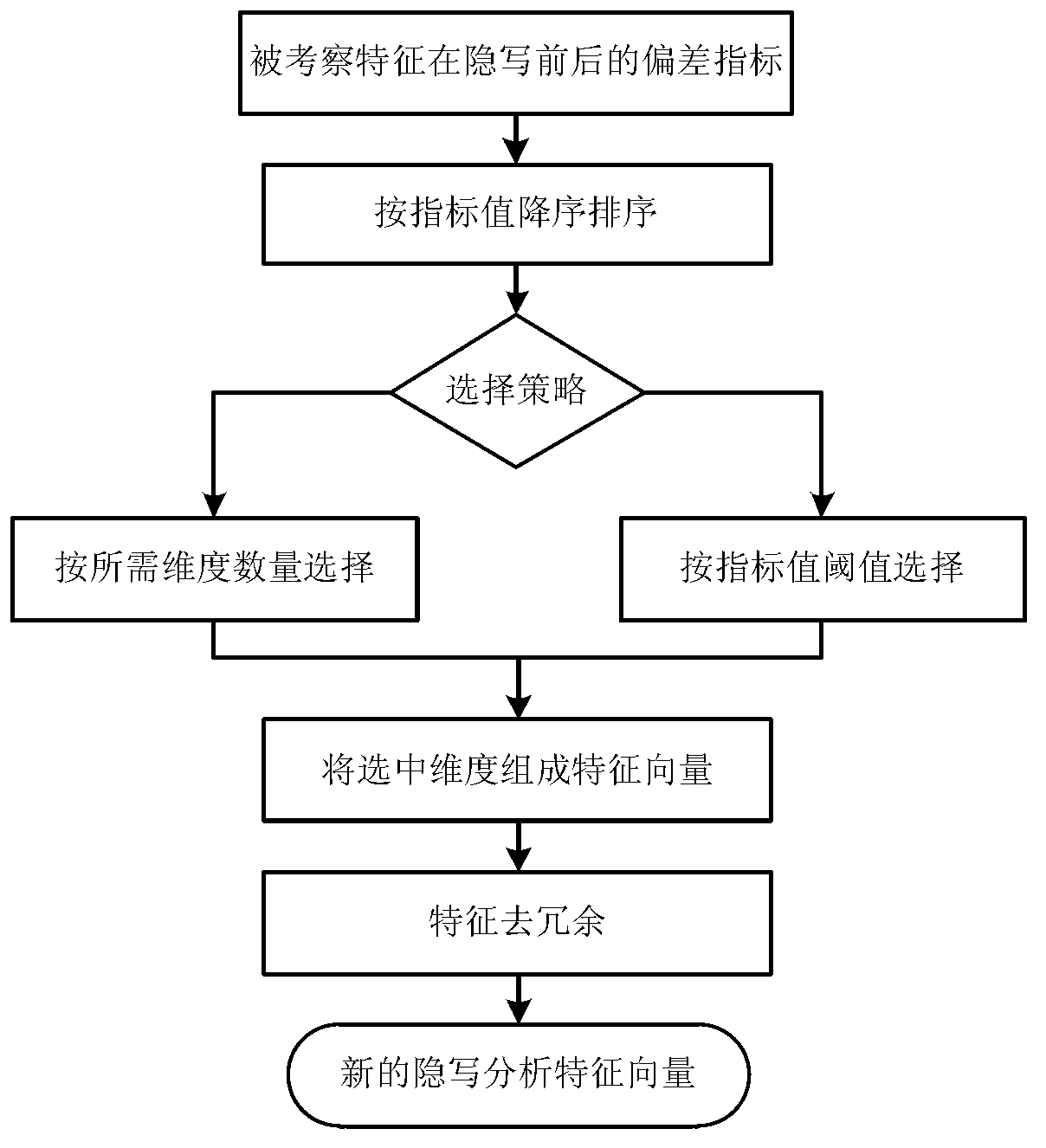
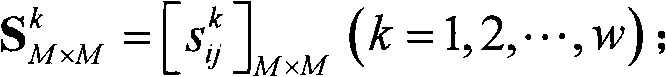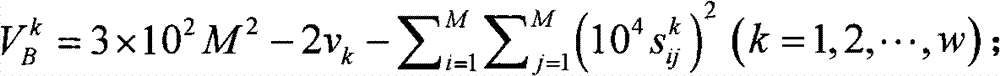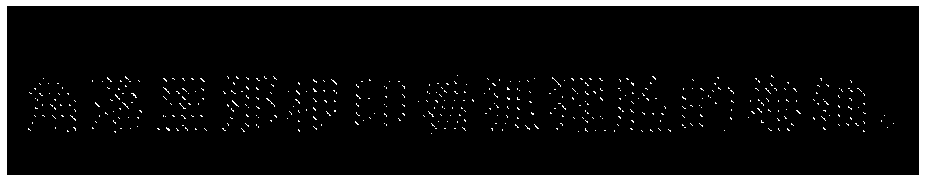Patents
Literature
46 results about "Hidden text" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Hidden text is computer text that is displayed in such a way as to be invisible or unreadable. Hidden text is most commonly achieved by setting the font colour to the same colour as the background, rendering the text invisible unless the user highlights it.
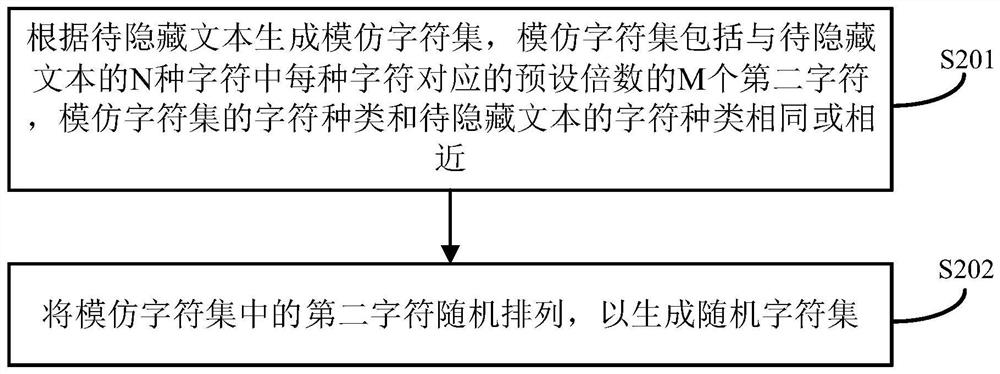
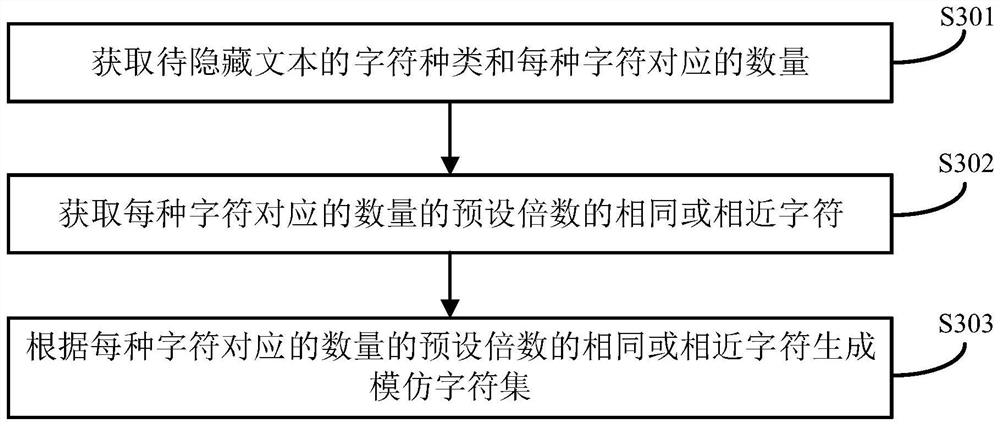
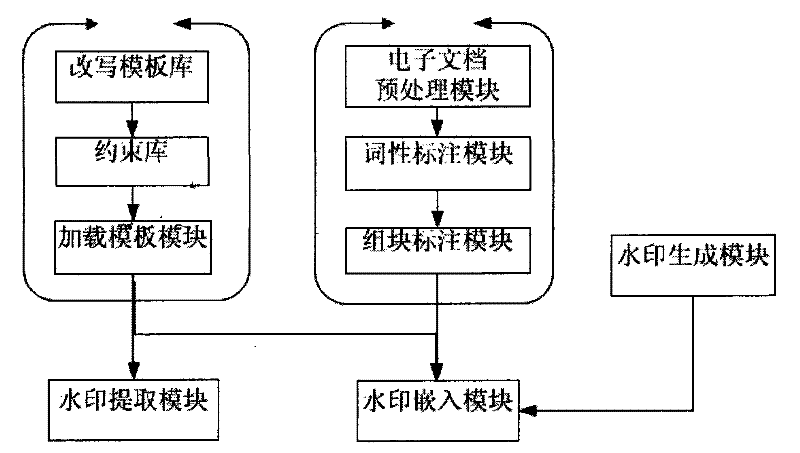
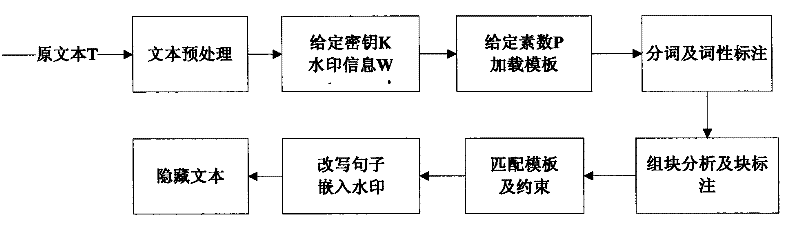
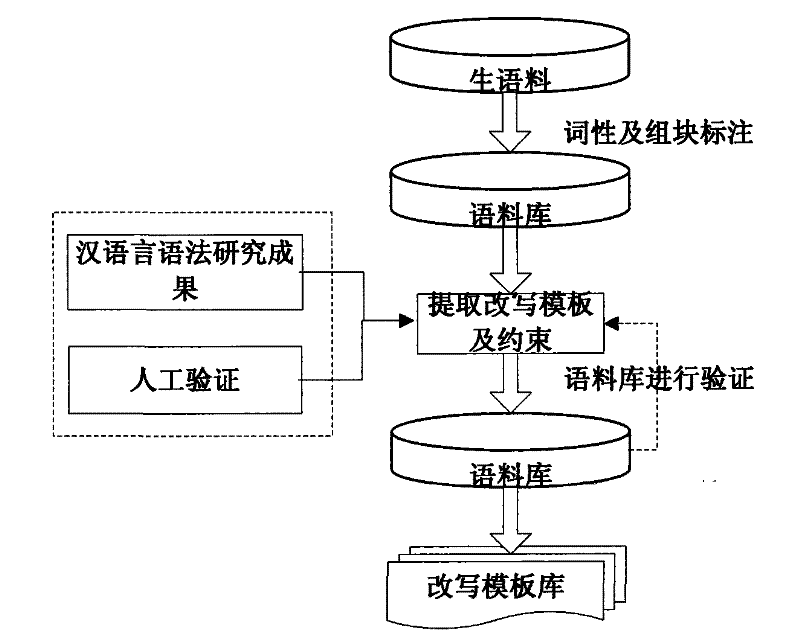
Text hidden method based on Chinese sentence pattern template transformation
InactiveCN101639826AConform to the semantic idiomPrevent rewritingSpecial data processing applicationsElectronic documentComputerized system
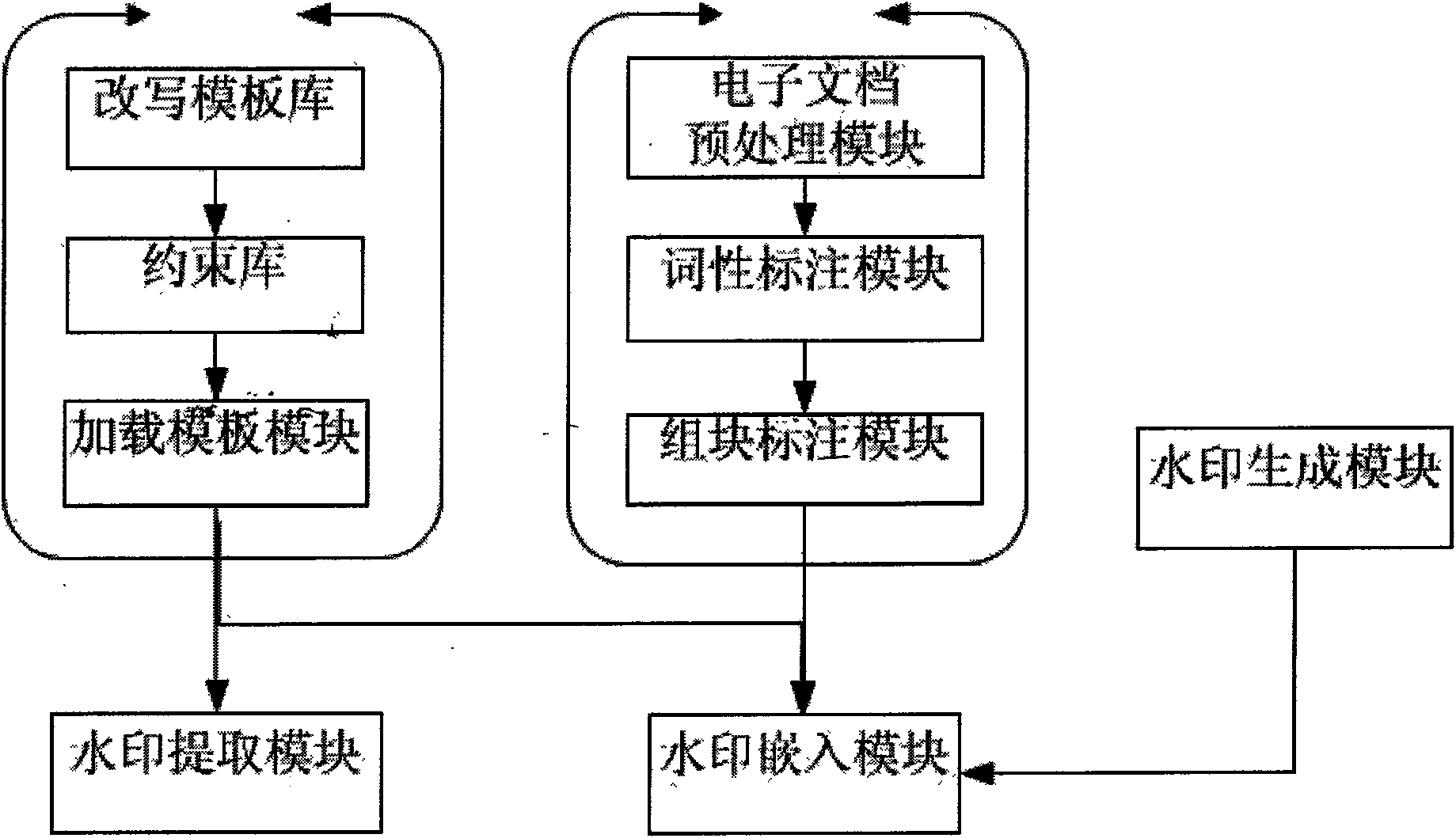
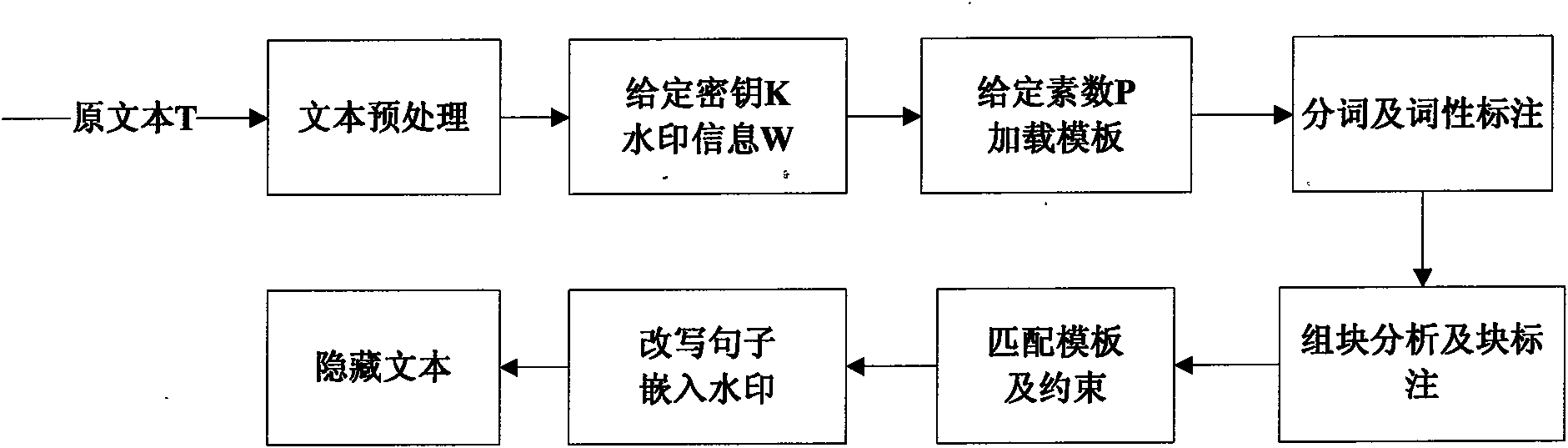
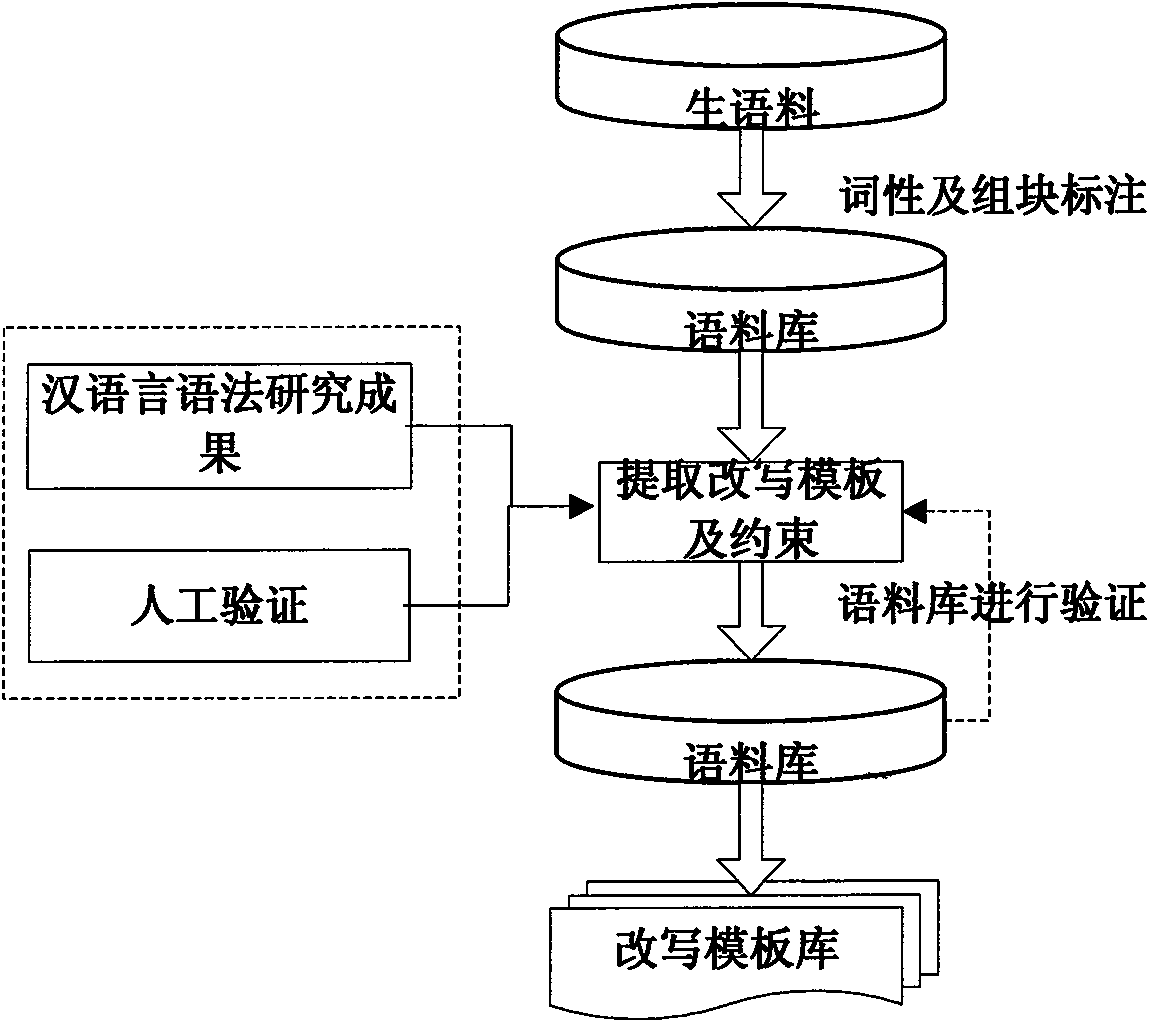
The invention discloses a text hidden method based on Chinese sentence pattern template transformation. The method utilizes the computer system to carry out watermark embedment and extraction on textinformation to hide the text information, comprising the following steps: (1) carrying out pre-treatment on an electronic file; (2) generating watermark information sign and setting a key; (3) carrying out part-of-speech tagging to format-free file generated in step (1) by a part-of-speech tagging module and outputting a part-of-speech tagging string of a sentence; (4) simplifying the part-of-speech tagging string output in the step (3) by a chunk tagging module; (5) loading a template module to select a sentence pattern module; (6) embedding watermark information by a watermark embedment module; (7) outputting the hidden text with embedded watermark; and (8) extracting the watermark information from the hidden text by a watermark extraction module through the key. The text hidden method changes sentence pattern through a template, avoids complex understanding and processing of grammar and semanteme, ensures the carrier text better satisfying grammar and semanteme habit and prevents blindfold rewrite.
