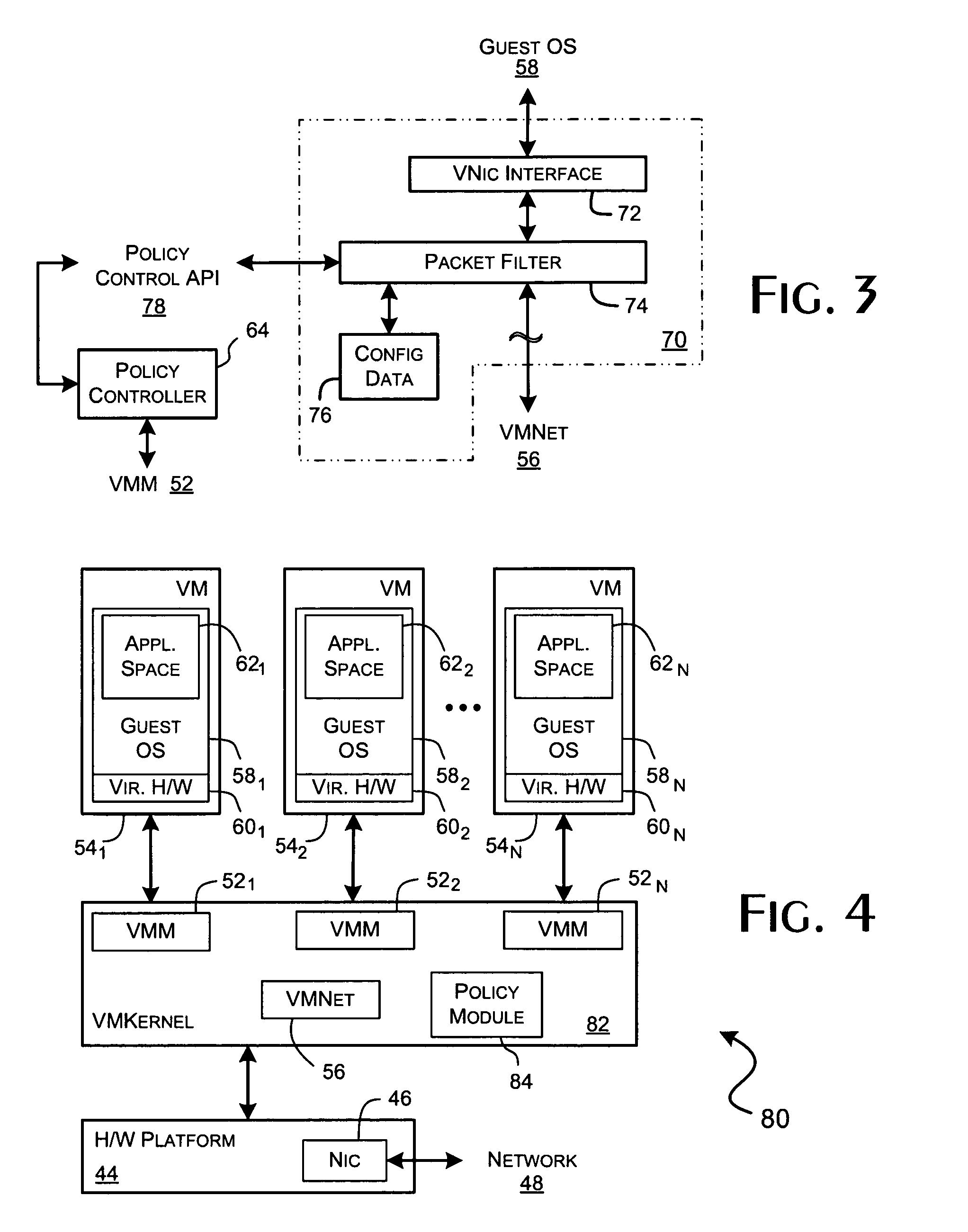
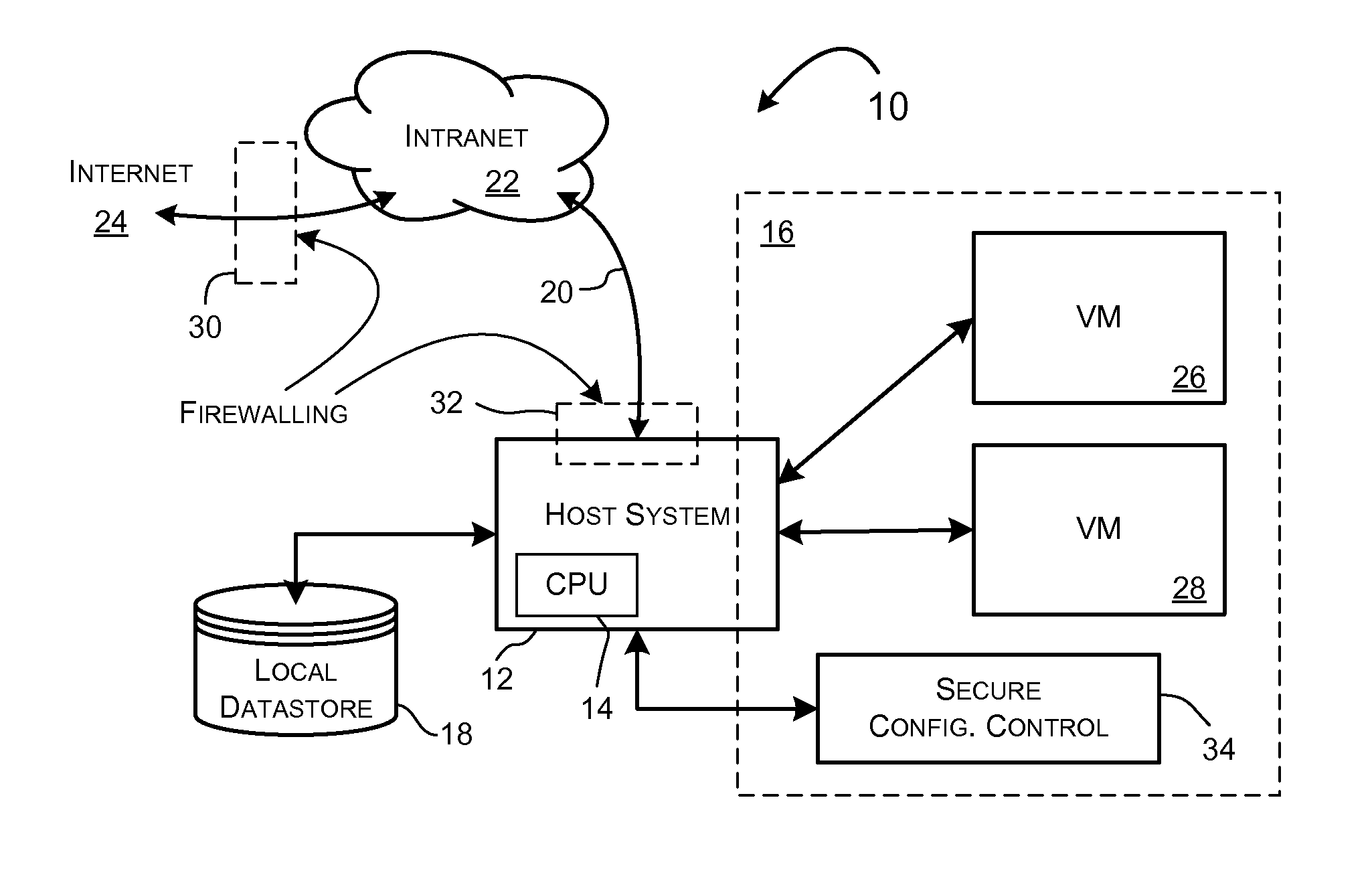
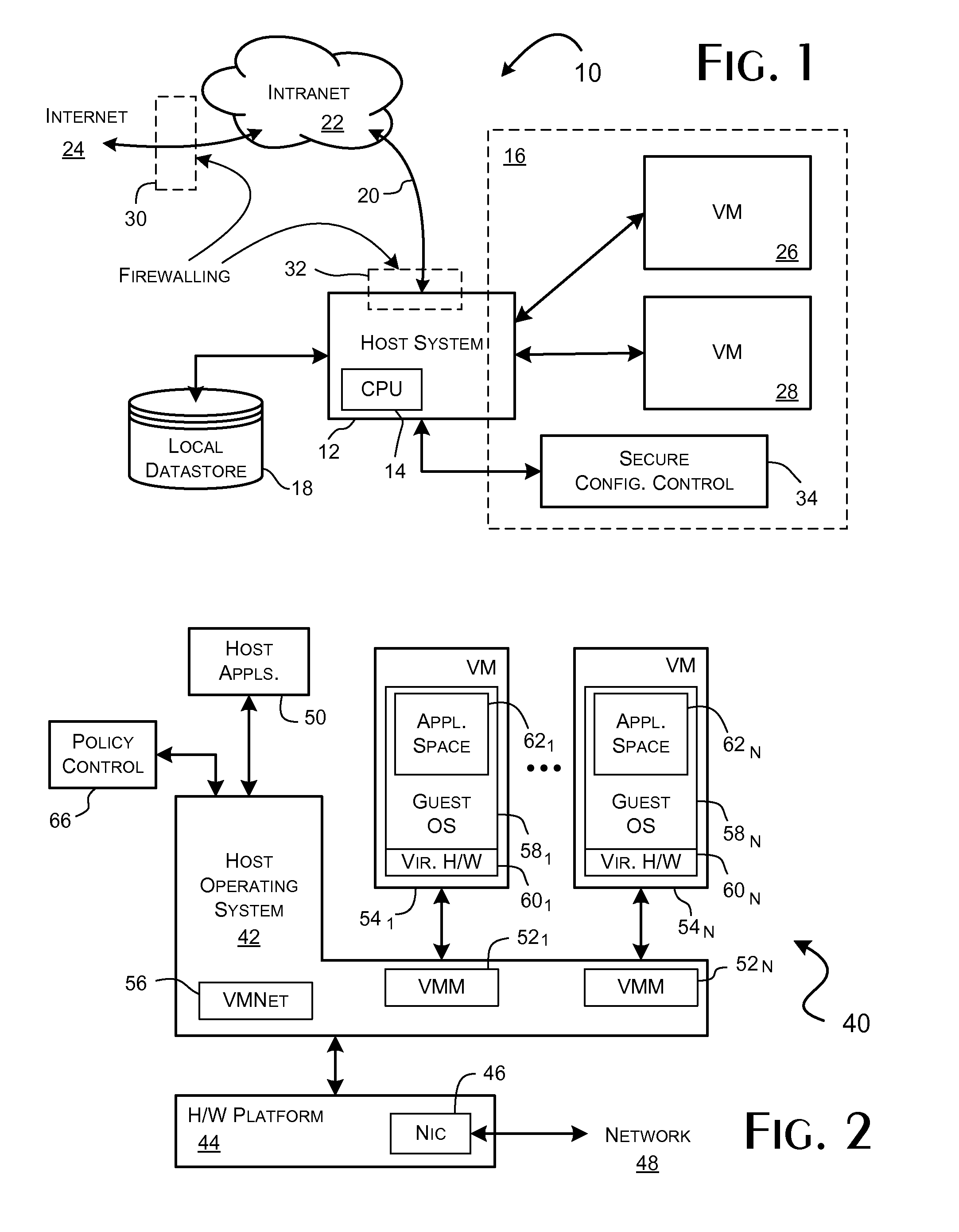
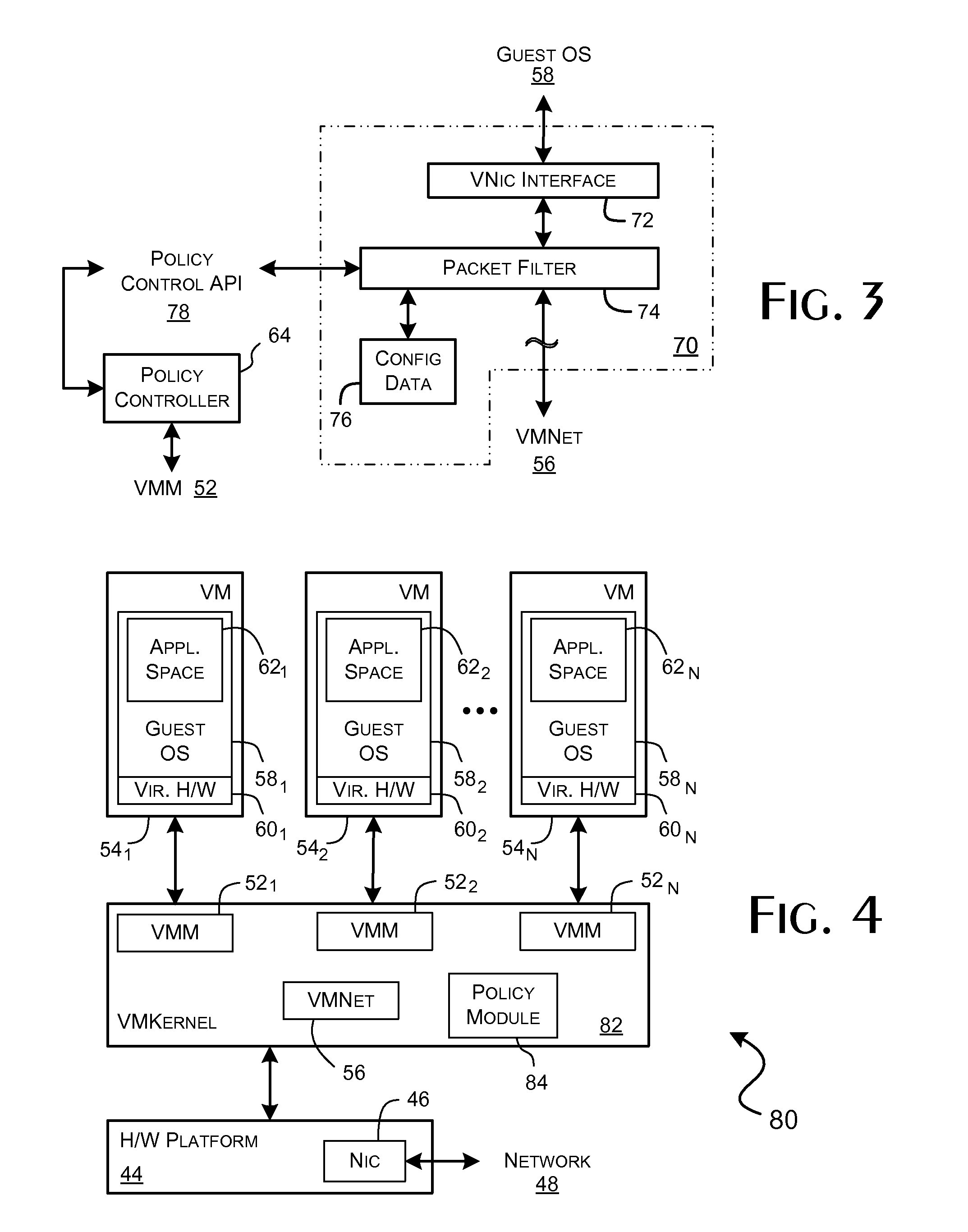
System and methods for implementing network traffic management for virtual and physical machines
ActiveUS8166474B1Ensure safetyEasy to useDigital computer detailsSoftware simulation/interpretation/emulationVirtualizationTraffic capacity
A virtualization framework provides security between multiple virtual machines with respect to network communications between the virtual machines and between the virtual machines and a physical network coupled to the underlying physical computer platform. The virtualization framework includes a network interface controller driver that provides an interface to the platform network interface controller and supports execution of a plurality of virtual machines. Each virtual machine includes a virtual network interface controller that provides a network communications path between the virtual machines and to the network interface controller driver. Each virtual network interface controller further contains a programmable network packet filter that controls the selective transfer of network packets with respect to a corresponding virtual machine.
