Patents
Literature
34 results about "Accessible computing" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
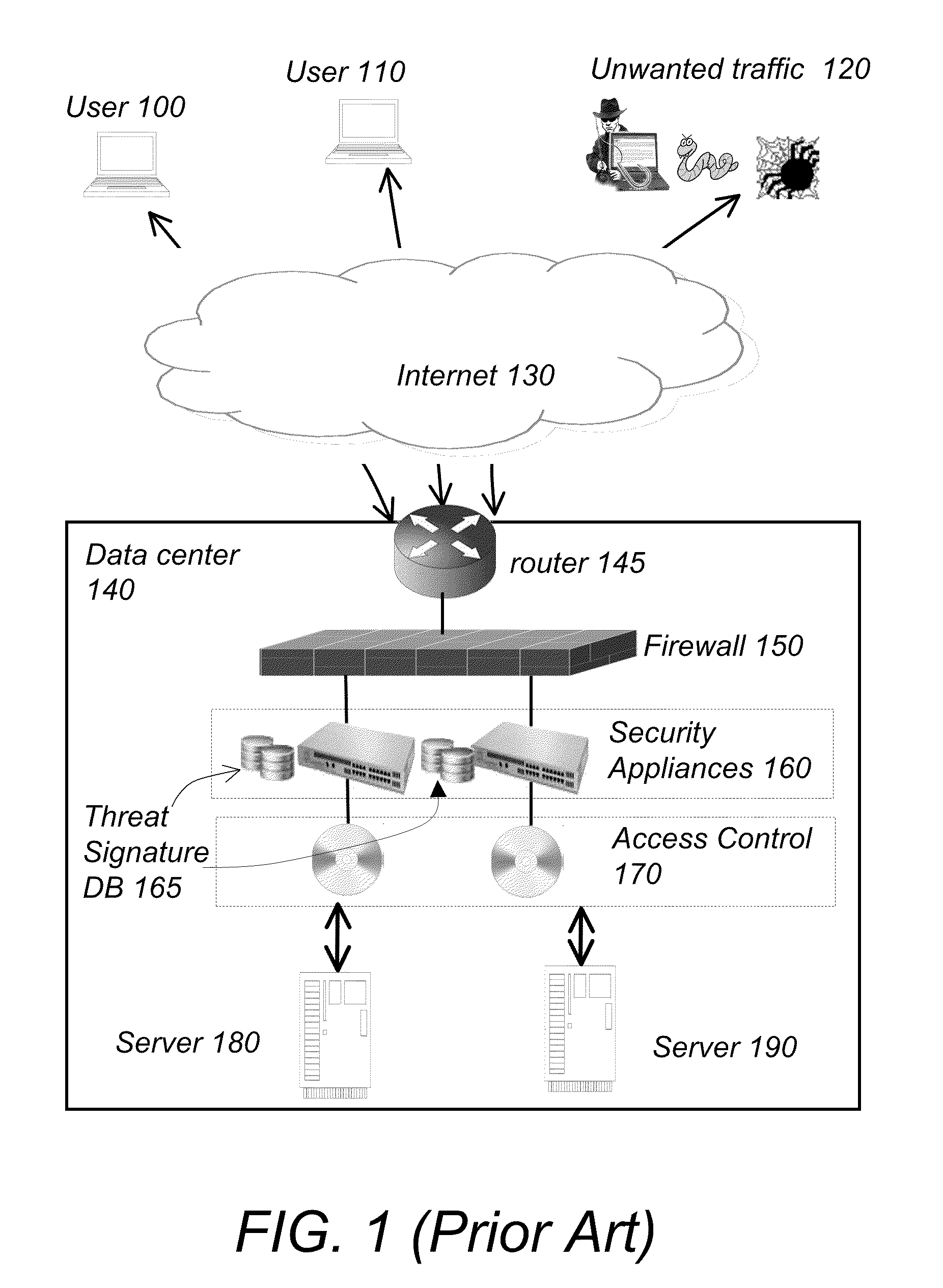
In human–computer interaction, computer accessibility (also known as accessible computing) refers to the accessibility of a computer system to all people, regardless of disability type or severity of impairment.
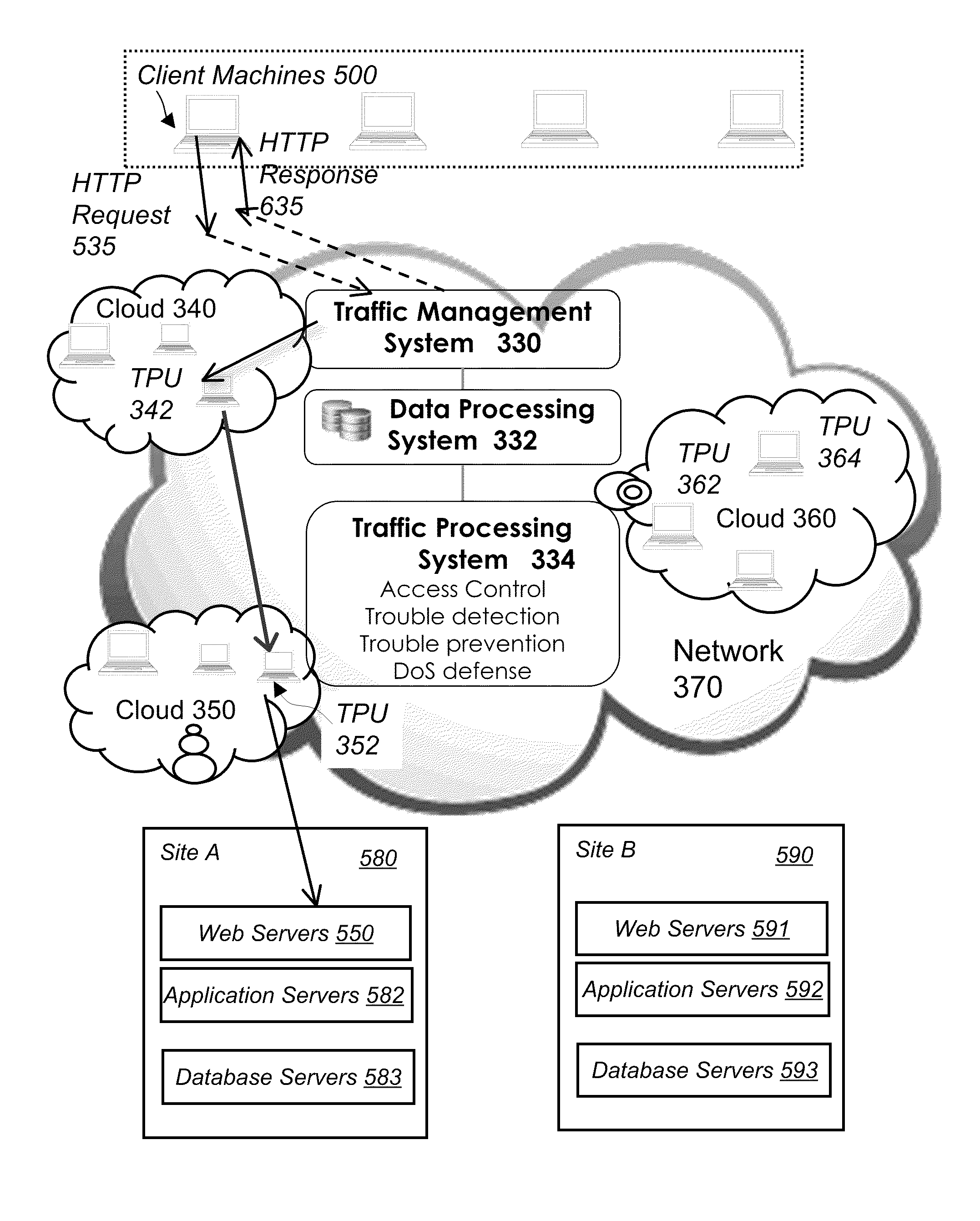
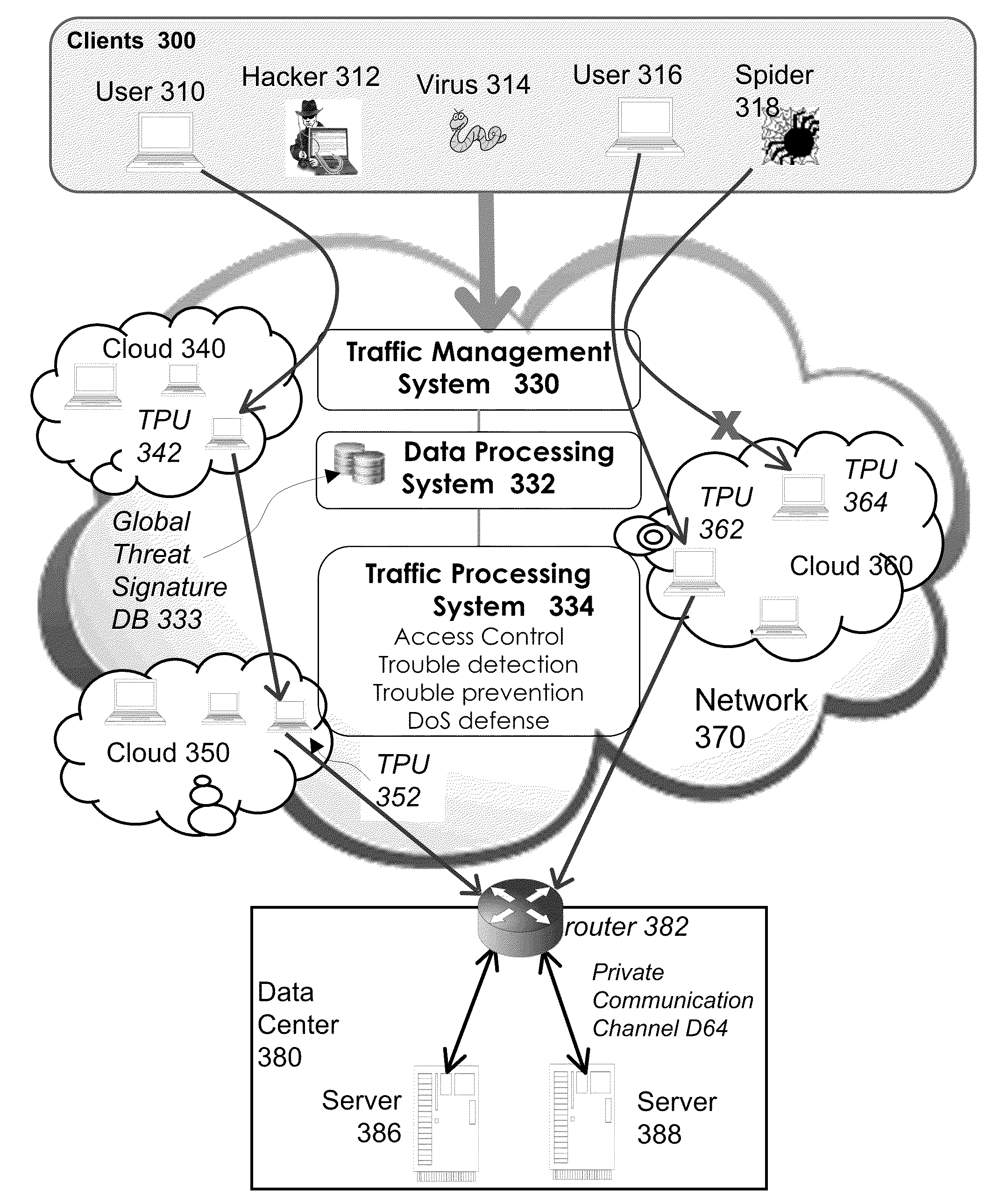
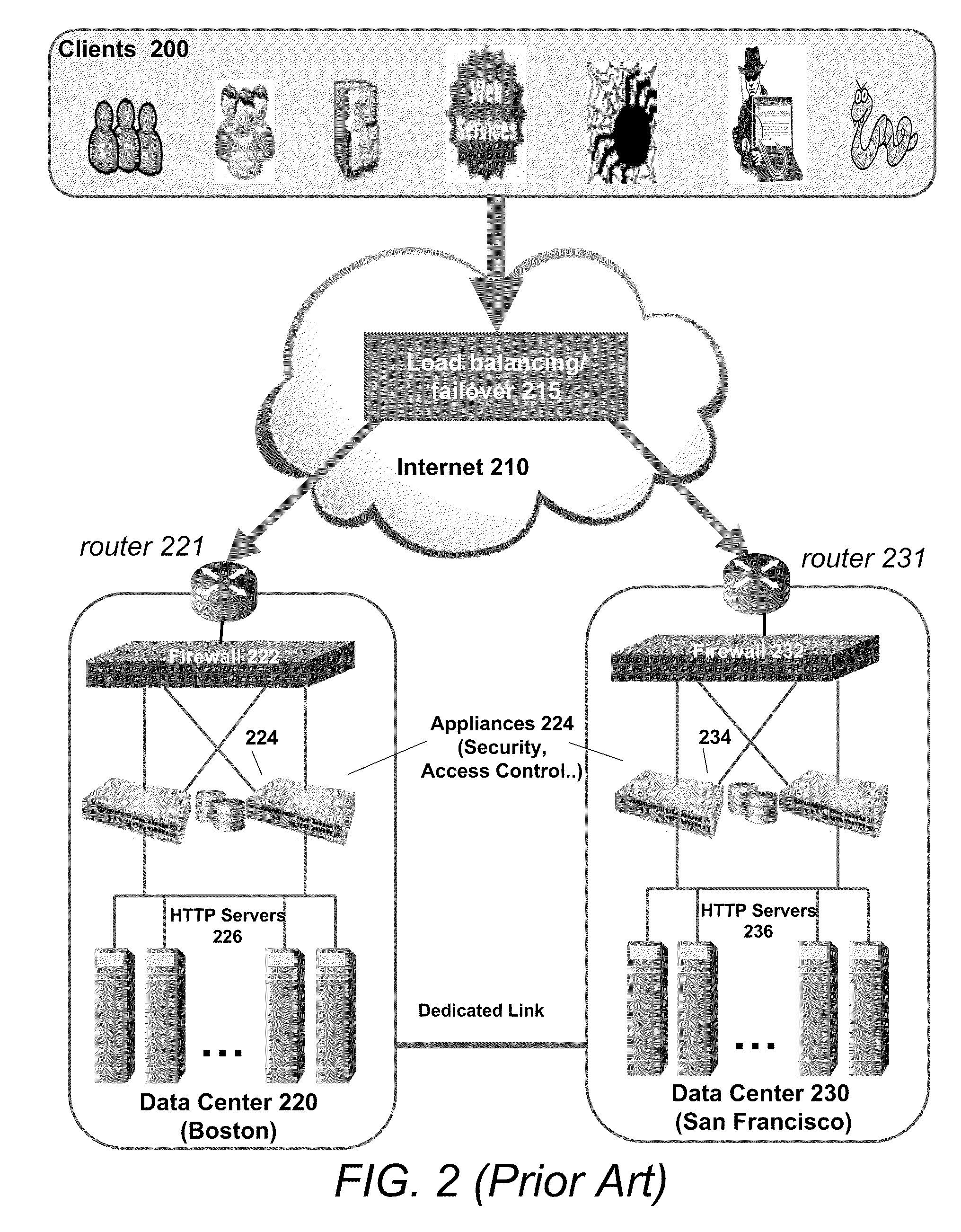
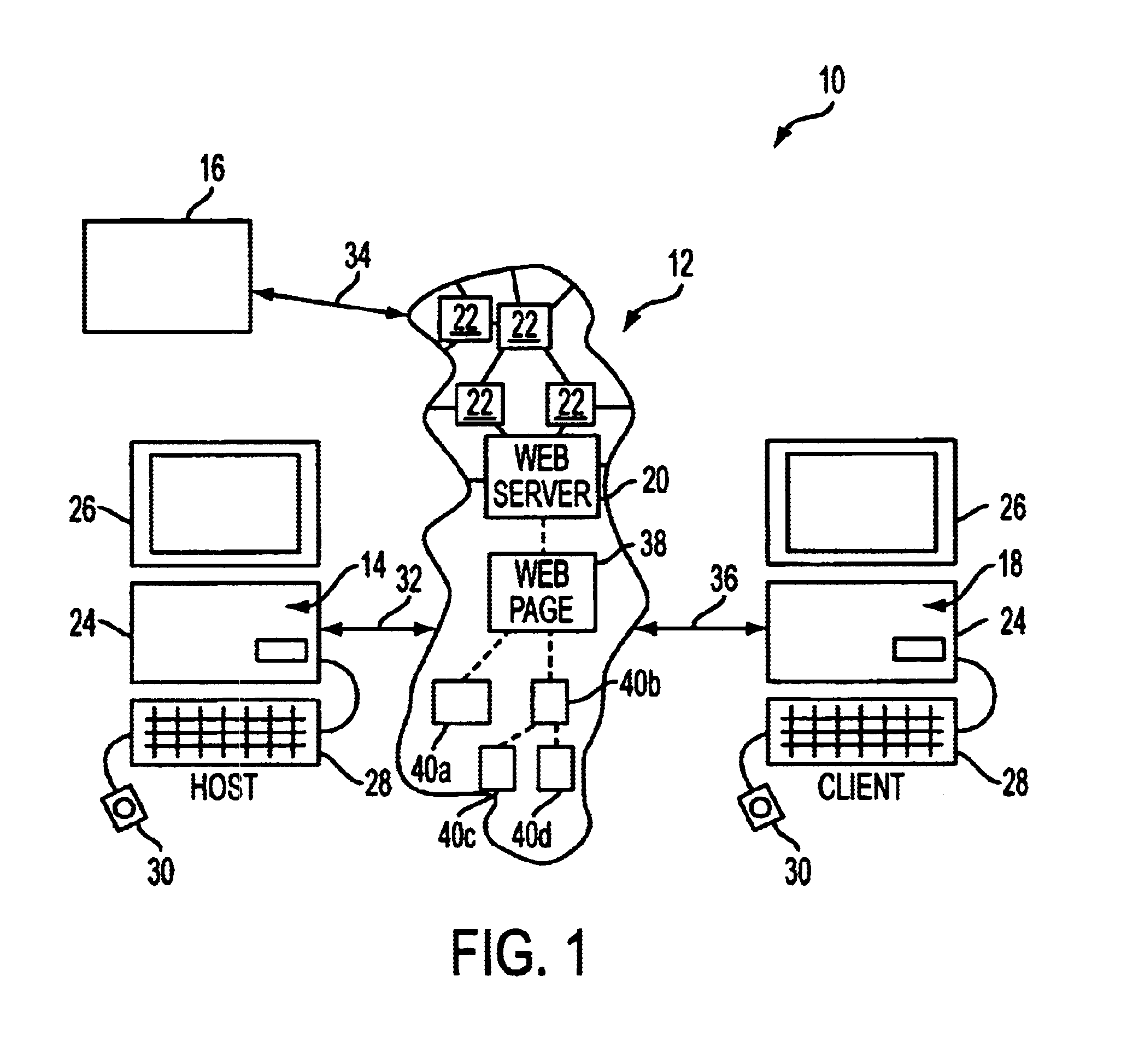
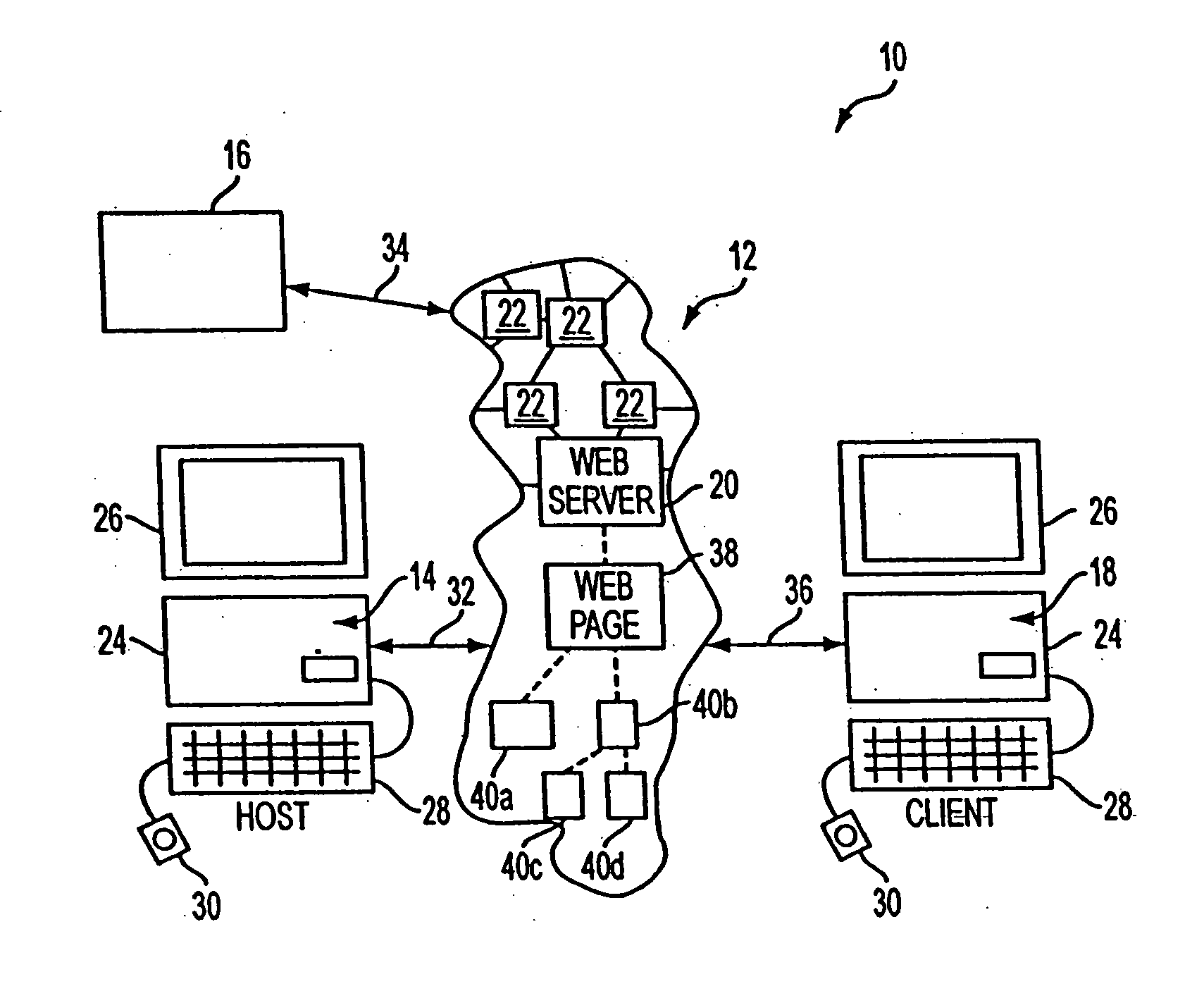
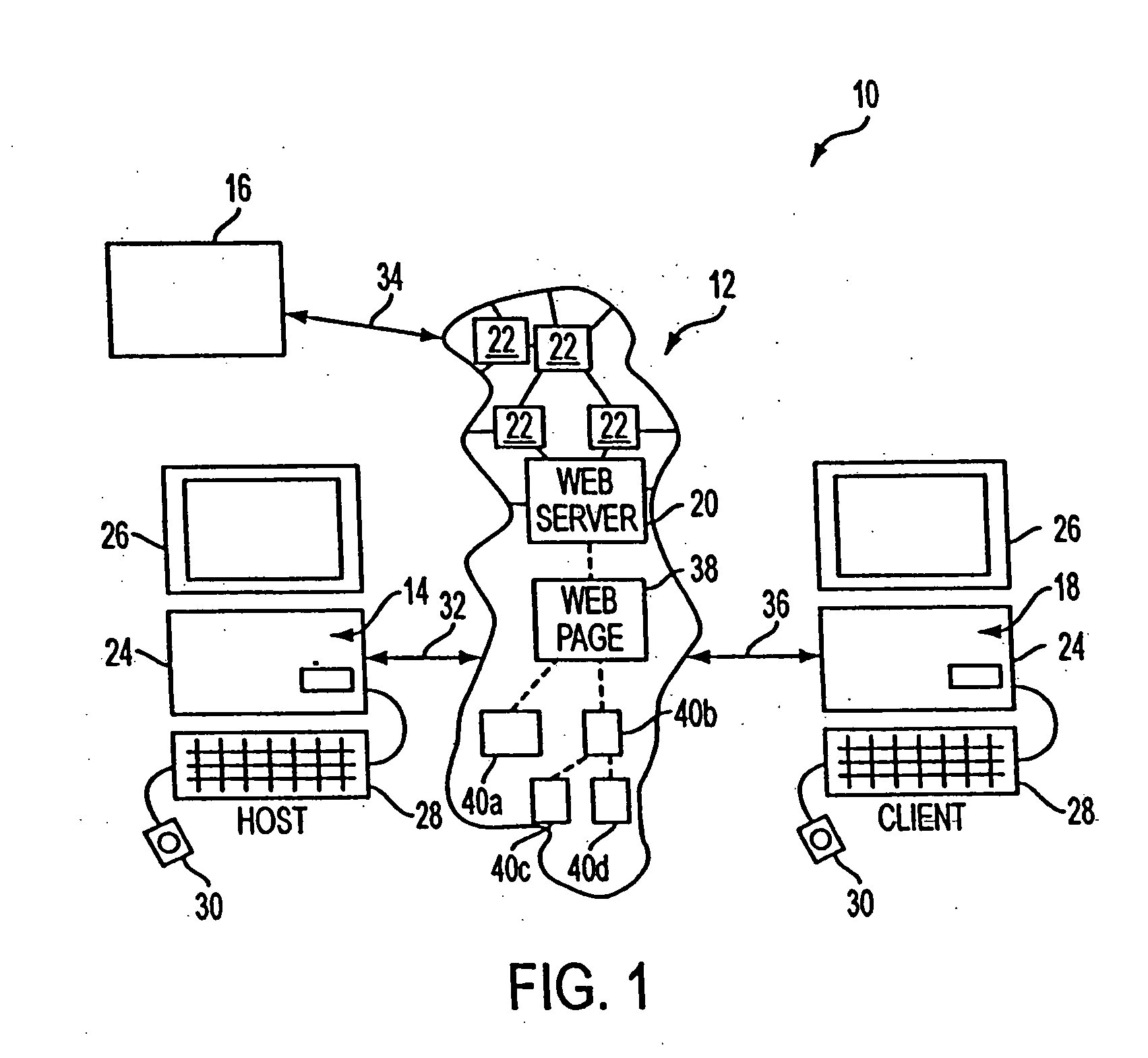
System and method for network traffic management and load balancing
InactiveUS20100223364A1Improve application performanceImprove availabilityMultiple digital computer combinationsLocation information based serviceTraffic capacityFailover
A method for providing load balancing and failover among a set of computing nodes running a network accessible computer service includes providing a computer service that is hosted at one or more servers comprised in a set of computing nodes and is accessible to clients via a first network. Providing a second network including a plurality of traffic processing nodes and load balancing means. The load balancing means is configured to provide load balancing among the set of computing nodes running the computer service. Providing means for redirecting network traffic comprising client requests to access the computer service from the first network to the second network. Providing means for selecting a traffic processing node of the second network for receiving the redirected network traffic comprising the client requests to access the computer service and redirecting the network traffic to the traffic processing node via the means for redirecting network traffic. For every client request for access to the computer service, determining an optimal computing node among the set of computing nodes running the computer service by the traffic processing node via the load balancing means, and then routing the client request to the optimal computing node by the traffic processing node via the second network.
Owner:YOTTAA
System and method for access management and security protection for network accessible computer services
InactiveUS20100251329A1Detection problemGrows and shrinks capacity and bandwidth capacityMemory loss protectionError detection/correctionTraffic capacityService provision
A method for providing access management and security protection to a computer service includes providing a computer service that is hosted at one or more servers and is accessible to clients via a first network, providing a second network that includes a plurality of traffic processing nodes and providing means for redirecting network traffic from the first network to the second network. Next, redirecting network traffic targeted to access the computer service via the first network to a traffic processing node of the second network via the means for redirecting network traffic. Next, inspecting and processing the redirected network traffic by the traffic processing node and then routing only redirected network traffic that has been inspected, processed and approved by the traffic processing node to access the computer service via the second network.
Owner:YOTTAA
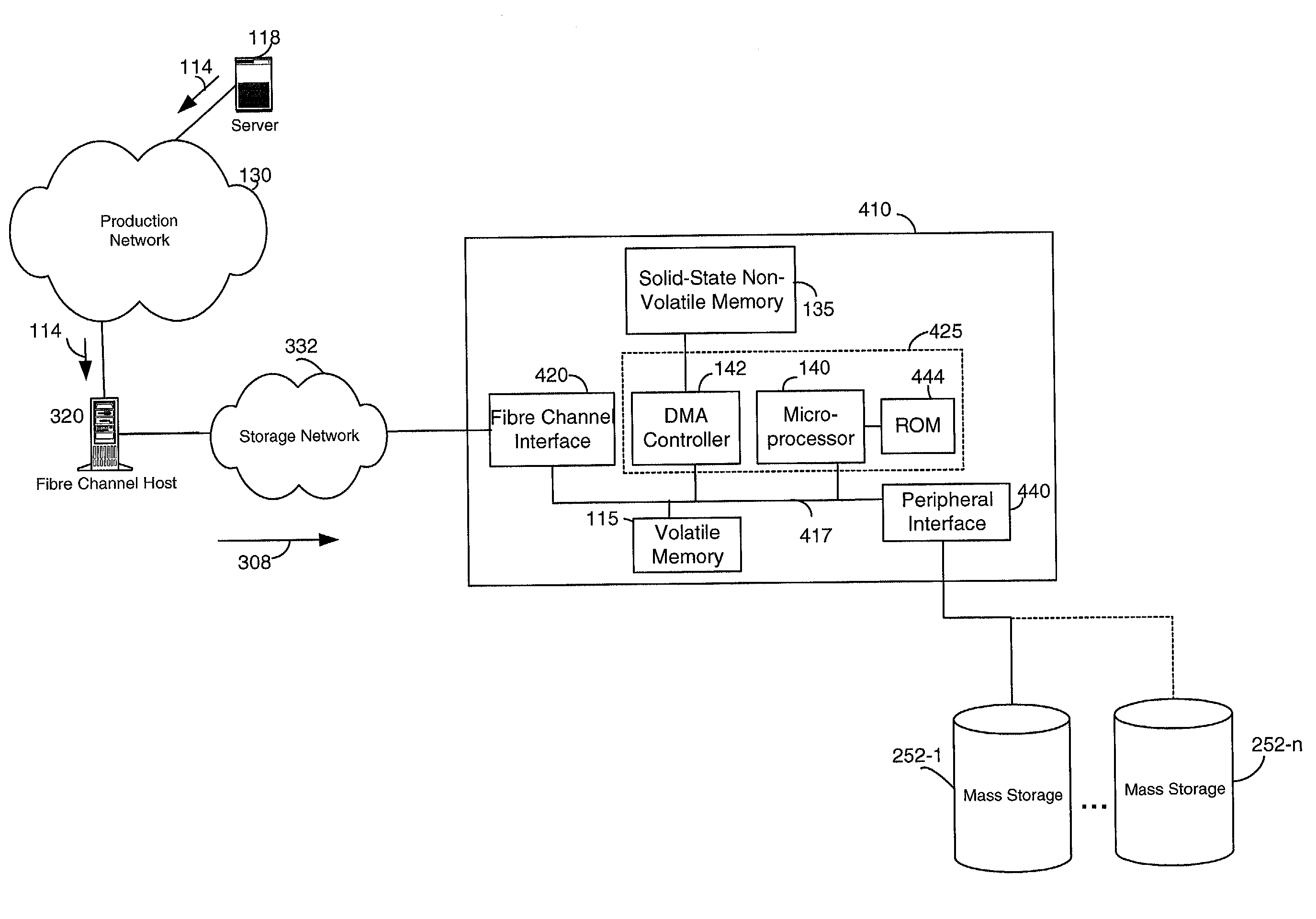
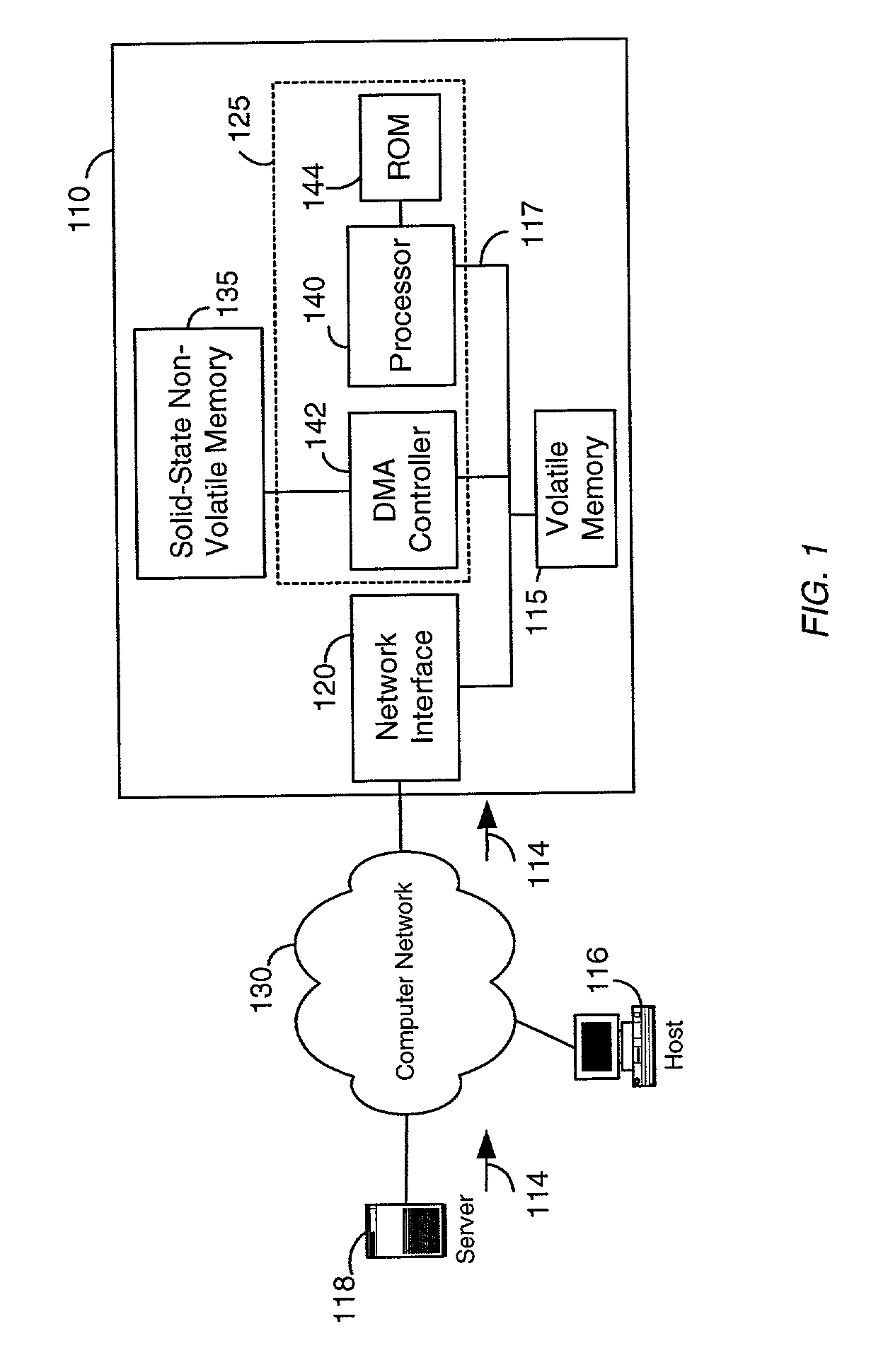
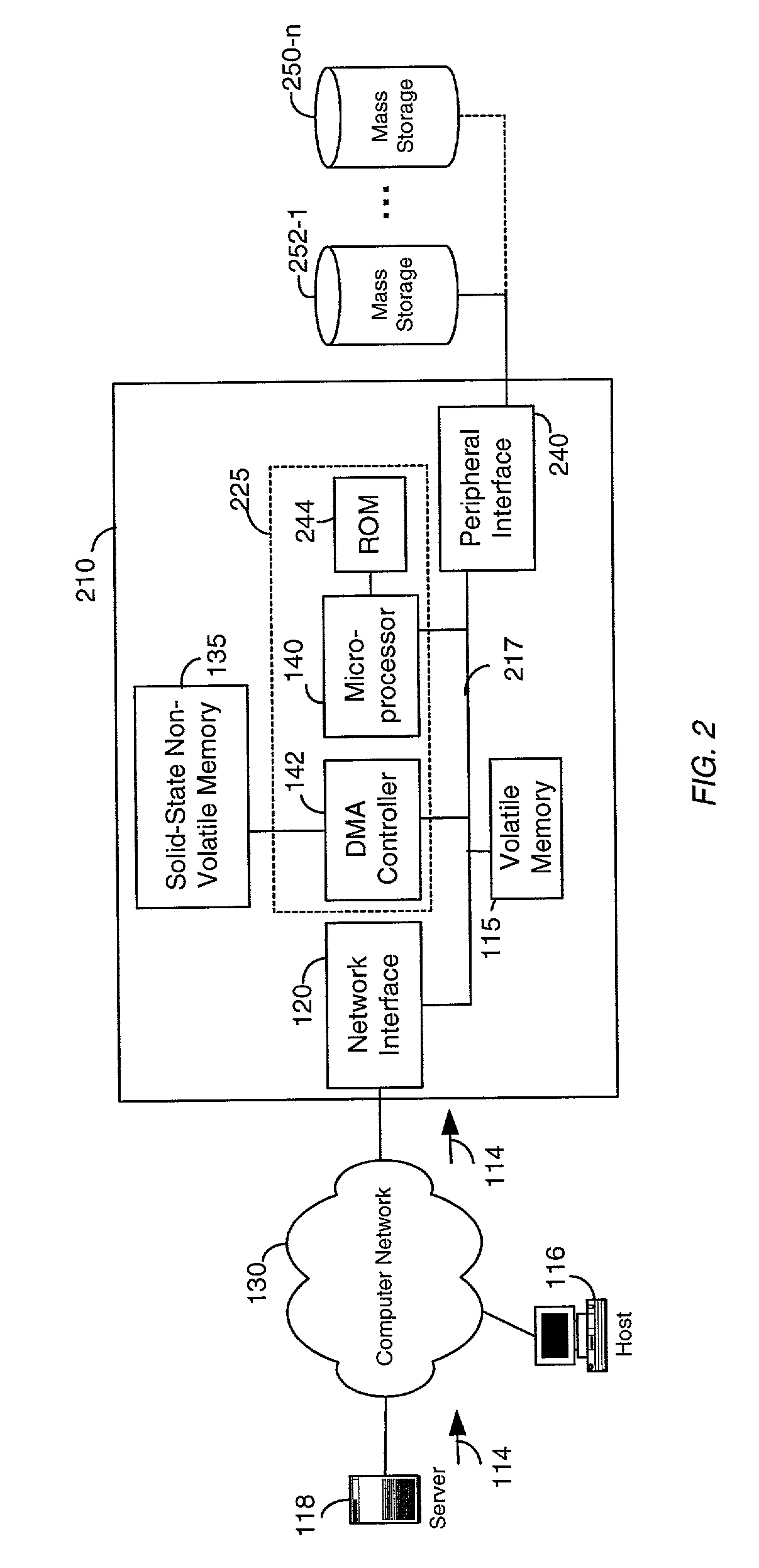
Network storage device having solid-state non-volatile memory
InactiveUS6981070B1Great access timeSmall currentMemory architecture accessing/allocationInput/output to record carriersMass storageRAID
A network storage device. In one embodiment, the network storage device of the present invention uses solid-state non-volatile memory (e.g., flash-memory) as a storage medium, and has at least one interface configured for coupling to a computer network. The network storage device of the present invention is accessible to client(s) and / or server(s) of the computer network, and uses solid-state non-volatile memory to store data received therefrom. The network storage device may also be configured to include a memory for caching data to be written to the solid-state non-volatile memory. In order to provide additional storage, the network storage device may also include a peripheral interface or another network interface for coupling to a mass storage device (e.g., a RAID system), and / or another network interface for coupling to a network of mass storage devices. The network storage device may be a stand-alone unit, or may be implemented as part of a network server, or as part of a mass storage device.
