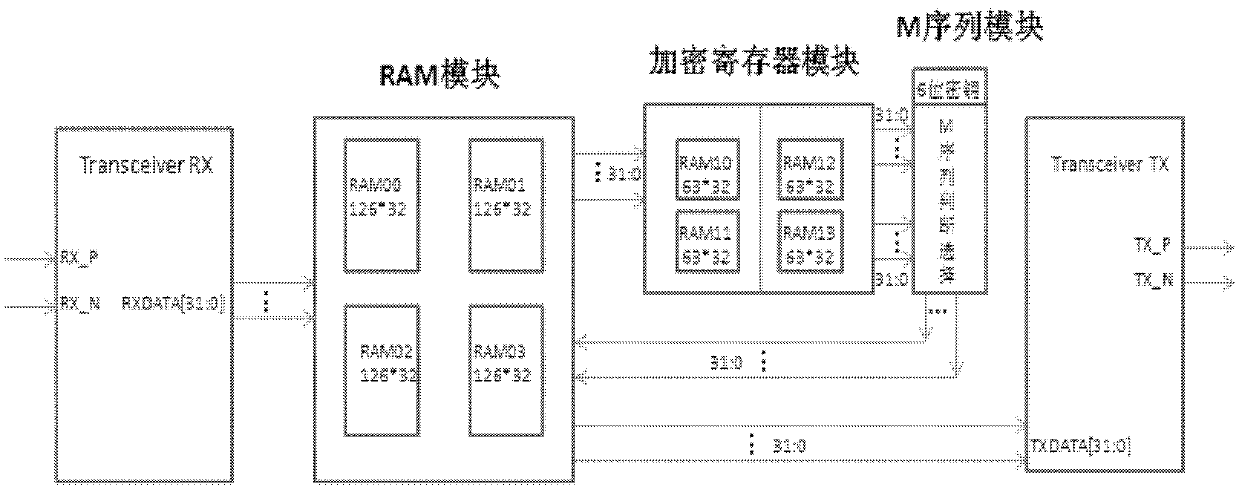
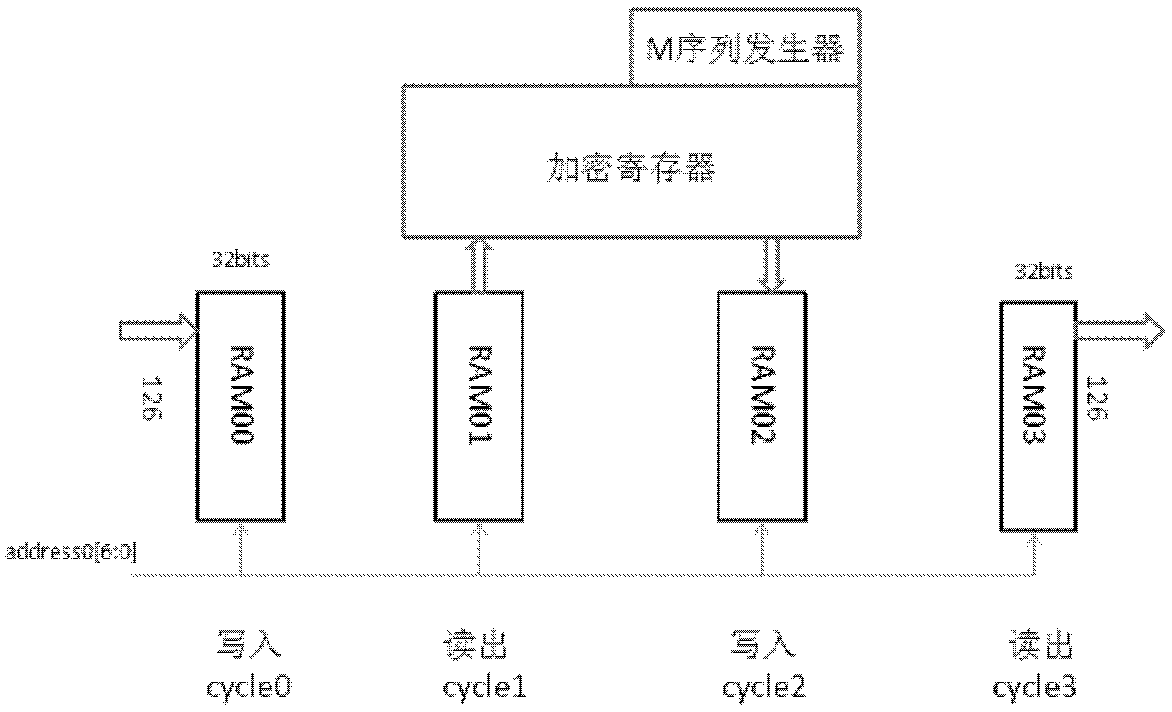
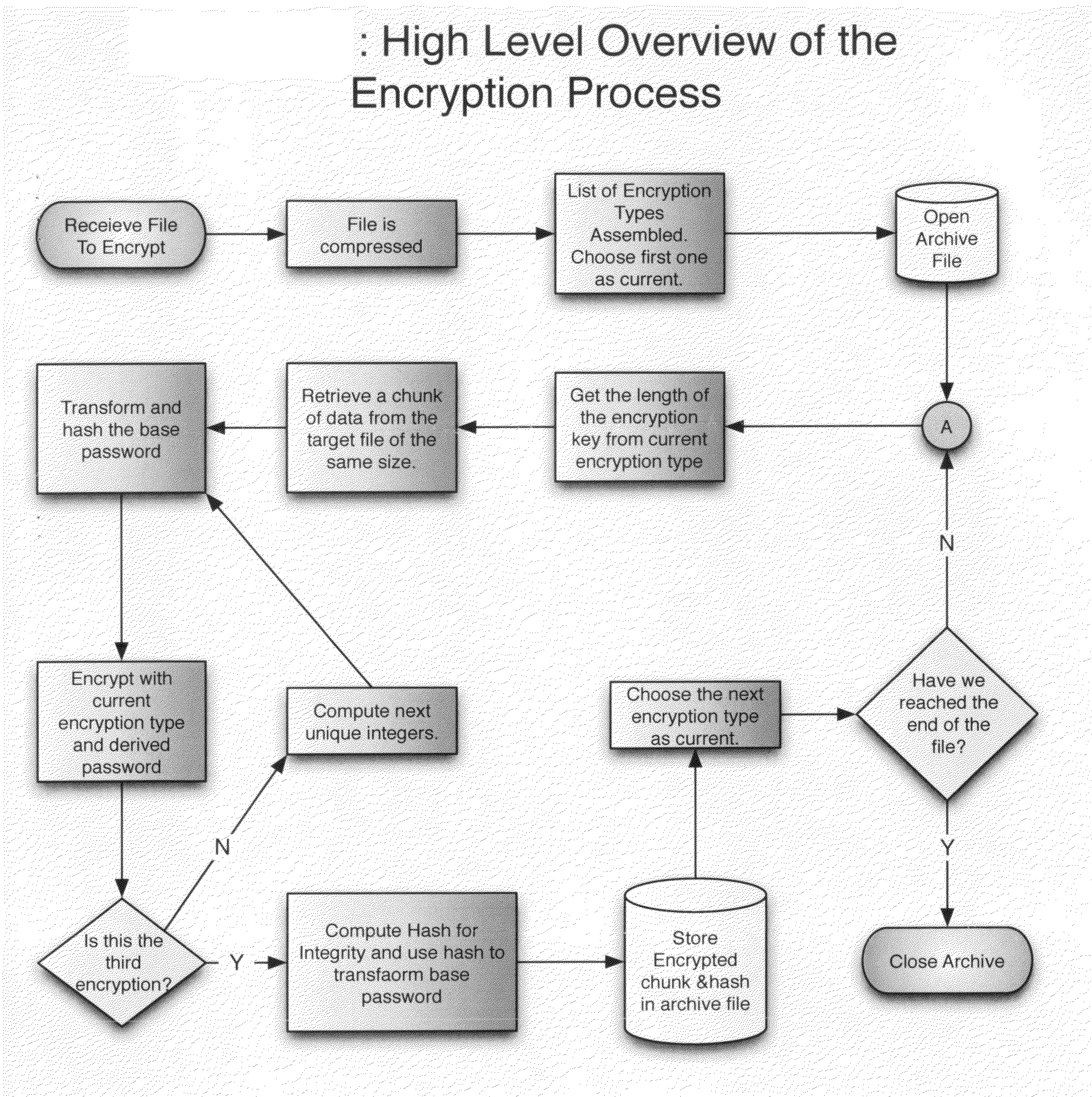
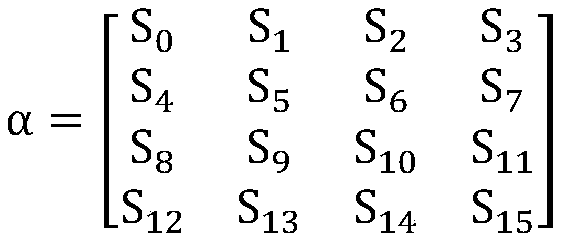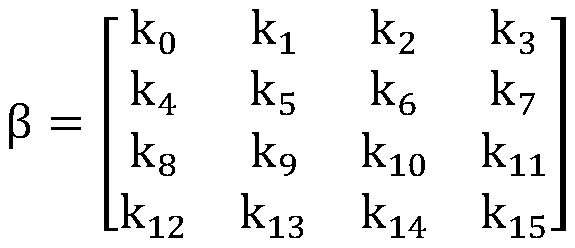Patents
Literature
187results about How to "Increase confusion" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
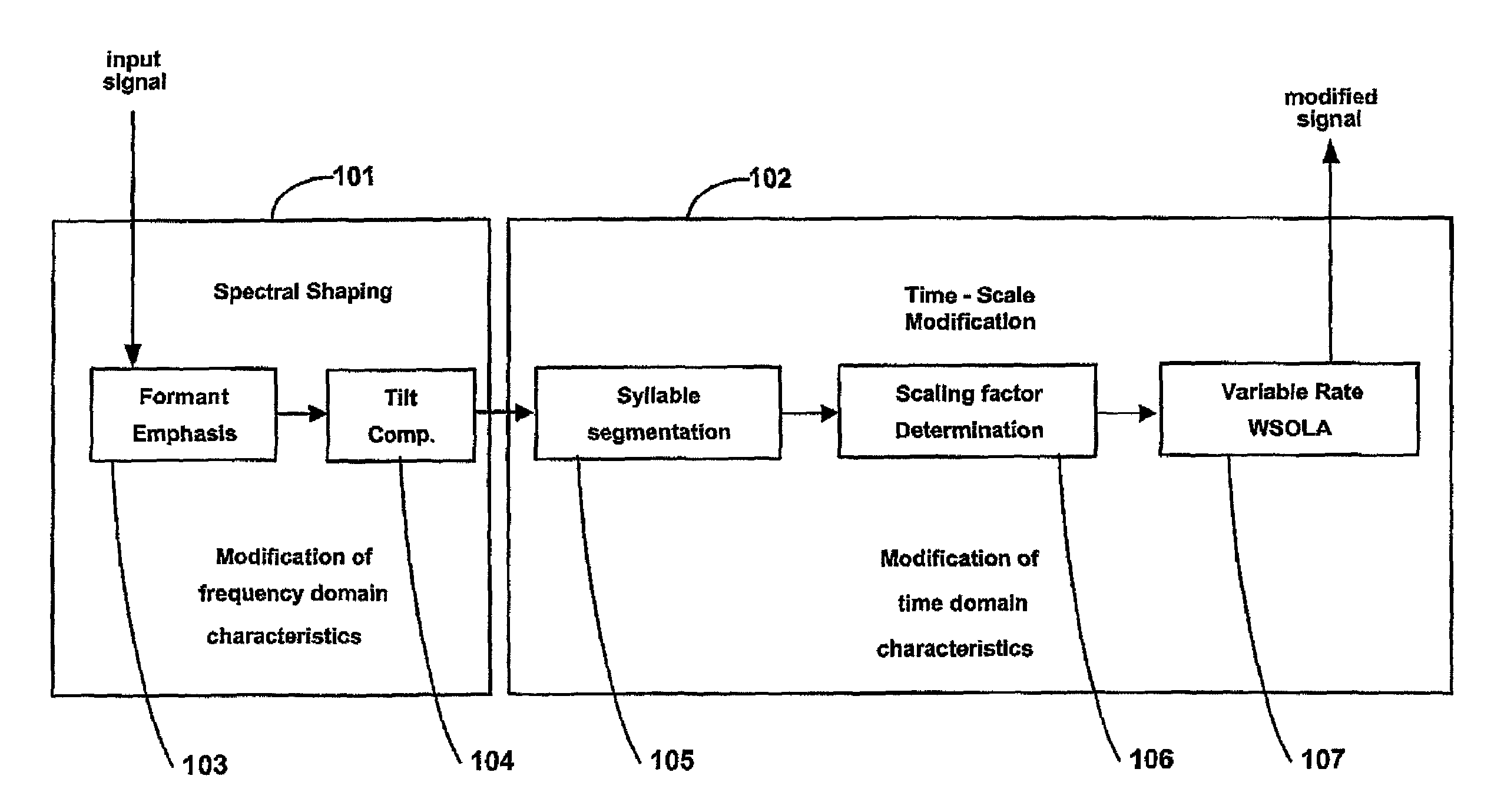
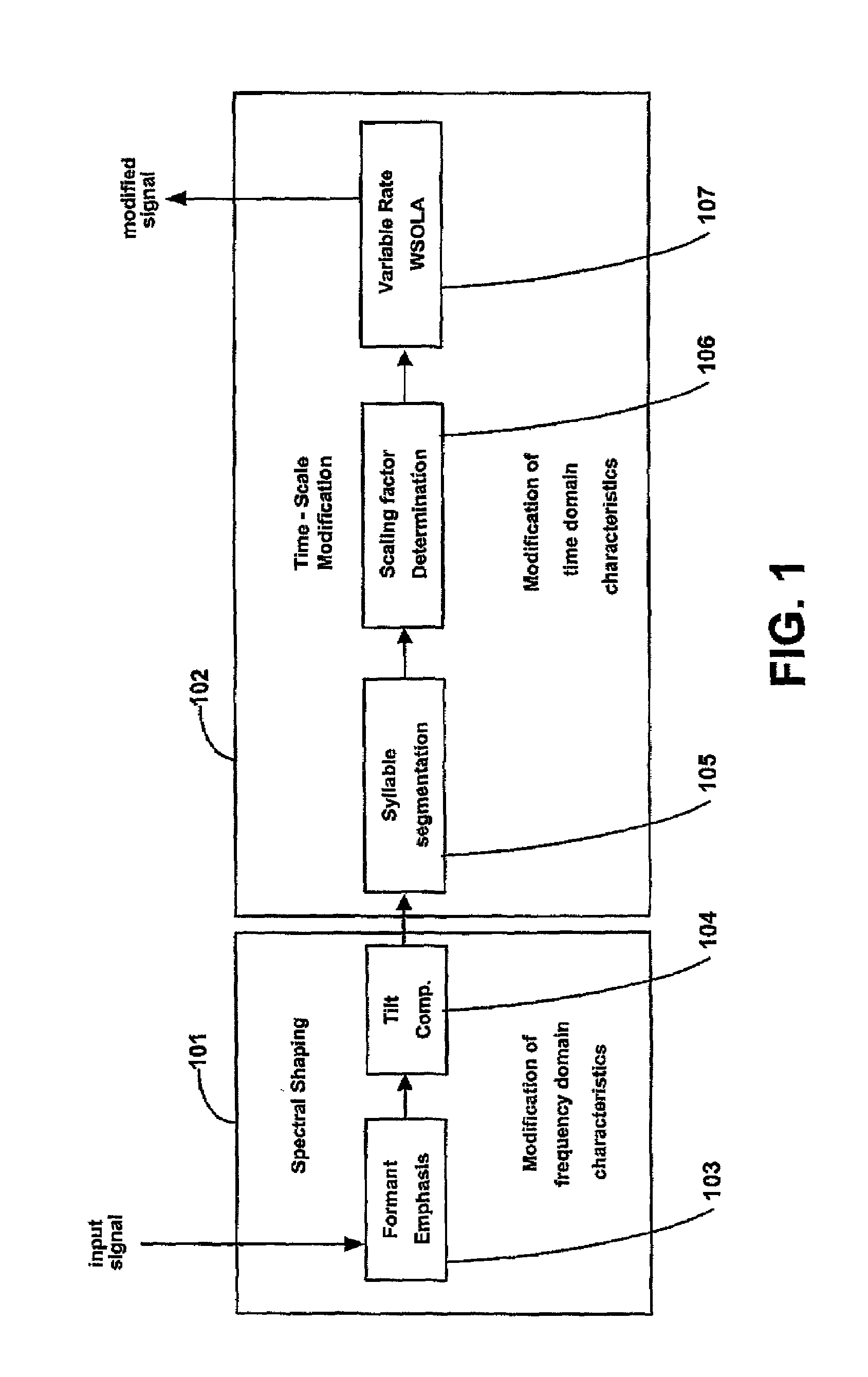
Enhancing speech intelligibility using variable-rate time-scale modification
The method and preprocessor enhances the intelligibility of narrowband speech without essentially lengthening the overall time duration of the signal. Both spectral enhancements and variable-rate time-scaling procedures are implemented to improve the salience of initial consonants, particularly the perceptually important formant transitions. Emphasis is transferred from the dominating vowel to the preceding consonant through adaptation of the phoneme timing structure. In a further embodiment, the technique is applied as a preprocessor to a speech coder.
Owner:NUANCE COMM INC
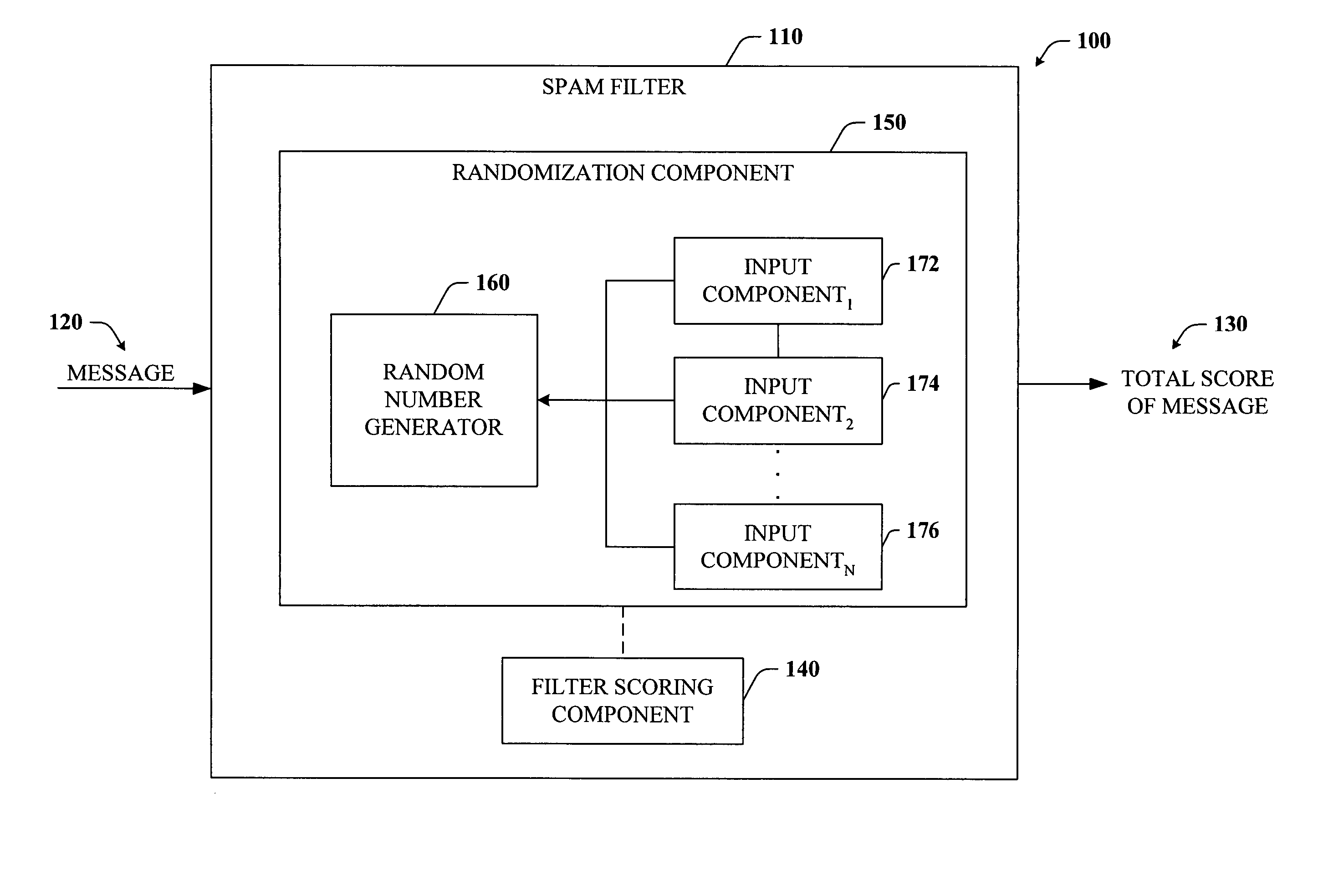
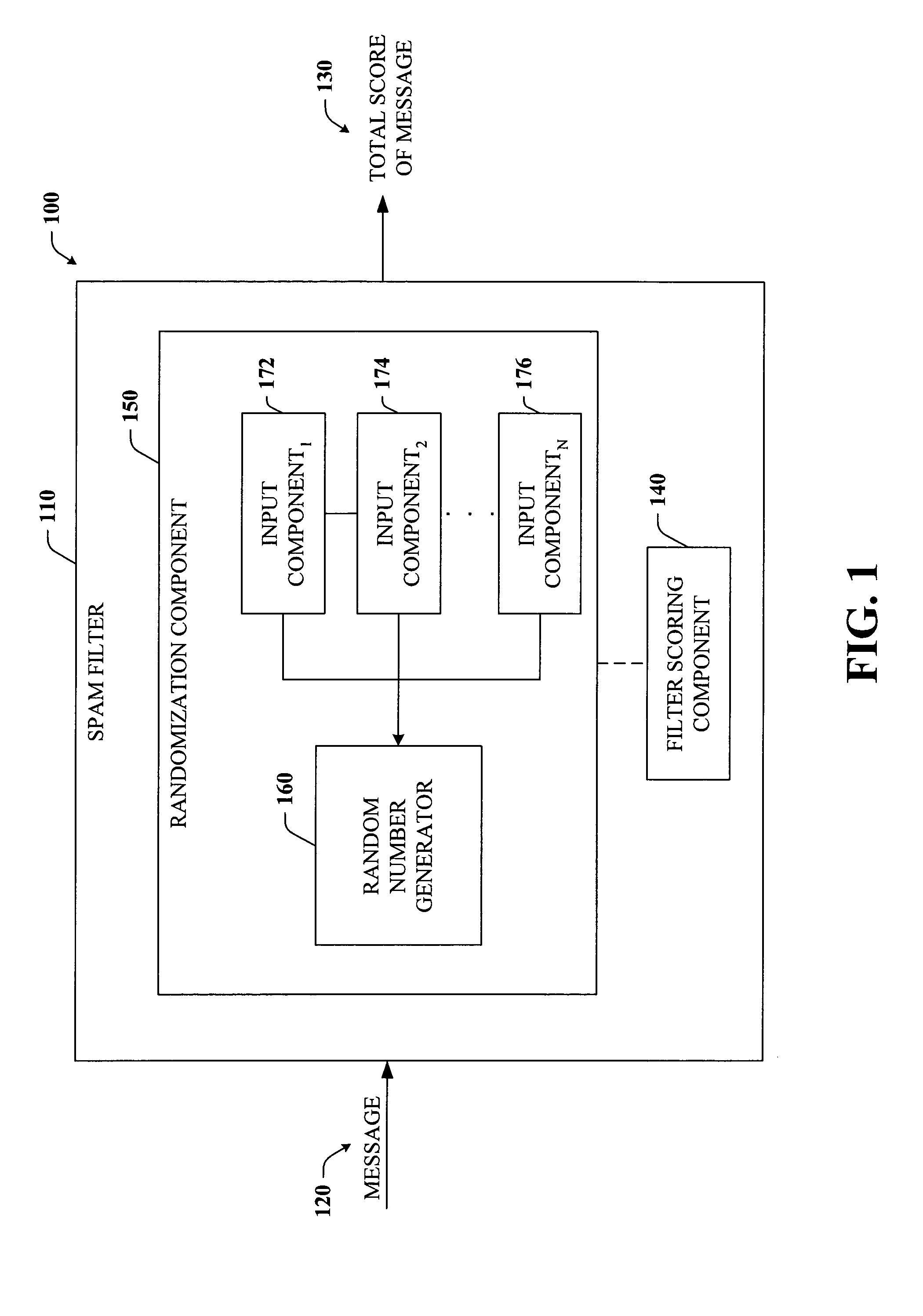
Obfuscation of spam filter
InactiveUS20050015454A1Increase confusionTest is expensiveData processing applicationsUser identity/authority verificationComputer hardwareFilter system
The subject invention provides systems and methods that facilitate obfuscating a spam filtering system to hinder reverse engineering of the spam filters and / or to mitigate spammers from finding a message that consistently gets through the spam filters almost every time. The system includes a randomization component that randomizes a message score before the message is classified as spam or non-spam so as to obscure the functionality of the spam filter. Randomizing the message score can be accomplished in part by adding a random number or pseudo-random number to the message score before it is classified as spam or non-spam. The number added thereto can vary depending on at least one of several types of input such as time, user, message content, hash of message content, and hash of particularly important features of the message, for example. Alternatively, multiple spam filters can be deployed rather than a single best spam filter.
