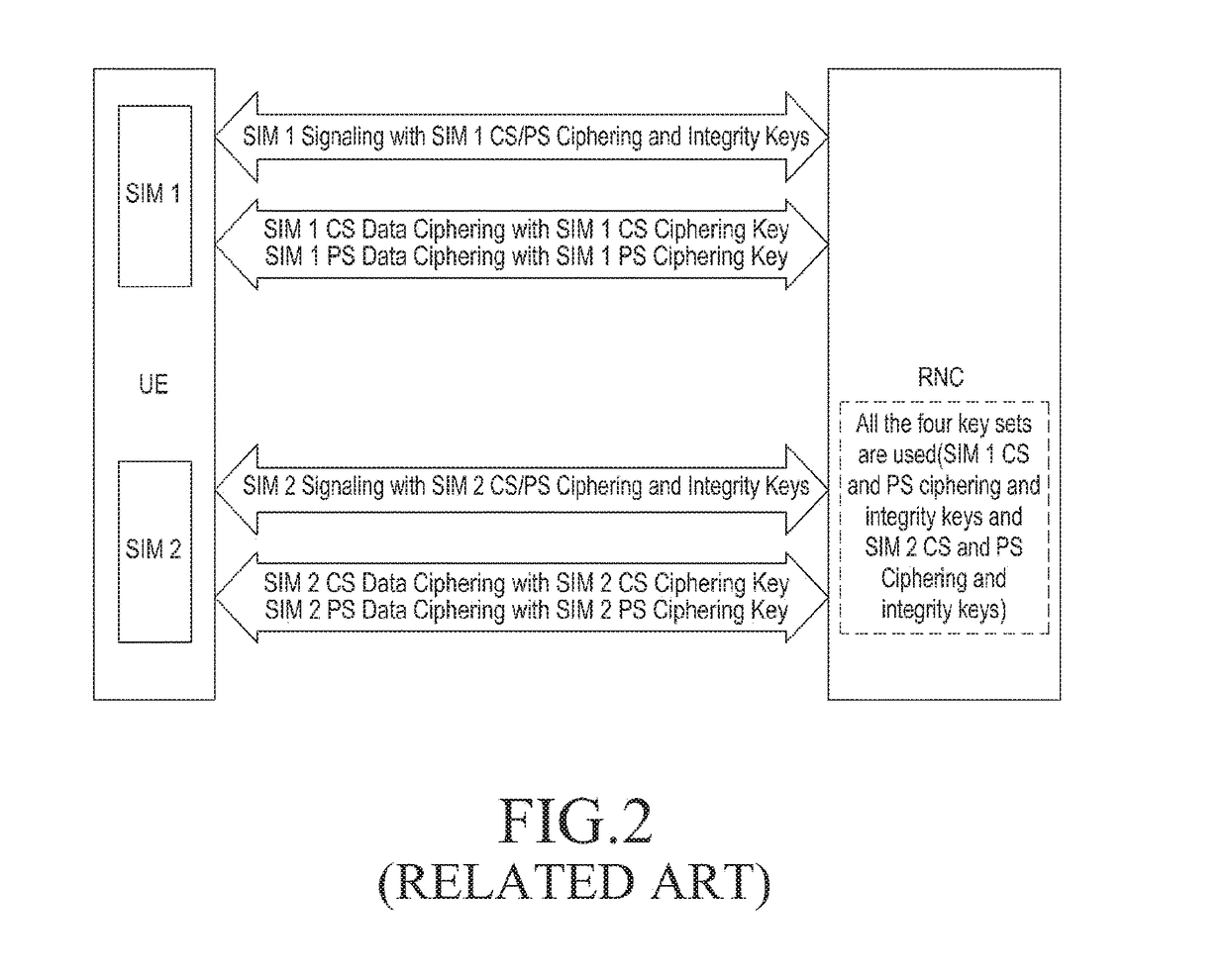
Patents
Literature
290 results about "User identity module" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
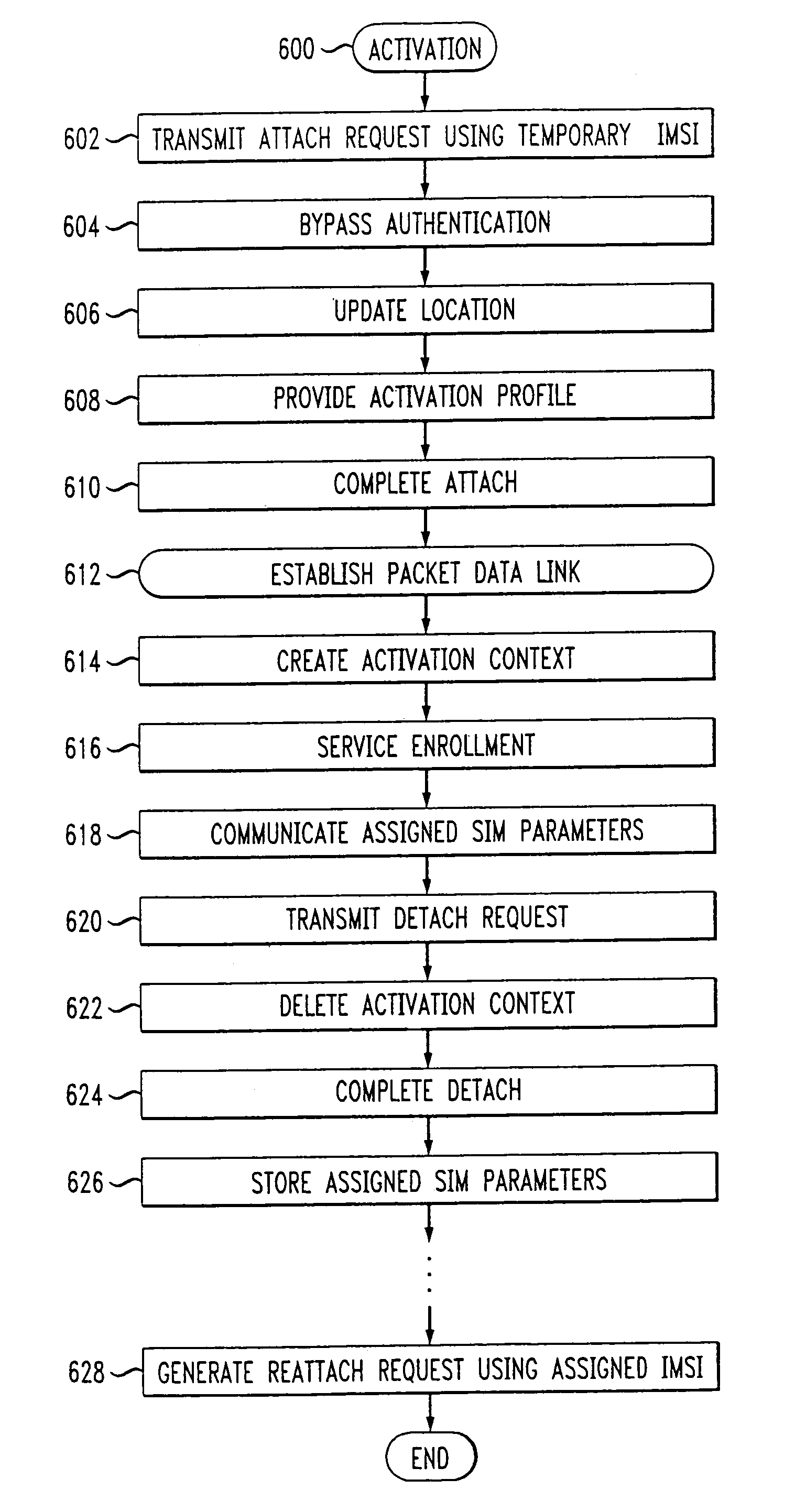
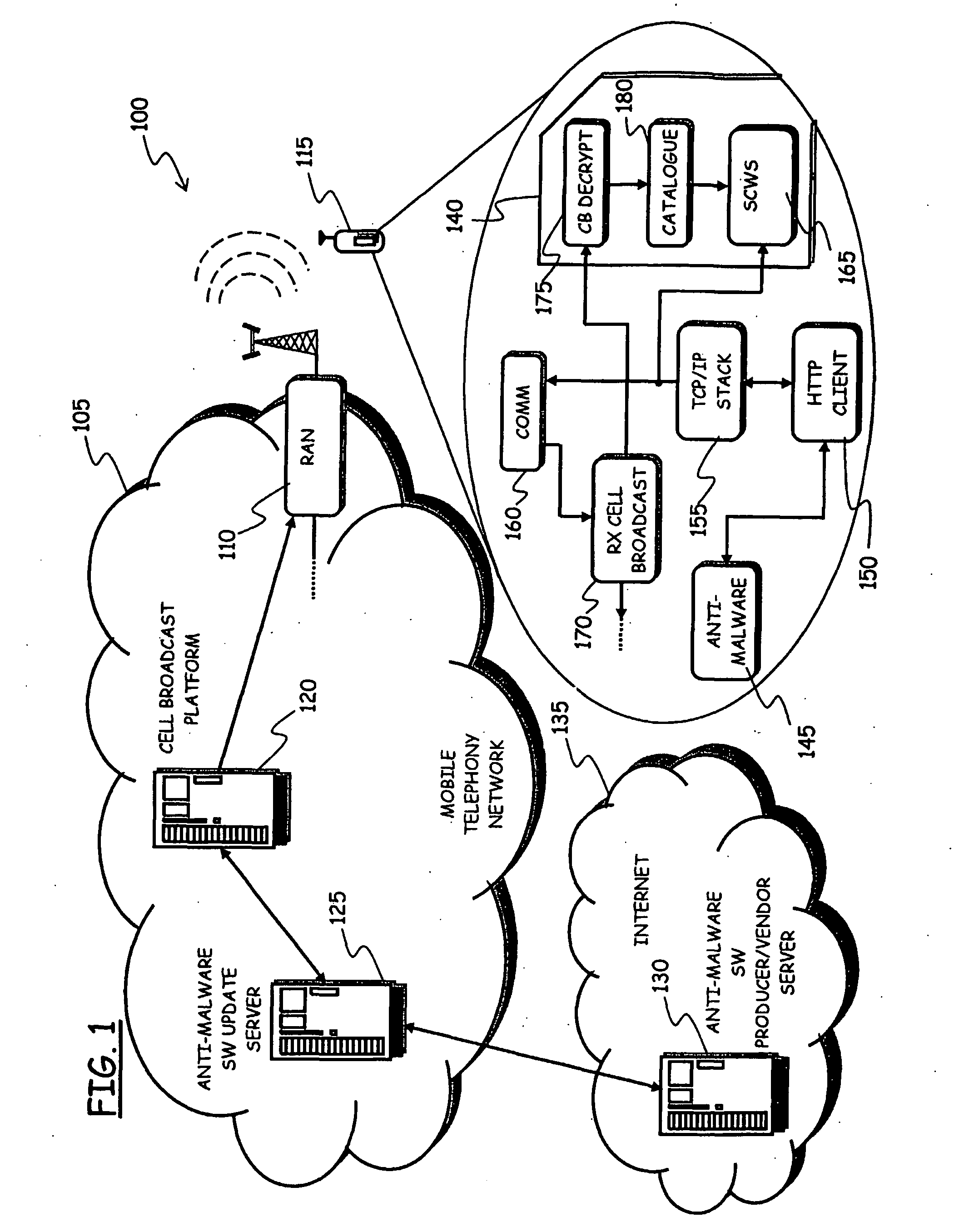
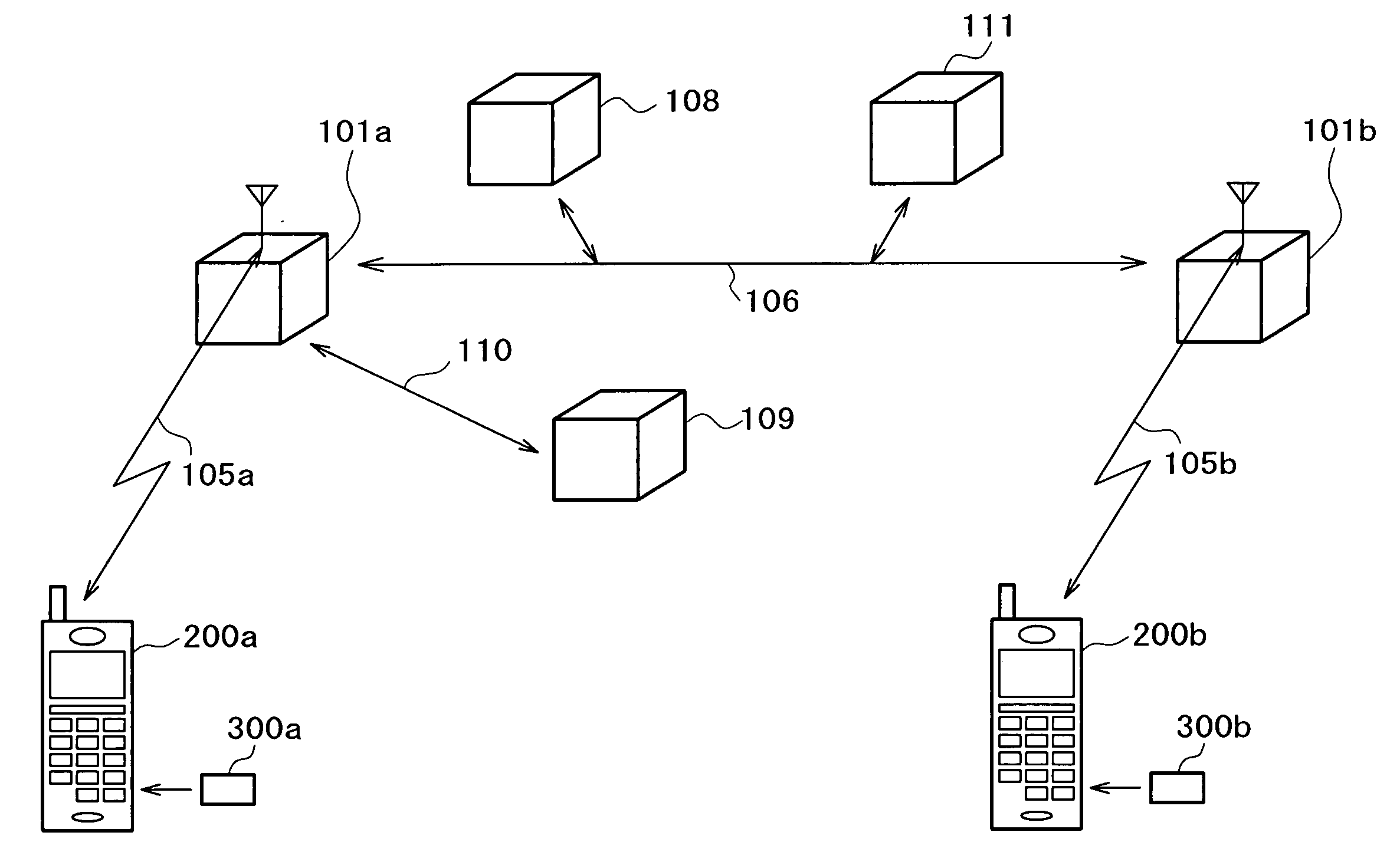
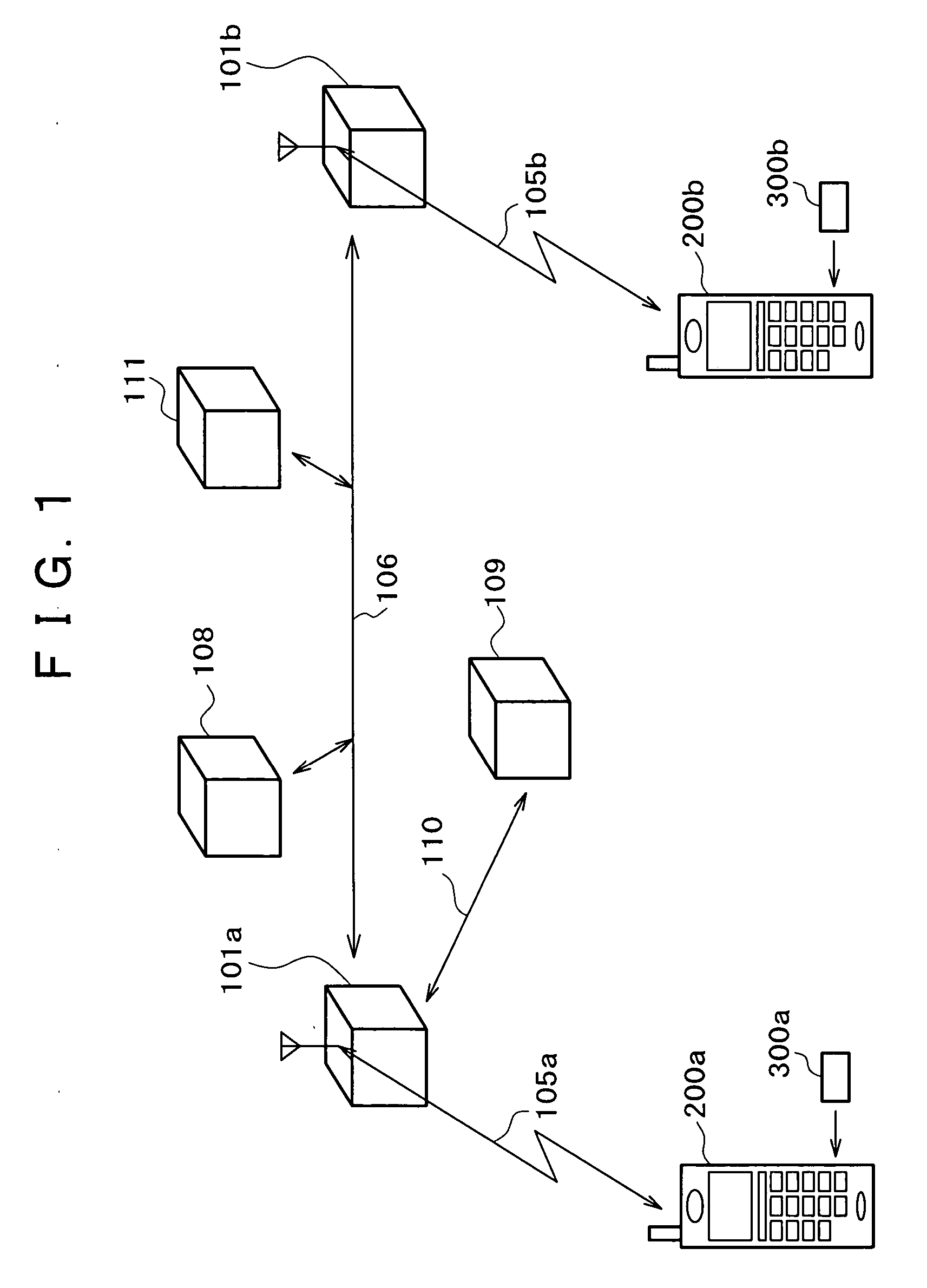
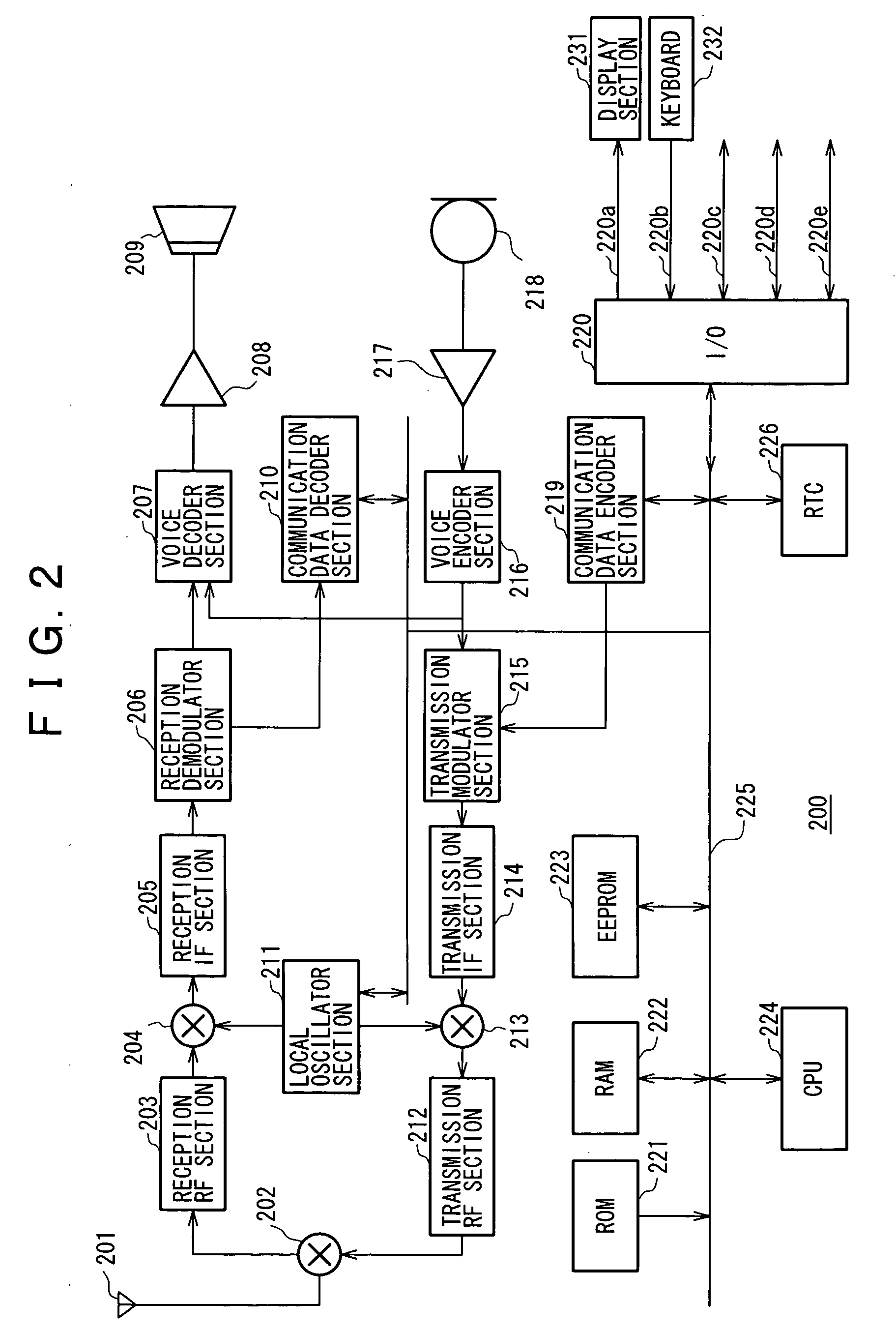
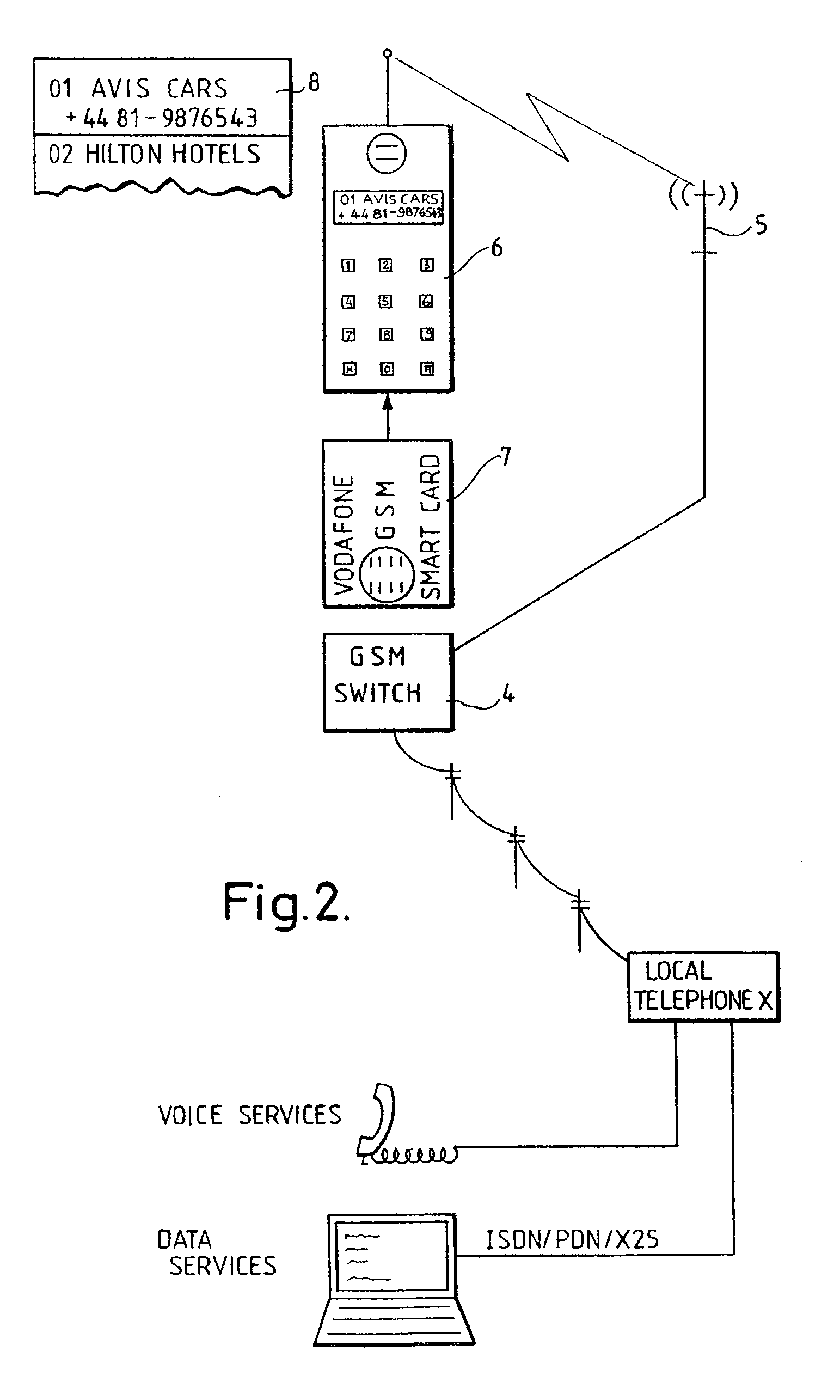
Activation and remote modification of wireless services in a packet network context
InactiveUS7266371B1The process is convenient and fastConvenient and quick mobile device activationRadio/inductive link selection arrangementsSubstation equipmentTerms of serviceThird generation
A third generation (3G) mobile communication system supports an over-the-air activation scheme utilizing a wireless packet data protocol. A subscriber identity module (SIM) is preloaded with temporary operating parameters such as a temporary international mobile subscriber identity (IMSI) that is used for initial access to a network. Once a packet data protocol communication link is established between the mobile device and a network support node, the user may remotely subscribe to a number of service terms using the mobile device. In addition, an activation procedure is carried out to assign permanent operating parameters, e.g., a permanent IMSI, to the SIM. After activation, the user can remotely modify existing terms or remotely enroll in additional service features via a wireless IP link between the mobile device and a network support node.
Owner:AT&T WIRELESS SERVICES
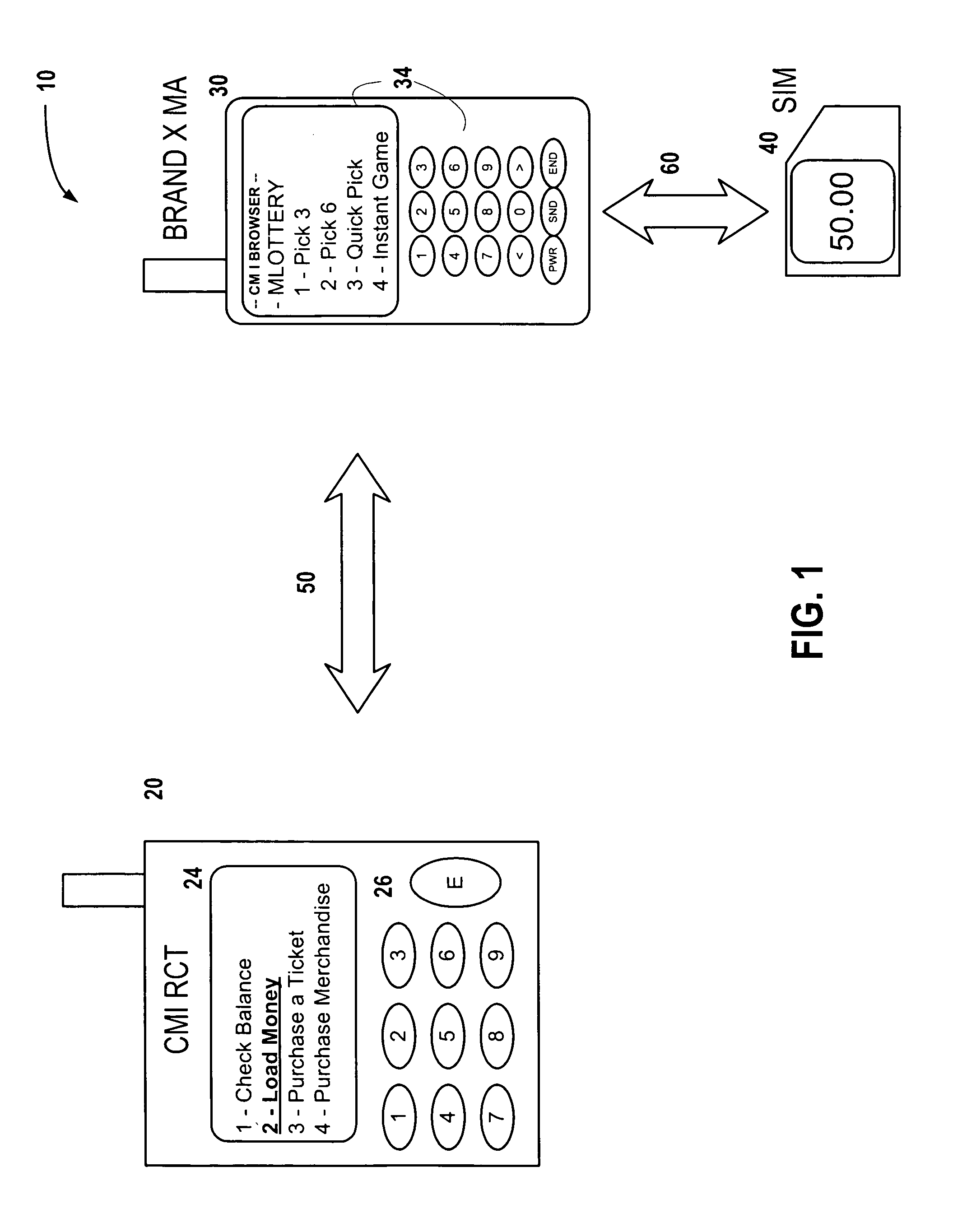
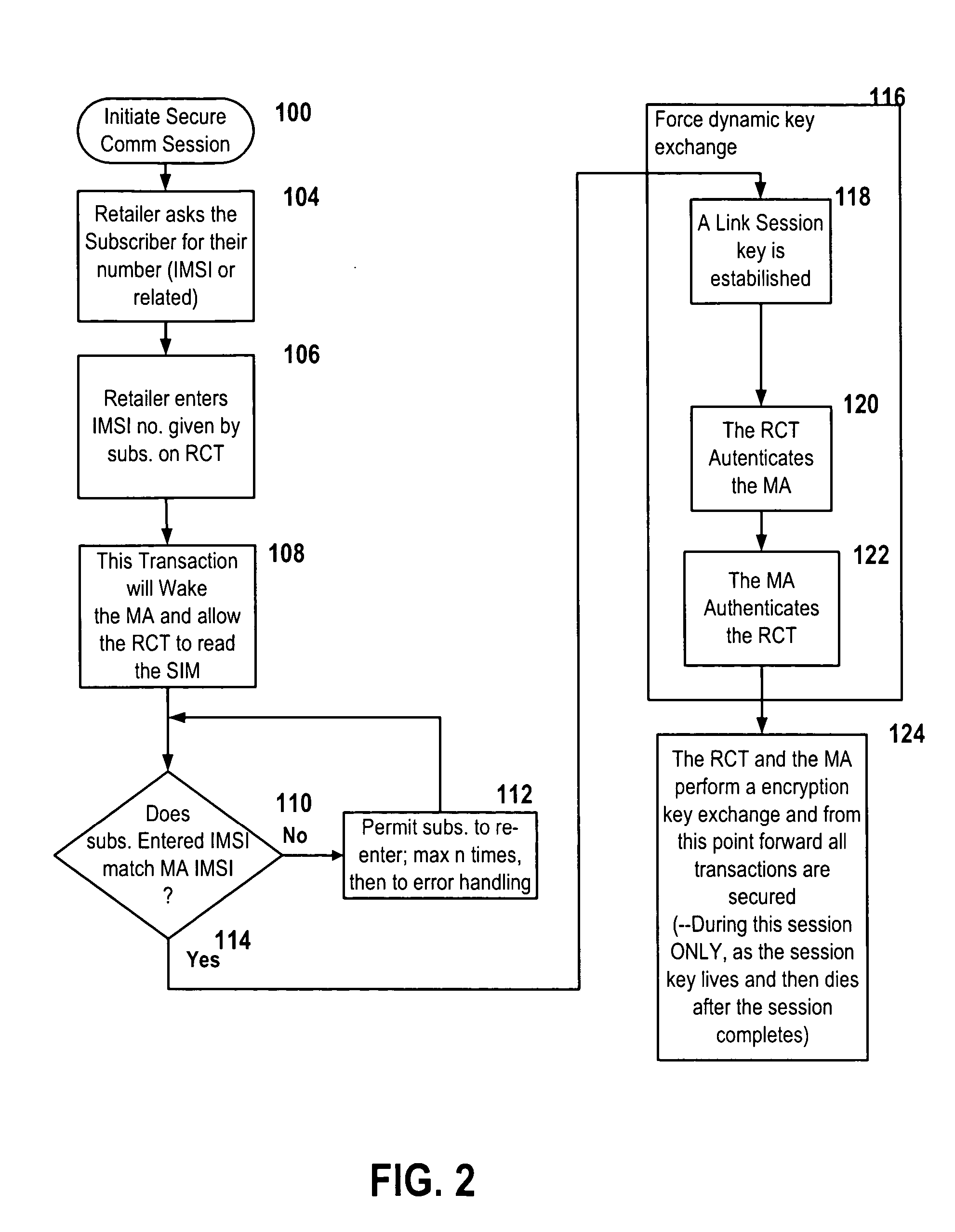
Mobile lottery, gaming and wagering system and method
InactiveUS20050181875A1Credit registering devices actuationTelephonic communicationPagerElectronic cash
An apparatus or method to allow the secure downloading of an operating system, file management system and or state machine to a Miniature Smart Card (MSC) such as a Subscriber Identity Module (SIM), Universal Subscriber Identity Module (USIM), Removable User Identity Module (RUIM) or Universal Integrated Chip Card (UICC) in a mobile appliance (MA), such as but not limited to a mobile phone, personal digital assistant (PDA), pager or a proprietary device. This would in turn allow an E-purse applet as well as Lottery, Wagering and Gaming applets to be downloaded to the same Miniature Smart Card (MSC) and further allow the downloading of e-cash to be used to remotely play the Lottery, Wagering or Gaming applets as well as make retail purchases.