Owner:BITMICRO LLC
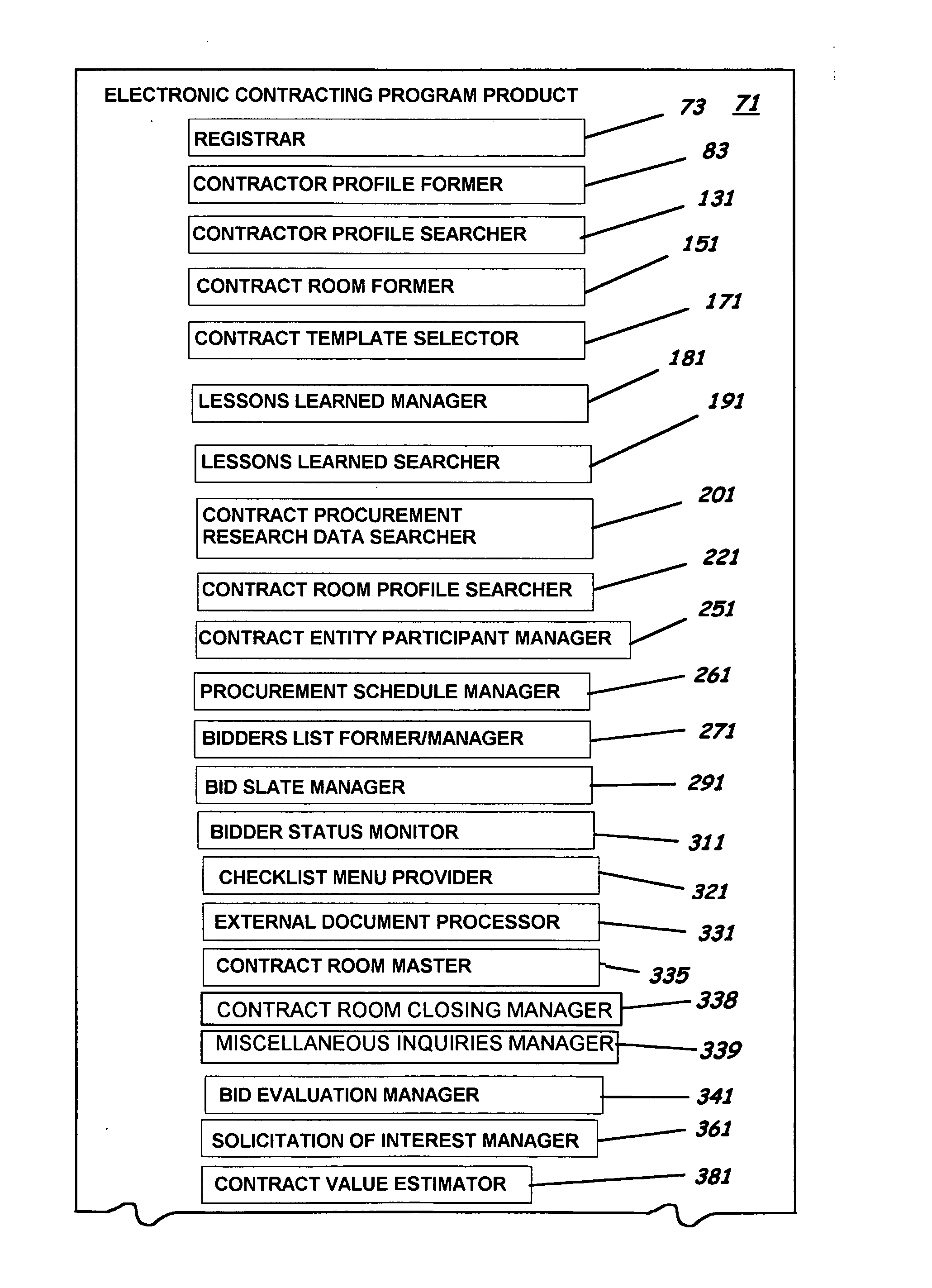
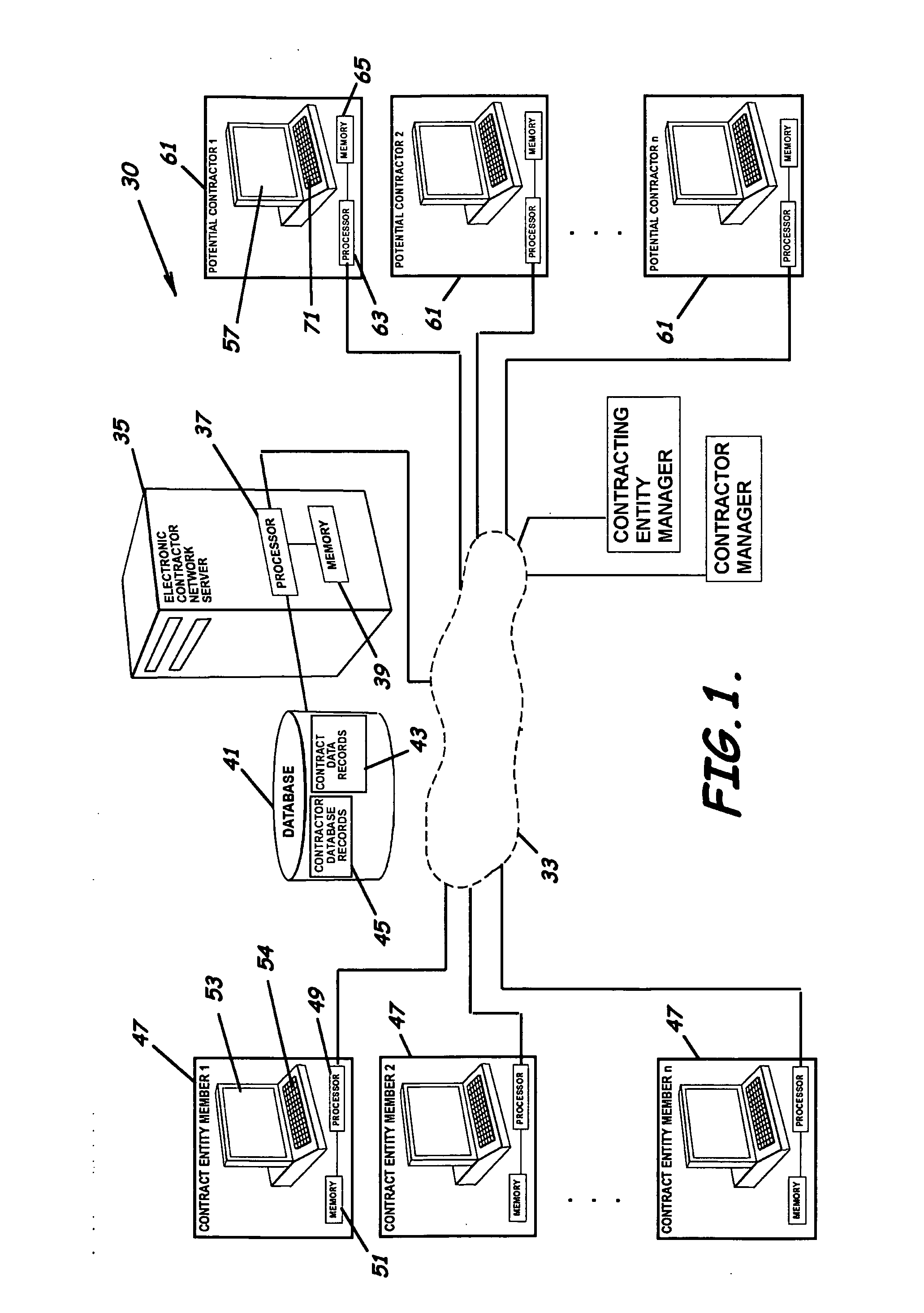
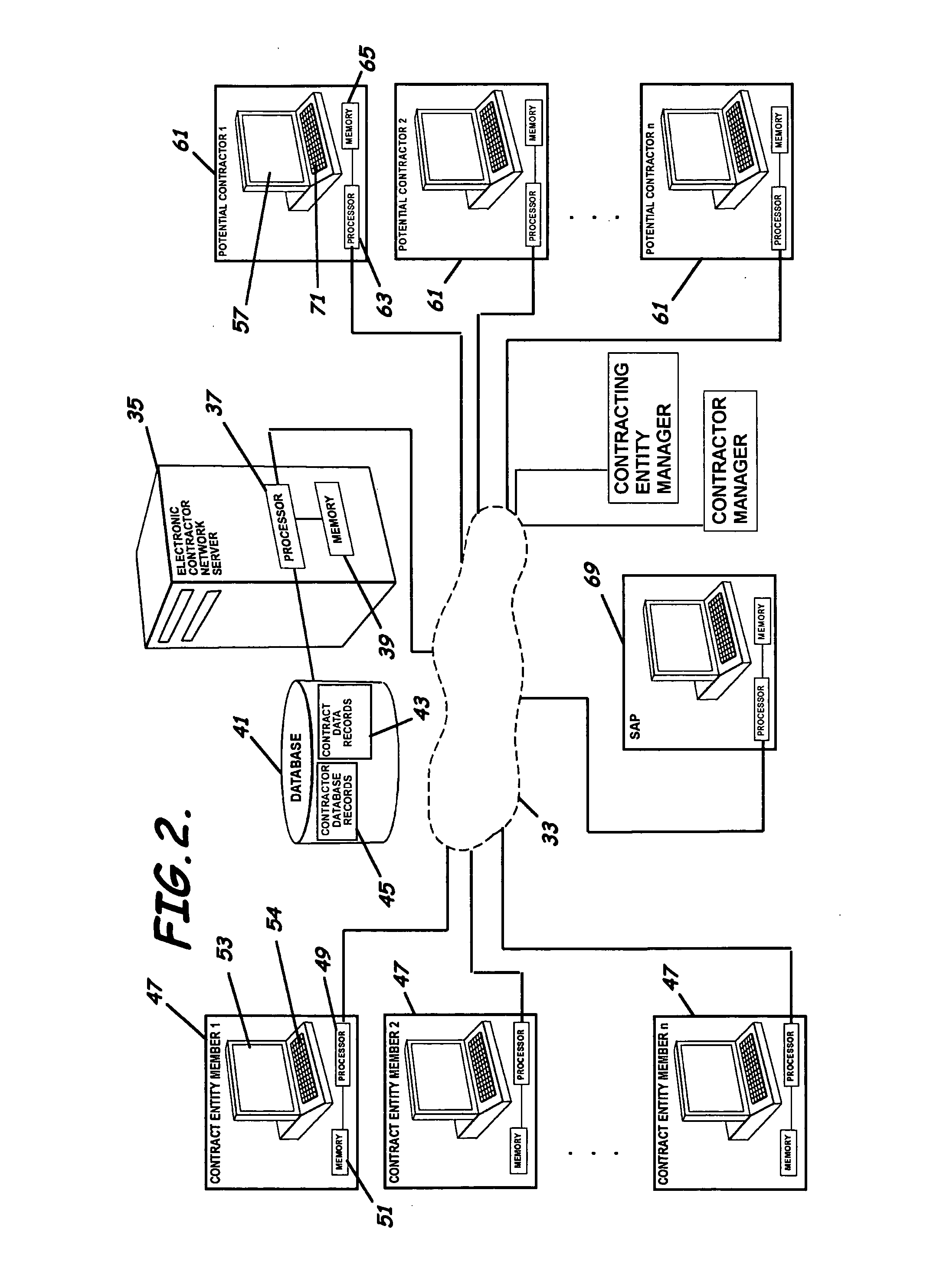
System, program product, and methods for managing contract procurement
InactiveUS20070016514A1Lower requirementReduce delaysFinanceResourcesNetwork serviceDistributed computing
A system to facilitate contract procurement and contract management through an online contract procurement and management website over a computer network, program product, and associated methods are provided. The system includes an electronic contracting network server accessible to a computer network, a database accessible to the electronic contracting network server through the computer network, a plurality of plurality of electronic contracting entity member user computers in communication with the electronic contracting network server through the computer network, and a plurality of potential contractor member user computers also in communication with the electronic contracting network server through the computer network. The system also includes an electronic contracting program product stored in the memory of the electronic contracting network server and positioned to perform various contract procurement and contract management functions.
Owner:SAUDI ARABIAN OIL CO
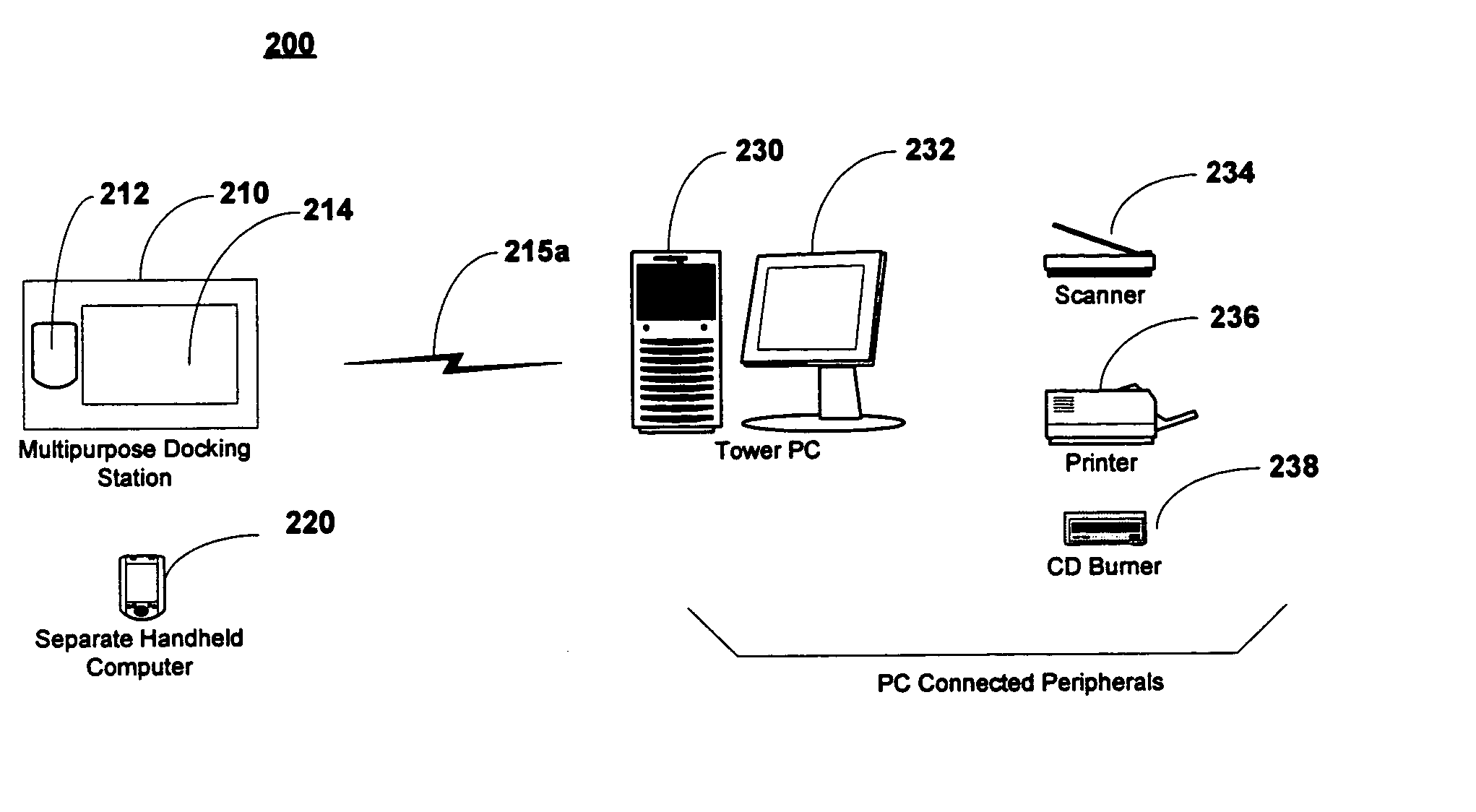
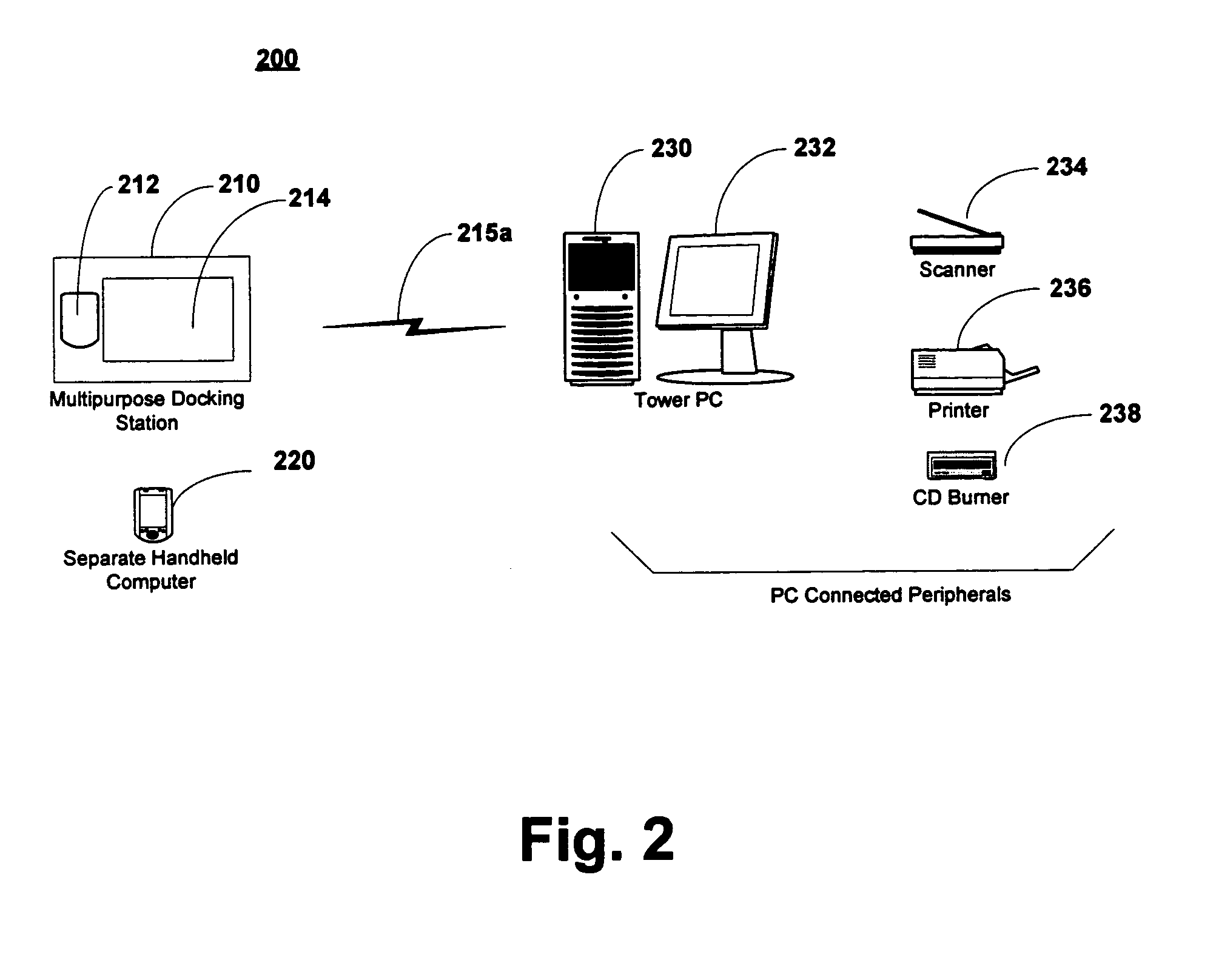
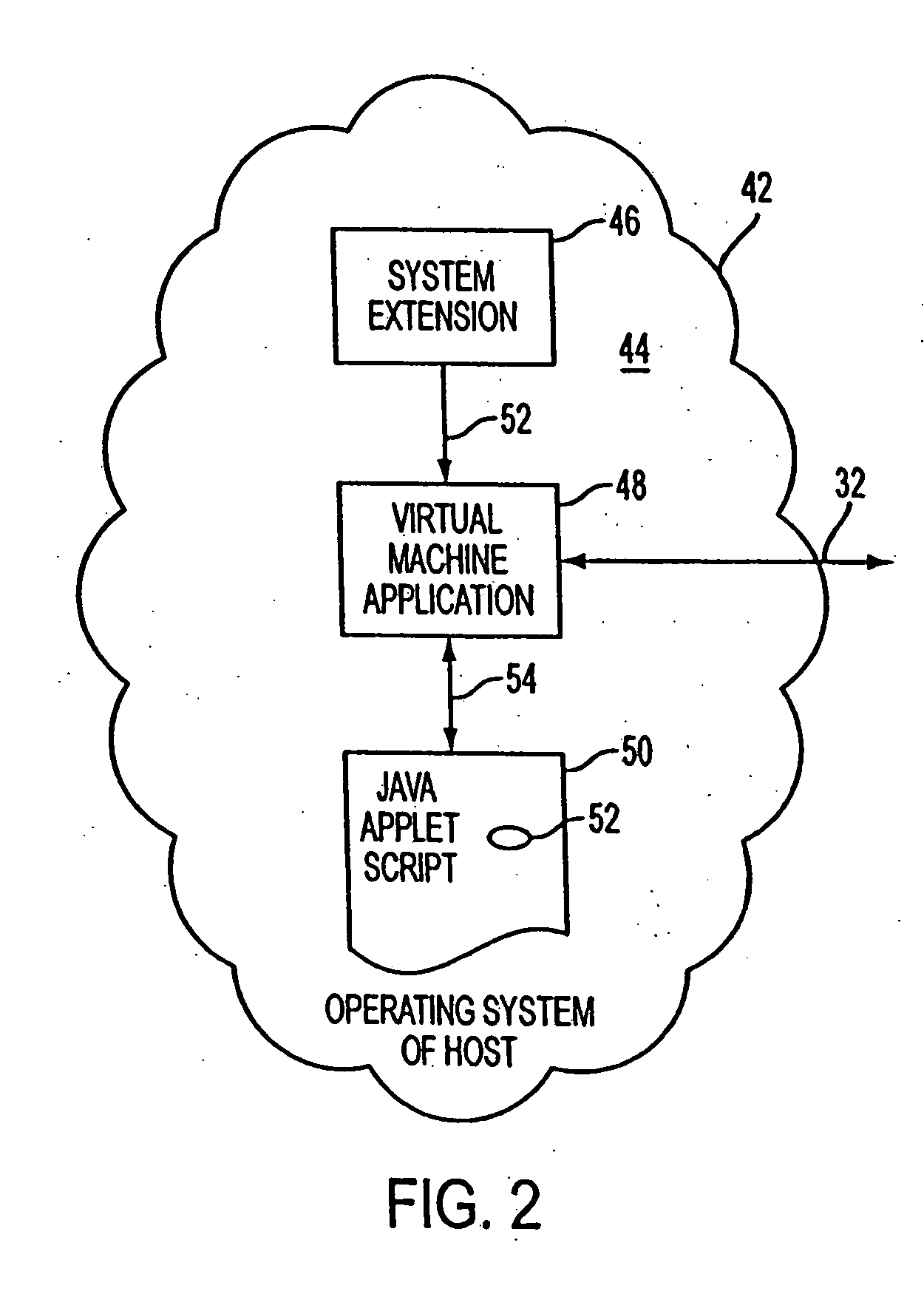
Multipurpose docking apparatus for a mobile computer
InactiveUS20050013103A1Digital data processing detailsElectrical apparatus contructional detailsDocking stationPersonal computer
An multipurpose docking apparatus for mobile or other computers for operation both with and without an installable mobile computer is presented. The multipurpose docking station includes a port for insertion of a handheld or other mobile computer or computer code. Without the mobile computer installed, the multipurpose docking apparatus is functional as a remote display or terminal for a personal computer. When the mobile computer is installed into the installation port, the combination is functional as a fully accessible computing system with the ability to communicate with other computers, peripherals and network interfaces.
