Patents
Literature
38results about How to "Prevent rewriting" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Text hidden method based on Chinese sentence pattern template transformation
InactiveCN101639826AConform to the semantic idiomPrevent rewritingSpecial data processing applicationsElectronic documentComputerized system
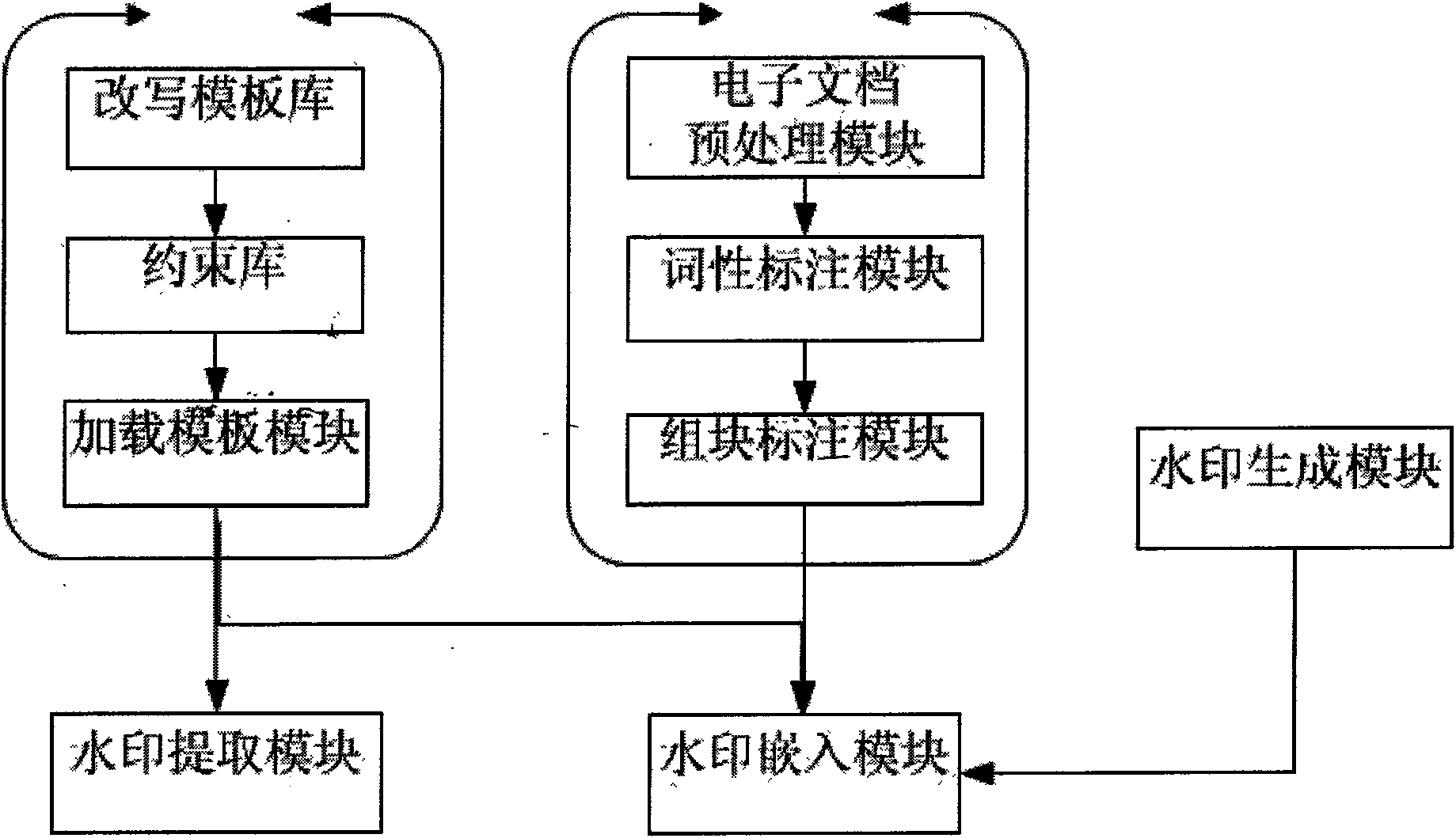
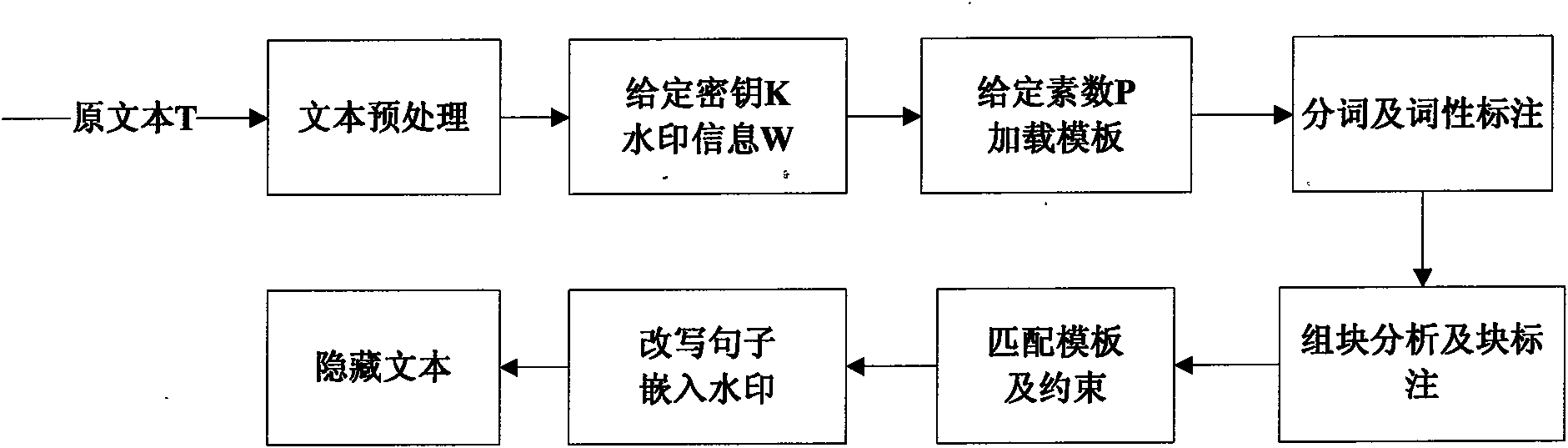
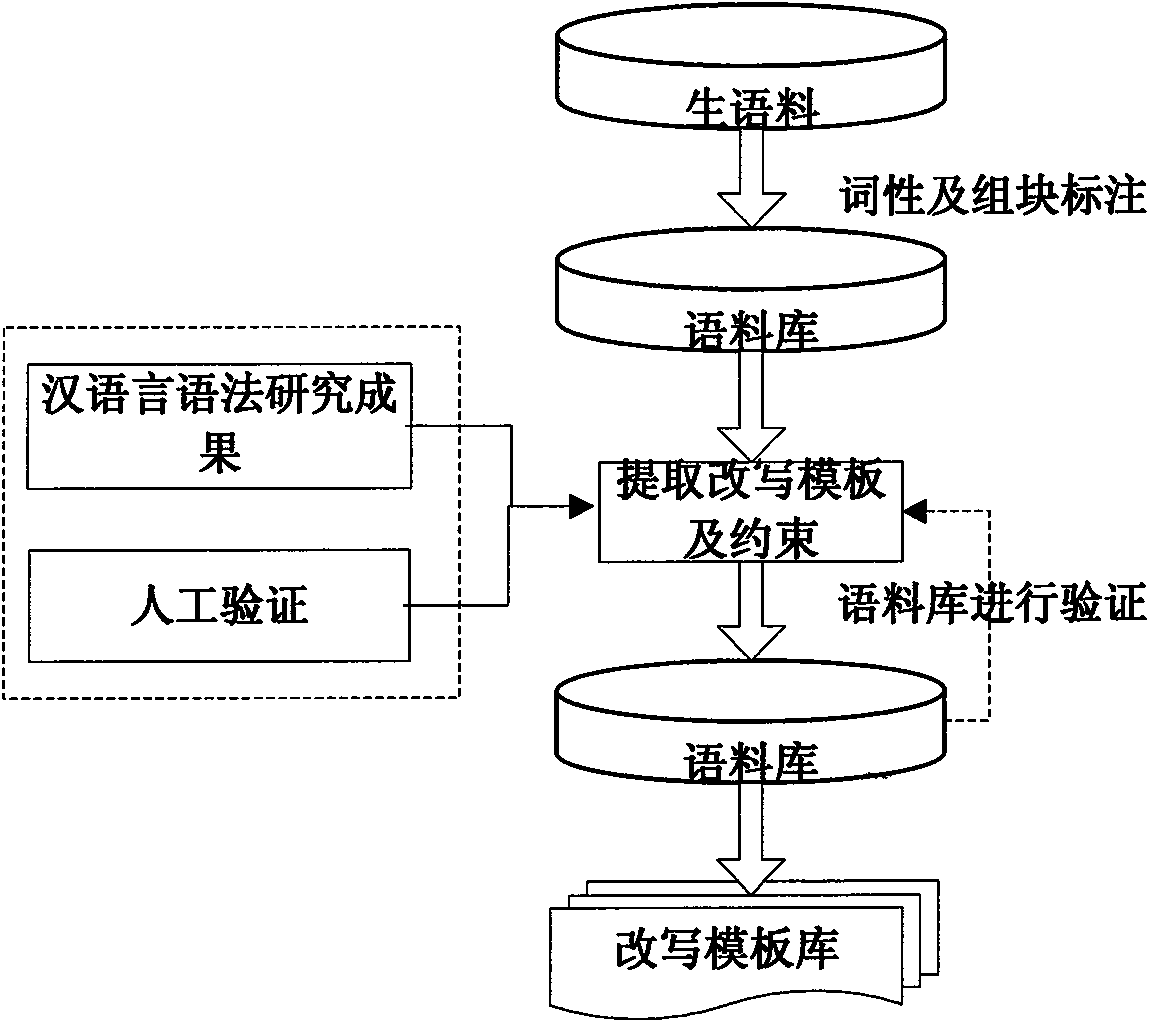
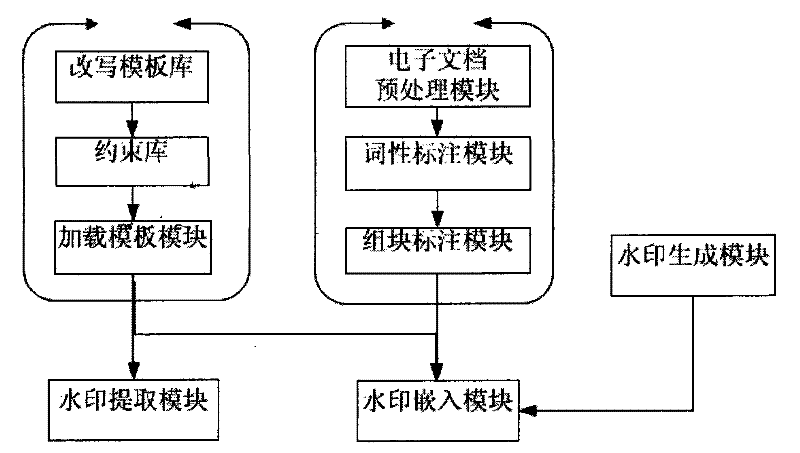
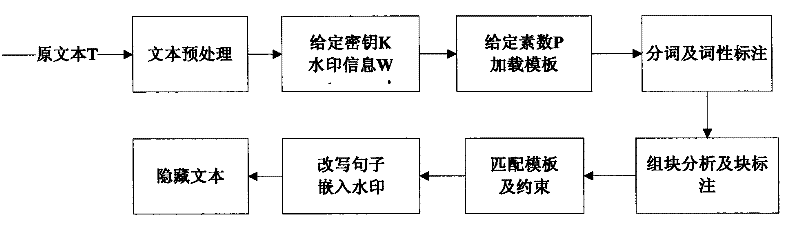
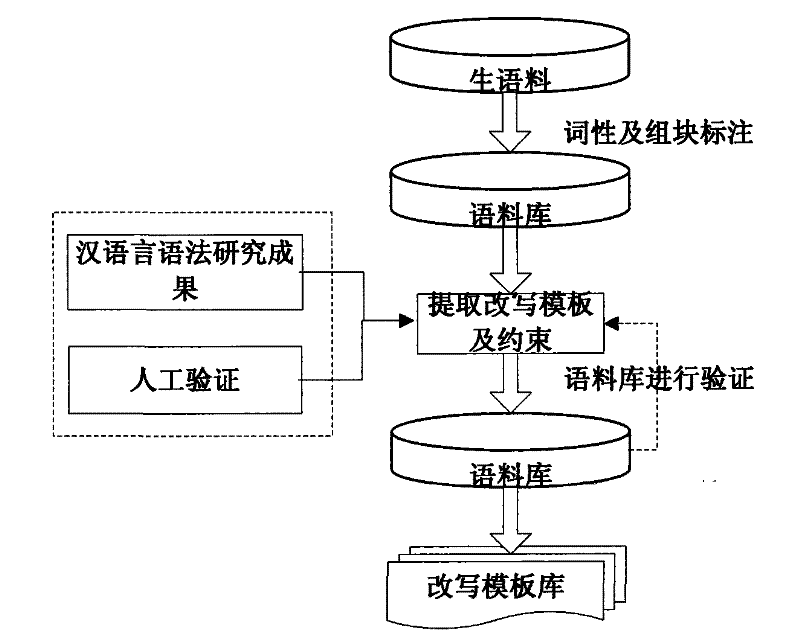
The invention discloses a text hidden method based on Chinese sentence pattern template transformation. The method utilizes the computer system to carry out watermark embedment and extraction on textinformation to hide the text information, comprising the following steps: (1) carrying out pre-treatment on an electronic file; (2) generating watermark information sign and setting a key; (3) carrying out part-of-speech tagging to format-free file generated in step (1) by a part-of-speech tagging module and outputting a part-of-speech tagging string of a sentence; (4) simplifying the part-of-speech tagging string output in the step (3) by a chunk tagging module; (5) loading a template module to select a sentence pattern module; (6) embedding watermark information by a watermark embedment module; (7) outputting the hidden text with embedded watermark; and (8) extracting the watermark information from the hidden text by a watermark extraction module through the key. The text hidden method changes sentence pattern through a template, avoids complex understanding and processing of grammar and semanteme, ensures the carrier text better satisfying grammar and semanteme habit and prevents blindfold rewrite.
Owner:NORTHWEST UNIV(CN)
Gamma correction buffer circuit, display device and anti-interference method
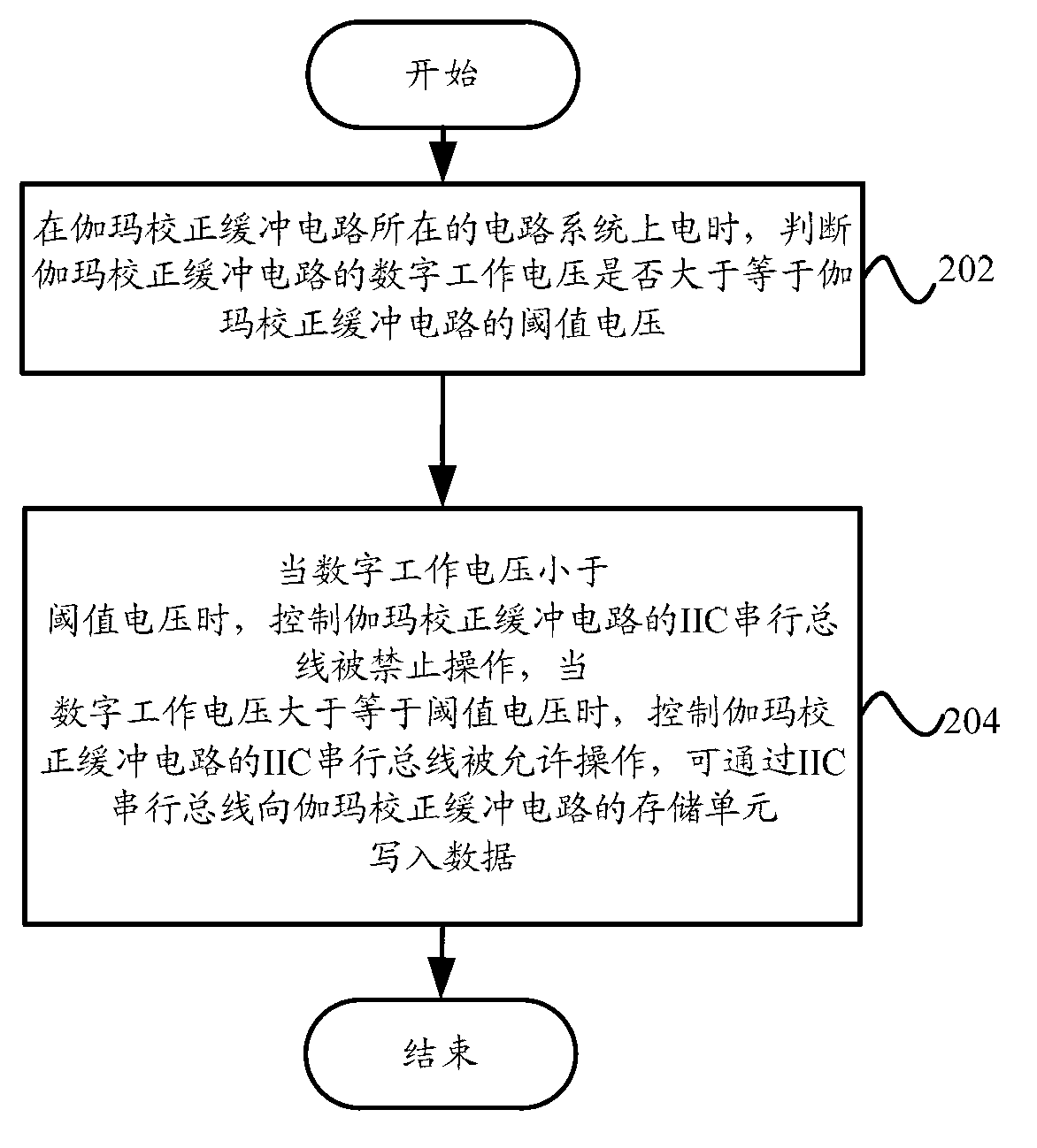
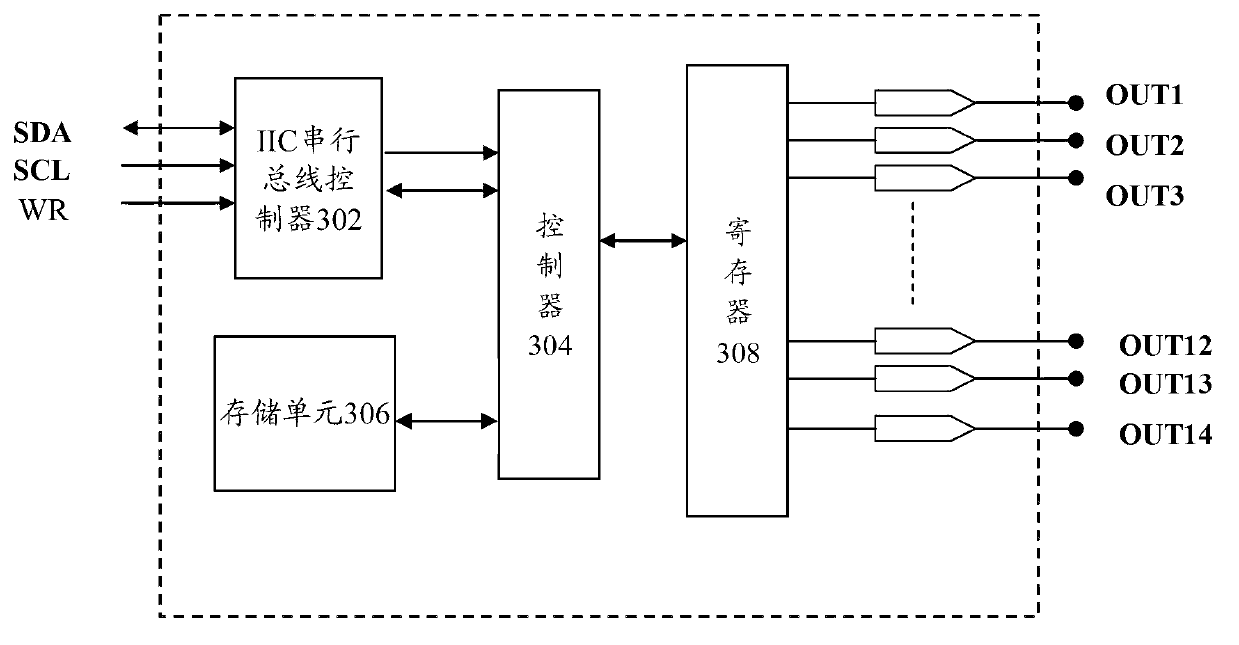
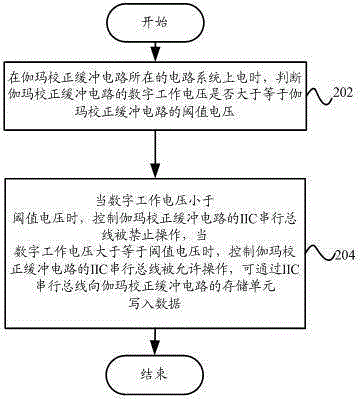
ActiveCN103345896APrevent rewritingStable outputStatic indicating devicesElectricityProcessor register
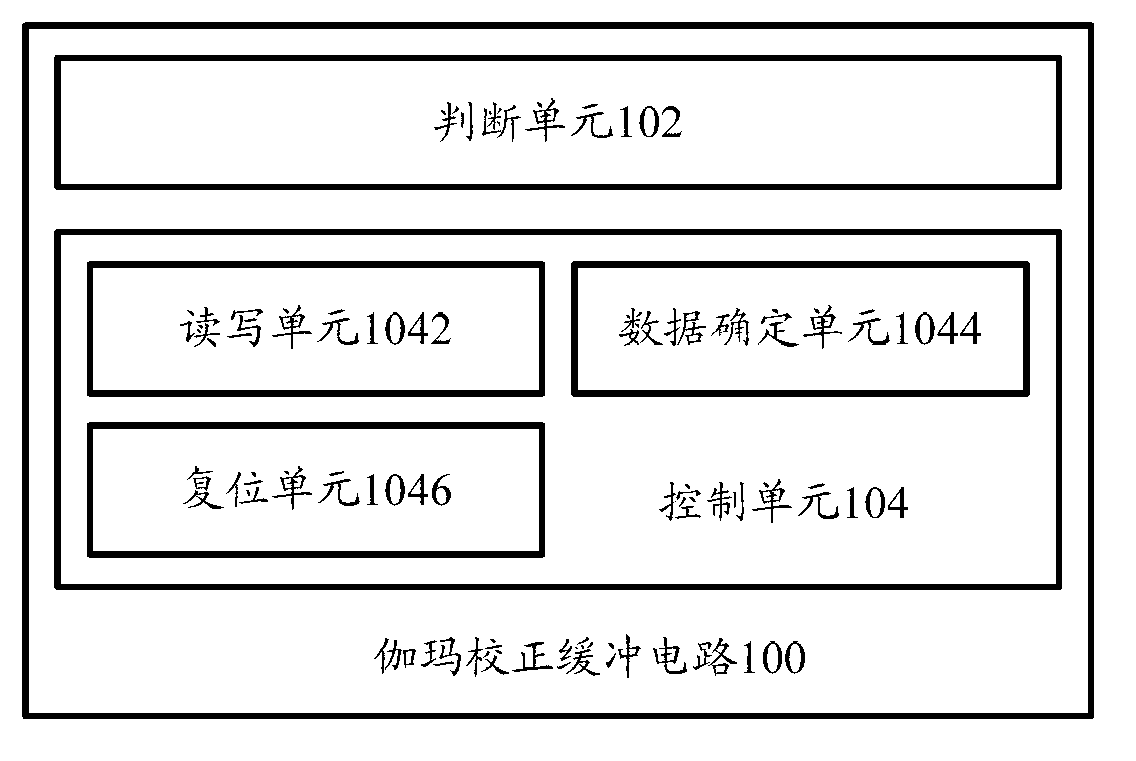
The invention provides a gamma correction buffer circuit which comprises a judgment unit and a control unit. According to judgment unit, when a circuit system where the gamma correction buffer circuit is located is powered on, whether digital working voltage of the gamma correction buffer circuit is larger than or equal to threshold value voltage of the gamma correction buffer circuit or nor is judged. According to the control unit, when the digital working voltage is determined to be smaller than the threshold value voltage, an IIC serial bus of the gamma correction buffer circuit is prohibited from being operated, data are not allowed to be written into a storage unit of the gamma correction buffer circuit through the IIC serial bus, and when the digital working voltage is larger than or equal to the threshold value voltage, the control unit controls the IIC serial bus to be allowed to be operated, and the data can be written into the storage unit of the gamma correction buffer circuit through the IIC serial bus. The invention further provides an anti-interference method and a display device. According to the technical scheme, external disturbance can be prevented from affecting the data in a register of the gamma correction buffer circuit, the capacity of resisting the disturbance of a system is enhanced, and stability of the system is improved.