Owner:MICROSOFT TECH LICENSING LLC
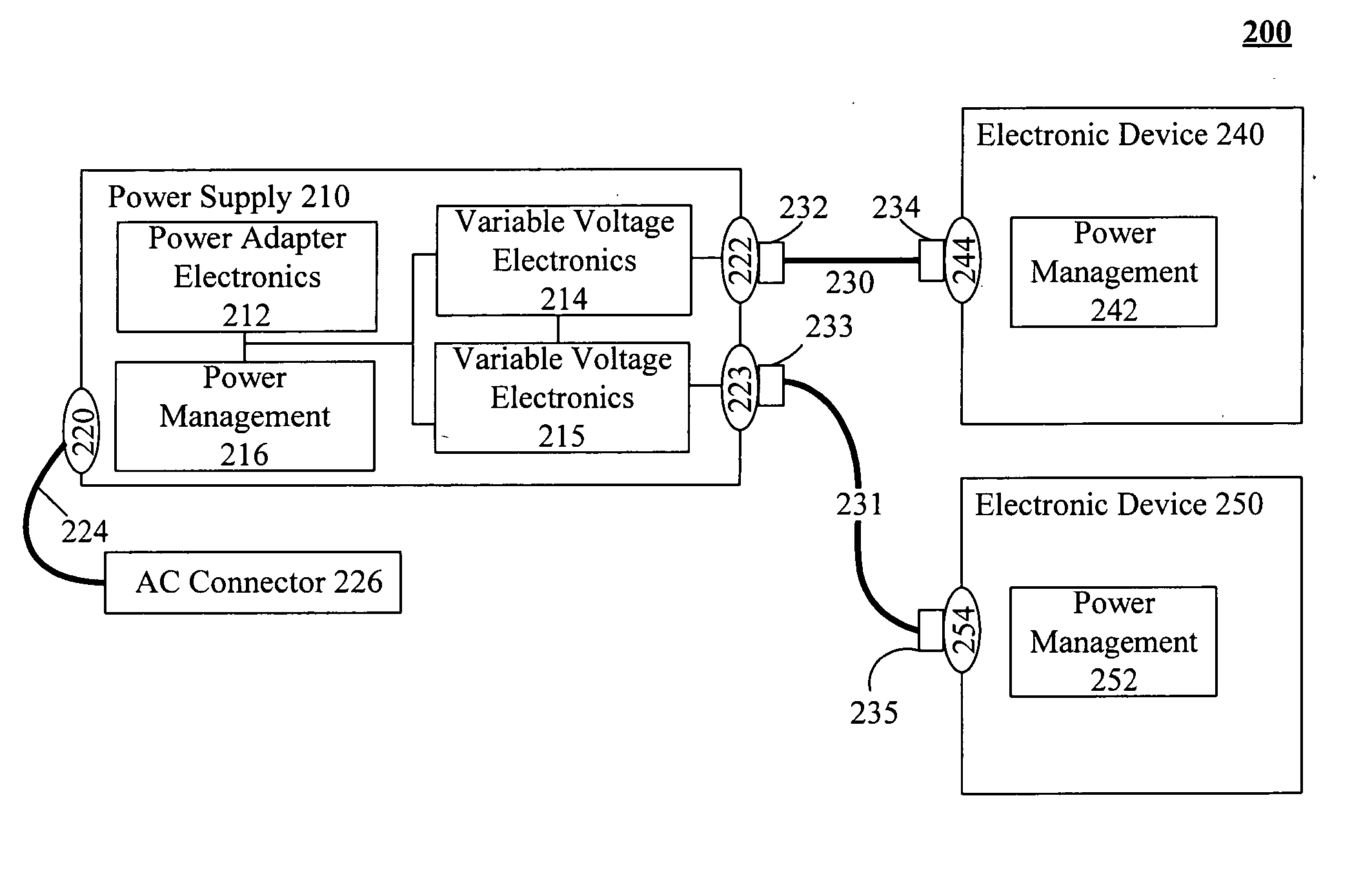
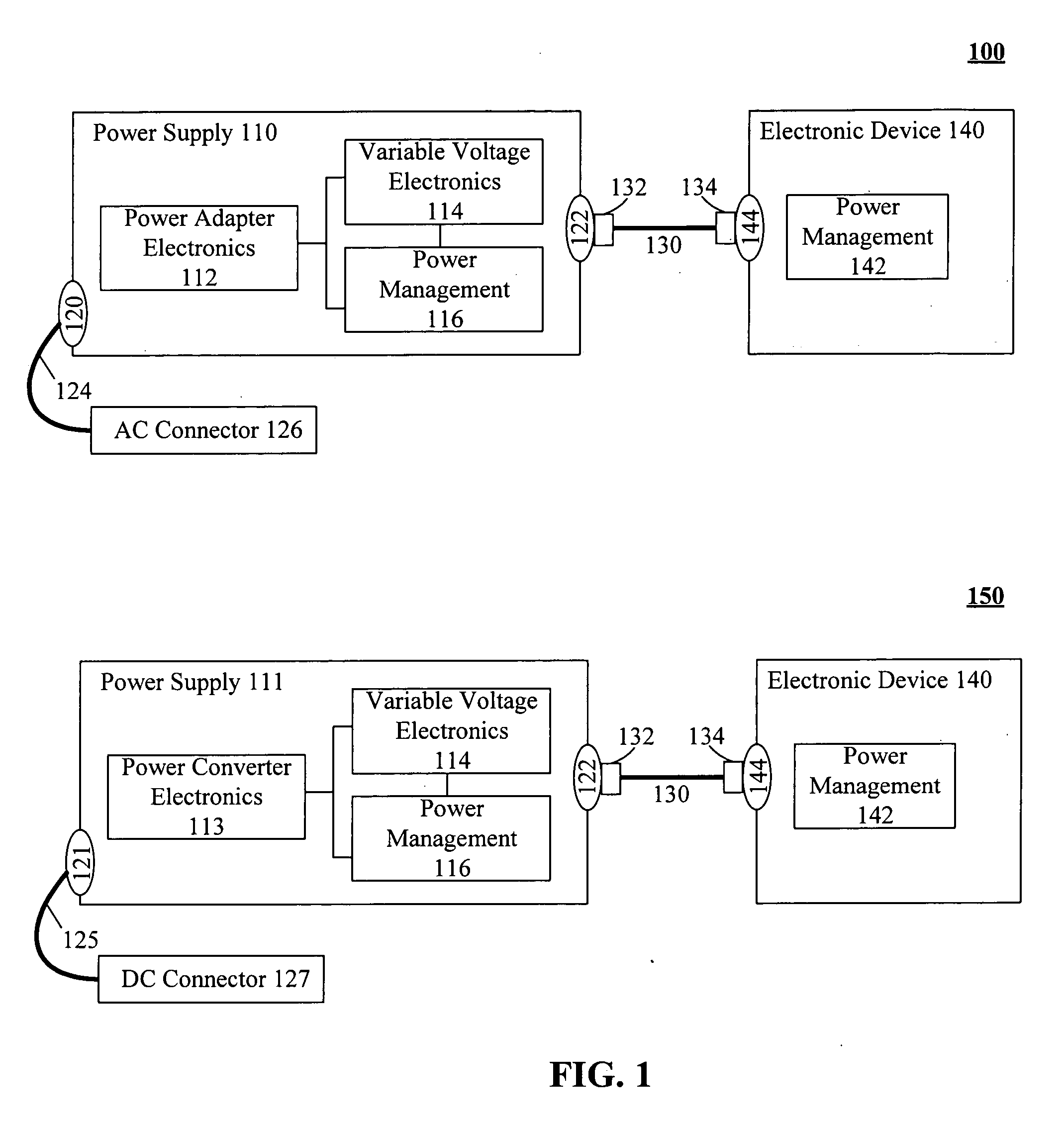
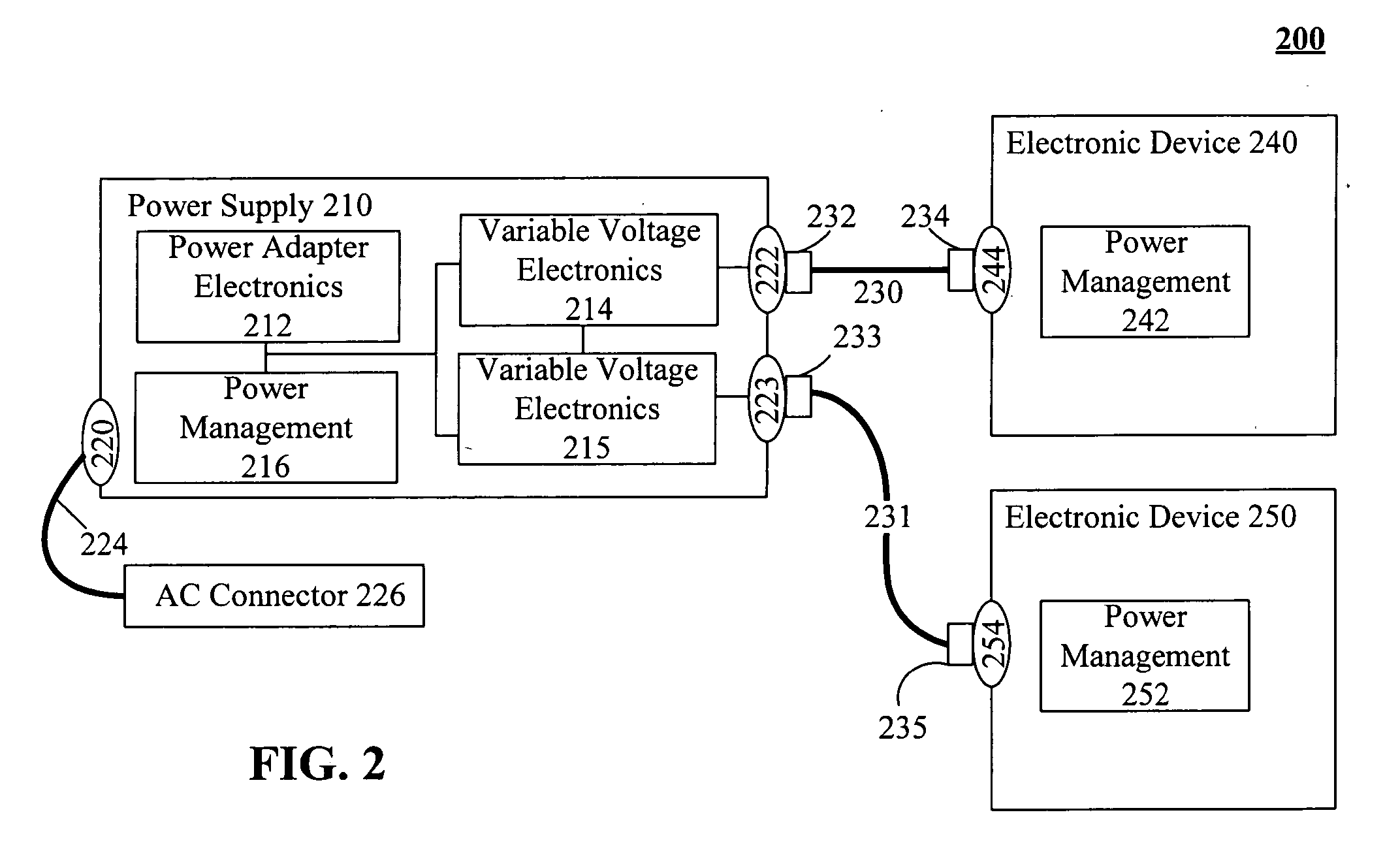
Intelligent direct current power supplies
InactiveUS20060214510A1Reduce needIncrease confusionCoupling device detailsSignalling system detailsCarrier signalElectric power
A power supply including a power supplying connector, a direct current (DC) connector, an information extractor, power adaptor electronics, and variable voltage electronics. The information extractor being configured to extract digitally encoded data from a carrier wave. The digitally encoded data can specify power requirements of the DC power receiving device. The variable voltage electronics can adapt DC power generated by the power adaptor in accordance with settings provided by the information extractor. This adapted power can be provided to the DC power receiving device connected to the power supply via the DC connector.
Owner:IBM CORP
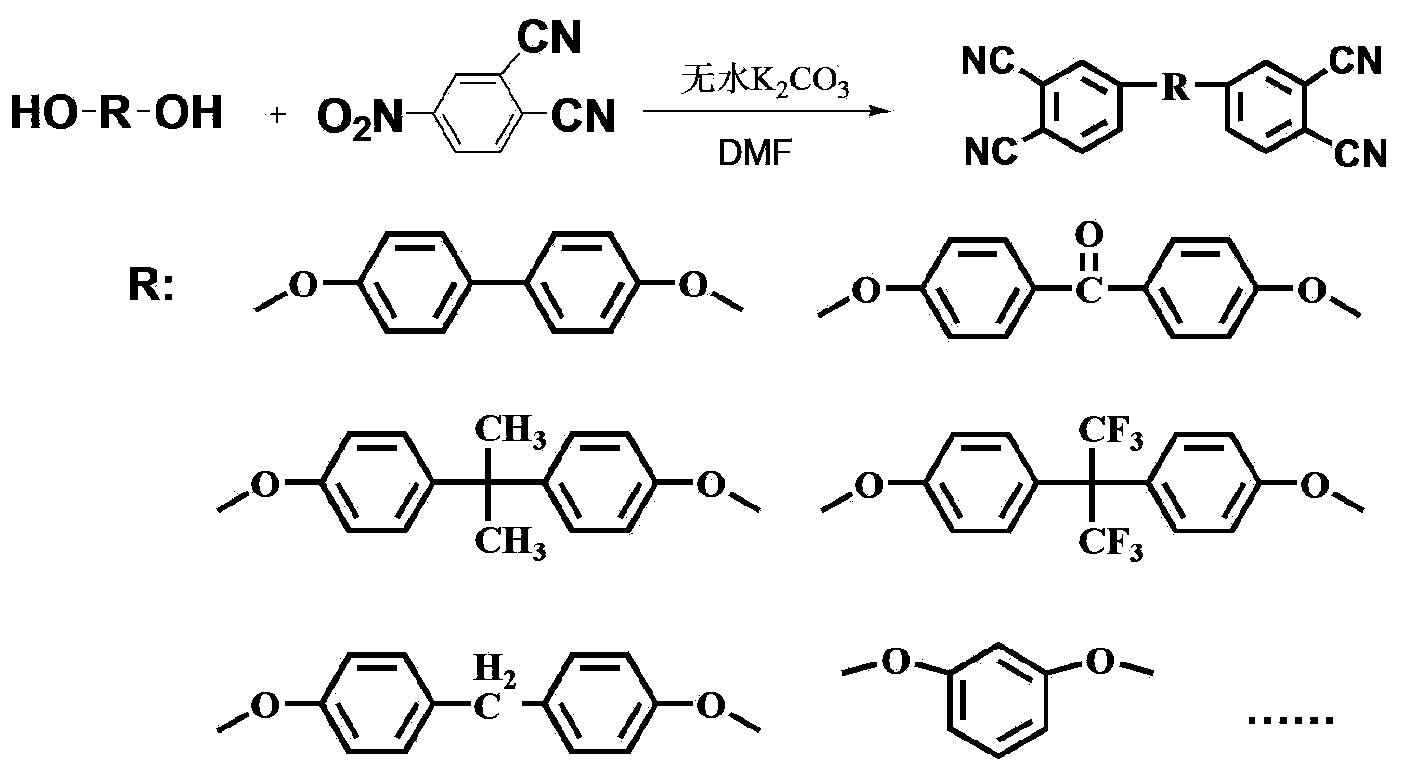
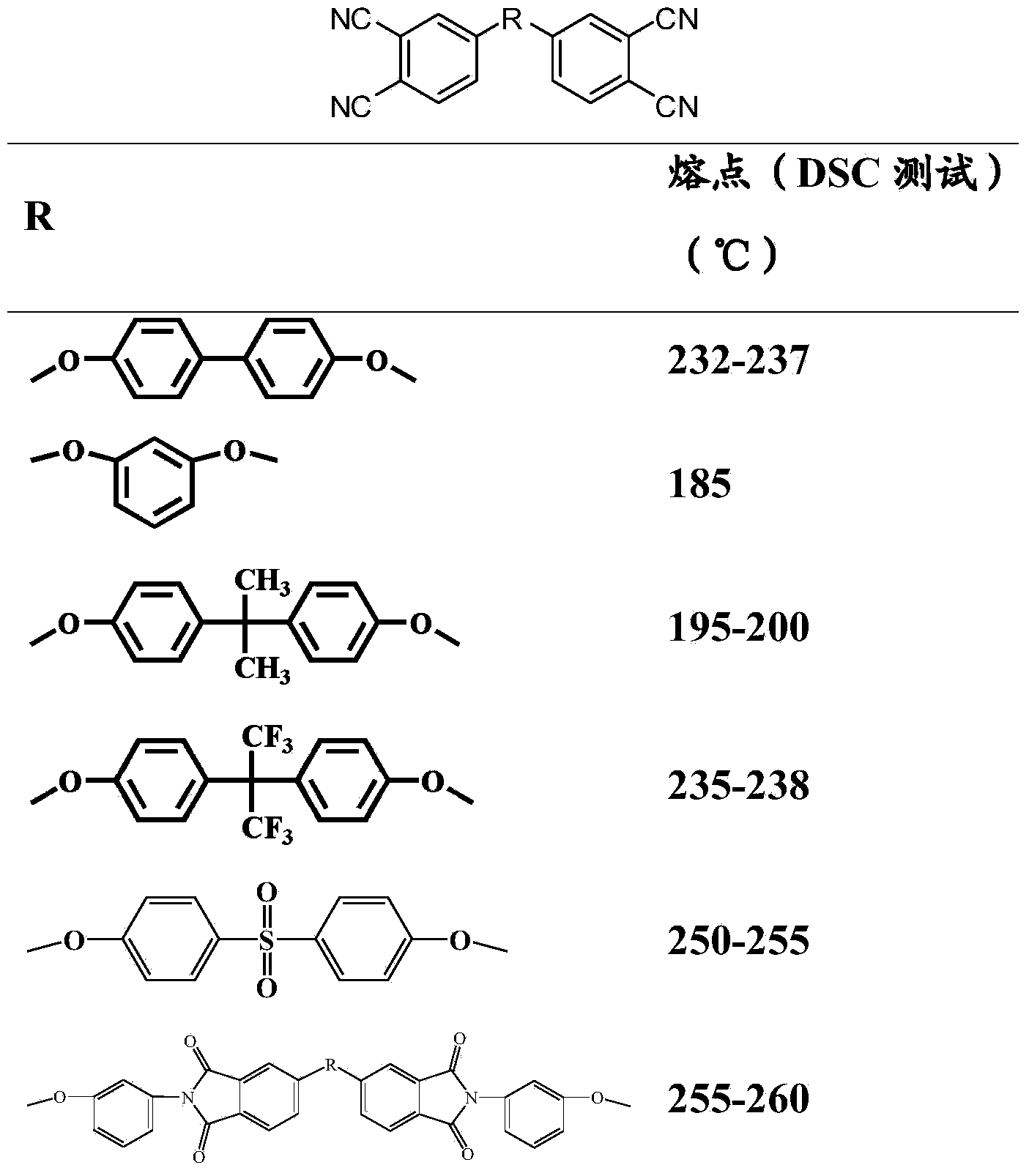
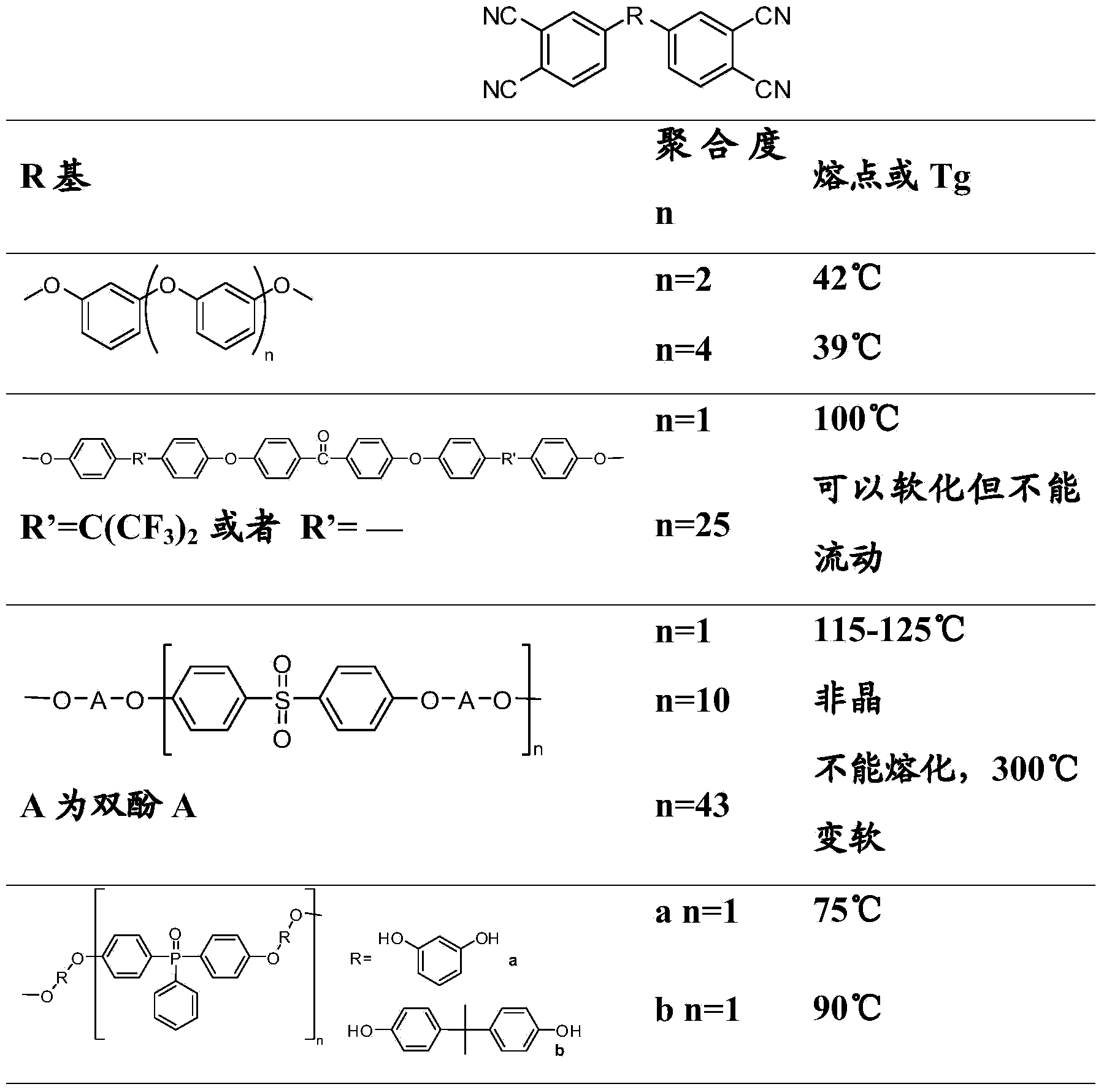
Novel phthalonitrile resin and preparation method thereof
ActiveCN103834008AIncrease asymmetryIncrease confusionSynthetic resin layered productsPhthalonitrileChemistry
The invention discloses a novel phthalonitrile resin and a preparation method thereof. Compared with a conventional phthalonitrile resin (only 4-nitro phthalonitrile as an end-capping reagent, the novel phthalonitrile resin is introduced with 3-nitro novel phthalonitrile resin to cooperate end capping, and thus the asymmetry of a resin structure is increased and the turbidity of a resin component is increased (see a formula 1). Compared with the conventional phthalonitrile resin, the novel phthalonitrile resin disclosed by the invention has the characteristics of low melting temperature, good solubility, wide processing window, low curing temperature and the like; a prepared resin molded part and a resin-based composite material are low in porosity, excellent heat-resistant quality, and high in mechanical property, and can be applied to the fields of aerospace, a space technology, machine manufacturing, and the like as a light-weight and high-temperature resistant part. The formula is described in the specification.
