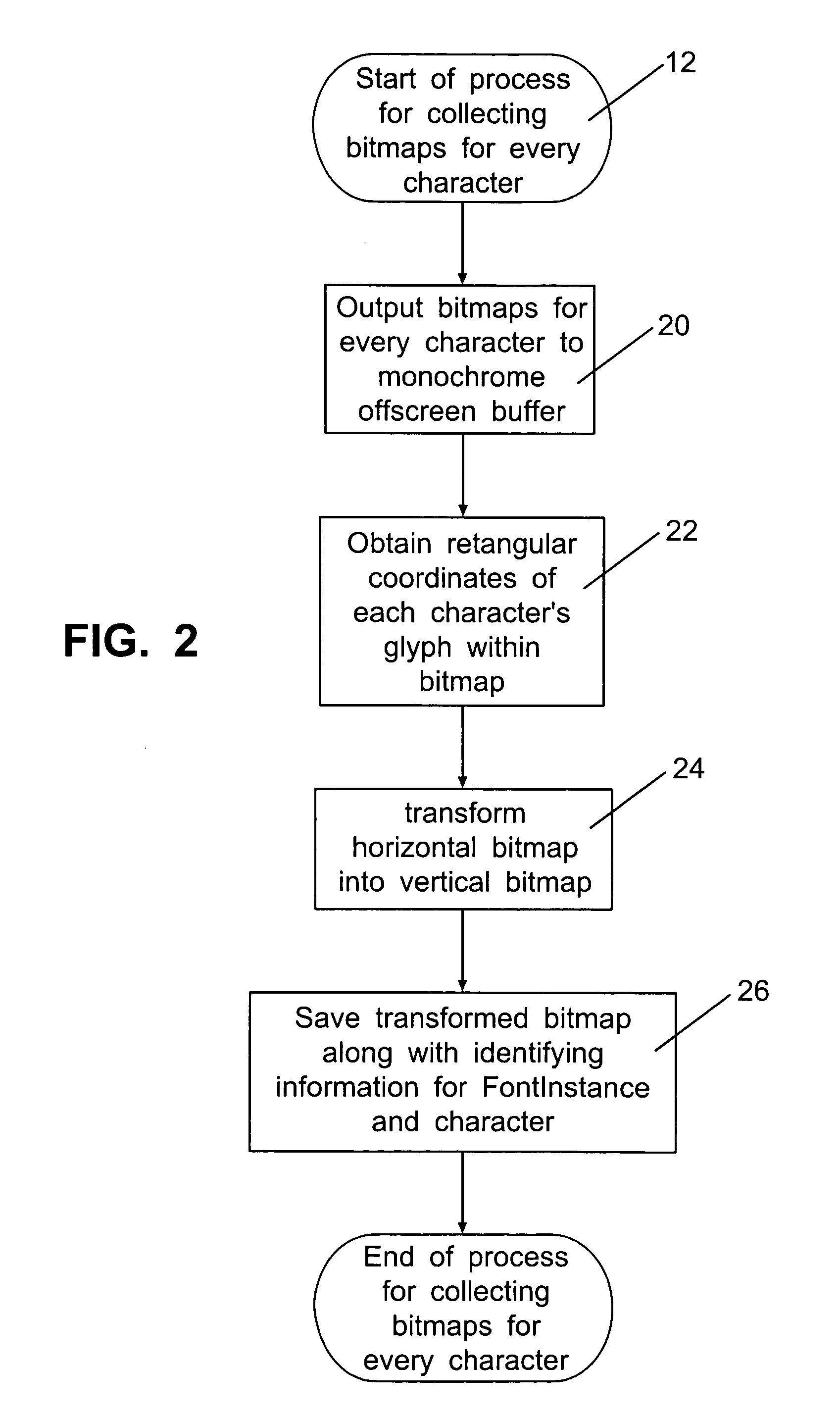
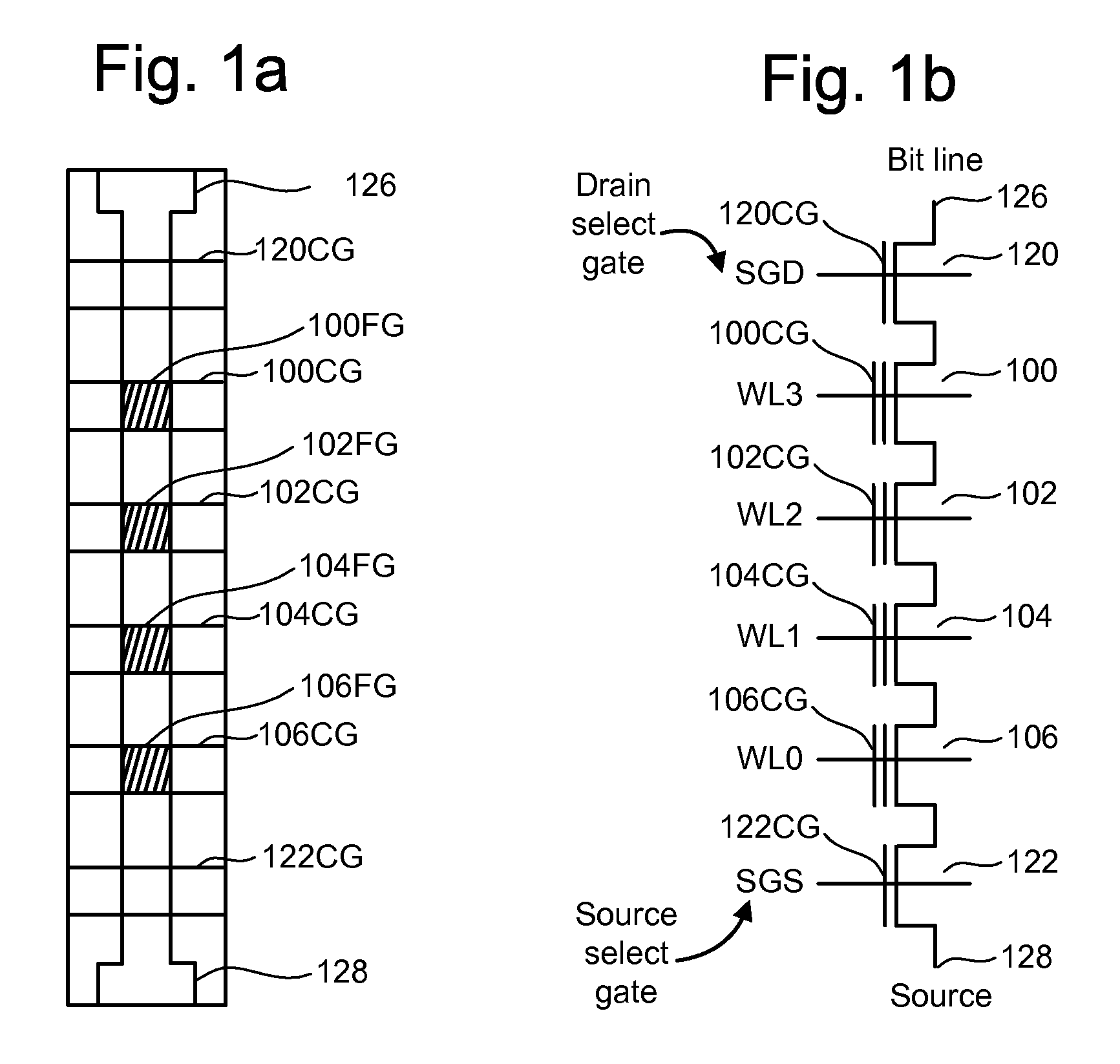
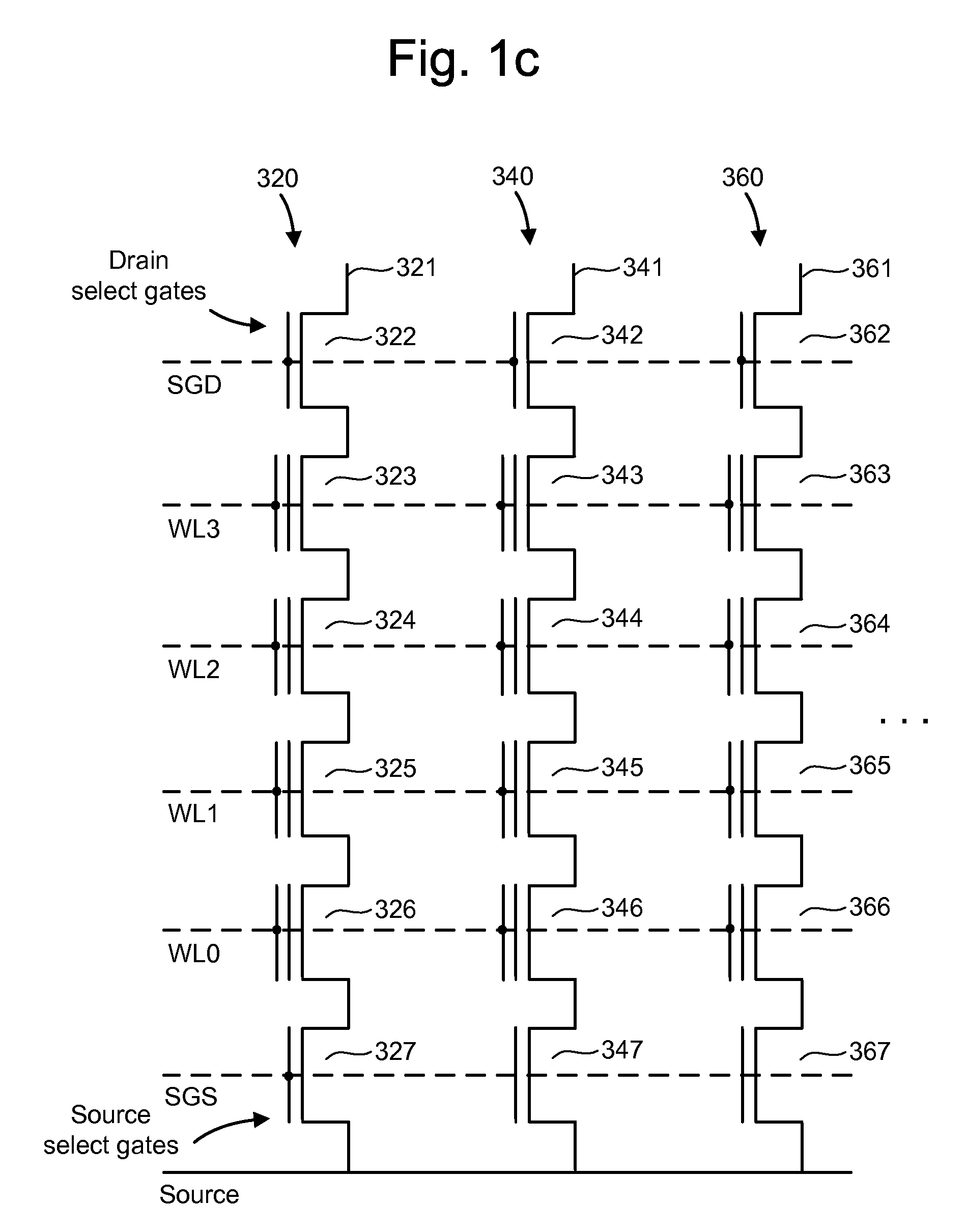
Patents
Literature
1010 results about "Glyph" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
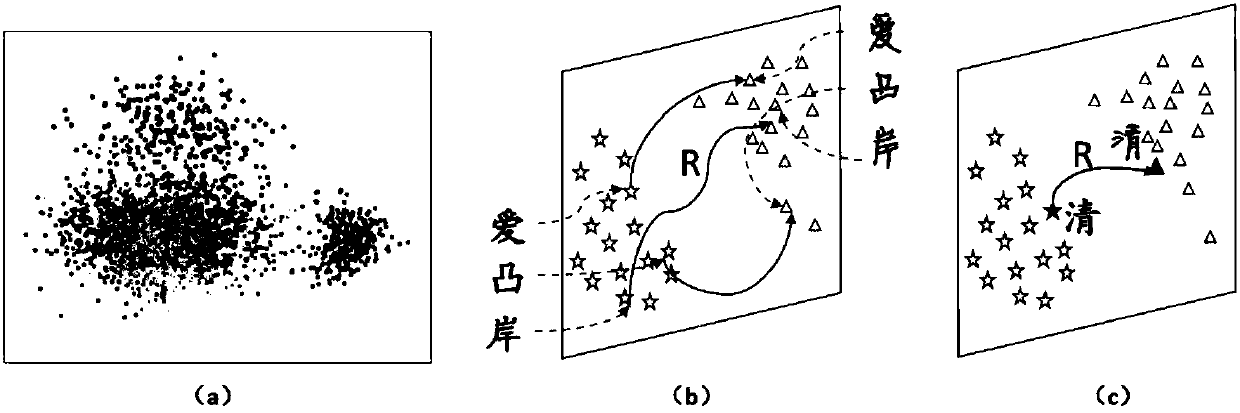
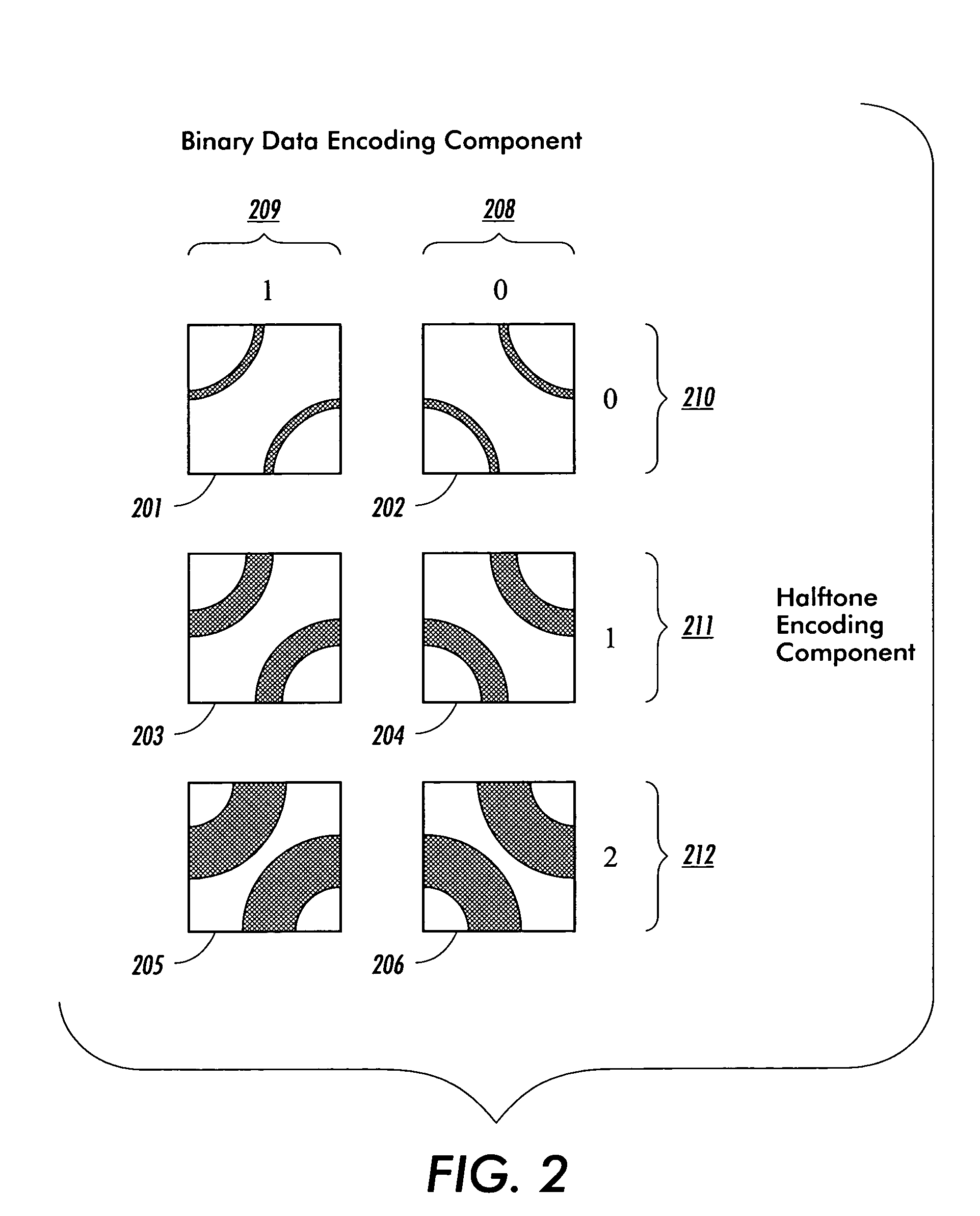
In typography, a glyph /ɡlɪf/ is an elemental symbol within an agreed set of symbols, intended to represent a readable character for the purposes of writing. Glyphs are considered to be unique marks that collectively add up to the spelling of a word or contribute to a specific meaning of what is written, with that meaning dependent on cultural and social usage.
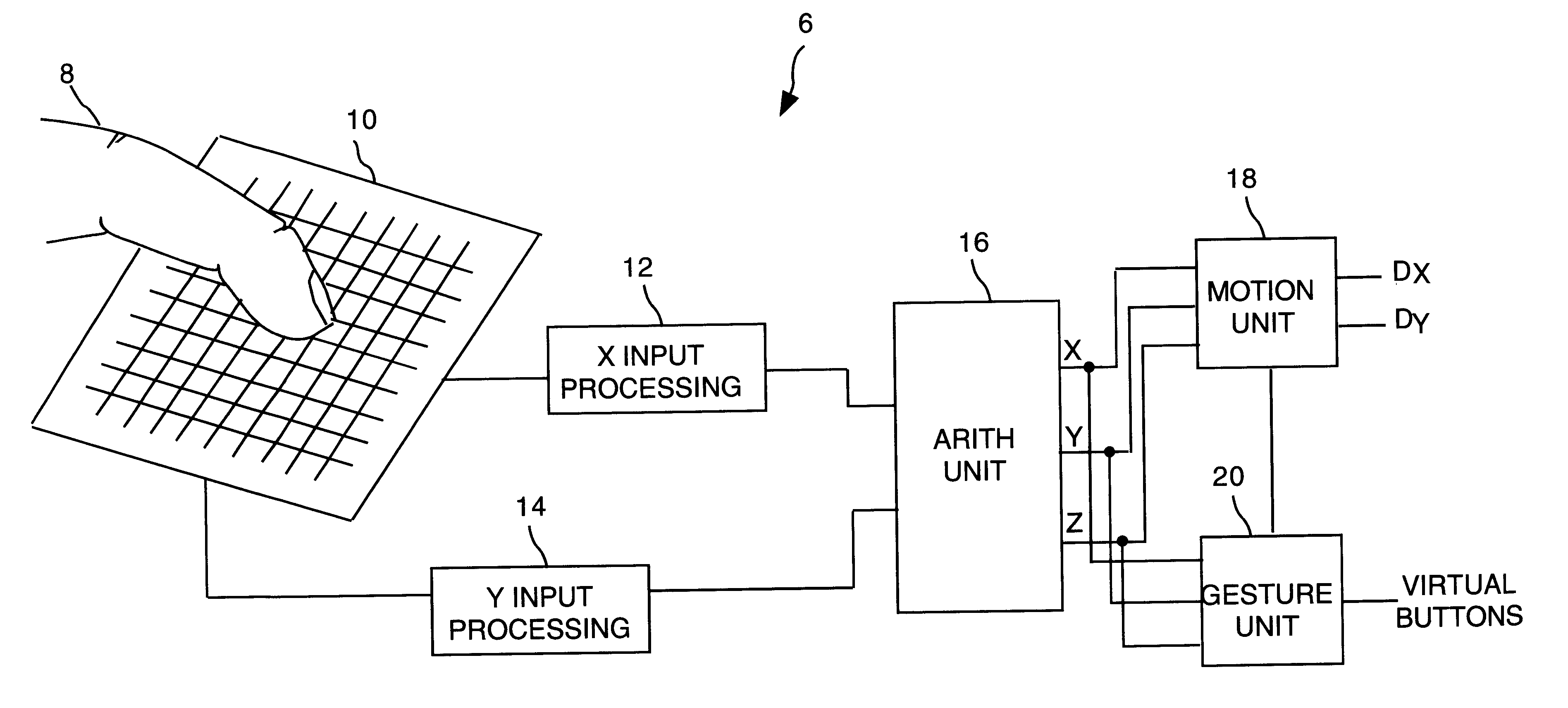
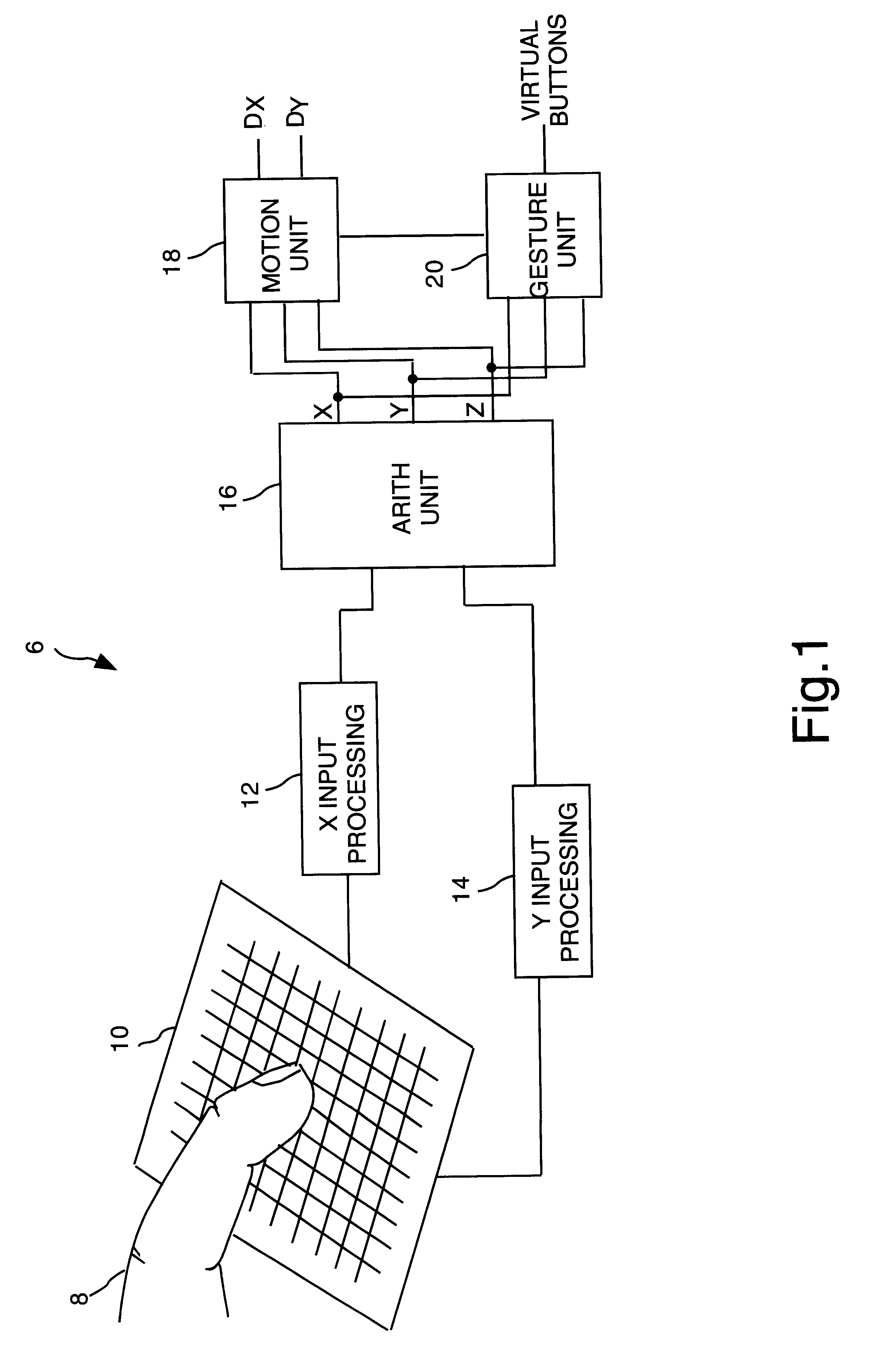
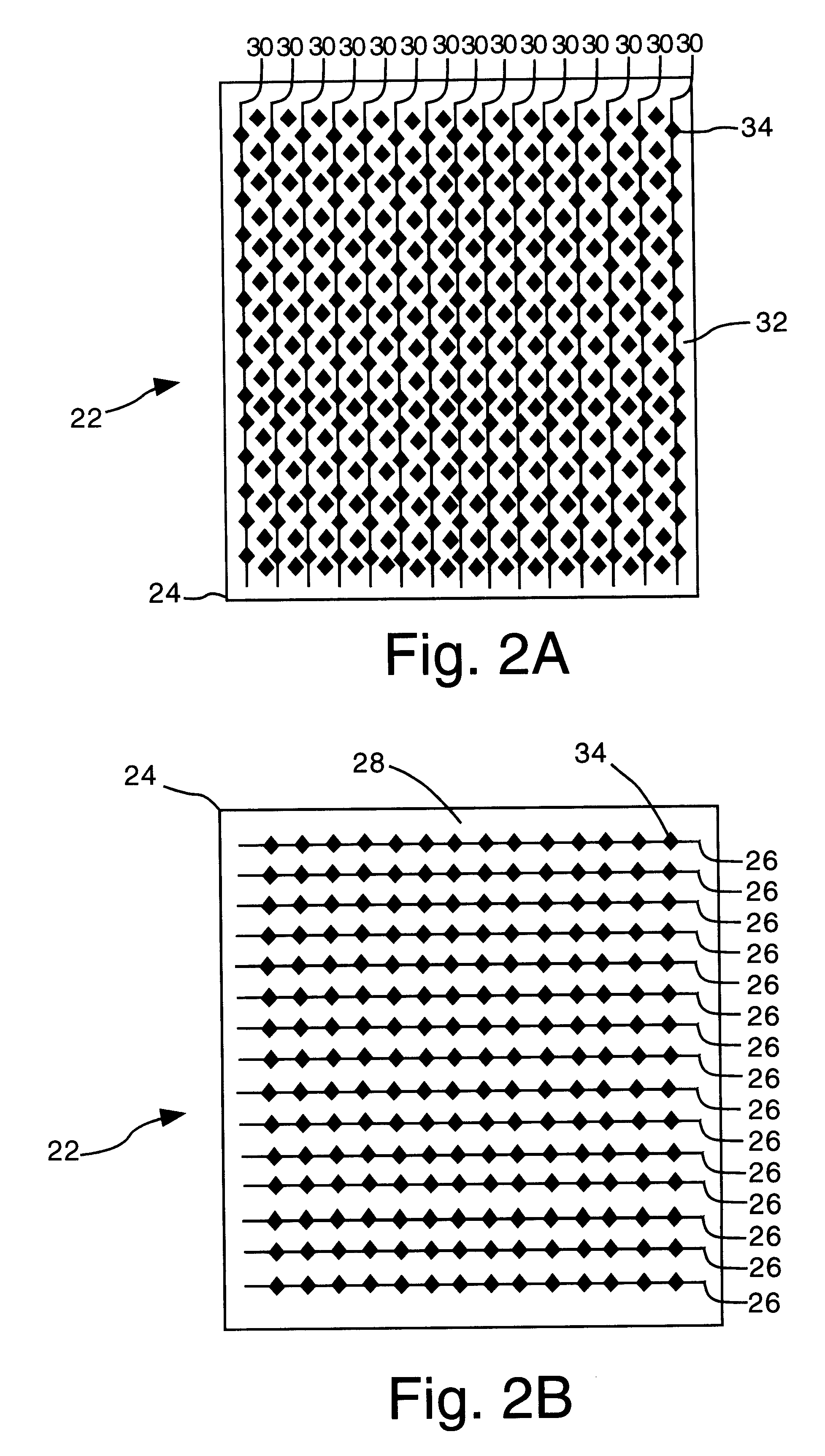
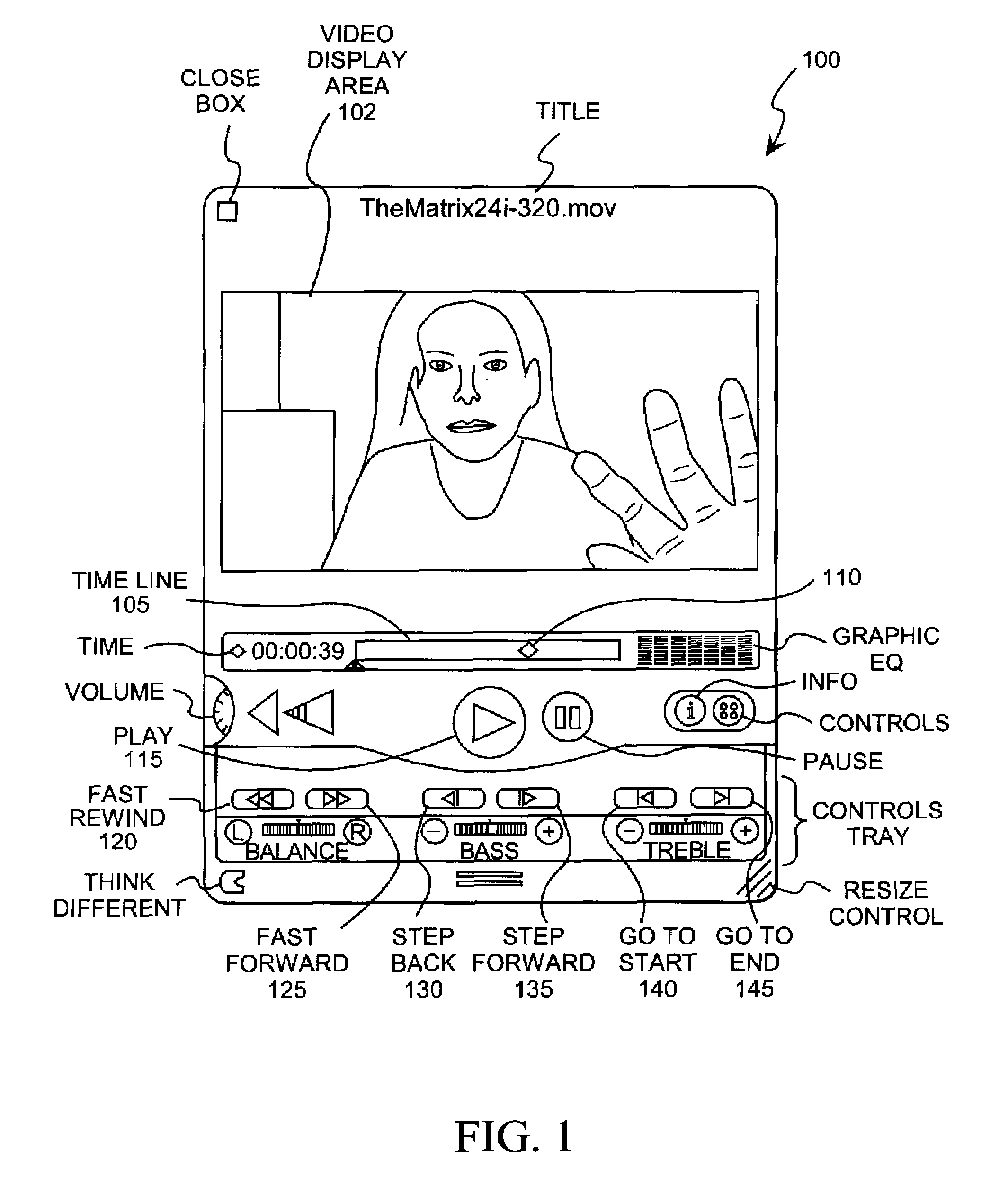
Object position detector with edge motion feature and gesture recognition
InactiveUS6380931B1Easy CalibrationEasy to implementTransmission systemsCharacter and pattern recognitionGlyphComputer vision
Owner:SYNAPTICS INC
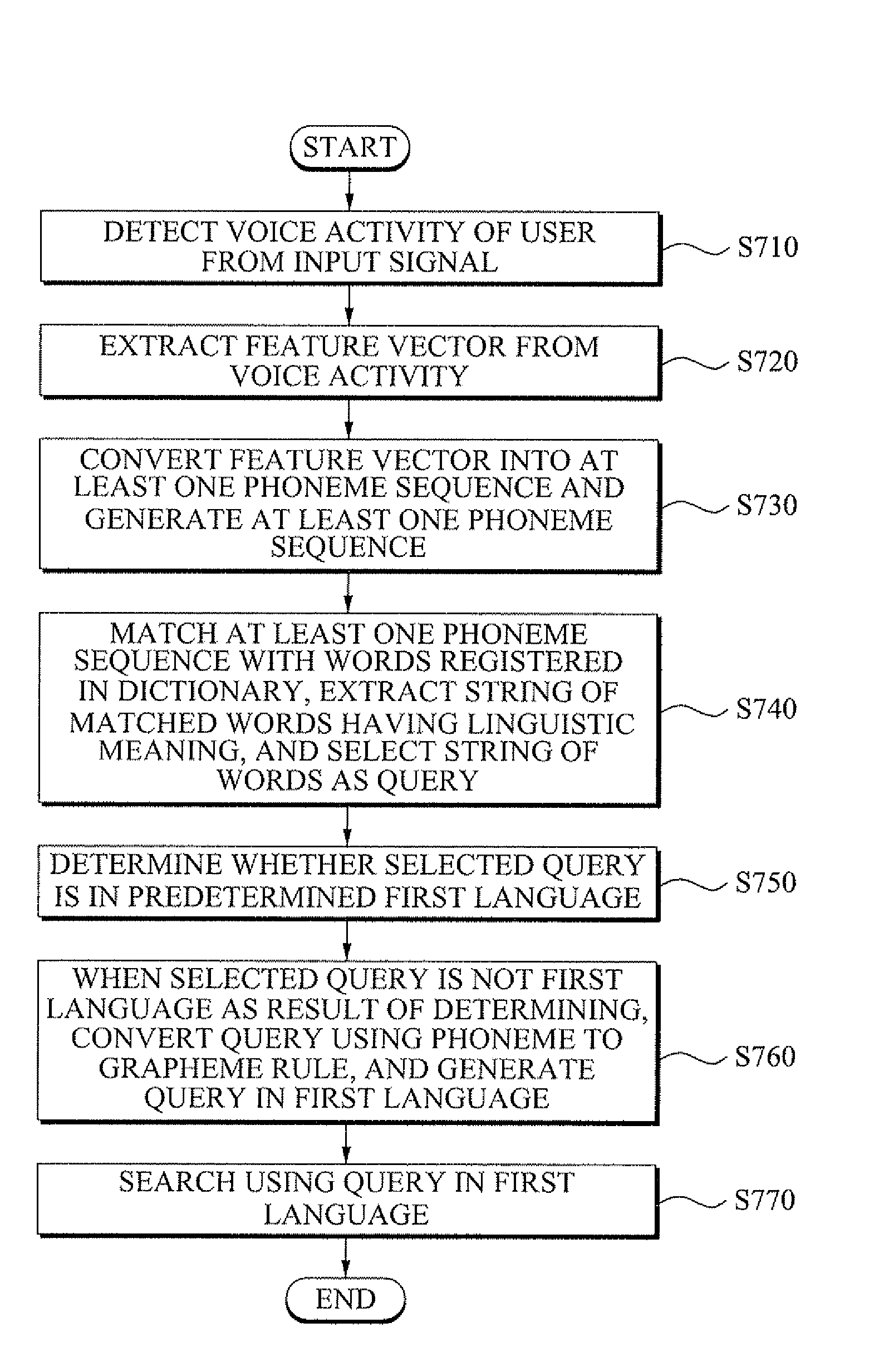
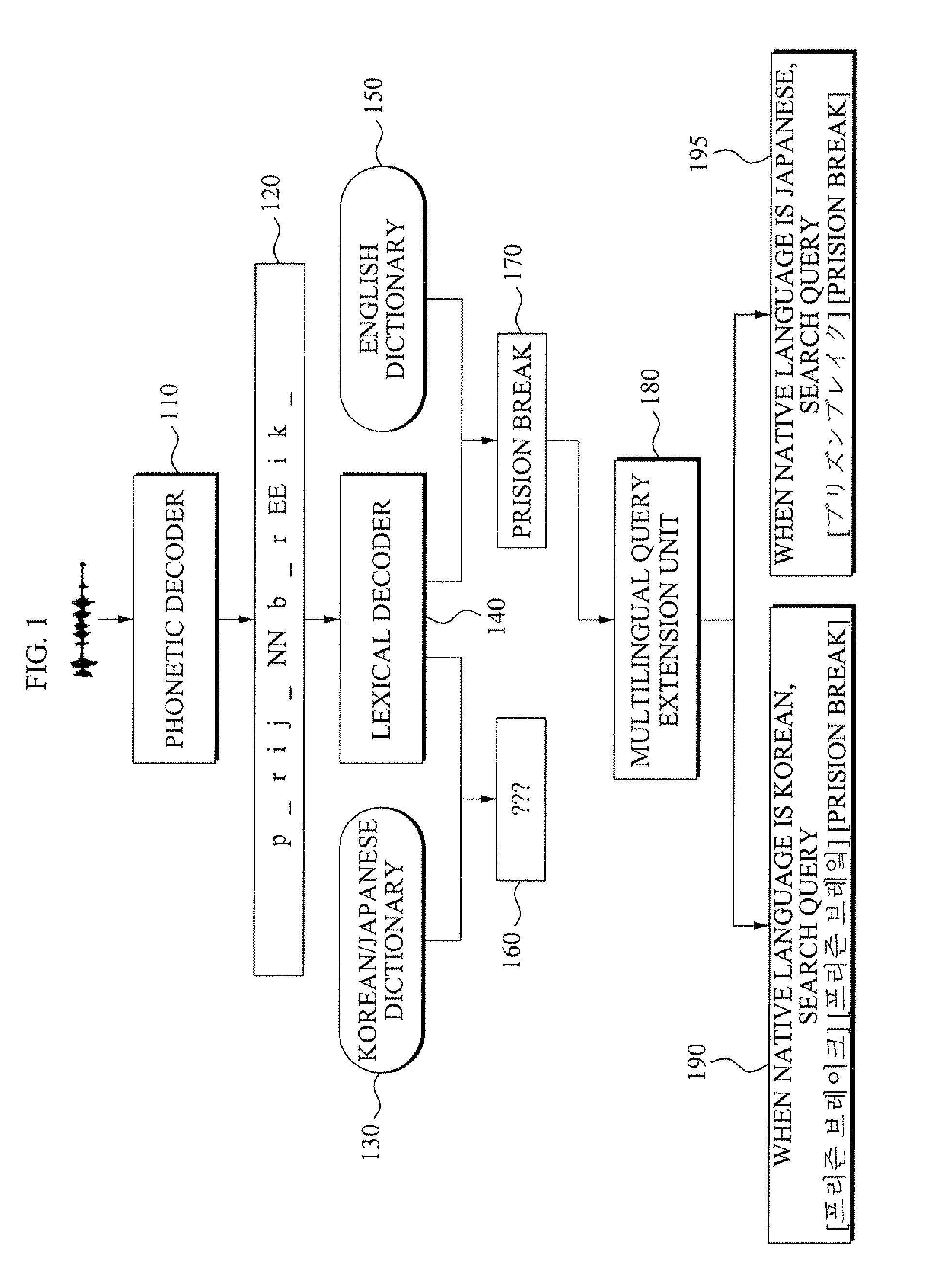
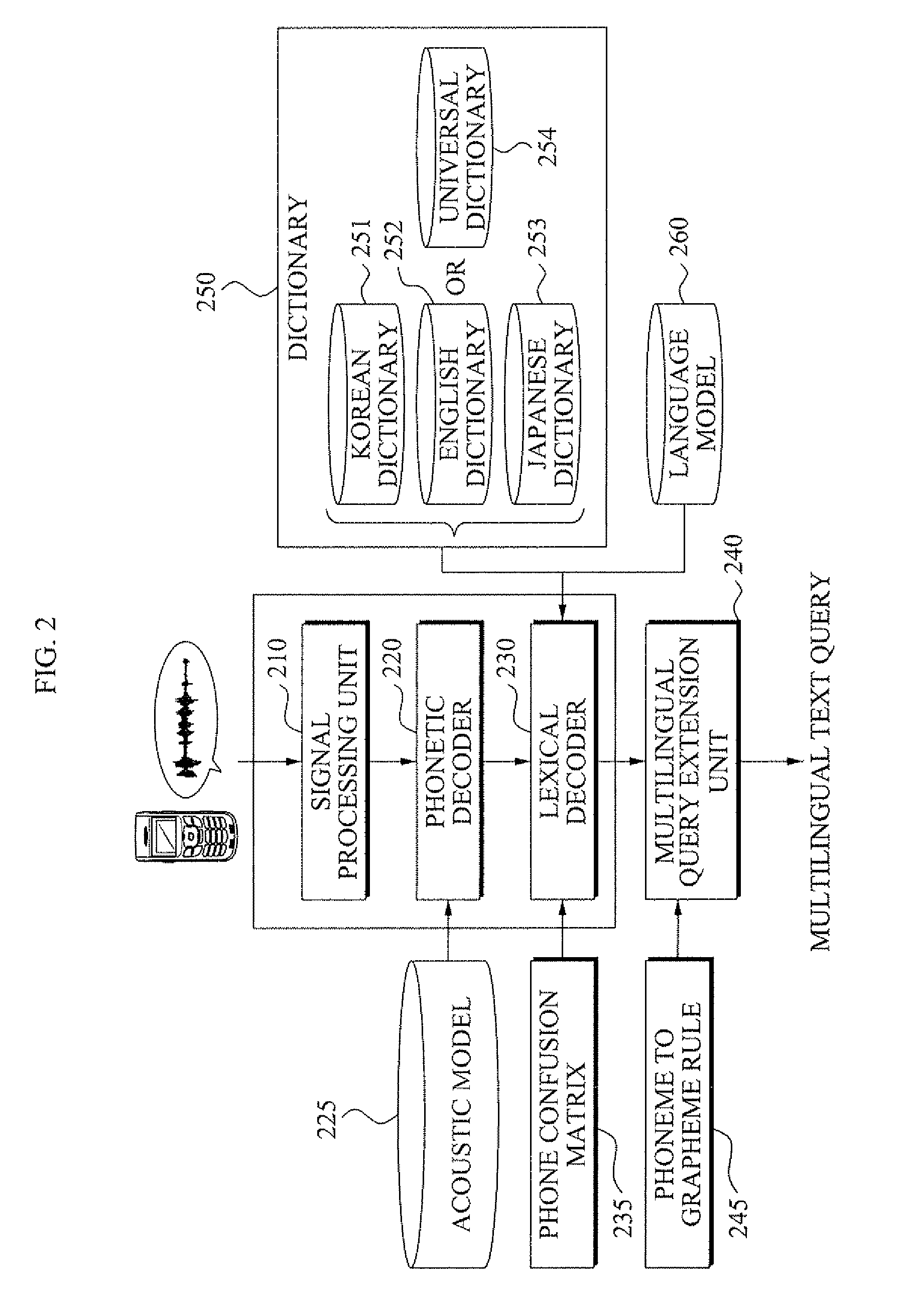
Voice query extension method and system
InactiveUS8155956B2Increase success rateDigital data information retrievalSpeech recognitionFeature vectorGlyph
A voice query extension method and system. The voice query extension method includes: detecting voice activity of a user from an input signal and extracting a feature vector from the voice activity; converting the feature vector into at least one phoneme sequence and generating the at least one phoneme sequence; matching the at least one phoneme sequence with words registered in a dictionary, extracting a string of the matched words with a linguistic meaning, and selecting the string of the matched words as a query; determining whether the query is in a predetermined first language, and when the query is not in the first language as a result of the determining, converting the query using a phoneme to grapheme rule, and generating a query in the first language; and searching using the query in the first language.