Owner:MICROSOFT TECH LICENSING LLC
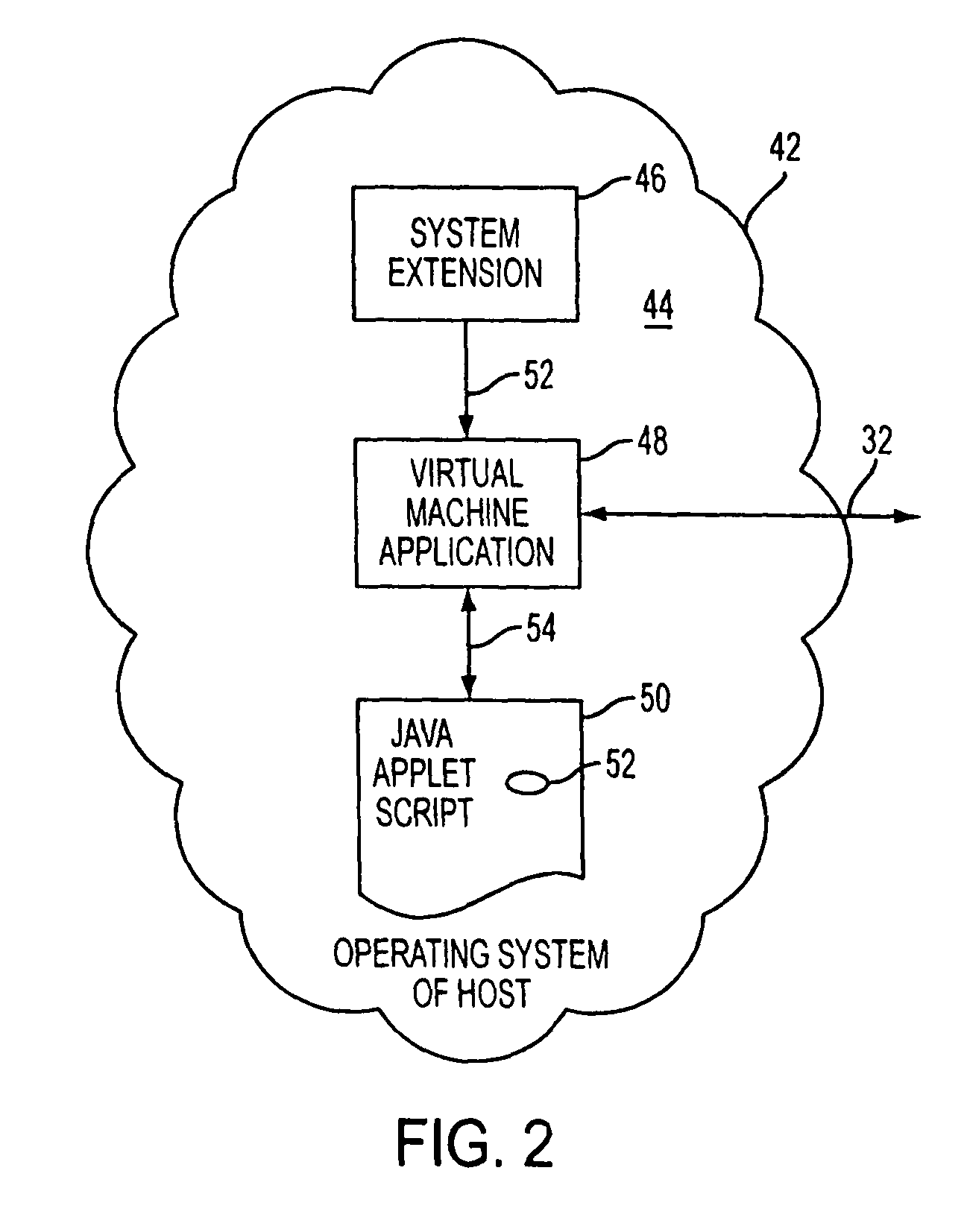
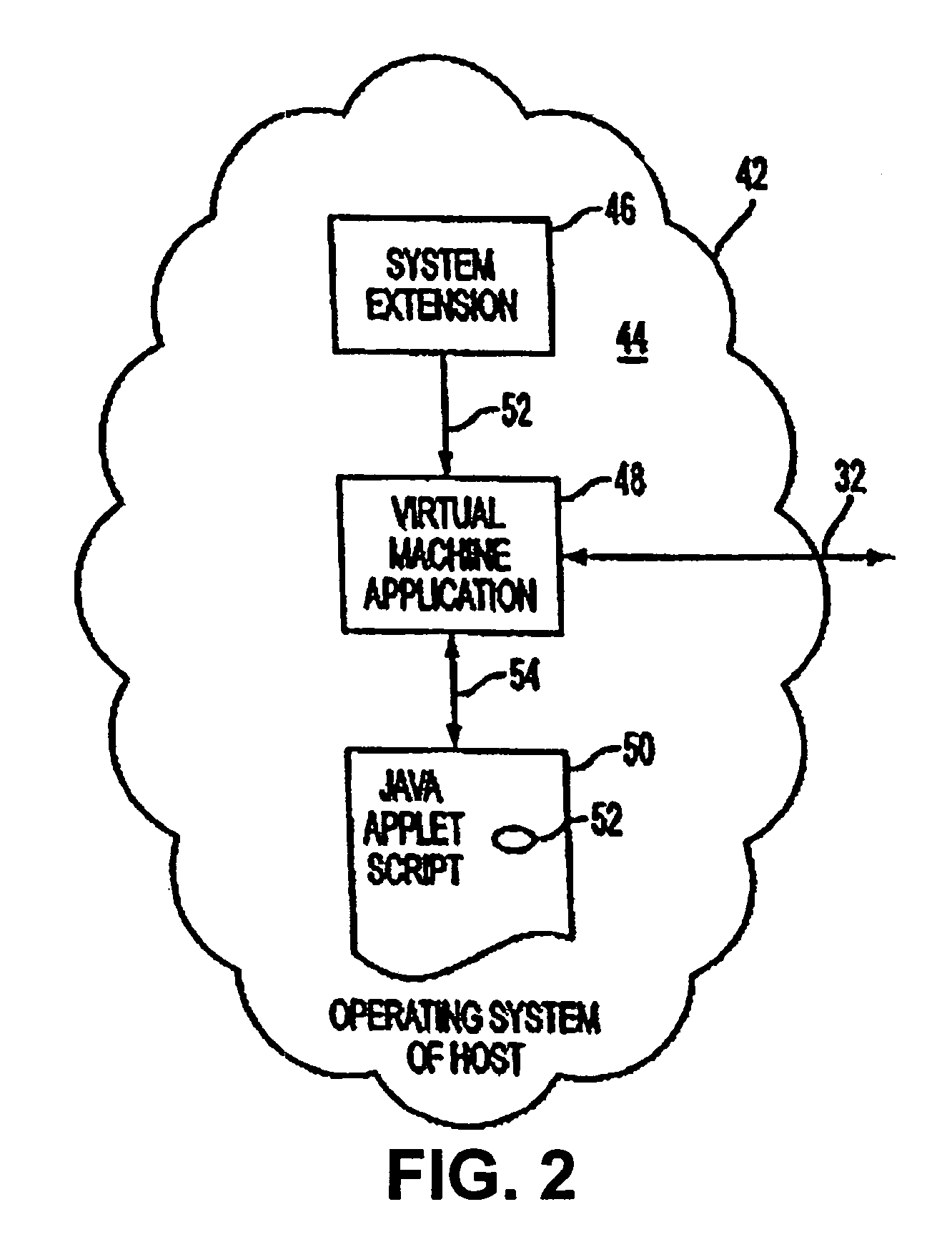
Method and apparatus for computing over a wide area network
InactiveUS7007070B1Strong computing powerMaintain performanceMultiple digital computer combinationsTransmissionNetwork addressingNetwork address
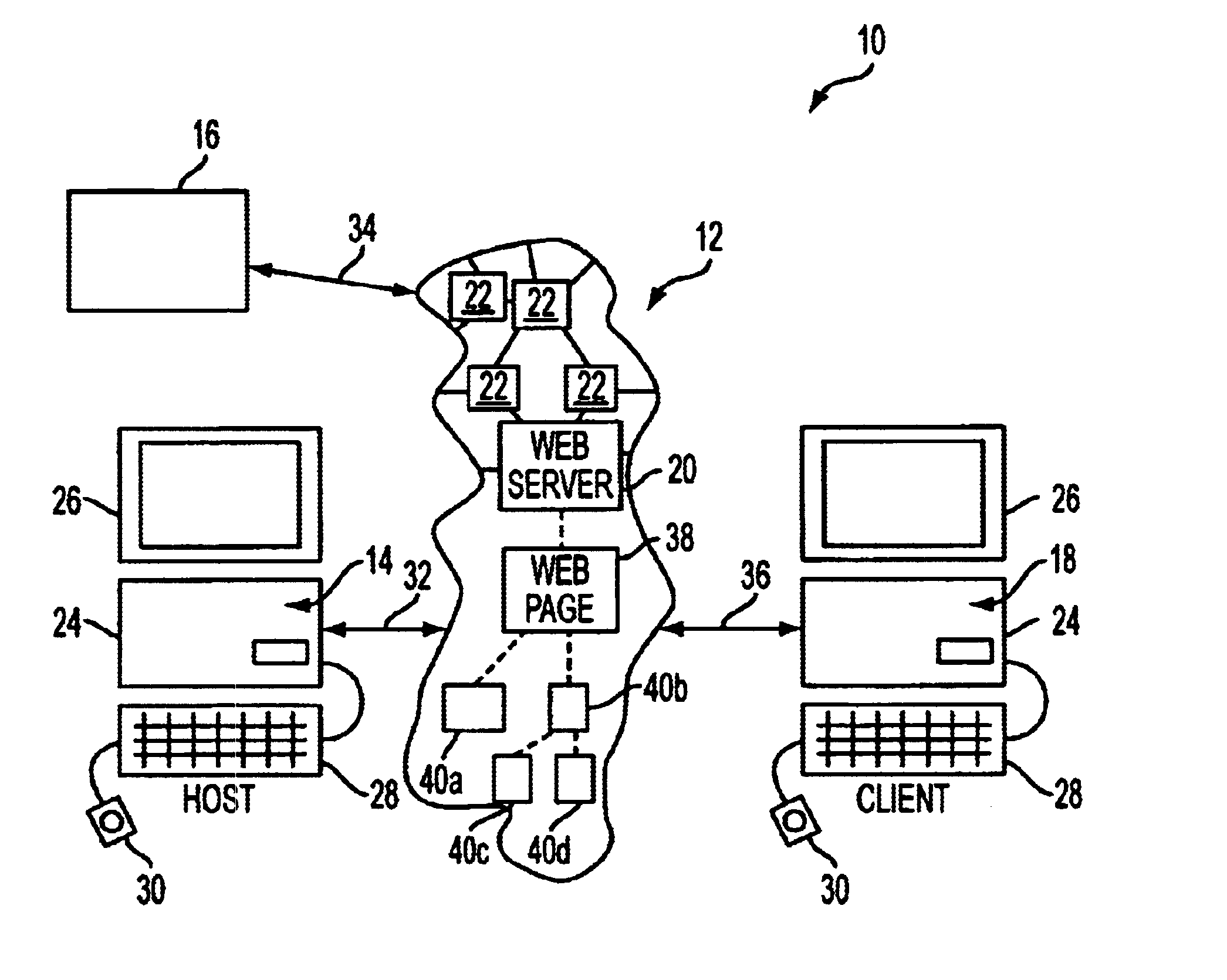
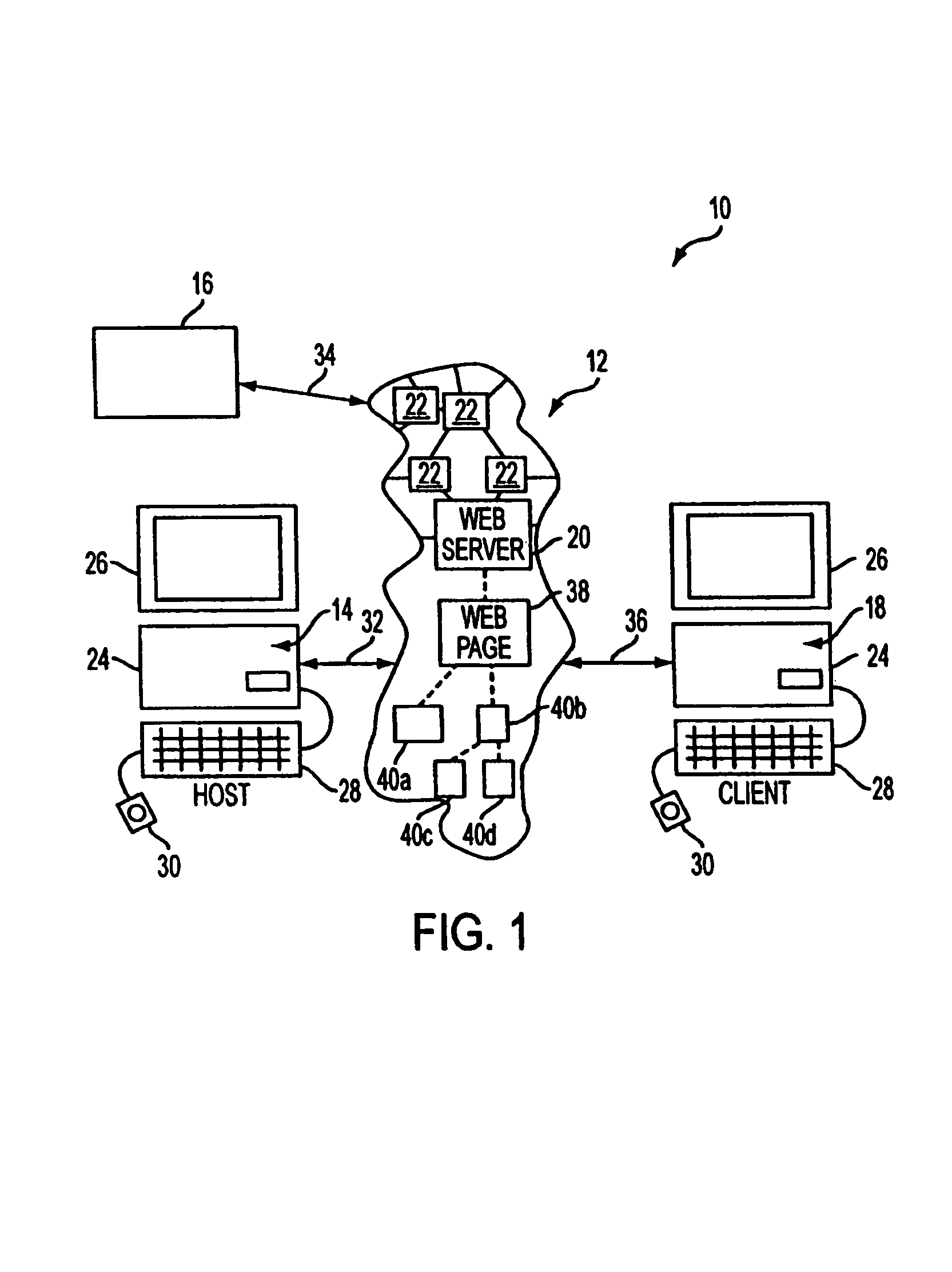
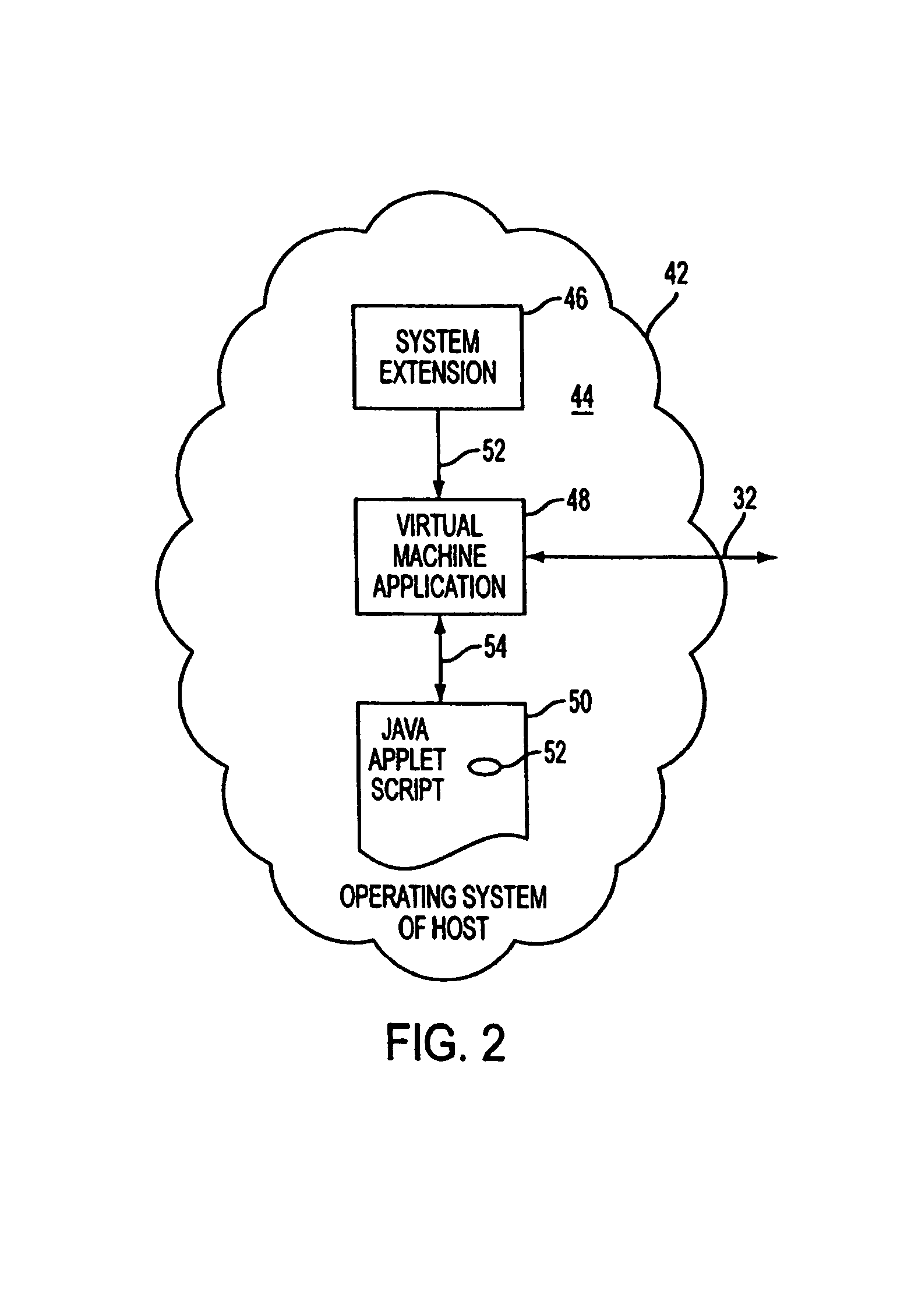
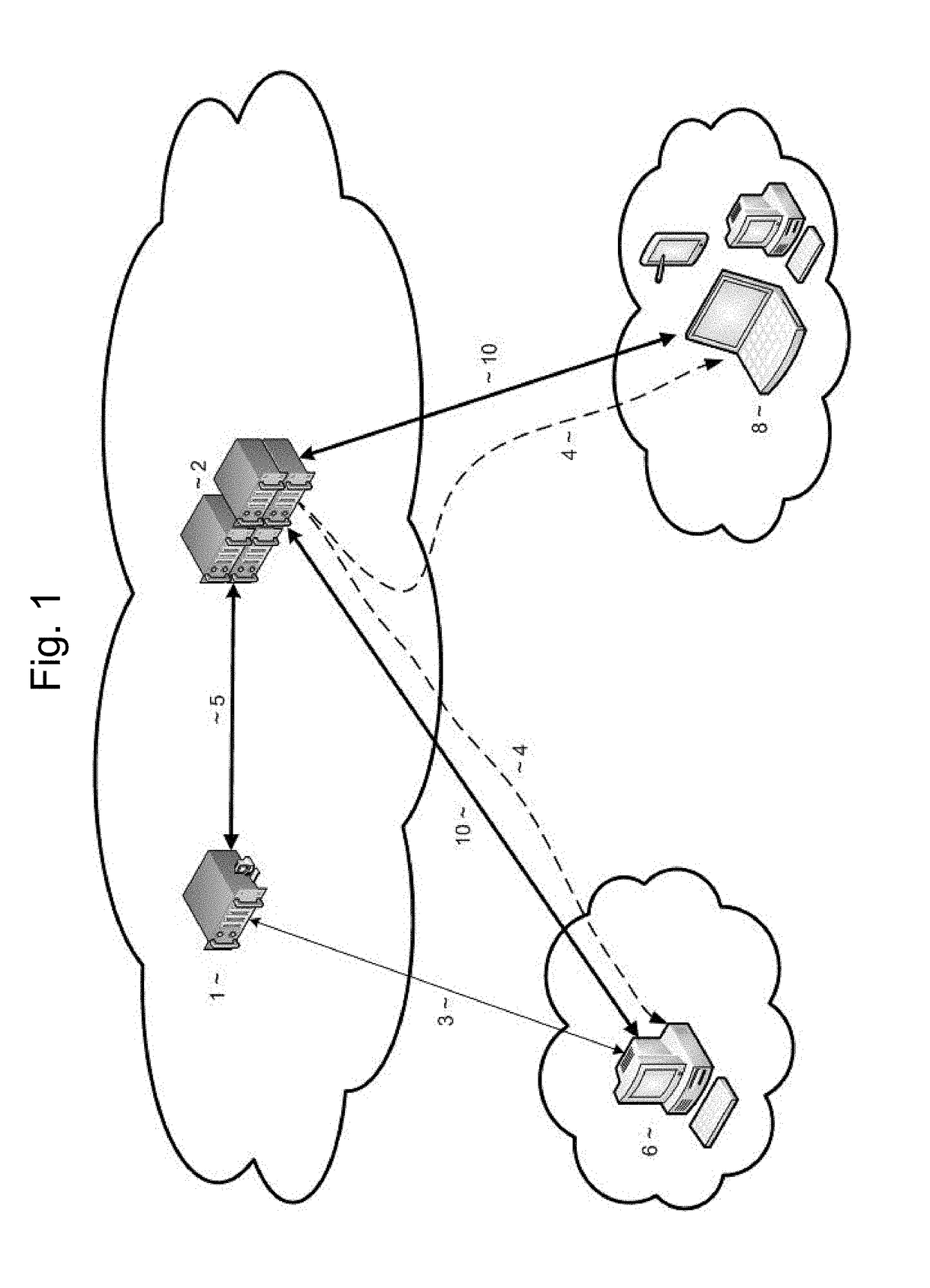
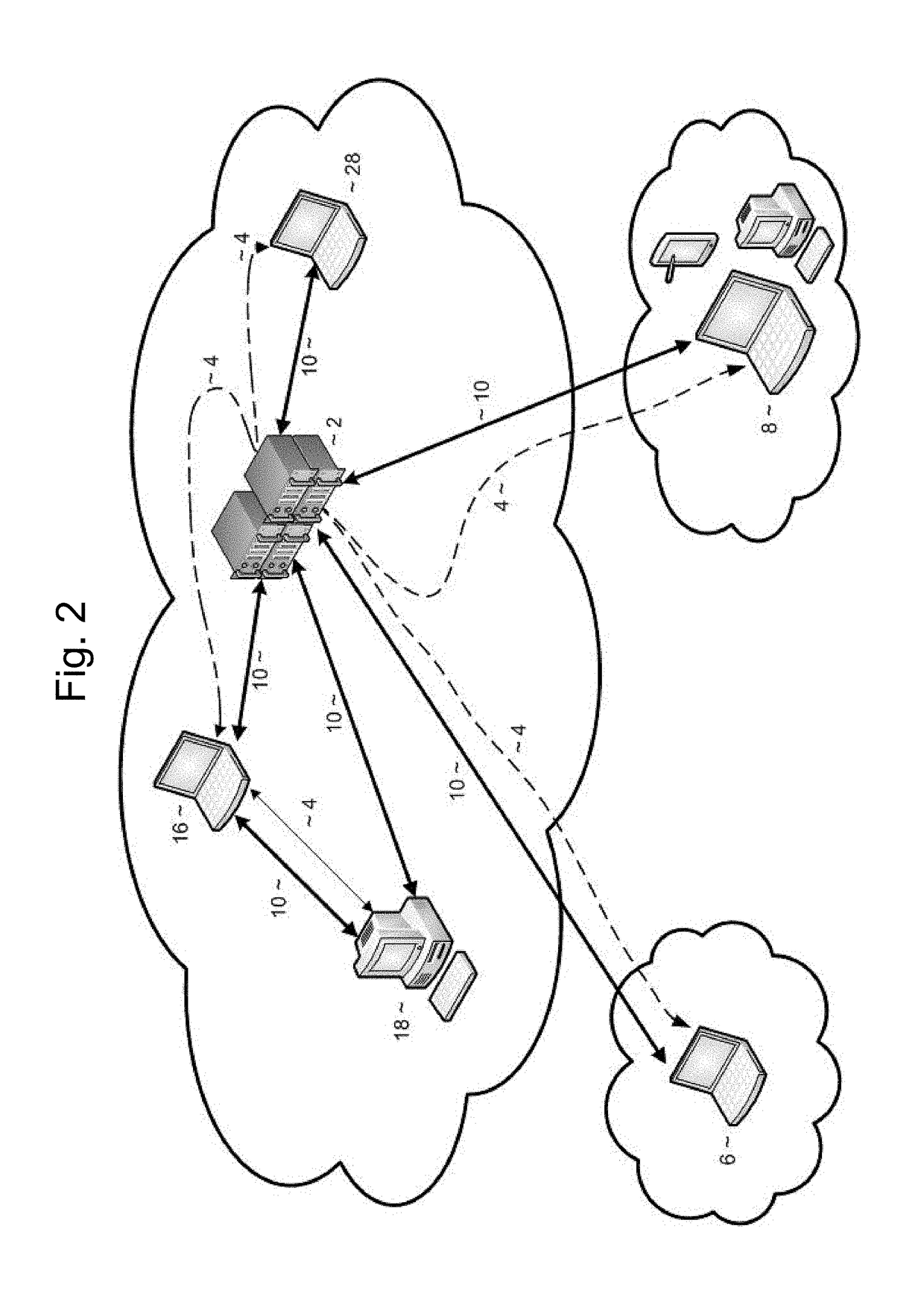
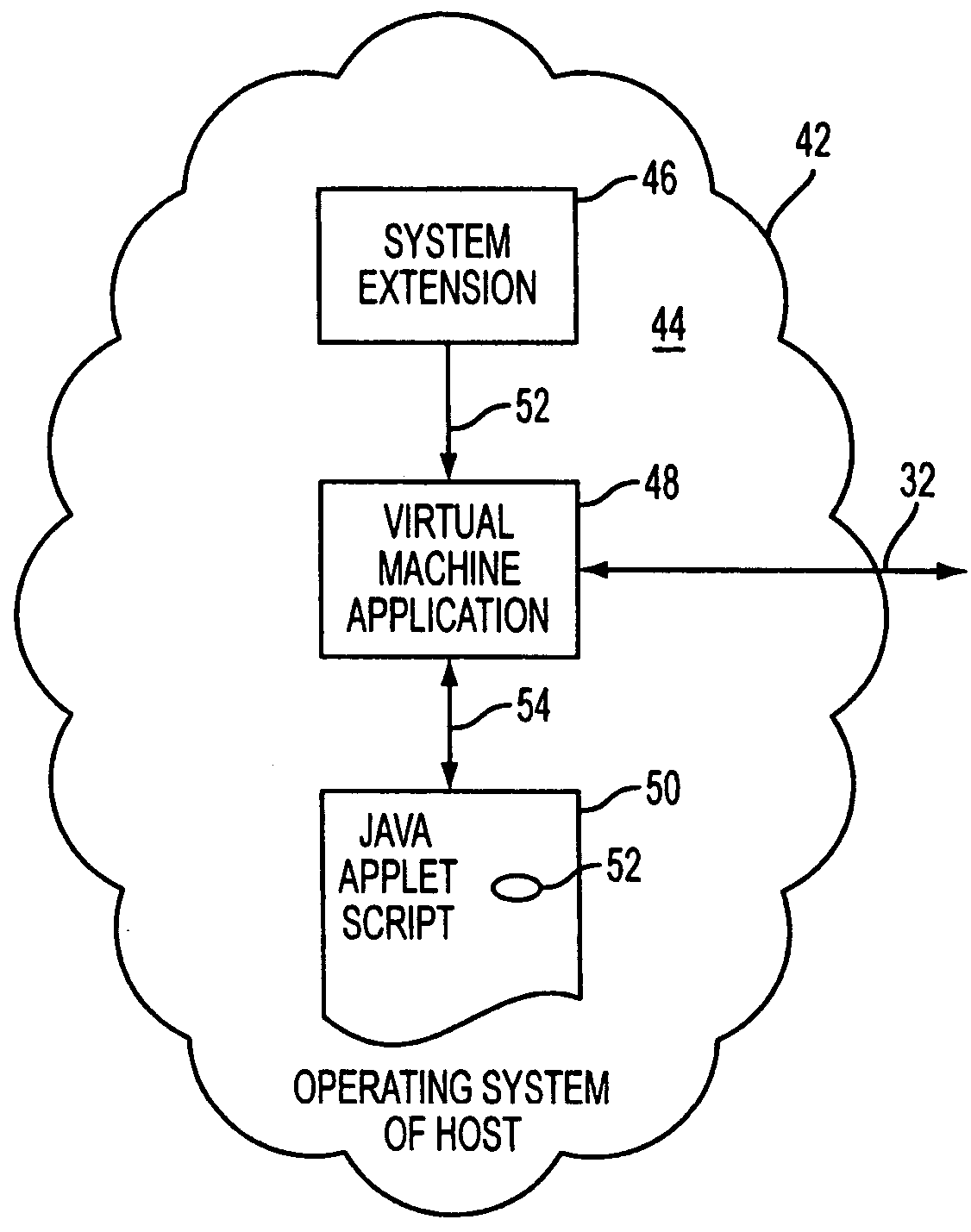
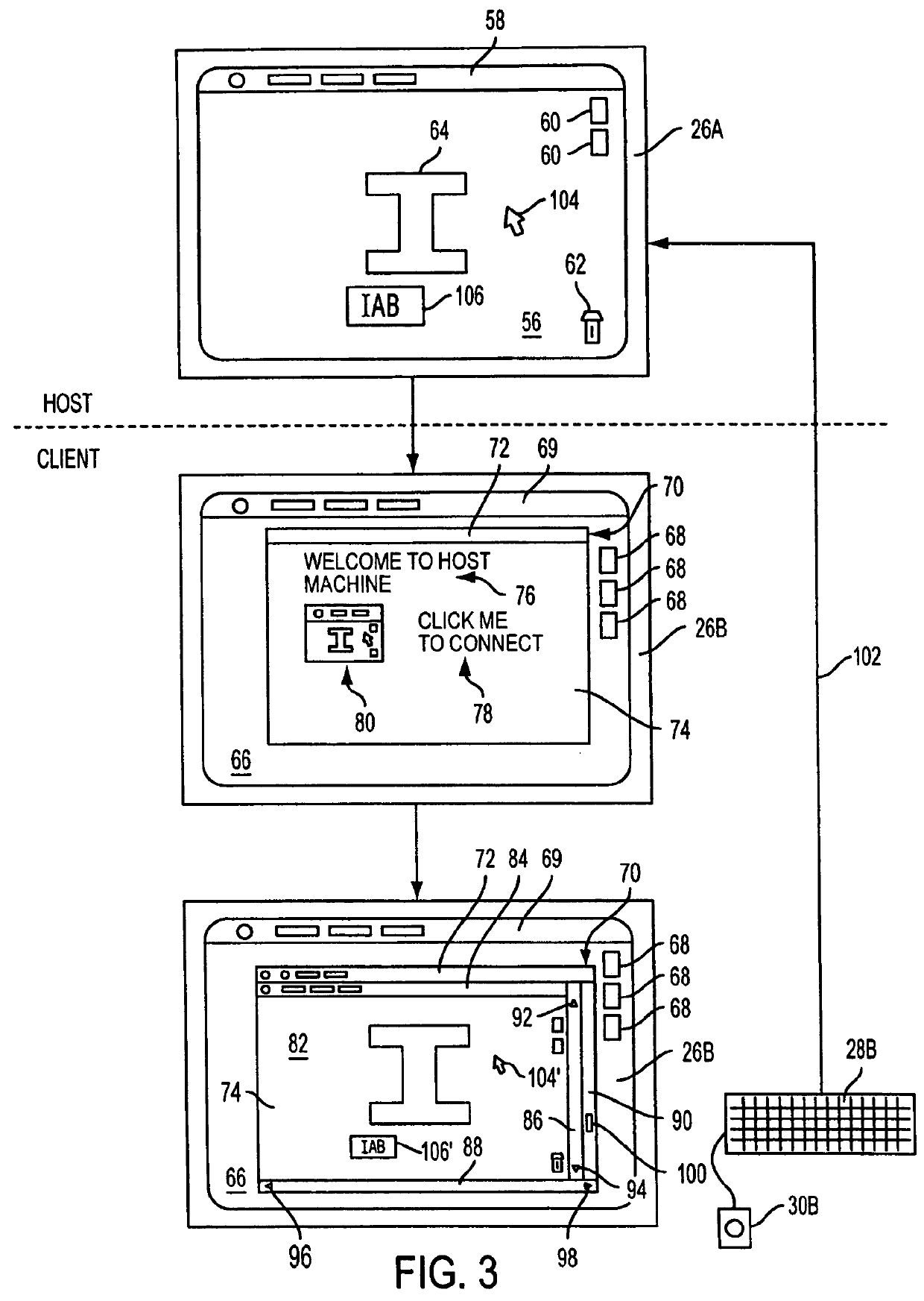
A cluster computer system including multiple network accessible computers that are each coupled to a network. The network accessible computers implement host computer programs which permits the network accessible computers to operate as host computers for client computers also connected to the network, such that input devices of the client computers can be used to generate inputs to the host computers, and such that image information generated by the host computers can be viewed by the client computers. The system also includes a cluster administration computer coupled to the multiple network accessible computers to monitor the operation of the network accessible computers. A method for providing access to host computers by client computers over a computer network includes receiving a request for a host computer coupled to a computer network from a client computer coupled to the computer network, wherein the relationship of the host computer to the client computer is to be such that after the client computer becomes associated with a host computer, an input device of the client computer can be used to generate inputs to the host computer, and such that image information generated by the host computer can be viewed by the client computer. Next, a suitable host computer for the client computer is determined, and the client computer is informed of the network address of the suitable host computer.
Owner:GULA CONSULTING LLC
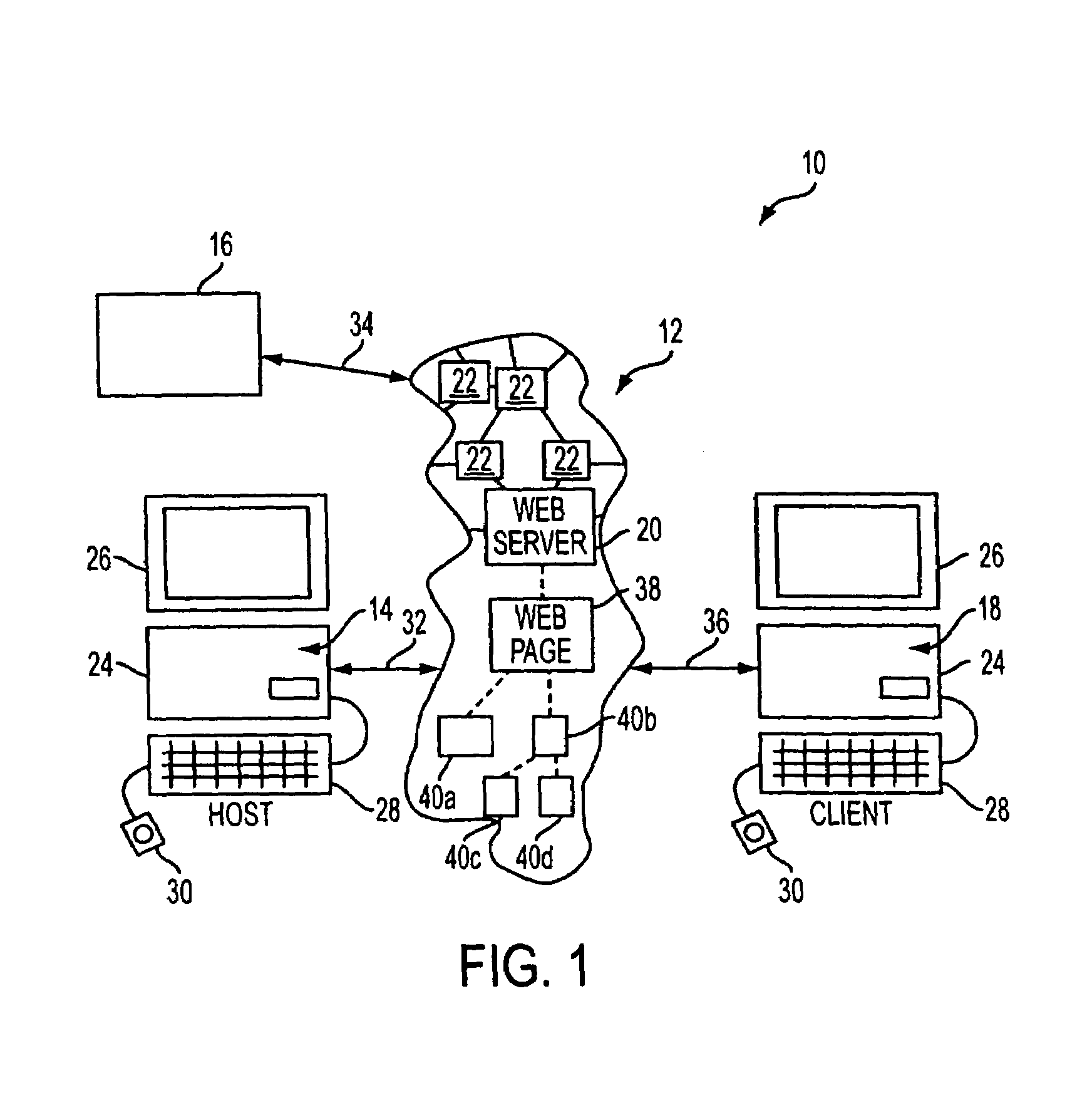
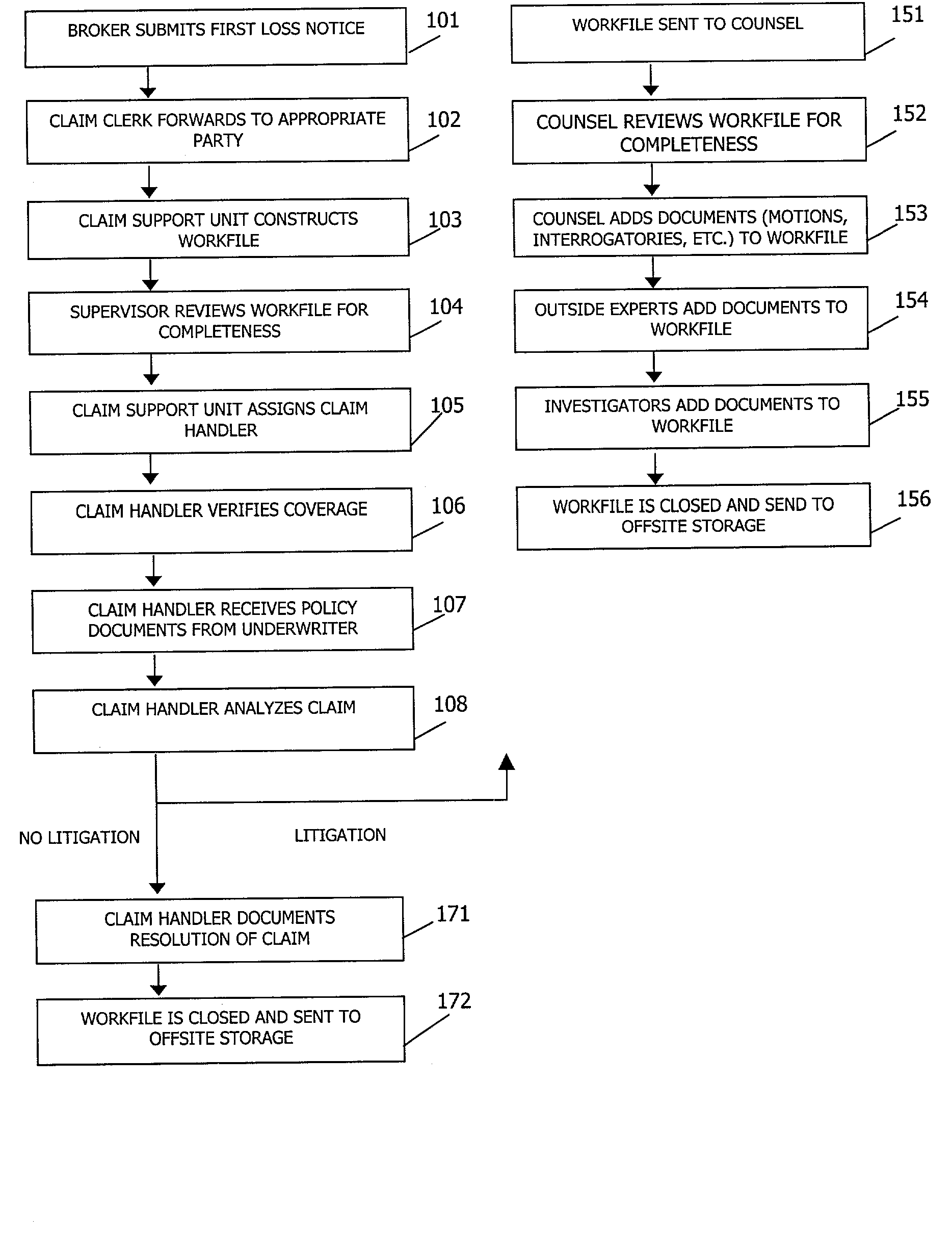
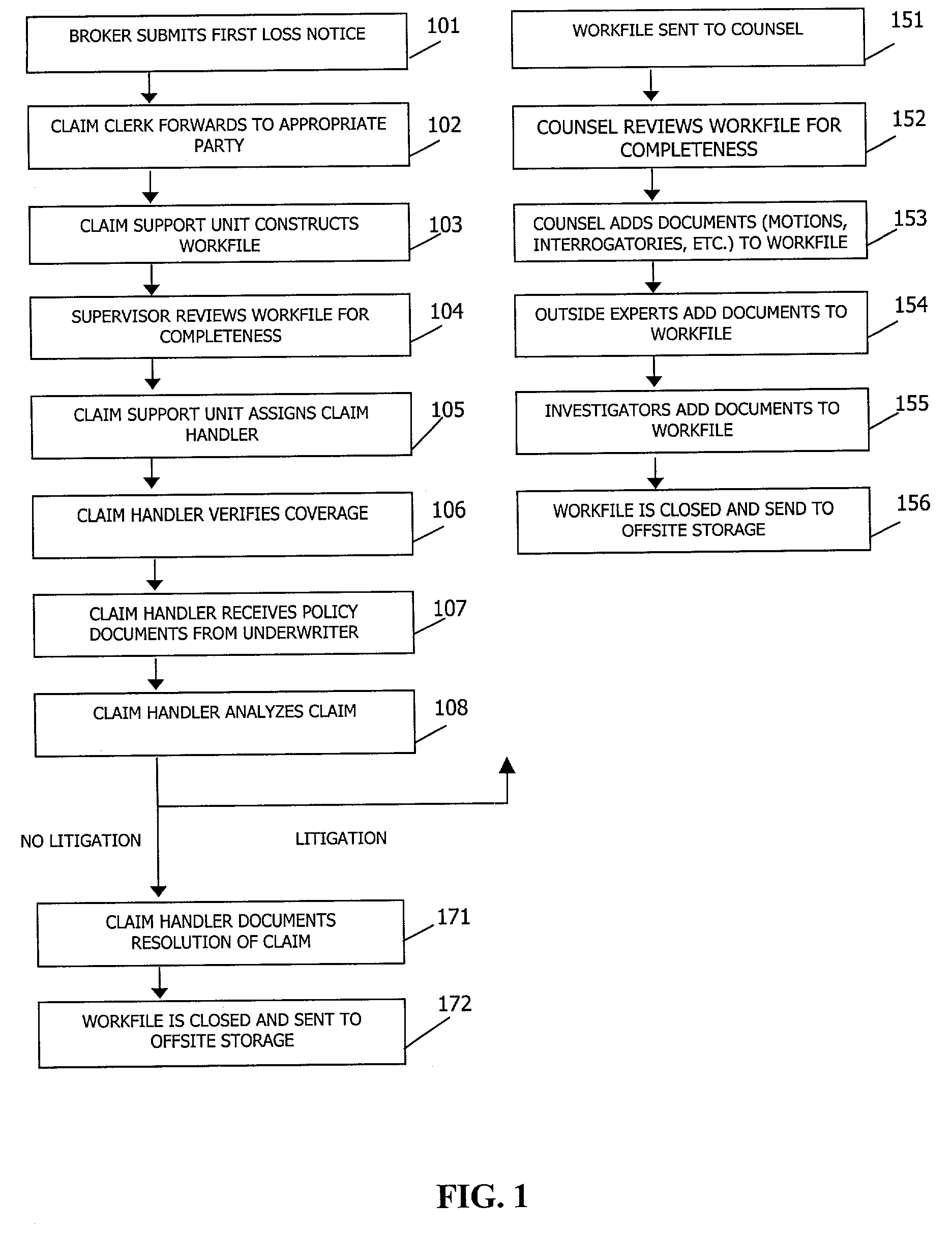
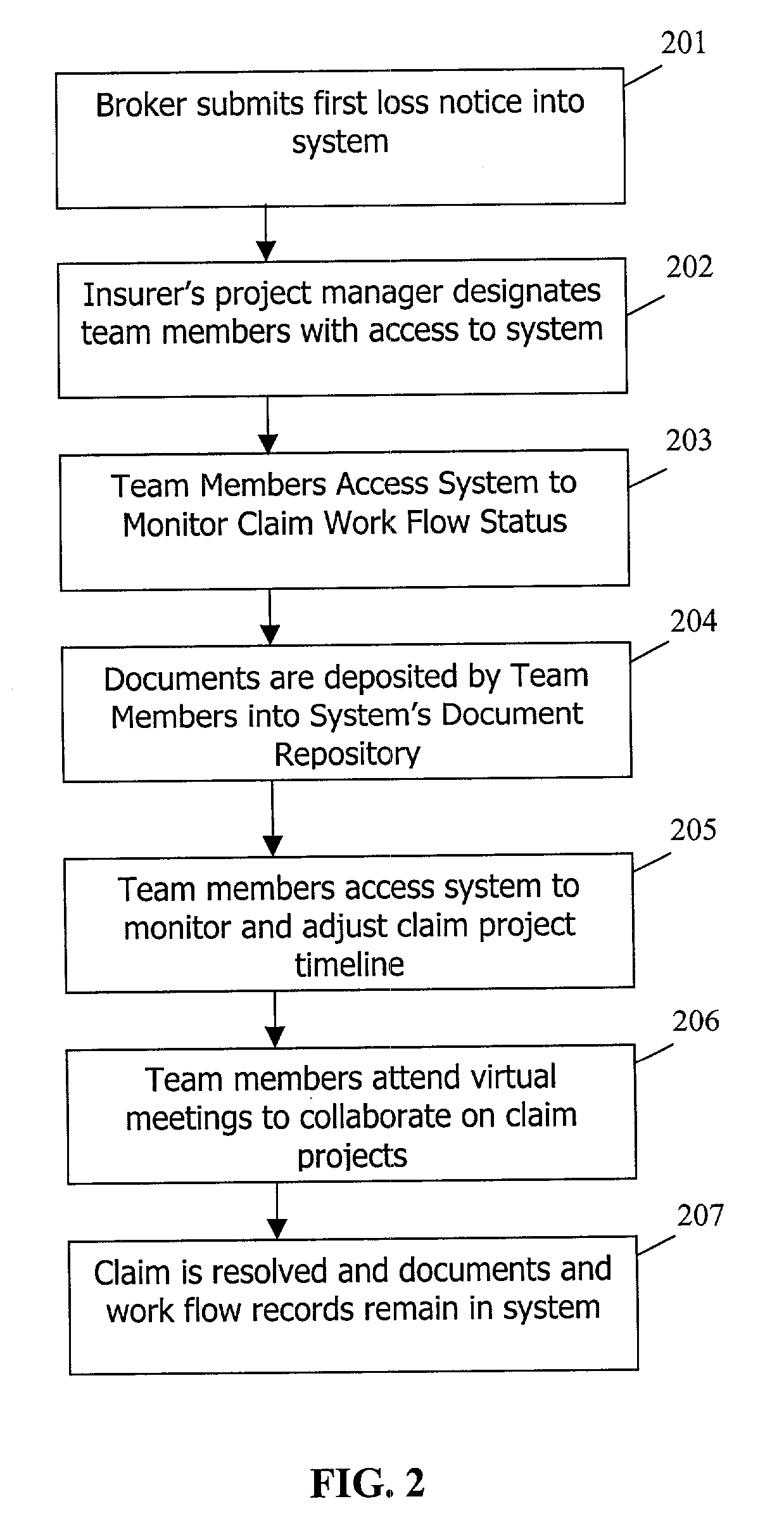
System and method for collaborative insurance claim processing
A system for collaboratively managing complex, longtail property and casualty insurance claims which is remotely and continuously accessible by all users designated by the insurer. The users can access documents retained in a centralized database through an application layer. The application layer includes a workflow application, a document management application and an administrative application. A method for collaboratively managing complex claims includes the storage of documents in a centralized remotely-accessible computer database, access to the documents through an application layer, and management of the claim management process through a workflow management application used in connection with a document management application.
