Hiding method and system for Web security login password
A technology for login password and secure login, applied in transmission systems, electrical components, etc., can solve problems such as occupying computers, and achieve the effects of low learning cost, network security, and easy operation.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
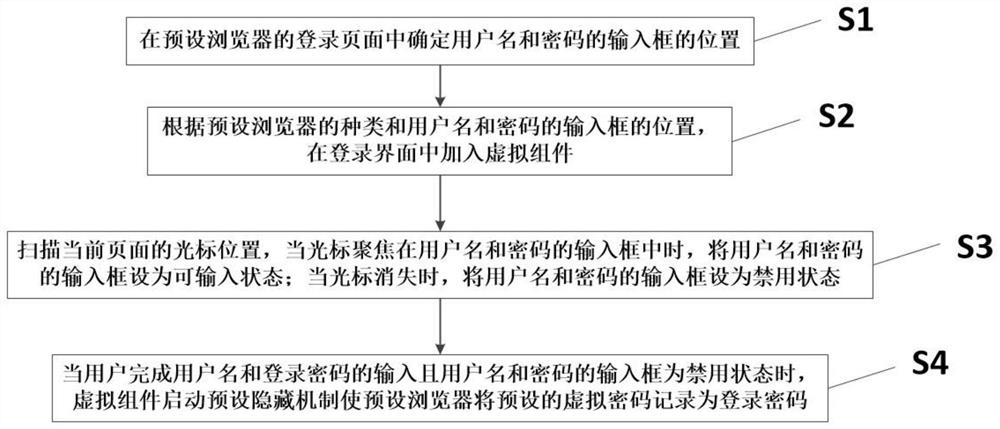
[0047] Such as figure 1 A method for hiding a Web security login password shown includes the following steps:
[0048] S1: Determine the positions of the input boxes of the user name and the password on the login page of the preset browser.
[0049] S2: Add a virtual component to the login interface according to the type of the preset browser and the positions of the input boxes of the user name and password.
[0050] S3: Scan the cursor position on the current page. When the cursor is focused on the input box of the user name and password, set the input box of the user name and password to the input state; when the cursor disappears, set the input box of the user name and password to disabled state.
[0051] S4: When the user finishes inputting the user name and login password and the input boxes of the user name and password are disabled, the virtual component activates a preset hiding mechanism to make the preset browser record the preset virtual password as the login pas...
Embodiment 2
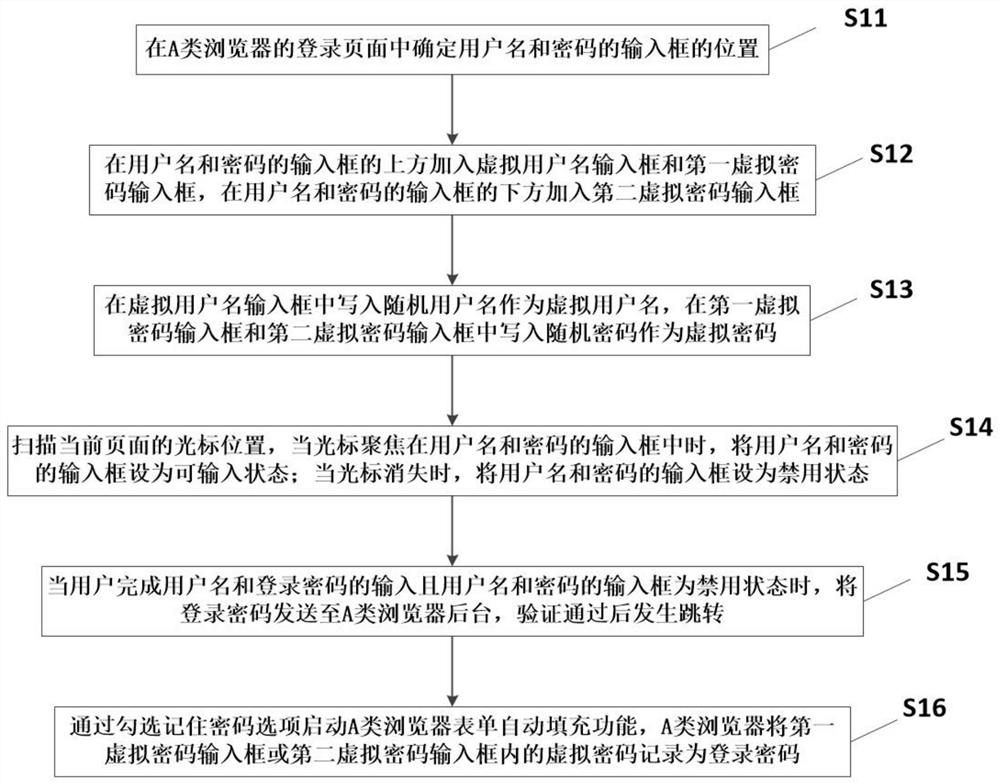
[0054] Based on Embodiment 1, this embodiment provides a method for hiding a Web security login password. The browser used in this method is a class A browser, that is, IE browser, Firefox browser, or a browser with the same architecture. Such as figure 2 As shown, it specifically includes the following steps:
[0055] S11: Determine the positions of the input boxes of the user name and the password on the login page of the type A browser.
[0056] S12: Add a virtual username input box and a first virtual password input box above the username and password input boxes, and add a second virtual password input box below the username and password input boxes.
[0057] S13: Write a random user name in the virtual user name input box as the virtual user name, and write a random password in the first virtual password input box and the second virtual password input box as the virtual password.
[0058] S14: Scan the cursor position on the current page, when the cursor is focused on t...
Embodiment 3
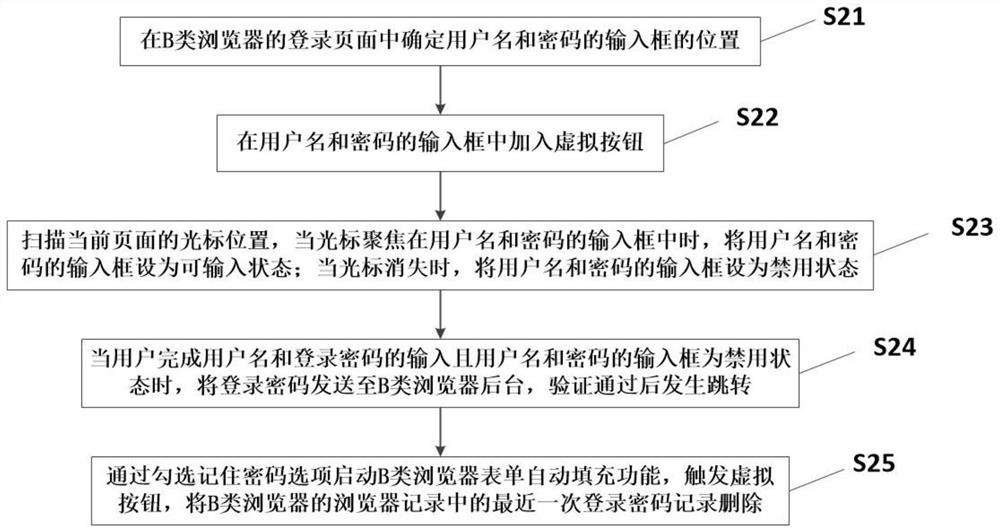
[0064] Based on embodiment one, present embodiment provides a kind of hiding method of Web security login password, and the browser that this method adopts is B class browser, i.e. I Google browser, or the browser identical with its structure. Such as image 3 As shown, it specifically includes the following steps:
[0065] S21: Determine the positions of the input boxes of the user name and the password on the login page of the type B browser.
[0066] S22: Add a virtual button in the input box of the user name and password.
[0067] S23: Scan the cursor position on the current page, when the cursor is focused on the input box of the user name and password, set the input box of the user name and password to the input state; when the cursor disappears, set the input box of the user name and password to disabled state.
[0068] S24: When the user completes the input of the user name and login password and the input boxes of the user name and password are disabled, the login ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com