Owner:SAMSUNG ELECTRONICS CO LTD
Method and system for recognizing machine generated character glyphs and icons in graphic images
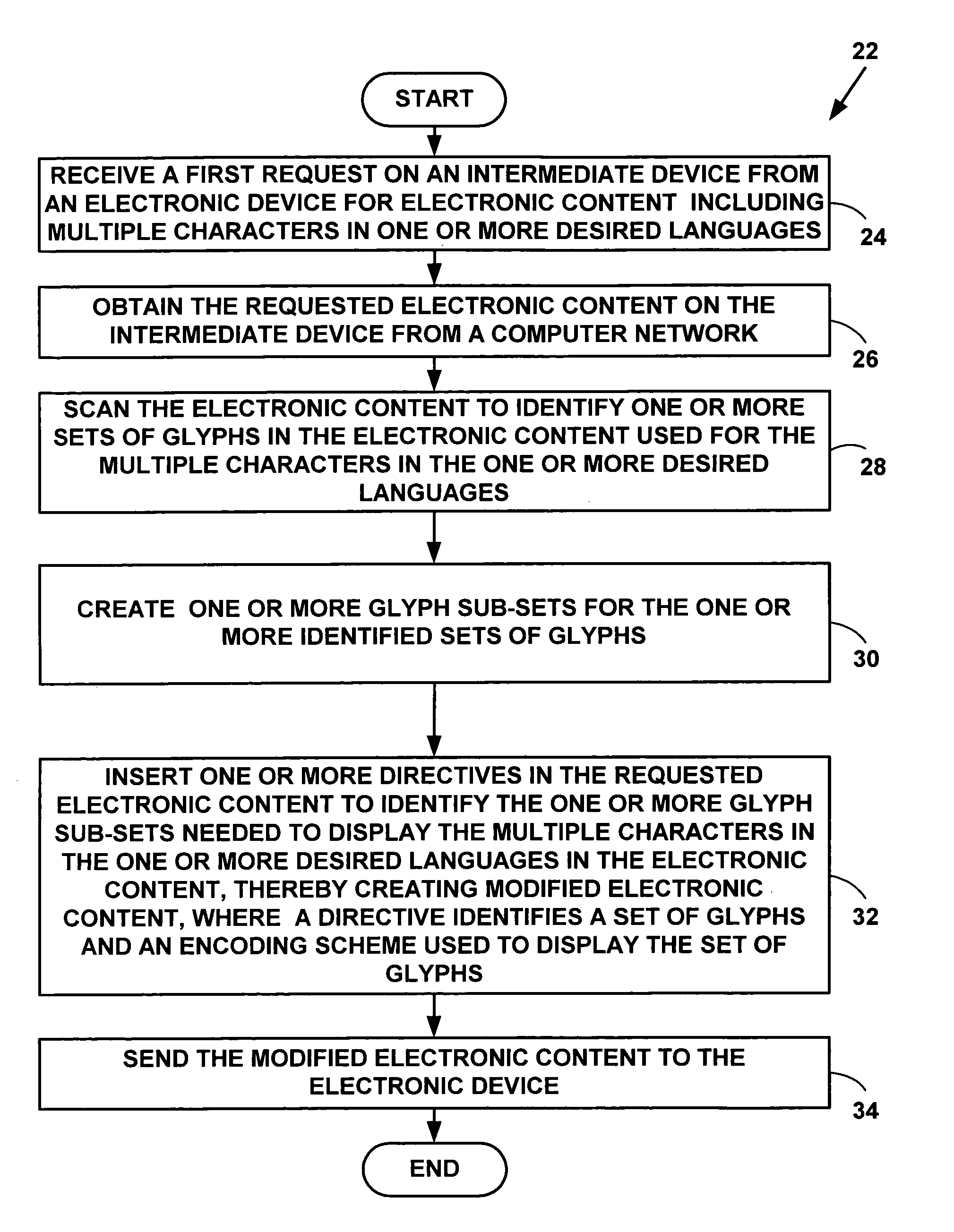
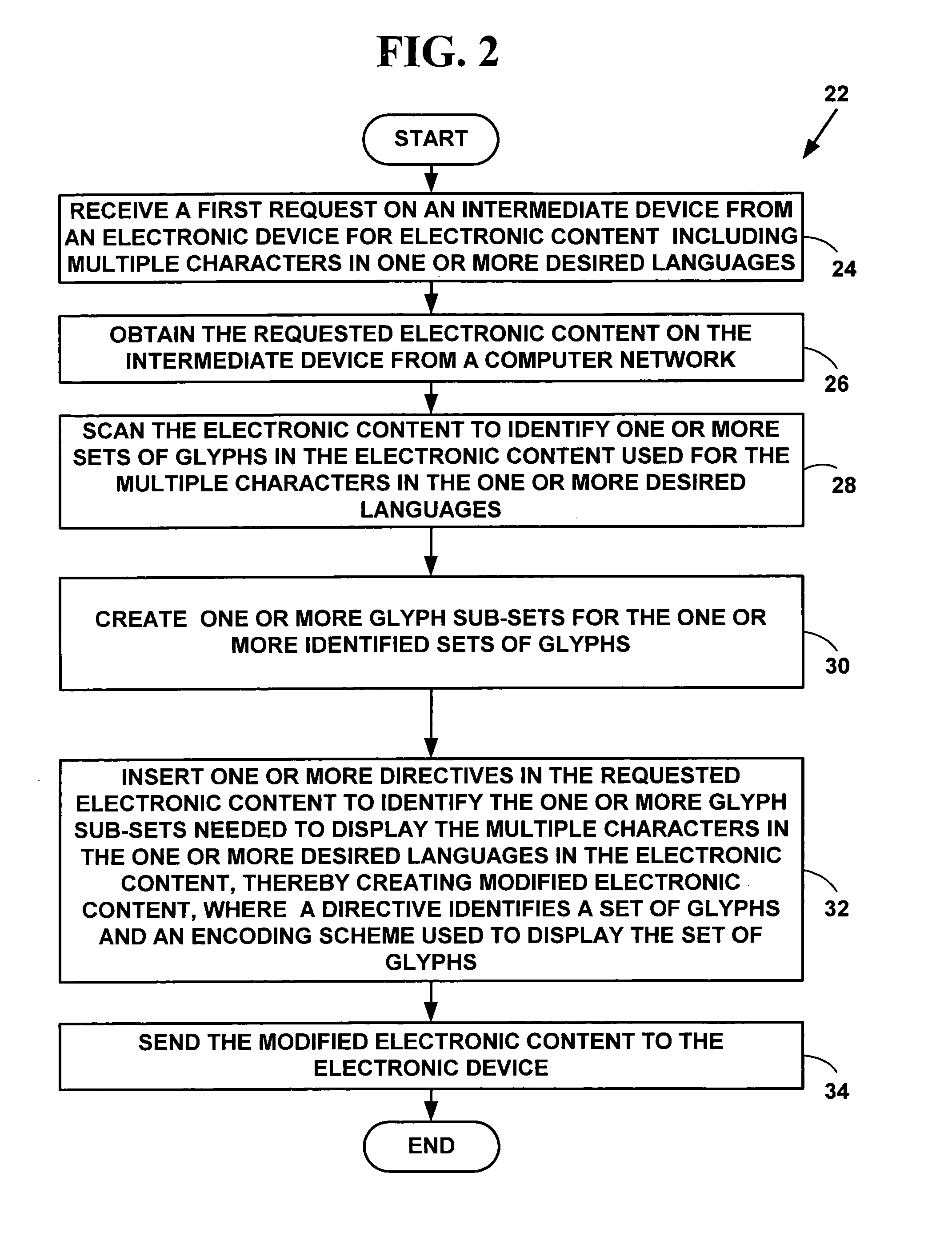
A deterministic finite automaton uses binary search (and optionally hashing) method(s) of sparse matrix representation to recognize the graphical representations of characters or icons from a bitmap representation of the computer screen. This recognition can be applied to translate data from an unknown form of original specification (file format) into a known form of representation, such as HTML. Alternatively this recognition can be applied to another process that can “see” what is on the screen, and perform programmed actions, based on what it “sees”.
Owner:OLCOTT PETER L
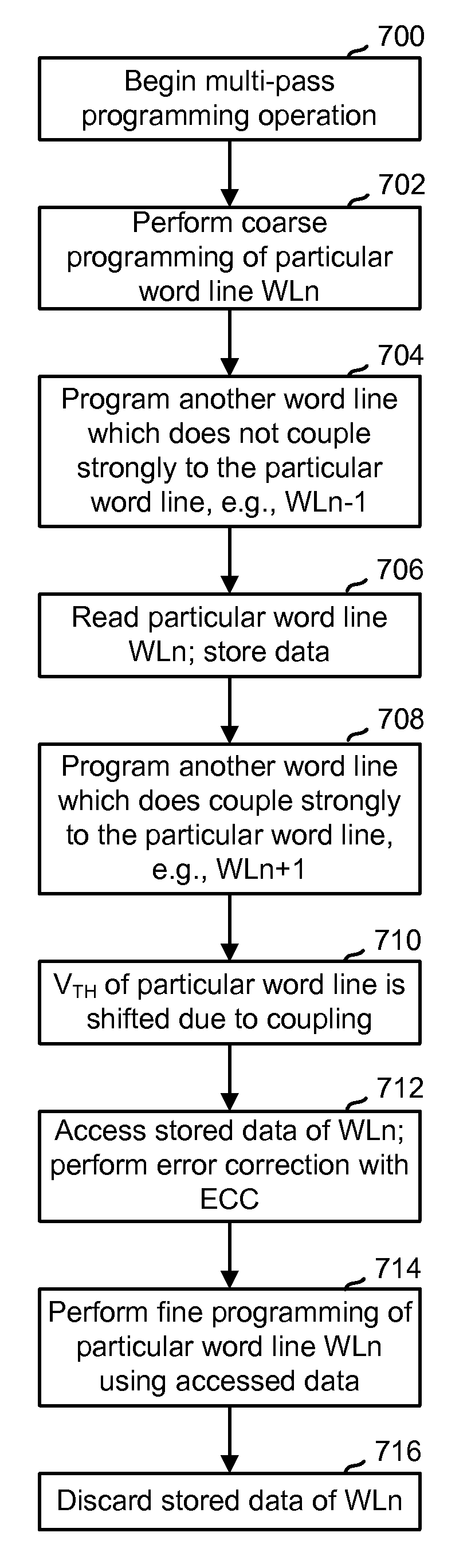
Multi-pass programming for memory with reduced data storage requirement
Coupling effects between adjacent floating gates in a non-volatile storage device are reduced in a multi-pass programming operation, while reducing program data storage requirements. In one approach, storage elements are programmed in an out of sequence or zigzag word line order. A particular word line is programmed with a coarse program pass, after which another word line is programmed with a fine program pass, after which the particular word line is read. The particular word line is read before another word line is programmed with a coarse program pass which causes coupling interference to storage elements of the particular word line. The read data is subsequently used to perform a fine program pass for the particular word line. This avoids the need to store program data of multiple word lines concurrently, so that storage hardware can be reduced in size along with power consumption.