Owner:INST OF CHEM CHINESE ACAD OF SCI
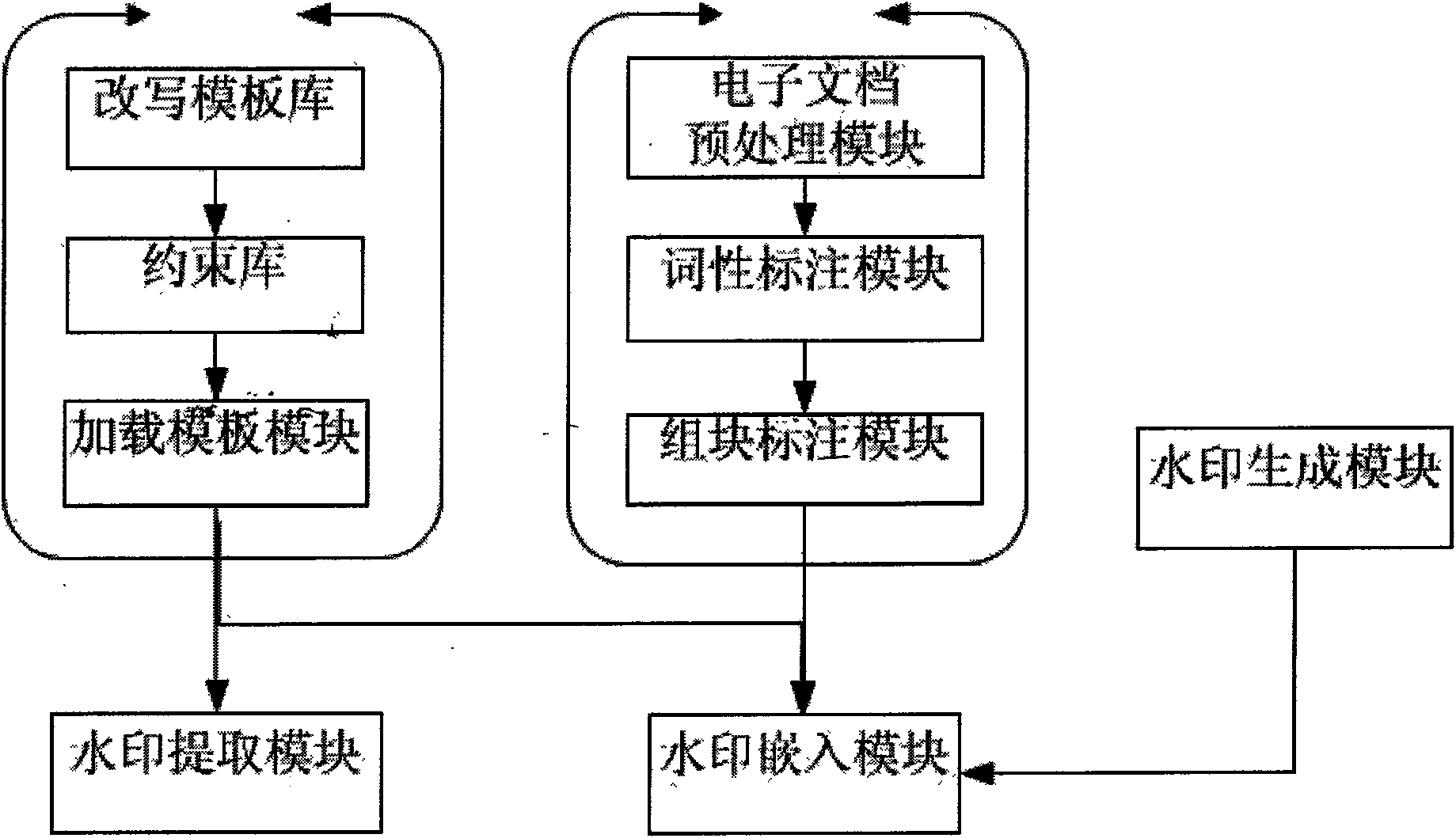
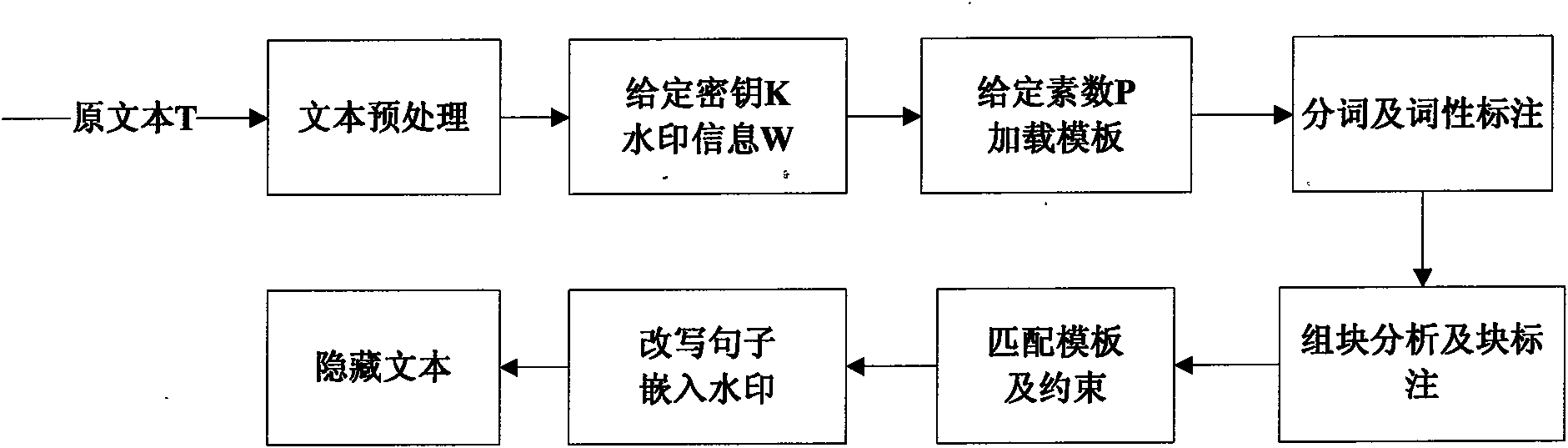
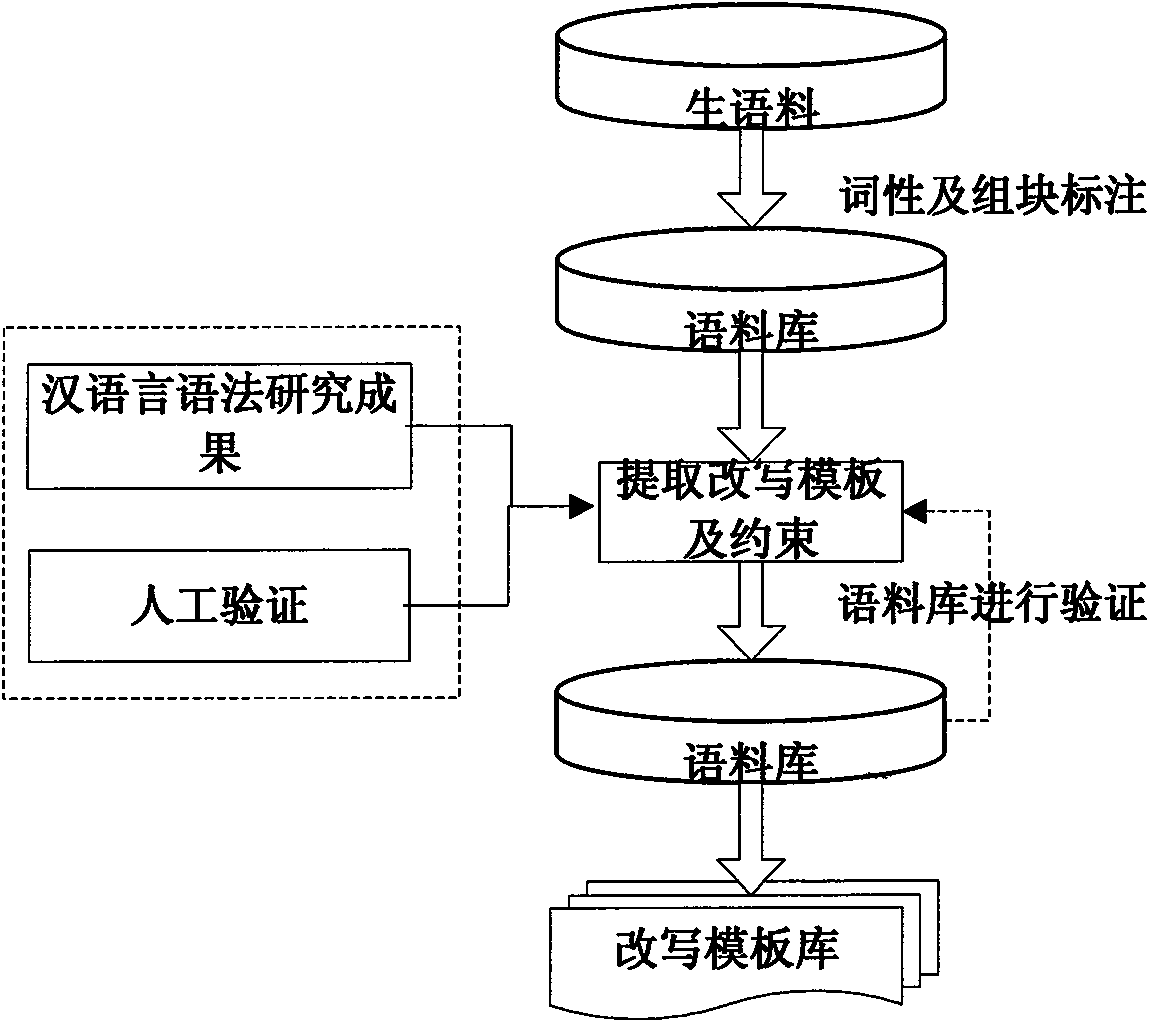
Text hidden method based on Chinese sentence pattern template transformation
InactiveCN101639826AConform to the semantic idiomPrevent rewritingSpecial data processing applicationsElectronic documentComputerized system
The invention discloses a text hidden method based on Chinese sentence pattern template transformation. The method utilizes the computer system to carry out watermark embedment and extraction on textinformation to hide the text information, comprising the following steps: (1) carrying out pre-treatment on an electronic file; (2) generating watermark information sign and setting a key; (3) carrying out part-of-speech tagging to format-free file generated in step (1) by a part-of-speech tagging module and outputting a part-of-speech tagging string of a sentence; (4) simplifying the part-of-speech tagging string output in the step (3) by a chunk tagging module; (5) loading a template module to select a sentence pattern module; (6) embedding watermark information by a watermark embedment module; (7) outputting the hidden text with embedded watermark; and (8) extracting the watermark information from the hidden text by a watermark extraction module through the key. The text hidden method changes sentence pattern through a template, avoids complex understanding and processing of grammar and semanteme, ensures the carrier text better satisfying grammar and semanteme habit and prevents blindfold rewrite.
Owner:NORTHWEST UNIV(CN)
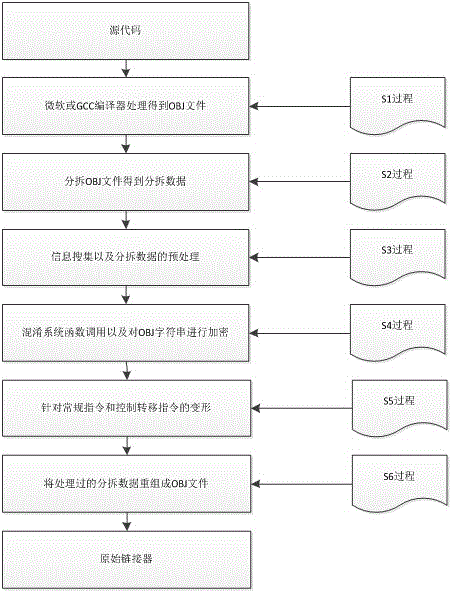
Software protection method based on intermediate result compiling
ActiveCN104091100APrevent illegal crackingAvoid analysisProgram/content distribution protectionSoftware engineeringConfusion
The invention discloses a software protection method based on intermediate result compiling. The software protection method includes the following steps (1), software source codes are compiled to obtain an original object file (OBJ); (2), the original OBJ is analyzed to obtain partitioned data aiming at the original OBJ; (3), the analysis result of the step (2) is preprocessed; (4), system function call is concealed, redundant functions are inserted, and global character strings used for a system are encrypted; (5), deformation is performed for a common instruction; (6), the scattered data obtained through processing in the processes are recombined to form the OBJ, and then an executable file is generated through link of a linker. Confusion and protection at the instruction level for the OBJ are achieved, errors can be avoided, the confusion effect and the confusion quality are improved, and software is prevented from being illegally cracked or analyzed.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
Composite all solid-state polymer electrolyte lithium ion battery and preparation method of composite all solid-state polymer electrolyte lithium ion battery
ActiveCN102709597AReduce crystallinityImprove ionic conductivityFinal product manufactureElectrolyte accumulators manufactureDimethyl siloxaneLithium-ion battery
The invention discloses a composite all solid-state polymer electrolyte lithium ion battery and a preparation method of the composite all solid-state polymer electrolyte lithium ion battery, and belongs to the all solid-state polymer electrolyte preparation technology and the lithium ion battery field. The composite all solid-state polymer electrolyte lithium ion battery disclosed by the invention comprises a battery case and an electrode core, wherein the electrode core is accommodated in the battery case in a sealed way and comprises a positive electrode, a negative electrode and composite all solid-state polymer electrolytes positioned between the positive electrode and the negative electrode, and the composite all solid-state polymer electrolytes comprise dimethyl siloxane-ethylene oxide copolymers, lithium salts and nanometer inorganic fillers. Compared with the existing composite all solid-state polymer electrolytes, the composite all solid-state polymer electrolytes adopted by the invention have the advantages that base materials are the dimethyl siloxane-ethylene oxide copolymers, the regularity of the polymer chain segment is reduced, and the crystallization degree of the polymers at the surface is reduced, so higher ionic conductivity is realized at normal temperature.