Owner:HISENSE VISUAL TECH CO LTD
Memory data reading method, display device, and computer readable storage medium
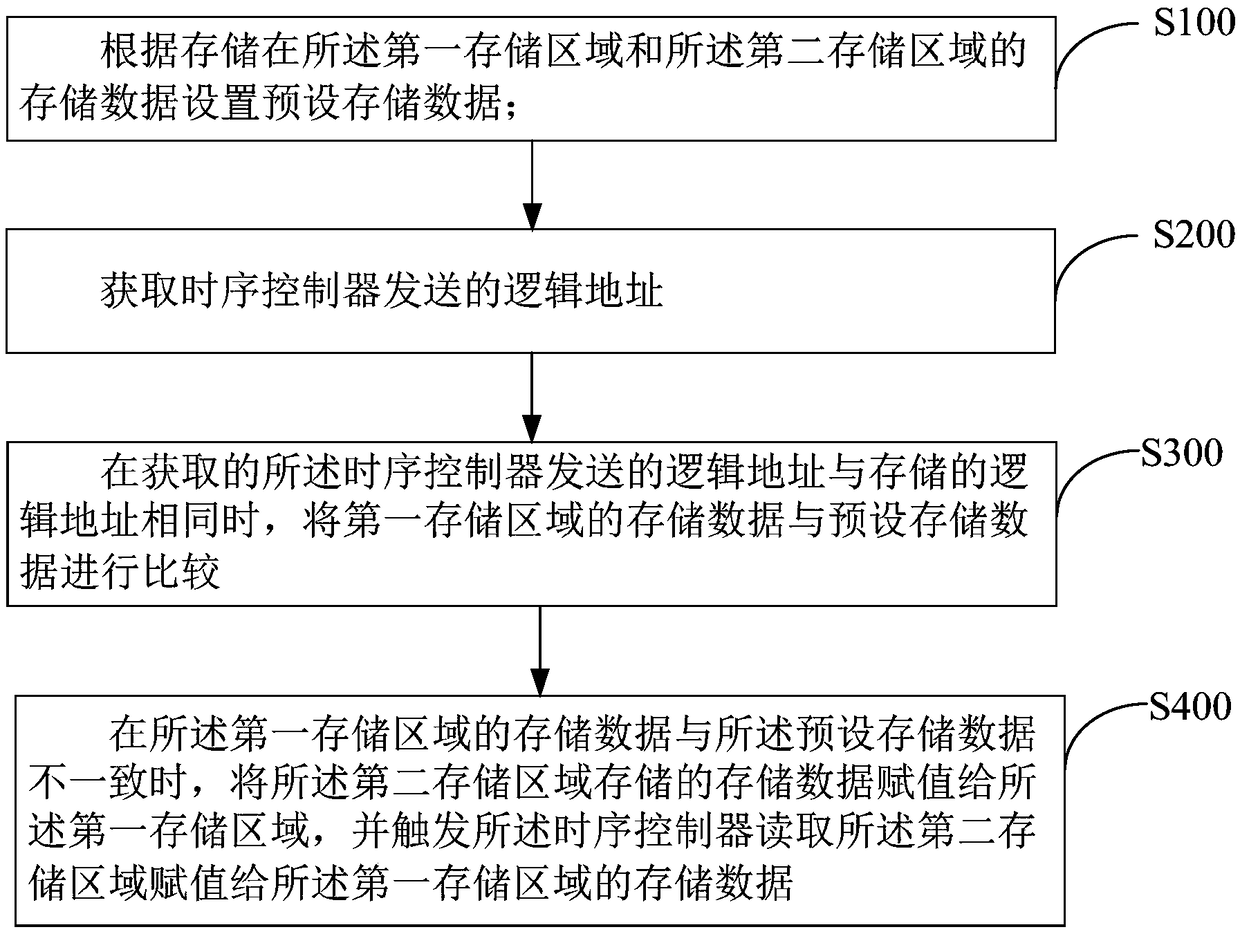
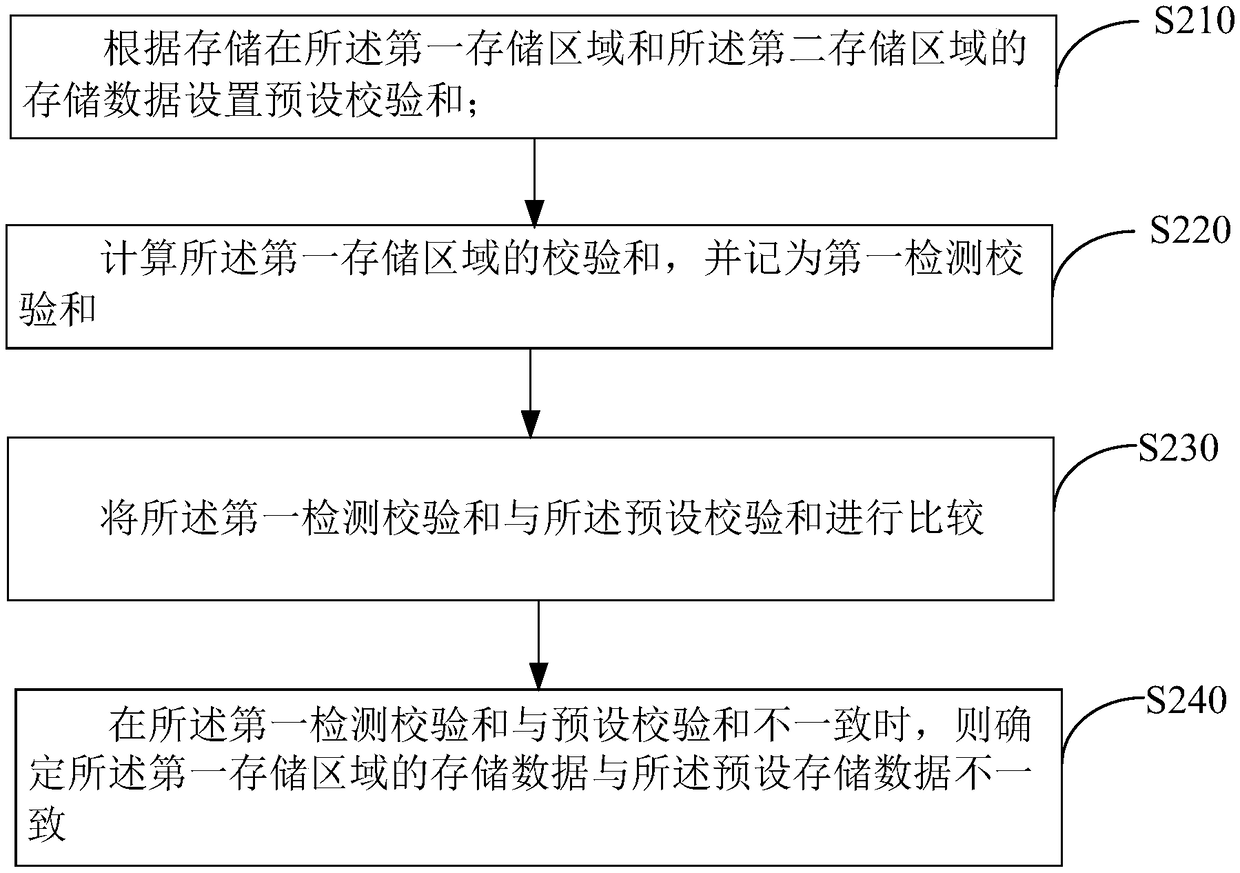
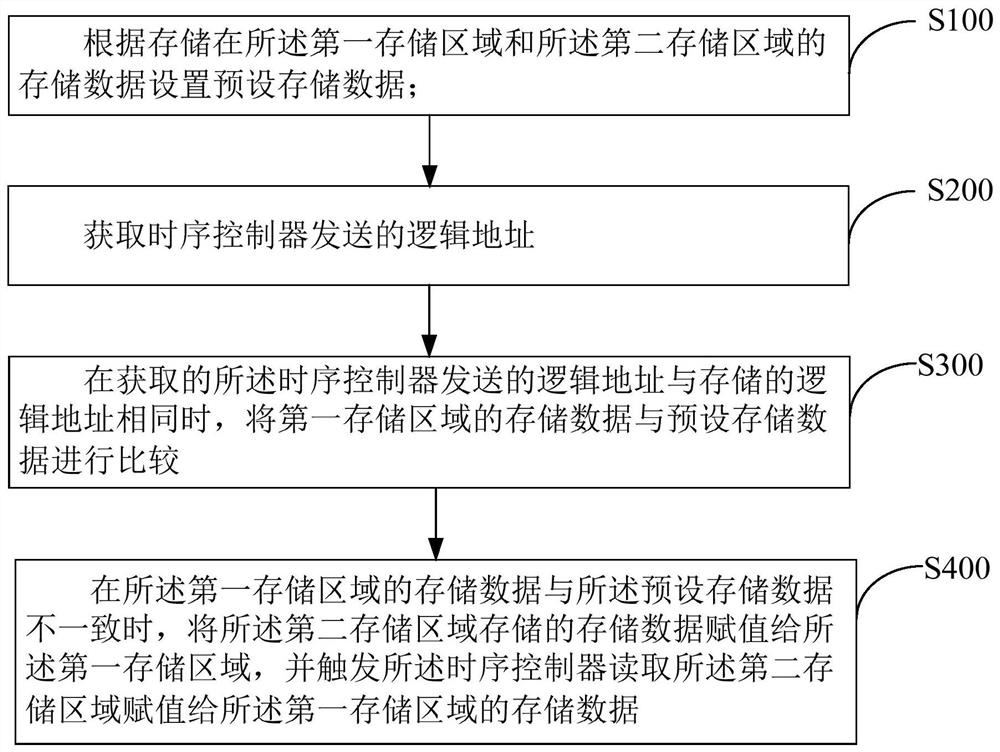
ActiveCN109388345APrevent rewritingInput/output to record carriersRedundant data error correctionLogical addressElectricity
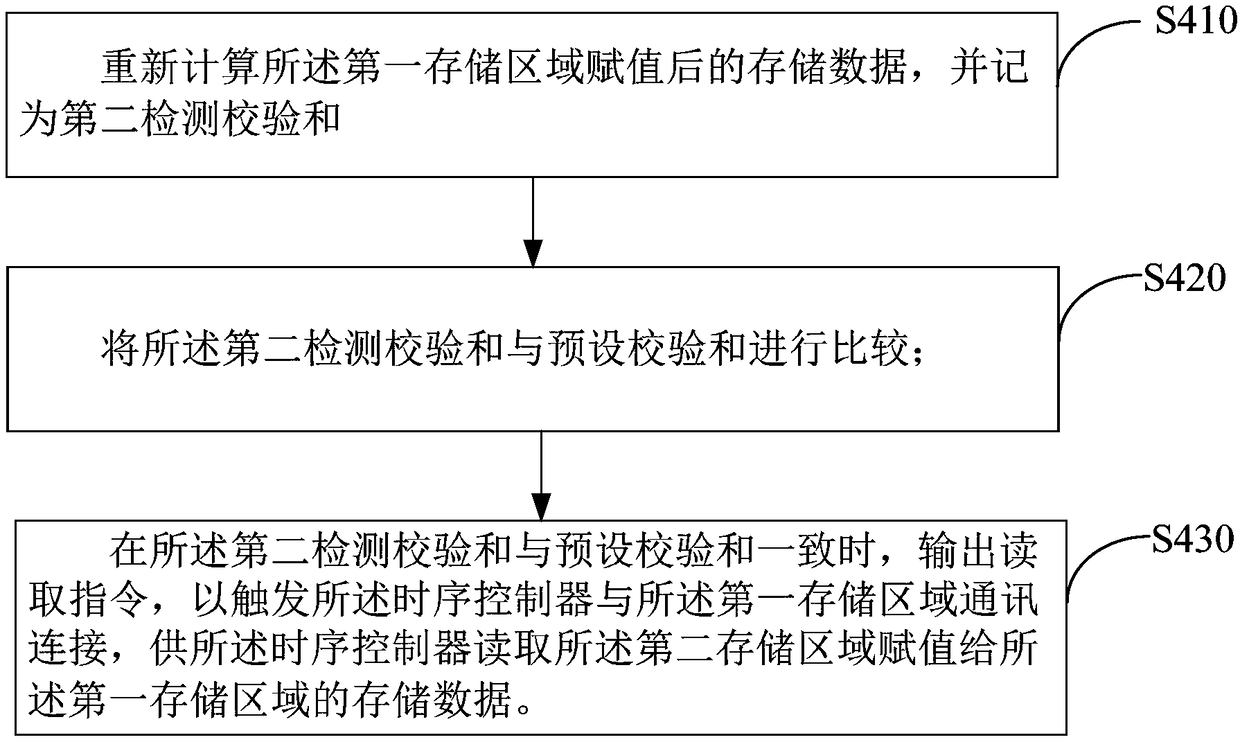
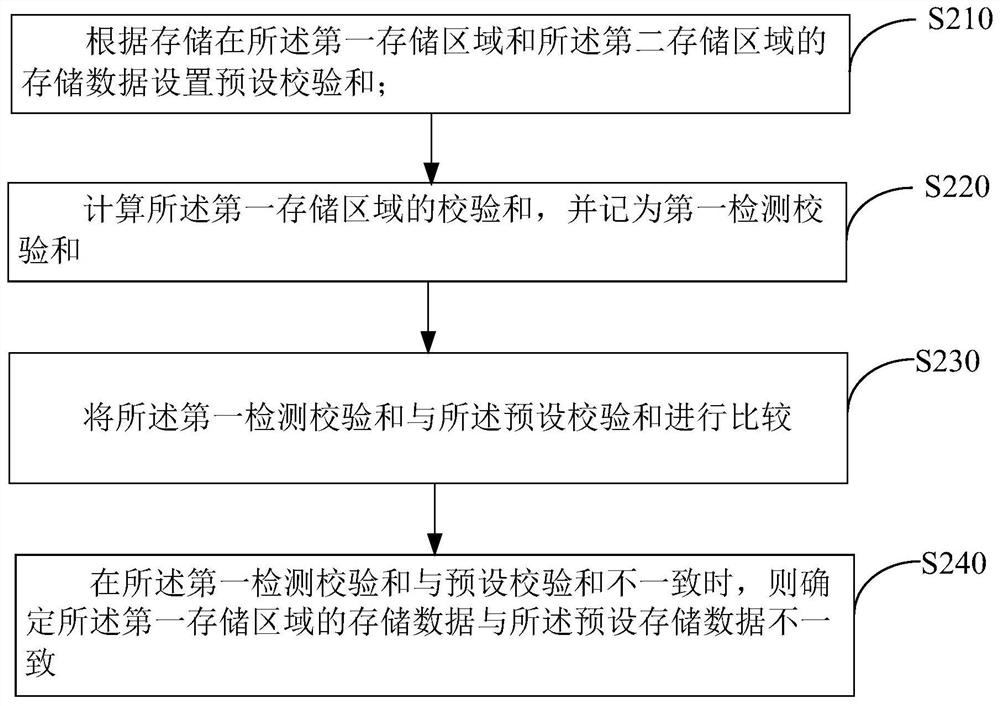
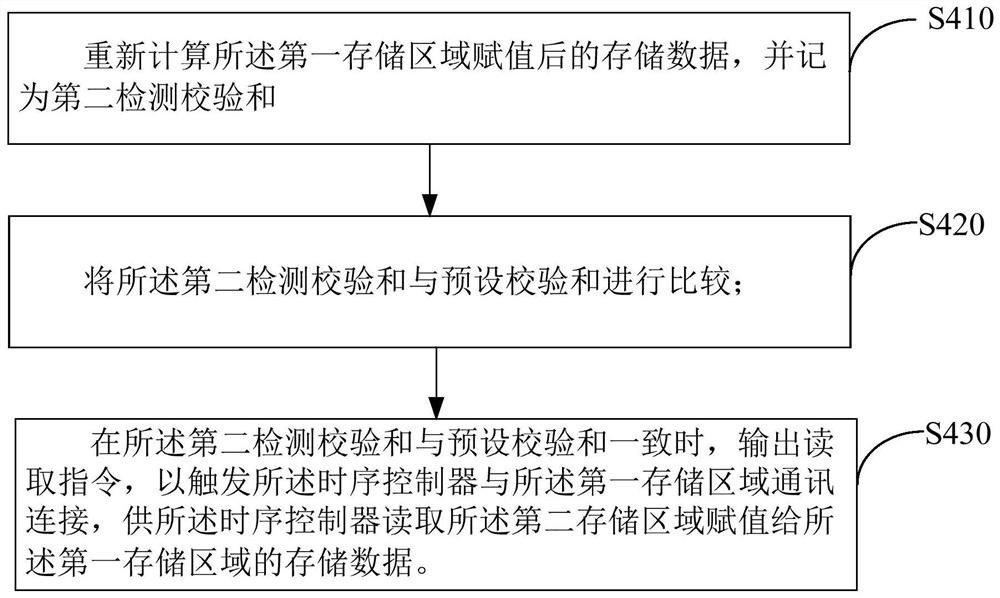
The invention discloses a memory data reading method of a memory, a display device, and a computer readable storage medium. The display device comprises a memory including a first storage area and a second storage area. The first storage area is electrically connected with a timing controller. The data reading method of the memory comprises the following steps: setting preset storage data according to the storage data stored in the first storage area and the second storage area; acquiring a logical address transmitted by the sequencer; When the logical address sent by the acquired timing controller is the same as the stored logical address, comparing the stored data of the first storage area with the preset storage data; when the stored data of the two storage areas do not coincide, assigning the storage data stored in the second storage area to the first storage area, and triggering the timing controller to read the stored data of the first storage area. The invention solves the problem that the timing control data stored in the memory is overwritten by the interference signal, and the display panel display picture ca not be driven normally.