Owner:GREENWICH SOLUTIONS
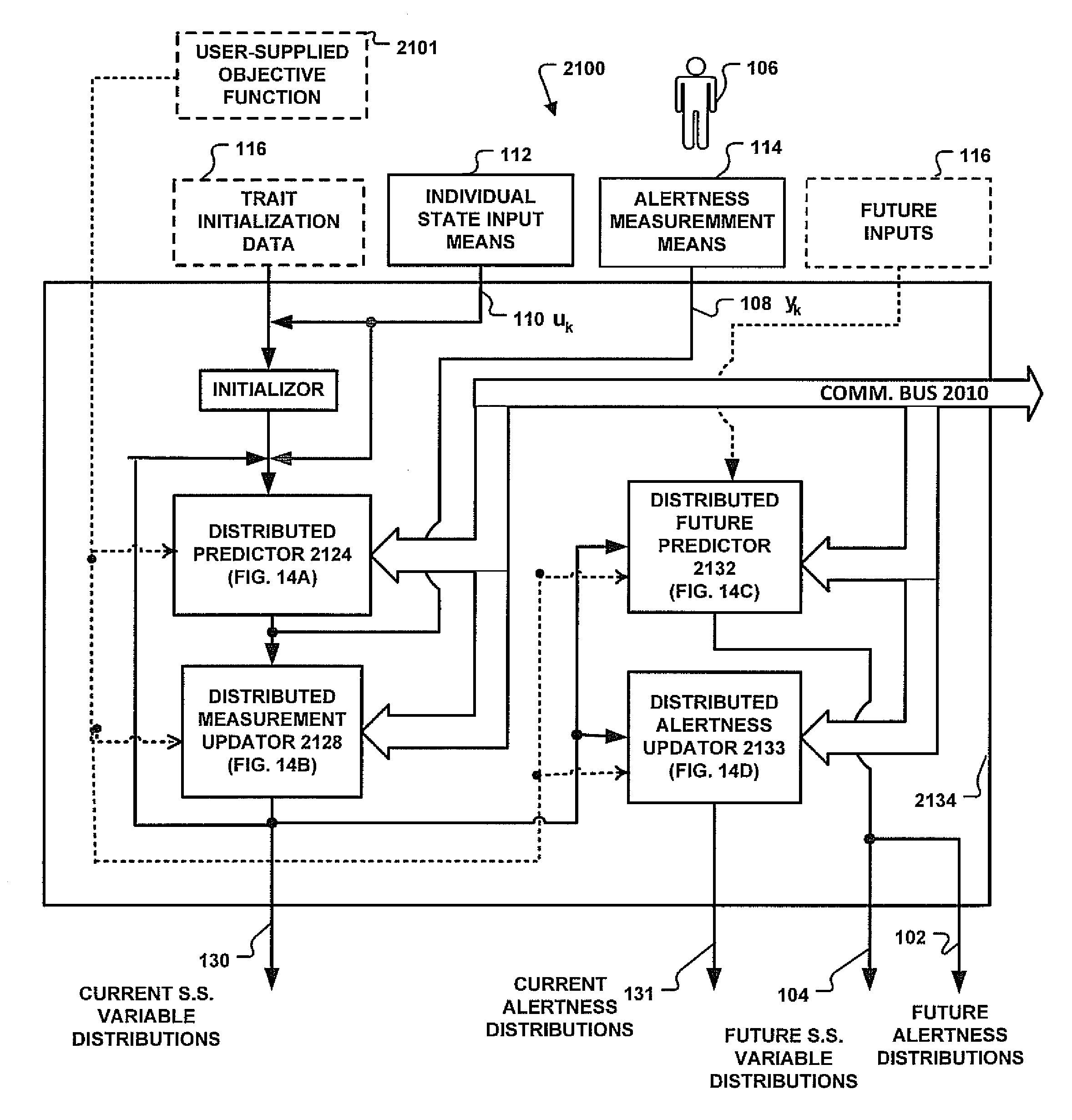
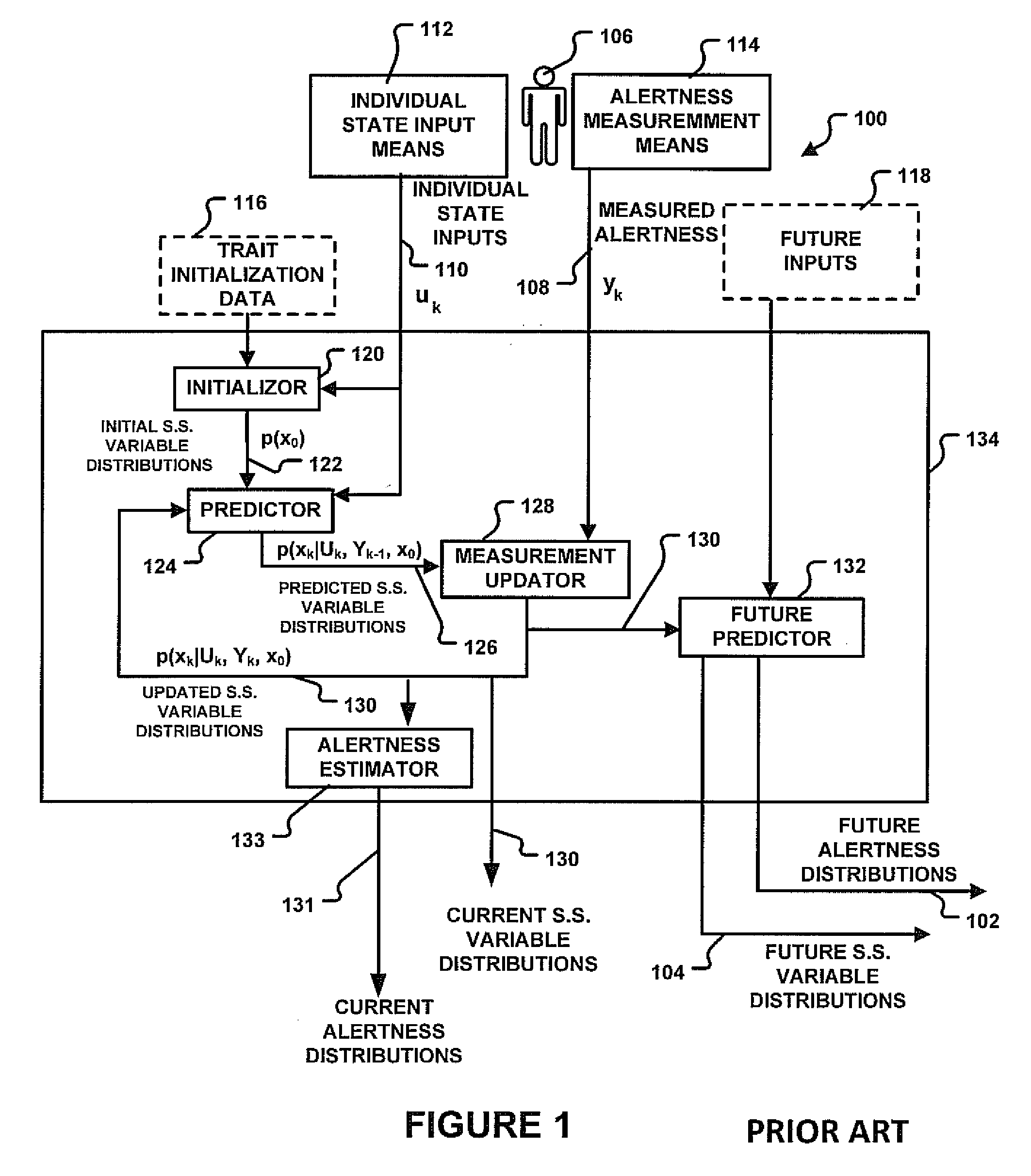
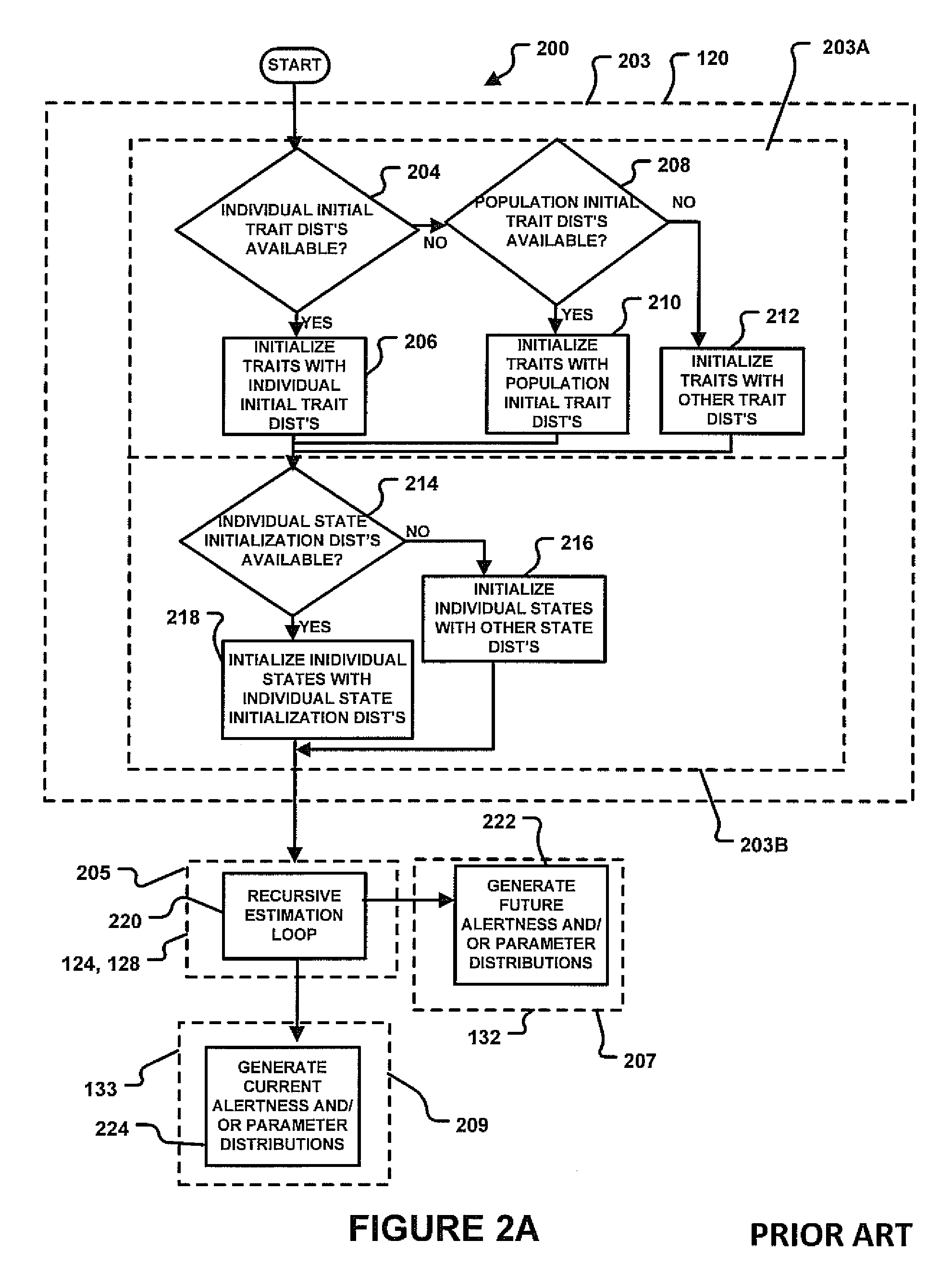
Systems and Methods for Distributed Calculation of Fatigue-Risk Prediction and Optimization
InactiveUS20120316845A1Useful resultImprove accuracyEnergy efficient ICTResource allocationUser needsComputing Methodologies
Distributed computing methods and systems are disclosed, wherein intensive fatigue-risk calculations are partitioned according to available computing resources, parameters of the fatigue-risk calculation, time-sensitive user demands, and the like. Methods are disclosed wherein execution-cost functions are used to allocate accessible computing resources. Additional methods include partitioning calculation tasks by user-prioritized needs and by general mathematical features of the calculations themselves. Included herein are methods to calculate only prediction-maximum likelihoods instead of full probability distributions, to calculate prediction likelihoods using Bayesian prediction techniques (instead of full re-tabulation of all data), to collate interim results of fatigue-risk calculations where serial results can be appropriately collated (e.g., serial time-slice independence of the cumulative task involved), to use simplified (e.g., linear, first-order) approximations of richer models of fatigue prediction, to assign user-identified priorities to each computational task within a plurality of such requests, and the like.
Owner:PULSAR INFORMATICS
Method and system for displaying and operating remote computer on mobile phone
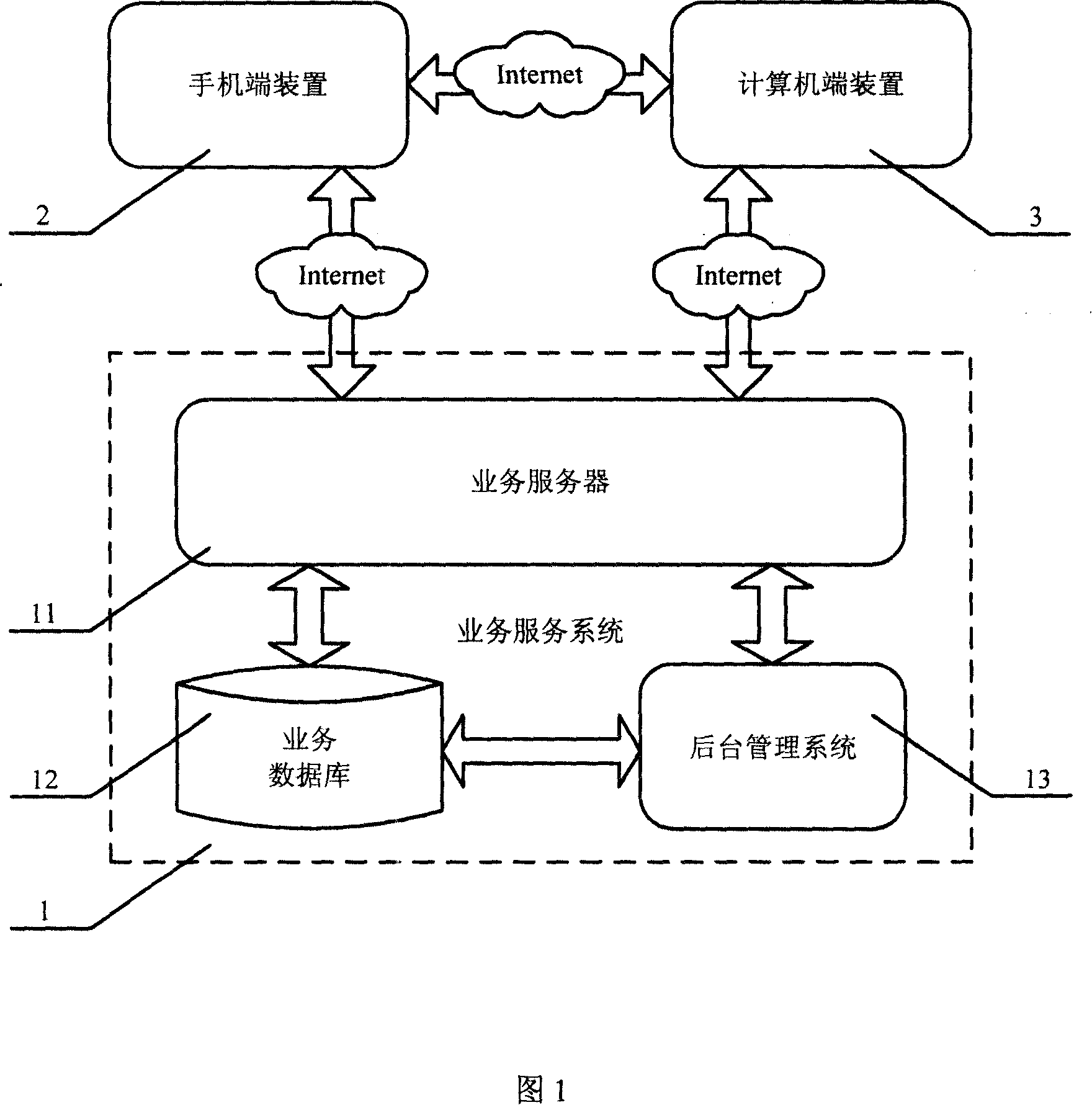
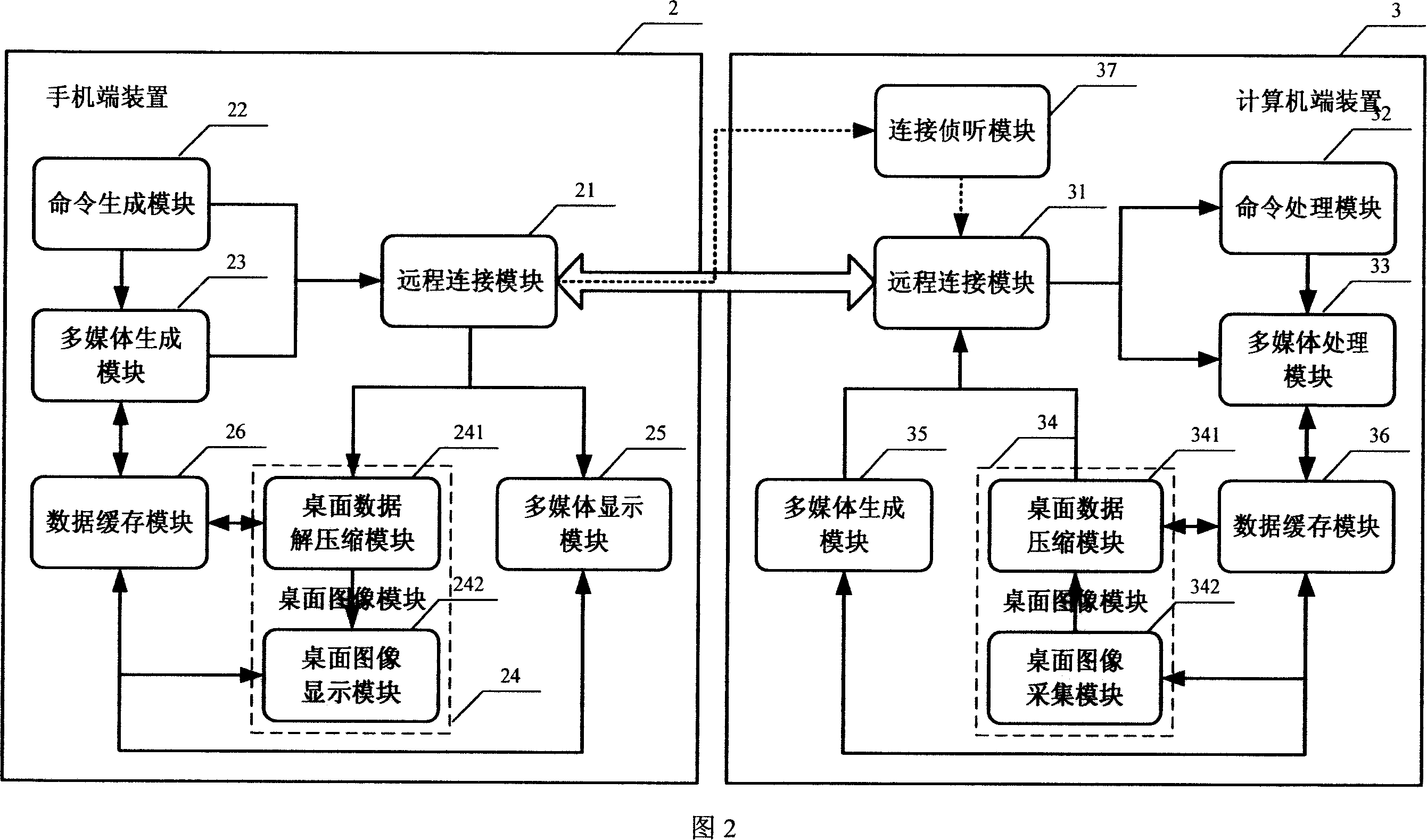
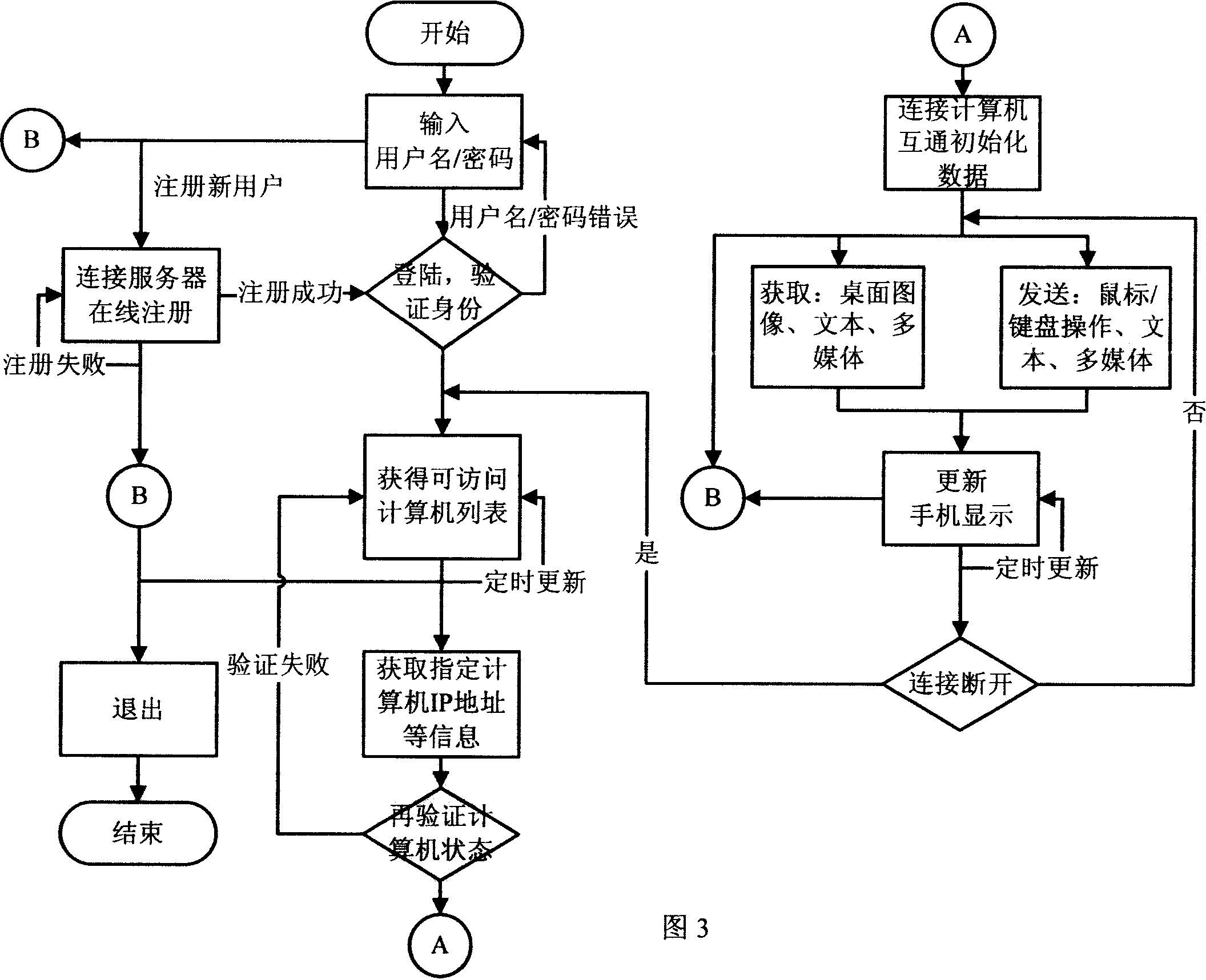
InactiveCN101132571AEasy to operateRadio/inductive link selection arrangementsAutomatic exchangesRemote desktopIp address
This invention discloses a method and a system for displaying desktop of remote computer and operating it quickly on a cell phone by Internet, in which, the method includes: a, a cell phone is connected to a remote computer by Internet, b, the remote computer gets images of a desktop region and carries out optimized compression according to the display ability of the cell phone and feeds it back to the cell phone, c, a user operates the remote computer quickly on the keyboard of the cell phone and sees the operating result. This invented system includes a service system, a terminal device of a cell phone and a terminal device of computer, and the service system provides a visitable list to the cell phone terminal device and gets the Ip address from the remote computer, the cell phone terminal device sets up connection with the computer terminal device to carry out remote desktop operation.
Owner:薛飞
Method and apparatus for computing within a wide area network
InactiveUS7013327B1Strong computing powerMaintain performanceMultiple digital computer combinationsTransmissionNetwork addressingNetwork address
A cluster computer system including multiple network accessible computers that are each coupled to a network. The network accessible computers implement host computer programs which permits the network accessible computers to operate as host computers for client computers also connected to the network, such that input devices of the client computers can be used to generate inputs to the host computers, and such that image information generated by the host computers can be viewed by the client computers. The system also includes a cluster administration computer coupled to the multiple network accessible computers to monitor the operation of the network accessible computers. A method for providing access to host computers by client computers over a computer network includes receiving a request for a host computer coupled to a computer network from a client computer coupled to the computer network, wherein the relationship of the host computer to the client computer is to be such that after the client computer becomes associated with a host computer, an input device of the client computer can be used to generate inputs to the host computer, and such that image information generated by the host computer can be viewed by the client computer. Next, a suitable host computer for the client computer is determined, and the client computer is informed of the network address of the suitable host computer.