Owner:NORTHWEST UNIV(CN)
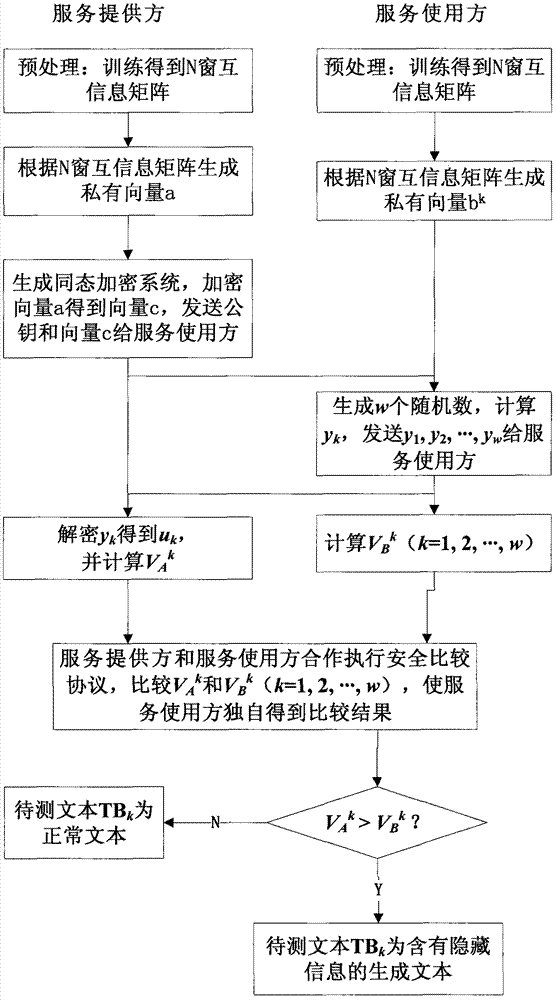
Method for securely detecting hidden text information based on homomorphic encryption system
InactiveCN102012980AWon't leakThe test result is accurateDigital data protectionCommunication with homomorphic encryptionService provisionInformation hiding
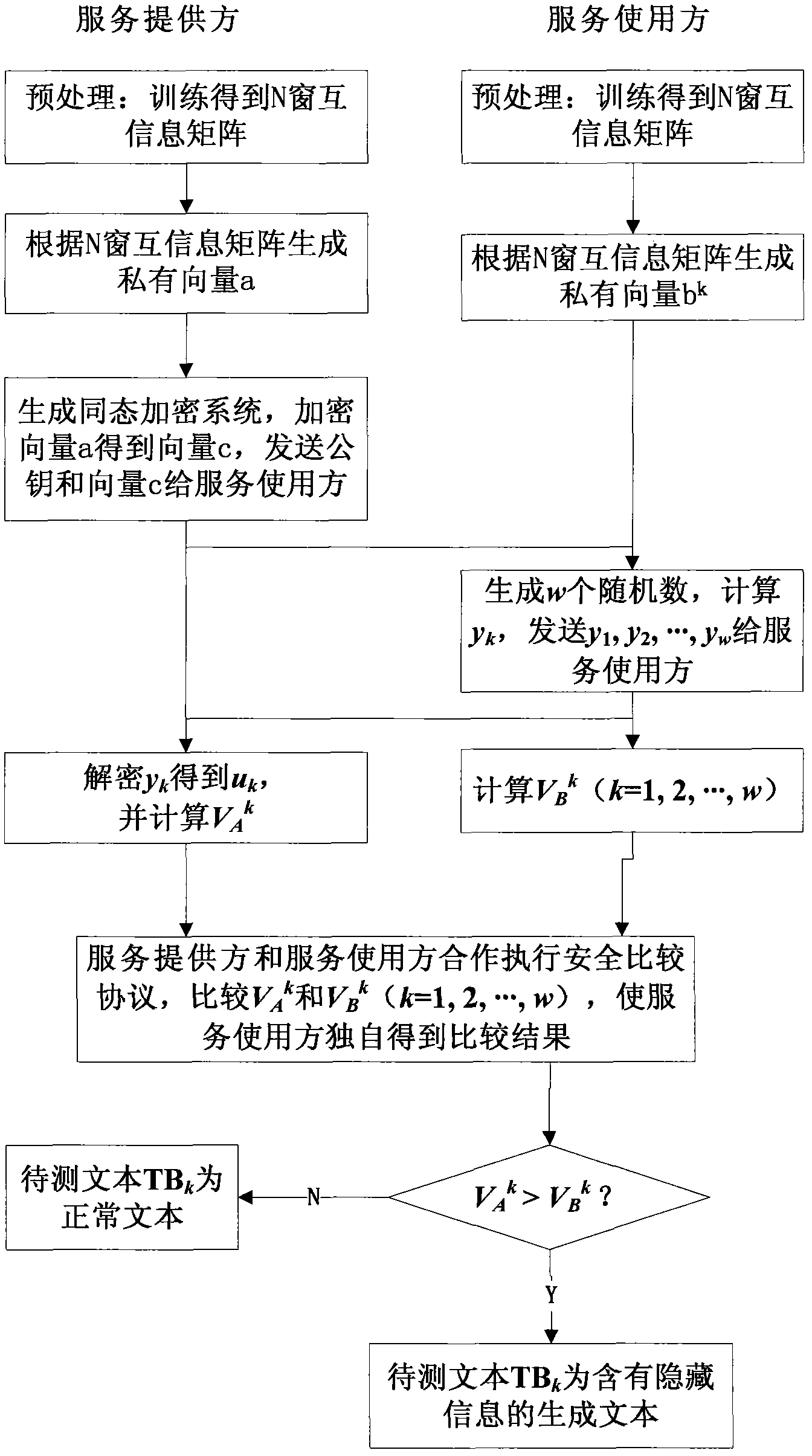
The invention discloses a method for securely detecting hidden text information based on a homomorphic encryption system, and the method is used for a service provider to detect the hidden text information of a service user. The method comprises the following steps: the service provider and the service user which are mutually independent transfer non-private information interactively so as to complete the detection on the hidden text information; and then, according to the comparand of the service provider and the service user, the two parties judge whether the text information contains hidden information by utilizing the homomorphic encryption system and an executive safety comparison protocol. By using the method, the detection on the hidden text information can be performed between twoindependent parties which are lack of mutual trust.
Owner:SUZHOU INST FOR ADVANCED STUDY USTC
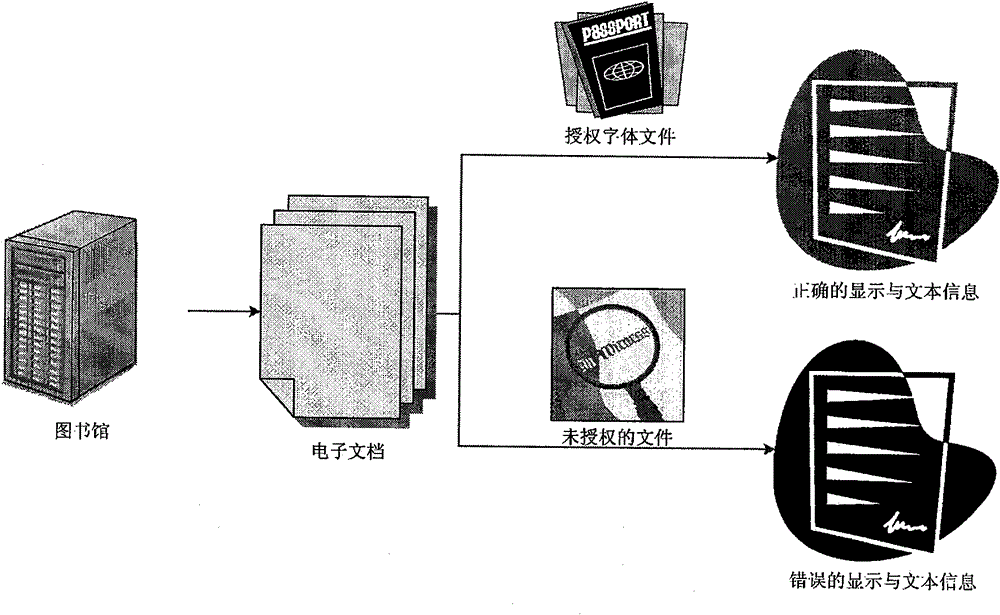
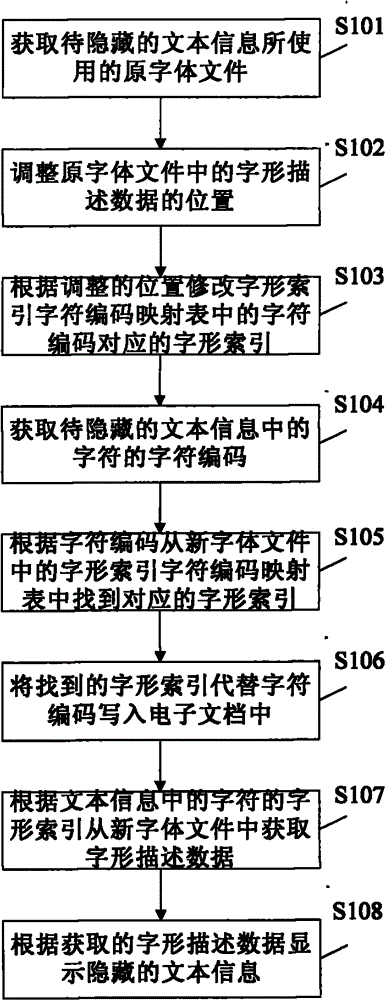
Text information hiding method and device
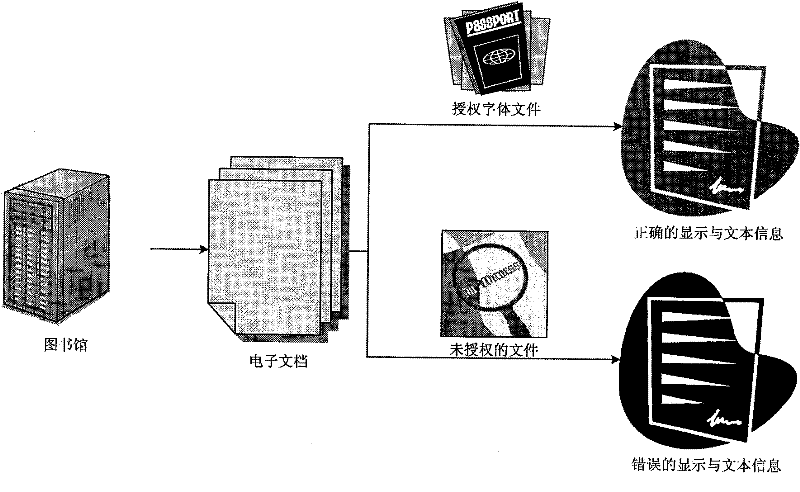
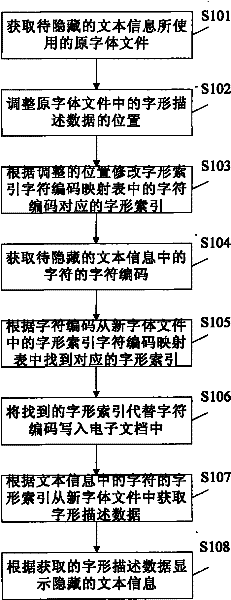
ActiveCN102542212AAchieve concealmentImprove concealmentDigital data protectionData displayElectronic document
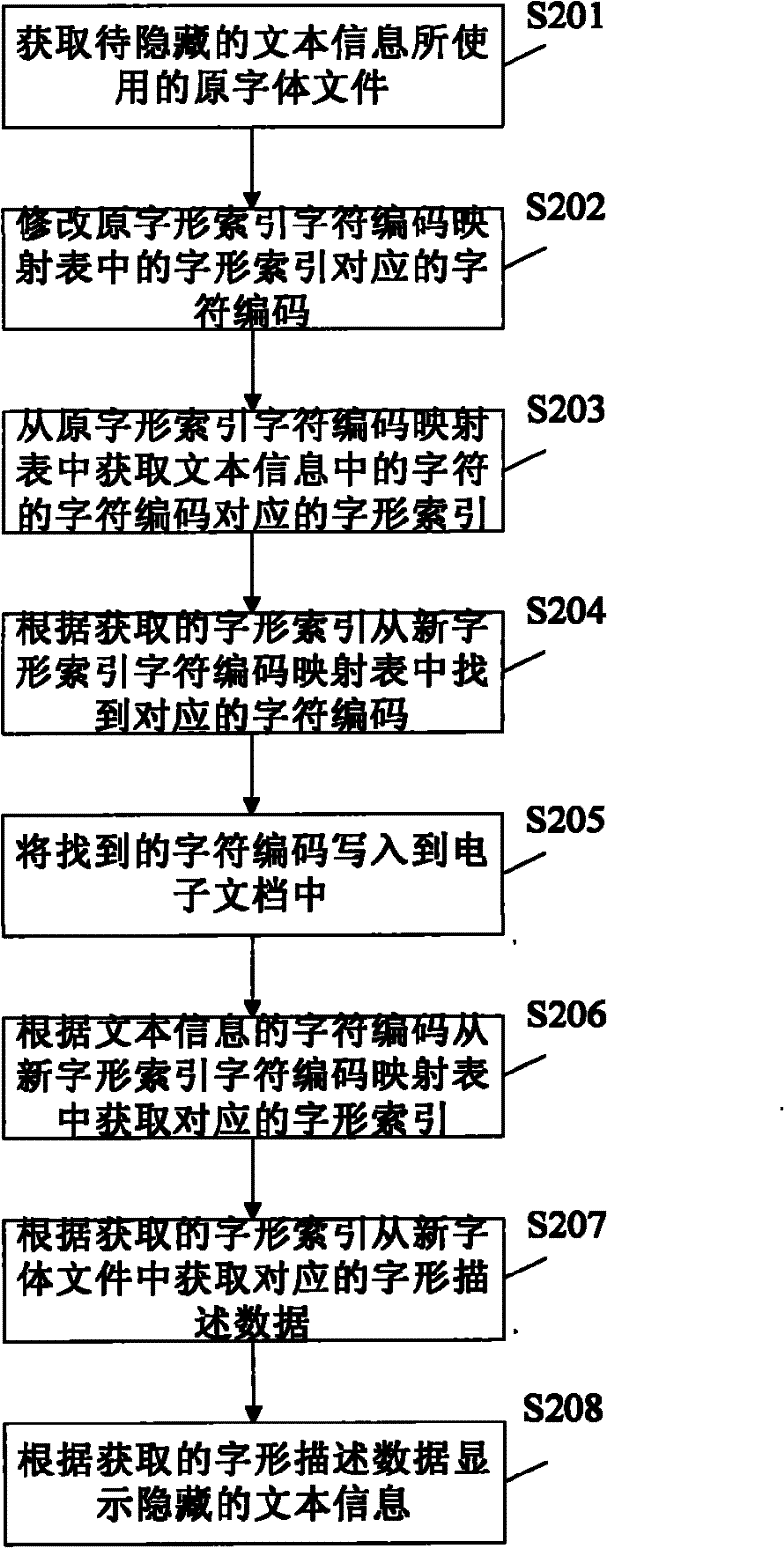
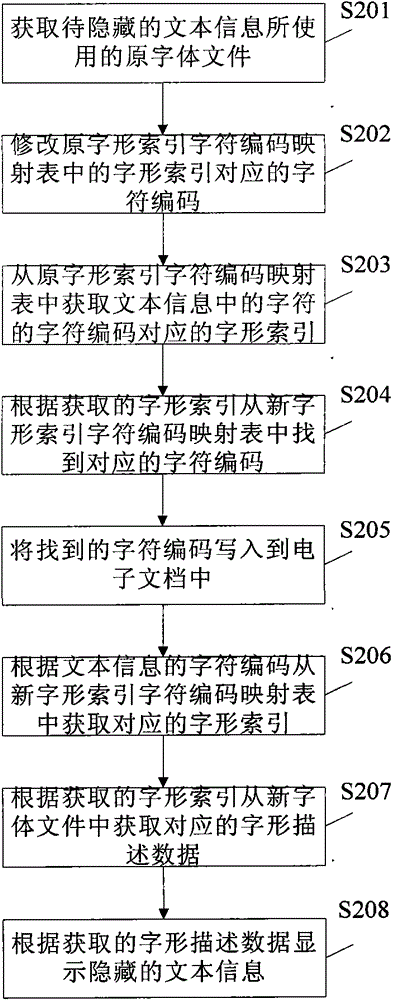
The invention provides a text information hiding method, which includes: acquiring an original font file used by to-be-hidden text information, generating a new font file by rectifying mapping relation between font index and character codes in the original font file; rectifying the text information according to the new font file, writing the rectified text information into an electronic document; acquiring font description data of characters in the text information from the new font file when the electronic document is opened, and displaying the text information according to the acquired description data. Correspondingly, the invention further provides a text information hiding device, character codes of the text information cannot be changed and any encryption method is omitted, effect of hiding the text information can be realized simply, and safety, hiding performance and robustness are high.