Owner:CHONGQING HKC OPTOELECTRONICS TECH CO LTD +1
Memory electromagnetic interference protection circuit and vehicle electronic equipment
InactiveCN106463157AAvoid confusionPrevent rewritingDigital storageEMI or RFI carrier shieldingElectromagnetic interferenceSwitching signal
A memory electromagnetic interference protection circuit and vehicle electronic equipment are provided; in the daily work, a protection unit (2) outputs a switching signal to control the memory (1) in the write-protected state; when the contents of the memory (1) need to be updated online, the protection unit (2) outputs the switching signal to control the memory (1) in a non-write-protected state, thus preventing the contents of the memory (1) to be overwritten by the serious electromagnetic interference environment, and causing memory content chaos.
Owner:SHENZHEN STREAMING VIDEO TECH
Test system and method of display panel
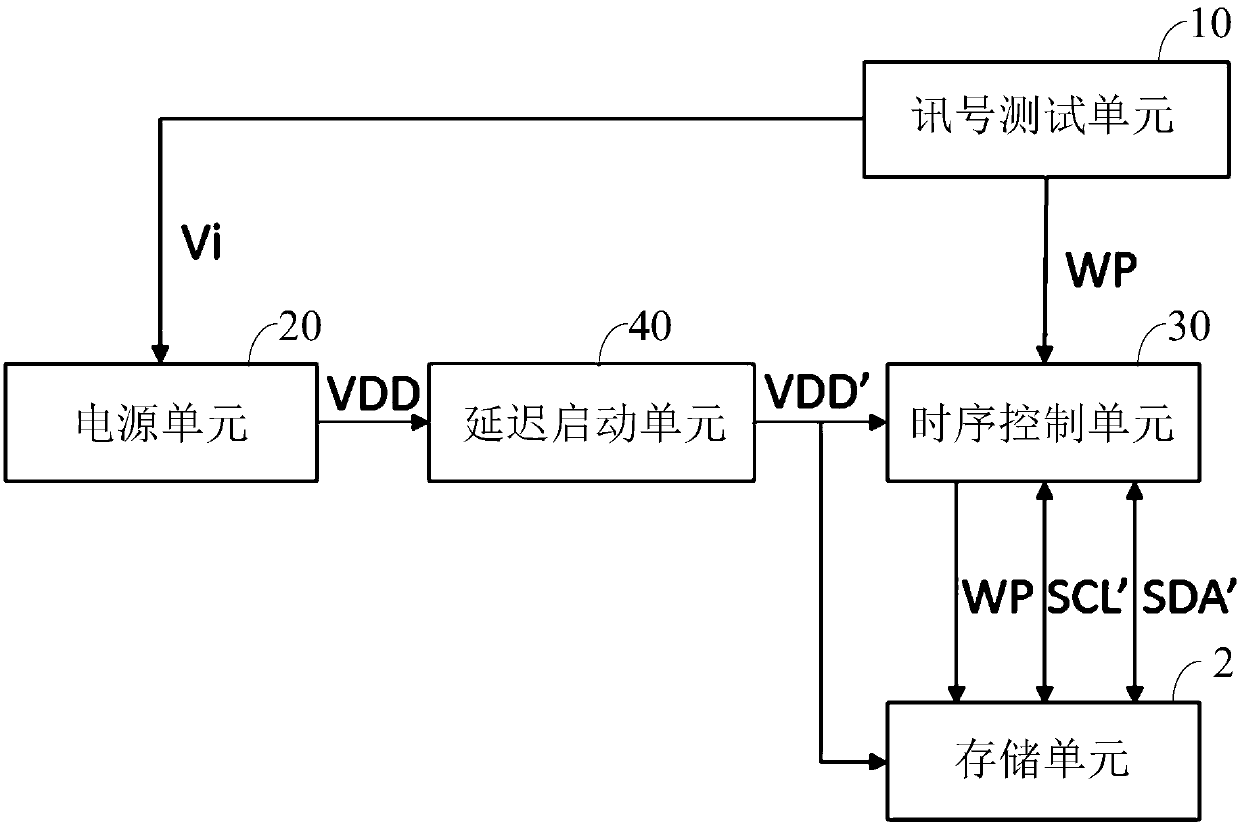
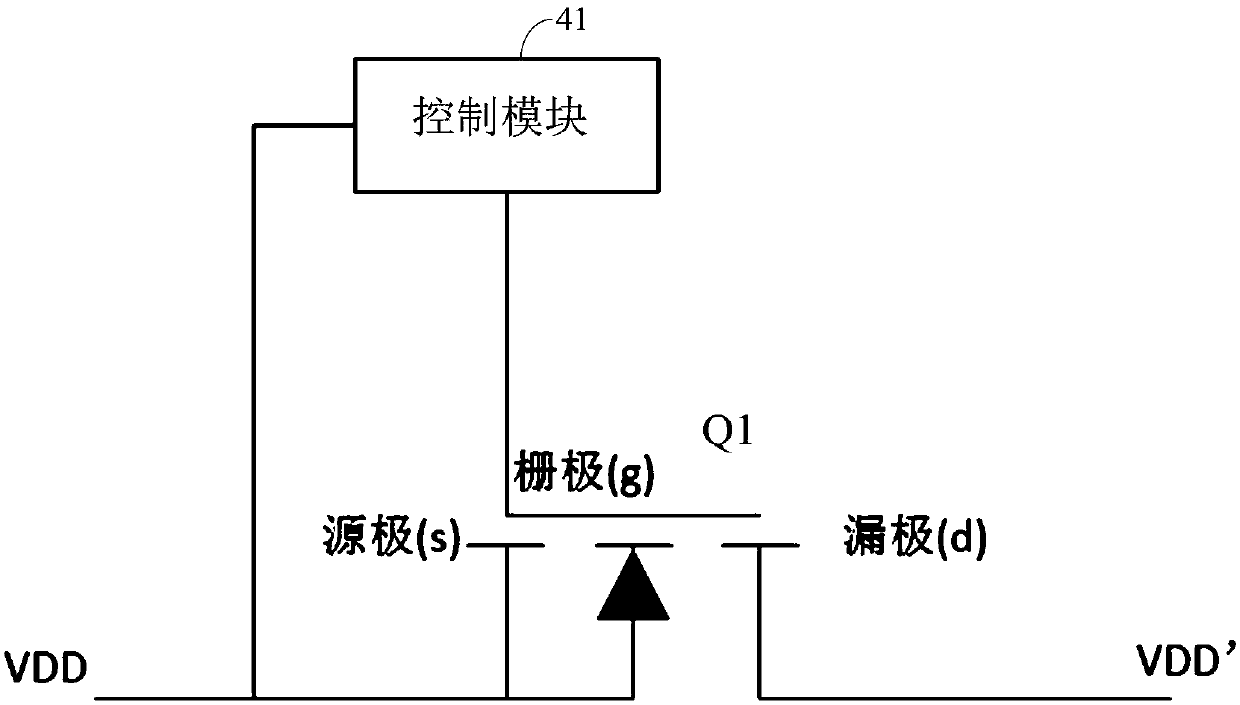
The invention is applicable to the technical field of display, and provides a test system and a test method of a display panel, and the test system of the display panel comprises a signal test unit, apower supply unit, a time sequence control unit and a delay starting unit. A delay starting unit is arranged between the power supply unit and the time sequence control unit, and the power supply unit is temporarily restarted again after power failure. A time delay signal is outputted so as to control the power supply state of the power supply unit to the time sequence control unit, so that the restart of the time sequence control unit after power failure caused by short restart of the power supply unit after power failure causes a problem that the memory cell cannot meet the rewriting condition, and the data of the memory cell is prevented from being rewritten.
Owner:HKC CORP LTD
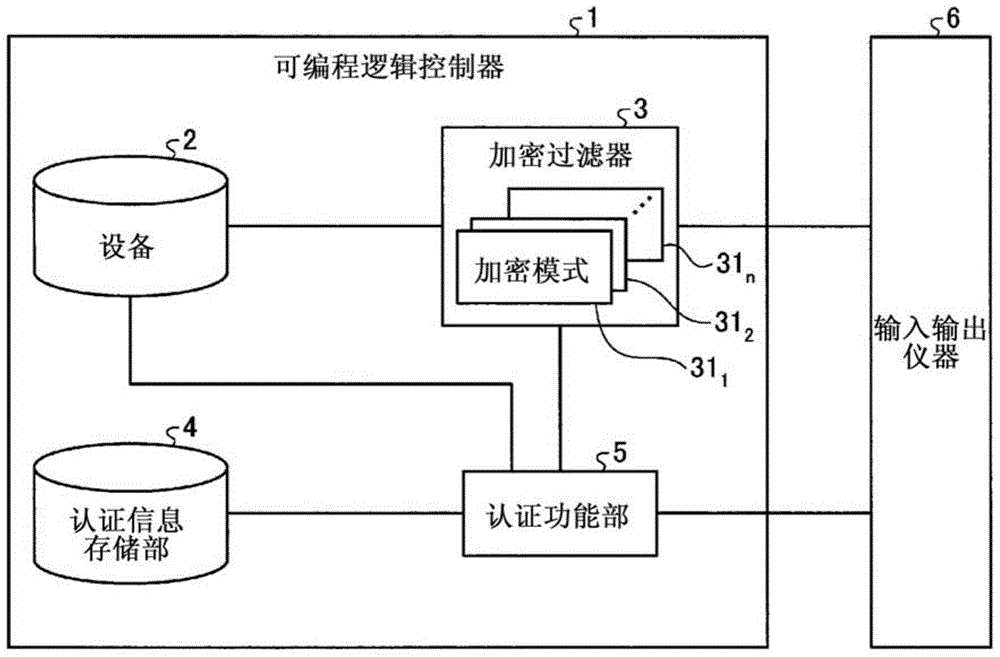
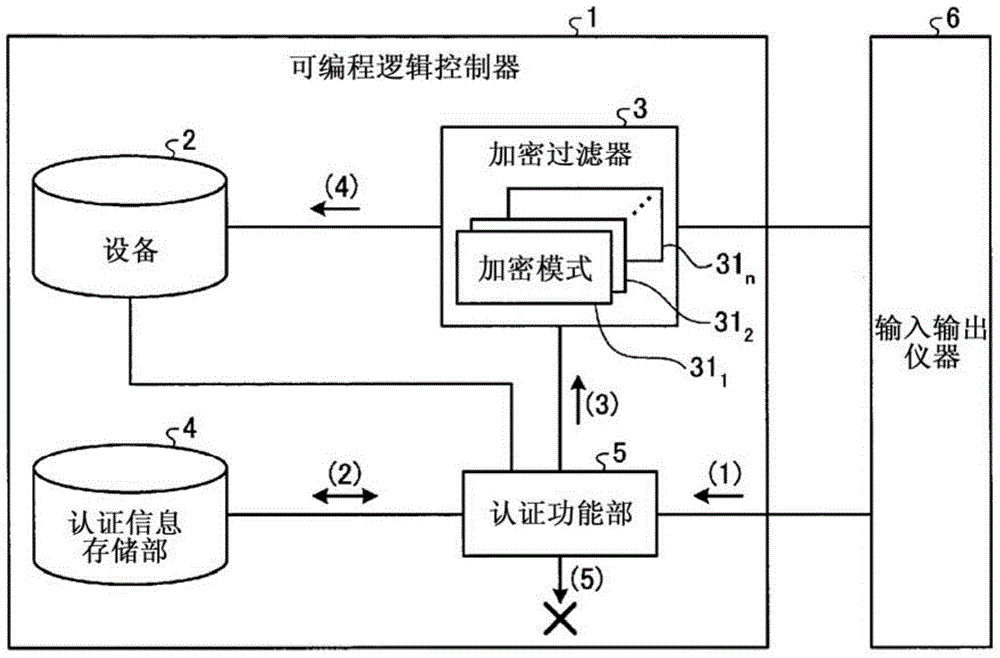
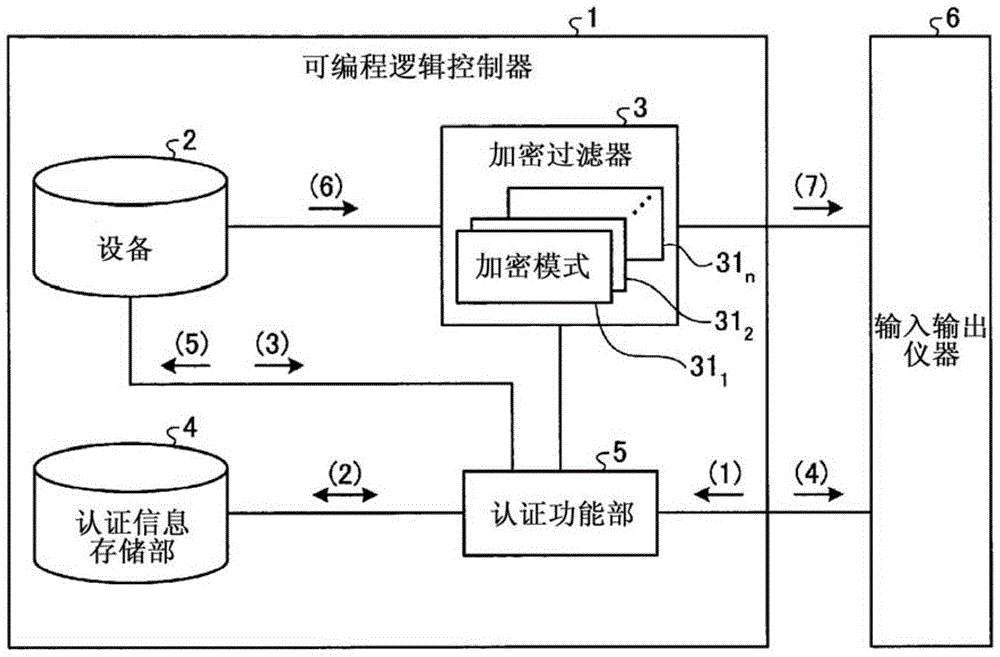
Programmable logic controller
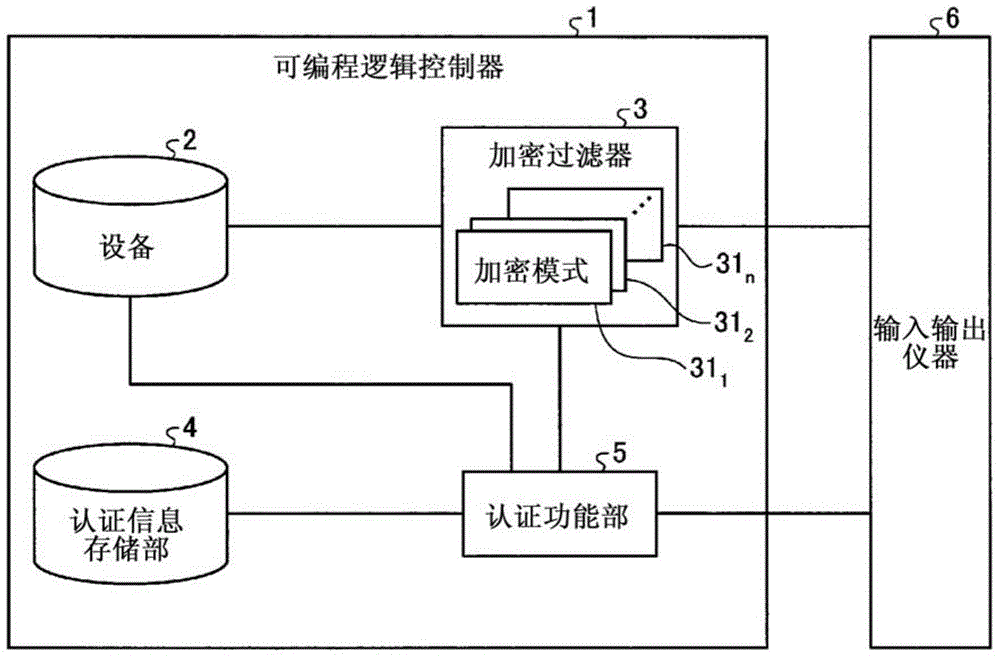
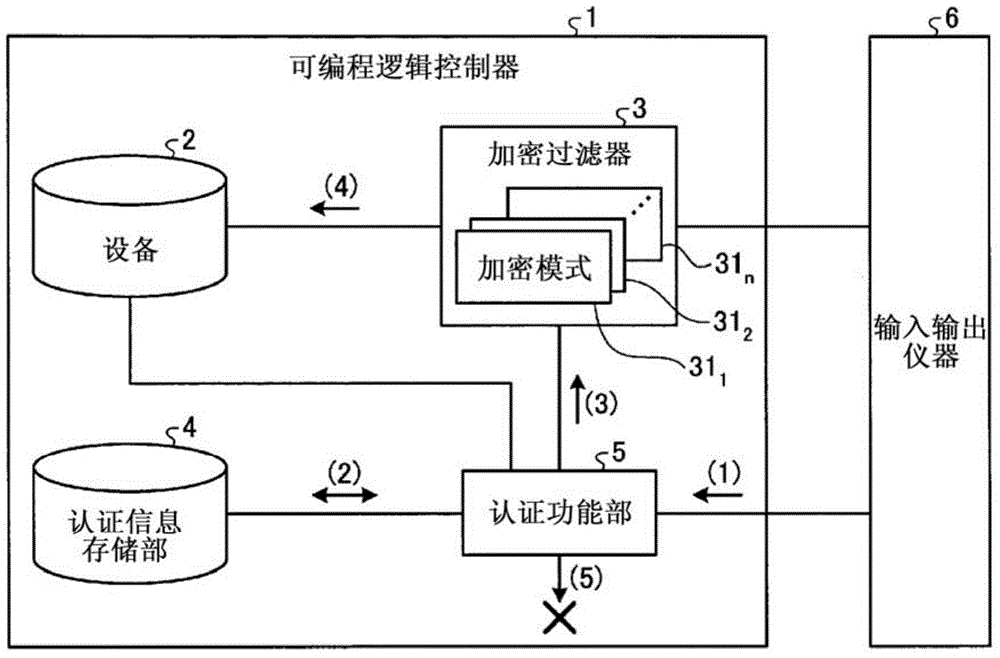
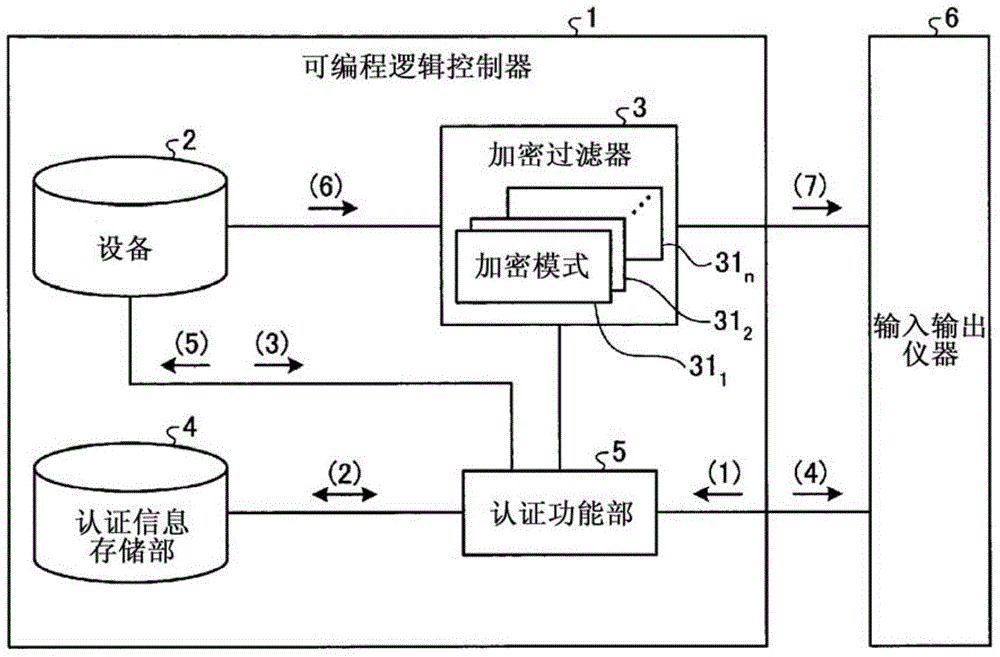
ActiveCN104428782APrevent information from being overwrittenPrevent rewritingDigital data protectionInternal/peripheral component protectionUser authenticationProgrammable logic controller
This programmable logic controller comprises: a device (2) that stores data; an authentication information storage unit (4) that stores authentication information; an authentication function unit (5) that performs user authentication on the basis of the authentication information; and an encryption filter (3) that includes a plurality of encryption patterns (311-31n), one of which is set in advance by a user for encryption processing. The authentication function unit (5) performs user authentication when there is a request from an external instrument to write data into the device, and if the user authentication is successful, the authentication function unit makes the encryption filter (3) perform encryption processing on the data to be written into the device (2) by using the encryption pattern (311-31n) set in advance by the user, and then writes the data into the device (2). If the user authentication fails, the authentication function unit makes the encryption filter (3) perform encryption processing on the data to be written into the device (2) by using an encryption pattern (311-31n) that is different from the pattern set in advance by the user, and then writes the data into the device (2).
