Patents
Literature
78results about How to "Achieve concealment" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
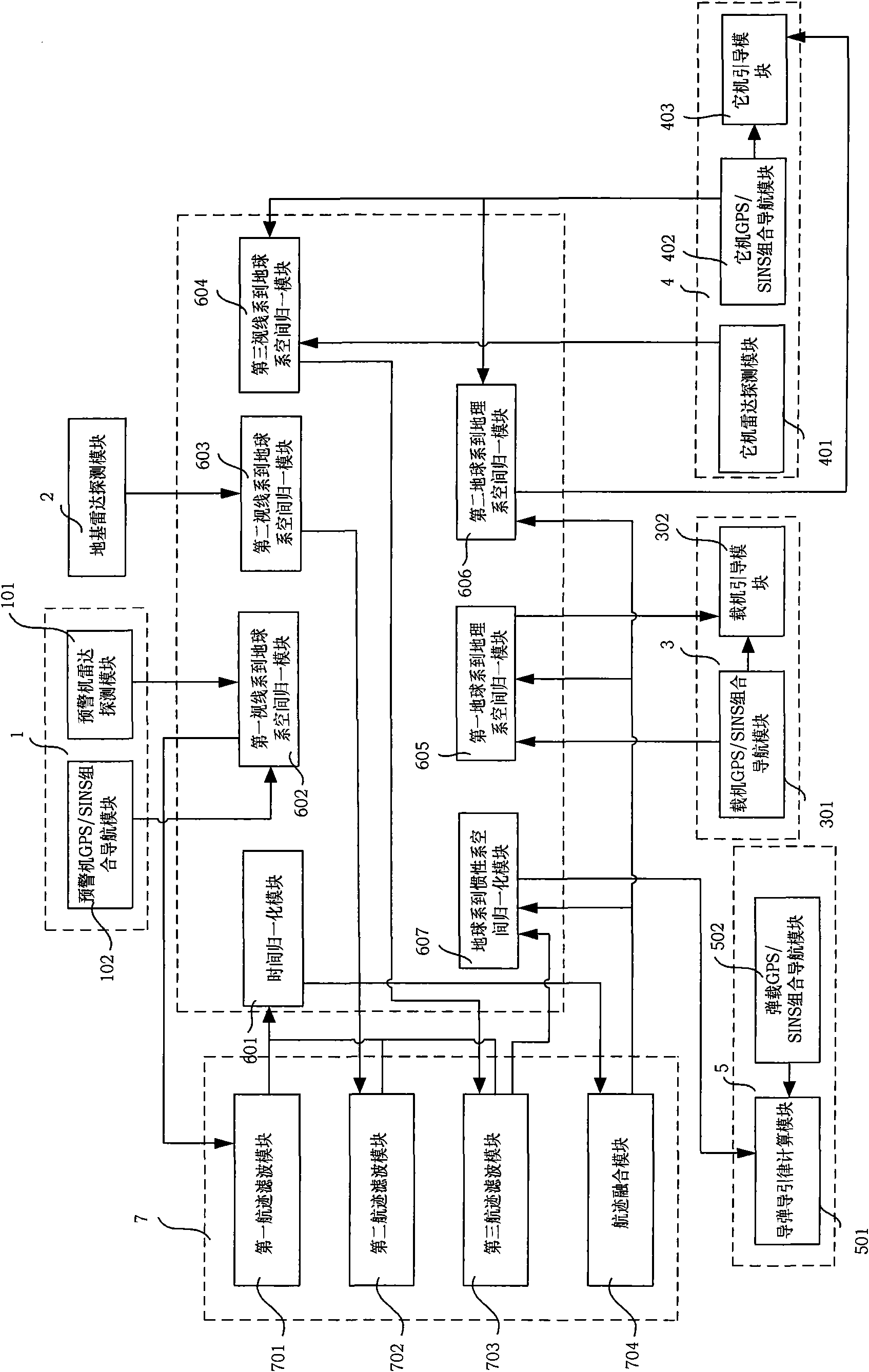
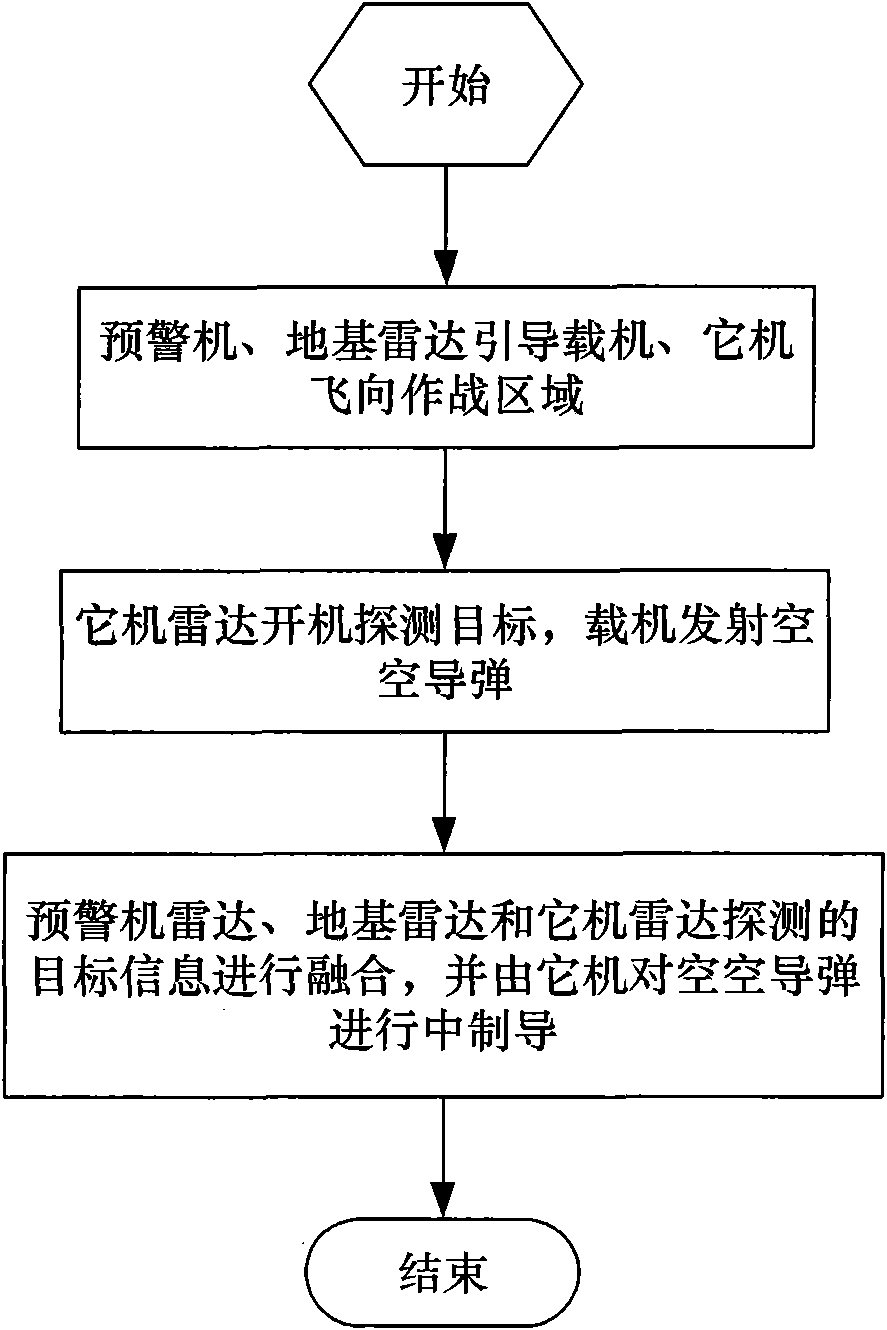
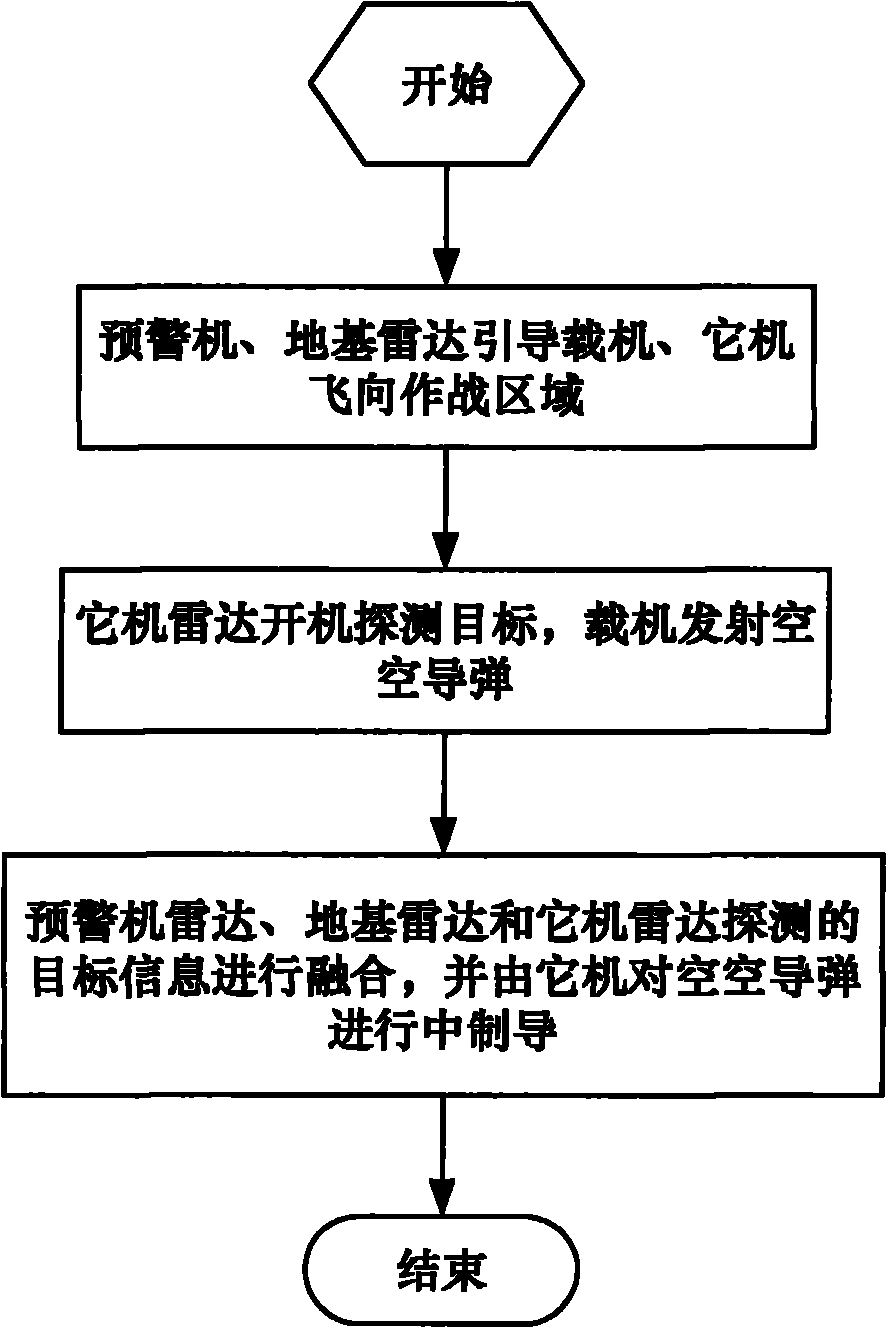
Remote air-to-air missile multi-platform cooperative guidance system and realization method thereof
InactiveCN101832738AExpand attack rangeReduce attack reaction timeAiming meansGuidance systemInformation space
The invention discloses a remote air-to-air missile multi-platform cooperative guidance system and a realization method thereof. The multi-platform cooperative guidance system comprises an early warning plane module, a ground base radar detecting module, an aerial carrier module, a friend plane module, a remote air-to-air missile module, a target information space-time normalizing module and a target information fusion module. The realization method comprises the following steps: 1. an early warning plane, a ground base radar guided aerial carrier and a friend plane fly to a war area; 2. the radar of the friend plane operates to detect a target, and the aerial carrier launches an air-to-air missile; and 3. the targets detected by the radar of the early warning plane, the ground base radar and the radar of the friend plane are fused, and the friend plane carries out midcourse guide on the air-to-air missile. By adopting a multi-platform combat network formed by the early warning plane, the ground base radar, the aerial carrier and the friend plane to provide high-accuracy target information for the remote air-to-air missile, and adopting the friend plane to perform midcourse guide on the remote air-to-air missile, a remote target can be attacked stealthily and accurately.
Owner:BEIHANG UNIV
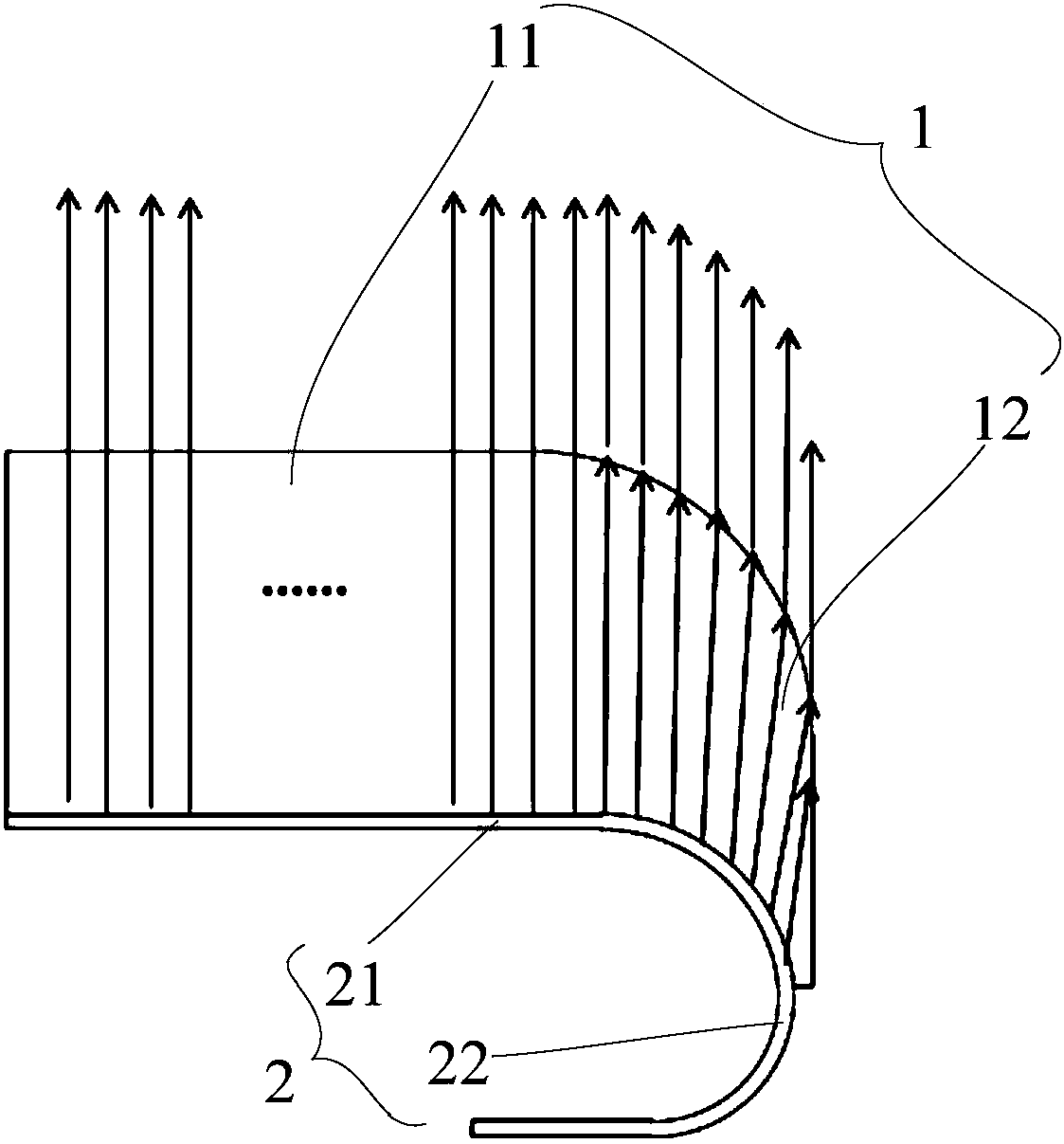
Display screen and display device
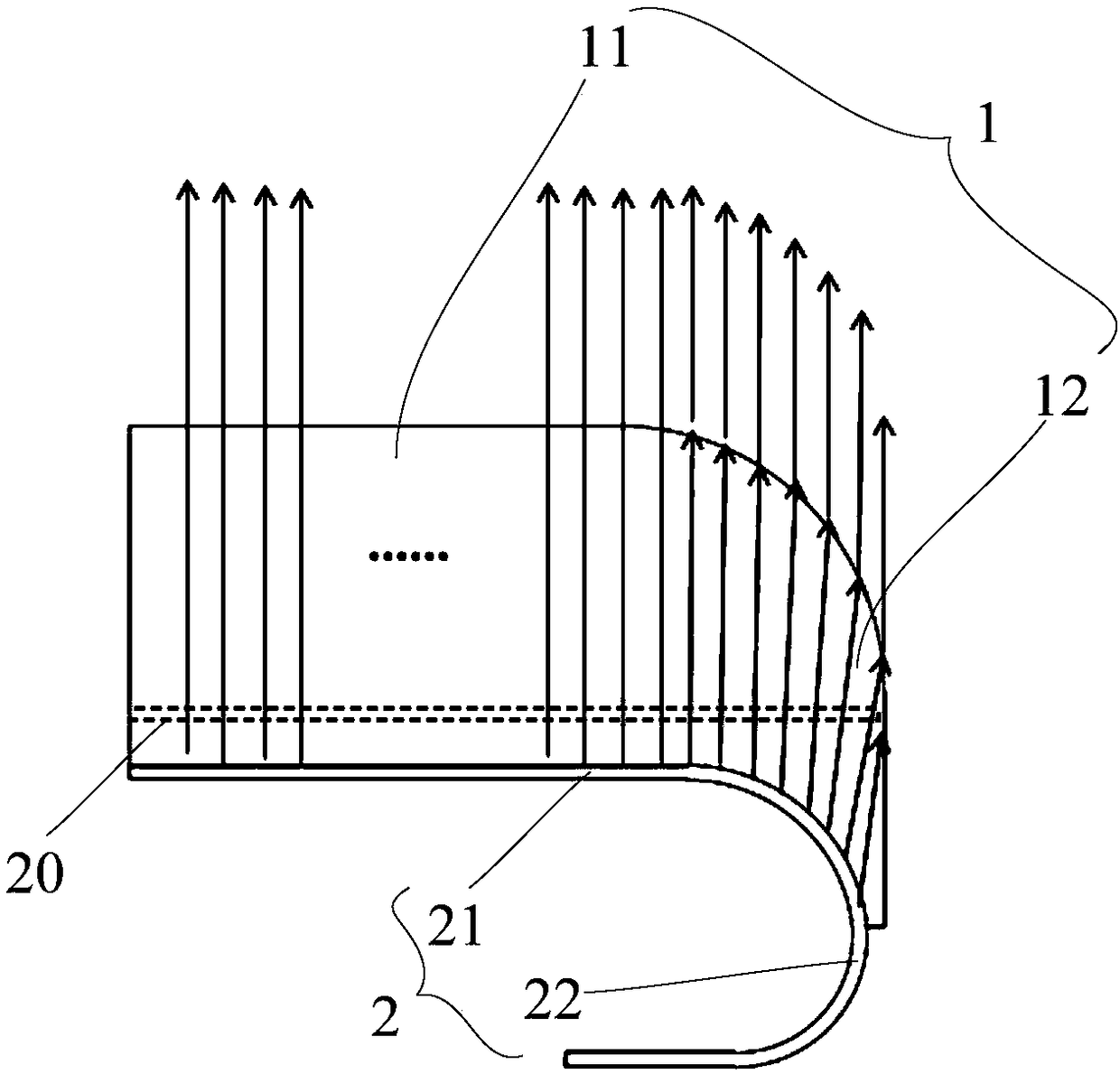
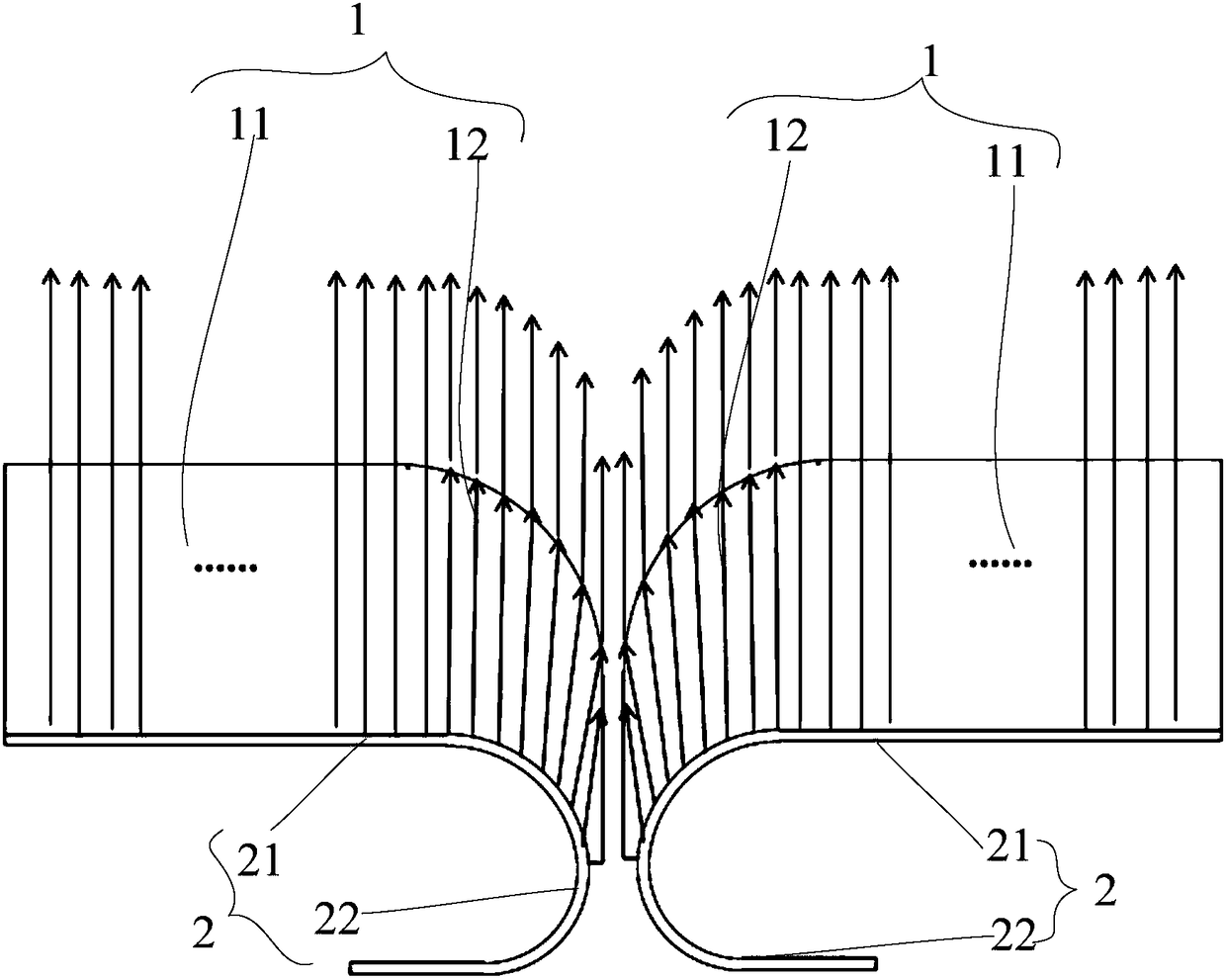
InactiveCN108279737AAchieve hidden effectAchieve concealmentDigital data processing detailsIdentification meansPixel densityEngineering
The invention provides a display screen. The display screen includes a first light transmitting area, at least one bent frame area which is bent along at least one side edge of the first light transmitting area, and a flexible display panel which overlays a transparent cover plate; the flexible display panel includes a first display area and at least one bent display area which is bent along at least one bent side edge of the first display area, wherein the bent display area of the flexible display panel fills space under the corresponding bent frame area. When light emitted by luminous pixelpoints of the bent display area of the flexible display panel of the display screen is reflected by the bent frame area of the transparent cover plate covering the bent display area, the effect can bevisually achieved that the luminous pixel points of the bent display area of the flexible display panel fill the frame area, the hidden effect of the frame is achieved, and the pixel density of the bent display area does not need to be changed.
