Text information hiding method and device
A text information and file technology, applied in the field of information hiding, can solve problems such as data loss, and achieve the effect of high concealment and robustness
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
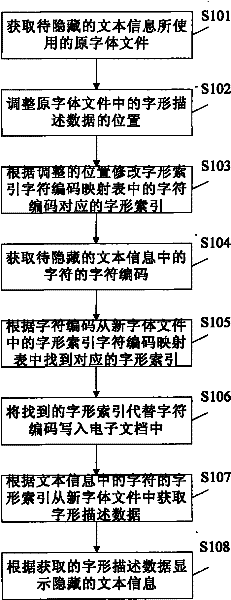
[0042] The technical idea of this embodiment is to change the glyph index corresponding to the character code by changing the position of the glyph description data in the font file, thereby changing the mapping relationship between the glyph index and the character code.
[0043] figure 1 is a flow chart of the text information hiding method according to the first embodiment of the present invention.
[0044] Such as figure 1 As shown, first, in step S101, the original font file used by the text information to be hidden is acquired.
[0045] Next, a new font file is generated based on the original font file. Specifically, first, in step S102, the position of the font description data in the original font file is adjusted. Here, the adjustment method can be adjusted according to a predetermined rule (for example, in reverse order), or it can be adjusted randomly. Then, in step S103, the glyph index corresponding to the character code in the glyph index character code mapp...
no. 2 example
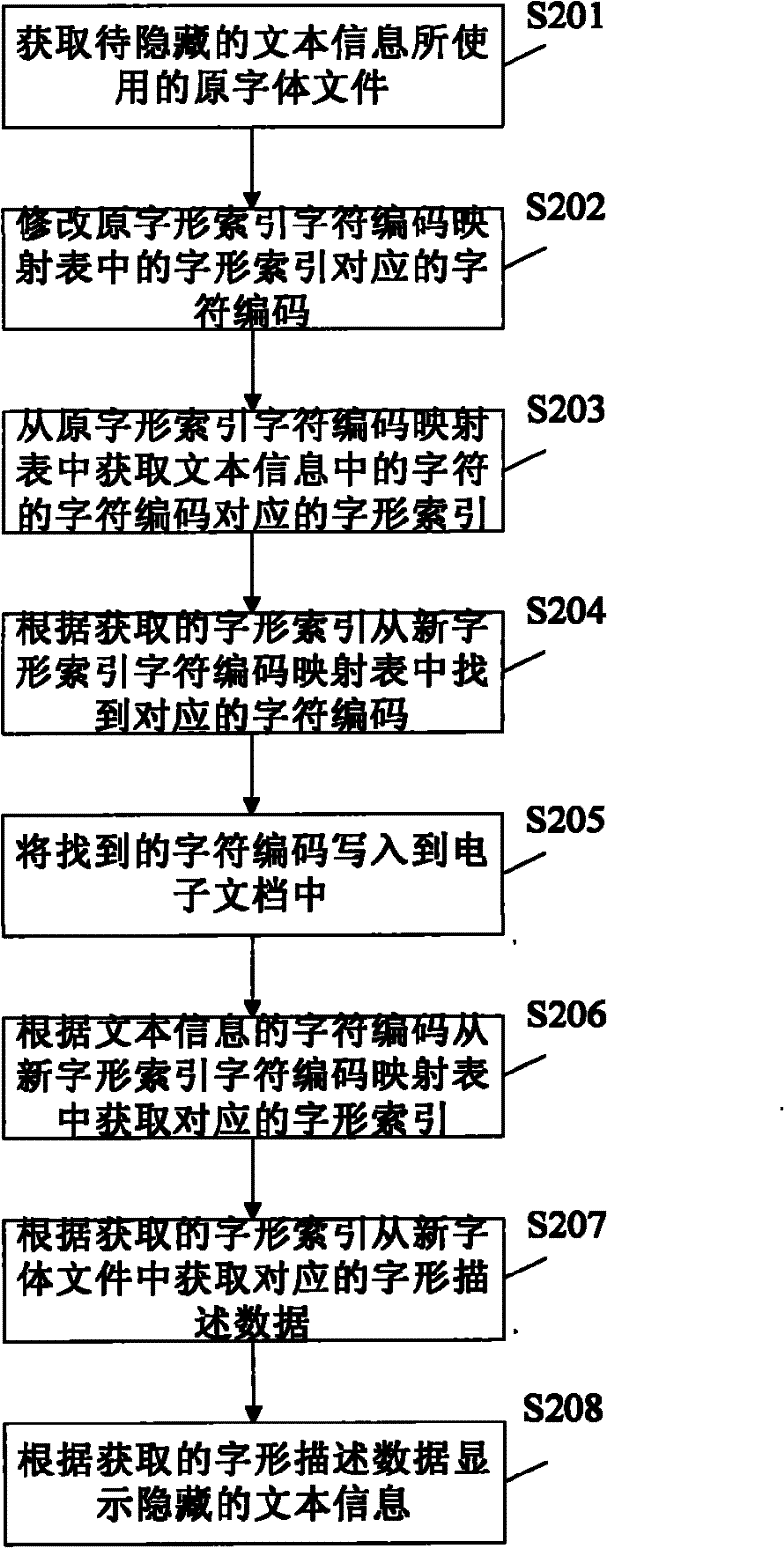
[0076] The technical idea of this embodiment is to change the mapping relationship between the glyph index and the character code by changing the character code corresponding to the glyph index in the glyph index character code mapping table, while the position of the glyph description data in the font file does not change .