Owner:SANDISK TECH LLC
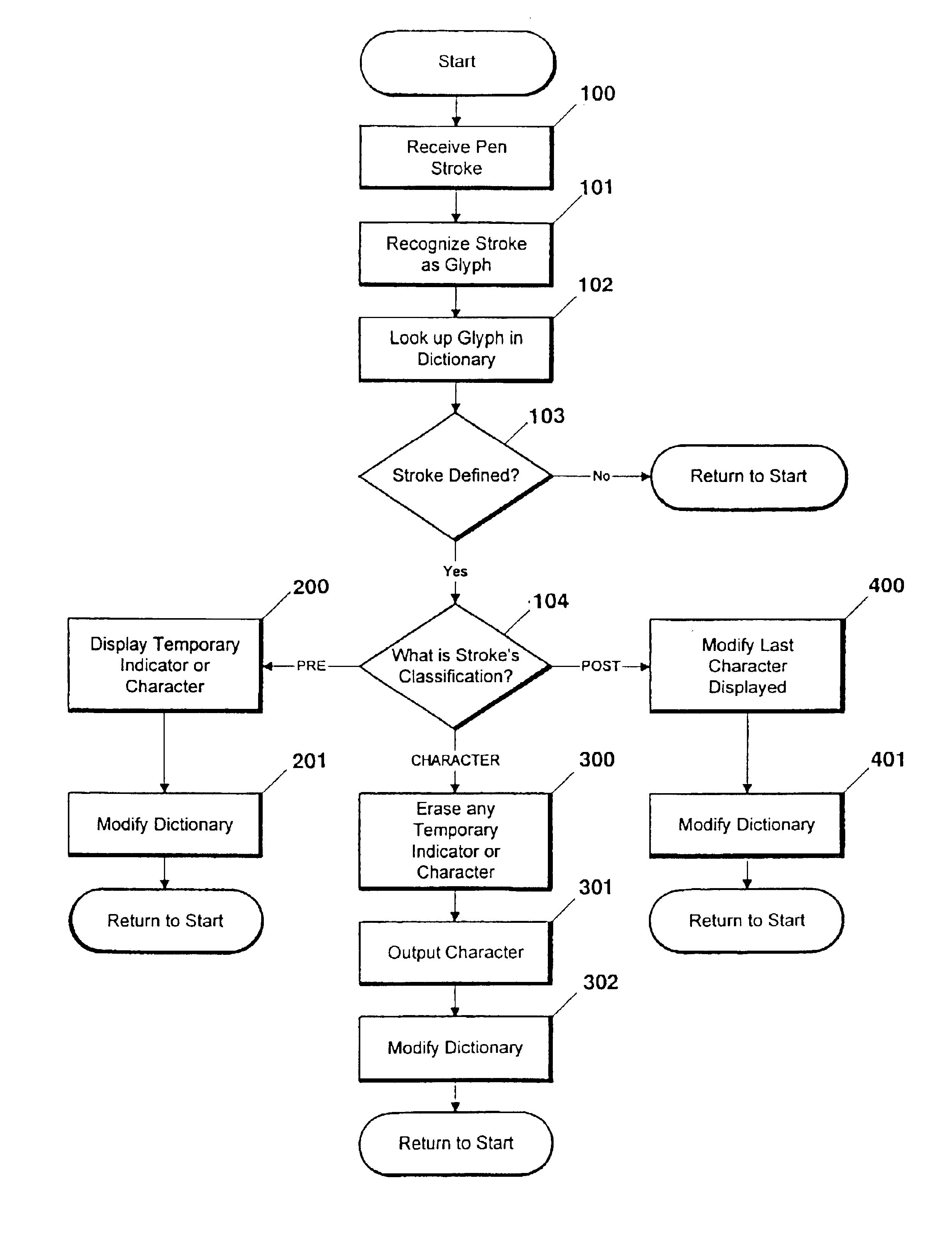
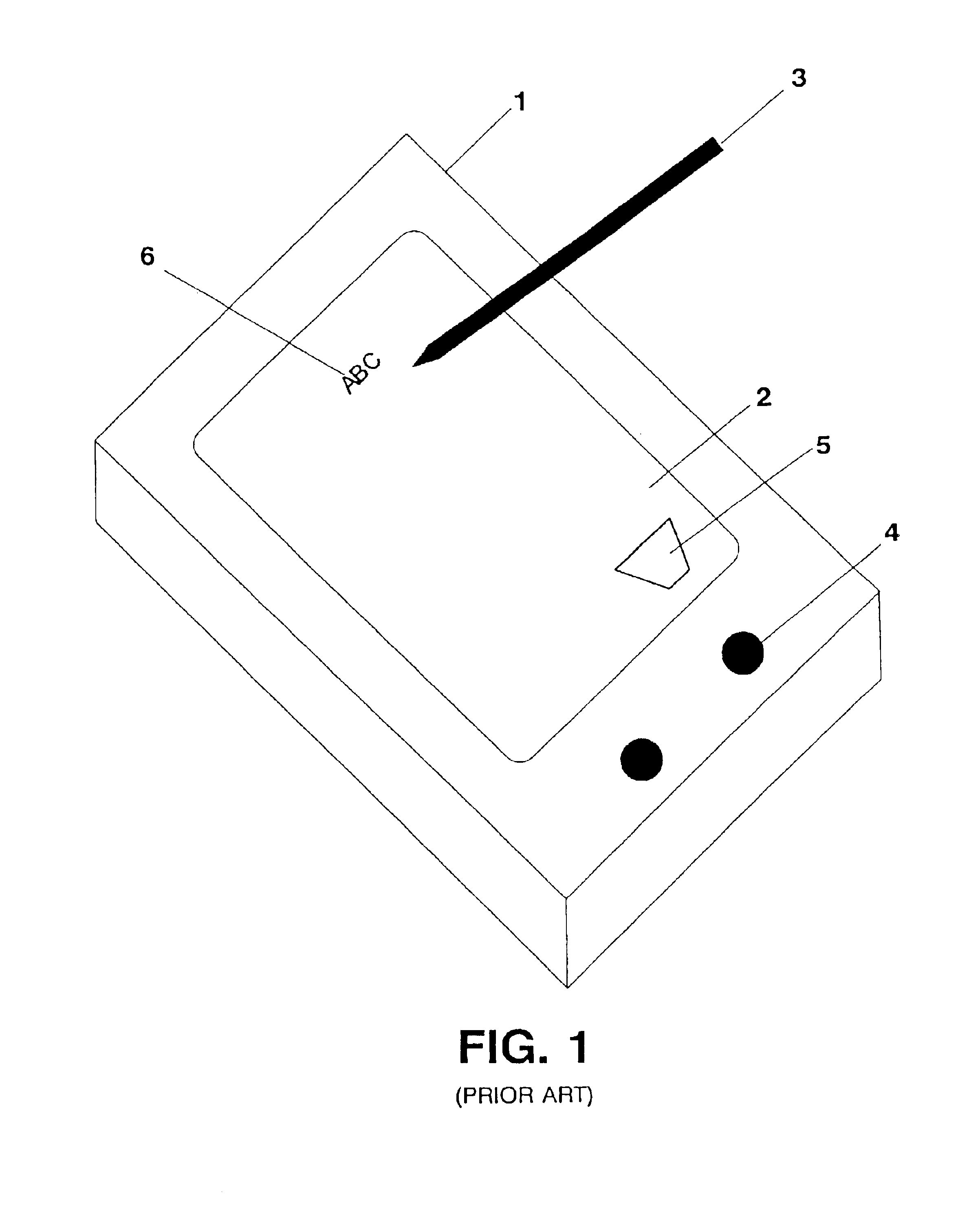
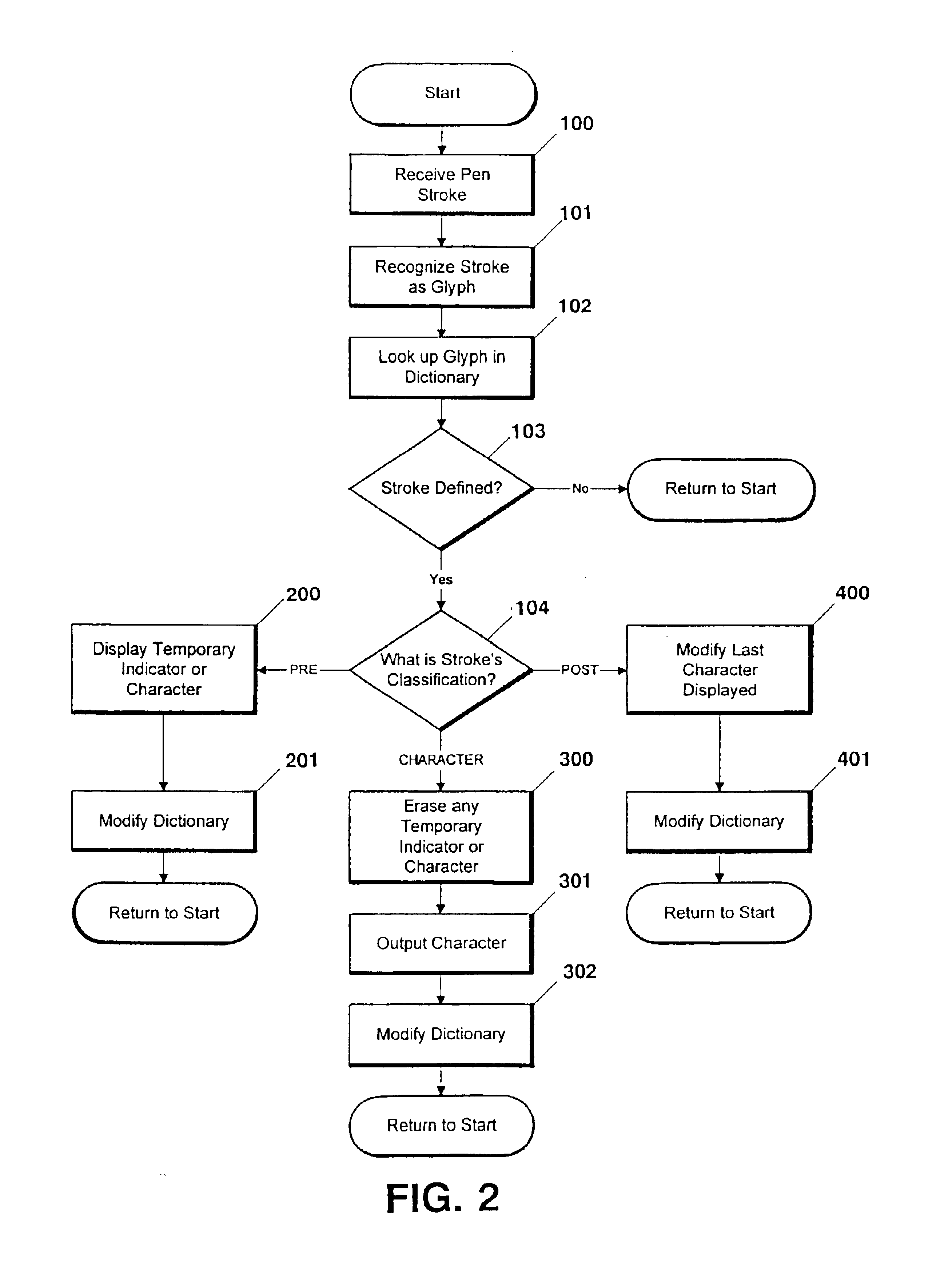
Multiple pen stroke character set and handwriting recognition system with immediate response
InactiveUS6839464B2Easy to learnDigital computer detailsCharacter recognitionPhysical medicine and rehabilitationText entry
A pen-based computer text input system capable of interpreting a special pre-defined set of single stroke glyphs. Each input stroke is identified with one of three categories: (1) pre-character modifier strokes, (2) character or symbol strokes, or (3) post-character modifier strokes. Pre-character modifier strokes precede character strokes and inform the present recognition system that a subsequently entered character stroke is to be modified by the pre-character modifier stroke in a pre-defined manner. Character strokes cause a character or symbol to be displayed on the display device the moment it is input on the writing tablet, interpreted in accordance with any pre-character modifier stroke. A post-character modifier stroke causes the recognition system to modify, in a pre-defined manner, a character or symbol which was previously entered and displayed. An important advantage of the present invention is its ability to provide immediate recognition of multiple stroke characters without using boxed input.
Owner:ACCESS
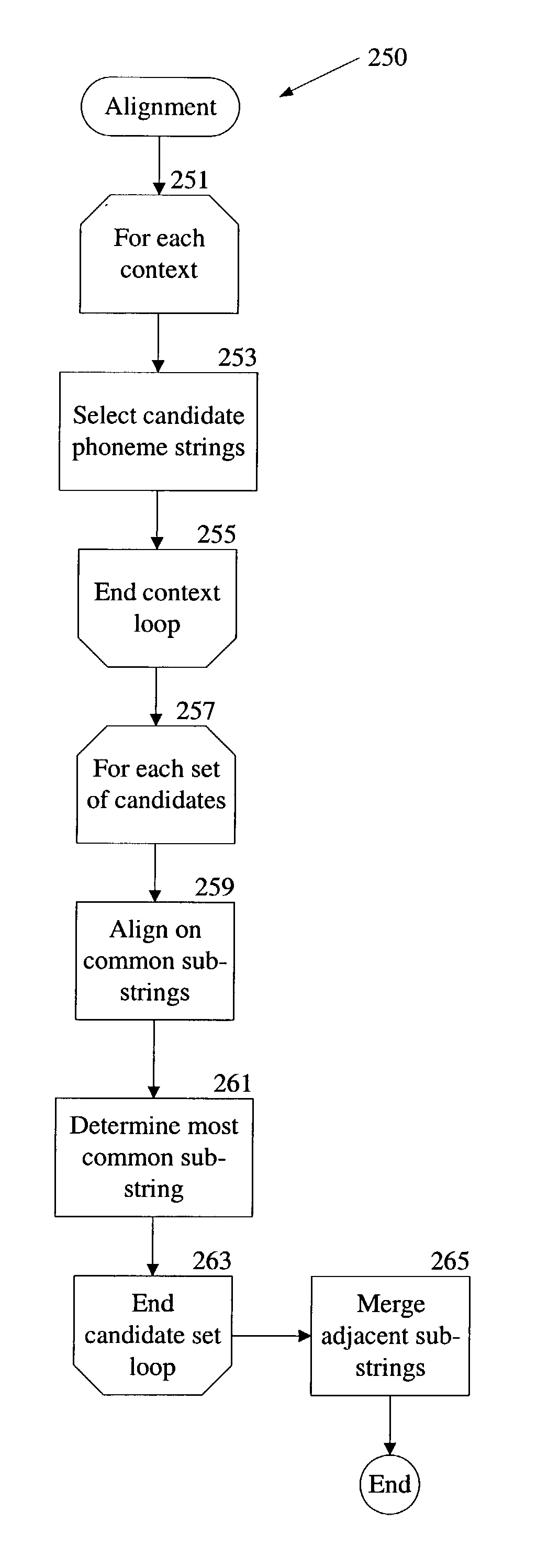
Unsupervised data-driven pronunciation modeling
Owner:APPLE INC
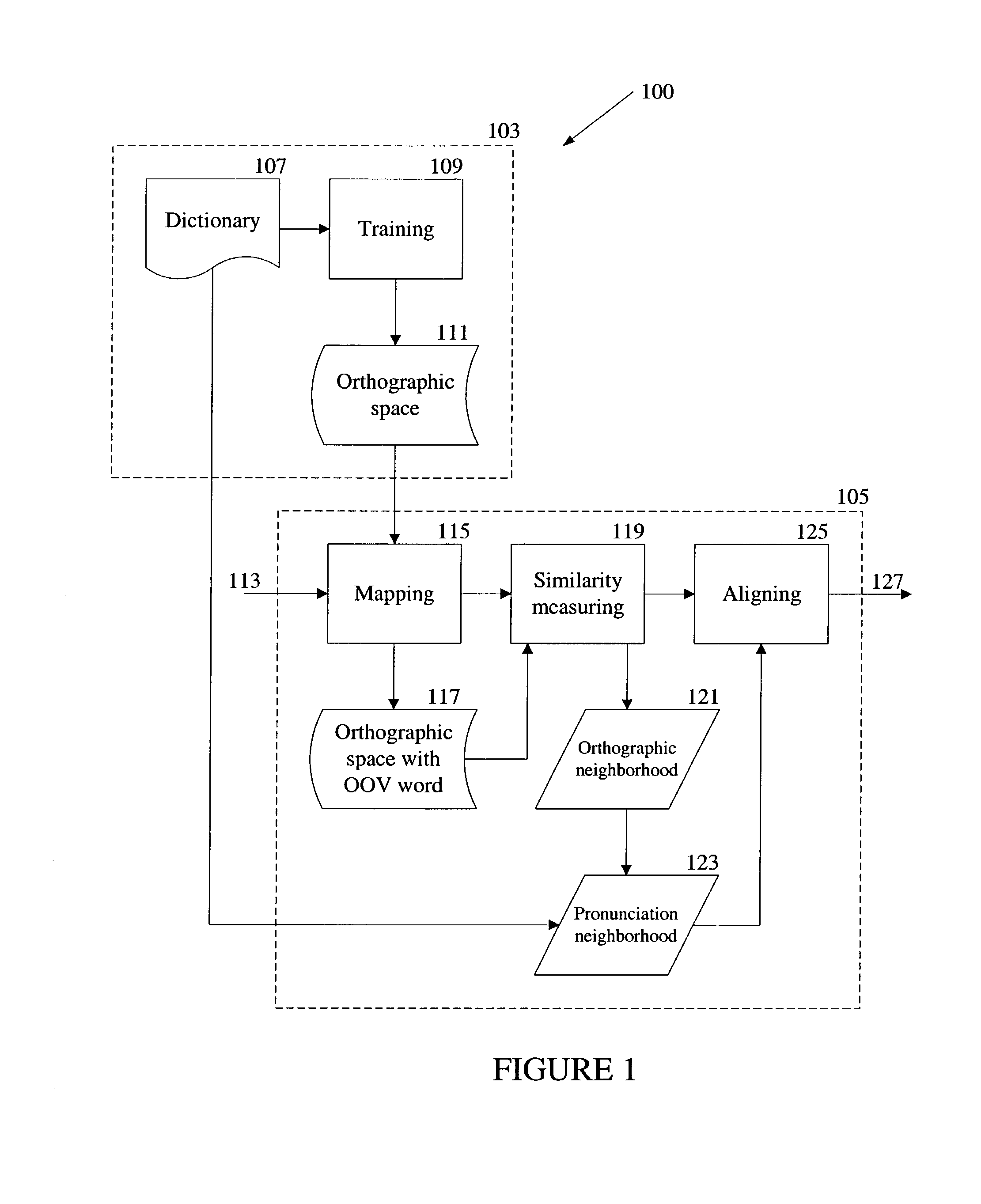
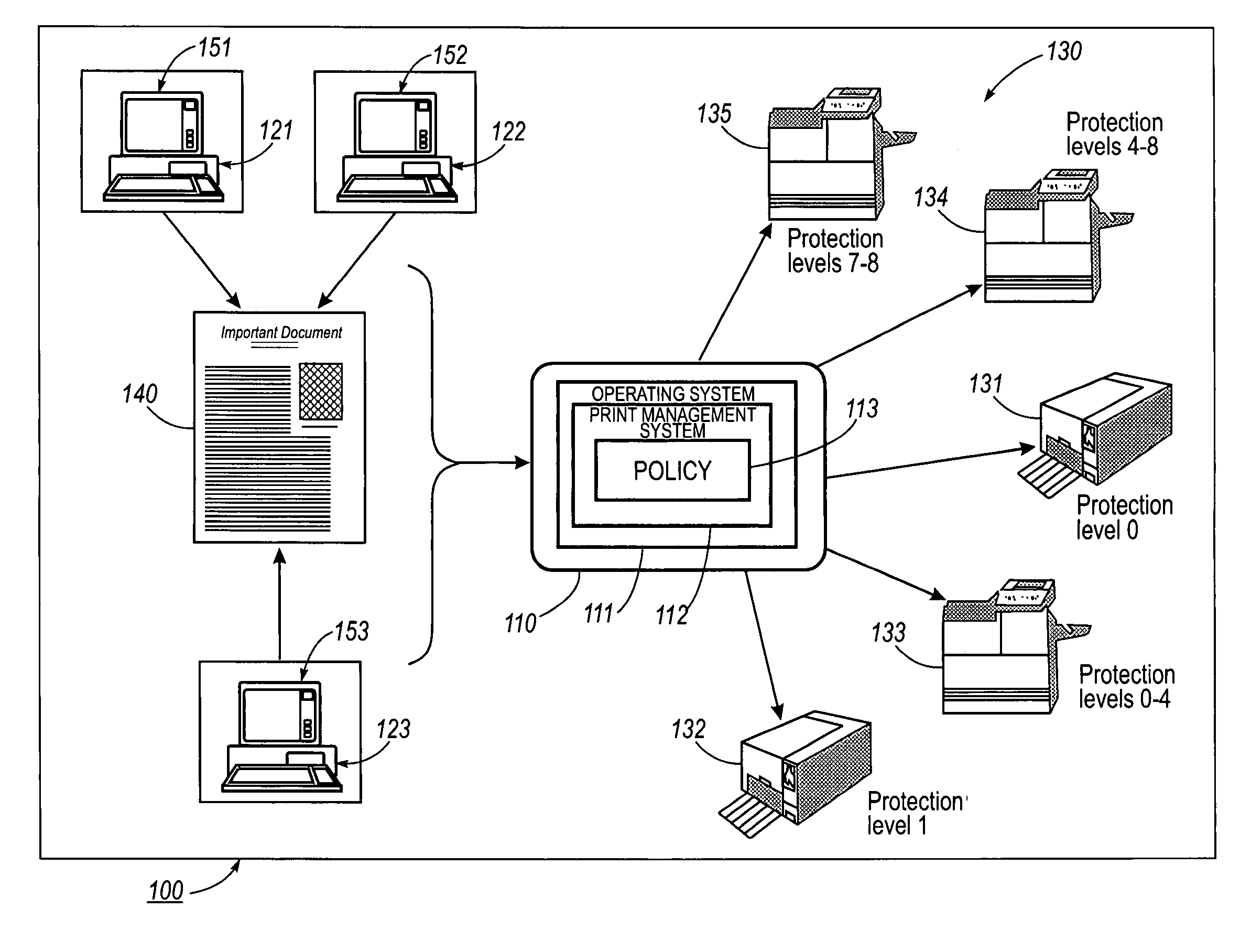
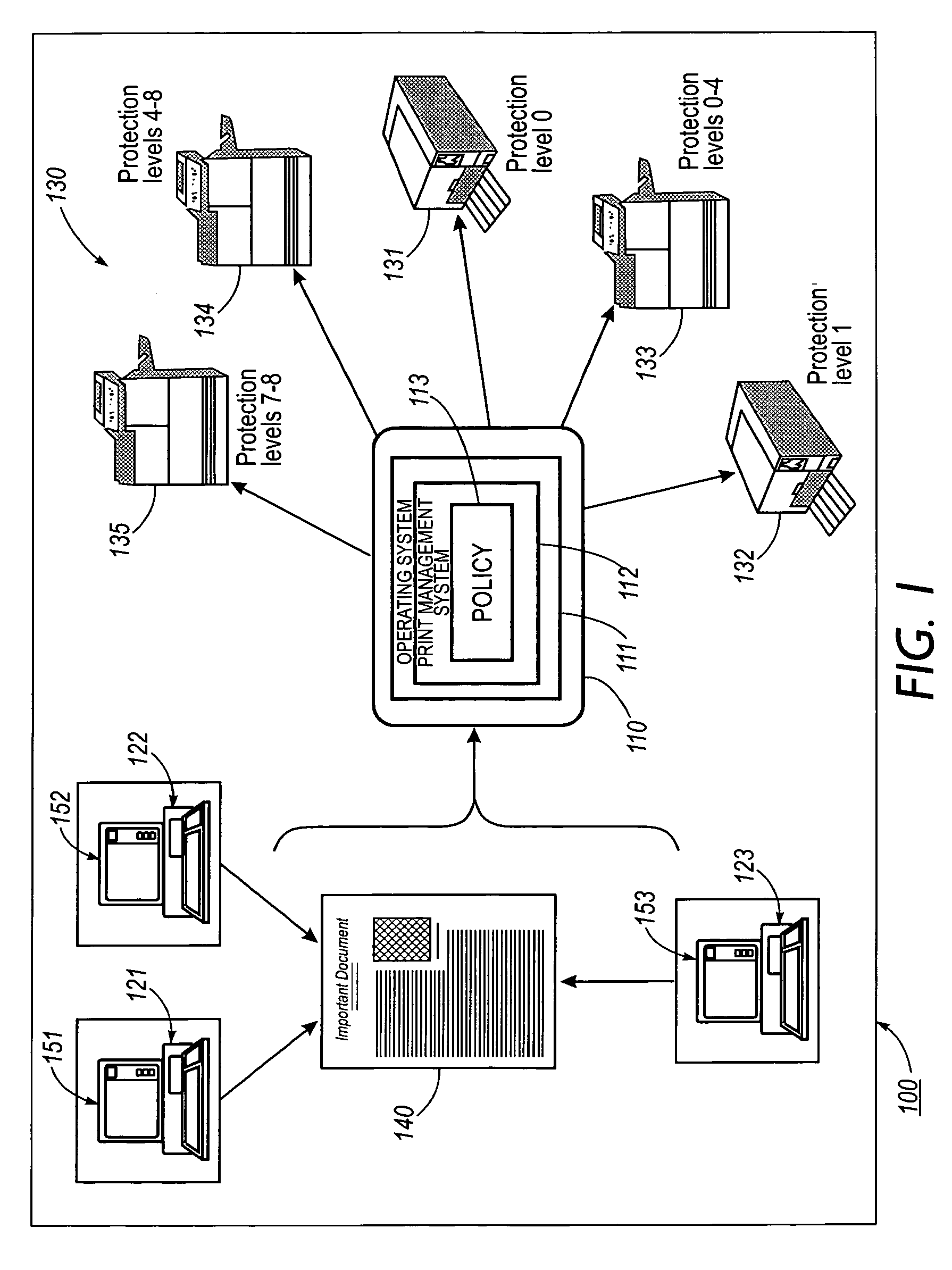
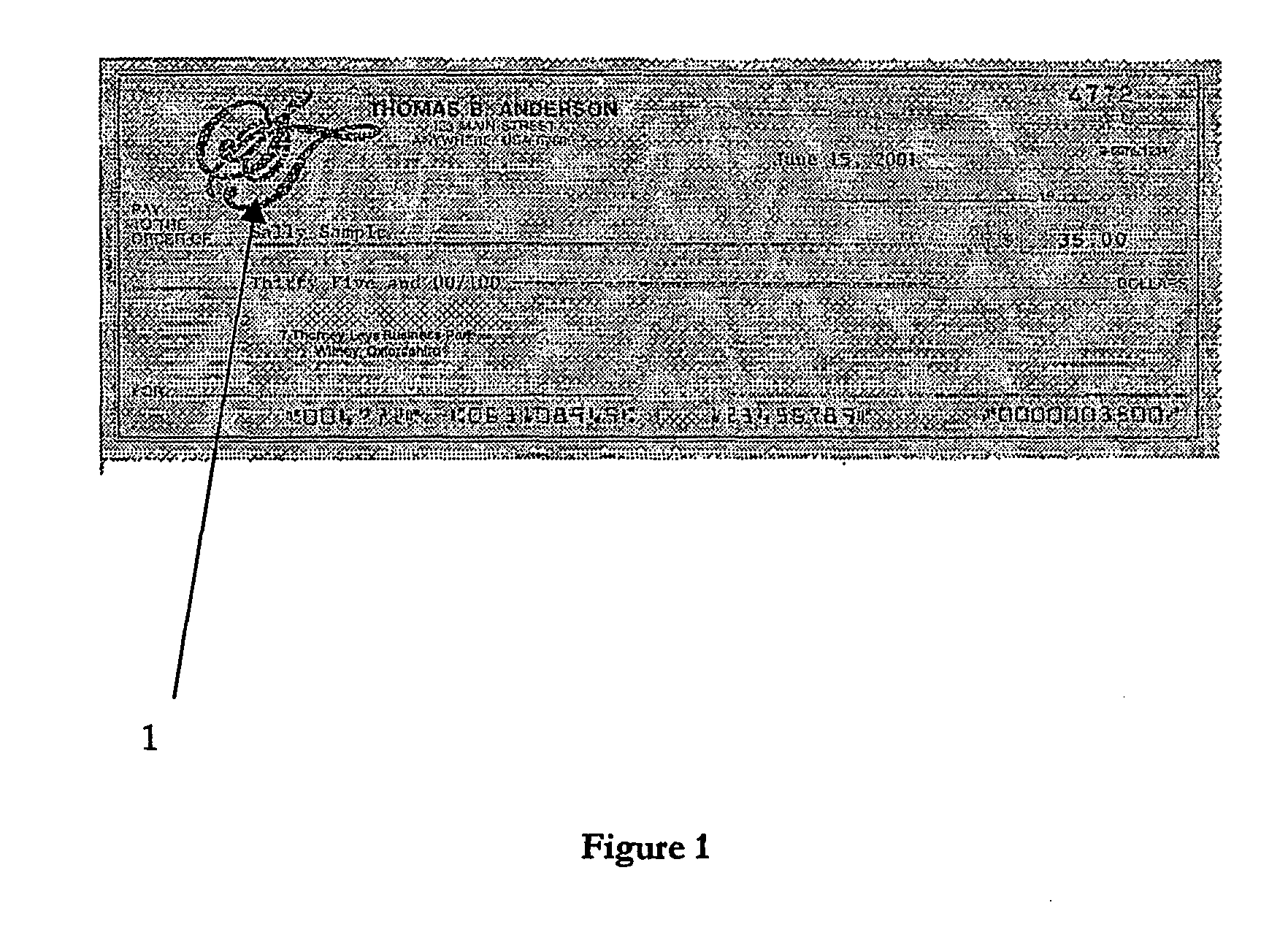
Systems and methods for forgery detection and deterrence of printed documents
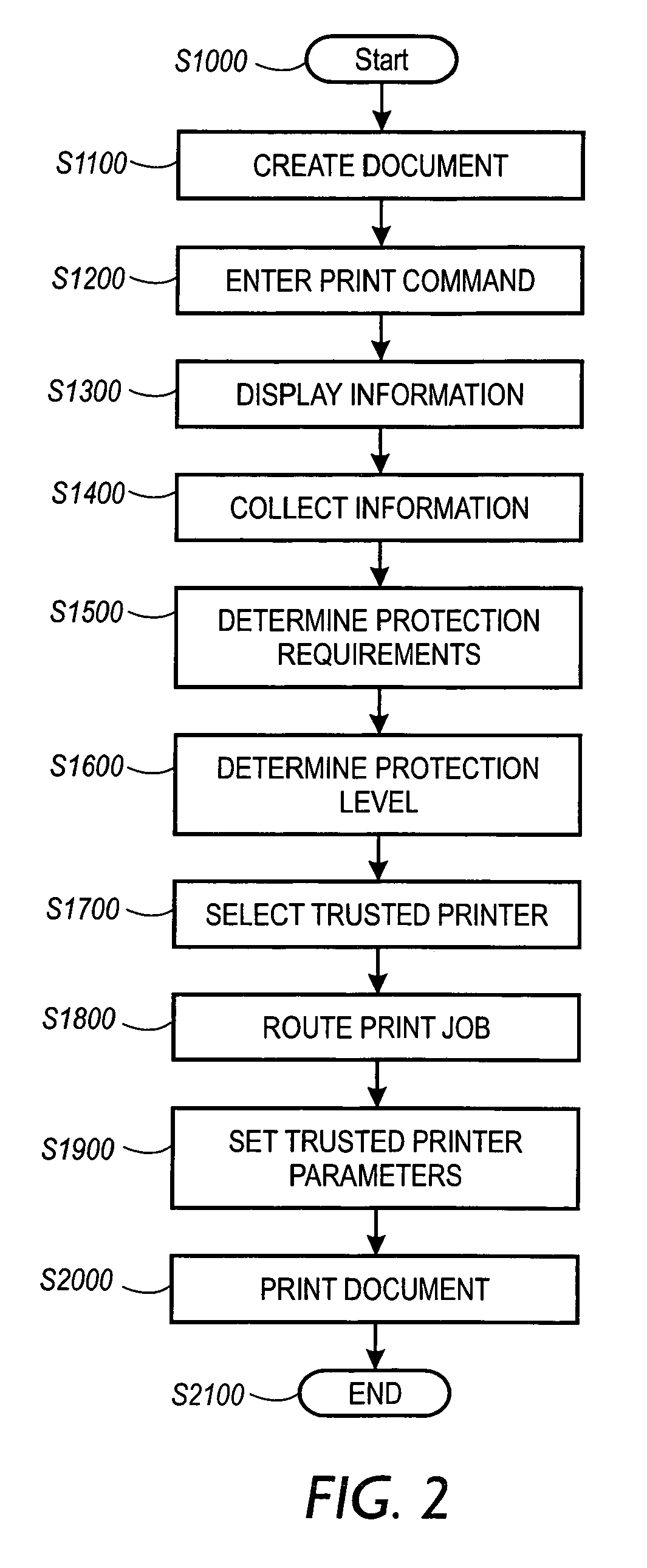
InactiveUS6970259B1Digitally marking record carriersUser identity/authority verificationDigital signatureGlyph
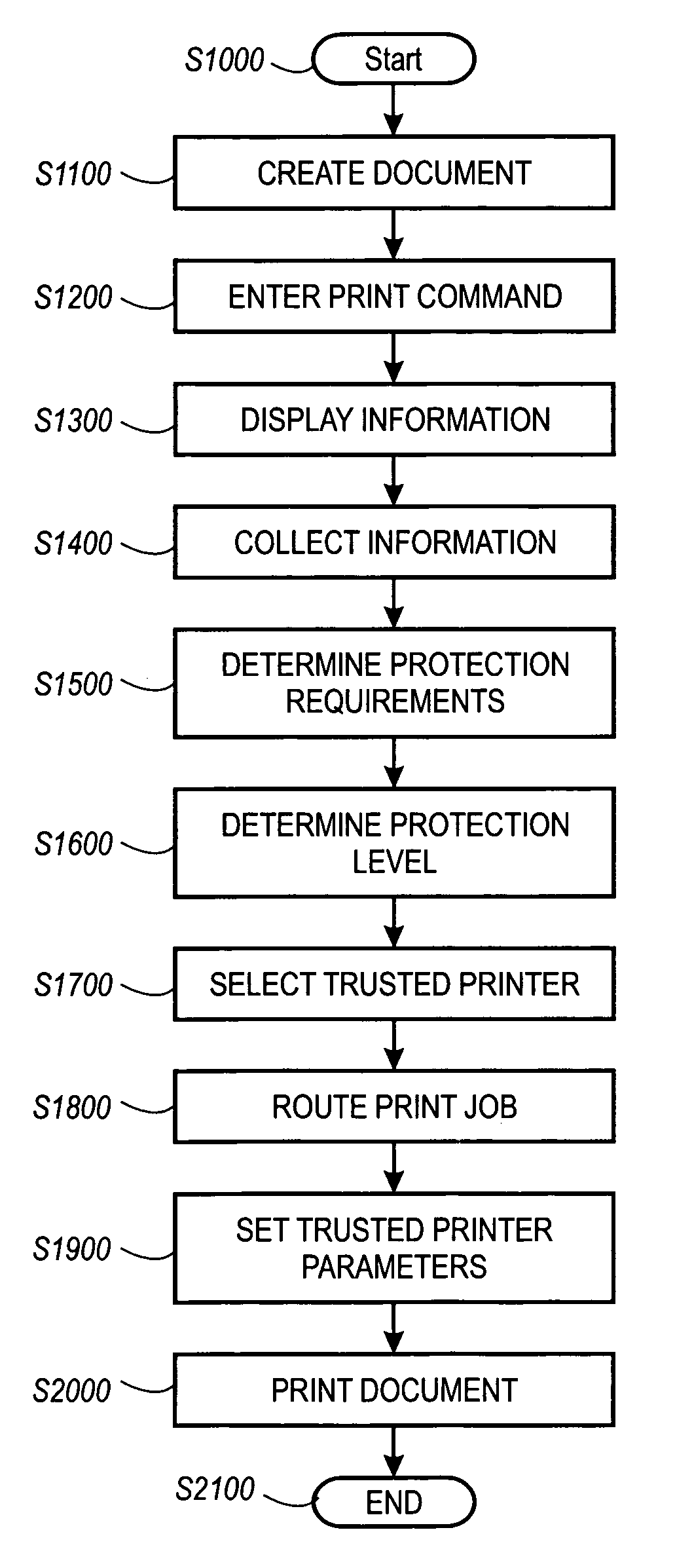
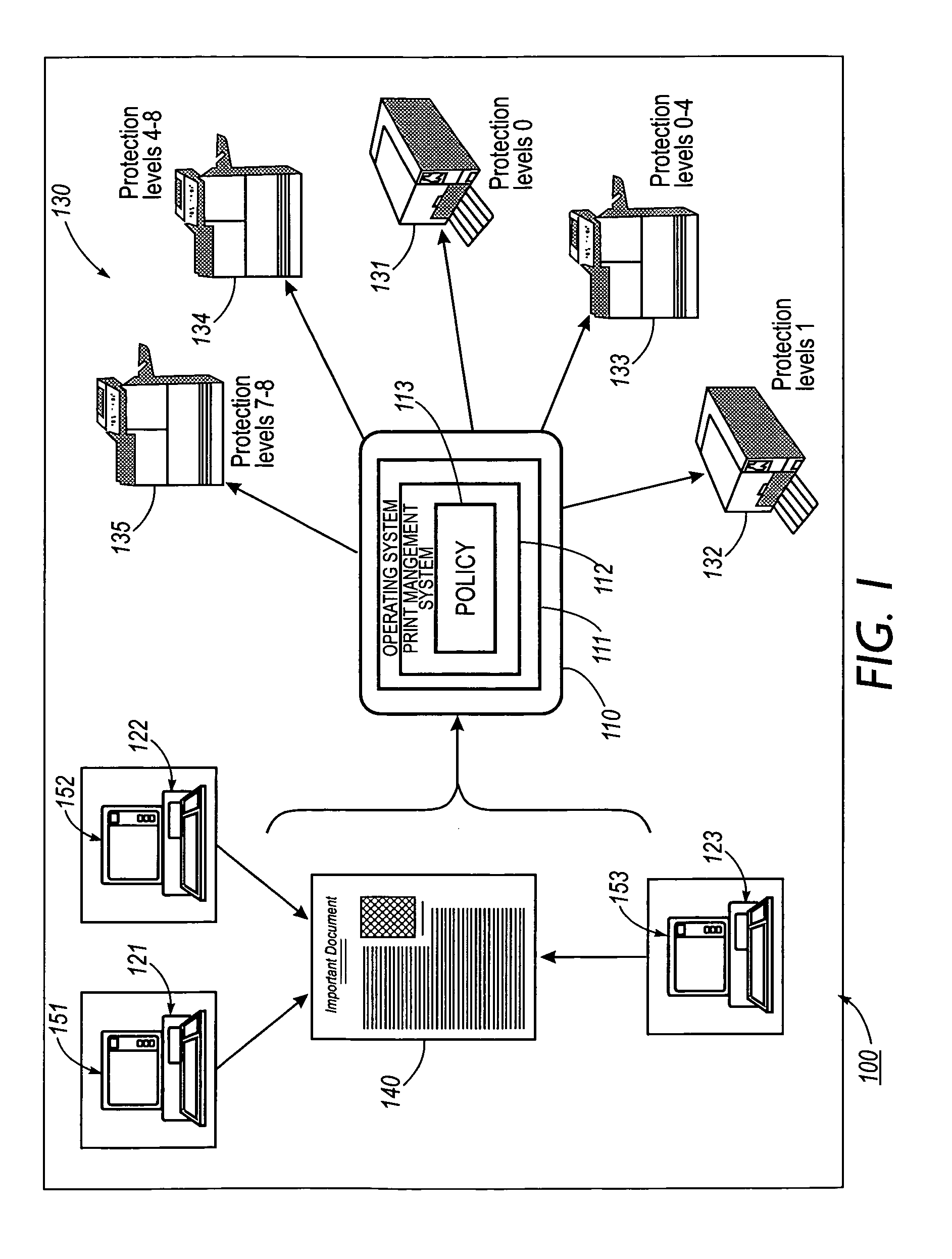
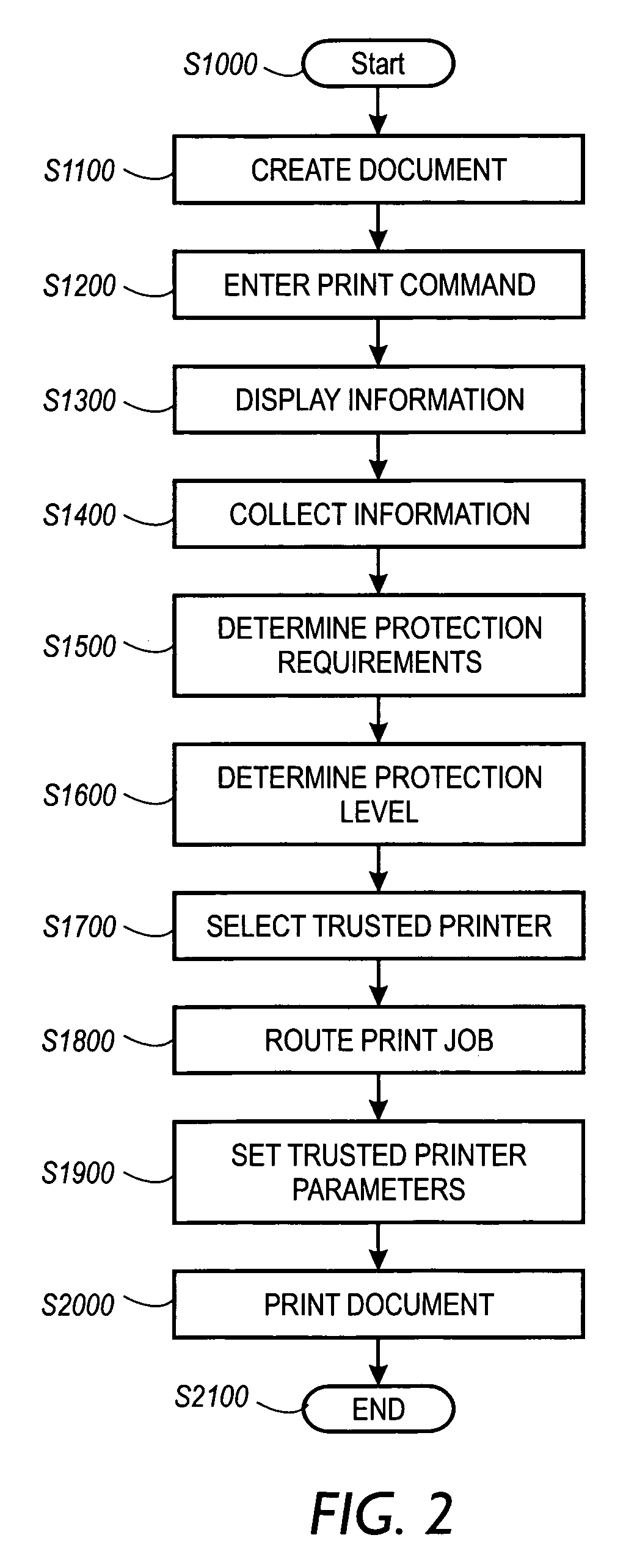
A print management system includes a policy that determines a protection level for a document to be printed. The document is printed using forgery detection and deterrence technologies, such as fragile and robust watermarks, glyphs, and digital signatures, that are appropriate to the level of protection determined by the policy. A plurality of printers are managed by a print management system. Each printer can provide a range of protection technologies. The policy determines the protection technologies for the document to be printed. The print management system routes the print job to a printer that can apply the appropriate protections and sets the appropriate parameters in the printer. Copy evidence that can establish that a document is a forgery and / or tracing information that identifies the custodian of the document and restrictions on copying of the document and use of the information in the document are included in the watermark that is printed on the document. A document can be verified as an original or established as a forgery by inspecting the copy evidence and / or tracing information in the watermark.