Owner:YUNGU GUAN TECH CO LTD
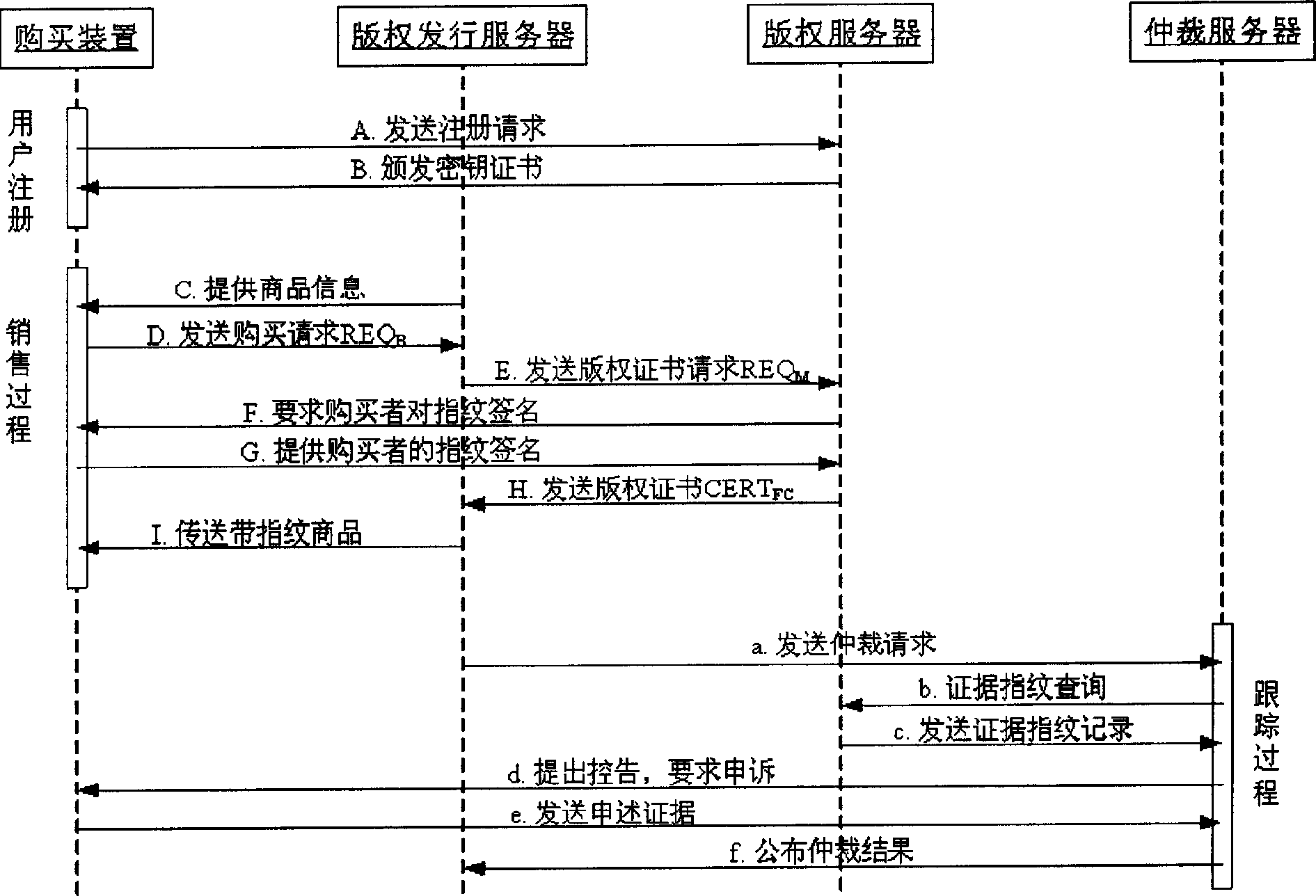
Finger print structure in digital products, its authentication and digital products issue system
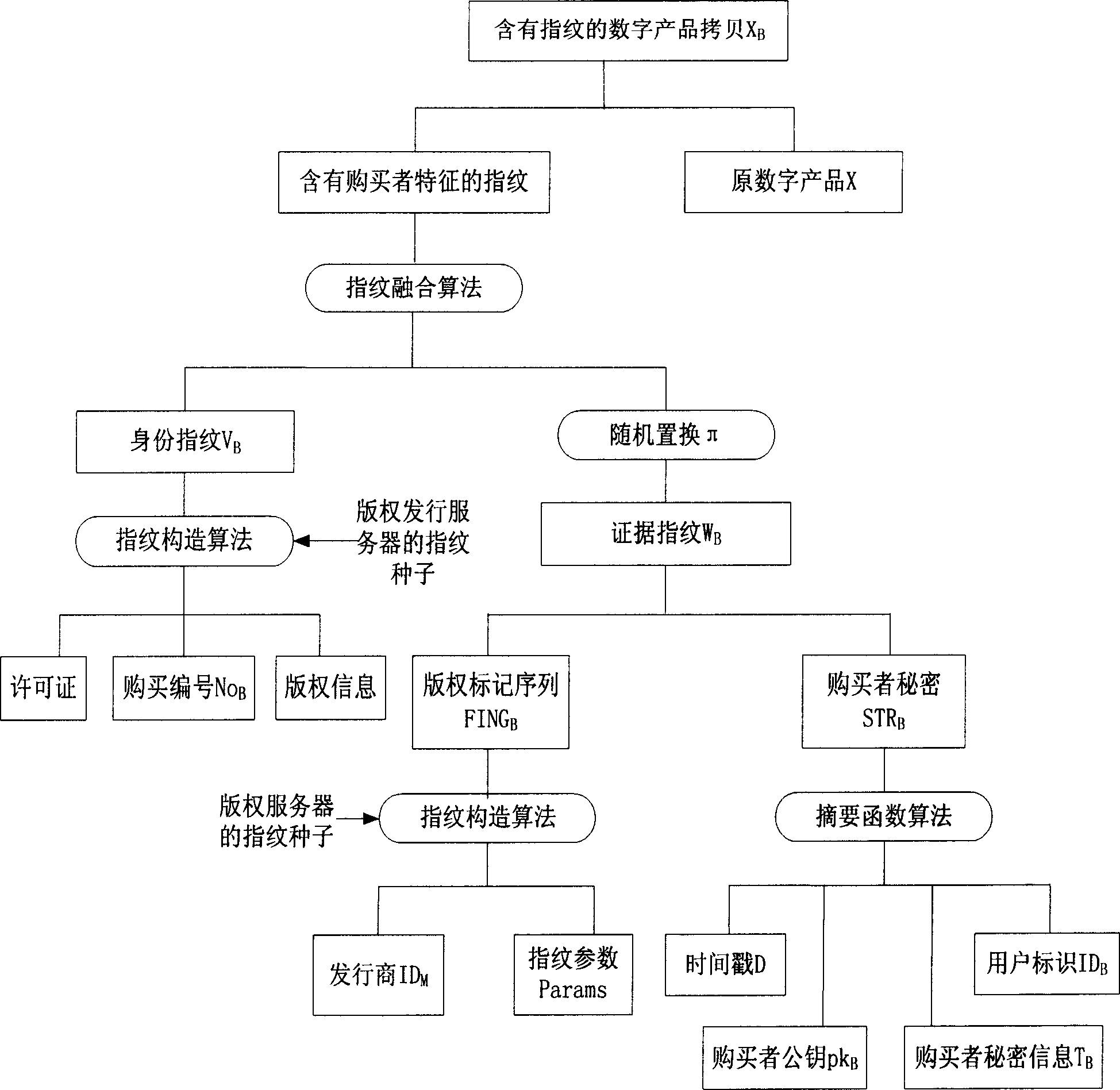
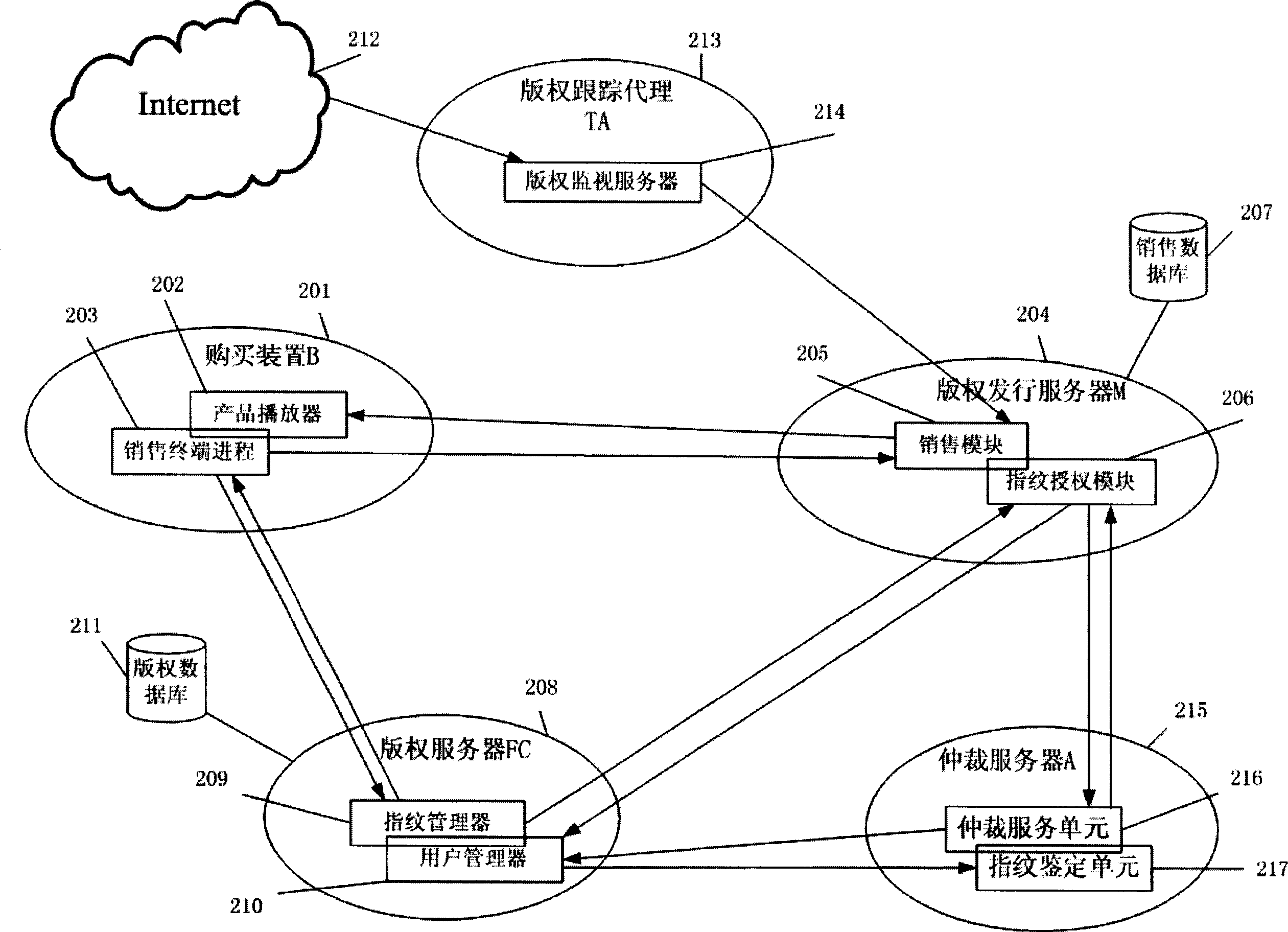
InactiveCN1834973AEnhanced construction flexibility and fingerprint security and robustnessImprove reliabilityProgram/content distribution protectionMarketingSystem safetyFingerprint
The invention relates to an in-digital product fingerprint constructing and verifying method, and the constructing method obtains purchase secret information from a purchaser, and uses a copyright server to construct an evidence fingerprint unable to be forged, and then uses a copyright issuing server to construct an ID fingerprint with license issued by the copyright server and sale information, and finally adopts fusion technique to construct a fingerprint-containing copy. And the verifying method extracts the ID fingerprint stored in the digital product to check the product license and identify the ID of the purchaser, and then checks and confirms the belonging relation by comparability of the evidence fingerprint. Correspondingly, the invention provides a digital product issuing system, comprising purchasing device, copyright issuing server and copyright server. And it provides a user-friendly and simple-to-apply method, largely improving safety and extendibility of the existing system.