Owner:DONGFANG ELECTRIC CORP LTD
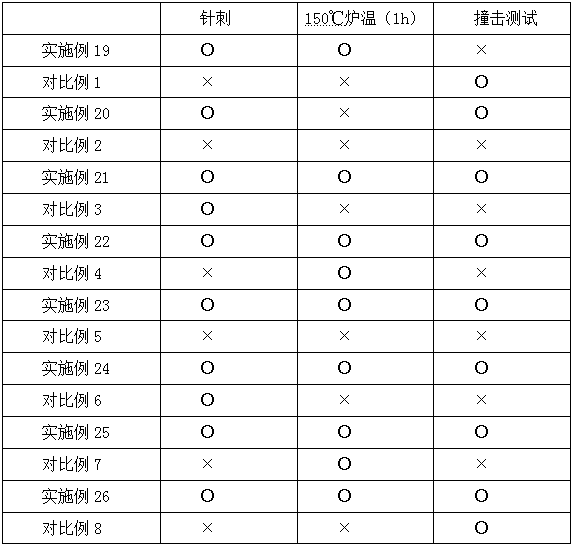
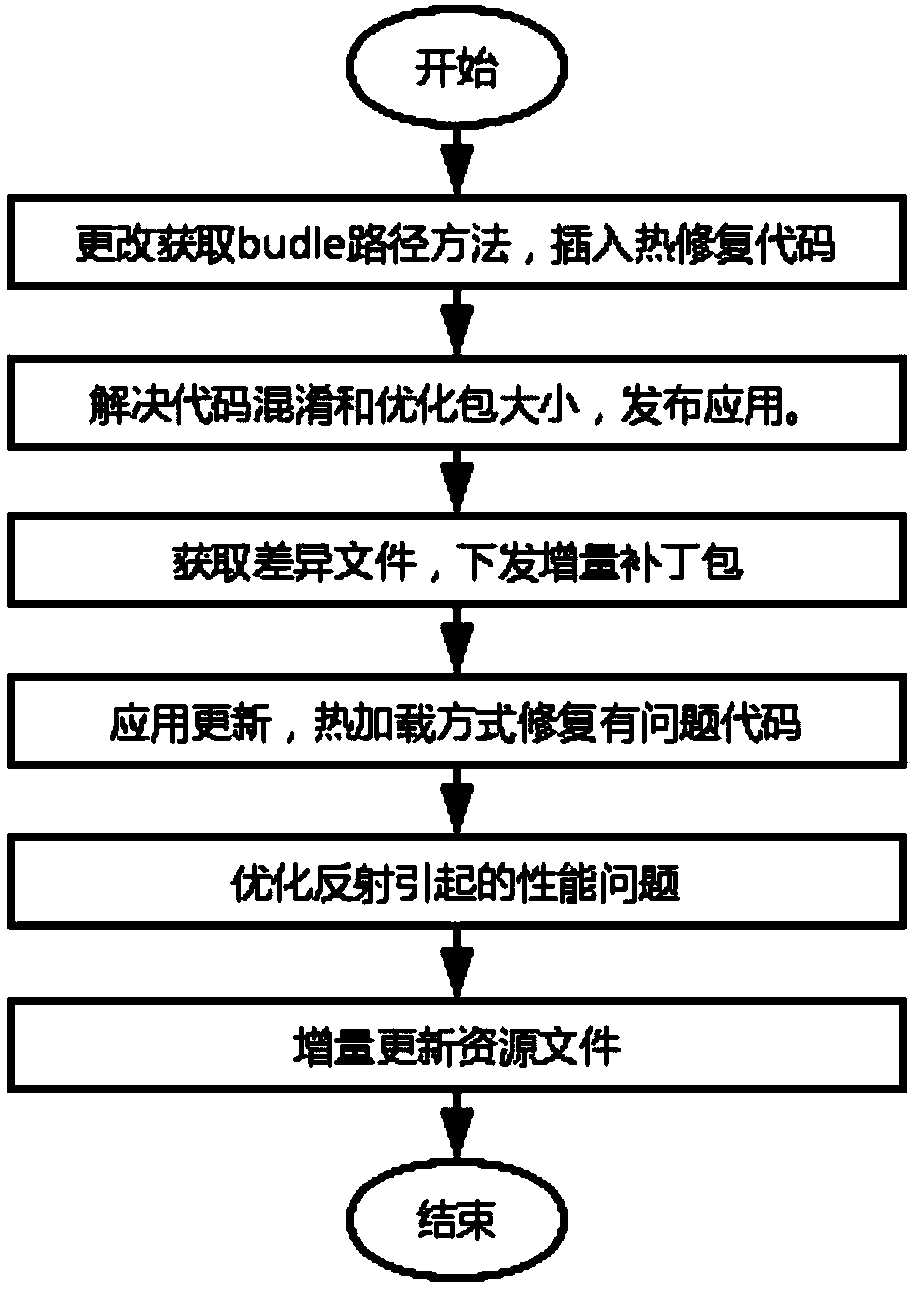
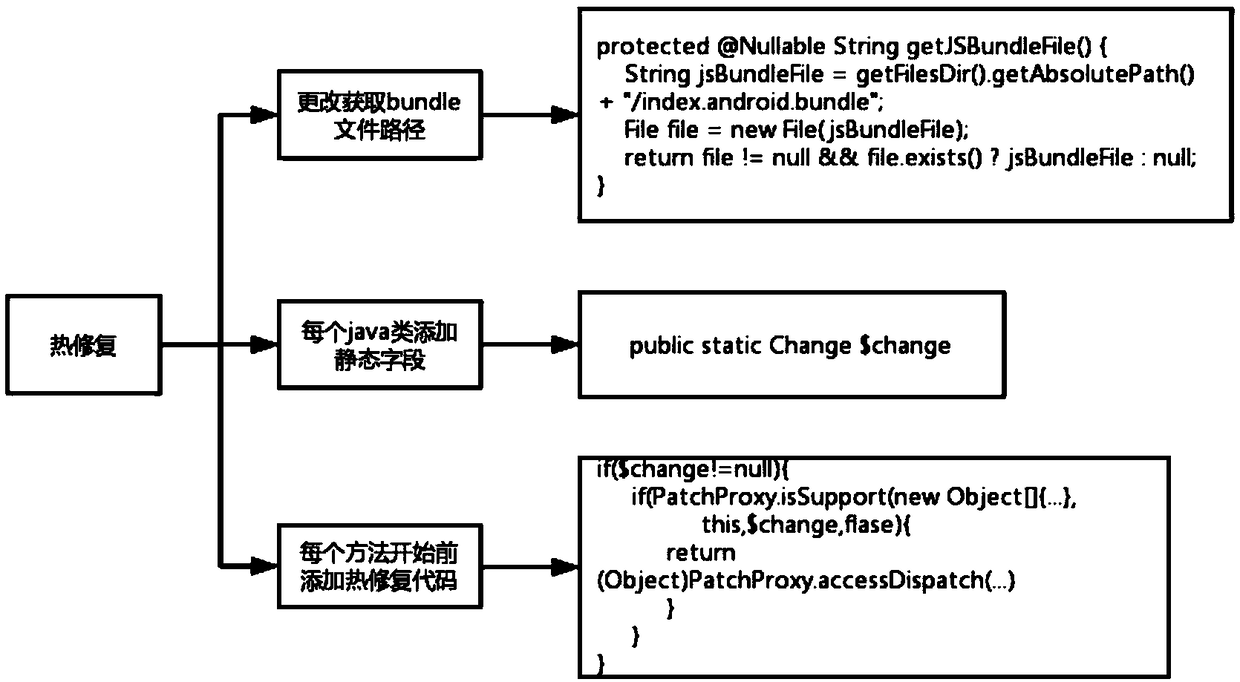
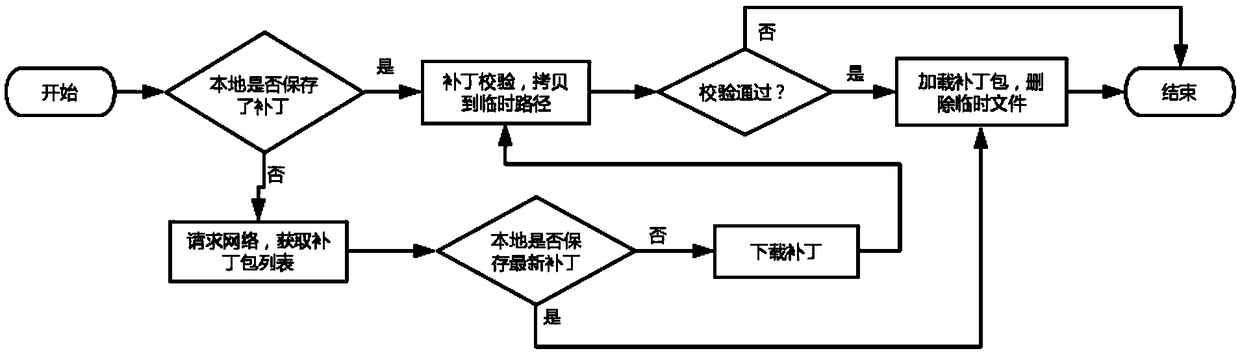
Incremental updating method of an integrated Android application
ActiveCN109491695AReduce trafficImprove application experienceCode compilationProgramming languageComputer compatibility
The invention discloses an incremental updating method of an integrated Android application, which is based on React Native, adds a static field to all classes in an Android native code serving as anapplication, inserts a skip code at an entrance of the method, and comprises condition judgment on the static field; in addition, the method for reading the bundle path is changed, and the bsdiff is used for achieving incremental updating of the application. According to the invention, the existing thermal remediation technology is optimized; a hot repair framework which is higher in compatibilityand can take effect in real time without restarting is achieved, online bugs can be repaired at any time without releasing a new version, resource files can be updated, discovered problems can be quickly repaired, great help is provided for developers, and great significance is achieved for improving the application use experience.
Owner:SOUTH CHINA UNIV OF TECH
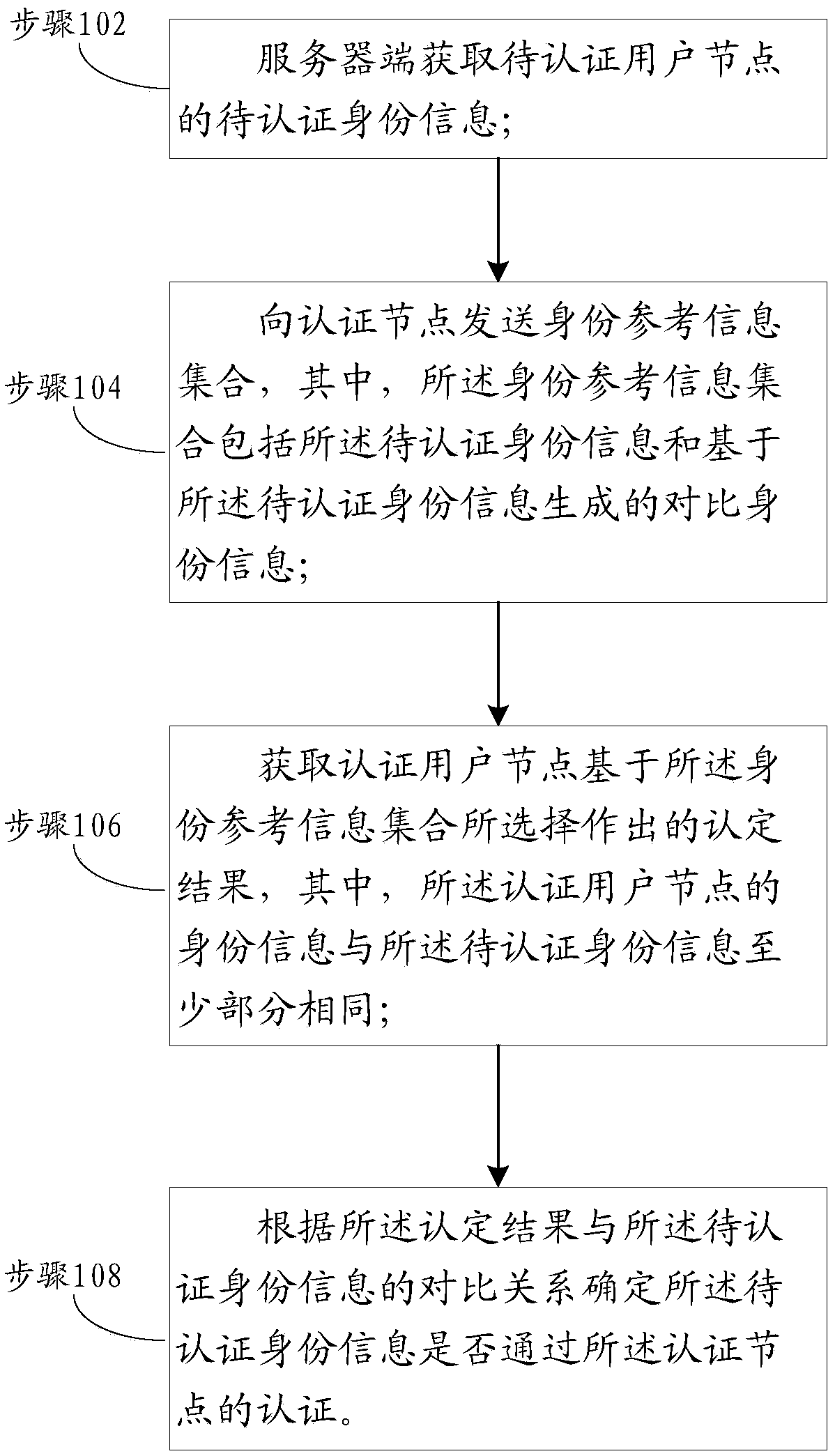
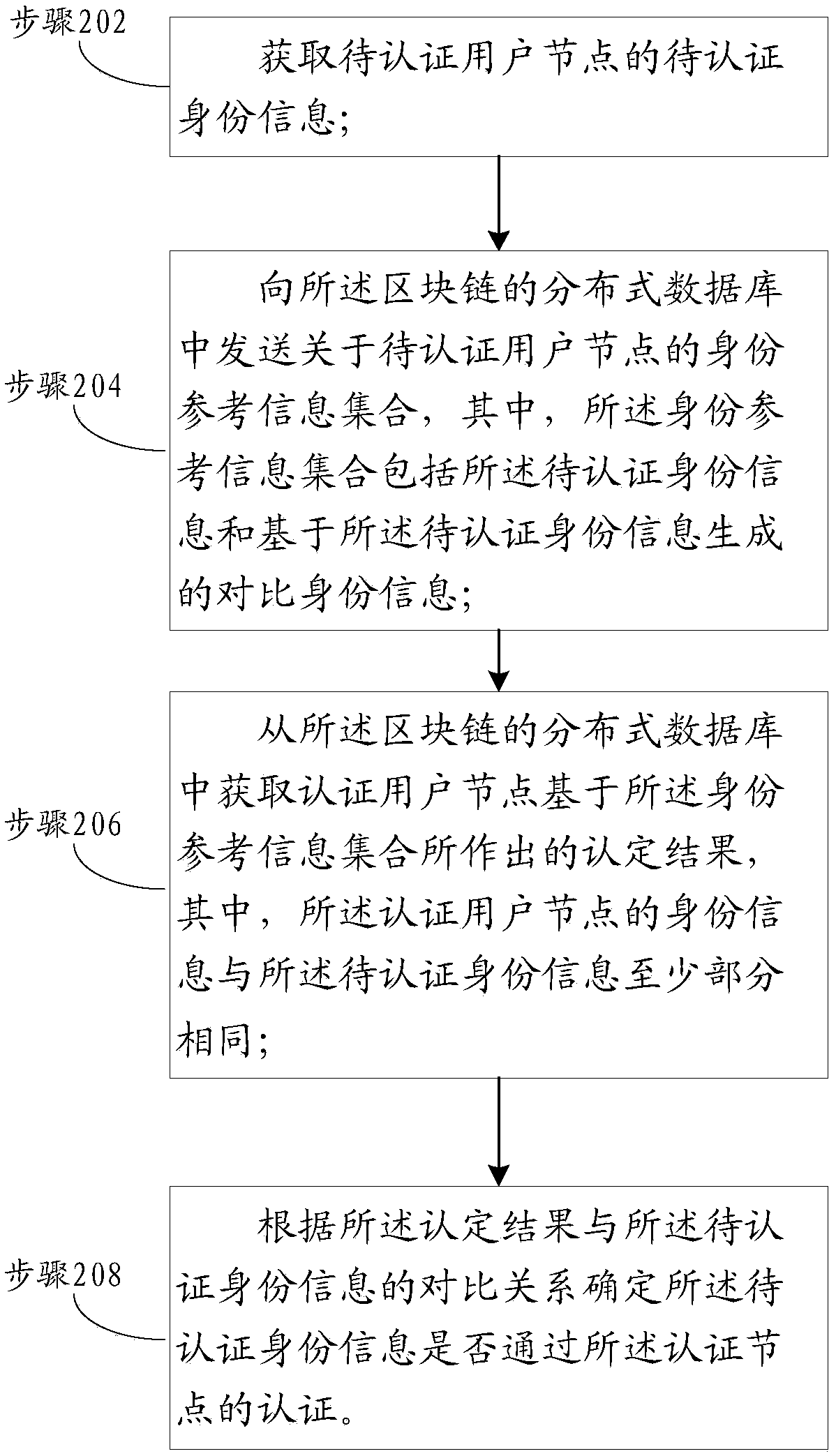
A method and apparatus for authenticate user identity in a network
ActiveCN109067791AIncrease confusionPrevent False AuthenticationTransmissionChain networkAuthentication
One or more embodiments of the present specification provide a user identity authentication method and apparatus in a network, which are applied to a block chain network including a plurality of authenticated user nodes and a user node to be authenticated. The method comprises the following steps of: obtaining identity information to be authenticated of the user node to be authenticated; sending aset of identity reference information about a user node to be authenticated, wherein the set of identity reference information comprises the identity information to be authenticated and comparison identity information generated based on the identity information to be authenticated; acquiring a determination result made by an authenticated user node based on the set of identity reference information, wherein the identity information of the authenticated user node is at least partially the same as the identity information to be authenticated; determining whether the identity information to be authenticated passes the authentication of the authentication node according to the comparison relationship between the identification result and the identity information to be authenticated.
Owner:ADVANCED NEW TECH CO LTD
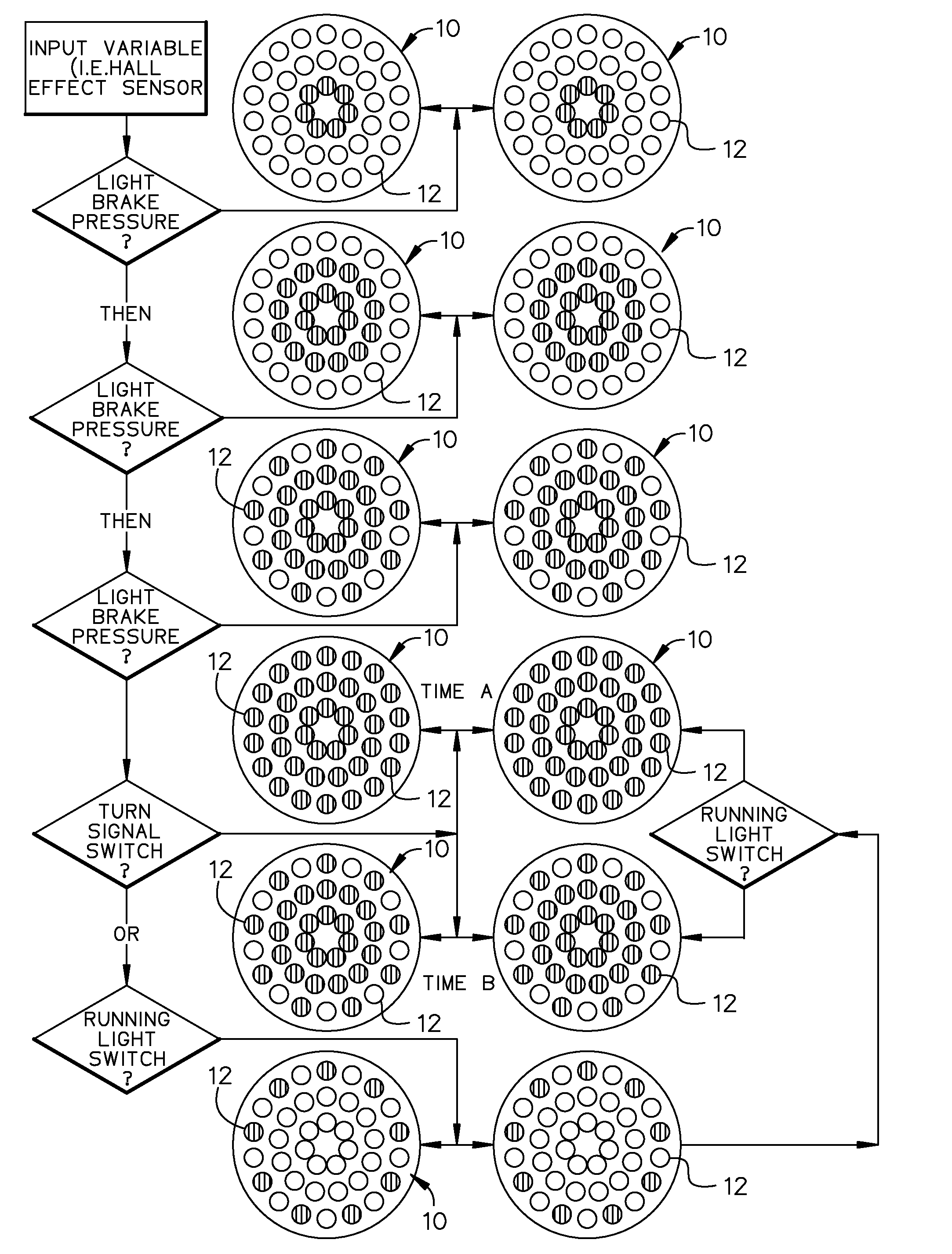
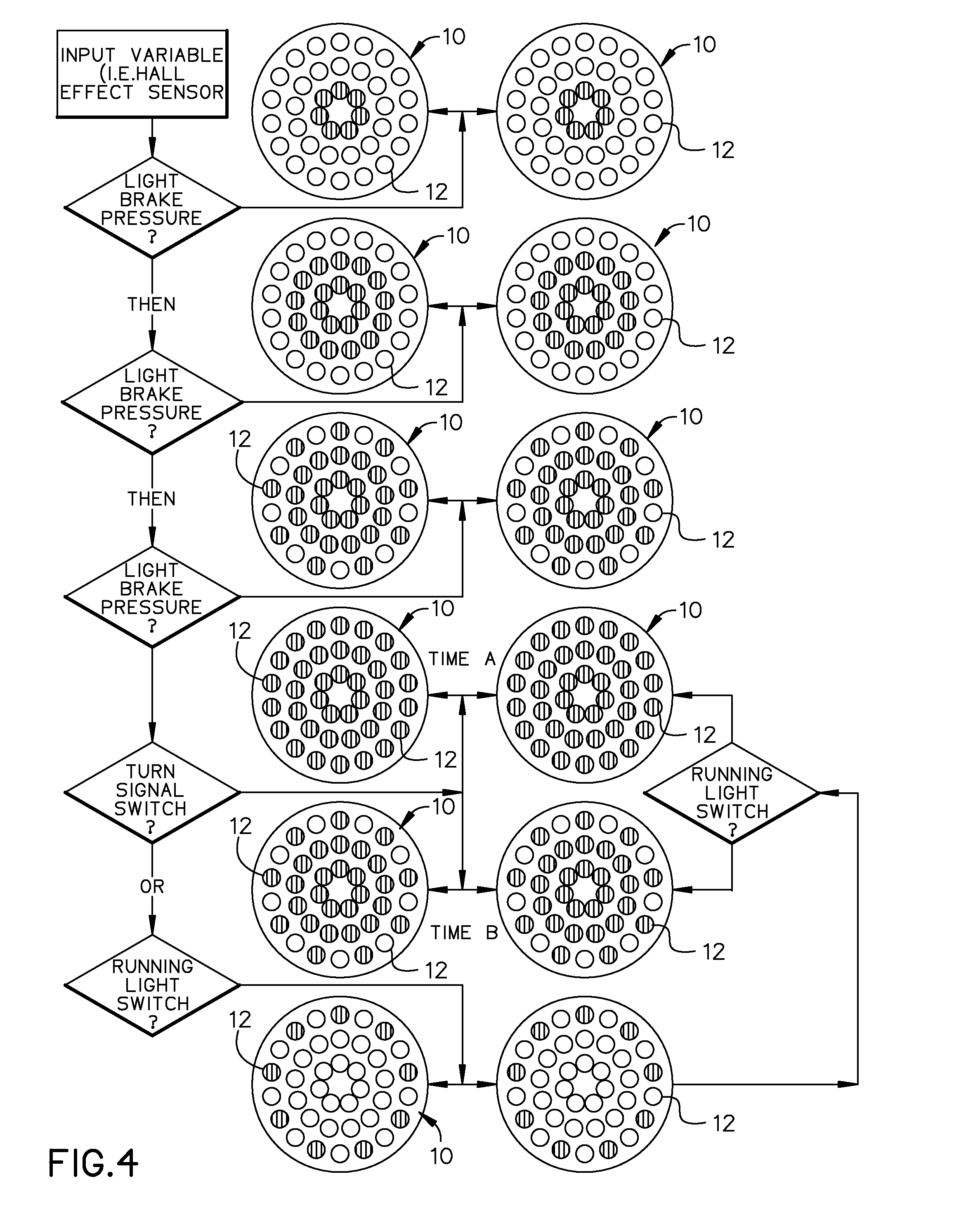
Vehicular Sequential LED Ring Warning (VSLRW) System
InactiveUS20150137965A1Quick identificationImprove securityOptical signallingSystems designDriver/operator
Vehicular Sequential LED Ring Warning System is disclosed. This system improves upon existing taillight configurations by providing operators with distinct LED rings that sequential illuminate based upon the vehicle operator's braking intensity. This system will provide all drivers with a significantly more effective method of determining braking intensity. Using a simple and consistent sequence of three LED rings, the Sequential Warning System has the capacity to revolutionize existing brake light warning system design concepts by providing driver's with a decisive illumination pattern that simply replaces the vehicle's brake lights rather than adding a separate set of LED or light bulb arrays, which only increase driver confusion when simultaneously interpreting separate brake light signals.
