Steganalysis method based on blindness of steganalysis systems
A steganalysis and steganography technology, which is applied in the information hiding sub-field in the field of information security technology, can solve the problems of basic purpose and different ideas, and achieve the effect of improving the analysis
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment approach
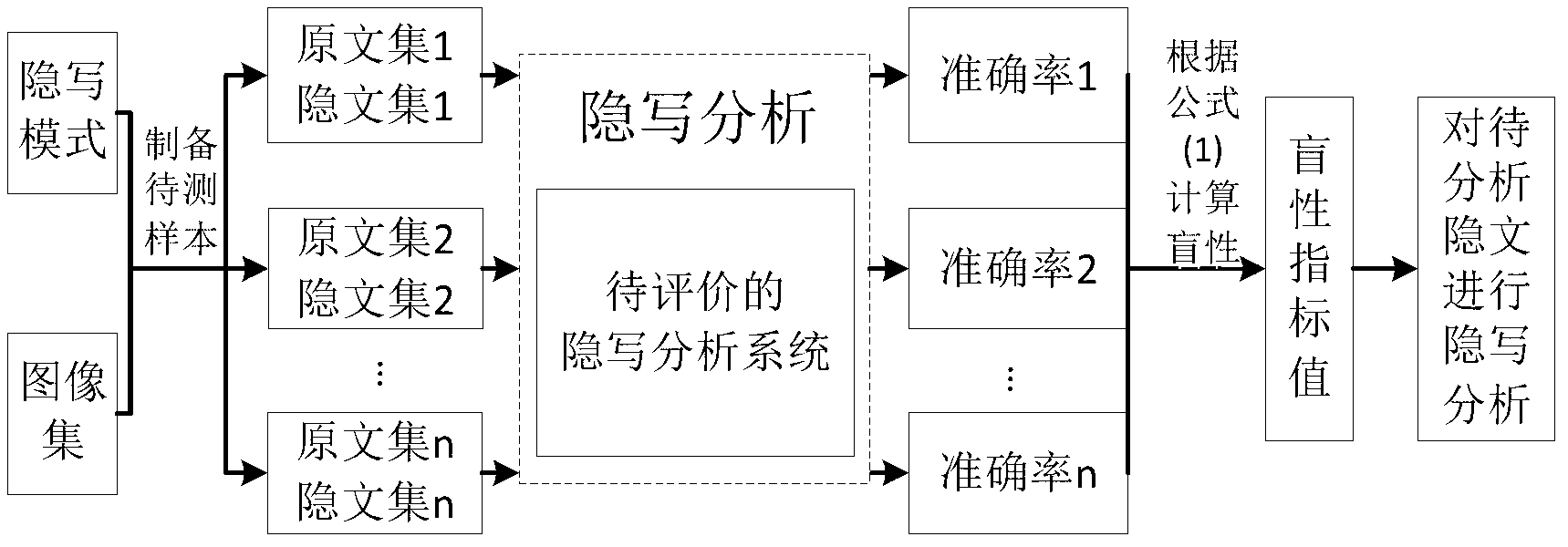
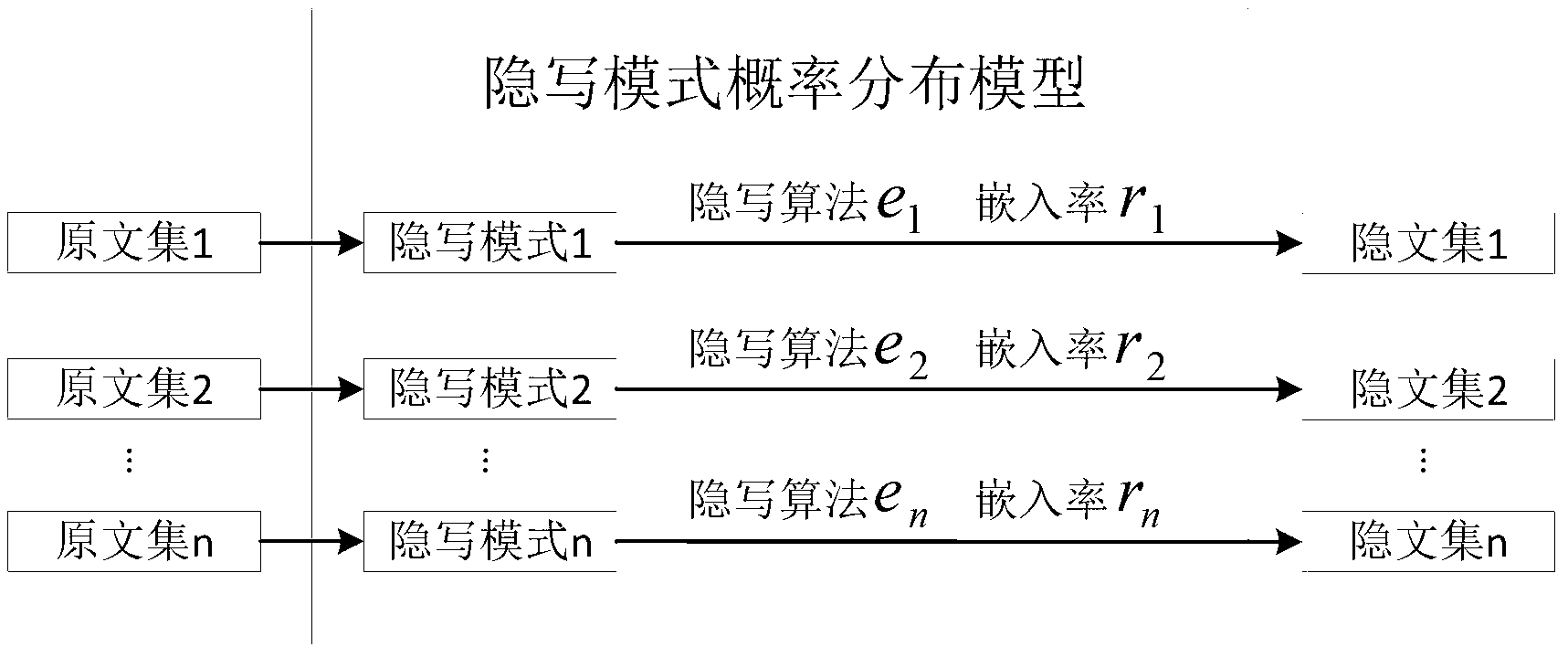
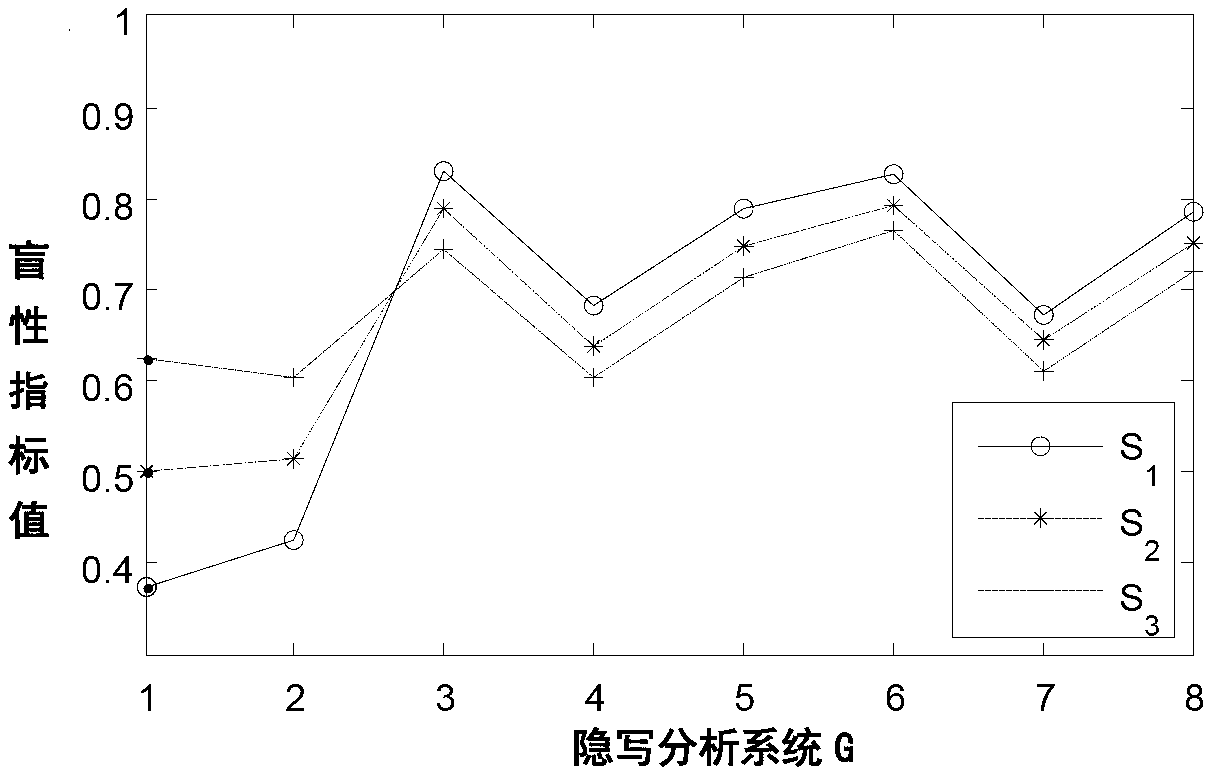
[0039] 1. Construct the probability distribution model of the steganographic mode
[0040] Select a set of steganographic methods T that may be used e ,e=1,2,…,E, and set a set of embedding rate A r ,r=1,2,…,R, thus obtaining a set of steganographic patterns S e,r . According to the experience or the prior knowledge of the occurrence probability of the steganographic algorithm, the probability distribution model of the steganographic mode under this configuration is constructed. Set steganographic mode S e,r The probability of a certain steganographic algorithm e appearing when the embedding rate is r is P e,r ,p e,r The higher the value of , the greater the possibility of the occurrence of the steganographic pattern, and ensure that the sum of the occurrence probabilities of all steganographic patterns is 1, that is: ∑P e,r =1. Tables 2 to 4 are examples of probability distribution models of three different steganographic modes.
[0041] Table 2 Probability distributi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com