Owner:COIN MECHANISMS
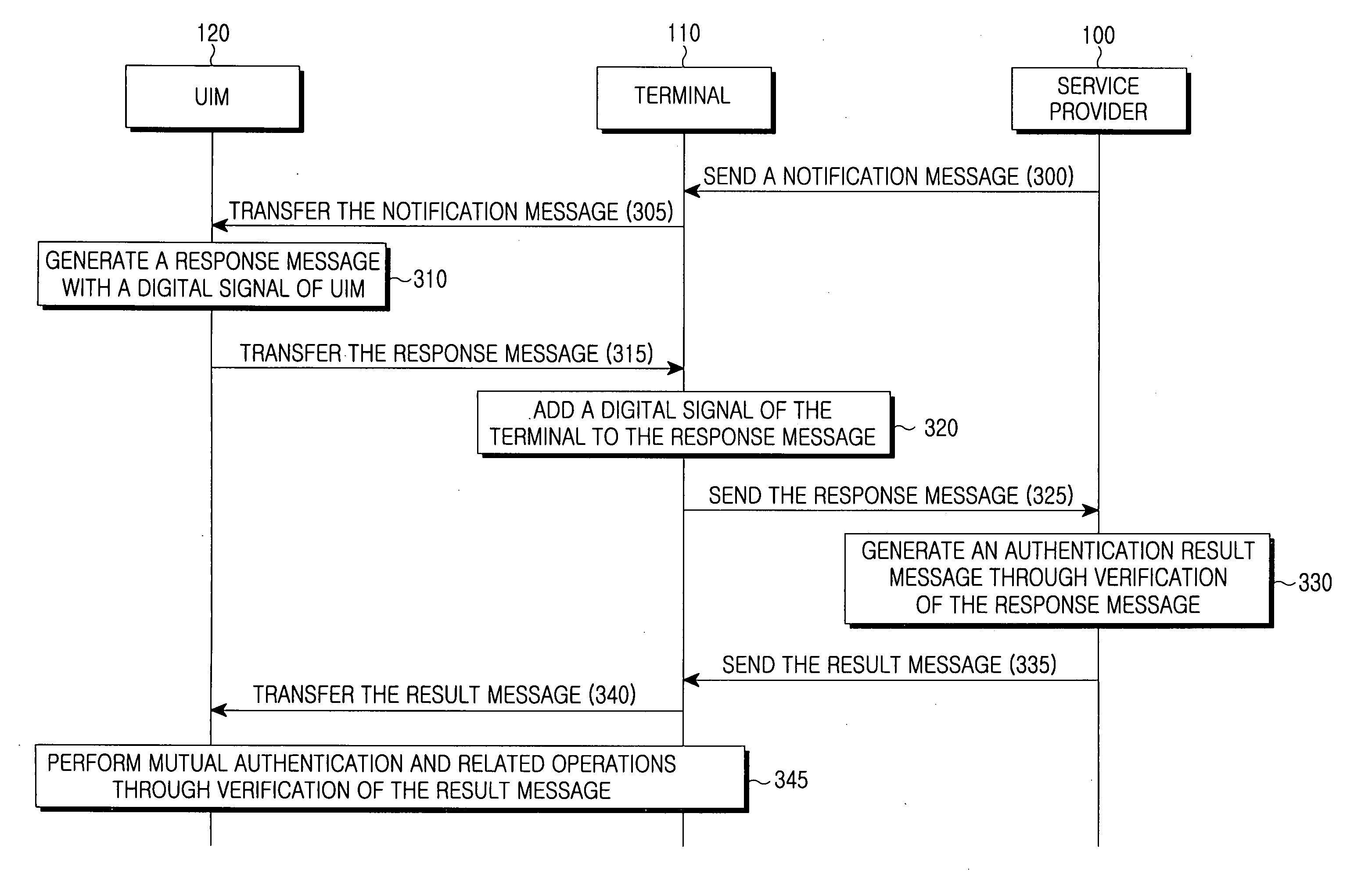
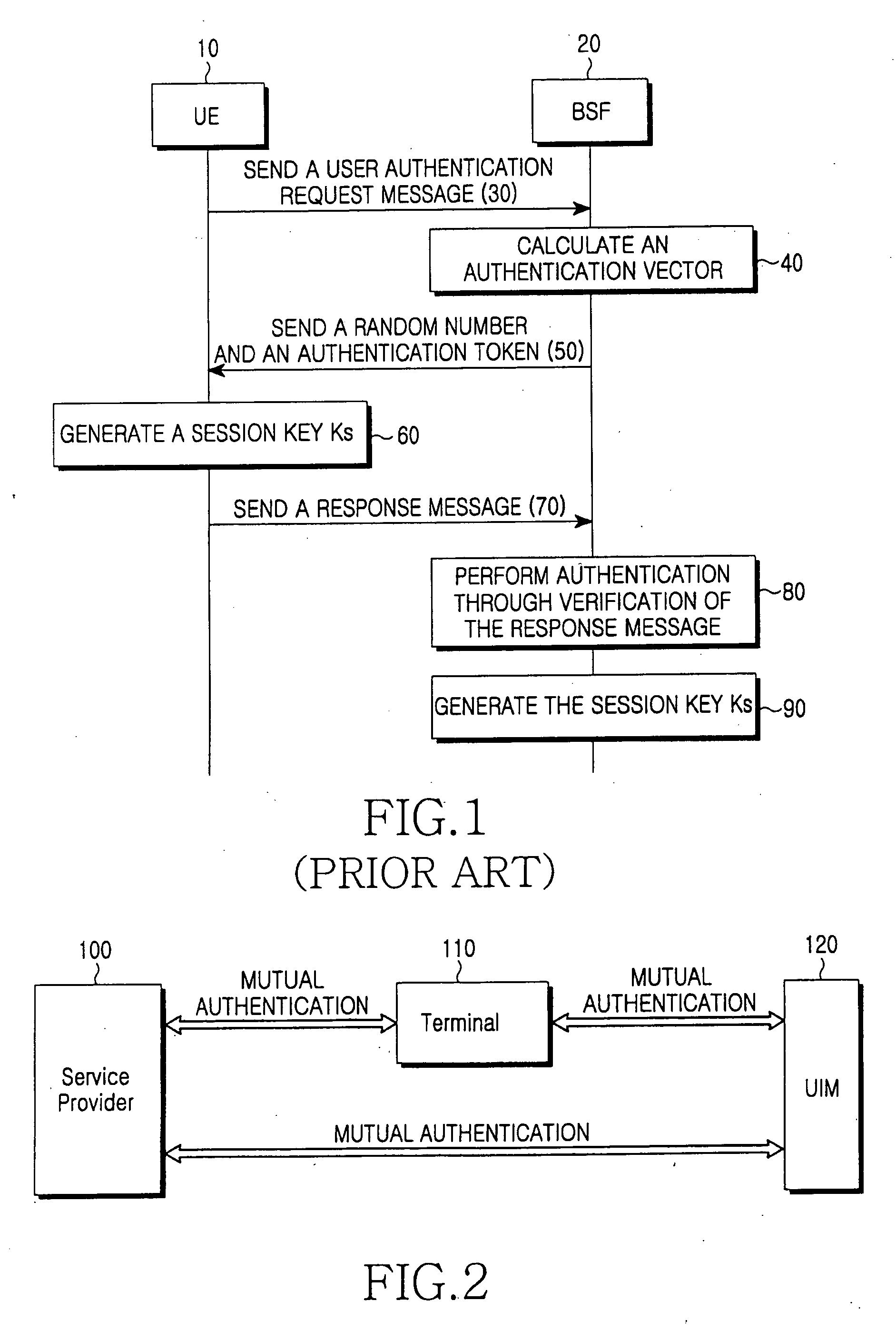
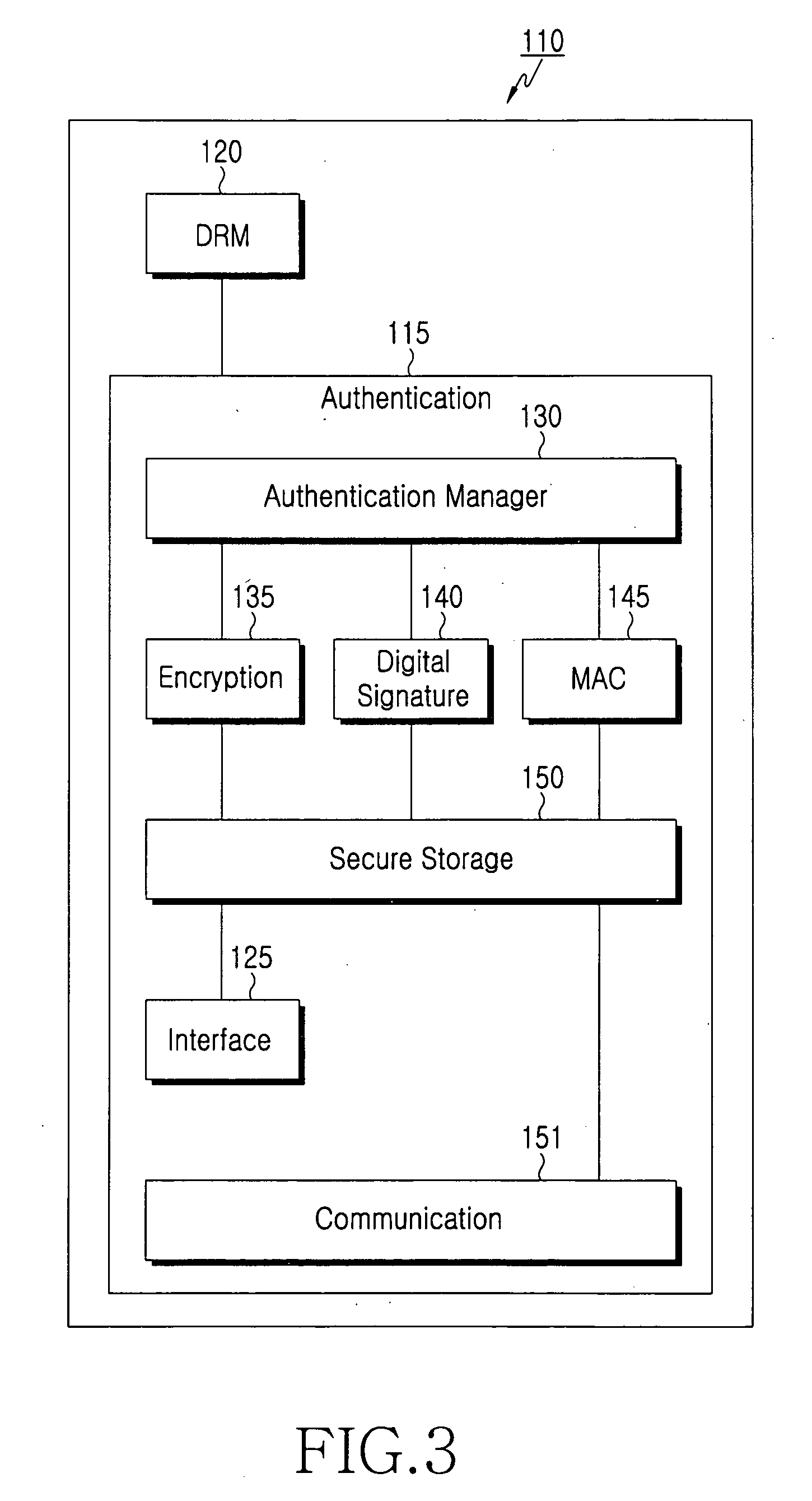
Method for inclusive authentication and management of service provider, terminal and user identity module, and system and terminal device using the method
ActiveUS20060281442A1Unauthorised/fraudulent call preventionEavesdropping prevention circuitsPublic key authenticationNetworked system
Disclosed are a method and a system for mutual inclusive authentication between a service provider, a terminal and a user identity module. The authentication system is configured in a structure that can interact with a public key infrastructure of the current network security environment and can be independently used in a specific network system. The inclusive authentication method is divided into public key authentication and symmetric key authentication. Mutual authentication can be made between a service provider, a terminal and a user identity module using any of the two authentication schemes. Then a user can access content on any terminal device using the content license based on the user's identity.
Owner:SAMSUNG ELECTRONICS CO LTD
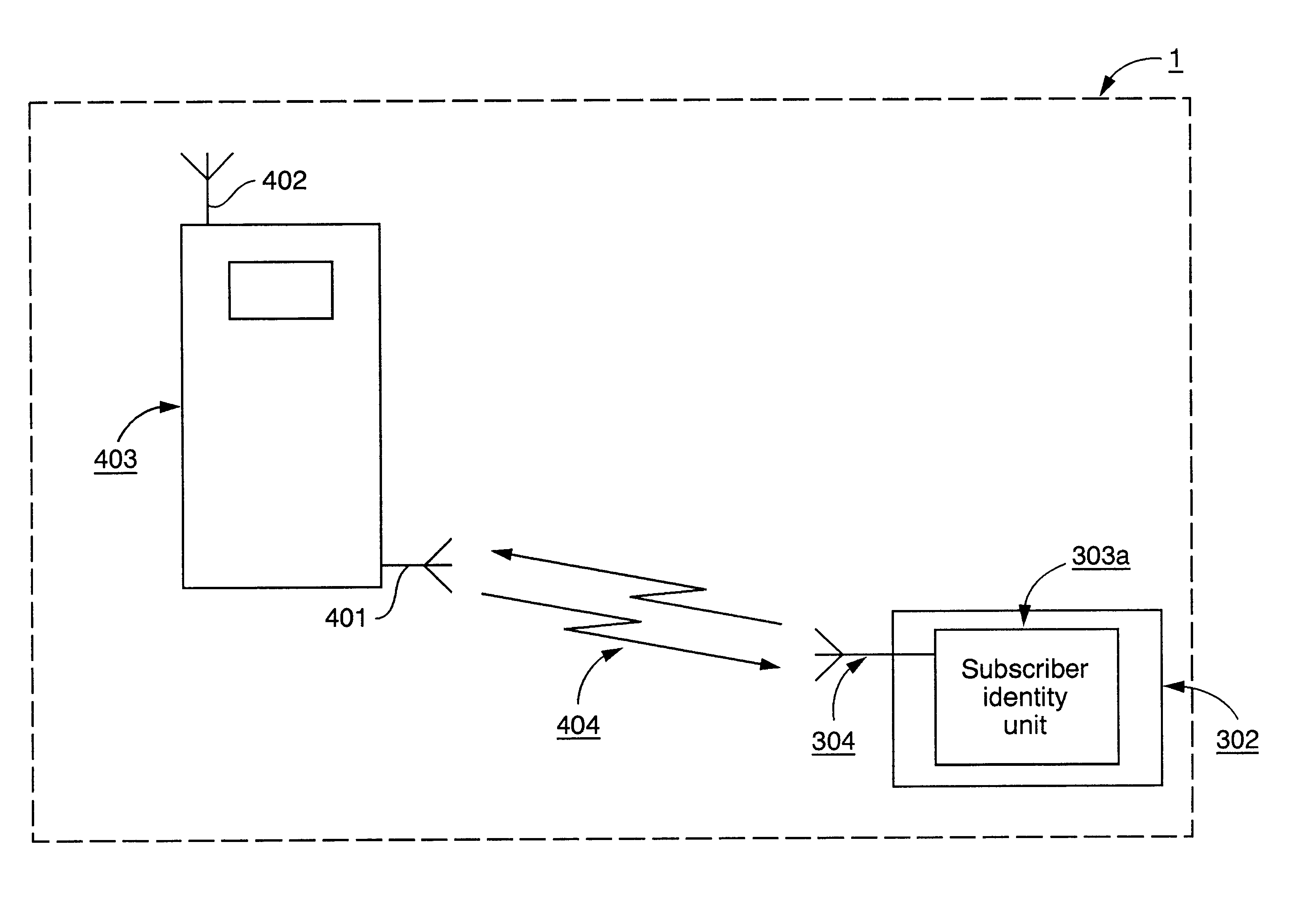
Method and arrangement for communicating subscriber related data in a wireless communications system
InactiveUS6615057B1Easy to changeConnection managementRadio/inductive link selection arrangementsTelecommunications linkCommunications system
The present invention relates to an arrangement for communication of subscriber identity module related data in a wireless communication system. The arrangement comprises a wireless communication terminal with a subscriber identity unit which includes a subscriber identity module, to which a subscriber identity is assigned. The present invention also relates to a method for communication of subscriber identity module related data in a wireless communication system for implementation in a wireless communication terminal having a subscriber identity unit. The subscriber identity unit is arranged to communicate the subscriber identity module related data, such as, for example the subscriber identity, to the terminal over a local wireless communication link. The arrangement according to the present invention makes it possible to separate the subscriber identity unit from the terminal while the terminal is communicating using the wireless system.
Owner:TELEFON AB LM ERICSSON (PUBL)
Apparatus and methods associated with open market handsets
ActiveUS20090081996A1Accounting/billing servicesSpecial service for subscribersService provisionNetwork addressing
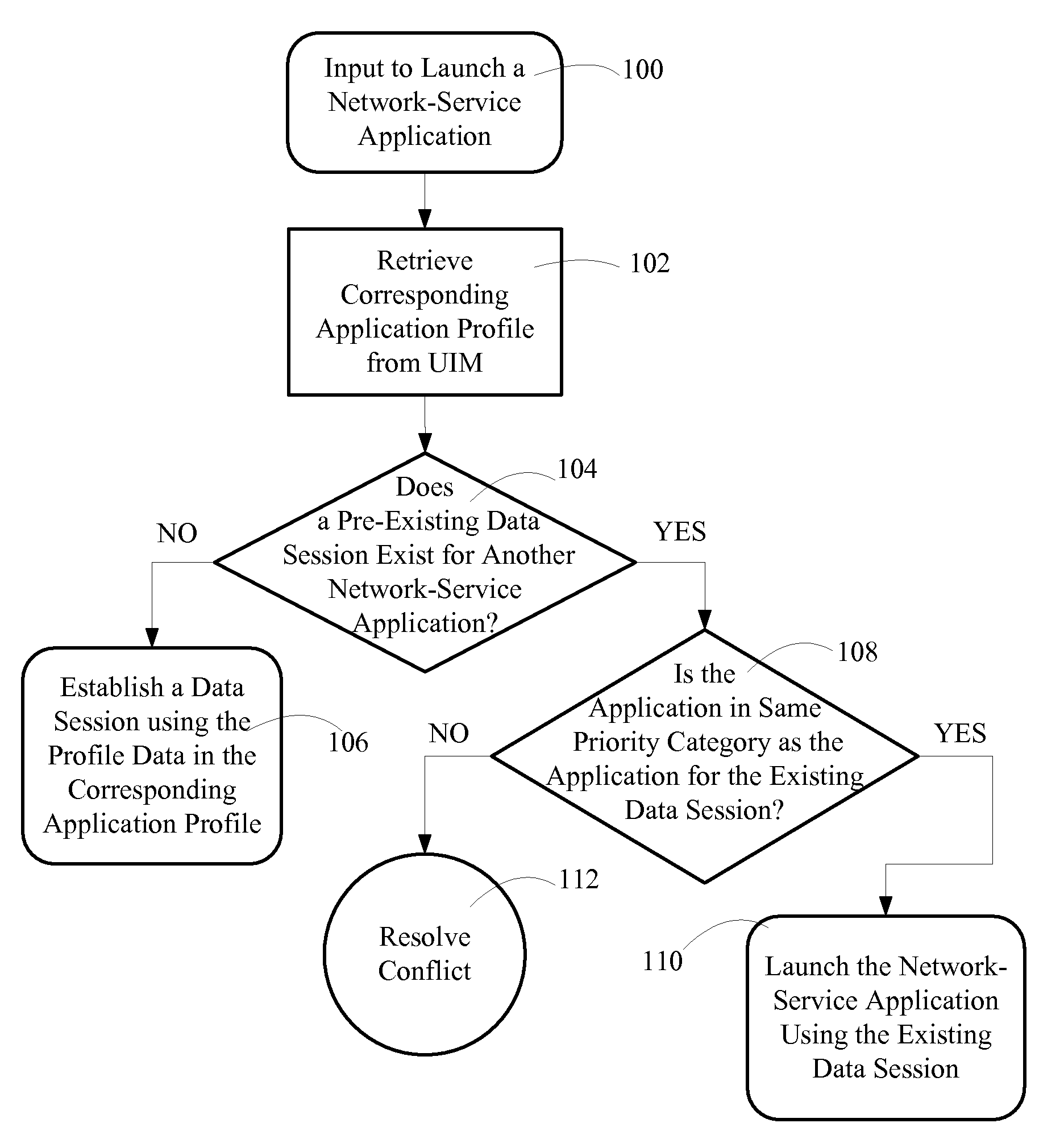
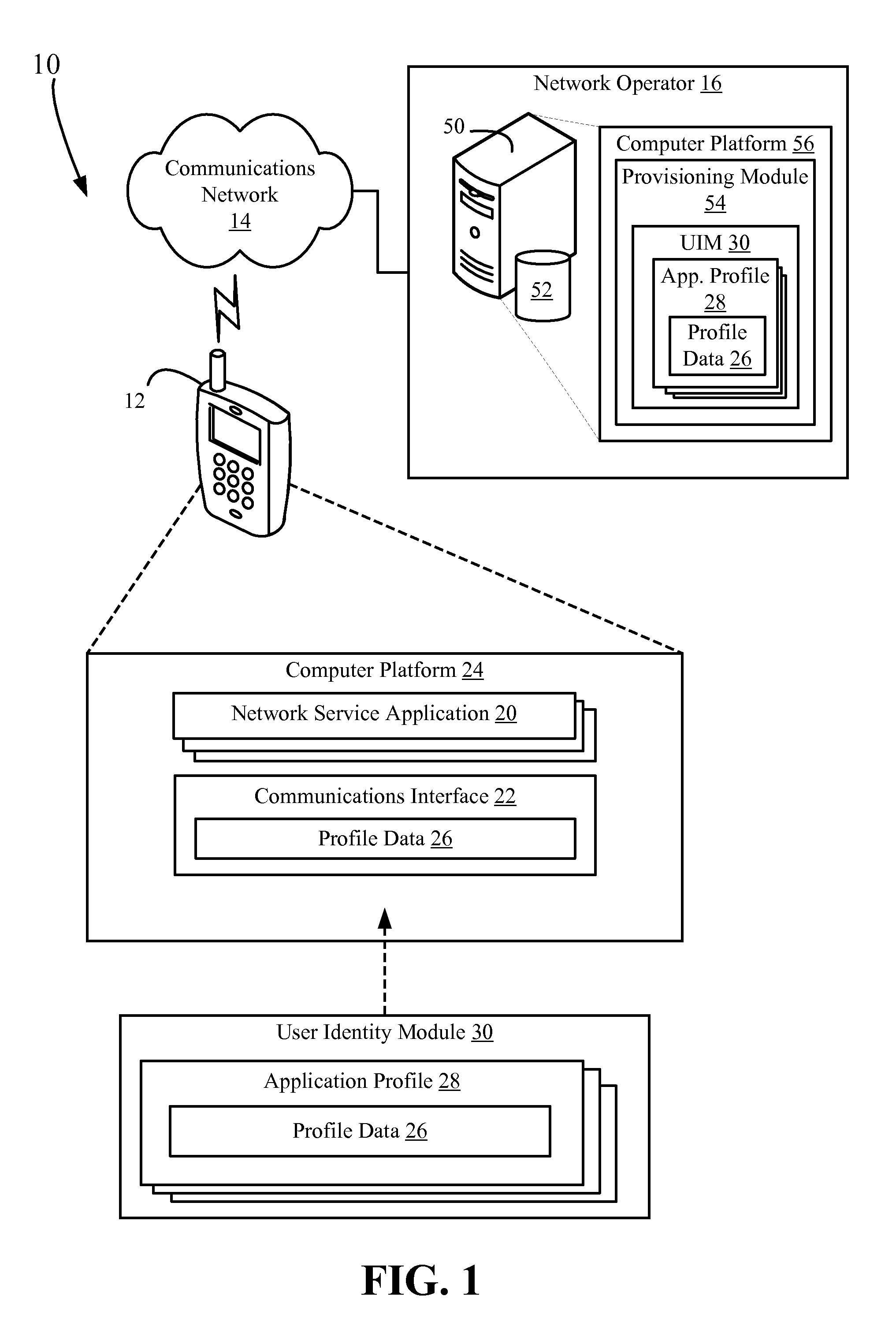
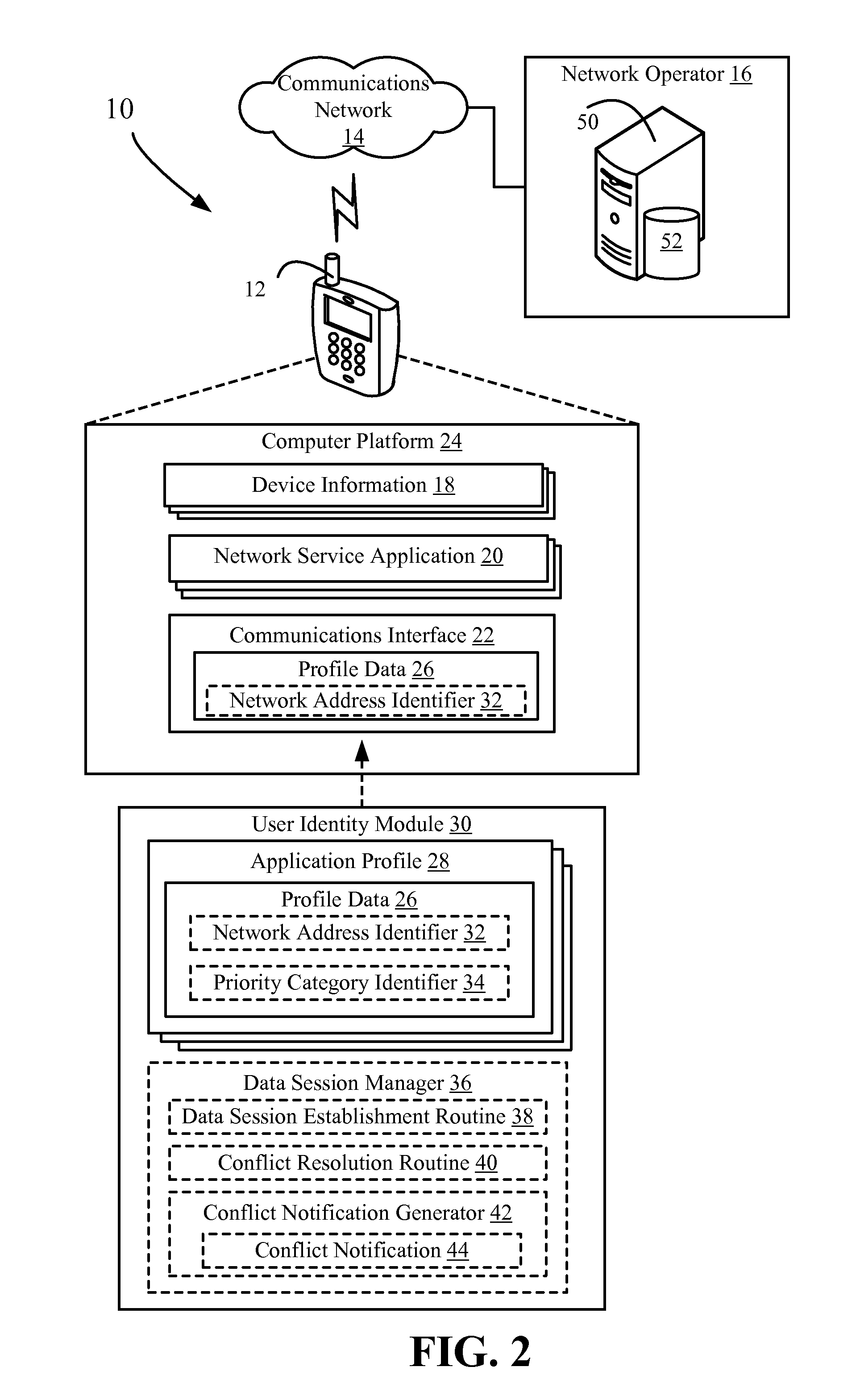
communication device and dynamic source determination of provisioning information on a wireless communication device are disclosed. User Identity Modules (UIMs) are provisioned such that network-service applications resident on the wireless device are associated with a corresponding application profile within the UIM. Each network-service application has a corresponding network address identifier defined within the user profile. The network address associated with the identifier is used to establish a data session for the corresponding network service application. By providing for application-specific network addresses, service providers and / or network operators can differentiate between what services a user is accessing during a data session. In addition, the UIMs may be provisioned with priority category identifiers that allow the associated network-service application to be prioritized for data session establishment.