Owner:NEW FOUNDER HLDG DEV LLC +1
Text carrier-free information hiding method based on tag model
ActiveCN107609356AGuaranteed success rateIncrease hidden capacityTransmissionProgram/content distribution protectionChinese charactersTheoretical computer science
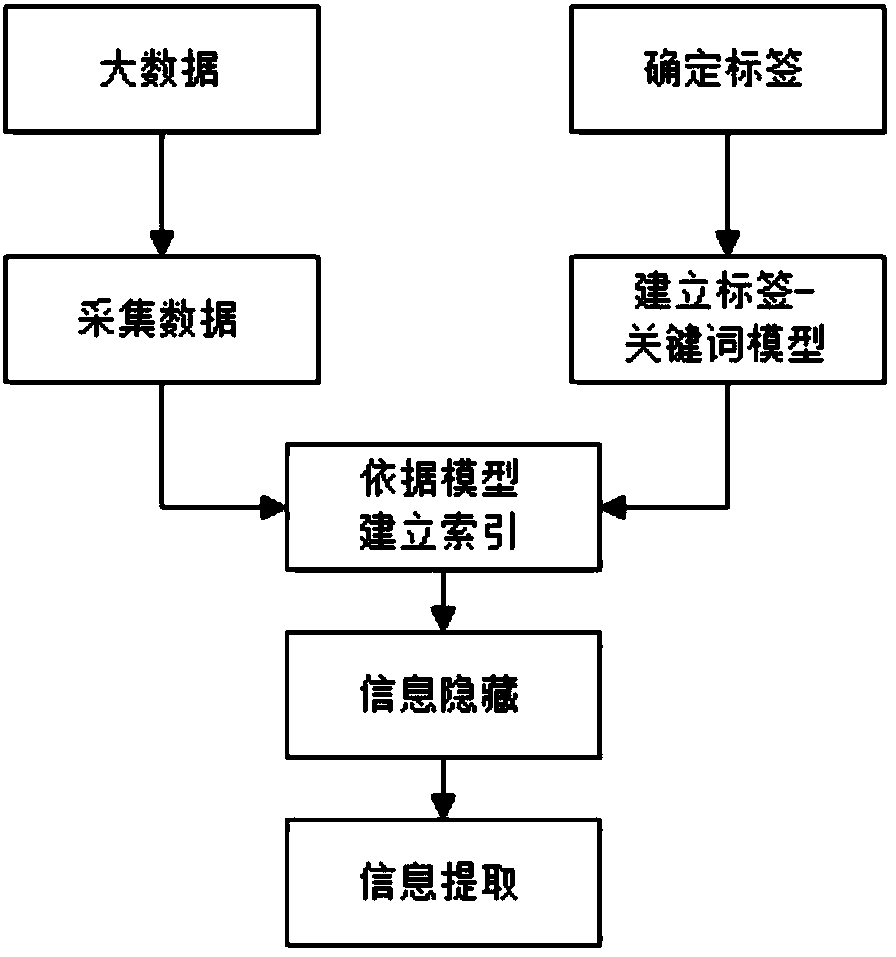
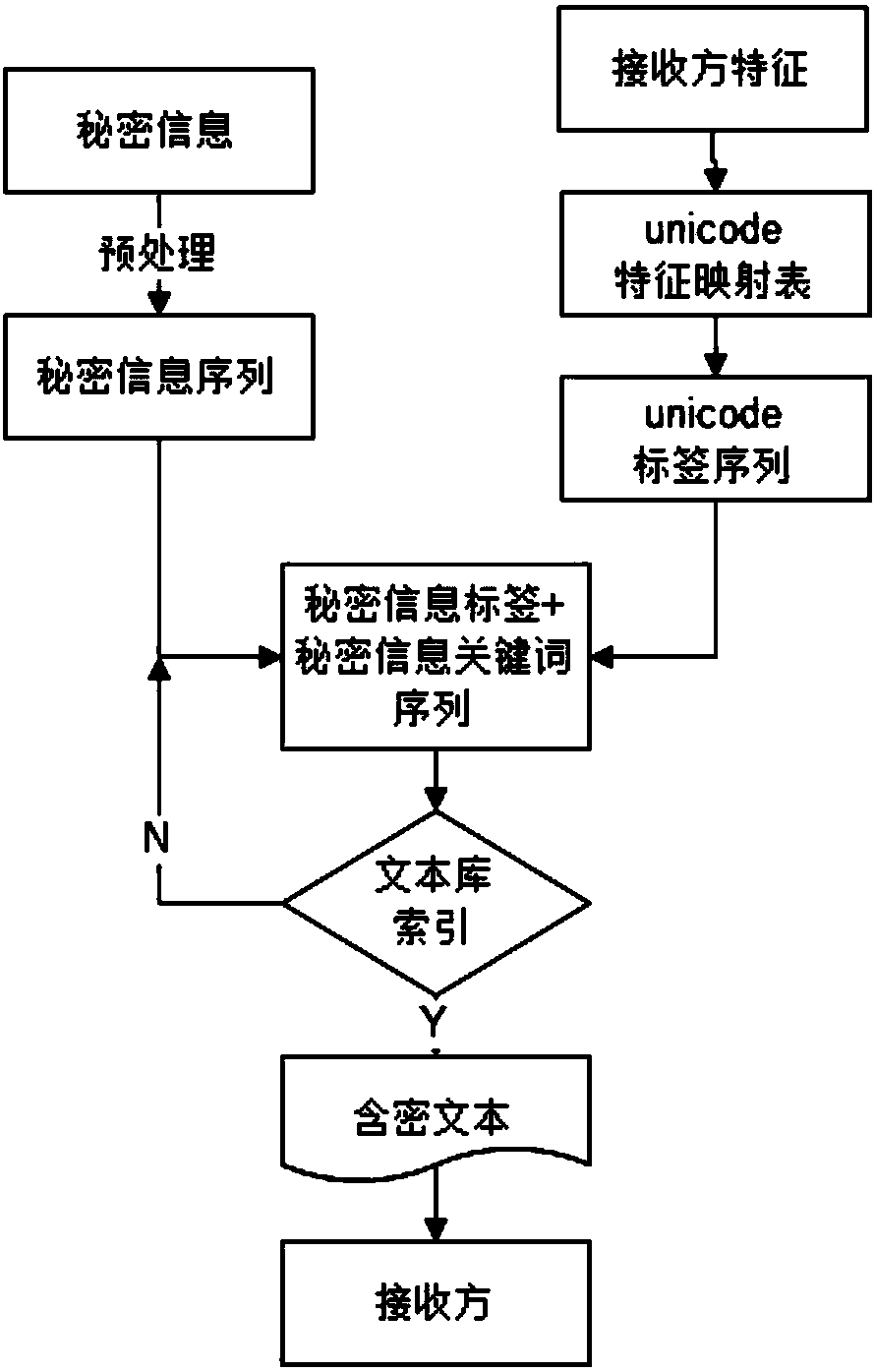
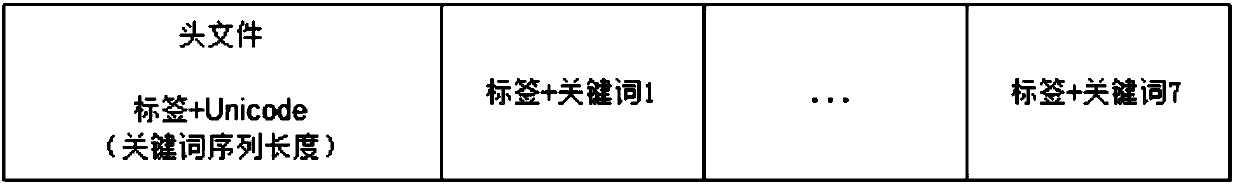
The invention provides a text carrier-free information hiding method based on a tag model. The method comprises the following steps that: collecting texts, and establishing indexes; hiding secret information: preprocessing the secret information to obtain the keyword sequence of the secret information; using the Unicode of Chinese characters as a secret information tag, and carrying out calculation according to the corresponding features of a receiver to obtain a secret information tag sequence; constructing a header file and a cipher containing text; through text index entries, selecting target text information corresponding to the header file and the cipher containing text one by one from a text library; and arranging all target text information in sequence, and sending the target text information to the receiver as a hidden text. By use of the method, while a hiding success rate is guaranteed, hiding capacity is improved.
Owner:NANJING UNIV OF INFORMATION SCI & TECH
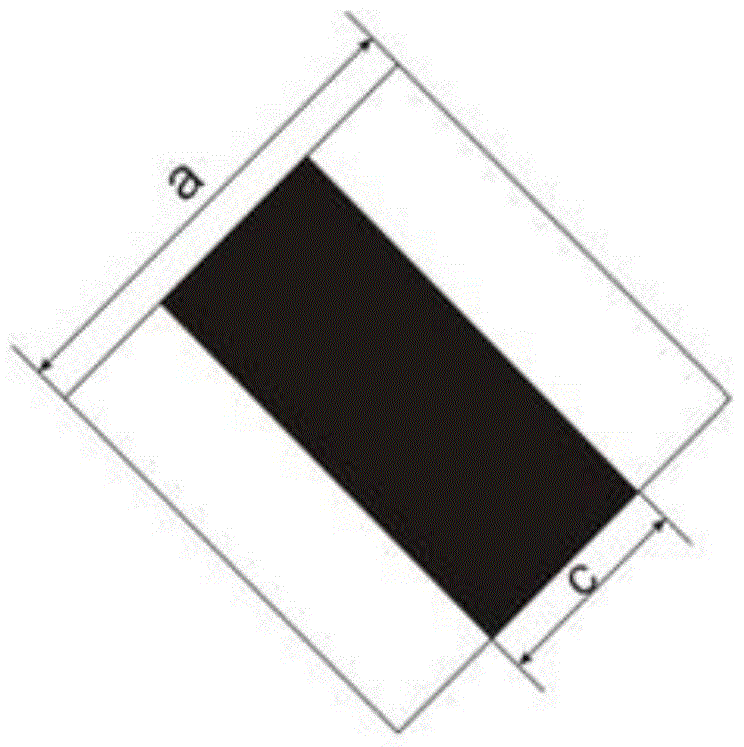
Method for matching simulation grating based on hidden image lattice point area ratio
ActiveCN103839260AGood effectSolve the problem that the matching degree is not high and the hidden image display effect is not goodImage analysisGratingAlgorithm
The invention discloses a method for matching a simulation grating based on a hidden image lattice point area ratio. The method comprises the specific steps that a master print map is manufactured; a hidden text or image is manufactured on the manufactured master print map; a matching relation between the hidden image lattice point area ratio and a simulation matching grating area ratio is established according to hidden text or image parameters; a simulation matching grating is manufactured according to the established matching relation; the manufactured simulation matching grating is placed on the master print map to detect hidden information. According to the method for matching the simulation grating based on the hidden image lattice point area ratio, the precise matching relation between the hidden image lattice point area ratio and the simulation matching grating area parameters is obtained according to the matching algorithm between the hidden image lattice point area ratio and the simulation matching grating area parameters, the better showing effect after the simulation matching grating is added into a hidden image is achieved, the problems that according to an existing method, the matching degree of the hidden image and the simulation matching grating is not high, and the showing effect of the hidden image is not good are solved, the computing method is simple, and operation is convenient.
Owner:SHAANXI UNIV OF SCI & TECH
Systems and methods for detecting hidden text and hidden links
ActiveUS8392823B1Web data indexingSpecial data processing applicationsStructural representationInterconnection
A system detects hidden elements in a document that includes a group of elements. The system may identify each of the elements in the document and create a structural representation of the document. The structural representation may provide an interconnection of the group of elements in the document. The system may also determine whether one or more elements of the group of elements are hidden based at least in part on locations or other attributes or properties of the one or more elements in the structural representation.
Owner:GOOGLE LLC
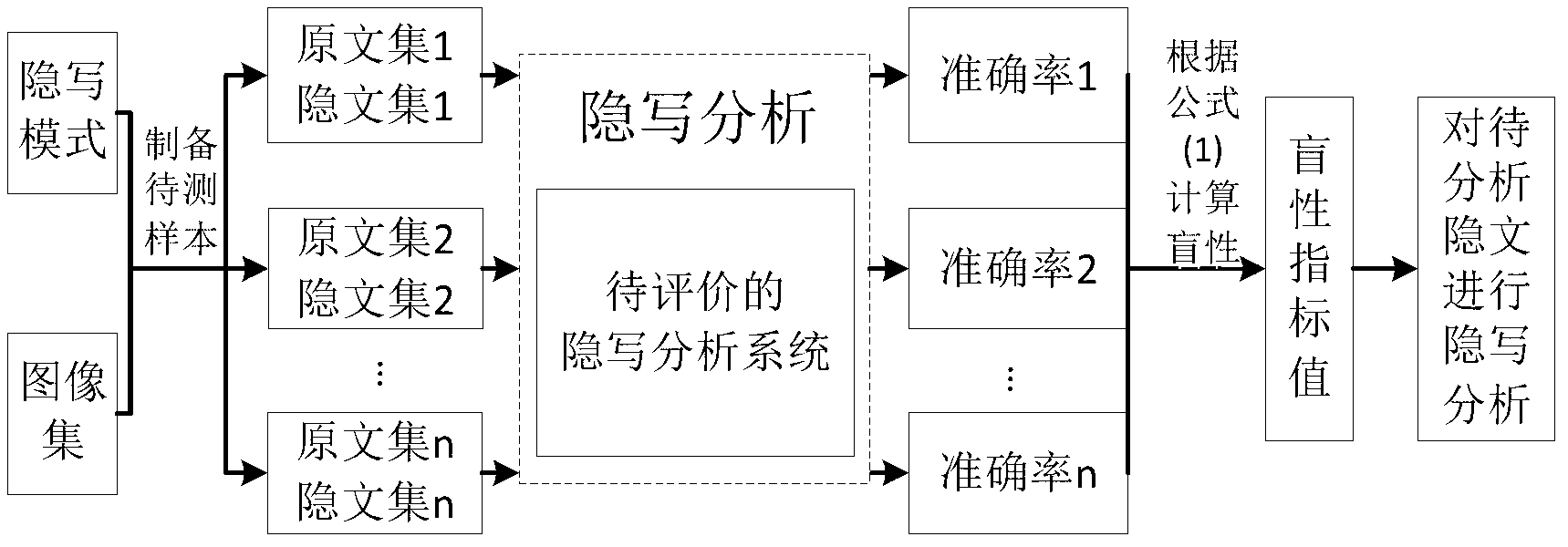
Steganalysis method based on blindness of steganalysis systems
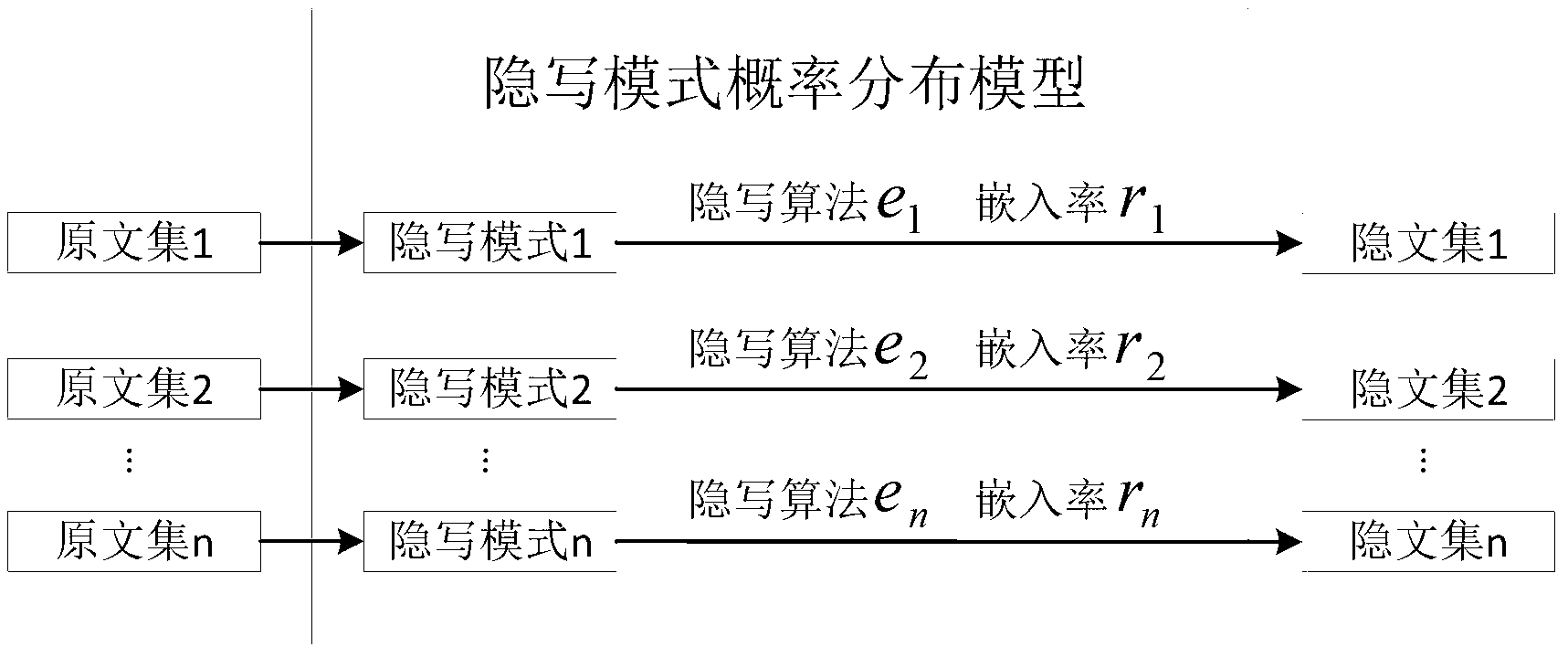
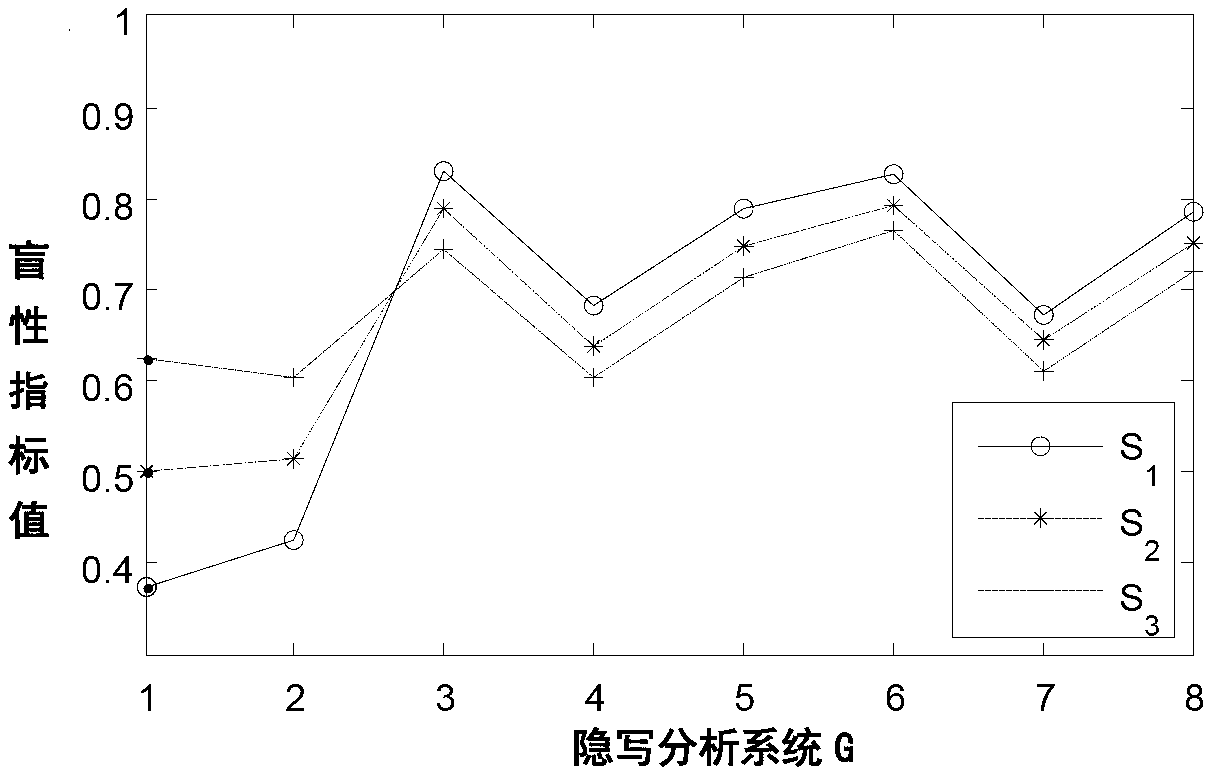
InactiveCN103258123AQuick analysisCharacter and pattern recognitionSpecial data processing applicationsAlgorithmSteganographic algorithm
The invention discloses a steganalysis method based on blindness of steganalysis systems. The method includes the steps of (1) constructing a probability distribution model of a steganalysis mode, wherein the probability distribution model comprises various steganalysis modes and occurrence probabilities of the steganalysis modes, (2) choosing a group of original text sample sets and carrying out stegannaysis on one original text sample set by means of each steganalysis mode in the probability distribution model to produce a corresponding steganalysis sample set, (3) regarding the steganalysis systems to be tested, calculating the analysis accuracy of the steganalysis system for each corresponding steganalysis mode according to each steganalysis sample set and each corresponding original text sample set and carrying out weighted average on the analysis accuracy of each steganalysis mode according to the occurrence probabilities of the steganalysis modes to obtain the blindness value of the steganalysis system, and (4) carrying the steganalysis on a hidden text to be analyzed according to the steganalysis system with the highest blindness value. The steganalysis method can objectively evaluate practical analysis capacity of the steganalysis systems and improve analysis for unknown steganalysis arithmetic hidden texts.