Owner:XEROX CORP
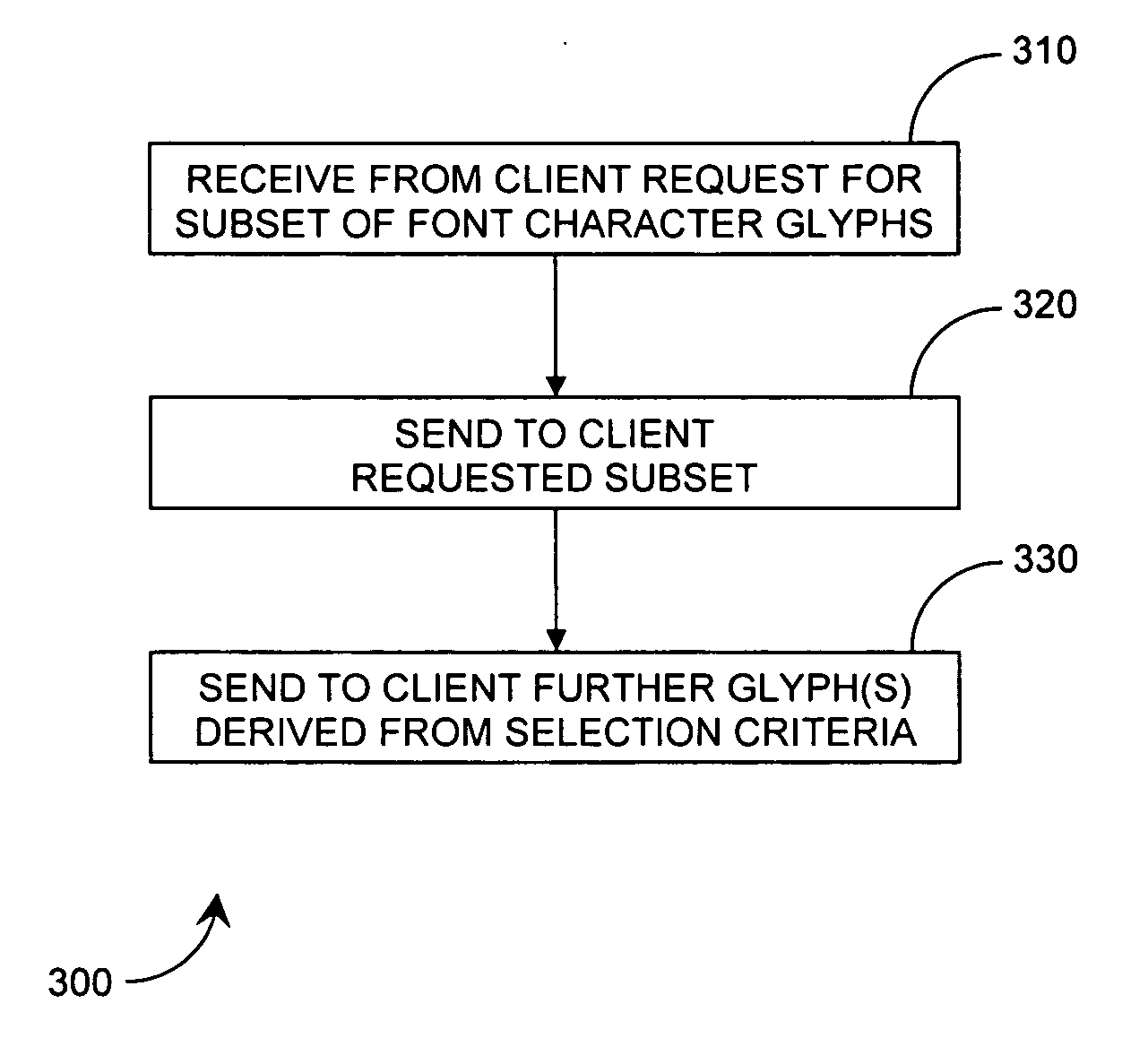
Method and arrangement for font building
A method and system for font building by providing for the downloading of a subset of glyphs at a client device from a server. The subset can include one or more particular requested glyphs. The subset is accompanied by one or more further glyphs determined by selection criteria, which can include: frequency of use of the glyphs in a particular language; frequency of use of the glyphs by at least one client device; and relationships between particular glyphs.
Owner:IBM CORP
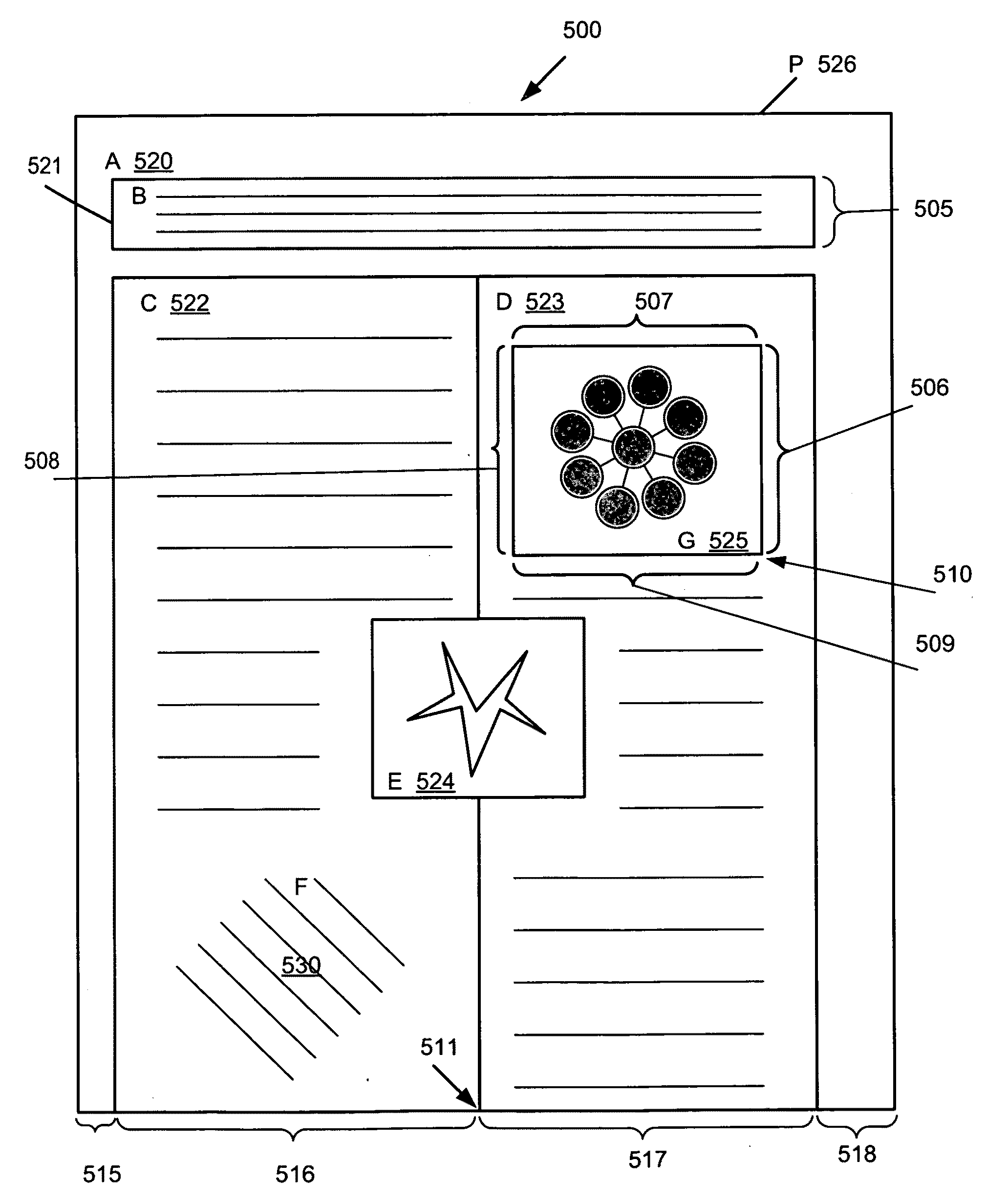
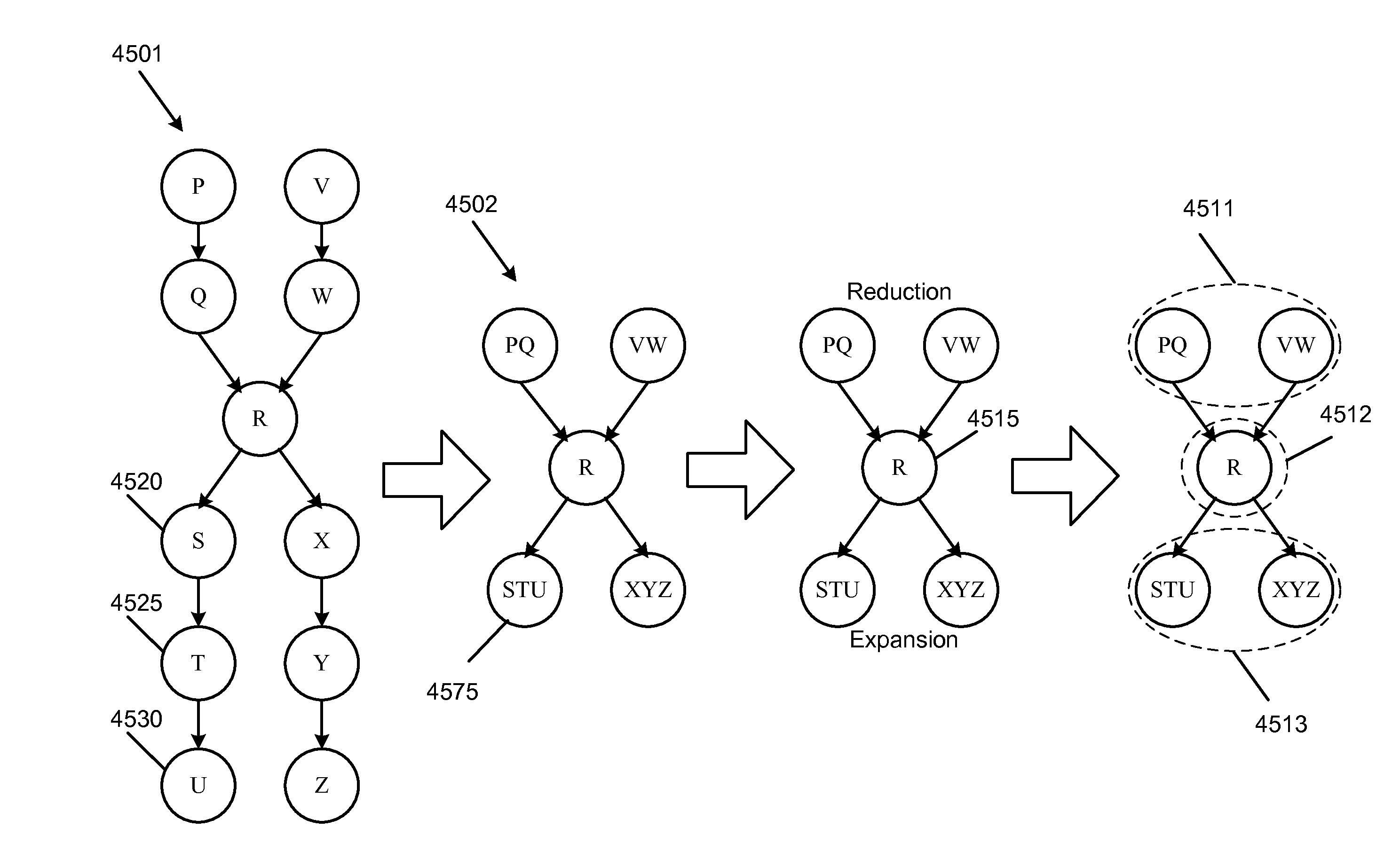
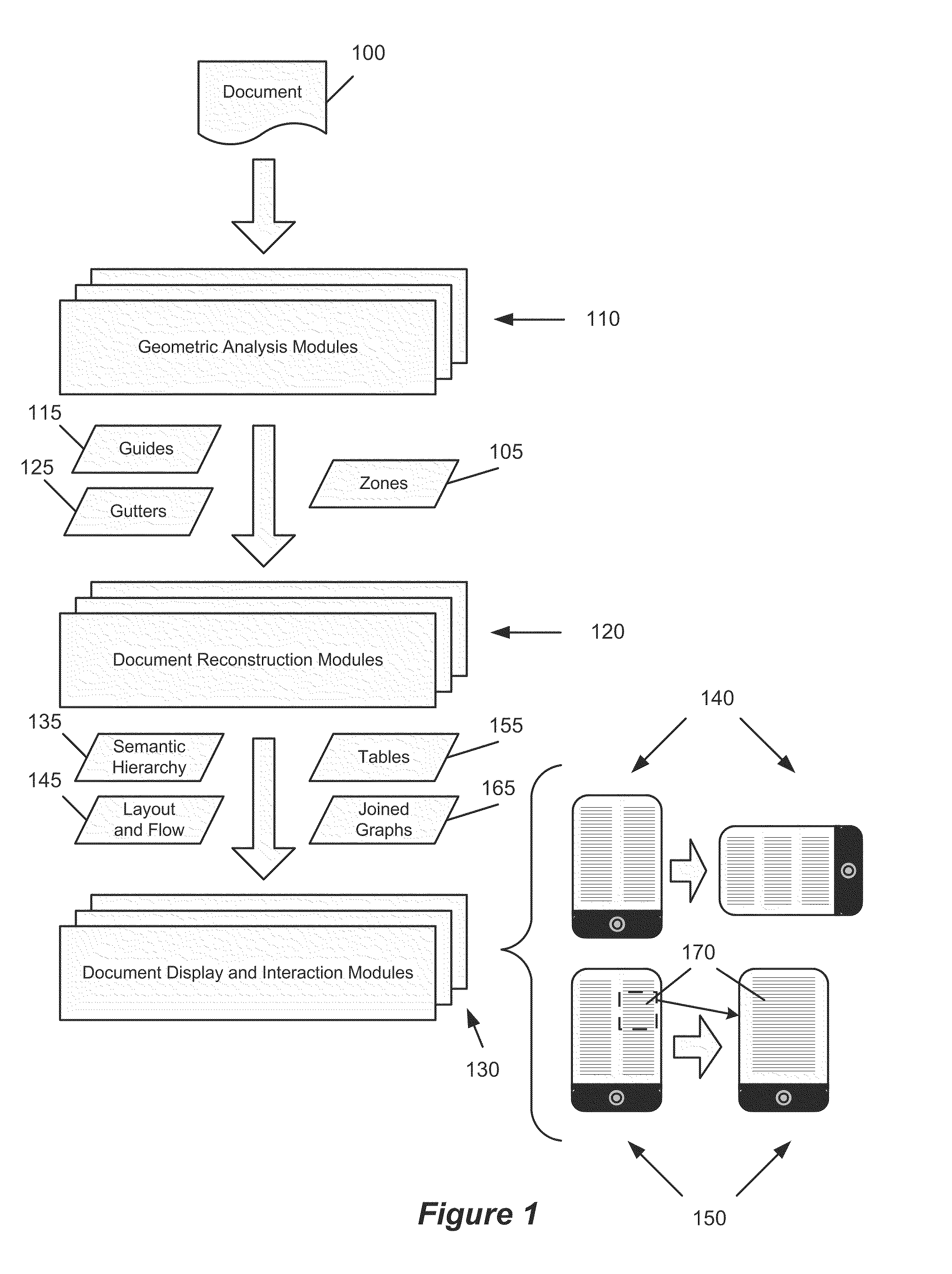
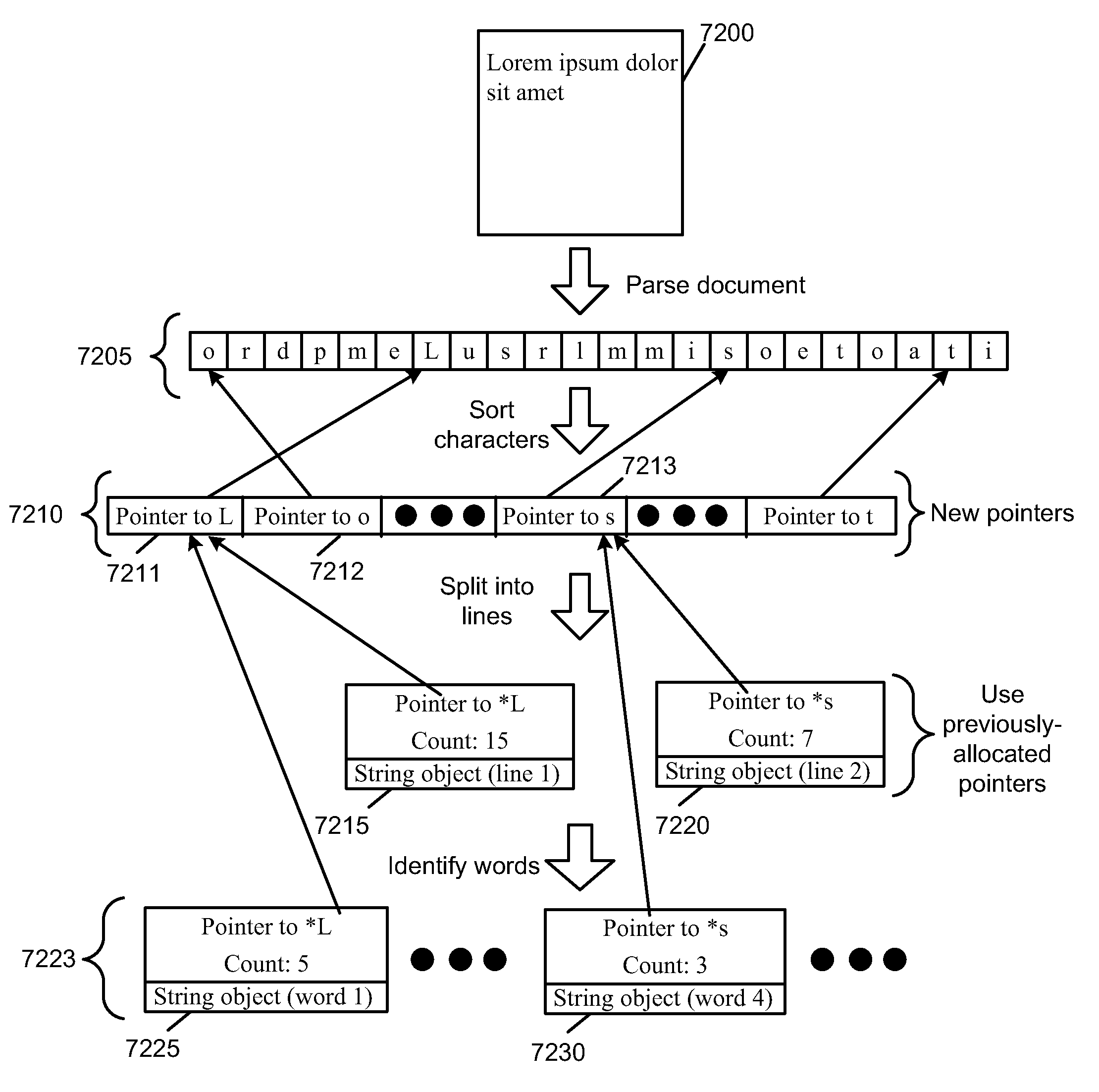
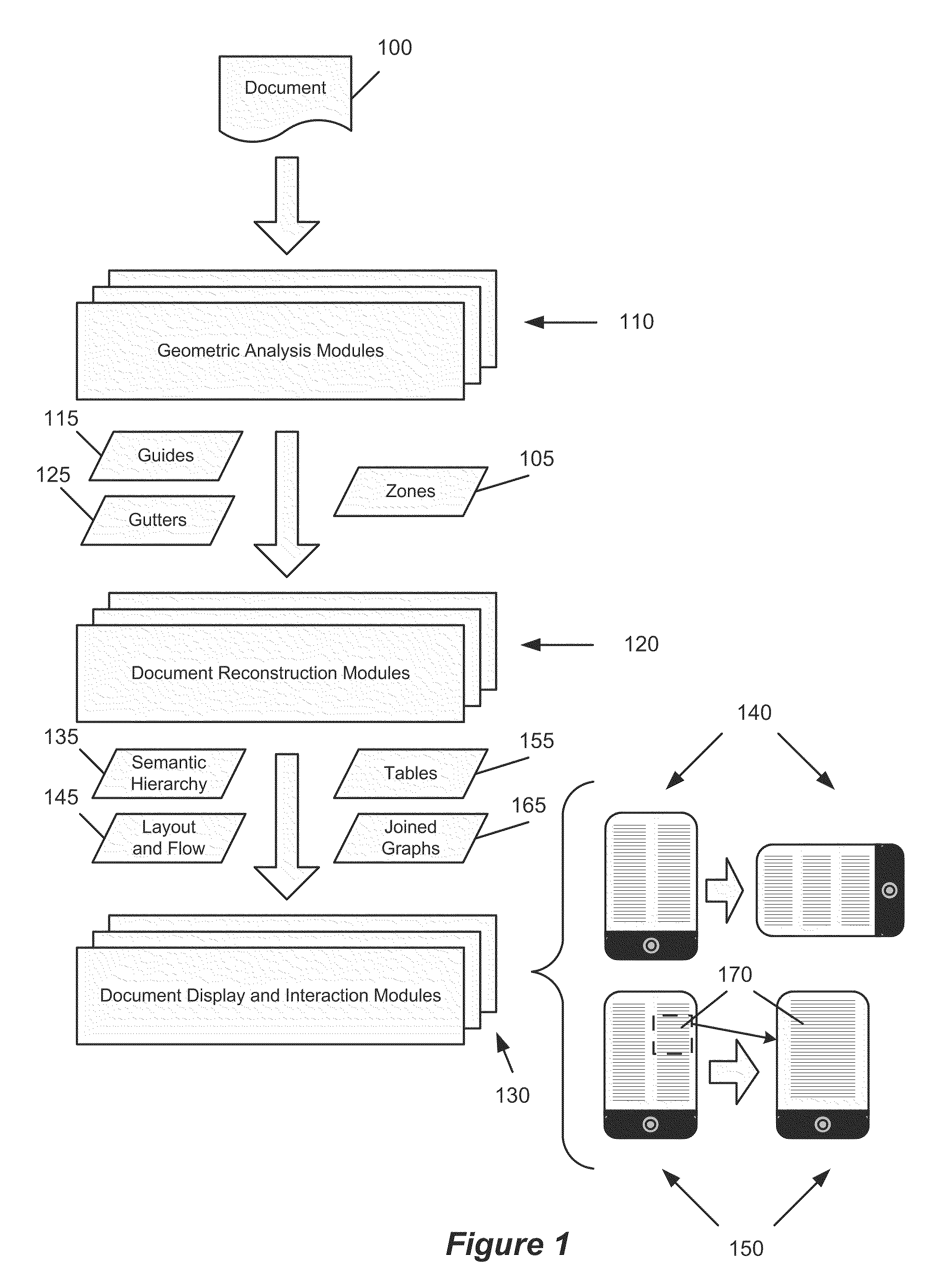
Identification of layout and content flow of an unstructured document
ActiveUS20100174985A1Improve efficiencyNatural language translationText processingGlyphPaper document
Owner:APPLE INC
Versatile keyboard input and output device
InactiveUS20110205161A1Improves core aspectImprove experienceInput/output for user-computer interactionContact mechanismsTouch SensesOutput device
A versatile keyboard input and output device is described. The keyboard device includes a housing having a plurality of buttons, with each button individually clickable, and a capacitive sensing element under each button for touch sensing. The versatile keyboard input and output device further includes a lighting element under each button to provide selective lighting for each button, and a plurality of button glyphs for the plurality of buttons respectively, wherein the button glyphs are selectively visually changeable. The keyboard input device also includes a haptic feedback mechanism included in the housing for providing haptic feedback for the plurality of buttons.