Owner:QUALCOMM INC
Method, system, and apparatus for providing wireless identification to standard telephone
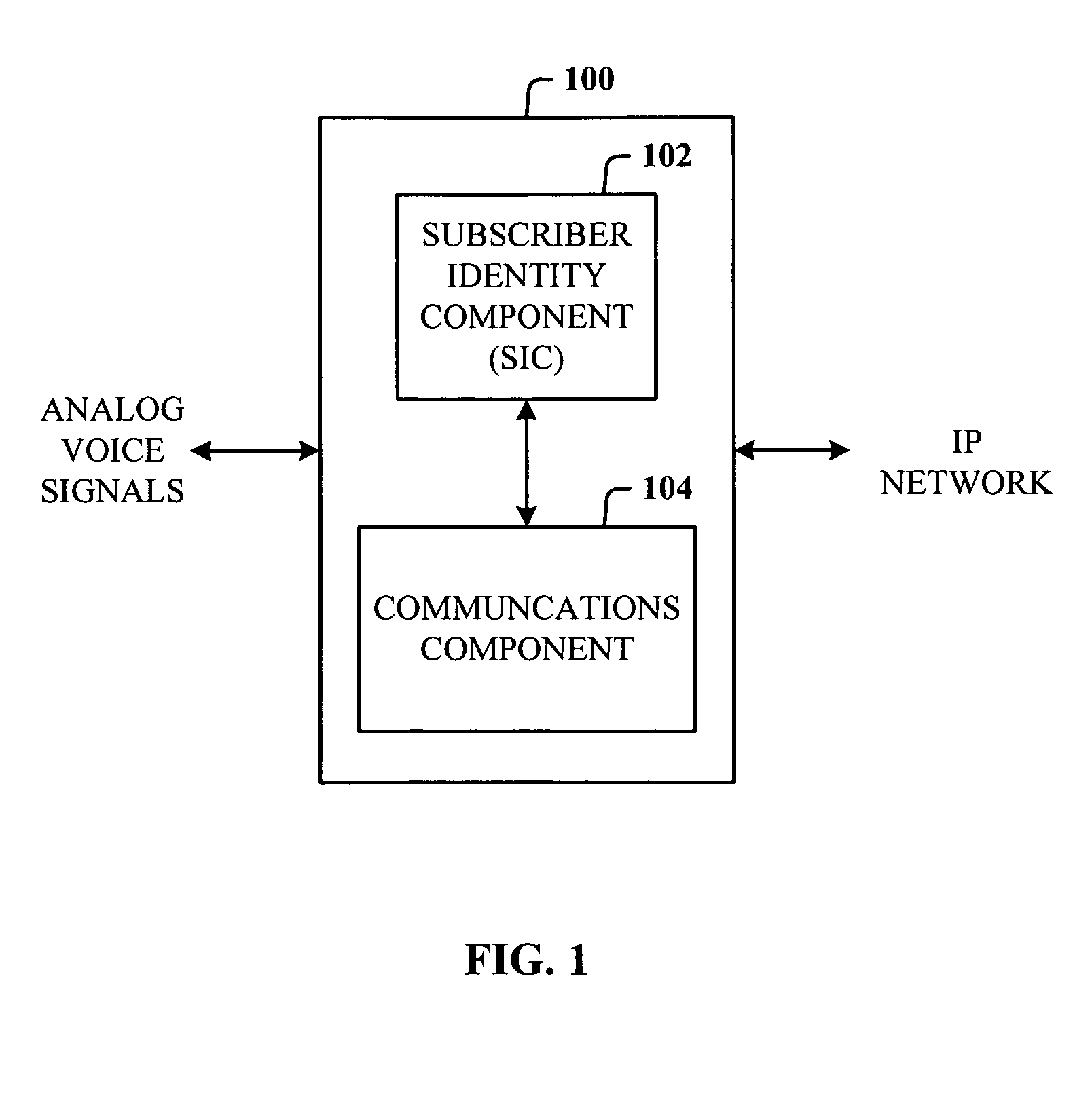
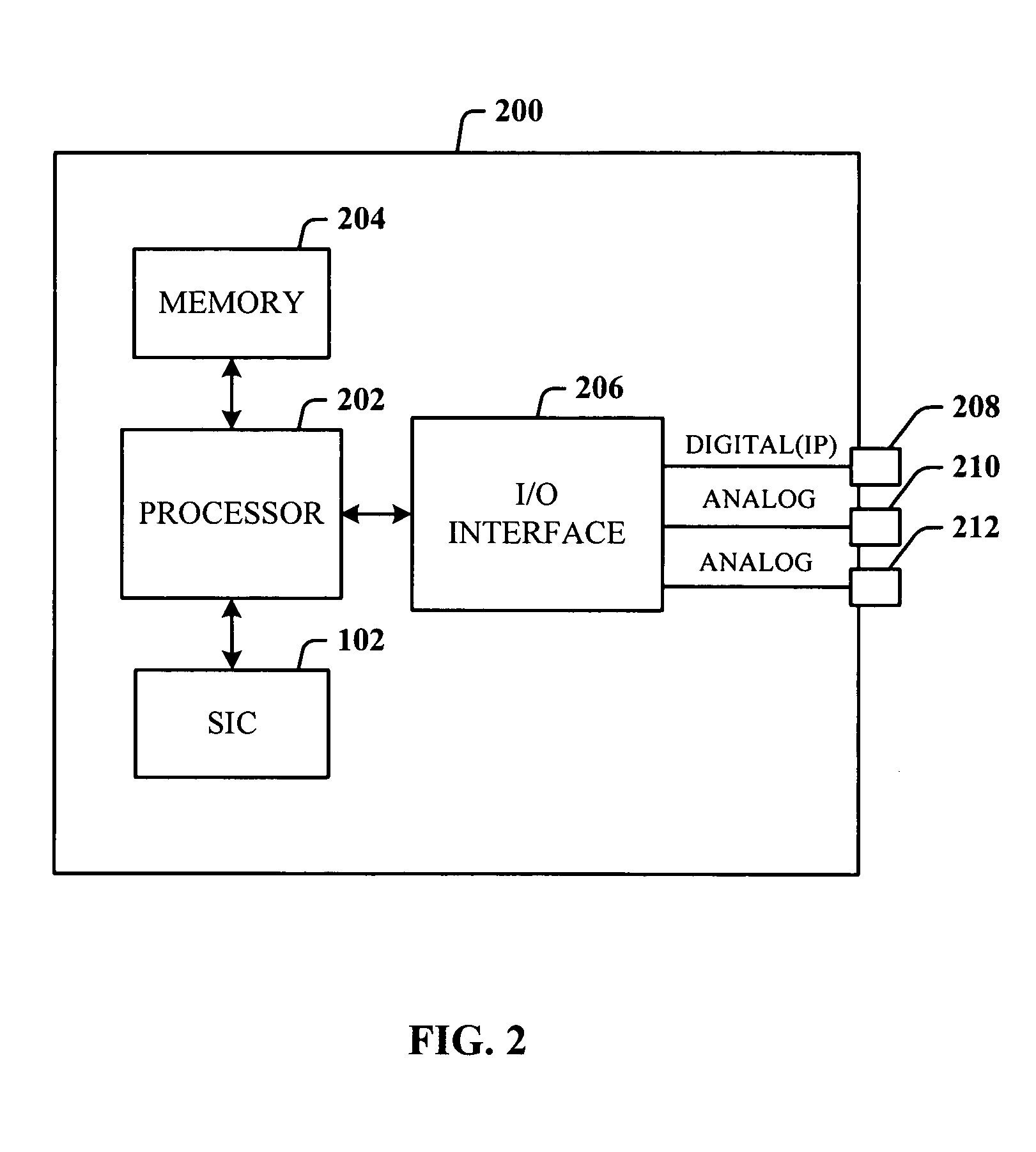
ActiveUS20050105512A1Reduce and eliminate needAuthentication is convenientSubstations coupling interface circuitsUnauthorised/fraudulent call preventionService userDigital signal
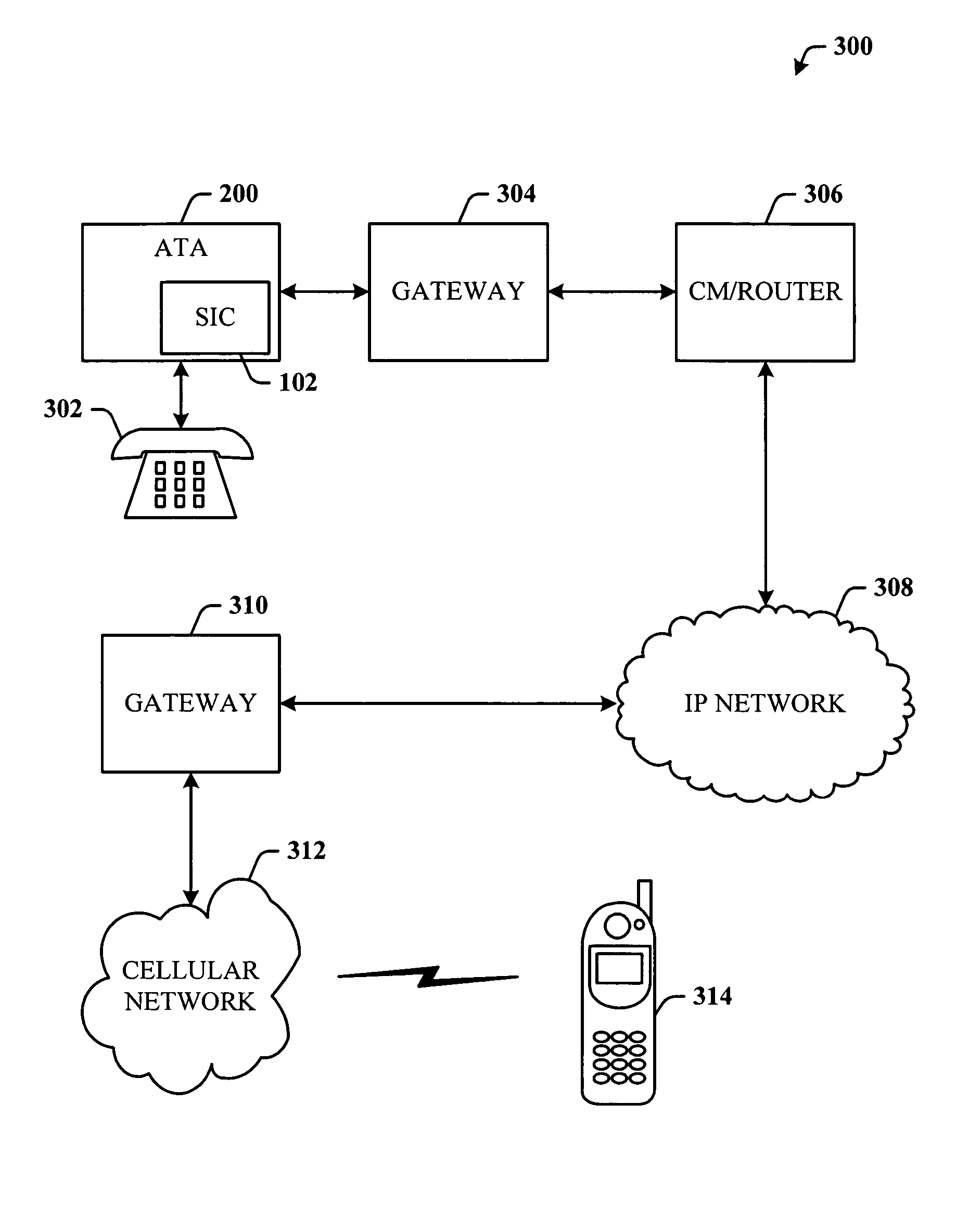
An analog telephone adapter (ATA) having a subscriber identity component in the format of a Subscriber Identity Module (SIM) that couples a telephone to a cellular network via Voice over Internet Protocol (VoIP), thereby allowing a cellular service provider to provide an alternative communication service for the home or business. Instead of using the plain old telephone service, a subscriber can plug their analog telephone into the SIM-enabled ATA (SIM-ATA) and receive telephone service from a cellular service provider, eliminating or reducing the need for a traditional Local Exchange Carrier. The SIM-ATA converts signals from analog to digital, and vice-versa. Once the analog telephone signal has been converted to digital, an IP-based protocol (e.g., VoIP) can be used to transmit the telephone call over a digital network. The cellular service provider can then track usage and bill the subscriber accordingly.
Owner:CHANYU HLDG
Providing multimedia system security to removable user identity modules
InactiveUS20070043947A1Well formedRandom number generatorsUser identity/authority verificationCommunications systemProtocol for Carrying Authentication for Network Access
The present invention provides a method of authenticating a user identity module to an entry node of a wireless communication system. The method may include receiving a first challenge formed according to a first security protocol from the entry node and forming, according to a second security protocol different from the first security protocol, a second challenge based on the first challenge. The method may also include providing the second challenge to the user identity module.
Owner:LUCENT TECH INC
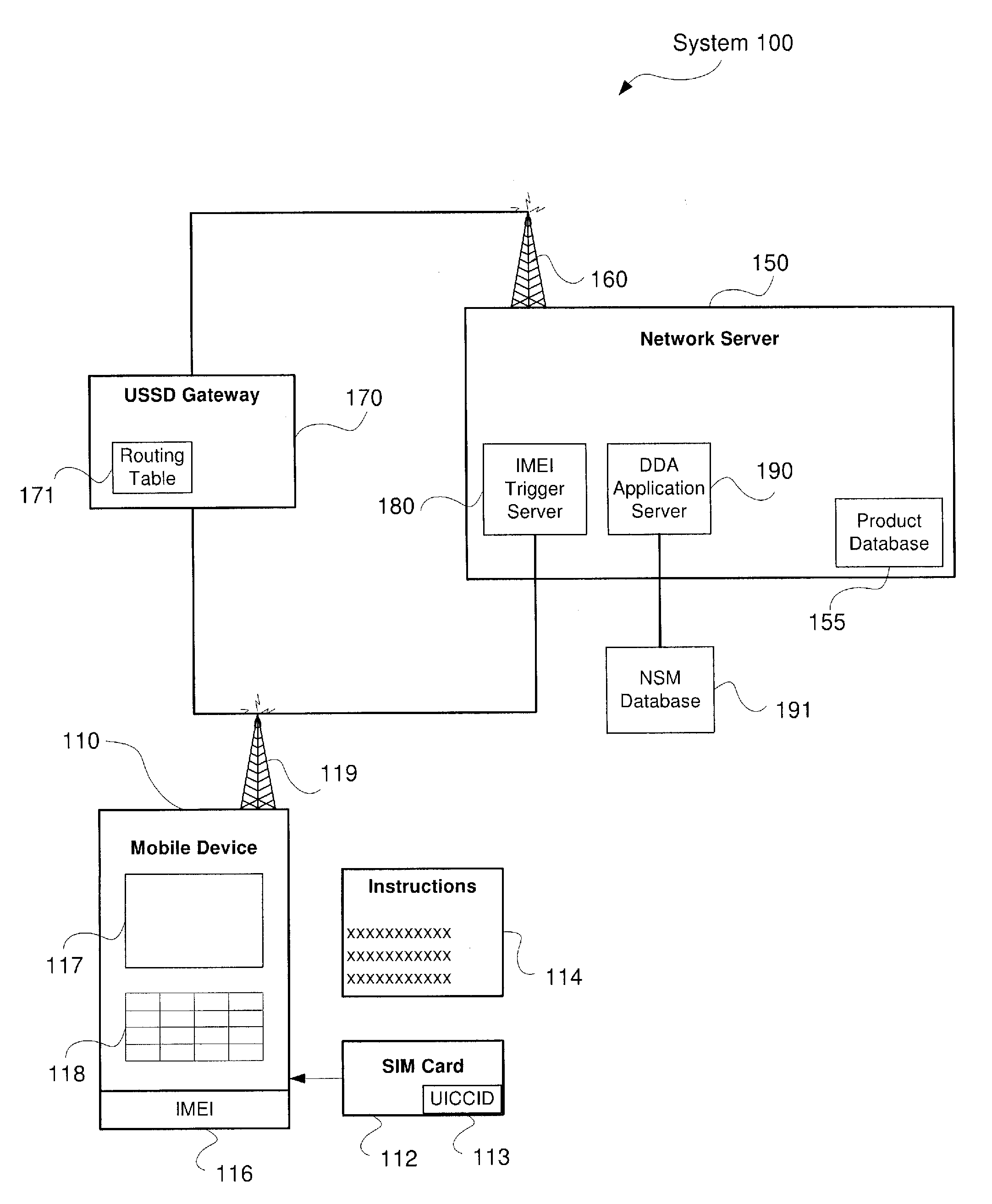
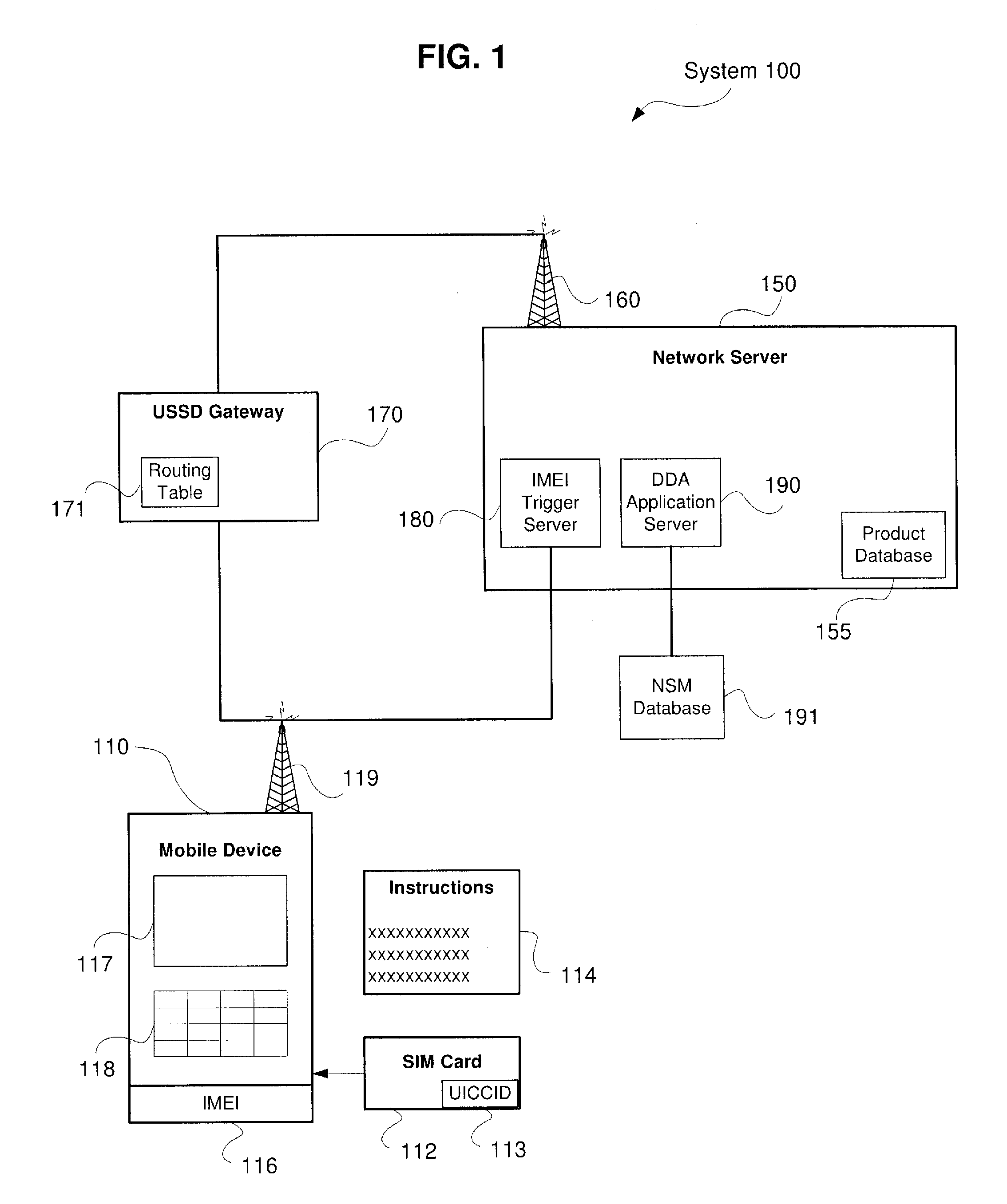
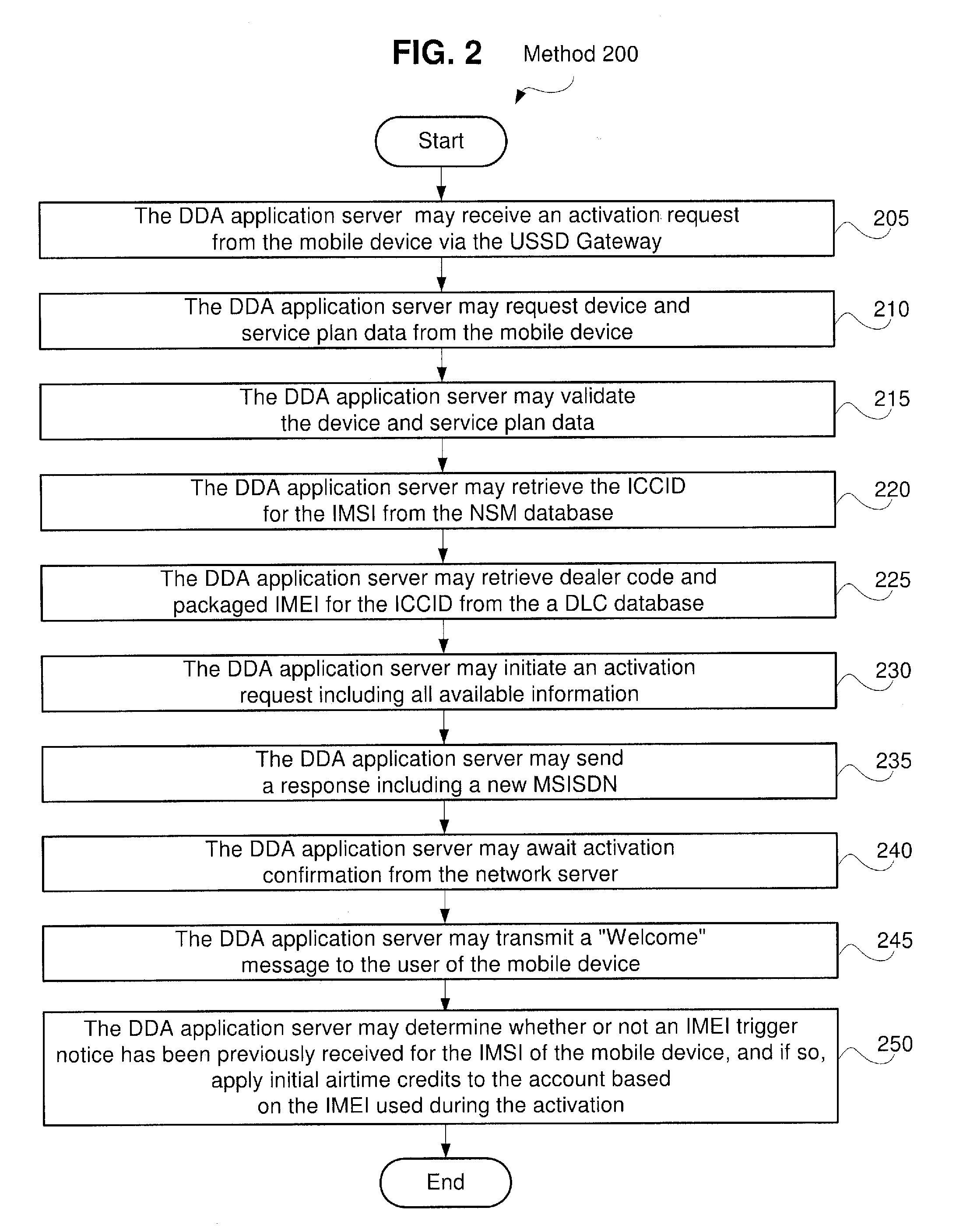
System and Method for Direct Device Activation
InactiveUS20110159843A1Unauthorised/fraudulent call preventionEavesdropping prevention circuitsTransceiverBiological activation
Described herein are systems and methods for single-step direct activation of telecommunication services for a mobile device. One embodiment of the disclosure of this application is related to a system comprising a transceiver receiving product information from a mobile device and receiving service plan information from the mobile device, and a server verifying availability of service for the mobile device based on at least one of the product information and the service plan information, and activating telecommunication service with the mobile device. The received product information including an international mobile equipment identity (“IMEI”) number received from an IMEI trigger event and an international mobile subscriber identity (“IMSI”) number received from a pre-provisioned subscriber identity module (“SIM”) component. The server accesses a national SIM manager (“NSM”) database, wherein the NSM includes pre-populated pairing of IMSI numbers with corresponding integrated circuit card identification (“ICCID”) numbers, and the server further retrieves a corresponding ICCID number for the IMSI of the mobile device and including the corresponding ICCID number with the product information.
Owner:AT&T INTPROP I L P
Authentication in a telecommunications network
InactiveUS7660772B2Easy to usePrevent forgeryAccounting/billing servicesData taking preventionTelecommunications networkTelecommunications link
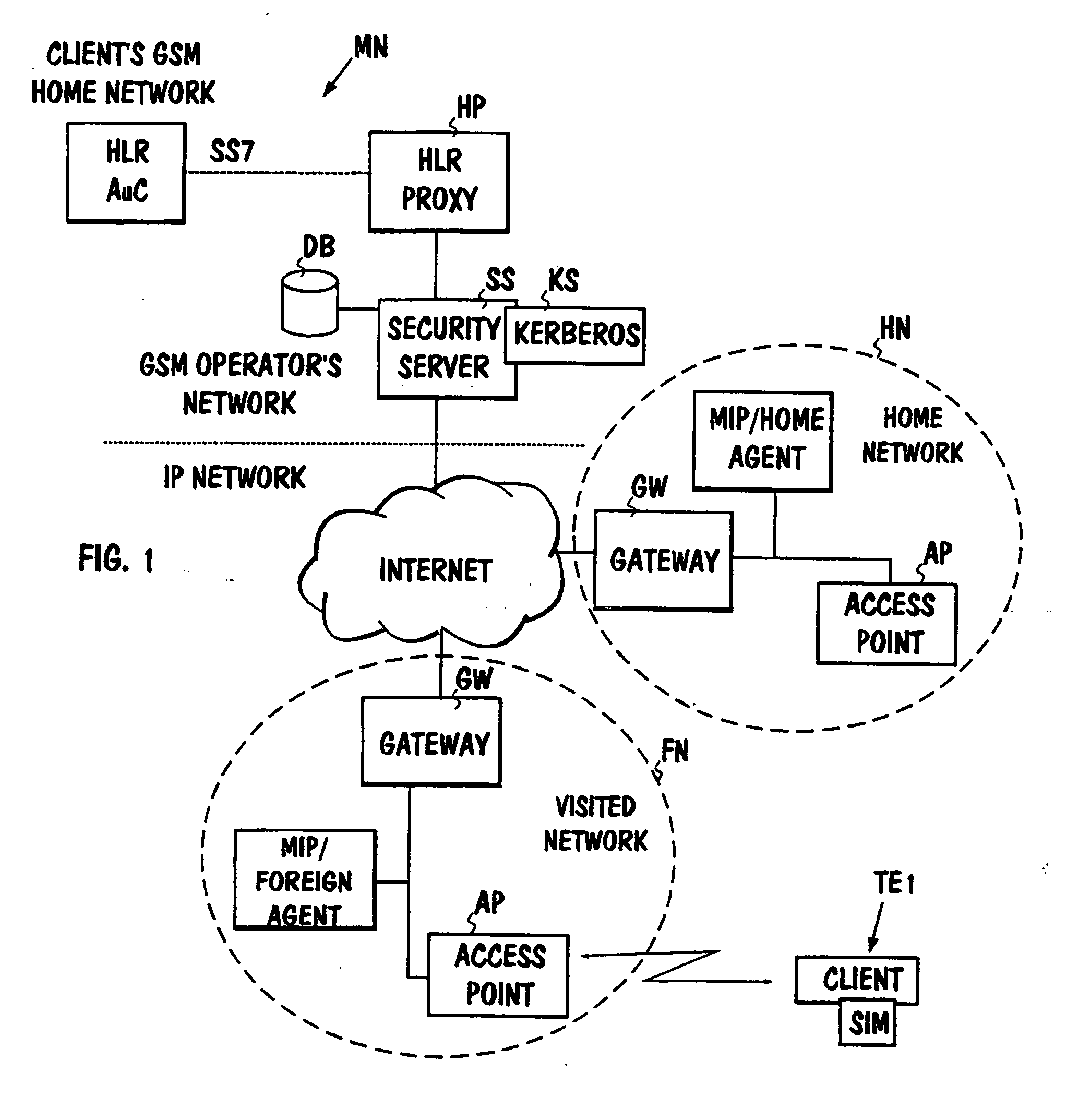
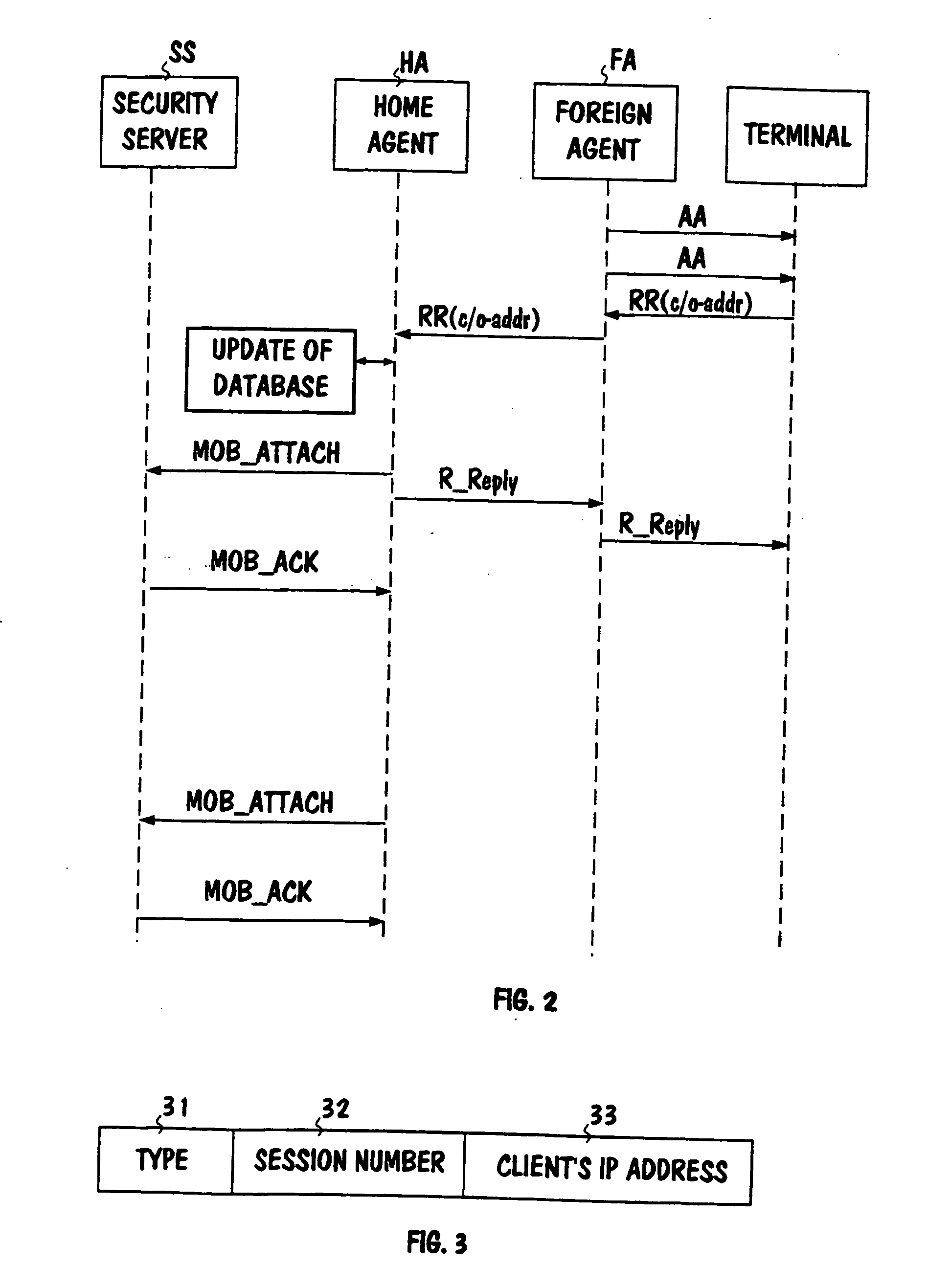
The invention relates to an authentication method intended for a telecommunications network, especially for an IP network. From a terminal (TE1) in the network a first message (RR) containing an authenticator and a data unit is transmitted to the network, the data unit containing information relating to the manner in which the authenticator is formed. For carrying out authentication in the network, the data unit contained in the first message is used for determining a check value, which is compared with the said authenticator. To make it unnecessary for the terminal to perform any complicated and heavy exchange of messages when attaching to the network and for still obtaining the desired security characteristics for use, such an identification unit is used in the terminal which receives as input a challenge from which a response and a key can be determined essentially in the same manner as in the subscriber identity module of a known mobile communications system, a set of authentication blocks is generated into the network, of which each contains a challenge, a response, and a key, whereby the generation is performed in the same manner as in the said mobile communication system, at least some of the challenges contained by the authentication blocks are transmitted to the terminal, one of the challenges is chosen for use at the terminal, and, based on it, a response and key for use are determined with the aid of the terminal's identification unit, in the said first message (RR) the network is notified with the aid of the said data unit of which key corresponding to which challenge was chosen, and the authenticator of the first message and the said check value are determined with the aid of the chosen key.
Owner:CORE WIRELESS LICENSING R L
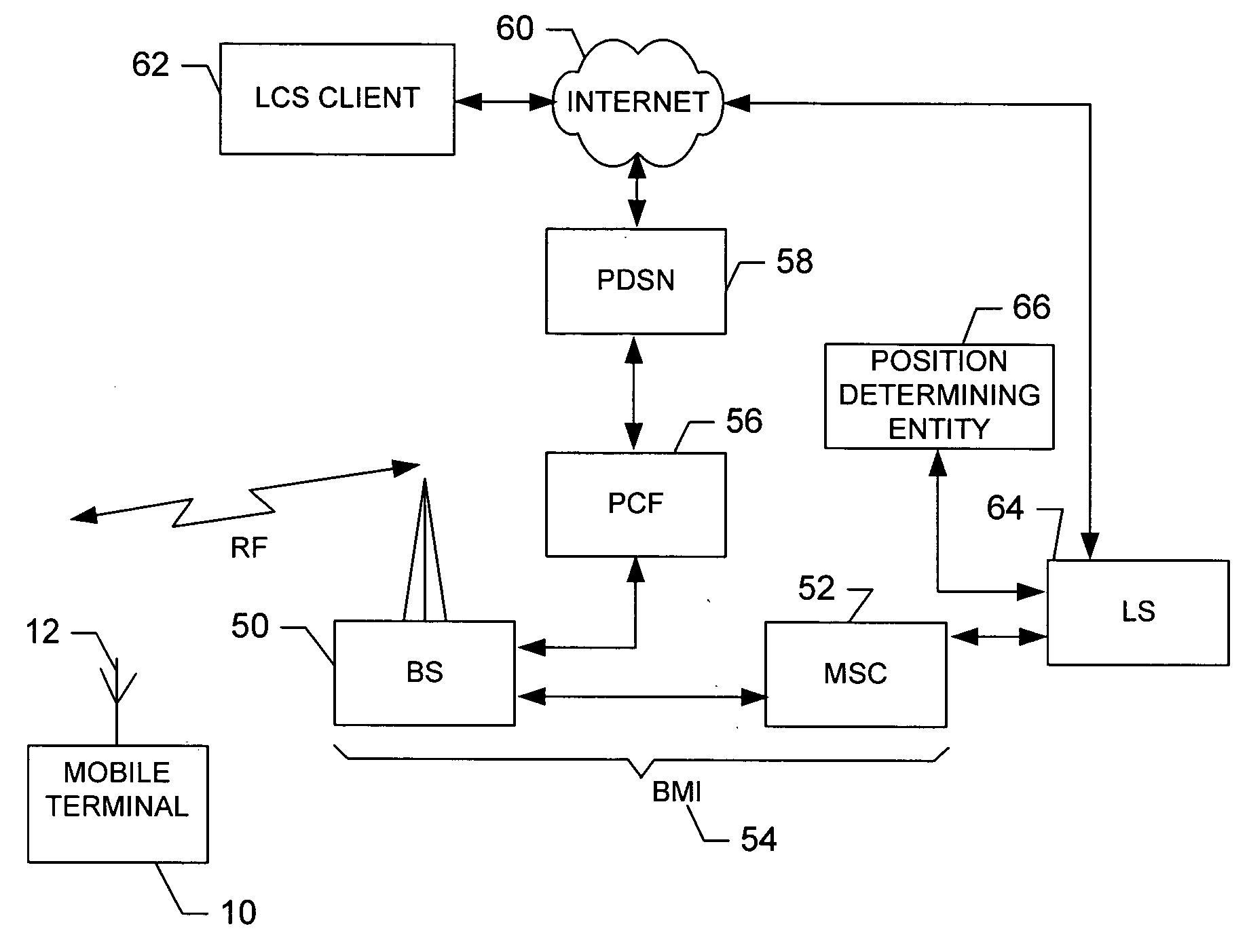
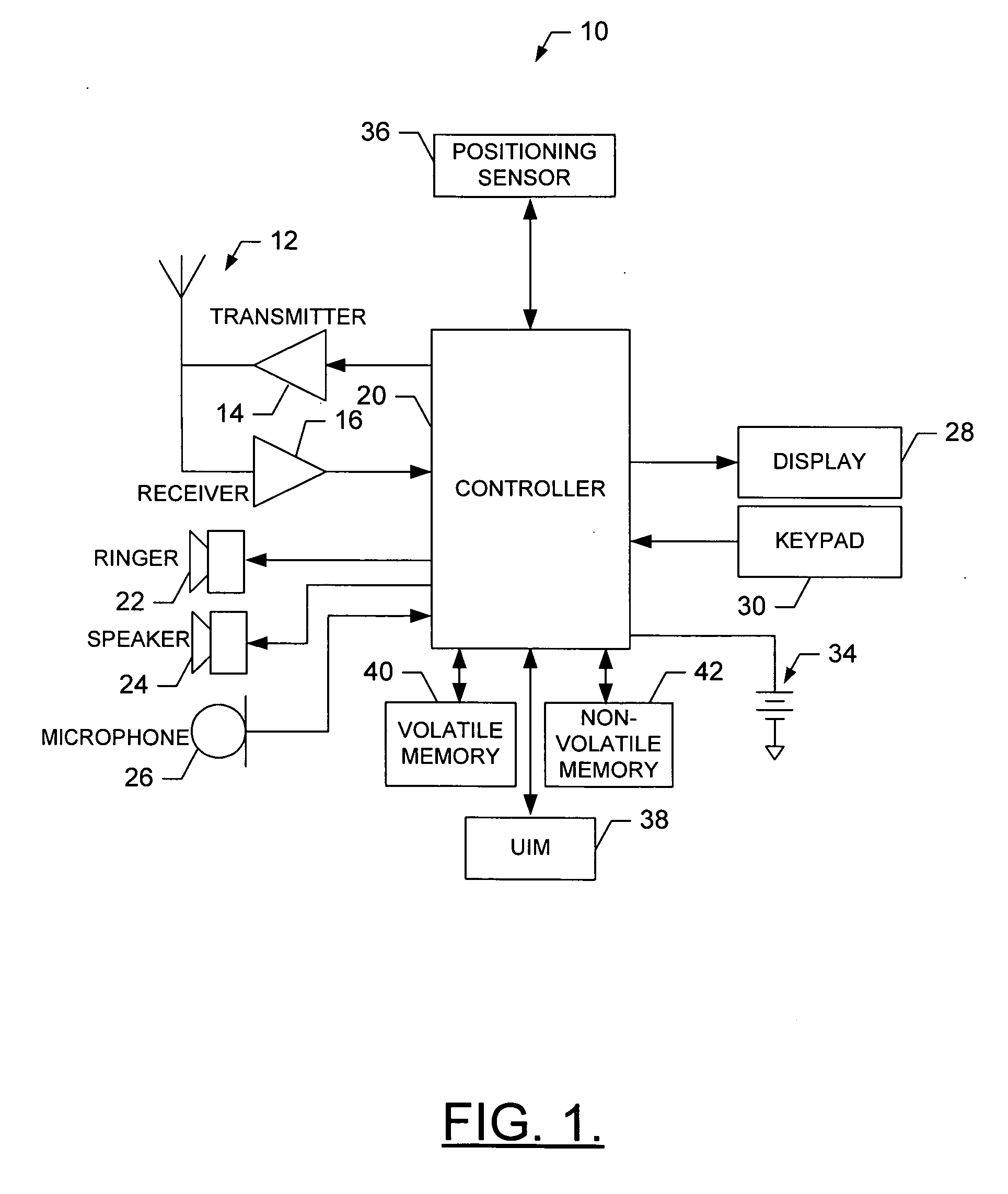
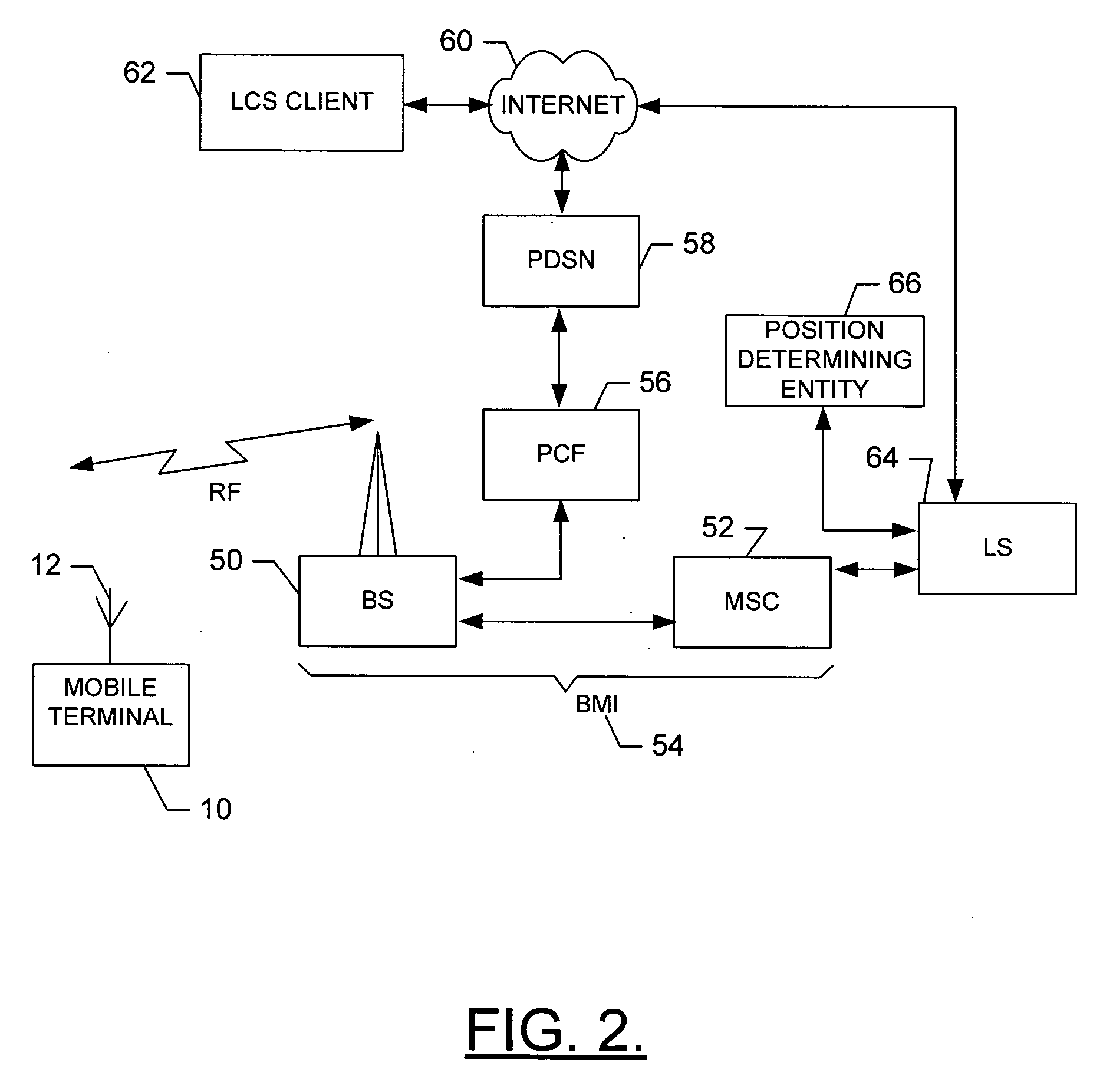
Method, apparatus and computer program product for determining location of a mobile terminal
InactiveUS20070155400A1Radio/inductive link selection arrangementsSubstation equipmentLocation dataComputer program
A method of determining a location of a mobile terminal using a user identity module (UIM) includes issuing an instruction from the UIM to the mobile terminal instructing the mobile terminal to perform a positioning event and receiving position data from the mobile terminal responsive to the positioning event.