Owner:VMWARE INC
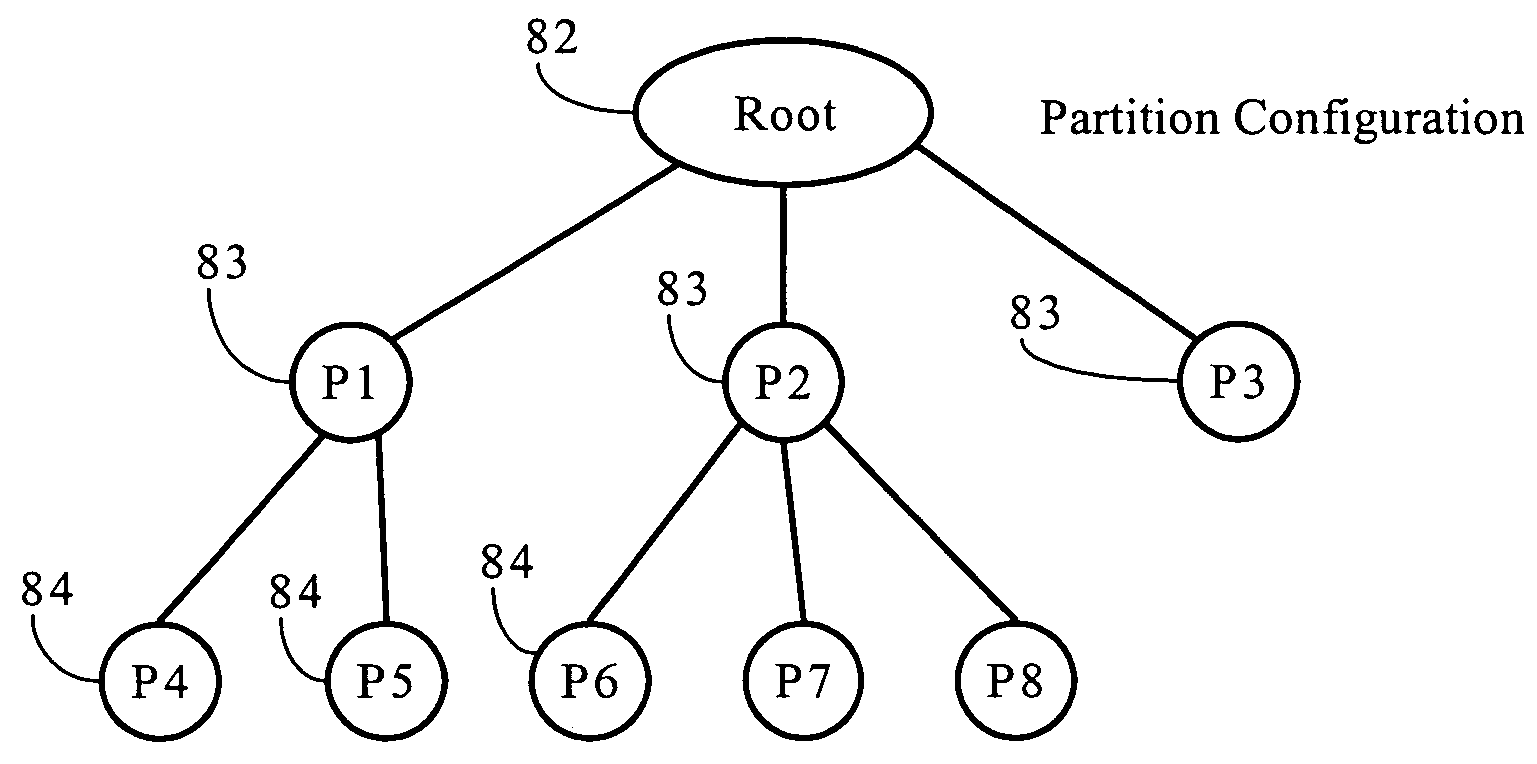
Partition Configuration and Creation Mechanisms for Network Traffic Management Devices
InactiveUS20110182180A1Improve predictabilityError preventionTransmission systemsPredictabilityNetwork traffic management
Owner:CA TECH INC
Configuration of congestion thresholds for a network traffic management system
InactiveUS20070237074A1Improve performancePrevent fallingError preventionTransmission systemsTraffic capacityCommunications system
A hierarchical congestion management system improves the performance of traffic through a communications system. In one embodiment of the invention, a first subset of thresholds is configured so as to guarantee the passage of a certain high-priority or other selected communications traffic. Further, a second subset of thresholds is configured to control interference among independent flows of traffic that are competing to pass through the system. As a result of these configurations, traffic flows that cause congestion at the output are isolated to prevent dropping other traffic, and high-priority traffic is ensured passage.
Owner:TELLABS OPERATIONS
Partition configuration and creation mechanisms for network traffic management devices
ActiveUS7925756B1Improve predictabilityMultiprogramming arrangementsMultiple digital computer combinationsTraffic capacityPredictability
Partition configuration and creation mechanisms for network traffic management devices. In some implementations, the present invention enhances the predictability of partition hierarchies that use weighting values and fixed rate guarantees. In some implementations, the present invention includes a configuration interface that constrains the manner in which partitions can be configured to achieve predictable and efficient results. In some implementations, the present invention includes a partition creation and deletion layer that operates to dynamically create partitions based on one or more partition patterns.
Owner:CA TECH INC
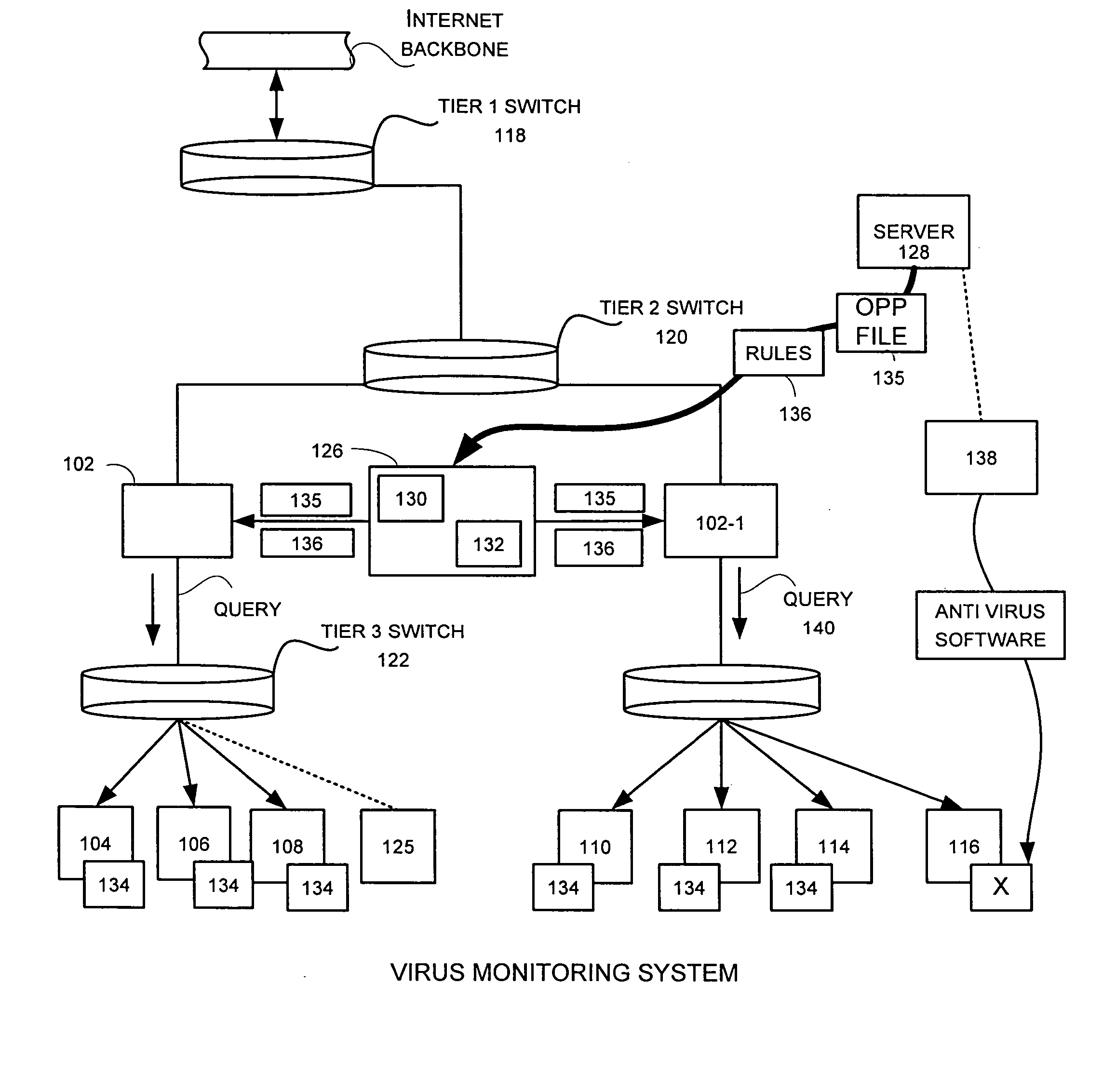
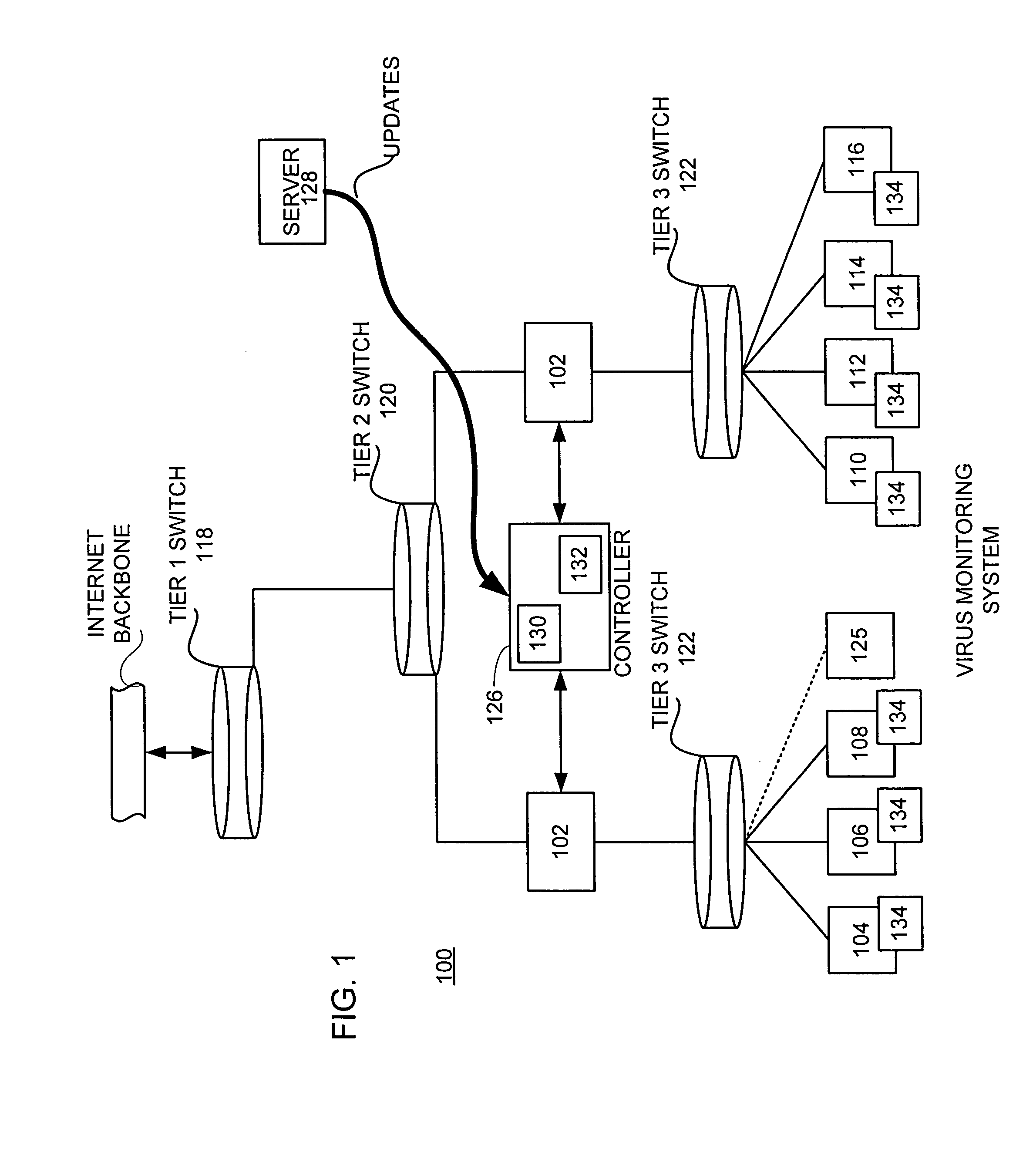
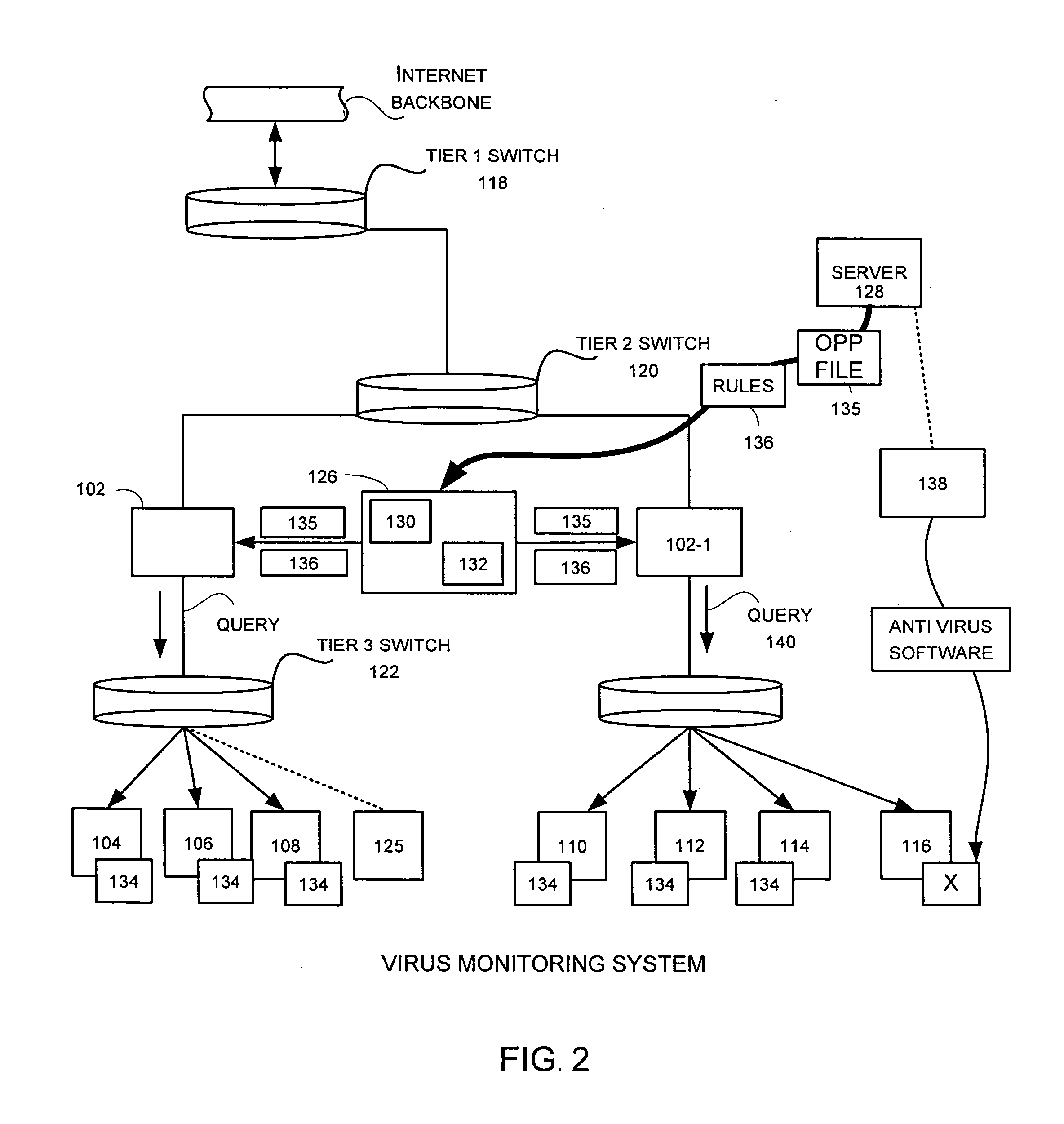
Network traffic management by a virus/worm monitor in a distributed network
InactiveUS20050050334A1Unauthorized memory use protectionHardware monitoringDowntimeInternet traffic
A network level virus monitoring system capable of monitoring a flow of network traffic in any of a number of inspection modes depending upon the particular needs of a system administrator. The system includes a network virus sensor self registration module coupled to a network virus / worm sensor arranged to automatically self register the associated network virus / worm sensor. The monitoring provides an early warning of a virus attack thereby facilitating quarantine procedures directed at containing a virus outbreak. By providing such an early warning, the network virus monitor reduces the number of computers ultimately affected by the virus attack resulting in a concomitant reduction in both the cost of repair to the system and the amount of downtime. In this way, the inventive network virus monitor provides a great improvement in system uptime and reduction in system losses.