Owner:PEKING UNIV
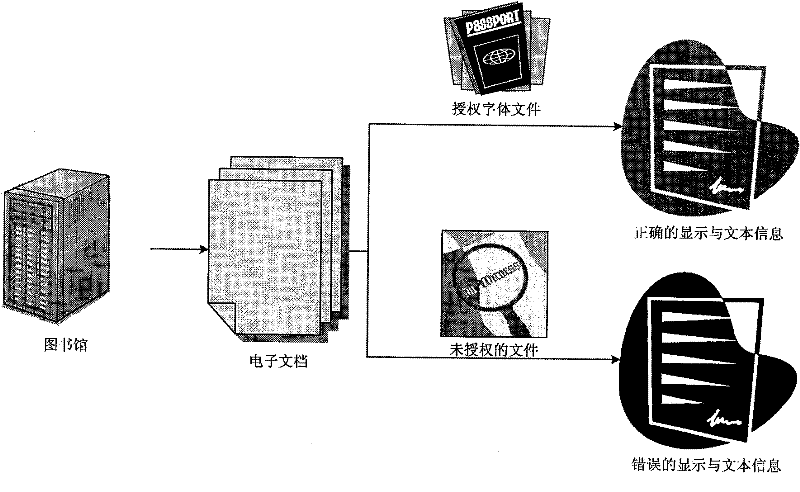
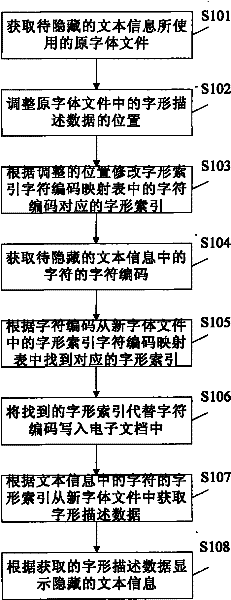
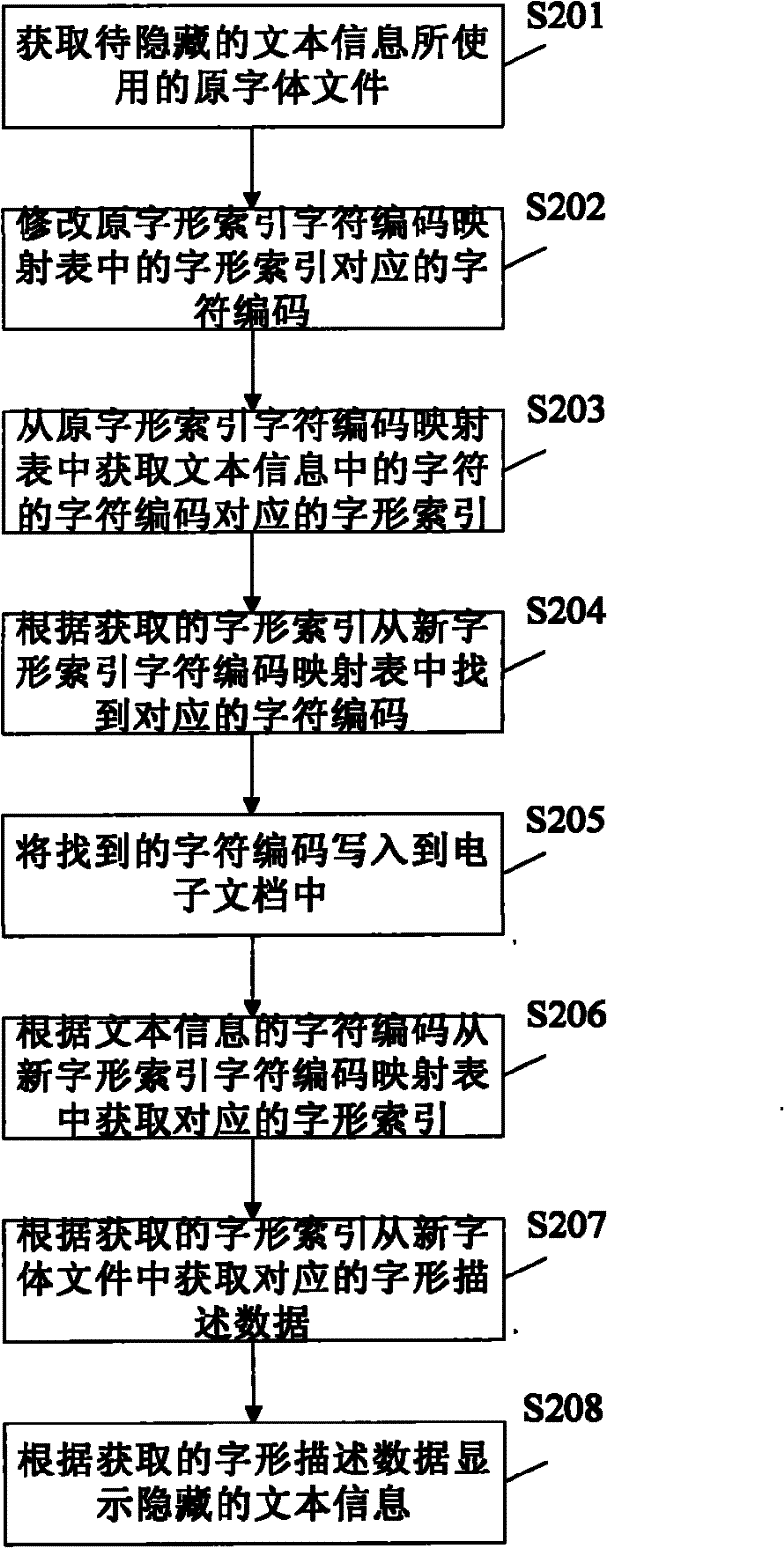
Text information hiding method and device
ActiveCN102542212AAchieve concealmentImprove concealmentDigital data protectionData displayElectronic document
The invention provides a text information hiding method, which includes: acquiring an original font file used by to-be-hidden text information, generating a new font file by rectifying mapping relation between font index and character codes in the original font file; rectifying the text information according to the new font file, writing the rectified text information into an electronic document; acquiring font description data of characters in the text information from the new font file when the electronic document is opened, and displaying the text information according to the acquired description data. Correspondingly, the invention further provides a text information hiding device, character codes of the text information cannot be changed and any encryption method is omitted, effect of hiding the text information can be realized simply, and safety, hiding performance and robustness are high.
Owner:NEW FOUNDER HLDG DEV LLC +1
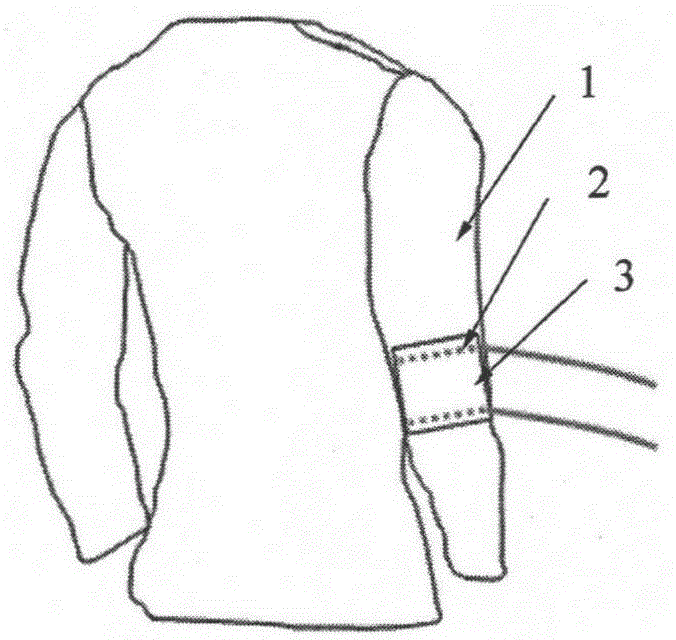
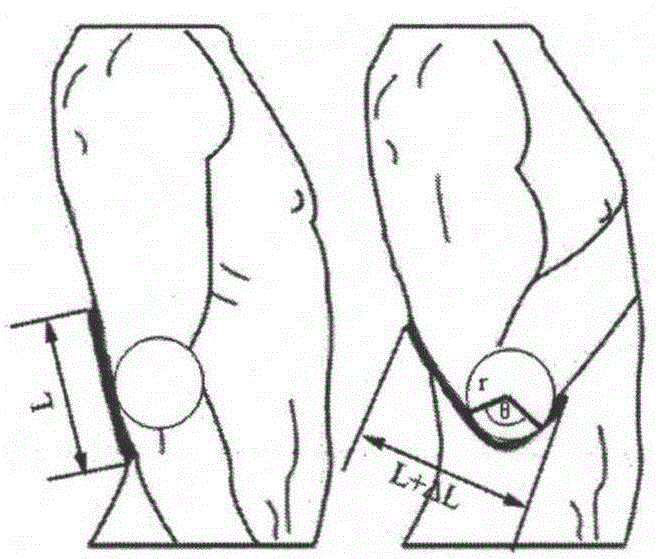
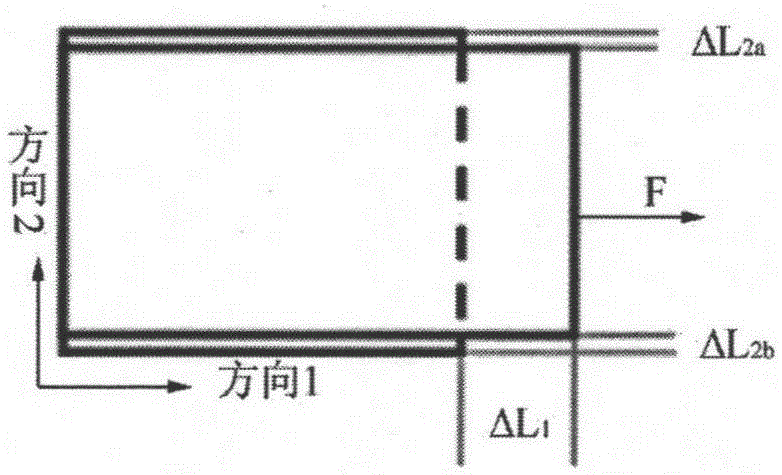
Upper limb functional movement monitoring system and method based on fabric sensor
ActiveCN105266817AImprove stabilityAchieve wearing comfort and concealmentDiagnostic recording/measuringSensorsTransmission lineVoltage
The present invention provides an upper limb functional movement monitoring system and method based on a fabric sensor. The system comprises a signal generating device which comprises a conductive fabric with a signal transmission line which is connected to a button battery, a signal collection and transmission device which collects a voltage signal and sends the signal to a signal receiving and displaying device, the signal receiving and displaying device which receives the voltage signal, carries out functional movement characterization on the signal, displays a functional movement state in real time at the same time, stores data and carries out imaging, wherein the conductive fabric is close to a body upper limb elbow joint, and an upper limb movement stretches the conductive fabric such that the voltage signals at two ends of the conductive fabric are changed. The invention also provides the upper limb functional movement monitoring method based on the fiber sensor. The upper limb functional movement monitoring system and the method have the advantages of low cost, good stability, high sensitivity and strong adaption ability, at the same time a sensitive element can be integrated to the daily clothes, and a basis is provided for biomechanics analysis of human body upper limb movement.
Owner:ANHUI HENGYI TEXTILE TECH CO LTD
Air outlet device, air conditioning system and transportation tool
PendingCN109823143AAdjustable sizeOperableAir-treating devicesVehicle heating/cooling devicesEngineeringAir conditioning
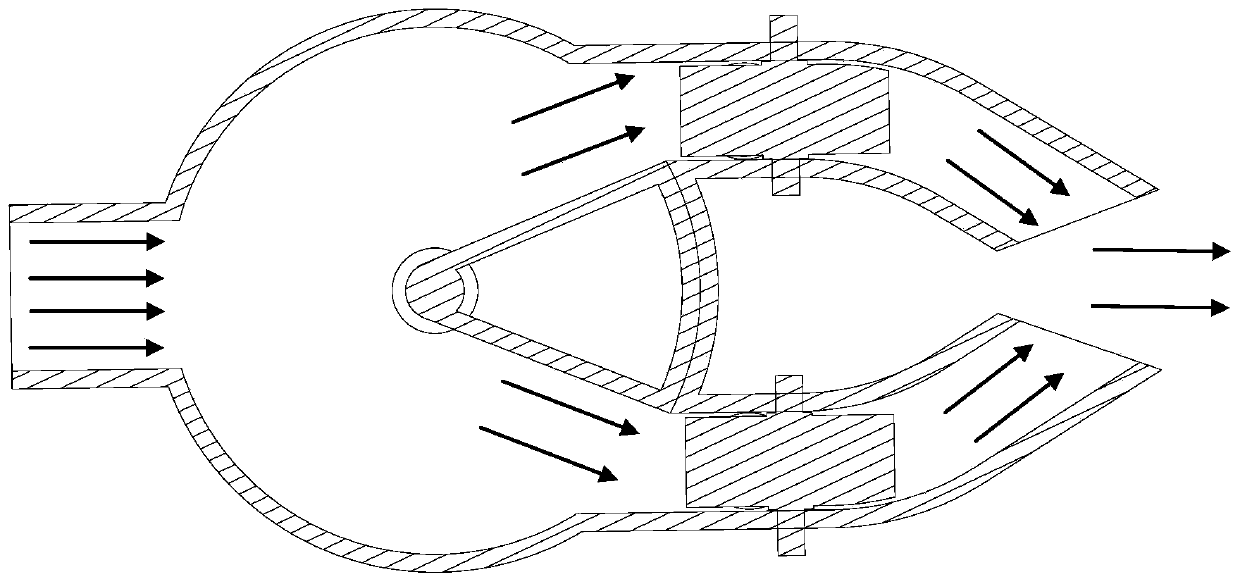
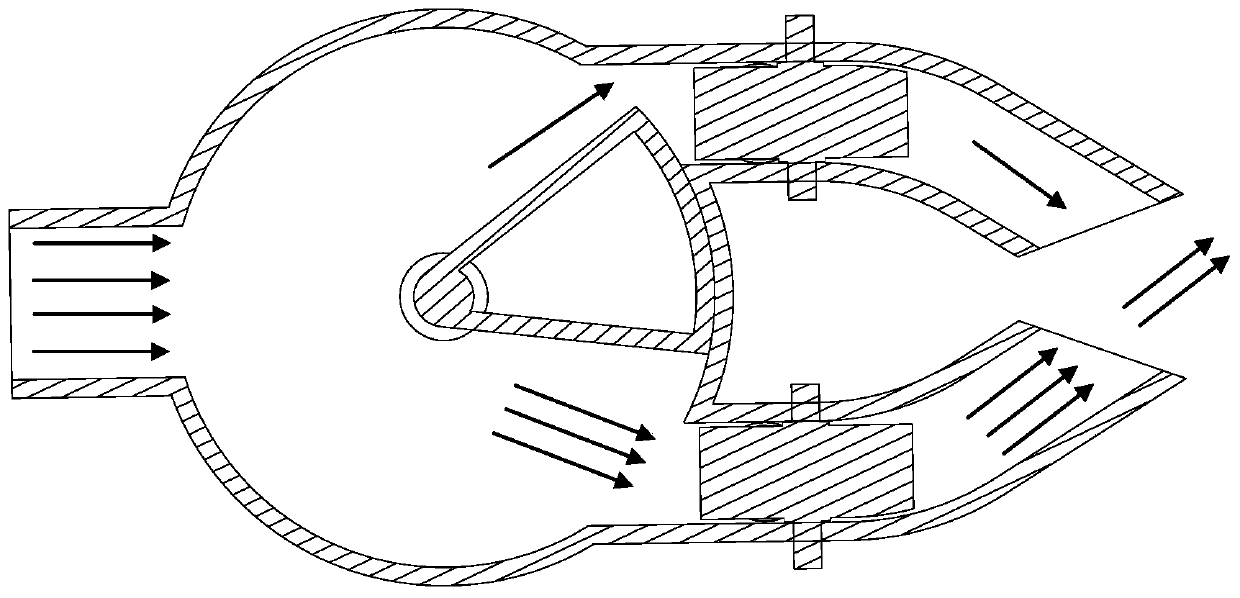
The invention provides an air outlet device, an air conditioning system and a transportation tool. The air outlet device comprises a first channel, a second channel, an air guide structure and direction adjusting devices. The first channel is provided with a first air inlet and a first air outlet; the second channel is provided with a second air inlet and a second air outlet; the air guide structure is used for adjusting the relative sizes of the first and second air inlets; the direction adjusting structures are arranged on the first channel and the second channel respectively so as to adjustthe first direction of outlet air of the first air outlet and the first direction of outlet air of the second air outlet.
Owner:NINGBO JOYSONQUIN AUTOMOTIVE SYST HLDG CO LTD
Loading system and loading method for DLL (Dynamic Link Library) file
InactiveCN106339247AAchieve concealmentPrevent detectionProgram loading/initiatingOperating systemComputer science
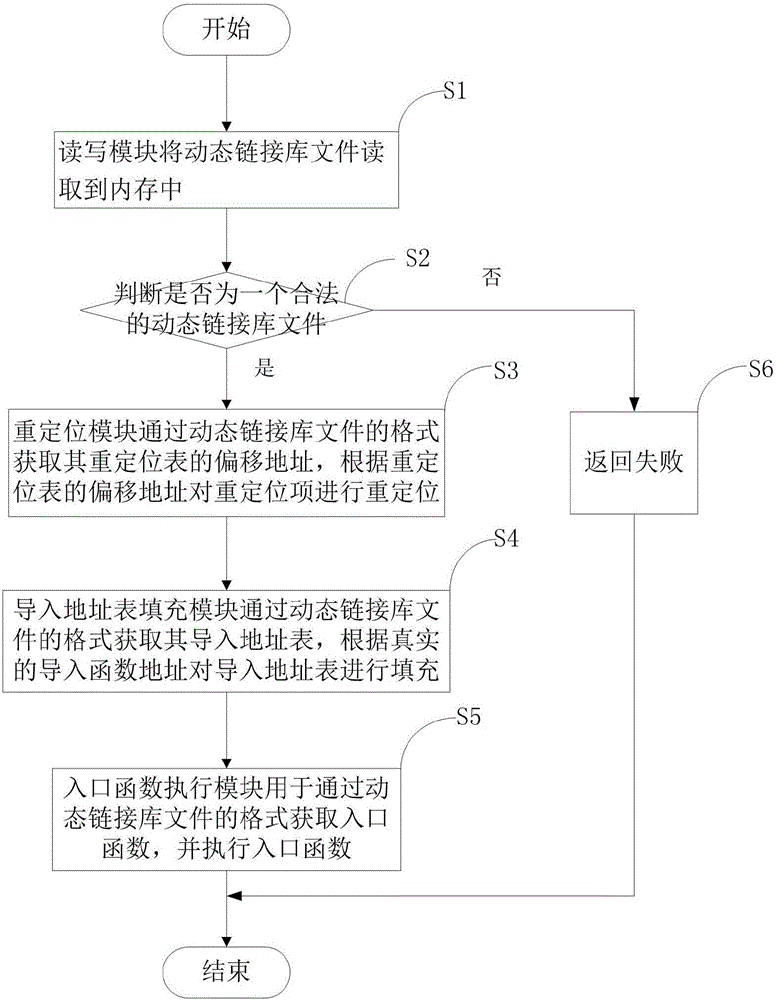
The invention discloses a loading system for a DLL (Dynamic Link Library) file and relates to the technical field of communication. The loading system comprises a read-write module, a resolving module, a re-positioning module, an address table-loading filling module and an inlet function execution module, wherein the read-write module is used for reading the DLL file into a memory; the resolving module is used for resolving a file header of the DLL file and judging whether the DLL file is a legal DLL file or not; the re-positioning module is used for acquiring the address of the re-positioning table through a format of the DLL file, and re-positioning the re-positioning items according to the address of the re-positioning table; the address table-loading filling module is used for acquiring the loaded address table through the format of the DDL file, and filling a real address of a to-be-loaded function; and the inlet function execution module is used for acquiring an inlet function through the formation of the DLL file, and executing the inlet function. The invention discloses a method for loading the DLL file based on the loading system for the DLL file.