Owner:INST OF INFORMATION ENG CHINESE ACAD OF SCI
Steganographic method with misguiding function of controllable secret key sequence
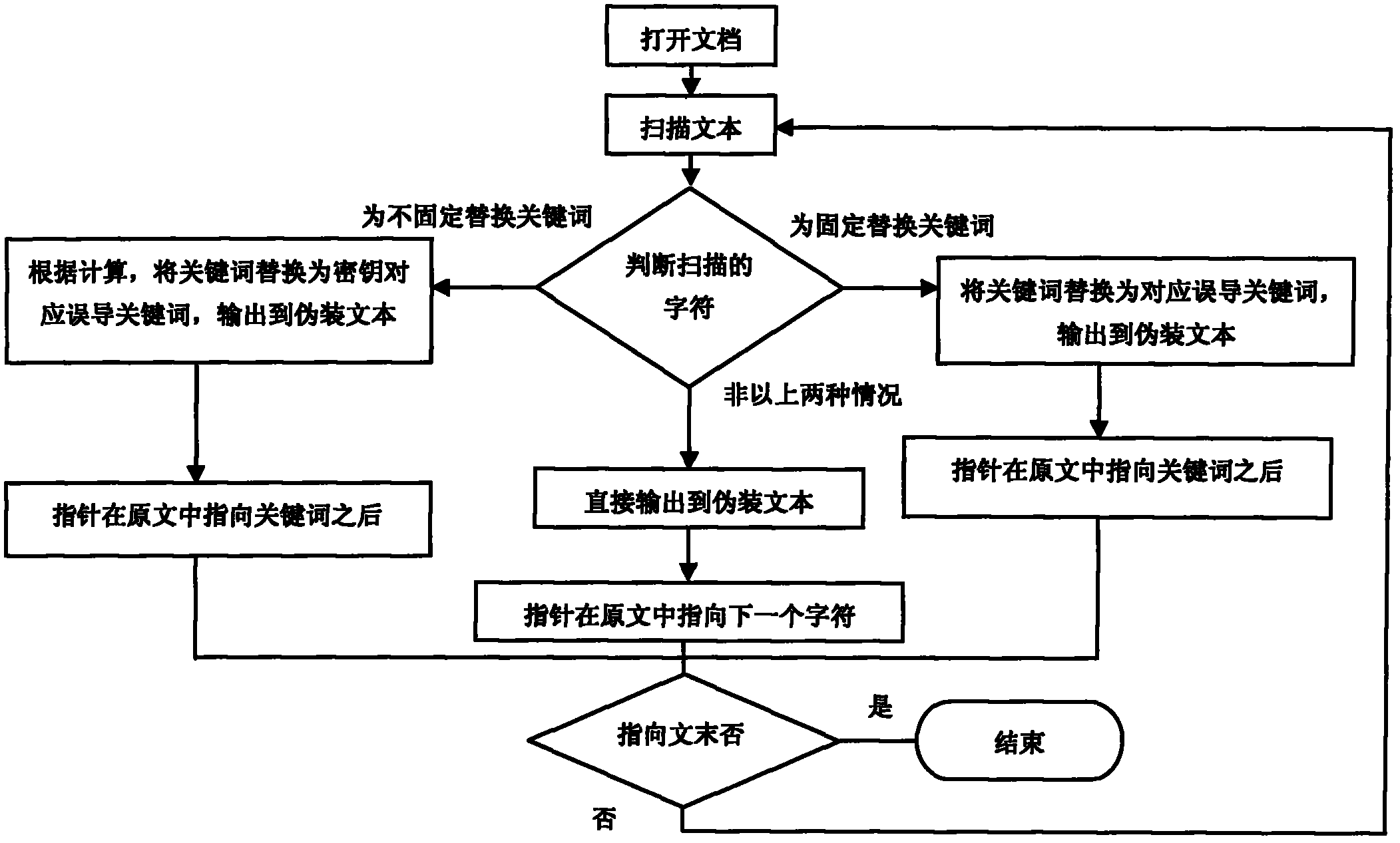
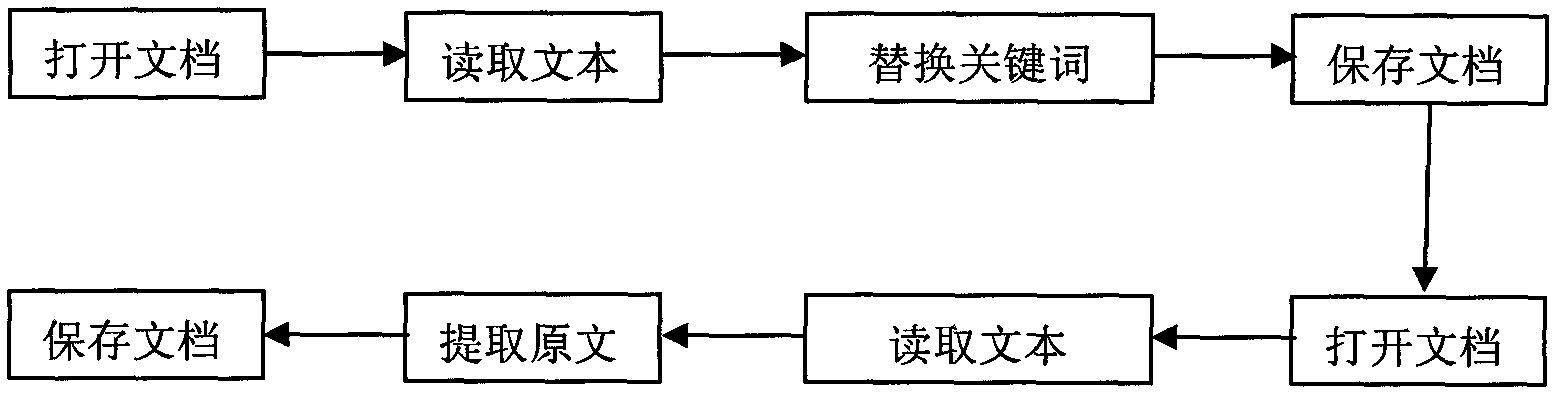
The invention relates to a text steganographic (secret writing) method with a misguiding function. The method comprises the steps of: opening a file, reading contents of the file, then replacing a keyword in the file with a keyword close, opposite or similar to the keyword in the file, and finally storing the file so that the misguiding function is achieved. The replacement of the keyword is achieved by adopting the combination of the fixed replacement and the floating replacement. The floating replacement is controlled by a secret key, a safe sequence generated by the secret key is used for carrying out tentative replacement, and if the replacement is not right, correction information can be added behind the secret key. Contents of the text subjected to steganography are possibly close, opposite or similar to contents of a hidden text, thus the misguiding effect can be obtained. The steganographic method is free of the defect that the traditional steganographic method needs large files of images, videos, audios and the like, and can directly misguide an opposite party.
Owner:桂林轻鸿科技有限公司
Steganography evaluation based steganalysis method
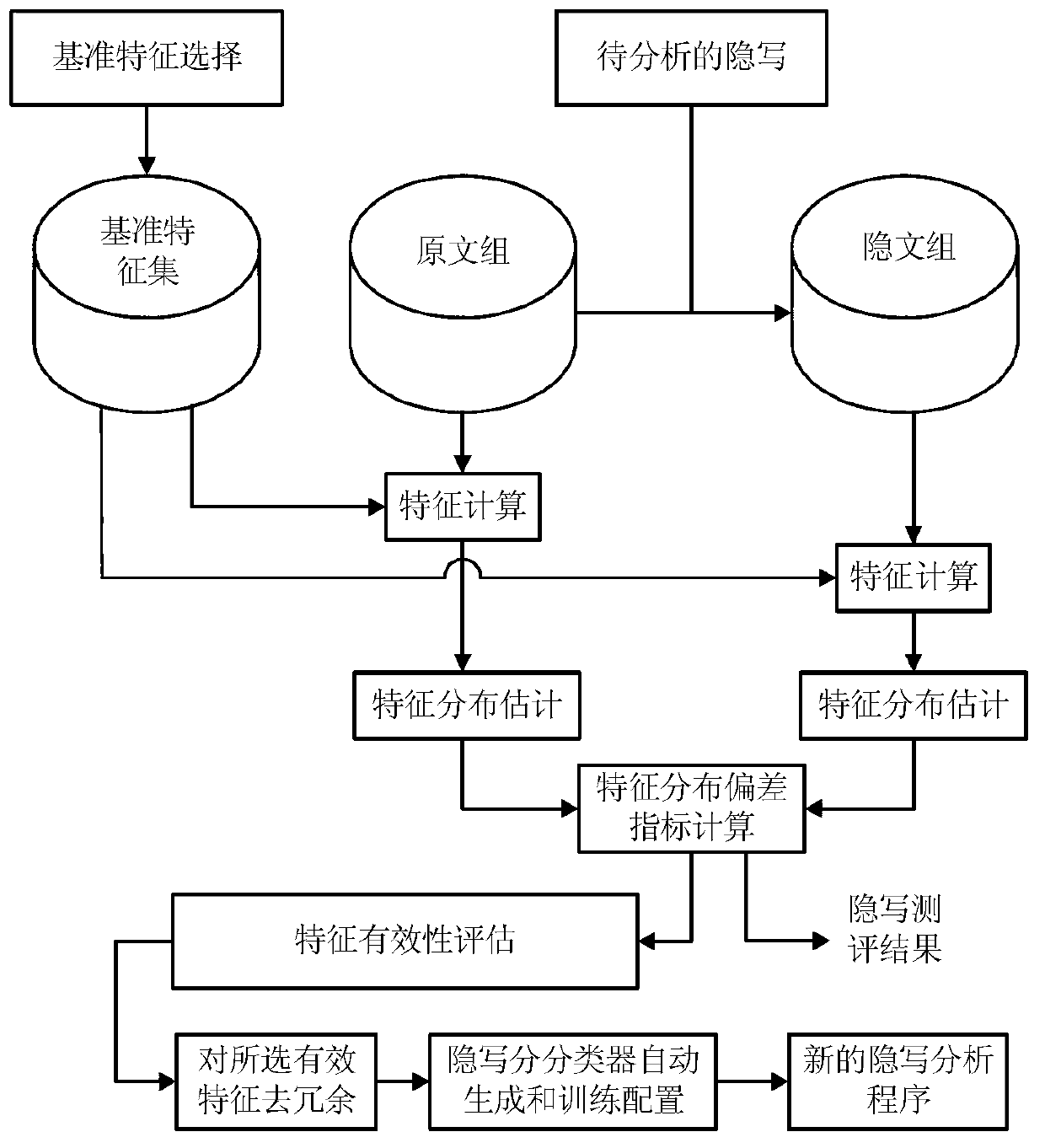
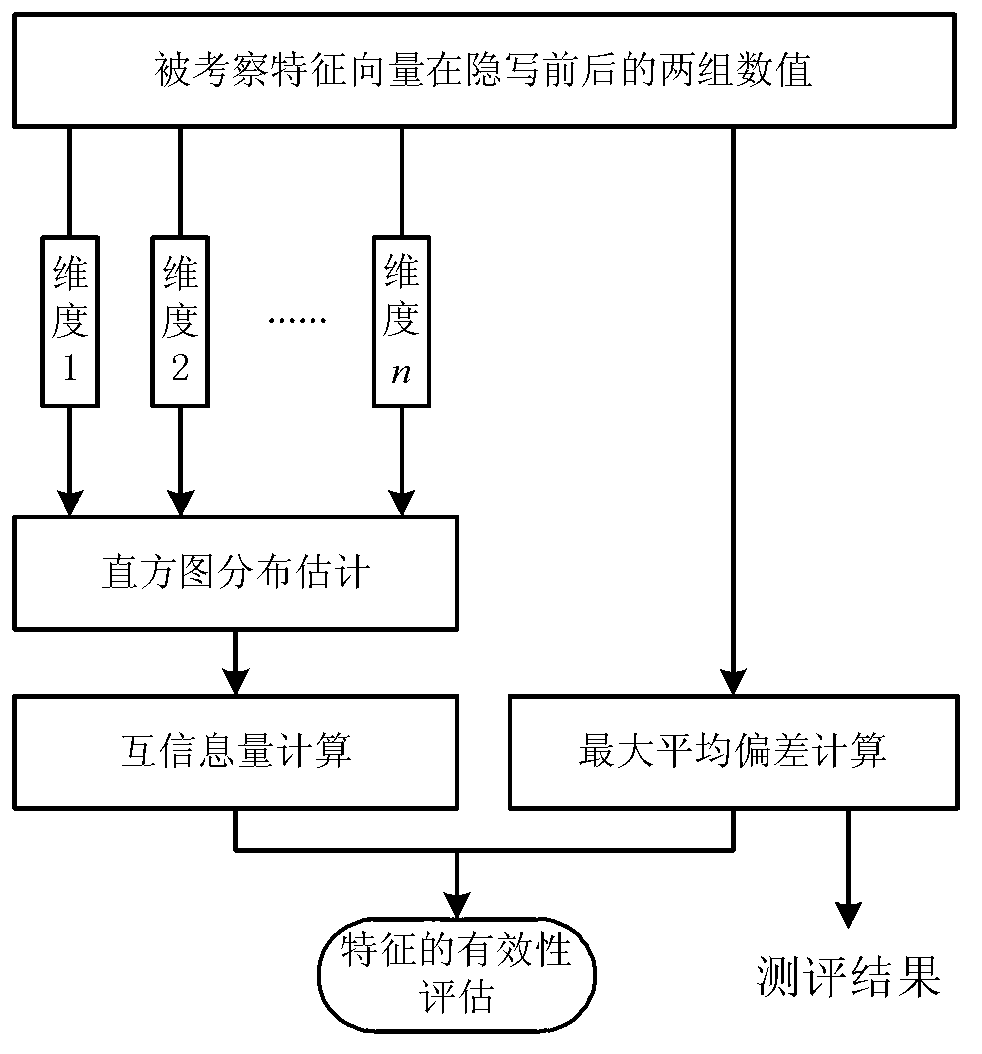
InactiveCN102930495AImprove efficiencyImproving the efficiency of steganalysis implementationImage data processing detailsFeature vectorEvaluation result
The invention discloses a steganography evaluation based steganalysis method. The steganography evaluation based steganalysis method comprises the steps of: (1) establishing a reference feature set containing a plurality of steganographic features; (2) performing steganography on a group of original text {Xi} by adopting a to-be-analyzed steganographic algorithm to generate a corresponding group of hidden text {Yi}; (3) selecting partial features in the reference feature set as inspecting features, calculating a inspecting feature vector of each sample in both the original text set and the hidden text set to respectively obtain feature vector sets {xi} and {yi} of both the original text set and the hidden text set; (4) evaluating effectiveness of each component of each inspecting feature vector serving as each hidden writing feature based on {xi} and {yi}; (5) repeating steps (3) and (4) for multiple times to obtain an effectiveness evaluation result of a group of feature vector components; and (6) selecting a plurality of components from an effectiveness evaluation result to build a new feature vector, performing redundancy elimination to obtain feature vectors of the steganographic algorithm for the steganalysis on the to-be-analyzed steganographic algorithm, and detecting if the to-be-analyzed steganographic algorithm contains hidden information. The steganography evaluation based steganalysis method, disclosed by the invention, has the advantage of greatly improving realization efficiency of steganalysis.