Owner:TREND MICRO INC
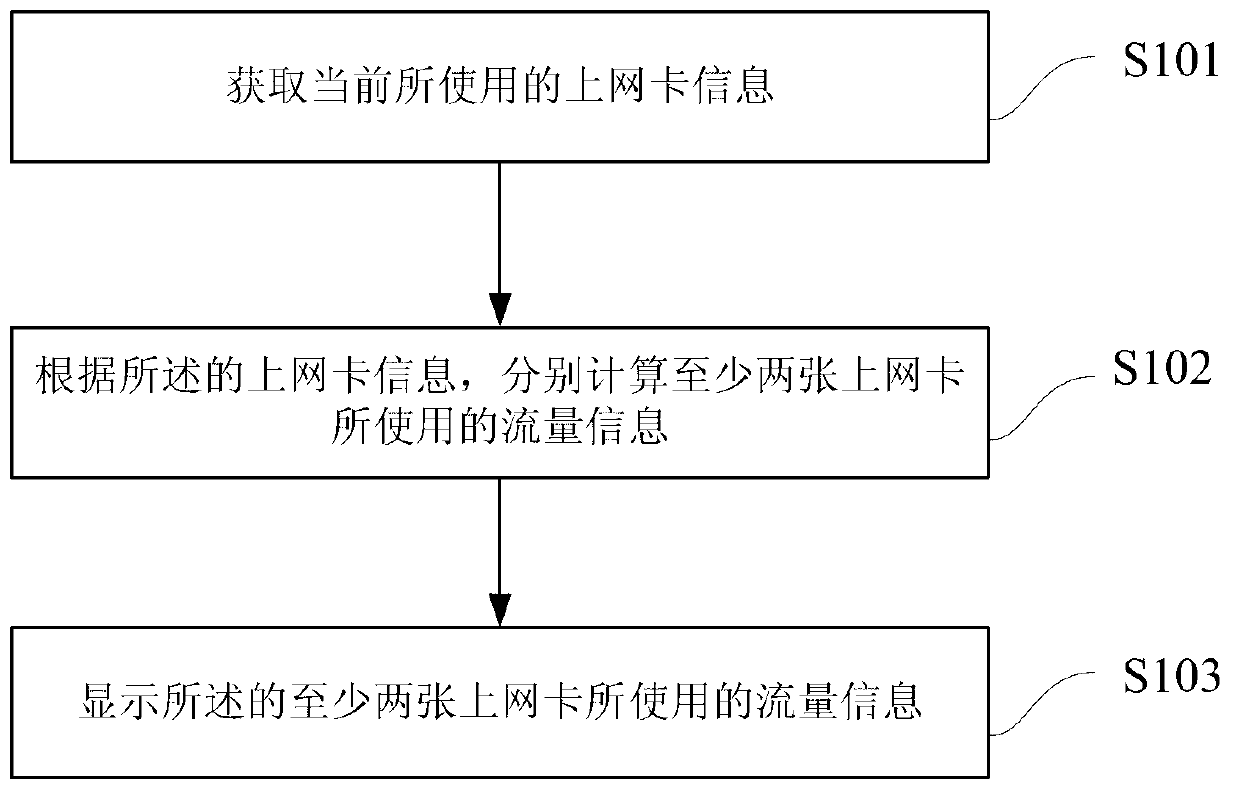
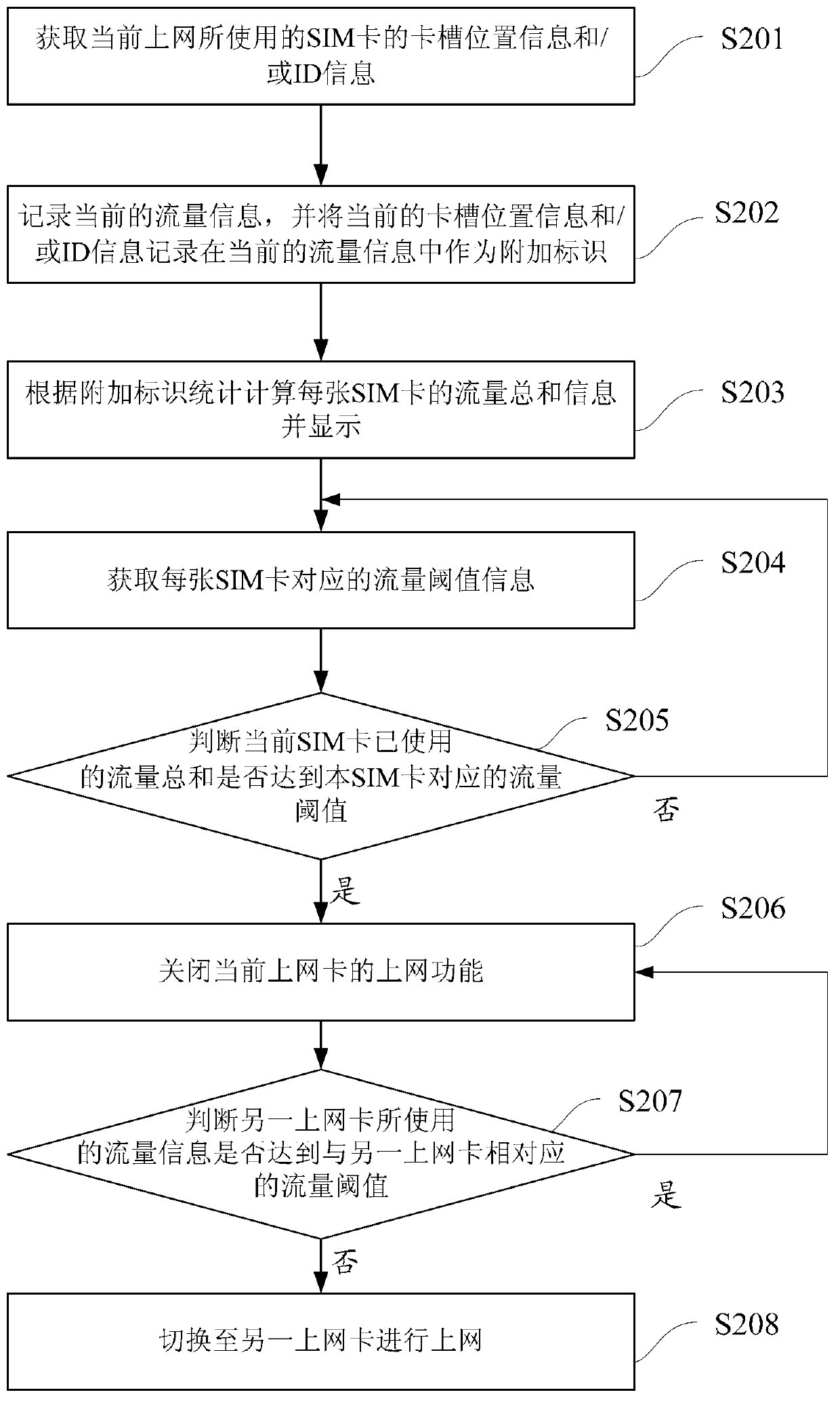
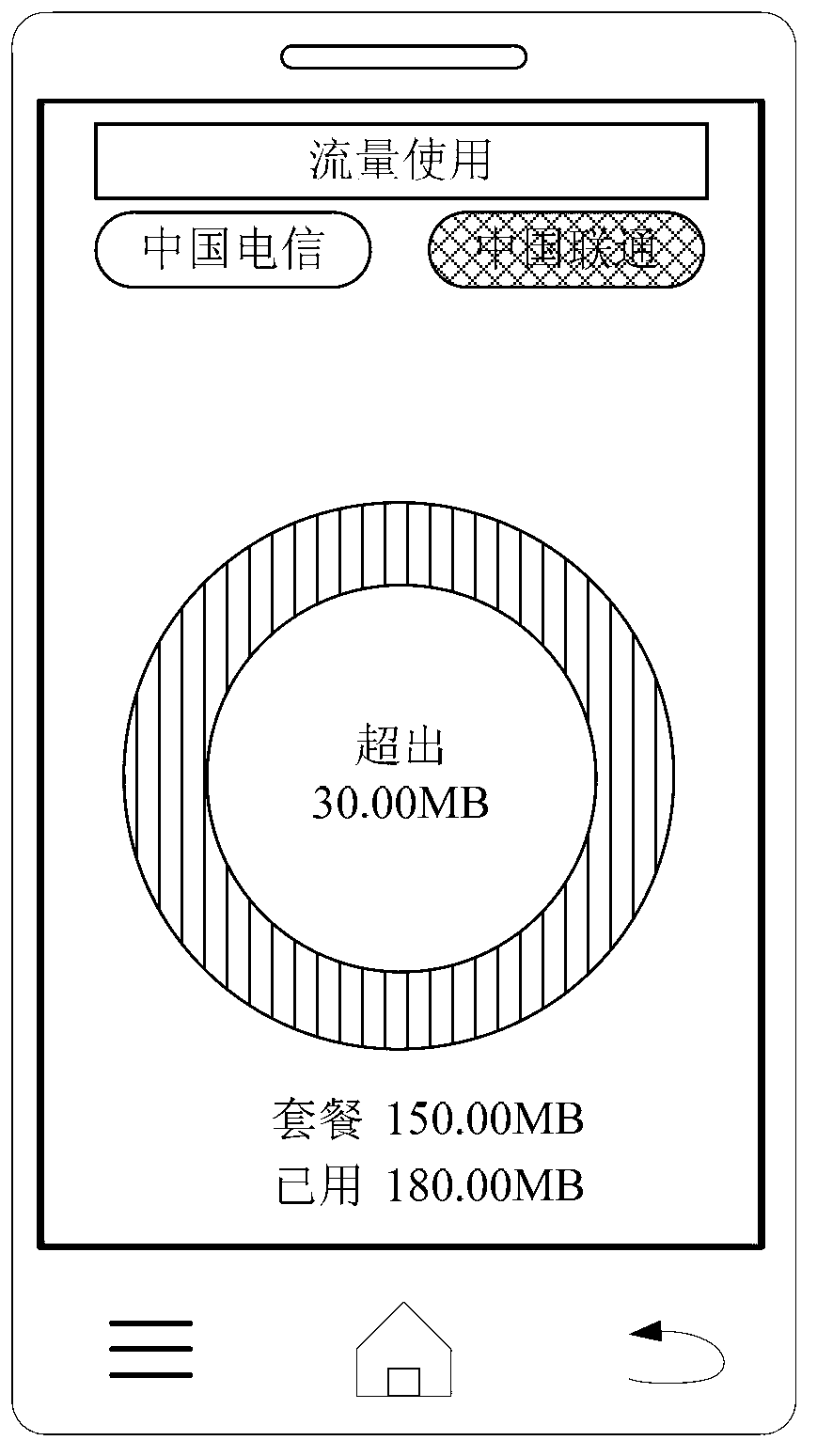
Network flow management method and device of double-card terminal
InactiveCN103281687AKeep abreast of usage status at any timeAccounting/billing servicesMessaging/mailboxes/announcementsNetwork traffic managementFlow management
The invention relates to a network flow management method and device of a double-card terminal. The method comprises the steps that the information of network cards currently used is acquired, the information of the flow used by at least two network cards is respectively calculated, and the information of the flow used by the at least two network cards is displayed. The network flow management method and device of the double-card terminal can respectively calculate the information of the flow generated by each network card, and ensure that a user can master the use condition of the flow at any time.