Owner:AI-CORE TECH LLC +1
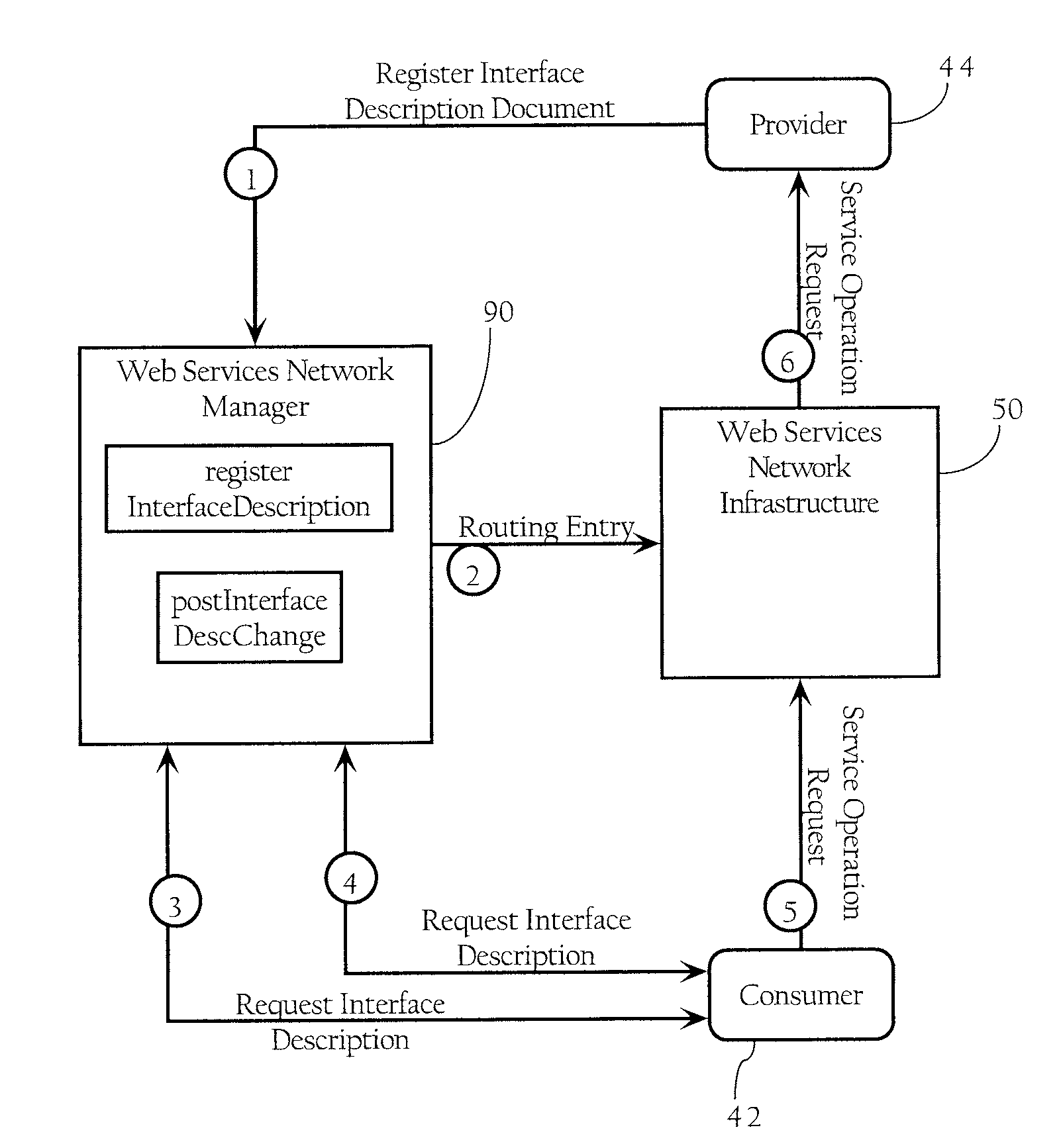
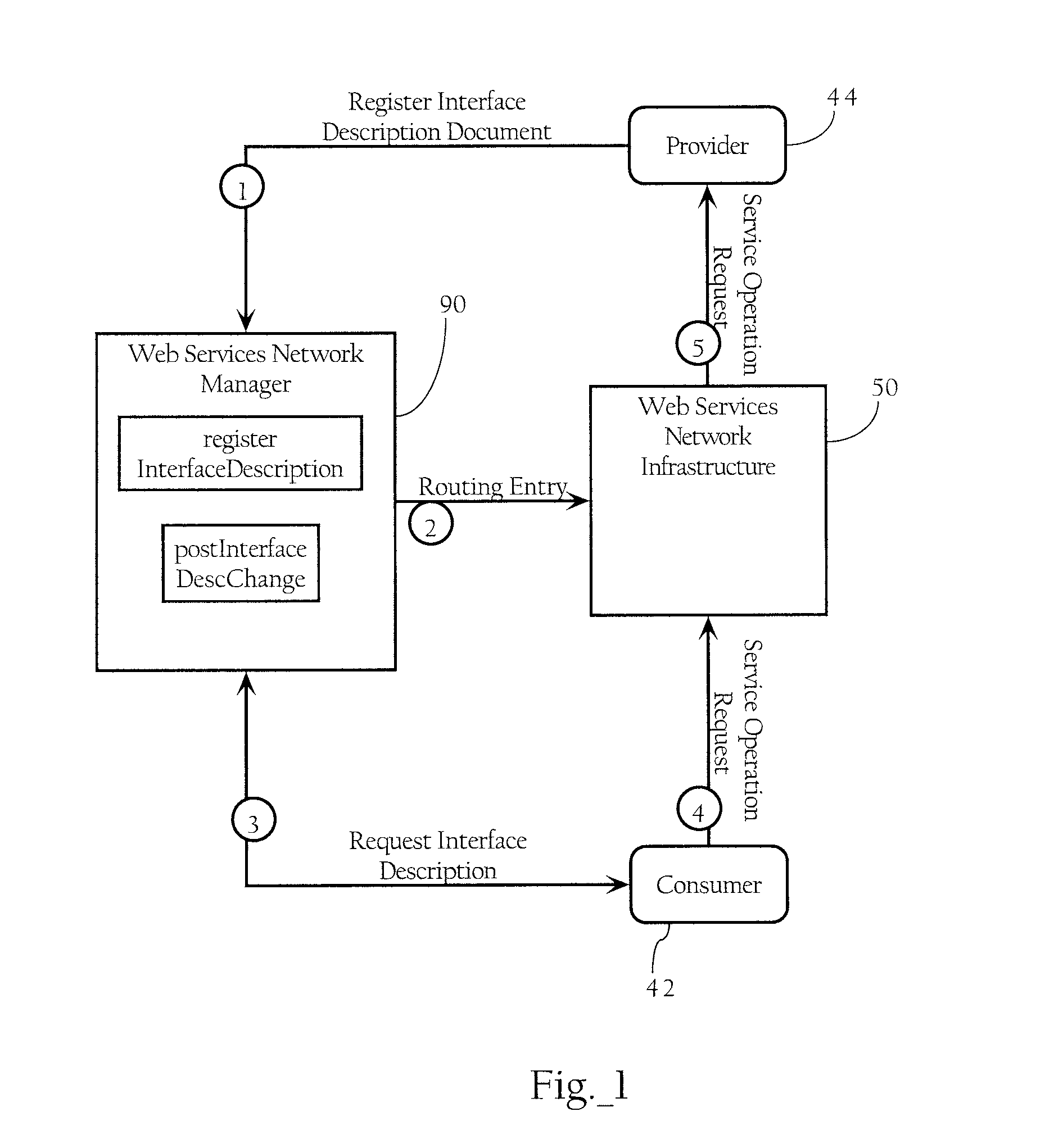
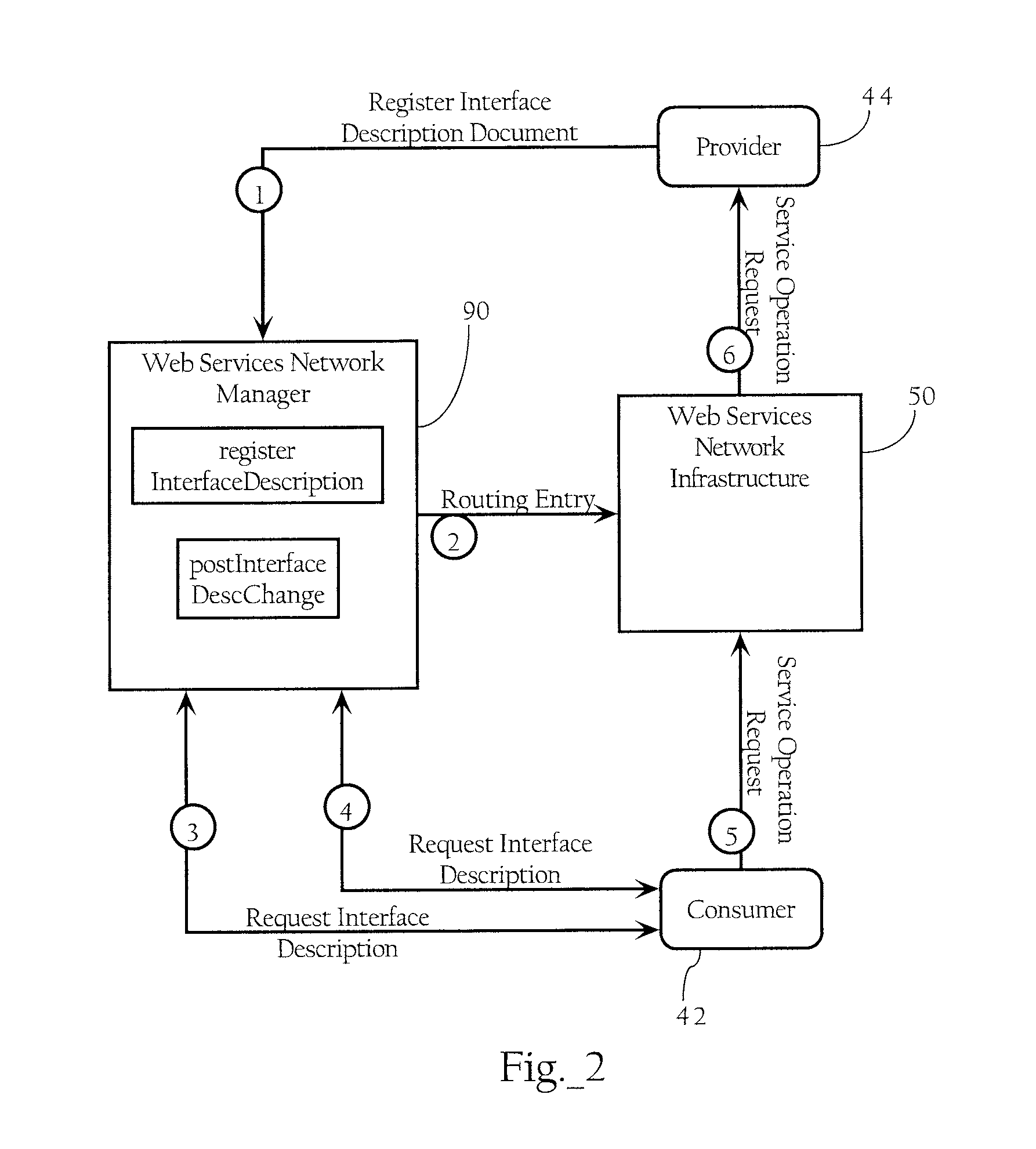
Web Services-Based Computing Resource Lifecycle Management
InactiveUS20110196940A1Facilitating life-cycle management and utilization of network resourceReduce developmentMultiple digital computer combinationsSecuring communicationVirtualizationWeb service
Methods, apparatuses and systems facilitating life-cycle management and utilization of network resources. In one embodiment, instancing, virtualization and dynamic provisioning functionality facilitating management and utilization of web services is provided. The instancing functionality supports a web services network platform allowing for registration and use of multiple instances or versions of a given web service or other network-accessible computing resource. In one embodiment, the present invention combines the virtualization and dynamic provisioning functionality to facilitate the development of client application code in routed web services network architectures. In one embodiment, a set of management functions that may be applied to management of computing resources in any IP-based network.
Owner:AKANA
System for Creating Associations Between Elements of a Message Application
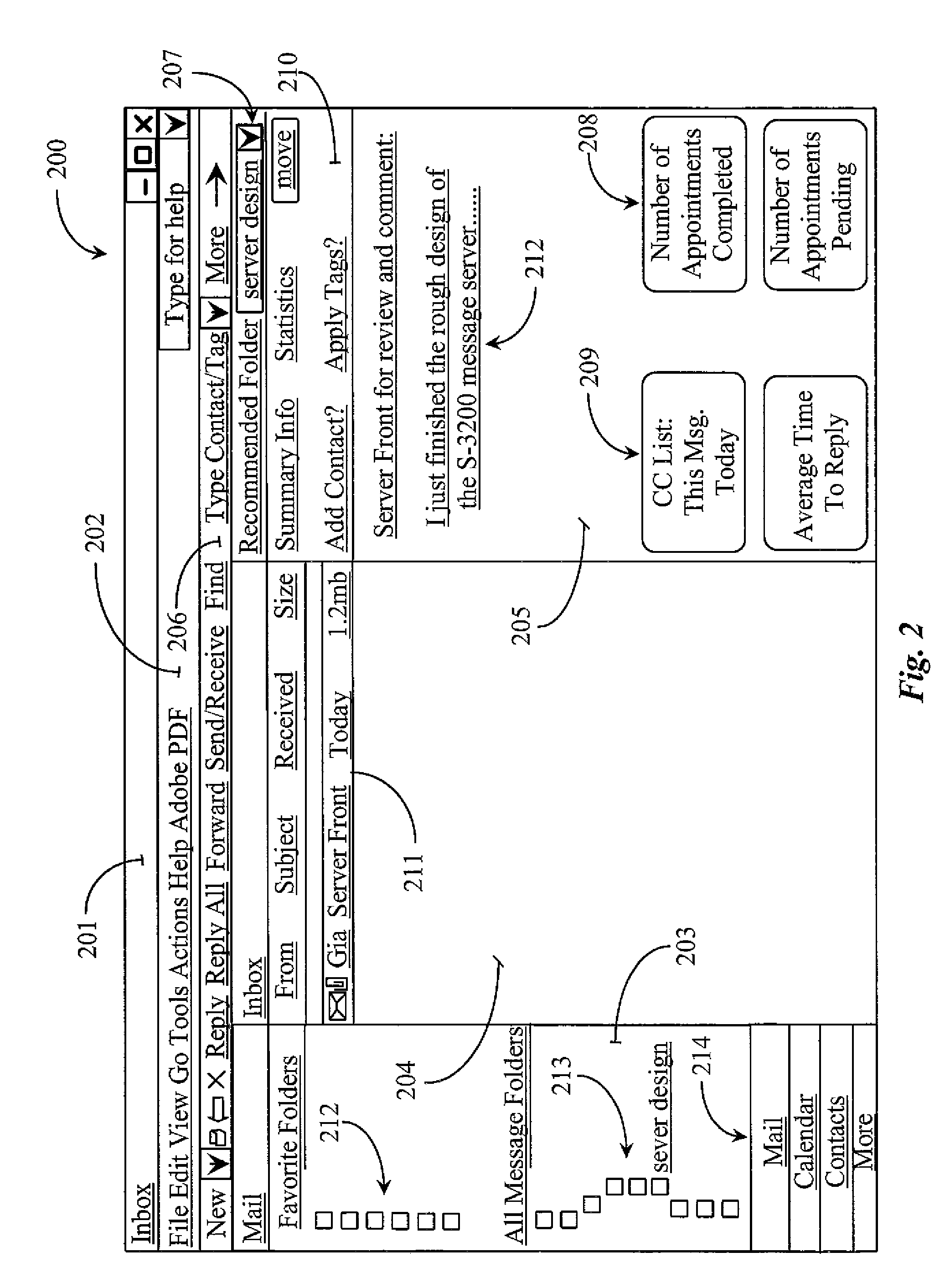
InactiveUS20100064231A1Improve organizationEasy searchData switching networksInput/output processes for data processingApplication softwareMessage passing
A messaging application includes a user interface executable from a digital media on a computing system onboard or accessible to a computing appliance, the user interface enabling display and access to one or more message folders, a list of contacts, a calendar, and a message generation template, and a word tagging utility installed to and executable from the digital media and made accessible through the user interface. The application is characterized in that the word tagging utility is operable to tag functional elements of the message application to create associations between the tagged elements, the associations recognized by the messaging application in the performance of tasks involving the elements.
Owner:SOUNDSTARTS
Method and system for automated pharmaceutical research and reporting
InactiveUS20050038673A1Data processing applicationsComputer-assisted medical data acquisitionMedical equipmentDrug study
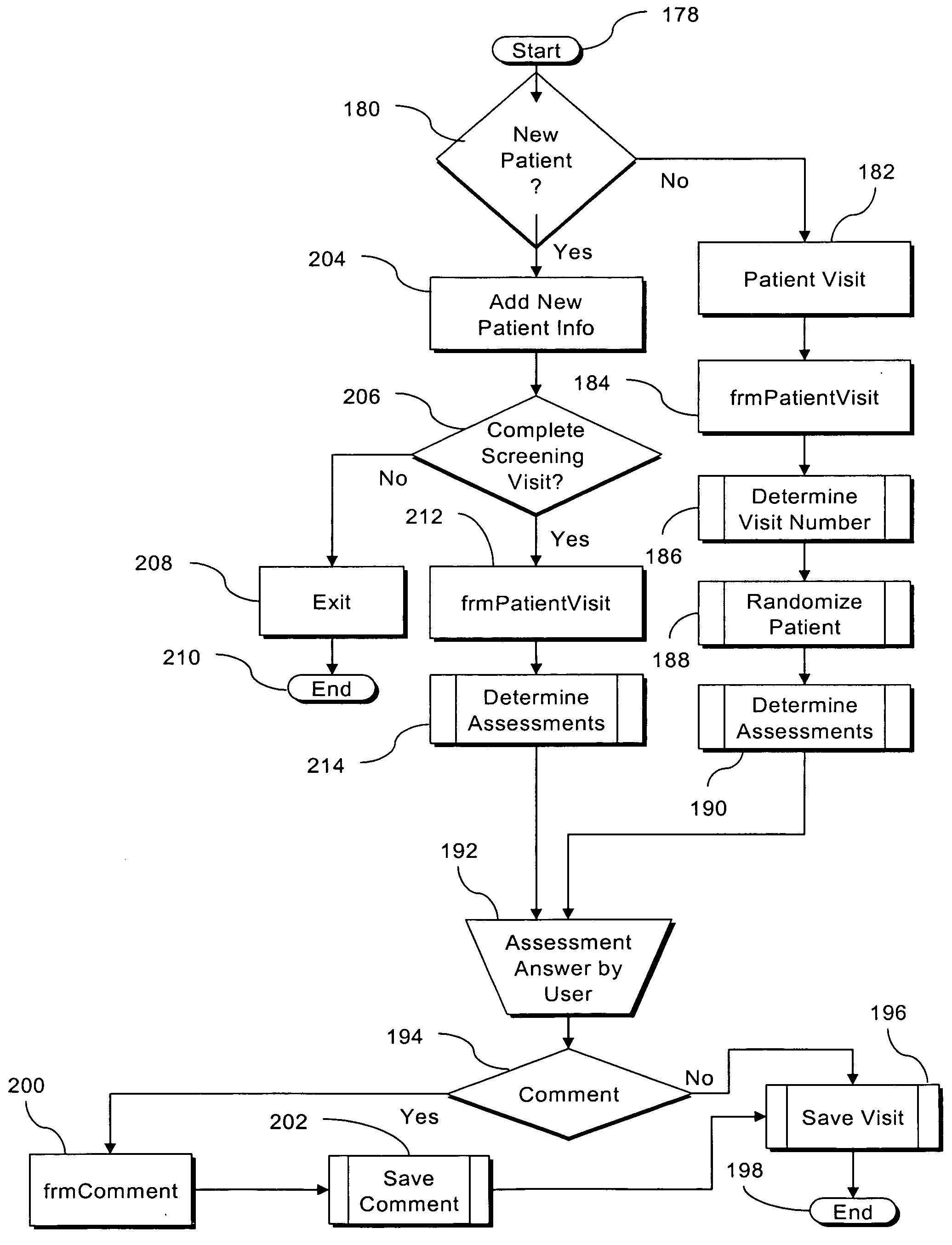
A system for automated management of a clinical trial for pharmaceutical, biomedical, and medical device development that facilitates pharmaceutical research and reporting, including at least one site server 222, at least one computing device 218 configured to collect primary clinical trial data, and an authorized user accessible computing device 234. The central server 232 is configured to receive the primary clinical trial data from each site server 222, to store the primary clinical trial data, to create secondary clinical trial data based on the primary clinical trial data, and to transmit the primary and secondary clinical trial data to the authorized user accessible computing device 234. Also provided is a method for automatically managing a clinical trial for pharmaceutical, biomedical, and medical device development in order to facilitate pharmaceutical research and reporting, which further includes a computer readable signal containing a set of instructions to perform a corresponding method.
Owner:PRECERCHE
Method and apparatus for computing within a wide area network
InactiveUS7080127B1Strong computing powerMaintain performanceMultiple digital computer combinationsTransmissionNetwork addressingNetwork address