Owner:WUHAN DOUYU NETWORK TECH CO LTD
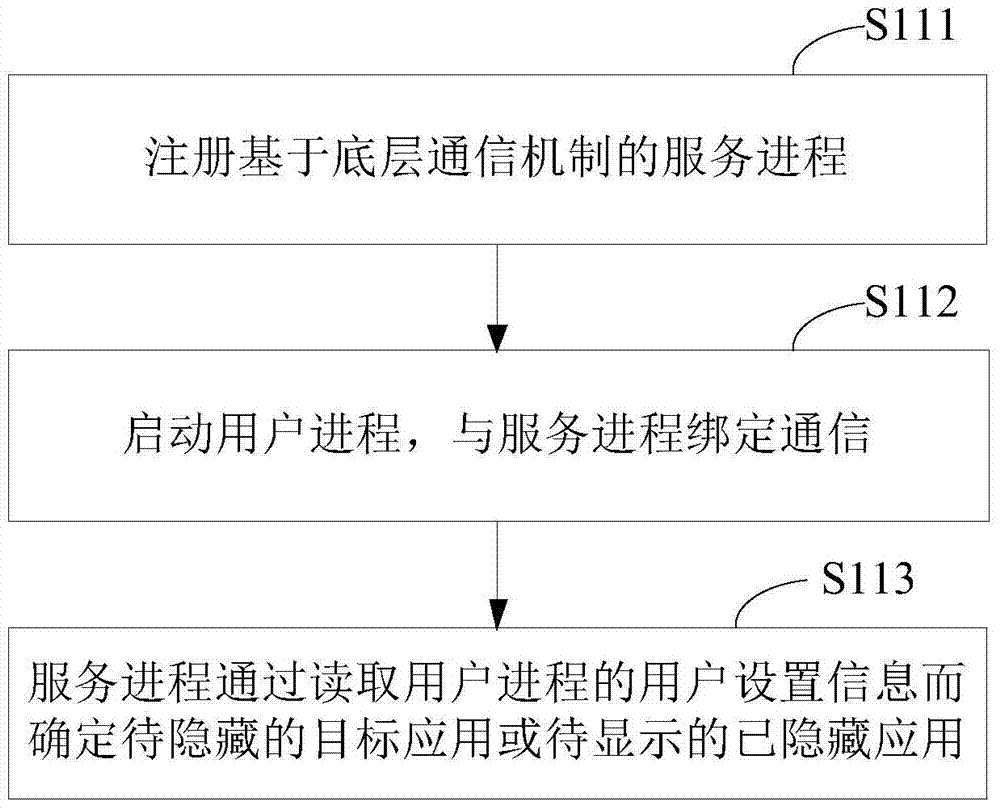
Application hiding control method and device
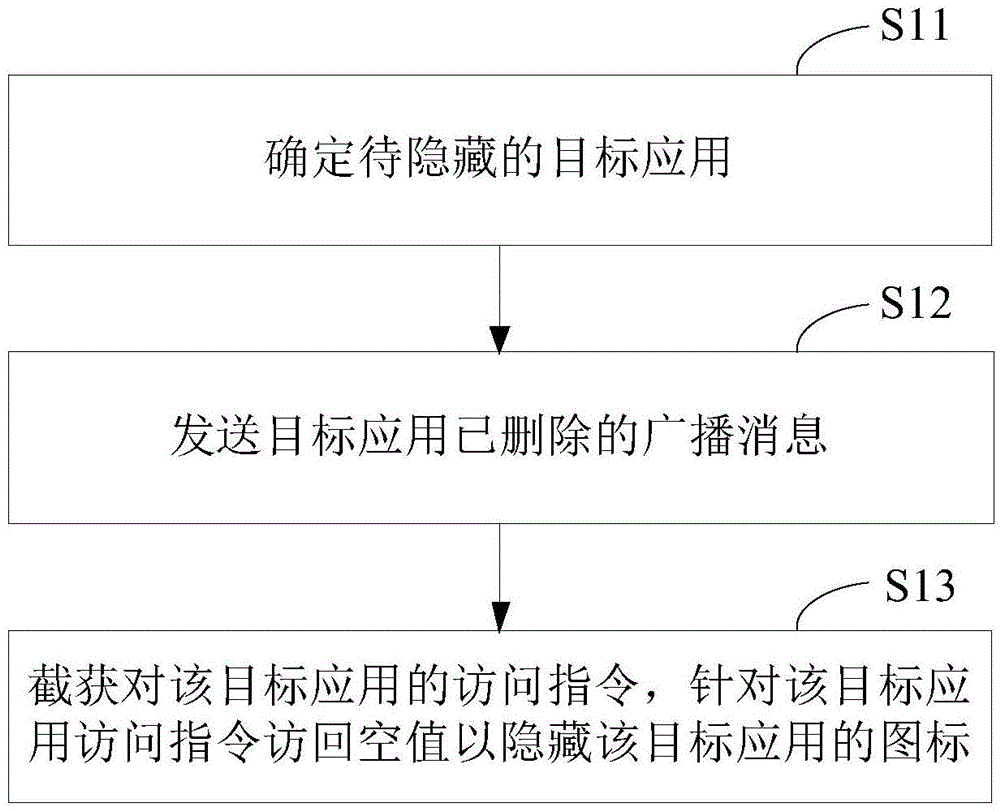
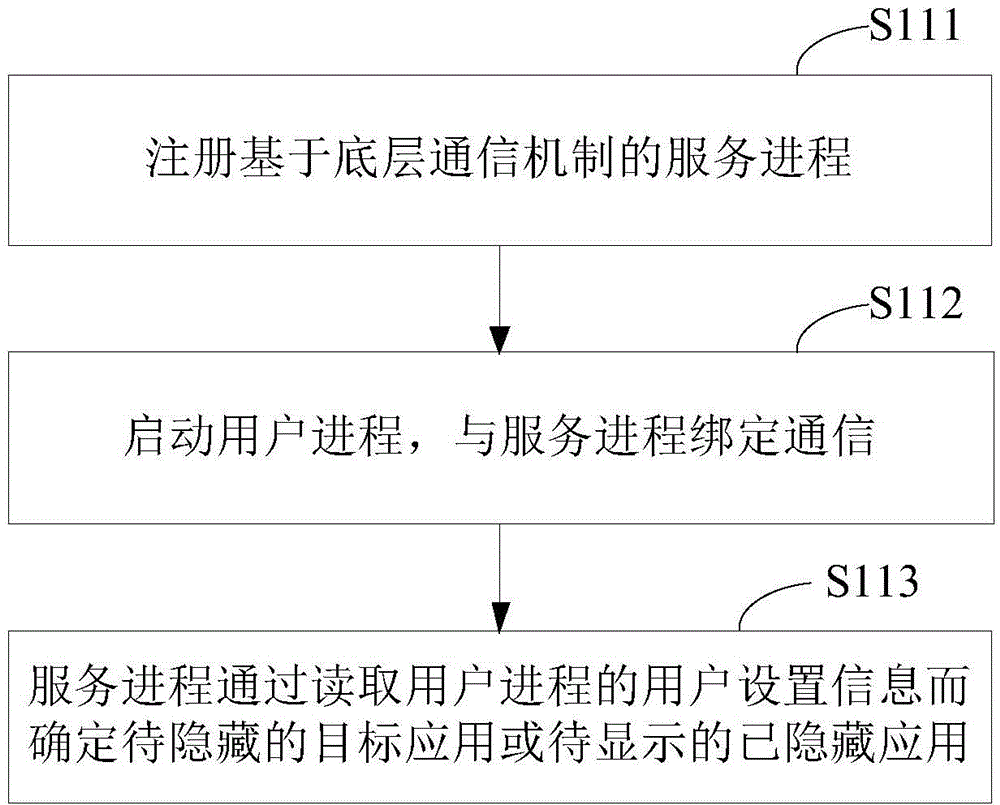
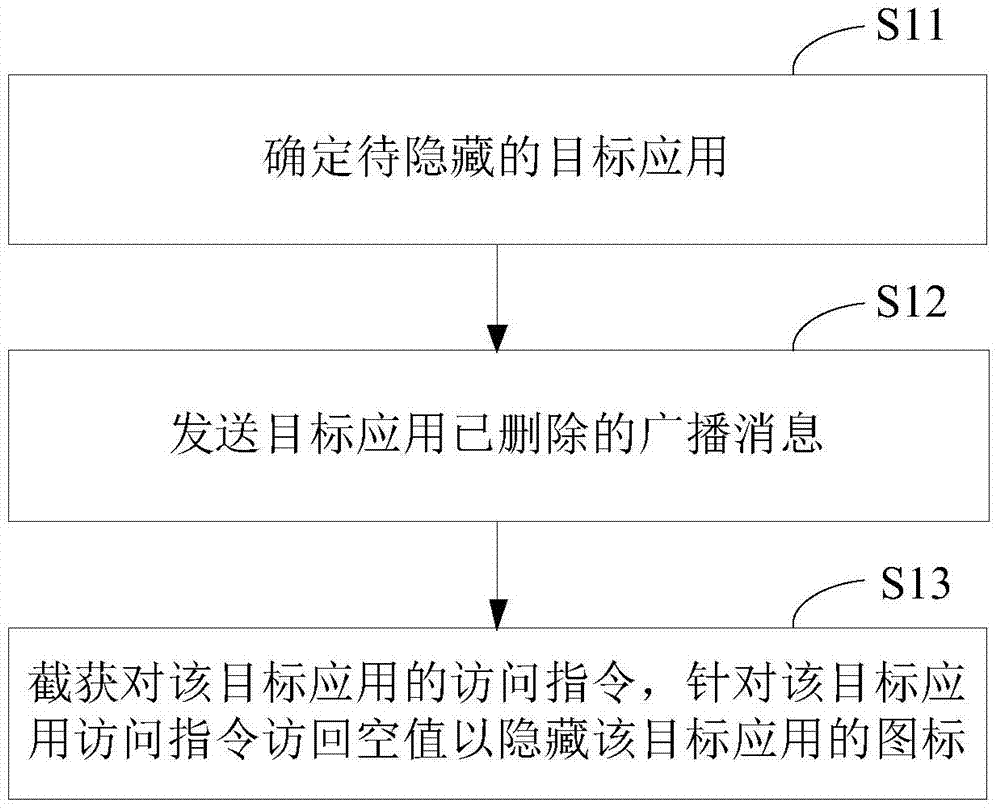
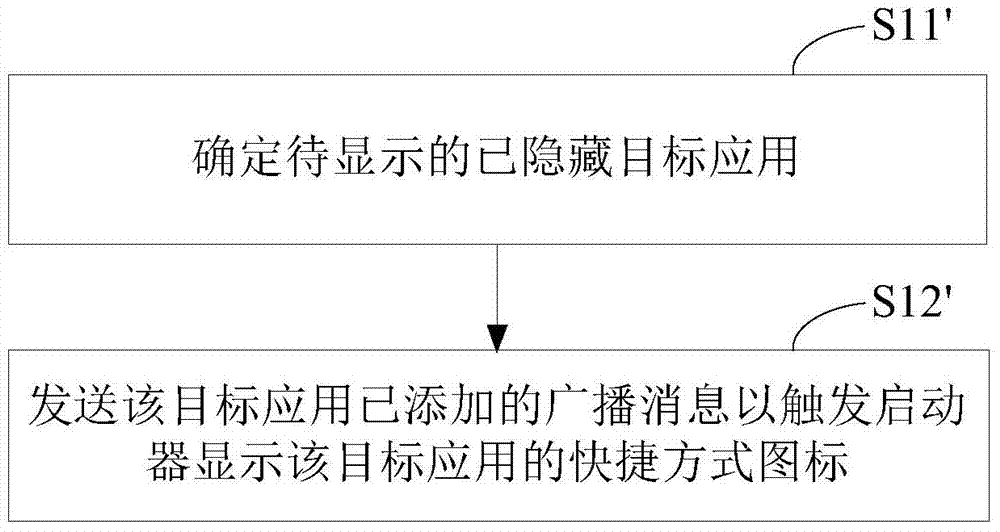
ActiveCN104376268ASafe hidden effectHidden effect thoroughlyDigital data protectionOperational systemSoftware engineering
The invention relates to the security control technology of intelligent equipment and discloses an application hiding control method. The method comprises the first step of determining a target application to be hidden, the second step of transmitting a broadcast message representing that the target application is deleted, and the third step of intercepting an access instruction of a starter process to the target application and correspondingly returning a null value to the process of the starter for the target application so as to hide a shortcut icon of the target application in the starter. Furthermore, the method can include the following supplementary steps of determining a hidden target application to be displayed and transmitting a broadcast message representing that the hidden target application is added so as to display a shortcut icon of the target application in the starter. By means of the method, the application program can be hidden in the starter, and follow-up normal running of the application program is not influenced. The application hiding control method can be applied to an Android operating system and can also be applied to an operating system environment provided with a similar framework or mechanism.
Owner:BEIJING QIHOO TECH CO LTD
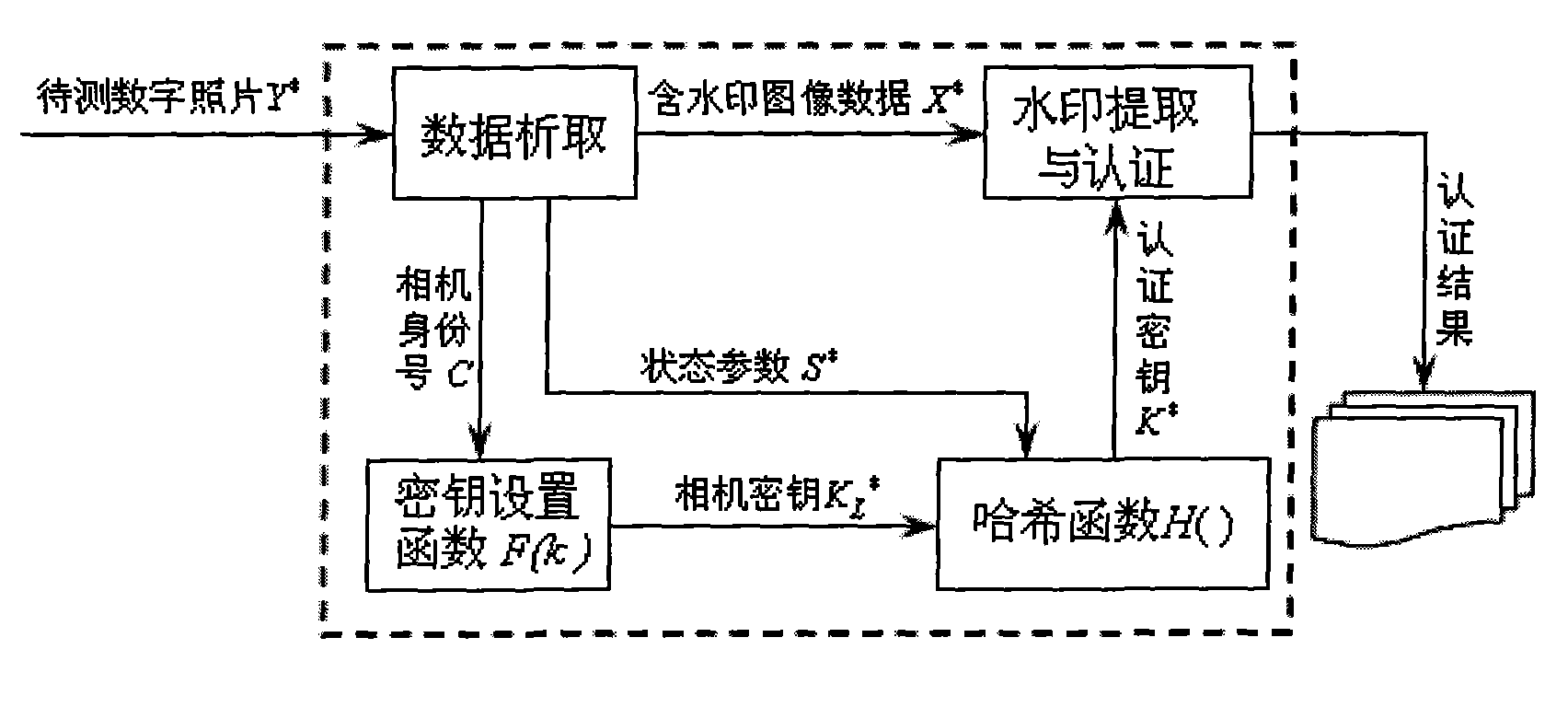
Method for generating digital photo containing watermark based on state parameter
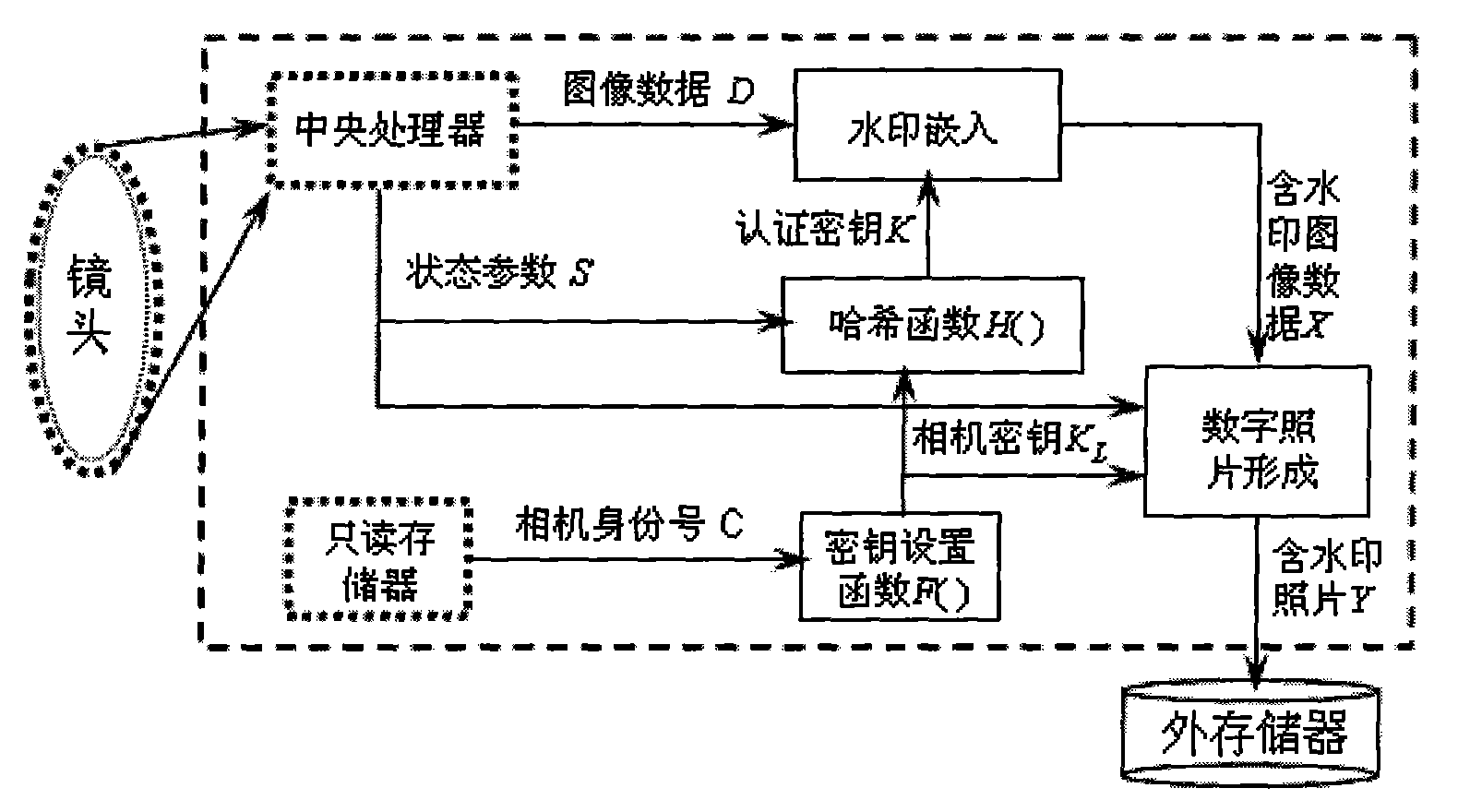
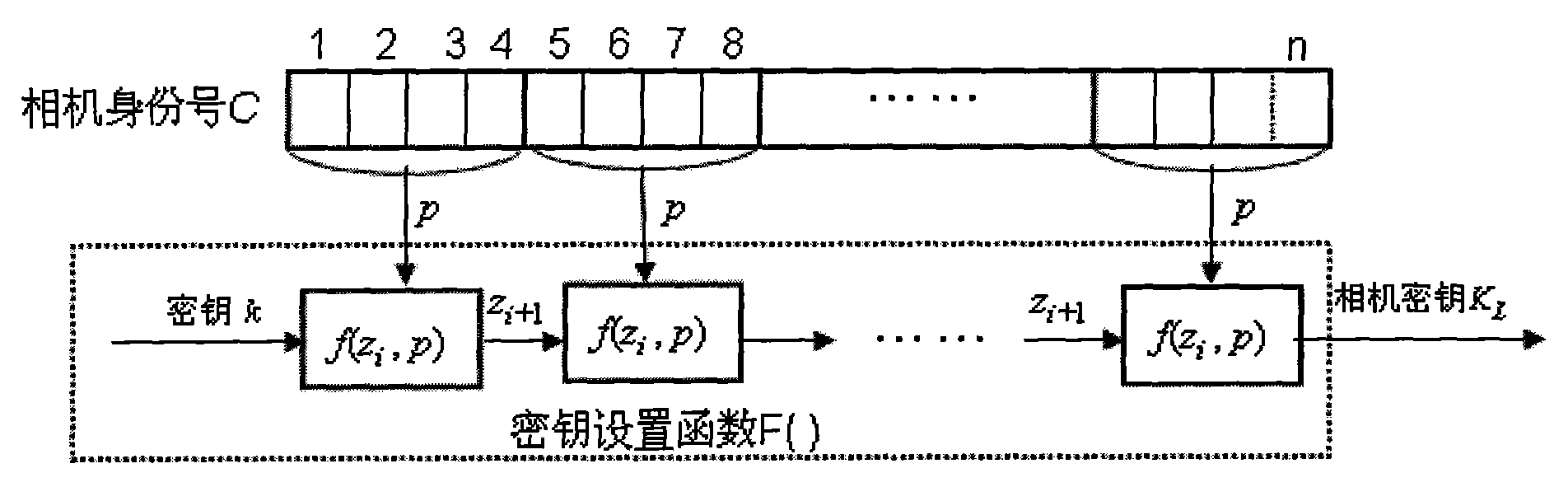
InactiveCN101562681AEliminate Collage AttacksReduce design requirementsPictoral communicationCopy attackDigital camera
The invention provides a method for generating a digital photo containing a watermark based on a state parameter. The method comprises that: when a digital camera takes a photo, an image signal is processed through a central processor to obtain digital image data; the central processor reads the focal length, aperture, exposure time, shooting time and photosensibility when taking the photo as state parameters; a camera key is generated by a camera identification number and a key set function; the state parameters and the camera key are used as a plaintext, and an authentication key of the digital photo is generated by hash function; the authentication key is used to generate watermark-containing digital image data of the image data; and the watermark-containing digital image data is synthesized with a header file EXIF of the photo into a photo output file to be stored in an external memory of the camera. The authentication key of the digital photo containing watermark generated by the method has good privacy, not only can effectively prevent 'collage attack', but also can effectively resist 'copying attack'. Meanwhile, participation of the digital camera or key transfer is not required in authentication, so that disclosure and high efficiency of the digital photo authentication are realized.