Owner:MITSUBISHI ELECTRIC CORP
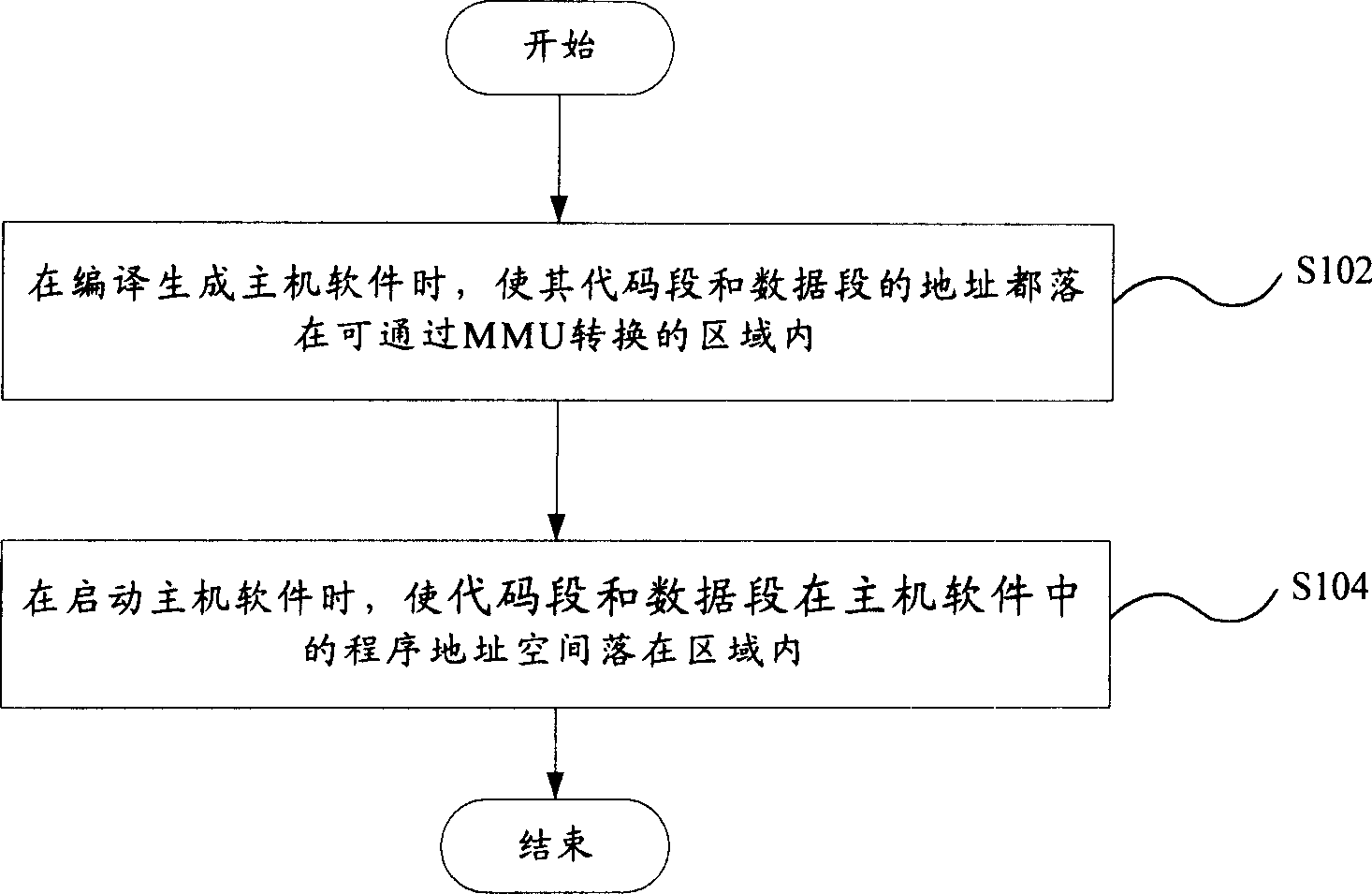
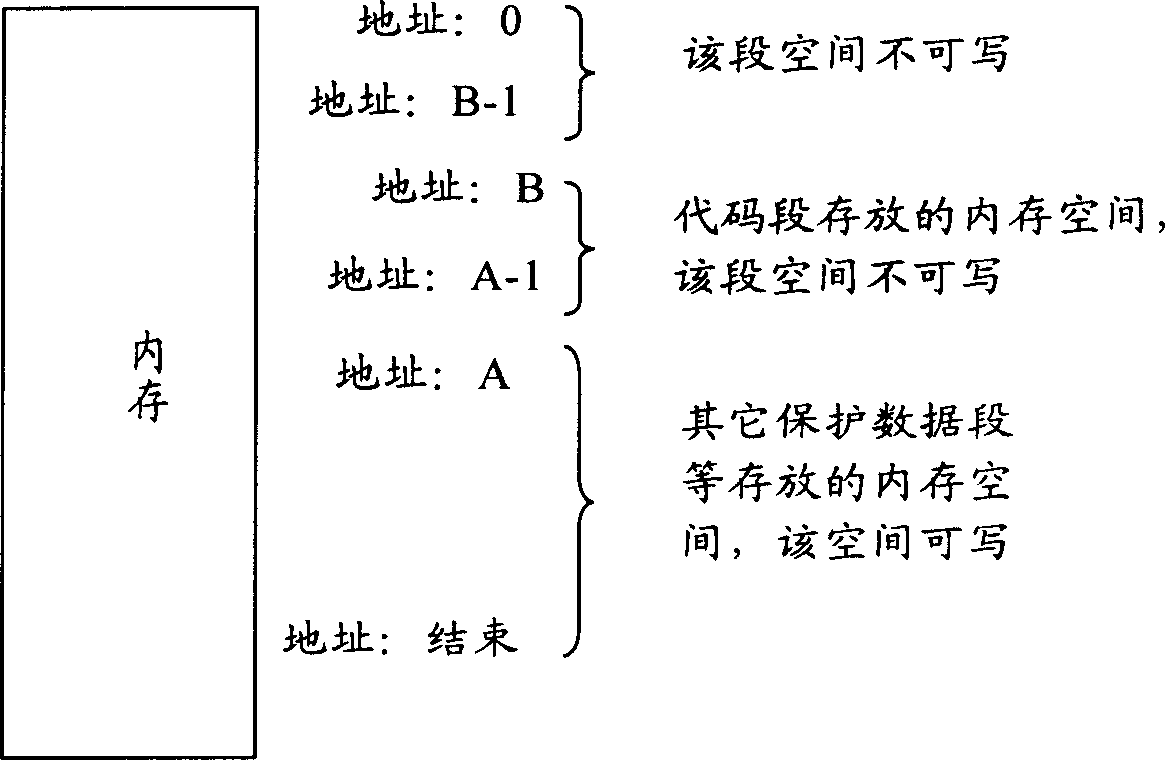
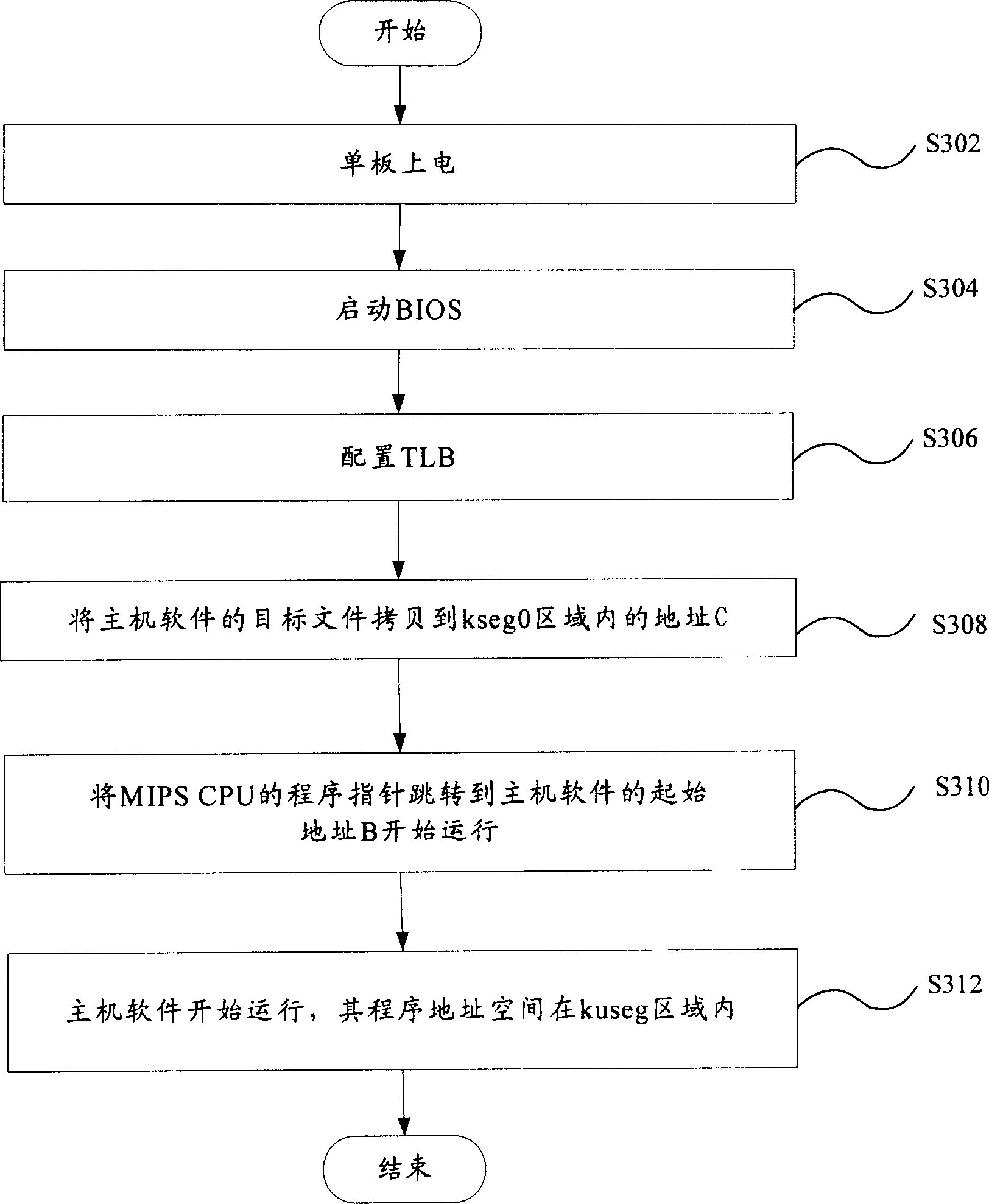
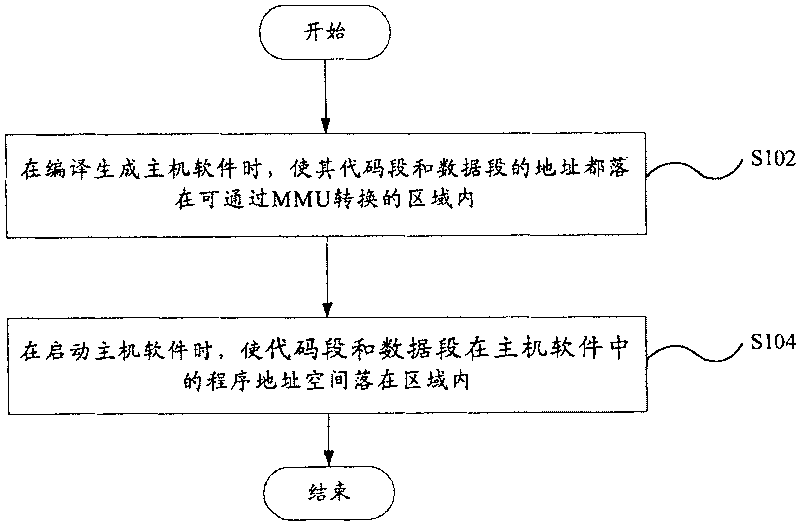
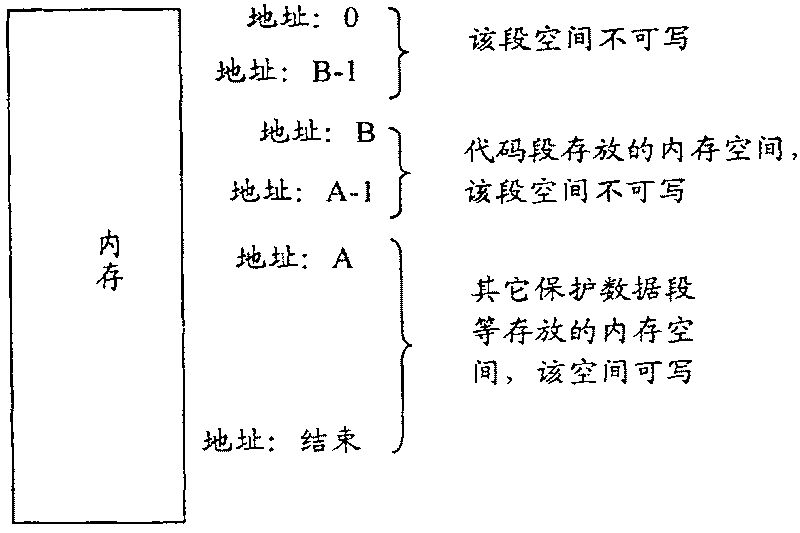
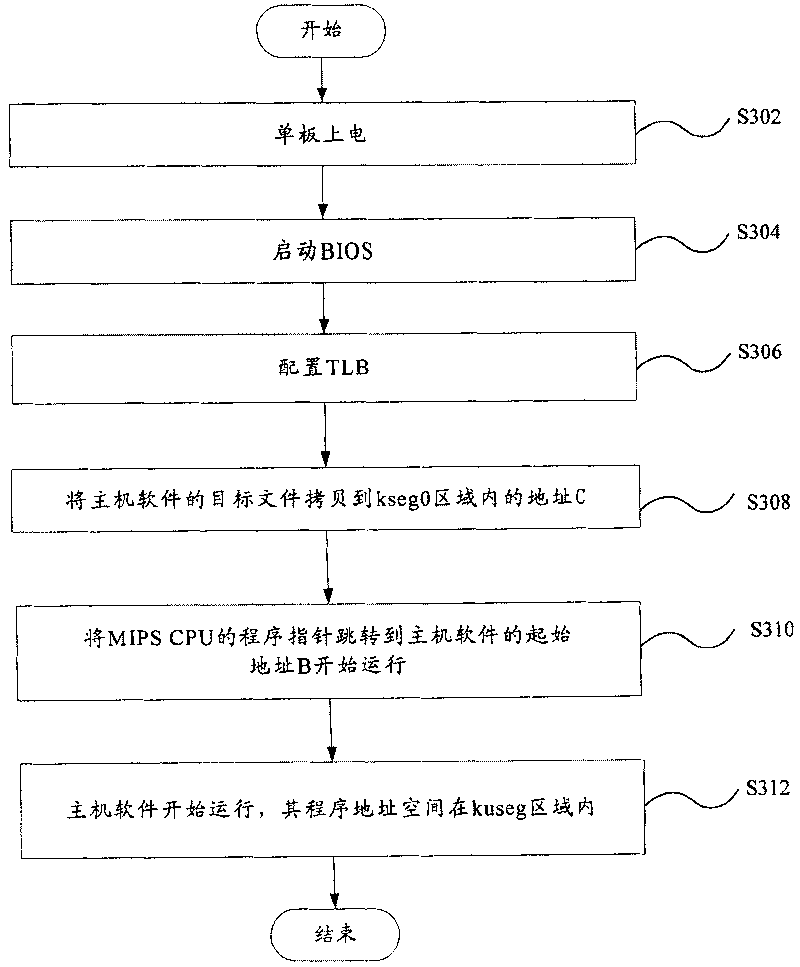
Method and device of protecting code segment in use for MIPS system
InactiveCN1916853APrevent rewritingImprove robustnessSoftware testing/debuggingProgram loading/initiatingInternal memoryManagement unit
A method for protecting code section used in MIPS system includes making addresses of code section and data section be both placed in region being able to be converted by internal memory management unit in MIPS system when host software is compiled and generated, making code section and data section be placed in said region in program address space of host software when host software is started up. The protection device for realizing said method is also disclosed.
Owner:HUAWEI TECH CO LTD
Communication architecture of display panel and display panel
ActiveCN111477154APrevent rewritingStatic indicating devicesEnergy efficient computingComputer hardwareComputer architecture
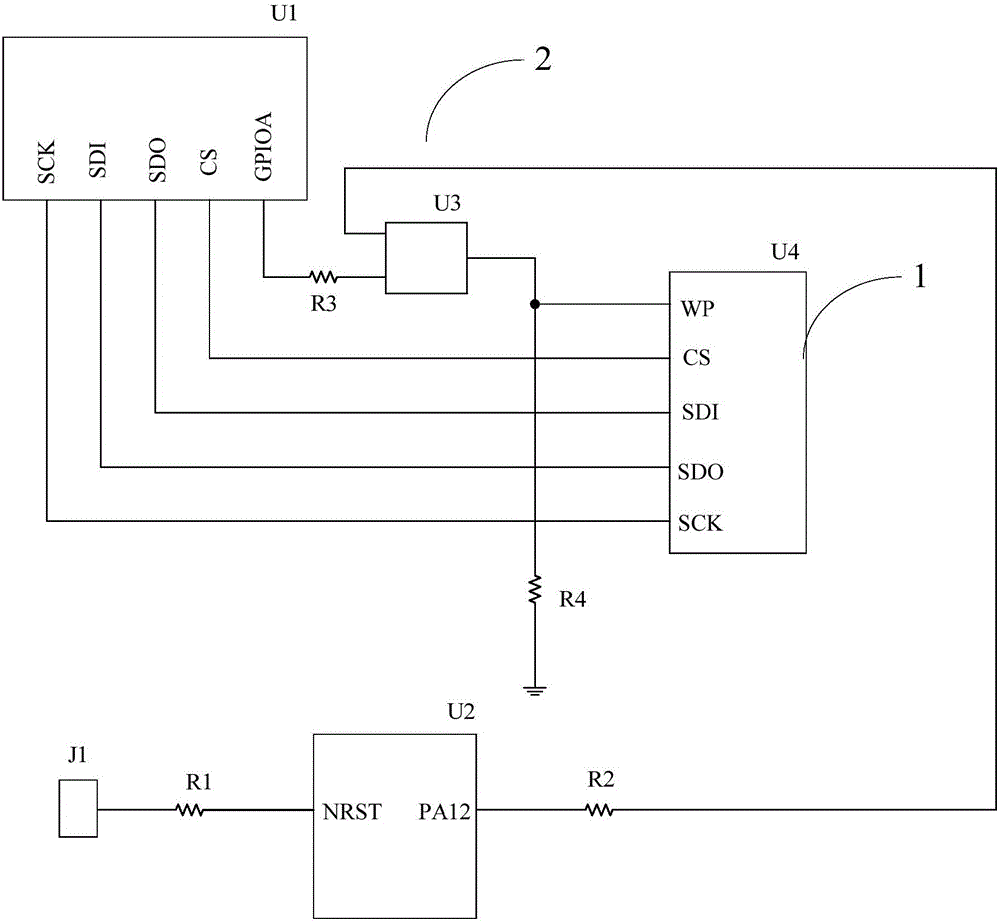
The invention discloses a communication architecture of a display panel. By arranging a time delay circuit, the write-in protection signal can delay the opening of the bus switch after flowing throughthe delay circuit until the process of checking codes in the power supply management integrated circuit is finished, the bus switch cannot be opened when the time sequence controller is checked, andthe checked communication content of the memory is prevented from being rewritten.