A cluster computer system including multiple network accessible computers that are each coupled to a network. The network accessible computers implement host computer programs which permits the network accessible computers to operate as host computers for client computers also connected to the network, such that input devices of the client computers can be used to generate inputs to the host computers, and such that image information generated by the host computers can be viewed by the client computers. The system also includes a cluster administration computer coupled to the multiple network accessible computers to monitor the operation of the network accessible computers. A method for providing access to host computers by client computers over a computer network includes receiving a request for a host computer coupled to a computer network from a client computer coupled to the computer network, wherein the relationship of the host computer to the client computer is to be such that after the client computer becomes associated with a host computer, an input device of the client computer can be used to generate inputs to the host computer, and such that image information generated by the host computer can be viewed by the client computer. Next, a suitable host computer for the client computer is determined, and the client computer is informed of the network address of the suitable host computer. Nodes of the network can be non-terrestrial.
Owner:GULA CONSULTING LLC
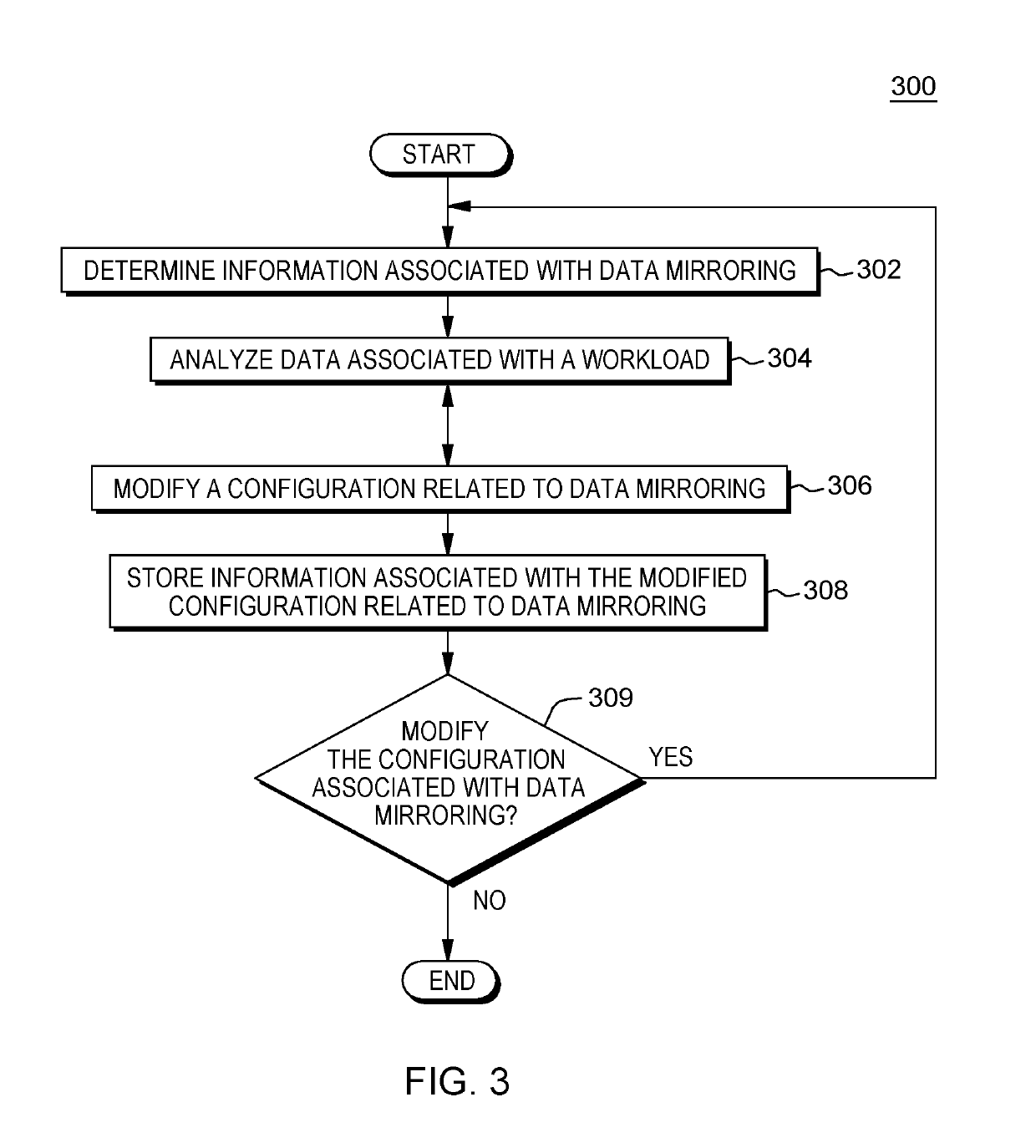
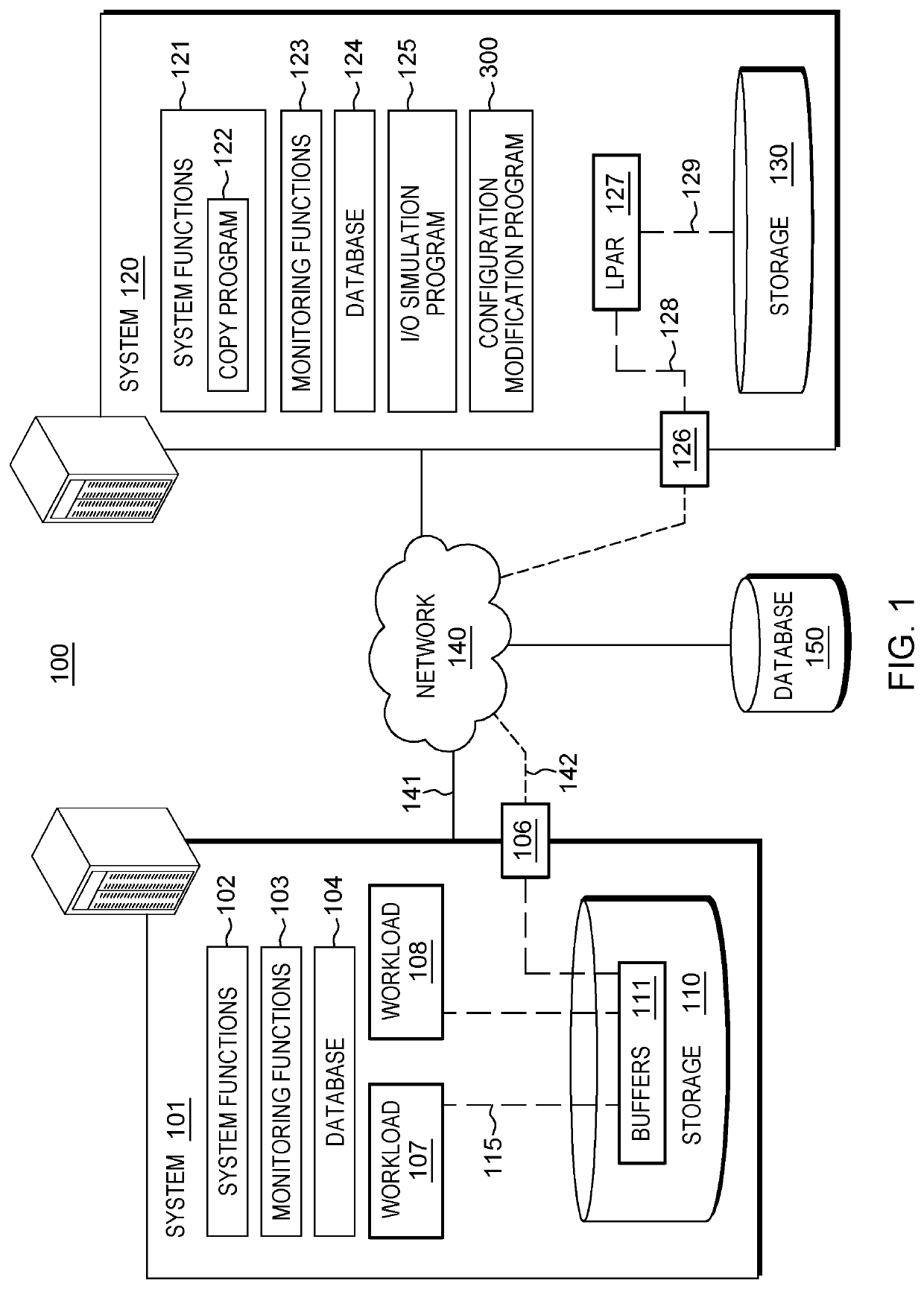
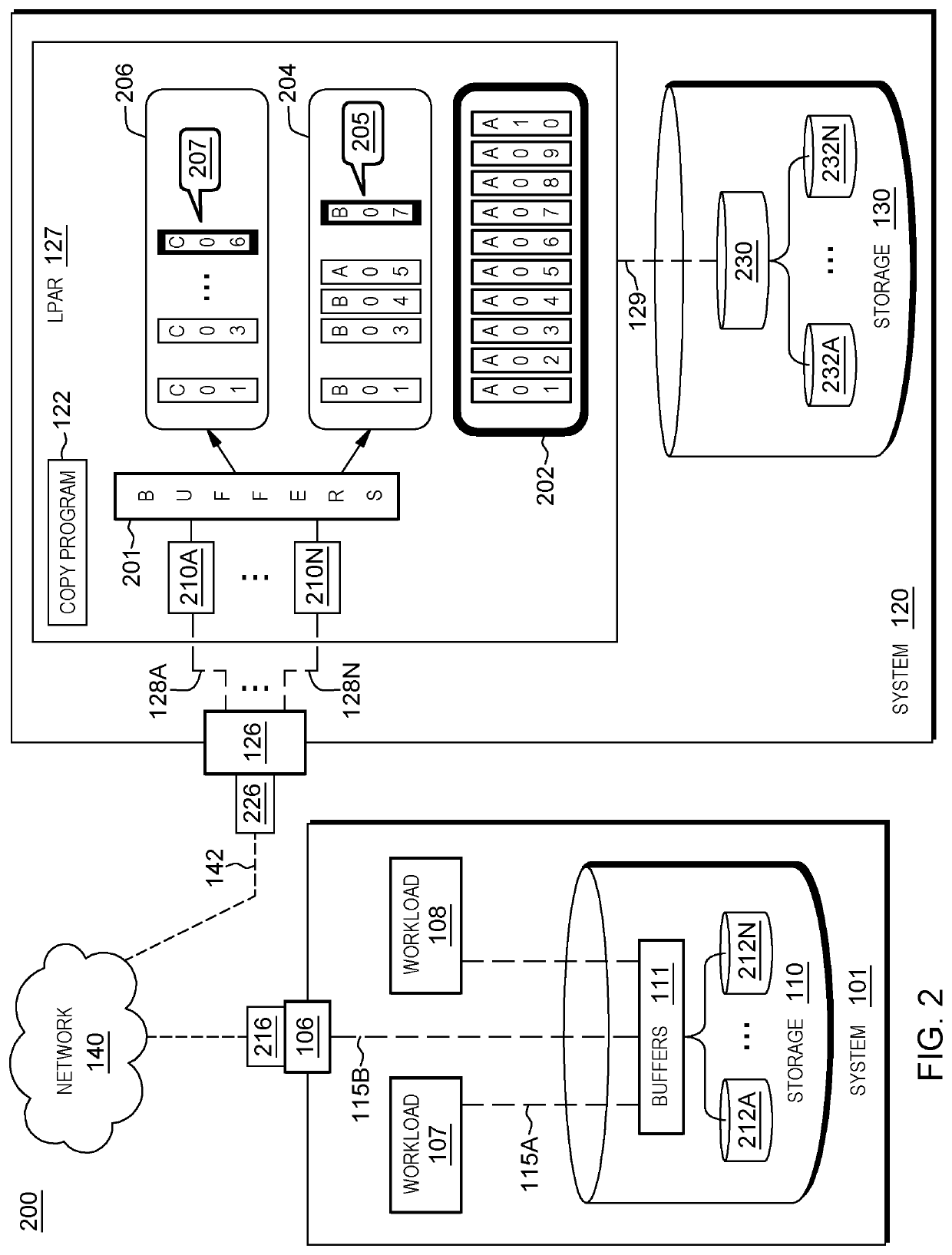
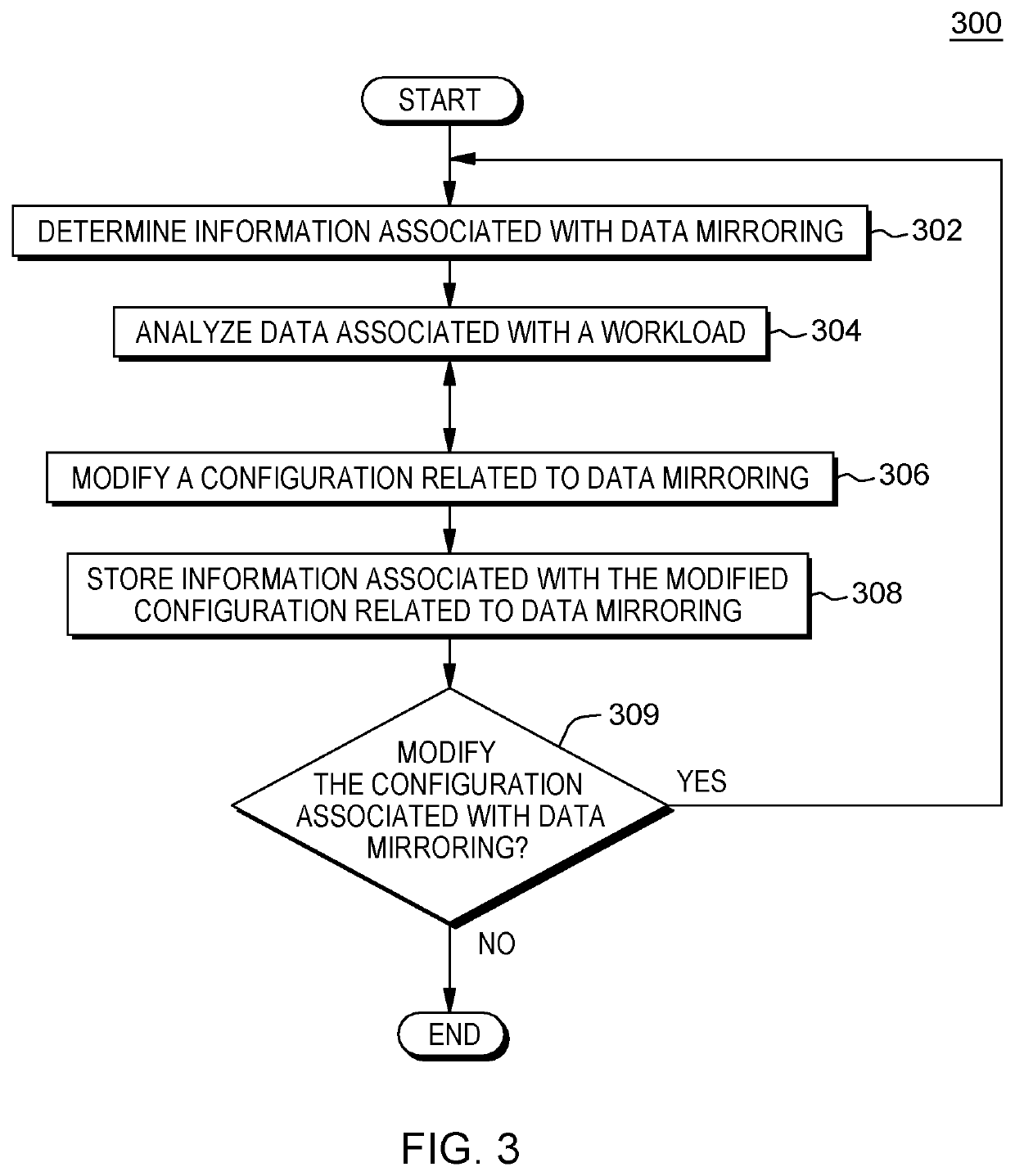
Modifying aspects of a storage system associated with data mirroring
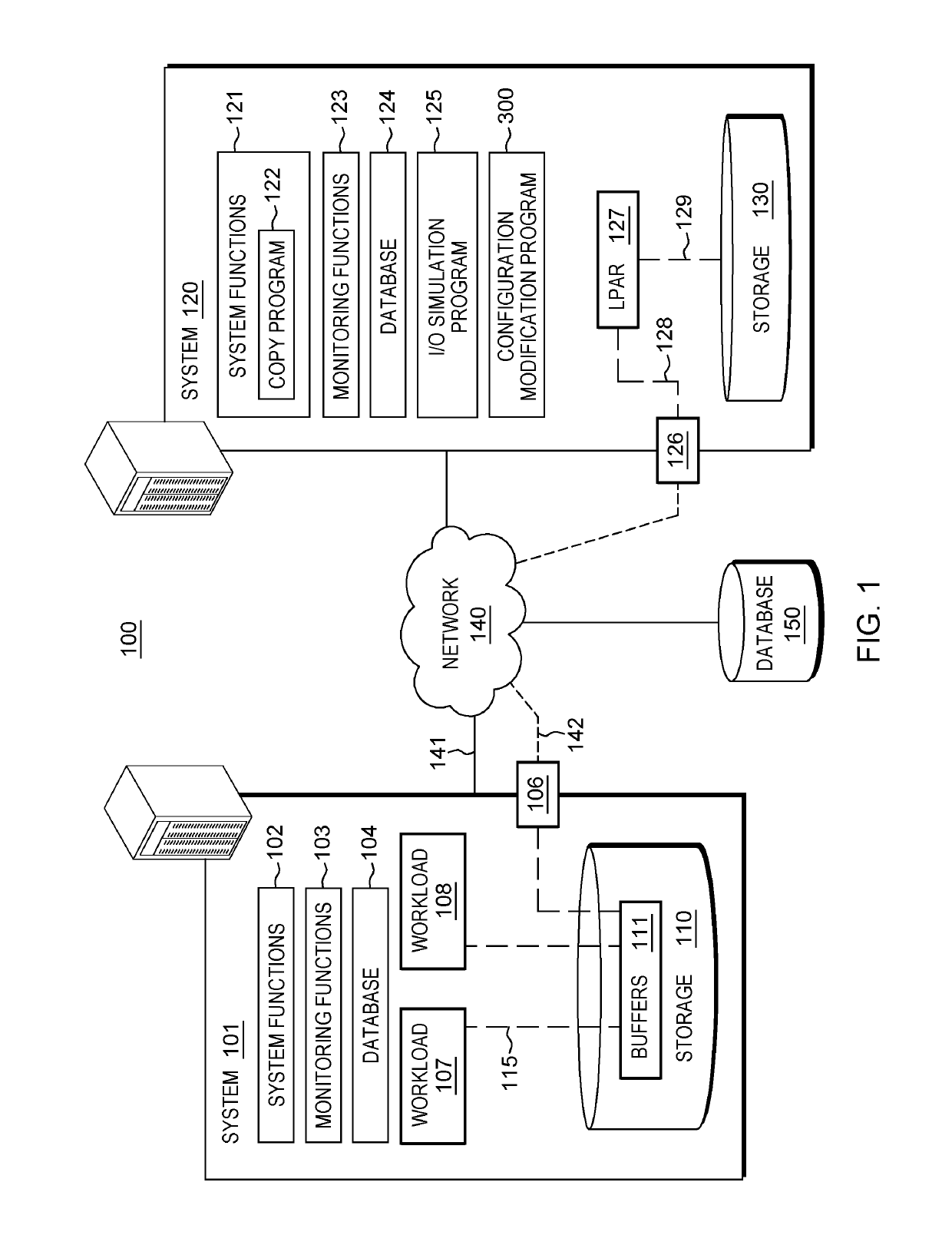
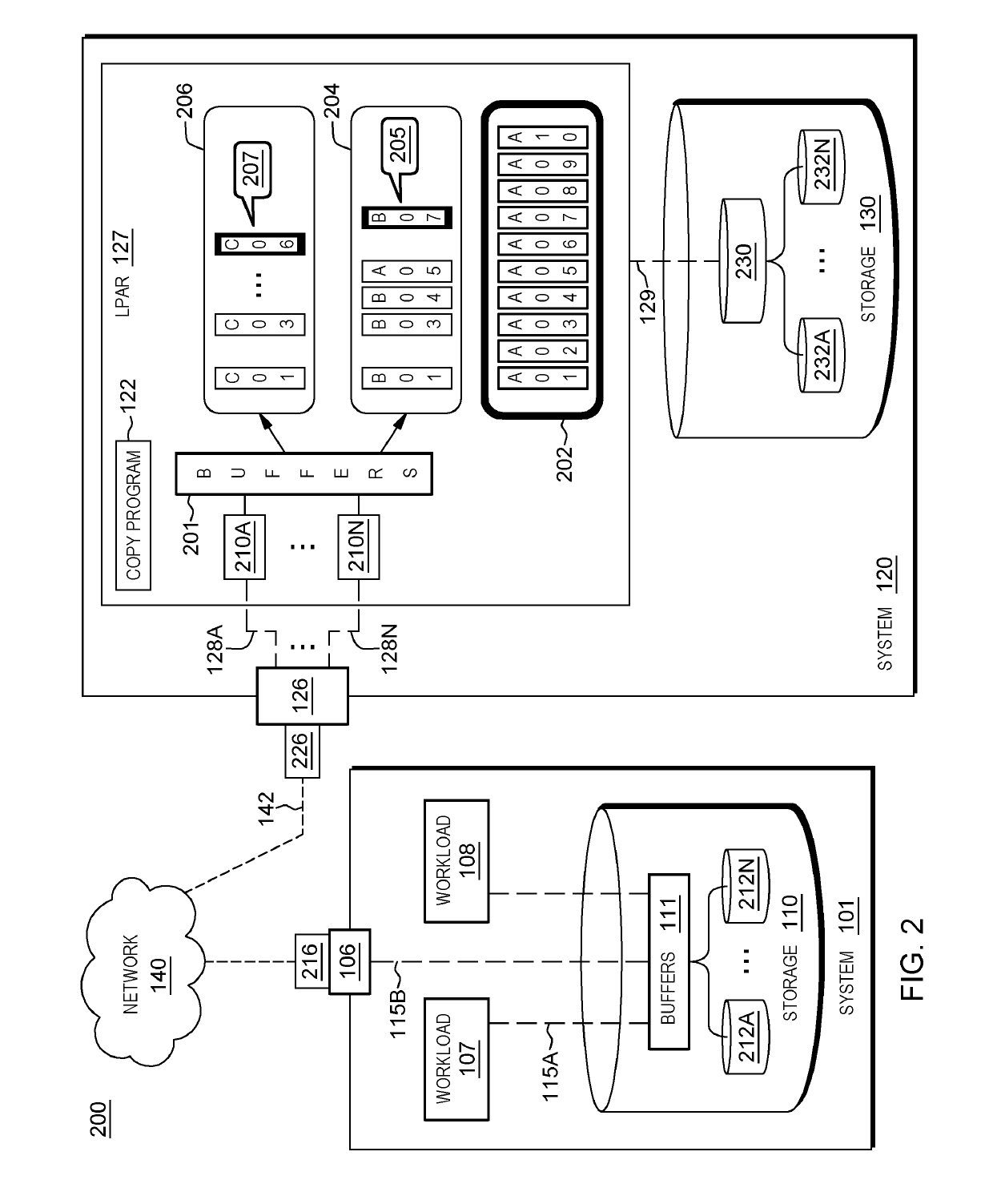
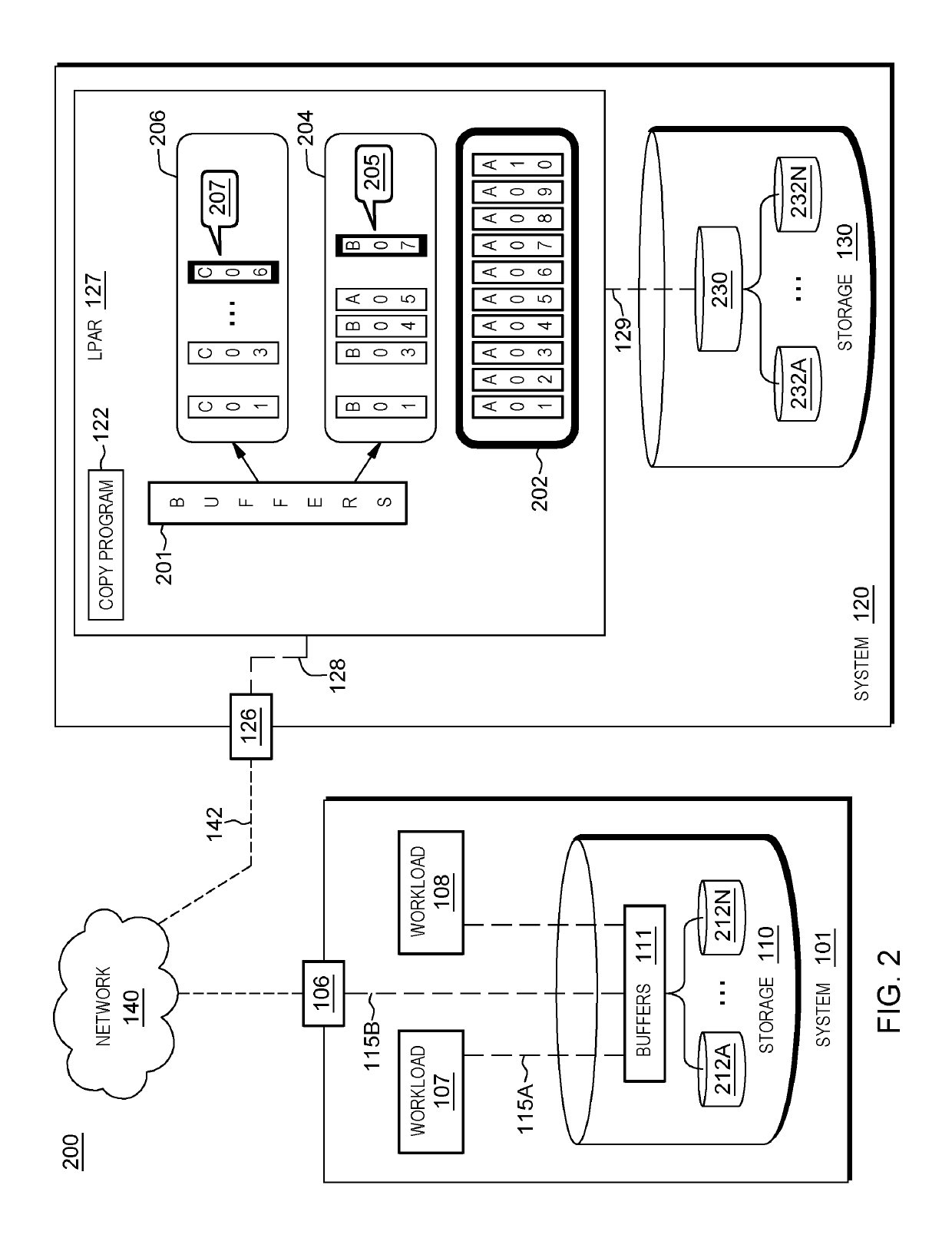
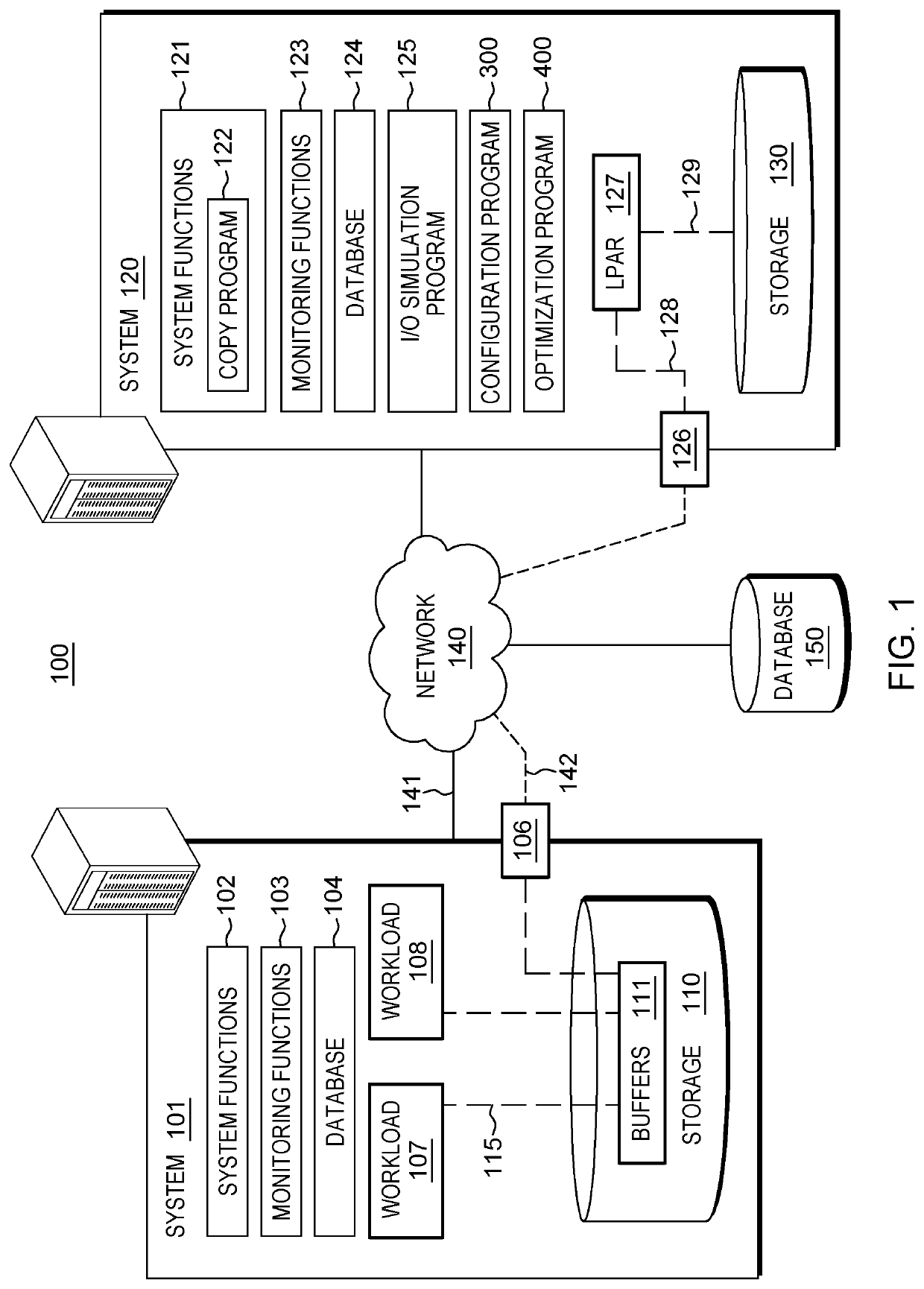
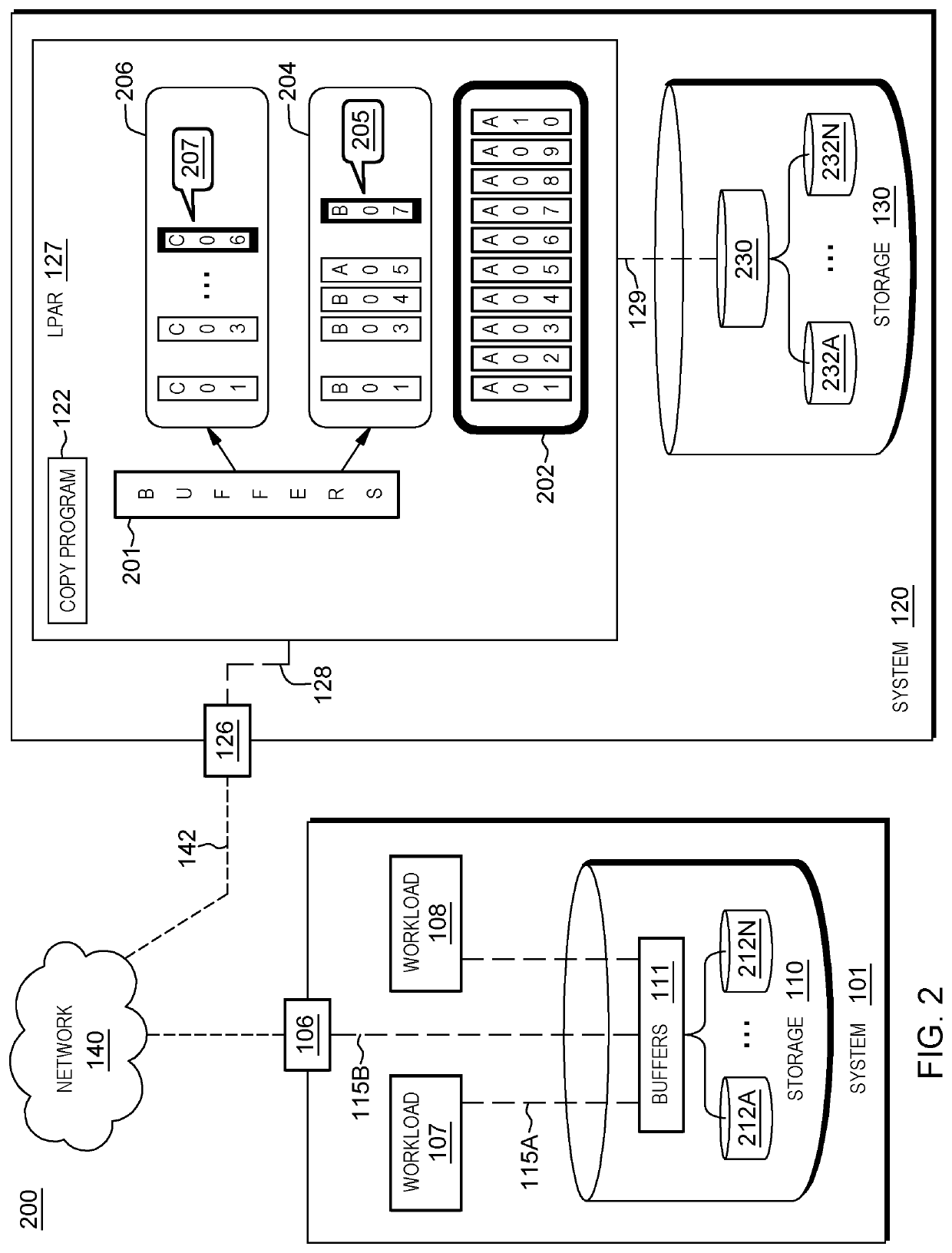
A method for modifying a configuration of a storage system. The method includes a computer processor querying a network-accessible computing system to obtain information associated with an executing application that utilizes a storage system for a process of data mirroring. The method further includes identifying a set of parameters associated with a copy program executing within a logical partition (LPAR) of the storage system based on the obtained information, where the set of parameters dictates a number of reader tasks utilized by the copy program, where the copy program is a program associated with the process for data mirroring from the network-accessible computing system to the storage system. The method further includes executing the dictated number of reader tasks for the process of mirroring data associated with the executing application, from the network-accessible computing system to the storage system.
Owner:IBM CORP
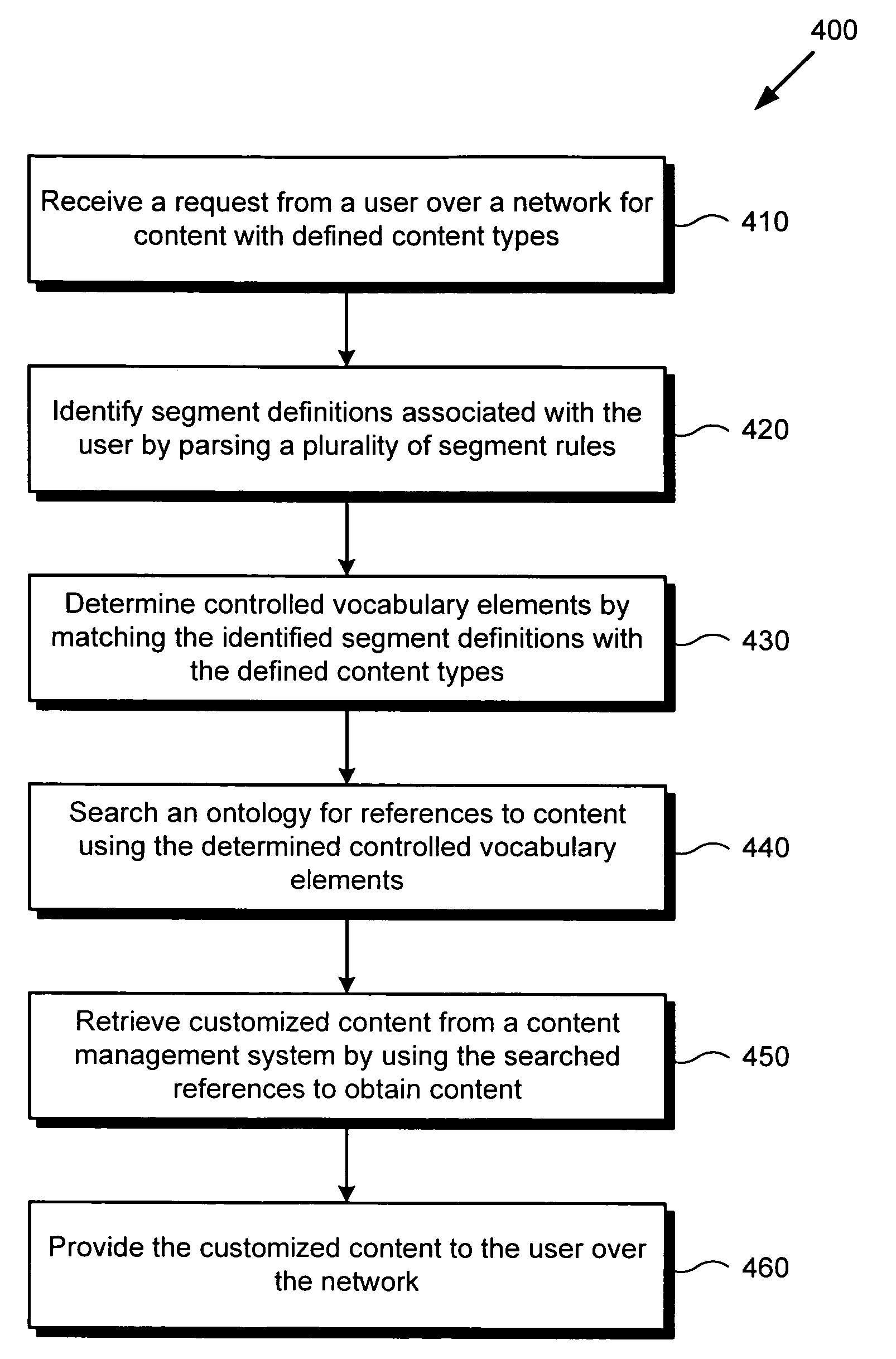
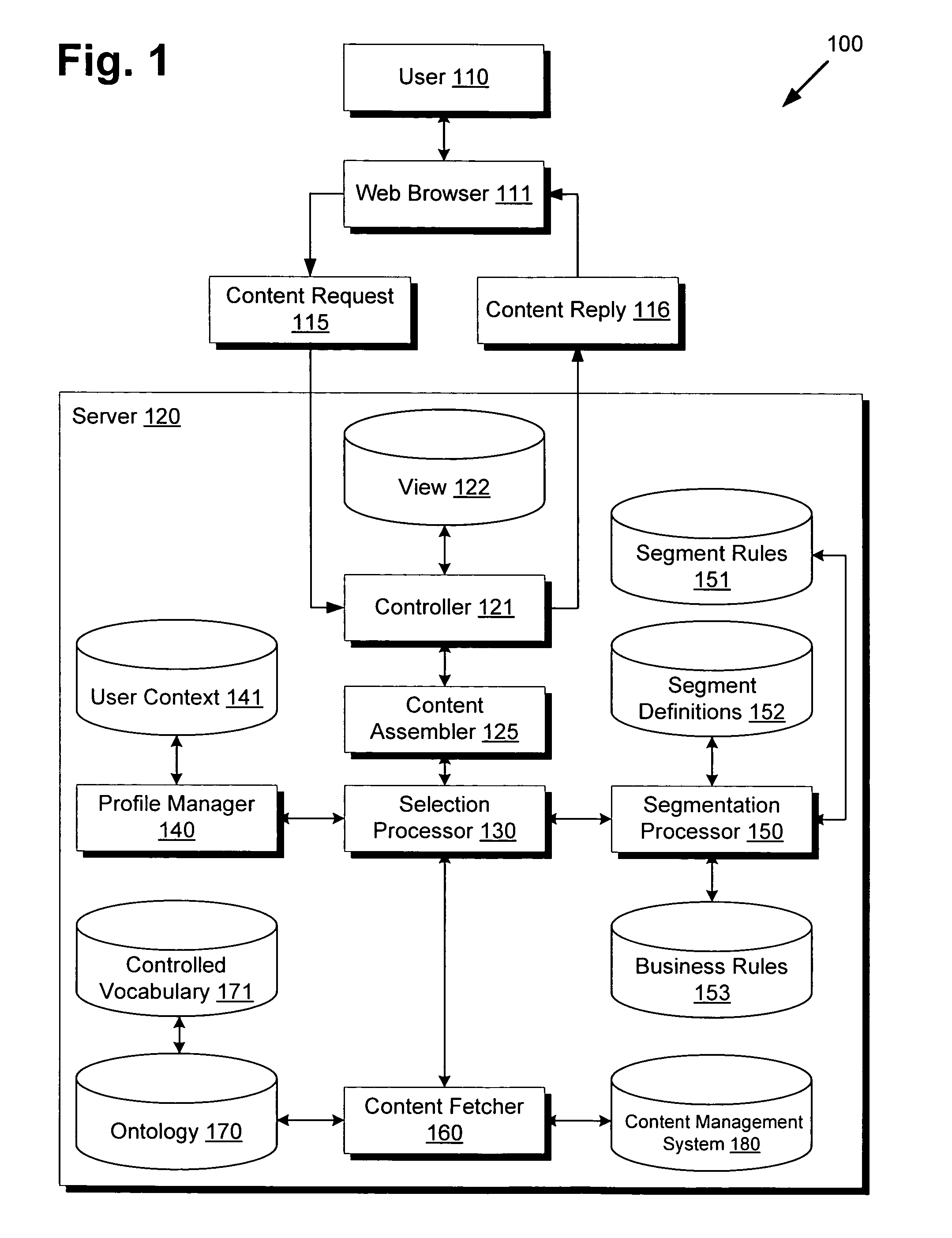
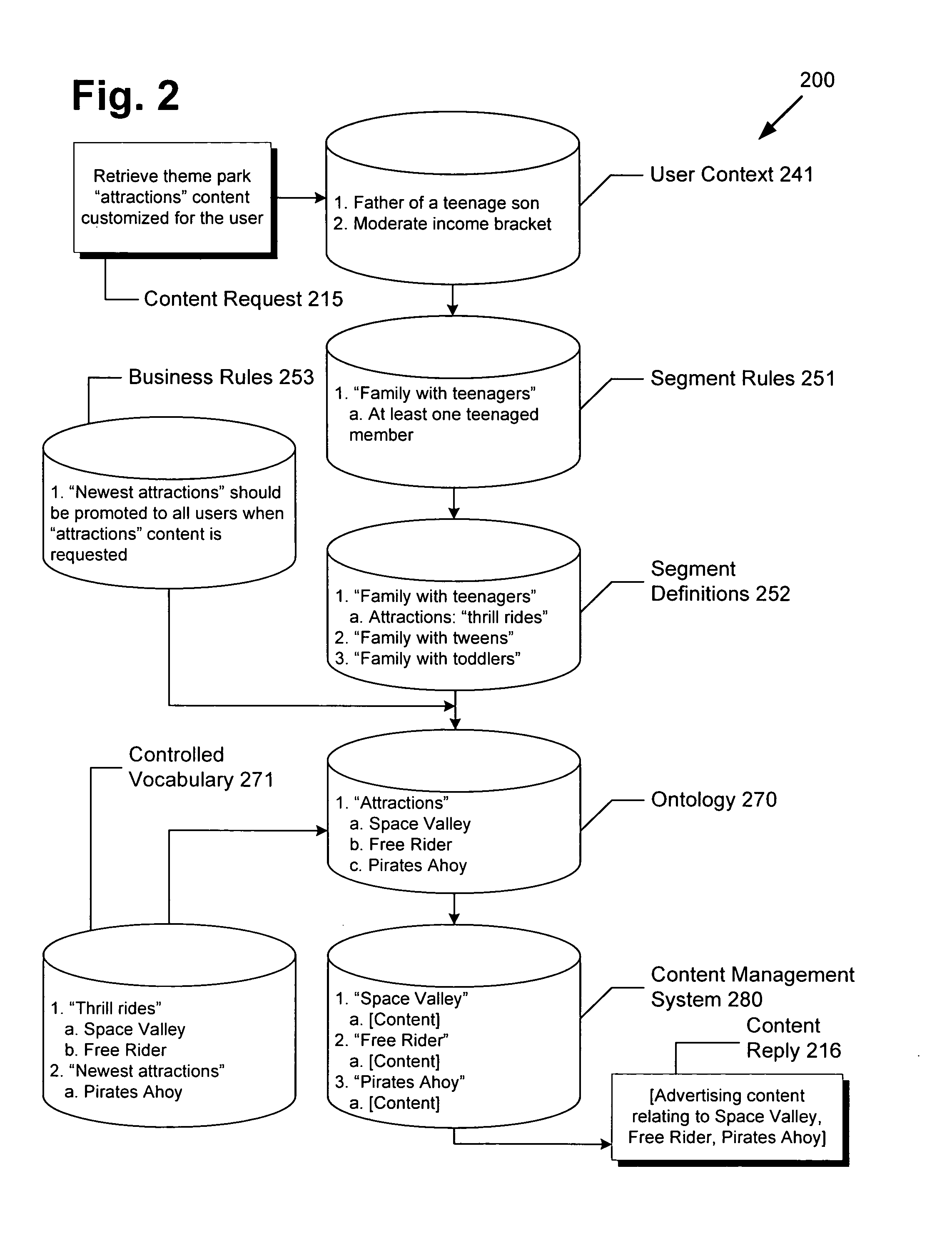
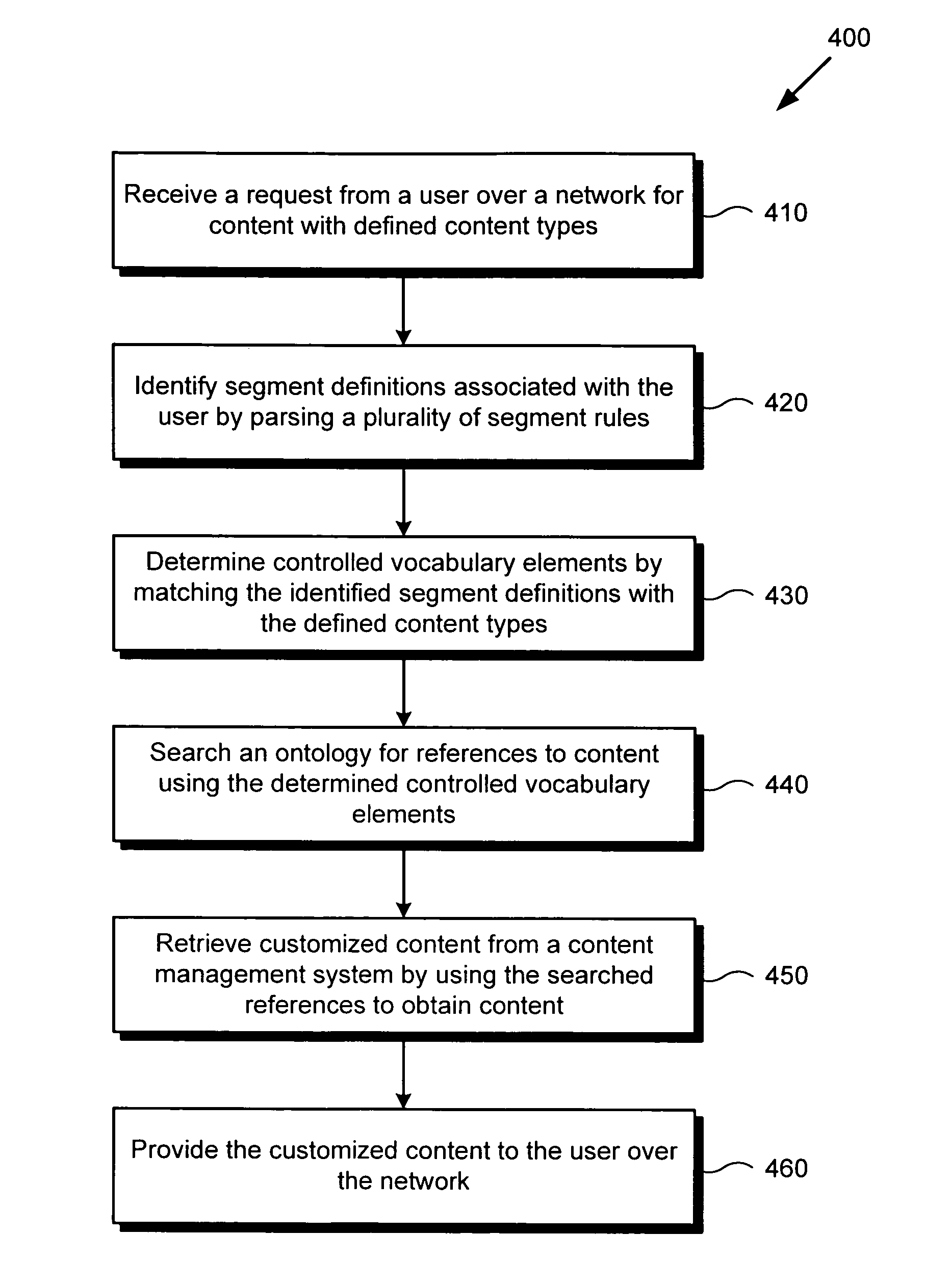
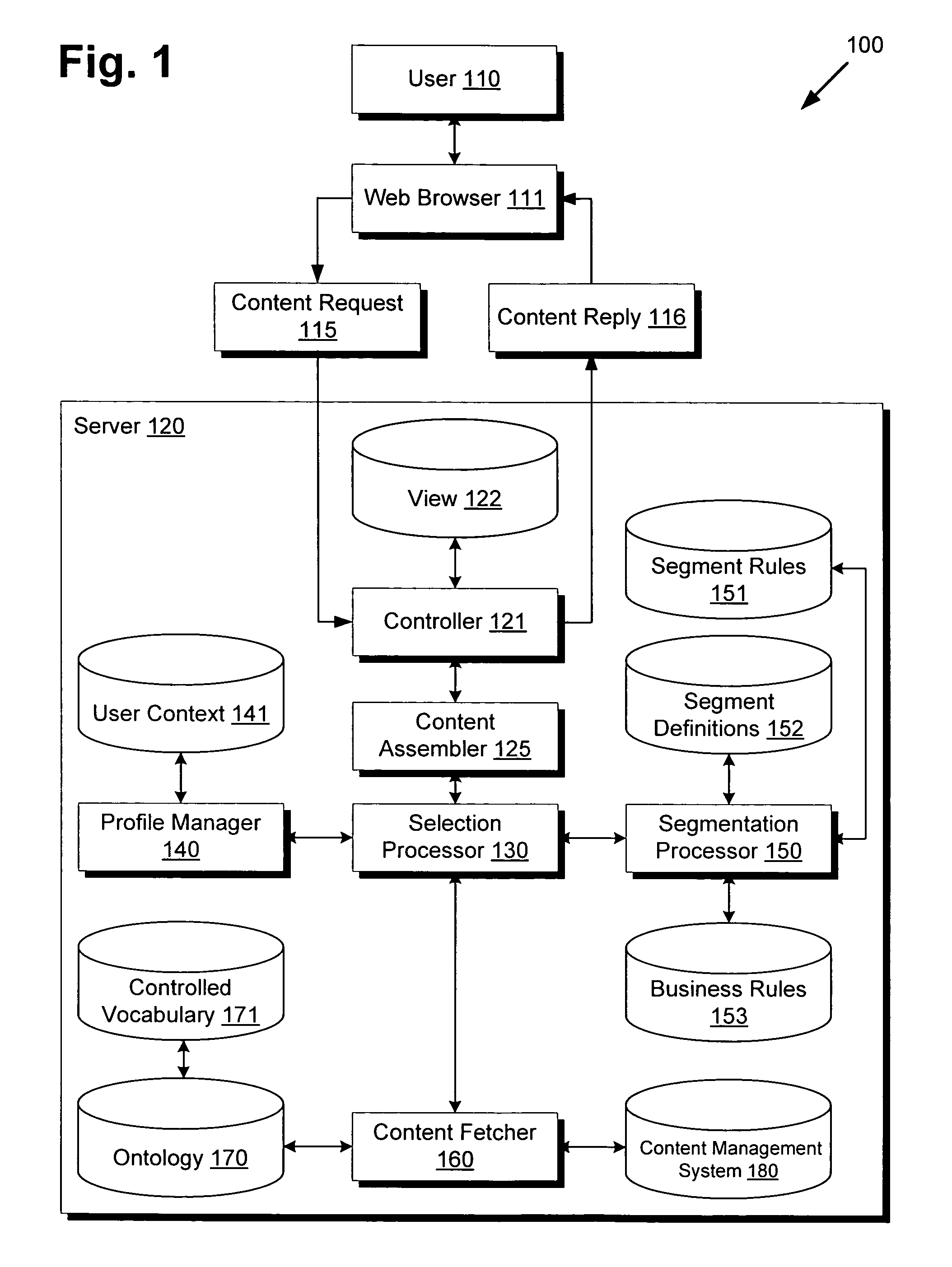
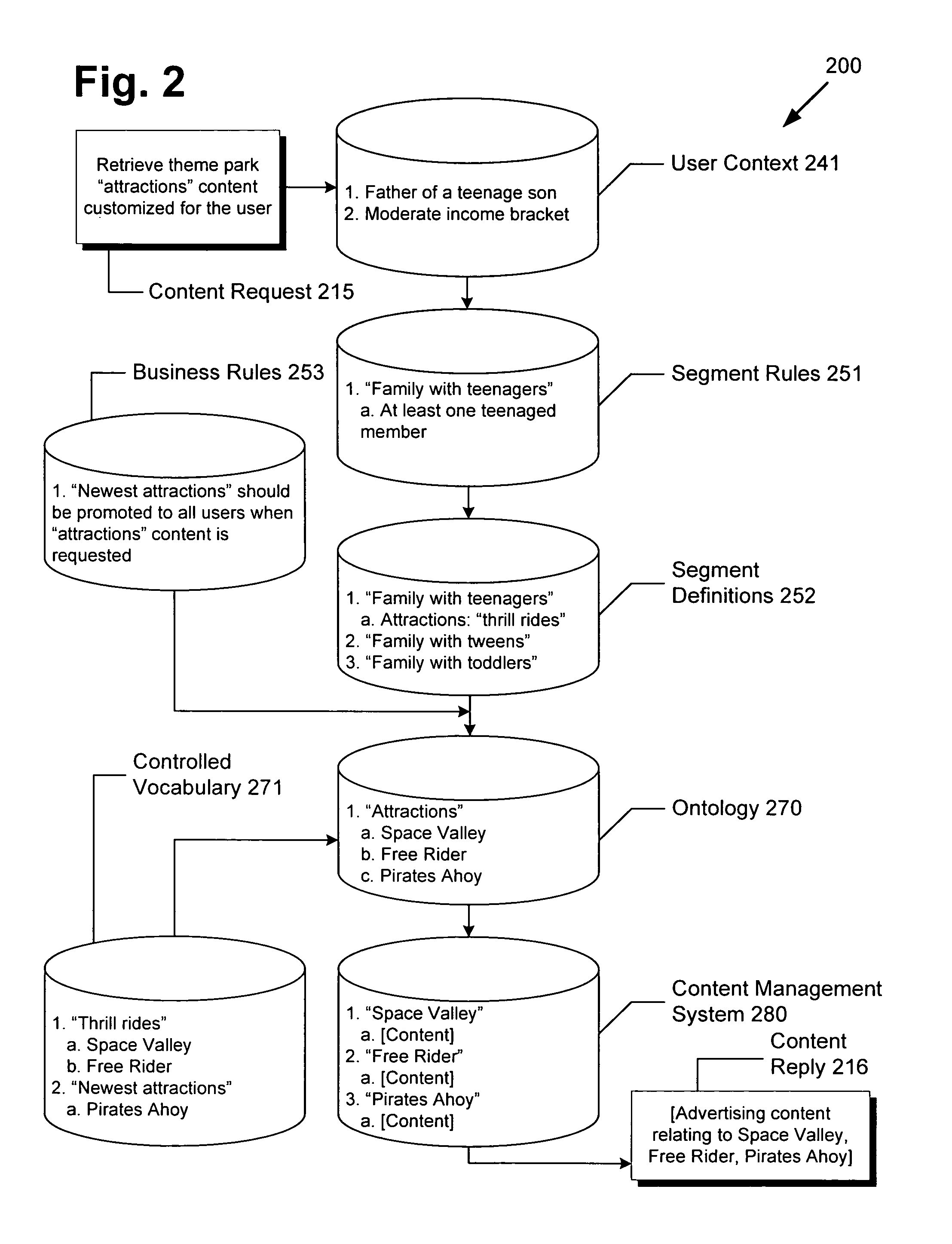
System and method for ontology and rules based segmentation engine for networked content delivery
ActiveUS20100088344A1Digital data information retrievalDigital data processing detailsControl vocabularyContent management system
There is provided a system and method for an ontological and rules based segmentation engine for networked content delivery. There is provided a segmentation engine for use by a network accessible computing device providing customized content for a user on the network, comprising a user context regarding the user, a content management system for storing content, a controlled vocabulary categorizing content, an ontology using the controlled vocabulary for referencing the content of the content management system, segment definitions grouping users into segments matching content types to controlled vocabulary elements, segment rules using user context to associate with segment definitions, and a segmentation processor. The segmentation processor can receive a content request from the user, and by using the elements of the segmentation engine, determine the segment definitions applicable to the user and provide customized content from the content management system. The segment definitions are readily modifiable without detailed low-level knowledge.