Owner:PANASONIC OF NORTH AMERICA
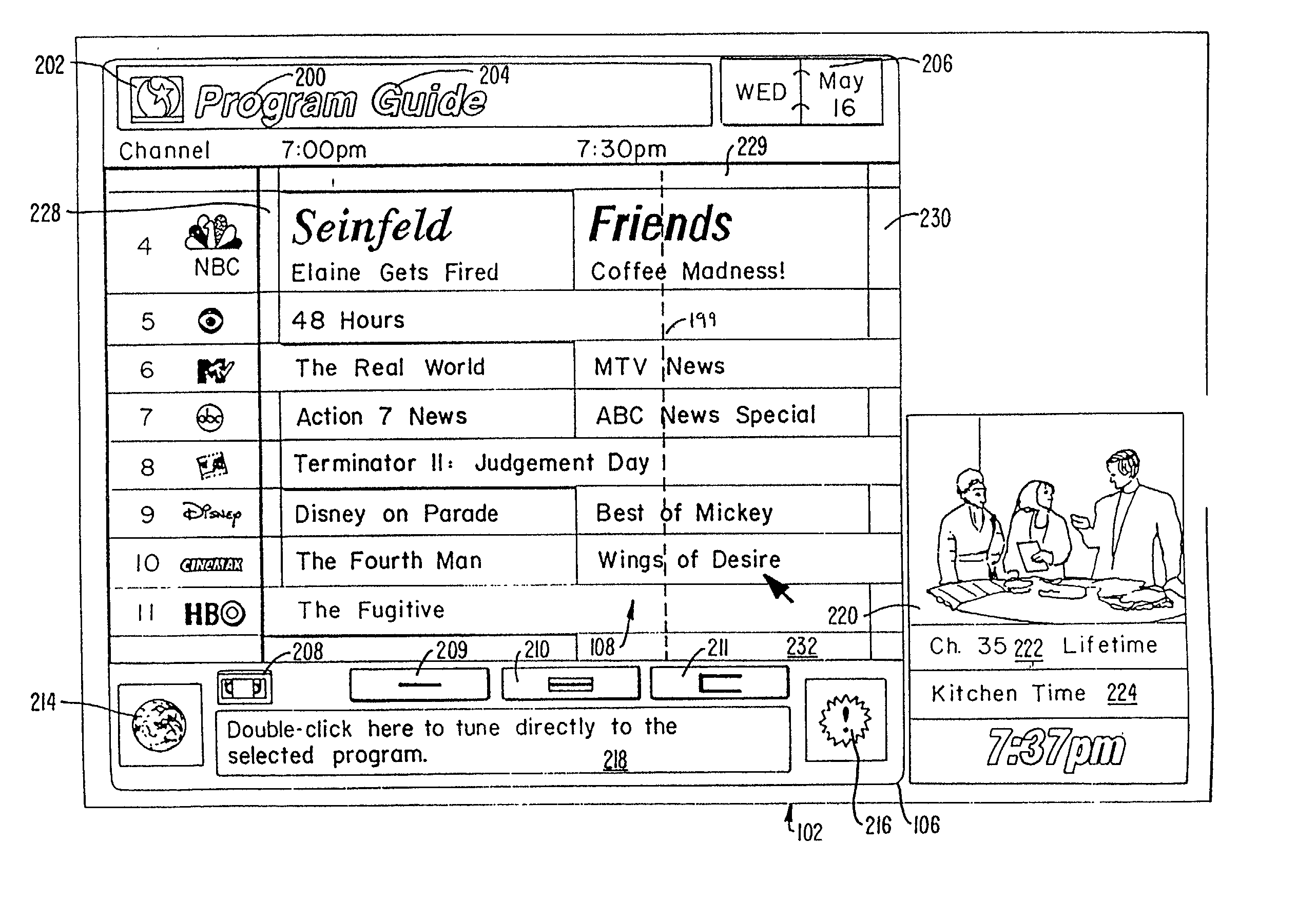
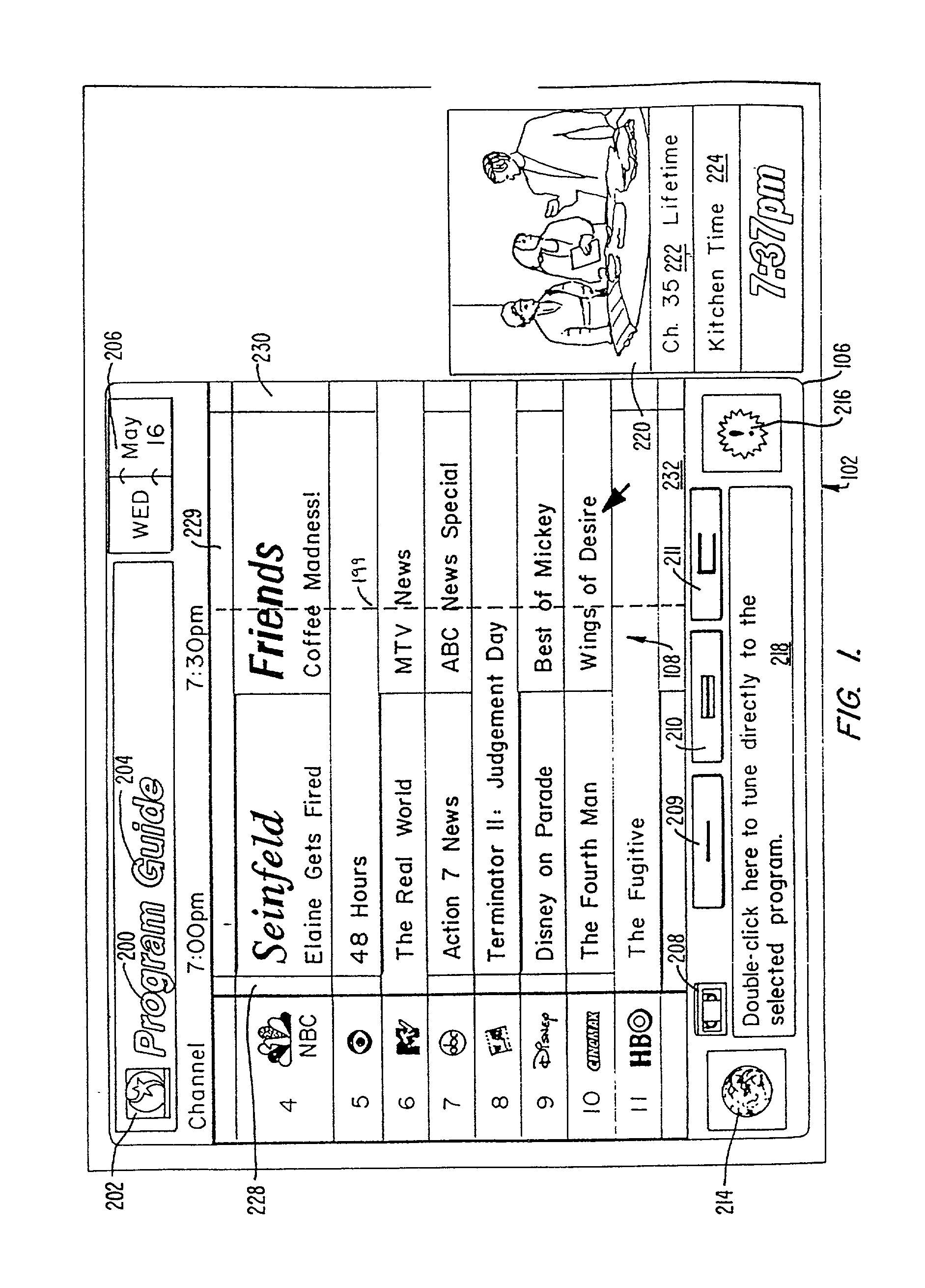
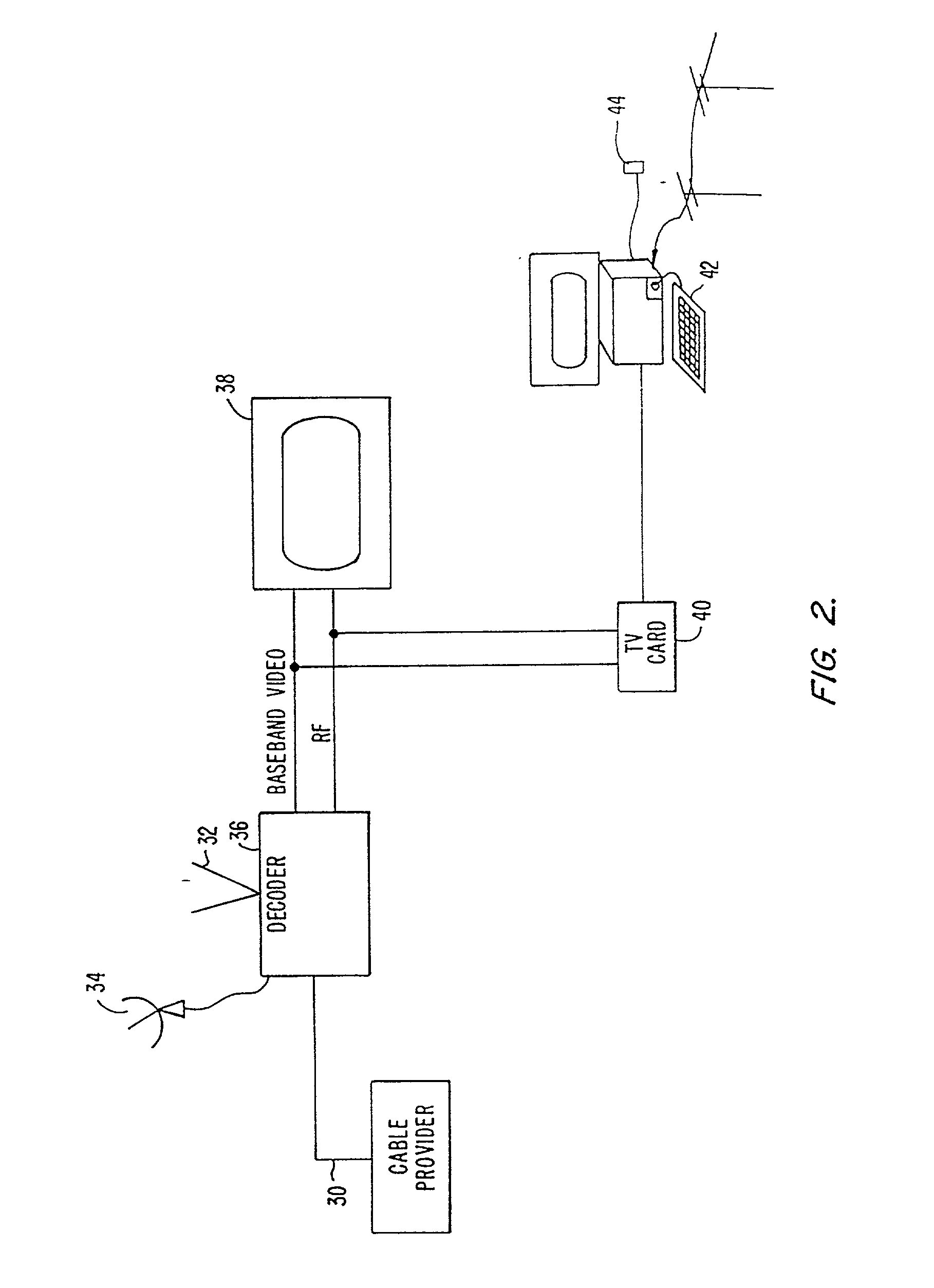
Electronic program guide with interactive areas
A television schedule system and method for displaying television schedule information on a television screen includes a program guide having a schedule information area that depicts the programs that are being presented on each channel at each time during the day. An input device allows the viewer to move a pointer over different interactive areas of the guide and the function performed when the area is activated is displayed in a contextual help window. Various control glyphs provide for recursive interaction with the guide. Additionally, a video window is interactive and provides tuning functions.
Owner:ROVI GUIDES INC
System and method for creating and sharing personalized fonts on a client/server architecture
InactiveUS20120001922A1Flexible representationCreate quickly2D-image generationNatural language data processingPersonalizationGlyph
The present invention concerns a method allowing an author to create a bitmap font and distributing it to at least an user's device connected to a server (2), comprising the steps of:drawing on an author's device and / or importing (5) in the author's device an image comprising at least one glyph;segmentation (6) of the image by the said author's device, in order to isolate the glyph or the different glyphs;uploading the bitmap file resulting of this segmentation (6) to the server (2);displaying (34) a text on said user's device, said text being rendered with a font depending on said bitmap file.The present invention relates also to a system and a computer program product for creating and sharing personalized font on a client-server architecture.
Owner:FONTSELF
System and apparatus for dynamically generating audible notices from an information network
InactiveUSRE42904E1Reduce the amount of data transferredReduce data transferMultiple digital computer combinationsAutomatic exchangesProgramming languageProgram instruction
An apparatus and method for converting information from a text format to an audio format using distributed processing. A first set of computer readable program instructions receive information from a data source, convert the information from the text format to an intermediate format, and transmit the information in the intermediate format to a second data processor. A second set of program instructions, executable on the second data processor, are also included to convert the information from the intermediate format to the audio format. The first set of program instructions are executed on a remote, or server side, data processor, while the second set of program instructions are executed on a client side data processor. The first set of program instructions expand the information in the text format into phonemes using a grapheme to phoneme dictionary. The second set of program instructions convert the phonemes to audio output signals.
Owner:ZARBANA DIGITAL FUND
System and method for video access from notes or summaries
InactiveUS7647555B1Increased ease of playbackImprove overall utilizationTelevision system detailsUsing non-detectable carrier informationWeb browserComputer graphics (images)
Recorded video is accessed from printed notes or summaries derived from the video. Summaries may be created automatically by analyzing the recorded video, and annotations are made by a user on a device for note-taking with digital ink and video. The notes and / or summaries are printed along with data glyphs that provide time based indexes or offsets into the recorded video. The indexes or offsets are retrieved by scanning the glyph on the printout. The glyph information can be embedded in the printouts in many ways. One method is to associate block glyphs with annotations or images on the printed pages. Another method is to provide an address carpet in an annotated timeline. Yet another method is to provide a two-dimensional address carpet with X-Y position mapped to time which can be used to provide selected access to the video. The accessed video may be played back on the note-taking device on a pen computer, or on a summary interface on a Web browser-type device.
Owner:FUJIFILM BUSINESS INNOVATION CORP +1
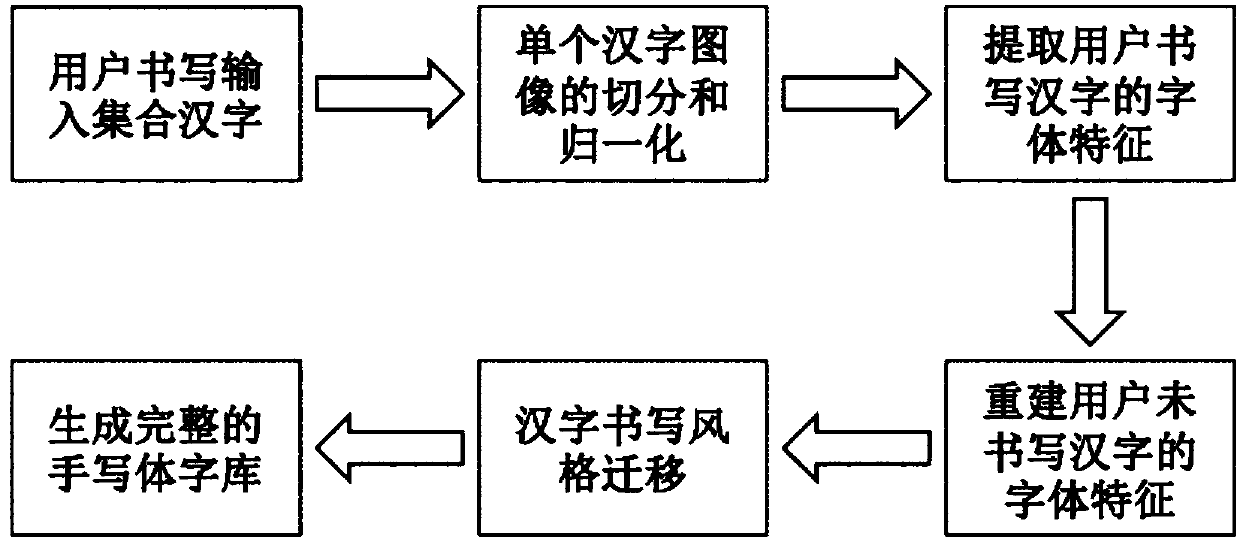
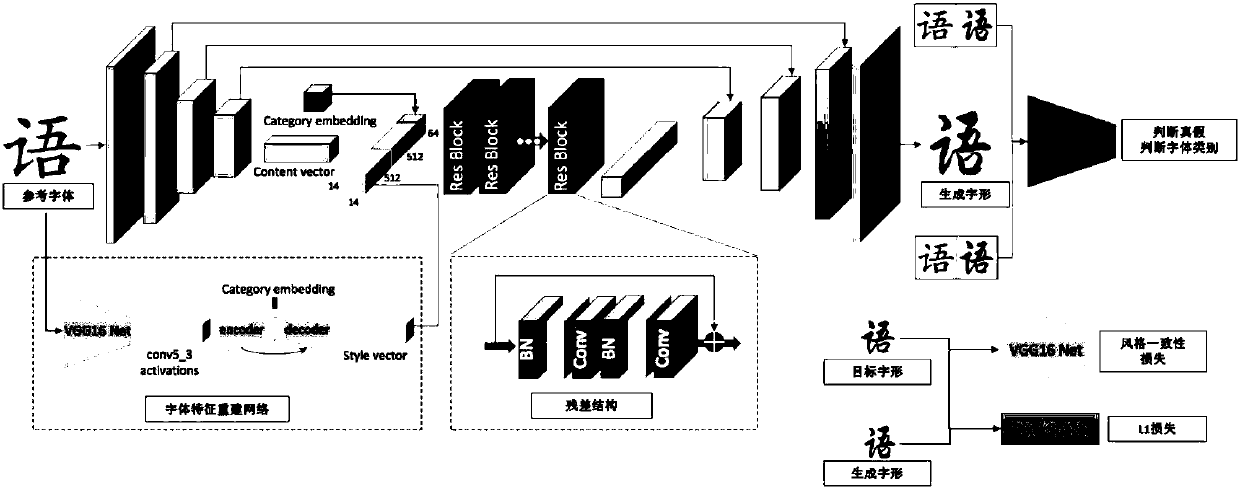
Automatic generation method for handwritten Chinese font library based on deep neutral network
ActiveCN107644006AImprove production efficiencyMeet needsCharacter and pattern recognitionNeural architecturesHandwritingPattern recognition
The invention discloses an automatic generation method for a handwritten Chinese font library based on a deep neutral network. The method is characterized in that font characteristics are reconstructed through a small number of handwritten Chinese characters; a font style migration network is established; and font style characteristics of font forms not handwritten by a user are estimated throughthe font style migration network, font form contents of a reference font are combined with a handwriting style of the user to achieve migration to a target handwriting style, and target font form pictures are generated, so that the complete handwritten Chinese font library is obtained. The method provided by the invention has the advantages that the method is an end-to-end generation method, and high-quality Chinese font forms are generated without extraction of strokes or components of Chinese characters or manual intervention, so that the handwritten font library creation efficiency is greatly improved, the generation of a personalized font library becomes simple and convenient, the requirement of ordinary people for the personalized handwritten font library can be met, and the development progress of the personalized font library can be accelerated.
Owner:PEKING UNIV
Character-level font linking
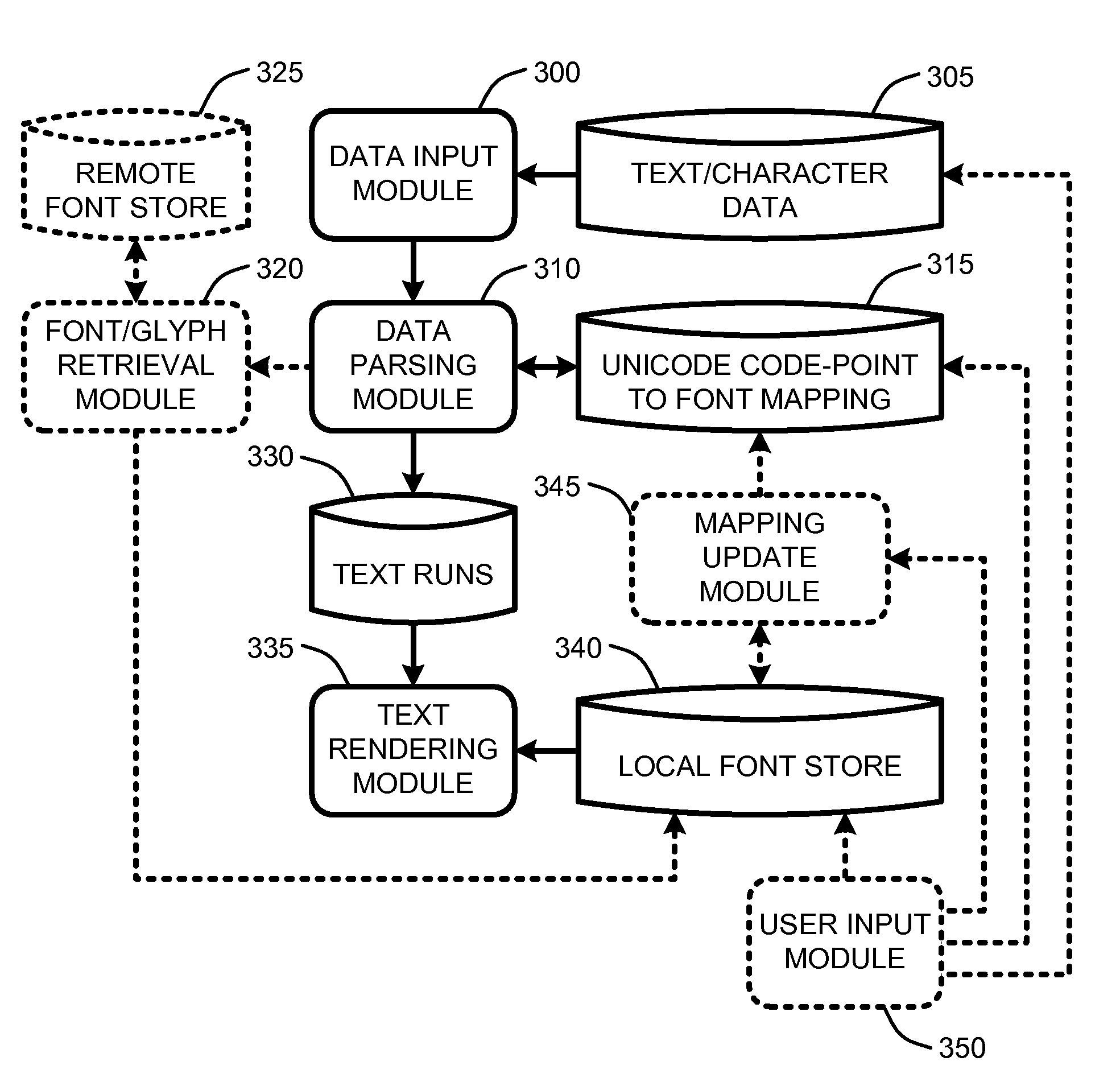
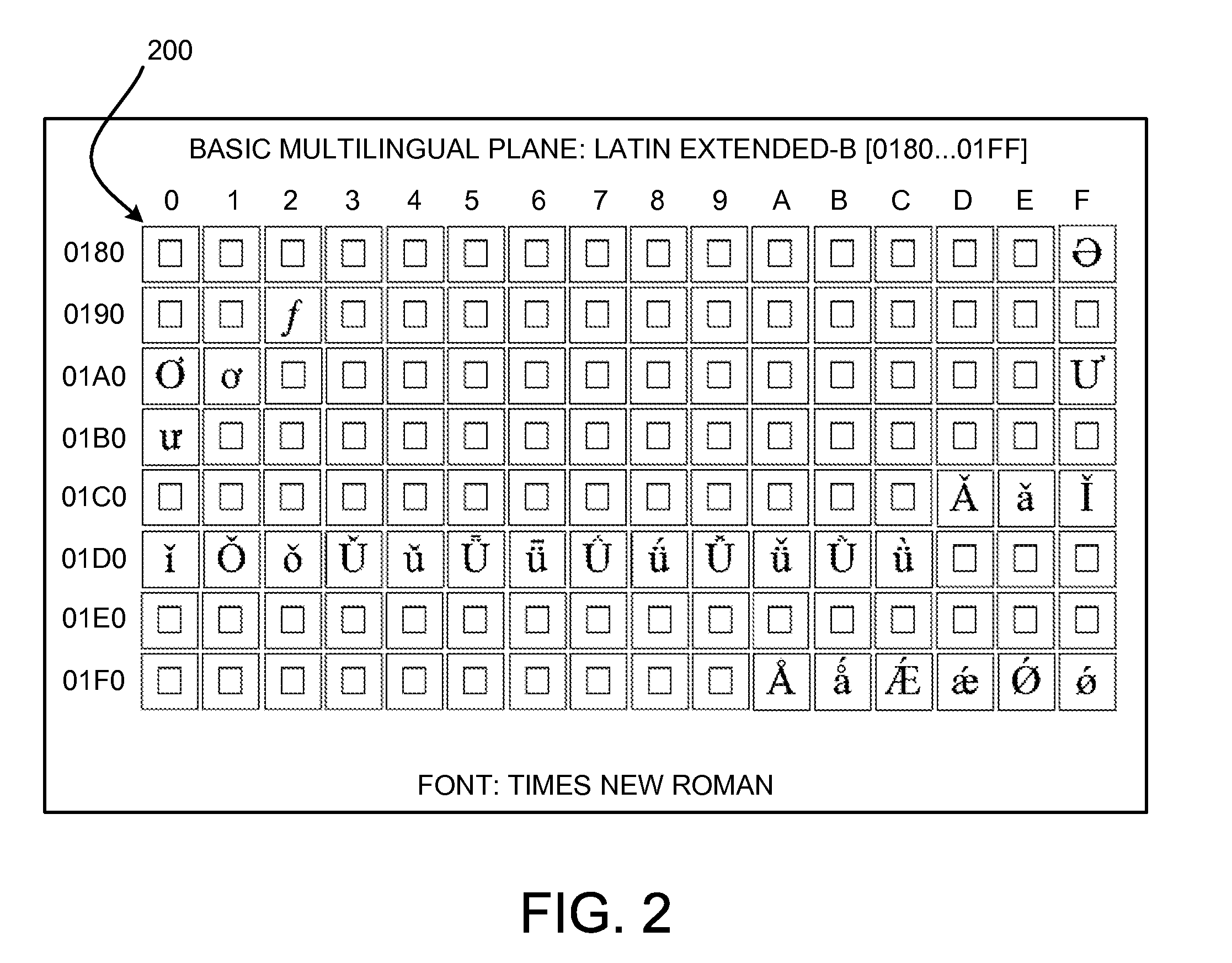
InactiveUS20080079730A12D-image generationNatural language data processingCode pointComputer graphics (images)
A “Character-Level Font Linker” provides character-level linking of fonts via Unicode code-point to font mapping. A lookup table is used to identify glyph-level support for runs of particular characters on a Unicode code-point basis for relative to a set of available fonts. This lookup table enables automatic selection of one or more specific fonts for rendering one or more runs of characters comprising a text string. The lookup table is constructed offline by automatically evaluating glyphs comprising a set of common or default fonts. The table is then used for automatically selecting fonts for rendering text strings. Alternately, the lookup table is generated (or updated) locally to include some or all locally installed fonts. Finally, in another embodiment, if no supporting font is identified in the table for a particular character, the system automatically downloads the necessary glyph from one or more remote servers.