Owner:NOKIA CORP
Roaming communication method based on mobile two-channel virtual card number authentication and roaming communication equipment based on mobile two-channel virtual card number authentication
InactiveCN103987025ASolve the problem of expensive roaming chargesPlay a stimulating roleSecurity arrangementNetwork data managementCommunications systemAuthentication server
The invention relates to mobile roaming communication and aims at providing a method and equipment capable of sharing communication resources with communication expense in a roaming destination without replacing a local UIM / SIM (user identity module / subscriber identity module) in a user terminal. The invention provides a roaming communication system based on mobile two-channel virtual card number authentication. The roaming communication system based on the mobile two-channel virtual card number authentication comprises a user terminal, a number server and a roaming destination authentication server, wherein the number server is used for linking a channel of a first communication module of user equipment (UE) to the roaming destination authentication server for browsing a page of the service and serves as a information transfer station between the UE and the roaming destination authentication server; the roaming destination authentication server is used for selecting a virtual mobile user number, sending authentication parameters of the system to the UE and comparing a returned authentication operation result which carries a UE identity authentication algorithm module the same with an authentication data storage, the same terminal secret key and corresponding sequence code and can assist virtual mobile user number authentication. The method and the equipment provided by the invention is applicable to the mobile roaming communication.
Owner:熊文俊
Method for supporting subscriber's service provider change restriction policy in mobile communications and apparatus therefor
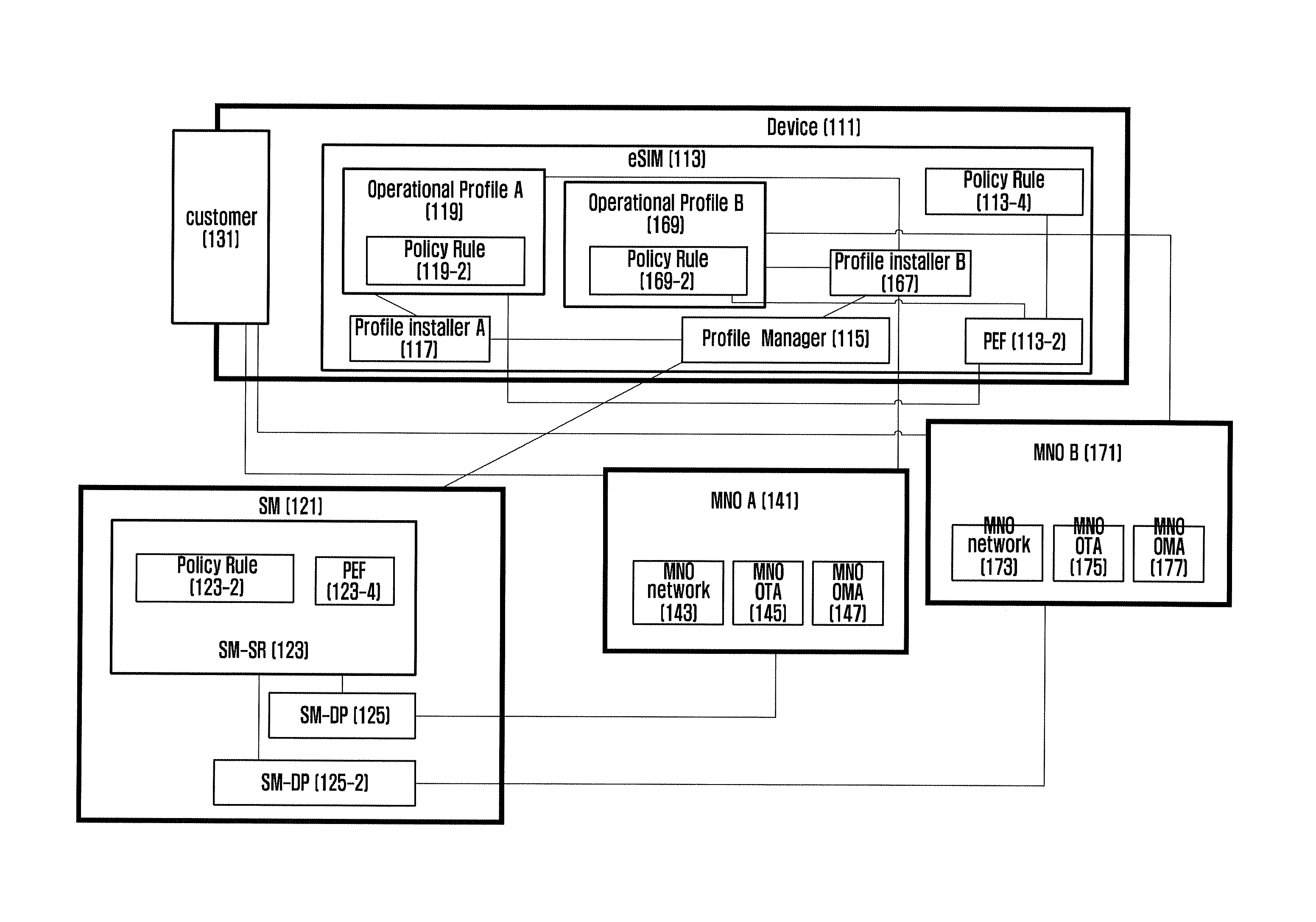
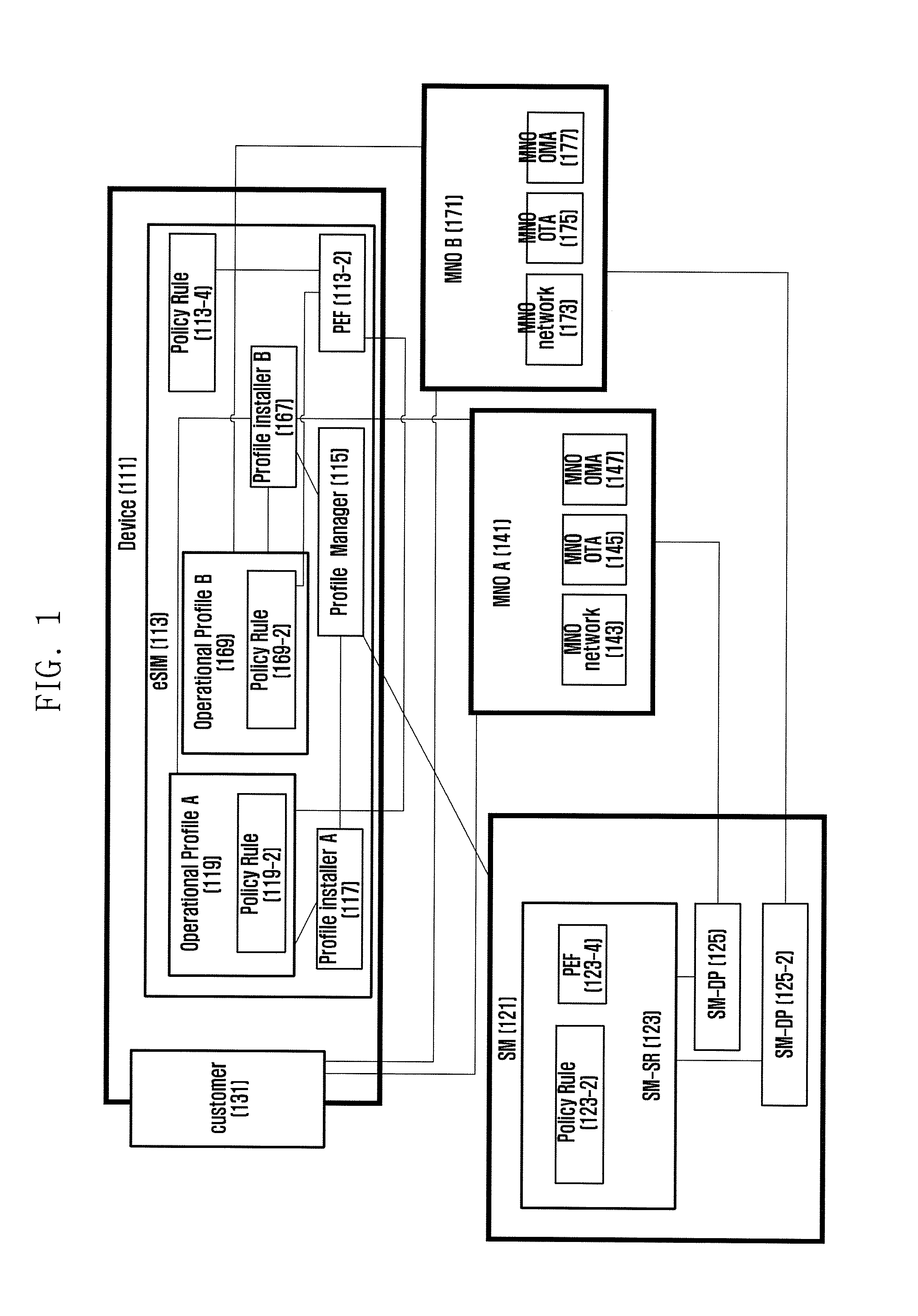
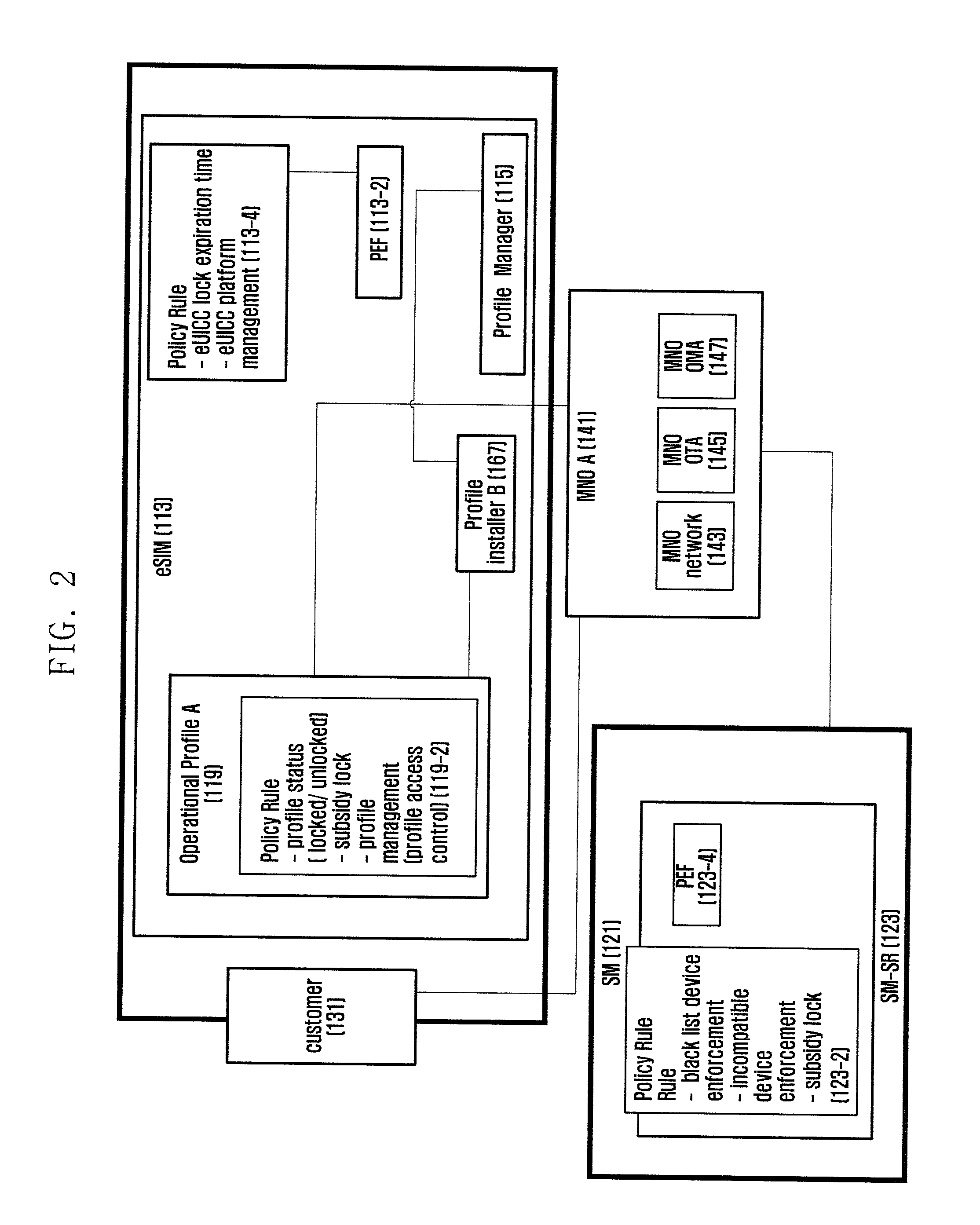
ActiveUS20160149903A1Facilitate communicationImprove communication efficiencyDigital data protectionTransmissionElectricity infrastructureEngineering
The present invention relates to a method and an apparatus for employing an embedded subscriber identity module (hereinafter referred to as eSIM) to apply a policy such as a subsidy policy to, activate, deactivate, add to, update, and delete a user profile in a mobile communications network. The present invention enables a mobile device to determine whether to host the policy of a new service provider when it changes the present service provider or to perform a lock for prohibiting the policy change, and to change the profile related to the determination. The present invention also enables a mobile device to replace the policy related to the service provider by applying the policy, or to employ eSIM so as to activate, deactivate, revise, add, or delete the rules of the policy related to the service provider. The present invention provides various examples of hosting and applying the policy and various examples of activating, deactivating, revising, adding, deleting the policy rules so as to make eSIM identify the subscriber as the existing subscriber identity module. The invention also enables the device or eSIM to be reused when changing the service provider throughout the life cycle thereof without limiting the use of eSIM to a single service provider. The invention also provides a method for locking the policy applied per service provider, and the use of eSIM when changing to another service provider by the policy per service provider. The present invention also provides a method for checking the criteria of decision and verifying the power of decision when administering the policy rules and eSIM through deleting, adding, revising, activating, and deactivating the profile management plan and policy rules by applying the service provider's policy. Thus the present invention enables the device to host a new service provider's policy for communicating therewith when changing from the existing service provider to the new service provider, or when the government changes the service provider for an M2M device related to the electricity, infrastructure, etc. under an environment such as EUTRAN (Evolved Universal Terrestrial Radio Access Network) or UTRAN (Universal Terrestrial Radio Access Network) / GERAN(GSM / EDGE Radio Access Network). The present invention also is advantageous in that if the change of a service provider is not allowed according the policy of the existing service provider, the information related to communication and the security information are set revised safely by locking, thus enhancing the communication efficiency and security. The present invention also enables the device to verify the power of the user or to revise safely the information of eSIM for adding, revising, deleting, activating, and deactivating the policy rules for managing the operation profile for administration of the policy of the service provider under an environment such as EUTRAN(Evolved Universal Terrestrial Radio Access Network) or UTRAN(Universal Terrestrial Radio Access Network) / GERAN(GSM / EDGE Radio Access Network), thus enhancing the communication efficiency and security.
Owner:SAMSUNG ELECTRONICS CO LTD
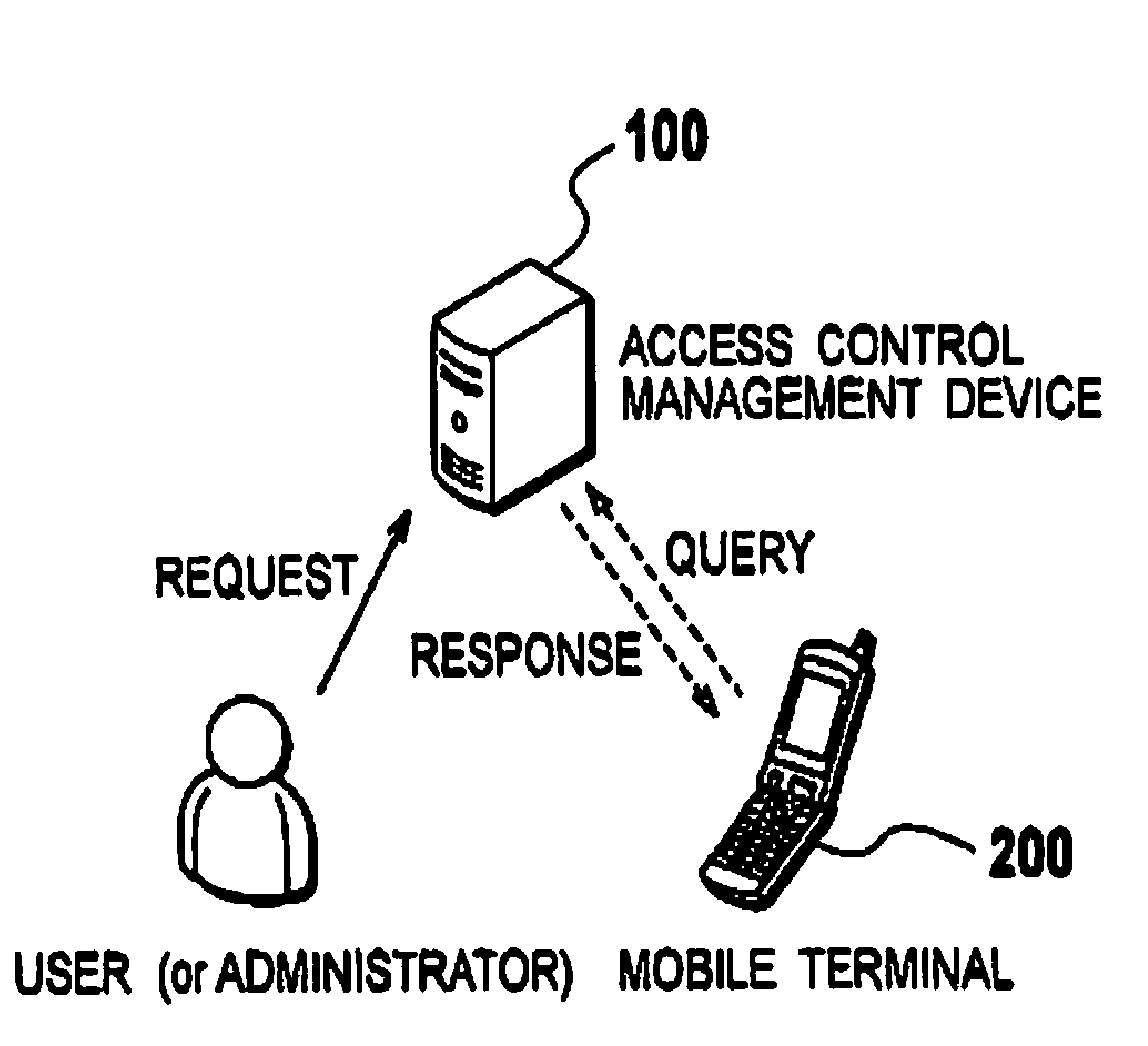
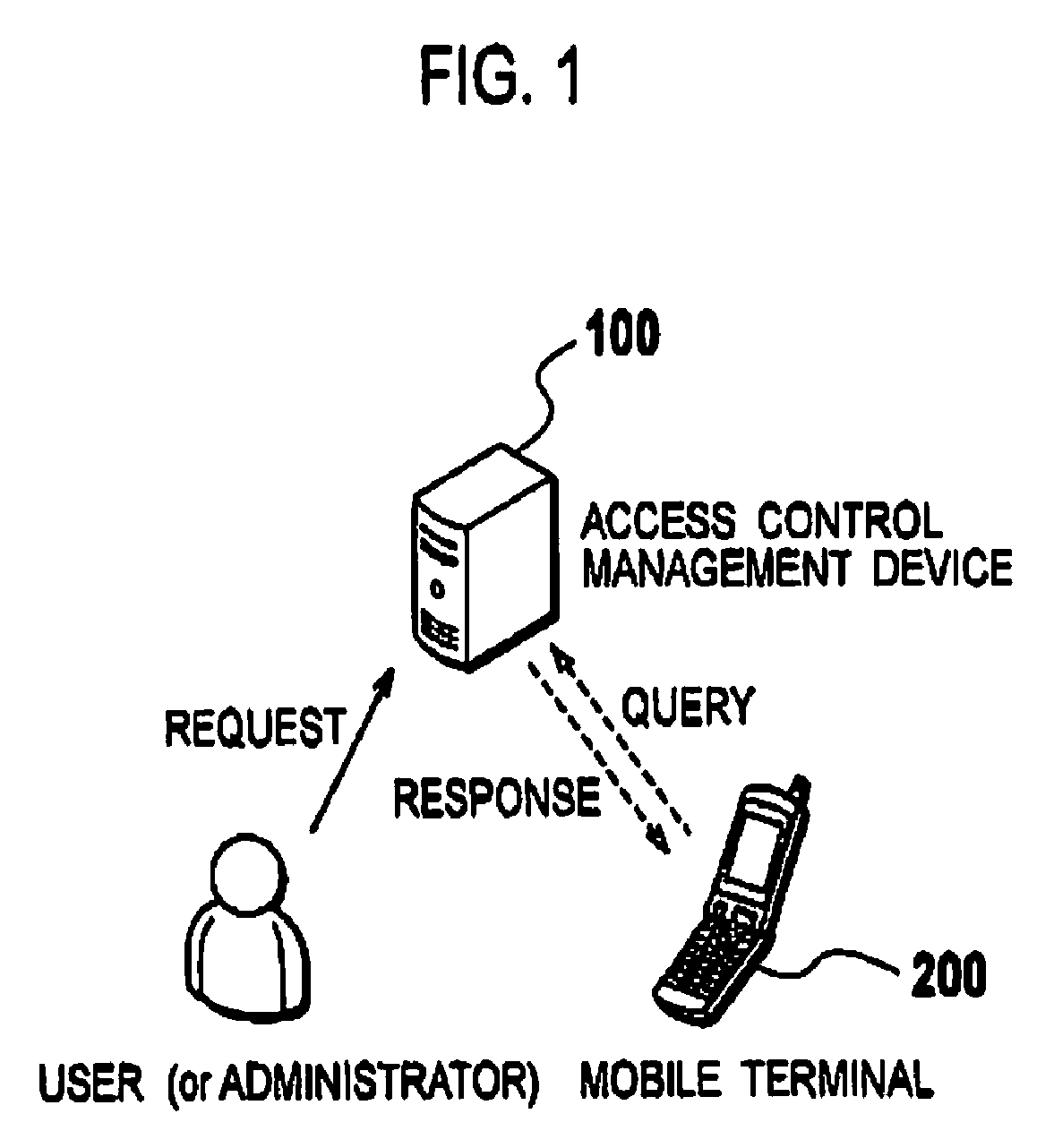
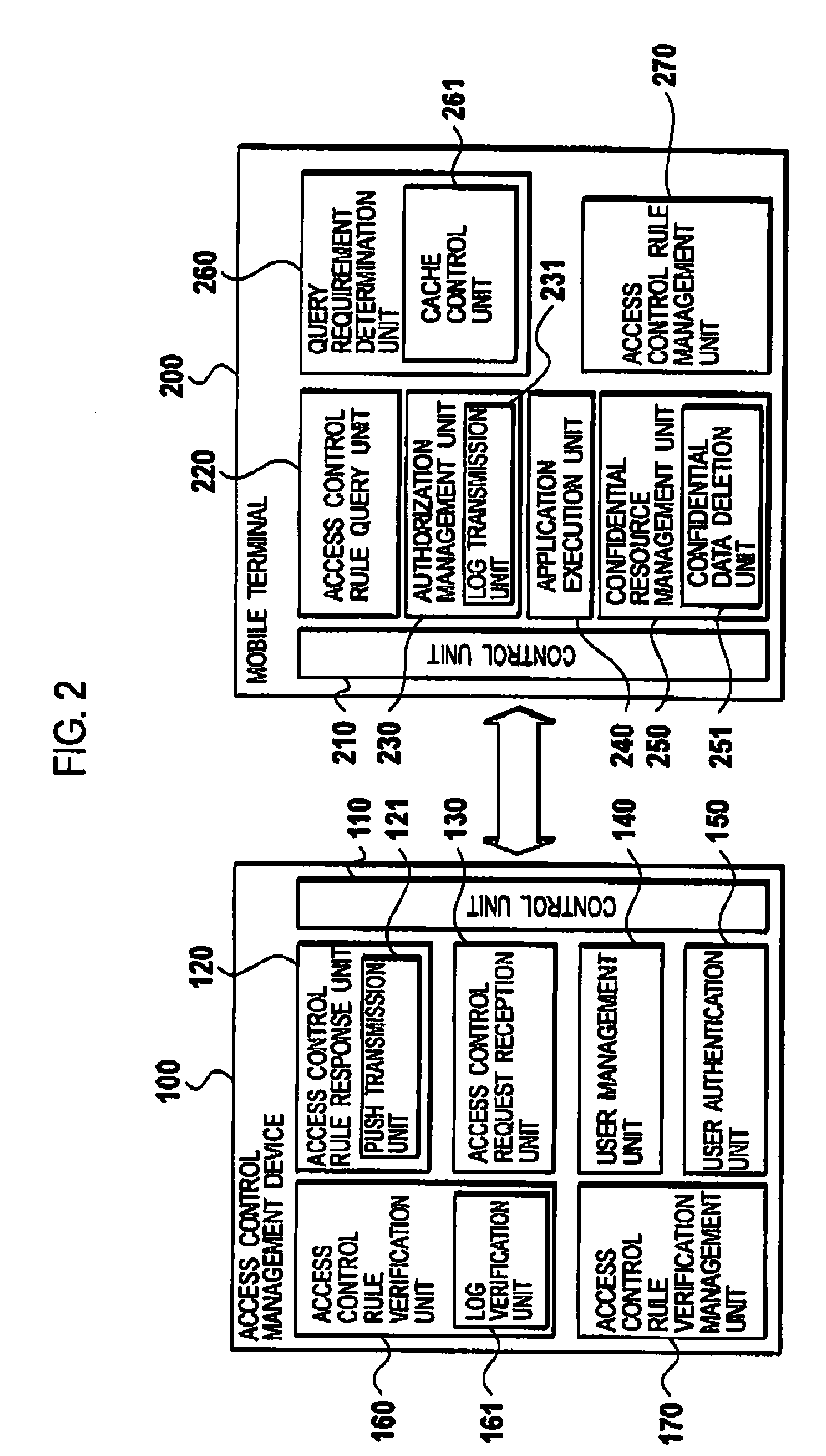
Mobile terminal, access control management device, and access control management method
InactiveUS20090221266A1Protect resourcesUnauthorised/fraudulent call preventionEavesdropping prevention circuitsManagement unitExecution unit
A mobile terminal (200) comprises an application execution unit (240) configured to execute an application program; an access control rule management unit (270) configured to retain an access control rule defining whether the application program has an access authorization to a confidential resource in the mobile terminal and a determining unit; an access control rule query unit (220) configured to acquire, from an external device, the access control rule by designating at least one of an identifier of a user identity module installed in the mobile terminal and an identifier of the mobile terminal, and to retain the acquired access control rule in the access control management unit; a query requirement determination unit (260) configured to determine whether to update the access control rule when the application program makes an access to the confidential resource, and to update the access control rule; an authorization management unit (230) configured to determine whether the application program has the access authorization based on the access control rule; and a confidential resource management unit (250) configured to determine whether to permit an access request to the confidential resource by the application program, based on a result of the determination of the authorization management unit (230).