Owner:INST OF INFORMATION ENG CHINESE ACAD OF SCI
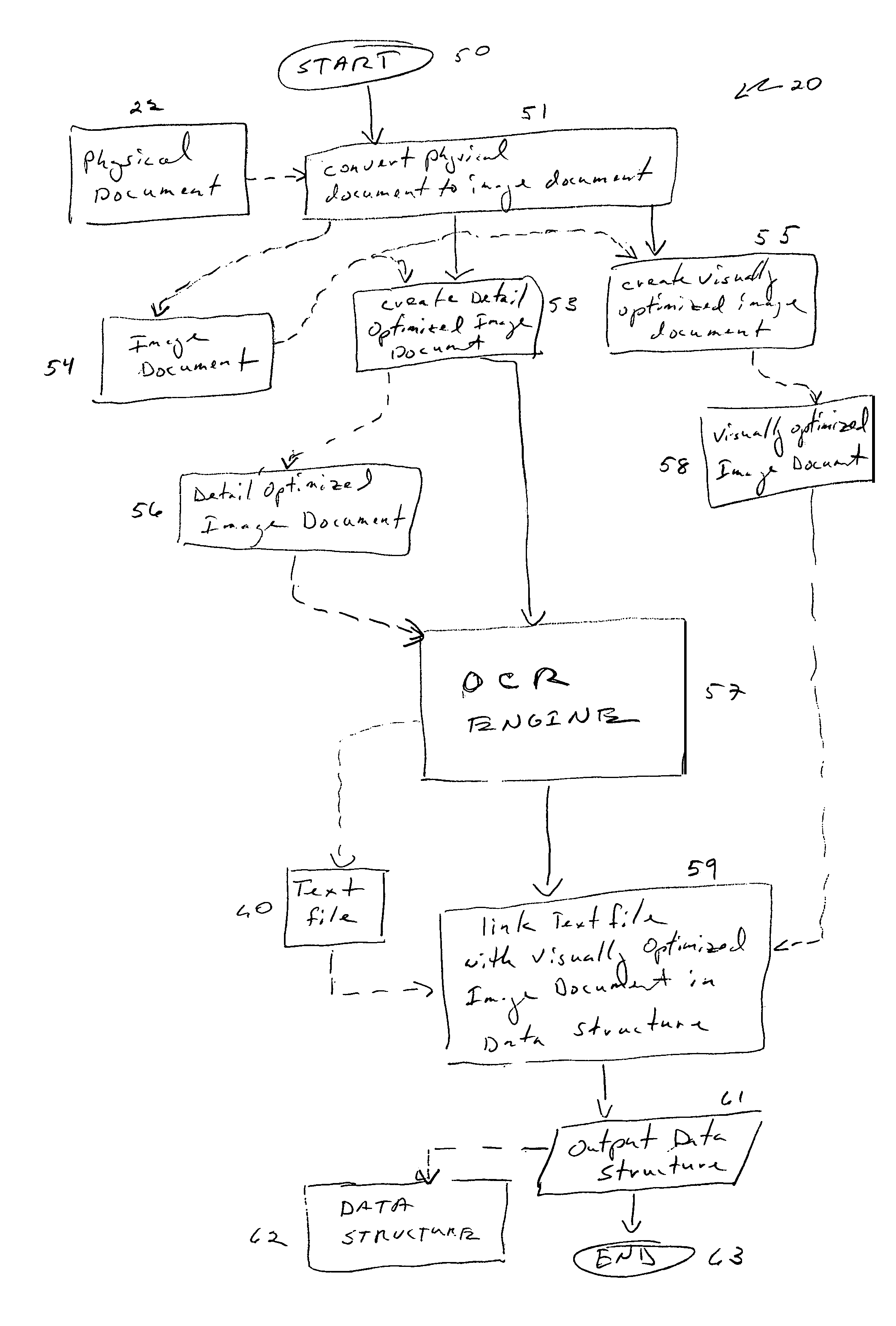
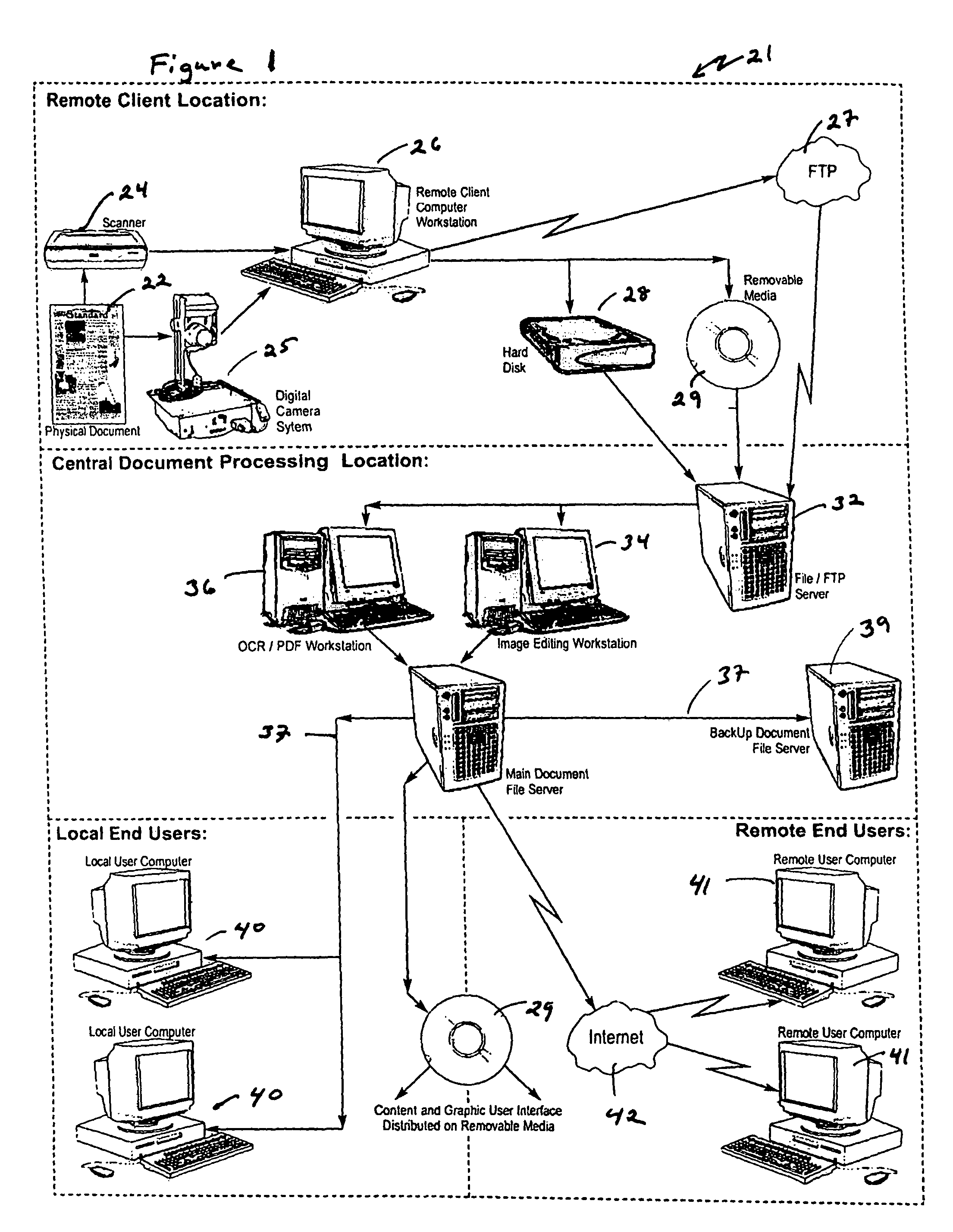
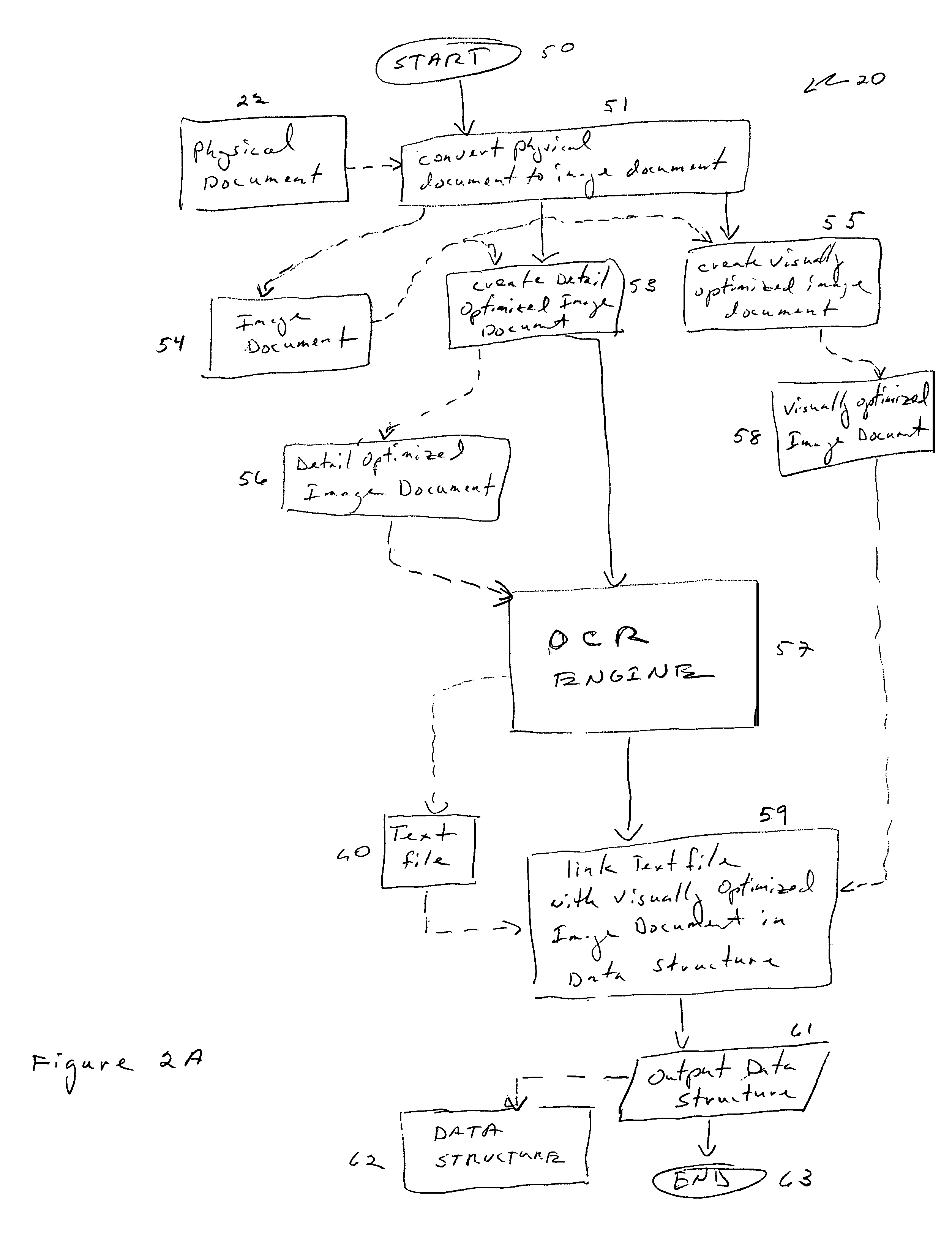
Apparatus and methods for management of electronic images
ActiveUS7773822B2Facilitate text based searching of textDigital data processing detailsCharacter and pattern recognitionSearch data structureDocument preparation
Systems including hardware and computer software and methods can create a text-searchable data structure that includes electronic image documents. The system may be configured in modules. The system converts an electronic image document into a visually optimized electronic image document and into a detail optimized electronic image document. The system also includes an OCR engine that abstracts character information from the detail optimized electronic image document and writes the character information into a text file. The visually optimized electronic image document is linked with the text file in a data structure by the system. The resulting data structure, which may be an image over hidden text pdf document, may be searched using various text based search techniques. When specified text is located in a text file, the corresponding visually optimized electronic image document may then be presented to the searcher.
Owner:COLORMAX
Character recognition device and method, image display device, and image retrieval device
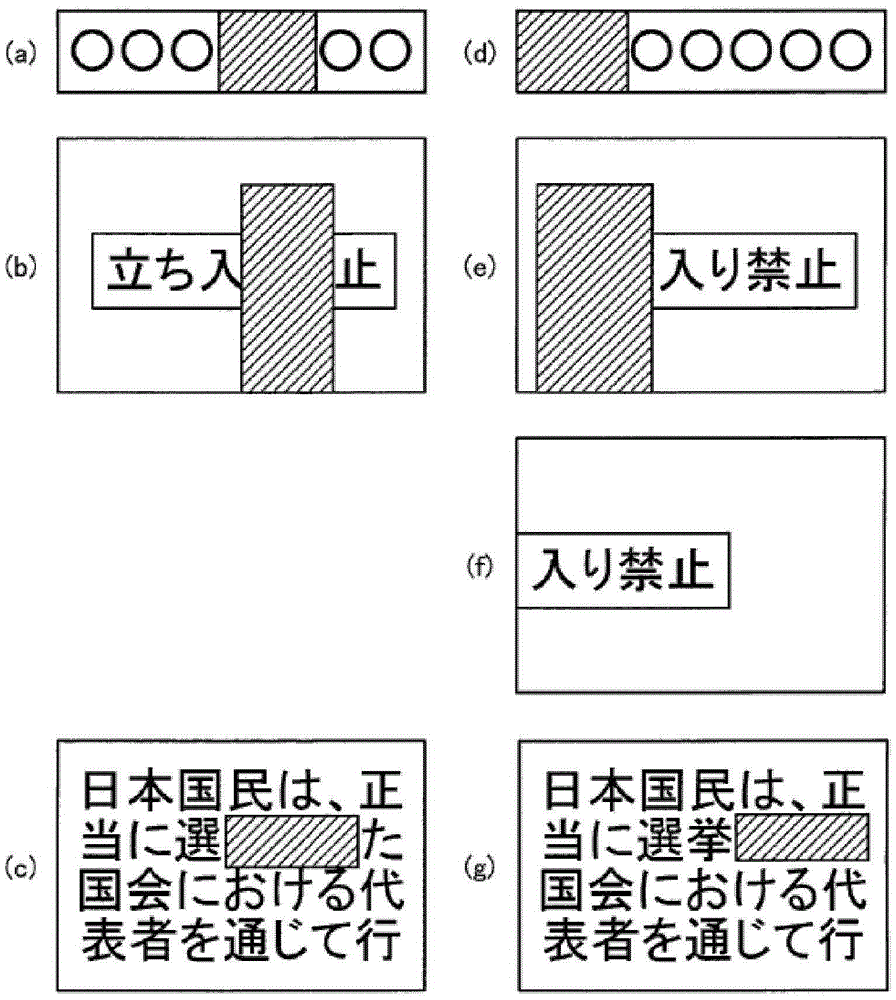
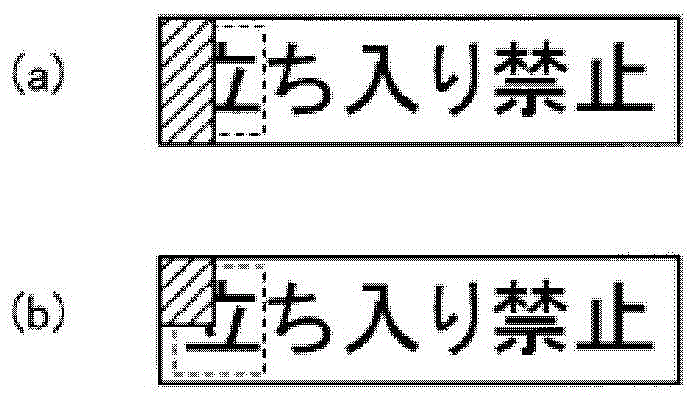
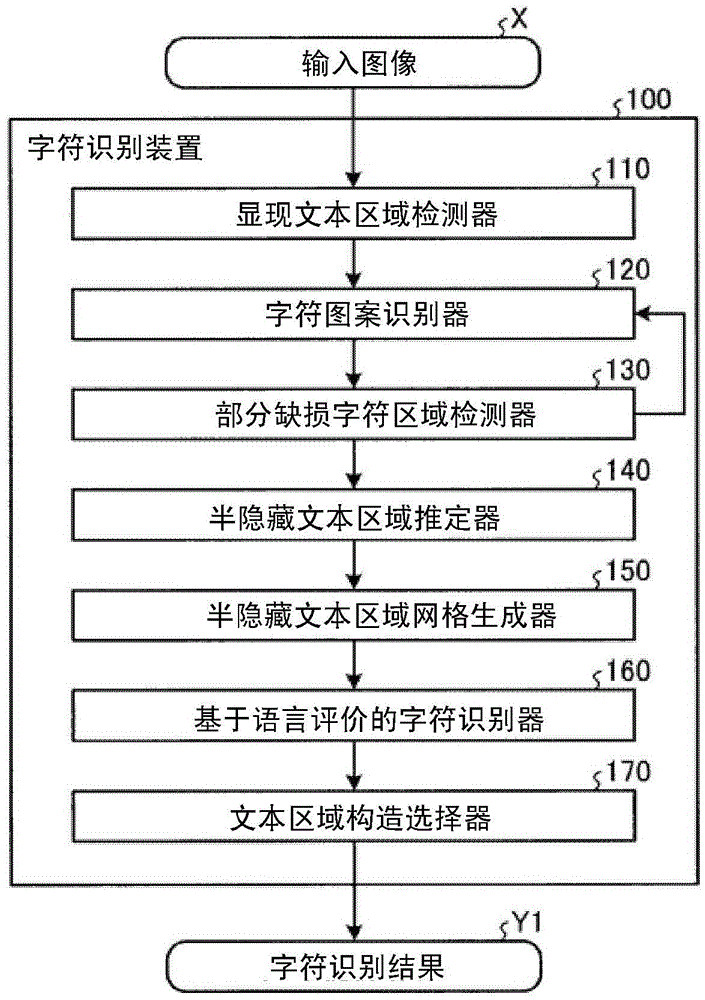
The invention provides a character recognition device and method, an image display device, and an image retrieval device. According to an embodiment, the character recognition device includes a detector, first and second recognizers, an estimator, a second recognizer, and an output unit. The detector is configured to detect a visible text area including a visible character from an image. The first recognizer is configured to perform character pattern recognition on the visible text area, and calculate a recognition cost according to a likelihood of a character pattern. The estimator is configured to estimate a partially-hidden text area into which a hidden text area estimated to have a hidden character and the visible text area are integrated. The second recognizer is configured to calculate an integrated cost into which the calculated cost and a linguistic cost corresponding to a linguistic likelihood of a text that fits in the entire partially-hidden text area are integrated. The output unit is configured to output a text selected or ranked based on the integrated cost.
Owner:KK TOSHIBA +1
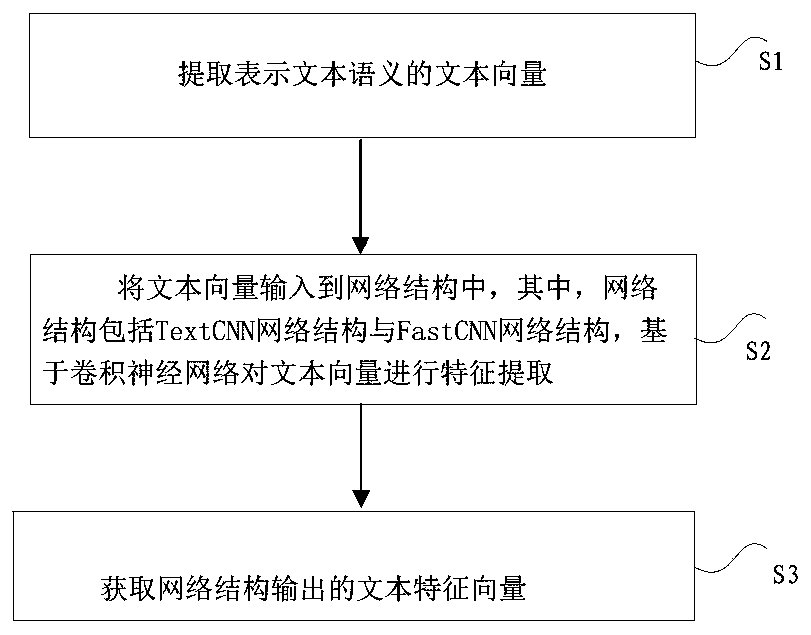
Text semantic analysis method and system
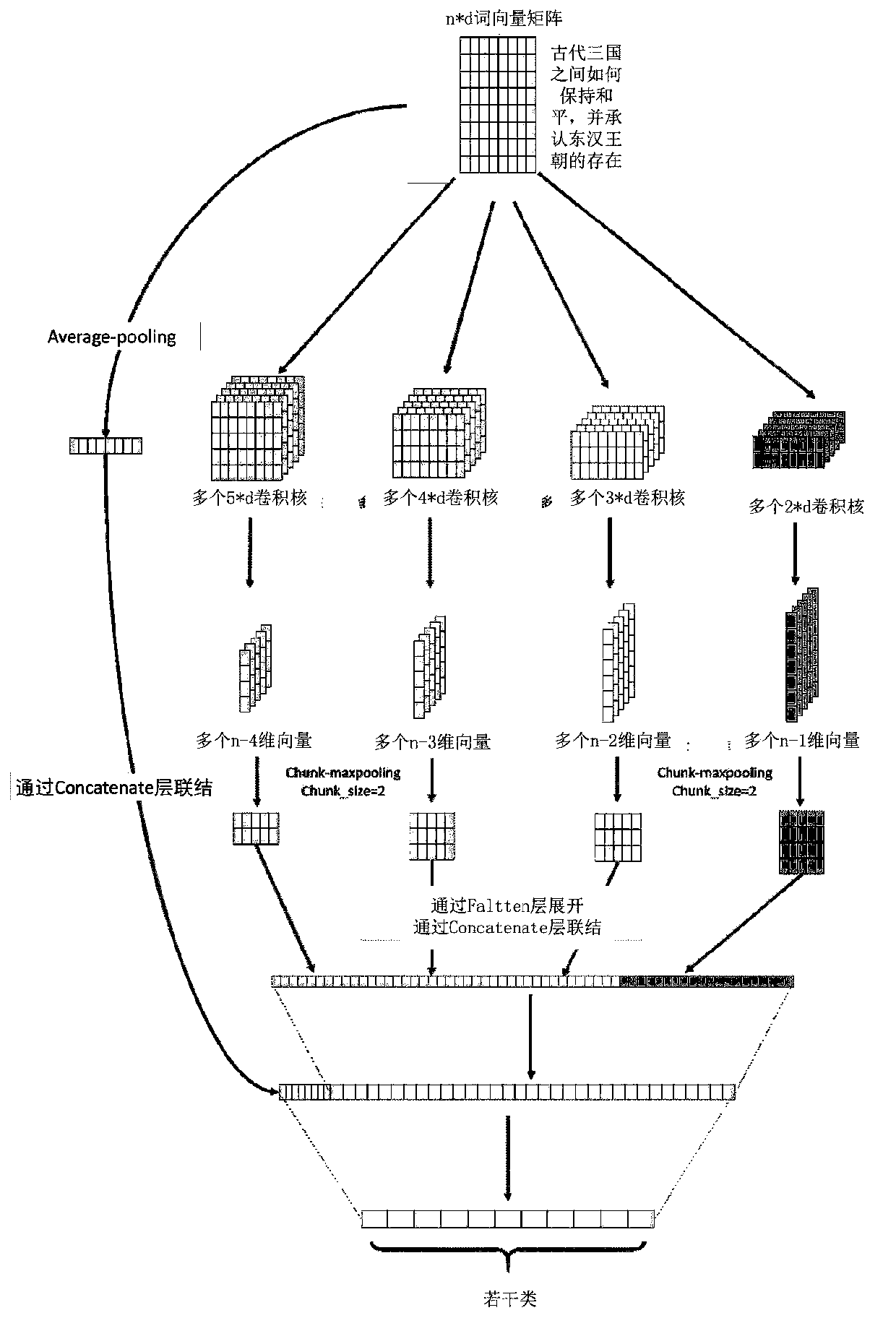
PendingCN111241849AEfficient and accurate classification resultsIncrease widthSemantic analysisNeural architecturesFeature extractionResidual neural network
The invention provides a text semantic analysis method and system, wherein the method comprises the steps: extracting a text vector representing text semantics, and inputting the text vector into a network structure which is based on a convolutional neural network and comprises a TextCNN and a FastCNN, and carrying out feature extraction. According to the method, the types or the number of convolution kernels are increased in the TextCNN; the width of the network structure is increased; the feature extraction capability of a convolution layer is greatly enhanced; a connection mode similar to a'residual neural network structure' is adopted, so that a first vector output by the convolution layer is connected with a text vector compressed by the FastCNN network structure to form a second vector, the second vector is transmitted to an output layer through a full connection layer, and the probability that the text vector classifies various categories is obtained. The initial text vector extracted from text semantics is mapped into a series of hidden text vectors through TextCNN convolution pooling nonlinear processing, FastCNN linear processing and other screening modes, and the classification result of the text vectors is obtained more efficiently and accurately.