Owner:DISNEY ENTERPRISES INC
Method and apparatus for computing within a wide area network
InactiveUS20060282520A1Strong computing powerMaintain performanceMultiple digital computer combinationsTransmissionNetwork addressingNetwork address
A cluster computer system including multiple network accessible computers that are each coupled to a network. The network accessible computers implement host computer programs which permits the network accessible computers to operate as host computers for client computers also connected to the network, such that input devices of the client computers can be used to generate inputs to the host computers, and such that image information generated by the host computers can be viewed by the client computers. The system also includes a cluster administration computer coupled to the multiple network accessible computers to monitor the operation of the network accessible computers. A method for providing access to host computers by client computers over a computer network includes receiving a request for a host computer coupled to a computer network from a client computer coupled to the computer network, wherein the relationship of the host computer to the client computer is to be such that after the client computer becomes associated with a host computer, an input device of the client computer can be used to generate inputs to the host computer, and such that image information generated by the host computer can be viewed by the client computer. Next, a suitable host computer for the client computer is determined, and the client computer is informed of the network address of the suitable host computer. Nodes of the network can be non-terrestrial.
Owner:AI CORE TECH LLC +1
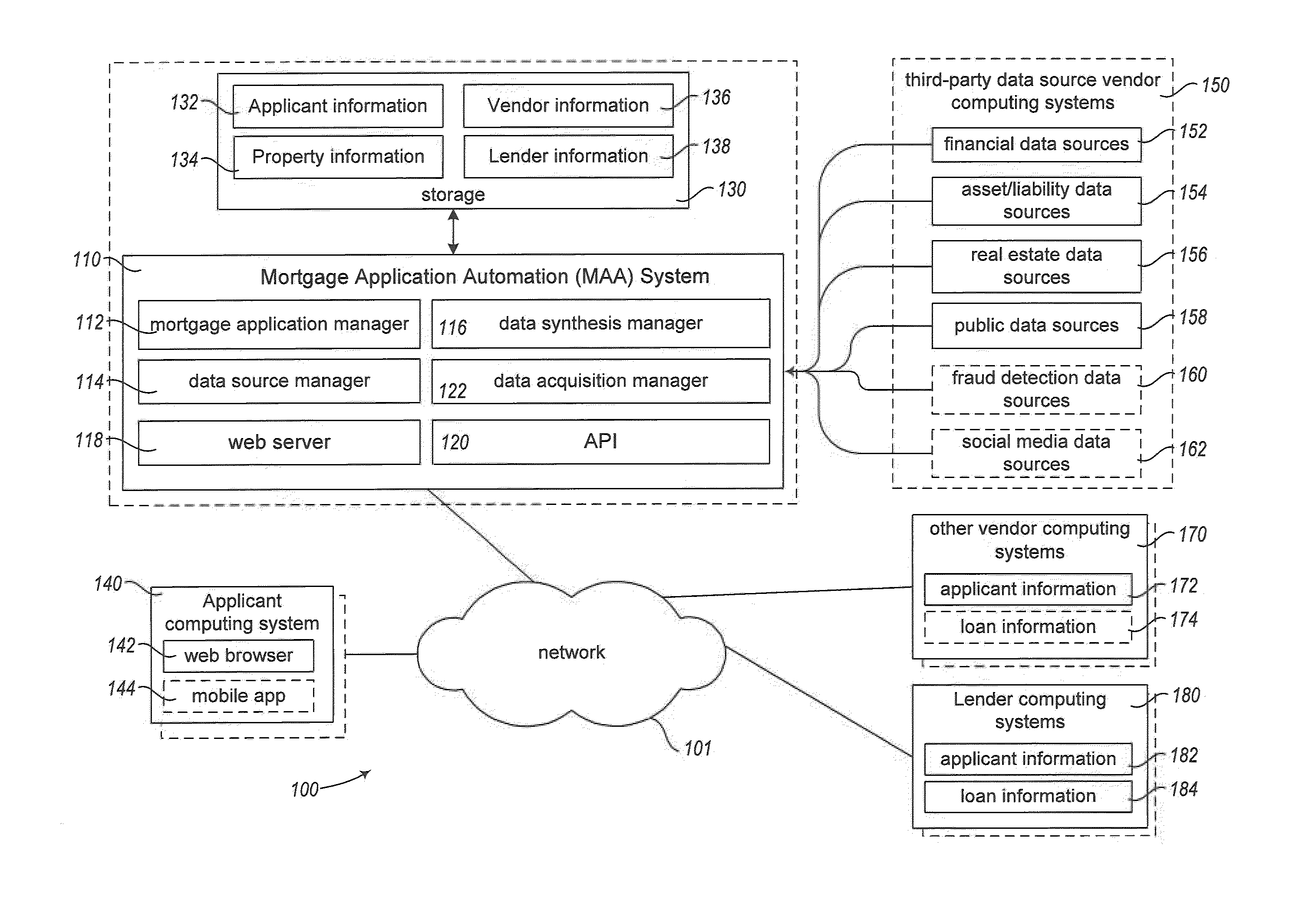
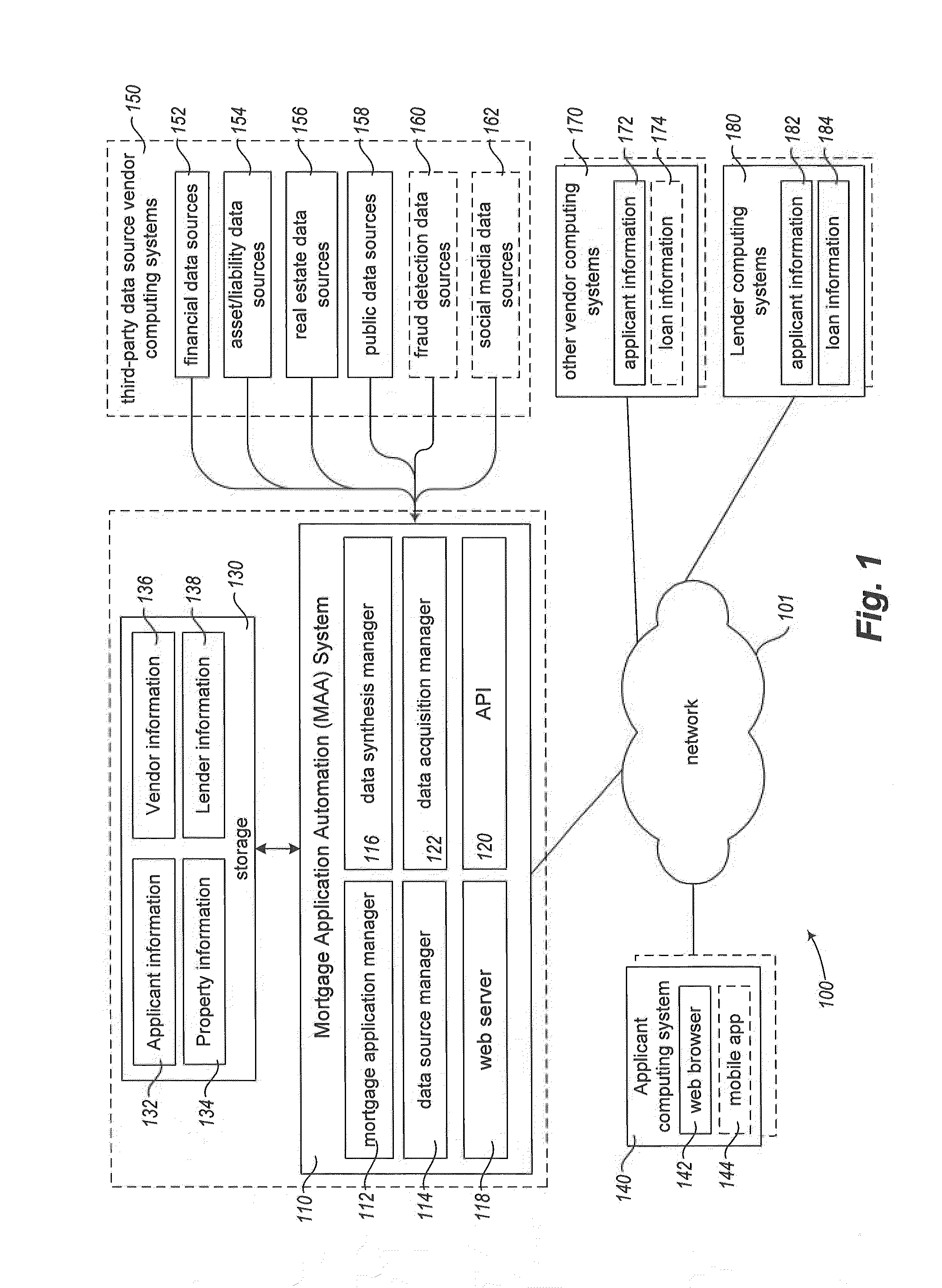
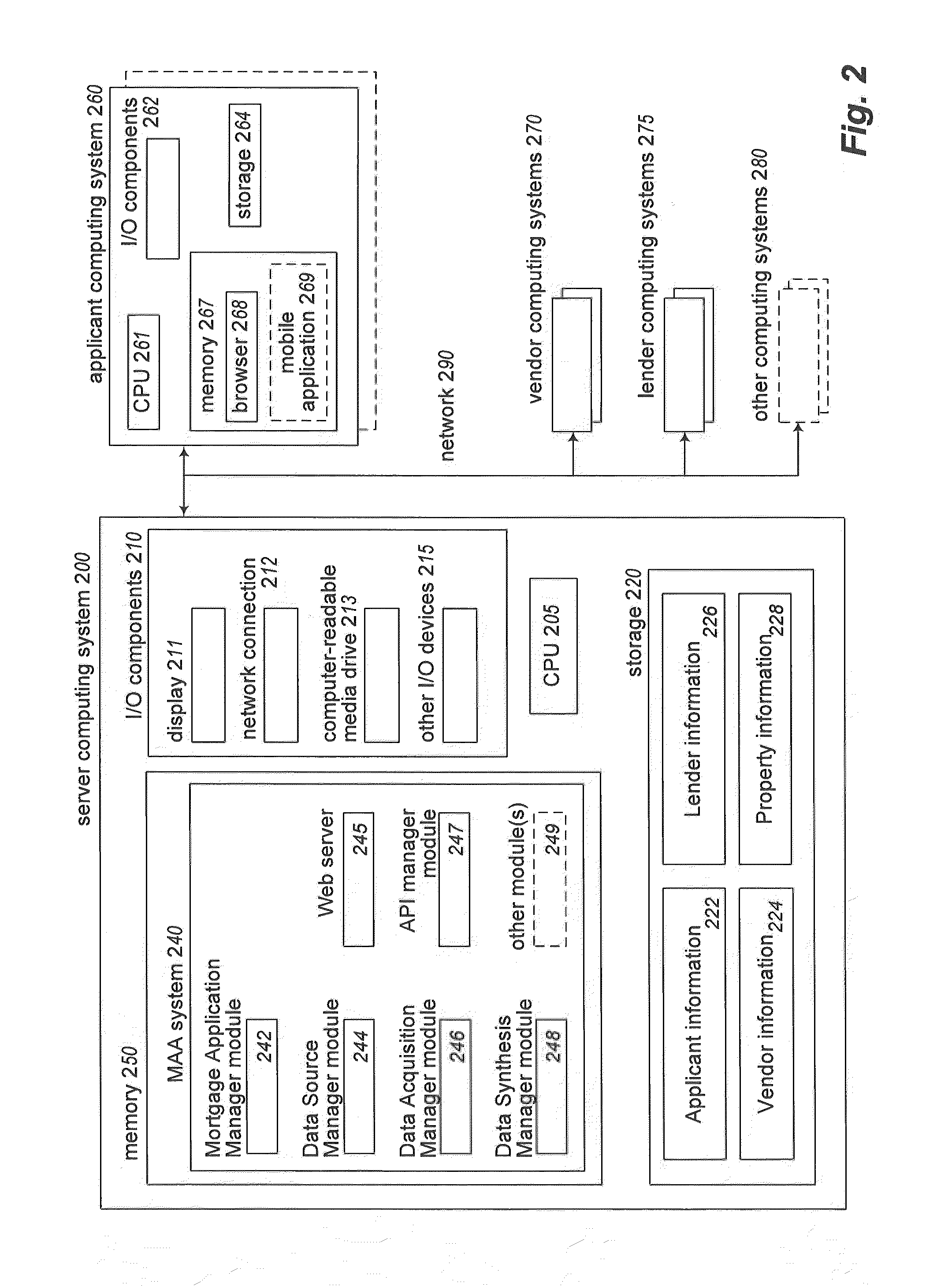
Mortgage synthesis and automation
Owner:BESMARTEE
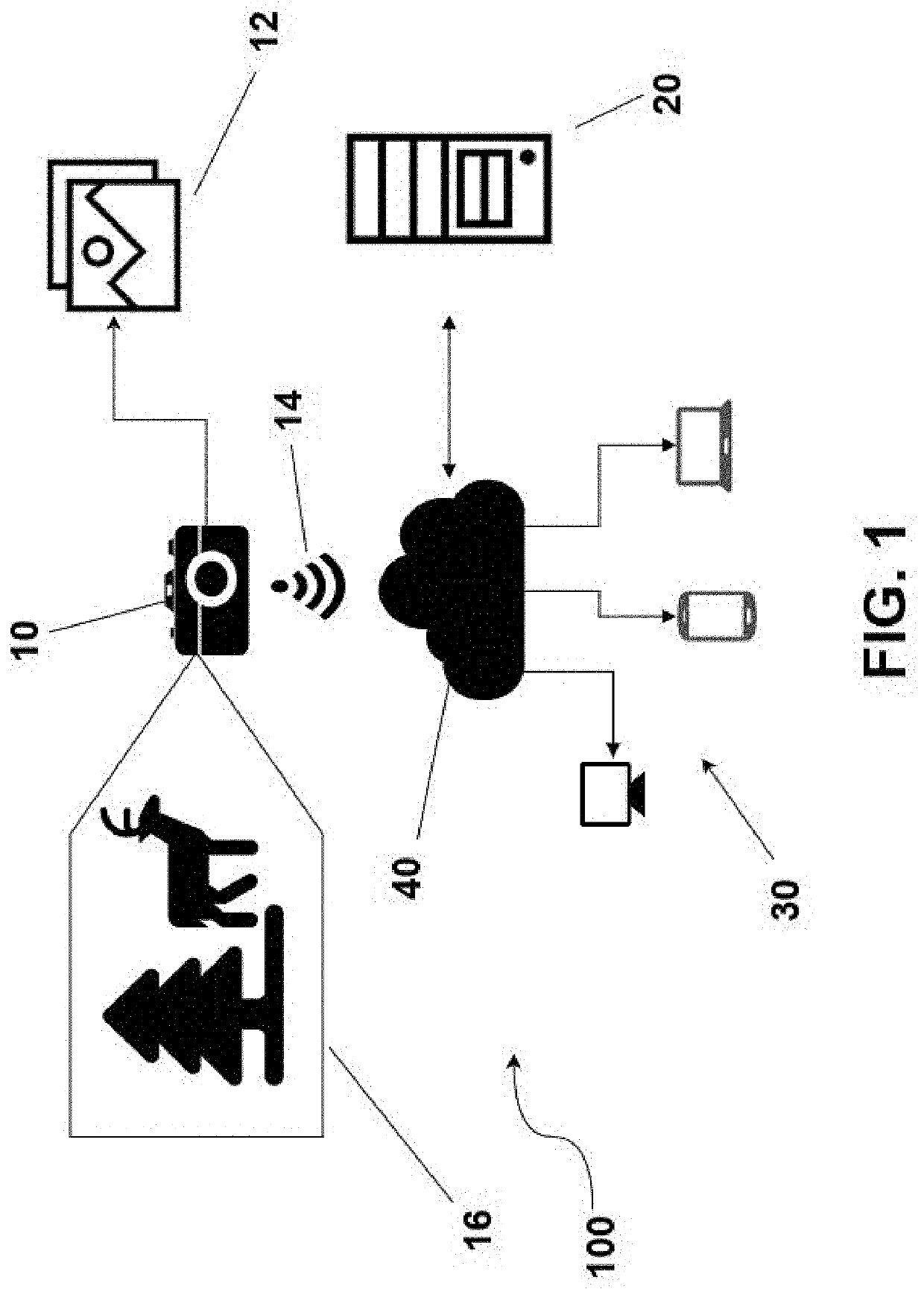
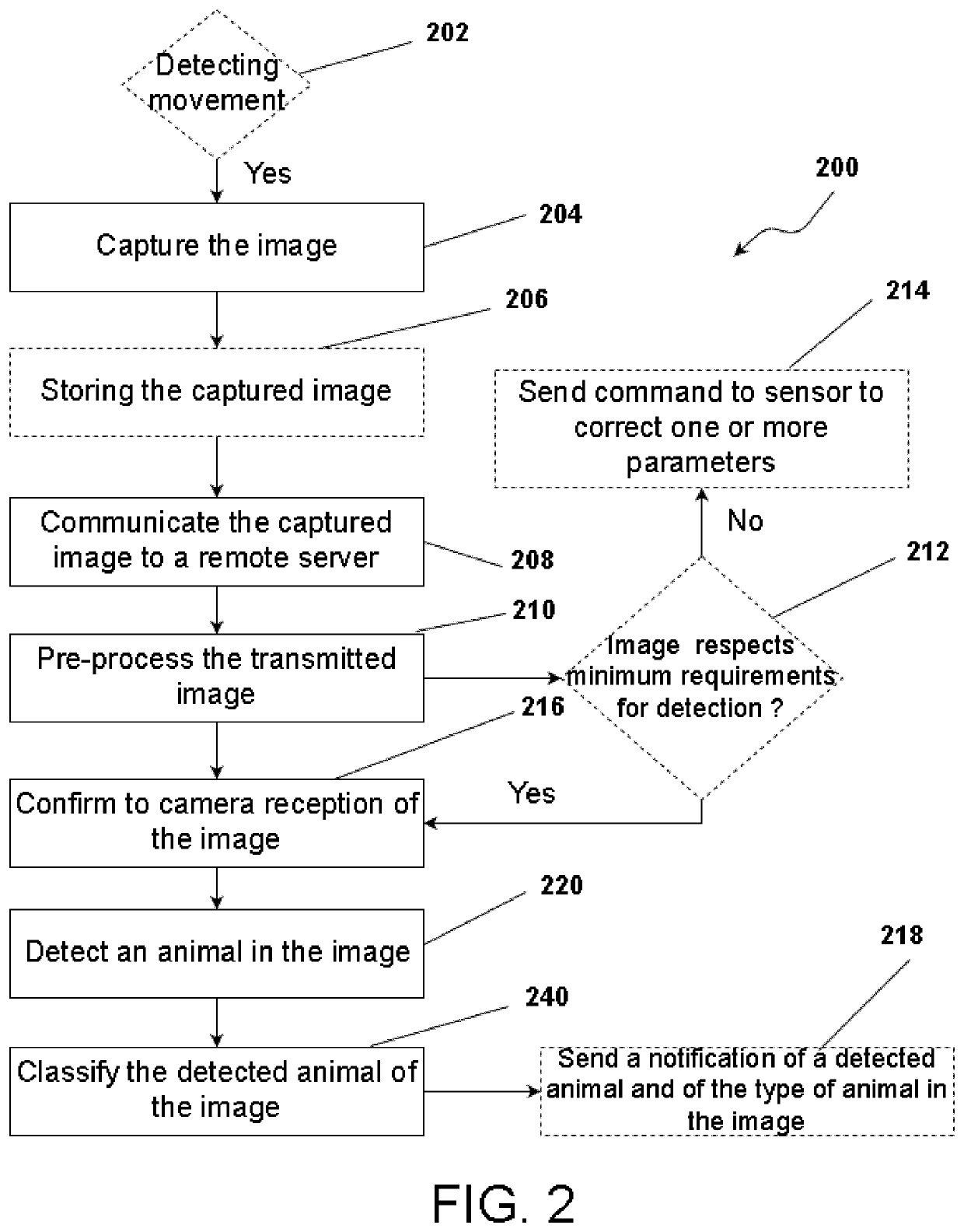
System and method for automatically detecting and classifying an animal in an image
InactiveUS20200226360A1Reduce disadvantagesTelevision system detailsImage analysisAnimal scienceComputer vision
A system for automatically identifying and classifying an animal in an image which comprises a hunting camera or sensor, a remotely server, one or more client computerized devices and a network adapted to connect the camera, the remotely accessible computing device and the client computerized devices. The hunting camera captures images of a scene of a remote area to track animals. The images are communicated to the server which process the images to automatically detect animals and to automatically classify the species, type and / or characteristic associated with the detected animal.
Owner:9138 4529 QUEBEC INC
System and method for ontology and rules based segmentation engine for networked content delivery
ActiveUS8108423B2Digital data information retrievalDigital data processing detailsControl vocabularyComputer science
There is provided a system and method for an ontological and rules based segmentation engine for networked content delivery. There is provided a segmentation engine for use by a network accessible computing device providing customized content for a user on the network, comprising a user context regarding the user, a content management system for storing content, a controlled vocabulary categorizing content, an ontology using the controlled vocabulary for referencing the content of the content management system, segment definitions grouping users into segments matching content types to controlled vocabulary elements, segment rules using user context to associate with segment definitions, and a segmentation processor. The segmentation processor can receive a content request from the user, and by using the elements of the segmentation engine, determine the segment definitions applicable to the user and provide customized content from the content management system. The segment definitions are readily modifiable without detailed low-level knowledge.
Owner:DISNEY ENTERPRISES INC
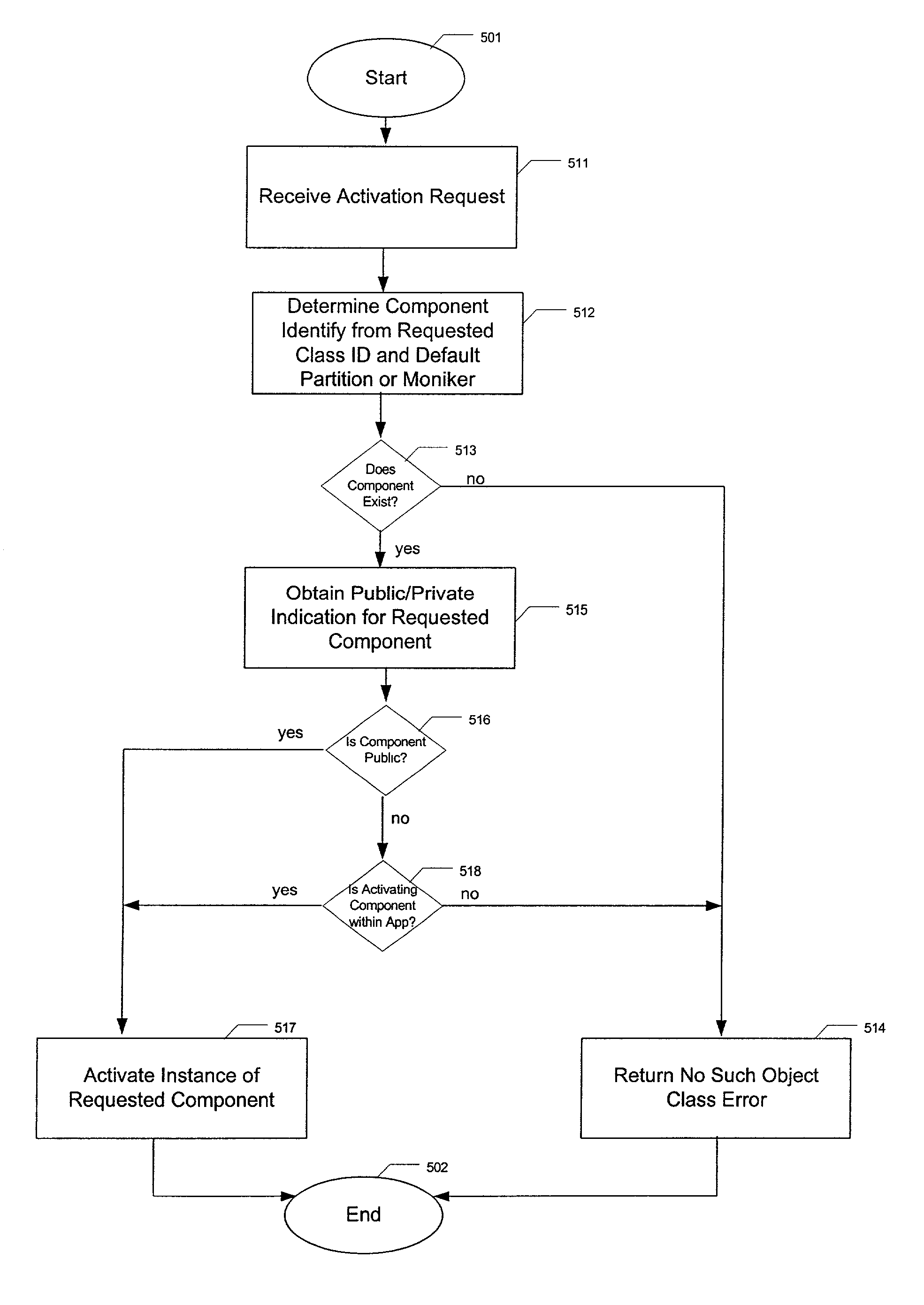
System determining whether to activate public and private components operating within multiple applications of a component-based computing system
InactiveUS6996830B1Specific access rightsMultiple digital computer combinationsComputer hardwareApplication software
A method, apparatus, and article of manufacture provide a component-based computing system having both publicly accessible and privately-only accessible computing components within multiple applications for providing component addressing / identification and naming spaces. A requested processing component is initiated by a calling component within a local computing system having one or more applications. The identity of the requested processing component, including an identity of a class ID and an identity of a partition from a request to activate a component initiated by a calling component, is obtained using configuration data for the requested component. The configuration data provides an indication of public-private status for the requested component. An instance of the requested component can be activated based on the public-private status.
Owner:MICROSOFT TECH LICENSING LLC
Systems and methods for remote forensics and data security services over public and private networks
Provided are systems and methods for employing remote forensics and data security services over public and private networks by obtaining full access to digital data from the non-transitory computer-readable media of geographically dispersed computing devices such that the entire physical or logical media from each device is fully accessible to one or more user computers over the network. This is achieved via WebSocket technology implemented in point-to-point connection configurations, WebSocket technology implemented in network based digital data software switch configurations, and in combinations thereof. Application of these systems and methods are generally employed for the purpose of conducting remote examinations and remediation efforts upon electronic data comprising non-transitory computer-readable media on a network accessible computing device. As a few examples, the application of these systems and methods may be applied for the purposes of data sharing, remote computer support, data recovery, data loss prevention, data backup, eDiscovery (electronic discovery), digital forensics, remote monitoring, audit compliance, incident response, security incident remediation, and mobile device data management purposes. Examples of computing devices include, but are not limited to, workstations, laptops, tablets, smart phones, network routers, network switches, mobile computing devices, electronic sensors, and any device comprising the Internet of Things (IoT).
Owner:SHANNON MATTHEW MARTIN +1
Method and apparatus for computing over a wide area network
InactiveUS8751597B1Strong computing powerMaintain performanceDigital data information retrievalMultiple digital computer combinationsNetwork addressingNetwork address
A cluster computer system including multiple network accessible computers that are each coupled to a network. The network accessible computers implement host computer programs which permits the network accessible computers to operate as host computers for client computers also connected to the network, such that input devices of the client computers can be used to generate inputs to the host computers, and such that image information generated by the host computers can be viewed by the client computers. The system also includes a cluster administration computer coupled to the multiple network accessible computers to monitor the operation of the network accessible computers. A method for providing access to host computers by client computers over a computer network includes receiving a request for a host computer coupled to a computer network from a client computer coupled to the computer network, wherein the relationship of the host computer to the client computer is to be such that after the client computer becomes associated with a host computer, an input device of the client computer can be used to generate inputs to the host computer, and such that image information generated by the host computer can be viewed by the client computer. Next, a suitable host computer for the client computer is determined, and the client computer is informed of the network address of the suitable host computer.
Owner:INTELLECTUAL VENTURES II +1
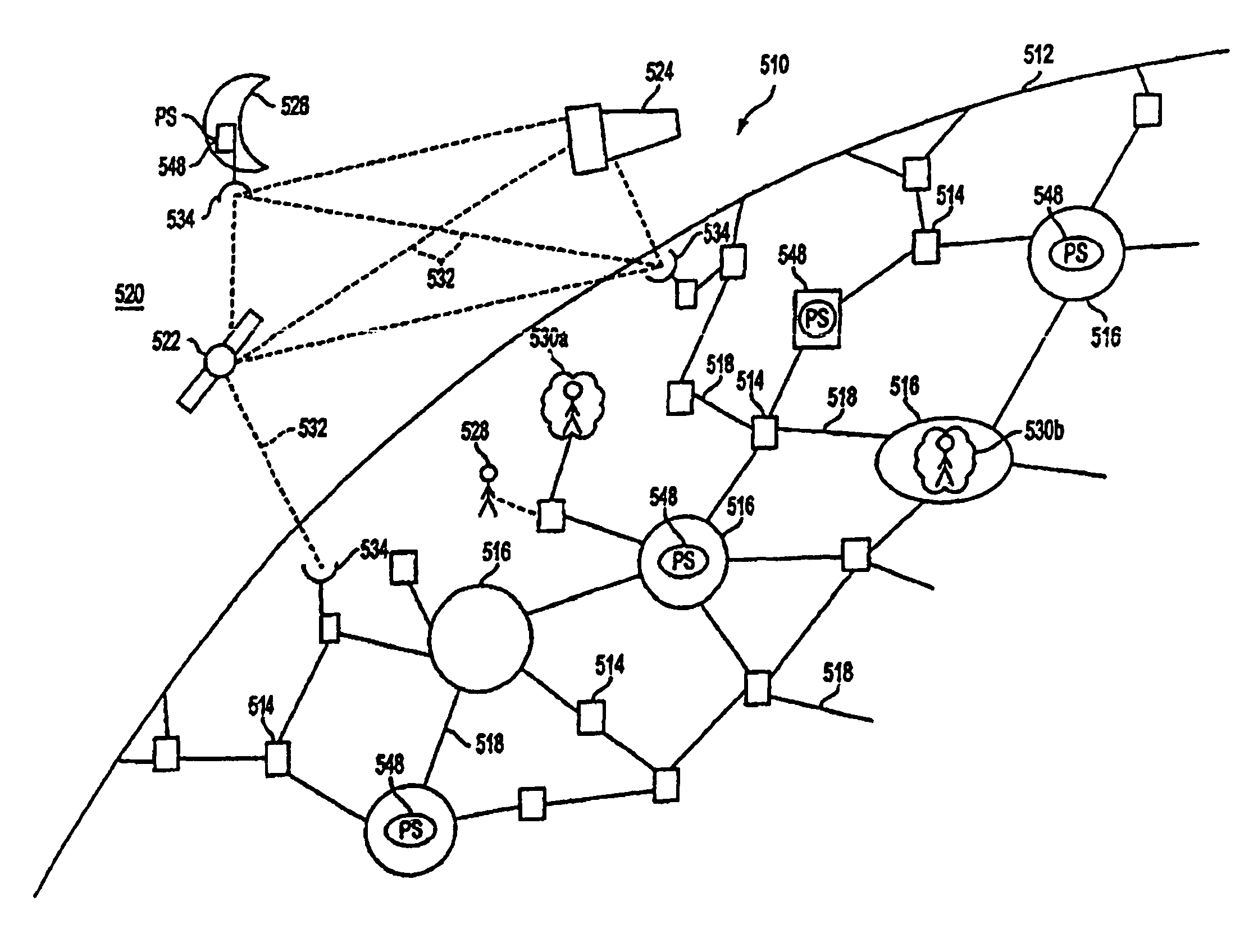
TCP/IP protocol network with satellite nodes
InactiveUS9094384B2Strong computing powerMaintain performanceMultiple digital computer combinationsRadio transmissionNetwork addressingNetwork address
A cluster computer system including multiple network accessible computers that are each coupled to a network. The network accessible computers implement host computer programs which permits the network accessible computers to operate as host computers for client computers also connected to the network, such that input devices of the client computers can be used to generate inputs to the host computers, and such that image information generated by the host computers can be viewed by the client computers. The system also includes a cluster administration computer coupled to the multiple network accessible computers to monitor the operation of the network accessible computers. A method for providing access to host computers by client computers over a computer network includes receiving a request for a host computer coupled to a computer network from a client computer coupled to the computer network, wherein the relationship of the host computer to the client computer is to be such that after the client computer becomes associated with a host computer, an input device of the client computer can be used to generate inputs to the host computer, and such that image information generated by the host computer can be viewed by the client computer. Next, a suitable host computer for the client computer is determined, and the client computer is informed of the network address of the suitable host computer.
Owner:GULA CONSULTING LLC
Modifying aspects of a storage system associated with data mirroring
A method for modifying a configuration of a storage system. The method includes a computer processor querying a network-accessible computing system to obtain information associated with an executing application that utilizes a storage system for a process of data mirroring. The method further includes identifying a set of parameters associated with a copy program executing within a logical partition (LIAR) of the storage system based on the obtained information, where the set of parameters dictates a number of reader tasks utilized by the copy program, where the copy program is a program associated with the process for data mirroring from the network-accessible computing system to the storage system. The method further includes executing the dictated number of reader tasks for the process of mirroring data associated with the executing application, from the network-accessible computing system to the storage system.