Owner:TCL CHINA STAR OPTOELECTRONICS TECH CO LTD
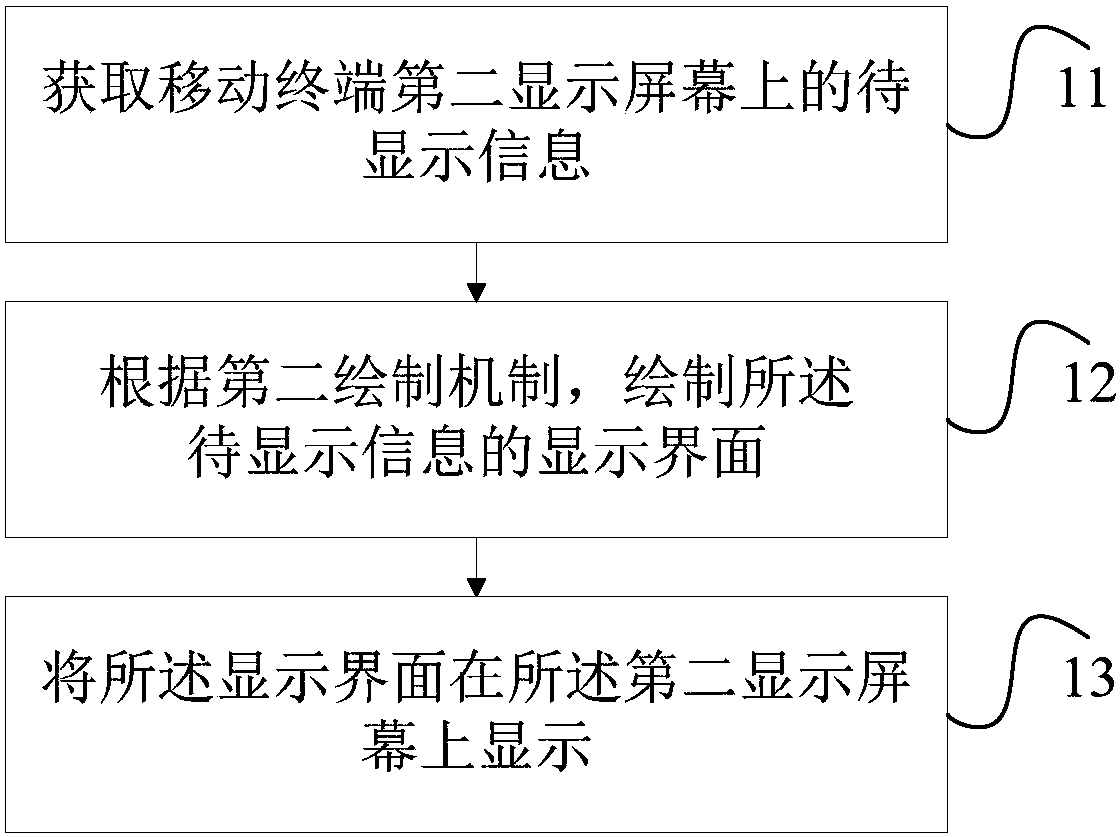
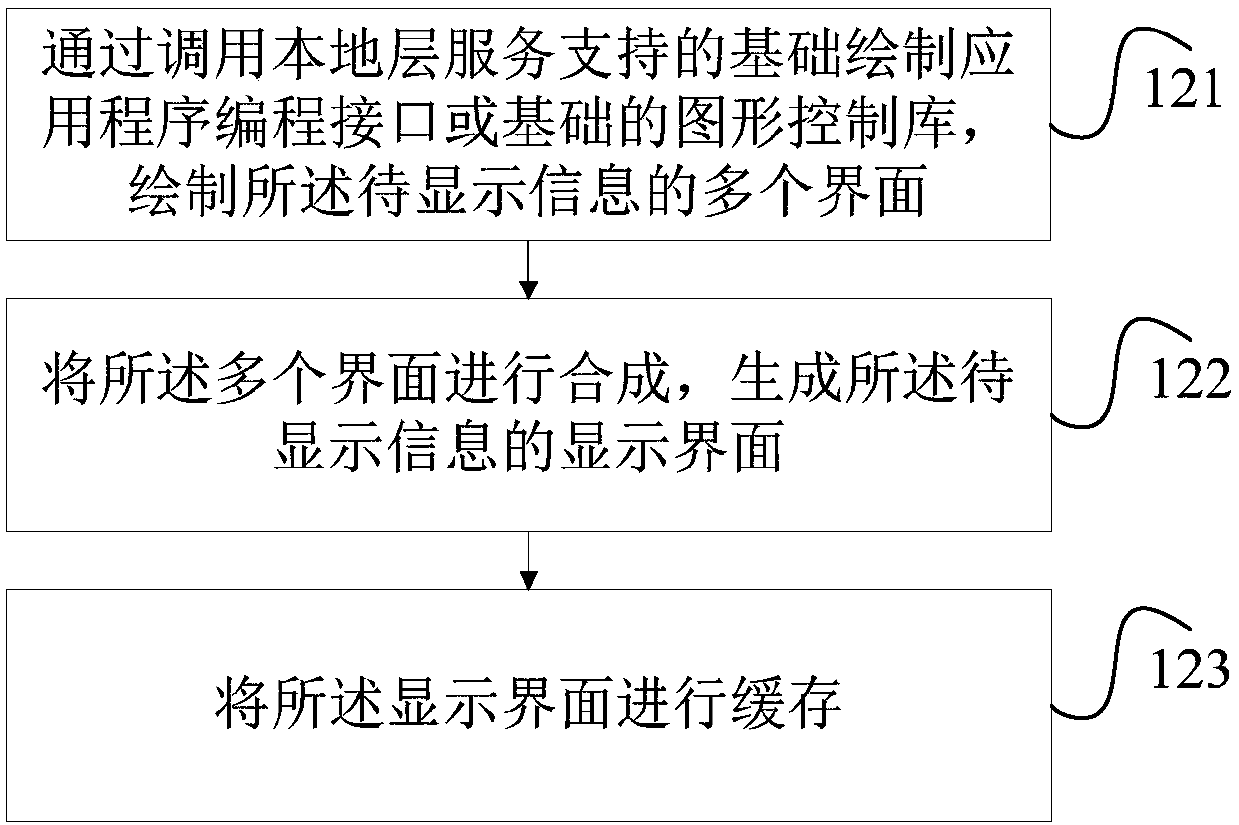
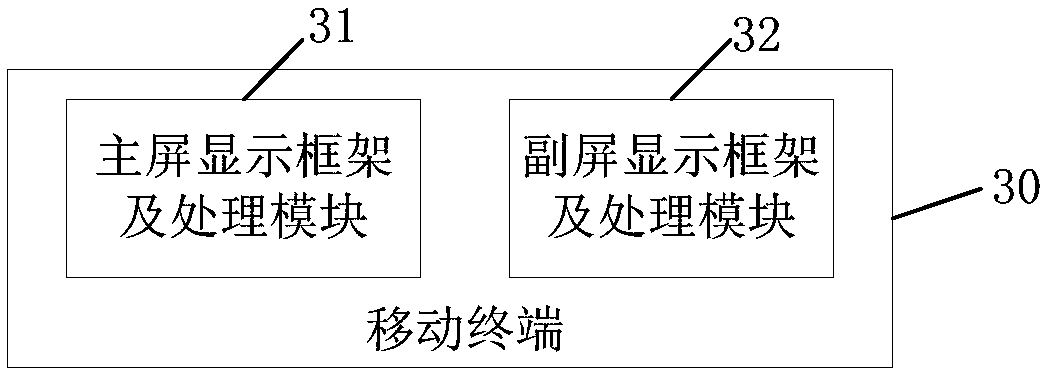
Screen displaying method and mobile terminal
InactiveCN107817960APrevent rewritingRealize heterogeneityDigital output to display deviceOn-screen displayMobile phone
The invention provides a screen displaying method and a mobile terminal. The screen displaying method is applied to the mobile terminal. The mobile terminal comprises a first display screen and a second display screen. The method comprises the steps that information to be displayed on the second display screen of the mobile phone is acquired; according to a second drawing mechanism, a display interface of the information to be displayed is drawn, wherein the second drawing mechanism and a first drawing mechanism which draws a display interface of the first display screen are different drawingmechanisms; the display interface is displayed on the second display screen. According to the technical scheme, a secondary screen of the mobile terminal is separately displayed and is independent ofa main screen, display of the secondary screen is controlled by adopting a mode which is different from a mode of the main screen, and rewriting for a system layer of the mobile terminal is avoided, and different display of the main screen and the secondary screen is achieved.
Owner:ZTE CORP
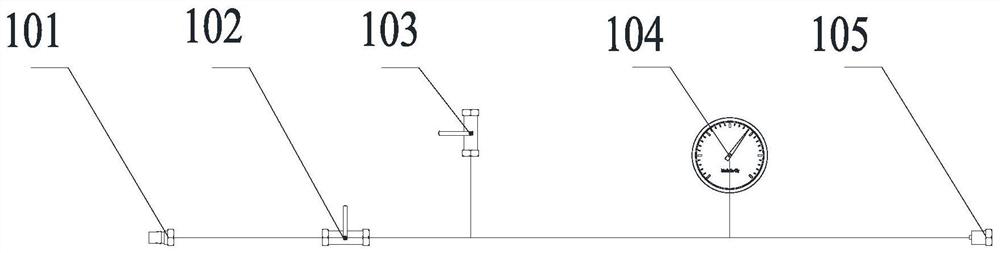
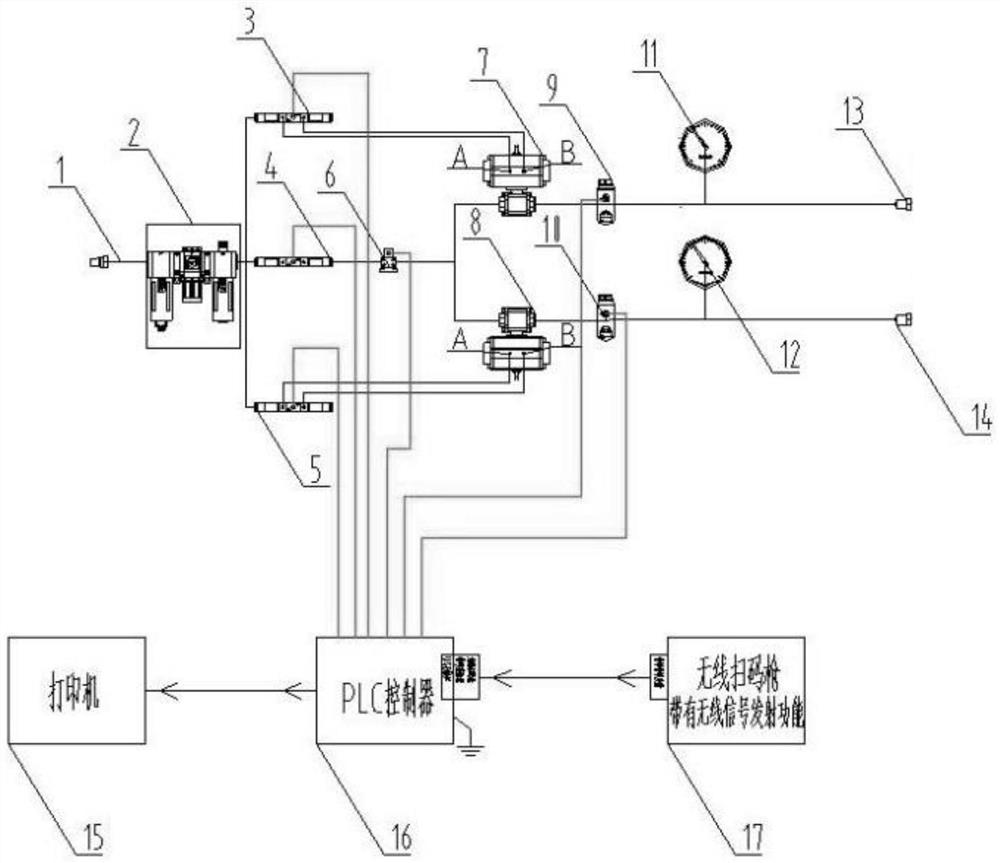
Automatic testing device for air tightness of bogie brake pipeline
PendingCN112179583AIncrease productivityAvoid artificial rewritingMeasurement of fluid loss/gain rateProgramme control in sequence/logic controllersBall valveTest program
The invention relates to an automatic testing device for the air tightness of a bogie brake pipeline. The automatic testing device comprises a quick plug, a pneumatic triple piece, a second electromagnetic switch control valve, an electromagnetic proportional control valve, a first ball valve controller, a first pressure sensor, a first pressure gauge and a first transition joint which are connected in sequence, wherein the electromagnetic proportional control valve is further sequentially connected with a second ball valve controller, a second pressure sensor, a second pressure gauge and a second transition connector; the quick plug is connected with a wind source; and the first transition joint and / or the second transition joint can be respectively connected with the brake pipeline. Theautomatic testing device for the air tightness of the bogie brake pipeline can compile an air tightness test program according to different brake pipeline air tightness test technical conditions, complete an air tightness test according to a set test program, and automatically print a test record after the test is finished.
Owner:CRRC CHANGCHUN RAILWAY VEHICLES CO LTD
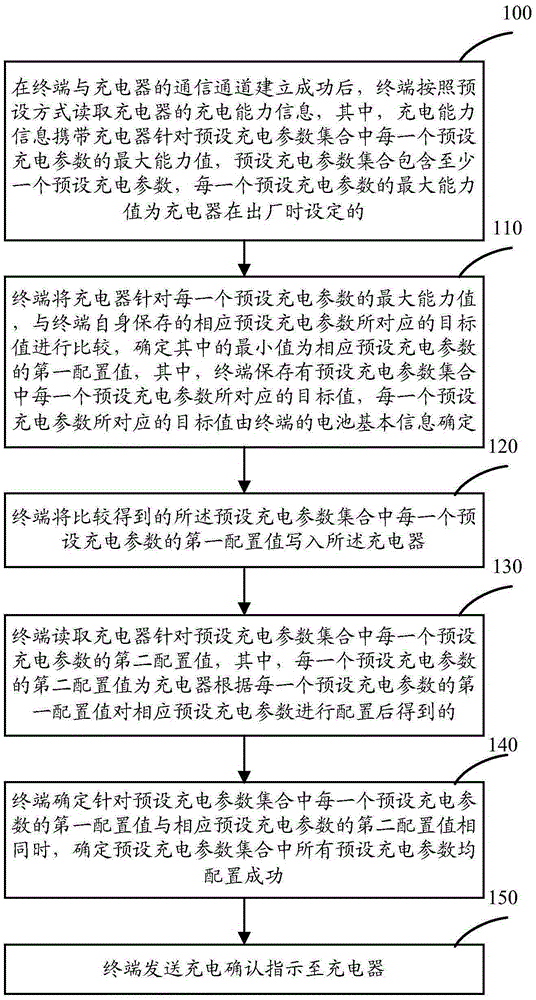
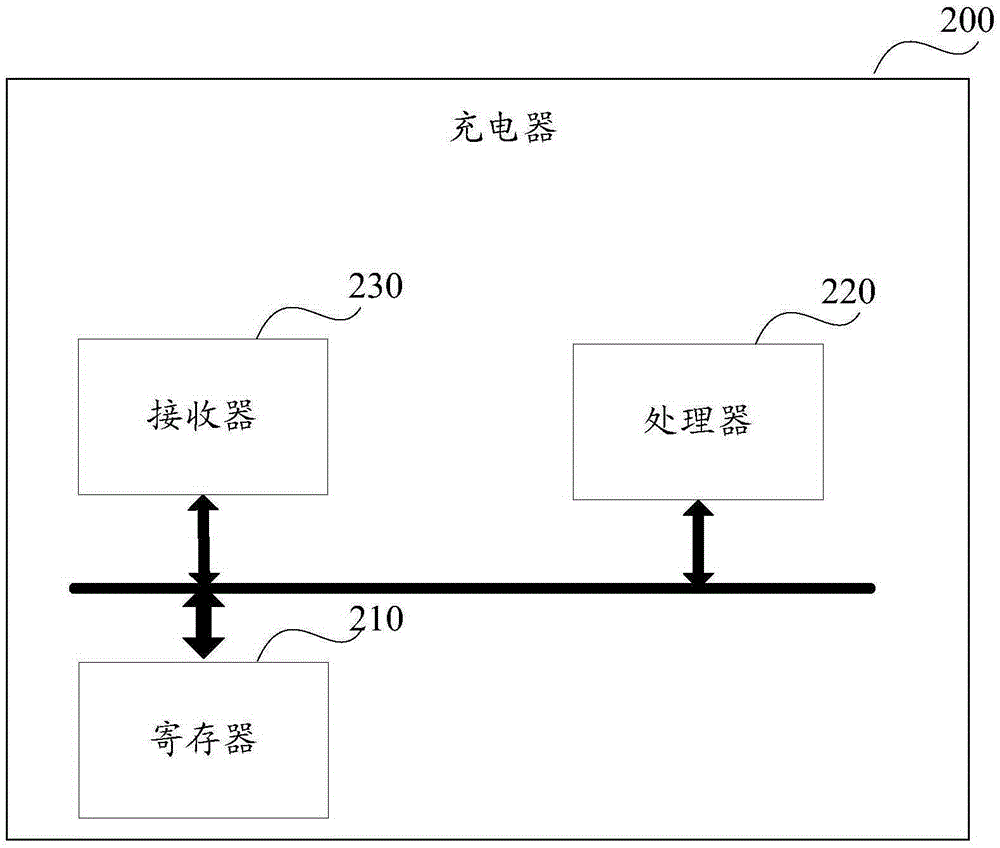
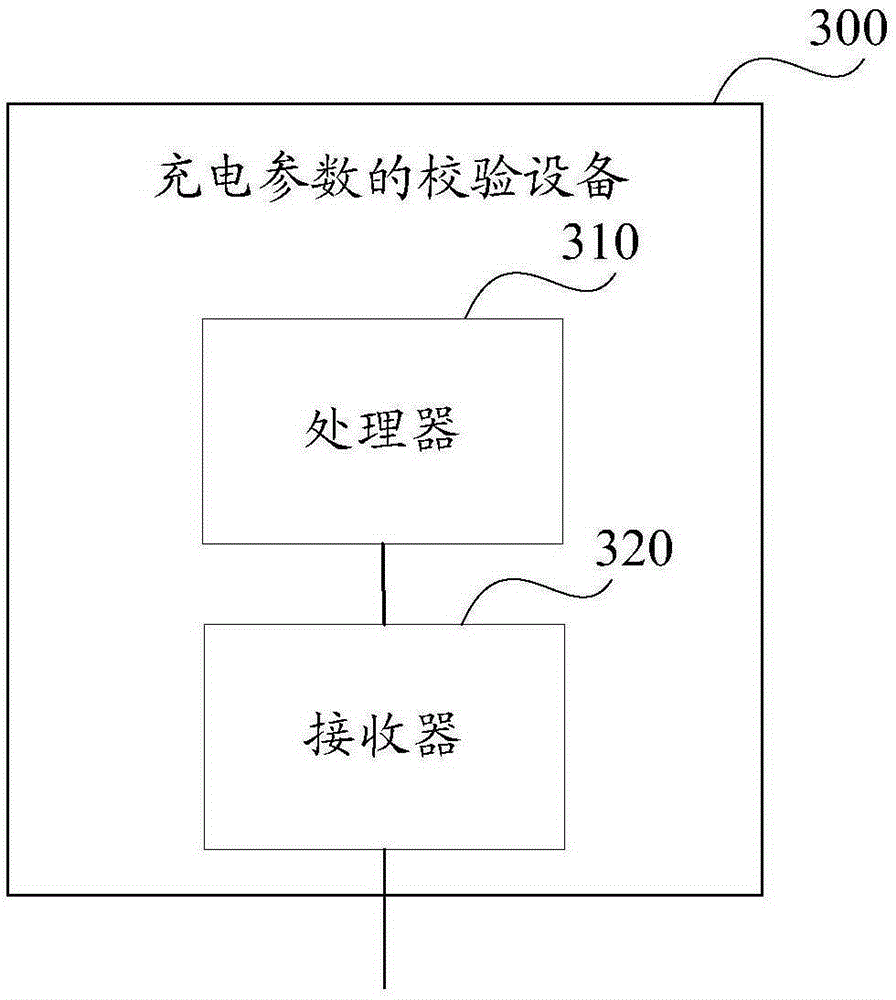
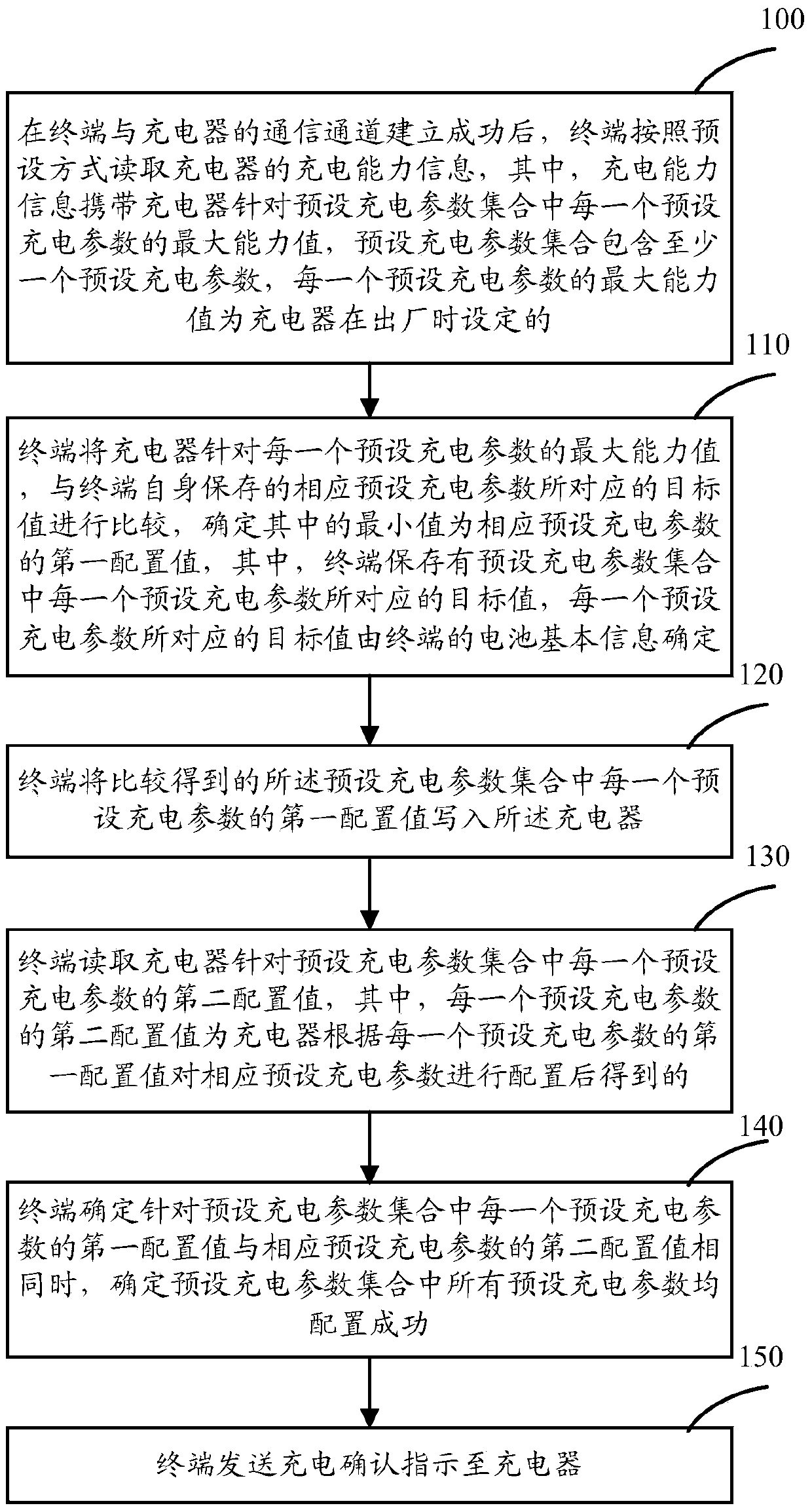
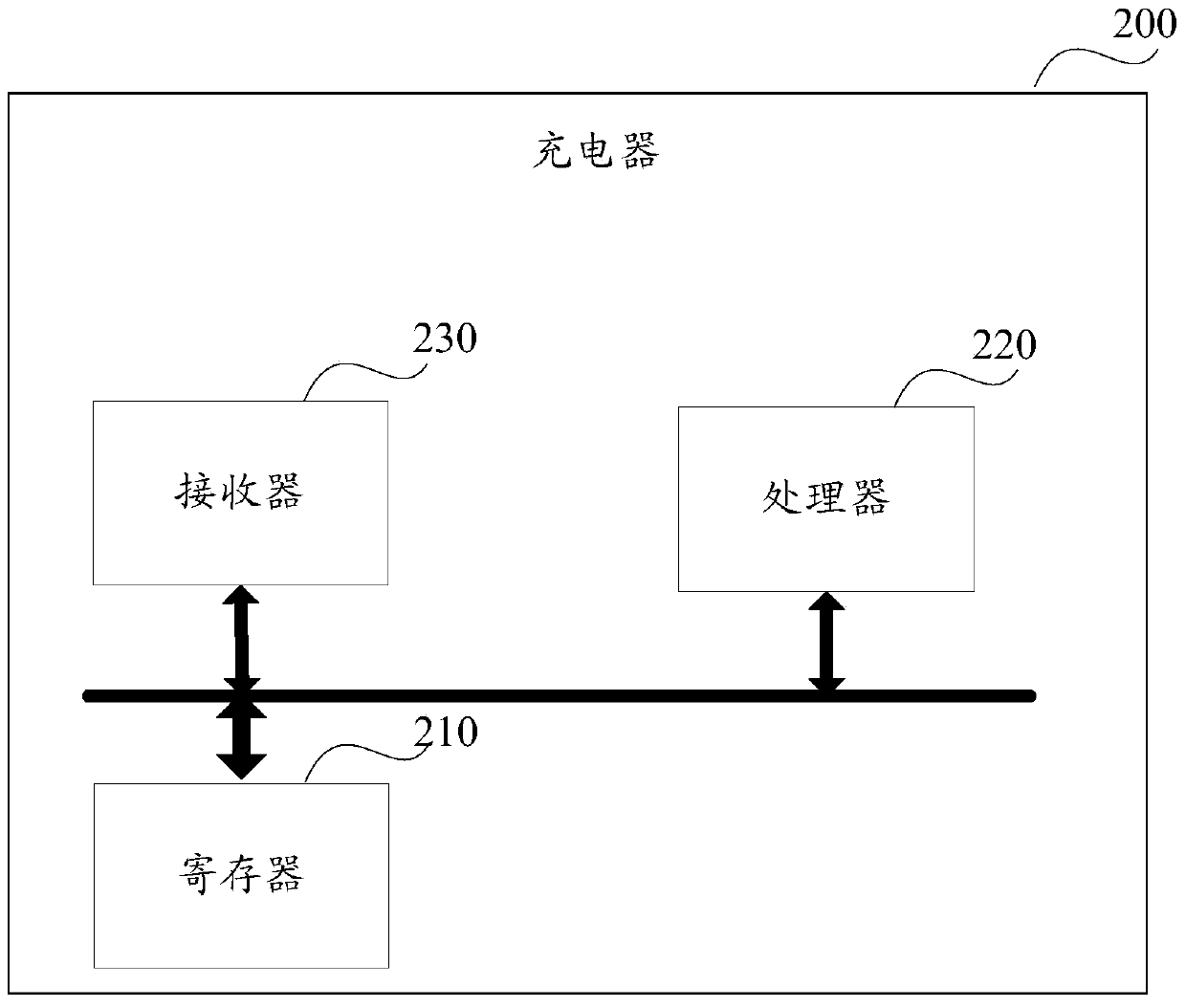
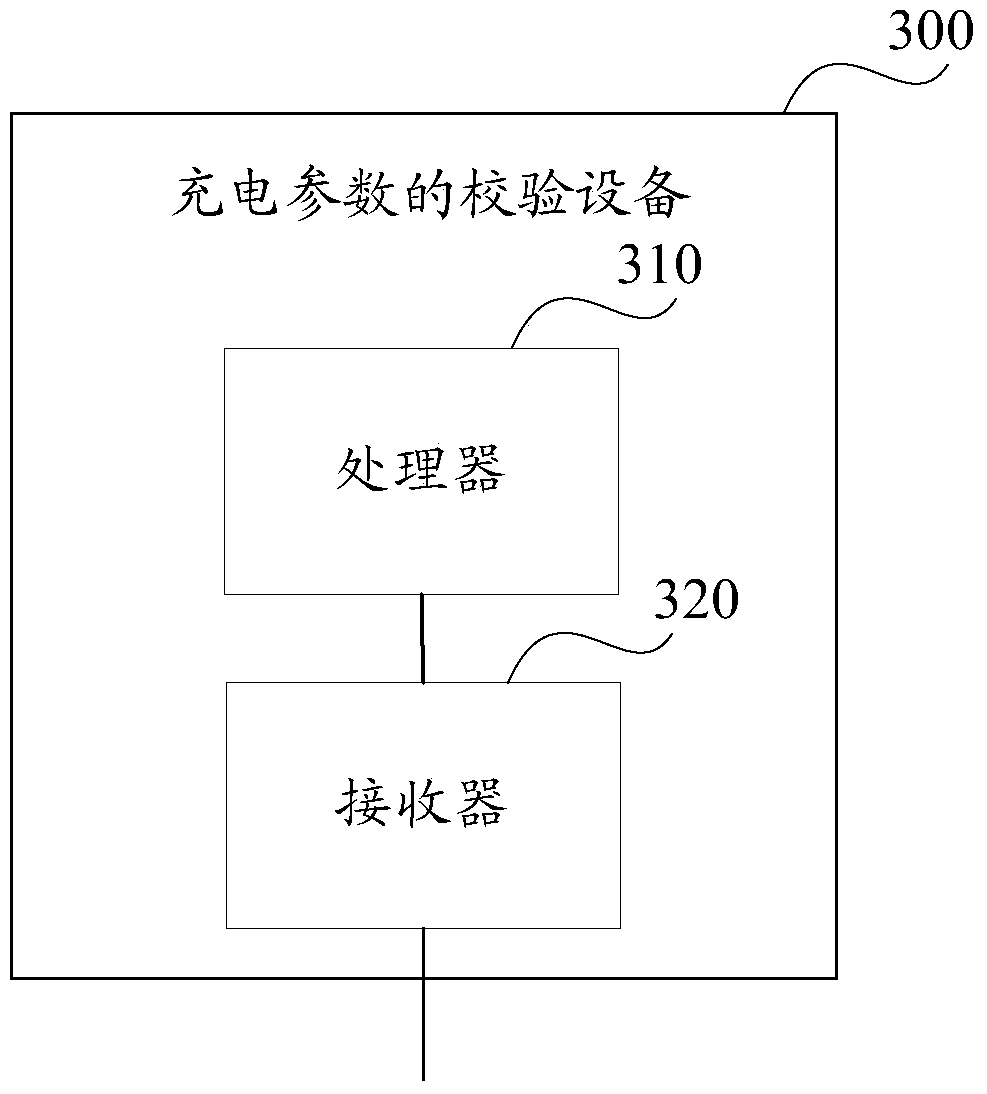
Charging parameter verification method and equipment, and charger
ActiveCN106684954APrevent rewritingAvoid security issuesSignal allocationElectric powerEngineeringElectrical and Electronics engineering
The invention relates to the technical field of charging, particularly to a charging parameter verification method and equipment, and a charger, and aims to solve the problem of charging failure caused by the fact that safety threshold of each charging parameter cannot be effectively controlled and judged. The charging parameter verification method comprises the following steps: after a communication channel between a terminal and the charger is established successfully, the terminal reads charging capability information of the charger according to a preset way, compares a maximum capability value of the charger specific to each preset charging parameter and a target value corresponding to a corresponding preset charging parameter stored by the terminal, determines the minimum value as a first configuration value of the corresponding preset charging parameter, writes the first configuration value, obtained by comparison, of each preset charging parameter into the charger, and reads a second configuration value, specific to each preset charging parameter, of the charger; and after it is determined that all preset charging parameters are configured successfully, the terminal transmits charging confirmation indication to the charger.