Owner:NTT DOCOMO INC
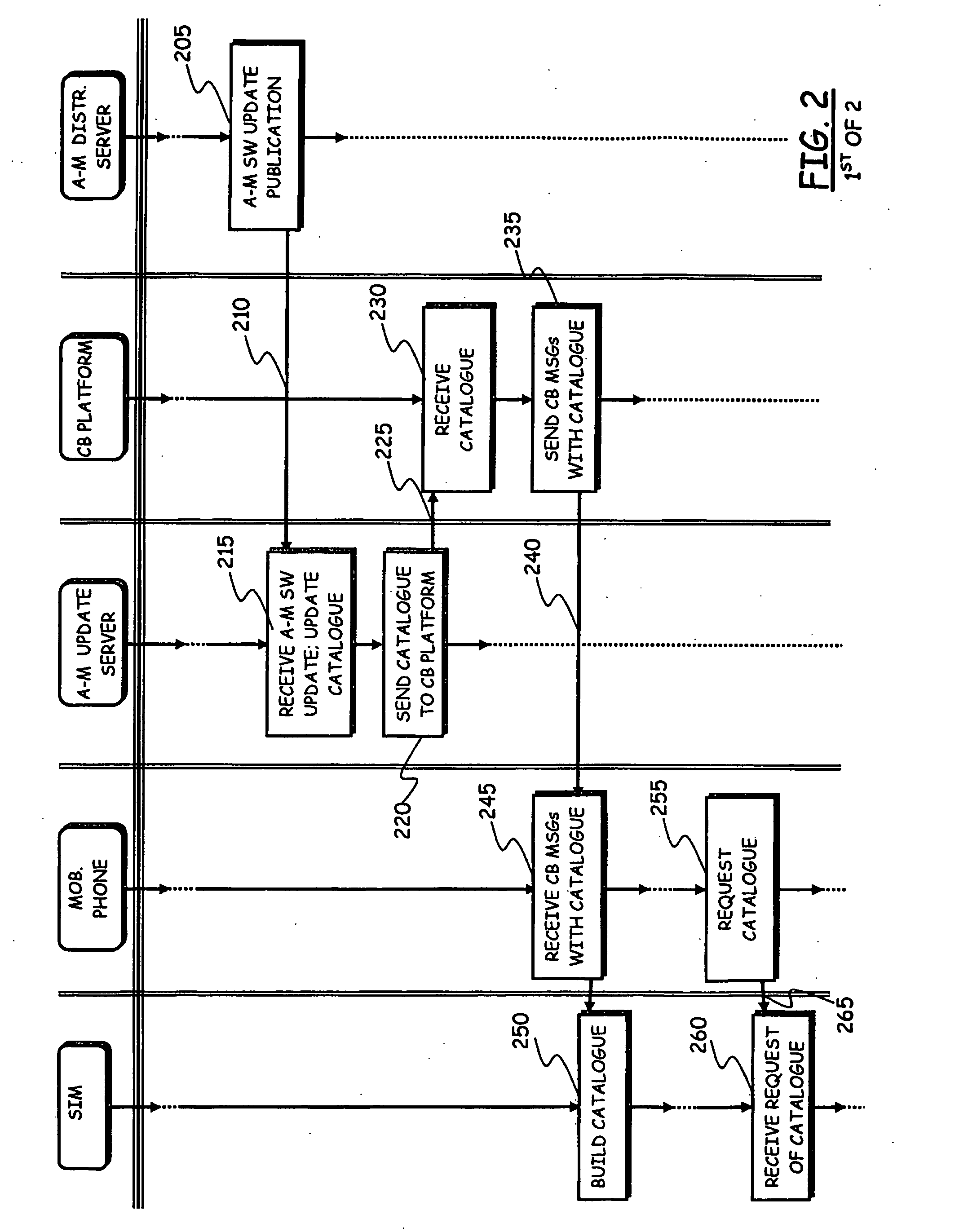
Method and System for Updating Applications in Mobile Communications Terminals
ActiveUS20090305687A1Multiple digital computer combinationsSubstation equipmentWeb serviceComputer module
A method is disclosed for checking updates of a software application installed in a wireless communications terminal adapted to be used in a wireless communications network in combination with a subscriber identity module. In the subscriber identity module, a web server function adapted to interact with the software application installed in the wireless communications terminal is provided. When an update of the software application is available, the wireless communications terminal is notified, so that information about availability of the update is made available to the web server function. The software application sends at least one update availability request to the web server function in the subscriber identity module, in order to check if an update is available.
Owner:TELECOM ITALIA SPA
Optimization of power consumption in dual sim mobiles in connected mode in a wireless network
ActiveUS20170150545A1Reduce power consumptionPower managementConnection managementRadio Resource ControlUser identity module
A method of optimizing connection mode procedures for a dual subscriber identity module (SIM) mobile communication device is provided. The method includes receiving, by a base station, a paging message for a first SIM in an idle mode from a core network; determining, by the base station, if a radio resource control (RRC) connection linked with the first SIM is available or not; triggering, by the base station, a second paging type message for the first SIM with a normal cause through the RRC connection linked with the first SIM if the RRC connection of the first SIM is available; determining, by the base station, if a RRC connection linked with a second SIM is available or not if the RRC connection of the first SIM is not available; triggering, by the base station, a second paging type message for the first SIM with a mapped new cause through the RRC connection linked with the second SIM if the second SIM is available; and triggering, by the base station, a first paging type message with a temporary identity and a cause received in the paging message from the core network through a paging channel if the RRC connection linked with the second SIM is not available.
Owner:SAMSUNG ELECTRONICS CO LTD
Apparatus and method for reducing power consumption in multi-mode portable terminal
ActiveUS20110077031A1Reduce power consumptionPower managementEnergy efficient ICTManagement unitEngineering
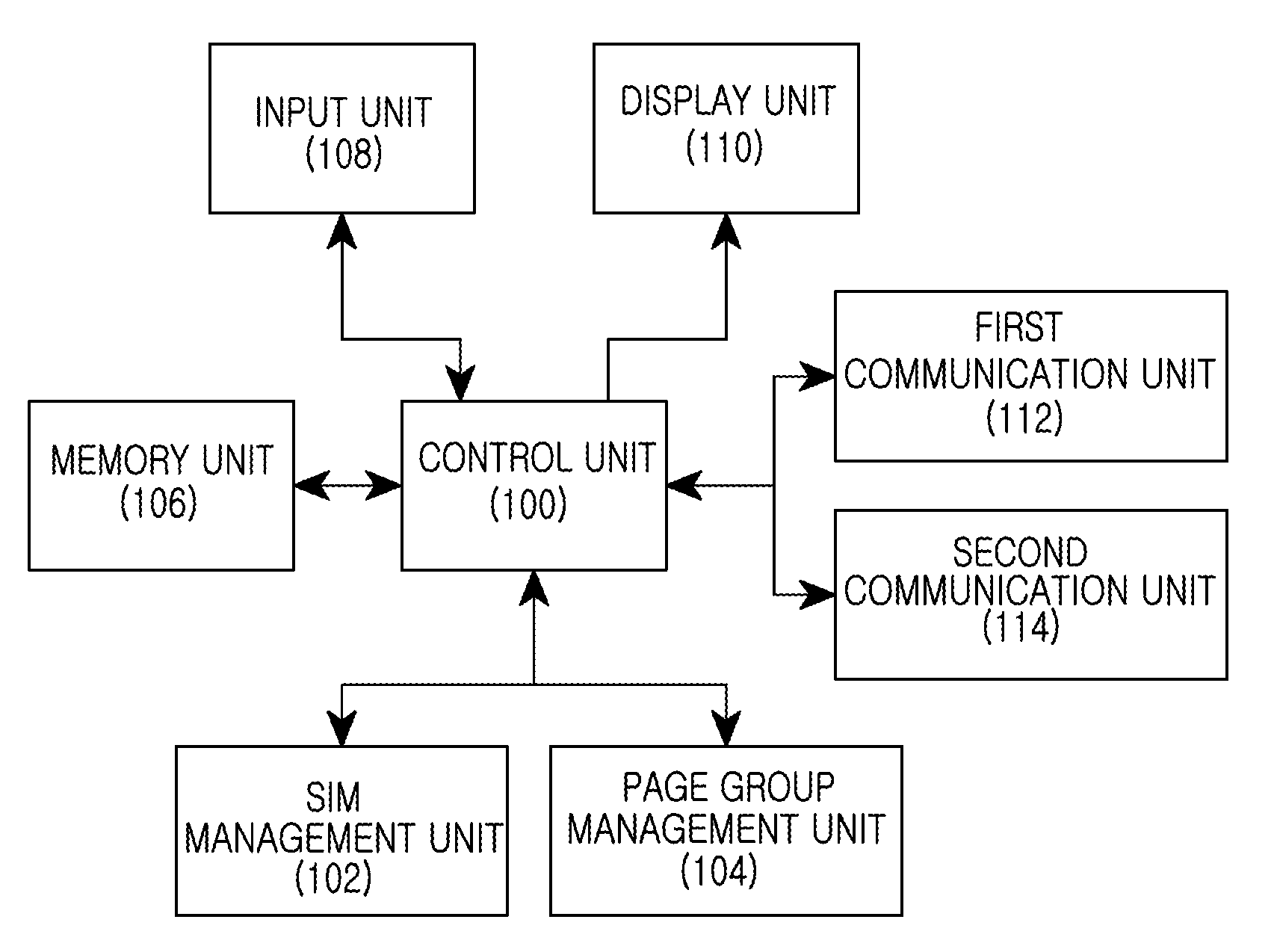
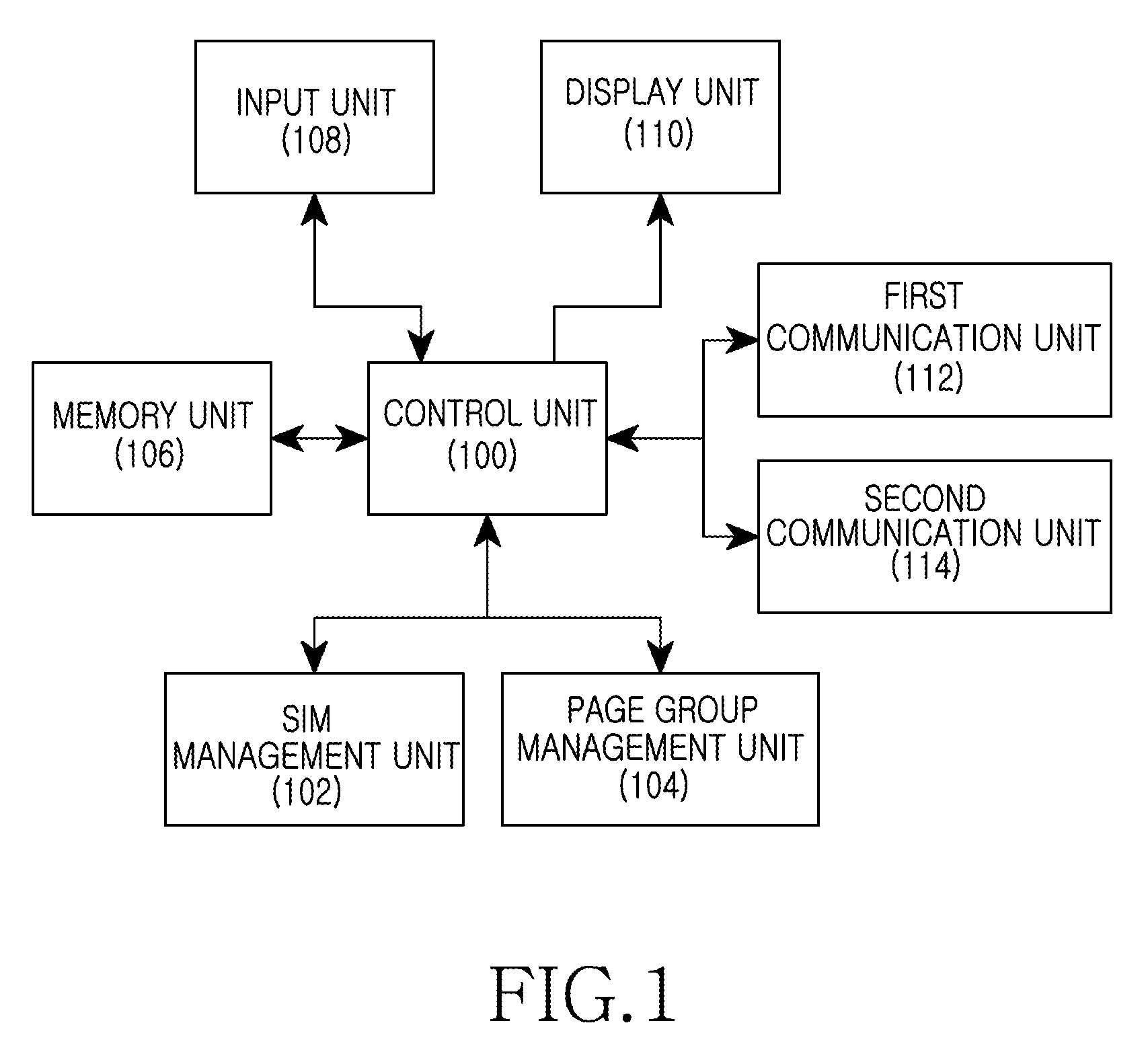
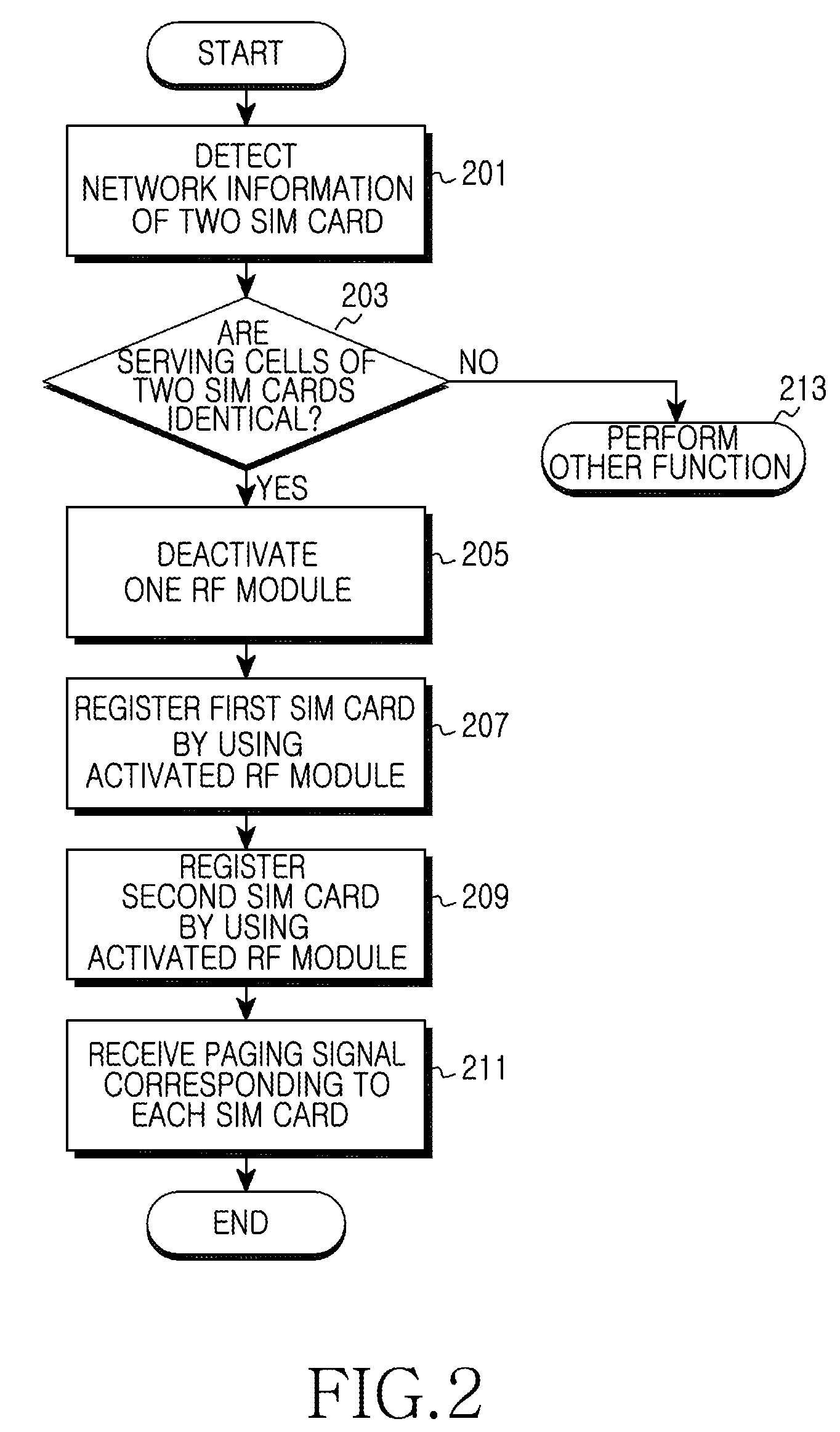
An apparatus and method for reducing power consumption in a multi-mode portable terminal are provided. The apparatus includes a Subscriber Identity Module (SIM) management unit and a control unit. The SIM management unit is configured to determine whether there are multiple SIM cards of the same serving cell in a portable terminal supporting a plurality of RF modules and a plurality of SIM cards. The control unit is configured to activate only one RF module corresponding to the SIM cards of the same serving cell when receiving information of the SIM cards of the same serving cell from the SIM management unit.
Owner:SAMSUNG ELECTRONICS CO LTD
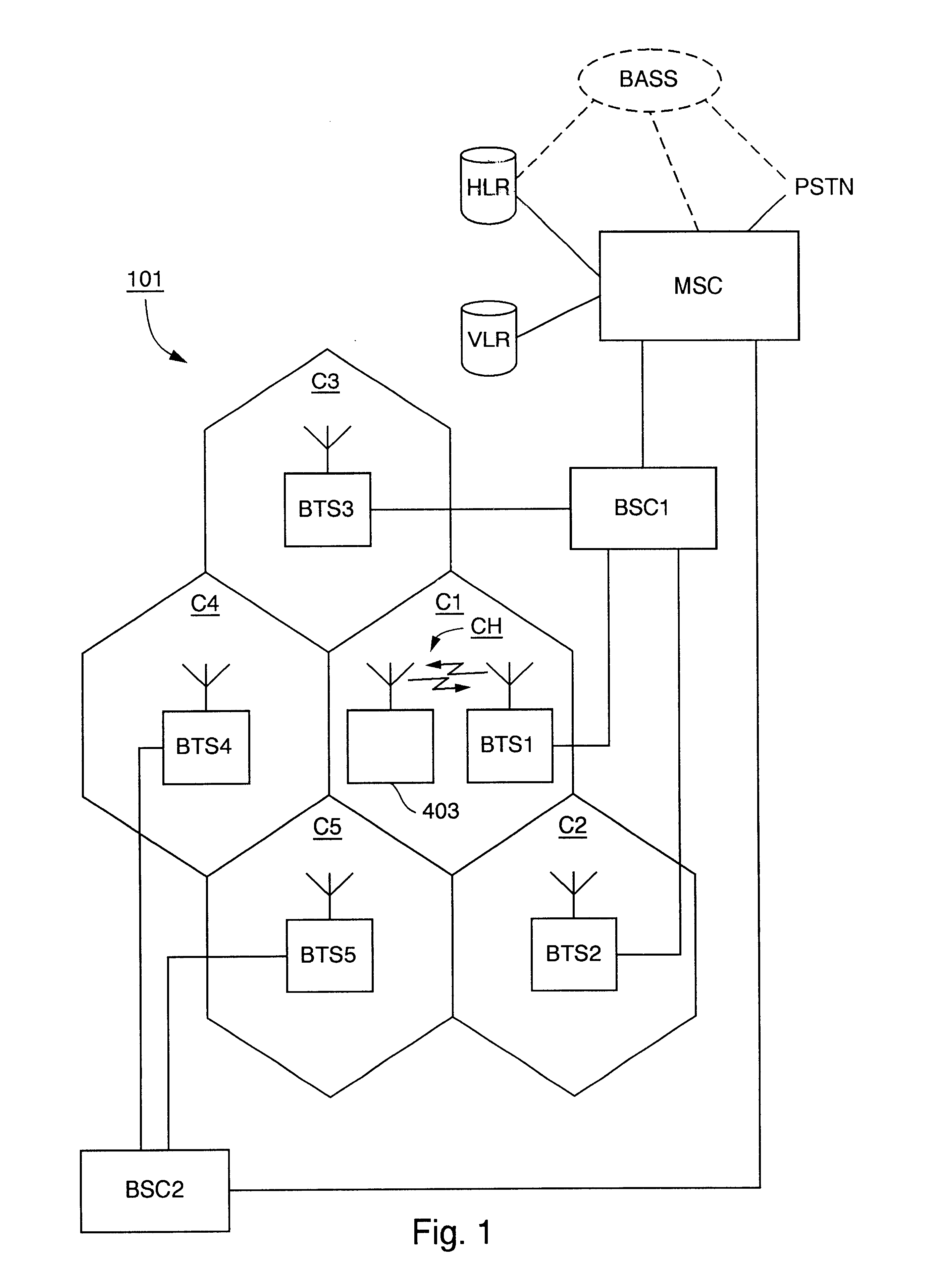
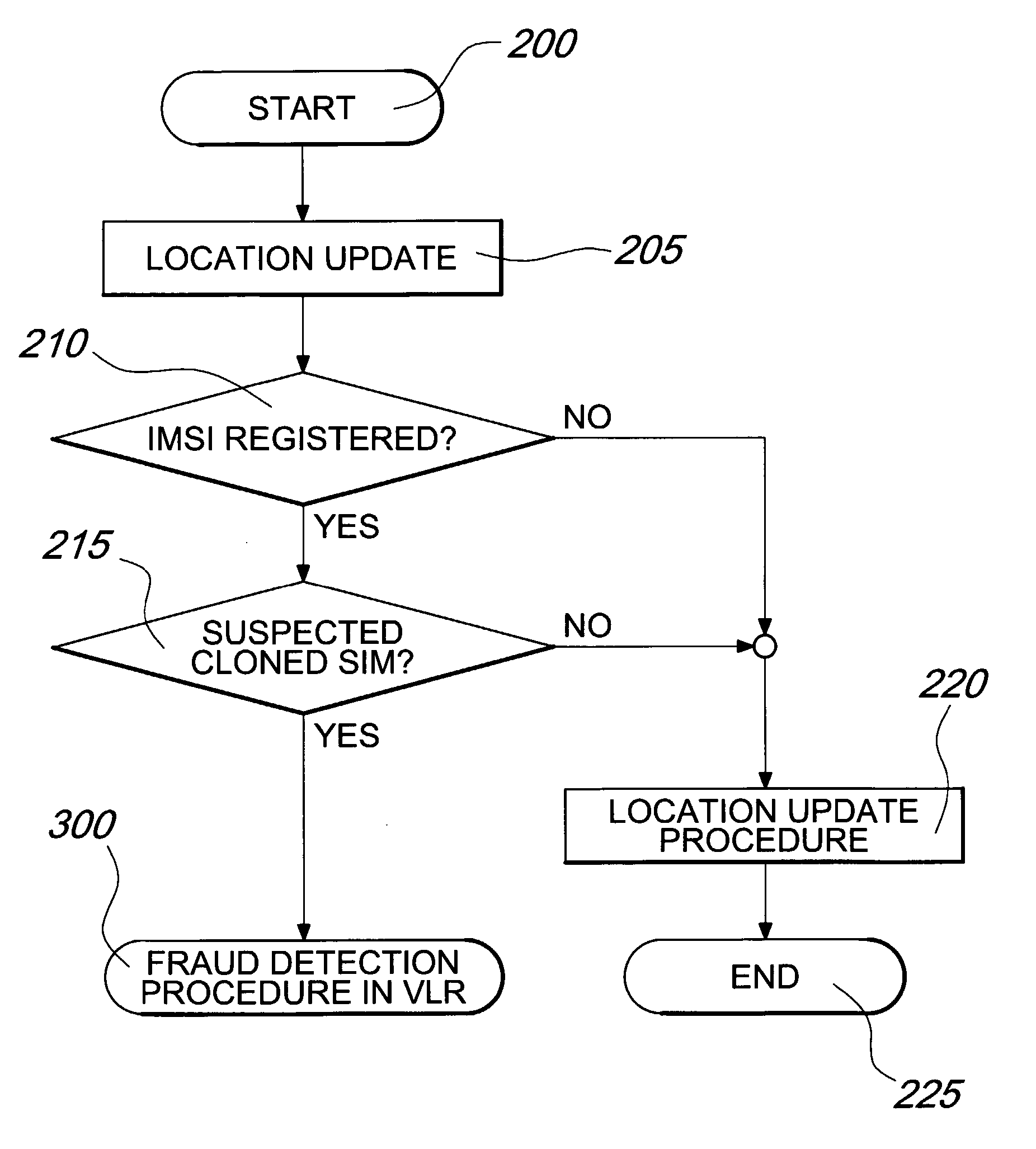
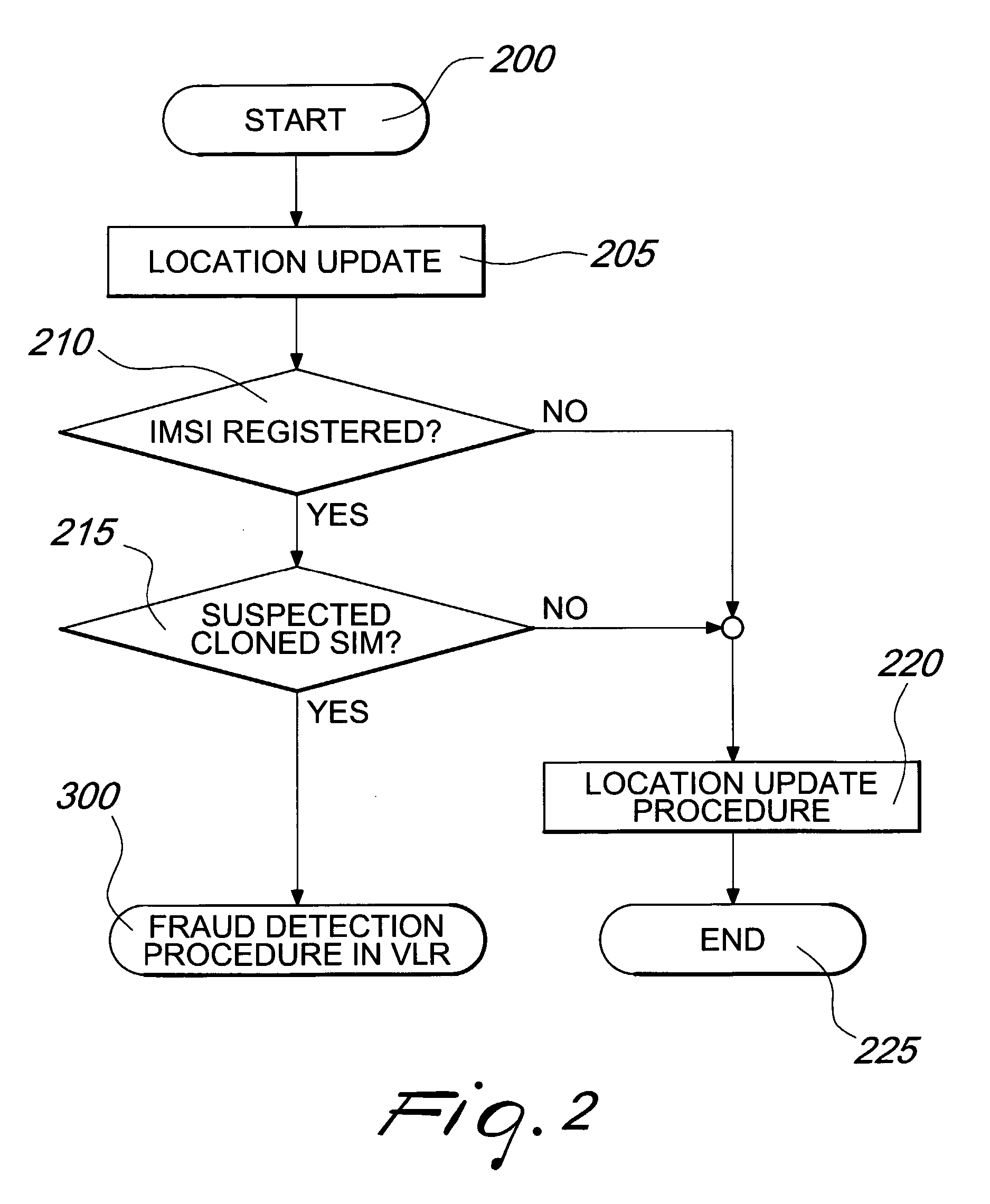
Method and Radio Communication Network For Detecting The Presence Of Fraudulent Subscriber Identity Modules
InactiveUS20070270127A1Unauthorised/fraudulent call preventionEavesdropping prevention circuitsUser equipmentUser identity module
A method for detecting the presence of fraudulent Subscriber Identity Modules in a network for cellular communications comprising the steps of: at a first Service Node, receiving a registration request by a first User Equipment comprising a Subscriber Identity Module for defining an identity of a subscriber; initiating a checking to establish whether the subscriber is already registered with the same identity in at least one Service Node over the network, including the first Service Node; if the subscriber results to be already registered with the same identity in at least a second Service Node over the network, retrieving status information on at least a second User Equipment associated with the already registered subscription for checking whether the second User Equipment is not the first User Equipment; and disabling any subscription of the subscriber associated with the identity if the second User Equipment results not to be the first User Equipment.
Owner:TELEFON AB LM ERICSSON (PUBL)
System and method for authentication in a mobile communications system
InactiveUS20060073811A1Simply and smoothly authenticatedEasily and smoothly authenticatedUnauthorised/fraudulent call preventionEavesdropping prevention circuitsNetwork terminationCommunications system
The present invention provides an authentication method and apparatus for authenticating an identity of a subscriber attached to a network. According to the invention, in a network terminal, a subscriber identity module is used so that a response is obtained as a result of a challenge given to the identity module as input. A special security server in the network is also used so that when a terminal attaches to the network, a message of a new user is transmitted to the security server. Subscriber authentication information corresponding to the new user is fetched from the mobile communications system to the network, wherein the authentication information includes at least a challenge and a response. Authentication is performed based on the authentication information obtained from the mobile communications system by transmitting the challenge to the terminal through the network, by checking at the terminal that the challenging is unique from challenges used in previous authentication exchanges, by generating, if the challenge is unique, a response from the challenge in the identity module of the terminal and by comparing the generated response with the response received from the mobile communications system.