Owner:LANHAM NICHOLAS AARON +1
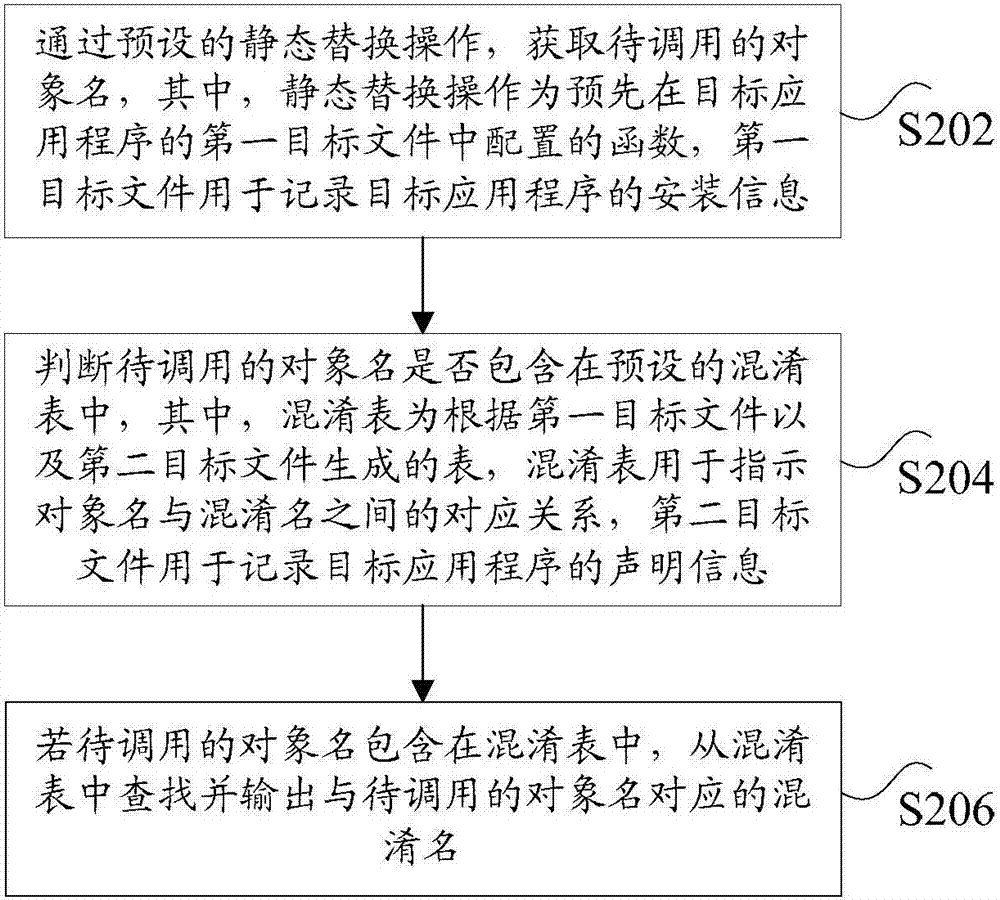
Code obfuscation method and code running method and device
InactiveCN107038354AIncrease confusionSolve technical issues with low confusion ratesProgram/content distribution protectionProgramming languageObfuscation
The invention discloses a code obfuscation method and a code running method and device. The method comprises the steps that an object name to be called is acquired through preset static replacement operation, wherein the static replacement operation is a function configured in a first target file of a target application in advance, and the first target file is used for recording installation information of the target application; whether the object name to be called is contained in a preset obfuscation table is judged, wherein the obfuscation table is generated according to the first target file and a second target file and used for indicating the corresponding relation between the object name and an obfuscation name, and the second target file is used for recording declaration information of the target application; and if the object name to be called is contained in the obfuscation table, the obfuscation name corresponding to the object name to be called is searched for in the obfuscation table and output. Through the method, the technical problem that in the prior art, the obfuscation rate of Java layer codes of an application is low is solved.
Owner:ALIBABA GRP HLDG LTD
Titanium alloy and annular titanium alloy forge piece forming method
InactiveCN104148554AIncrease contentImprove high temperature strengthMetal rollingTitanium alloyUltimate tensile strength
The invention discloses titanium alloy and an annular titanium alloy forge piece forming method. The chemical element content of the titanium alloy comprises, by weight, 7.50%-7.80% of A1, 1.00%-2.00% of Mo, 2.60%-2.80% of Zr, 2.60%-2.80% of Sn, 0.50%-1.50% of W, 0.10%-0.25% of Si, no more than 0.15% of Fe, no more than 0.10% of Cu, no more than 0.10% of Cr, no more than 0.10% of C, no more than 0.15% of O, no more than 0.04% of N, no more than 0.012% of H, and the balance Ti. The annular titanium alloy forge piece forming method comprises the following steps that after the titanium alloy is fed, and blanking is conducted at the temperature 30 DEG C below the phase transformation point; forming is conducted at the temperature 20 DEG C above the phase transformation point, and water cooling is conducted till the allay reaches the indoor temperature; double annealing is conducted on the materials obtained through the above two steps. The annular titanium alloy forge piece has the high-temperature tensile strength which can meet the use conditions and is large in affluence measure at the temperature ranging from 500 DEG C to 550 DEG C and can replace TC 25 to be used for manufacturing compressor parts and the like.
Owner:GUIZHOU ANDA AVIATION FORGING
Computing device storing look-up tables for computation of a function
ActiveUS20150067441A1Increase confusionOptimally protects against fault injectionOther decoding techniquesDigital data processing detailsAlgorithmTheoretical computer science
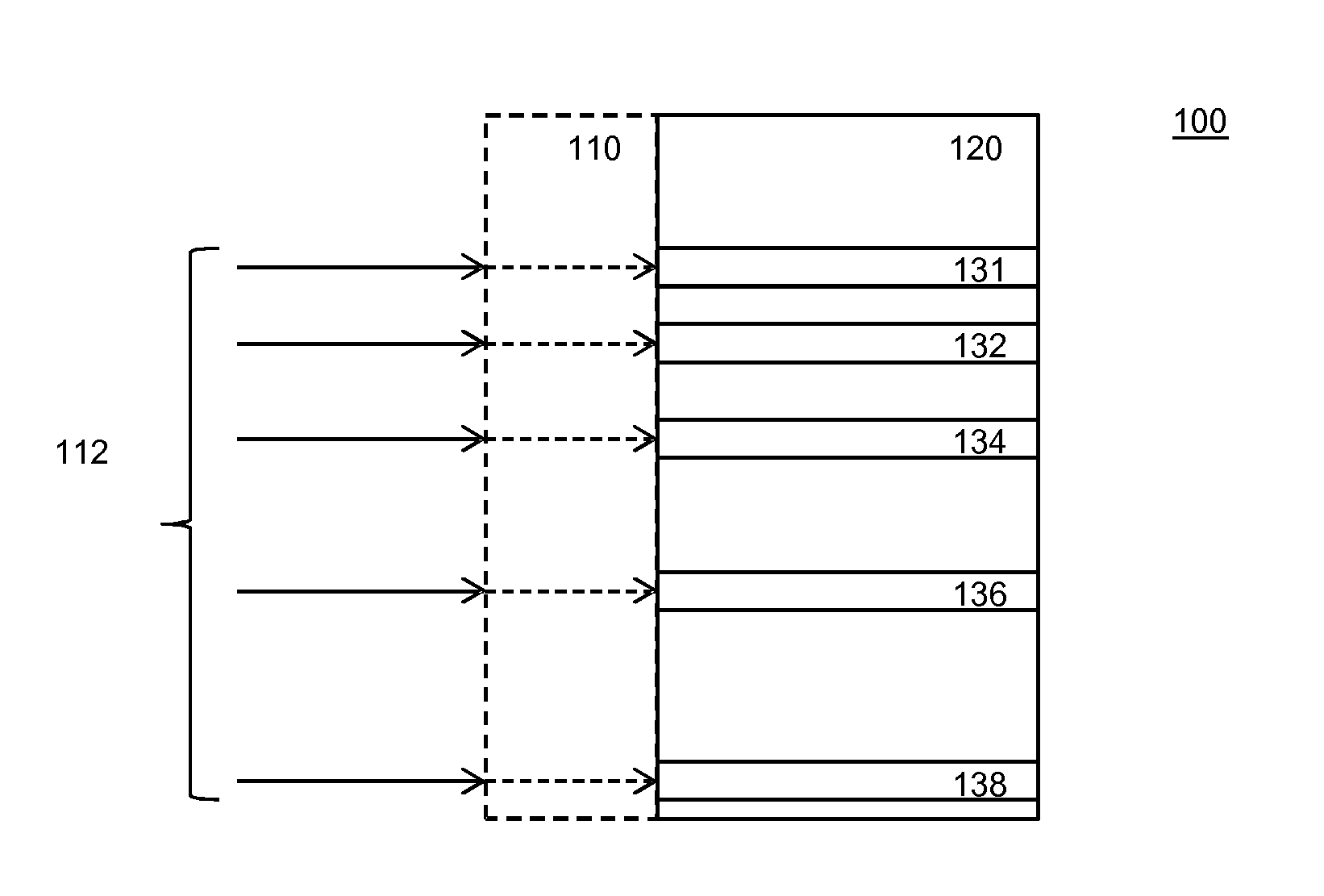
A computing device is provide, configured to compute a function of one or more inputs, the device comprising a storage device storing one or more look-up tables used in the computation of said function, the look-up tables mapping input values to output values, the look-up table being constructed with respect to the first error correcting code, a second error correcting code, a first error threshold and a second error threshold, such that any two input values (112) that each differ at most a first error threshold number of bits from a same code word of the first error correcting code, are mapped to respective output values (131-38) that each differ at most a second error threshold number of bits from a same code word of the second error correcting code, wherein the first error threshold is at least 1 and at most the error correcting capability (t1) of the first error correcting code, and the second error 10 threshold is at most the error correcting capability (t2) of the second error correcting code.
Owner:KONINKLJIJKE PHILIPS NV
Hash algorithm based on complex dynamic network
ActiveCN101872339AImprove computing efficiencyImprove securityTransmissionComplex mathematical operationsComputation complexityMessage structure
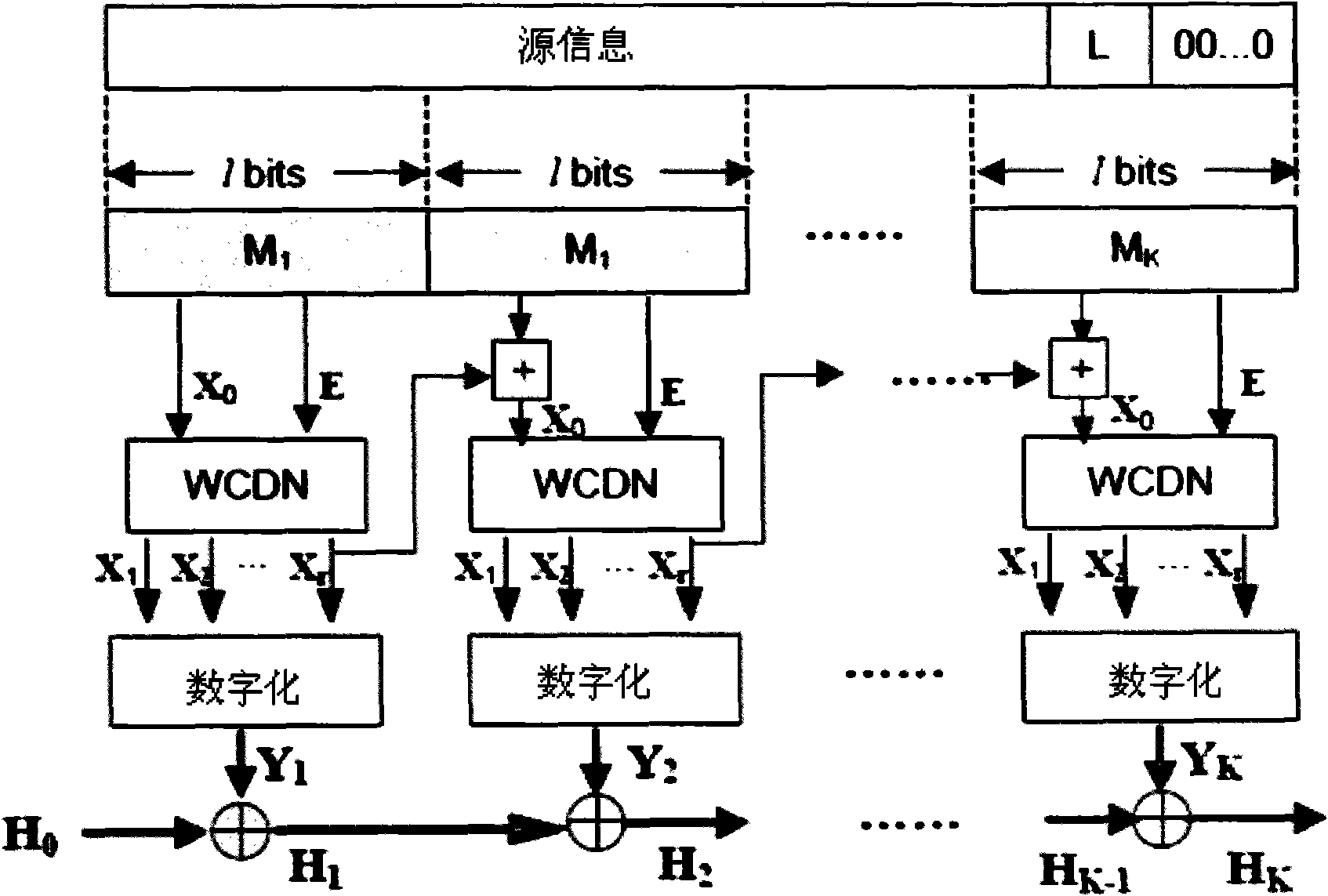
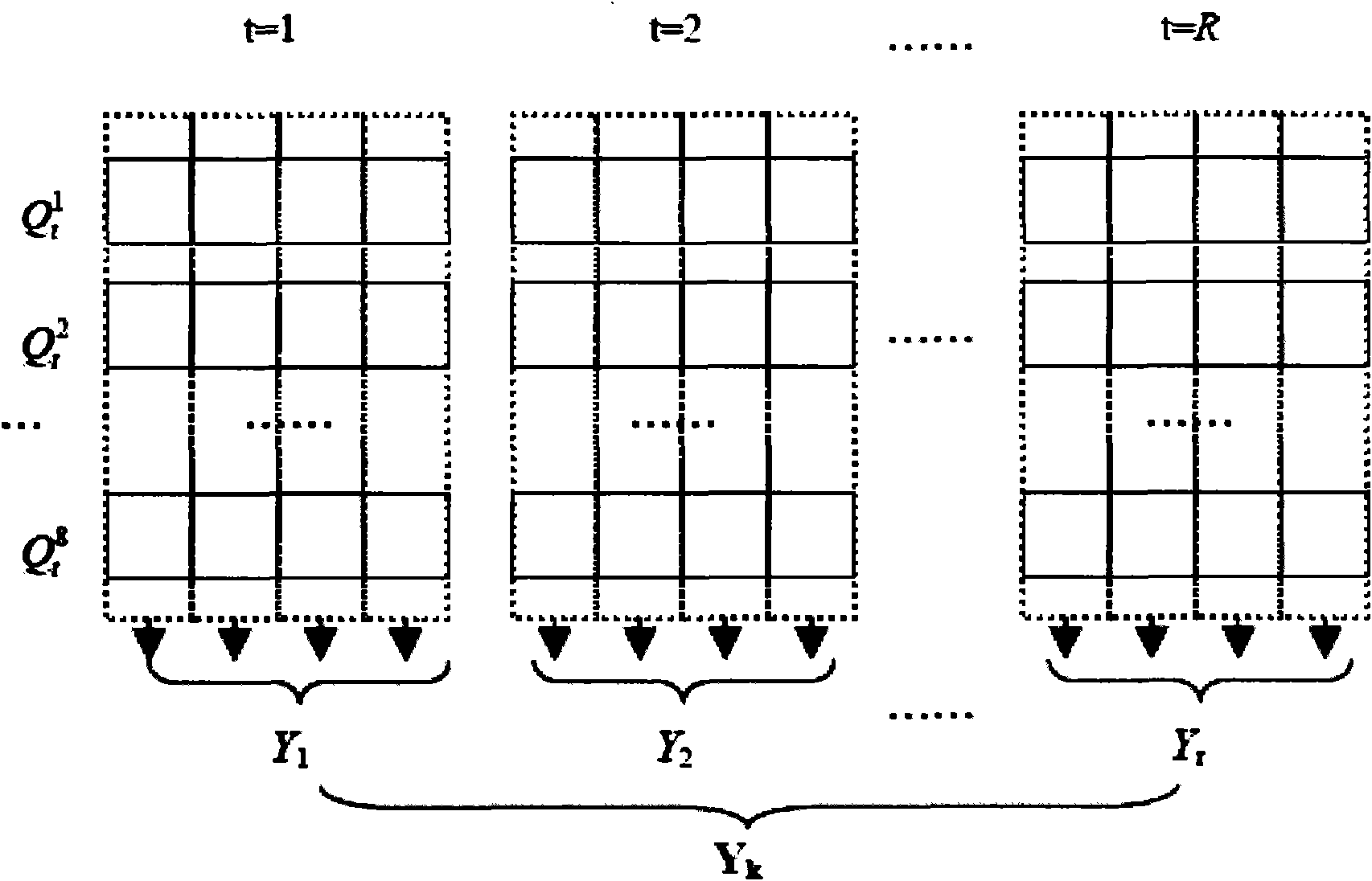
The invention discloses a Hash algorithm based on a complex dynamic network. The algorithm comprises constructing a message block network MBN with message blocks of original messages treating Hash according to certain rules, mapping point sets and edge sets of the MBN into initial values of node states and adjacency matrixes of a complex dynamic network CDN according to certain transformation rules, thereby forming the weighted complex dynamic network WCDN with an original message structure. The Hash value can be obtained finally through iteration, quantization and difference processing of the WCDN of each message block. The invention adopts the extreme sensitivity of the WCDN to the initial values and parameters, and can obtain safety performance with excellent confusion and diffusion after multiple WCDN iterations. Simultaneously, the invention can effectively reduce the computational complexity.