[0077] figure 2 is a flow chart of the text information hiding method according to the second embodiment of the present invention.
[0078] Such as figure 2 As shown, first, in step S201, the original font file used by the text information to be hidden is acquired.
[0079] Next, a new font file is generated based on the original font file. Specifically, in step S202, the character code corresponding to the glyph index in the glyph index character code mapping table in the original font file is modified, thereby generating a new font file.
[0080] Next, the text information to be hidden is written into the electronic document based on the new fon...
no. 3 example
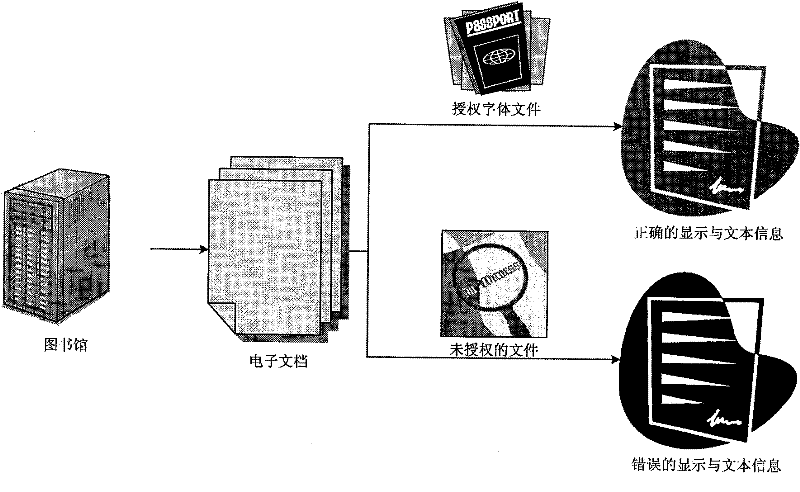
[0101] This embodiment is an application example of the first embodiment and the second embodiment. In this example, applying the text information hiding method according to the first embodiment or the second embodiment of the present invention to a library mainly includes the following three steps:
[0102] (1) Font file creation
[0103] According to the requirements of the library, the font file is modified according to the text information hiding method of the first embodiment or the second embodiment, and a proprietary font file is generated.
[0104] (2) Electronic document production
[0105] Generate documents that need to be made public based on the proprietary font files you have created.
[0106] (3) Viewing electronic documents
[0107] Such as image 3 As shown, users can read electronic documents displaying correct text information on the library's machines, or obtain and install proprietary font files through the network to view correct text information. If...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com