Owner:MICROSOFT TECH LICENSING LLC
Method and system for dynamic font subsetting
InactiveUS7155672B1Limited resourceNatural language data processingSpecial data processing applicationsLimited resourcesGlyph
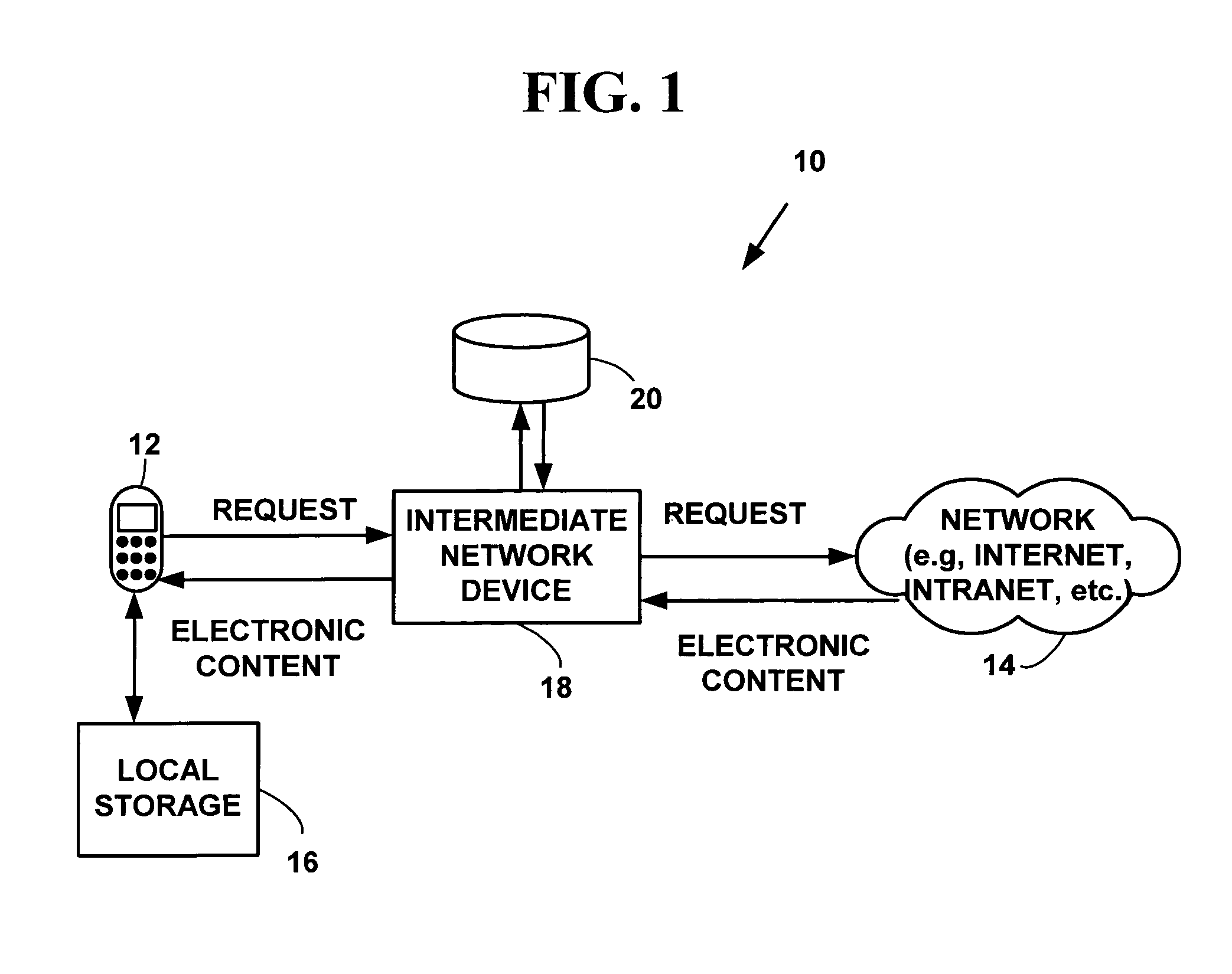
Methods and system for dynamic font subsetting. One or more directives are inserted into electronic content to identify one or more glyph sub-sets needed to display the multiple characters in one or more desired languages for electronic content. A directive identifies a glyph sub-set including set of glyphs identified in the electronic content and an encoding scheme used to encode the set of glyphs. The glyph sub-set identifies only those glyphs needed to display the electronic content. When electronic content with the one or more directives is processed the one or more directives are identified. If the electronic device does not have the glyph sub-sets needed to display the electronic content, requests are sent to an intermediate network device to obtain glyph sub-sets. These method and system may allow an electronic device with limited resources, such as a wireless telephone, personal digital assistant, network appliance, set-top box, etc., to display electronic content from a computer network such as the Internet or an intranet, with virtually any font, even if the fonts from the electronic content do not exist on the electronic device. Electronic content written in languages such as Chinese, Japanese, Korean, Vietnamese, etc. can be displayed on an electronic device with limited resources using a small number of glyphs from the multiple thousands of possible glyphs that represent characters in such languages.
Owner:OPEN TV INC
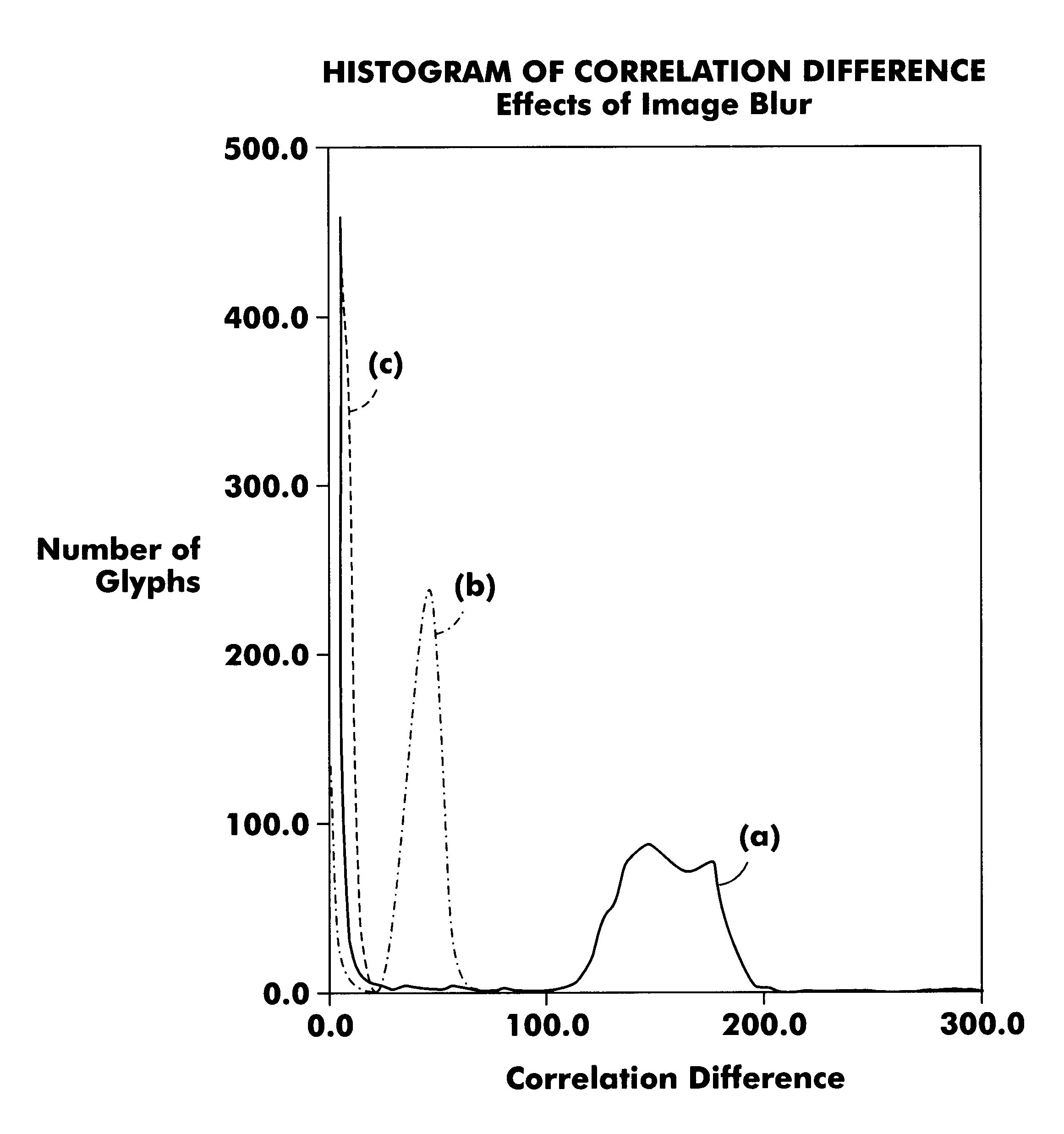
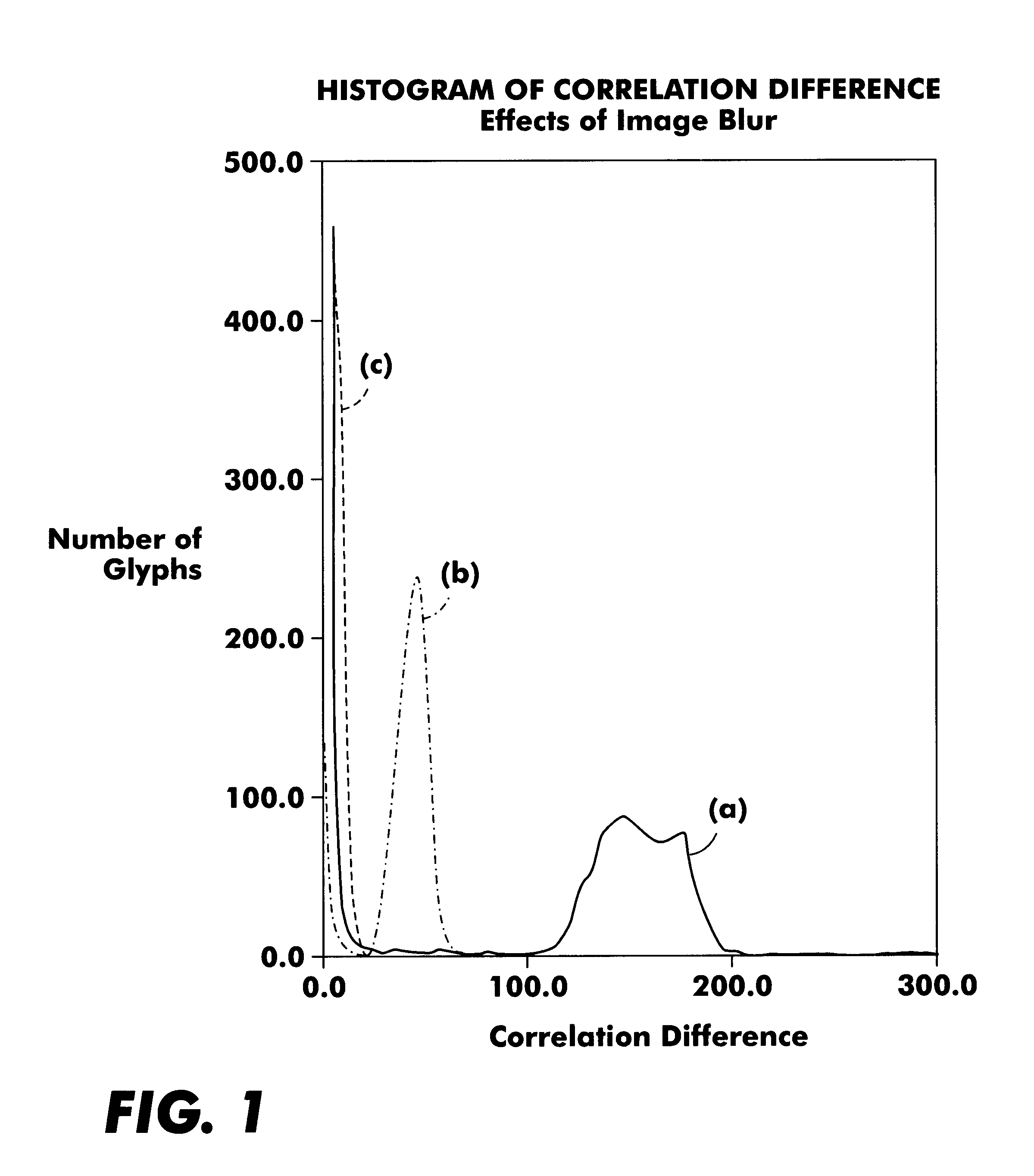
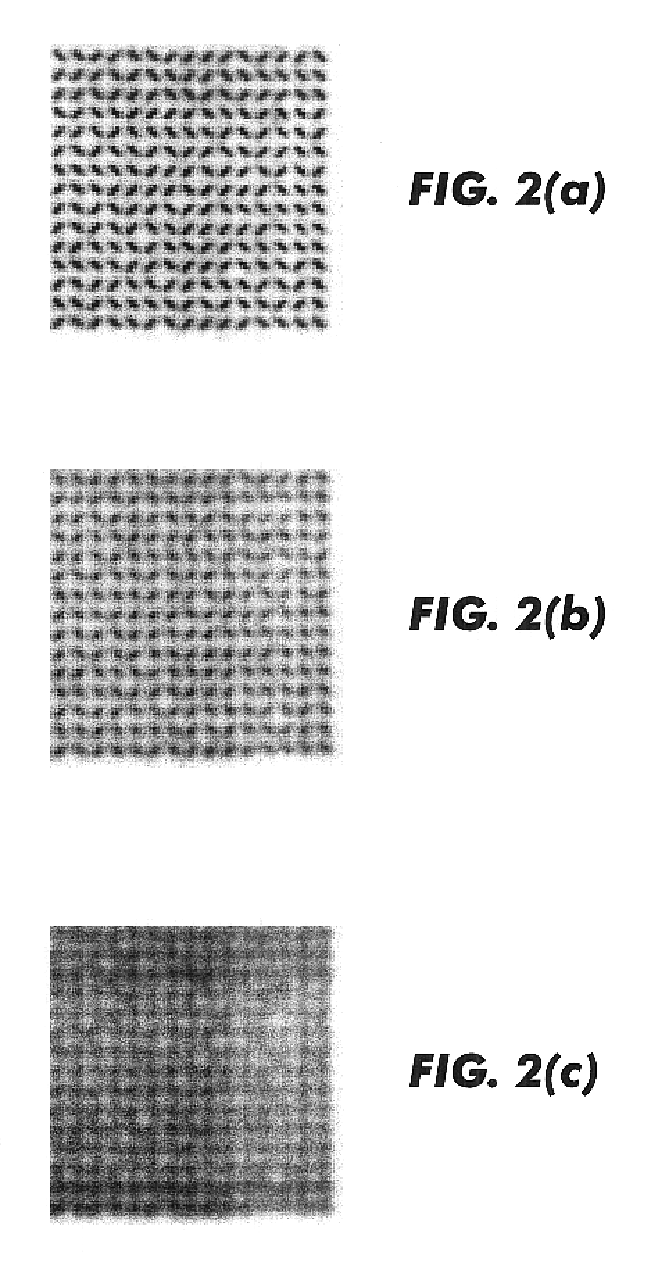
Use of correlation histograms for improved glyph decoding
InactiveUS6714677B1Character and pattern recognitionRecord carriers used with machinesAlgorithmGlyph
A method of decoding a plurality of glyphs comprising the steps of scanning a group of glyphs to form image data for expected glyph locations, assigning for each location a first value indicative of the likelihood that location contains a glyph in a first state, assigning for each location a second value indicative of the likelihood that location contains a glyph in a second state, determining the difference between the first and second values for each potential glyph location, establishing a distribution analysis of the determined differences and using that distribution analysis at least in part to control decoding of the plurality of glyphs.
Owner:XEROX CORP
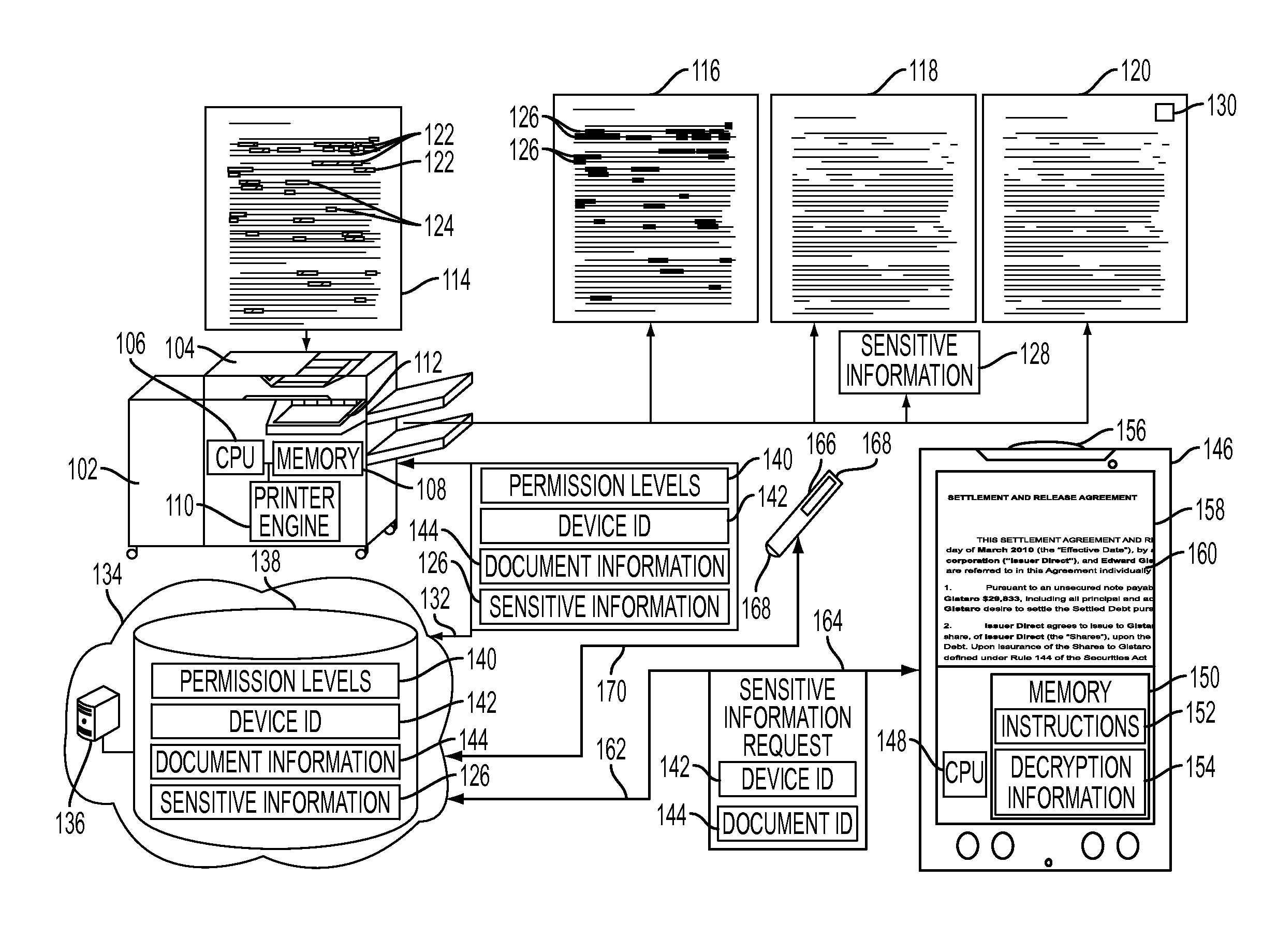
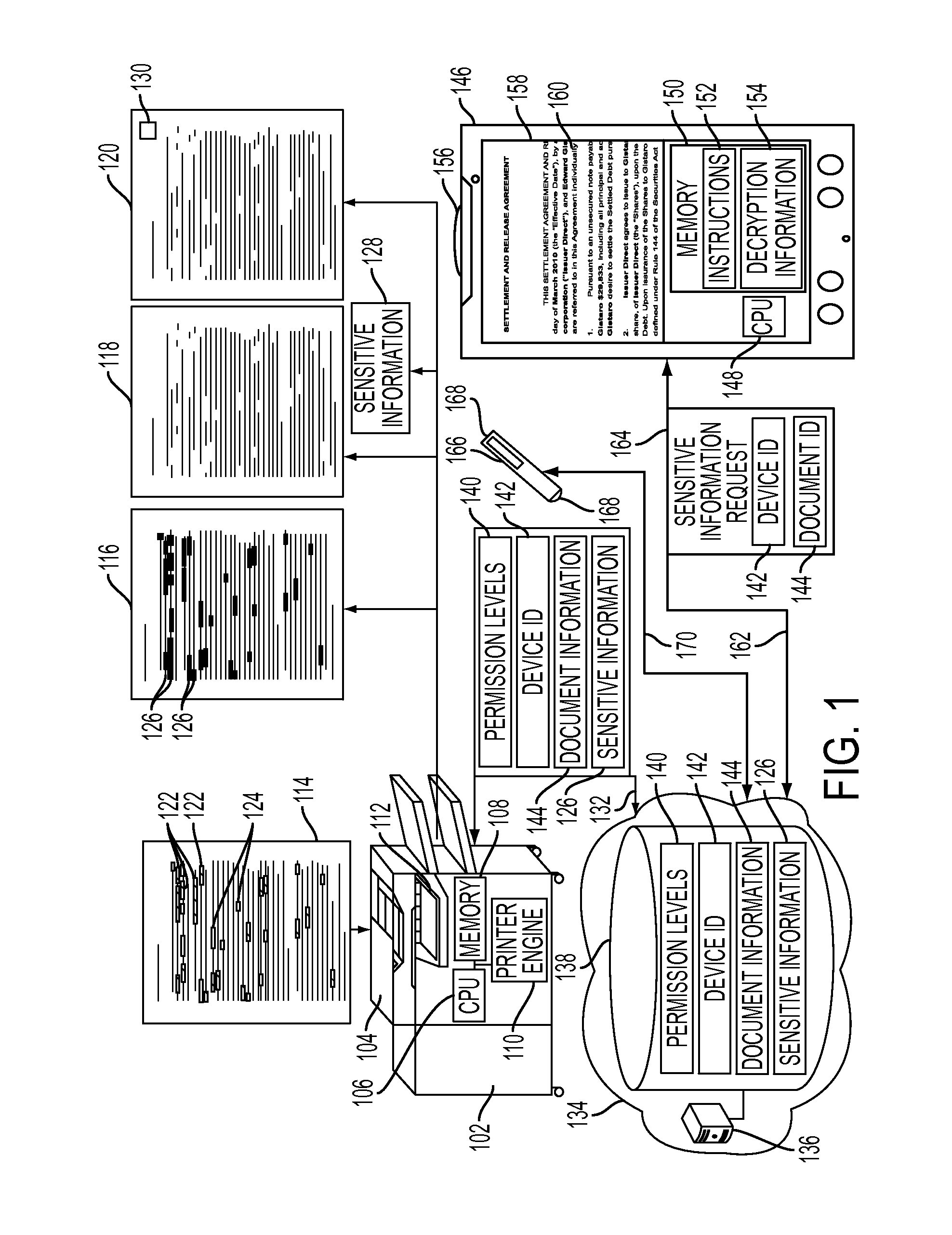
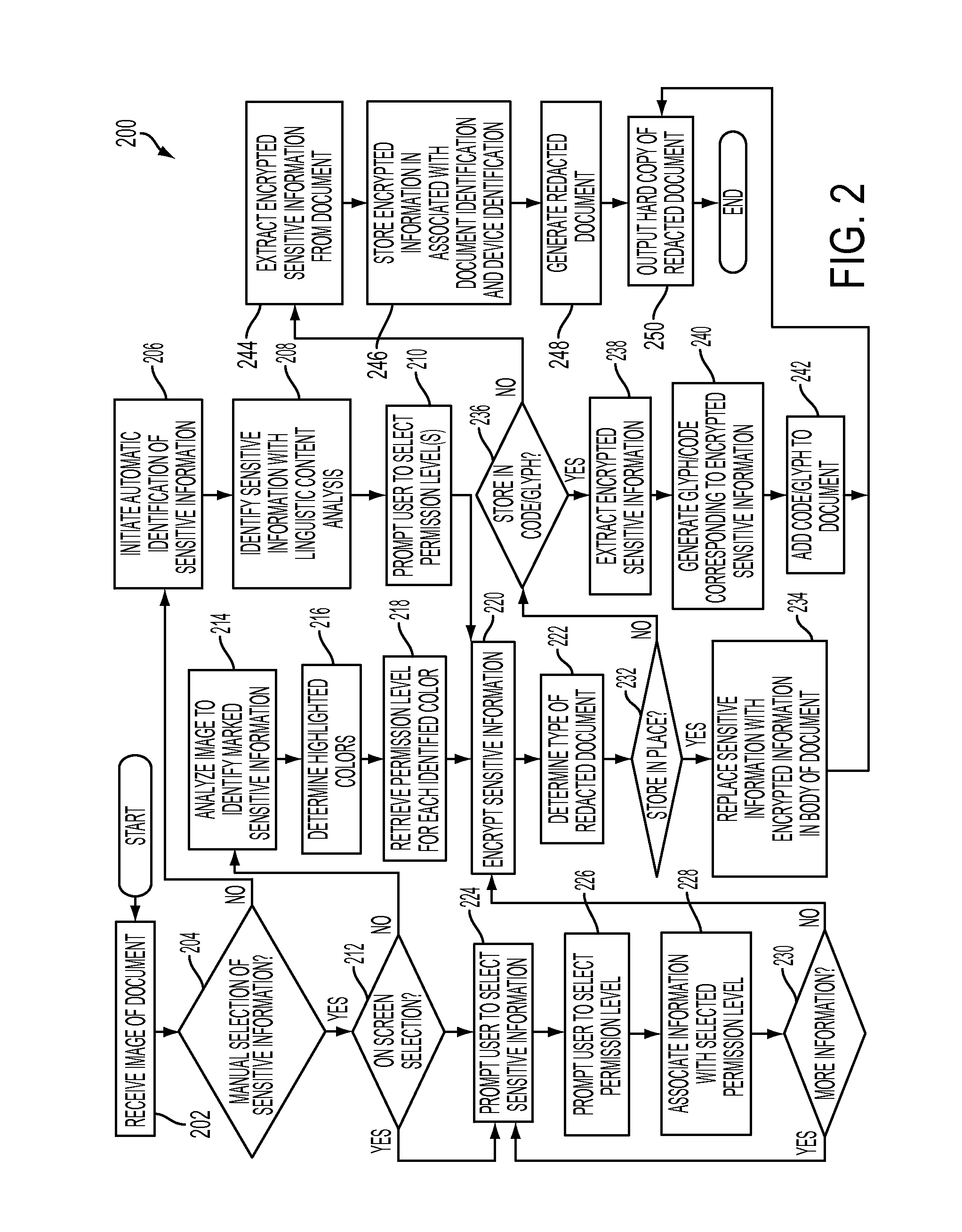
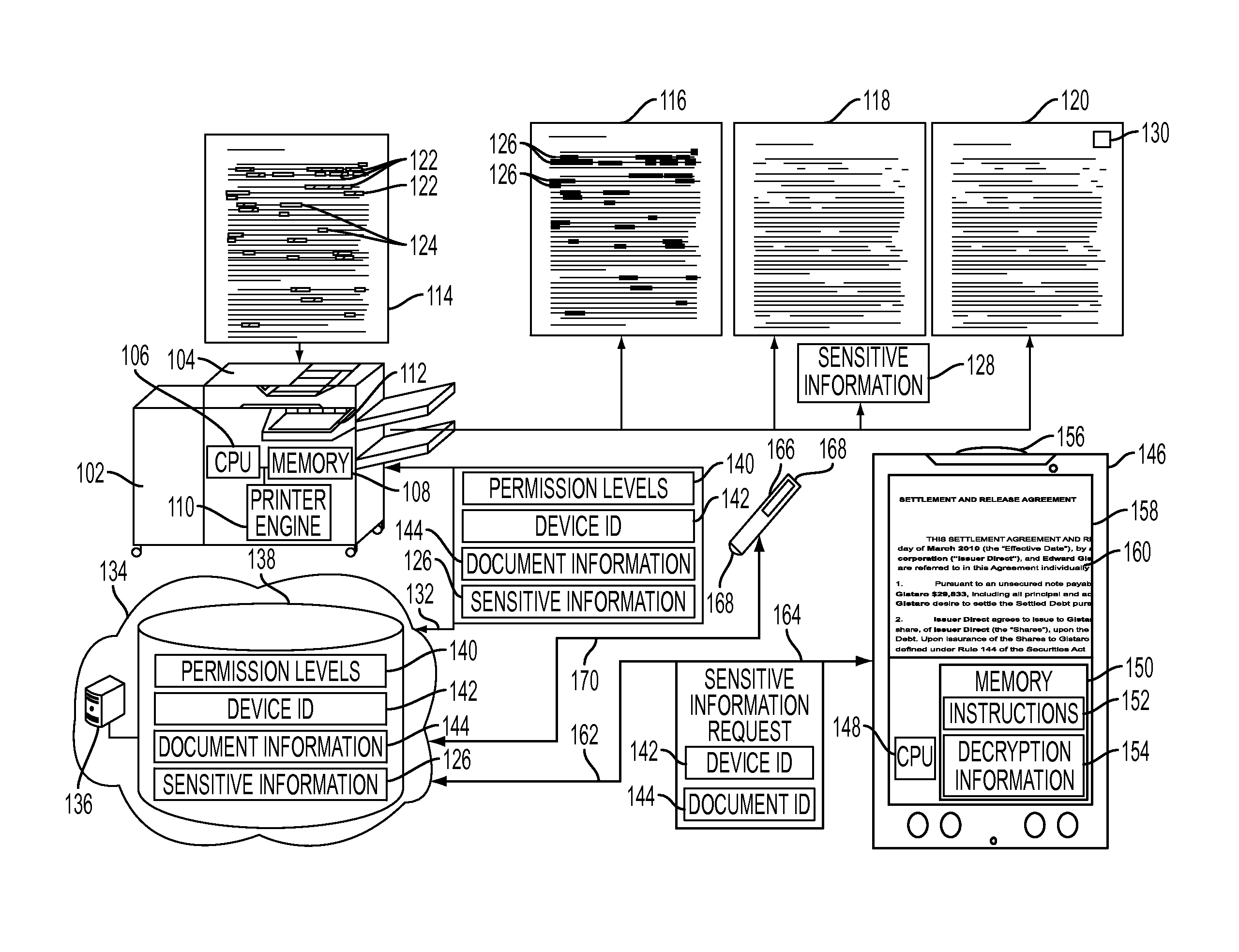
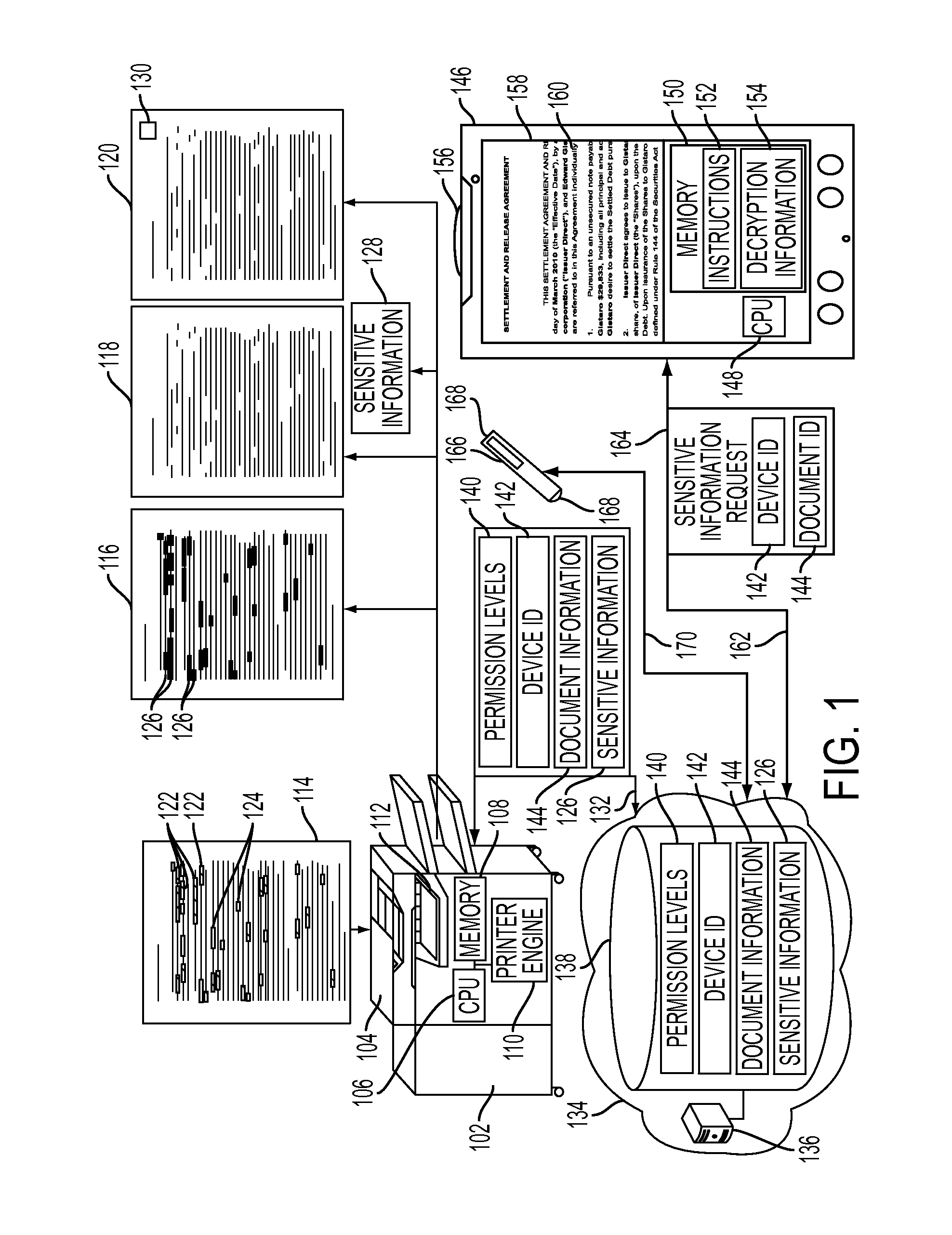
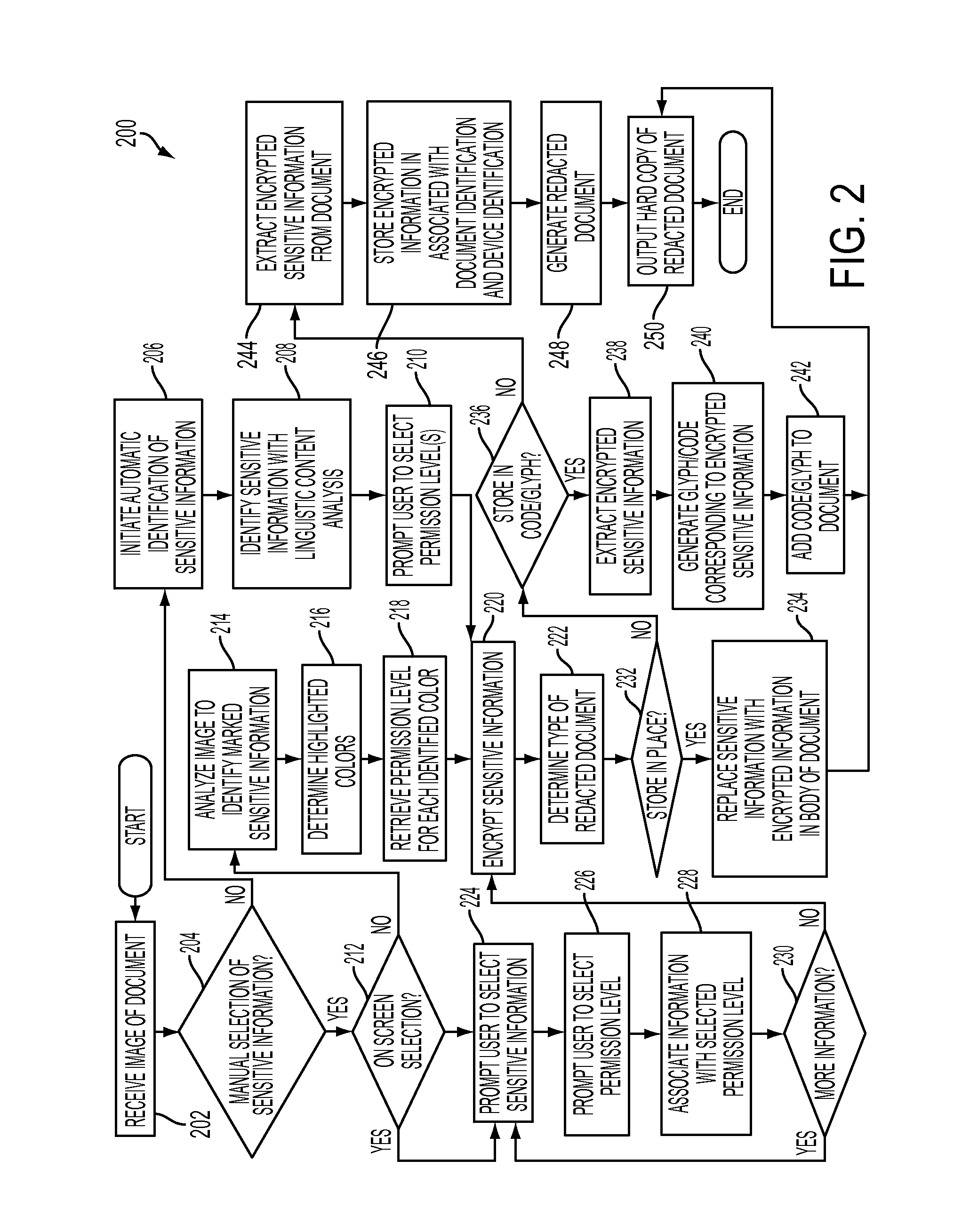
Mobile field level encryption of private documents
A method and system are disclosed for field level encryption of a document that provides a hardcopy having redacted sensitive information fields with multiple levels of access and an augmented reality view of the hardcopy displaying the unredacted sensitive information fields. Identification of the sensitive information fields may be accomplished via highlight color, user designation, or linguistic analysis. The identified fields are encrypted and may be stored separately, embedded in place, or embedded in a two-dimensional glyph. This information may be stored in association with a device identification of an authenticated mobile device and a document identification. A redacted hardcopy of the original document is output. A mobile device captures an image of the redacted hardcopy, decrypts the encrypted sensitive information fields, and generates an augmented reality view of the hardcopy with the previously redacted sensitive information fields visible on the display of the mobile device.