Owner:盐城市鹤业实业投资有限公司
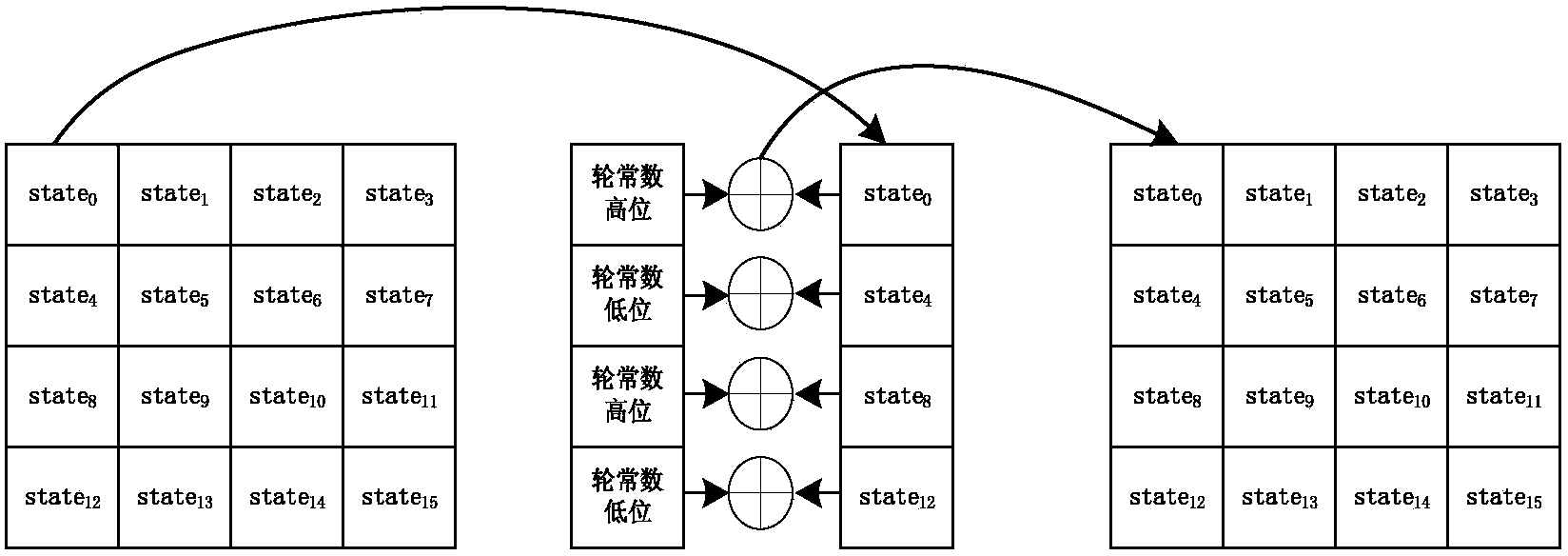
Novel low-resource efficient lightweight Surge block cipher implementation method
ActiveCN104065474AClear structureImprove performanceEncryption apparatus with shift registers/memoriesKey sizeComputer hardware
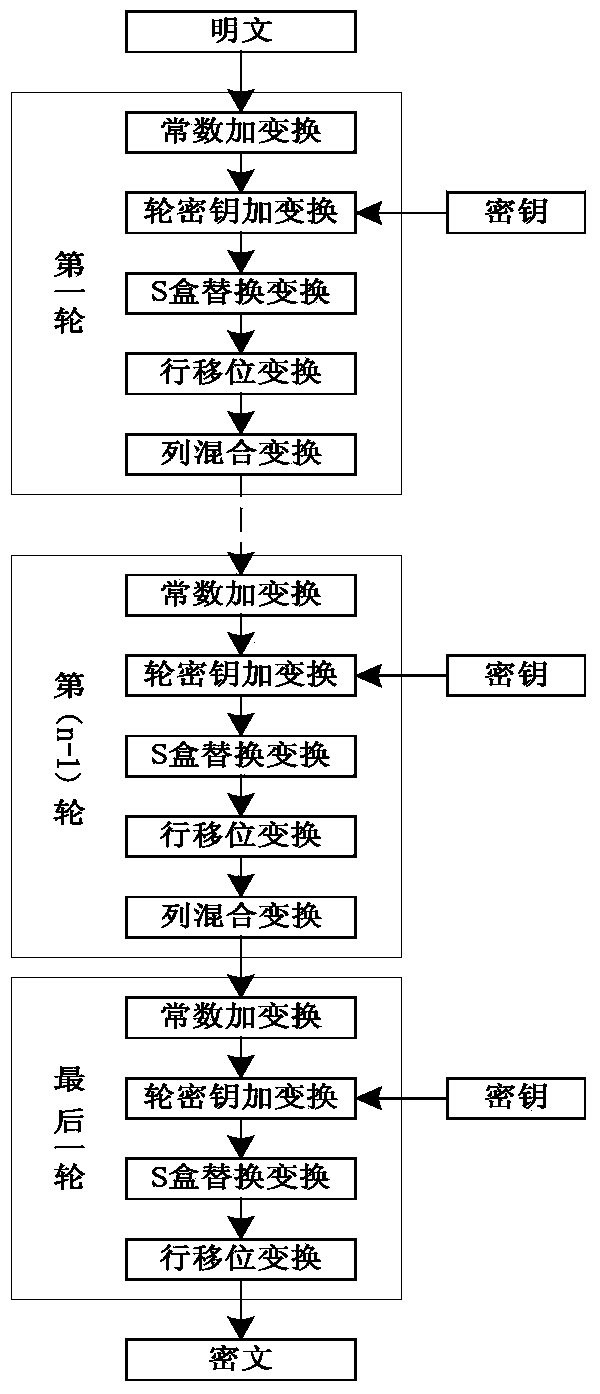
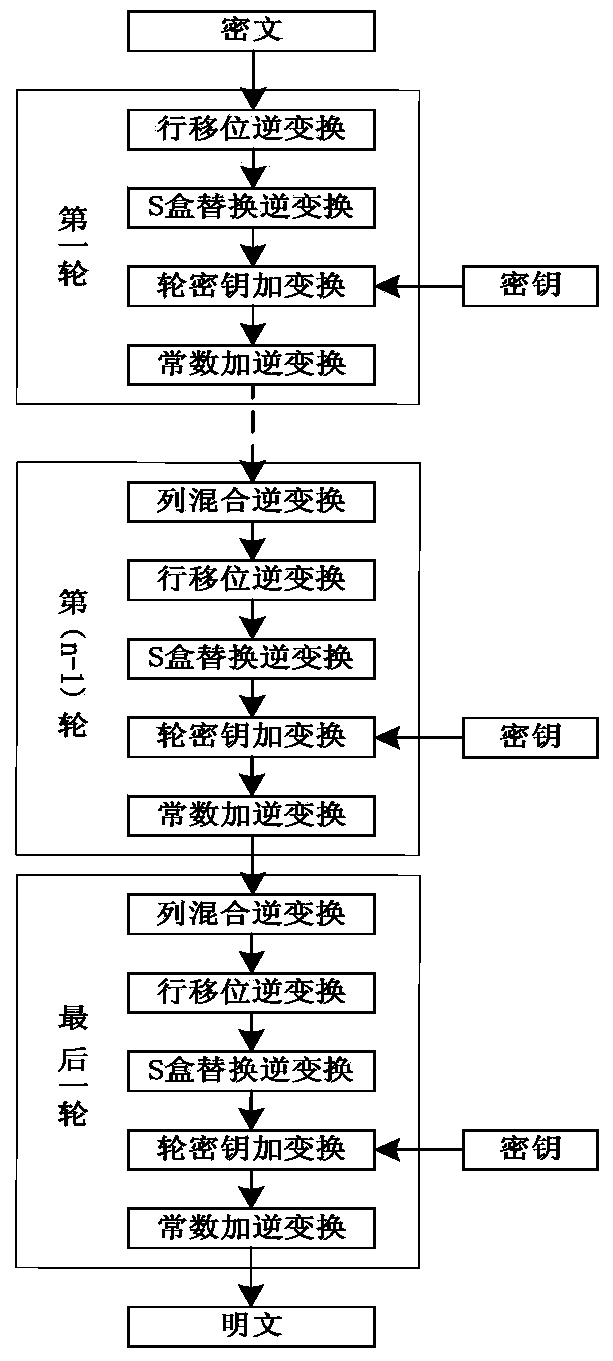
The invention discloses a novel low-resource efficient lightweight Surge block cipher implementation method. The method comprises the steps that the Surge block length is designed to be of a 64-bit type, and the secrete key length is designed to be of the 64-bit type, the 80-bit type and the 128-bit type on the basis of the SPN structure; a secrete key is in a non-extensible mode; five modules of a round function are combined in a new mode, the encryption sequence is constant addition, round key addition, S-box replacement, row shifting and column mixing transformation, and column mixing transformation does not exist in the last round; a constant addition transformation module operates a round constant in each round; according to the round constant selection combination, 0, 1, 2 and 3 are selected as the high bits, the combination of one odd number, one even number, one even number and one add number from 0 to 15 is selected as the low bits, and the obtained combinatorial numbers are randomly fixed into a permutation; a column mixing transformation module utilizes the (0,1,2 and 4) combination which facilitates hardware implementation for forming a matrix, and hardware is constructed on a galois field GF (24) to obtain the friendly matrix. The experimental result shows that the occupied area resources are smaller, meanwhile, the encryption performance is good and the known attacks can be resisted compared with existing lightweight ciphers of the SPN structure.
Owner:HENGYANG NORMAL UNIV
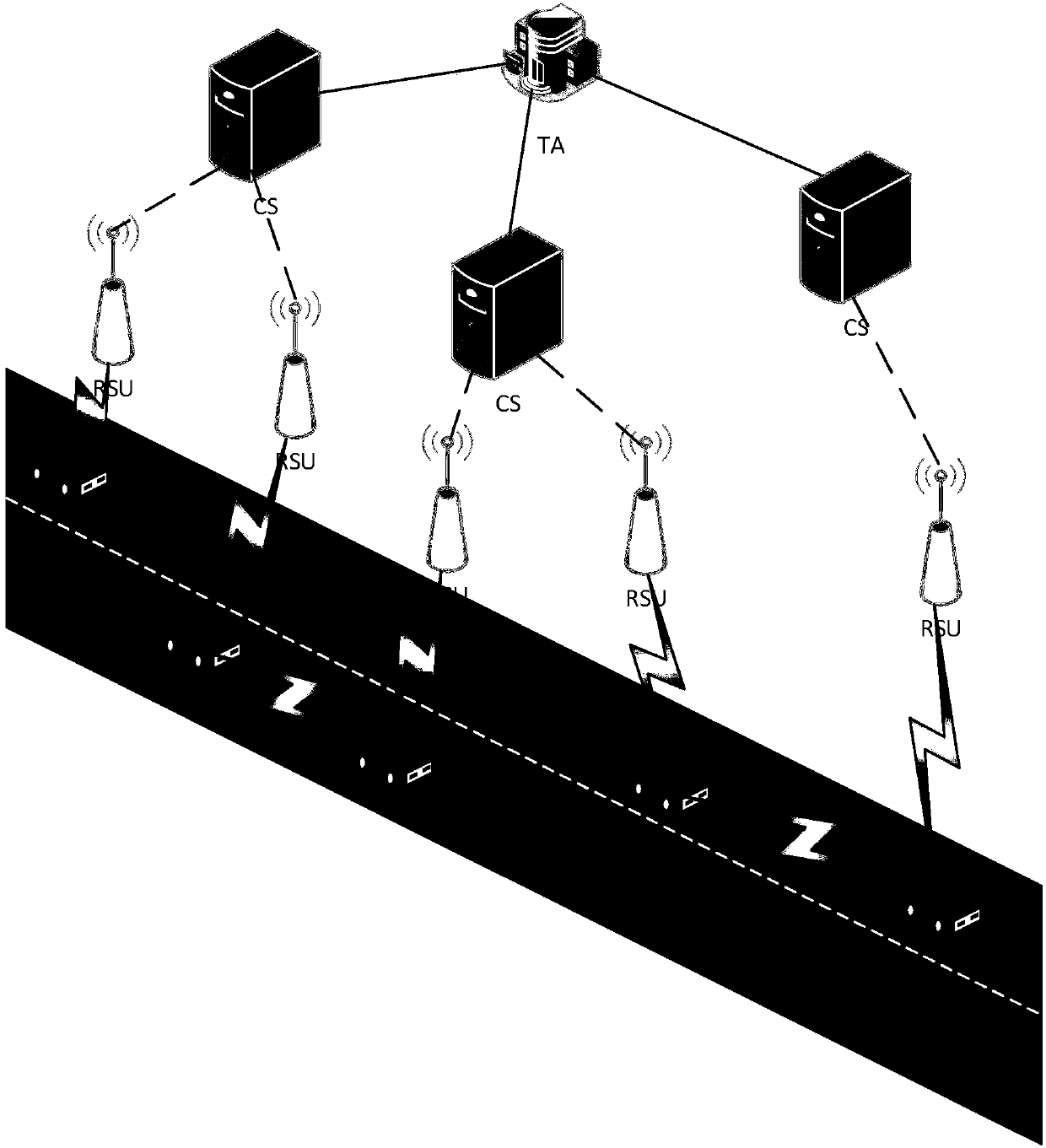
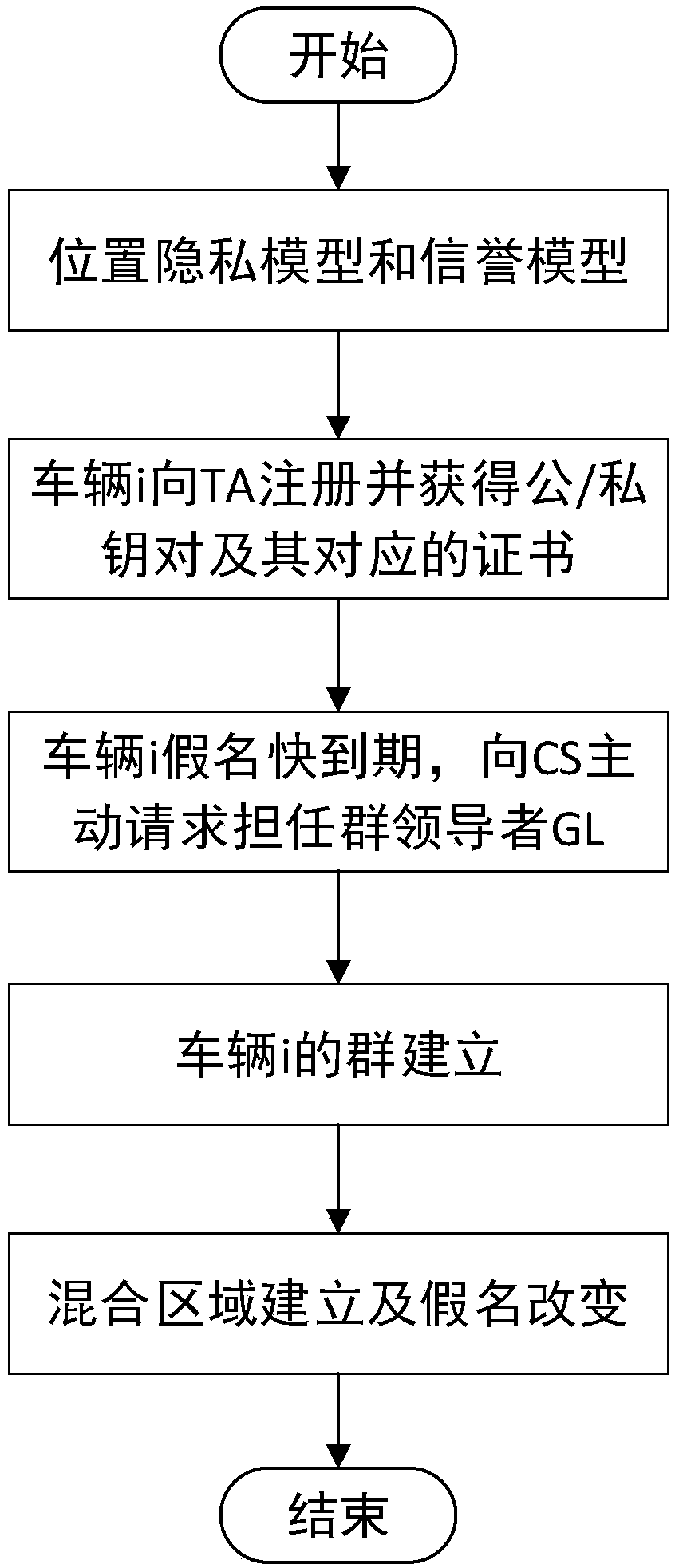
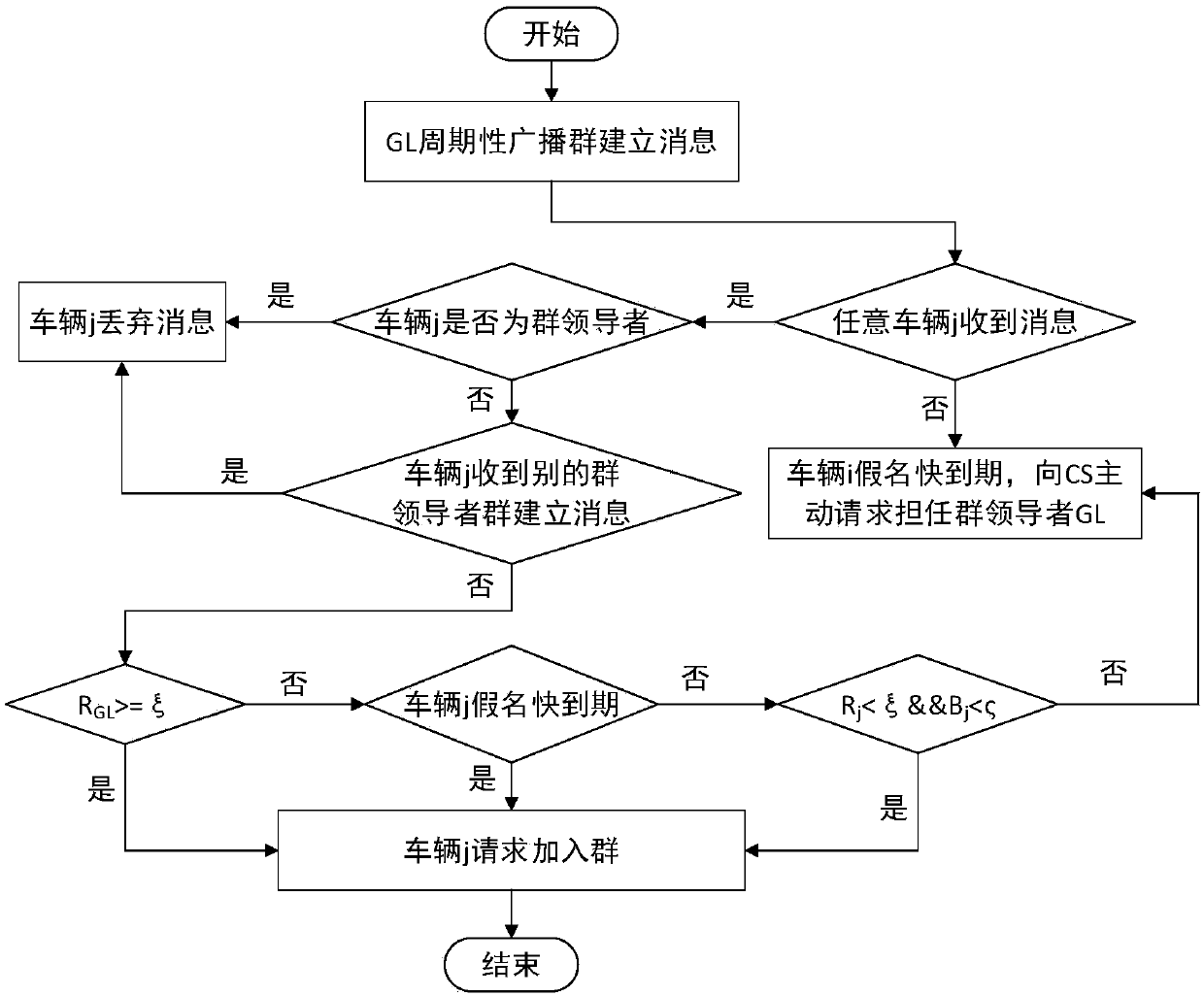
Vehicle position privacy protection method based on group signature and reputation
ActiveCN107947942AIncrease confusionReduce threatUser identity/authority verificationPrivacy protectionBroadcasting
The invention discloses a vehicle position privacy protection method based on group signature and reputation, which comprises a reputation model for encouraging more vehicles to cooperate with each other to form a group, a privacy model for evaluating the position privacy strength of the vehicle, a group forming and dynamic mixed region establishing mechanism, and a pseudonym replacement mechanism. Any vehicle in the vehicle-mounted ad hoc network actively requests establishment of a group from a control server according to the reputation value of the vehicle when the pseudonym of the vehicleis soon to be expired; the control server allocates a group leader role to the requesting vehicle and dynamically forms a mixed region according to the current position of the requesting vehicle; theother vehicles in the mixed region judge whether the cooperation is participated in or not to change the pseudonym according to the reputation value, privacy strength and the remaining time of the pseudonym of the other vehicles; and the reputation value of the vehicles can be dynamically adjusted. According to the method, more vehicles can be encouraged to join the group, thereby changing the pseudonym in cooperation and ensuring the position privacy of the vehicles; meanwhile, the vehicles do not need to keep a silent state in the formed mixed region but broadcast messages as a group identity so that the running safety of the vehicles is guaranteed; furthermore, resource expenditure caused by unnecessary frequent change of the pseudonym can be effectively reduced.
Owner:ANHUI UNIVERSITY
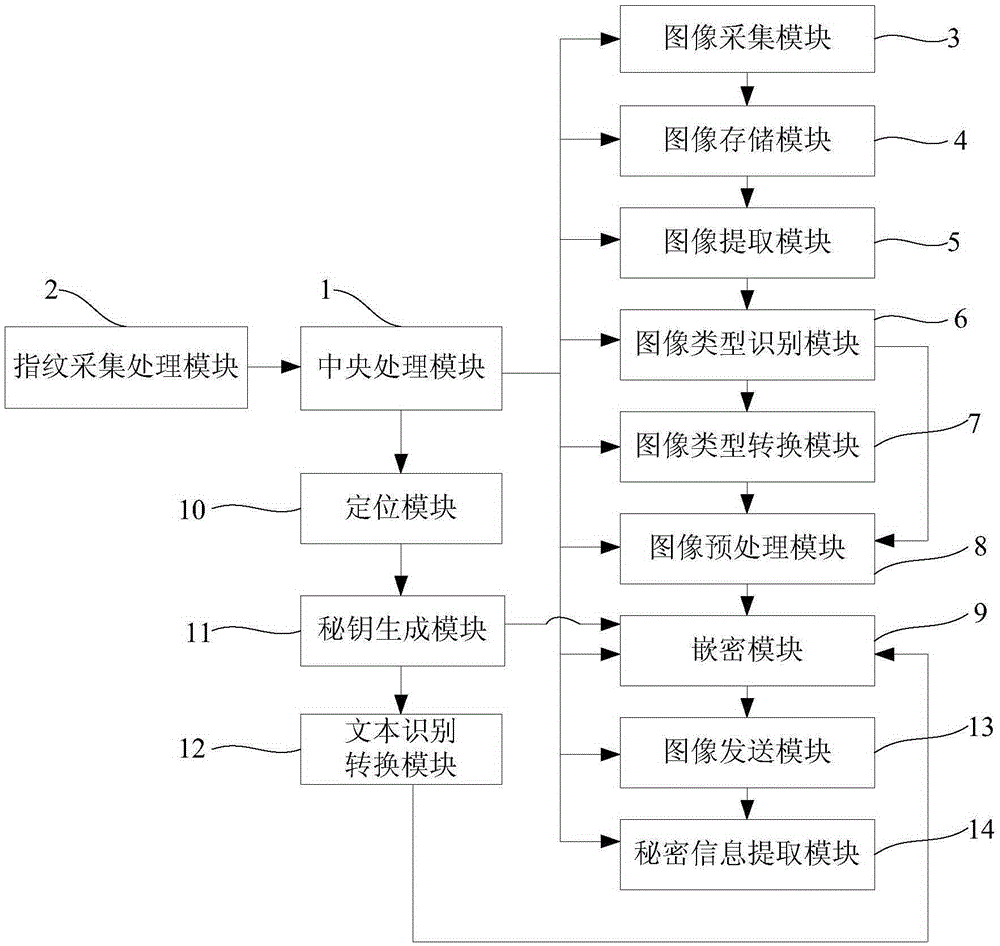
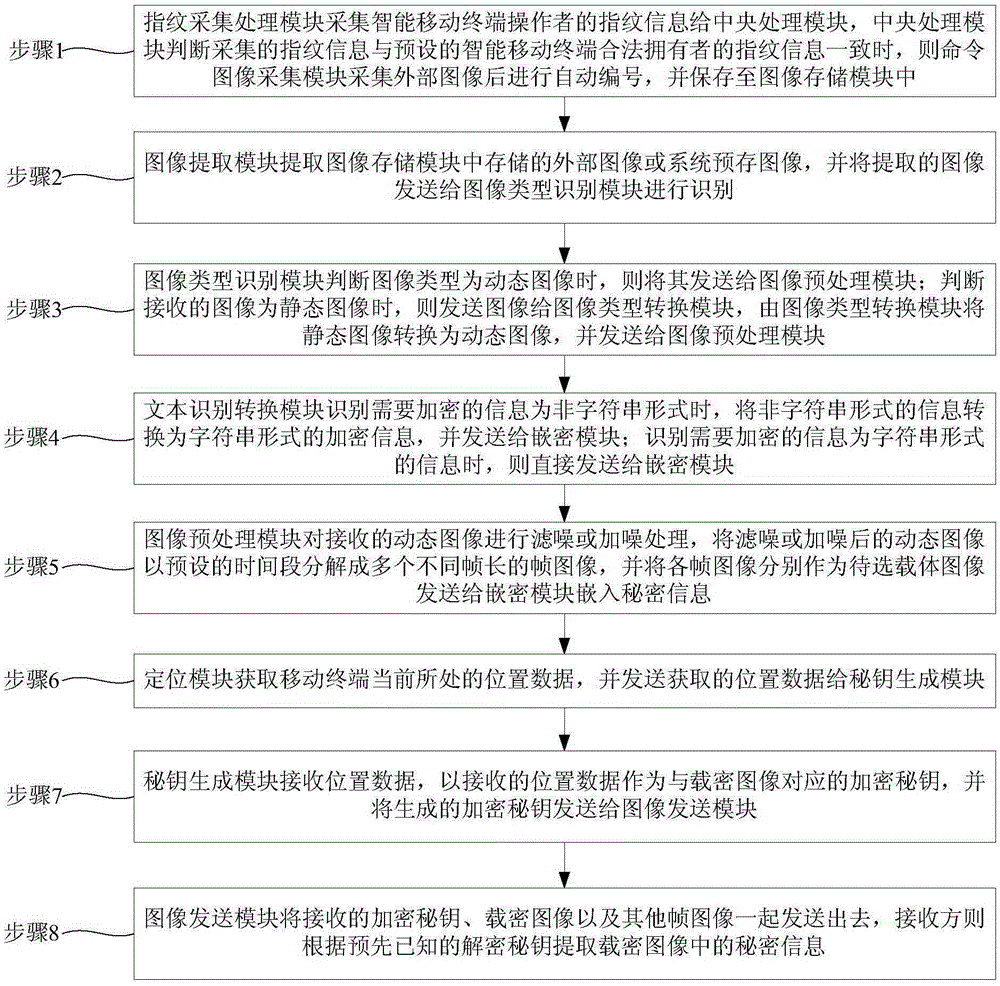
Industrial drawing encryption system based on image of intelligent mobile terminal and encryption method of system
ActiveCN105243309AEnsure safetyIncrease confusionDigital data protectionDigital data authenticationImage extractionText recognition
The present invention relates to an industrial drawing encryption system based on an image of an intelligent mobile terminal and an encryption method of the system. The intelligent mobile terminal comprises a central processing module and modules respectively connected to the central processing module, such as a fingerprint acquisition processing module, an image acquisition module, an image storage module, an image extraction module, an image type recognition module, an image type conversion module, an image pre-processing module, a cryptographic module, a positioning module, a private key generation module, a text recognition conversion module, an image transmission module and a private information extraction module; the image storage module is connected to the image acquisition module and the image extraction module; the image pre-processing module is connected to the image type recognition module, the image type conversion module and the cryptographic module; the positioning module is connected to the private key generation module; the text recognition conversion module is connected to the cryptographic module; the image transmission module is connected to the cryptographic module, the private key generation module and the private information extraction module; and not only can a legal identity of a mobile terminal operator be identified, but also private information can be safely embedded into an industrial drawing.