Owner:NOKIA CORP
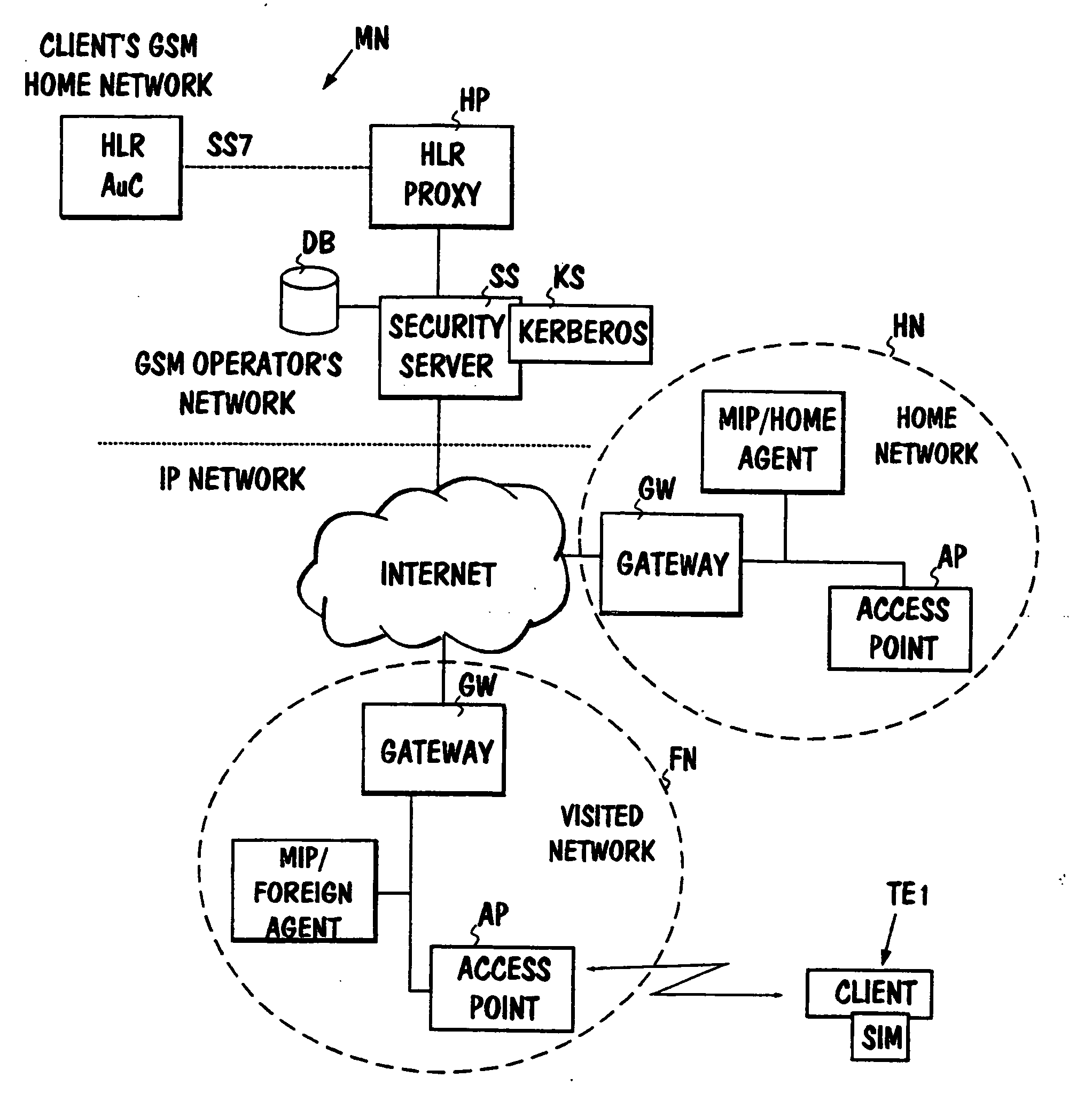
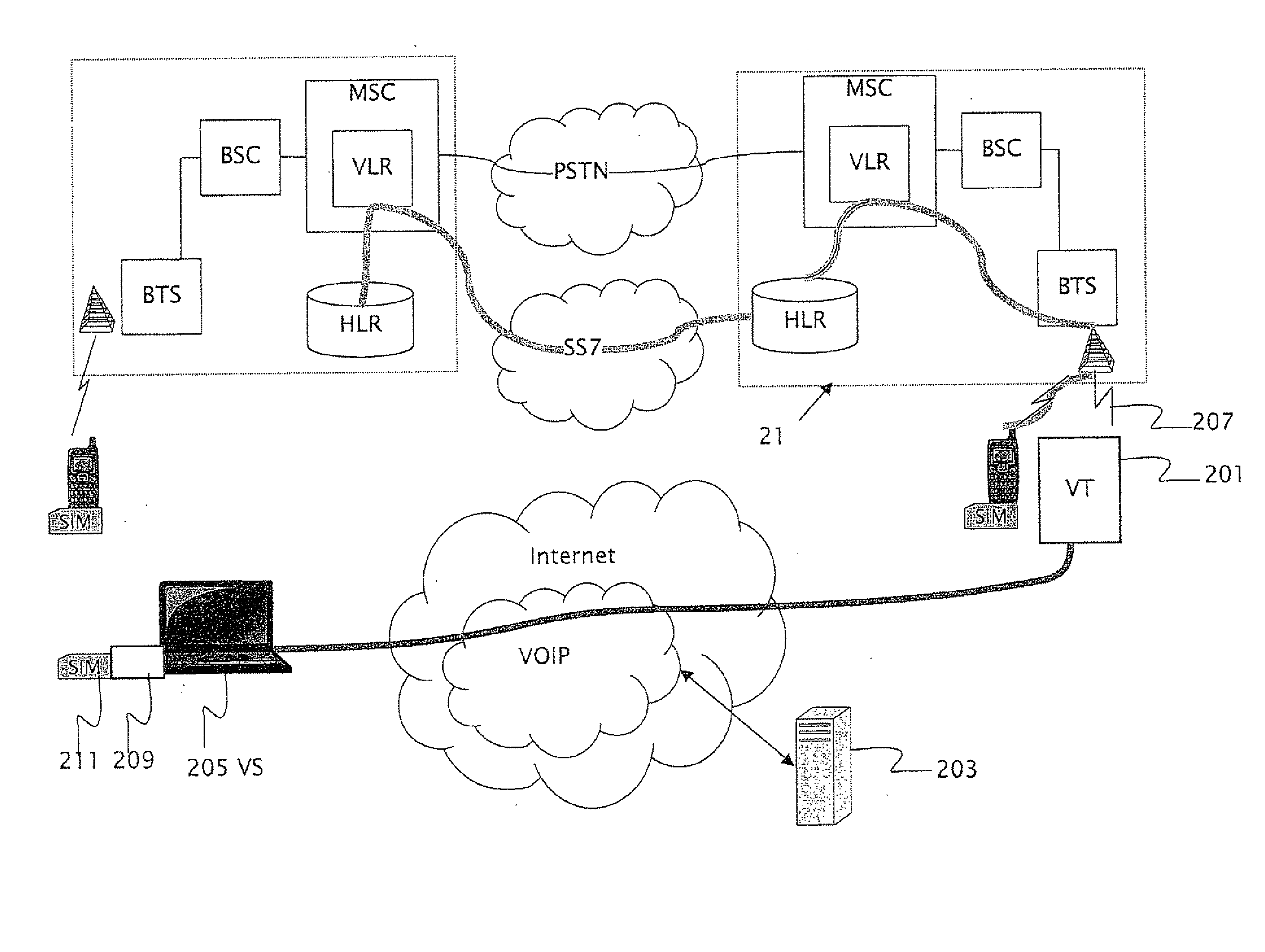
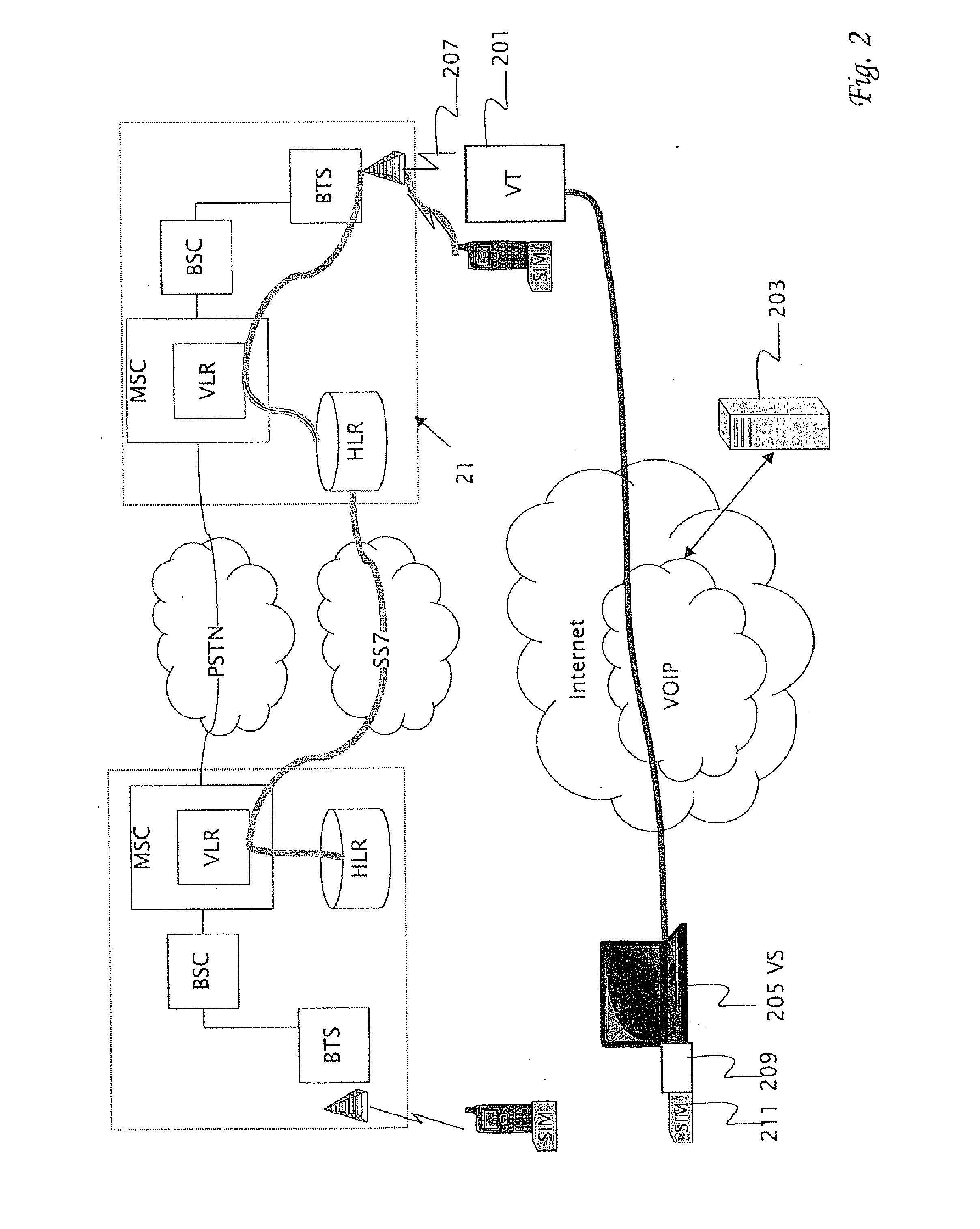
Bridging between a mobile cellular telephone network and a data, voice over internet protocol (VOIP) network
InactiveUS20090225736A1Unauthorised/fraudulent call preventionEavesdropping prevention circuitsWide areaMobile phone operator
A method for providing telephone communications in a system including a wide area data network and a wireless cellular mobile telephone network. A local cellular mobile telephone operator serves the wireless cellular mobile telephone network by providing a radio communications interface within a local region. The local cellular mobile telephone operator issues a subscriber identity module (SIM) to a user of the wireless cellular mobile telephone network. A communications terminal interfaces to the wide area data network using a radio interface to a base transceiver station (BTS) of the wireless cellular mobile telephone network within the local region. The communications terminal includes a communications module for handling a telephone communication through the wide area data network and the wireless cellular mobile telephone network. The communications terminal includes a subscriber identity module (SIM) emulator. A client computer is attached to the wide area data network at a remote site outside the local region. The client computer includes a subscriber identity module (SIM) reader. Telephone communications are provided by (a) inserting the SIM card into the SIM reader (b) transferring SIM identification data of the SIM card to the terminal over the wide area data network and (c) emulating the SIM card based on the SIM identification data. The emulation is performed by the emulator at the communications terminal. The SIM data is provided to the wireless cellular mobile telephone network operator within the local region over the radio communications interface.
Owner:PATARKAZISHVILI PINHAS
Simultaneous VoLTE and 2G/3G/LTE Data in Dual SIM Configuration
ActiveUS20160029222A1Connection managementCommmunication supplementary servicesRadio access technologyVoice communication
A user equipment (UE) device may perform uplink (UL) data communication using a first radio access technology (RAT) while performing an UL voice call communication using a second RAT. The UL data communication may be supported by a first subscriber identity module (SIM) and the UL packet switched voice call communication may be supported by a second SIM. The UL voice call communication may be a packet switched communication. The communications may be performed by a radio(s) of the UE. The radio(s) may include shared physical layer resources that are shared between the UL data and UL voice communications. The UE may also include a single transmitter that may be shared between the UL data and UL packet voice communications and the UL data communication may use a first portion of the single transmitter's TTI and the UL voice communication may use a second portion of the single transmitter's TTI.
Owner:APPLE INC
Subscriber identity module and method of preventing access thereto, and mobile communication terminal device
InactiveUS20050143059A1Low costAvoid accessUnauthorised/fraudulent call preventionInternal/peripheral component protectionThird partyTerminal equipment
A subscriber identity module (SIM) for subscriber identification configured so as to be detachably loaded on a mobile communication terminal device has a application section for storing an externally downloaded application program, a processing section (or a SAT function section) for executing this application program, a storage section for storing file administrative description, file description, and file data, and file administration section for administering these information and data. The processing section, after the downloading of the application program, executes the downloaded application program to control the file administration section. Consequently, access to the data stored in the subscriber identity module is prevented, thereby preventing the third party to access the data stored in the subscriber identity module of the lost or stolen mobile communication terminal.
Owner:SONY MOBILE COMM INC
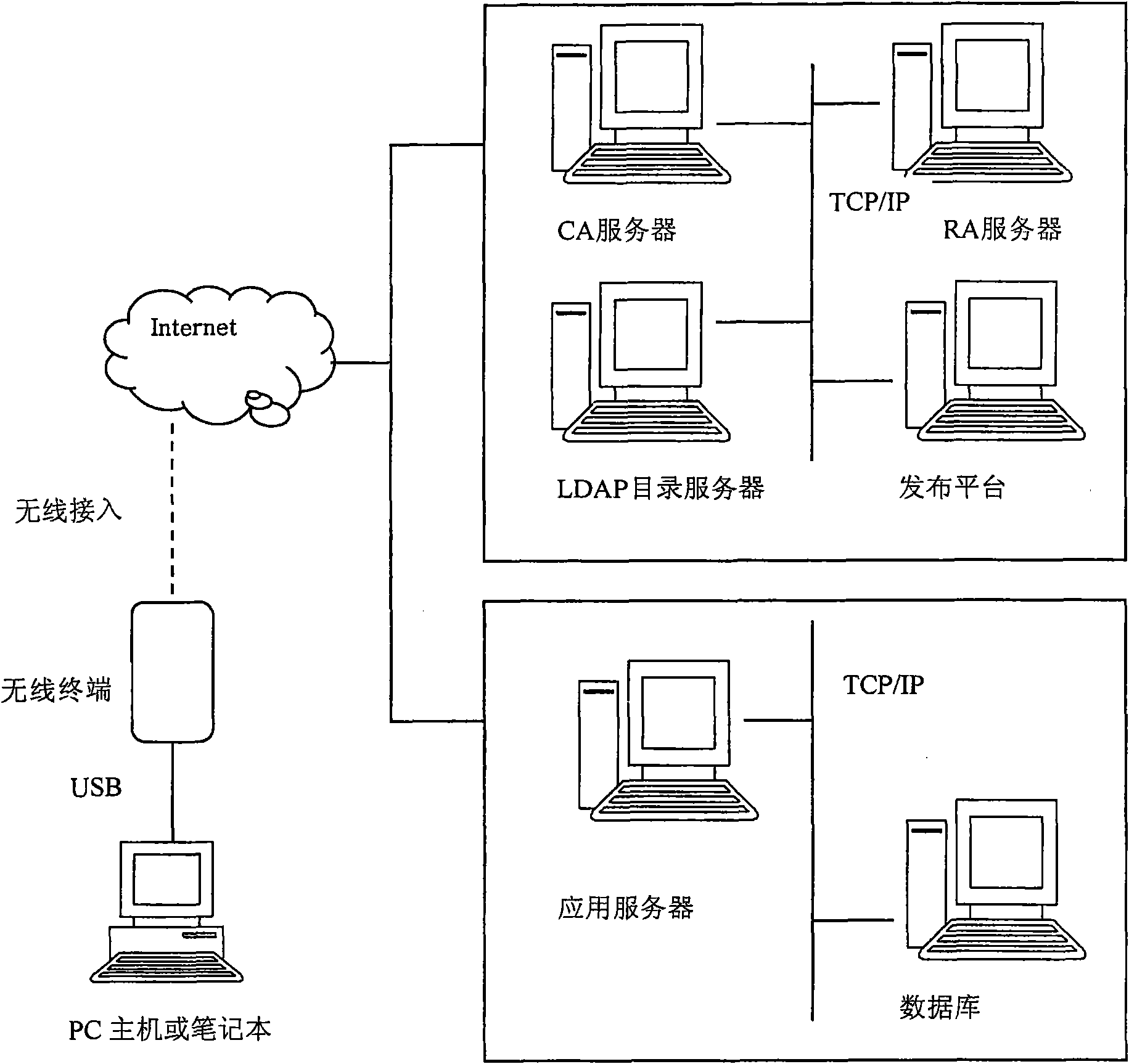
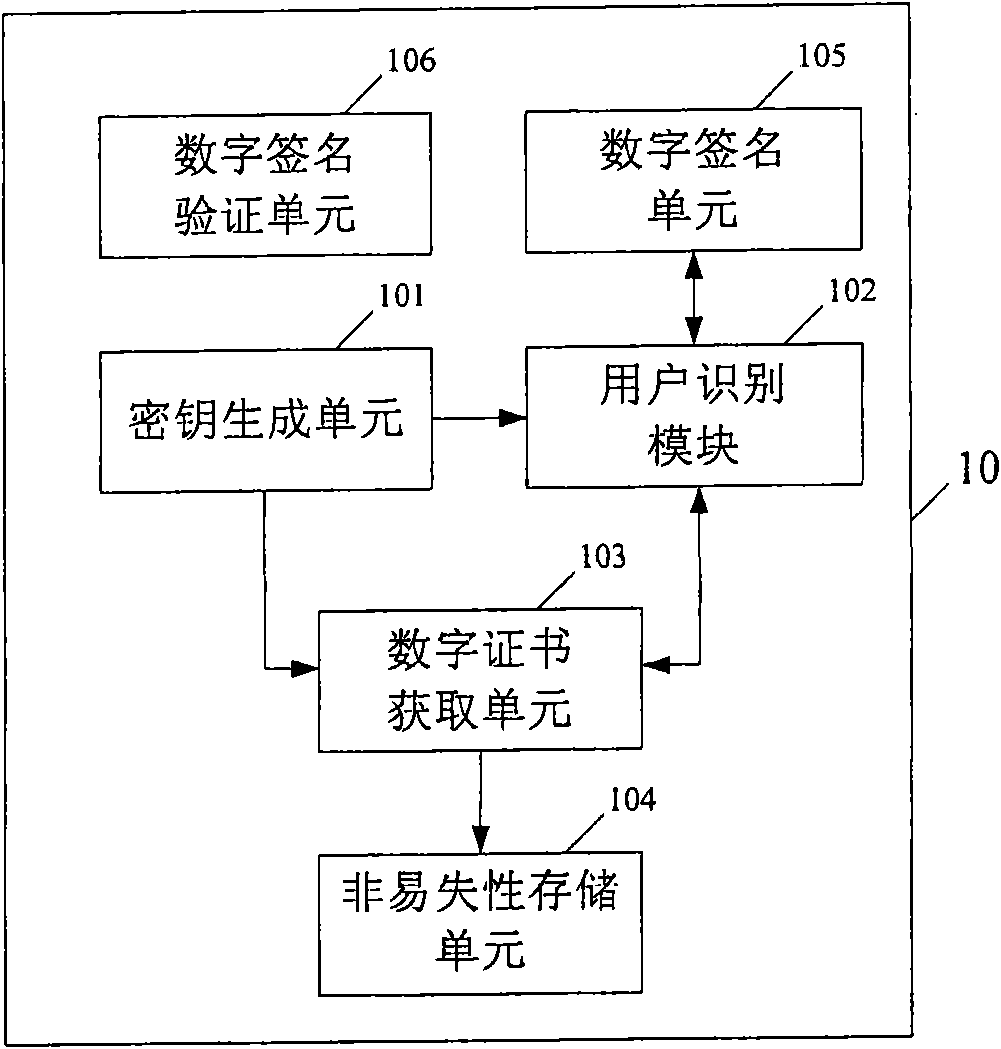
Method and system based on wireless terminal for applying digital certificate and wireless terminal
ActiveCN101777978AImprove securitySave storage spaceUser identity/authority verificationAuthentication serverCertificate server
The embodiment of the invention provides a method and a system based on a wireless terminal for applying a digital certificate and a wireless terminal. The method comprises the following steps: generating a key pair, a private key of the key pair is stored in a user identity module of the wireless terminal; sending a public key of the key pair, a user identity module number, application certificate information of user information to a certificate server; receiving a digital certificate issued by the certificate server; and storing the digital certificate into a nonvolatile storage of the wireless terminal. The technical scheme of the embodiment of the invention adopts the method separately storing the private key and the digital certificate to store the private key into an SIM card and store the digital certificate into a FLASH. Since the digital certificate can prove the hard core of a user ID to be the private key, the mode of storage can improve the safety of the private key.
Owner:HUAWEI DEVICE (SHENZHEN) CO LTD
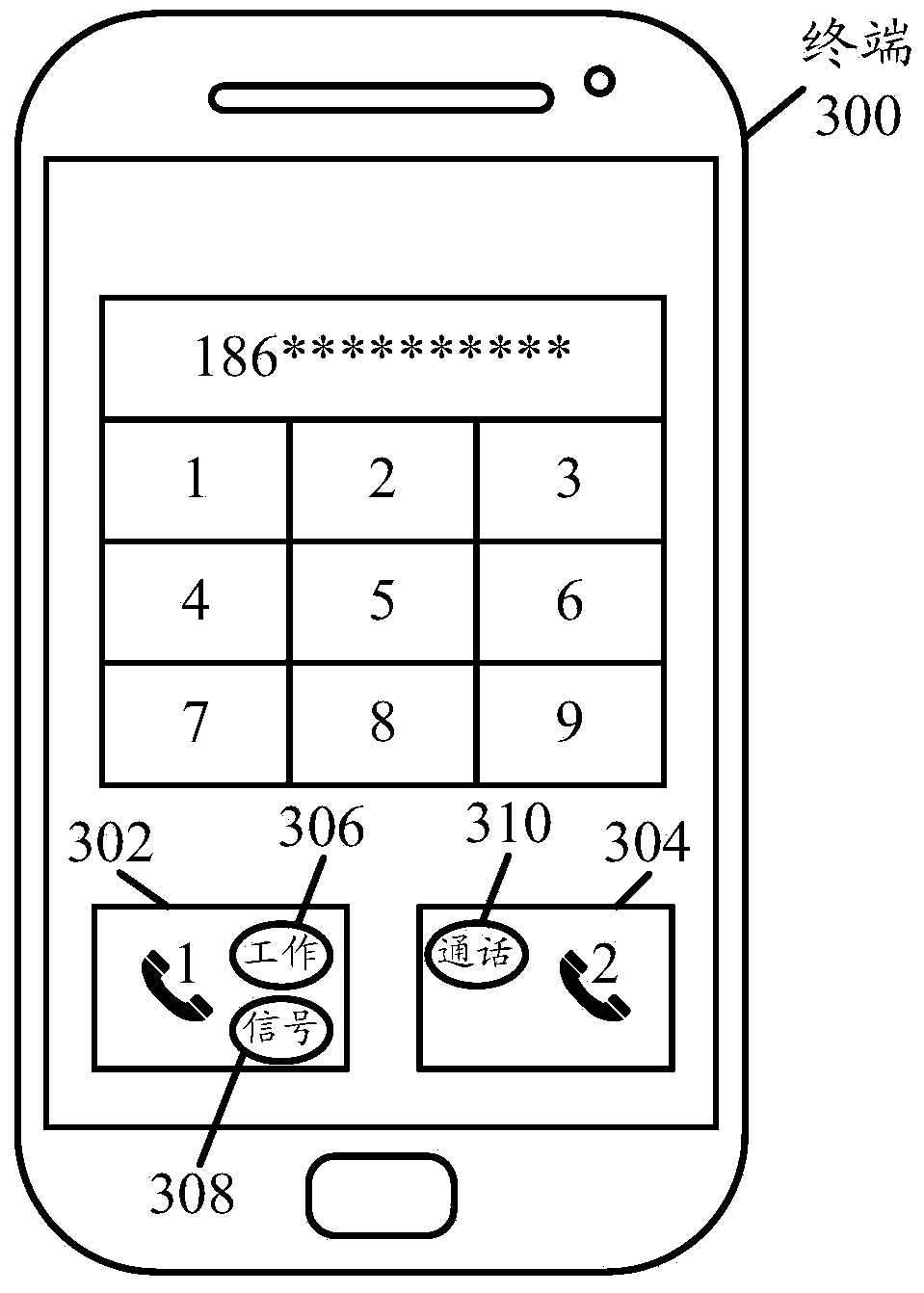
Method and system of implementing an advanced multifunctional dialer capable of managing multiple calling accounts
ActiveUS20200007675A1Easy to identifyAccounting/billing servicesSpecial service for subscribersGraphical user interfaceDialer
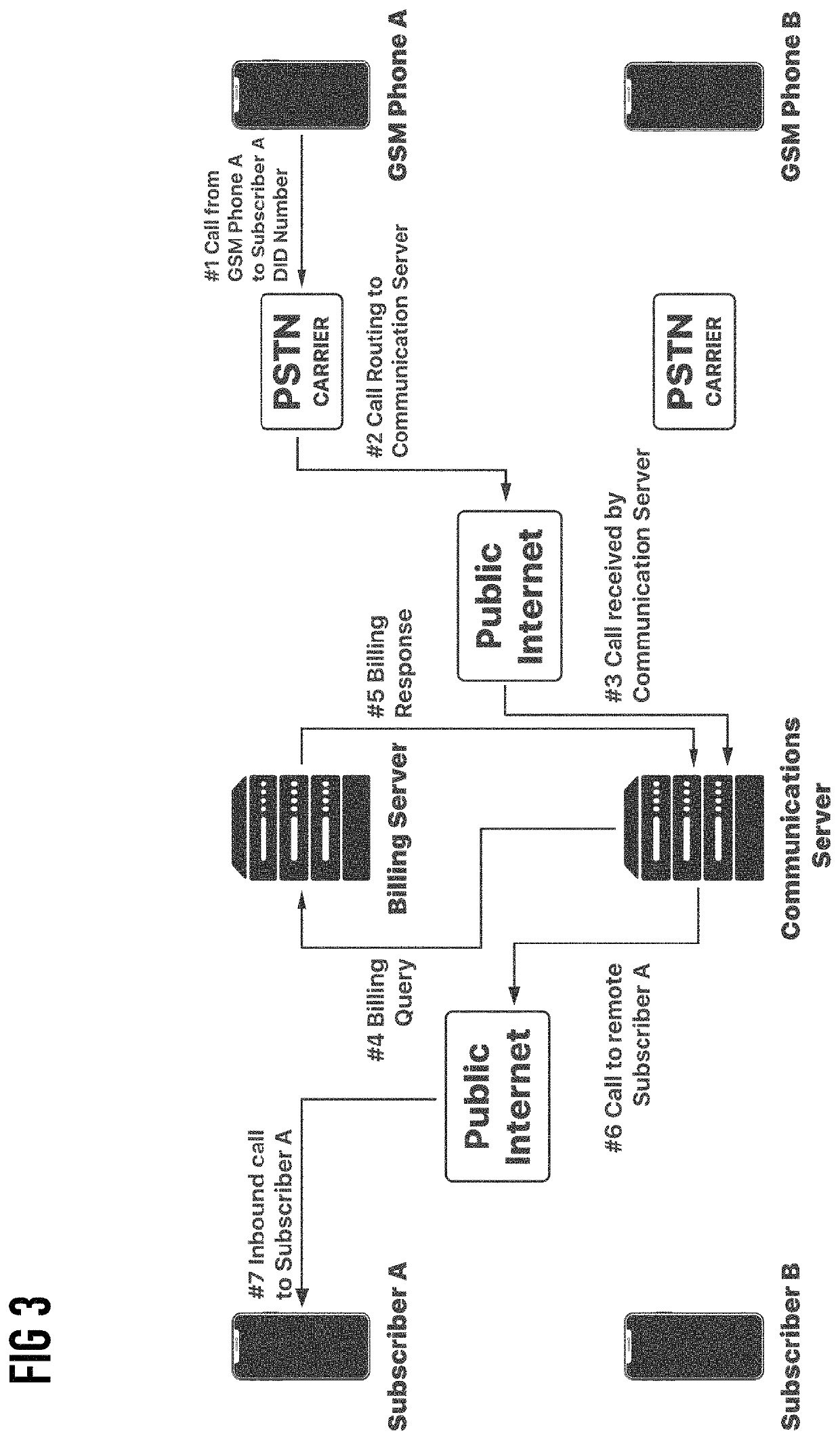
A method, system and graphical user interface (GUI) for a mobile device, the GUI including: (a) at least one multifunctional button having at least two activation states: (i) a first state, when actuated, providing a basic function, and (ii) a second state, when actuated, providing an advanced function; whereby each of the activation states is actuated by a different user action; and (b) a plurality of calling accounts, each of the plurality of calling account being logically associated with a subscriber identity module (SIM) card or a direct inward dial (DID) number; wherein the at least one multifunctional button is configured to facilitate selection of one of the plurality of calling accounts in order to perform a communication event.