Owner:XEROX CORP
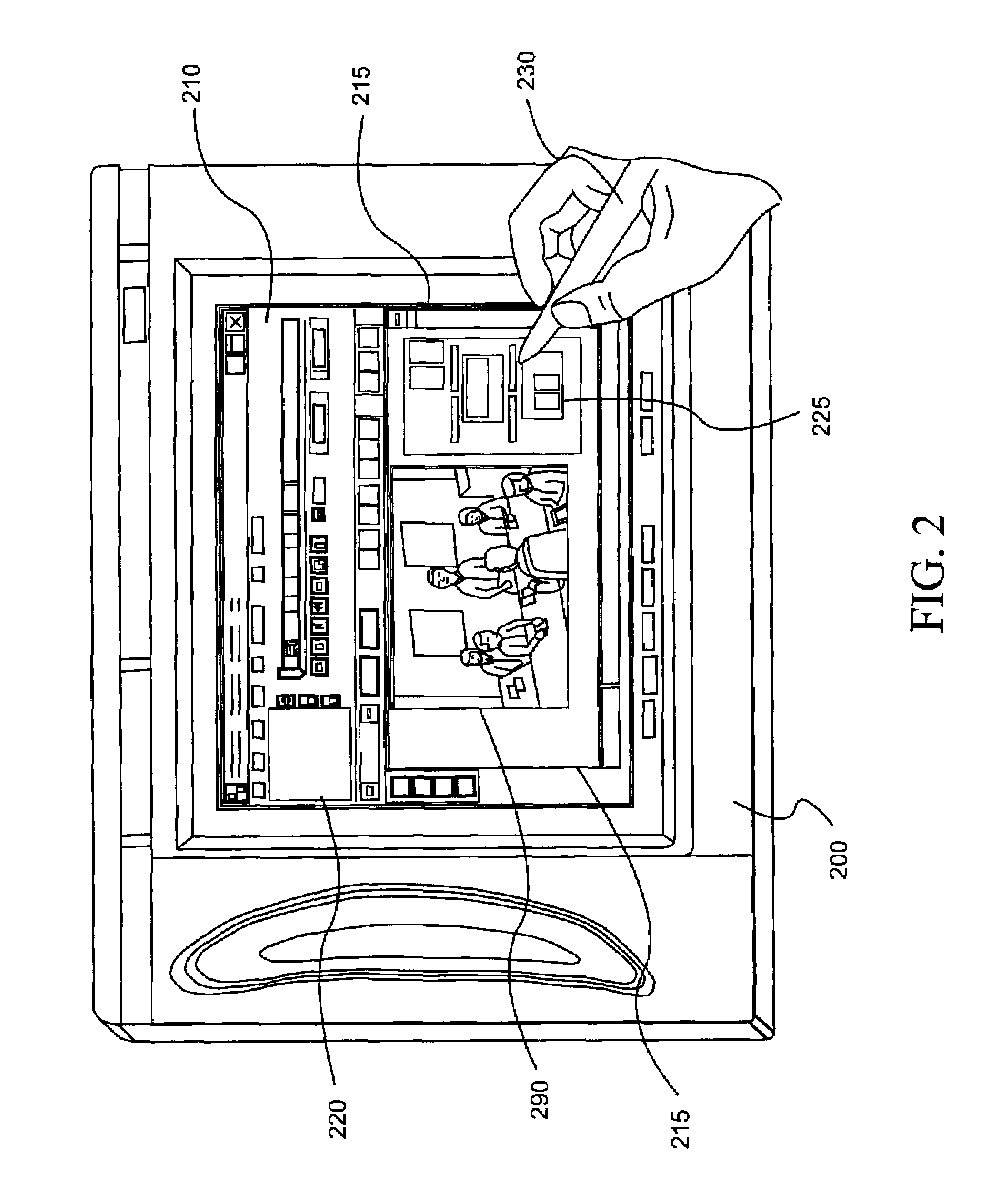
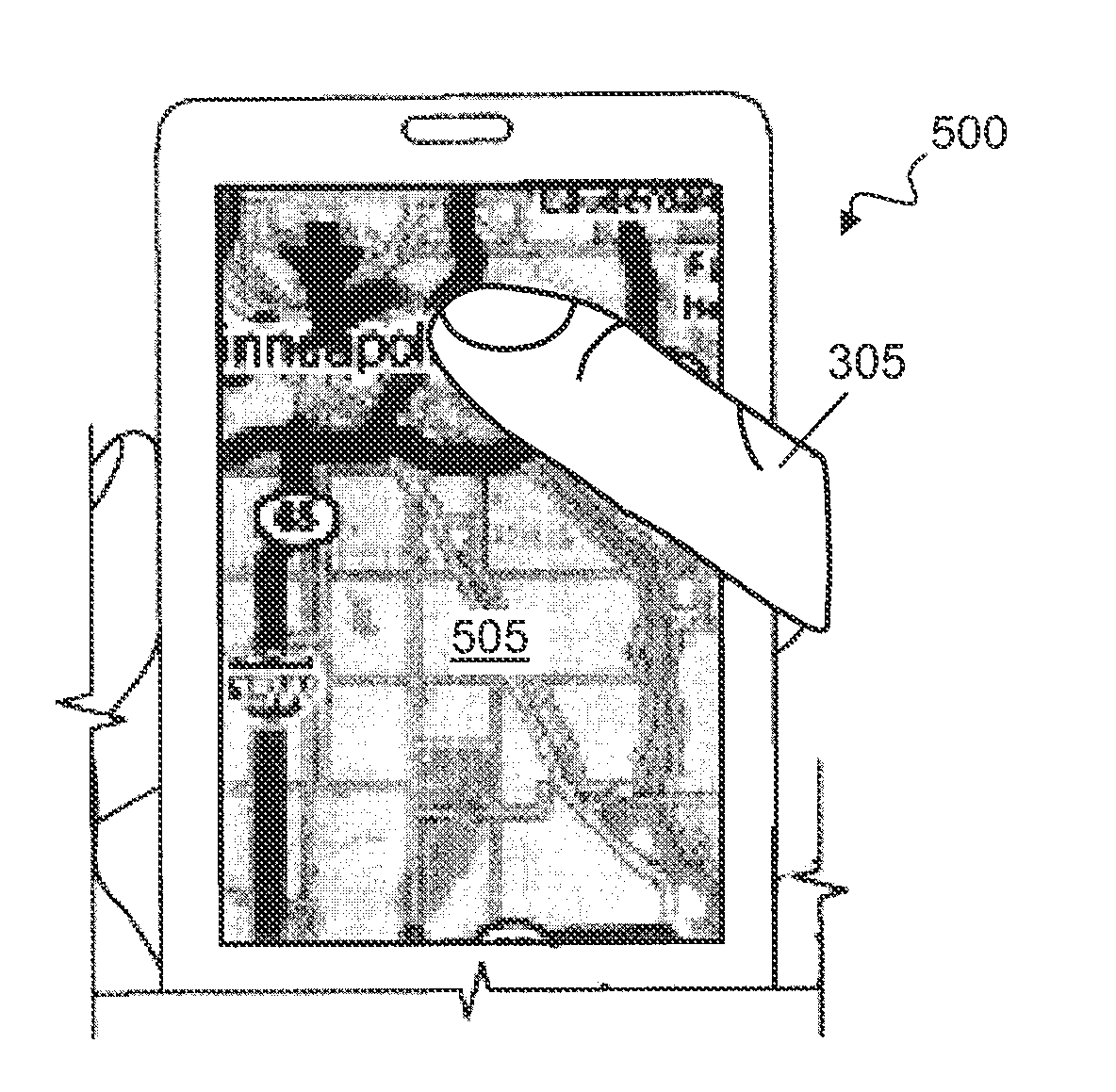
Touch screen device and method of displaying and selecting menus thereof
A touch screen device and method for displaying and selecting menus thereof are provided. The touch screen device includes a screen with a display for displaying menu images thereon and a detector for detecting a touch on a screen, and a controller which displays one or more menu bars on the screen. Each of the menu bars may have an expanded portion at one end thereof, and the menu bars may be displayed such that the expanded portions are arranged in a zigzag pattern to facilitate menu selection and reduce input errors. When two or more menu bars are erroneously touched, the controller may enlarge and display the touched menus so that a new touch input for the correct menu can be easily made. Thus, menus displayed on the touch screen may be arranged for easy selection, and input errors may be easily corrected.
Owner:LG ELECTRONICS INC
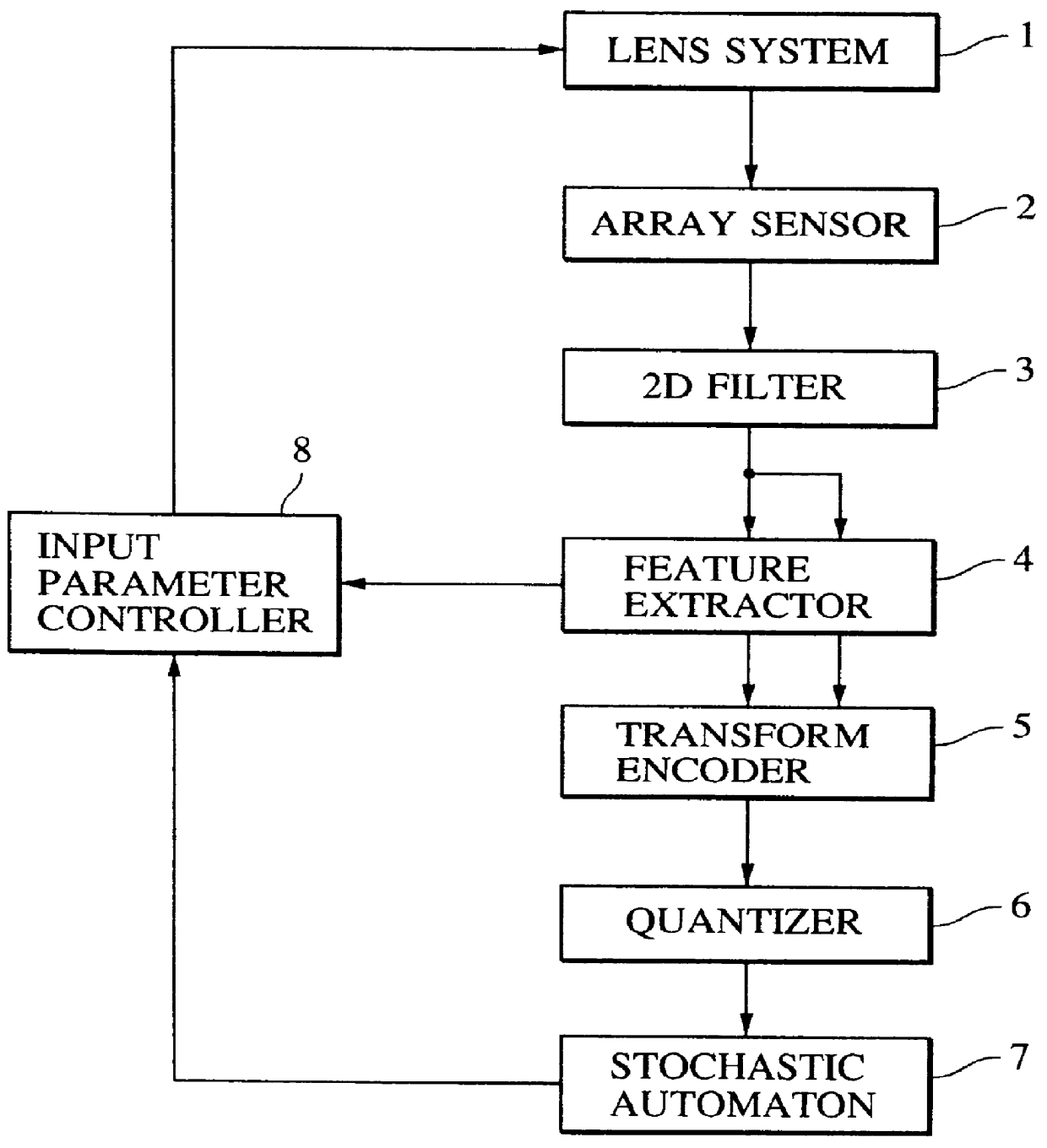
Method and apparatus for processing visual information
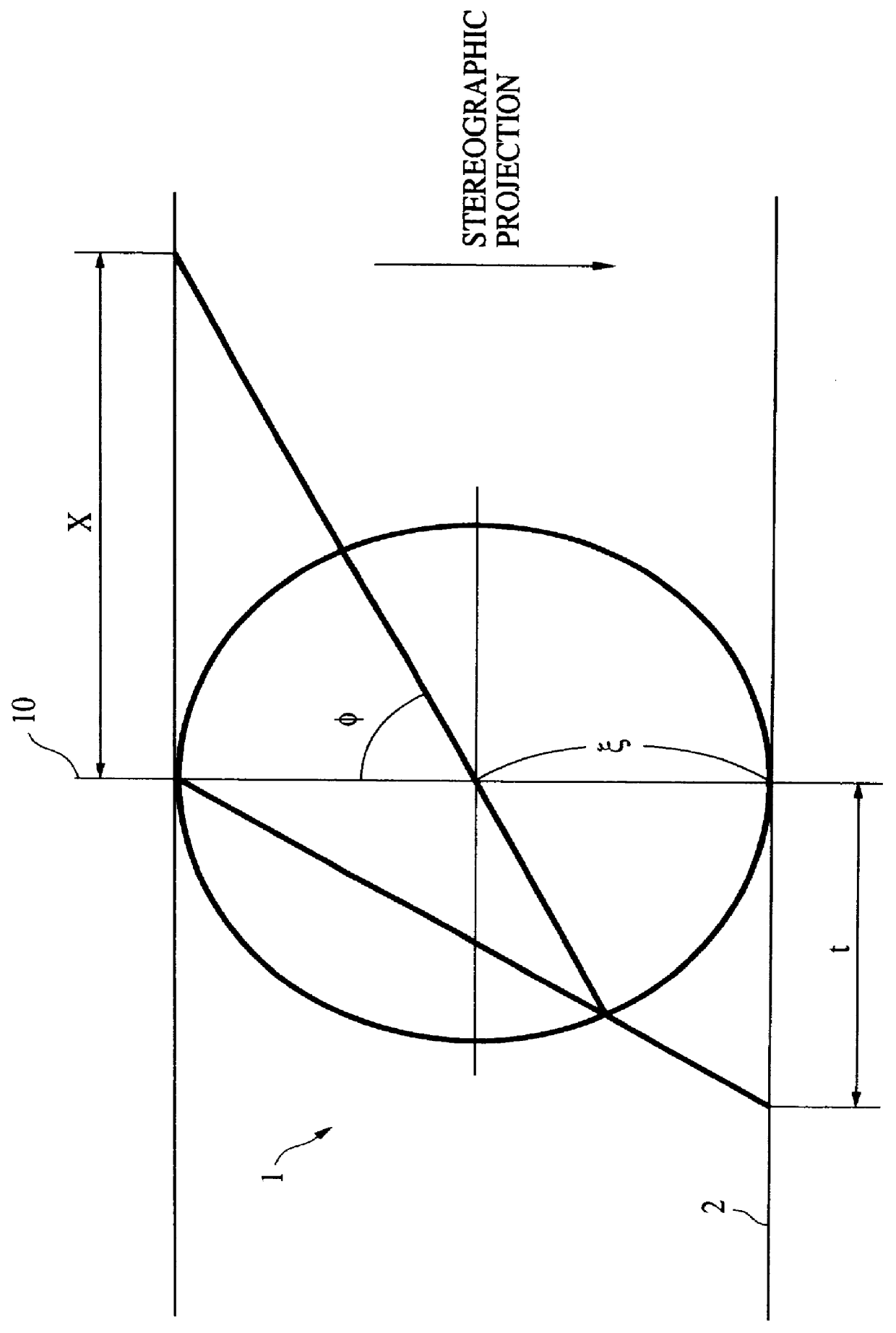
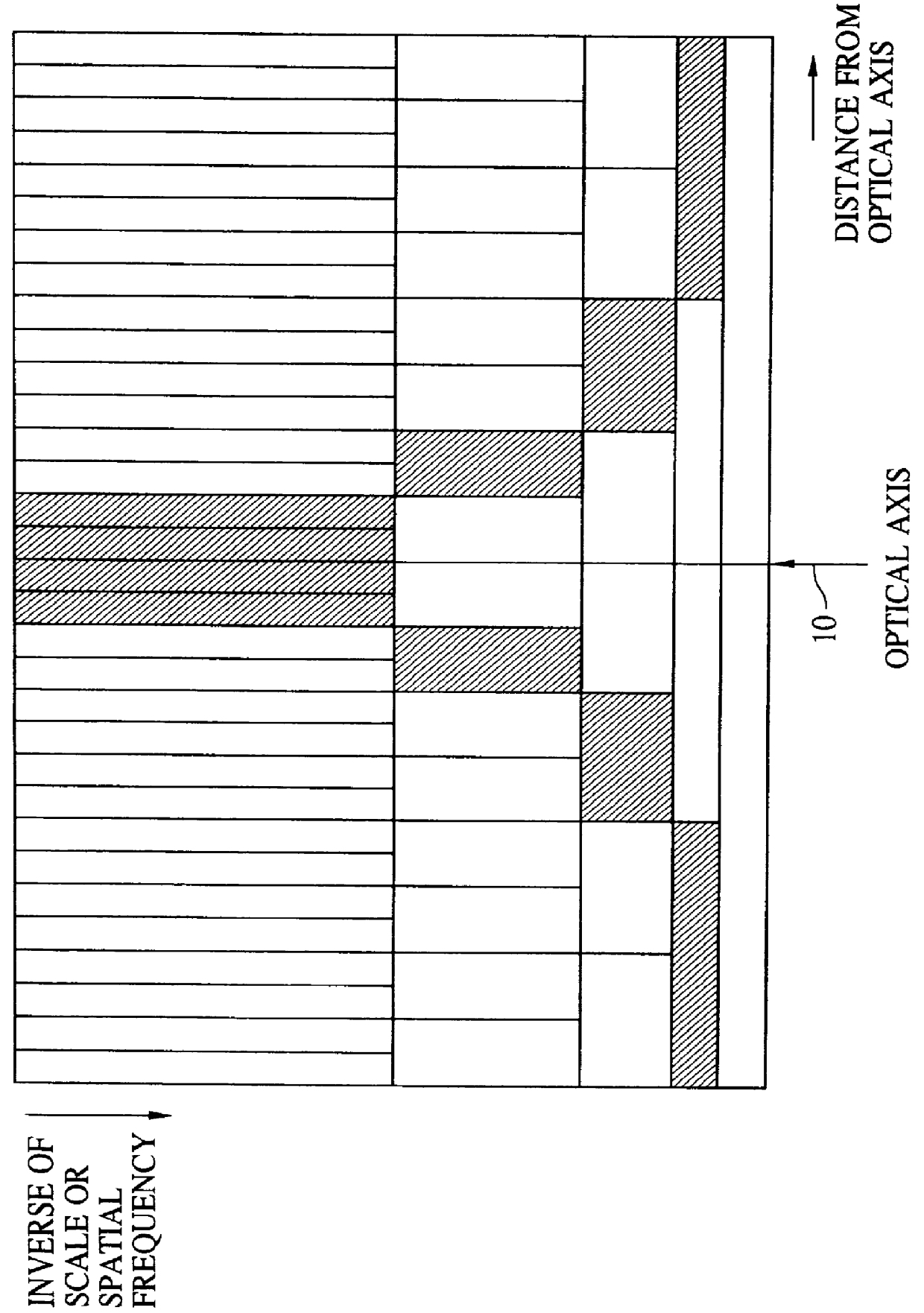
A 2D image supplied from an image input unit including a wide view lens is sampled into a discrete form by an array sensor, and then mapped to a multi-resolution space by a 2D filter. The feature of the supplied image is detected, and then the mapped image is transformed to a local pattern about the detected feature, and then the coordinates of the position of the feature and the code word of the local pattern are formed into a set which is then encoded. The code is supplied to each cell of a stochastic automaton. The quantity of visual information is calculated in accordance with the quantity of mutual information between different cells of the stochastic automaton consisting of cells in blocks, the coordinates of the position of the feature and the distance from the feature to the optical axis so as to control the optical axis of the image input unit in such a manner that the quantity of visual information is maximized.
Owner:CANON KK
Exposing various levels of text granularity for animation and other effects
InactiveUS20060227142A1Analogue computers for vehiclesAnalogue computers for trafficAnimationGranularity
Described is a system and method by which text elements to be rendered on a computer display (e.g., paragraph, line or any subset of text including a character or glyph) may be individually or collectively animated, at an author-selected level of granularity. Animation of text may be specified by setting animation properties via direct coding (e.g., in markup) or by specifying animation code to execute on text-related data, just prior to rendering. The text to animate may be static, or dynamically obtained at runtime from an external source. The text to animate is maintained as a whole with other text of the same element, in a text object, until a processing level that produces separate glyph runs, with an animation transform associated with each glyph run to be animated. Also described is an API that supports text animation.
