Software protection method based on intermediate result compiling
A software protection, intermediate result technology, applied in the direction of program/content distribution protection, etc., can solve problems such as program exposure, few types of packers, and limited language processing capabilities, to avoid errors, prevent illegal cracking and analysis, and improve confusion. Effects and Obfuscation Quality Effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
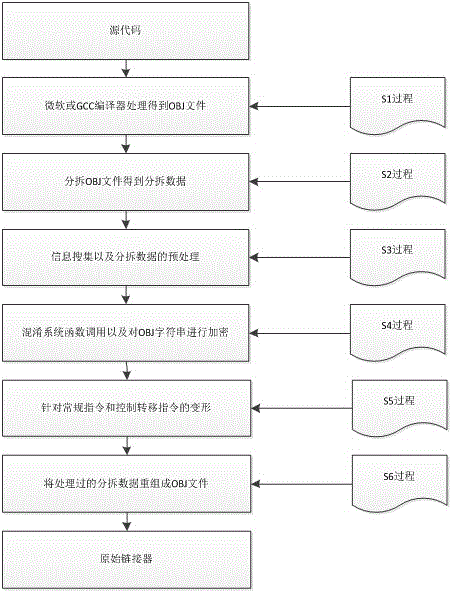
[0066] The present invention is aimed at compiling the software confusion protection method of intermediate result OBJ file, comprises the following steps:
[0067] Step S1 may directly use a Microsoft compiler or a GCC compiler to compile the source code.
[0068] Step S2 mainly includes some basic analysis and processing work, and splits the OBJ file according to a certain data structure. The later processing is carried out for this part of split data, therefore, this step is the first step to realize the main function.
[0069] The processing process of the compiler provided by Microsoft or GCC is similar. The generation of intermediate files is carried out according to the COFF standard, and there are very few differences between them. These differences can be processed by some compatible modules to ensure later analysis and confusion. able to execute normally. This method is only applicable to C / C++ language, you can find the official documents provided by Microsoft and...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com