Owner:CHONGQING UNIV OF TECH
Text document digital watermark embedding and extracting method
InactiveCN103310130AImprove concealmentImprove securityDigital data protectionProgram/content distribution protectionWord processingMATLAB
The invention provides a text document digital watermark embedding and extracting method. According to the invention, the watermark embedding is characterized in that raw information is made into a binary image; matlab and other programming softwares are adopted for reading out binary matrixes in one-to-one correspondence with the binary image to serve as the watermark information; '0' and '1', the two binary code characters, are written into a font object library with a TrueType coinage program to generate a secret key; a windows 'internal code' input method is adopted to call binary code characters, and the binary matrix is inserted into the text document; finally a hidden text function of word processing software is adopted for hiding the imbedded binary matrix, so that the watermark embedding is completed. According to the invention, through raw information conversion and application of the secret key, the raw information is better hidden; meanwhile, due to hiding of the watermark information, an interpolator can not easily find the watermark, so that the preventive performance is improved. Therefore, the security of the raw information is greatly enhanced.
Owner:XIAN UNIV OF SCI & TECH
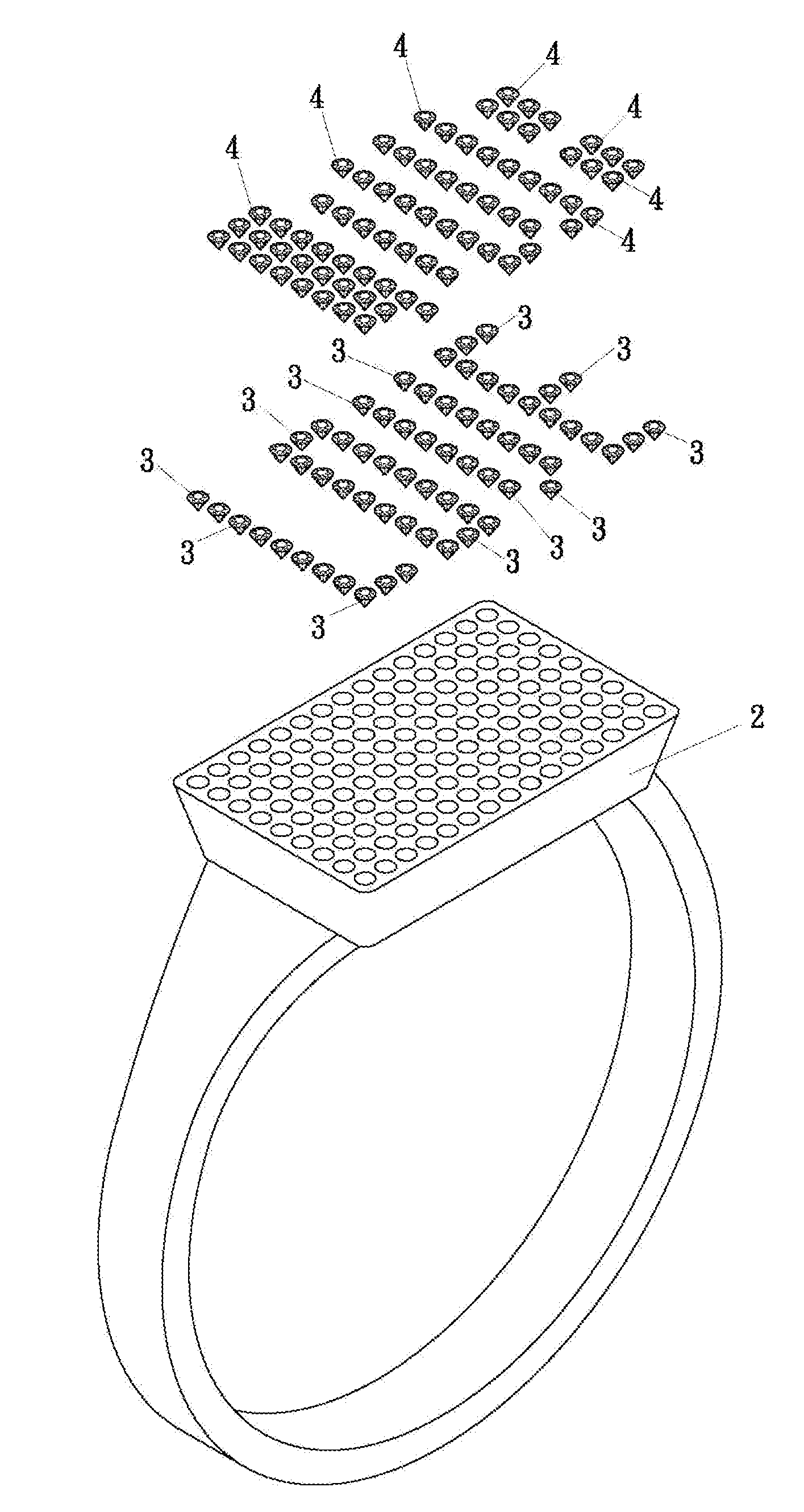
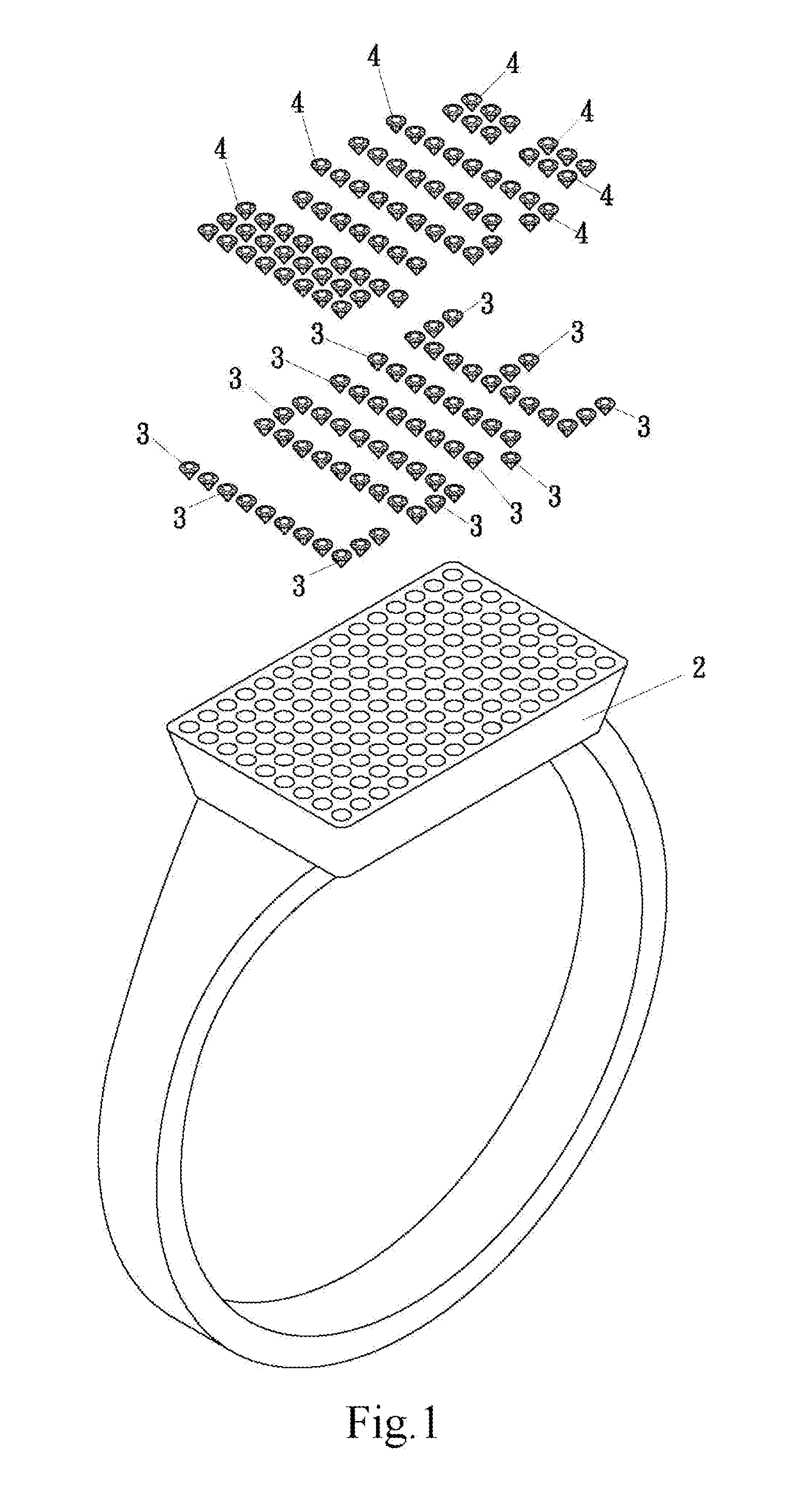
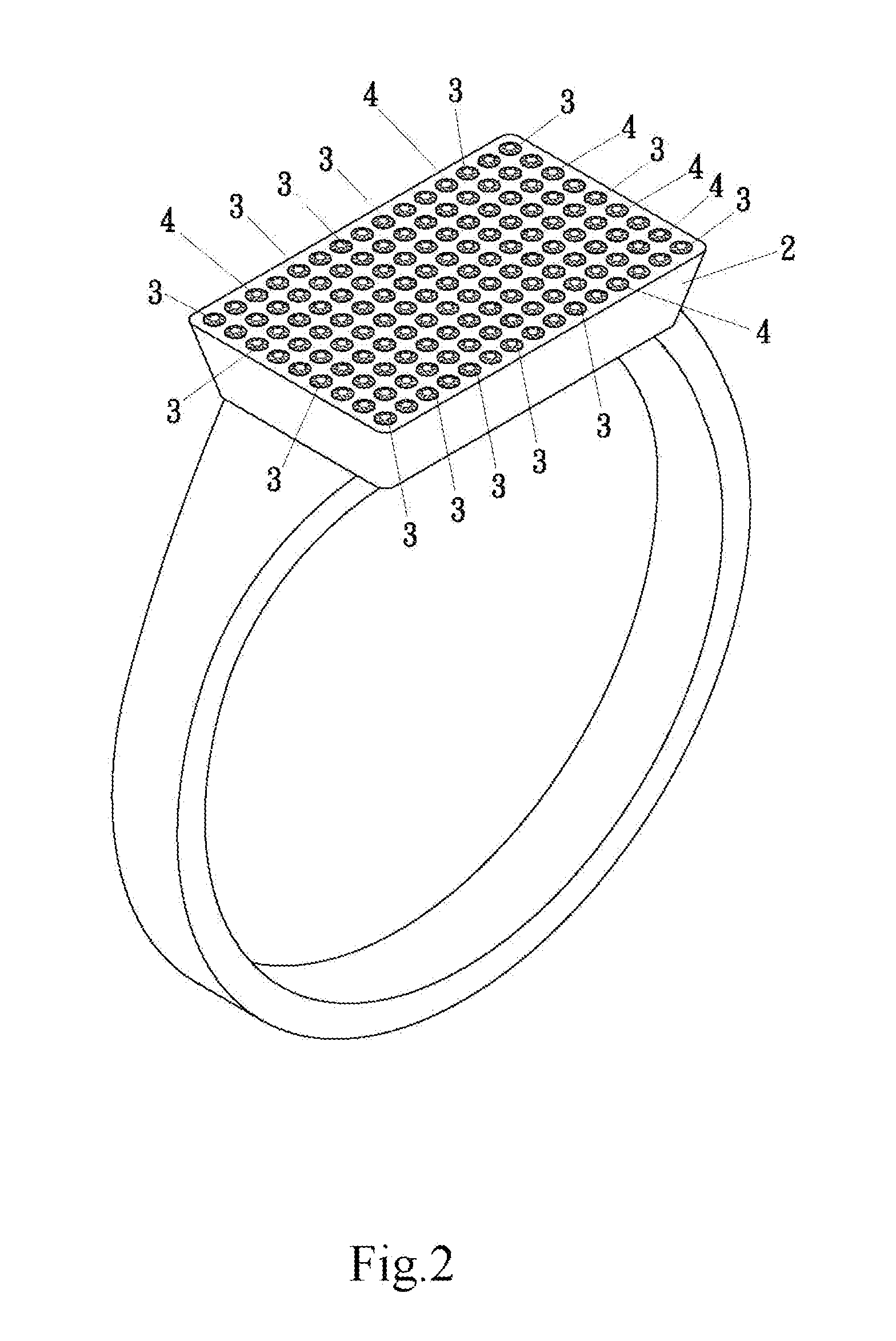
Natural fluorescent diamond ornament that emits multi-color light and hidden text/pattern
A natural fluorescent diamond ornament that emits multi-color light and hidden text / pattern includes an ornament base, multiple natural fluorescent diamonds inlaid on the ornament base and multiple natural non-fluorescent diamonds inlaid on the ornament base. Each of the natural fluorescent diamonds and the natural non-fluorescent diamonds is polygonal, refractive, and light-pervious. When exposed under UV light, the multiple natural fluorescent diamonds inlaid on the ornament base of the ornament will emit purplish-blue light which is distinct from the light emitted by the natural non-fluorescent diamonds inlaid on the ornament base. When the multiple natural fluorescent diamonds are arranged in a predetermined pattern and exposed to UV light, the natural fluorescent diamonds arranged in the predetermined pattern will emit purplish-blue light to exhibit a creative configuration that is amazingly mysterious and novel.
Owner:LIU SHU FEN
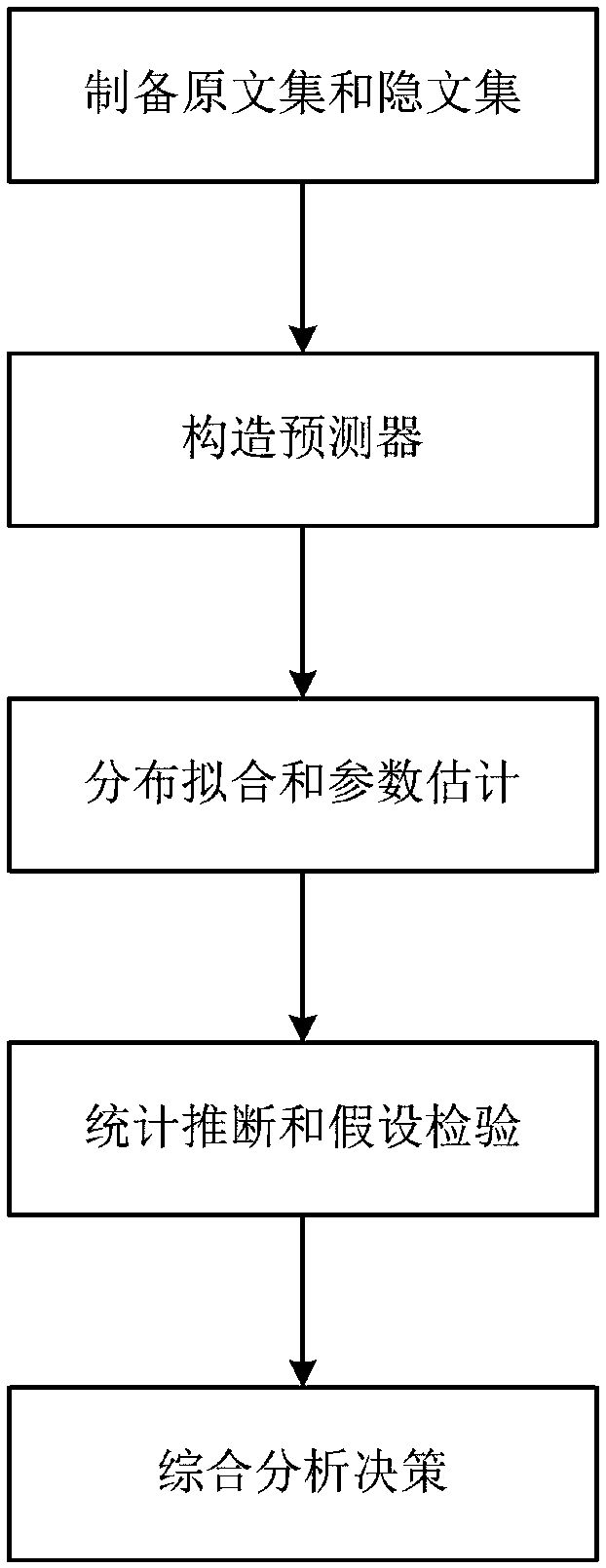
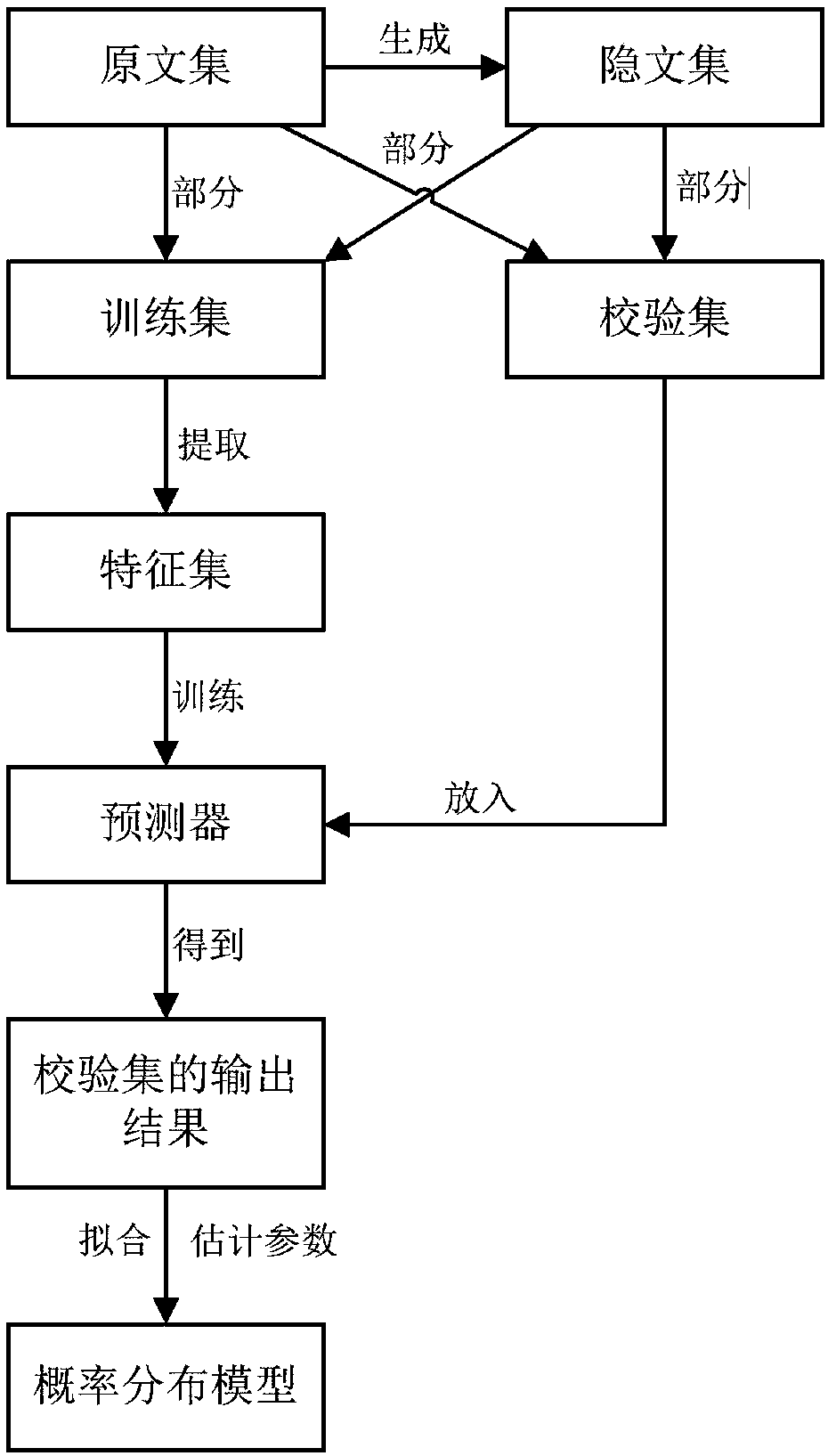
Multimedia integrated steganography analysis method based on window hypothesis testing
ActiveCN106530199AReduce false alarm rateSteganographic confidence is highSpeech analysisCharacter and pattern recognitionSteganalysisHypothesis
The invention relates to a multimedia integrated steganography analysis method based on window hypothesis testing. The method comprises the steps of (S1) preparing an original text set and a hidden text set, and dividing a training set and a testing set, (S2) extracting characteristic of the training set, and training to obtain a predictor, (S3) placing the testing set into the predictor to obtain output, fitting a probability distribution model according to the output, and estimating the parameter of the model by using the output, (S41) sampling the testing set according to the sizes of different windows, (S42) obtaining the null hypothesis and alternative hypothesis of a hypothesis test according to the probability distribution model and parameter selected in the (S3), (S43) according to the specific false alarm rate and false negative rate of a user, determining the judgment condition of the hypothesis test with the combination of the sampling scale of the windows, and carrying out statistical inference and window hypothesis testing, and (S5) carrying out comprehensive analysis decision on the result of the window hypothesis test. According to the method, whether the sample comprises steganography information or not can be detected, the false alarm rate and false negative rate of integrated steganography analysis can be reduced, and the running speed of steganography analysis is improved.