Owner:HUAWEI DEVICE CO LTD
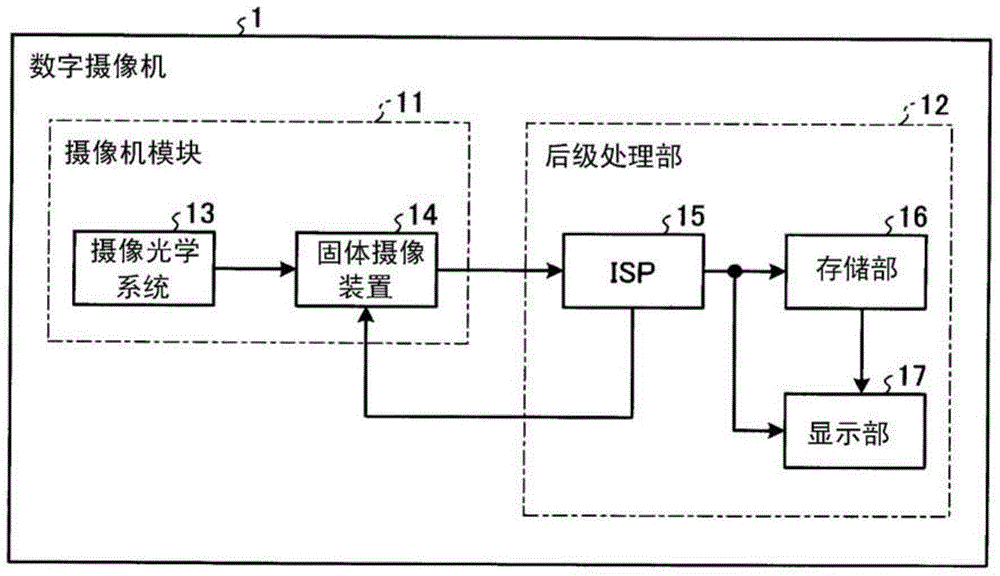
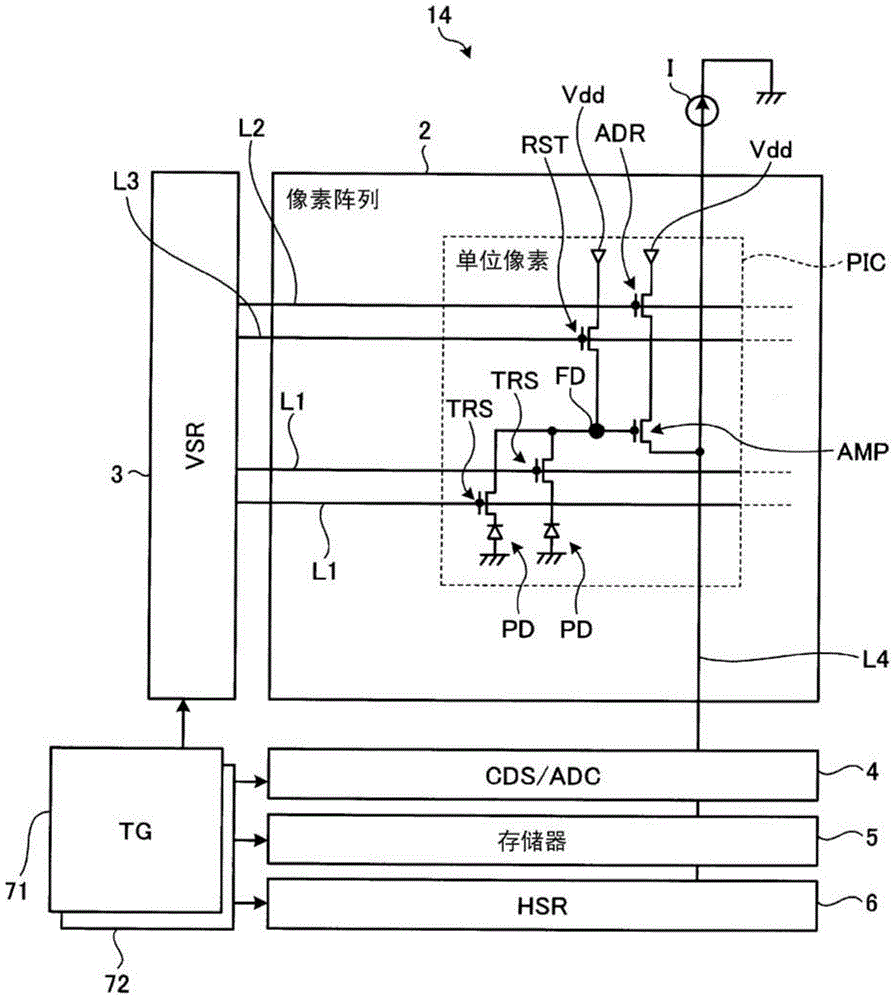
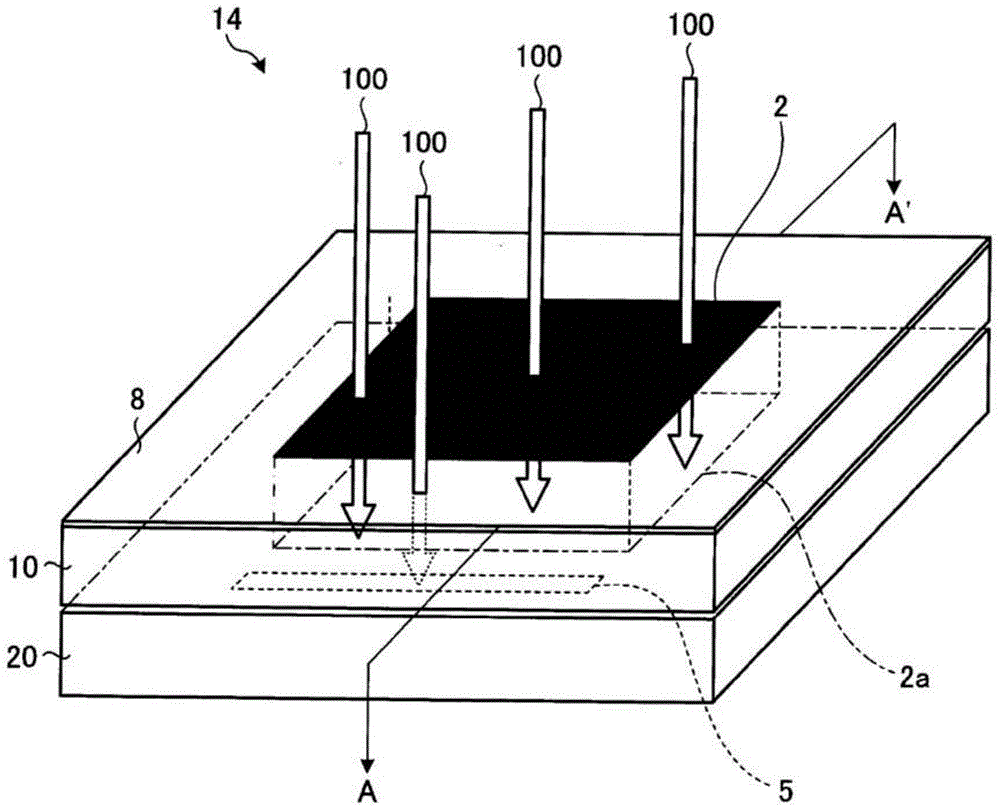
Solid-state imaging device
InactiveCN104681570APrevent rewritingSolid-state devicesRadiation controlled devicesPhotoelectric conversionPhotodiode
A solid-state imaging device includes a first chip and a second chip. The first chip includes a pixel array in which a plurality of photodiodes corresponding to each pixel of a captured image is disposed in a two-dimensional array shape. Each photodiode generates a pixel signal corresponding to a signal charge generated by the photoelectric conversion of the photodiode. The first chip is stacked on the second chip that includes a memory storing the pixel signals generated from the first chip, where the memory is located outside a projection region formed by projecting the pixel array and in a thickness direction of the first chip.
Owner:KK TOSHIBA
Read-write control method and apparatus of ultrahigh frequency electronic tag, and read-write device
PendingCN108763994APrevent rewritingImprove securitySensing by electromagnetic radiationPasswordComputer software
The embodiment of the invention discloses a read-write control method and apparatus of an ultrahigh frequency electronic tag, and a read-write device. The method comprises the following steps: performing encryption operation on a random number according to a preset encryption algorithm to generate a random password; receiving a third password calculated by upper computer software based on the random number, and a fourth password calculated by an encryption module based on the random number; respectively judging whether a random password is consistent with the third password and the fourth password; and if the random password is inconsistent with the third password, and / or random password is inconsistent with the fourth password, feeding back an authentication failure signal to the upper computer software, and controlling the read-write device to enter a standby state. Through the above manner, the embodiment of the invention can prevent the data in the electronic tag from being rewritten by unauthorized software or an unauthorized device, thereby ensuring the security of the data.
Owner:SHENZHEN MEGMEET ELECTRICAL CO LTD +1
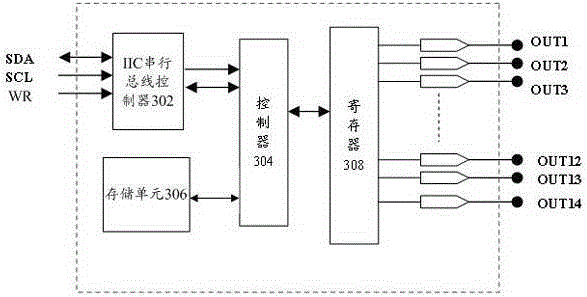
Gamma correction snubber circuit and anti-interference method for the gamma correction snubber circuit
ActiveCN105280151APrevent rewritingStable outputStatic indicating devicesElectricityProcessor register
The invention provides a gamma correction snubber circuit. The gamma correction snubber circuit comprises a determination unit and a control unit, wherein when a circuit system of the gamma correction snubber circuit is electrified, the determination unit determines whether the digital working voltage is greater than or equal to the threshold voltage of the gamma correction snubber circuit; when the determination unit determines that the digital working voltage is smaller than the threshold voltage, the control unit controls an IIC serial bus of the gamma correction snubber circuit so that the IIC serial bus is prohibited to operate and the data cannot be written into a memory unit of the gamma correction snubber circuit through the IIC serial bus; and when the digital working voltage is greater than or equal to the threshold voltage, the control unit controls the IIC serial bus to enable the IIC serial bus to be able to operate and the data can be written into the memory unit of the gamma correction snubber circuit through the IIC serial bus. The invention also provides an anti-interference method for the gamma correction snubber circuit. Through the technical scheme of the gamma correction snubber circuit and anti-interference method for the gamma correction snubber circuit, the external influence on the data in a register of the gamma correction snubber circuit can be avoided, and the anti-interference capability of the system and the stability of the system can be improved.