Owner:SOUTHWEST JIAOTONG UNIV
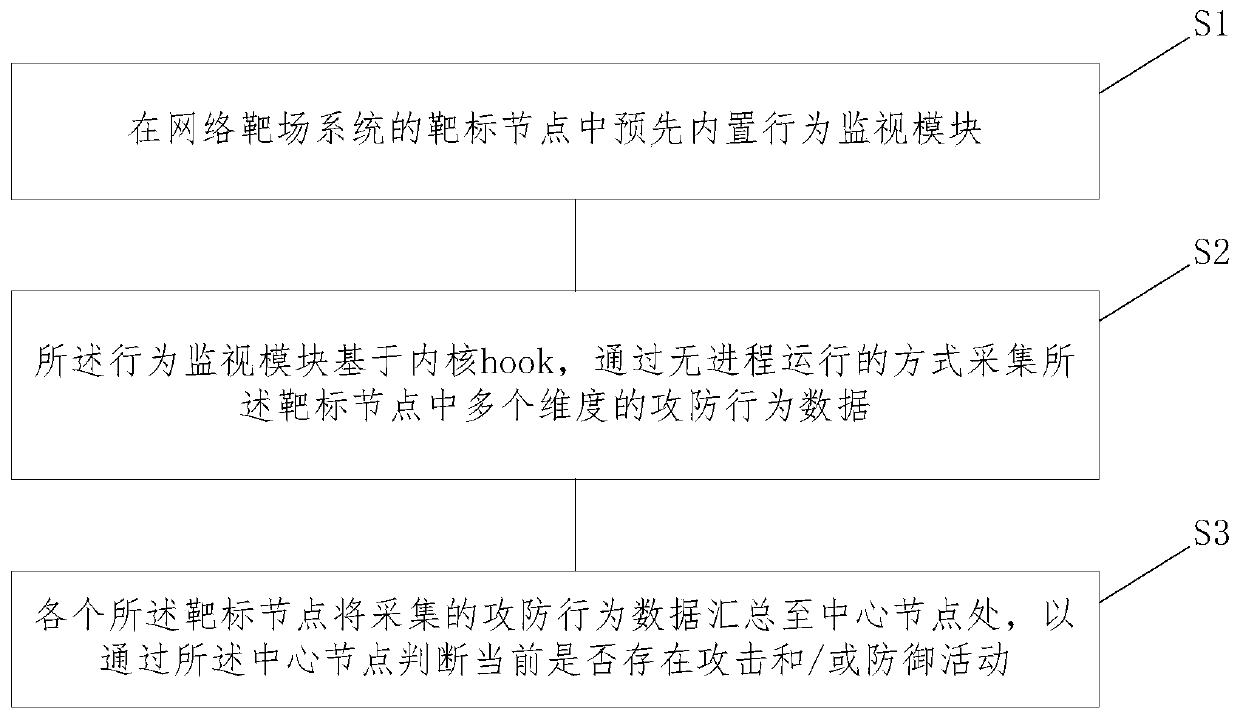
Data acquisition method and data acquisition system in network target range system
ActiveCN110351255AEnsure comprehensivenessDiversity guaranteedTransmissionMultiple dimensionTarget range
The embodiment of the invention relates to a data acquisition method and a data acquisition system in a network target range system, and the method comprises the steps: presetting a behavior monitoring module in a target node of the network target range system; enabling the behavior monitoring module to collect attack and defense behavior data of multiple dimensions in the target node in a process-free operation mode based on a kernel hook; and enabling each target node to summarize the collected attack and defense behavior data to a central node so as to judge whether an attack and / or defenseactivity exists currently through the central node. According to the technical scheme provided by the invention, more data can be collected, meanwhile, the concealment of the system is improved, andthe influence on the target node is reduced.
Owner:北京永信至诚科技股份有限公司
Flexible screen assembly and intelligent terminal
InactiveCN112839118AAchieve expansionAchieve concealmentTelephone set constructionsComputer hardwareEmbedded system
The invention discloses a flexible screen assembly and an intelligent terminal, and belongs to the technical field of electronic products. The flexible screen assembly comprises a flexible screen and two winding devices, the flexible screen comprises a non-display area and a display area, and the non-display area is provided with a camera hole; the two winding devices are connected to the two ends of the flexible screen correspondingly and used for driving the flexible screen to be wound in the two opposite directions correspondingly so that the flexible screen can be switched between a first state in which the non-display area can be unfolded and a second state in which the non-display area can be hidden. According to the flexible screen assembly, the flexible screen is driven to be rolled or unfolded through the winding device, the real full-screen display effect can be achieved, and when the flexible screen assembly is applied to the intelligent terminal, switching of the use state of the front-facing camera can be achieved. The invention further discloses an intelligent terminal comprising the flexible screen assembly.
Owner:ONEPLUS TECH SHENZHEN
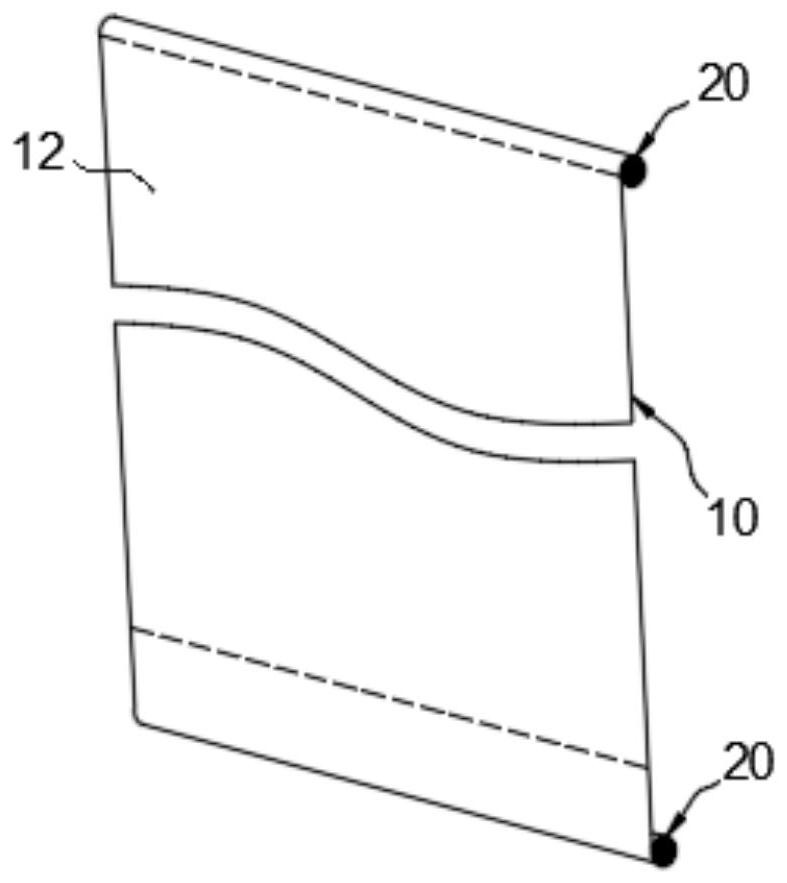
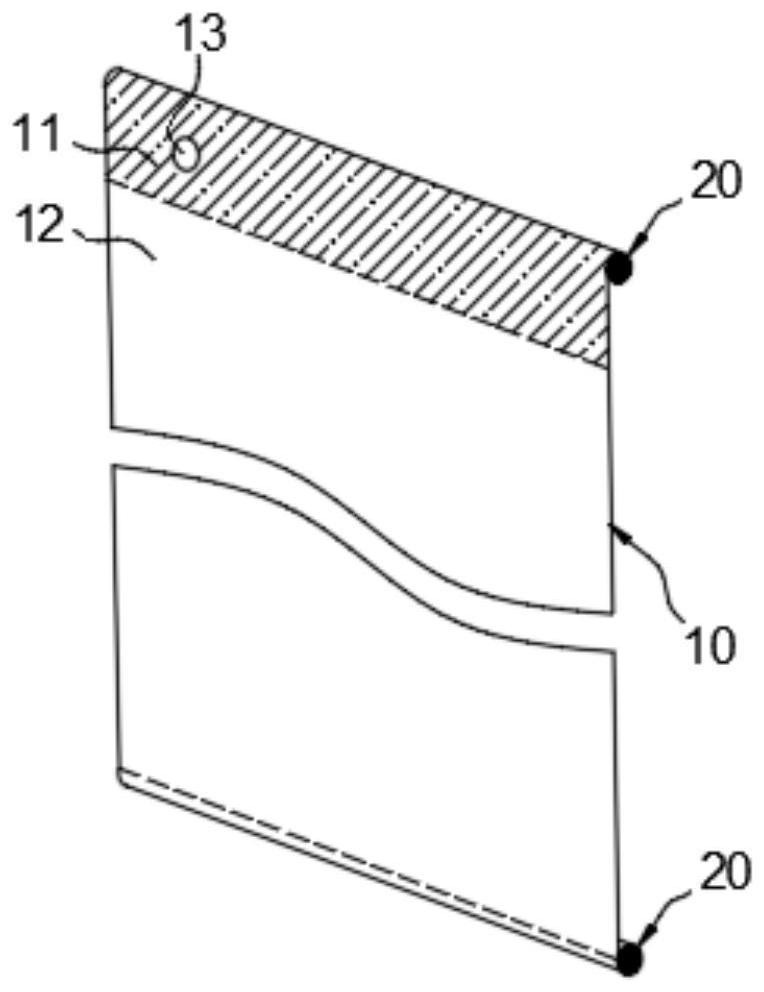
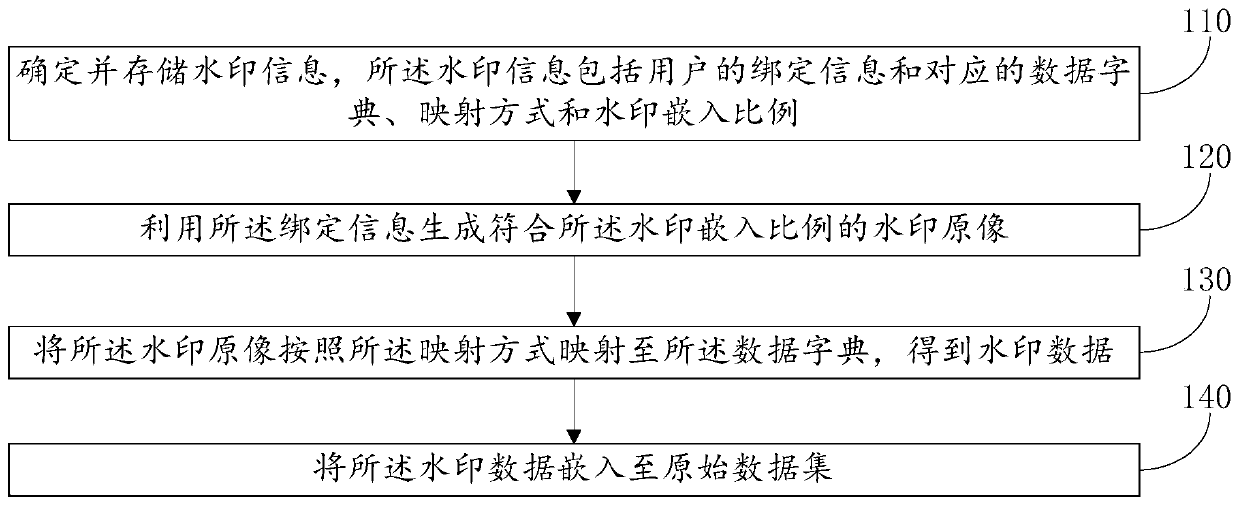
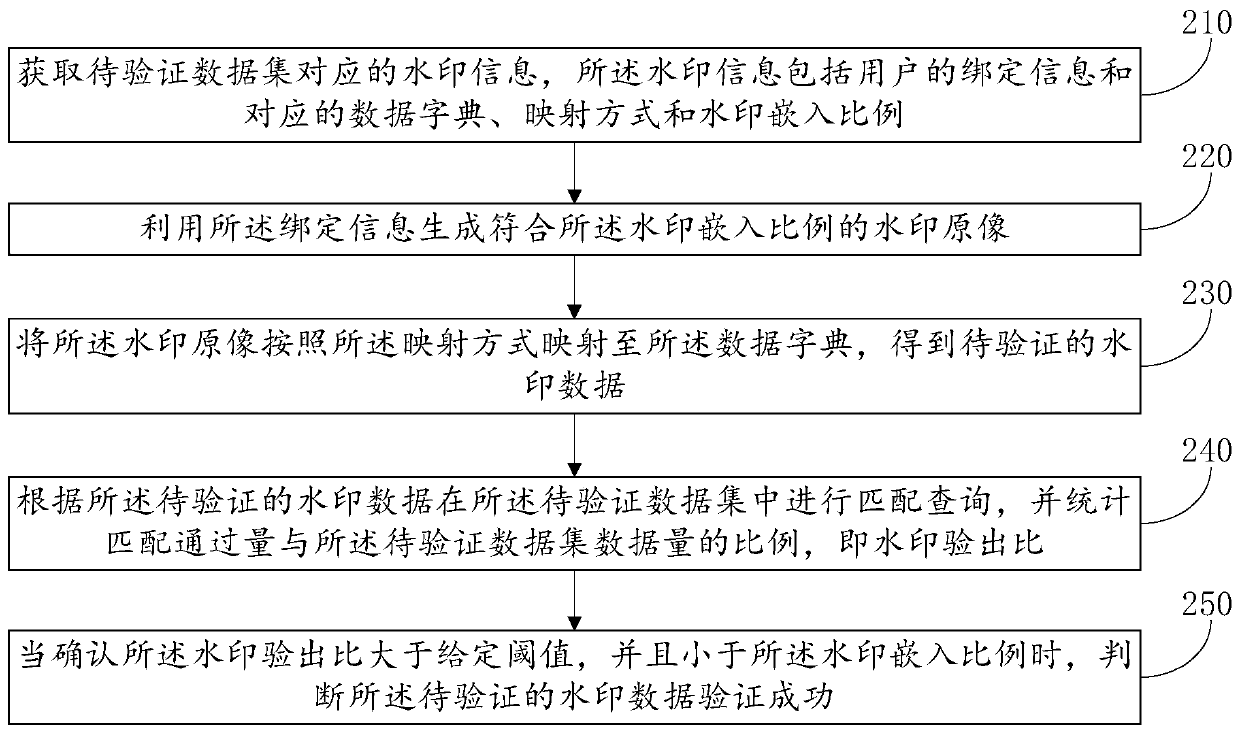
Dynamic watermark embedding and verifying method and system and dynamic watermark processing system
ActiveCN109740316AAchieve concealmentAvoid damageProgram/content distribution protectionComputer hardwareData validation
The invention relates to a dynamic watermark embedding and verifying method and system and a dynamic watermark processing system. The dynamic watermark embedding method comprises the following steps:determining and storing watermark information; generating a watermark original image conforming to the watermark embedding proportion by utilizing the binding information; mapping the watermark original image to a data dictionary according to a mapping mode to obtain watermark data; and embedding the watermark data into the original data set. When dynamic watermark verification is carried out, obtaining watermark information corresponding to the to-be-verified data set, and obtaining to-be-verified watermark data according to a method which is the same as an embedding method; performing matching query in the to-be-verified data set according to the to-be-verified watermark data, and counting the proportion of the matching passing amount to the to-be-verified data set data amount; and judging that the watermark data to be verified is verified successfully. According to the invention, identity binding and watermark hiding, low damage and attack resistance are realized, and the managementcost is reduced; And watermark data does not need to be stored, so that the storage cost is greatly reduced.