Owner:XIAMEN UNIV
Auxiliary recitation system with hidden text
InactiveCN107808556ASolve the display effectSolve hidden technical problemsElectrical appliancesComputer graphics (images)Computer terminal
The invention discloses an auxiliary recitation system with a hidden text. The system comprises a marking pen for marking a content in a written material, a camera for obtaining an original image of the written material that has been marked, an image processor for carrying out blurring image on the marked content in the original image, and a display screen for displaying the original image and theblurred image according to click switching of a user. Therefore, the user can complete a recitation task only by a mobile terminal without the need to carry all recitation materials; and with the marking by the marking pen, a technical problem that a recitation content is displayed and hidden difficulty is solved.
Owner:SHANGHAI GEZHI HIGH SCHOOL
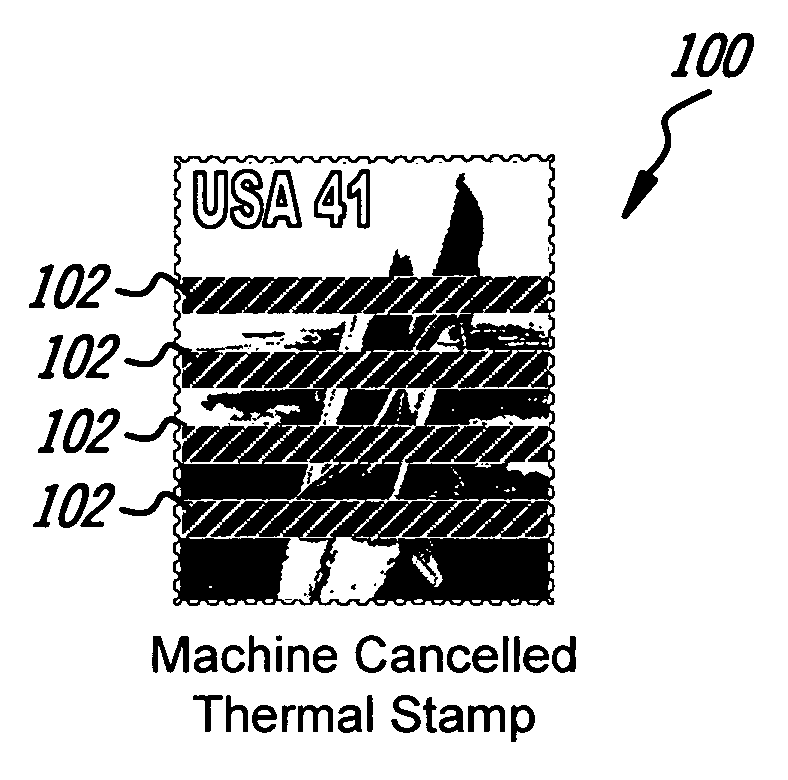
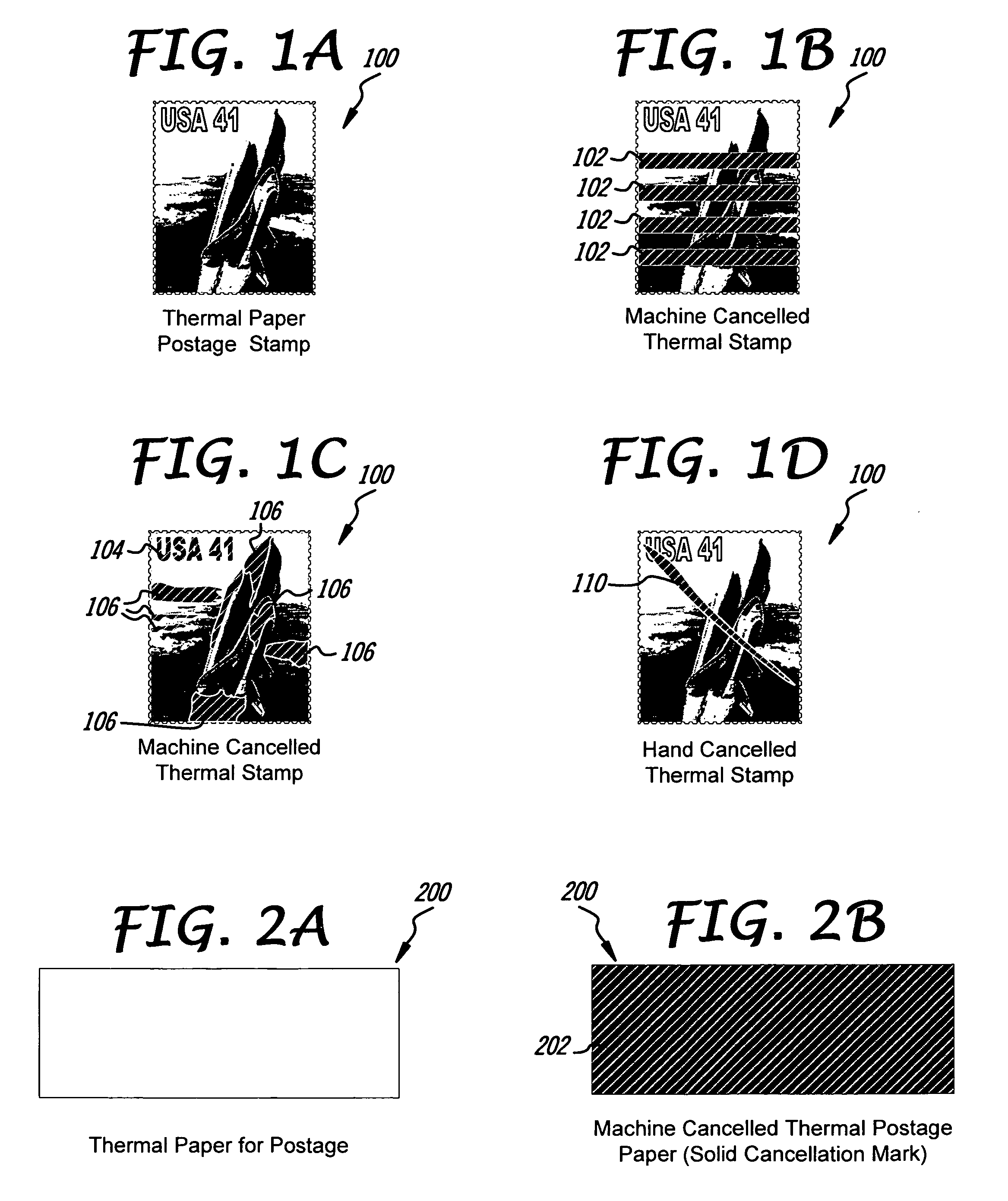
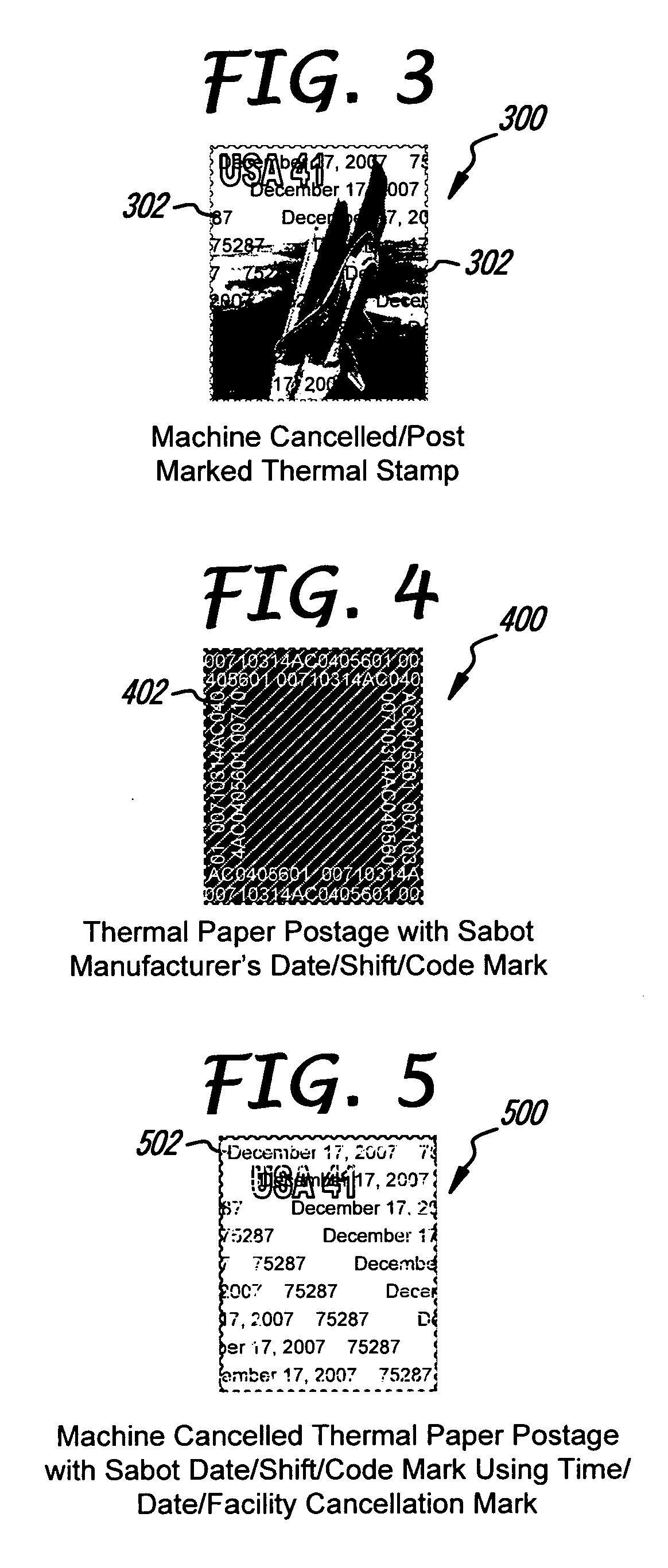
Stamp, envelope and meter in sticking, printing and cancelling
The present invention is directed to a system for thermally cancelling postage and a thermally cancellable picture postage stamp for use therein. A picture postage stamp is disclosed wherein the design and postage information are affixed on thermally reactive paper. Alternatively, the indicia may be comprised of thermally reactive inks or dyes. Cancelling a thermally cancellable picture postage stamp is accomplished with a heat source such as a cancellation write head. Hidden text of code can be embedded in the thermal paper and the cancellation mark can be any indicia or information that can be generated by a thermal print head. Cancelling the thermally cancellable picture postage stamp may also be accomplished manually with a pointed instrument or any semi hard edge such as a pen cap, ring or fingernail. Cancellation of the present thermally cancellable picture postage stamp can be further verified by placing the stamp on a presently described envelope or mailer having a thermally reactive area for receiving postage and cancellations. Using an envelope with a thermally reactive area allows for thermal cancellations that extend beyond the boundary of the thermally cancellable picture postage stamp, thereby effectively matching the thermal cancellation of the stamp to the cancellation on the envelope. The present thermally cancellable picture postage stamps may be manually applied using a cancellation gun that simultaneously applies postage and cancels same on a mailer.
Owner:LIU ZHONG REN
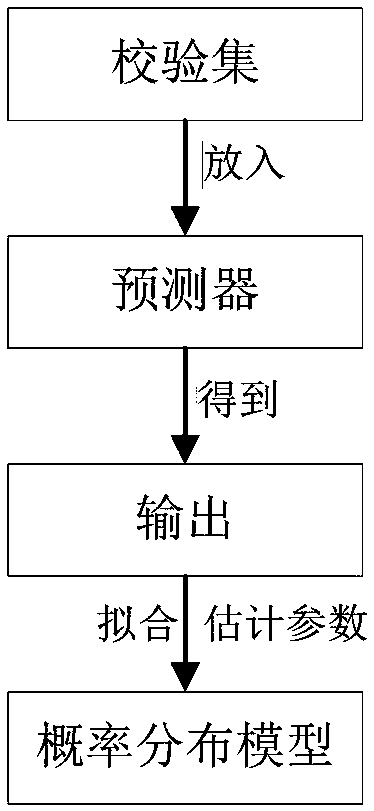
Multimedia Synthetic Steganalysis Method Based on Window Hypothesis Testing
ActiveCN106530199BReduce false alarm rateSteganographic confidence is highSpeech analysisCharacter and pattern recognitionSteganalysisHypothesis
The invention relates to a multi-media comprehensive steganalysis method based on a window-type hypothesis test, comprising the steps of: S1 preparing an original text set and a steganographic set, and dividing a training set and a verification set; S2 extracting features from the training set, and training to obtain a predictor; S3 puts the verification set into the predictor to get the output, fits the probability distribution model according to the output, and uses the output to estimate the parameters of the selected model; S41 samples the test set according to different window sizes; S42 according to the probability selected in step S3 Distribution model and parameters to obtain the null hypothesis and alternative hypothesis of hypothesis testing; S43 determines the judgment conditions of hypothesis testing according to the false alarm rate and missed detection rate specified by the user, combined with the sampling scale of the window, and performs statistical inference and window type hypothesis testing ; S5 conducts comprehensive analysis and decision-making on the results of the window hypothesis test. The invention can detect and determine whether steganographic information is contained in samples, reduce the false alarm rate and missed detection rate of comprehensive steganographic analysis, and improve the operation speed of steganographic analysis.
Owner:XIAMEN UNIV
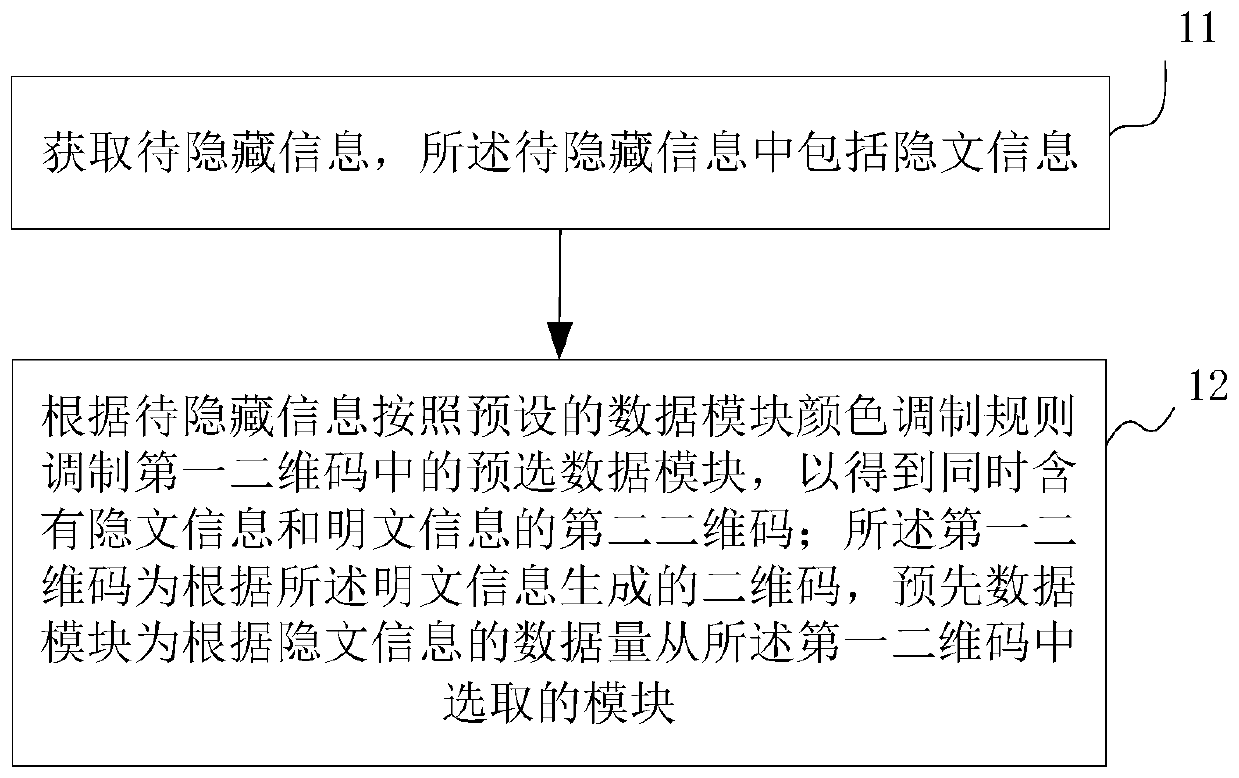
Information hiding method and device based on two-dimensional code and electronic device
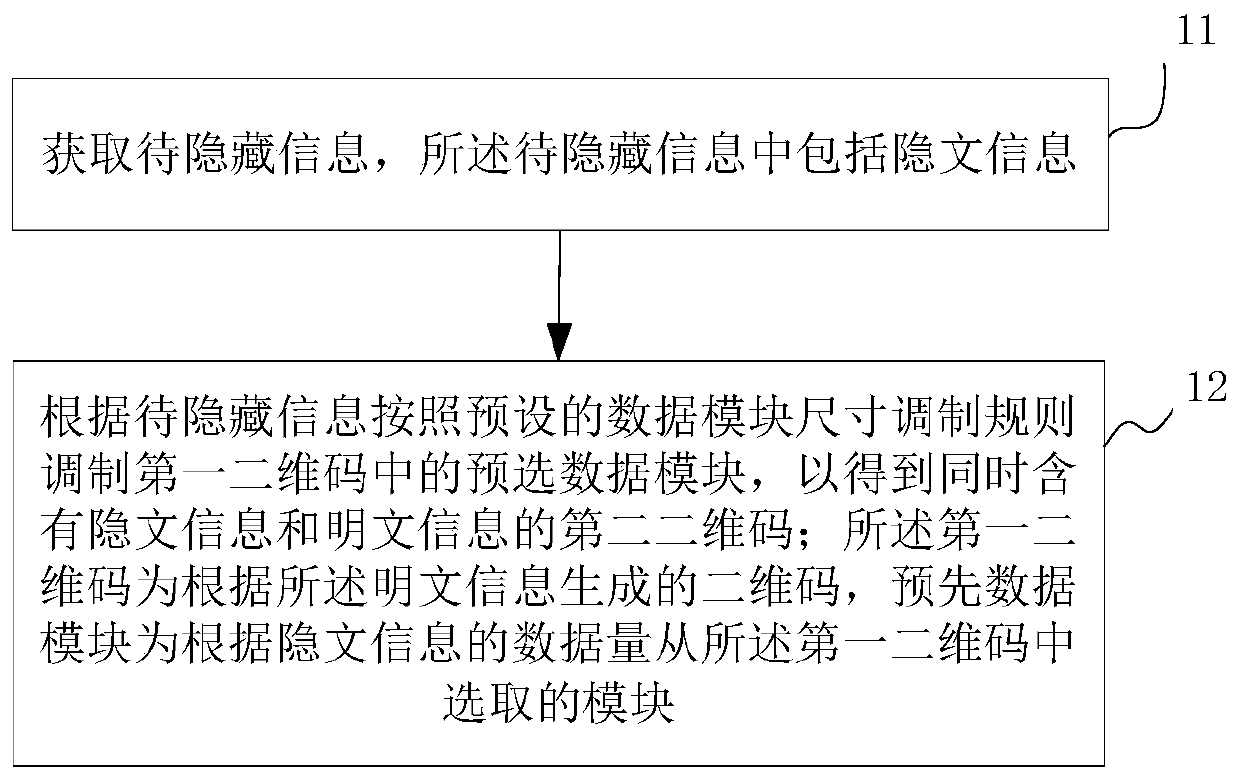
PendingCN109784454AWon't draw attentionAvoid attackRecord carriers used with machinesPlaintextComputer module
The embodiment of the invention relates to the technical field of information security, in particular to an information hiding method and device based on a two-dimensional code and an electronic device. The information hiding method comprises the steps of obtaining to-be-hidden information, wherein the to-be-hidden information comprises hidden text information; modulating a pre-selected data module in the first two-dimensional code according to the to-be-hidden information and a preset data module color modulation rule to obtain a second two-dimensional code containing hidden text informationand plaintext information at the same time; wherein the first two-dimensional code is a two-dimensional code generated according to the plaintext information, and the pre-data module is a module selected from the first two-dimensional code according to the data size of the ciphertext information; wherein the ciphertext information in the second two-dimensional code can be identified by a preset identifier according to a preset data module color modulation rule. The embodiment of the invention has the advantages that the two-dimensional code cannot be suspected to be a special two-dimensional code, so that the attention of an attacker cannot be caused, and the attack possibility is avoided from the source.