Owner:湖州菱创科技有限公司
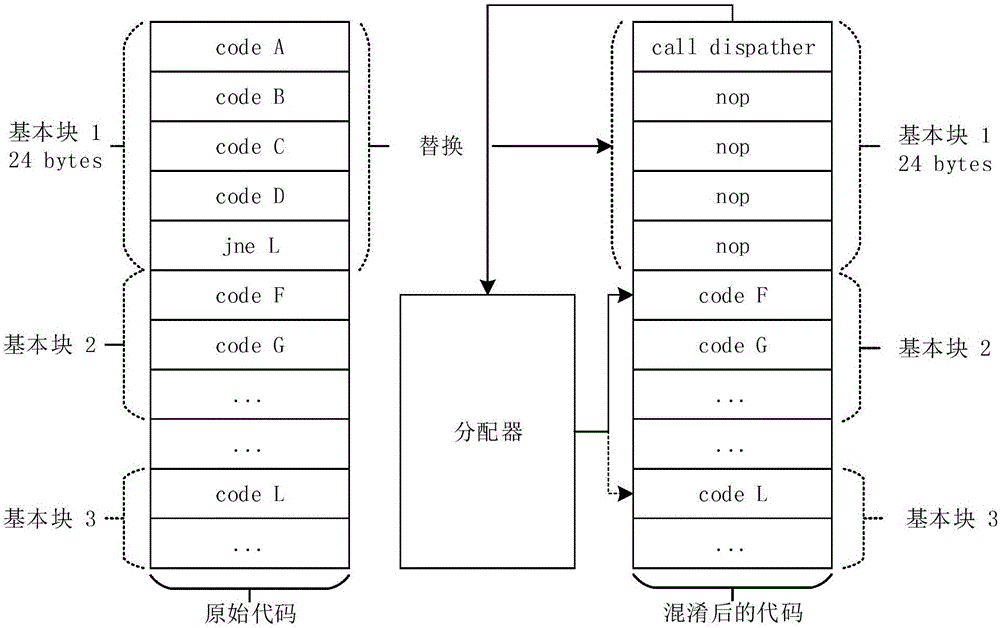
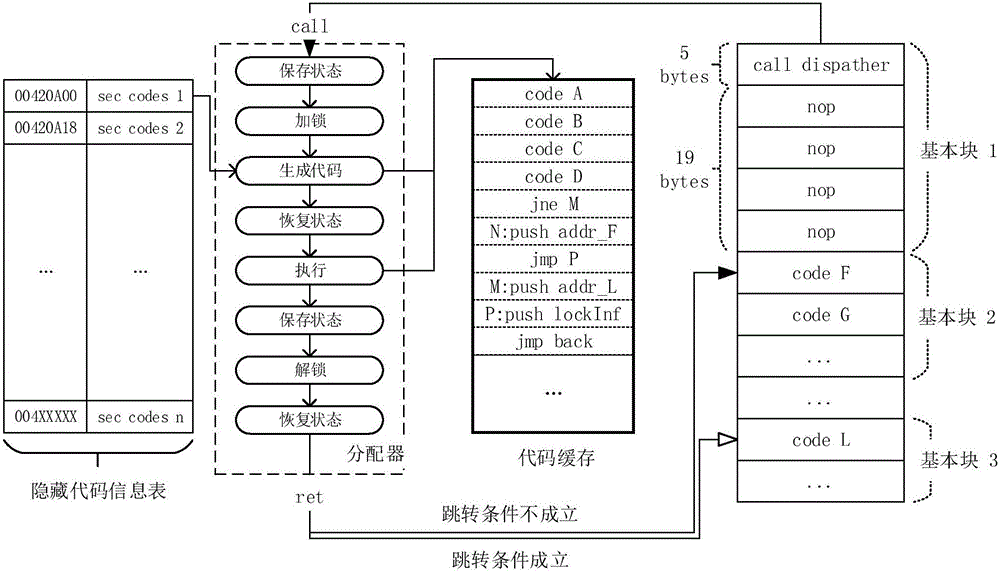
Binary software protection method by means of dynamic fine-grained code hiding and obfuscating technology
ActiveCN106650340AImprove securityResistance to static analysisProgram/content distribution protectionCoding blockRest position
The invention discloses a binary software protection method by means of a dynamic fine-grained code hiding and obfuscating technology. The method comprises the steps that S1, a hidden target is selected, wherein a to-be-hidden code block is selected in a target program with a basic block as a unit; S2, the selected basic block is hidden, wherein according to each to-be-hidden basic block, an original code segment is replaced with a distributor function call, and other obfuscating instructions are filled in the rest positions; S3, the codes are packaged again, a new code segment is created so as to save all additional logic and data. The method has the advantages of being wide in application range, light in magnitude, extendable, high in safety and the like.
Owner:NAT UNIV OF DEFENSE TECH
Flash-bang projectile
InactiveUS20050188885A1Increase confusionOvercome problemsHollow inflatable ballsHollow non-inflatable ballsTime delaysCompression device
A flash-bang projectile that generates one or more noise pulses and one or more flashes of light. In generating a noise pulse, the flash-bang projectile provides a housing that includes a gas chamber that entraps air. The gas chamber includes a compression device that, when the flash-bang projectile is shot or otherwise ejected by a gun or other form of ejection device, compresses the air that is entrapped in the gas chamber. A burst disk forms one wall of the gas chamber and is configured to rupture a selected time delay after the air has been compressed. Rupturing of the burst disk releases the compressed air entrapped in the gas chamber, allowing the air to be released through a horn nozzle, thereby generating a noise pulse. The flash-bang projectile may have more than one gas chambers, with associated compression devices, whose burst disks are configured to rupture with diverse time delays, in which case the flash-bang projectile can generate multiple noise pulses with corresponding delays. In generating a light flash, the flash-bang projectile includes one or more light generating devices, which may include items such as flash lamps, light-emitting devices, and the like, along with a control module for powering the light generating devices. The control module includes an electrical generating arrangement that uses a portion of the kinetic energy imparted to the flash-bang projectile when it is ejected to generate electrical energy. The electrical energy is, in turn, used to power the light generating devices. Electrical traces on the burst disks are broken when the burst disks rupture to facilitate synchronization of the light flashes with the noise pulses.
Owner:OPTICAL ALCHEMY
Shining thermal barrier coating system of rare earth niobate based on defective fluorite structure and preparation method of shining thermal barrier coating system
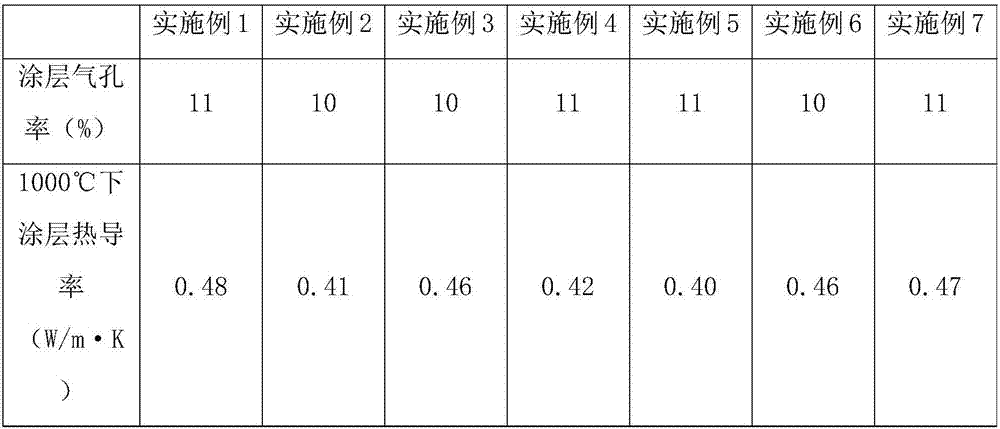
InactiveCN106967953ALow thermal conductivityImprove oxygen barrier performanceMolten spray coatingVacuum evaporation coatingElectron beam physical vapor depositionGas phase
Owner:乐延伟
Intelligent guiding system, with movable laser wall, for street crossing of pedestrians
InactiveCN106530683AMeet the needs of crossing the streetMeet the characteristics of crossing the streetControlling traffic signalsControl with pedestrian guidance indicatorEngineeringStreet crossing
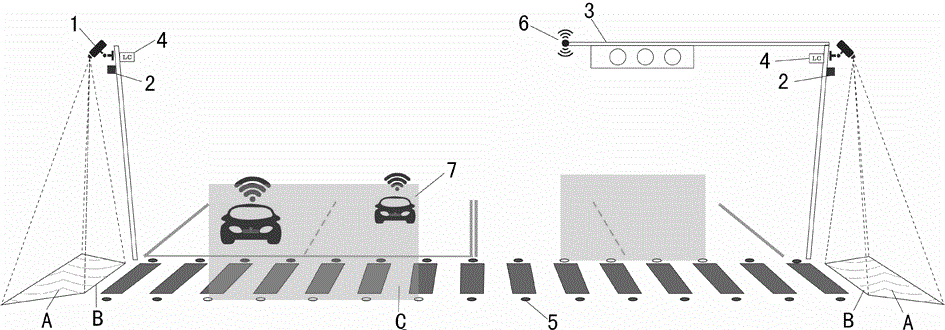
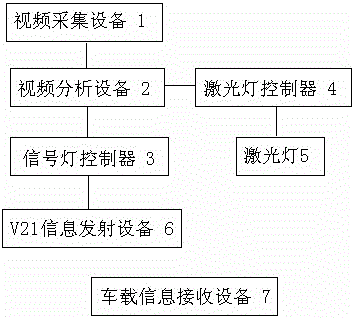
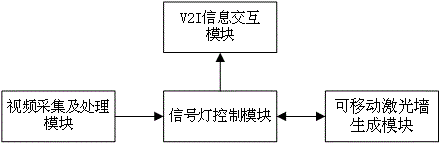
The invention relates to an intelligent guiding system, with a movable laser wall, for street crossing of pedestrians. The system comprises video collectors arranged at the two ends of a pedestrian zebra crossing respectively, video analyzers connected to the video collectors respectively, signal lamp controllers and a laser lamp controller connected to the video analyzers, laser lamps connected to the laser lamp controller, a V2I information emitter connected to the signal lamp controller, and vehicle-mounted information receivers arranged on motor vehicles respectively. The system satisfies the street crossing requirement of pedestrians to the largest degree, accords with street-crossing features of different types of pedestrians, can limit violated street crossing behaviors of the pedestrians effectively, and avoids disorder of street crossing in a crossing.
Owner:JILIN UNIV
Optically detectable, floatable, arsenic- and antimony-free, ceramisable lithium-aluminium-silicate glass
Optically detectable, arsenic- and antimony free, ceramic lithium-aluminosilicate float glass, in prestressed from, comprises e.g. silicon dioxide (55-69 wt.%), aluminum oxide (19-25 wt.%), lithium oxide (3.2-5 wt.%), sodium oxide (0-1.5 wt.%), potassium oxide (0-1.5 wt.%), magnesium oxide (0-2.2 wt.%), calcium oxide (0-2 wt.%), strontium oxide (0-2 wt.%), barium oxide (0-2.5 wt.%), zinc oxide (0 to less than 1.5 wt.%), titanium dioxide (1-3 wt.%), zirconium oxide (1-2.5 wt.%), tin oxide (0.1 to less than 1 wt.%), phosphorus pentoxide (0-3 wt.%) and boric oxide (0-2 wt.%). Optically detectable, arsenic- and antimony free, ceramic lithium-aluminosilicate float glass, in prestressed from, comprises silicon dioxide (55-69 wt.%), aluminum oxide (19-25 wt.%), lithium oxide (3.2-5 wt.%), sodium oxide (0-1.5 wt.%), potassium oxide (0-1.5 wt.%), magnesium oxide (0-2.2 wt.%), calcium oxide (0-2 wt.%), strontium oxide (0-2 wt.%), barium oxide (0-2.5 wt.%), zinc oxide (0 to less than 1.5 wt.%), titanium dioxide (1-3 wt.%), zirconium oxide (1-2.5 wt.%), tin oxide, (0.1 to less than 1 wt.%), phosphorus pentoxide (0-3 wt.%), neodymium oxide (0.01-0.6 wt.%, or 100-3000 ppm), cobalt oxide (0-0.005 wt.%), fluorine (0-1 wt.%) and boric oxide (0-2 wt.%), where the sum of titanium dioxide, zirconium oxide and tin oxide is 2.5-5 wt.%.
Owner:SCHOTT AG
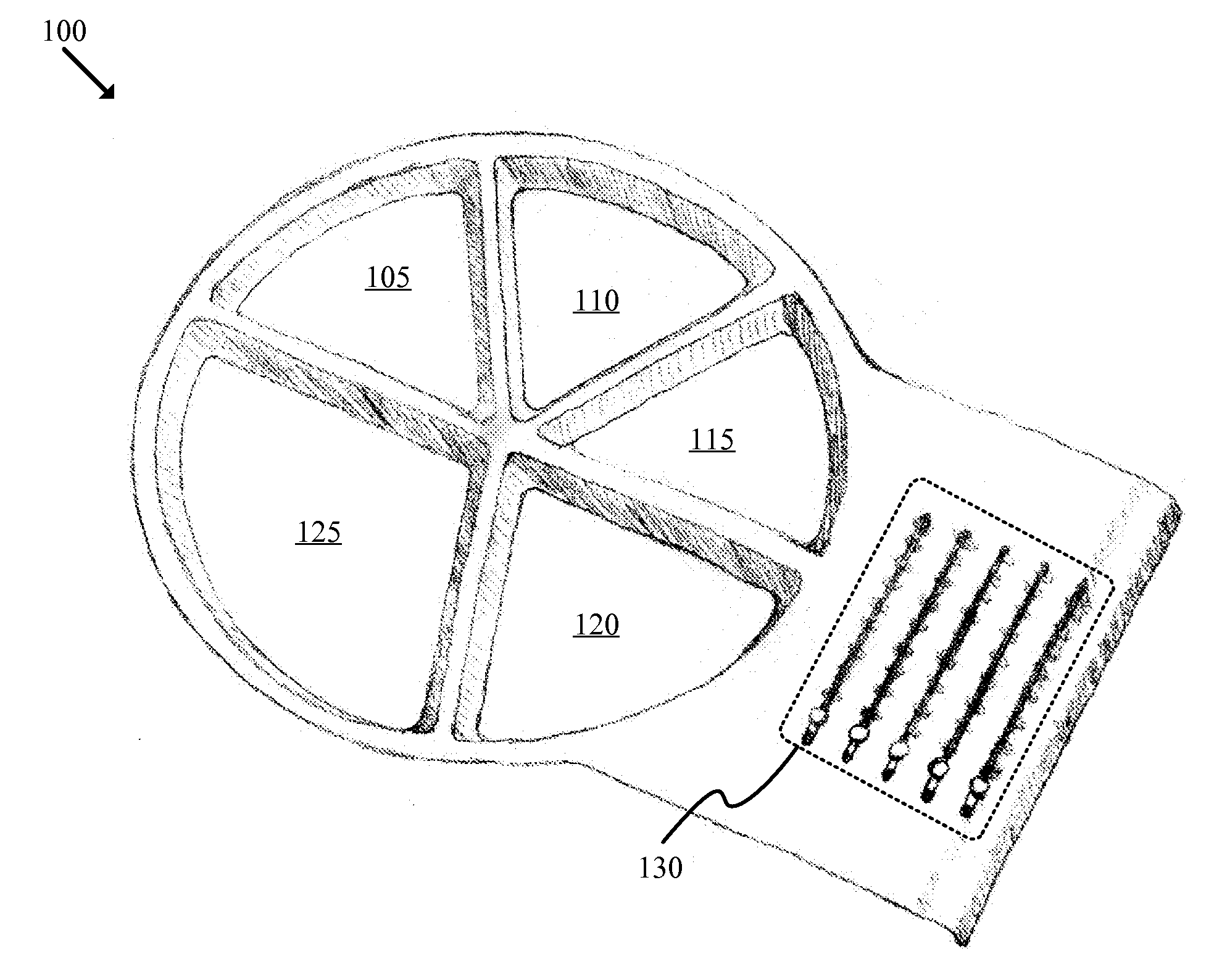
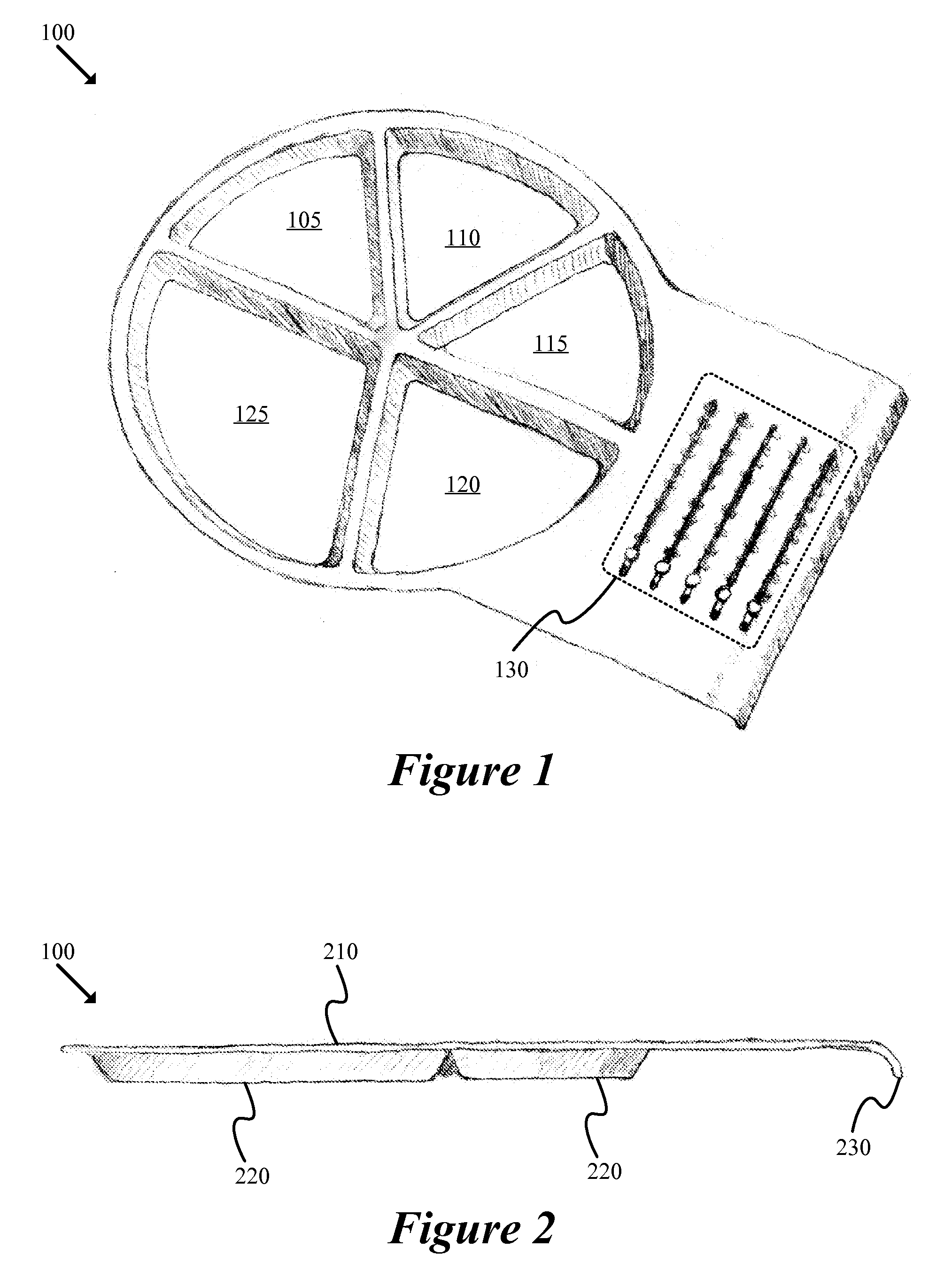
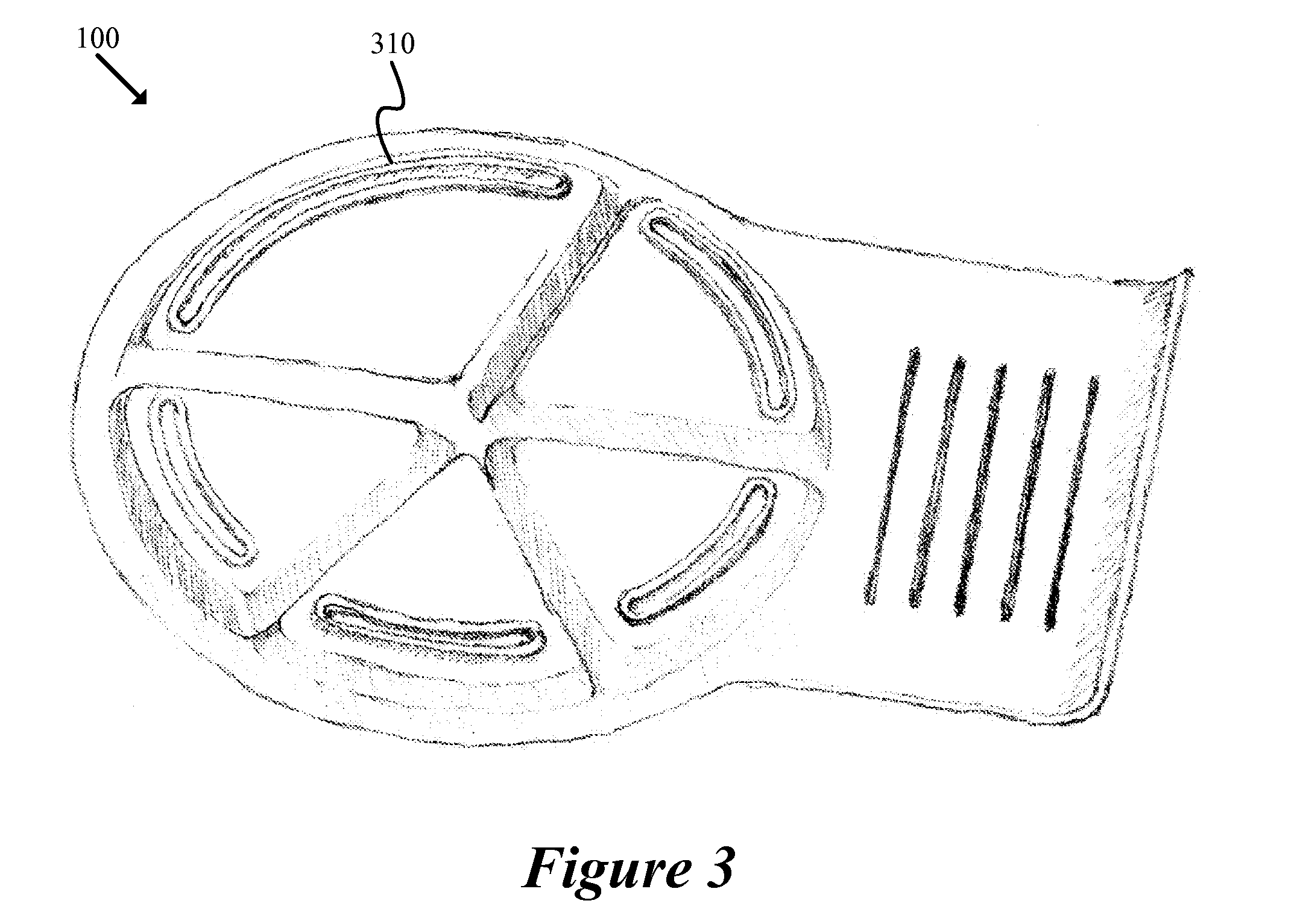
Dishware with Nutrition Guidance and Portion Tabulation
InactiveUS20120183933A1Increase confusionImprovement effortsNutrition controlPlatesServing sizeNutrition
A dishware item adapted to provide serving size guidance and tabulate portion size is described. The dishware item is optimized for use by young children, having functional and graphic design elements that provide stimulation, form a positive association with mealtime, and help instill a lifetime of healthy eating habits. The dishware item includes multiple food item compartments, each compartment associated with a type of food item. The dishware item also includes multiple tabulation counters, each counter associated with a food item compartment. In addition, the dishware item includes a non-skid base coupled to the food item compartments and the tabulation counters. The non-skid base is adapted to prevent movement of the dishware during use.
