System determining whether to activate public and private components operating within multiple applications of a component-based computing system
a component-based computing and component technology, applied in the field can solve problems such as the inability to activate public and private components operating within multiple applications of component-based computing systems, the inability to implement mechanisms, and the vulnerability of component-based systems to several different types of inappropriate and unauthorized behavior
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
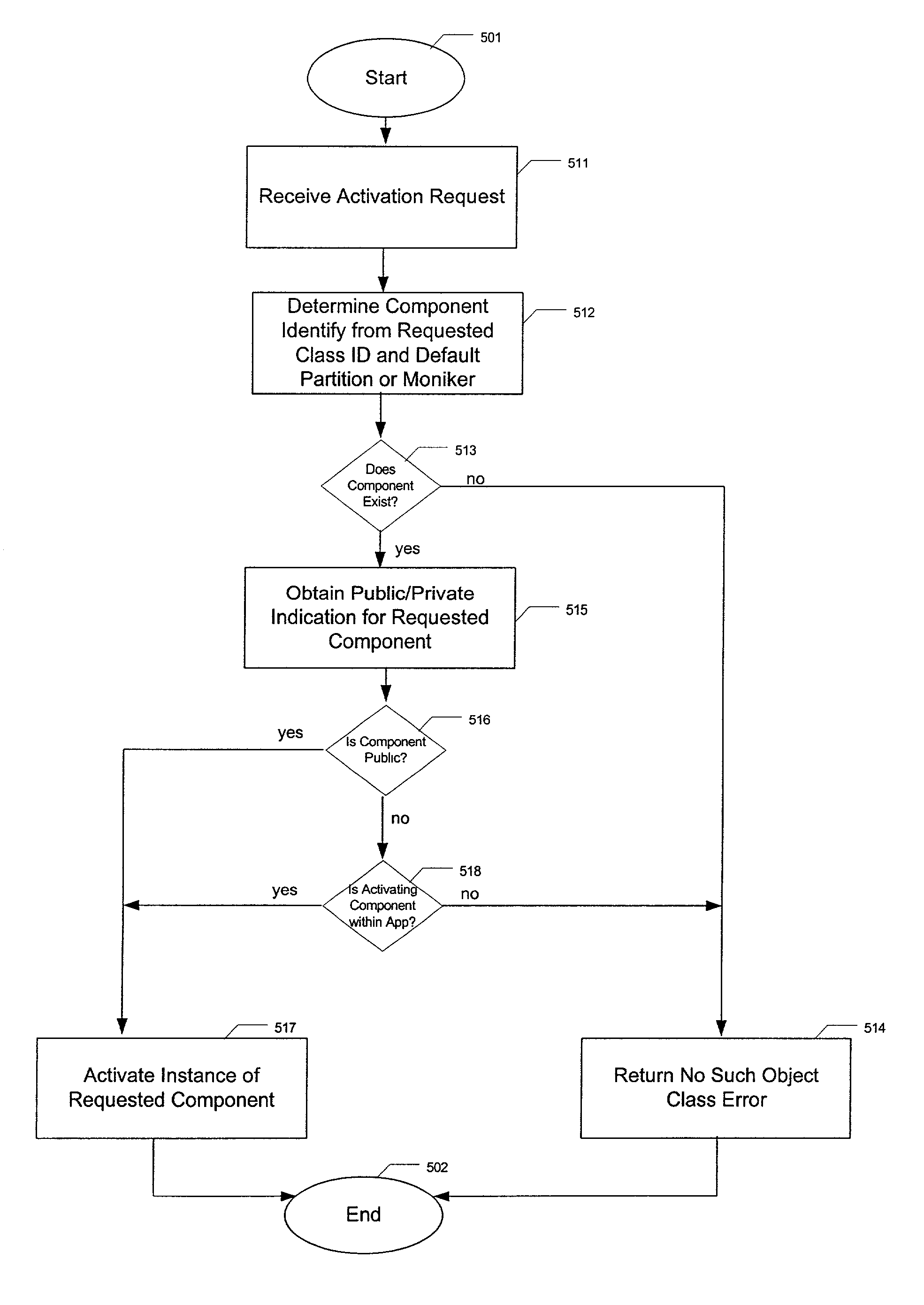
[0015]The present invention relates to a code generation method, apparatus, and article of manufacture for providing a component-based computing system having both publicly accessible and privately-only accessible computing components within multiple applications within a component based computer system.