Owner:HISENSE VISUAL TECH CO LTD
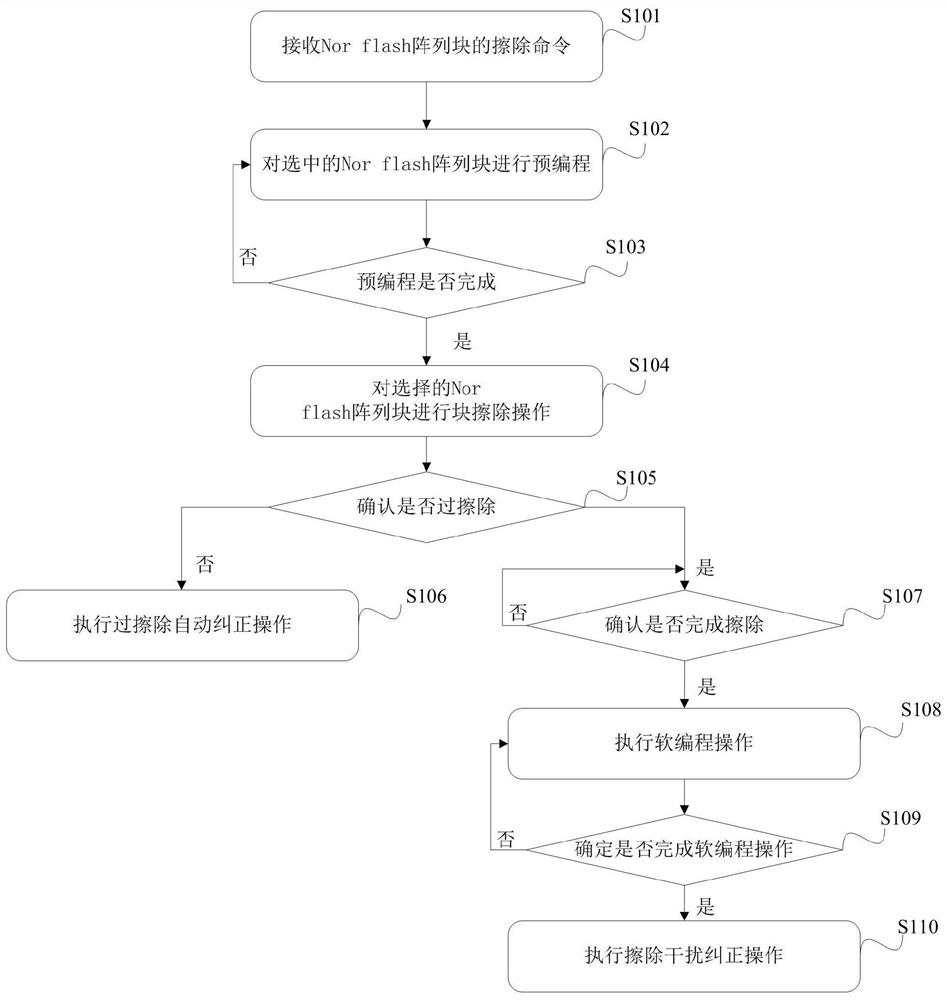
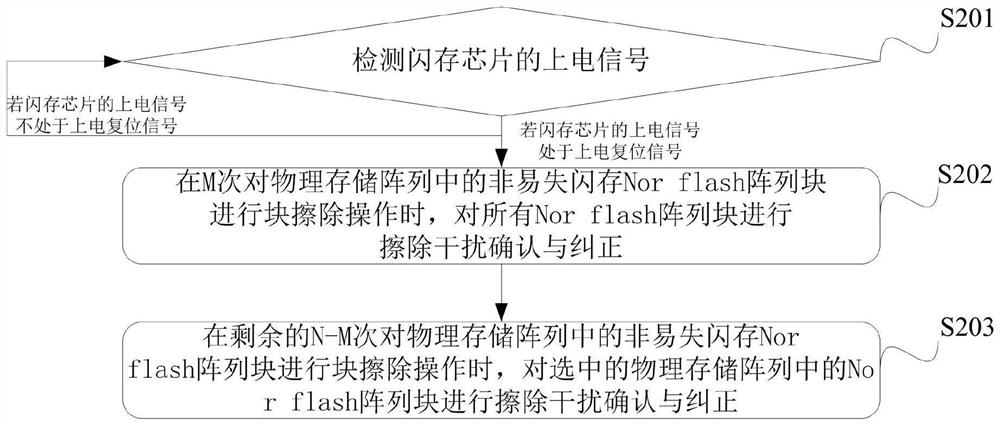
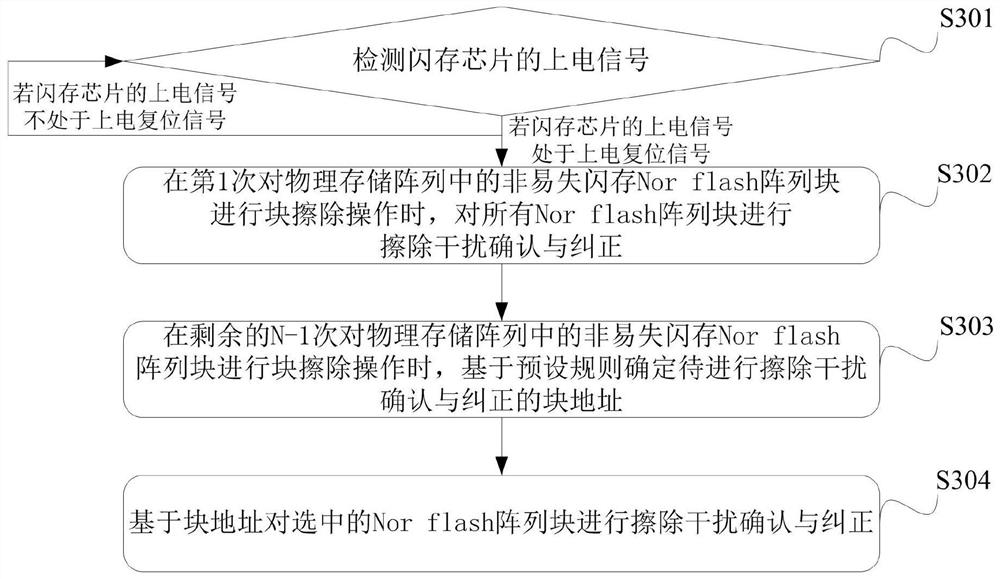
Nor flash erasure interference correction method and Nor flash erasure interference correction device
PendingCN112000290AShort timePrevent rewritingInput/output to record carriersMemory adressing/allocation/relocationPower-on resetFlash memory
The invention provides a Nor flash erasure interference correction method and a Nor flash erasure interference correction device. The method comprises: when a power-on signal of a flash memory chip isin a power-on reset signal, performing erasure interference confirmation and correction on all Nor flash array blocks when the Nor flash array blocks of a nonvolatile flash memory in a physical storage array are subjected to block erasure operation for M times; and performing erasure interference confirmation and correction on the Nor flash array block in the selected physical storage array whenthe Nor flash array block in the physical storage array is subjected to block erasure operation for the remaining N-M times. In the scheme, all Nor flash array blocks are subjected to interference erasing confirmation and correction for at least M times, and in the remaining N-M times, the selected Nor flash array blocks are subjected to interference confirmation and correction each time. Therefore, the time consumption and the power consumption of the whole erasing operation are reduced, and the stored data can be prevented from being rewritten.
Owner:ZHUHAI CHUANGFEIXIN TECH CO LTD
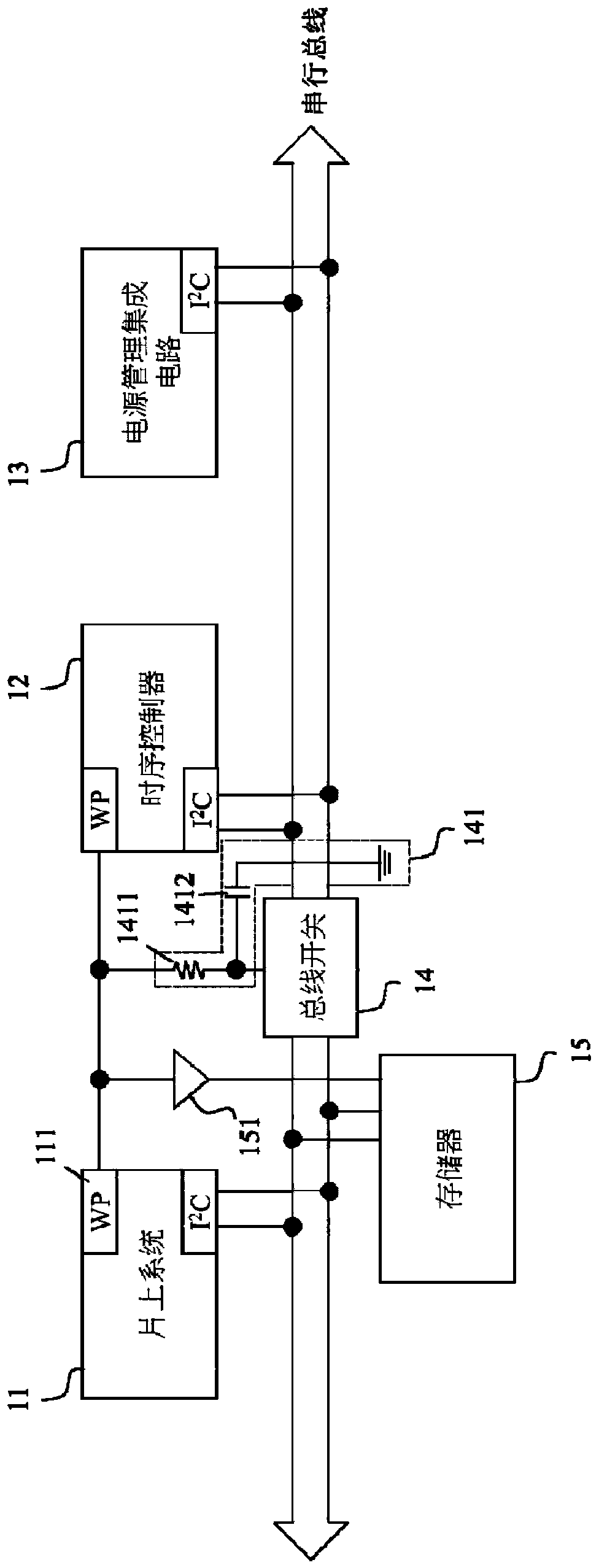
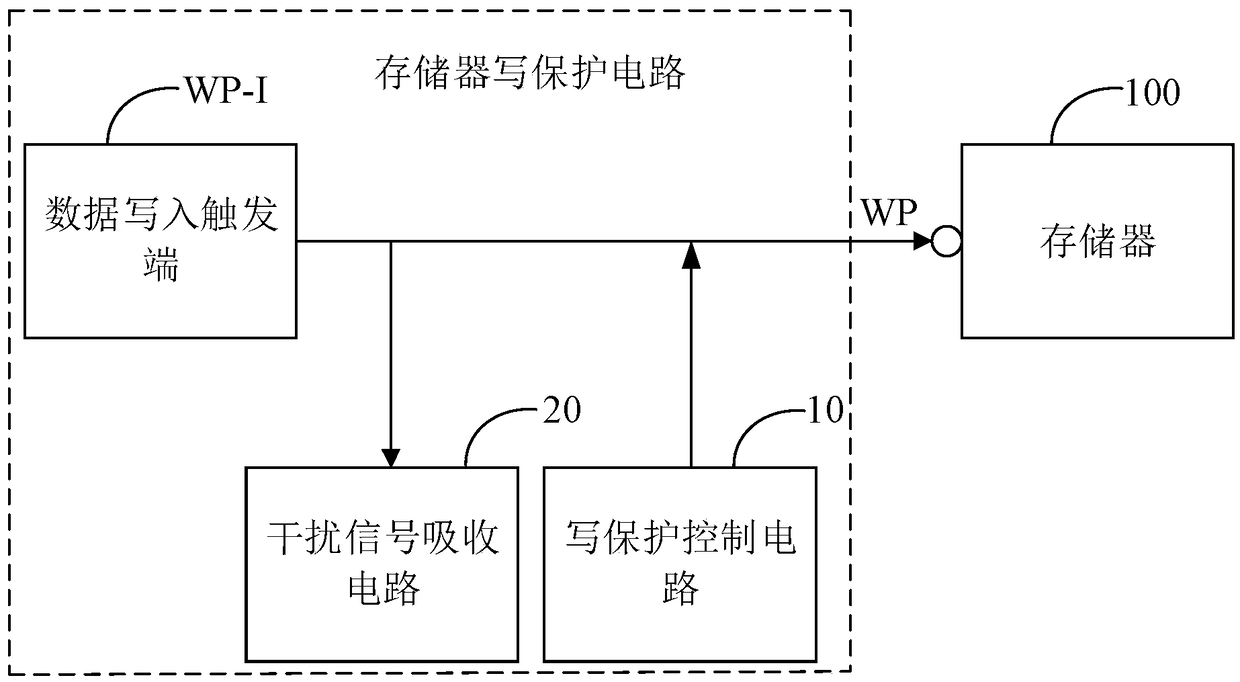
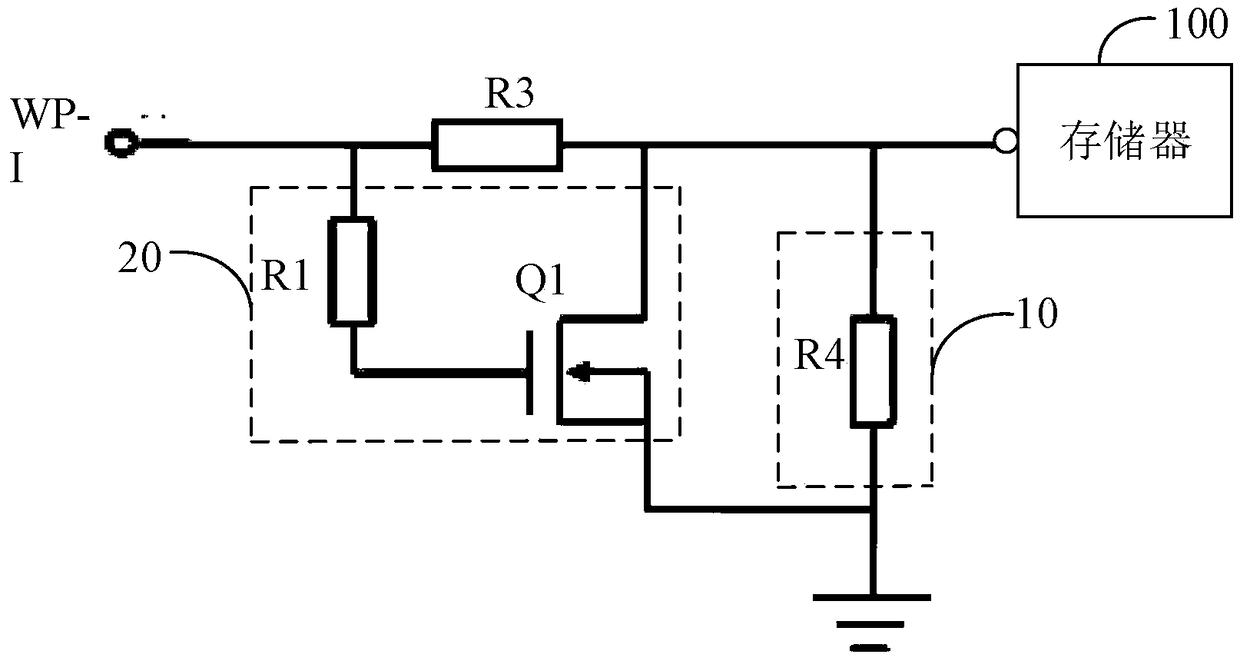
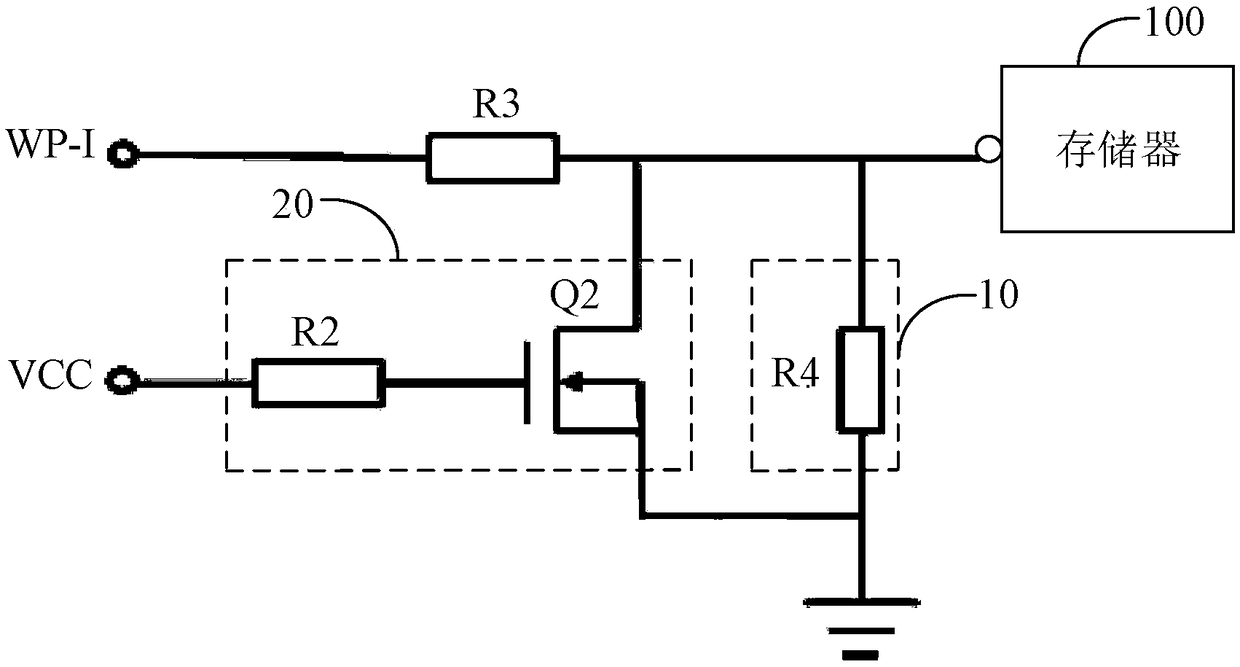
A memory write protection circuit and a display device
ActiveCN109192237APrevent rewritingRead-only memoriesCathode-ray tube indicatorsWrite protectionDisplay device
The invention discloses a memory write protection circuit and a display device. The memory write protection circuit comprises: a data write trigger end, wherein the data write trigger end is connectedwith a write protection pin of the memory and configured to receive a first level signal for controlling the memory to enter a write state; a write protection control circuit connected to the write protection pin of the memory and configured to provide a second level signal limiting the memory from being written with data to the write protection pin of the memory, wherein the polarity of the second level signal is opposite to that of the first level signal; an interference signal absorbing circuit connected to the data writing trigger terminal and configured to detect a level signal receivedby the data writing trigger terminal when the memory is in normal operation, and absorb the first level signal when the data writing trigger terminal is detected to receive the first level signal. Theinvention can effectively prevent the software data of the memory from being overwritten.