Owner:INT BUSINESS MASCH CORP
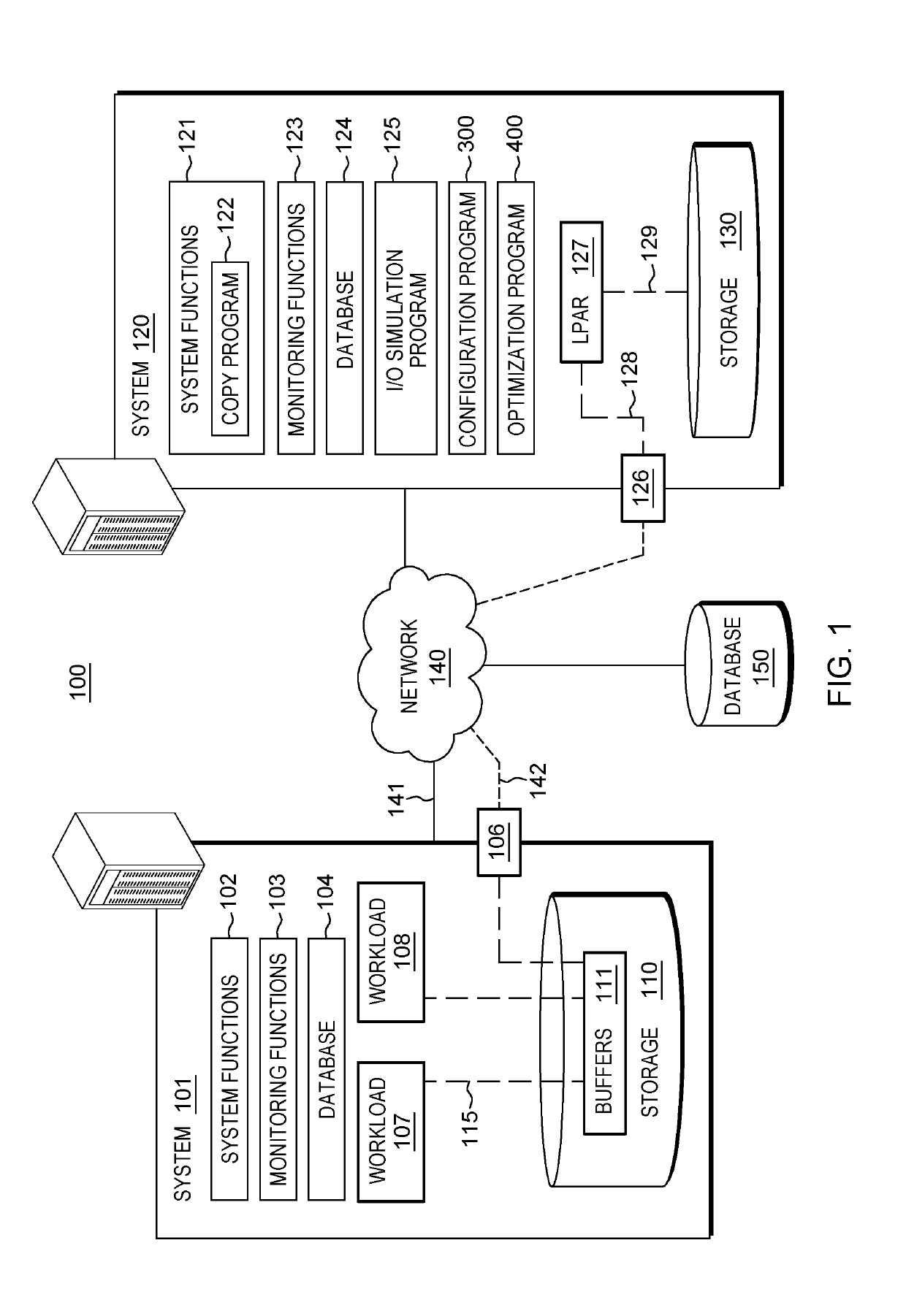
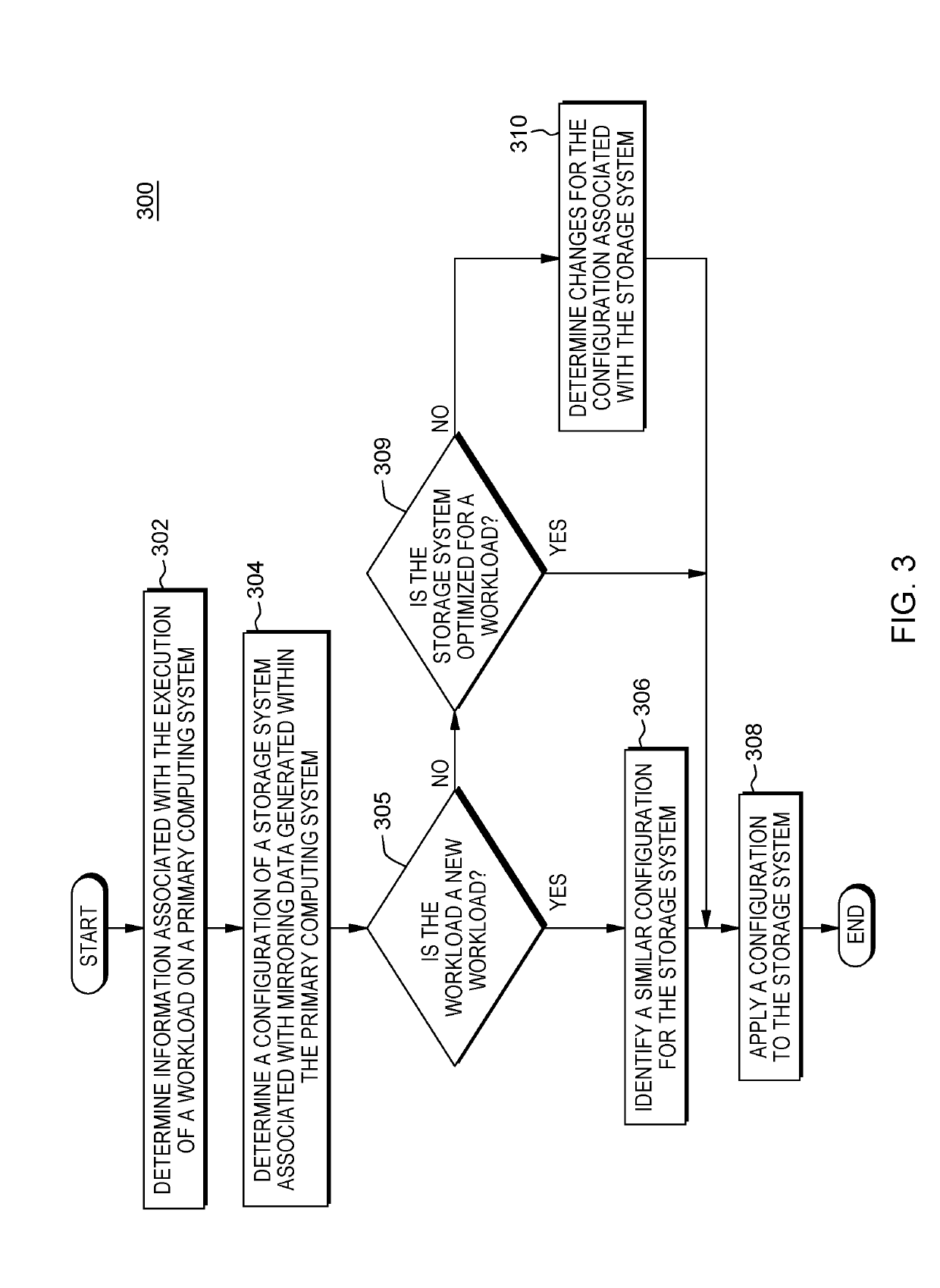
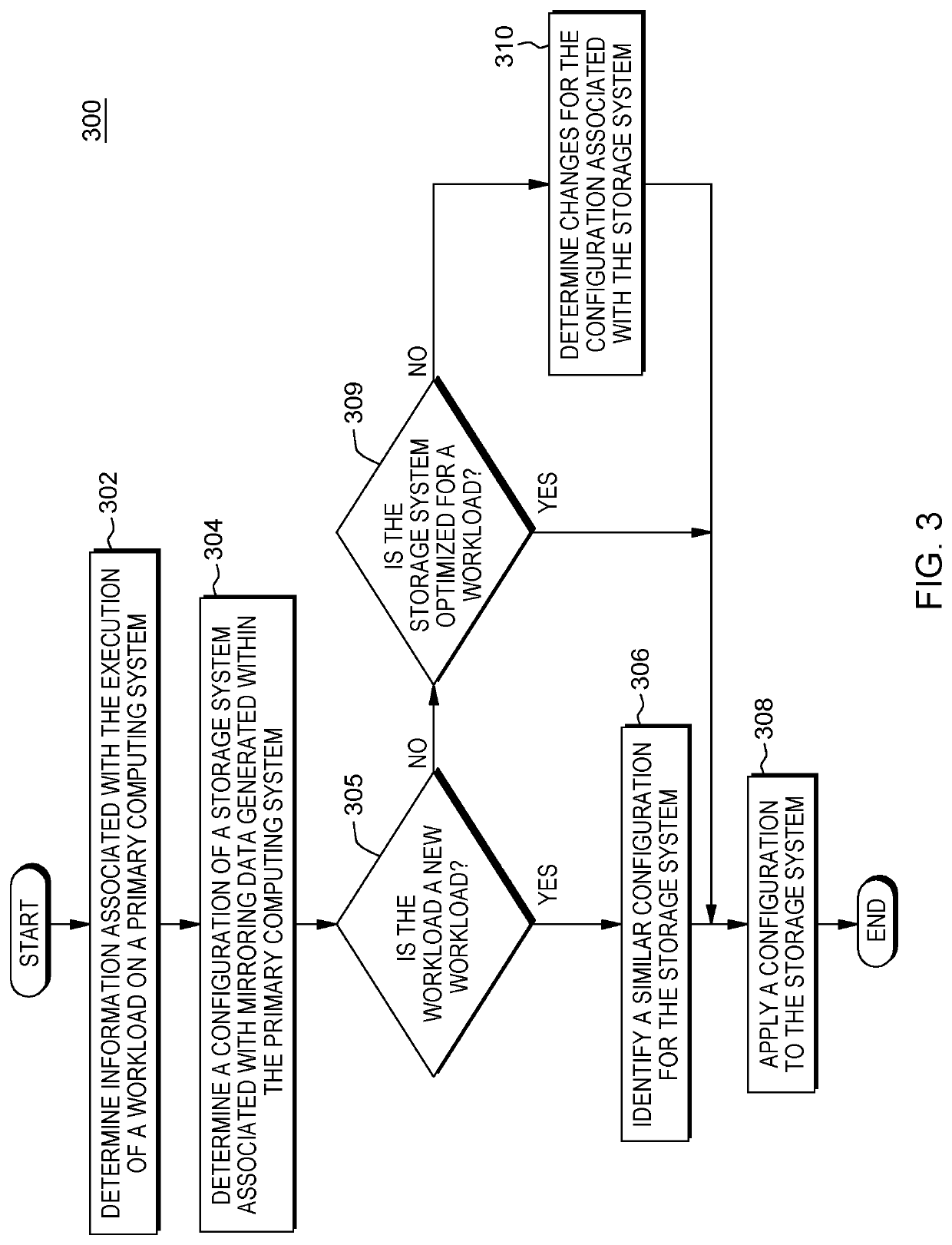
Configuring a secondary storage system for data mirroring
A method for configuring a storage system. The method includes a computer processor receiving at a storage system, an indication to initiate data mirroring for an application. The method further includes determining a set of information associated with a network-accessible computing system that hosts the application. The method further includes identifying an analysis of historic performance data associated with data mirroring to the storage system with respect to the application. The method further includes identifying a set configuration information associated with data mirroring from among a plurality of sets of configuration information associated with data mirroring based, at least in part, on the determined set of information associated with the network-accessible computing system and the identified analysis of performance data associated with data mirroring with respect to the application. The method further includes applying the identified set configuration information associated with data mirroring for the application to the storage system.
Owner:IBM CORP
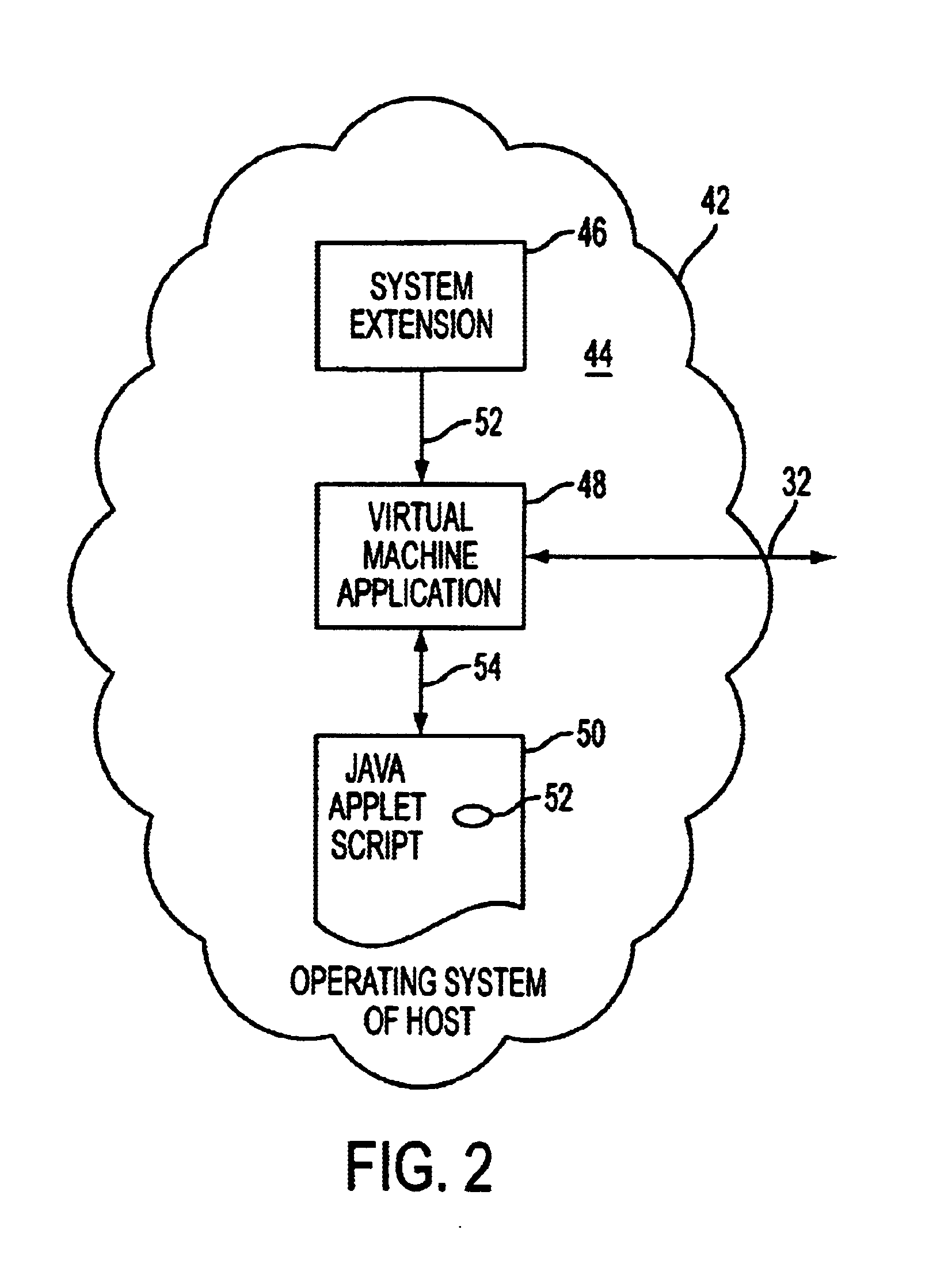
Container Interrupt Services
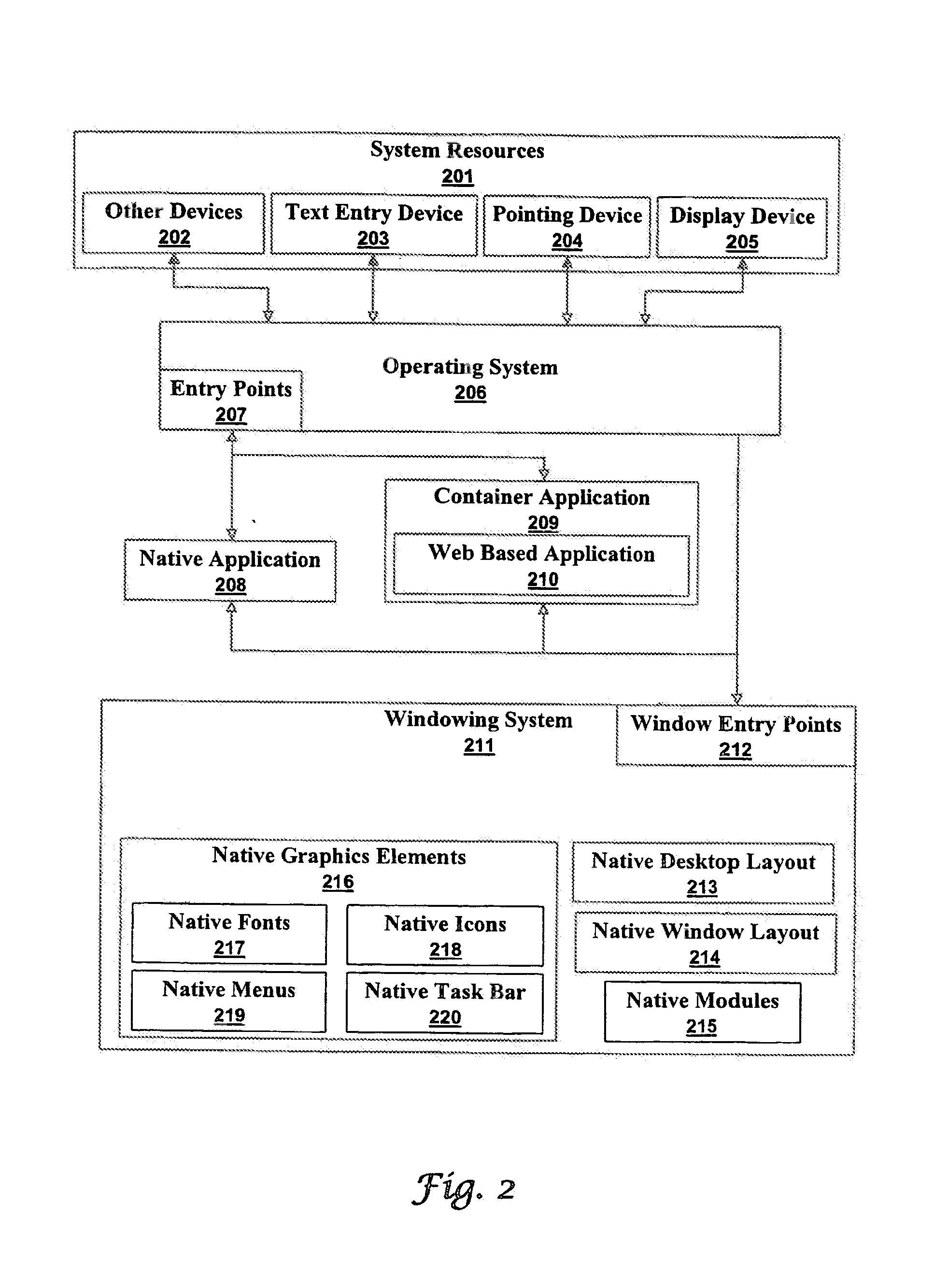
ActiveUS20140101295A1Multiple digital computer combinationsTransmissionApplication serverOperational system
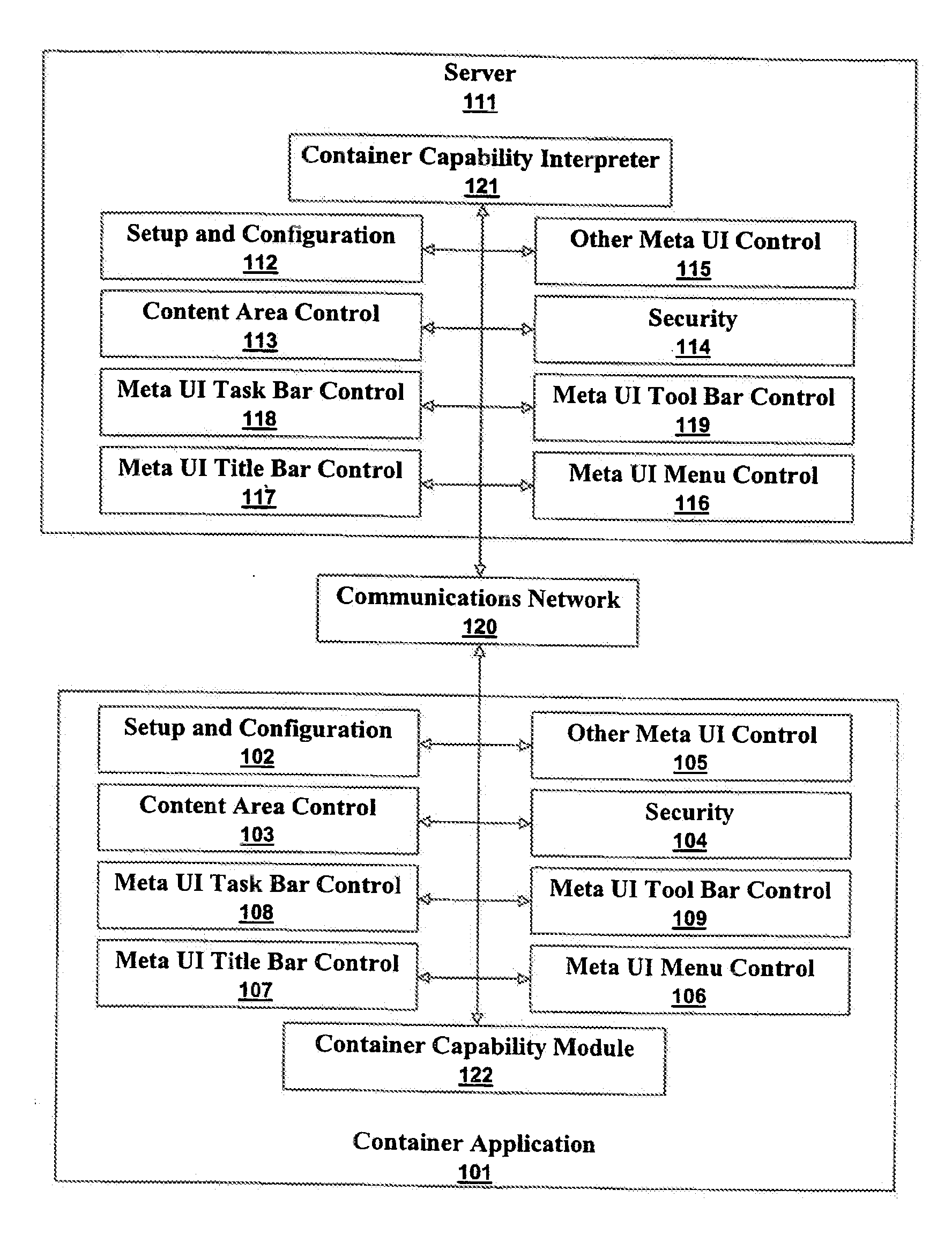
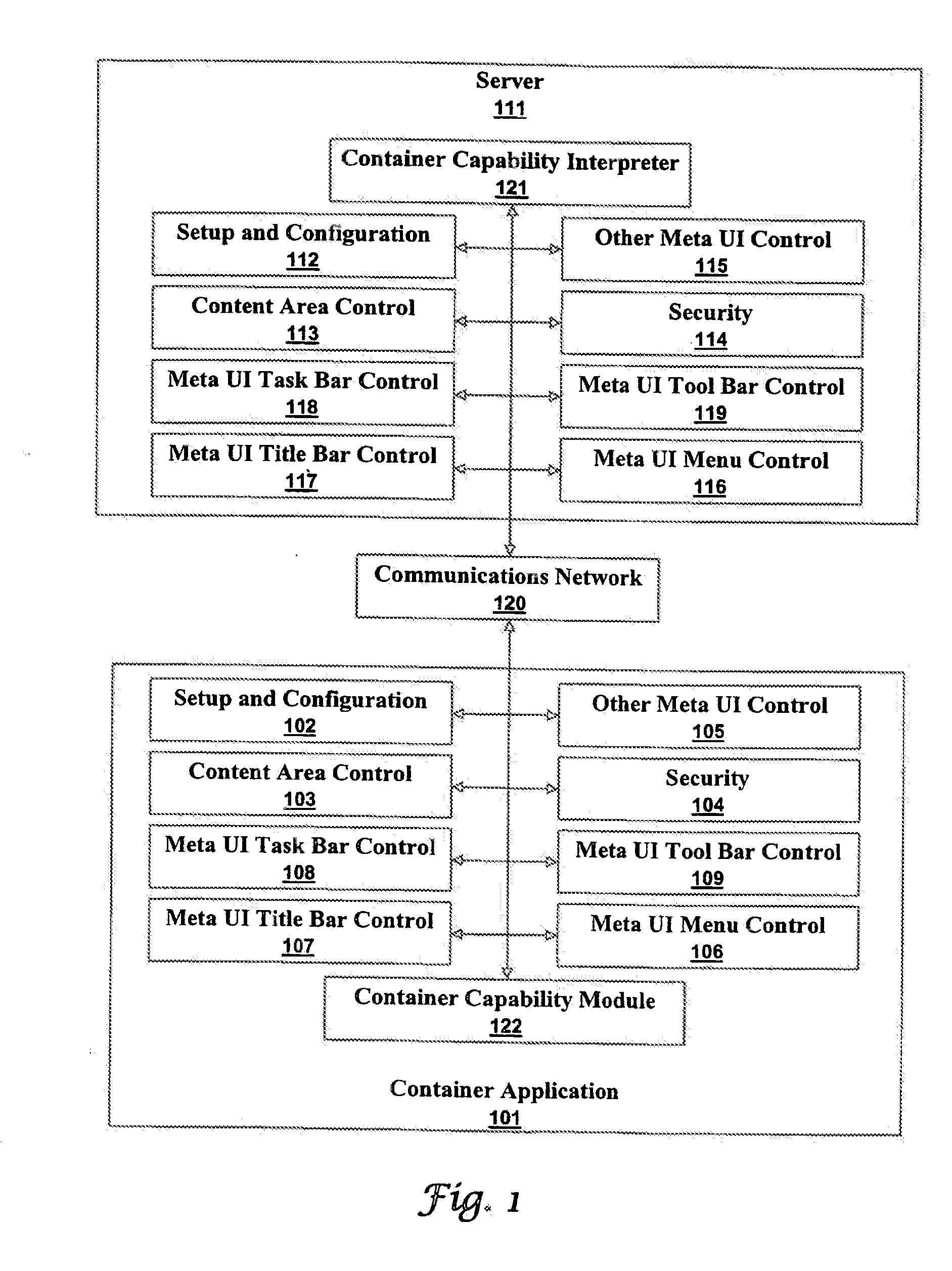
A container application is a native application that provides a web based application with access a computer's system resources and windowing system. If a container application is associated with a window, then the web based application can alter or control many, or all, aspects of the container application's content area and meta user interfaces (Uis). Web based applications are downloaded from application servers and run inside container applications. A container application can run a web based application as a service. Services made from web based applications running in container applications are almost indistinguishable from operating system services when there is no associated window.
Owner:GOOGLE LLC
Configuring a secondary storage system for data mirroring
A method for configuring a storage system. The method includes a computer processor receiving at a storage system, an indication to initiate data mirroring for an application. The method further includes determining a set of information associated with a network-accessible computing system that hosts the application. The method further includes identifying an analysis of historic performance data associated with data mirroring to the storage system with respect to the application. The method further includes identifying a set configuration information associated with data mirroring from among a plurality of sets of configuration information associated with data mirroring based, at least in part, on the determined set of information associated with the network-accessible computing system and the identified analysis of performance data associated with data mirroring with respect to the application. The method further includes applying the identified set configuration information associated with data mirroring for the application to the storage system.
Owner:INT BUSINESS MASCH CORP
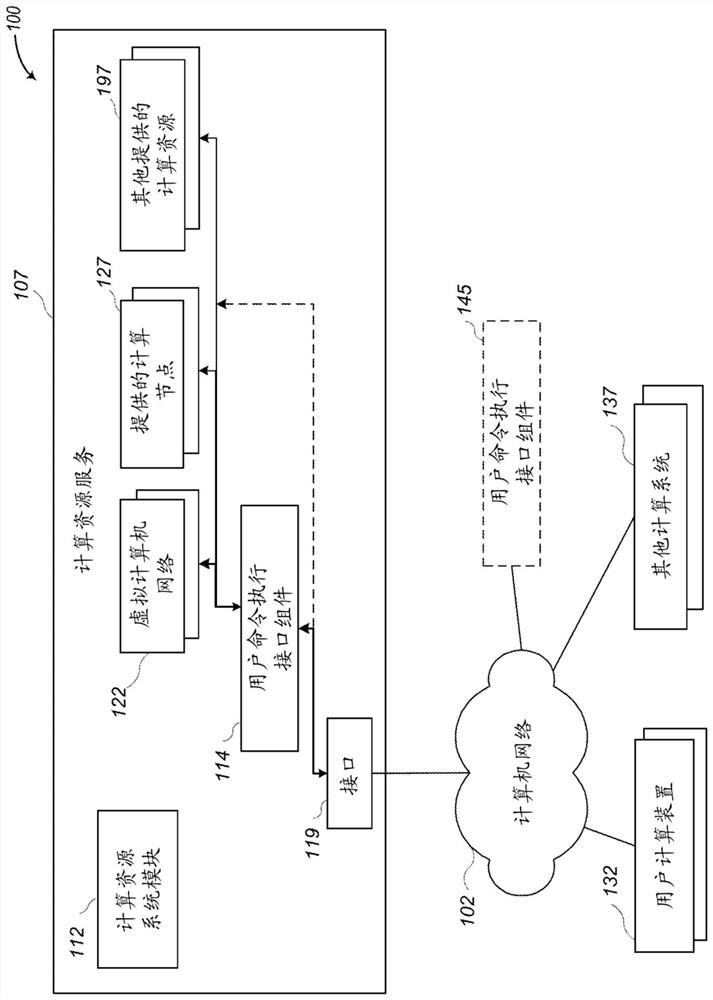
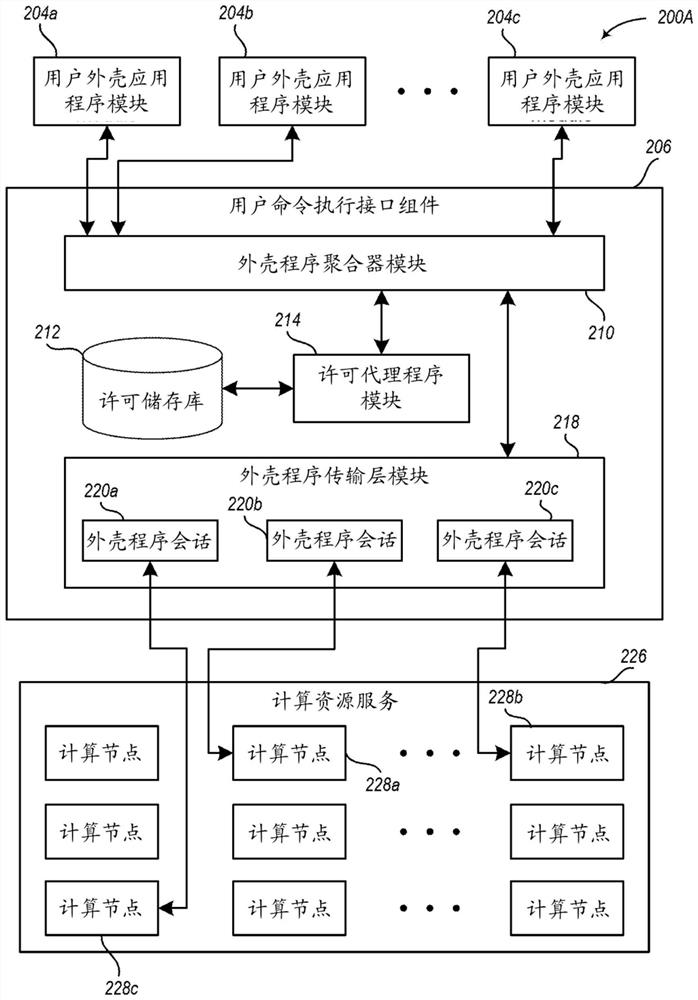
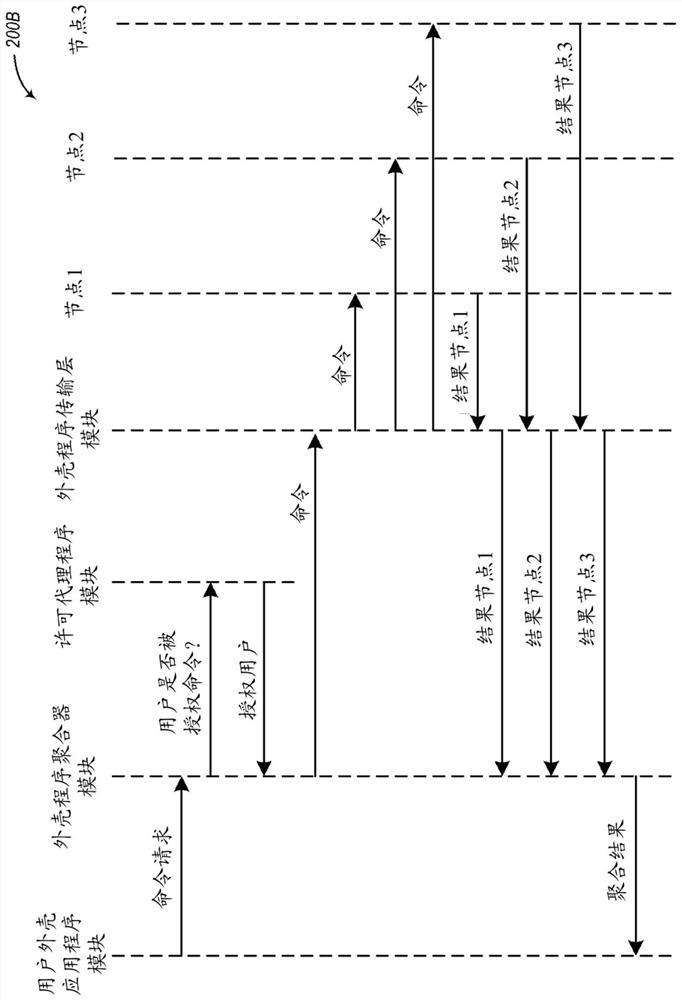
Systems and methods for controlling user access to command execution
This disclosure describes techniques for providing users with access to execute commands on network-accessible computing resources. In some cases, permissions are established for users to execute commands on computing nodes provided by online services, such as by maintaining various permission information external to those provided computing nodes, for use in controlling user access, use and / or Ability to modify provided compute nodes. The interface component may use such external permission information in order to determine whether a particular user is authorized to execute one or more particular commands on one or more particular compute nodes, and when authorized to initiate concurrently and independently Execute said command. The interface component can also aggregate results from each compute node executing the command before providing the results to the user.
Owner:AMAZON TECH INC
Method and apparatus for computing within a wide area network
InactiveUS9338217B2Strong computing powerMaintain performanceMultiple digital computer combinationsTransmissionNetwork addressingNetwork address
A cluster computer system including multiple network accessible computers that are each coupled to a network. The network accessible computers implement host computer programs which permits the network accessible computers to operate as host computers for client computers also connected to the network, such that input devices of the client computers can be used to generate inputs to the host computers, and such that image information generated by the host computers can be viewed by the client computers. The system also includes a cluster administration computer coupled to the multiple network accessible computers to monitor the operation of the network accessible computers. A method for providing access to host computers by client computers over a computer network includes receiving a request for a host computer coupled to a computer network from a client computer coupled to the computer network, wherein the relationship of the host computer to the client computer is to be such that after the client computer becomes associated with a host computer, an input device of the client computer can be used to generate inputs to the host computer, and such that image information generated by the host computer can be viewed by the client computer. Next, a suitable host computer for the client computer is determined, and the client computer is informed of the network address of the suitable host computer.
Owner:AI CORE TECH LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com