Owner:BEIJING SANSEC TECH DEV
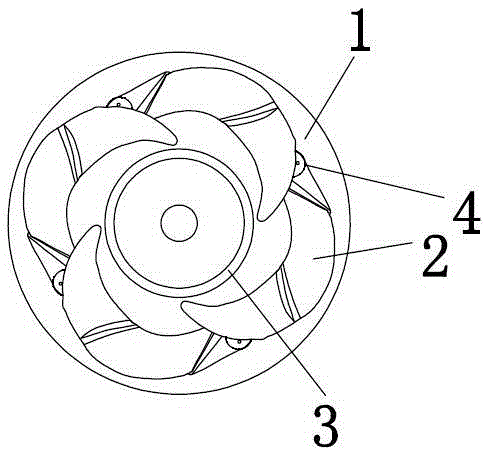
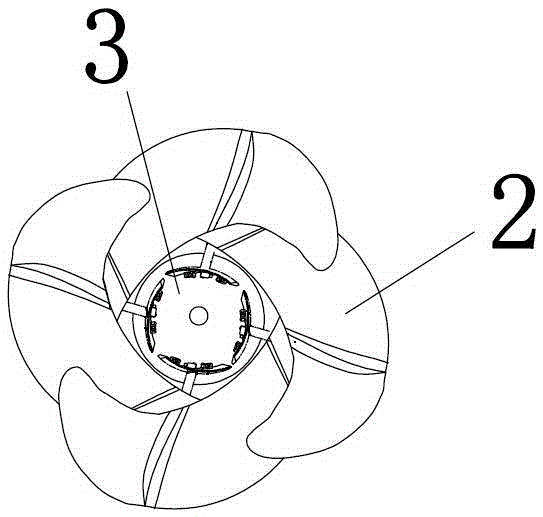
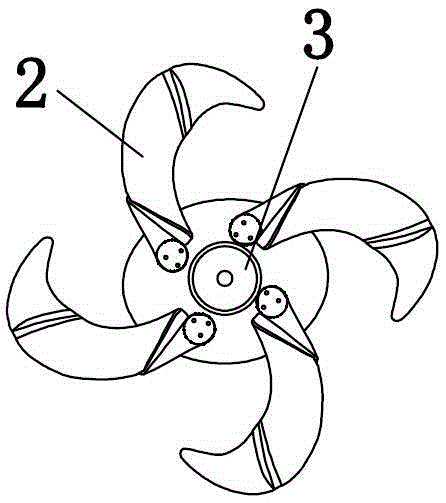
Hidden type ceiling fan lamp
InactiveCN105240294AAchieve concealmentReasonable designPump componentsLighting elementsCeiling fanAgricultural engineering
The invention discloses a hidden type ceiling fan lamp which comprises a disc, blades, a drive motor and blade fixing devices. A rotary shaft is arranged in the center of a bottom disc. A long-service-life mute bearing is arranged at the lower end of the rotary shaft in a sleeved manner. Two U-shaped grooves are formed in the bottom of a rotary disc. Blade fixing columns and a leaf spring installation position are arranged at the upper portion of the rotary disc. A built-in high-strength leaf spring is arranged between a disc face and the rotary disc. The center end of the built-in high-strength leaf spring is fixed to the rotary shaft. The tail end of the built-in high-strength leaf spring is fixed to the blade fixing columns. The upper end of the rotary shaft is sleeved with the rotary disc. Fixing column installation holes are formed in the circumference of the disc face. The blades are installed on the blade fixing columns. The blade fixing columns and the fixing column installation holes are fixedly connected through blade fixing screws. The rotary disc and the disc face are fixedly connected through disc face fixing screws. The hidden type ceiling fan lamp is reasonable in design, simple in structure and good in blade hiding effect and has market popularization value.
Owner:ZHONGSHAN ZHONGHE MOTOR IND CO LTD
Camera assembly for high-sensitivity mobile terminal
InactiveCN110493394AAchieve concealmentAvoid occupyingTelevision system detailsColor television detailsComputer terminalEngineering
The invention discloses a camera assembly for a high-sensitivity mobile terminal. The camera assembly comprises a mobile terminal body and a display screen. A storage groove is embedded in the front end of the mobile terminal main body; a motor is arranged in the storage groove, the output end of the motor is connected with a threaded rod; a pushing block is arranged at the front end of the threaded rod; a threaded groove is formed in the pushing block; the threaded rod is in threaded connection with the threaded groove; the front end of the pushing block is fixedly connected with a camera; sliding grooves are formed in the positions, located above and below the storage groove, of the front end of the mobile terminal body, electromagnets are arranged in the sliding cavities, Hall sensors are further arranged in the storage groove, the Hall sensors are electrically connected with the motor and the electromagnets respectively, and the Hall sensors, the motor and the electromagnets are further electrically connected with a controller respectively. By arranging the Hall sensor, the sensitivity is high, and the front camera can be prevented from occupying the display area of the displayscreen.
Owner:广东中晶电子有限公司
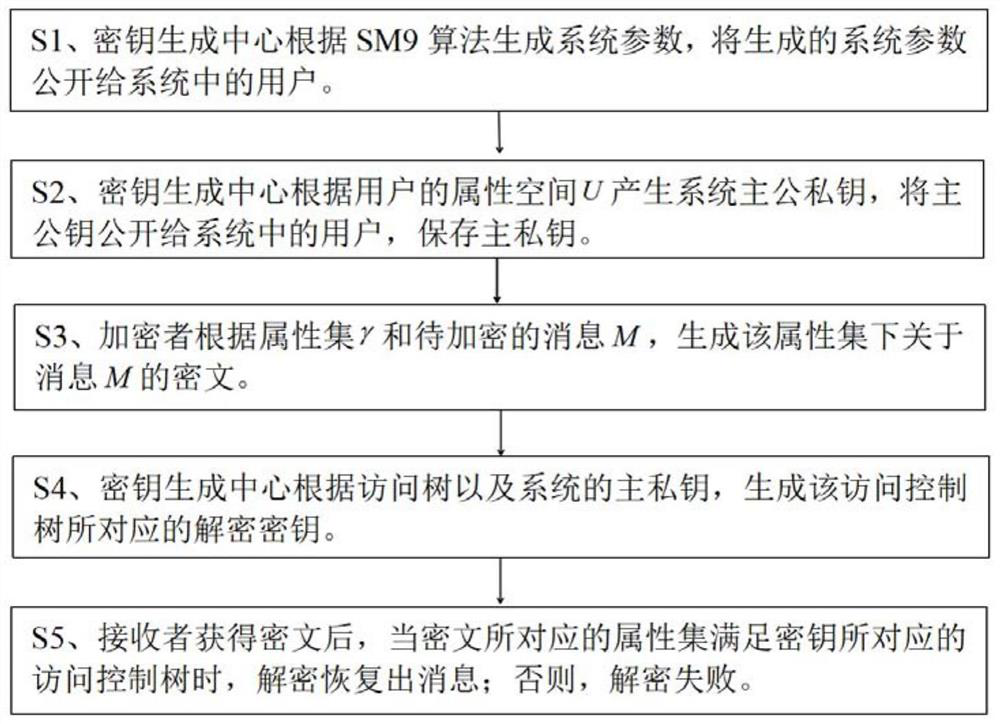
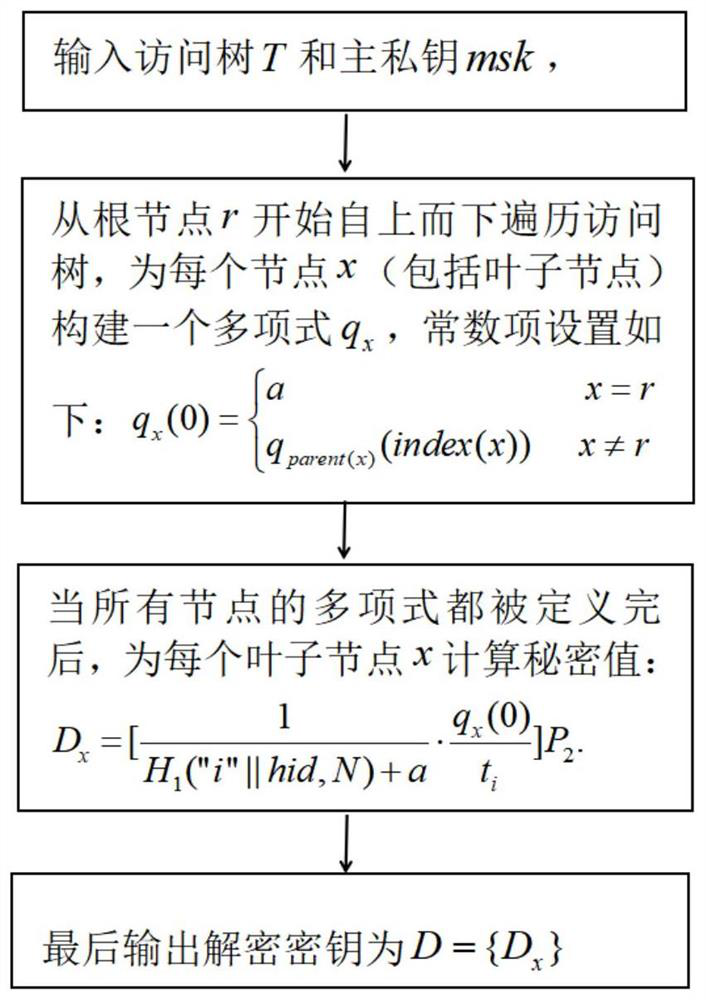
SM9-based key policy attribute-based encryption method
ActiveCN114039730AGuaranteed confidentialityImprove securityKey distribution for secure communicationEncryption apparatus with shift registers/memoriesCiphertextEngineering
The invention discloses an SM9-based key policy attribute-based encryption method. The method comprises the following steps that: S1, a key generation center generates system parameters according to an SM9 algorithm, and discloses the generated system parameters to users in a system; S2, the key generation center generates a main public key and a private key of the system according to the attribute space of the users, the main public key is published to the users in the system, and the main private key is stored; S3, an encryptor generates a ciphertext about a to-be-encrypted message under an attribute set according to the attribute set and the to-be-encrypted message; S4, the key generation center generates a decryption key corresponding to an access control tree according to the access tree and the main private key of the system; and S5, after a receiver obtains the ciphertext, when the attribute set corresponding to the ciphertext meets the access control tree corresponding to the key, the message is decrypted to be recovered, otherwise, the decryption fails. According to the method, the attribute is used as the public key, the ciphertext is associated with the attribute, and the secret key is associated with the access control tree, so that the purpose of flexibly representing an access control strategy is achieved, and the processing overhead of the network bandwidth and the sending node caused by data sharing and fine-grained access control is greatly reduced.
Owner:FUJIAN NORMAL UNIV
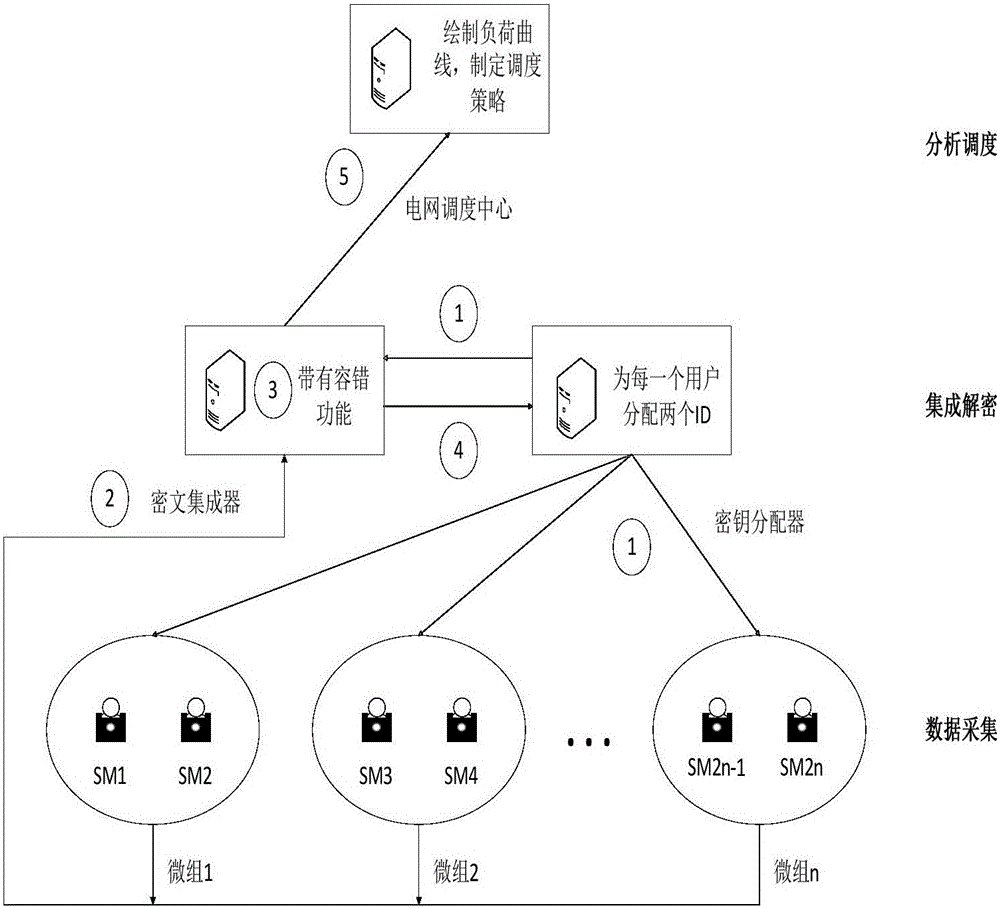
Power consumption data collection method and system capable of protecting power consumption privacy of users and provided with fault-tolerant mechanism
InactiveCN105959153AImprove fault toleranceImprove robustnessPower network operation systems integrationCircuit arrangementsComputer hardwareSmart meter
The invention belongs to the technical field of smart power grids, and particularly relates to a power consumption data collection method and system capable of protecting the power consumption privacy of users and provided with a fault-tolerant mechanism in a smart power grid. The method comprises the following steps: classifying two users with similar daily power consumption behaviors into a micro-group, wherein the two users in the same micro-group share a private key, and the sum of the private keys of all the micro-groups is 0; assigning two IDs, which are respectively used for normal charging and power dispatching, for each user; when data is uploaded, firstly judging whether messages are received from all smart meters or not, and carrying out integrated decryption if the messages are received from all the smart meters; if normal decryption is failed due to damages of one smart meter and loss of the corresponding private key, using the message of the other smart meter in the same micro-group as a replacement; recording an ID of the damaged smart meter and notifying the corresponding user to repair the smart meter; and according to the sum of uploaded power consumptions of all the users, drawing a load curve and formulating a dispatching strategy and a power generation plan.
Owner:NORTH CHINA ELECTRIC POWER UNIV (BAODING)
Bedside table with hidden storage box
InactiveCN108095367AWith hidden storage spaceAchieve concealmentBedside cabinetsDrawersLight sensingBrightness perception
The invention discloses a bedside table with a human body induction function. The intelligent bedside table comprises a table body. An indicating light source is arranged on the top face of the tablebody. The bedside table further comprises a human body induction module arranged on the table body, a light sensing module for detecting ambient brightness in real time, and a light adjusting module for adjusting the brightness of the indicating light source. The human body induction module is used for detecting whether a moving human body signal is close to the table body or not, when the human body induction module detects that the moving human body signal is close to the table body, the indicating light source is switched on, and the light adjusting module adjusts the brightness of the indicating light source to be slowly increased to a corresponding brightness value according to the ambient brightness value detected by the light sensing module. When the human body induction module doesnot detect the moving human body signal around the table body within a preset time, the indicating light source is switched off.
Owner:FOSHAN CITY EDENS TECH CO LTD
Storage rack with cinerary casket hiding and article storage function
Owner:JIANGXI GOODLE FINE STORAGE TECH
Method and system for realizing background light and dot matrix patterns of glass curtain wall of building
InactiveCN102168840AAchieve the effect of "seeing the light but not the light"To achieve the effect of "seeing the light but not seeing the light"Point-like light sourceWallsDot matrixControl system
The invention relates to a method and a system for realizing background light and dot matrix patterns of a glass curtain wall of a building. The system comprises a plurality of light reflecting membranes, a plurality of luminescent devices and a control system consisting of a scene control server, a plurality of scene control substations and the like. The method comprises the following steps of: a, arranging the light reflecting membranes on the inner side of the glass curtain wall of the building; b, arranging a plurality of luminescent devices between the glass curtain wall of the building and the light reflecting membranes on the inner side of the glass curtain wall of the building; and c, packing background light data and pixel dot pattern data by the scene control server, and transmitting the data to each scene control substation, so that light emitted by the luminescent devices from the front side is projected onto the light reflecting membranes vertically, and the light is subjected to diffuse reflection by the light reflecting membranes to the glass curtain wall and is transmitted to the outside to form white or color background light and / or the luminescent devices emit pixel dot light from the lateral side to form dynamic or static or dynamic and static combination dot matrix patterns. The system can achieve the effect of 'light but no lamps' when applied to transparent glass curtain walls with triangular gridding.
Owner:SHENZHEN TRONSIN ILLUMINATING TECHN
Mobile terminal
InactiveCN108462773APlay a protective effectAchieve concealmentTelephone set constructionsEngineeringComputer terminal
The present application provides a mobile terminal which comprises a front end surface, a rear end surface and a side surface. The front end surface, the rear end surface, and the side surface are collectively arranged to form an accommodation space; the accommodation space is provided with a partitioning plate; the partitioning plate partitions the accommodation space into a first accommodation space and a second accommodation space; the second accommodation space is capable of accommodating a rolled flexible display screen; the flexible display screen can be protruded and retracted from an opening provided in the second accommodation space; and in the state of protruding from the second accommodation space, the flexible display screen at least can be laid on the outer surface of the front end surface. The mobile terminal is provided with two accommodation spaces, one accommodation space for accommodating the flexible display screen and the other accommodation space for accommodatingcircuit components. When in the state of needing to be used, the flexible display screen can be protruded from the accommodation space and be laid on the end surface so as to perform display and interoperation; and when in the state of not needing to be used, the flexible display screen can be retracted into the accommodation space to achieve the hidden effect of the display screen.
Owner:GUANGDONG OPPO MOBILE TELECOMM CORP LTD
Illuminating apparatus for panoramic photography
PendingCN108535938AImprove processing efficiencyQuick calibrationCo-operative working arrangementsPhotographyPanoramic photographyComputer engineering
The invention discloses illuminating apparatus for panoramic photography. The illuminating apparatus comprises a casing, wherein a data receiving and dispatching module and a processor are arranged inthe casing; display screens are arranged on the casing, each display screen displays a unique identification code, the identification code calibrates recognition attribute of the display screen to which the identification code belongs, after the identification code is recognized, the data receiving and dispatching module receives image information sent by an external server, the image informationcarries the recognition attribute of the display screen where the identification code is located, an image is displayed on the corresponding display screen by the processor according to the recognition attribute of the display screen, the data receiving and dispatching module continuously receives information sent by the external server, and the processor responds to requirements for zooming, rotating and brilliance control of the image displayed on the related display screen. The corresponding image of the position where each display screen is located is obtained, the image on each display screen changes with the position change of the illuminating apparatus, so that the hiding effect of the illuminating apparatus is realized, camera shooting goof is avoided, and camera shooting efficiency is improved.
Owner:厦门变趣物联科技有限公司
Application hidden control method and device
ActiveCN104376268BSafe hidden effectHidden effect thoroughlyDigital data protectionBroadcastingIntelligent equipment
The invention relates to the security control technology of intelligent equipment and discloses an application hiding control method. The method comprises the first step of determining a target application to be hidden, the second step of transmitting a broadcast message representing that the target application is deleted, and the third step of intercepting an access instruction of a starter process to the target application and correspondingly returning a null value to the process of the starter for the target application so as to hide a shortcut icon of the target application in the starter. Furthermore, the method can include the following supplementary steps of determining a hidden target application to be displayed and transmitting a broadcast message representing that the hidden target application is added so as to display a shortcut icon of the target application in the starter. By means of the method, the application program can be hidden in the starter, and follow-up normal running of the application program is not influenced. The application hiding control method can be applied to an Android operating system and can also be applied to an operating system environment provided with a similar framework or mechanism.