Owner:XIAOMI INC
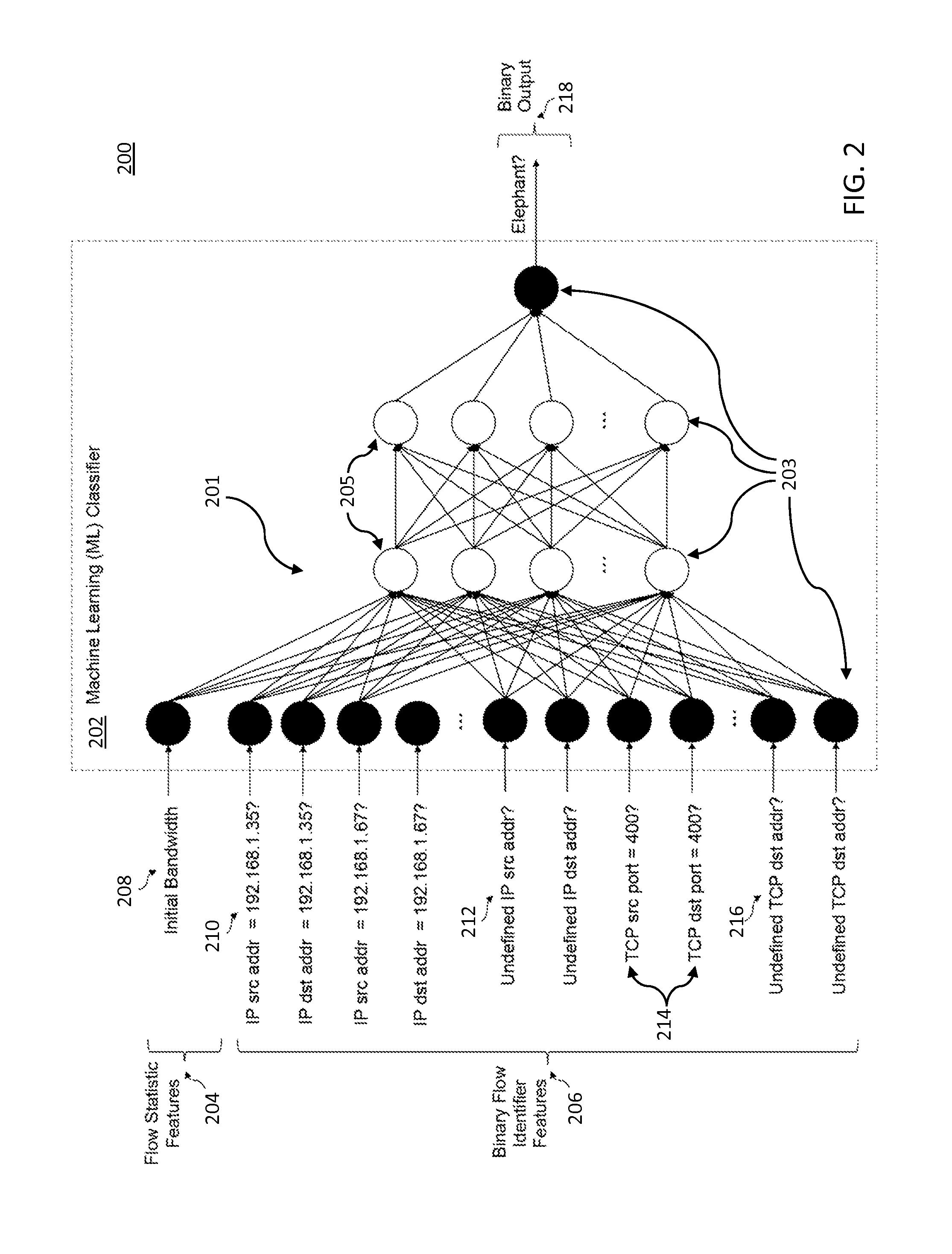
Network traffic flow management using machine learning
ActiveUS20160105364A1Error preventionFrequency-division multiplex detailsTraffic capacityTraffic flow management
A system and method for management of network traffic flow for one or more networks of interconnected computing devices, including predicting one or more types of network traffic data flows using a Machine Learning (ML) classifier, and updating the ML classifier according to identified changes in the network traffic data flows. Using software-defined-networking (SDN) tools and an updated ML classifier, training data is generated to formulate accurate new predictions of the one or more types of network traffic data flows. Network traffic flow is regulated based on the generated new predictions.
Owner:NEC CORP
Wireless provisioning device
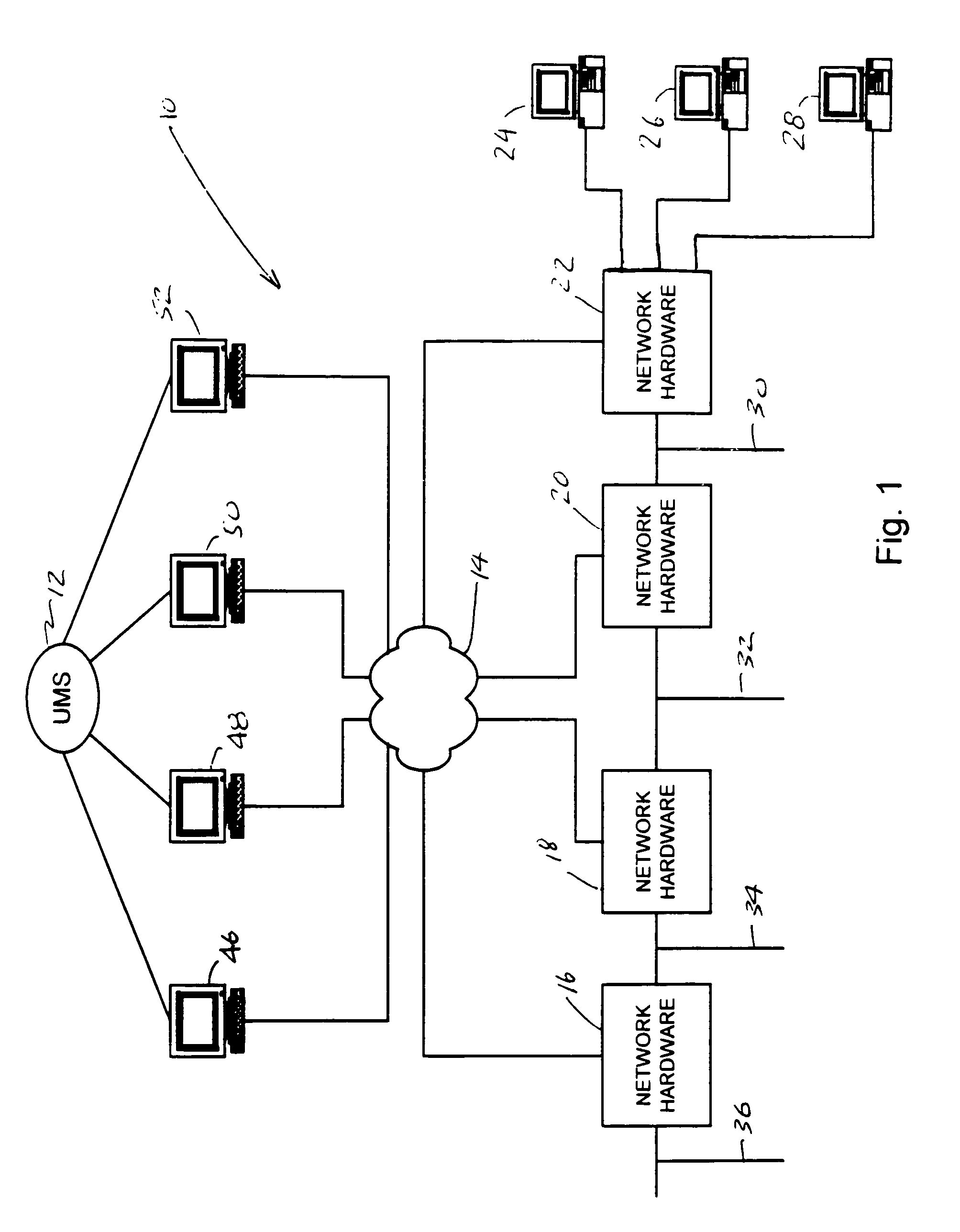
InactiveUS7765309B2Facilitate data traffic managementImprove effective throughputNetwork topologiesMultiple digital computer combinationsWireless mesh networkFrequency spectrum
A wireless provisioning device (WPD) is a computer data traffic management system capable of routing TCP / IP traffic using unlicensed spectrum equipment. This WPR is to be strategically placed in logical segment regions within a wireless network to facilitate data traffic management. This device acts to provide connectivity between wireless backbone access points. The device may also be located within customer local area network (LAN) while providing connectivity to a wide area network (WAN). The wireless device has seven total wireless segments. The wireless device is capable of filtering IP addresses, spam, pornographic content, steganographic decryption, controlling firewall and / or routing and / or bridging. The increases effective throughput of TCP / IP traffic over the WAN or LAN while providing for secure management and greater connectivity.
Owner:WECOM SYST
Network configuration predictive analytics engine
InactiveUS20130290520A1Ensuring Safe ExecutionDigital computer detailsData switching networksConfiguration analysisNetwork management
A mechanism associated with a network management system (NMS) interprets and predicts the impact on a network of a network configuration change proactively. By providing pre-configuration analysis in this manner, a network administrator can determine the potential effect of the proposed configuration change in advance of actually inserting a configuration command in the network that might otherwise have unforeseen and damaging consequences. The technique is implemented using a predictive analytics engine that receives a proposed network command and, using a current network topology, executes the command against one or more NMS algorithms to verify that the command can be implemented safely.
Owner:IBM CORP
Load balancing array packet routing system
InactiveUS7340532B2Digital data processing detailsMultiprogramming arrangementsTraffic capacityWeb service
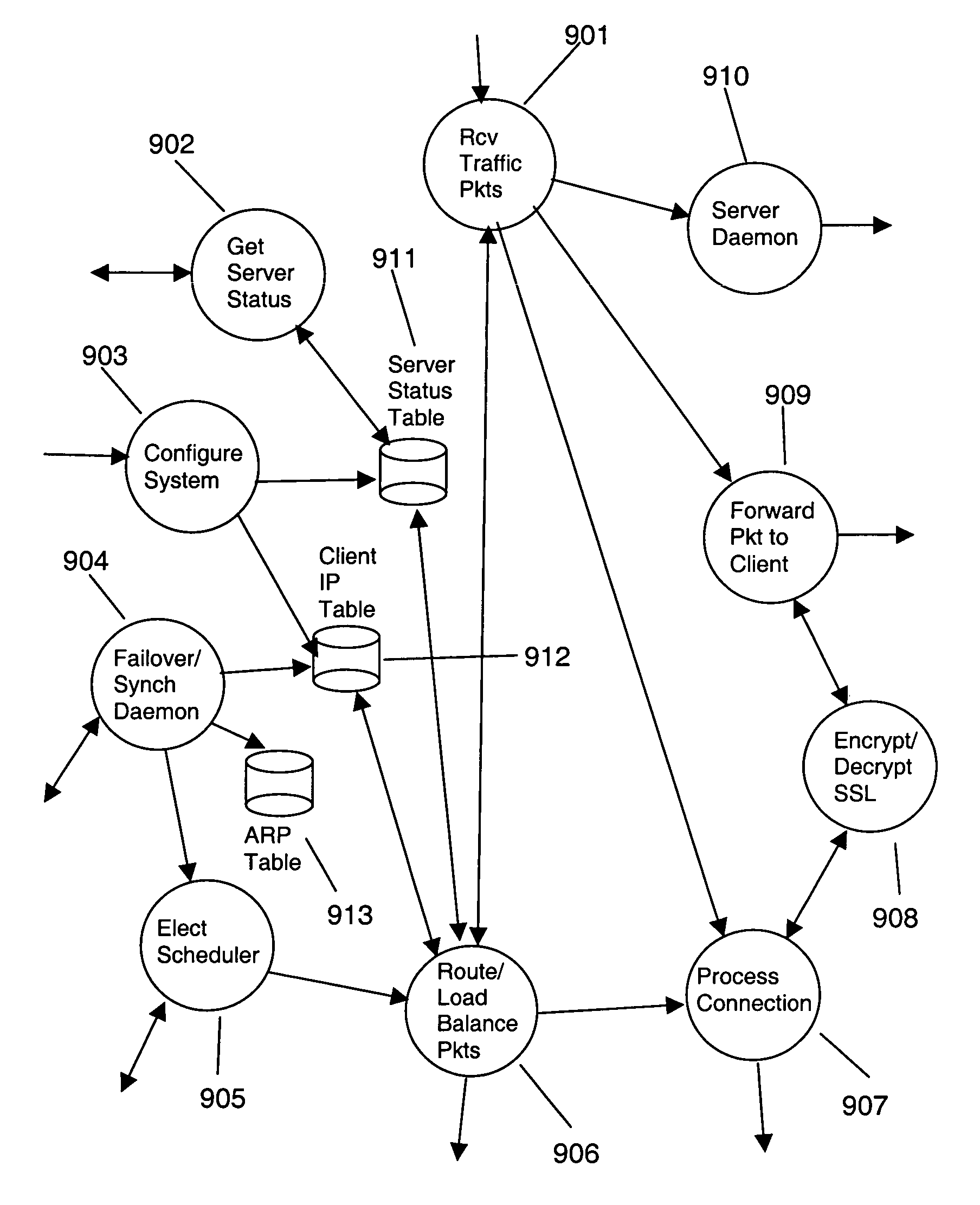
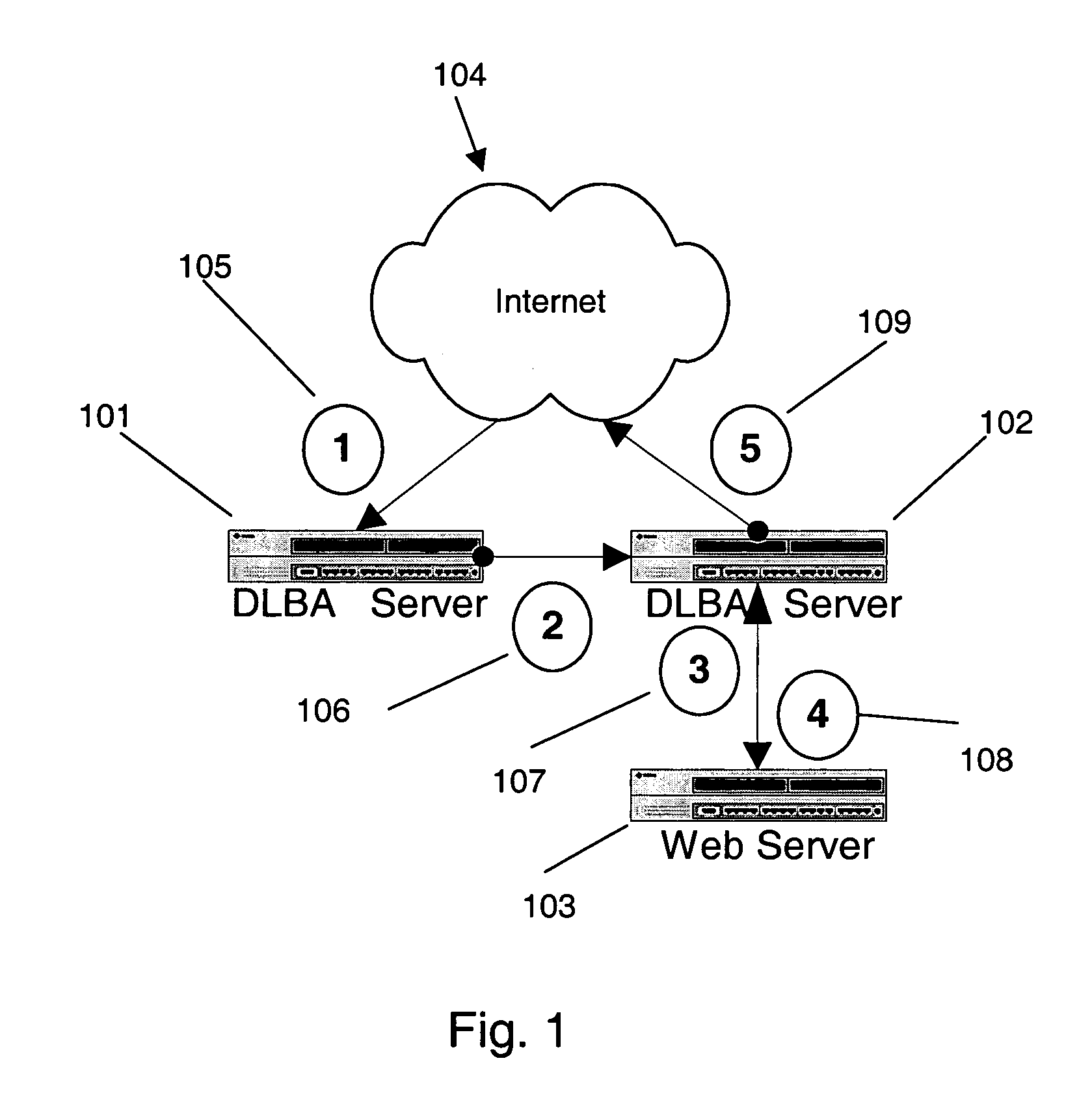
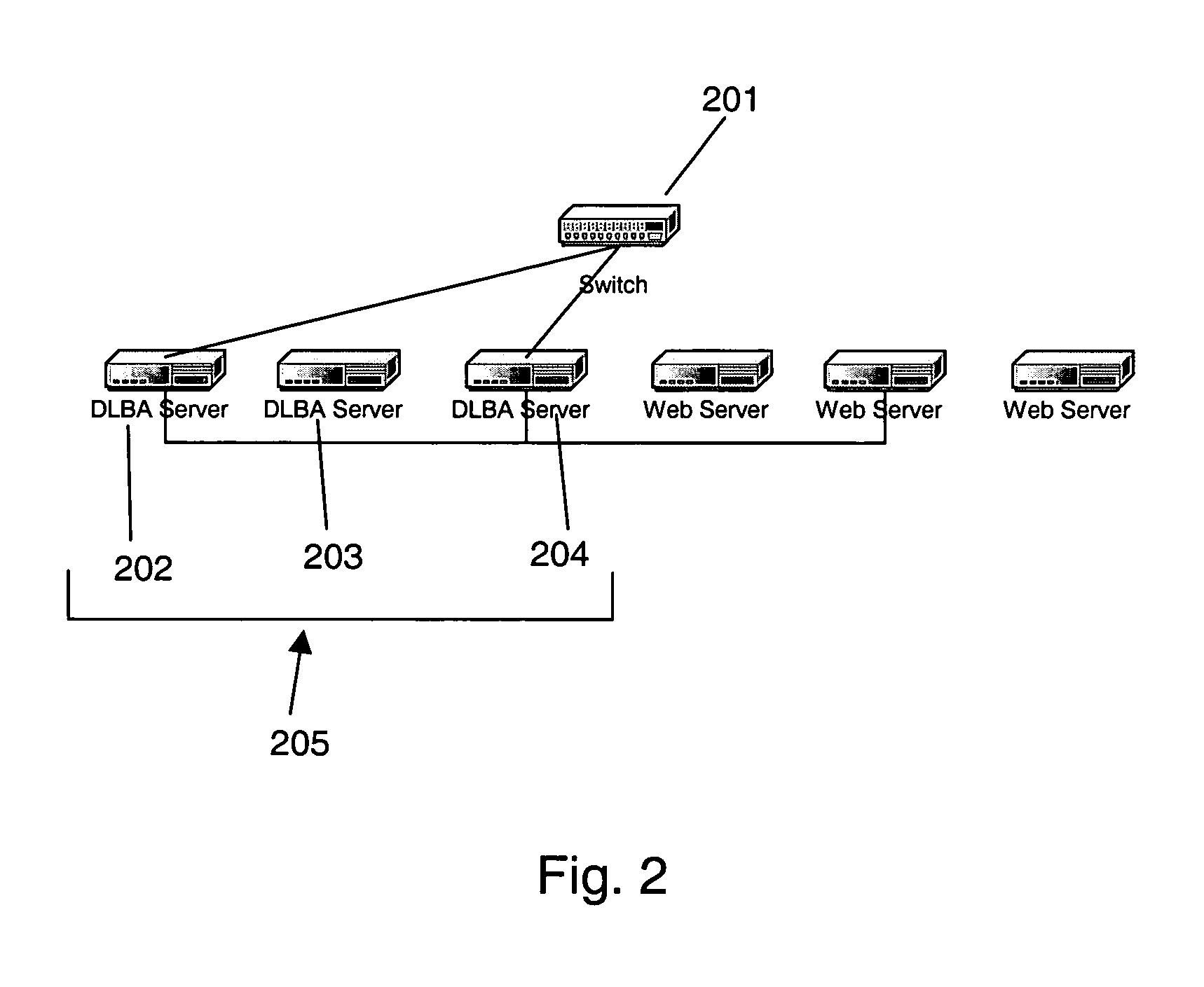
A decrypting load balancing array system uses a Pentaflow approach to network traffic management that extends across an array of Decrypting Load Balancing Array (DLBA) servers sitting in front of back end Web servers. One of the DLBA servers acts as a scheduler for the array through which all incoming requests are routed. The scheduler routes and load balances the traffic to the other DLBA servers (including itself) in the array. Each DLBA server routes and load balances the incoming request packets to the appropriate back end Web servers. Responses to the requests from the back end Web servers are sent back to the DLBA server which forwards the response directly to the requesting client. SSL packets are decrypted in the DLBA server before being routed to a back end Web server, allowing the DLBA server to schedule SSL sessions to back end Web servers based on a cookie or session ID. Response packets are encrypted by the DLBA server before being forwarded to the client. The invention also uses cookie injection to map a client to a specific back end Web server. In addition, any DLBA server in the array is capable of taking over the scheduler functionality in case of scheduler failure. URL based scheduling and hash scheduling of request packets with keepalive connections is easily performed due to the invention's architecture.
Owner:AKAMAI TECH INC
Network traffic management through protocol-configurable transaction processing
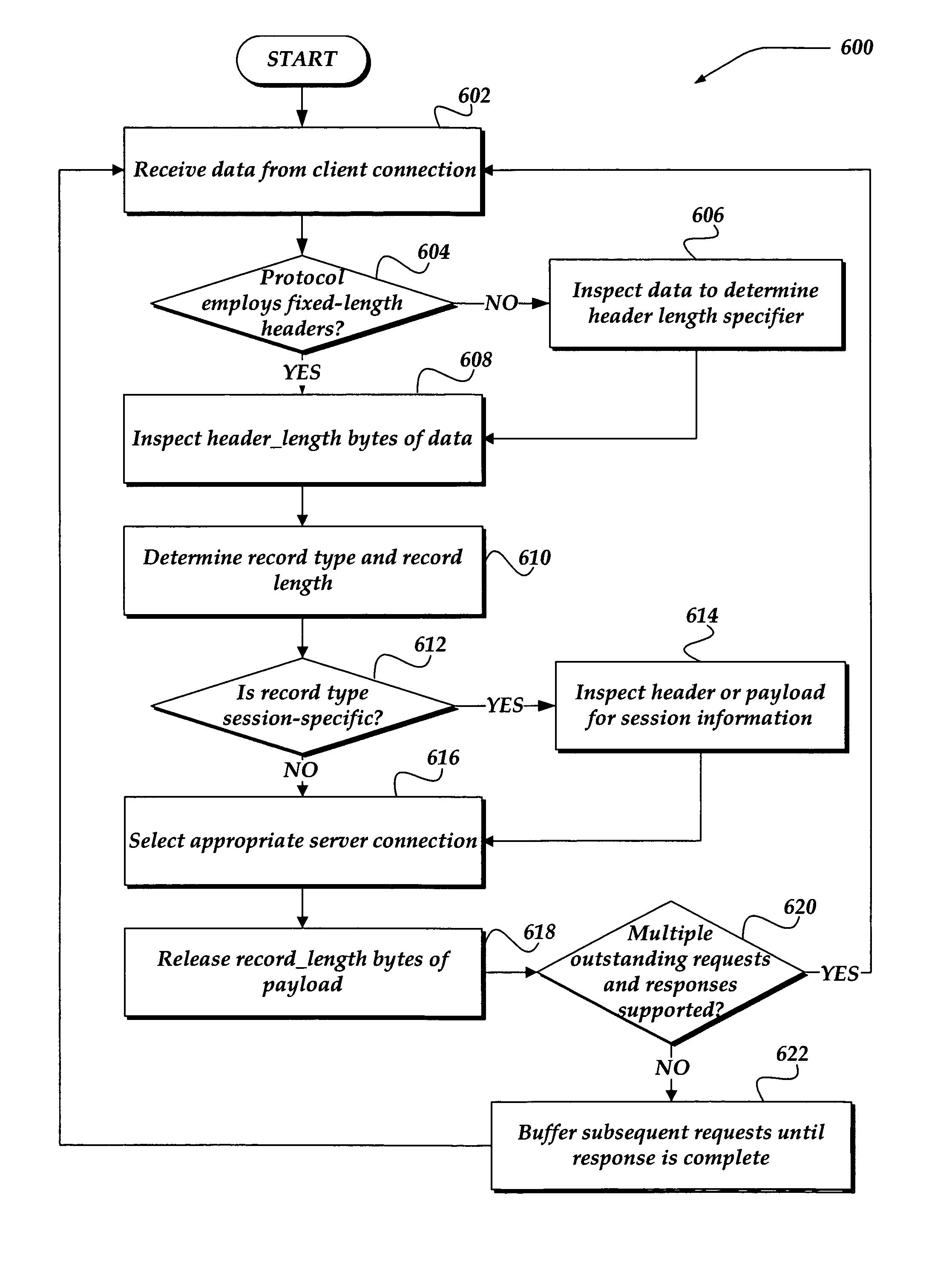
A traffic management device or other intermediate network device is configured to enable the device to support connection splitting and / or connection aggregation or to otherwise process network transactions for an arbitrary transaction-oriented protocol. The configuration may be accomplished by providing one or more traffic management rules defined by way of a scripting language and provided to an interpreter. The traffic management rule may follow a basic approach common to many protocols and is adapted to the particular protocol being supported. The rule may configure the network device to inspect incoming data, extract length and record type specifiers, buffer an appropriate amount of data to determine transactions or transaction boundaries, and perform other operations. Transaction processing may be enabled for various kinds of protocols, including application-level, proprietary, quasi-proprietary, and special-purpose protocols, protocols for which limited information is available, and protocols not natively supported by the network device.