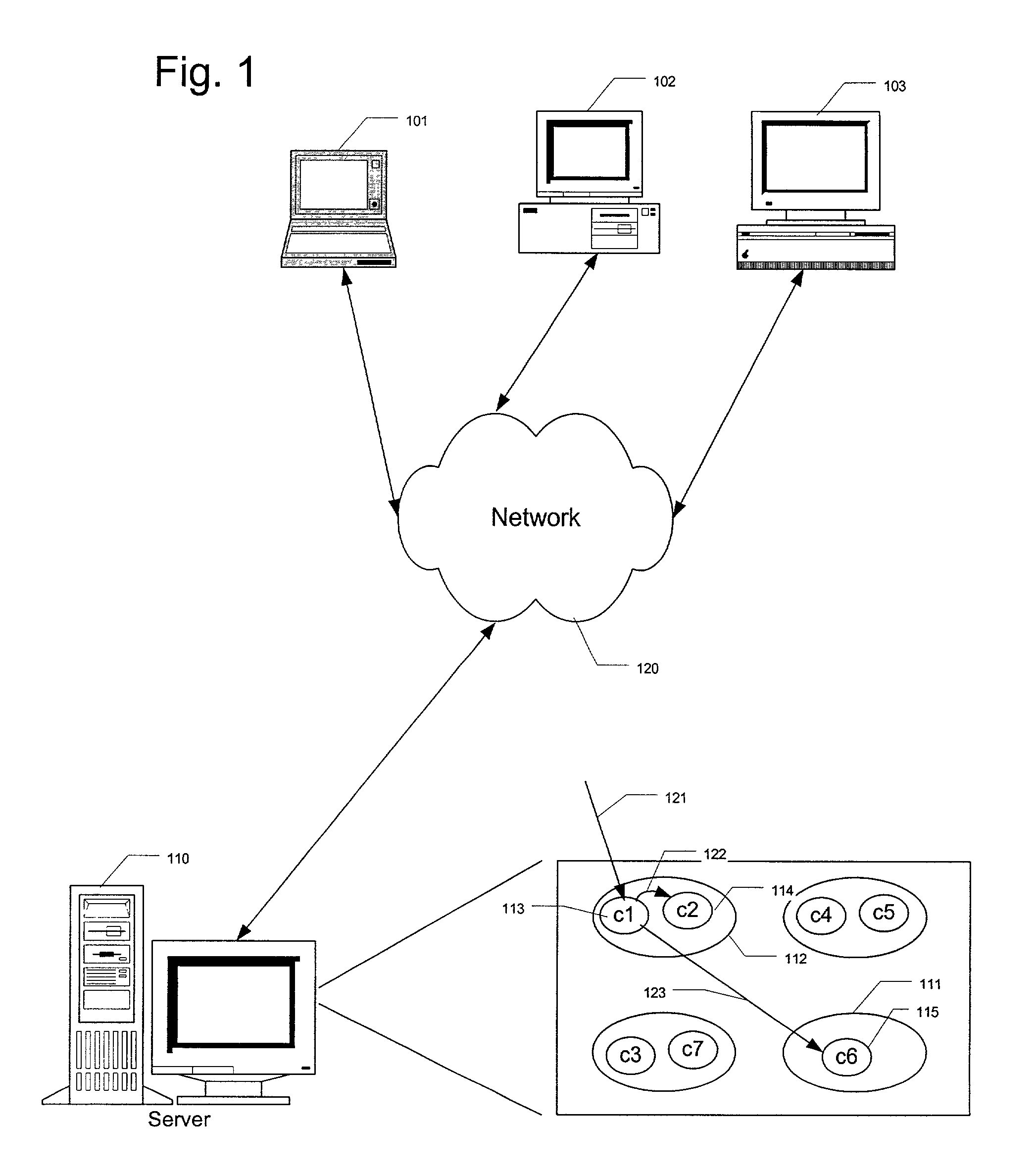
[0016]FIG. 1 illustrates a distributed computing environment for using public and private components within multiple applications located on a remote server according to an example embodiment of the present invention. In an exemplary embodiment, remotely located client computing systems 101–103 access programmable computing processing components on a remote server 110 across a communications network 120. Within the server 110, at least two programming applications are included.
[0017]When an active component on the server 110 needs to activate additional components to complete one or more processing tasks, the component selected for activation using the ID of the original calling clie...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com