Owner:MICROSOFT TECH LICENSING LLC
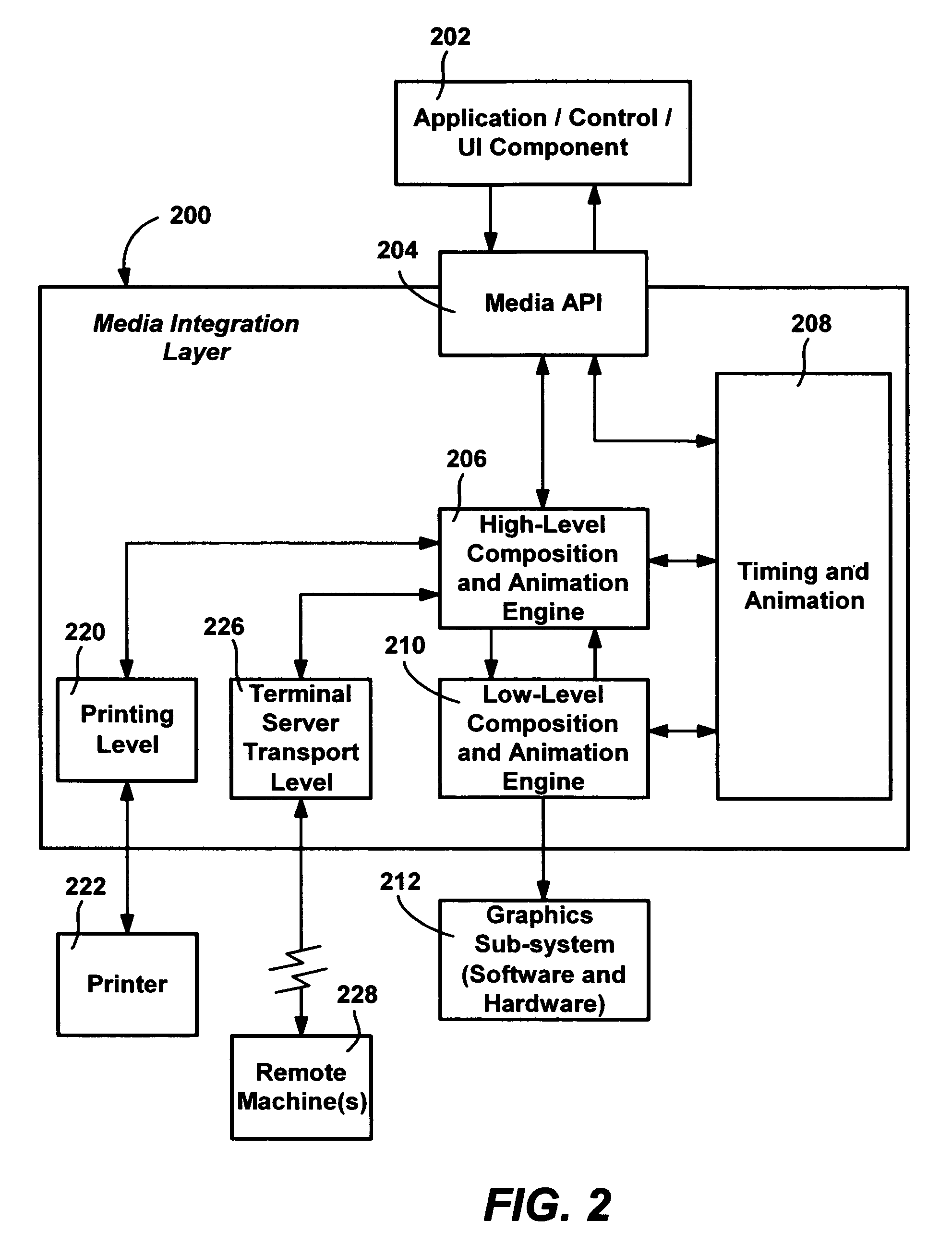
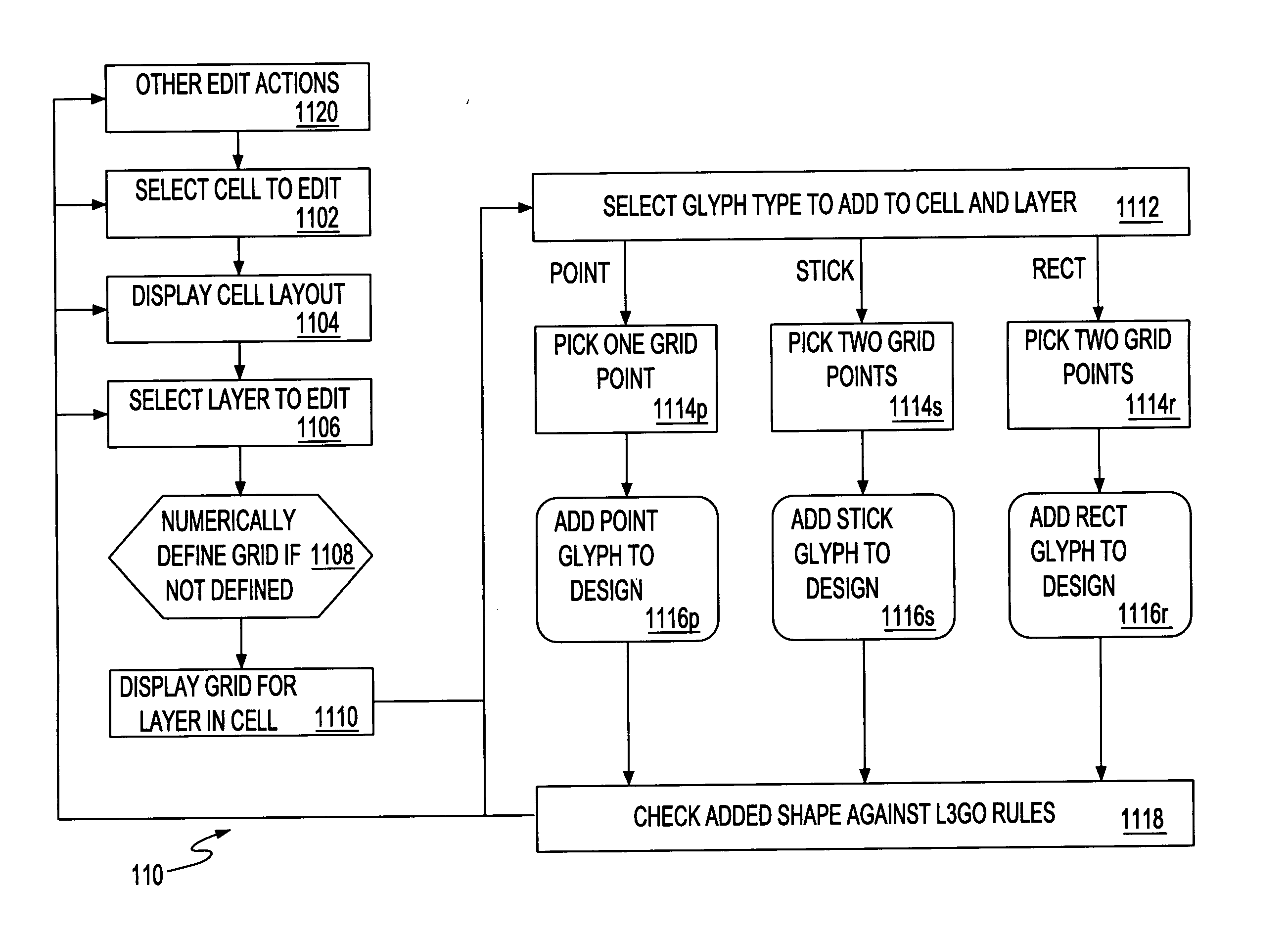
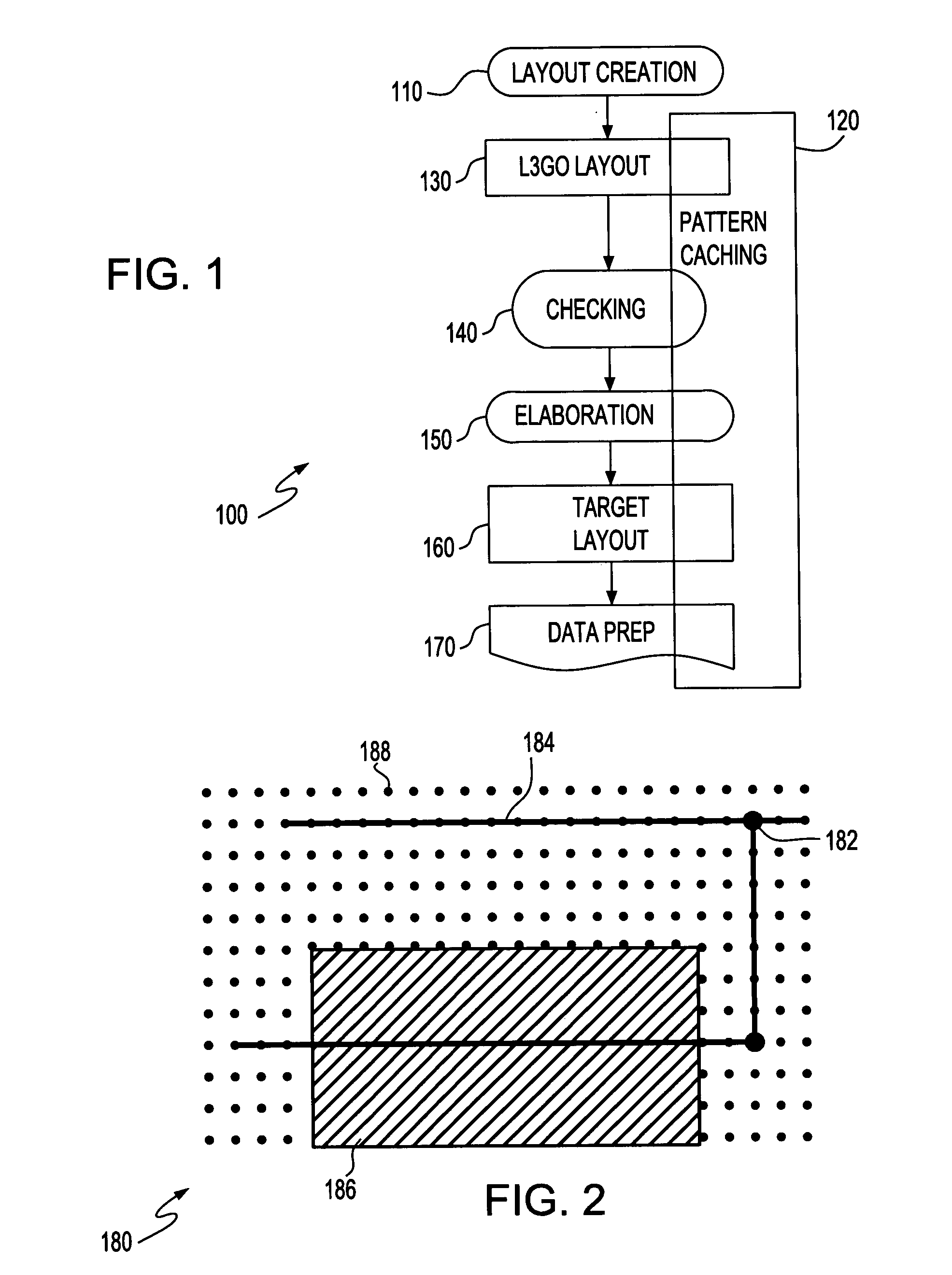
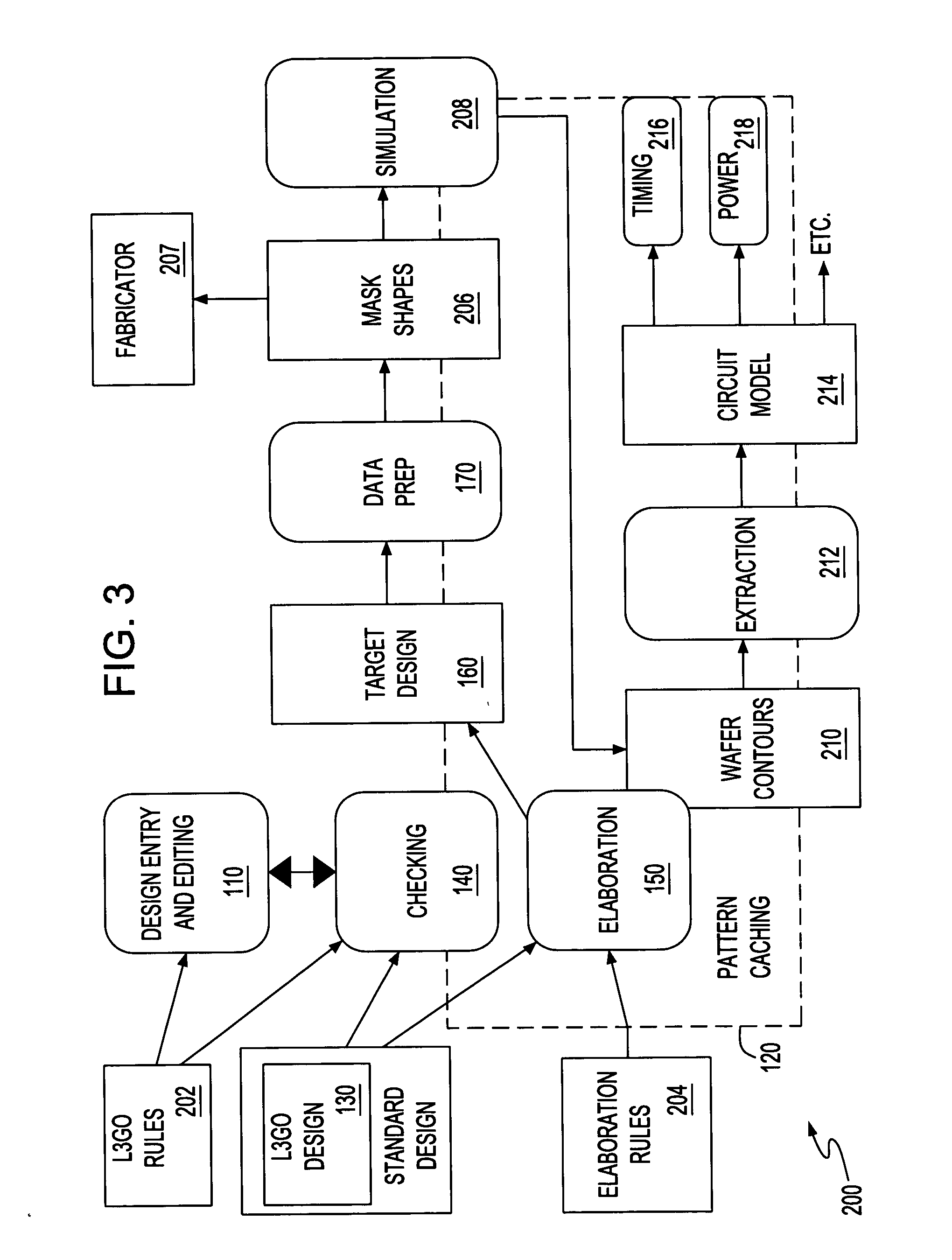
Physical design system and method
InactiveUS20060036977A1Low costReduce riskDesign optimisation/simulationSoftware simulation/interpretation/emulationGlyphEngineering
A design system for designing complex integrated circuits (ICs), a method of IC design and program product therefor. A layout unit receives a circuit description representing portions in a grid and glyph format. A checking unit checks grid and glyph portions of the design. An elaboration unit generates a target layout from the checked design. A data prep unit prepares the target layout for mask making. A pattern caching unit selectively replaces portions of the design with previously cached results for improved design efficiency.
Owner:GLOBALFOUNDRIES INC
Selection of Text in an Unstructured Document
ActiveUS20100174983A1Improve efficiencyNatural language translationText processingNatural language processingGlyph
Owner:APPLE INC
Document printed with graphical symbols which encode information
Owner:FISERV CIR
Systems and methods for policy based printing
InactiveUS7110541B1User identity/authority verificationCharacter and pattern recognitionDigital signatureGlyph
A print management system includes a policy that determines a protection level for a document to be printed. The document is printed using forgery detection and deterrence technologies, such as fragile and robust watermarks, glyphs, and digital signatures, that are appropriate to the level of protection determined by the policy. A plurality of printers are managed by a print management system. Each printer can provide a range of protection technologies. The policy determines the protection technologies for the document to be printed and the print management system routes the print job to a printer that can apply the appropriate protections and sets the appropriate parameters in the printer. Copy evidence that can verify that a document is a forgery and / or tracing information that identifies the custodian(s) of the document and restrictions on copying of the document and use of the information in the document are included in the watermark that is printed with the document information. A document can be verified as an original or a forgery by inspecting the copy evidence and / or tracing information in the watermark.
Owner:XEROX CORP
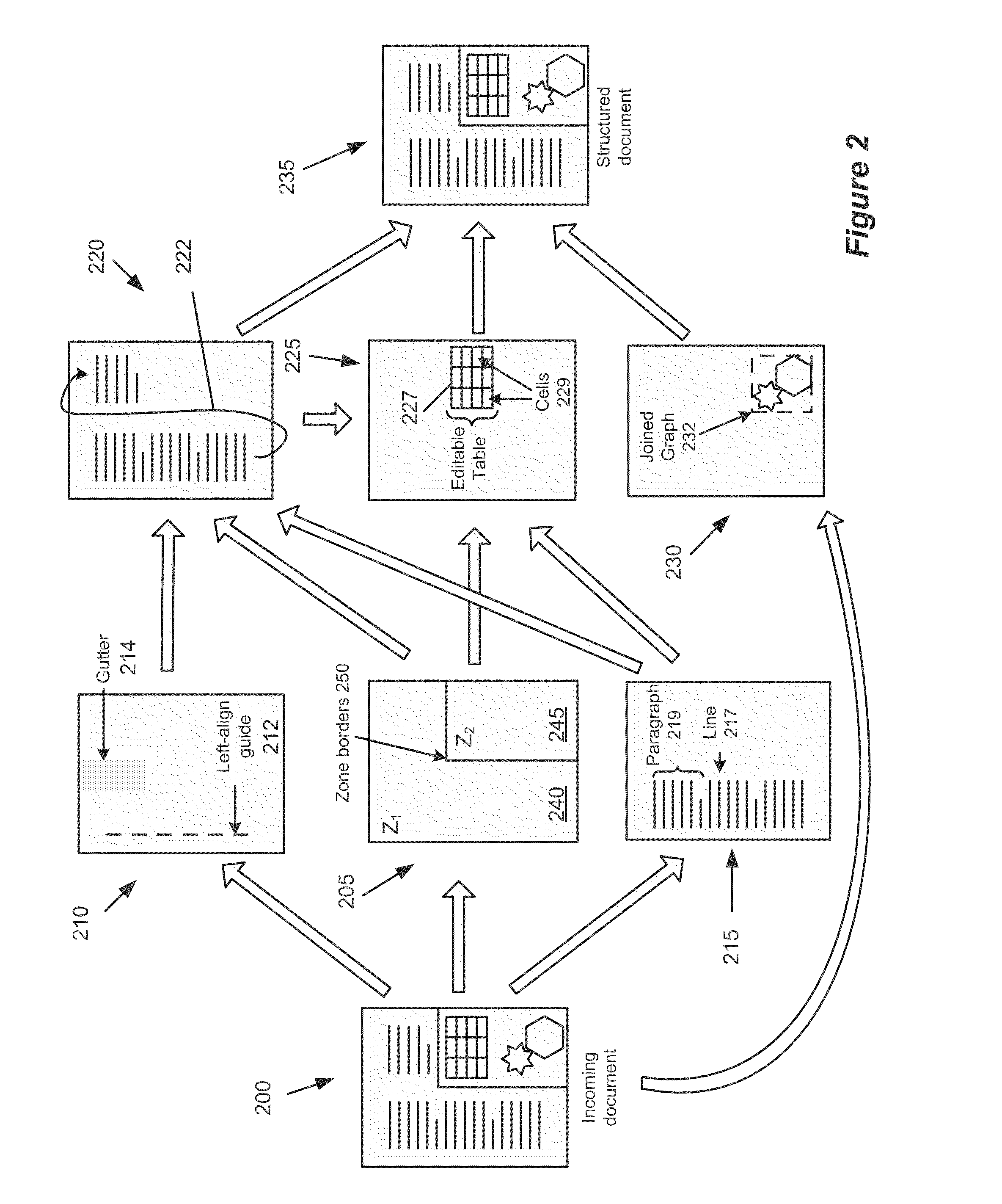
Identification of Tables in an Unstructured Document
ActiveUS20100174975A1Improve efficiencyNatural language translationText processingGlyphDocumentation
Some embodiments provide a method for analyzing an unstructured document that includes a number of glyphs. The method identifies boundaries between sets of glyphs. The method identifies that several of the boundaries form a table. The method defines a tabular structural element based on the table. The tabular structural element includes several cells arranged in a plurality of rows and columns, each of which includes an associated set of glyphs.
Owner:APPLE INC
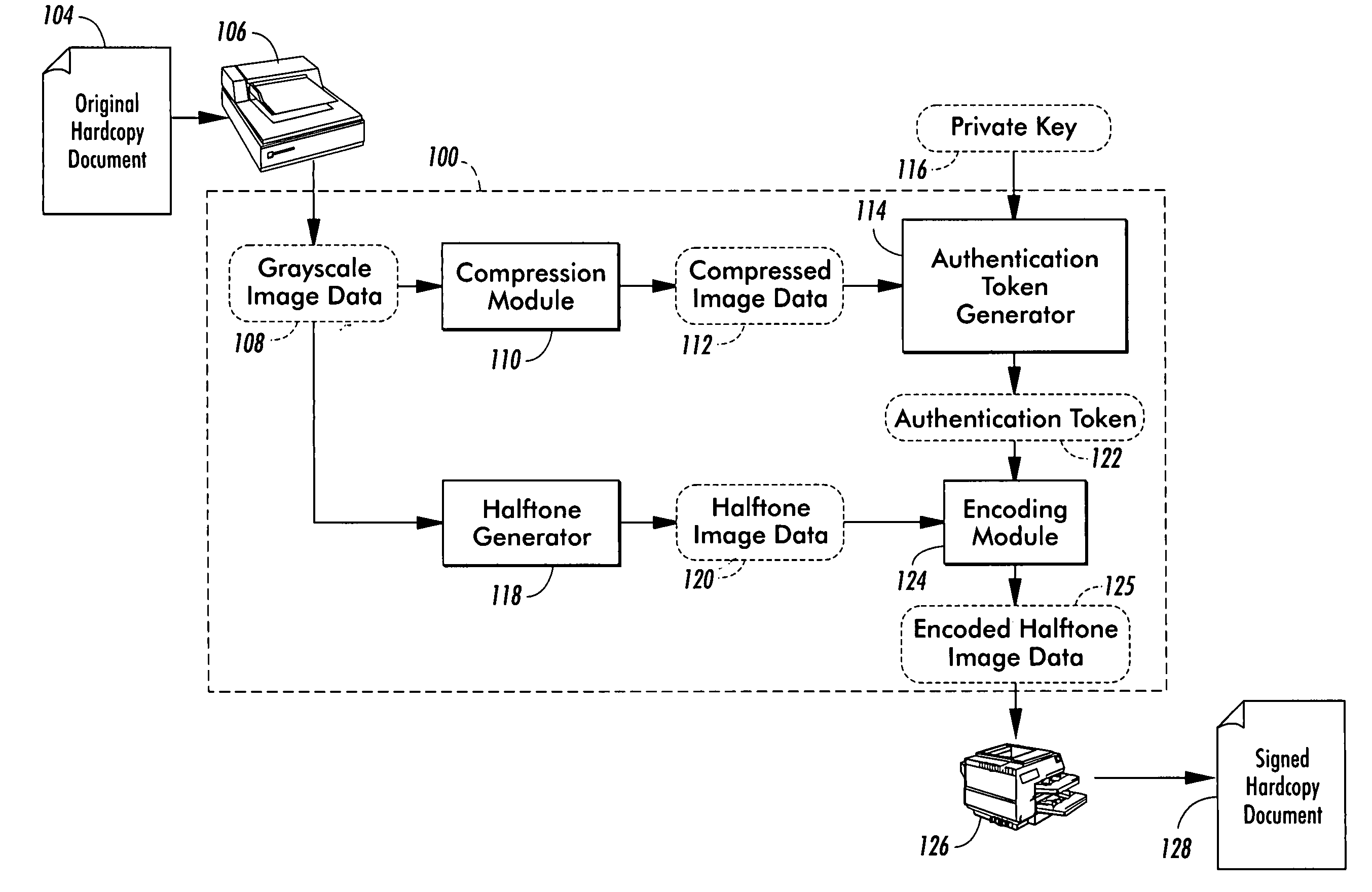
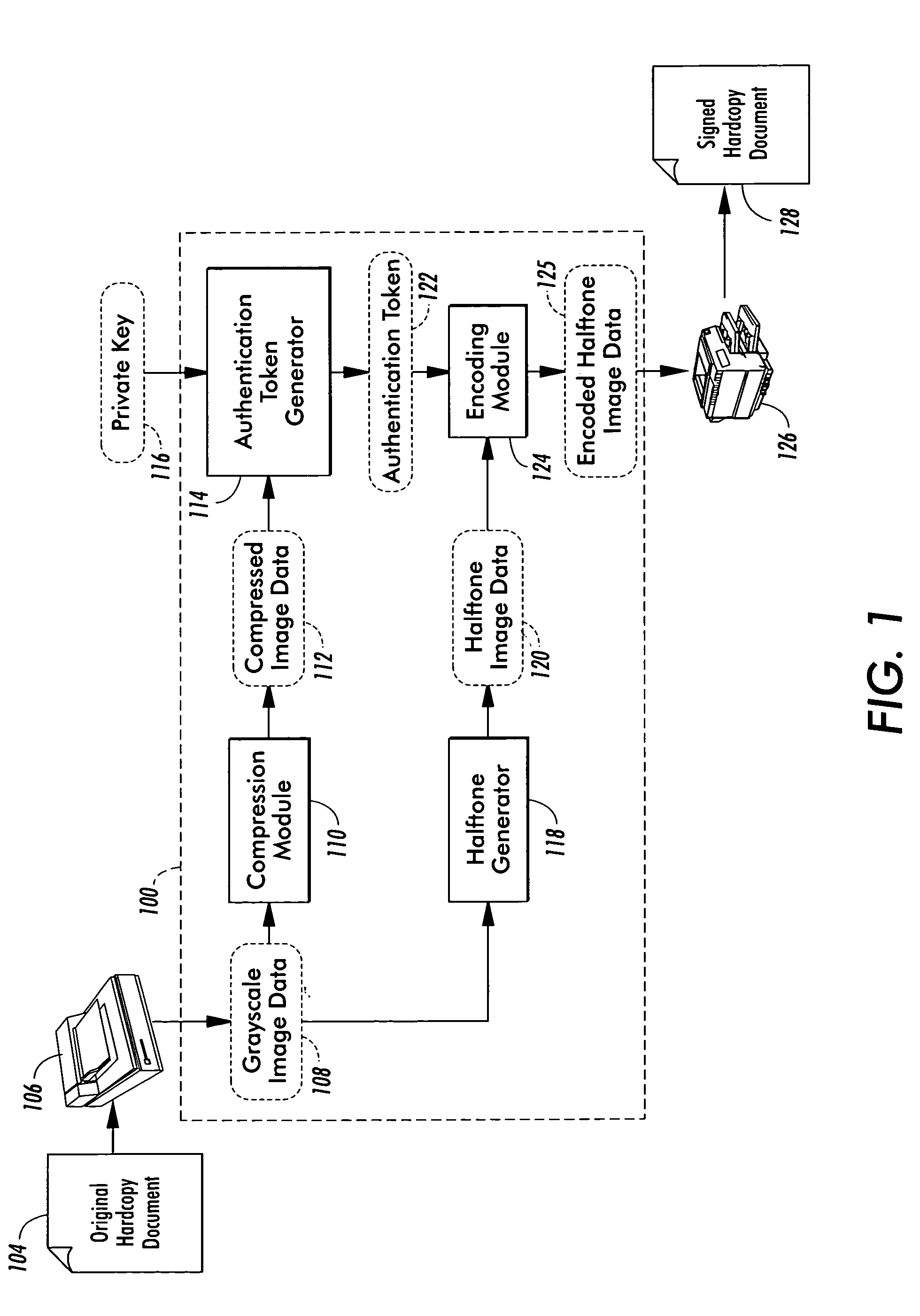
System for authenticating hardcopy documents
InactiveUS7394573B1Convenient verificationEasy to compressDigitally marking record carriersPaper-money testing devicesDigital signatureDisplay device
A system authenticates an original hardcopy document using a digital signature generation system and a digital signature verification system. Initially, the original hardcopy document is scanned to provide a bitmap image to the signature generation system. The bitmap image is highly compressed by the signature generation system using compression schemes such as MPEG (for gray images) or a low-fidelity symbol based compression scheme (for bi-level images). A signed hardcopy document is then printed that includes the bitmap image and an authentication token. The authentication token is encoded in the signed hardcopy document using either serpentine halftone patterns or data glyphs. The authenticity of the signed hardcopy document is verified by inputting a scanned bitmap image of the signed hardcopy document into the signature verification system. Once received, the signature verification system decodes, authenticates, and decompresses the bitmap image to define decompressed image data. The decompressed image data is then output to a display or printer and compared with the signed hardcopy document to determine whether it is authentic.
Owner:XEROX CORP
Mobile field level encryption of private documents
ActiveUS8867741B2Unauthorized memory use protectionHardware monitoringInternet privacyDisplay device
A method and system are disclosed for field level encryption of a document that provides a hardcopy having redacted sensitive information fields with multiple levels of access and an augmented reality view of the hardcopy displaying the unredacted sensitive information fields. Identification of the sensitive information fields may be accomplished via highlight color, user designation, or linguistic analysis. The identified fields are encrypted and may be stored separately, embedded in place, or embedded in a two-dimensional glyph. This information may be stored in association with a device identification of an authenticated mobile device and a document identification. A redacted hardcopy of the original document is output. A mobile device captures an image of the redacted hardcopy, decrypts the encrypted sensitive information fields, and generates an augmented reality view of the hardcopy with the previously redacted sensitive information fields visible on the display of the mobile device.
Owner:XEROX CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com