Owner:F5 NETWORKS INC
System and method for network traffic management and load balancing
InactiveCN102439913AEfficient use ofEasy maintenanceData switching by path configurationLocation information based serviceClient-sideNetwork traffic management
A method for providing load balancing and failover among a set of computing nodes running a network accessible computer service includes providing a computer service that is hosted at one or more servers comprised in a set of computing nodes and is accessible to clients via a first network. Providing a second network including a plurality of traffic processing nodes and load balancing means. The load balancing means is configured to provide load balancing among the set of computing nodes running the computer service. Providing means for redirecting network traffic comprising client requests to access the computer service from the first network to the second network.; Providing means for selecting a traffic processing node of the second network for receiving the redirected network traffic comprising the client requests to access the computer service and redirecting the network traffic to the traffic processing node via the means for redirecting network traffic. For every client request for access to the computer service, determining an optimal computing node among the set of computing nodes running the computer service by the traffic processing node via the load balancing means, and then routing the client request to the optimal computing node by the traffic processing node via the second network.
Owner:YOTTAA
Upgrading network traffic management devices while maintaining availability
ActiveUS8209403B2Software engineeringMultiple digital computer combinationsTraffic capacityVirtual cluster
A method, system, machine-readable storage medium, and apparatus are directed towards upgrading a cluster by bifurcating the cluster into two virtual clusters, an “old” virtual cluster (old active cluster) and a “new” virtual cluster (new standby cluster), and iteratively upgrading members of the old cluster while moving them into the new cluster. While members are added to the new cluster, existing connections and new connections are seamlessly processed by the old cluster. Optionally, state mirroring occurs between the old cluster and the new cluster once the number of members of the old and new clusters are approximately equal. Once a threshold number of members have been transferred to the new cluster, control and processing may be taken over by the new cluster. Transfer of control from the old cluster to the new cluster may be performed by failing over connectivity from the old cluster to the new cluster.
Owner:F5 NETWORKS INC
Network management system and graphical user interface
InactiveUS6963916B1Change is minimalMultiple digital computer combinationsData switching networksNetwork connectionNetworking hardware
A network management system and graphical user interface for configuring a network connection between first and second service access points utilizes a configuration manager and information manager to provide a generic set of models so that different manufacturer's nodal processors and other network hardware can be inserted into the network with minimal changes to the software which controls the device. The system comprises an information manager including routing information for the network. The configuration manager operates to establish a connection across each subnet on the route by sending requests to element managers to program the subnet elements.
Owner:QWEST
Implementing network traffic management for virtual and physical machines
ActiveUS20120185914A1Maintain securityEasy to useComputer security arrangementsMultiple digital computer combinationsTraffic capacityVirtualization
A virtualization framework provides security between multiple virtual machines with respect to network communications between the virtual machines and between the virtual machines and a physical network coupled to the underlying physical computer platform. The virtualization framework includes a network interface controller driver that provides an interface to the platform network interface controller and supports execution of a plurality of virtual machines. Each virtual machine includes a virtual network interface controller that provides a network communications path between the virtual machines and to the network interface controller driver. Each virtual network interface controller further contains a programmable network packet filter that controls the selective transfer of network packets with respect to a corresponding virtual machine.
Owner:VMWARE INC
Network topology structure and node information gathering method
InactiveCN102195857AReal-time acquisitionReal-time performanceData switching networksIndustrial EthernetNeighbor finding
The invention relates to a network topology structure and a node information gathering method, which are applied to a network topology structure in industrial Ethernet equipment and accurate search of network information. The method mainly comprises the following steps of: presetting interface information and an interface index of neighboring node state information in an exchange equipment host computer; receiving a neighbor finding report by using a network management terminal; determining the linking relation between ports according to the port linking state of the neighbor finding report and neighboring node information by using a network equipment node; and establishing a network topological diagram according to the port linking relation by using the network management terminal to perform corresponding network management.