Owner:KHANUKAEV OLEG
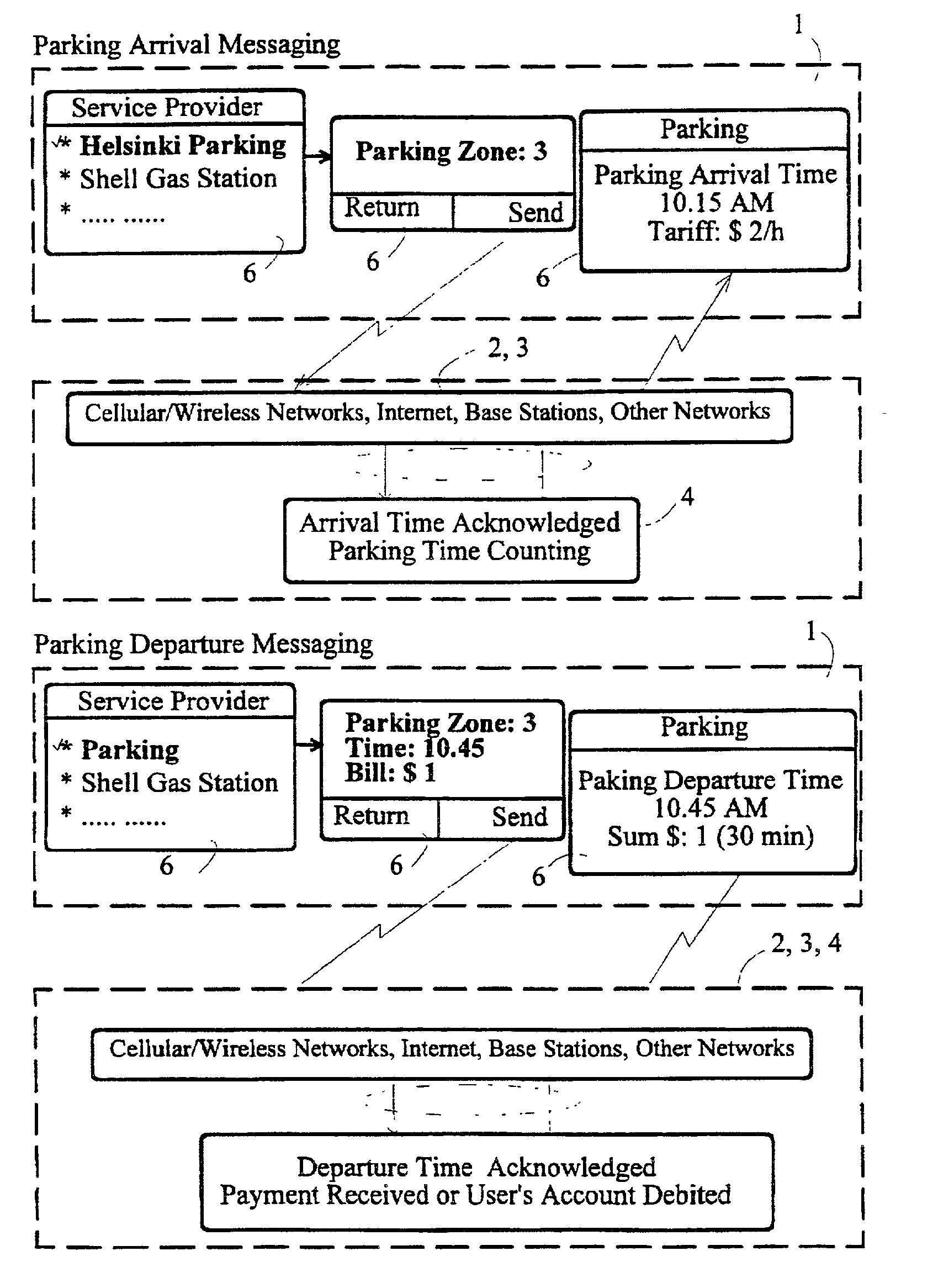
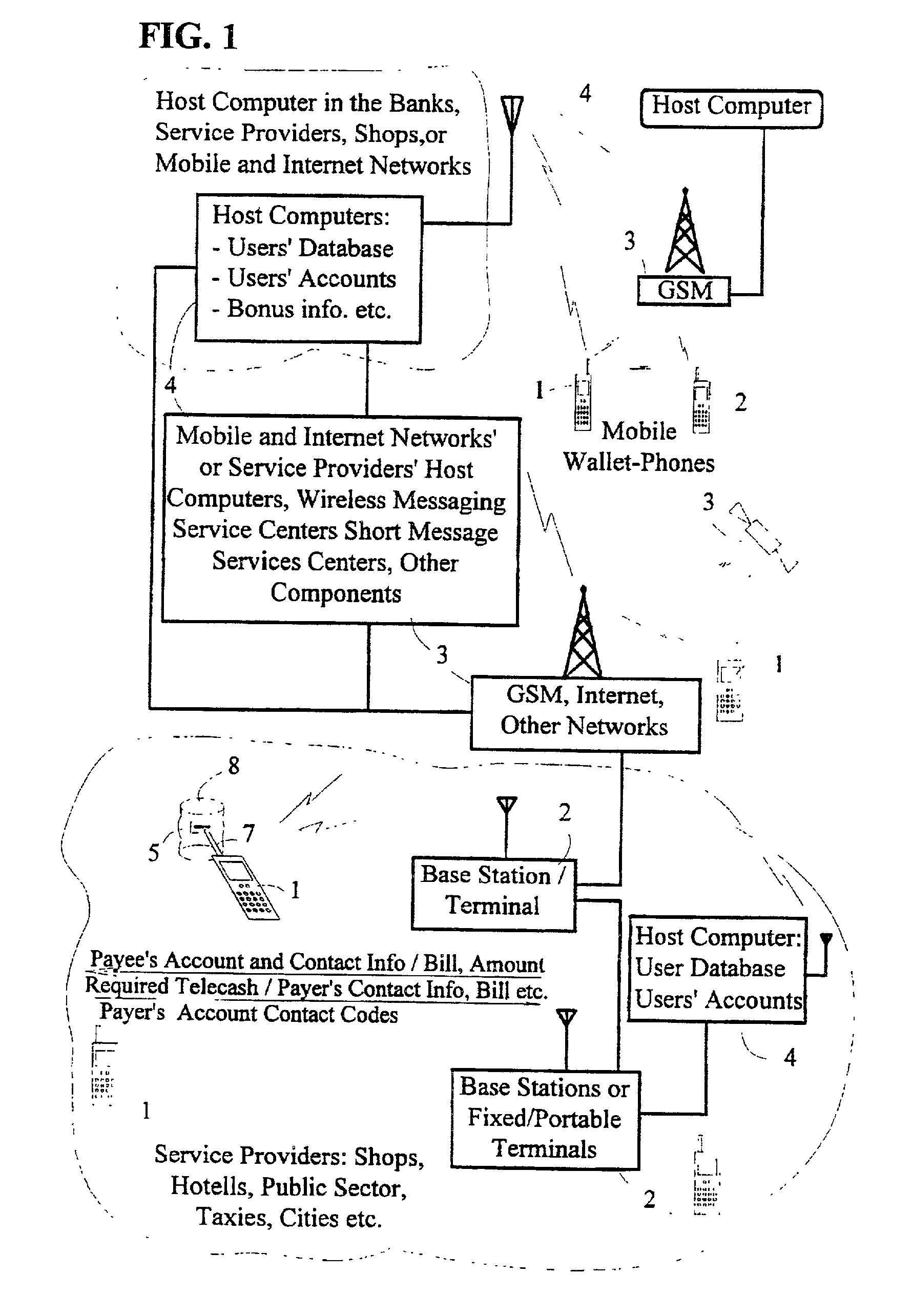
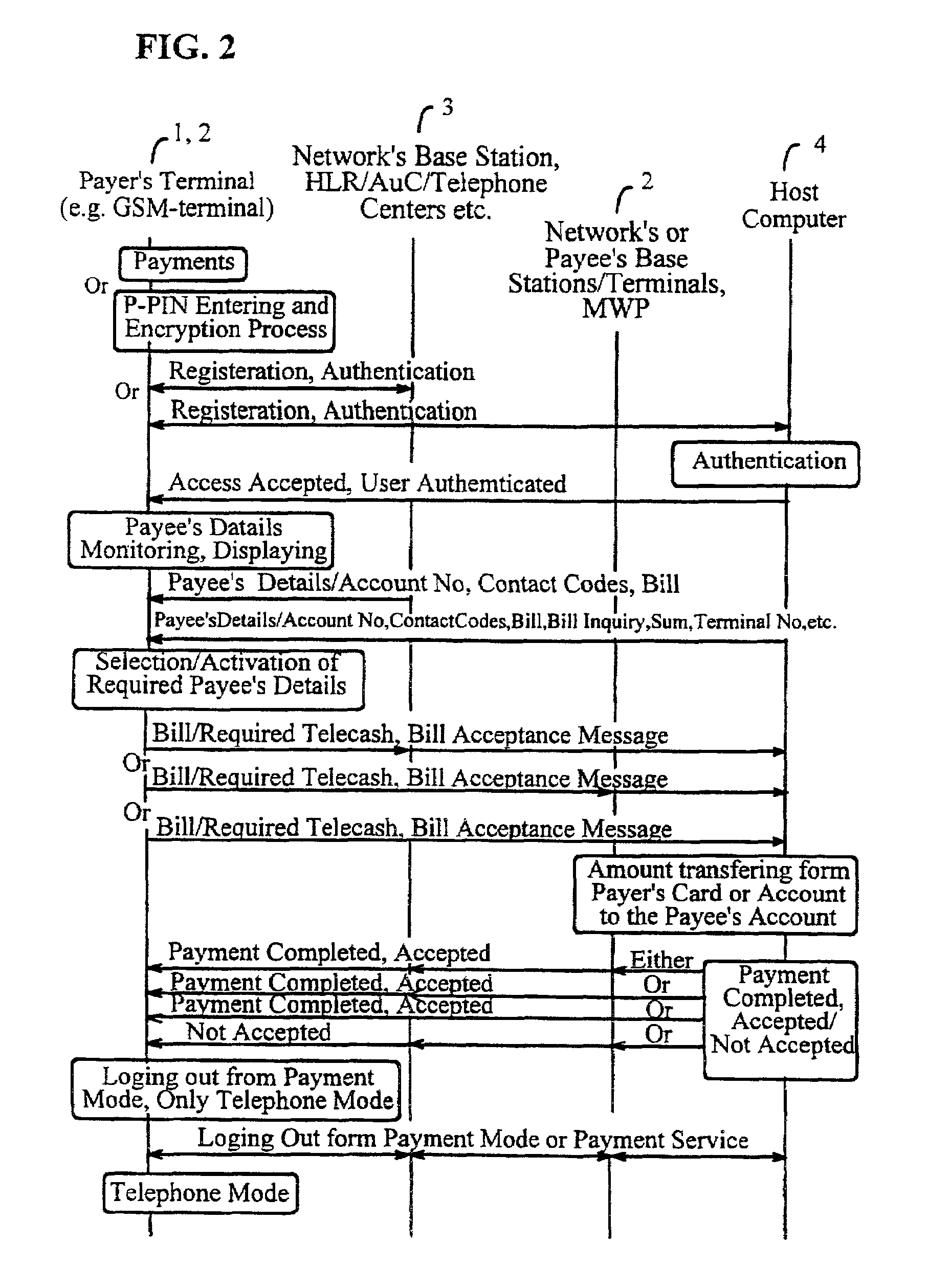
System and method for implementing secure mobile-based transactions in a telecommunication system
InactiveUS20030008637A1Easy to implement payment applicationSimplify verification operationsUnauthorised/fraudulent call preventionEavesdropping prevention circuitsUser inputDigital signature
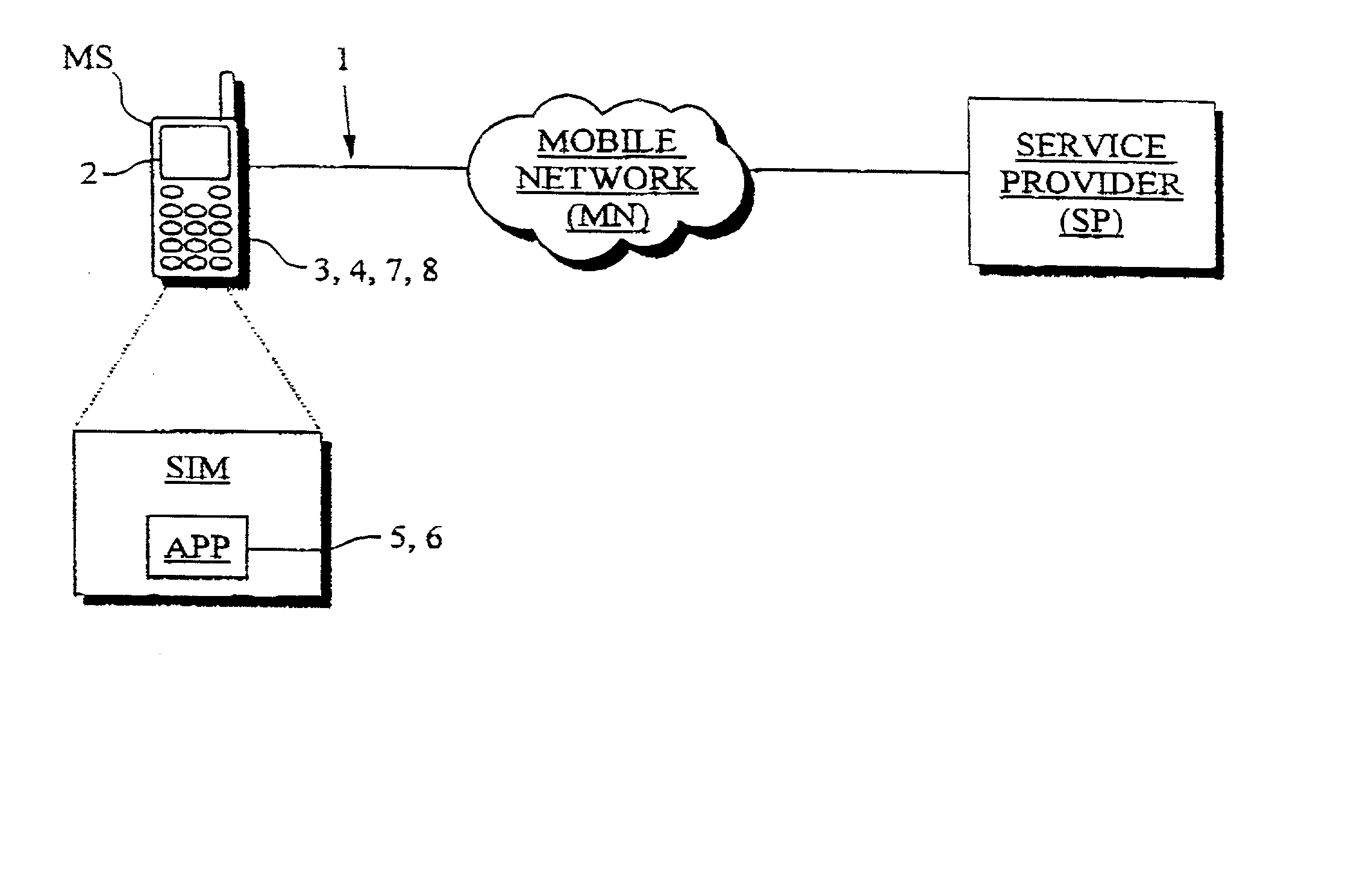
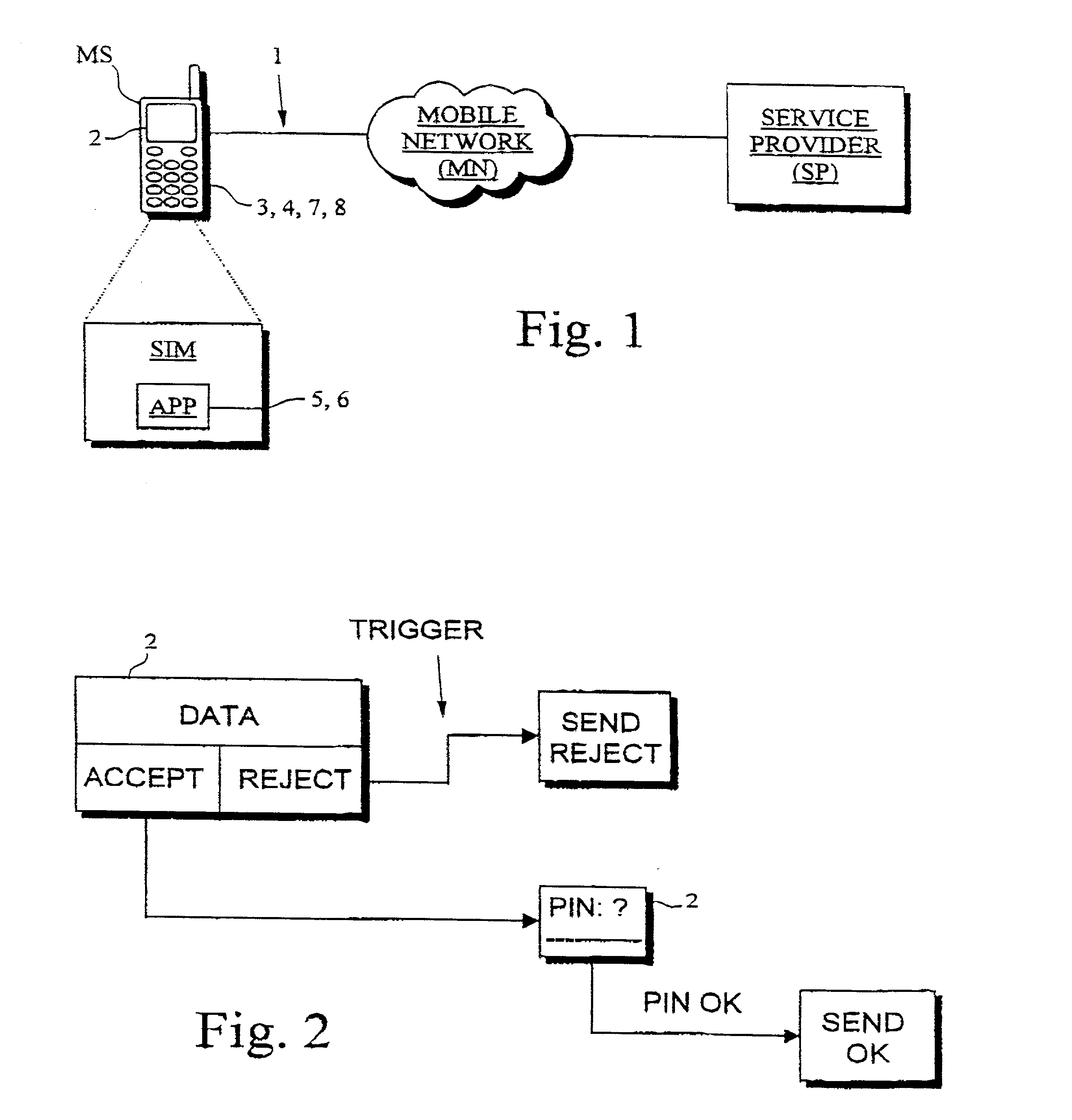
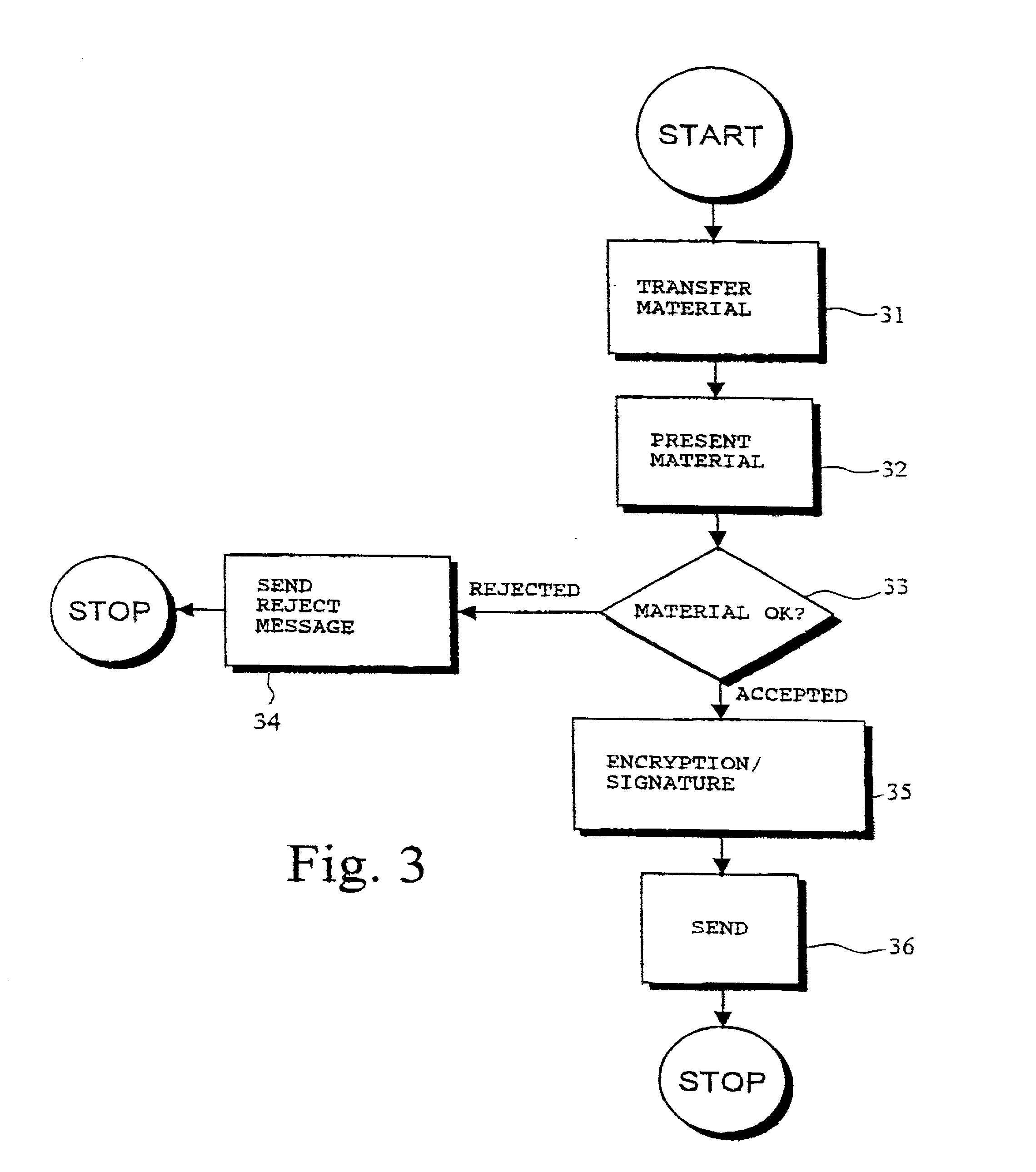
A system for implementing secure transactions includes a mobile communication network, a service provider communicating with the mobile communication network and a mobile station communicating with the mobile network and, through the network, with the service provider. A subscriber identity module, in which an executable service application is stored, is associated with the mobile station. The system further includes means for transferring the material needed in implementing the transaction into the mobile station, means in the mobile station for presenting the transferred material to the user, means for requesting the user's acceptance of the presented material for digital signing, means for activating a PIN inquiry if the user accepts the material, means for checking, in the subscriber identity module, the correctness of the PIN code entered by the user, and means for encrypting and / or digitally signing the transmitted material using the service application stored in the subscriber identity module if the PIN code entered by the user is correct.
Owner:SONERA SMARTTRUST LTD
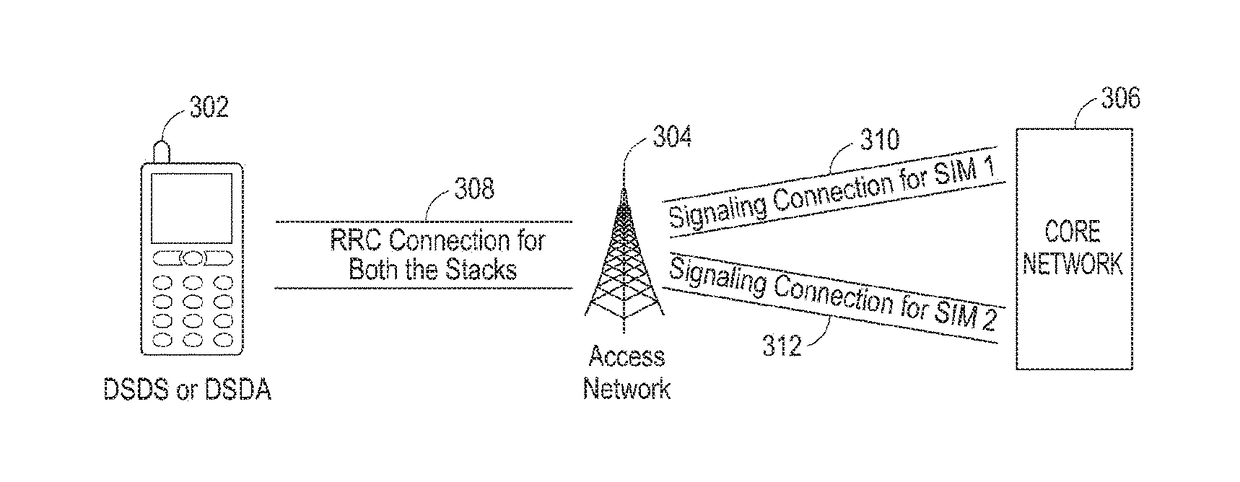
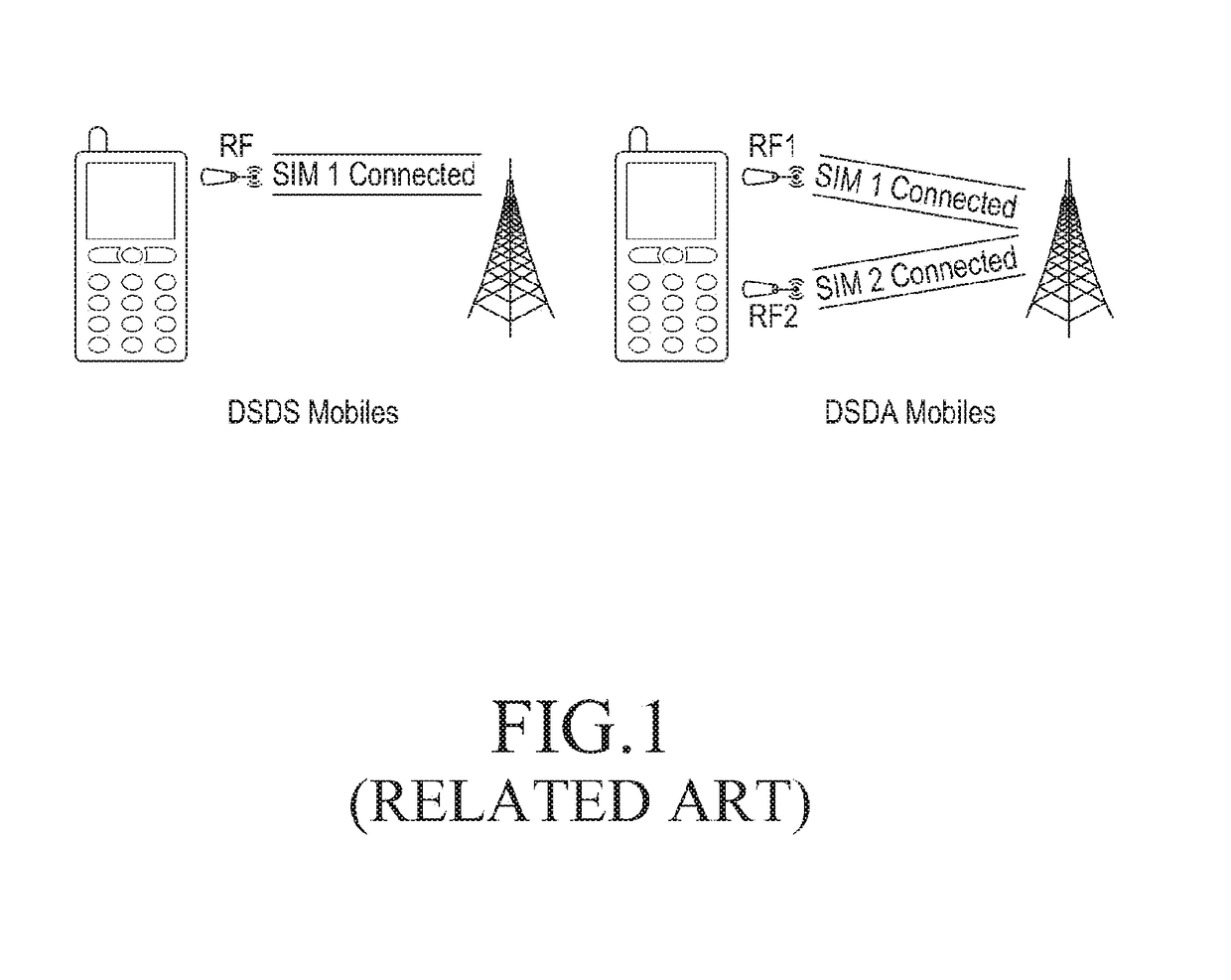
Methods and apparatus to support parallel communication for multiple subscriber identities in a wireless communication device
Apparatus and methods to support parallel communication using multiple subscriber identities in a wireless communication device via multiple subscriber identity modules (SIMs) are disclosed. A representative method includes establishing a connection with a first wireless network via a first wireless cellular protocol software stack for a first subscriber identity associated with a first subscriber identity module; registering with a second wireless network via a second wireless cellular protocol software stack for a second subscriber identity associated with a second subscriber identity module; and receiving radio frequency signals from the second wireless network via the second wireless cellular protocol software stack in parallel with communicating with the first wireless network via the first wireless cellular protocol software stack. The first and second wireless cellular protocol software stacks share at least a portion of radio frequency wireless circuitry for communicating with the first and second wireless network respectively.
Owner:APPLE INC
Secure virtual transfer of subscriber credentials
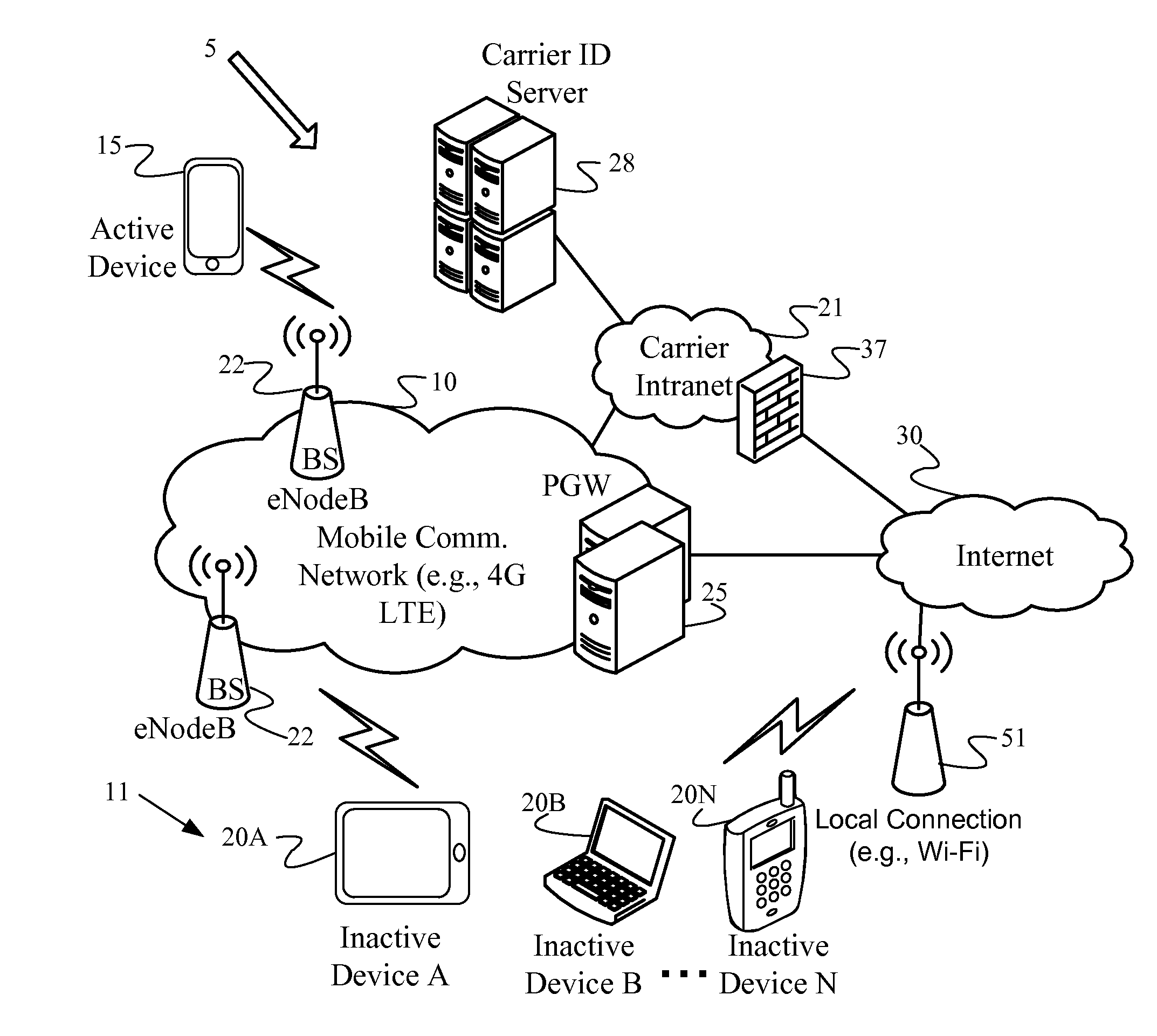
ActiveUS20160164883A1Digital data processing detailsMultiple digital computer combinationsTransport layerInternational mobile subscriber identity
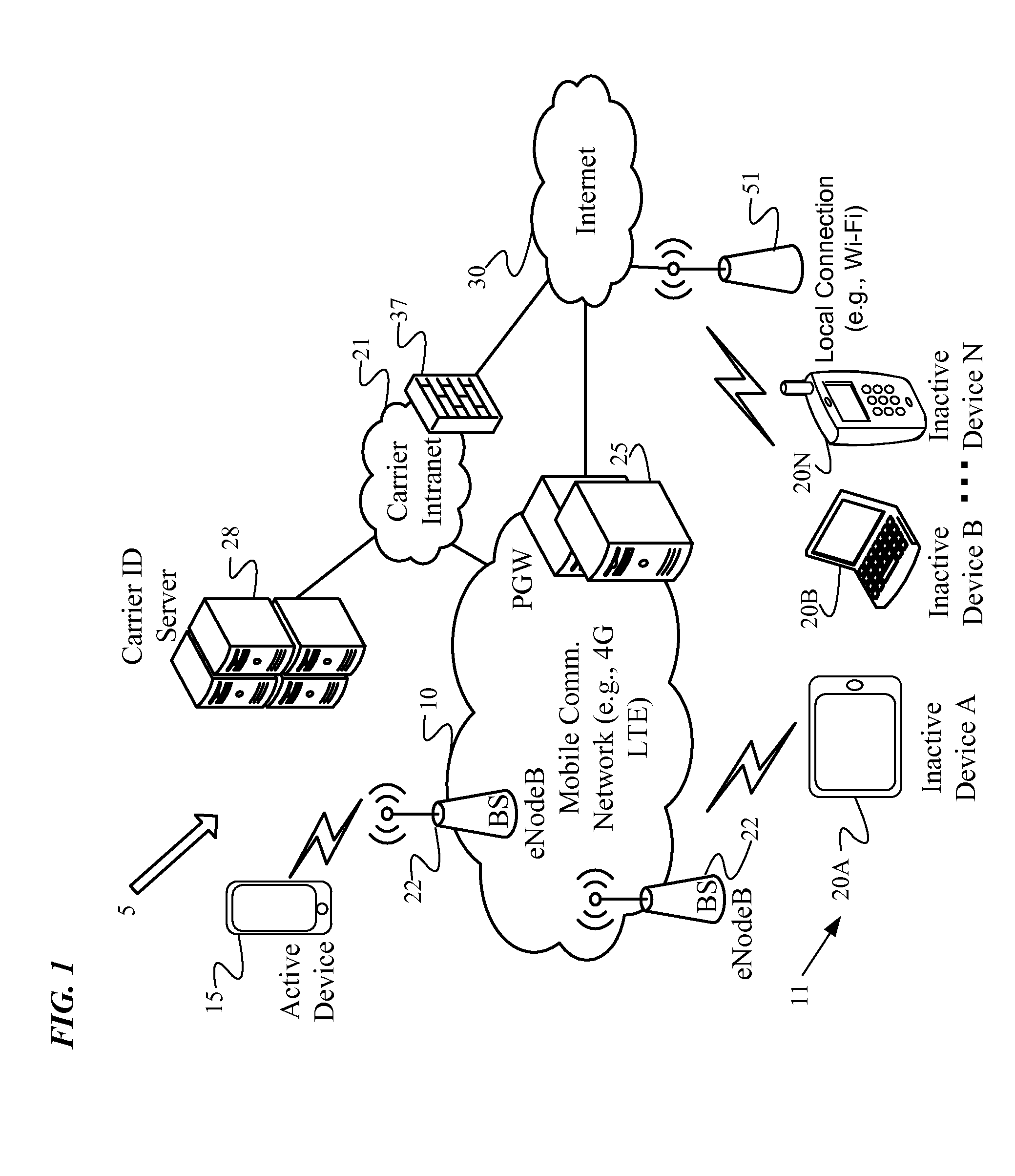
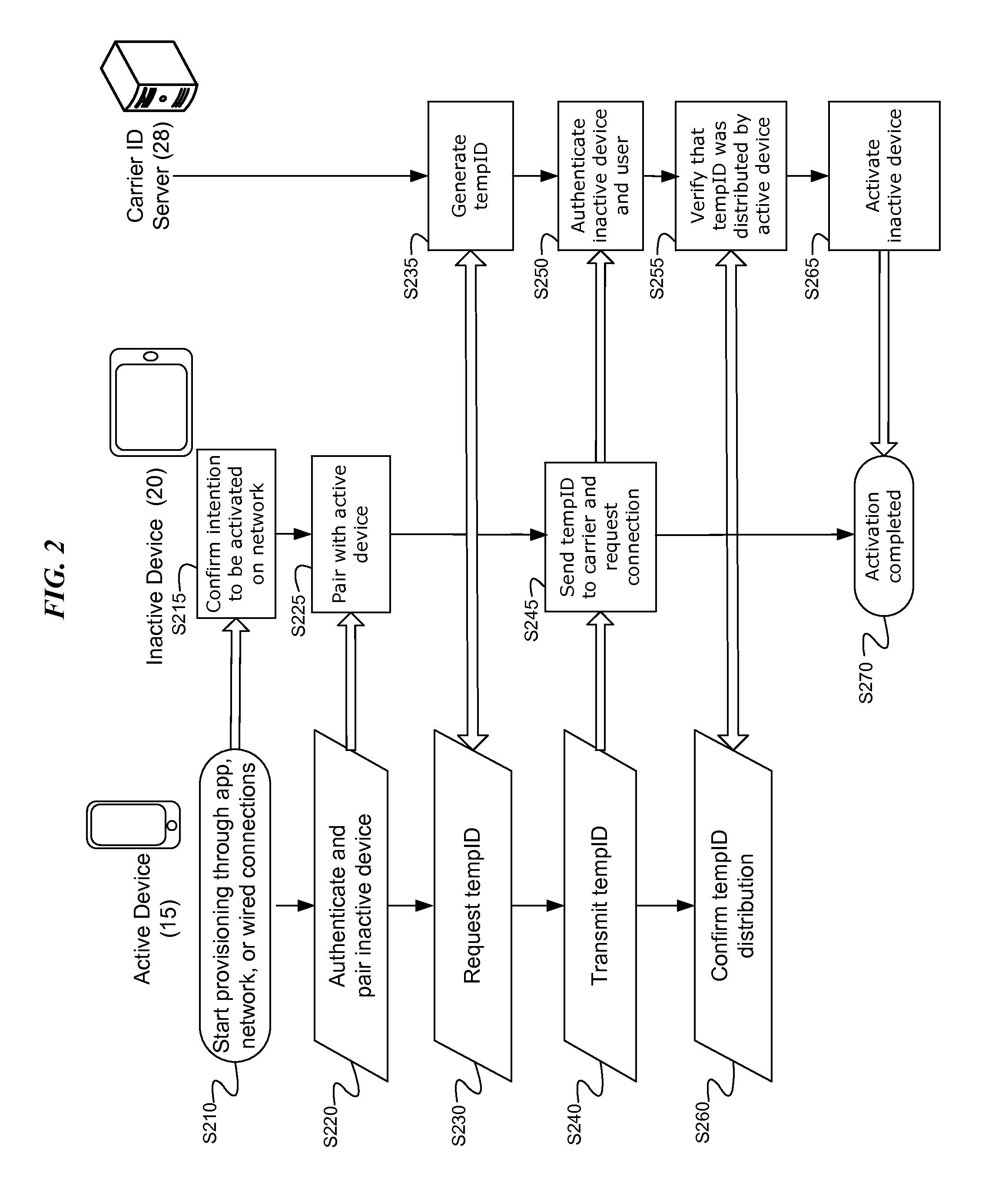
To virtually transfer subscriber identity module (“SIM”) credentials from an active device to an inactive device in order to share carrier network access, temporary identifiers and SIM credentials are transferred using secure connections and an optional public-private key pair with encryption at the transport layer. In an example, a carrier identification (“ID”) server receives a temporary identifier, such as a temporary international mobile subscriber identity (“TIMSI”), from an inactive device via a carrier network. The carrier ID server authenticates the inactive device using the TIMSI by issuing a network challenge. Next, the carrier ID server verifies with an active device associated with the inactive device that the active device distributed the TIMSI. After authenticating and verifying with both devices, the carrier ID server activates the inactive device by allowing the TIMSI to behave as virtual SIM credentials on the carrier network.
