Systems and methods for controlling user access to command execution
A technology for command execution and control, applied in the computer field, can solve problems such as complex tasks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
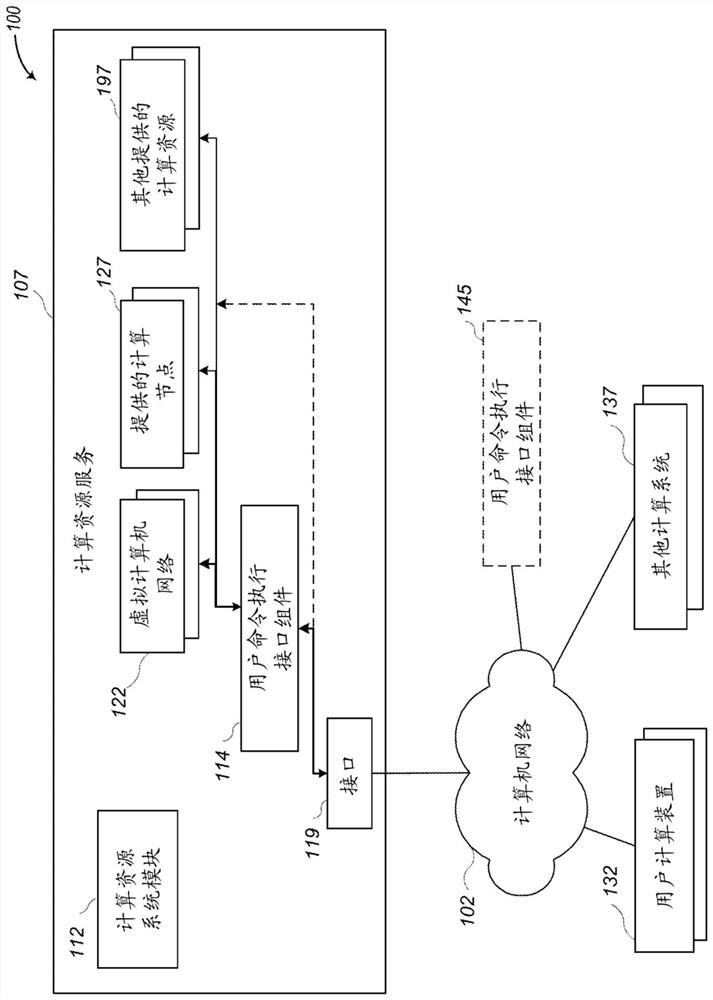
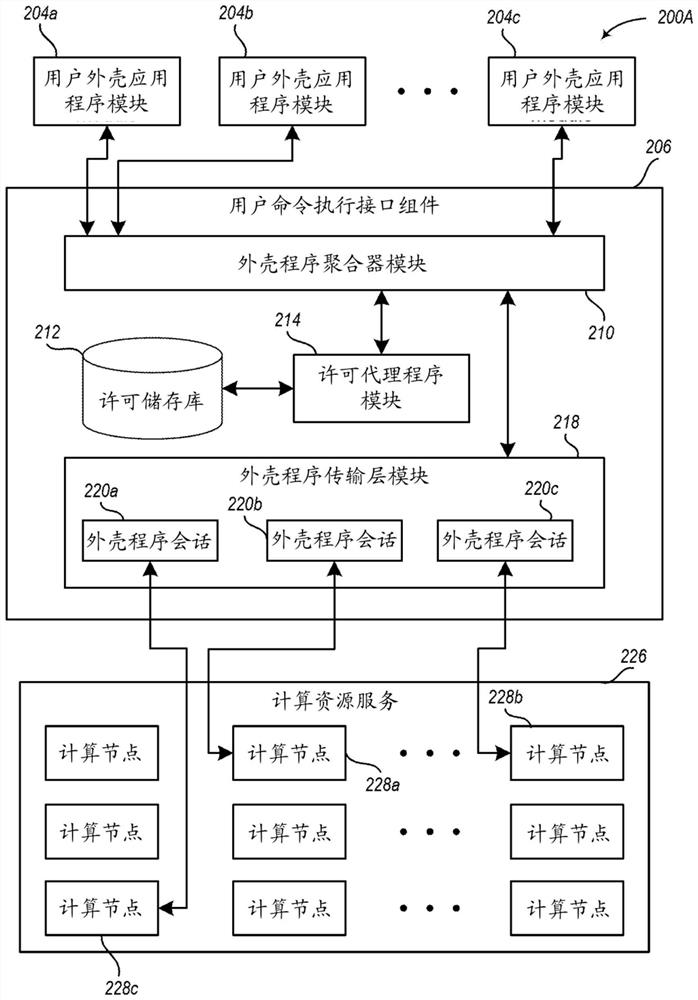
[0014] This disclosure describes techniques for controlling network-accessible computing resources, such as computing nodes and other computing-related resources, provided by service provider environments to customers and other users. In at least some embodiments, the service provider environment may provide a user command execution interface component for use by such users, such as to provide a similar interface to a shell tool. The user command execution interface component may also maintain various licensing information for controlling a user's ability to access, use, and / or modify provided computing nodes and other computing-related resources, such as stored on those provided computing nodes and other computing-related resources External licensing information.
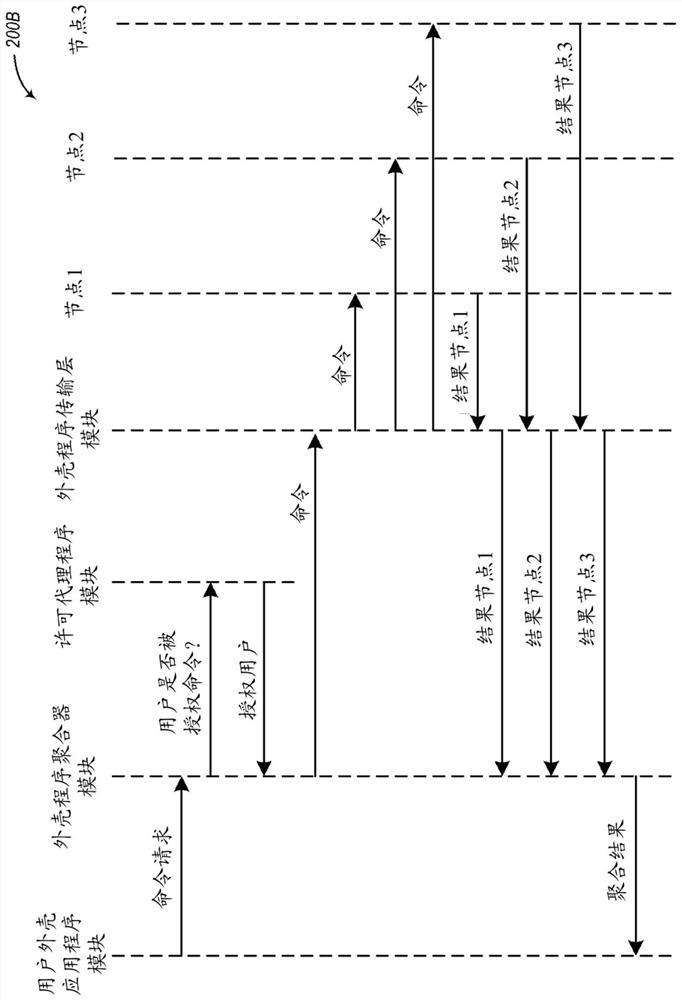
[0015] In at least some embodiments, a user command execution interface component can determine whether a user is authorized to execute one or more indicated commands on one or more computing nodes or other computi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com