Owner:WUHAN MAIWE OPTOELECTRONICS TECH
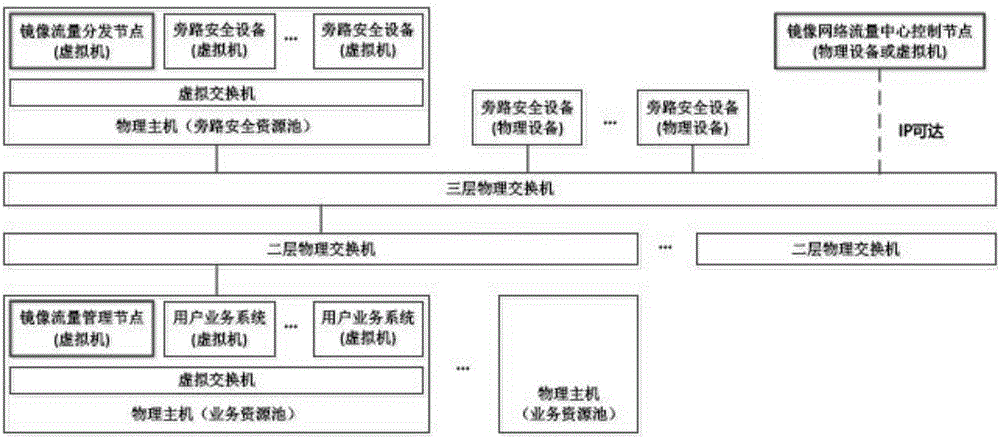
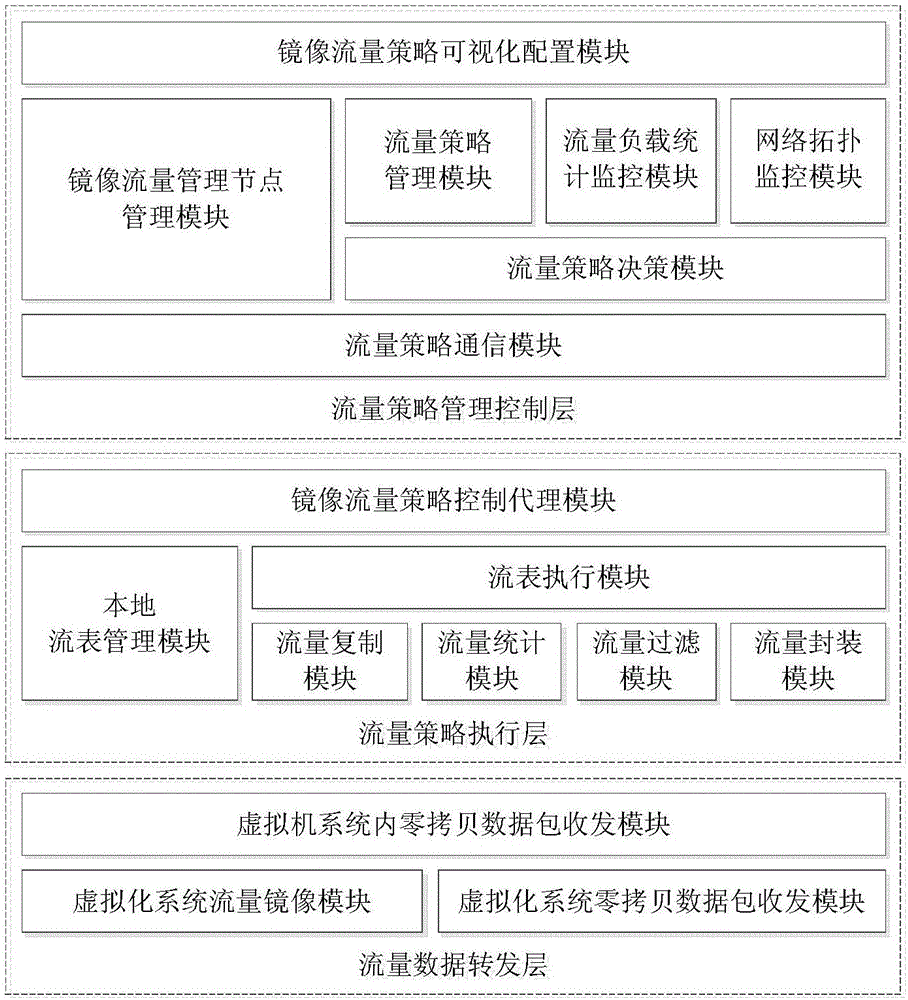
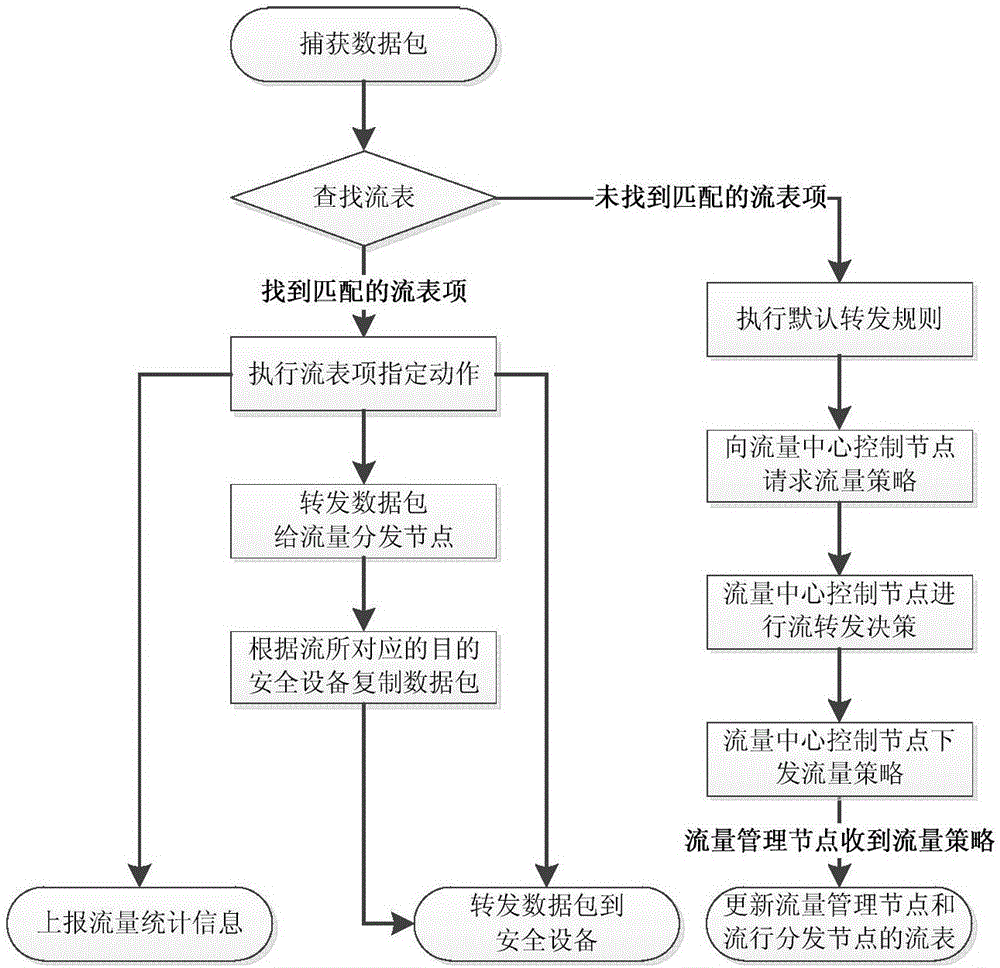
Management system of mirror network flow in virtual network environment and control method
ActiveCN106375384ARealize Agile SchedulingIntegrity guaranteedData switching networksFlow managementCopying
The invention discloses a management system of mirror network flow in a virtual network environment and a software definition based mirror flow management and control method. A mirror network flow management and control system comprises a mirror network flow central control node, virtual mirror flow management nodes and virtual mirror flow distribution nodes. The mirror network flow central control node is utilized for global control; the virtual mirror flow management nodes deployed near a service virtual machine are utilized for realizing capturing of data packets and forwarding based on a flow table; and the virtual mirror flow distribution nodes deployed near a safety device are utilized for copying and distribution of the data packets based on safety services. According to the management system of the mirror network flow in the virtual network environment and the software definition based mirror flow management and control method, an optimal mirror flow exporting policy in a global perspective is obtained, the mirror flow scheduling is quick and complete, and only a few computing resource is occupied by the mirror flow management nodes.
Owner:BEIJING RUIHE YUNTU TECH CO LTD
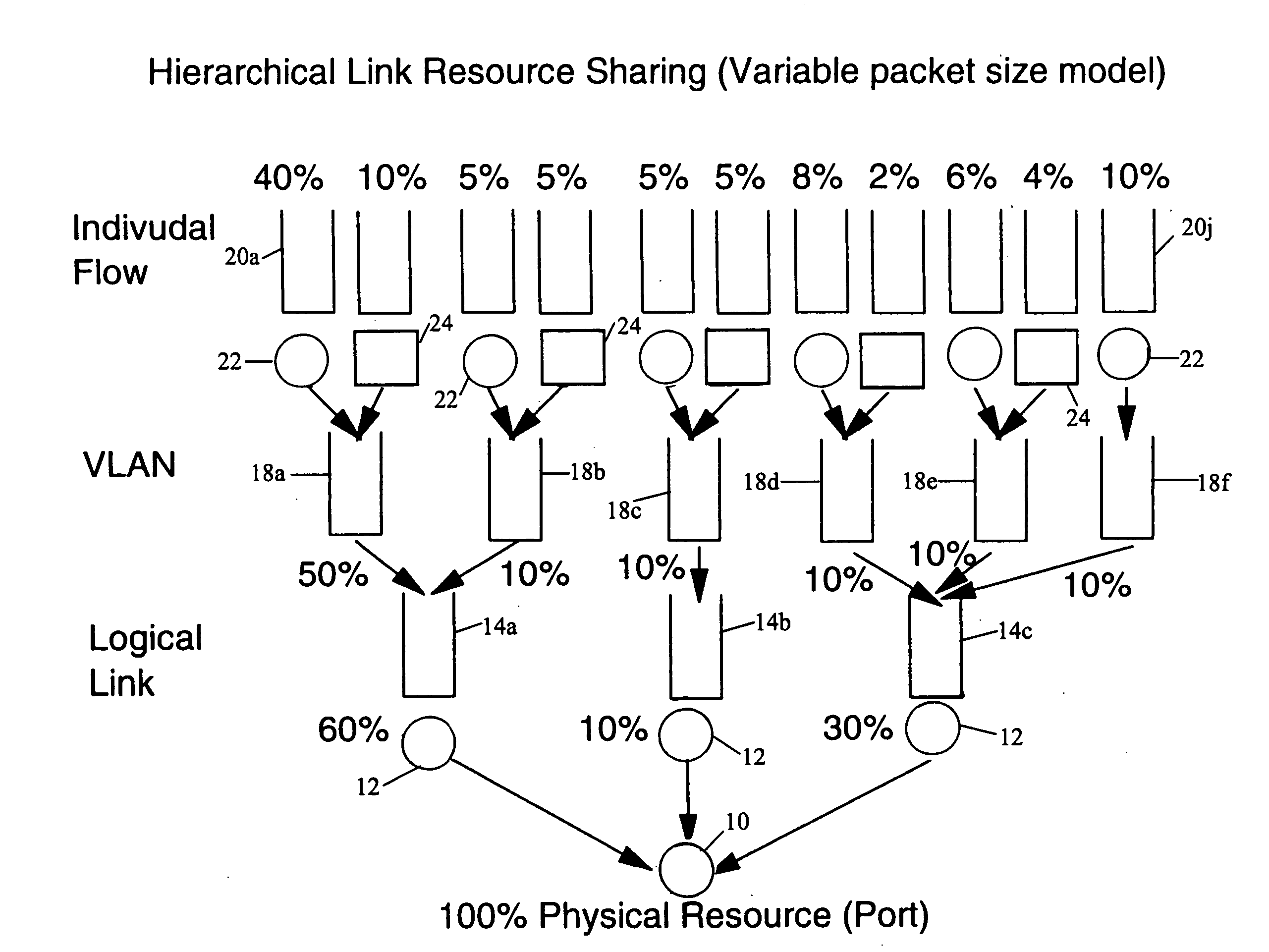
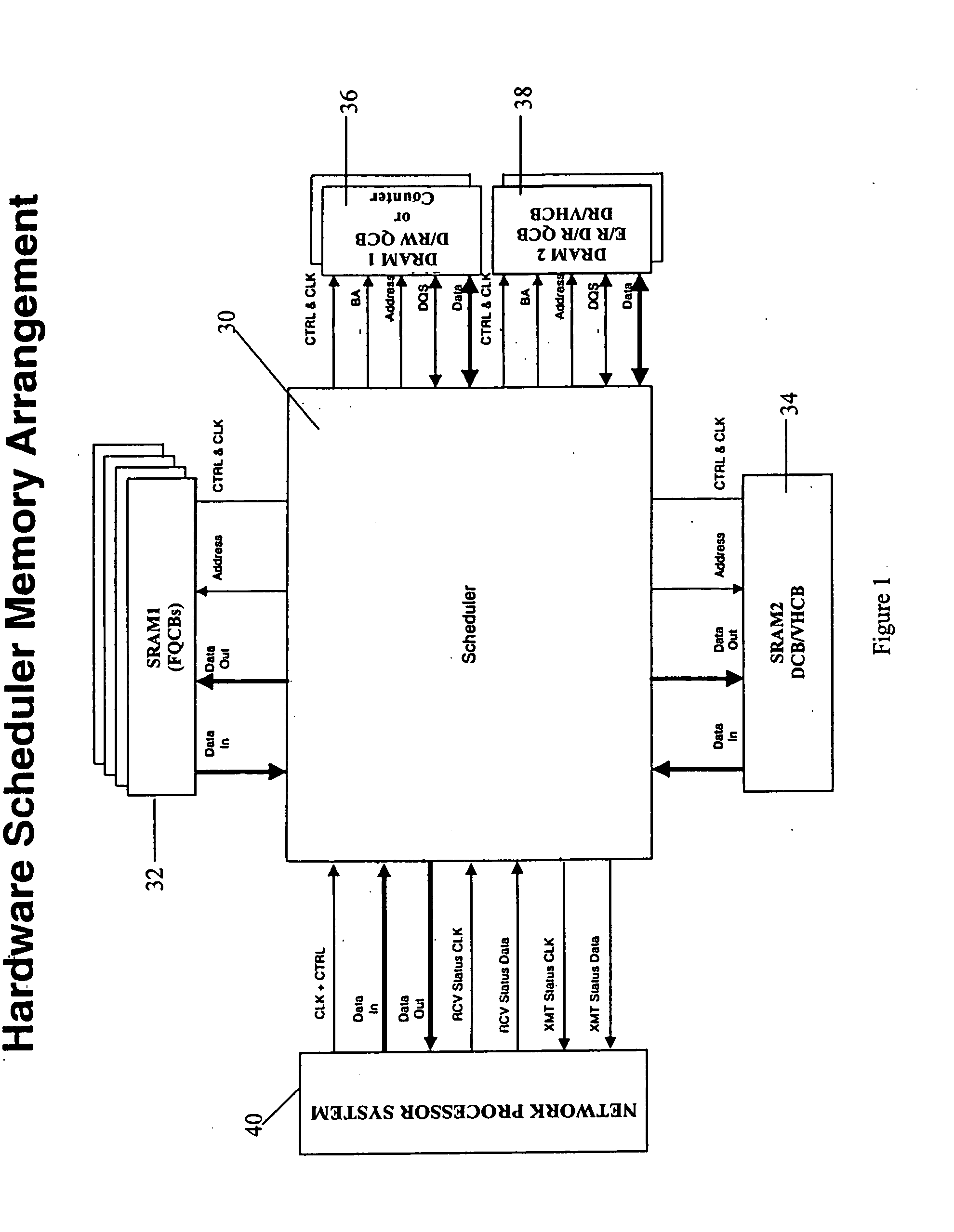
Structure and method for scheduler pipeline design for hierarchical link sharing
InactiveUS20050177644A1Reduce in quantityMultiple digital computer combinationsData switching networksTraffic capacityExternal storage
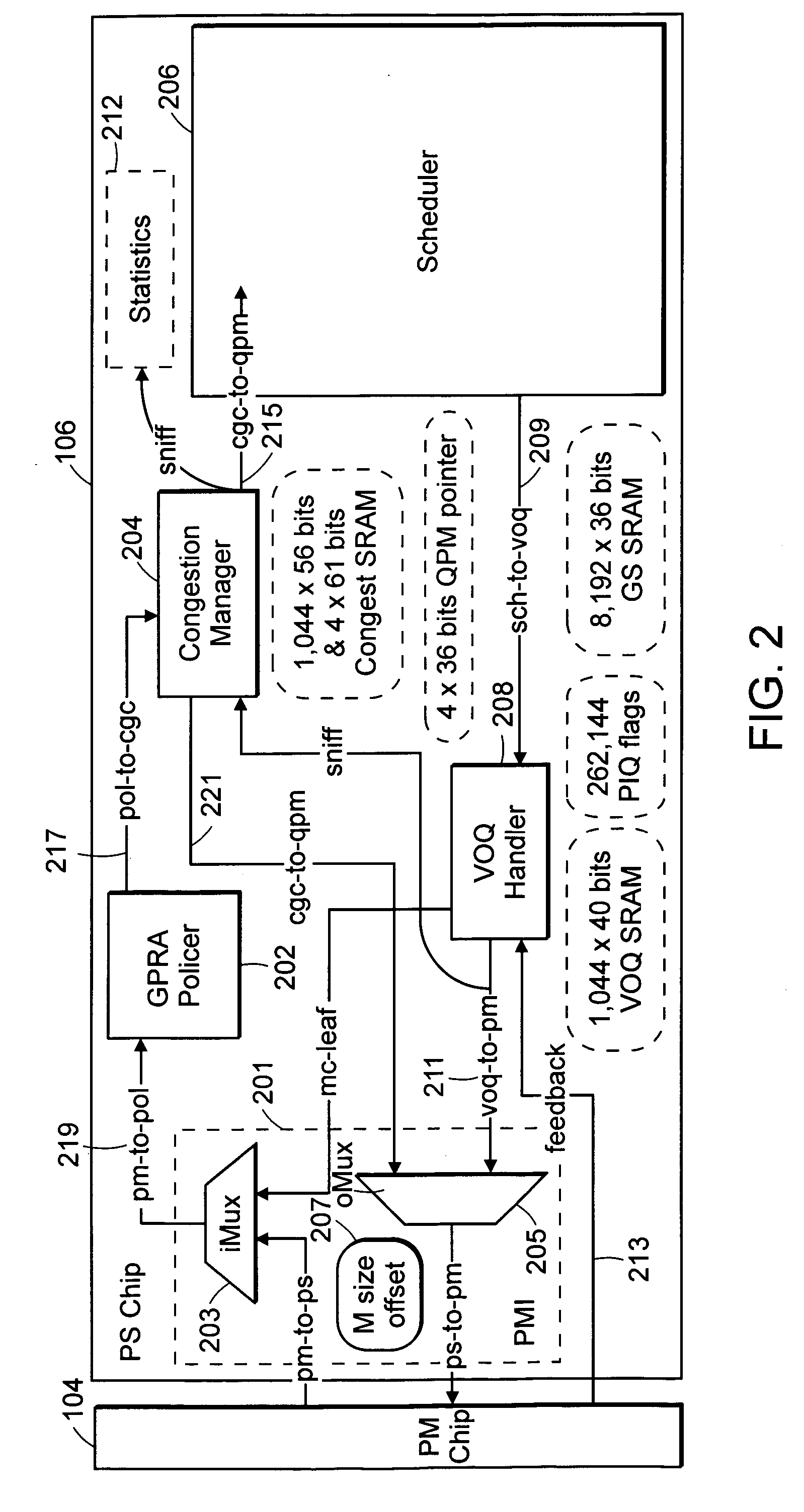
A pipeline configuration is described for use in network traffic management for the hardware scheduling of events arranged in a hierarchical linkage. The configuration reduces costs by minimizing the use of external SRAM memory devices. This results in some external memory devices being shared by different types of control blocks, such as flow queue control blocks, frame control