Owner:BEIJING QIHOO TECH CO LTD
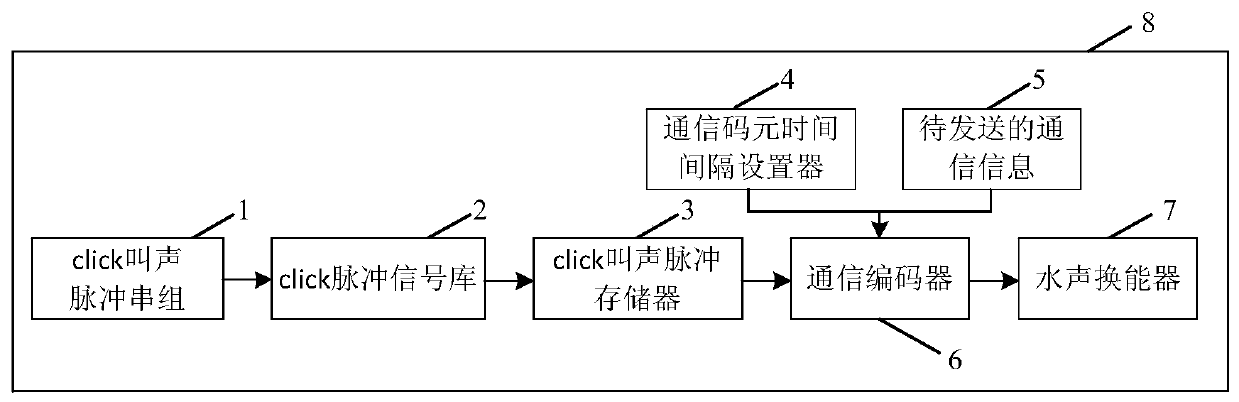
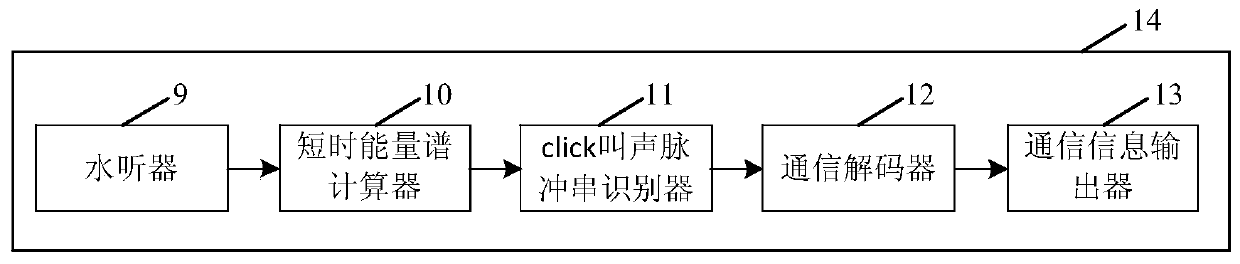
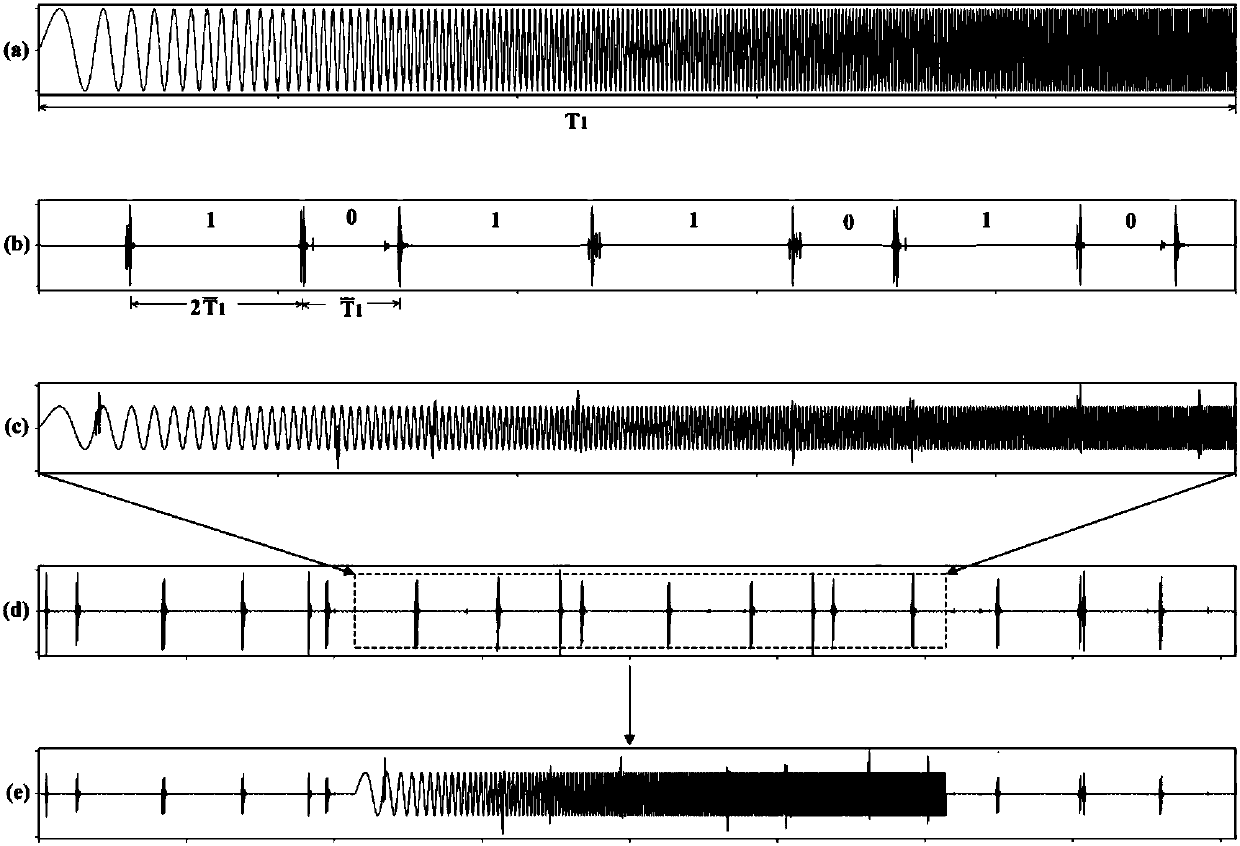
Communication method for encoding and decoding by using whale/dolphin sound pulse number difference
InactiveCN110460393ADiversity guaranteedAvoid oblivionSonic/ultrasonic/infrasonic transmissionTime delaysPulse number
The invention discloses a communication method for encoding and decoding by using whale / dolphin click sound quantity difference, which comprises the following steps of: decoding communication information according to a preset condition satisfied by time delay difference between click sound pulses; a launching platform for coding m groups of click sound pulse strings representing N-bit informationand click sound pulse time delay differences tau d, identifying the time interval set by the communication code element time interval setter, setting the time interval between the adjacent click soundpulse strings, and converting the coded communication information into a sound wave signal through the underwater acoustic transducer to be sent; a receiving platform; carrying out normalized short-time energy spectrum calculation on the received sound wave signal, detecting and positioning the position and the duration of each click sound pulse in the received signal; the click sound pulse string recognizer for recognizing click sound pulse strings according to the principle of time intervals between adjacent click sound pulse strings set in communication codes, identifying and extracting each click sound pulse string, sending the click sound pulse string to a communication decoder, demodulating the number of click sound pulse strings contained in each click sound pulse string and the time delay difference between click sound pulses, and decoding communication information.
Owner:TIANJIN UNIV
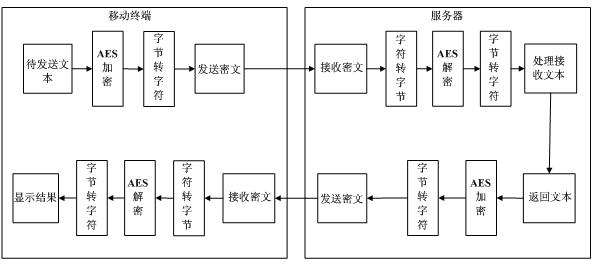
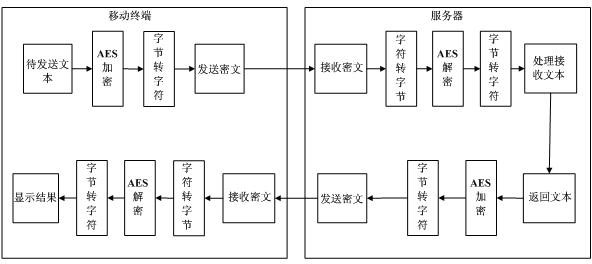
Data transfer encryption method for mobile communication
InactiveCN102256246AImprove securityAchieve concealmentEncryption apparatus with shift registers/memoriesSecurity arrangementComputer hardwareCiphertext
The invention relates to a data transfer encryption method for mobile communication, belonging to the technical field of data communication and aiming at improving the safety of data transfer. The method comprises the following specific steps: a mobile terminal encrypts a text to be sent into a cipher text by using an AES (Advanced Encryption Standard) algorithm and sends the cipher text to a server; the server deciphers the received cipher text by using the AES algorithm and processes the deciphered text; the server generates a text to be returned after processing the received text, encrypts the text to be returned into a cipher text by using the AES algorithm and sends the cipher text to the mobile terminal; and the mobile terminal deciphers the received cipher text into a plain text by using the AES algorithm and outputs the plain text to a display screen to display. Through the method provided by the invention, the safety of data transfer can be improved.
Owner:SHANGHAI INST OF WORK SAFETY SCI
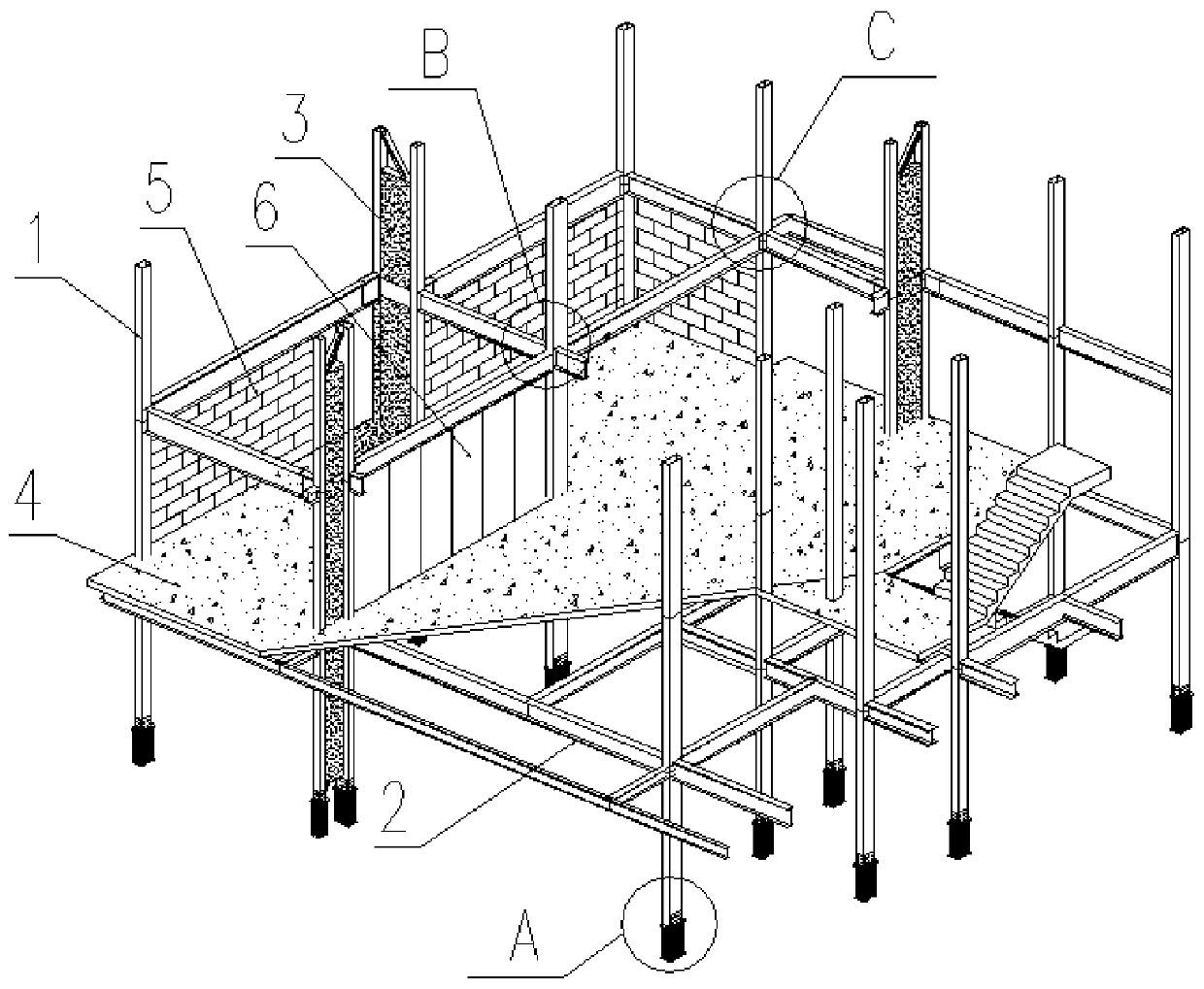
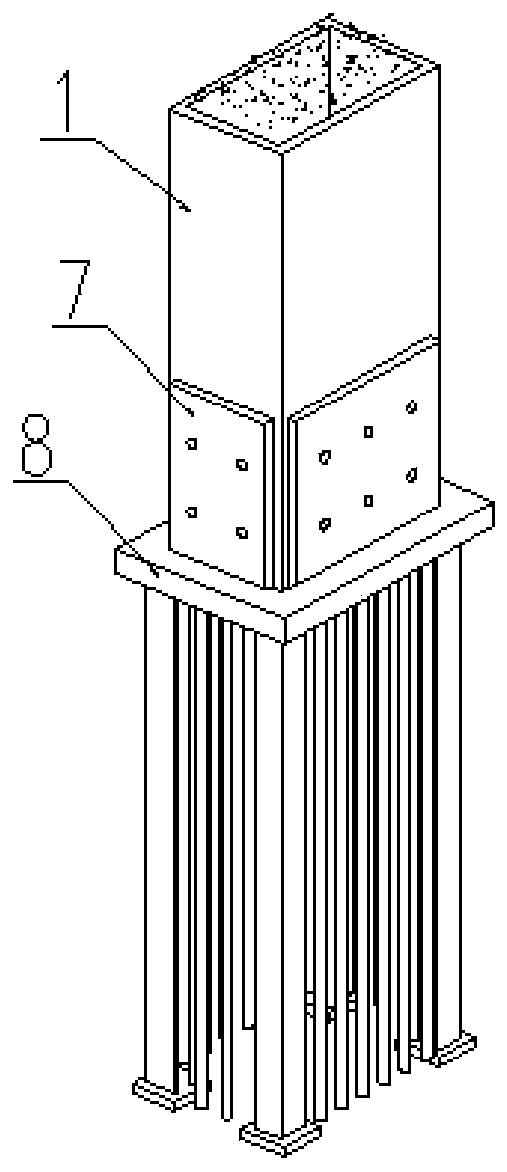
Assembled concrete filled steel tubular column steel frame-beam column wall residence system
PendingCN111255061AImprove lateral force resistanceReduce layoutWallsDwelling buildingFloor slabLine tubing
The invention relates to an assembled concrete filled steel tubular column steel frame-beam column wall residence system. The system is formed by assembling a rectangular cross-section column body, anH-shaped steel beam, a steel beam column wall, a floor slab, a base layer inner wall body and an enclosure outer wall. In order to achieve the purpose that a beam column is not exposed indoors, the column body with the narrow side width smaller than the thickness of the base layer inner wall body is adopted to be connected with the beam column, and the outer side of the long side of the column body is coated with a fireproof coating to achieve the thickness equal to the thickness of the wall body; the steel beam with the flange width smaller than the thickness of the base layer inner wall body is selected to be connected with the wall body, a steel mesh is laid on the outer side of a steel beam web to prevent cracking, a cavity between the steel mesh and the steel beam web is filled witha filler, a leveling layer is arranged along the outer side of the steel mesh to the surface of the base layer inner wall body, and the steel beam is integrally flush with the surface of the base layer inner wall body; the steel beam column wall integrates the functions of the column, the support and the enclosure wall into a whole, a larger anti-side force can be formed, and the requirements suchas equipment opening, and equipment pipe penetrating can be met; and the assembled concrete filled steel tubular column steel frame-beam column wall residence system has the advantages that the beamcolumn is not exposed indoors, the spatial layout is reasonable, pipeline arrangement of pipelines are convenient, and the like.
Owner:浙江力维数智建筑科技有限公司
Concealed blood collection device used in blood cell analyzer
ActiveCN106405134AImprove test accuracyAchieve concealmentMaterial analysisBlood collectionMedical equipment
The invention relates to the technical field of medical equipment, in particular to a concealed blood collection device used in a blood cell analyzer. The concealed blood collection device includes a blood cell analyzer body, a control panel is fixedly installed on the blood cell analyzer body, the bottom of the blood cell analyzer body is fixedly connected to a pedestal through support columns, the bottom ends of blood temporary storage tubes are communicated with a blood transfer cavity, and the concealed blood collection device is installed at the bottom of the blood transfer cavity. According to the concealed blood collection device used in the blood cell analyzer, by setting the concealed blood collection device, the blood cell analyzer not only has blood cell analysis function, but also can pump collected fresh blood into a blood cell extraction analysis device for detection, thus achieving efficient and rapid work. Therefore, the test precision of the blood cell analyzer can be enhanced.
Owner:山丹县天马科技有限责任公司
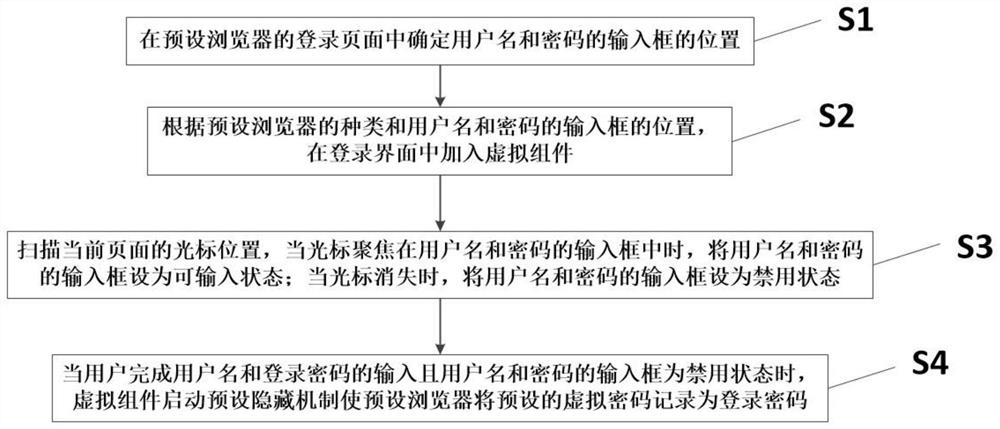
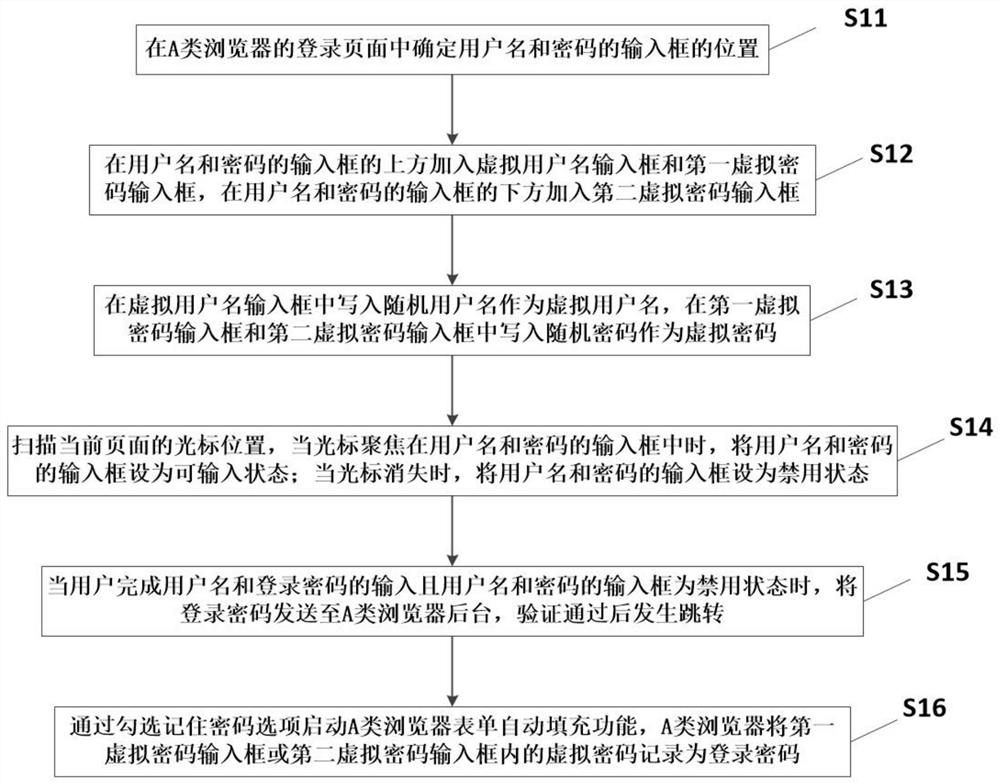
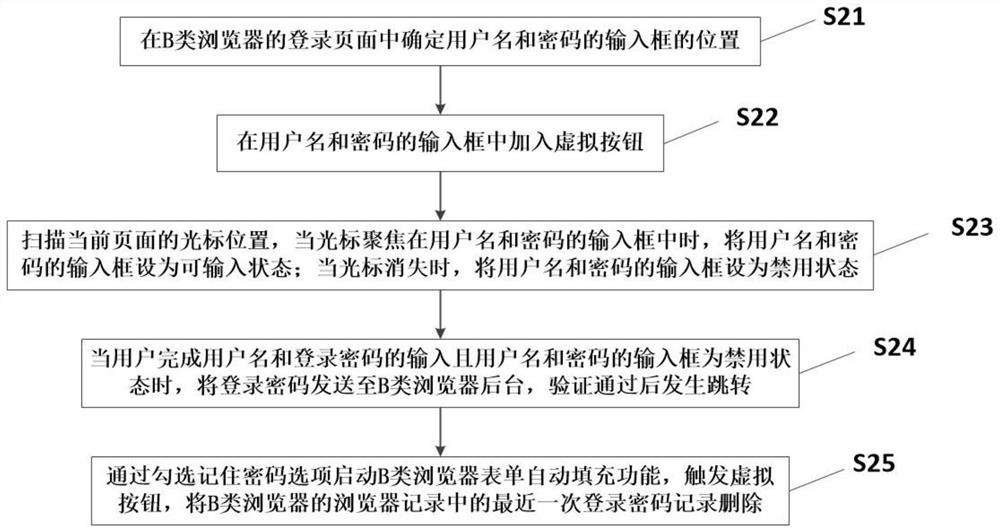
Hiding method and system for Web security login password
According to the hiding method and system for the Web security login password, on the basis that browser design is not damaged, password hiding is achieved, virtual passwords and hidden real passwordscan be exposed for projects with high requirements for security and secrecy levels through the hiding method and system, the learning cost is low, operation is easy, and a guarantee is provided for security of the passwords.