Owner:SMILER ELLEN MAE
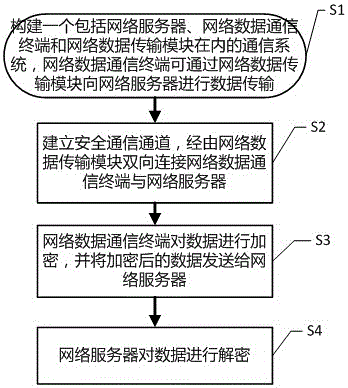
Network data encryption transmission method
InactiveCN106067878AEnsure safetyGuaranteed reliabilityTransmissionCommunications systemComputer terminal
Owner:STATE GRID SHANDONG ELECTRIC POWER CO SHOUGUANG POWER SUPPLY CO +2
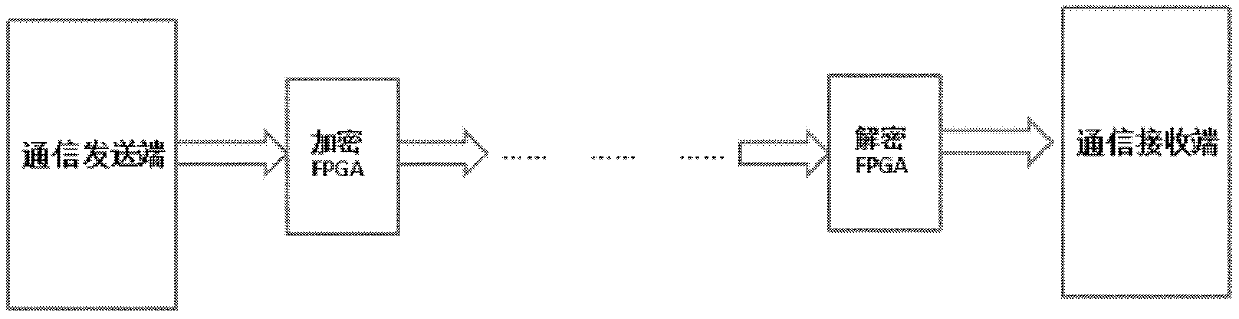
Secret communication method based on FPGA high-speed serial IO
ActiveCN103346878AData confusion is highGood encryptionSecret communicationSecuring communicationData transmission circuitData transmission systems
The invention discloses a secret communication method based on an FPGA high-speed serial IO. The secret communication method includes the steps of building a data transmission channel in an FPGA chip, allocating the FPGA chip with the data transmission channel at the position where a communication transmitting end is connected in a communication transmission network, allocating the FPGA chip with the data transmission channel at the position where a communication receiving end is connected in the communication transmission network, at the communication transmitting end, transmitting data to be transmitted into the FPGA chip, carrying out primary transmission in the data transmission channel, completing data encryption, then outputting the data from the FPGA chip, enabling the data to enter the communication transmission network, at the communication receiving end, transmitting the data received from the communication transmission network into the FPGA chip, carrying out primary transmission in the data transmission channel, completing data decryption, then outputting the data from the FPGA chip, and enabling the data to enter a communication terminal. By means of the secret communication method, the data transmission rate is improved, and the equipment loads are reduced.
Owner:INST OF SEMICONDUCTORS - CHINESE ACAD OF SCI
Method for providing stronger encryption using conventional ciphers
InactiveUS20090168994A1Increase obfuscationIncrease confusionEncryption apparatus with shift registers/memoriesSecret communicationCipher
A method of transforming files that will produce a much stronger encryption over conventional encryption methods.
Owner:HEUSS MICHAEL R
Polymerization method capable of effectively controlling phase transformation in PPTA (poly-p-phenylene terephthamide) synthesis process
InactiveCN103467736AImprove mechanical propertiesIncrease confusionMonocomponent copolyamides artificial filamentTurbidityThymolphthalein
The invention relates to a polymerization method capable of effectively controlling the phase transformation in a PPTA (poly-p-phenylene terephthamide) synthesis process. The polymerization method comprises the following steps of firstly dissolving LiCl in a solvent NMP (N-methyl-2-pyrrolidone) under the condition of nitrogen atmosphere protection, then adding comonomer p-phenylenediamine, terephthaloyl chloride and trace comonomer, adding acid absorbent pyridine, stirring so as to completely dissolve the acid absorbent pyridine, then adding PPD ((Para Phenylene Diamine), stirring so as to completely dissolve the PPD, then feeding condensing oil bath, maintaining the temperature of the condensing oil bath at -15 DEG C to -5 DEG C, adding TPC (Thymolphthalein Complexone) in three times, and stirring so as to fully react the TPC, thus obtaining modified PPTA resin, wherein the logarithmic viscosity number of the modified PPTA resin is in the range of 5.0-8.0, and the trace comonomer is a diamine monomer containing a flexible chain structure. The polymerization method is a method of effectively increasing the molecular weight by using the phase transformation; and according to the method, the phase transformation time of transforming a liquid phase into a solid phase can be delayed in the polymerization process, so that the molecular weight is effectively increased and the turbidity of a liquid crystal spinning solution is improved.
Owner:DONGHUA UNIV +1
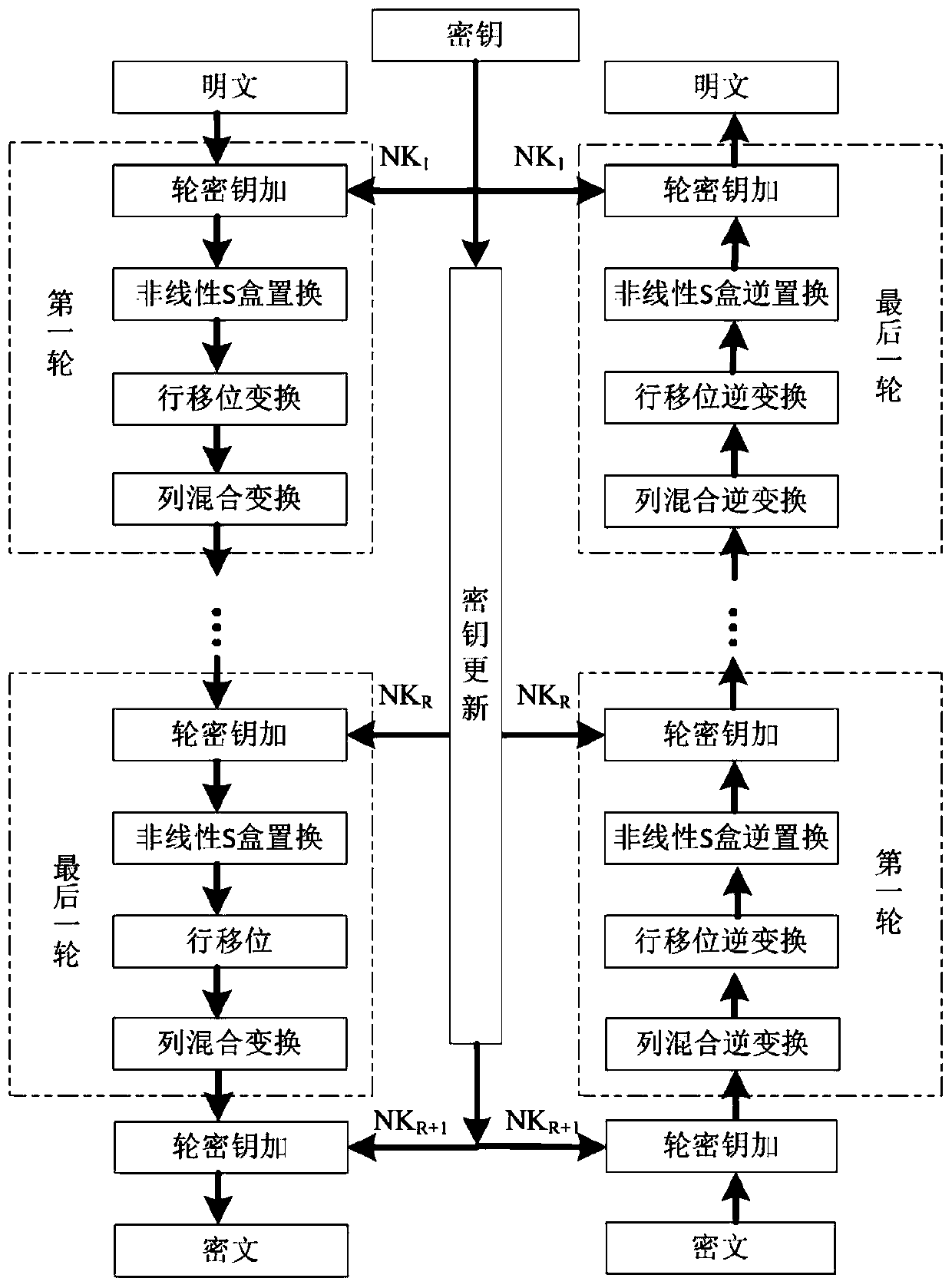
Lightweight block cipher algorithm Shadow implementation method and device and computer readable medium
ActiveCN110572255AIncrease confusionEffective against attackEncryption apparatus with shift registers/memoriesDigital data protectionComputer hardwareS-box
The invention discloses a lightweight block cipher algorithm Shadow implementation method and device based on an SPN structure and a computer readable medium. The method comprises the following steps:obtaining a 64-bit plaintext to be encrypted, and determining an iteration round number R according to the number of key bits; in the first round of operation to the Rth round of operation, enablingeach round of operation to be sequentially subjected to round key addition operation, nonlinear S-box replacement operation, row displacement operation and linear column hybrid operation, and updatinga key; taking the data obtained after the linear column hybrid operation as the to-be-encrypted data of the next round of operation, and taking the updated key as the key of the next round of operation; and performing round key addition operation on the data after the Rth round of operation and the key, and outputting a ciphertext. On the basis that part of cryptographic indexes of the S box arenot affected by affine transformation, a composite affine mathematical method is adopted, the pseudo-random key related S box is constructed on a finite field GF (24), meanwhile, a column hybrid matrix is constructed according to the Schmidt matrix orthogonalization principle, and attacks can be effectively resisted.
Owner:HENGYANG NORMAL UNIV
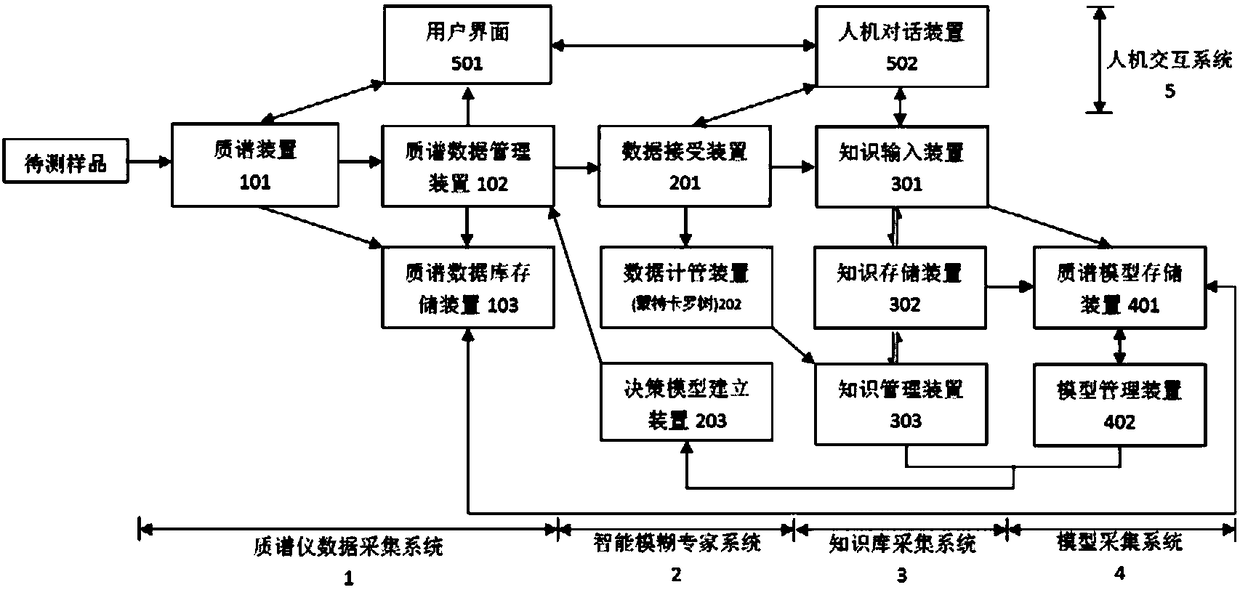
Mass spectrum system used for detecting biomolecules
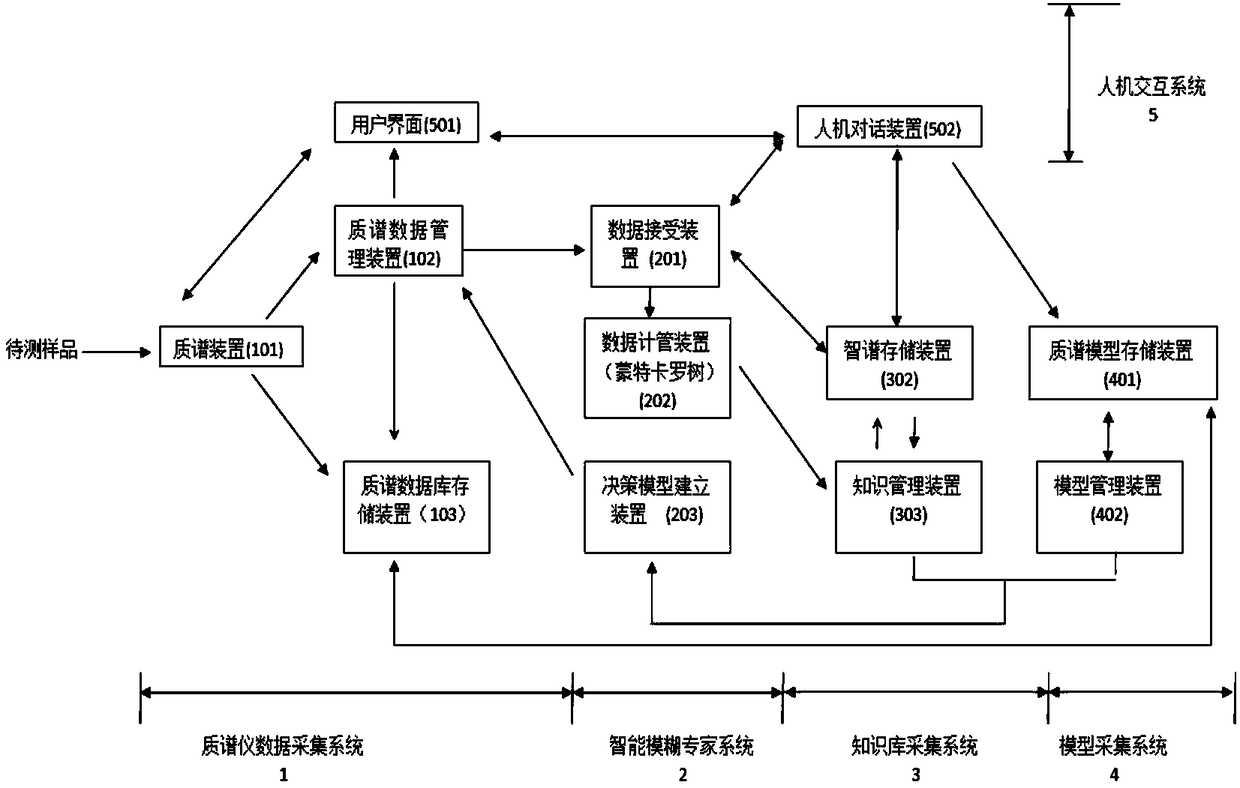
ActiveCN108363908AImprove stabilityUnique test resultSequence analysisSpecial data processing applicationsPersonalizationData collecting
The invention provides a mass spectrum system used for detecting biomolecules. The system comprises a mass spectrometer data collecting system, an intelligent fuzzy expert system, a knowledge base collecting system and a model collecting system. The mass spectrometer data collecting system is used for detecting mass spectrum data of a sample; the intelligent fuzzy expert system can carry out intelligent analysis on the mass spectrometer data; the knowledge base collecting system can store and manage related knowledge of mass spectrum detection in advance through a cloud center; the model collecting system is used for sending the known mass spectrum model data to a knowledge management system and a mass spectrum model storage device according to instructions. The system is supported by cloud center calculation, intelligent learning and storage are performed through the knowledge base collecting system, the intelligent analysis is carried out on the mass spectrum data through the intelligent fuzzy expert system, and simulation with lower cost is carried out to generate a large amount of training data; the system is conductive to analyzing large samples, is suitable for nonprofessional operations, achieves monitoring personal health information in real time, and meets personalized medical service requirements.
Owner:BIOYONG TECH
Forging forming method of high-toughness titanium ring
InactiveCN107803454AIncrease confusionImprove high temperature strengthForging press drivesMetal rollingStable elementForging
The invention discloses a forging forming method of a high-toughness titanium ring. The forging forming method of the high-toughness titanium ring is carried out according to the following steps that1, a titanium alloy is blanked into a bar; 2, a titanium alloy pre-rolling ring blank is obtained; 3, the ring blank is subjected to rolling forming; 4, double annealing is conducted; 5, coarse grainsof the ring blank are broken; 6, the coarse broken grains are refined and uniformized; 7, the grains at a beta area of a forging structure are refined; 8, constant-temperature correction is conducted; and 9, low-temperature heat treatment is conducted, and air cooling is conducted to the indoor temperature. The forging forming method is simple, clear and convenient to apply; the content of the alpha stable is increased appropriately, and the content of the beta stable element is decreased appropriately, so that the number of alpha strips in the titanium alloy is increased; and therefore, after subsequent forging, a mesh basket structure with the high confusion degree can be obtained for improving the high-temperature strength of a forging, and meanwhile, the high-temperature tensile strength of the forging is improved.
Owner:陕西海恩得工贸股份有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com