blocks and hierarchy control blocks. Both SRAM and DRAM memory devices are used, depending on the content of the control block (Read-Modify-Write or ‘read’ only) at enqueue and dequeue, or Read-Modify-Write solely at dequeue. The scheduler utilizes time-based calendars and weighted fair queueing calendars in the egress calendar design. Control blocks that are accessed infrequently are stored in DRAM memory while those accessed frequently are stored in SRAM.
Owner:IBM CORP
Network application classification for network traffic management
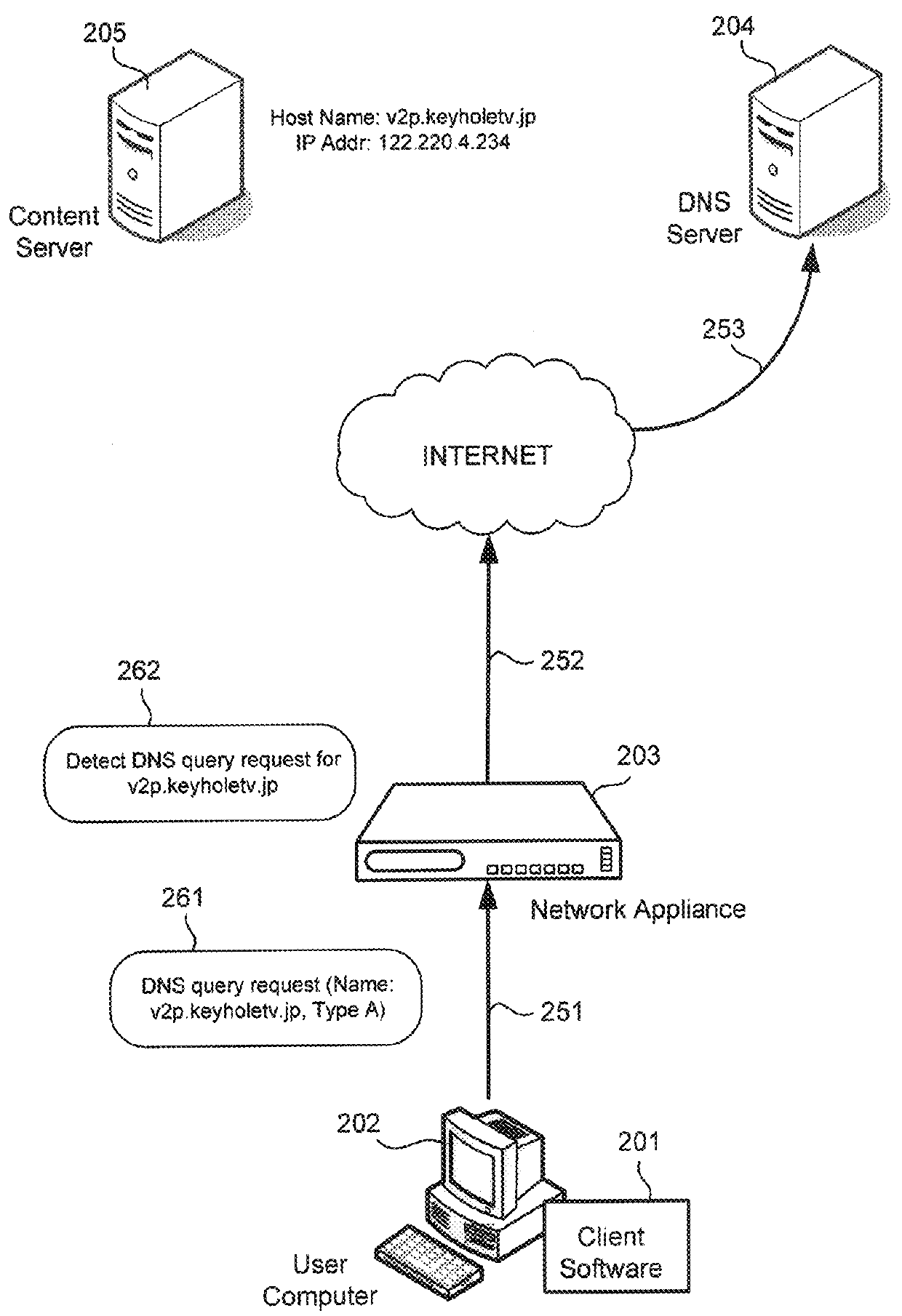
Network traffic with encrypted packet payloads is classified based on monitored Domain Name System (DNS) query requests and responses. A network appliance, or some other computer, receives a DNS query request for a network name (e.g., host name) of a content server, and starts monitoring for a corresponding DNS query response. The network appliance receives the DNS query response and parses the DNS query response to retrieve an Internet Protocol (IP) address associated with the network name. The network appliance classifies the IP address as belonging to the content server or a network application associated with the content server. When the network appliance subsequently receives packets with a source or destination address that matches the IP address, the network appliance classifies the received packets as belonging to the content server or a network application associated with the content server.
Owner:TREND MICRO INC
Automated policy builder
ActiveUS20120278851A1Computer security arrangementsTransmissionInternet trafficNetwork traffic management
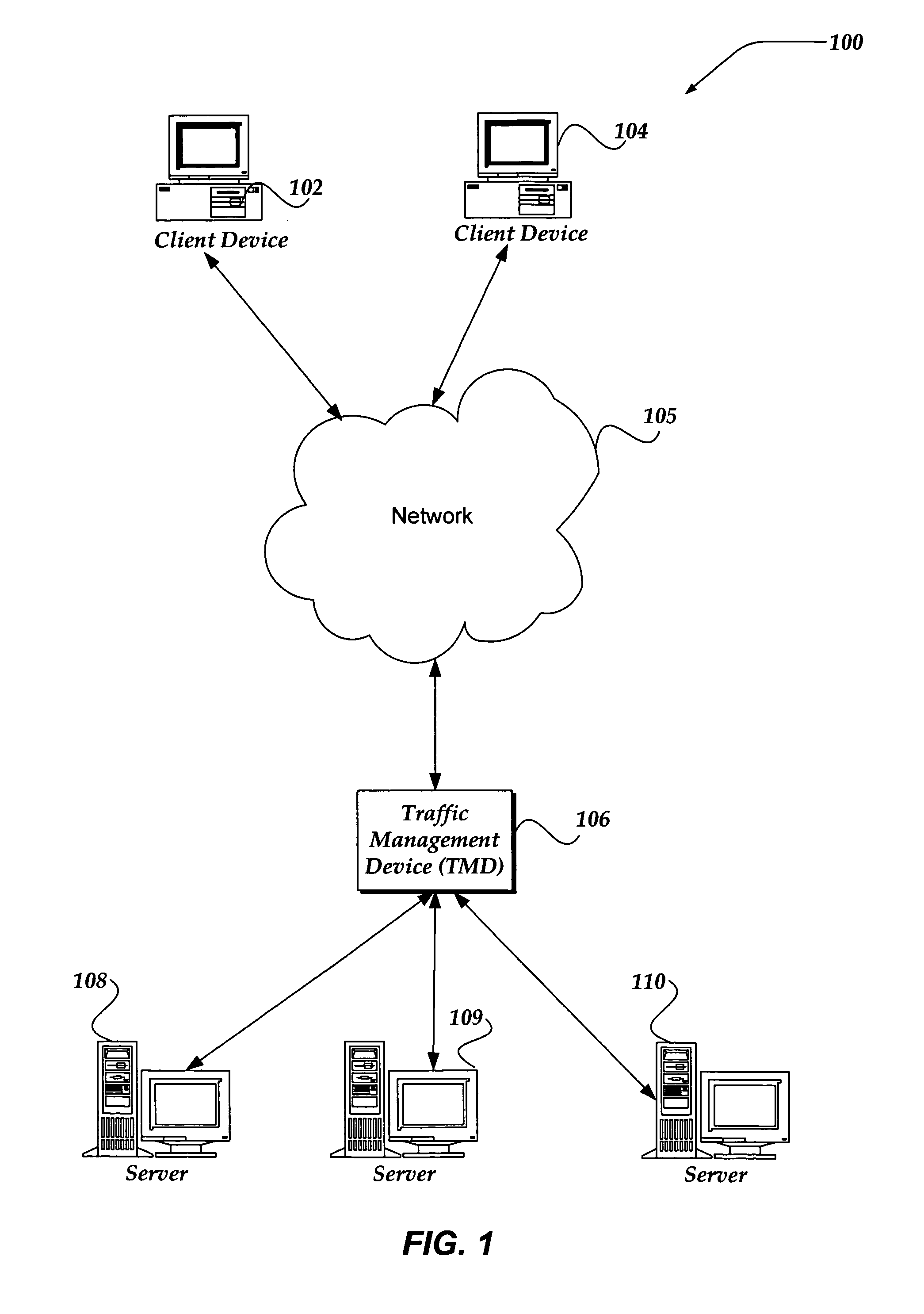
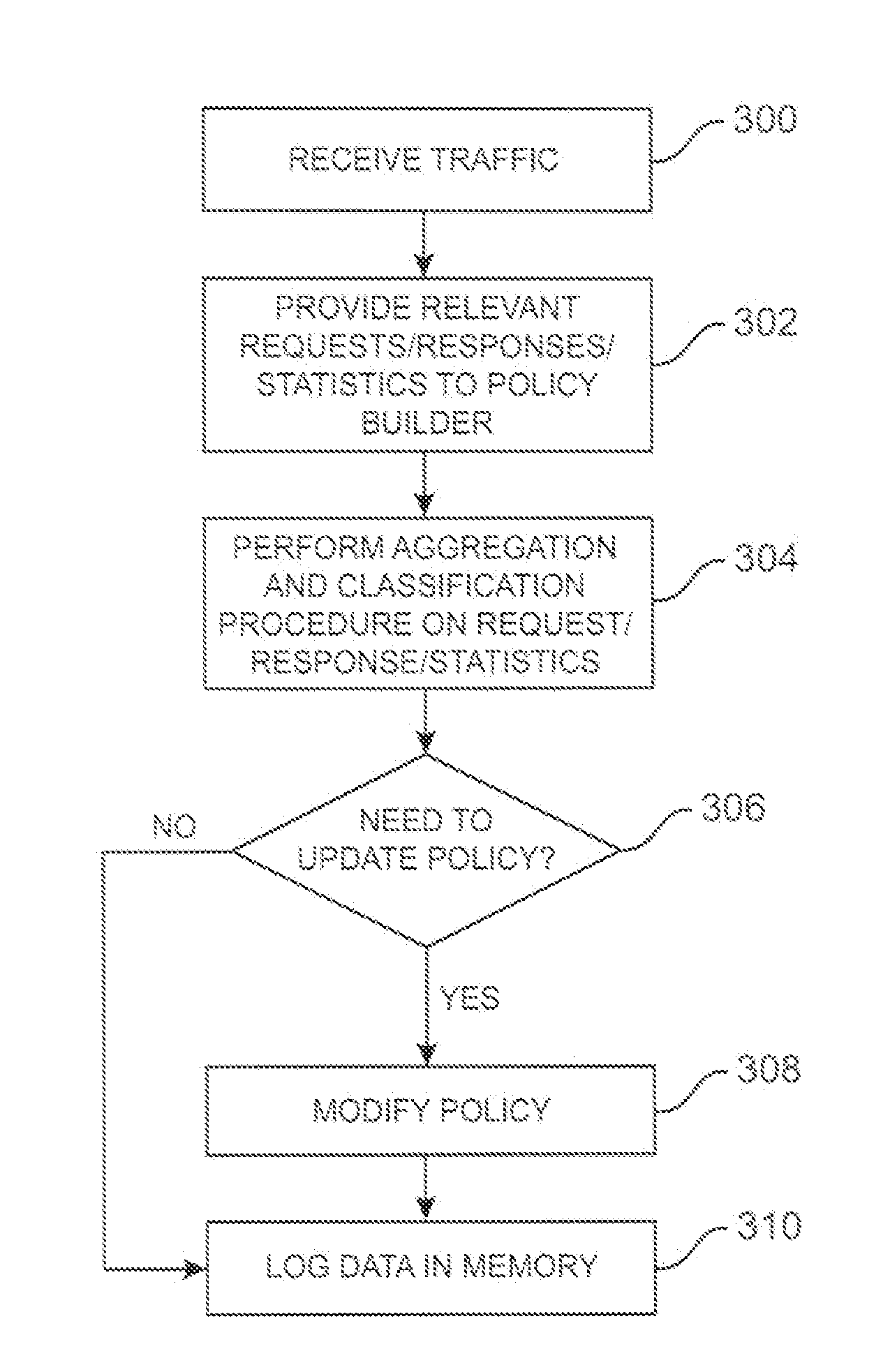
A system, method and machine readable medium for automated policy building in a policy module of a network traffic management device is disclosed. Parsed network traffic data is received at a policy builder of a network traffic management device. The received network traffic data is analyzed in accordance with one or more threshold conditions specified by a user, via a user interface, for an existing policy. The existing policy is modified by the policy builder if the one or more threshold conditions for the network traffic have been met.