Owner:中孚安全技术有限公司 +3
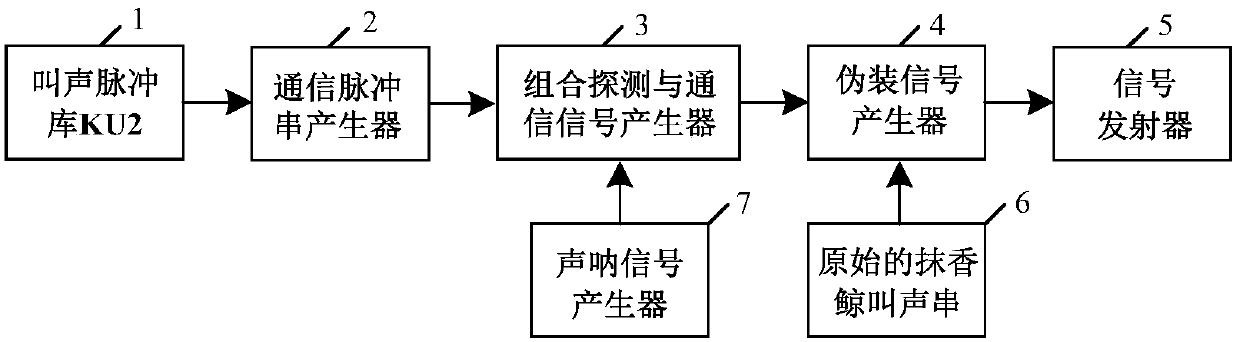
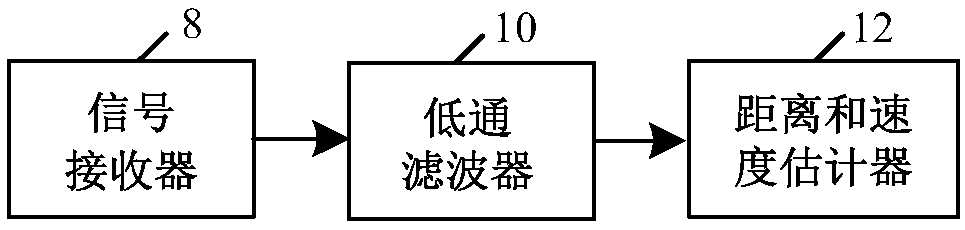
Combined detection and communication device and method utilizing whale sound
PendingCN108279418AIncrease profitAchieve concealmentSonic/ultrasonic/infrasonic transmissionAcoustic wave reradiationVIT signalsHigh-pass filter
The invention belongs to the field of target detection and communication and provides a combined detection and communication signal construction method and processing technology utilizing whale sound.A transmitting end is composed of a call pulse library storer, a communication pulse string generator, a combined detection and communication signal generator, a disguising signal generator, a signaltransmitter and a sonar signal generator in sequential connection, and a receiving end is composed of a signal receiver, a low pass filter, a distance and speed estimator, a high pass filter and a communication decoder. The combined detection and communication signal construction method is mainly used for target detection and communication occasions.
Owner:TIANJIN UNIV
All-directional ultrasound detecting movement mechanism
InactiveCN101118285AOmnidirectional Ultrasonic Detection RealizationRealize all-round three-dimensional detectionAcoustic wave reradiationSonificationElectric machine
The present invention provides an omni-directional ultrasonic detection motion mechanism and comprises a cabin and an overall mechanism arranged in the cabin. The cabin consists of an upper hatchcover and a lower hatchcover; the overall mechanism consists of a movement input mechanism, a movement transformation mechanism, a direction transform mechanism and an extending displacement increasing mechanism; the movement input mechanism comprises a DC electric machine and a crank block mechanism; the DC electric machine connects with the crank block mechanism; the crank block mechanism connects with the movement transformation mechanism; the direction transform mechanism connects with the movement transformation mechanism; the movement of the extending displacement increasing mechanism is inputted by the same DC electric machine, and the extending displacement increasing mechanism connects with an external connecting lateral plate through a transmission fork, then drives the external connecting lateral plate to movjinakanishe axially; the external connecting lateral plate connects with the lateral plate of an ultrasonic detector of an installation embarkation ultrasonic detector 10. The present invention realizes the space coupling movements of 2 degree of freedom using the single degree of freedom drive, and can realize the required omni-directional space detection of the ultrasonic detector by appropriately arranging the basic parameters such as the crank length, the connecting rod length and the mechanism bias, the teeth number of gear, and so on.
Owner:HARBIN INST OF TECH
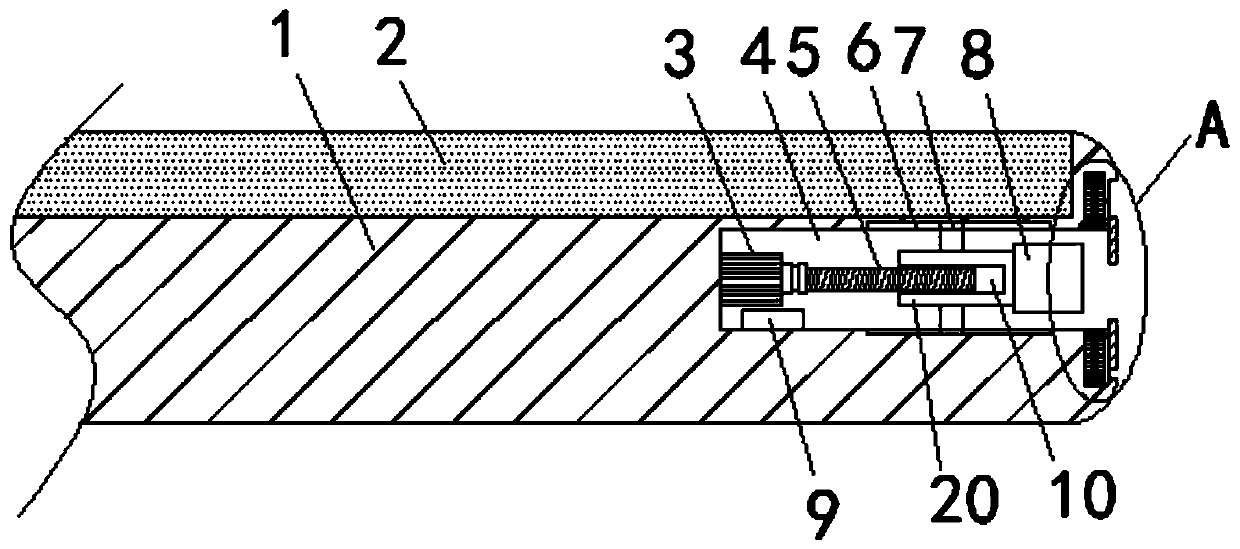
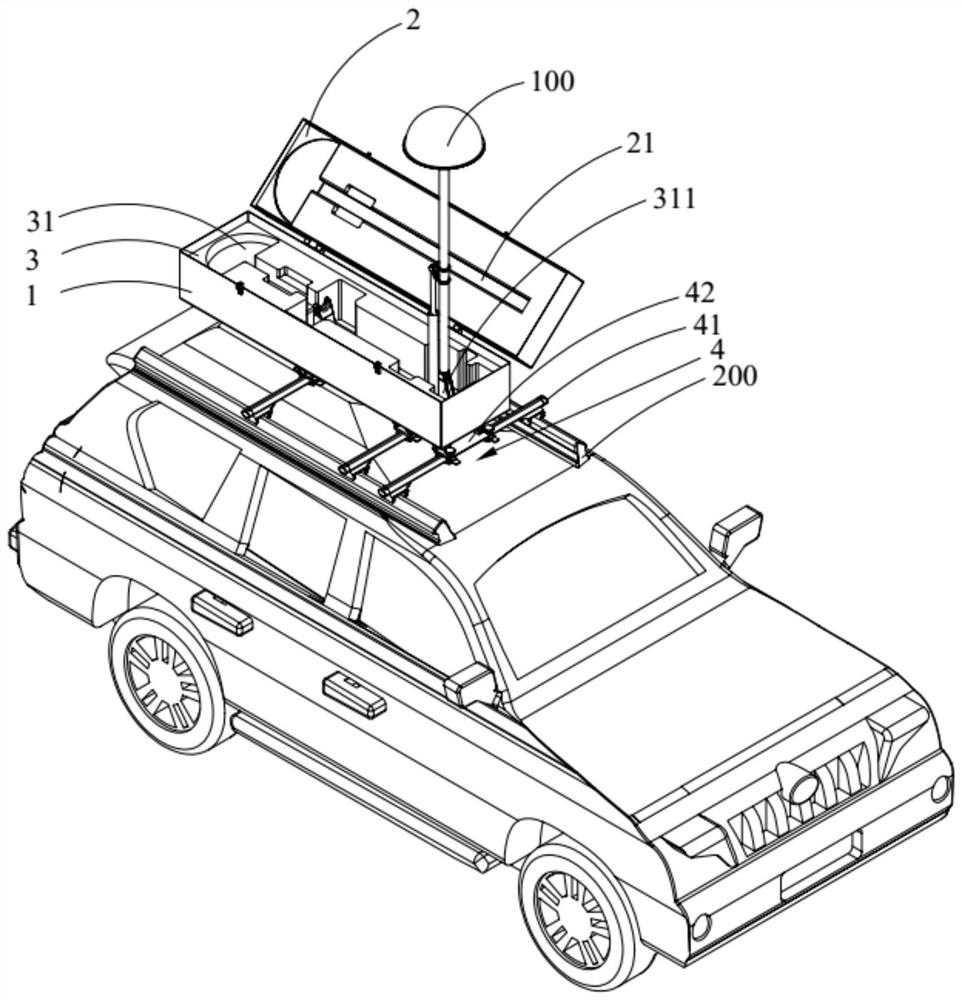
Vehicle-mounted antenna protection device
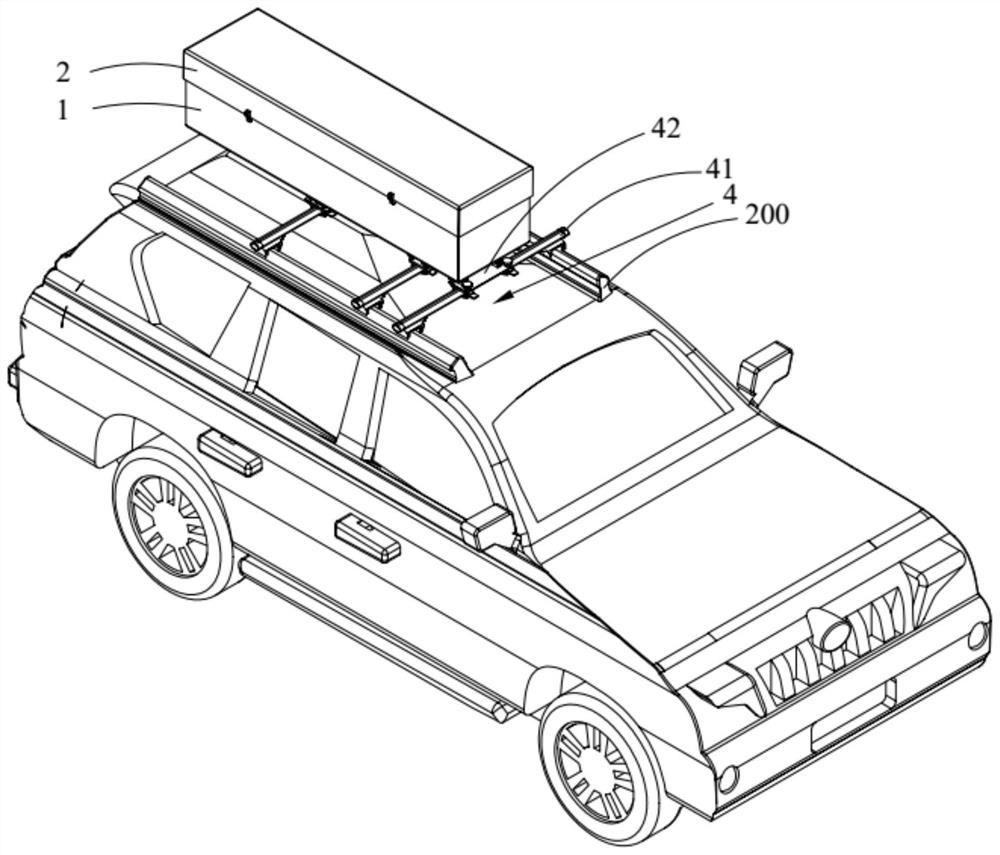
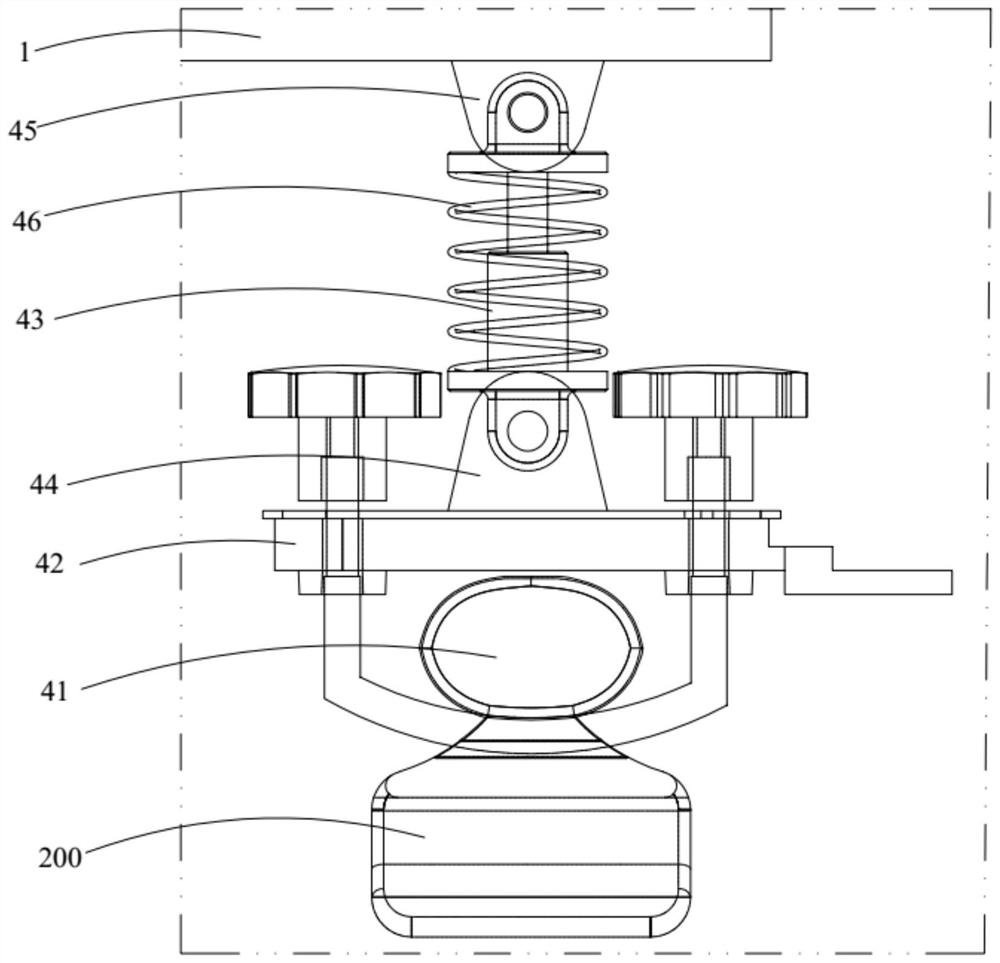
ActiveCN111816976APlay a protective effectPrevent rustInternal combustion piston enginesPivotable antennasIn vehicleUncrewed vehicle
The invention belongs to the technical field of unmanned aerial vehicles, and discloses a vehicle-mounted antenna protection device. The vehicle-mounted antenna protection device comprises: a protection box which is arranged on a luggage rack on the roof of an automobile, wherein one end of the protection box is open; a cover plate rotatably arranged on the protection box, wherein the cover plateis configured to selectively block the opening; and a buffer piece arranged in the protection box, wherein a containing groove is formed in the buffer piece, and a vehicle-mounted antenna is configured to be selectively contained in the containing groove. According to the vehicle-mounted antenna protection device, the vehicle-mounted antenna can be accommodated in the protection box, the protection box plays a role in protecting the vehicle-mounted antenna so as to ensure the precision of the vehicle-mounted antenna, and the protection box and the cover plate also play a role in hiding the vehicle-mounted antenna. Besides, when the automobile runs on a bumpy road condition, the buffering piece plays a role in buffering the vehicle-mounted antenna, the situation that the vehicle-mounted antenna is damaged due to vibration is avoided, the safety coefficient is high, the reliability is good, and the service life is long.
Owner:广东电网有限责任公司韶关供电局
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com