Owner:王诗会 +1
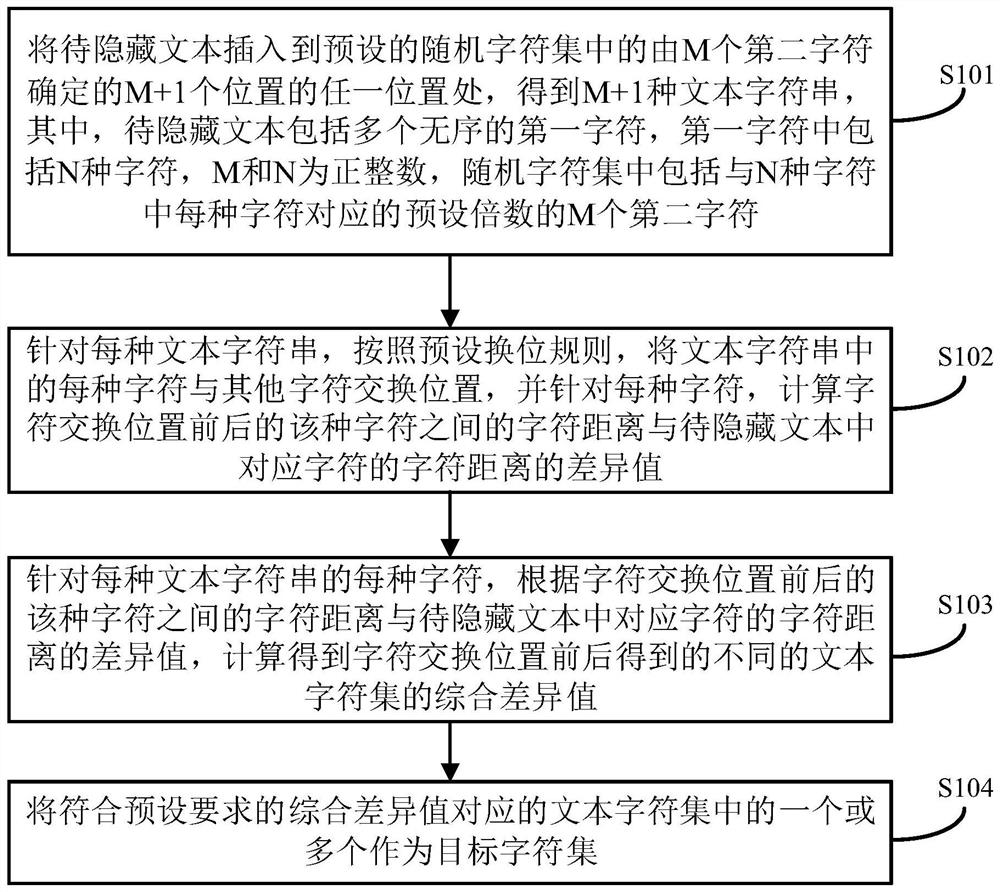
Text information hiding method and device, electronic equipment and storage medium
ActiveCN111950007AReduce the chance of detectionReduce the degree of varianceDigital data protectionProgram/content distribution protectionAlgorithmEngineering
The embodiment of the invention provides a text information hiding method and device, electronic equipment and a storage medium. The method comprises the steps of inserting a to-be-hidden text into any one of M+1 positions determined by M second characters in a preset random character set to obtain M+1 text character strings; for each text character string, exchanging the position of each character in the text character string with other characters, and for each character, calculating the difference value between the character distance between the characters before and after the character exchange position and the character distance of the corresponding characters in the to-be-hidden text; for each character of each text character string, according to the difference value between the character distance between the characters before and after the character exchange position and the character distance of the corresponding characters in the to-be-hidden text, conducting calculating to obtain the comprehensive difference value of different text character sets obtained before and after the character exchange position; and taking one or more of the text character sets corresponding to the comprehensive difference values meeting the preset requirements as a target character set.
Owner:PRANUS BEIJING TECH CO LTD
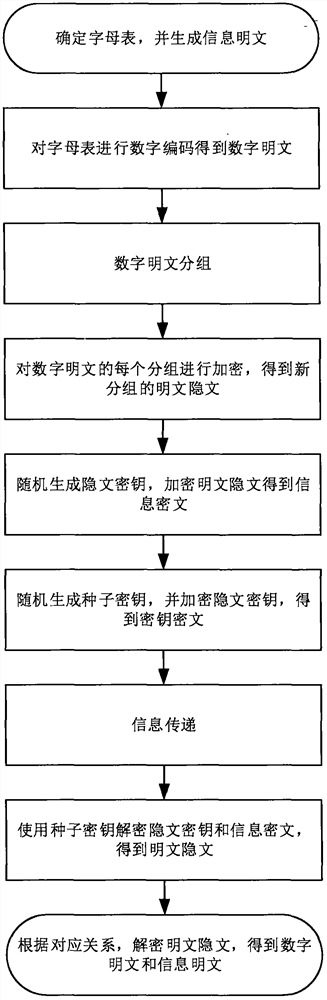
A New Shannon Perfect Secrecy Method
ActiveCN109344627BShorten the lengthEfficient methodDigital data protectionPlaintextInformation transmission
The invention discloses a novel Shannon's perfect secrecy method, which belongs to the field of information technology and includes the following steps: Step 1: determine the basic alphabet according to the information to be transmitted, and combine to form information plaintext; Step 2: encode the alphabet to obtain numbers plaintext; step 3: group the digital plaintext with a certain fixed length in order; step 4: encrypt each group of digital plaintext to obtain the plaintext and hidden text of the new group; step 5: use the permutation relationship to generate the hidden text key, Encrypt to obtain the information ciphertext; Step 6: Encrypt the cryptography key to obtain the key ciphertext; Step 7: Information transmission; Step 8: The receiver uses the seed key received by the secure channel to calculate all cryptography keys, and uses the cryptography The text key decrypts the ciphertext of the information to obtain the plaintext and hidden text; Step 9: Calculate the plaintext corresponding to the plaintext and hidden text. The encryption and decryption of the present invention are linear time, so that Shannon's perfect secrecy concept can be applied to the secure transmission of large-scale plaintext.
Owner:CHONGQING INST OF GREEN & INTELLIGENT TECH CHINESE ACADEMY OF SCI +1
A Matching Method of Analog Raster Based on Hidden Image Dot Area Ratio
The invention discloses a method for matching a simulation grating based on a hidden image lattice point area ratio. The method comprises the specific steps that a master print map is manufactured; a hidden text or image is manufactured on the manufactured master print map; a matching relation between the hidden image lattice point area ratio and a simulation matching grating area ratio is established according to hidden text or image parameters; a simulation matching grating is manufactured according to the established matching relation; the manufactured simulation matching grating is placed on the master print map to detect hidden information. According to the method for matching the simulation grating based on the hidden image lattice point area ratio, the precise matching relation between the hidden image lattice point area ratio and the simulation matching grating area parameters is obtained according to the matching algorithm between the hidden image lattice point area ratio and the simulation matching grating area parameters, the better showing effect after the simulation matching grating is added into a hidden image is achieved, the problems that according to an existing method, the matching degree of the hidden image and the simulation matching grating is not high, and the showing effect of the hidden image is not good are solved, the computing method is simple, and operation is convenient.
Owner:SHAANXI UNIV OF SCI & TECH
Text hidden method based on Chinese sentence pattern template transformation
InactiveCN101639826BConform to the semantic idiomPrevent rewritingSpecial data processing applicationsElectronic documentComputerized system
The invention discloses a text hidden method based on Chinese sentence pattern template transformation. The method utilizes the computer system to carry out watermark embedment and extraction on text information to hide the text information, comprising the following steps: (1) carrying out pre-treatment on an electronic file; (2) generating watermark information sign and setting a key; (3) carrying out part-of-speech tagging to format-free file generated in step (1) by a part-of-speech tagging module and outputting a part-of-speech tagging string of a sentence; (4) simplifying the part-of-speech tagging string output in the step (3) by a chunk tagging module; (5) loading a template module to select a sentence pattern module; (6) embedding watermark information by a watermark embedment module; (7) outputting the hidden text with embedded watermark; and (8) extracting the watermark information from the hidden text by a watermark extraction module through the key. The text hidden method changes sentence pattern through a template, avoids complex understanding and processing of grammar and semanteme, ensures the carrier text better satisfying grammar and semanteme habit and prevents blindfold rewrite.
Owner:NORTHWEST UNIV
Information hiding method and device based on two-dimensional code and electronic equipment
PendingCN109829844AWon't draw attentionAvoid attackImage data processing detailsRecord carriers used with machinesComputer hardwareInformation hiding
The embodiment of the invention relates to the technical field of information security, in particular to an information hiding method and device based on a two-dimensional code and electronic equipment. The information hiding method comprises the steps of obtaining to-be-hidden information, wherein the to-be-hidden information comprises hidden text information; Modulating a pre-selected data module in the first two-dimensional code according to the to-be-hidden information and a preset data module size modulation rule to obtain a second two-dimensional code containing hidden text information and plaintext information at the same time; Wherein the first two-dimensional code is a two-dimensional code generated according to the plaintext information, and the pre-data module is a module selected from the first two-dimensional code according to the data size of the ciphertext information; Wherein the ciphertext information in the second two-dimensional code can be identified by a preset identifier according to a preset data module size modulation rule. The embodiment of the invention has the advantages that the two-dimensional code cannot be suspected to be a special two-dimensional code, so that the attention of an attacker cannot be caused, and the attack possibility is avoided from the source.
Owner:王诗会 +1
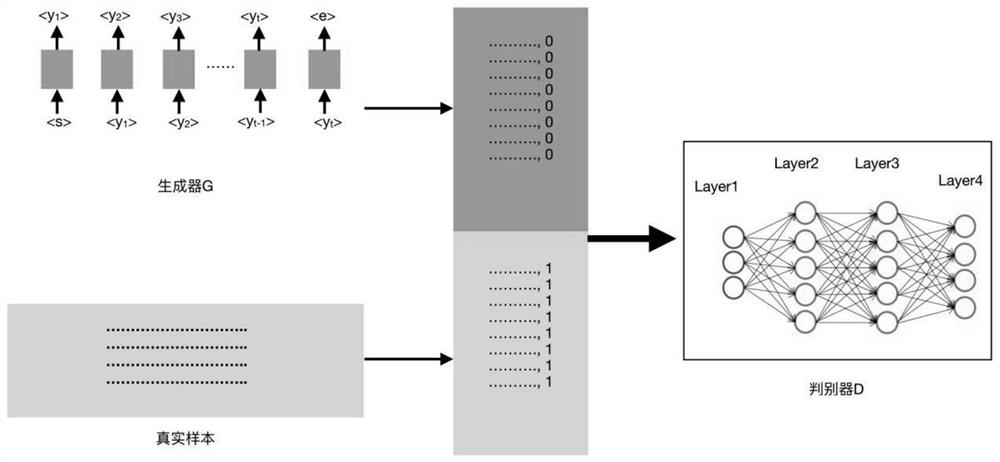
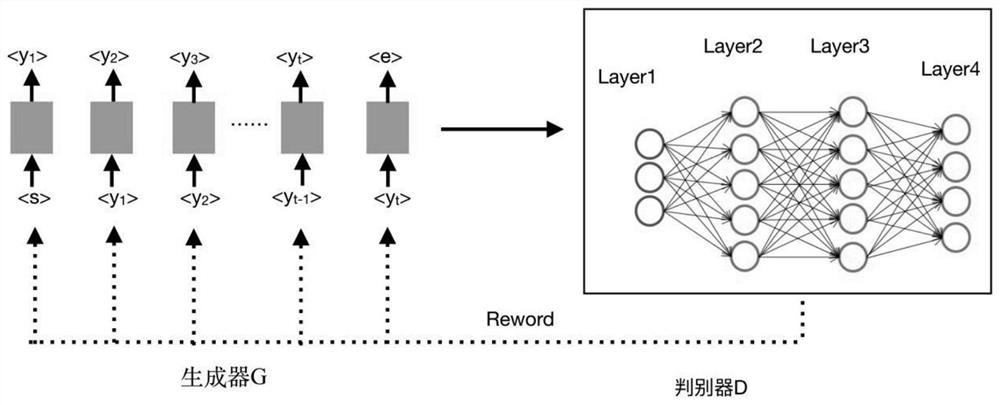
A Text Steganography Method Based on Generative Adversarial Networks
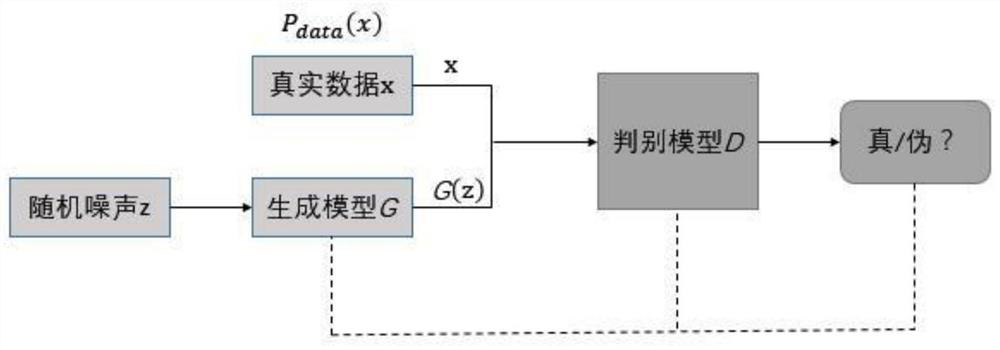
ActiveCN108923922BFitted distributionQuality improvementKey distribution for secure communicationNeural architecturesGeneration processGenerative adversarial network
The invention discloses a text steganography method based on a generative confrontation network. The model regards text steganography as a text sequence generation process, and effectively steganographically secrets text in the generated text through a key mapping table, while ensuring In order to generate high-quality text, the policy gradient optimization generator is used in the adversarial training, and finally the generative model can generate high-quality steganographic text. Compared with traditional training methods, the adversarial learning process can make the model better simulate Combine the distribution of the entire corpus to generate more reasonable phrase collocations and long texts.
Owner:BEIJING TECHNOLOGY AND BUSINESS UNIVERSITY
Text information hiding method and device
ActiveCN102542212BAchieve concealmentImprove concealmentDigital data protectionData displayElectronic document
The invention provides a text information hiding method, which includes: acquiring an original font file used by to-be-hidden text information, generating a new font file by rectifying mapping relation between font index and character codes in the original font file; rectifying the text information according to the new font file, writing the rectified text information into an electronic document; acquiring font description data of characters in the text information from the new font file when the electronic document is opened, and displaying the text information according to the acquired description data. Correspondingly, the invention further provides a text information hiding device, character codes of the text information cannot be changed and any encryption method is omitted, effect of hiding the text information can be realized simply, and safety, hiding performance and robustness are high.
Owner:NEW FOUNDER HLDG DEV LLC +1
Flexible packaging bag with hidden information pattern and method for hiding graphic information
ActiveCN105173341BPlay the role of graphic informationPlay the role of anti-counterfeitingBagsSacksEngineeringFlange
Owner:罗仕泽
Method for protecting wireless beep pager by encoding handset codes
InactiveCN1200573CRadio/inductive link selection arrangementsWireless communicationComputer hardwarePager
The beep pager possesses the coded hidden text of the handset codes. The hidden texi is obtained by executing the routine for compiling the handset codes of the beep pager with at least one key valuebeing used. With the information having additional handset codes being received, the beep pager executes the routine for decoding the hidden text of handsets with at least one key valiue so as to generate the handset codes, which is compared to the handset codes in the received information which is processed only both of codes are consistent.
Owner:E-TEN
Method for securely detecting hidden text information based on homomorphic encryption system
InactiveCN102012980BWon't leakThe test result is accurateDigital data protectionCommunication with homomorphic encryptionEngineeringProtocol for Carrying Authentication for Network Access
Owner:SUZHOU INST FOR ADVANCED STUDY USTC
A Method for Recognizing Hidden Text Graphics Using Moiré Phenomenon
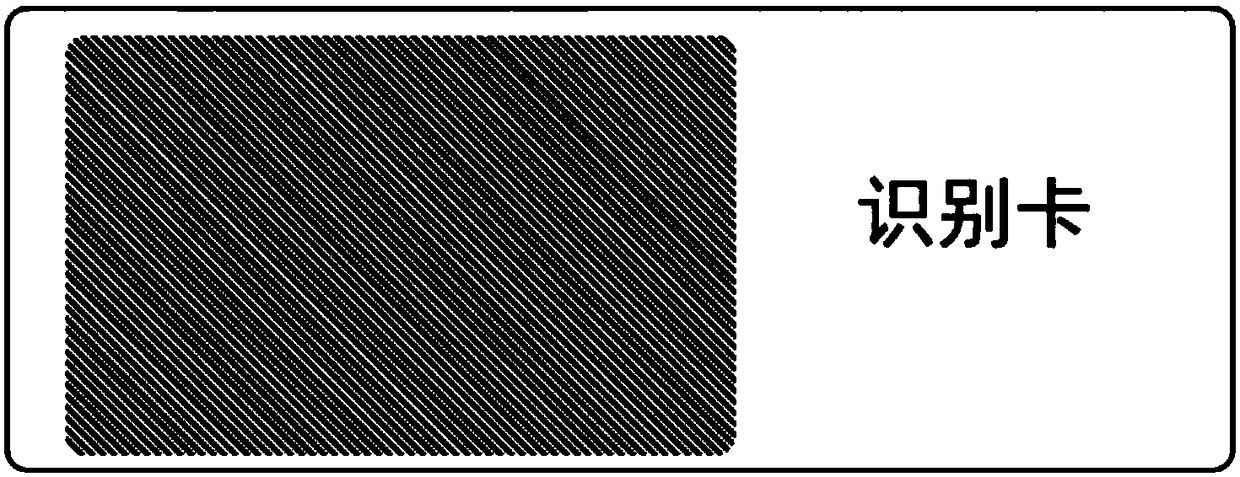
ActiveCN106274098BConvenient verificationChildlikePattern printingOther printing apparatusGraphicsPattern recognition
The invention discloses a method of identifying hidden characters and patterns by a moire phenomenon. In order to solve the improper design of the key to questions of existing textbooks and books and reduce interference on thinking to reading caused by the key, according to the method, characters and patterns and the background are screened by a same way and are distributed in a staggered manner, and the characters and patterns are hidden under high resolution screen line numbers; an identification card is manufactured by selecting proper material and printing mode, and the screening mode of the identification card is as same as that of the hidden region, so that the identification card and the hidden region are superposed to generate moire interference, and therefore, reverse interference is generated for the characters and patterns and the background, thereby increasing the difference of the two, and identifying information of the characters and patterns. The method is simple and understandable, convenient to set type and print and simple in verification operation, and the user can enjoy the pleasure of reading in a process of verifying the key.
Owner:杭州印校印务有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com