Owner:F5 NETWORKS INC
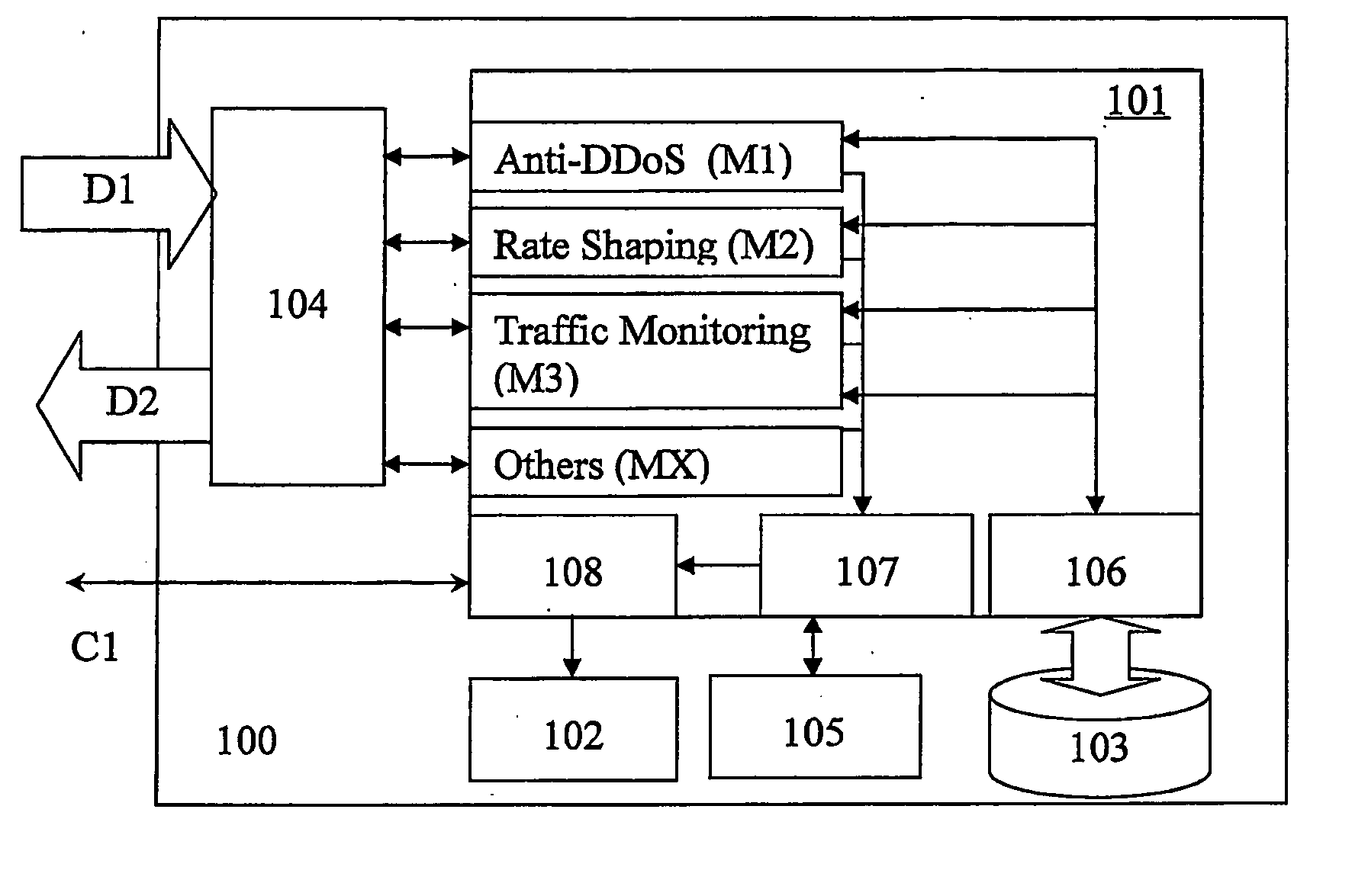
Network traffic management system with floating point sorter
InactiveUS7362765B1Minimal impactBig amount of dataData switching by path configurationStore-and-forward switching systemsTraffic capacityClass of service
A technique to implement a network traffic management system with an integrated multidimensional floating point sorter (306) is to store data such that it may be retrieved in a sorted fashion. Entries are stored (407) into a memory according to time stamp value, represented in a floating point format, and the time stamp value is divided (412) into at least two portions, exponent and mantissa. The memory is organized as a pointer memory (505, 508, 513, and 520). An integrated multidimensional floating point sorter may be implemented using integrated circuit technology using one or more integrated circuits (306). These integrated circuits may be used in management of network traffic, and provides quality of service (QoS) or class of service (CoS) control.
Owner:DINOCHIP
Flow control device, flow control method, network flow management system, and network flow management method
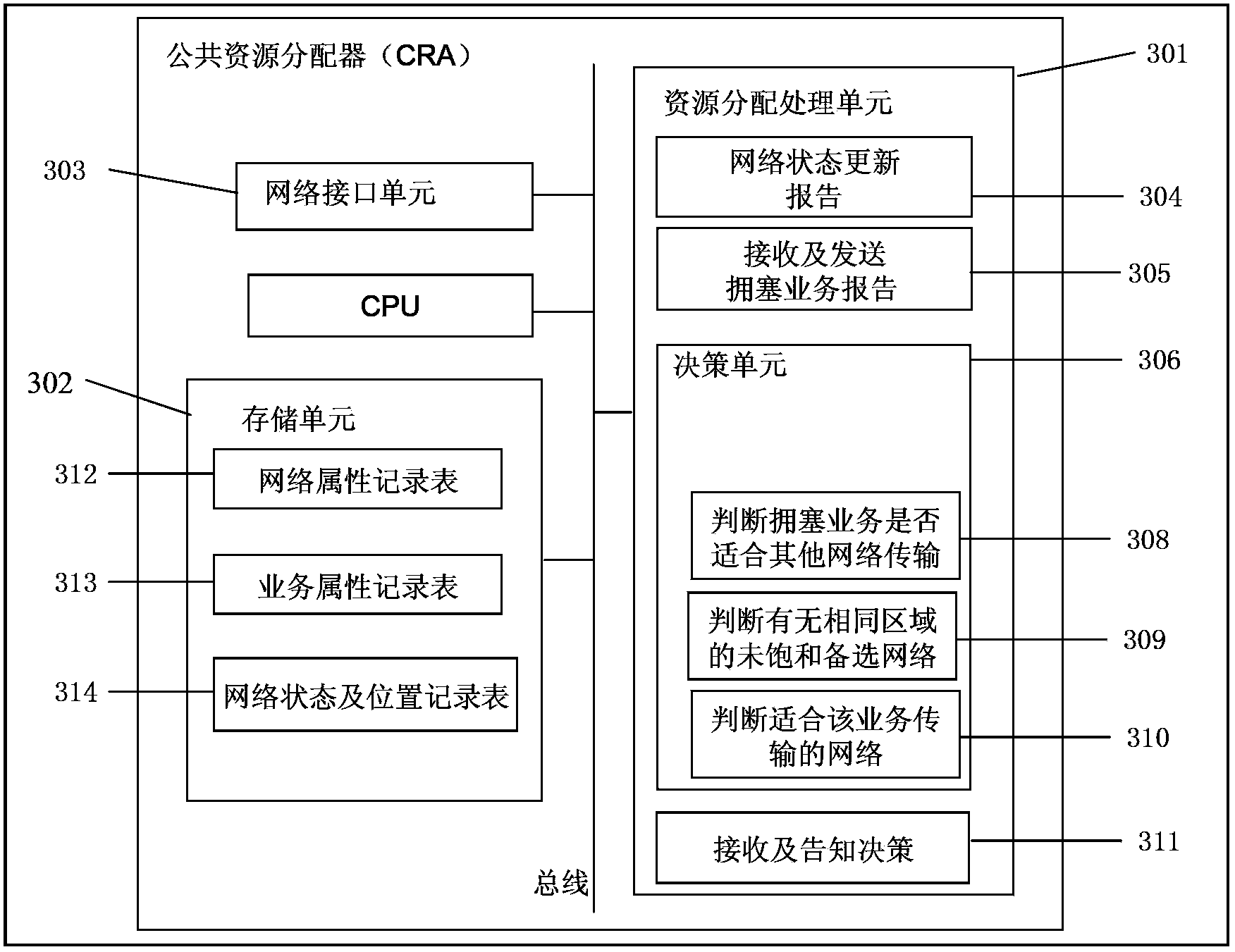
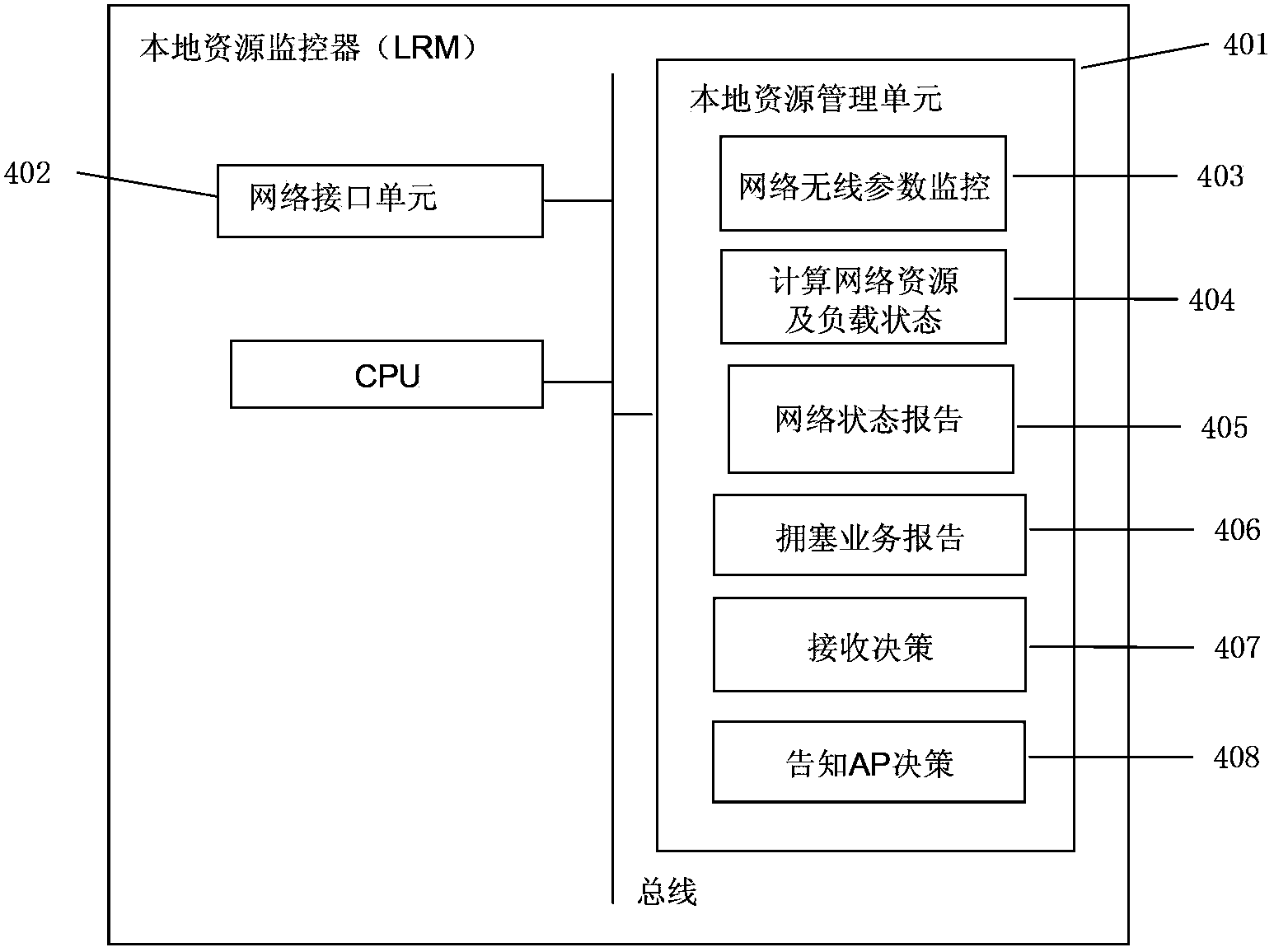
InactiveCN103458466ATransmission optimizationIncrease profitNetwork traffic/resource managementTraffic capacityHeterogeneous network
The invention provides a flow control device, a flow control method, a network flow management system and a network flow management method in order to effectively reduce user blocking rate and improve utilization of each network in a heterogeneous network. The flow control device comprises a receiving unit, a judging unit and a distributing unit, wherein the receiving unit receives network status information and network congestion information, the network status information comprises multiple network types between a base station and terminals and a service type requested by a user, the network congestion information shows whether the base station and the terminals congest or not, the judging unit judges whether the service type requested by the user is suitable for other network transmission in user's area or not under the condition that the network congestion information shows current network congestion of the service requested by the user, and from the other networks which are judged out by the judging unit and suitable for transmission, the distributing unit selects a certain network as an alternative target network to replace the current network.
Owner:HITACHI LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com