Owner:VERIZON PATENT & LICENSING INC
Telecommunications System
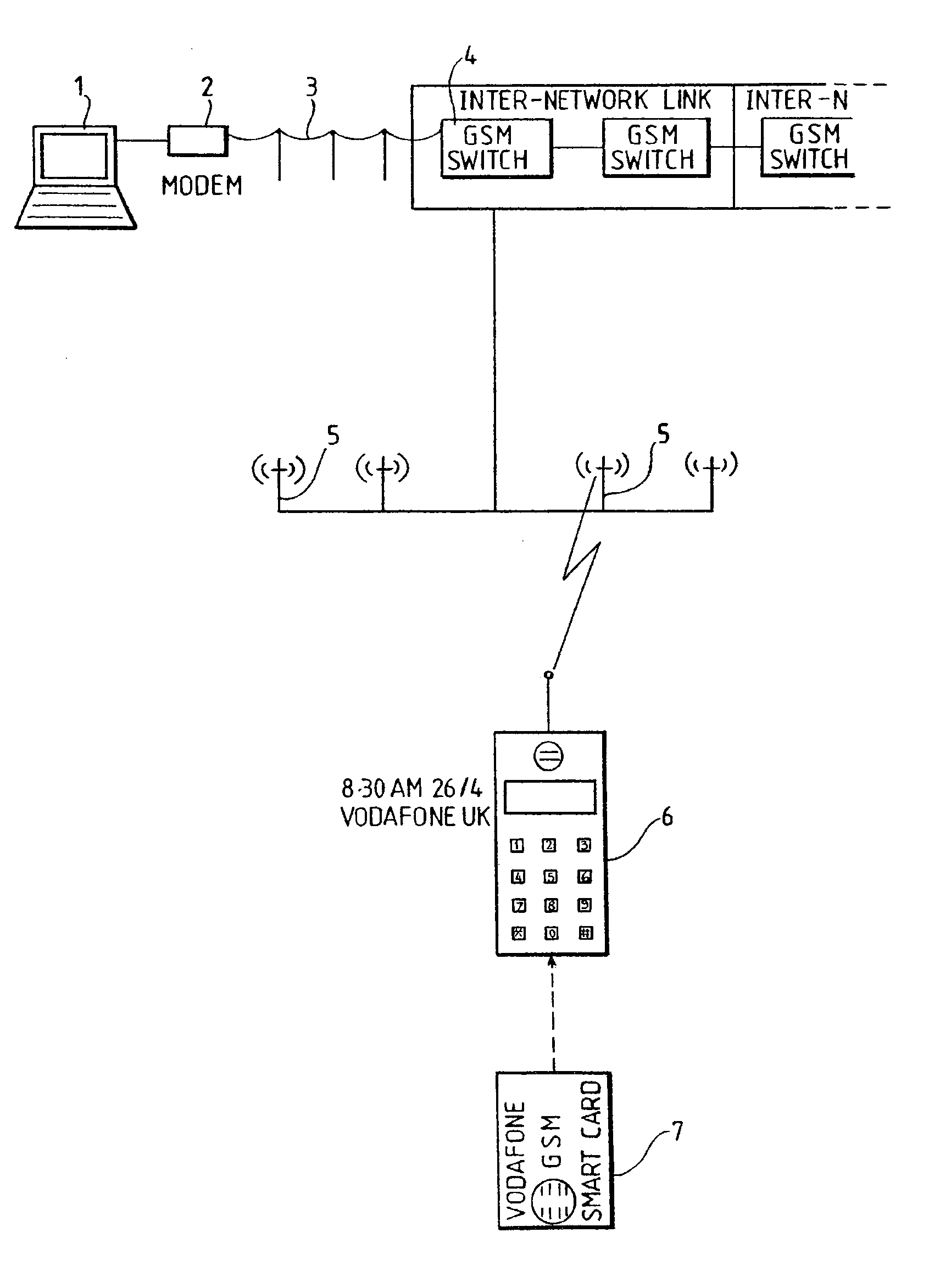
InactiveUS20050026635A2Easy accessConvenient transactionDevices with card reading facilityNetwork topologiesPersonal identification numberUser input
Abstract of the DisclosureIn a telecommunications system such as a global mobile telephone network in which each subscriber unit includes a Subscriber Identity Module (SIM card), each SIM card has fixed memory locations, to which data can be addressed over the air. Some of the locations can not be overwritten from the subscriber unit but can be accessed therefrom on the entry of short simple codes, each associated with one of the locations. Further fixed memory locations can be read over the air only when the subscriber enters a personal identification number. Locking control files are used to control read / write access to the locations respectively.
Owner:RPX CORP +1
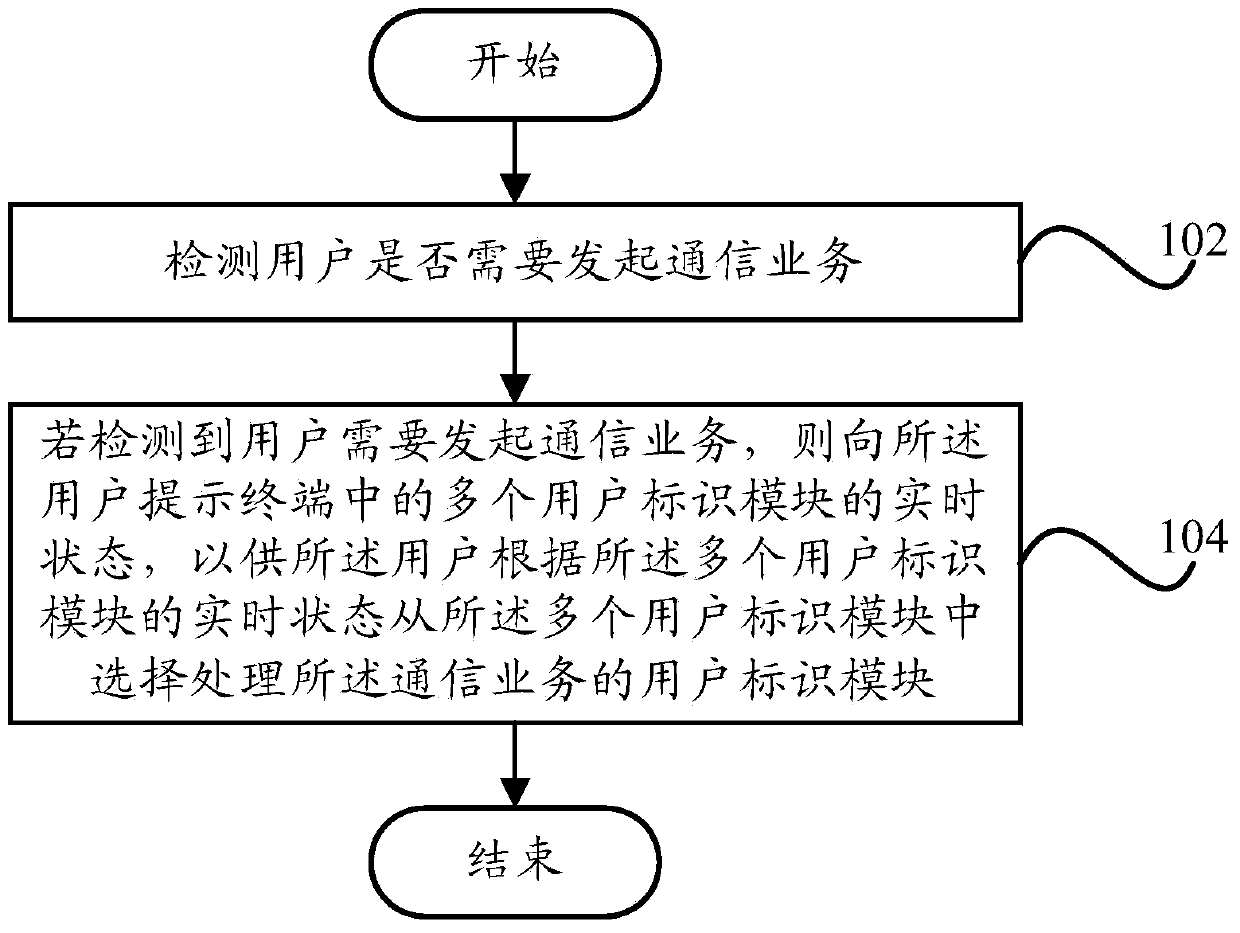
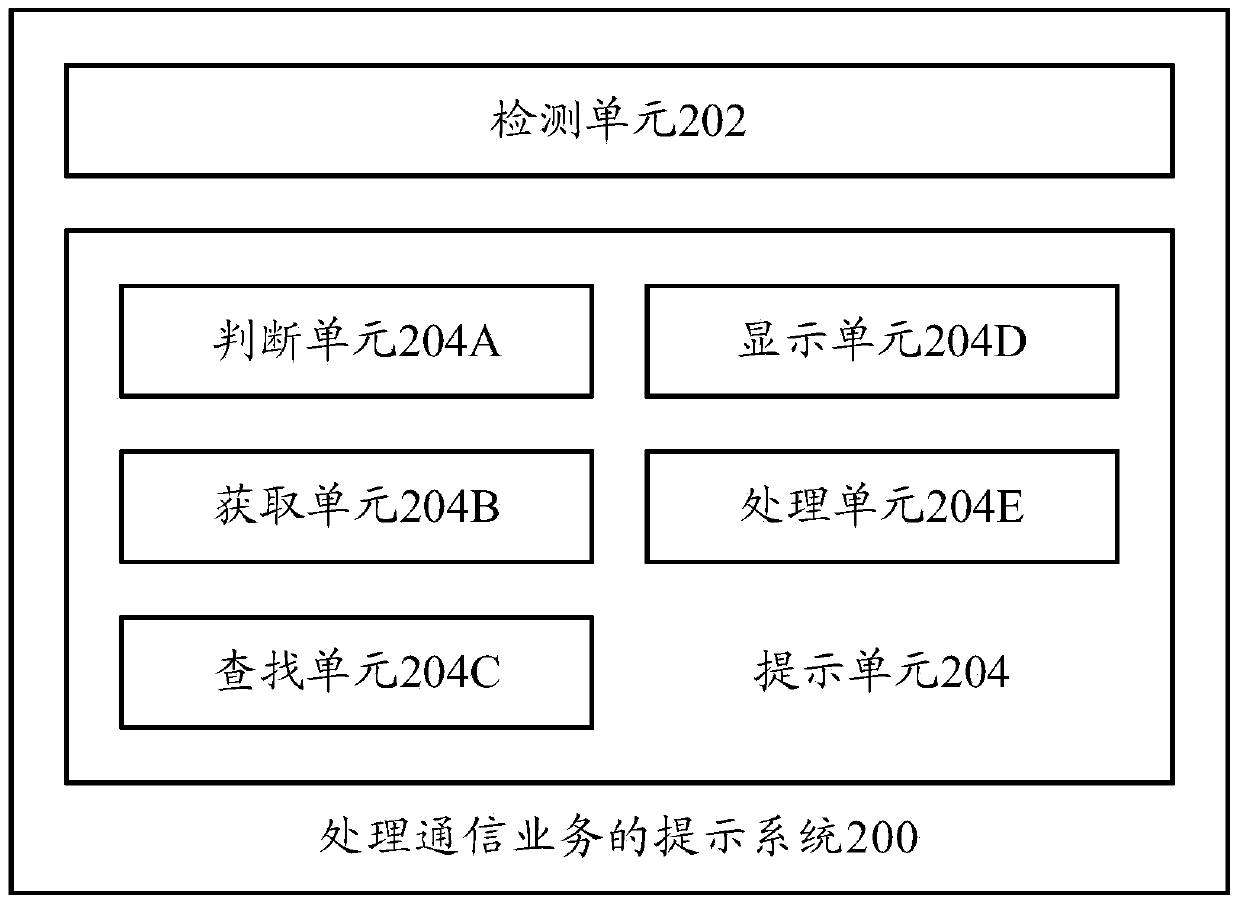
Prompting method, prompting system and terminal for processing communication service
ActiveCN103747152AAffect the use effectIntuitive graspSpecial service for subscribersUser needsComputer terminal
The invention provides a prompting method for processing communication service, a prompting system for processing the communication service and a terminal. The prompting method for processing the communication service comprises the following steps of detecting whether a user needs to initiate the communication service or not; prompting the real-time state of a plurality of user identity modules in the terminal to the user if the user needs to initiate the communication service, so that the user can select the user identity module from multiple user identity modules to process the communication service according to the real-time state of the user identity module. Through the technical scheme, the state information of each SIM (subscriber identity module) card can be intuitively and clearly controlled by the user, so that the appropriate SIM card is conveniently selected to process the communication service, and the loss caused by mistake selection of the SIM card can be avoided.
Owner:YULONG COMPUTER TELECOMM SCI (SHENZHEN) CO LTD
Method and device for controlling the function of mobile communication equipment
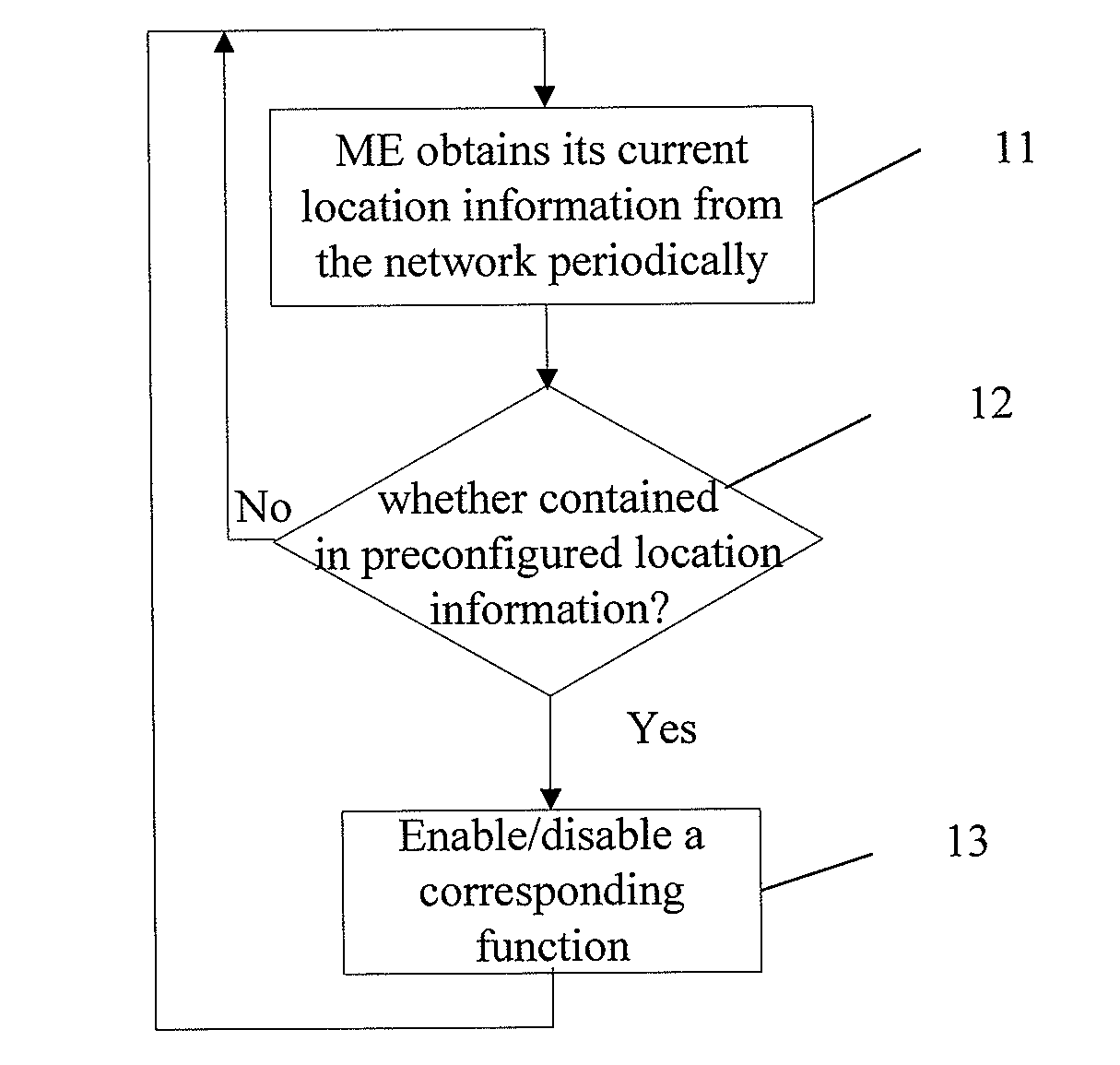
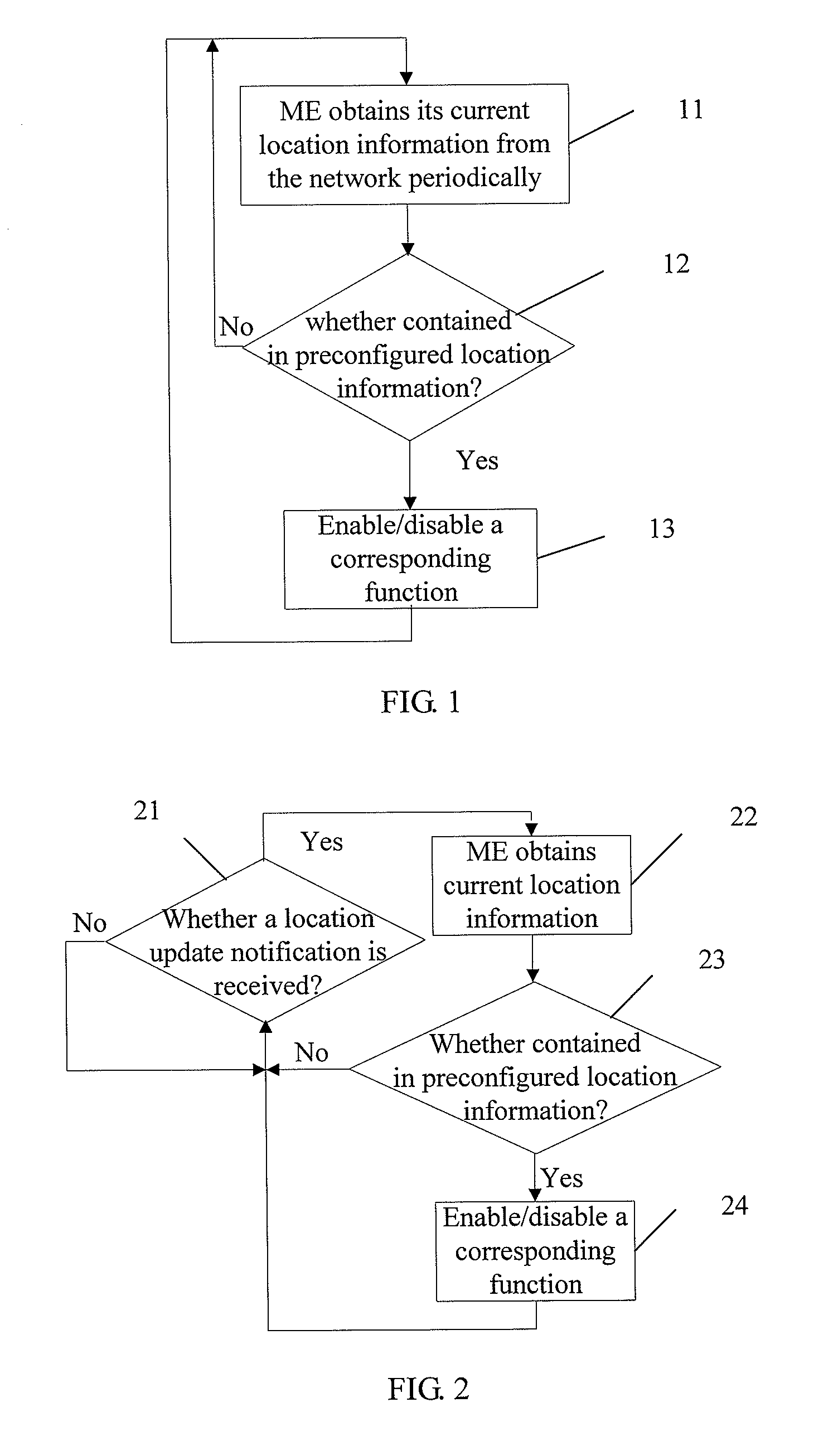
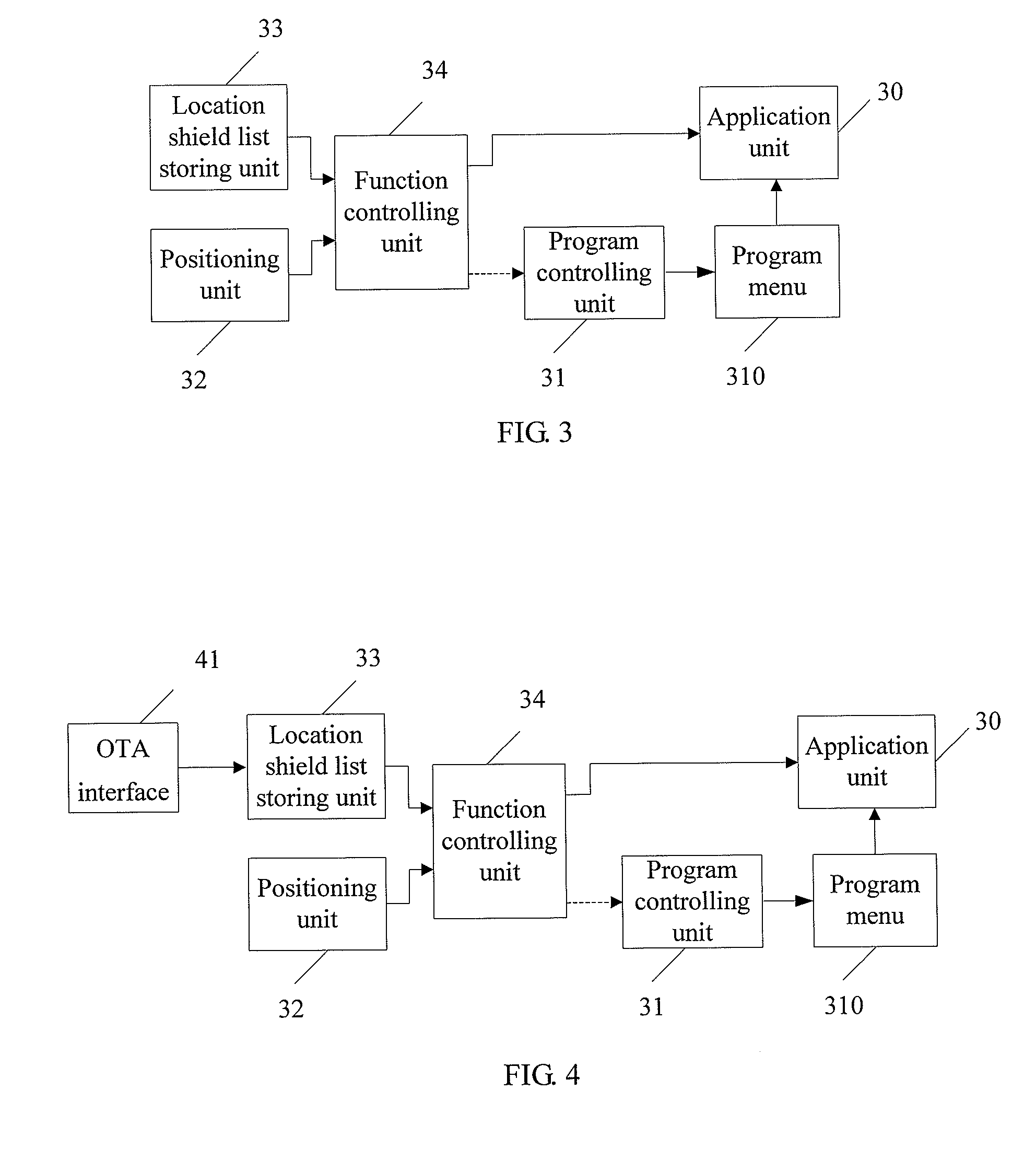
InactiveUS20090082001A1Easy to implementPut into the market rapidlyAssess restrictionDevices with GPS signal receiverTelecommunicationsMobile device
The present invention discloses a method for controlling functions of a mobile equipment. In the method, current location of a mobile equipment is compared with preconfigured location information associated with a function of the mobile equipment and the mobile equipment is controlled, according to a result of the comparing. The present invention may be implemented by an approach that the mobile equipment itself is in control or by an approach that a user identity module or a network is in control on the basis of the existing toolkit technology or over-the-air technology. The present invention also provides device solutions corresponding to the different approaches. With the present invention, an organization may set a restriction for the purpose of information security, while the employees of the organization may use high-end mobile equipments without changing the mobile equipments frequently. A mobile equipment may change its function status depending on different locations.
Owner:HUAWEI TECH CO LTD
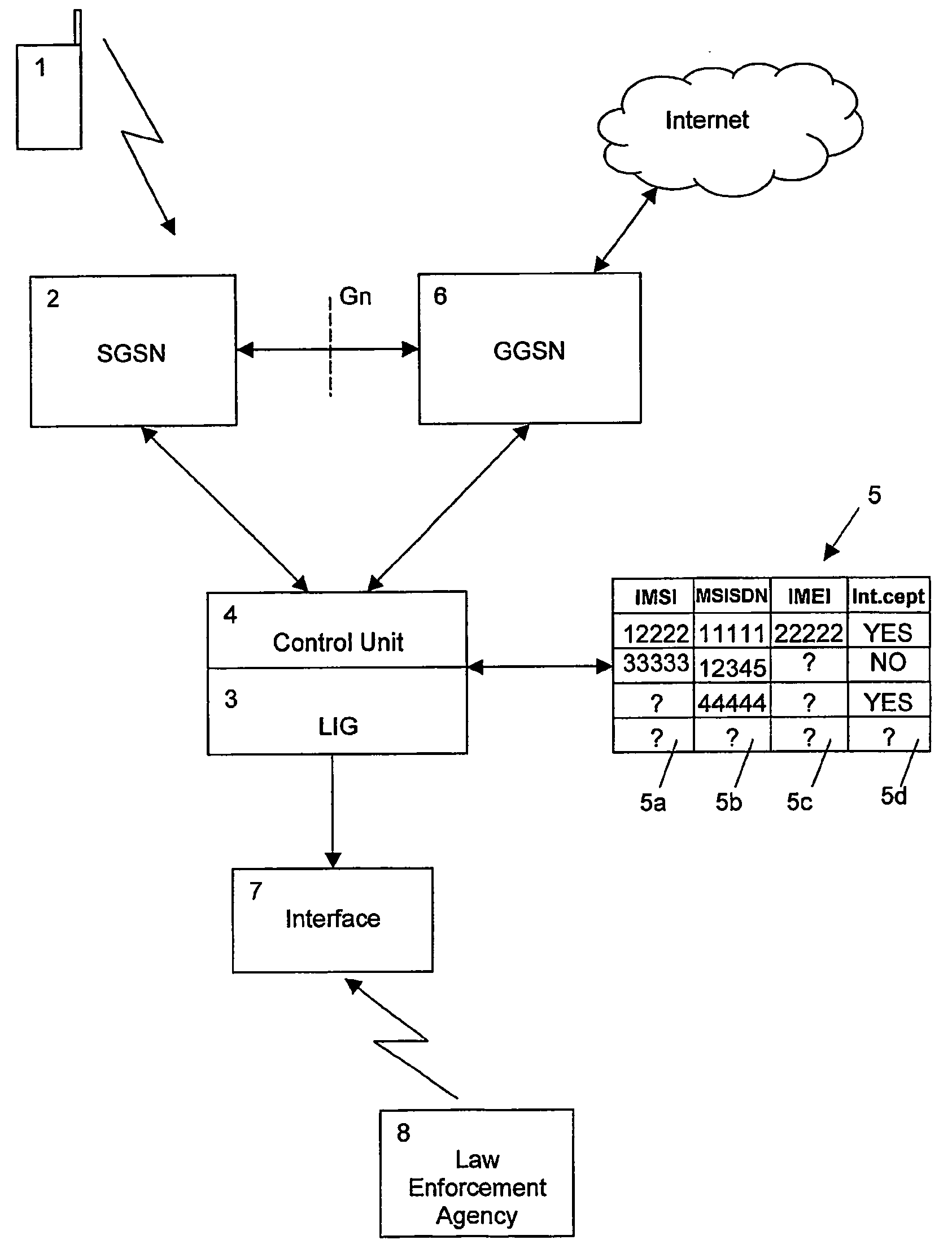
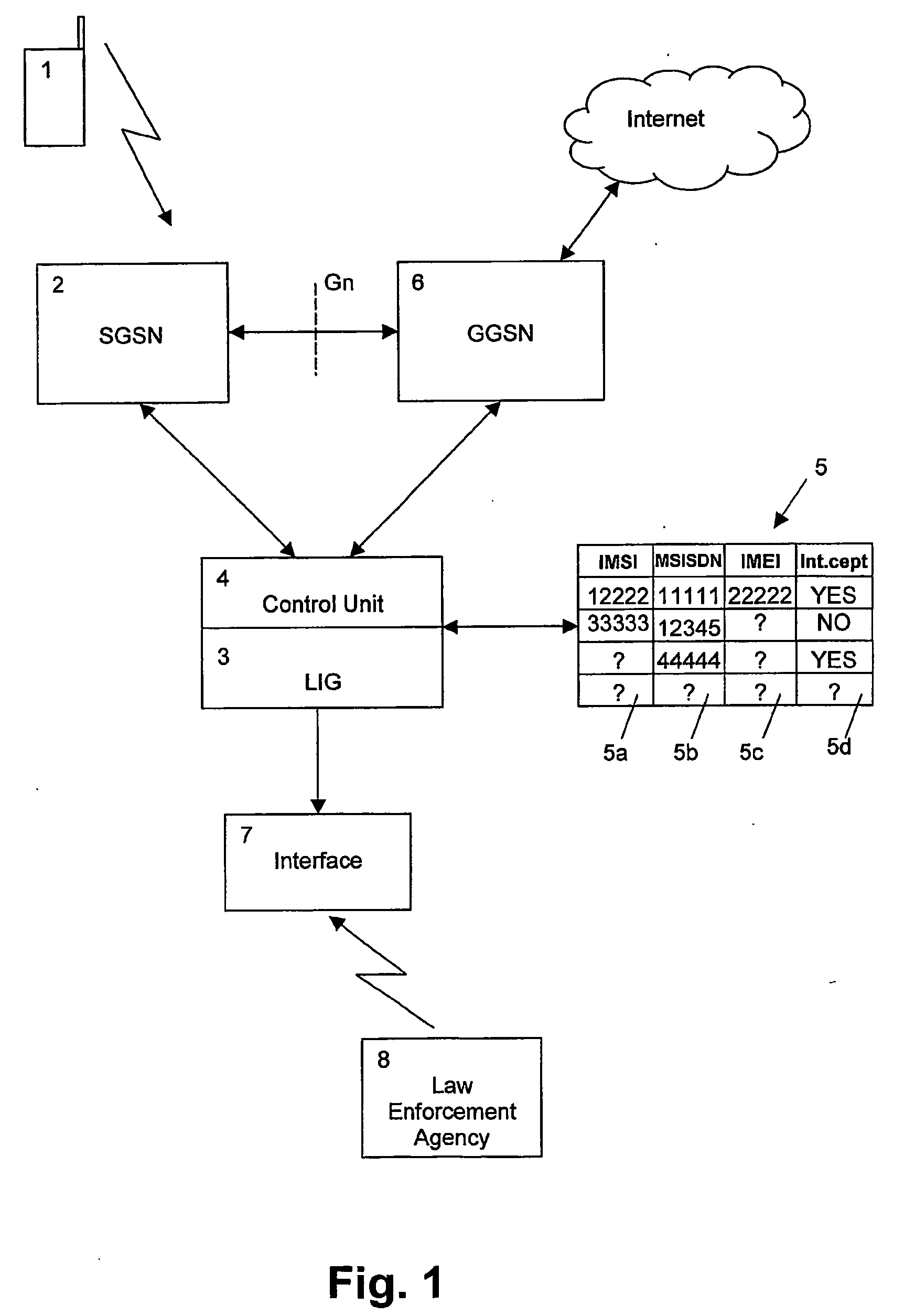
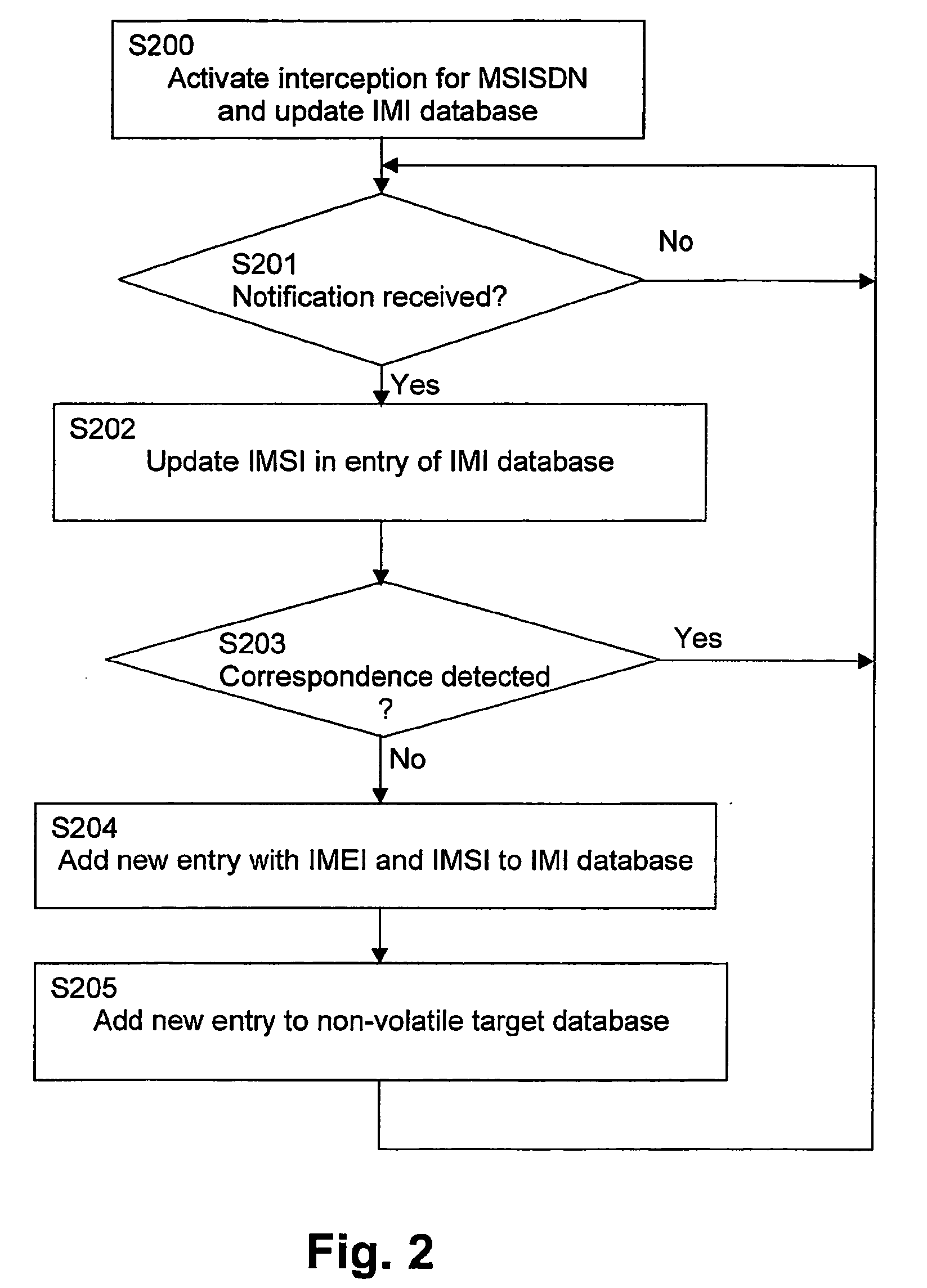
Infection-based monitoring of a party in a communication network
InactiveUS20050210127A1Increase coverageReduce physical laborSupervisory/monitoring/testing arrangementsMultiple digital computer combinationsData linkData bank
The present invention relates to a method and network device for monitoring a party in a communication network, wherein a link information linking at least two types of identifier data for identifying parties to be monitored is stored, and a correspondence between the stored link information of the monitor party and identifier data supplied from the communication network for the monitored party is checked. A new link information linking supplied non-matching identifier data to a stored other type of the at least two types of identifier data linked by the stored link information is added to the stored link information, to thereby provide an automatic Subscriber Identity Module (SIM) infecting feature. Thereby, no connections are missed as each new set of identifier data generates a new entry in the database.
Owner:NOKIA TECHNOLOGLES OY
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com