Owner:HKC CORP LTD
Data authority control method and device, equipment and storage medium
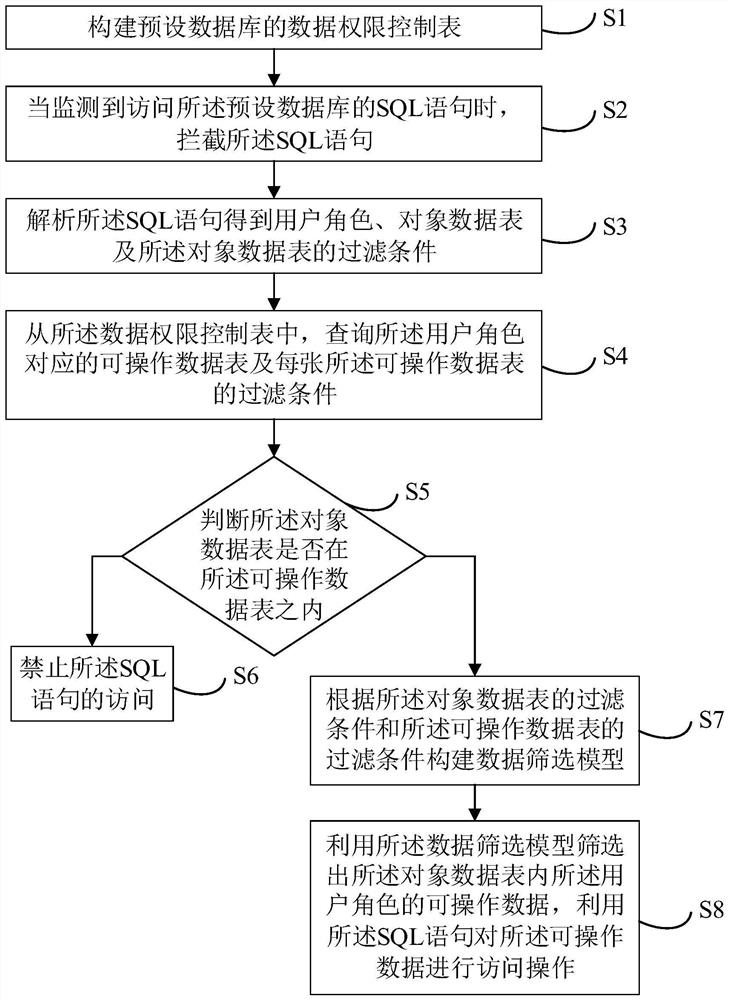
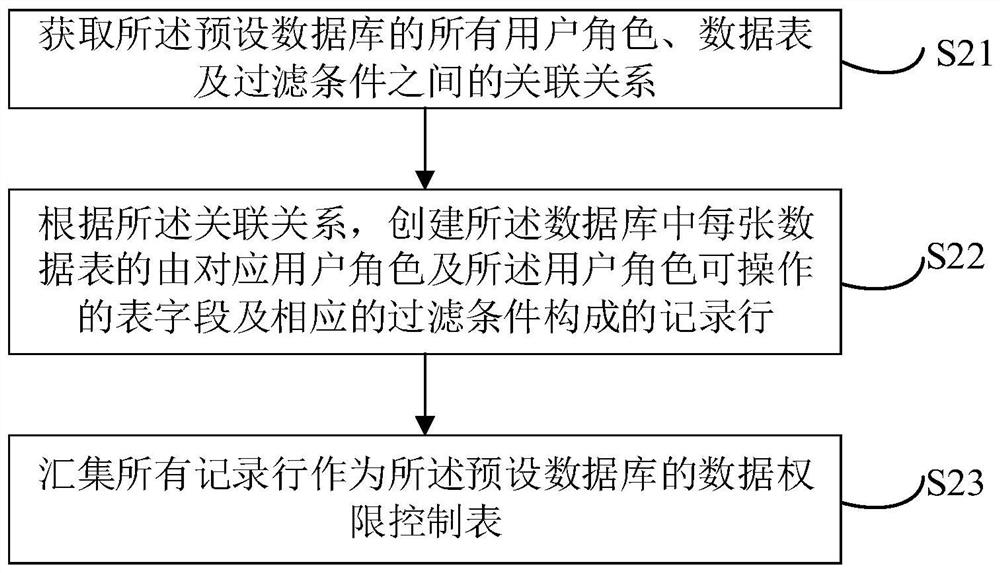
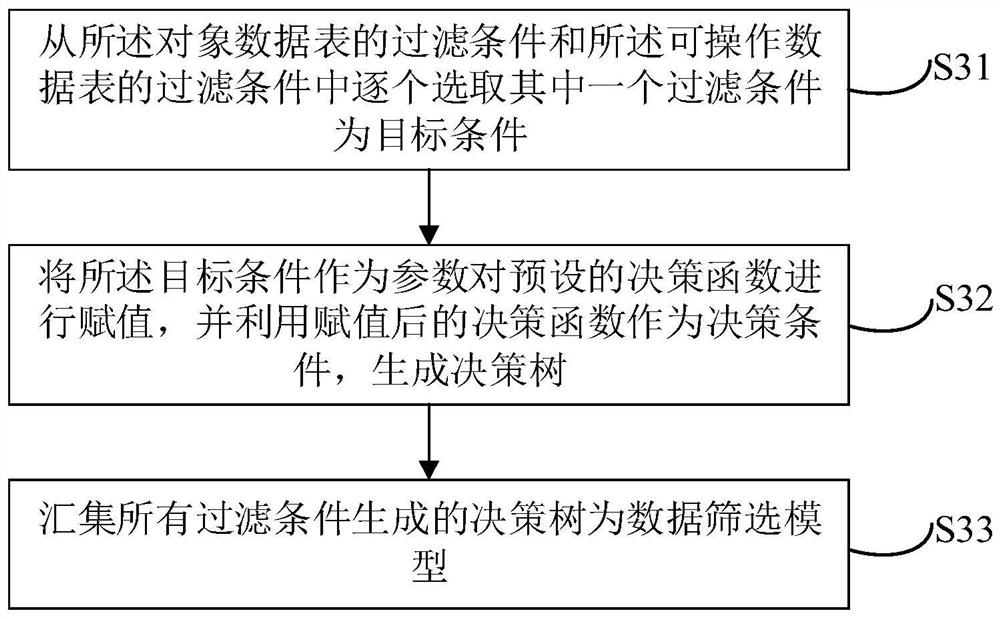
PendingCN114528593APrevent rewritingSolve the difficulty of maintenanceDigital data protectionNatural language data processingTable (database)Datasheet
The invention relates to an artificial intelligence technology, and discloses a data authority control method, which comprises the following steps of: constructing a data authority control table of a preset database; intercepting an SQL statement accessing a preset database; analyzing the SQL statement to obtain a user role, an object data table and a filtering condition of the object data table; querying operable data tables corresponding to the user roles and filtering conditions of each operable data table from the data authority control table; judging whether the object data table is in the operable data table or not; if the SQL statement is not in the operable data table, prohibiting the access of the SQL statement; if the object data table is in the operable data table, constructing a data screening model according to the filtering condition and the filtering condition of the operable data table; and screening out operable data of the user role in the object data table by utilizing the model, and performing access operation on the operable data by utilizing the SQL statement. The invention further provides a data authority control device, equipment and a medium. The maintenance difficulty of the data authority control process can be reduced.
Owner:PINGAN INT SMART CITY TECH CO LTD
Memory data reading method, display device, and computer-readable storage medium
ActiveCN109388345BPrevent rewritingInput/output to record carriersRedundant data error correctionDisplay deviceControl data
The invention discloses a data reading method of a memory, a display device and a computer-readable storage medium. The display device includes: a memory including a first storage area and a second storage area, the first storage area is electrically connected to a timing controller, and the memory The data reading method comprises the steps of: setting preset storage data according to the storage data stored in the first storage area and the second storage area; obtaining the logical address sent by the timing controller; and matching the obtained logical address sent by the timing controller with When the stored logical addresses are the same, compare the storage data in the first storage area with the preset storage data; when the storage data in the two are inconsistent, assign the storage data stored in the second storage area to the first storage area, and trigger The timing controller reads stored data in the first storage area. The invention solves the problem that the timing control data stored in the memory is rewritten by the interference signal, which leads to the problem that the display screen of the display panel cannot be normally driven.
Owner:CHONGQING HKC OPTOELECTRONICS TECH CO LTD +1
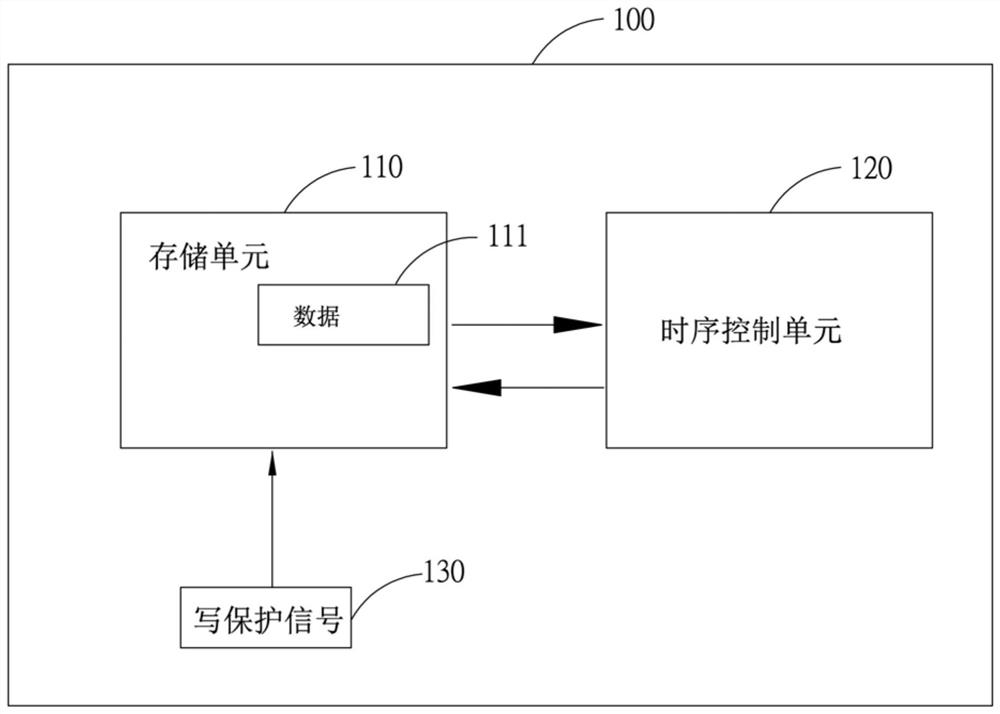
A method for protecting data in a display panel and a display device thereof
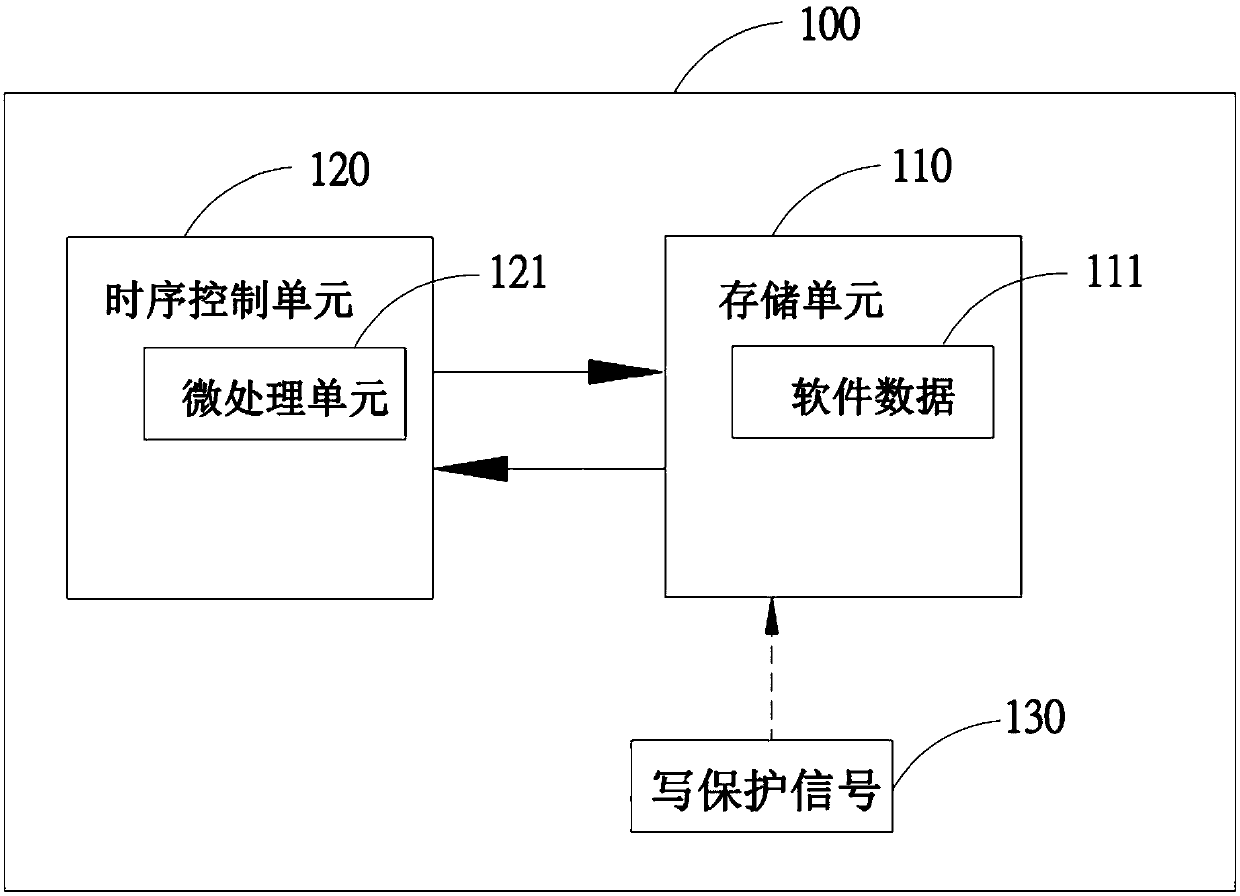
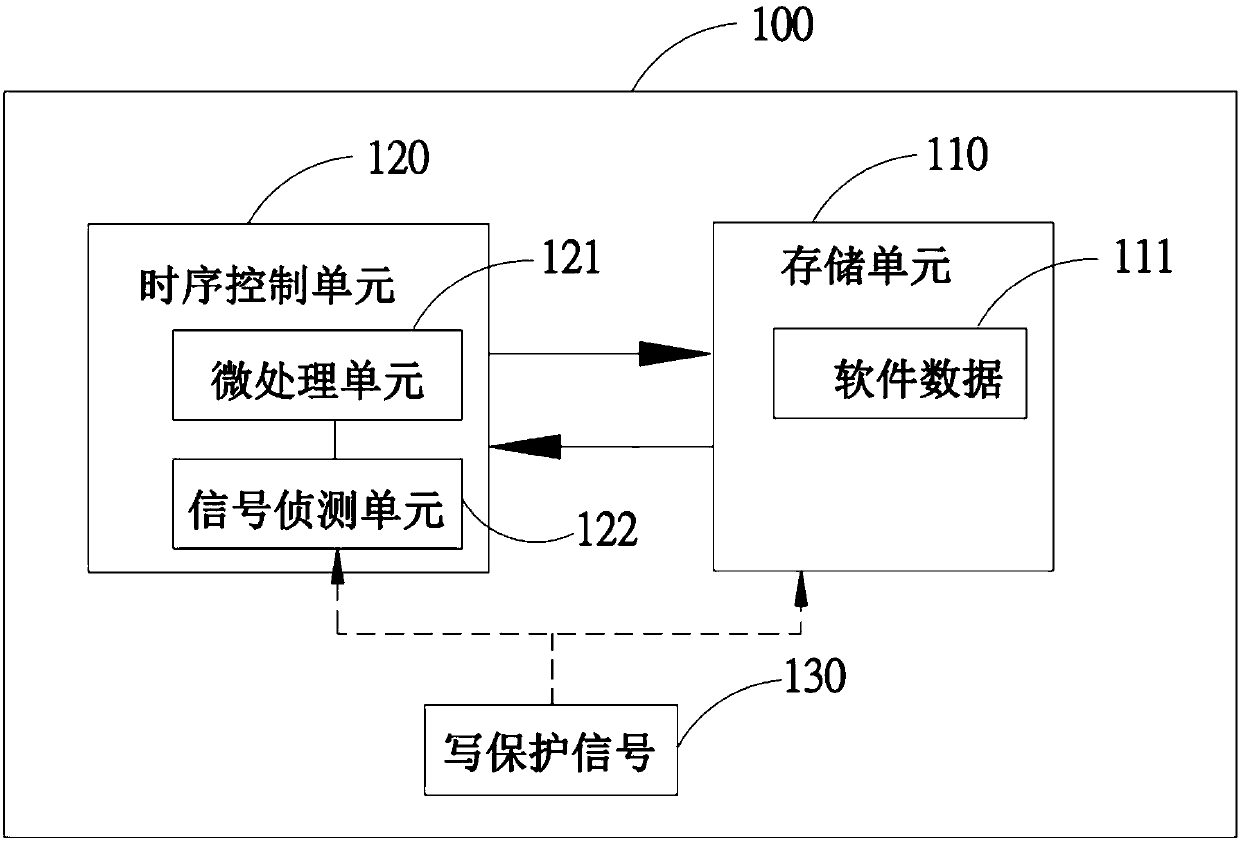
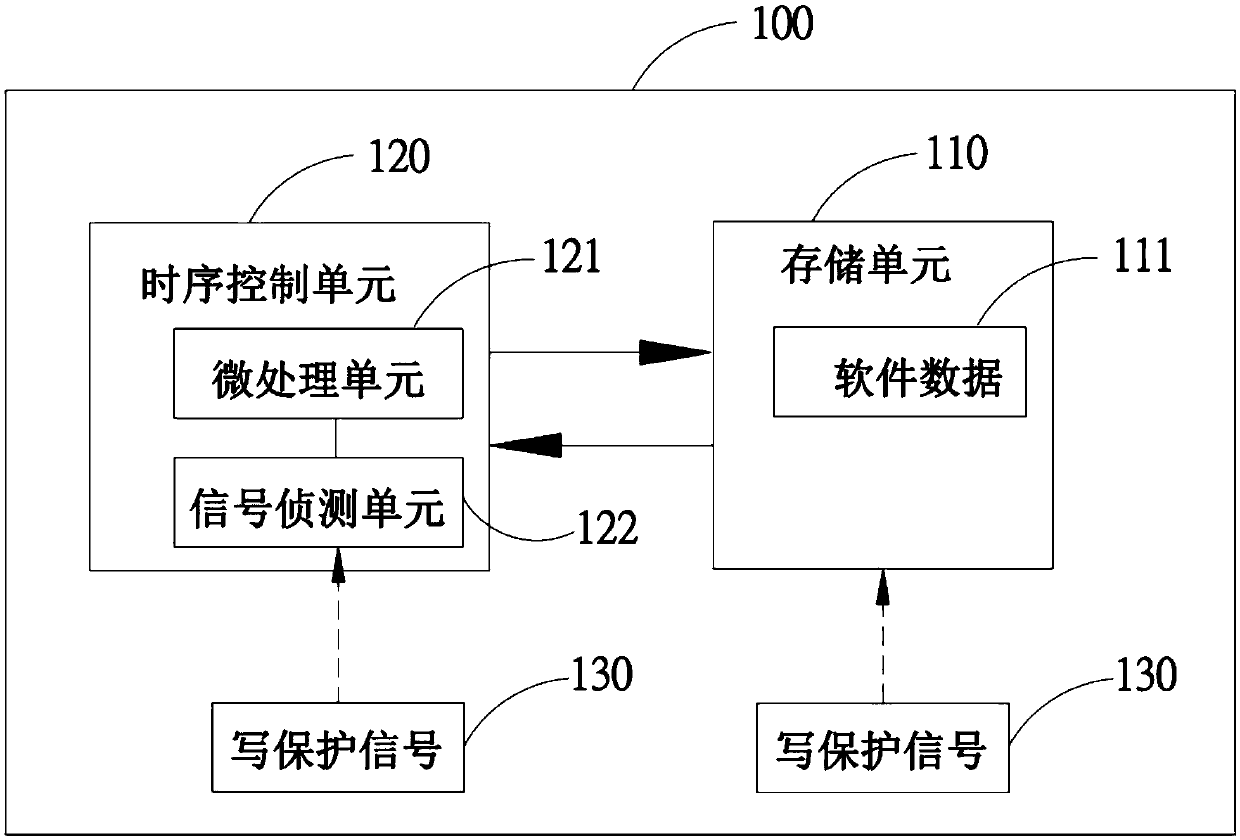
InactiveCN109597704AEasy detectionPrevent rewritingNon-redundant fault processingWrite protectionDisplay device
The invention discloses a method for protecting data in a display panel and a display device thereof. The display device comprises a display panel; a storage unit which is arranged on a driving boardin the display panel and is used for storing data of a time sequence control unit; a time sequence control unit which is arranged in the display panel, and comprises a signal detection unit for detecting the state of a write protection signal; and a micro-processing unit which is used for determining to request or stop the storage unit from sending the data according to the state of the write protection signal.
Owner:HKC CORP LTD
Text hidden method based on Chinese sentence pattern template transformation
InactiveCN101639826BConform to the semantic idiomPrevent rewritingSpecial data processing applicationsElectronic documentComputerized system
The invention discloses a text hidden method based on Chinese sentence pattern template transformation. The method utilizes the computer system to carry out watermark embedment and extraction on text information to hide the text information, comprising the following steps: (1) carrying out pre-treatment on an electronic file; (2) generating watermark information sign and setting a key; (3) carrying out part-of-speech tagging to format-free file generated in step (1) by a part-of-speech tagging module and outputting a part-of-speech tagging string of a sentence; (4) simplifying the part-of-speech tagging string output in the step (3) by a chunk tagging module; (5) loading a template module to select a sentence pattern module; (6) embedding watermark information by a watermark embedment module; (7) outputting the hidden text with embedded watermark; and (8) extracting the watermark information from the hidden text by a watermark extraction module through the key. The text hidden method changes sentence pattern through a template, avoids complex understanding and processing of grammar and semanteme, ensures the carrier text better satisfying grammar and semanteme habit and prevents blindfold rewrite.
Owner:NORTHWEST UNIV
Method, device, and charger for checking charging parameters
ActiveCN106684954BPrevent rewritingAvoid security issuesSignal allocationElectric powerEngineeringComputer terminal
The present invention relates to the technical field of charging, in particular to a method for verifying charging parameters and a device and a charger to solve the problem that the safety threshold of each charging parameter cannot be effectively controlled and judged, resulting in charging failure. The method is : After the communication channel between the terminal and the charger is successfully established, the terminal reads the charging capacity information of the charger according to the preset method, and compares the maximum capacity value of the charger for each preset charging parameter with the corresponding preset value saved by the terminal itself. The target value corresponding to the charging parameter is compared, and the minimum value is determined to be the first configuration value of the corresponding preset charging parameter, and the first configuration value of each preset charging parameter obtained by comparison is written into the charger, and read The second configuration value of the charger for each preset charging parameter; after determining that all preset charging parameters are successfully configured, the terminal sends a charging confirmation instruction to the charger.
Owner:HUAWEI DEVICE CO LTD
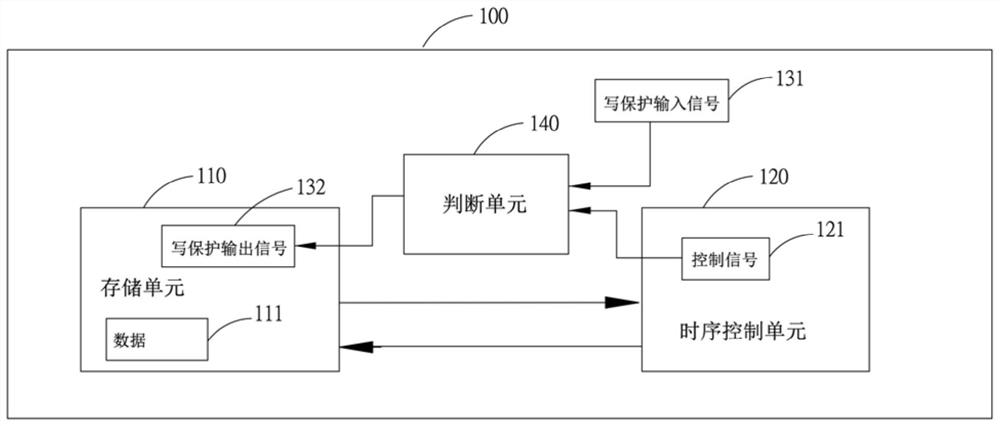
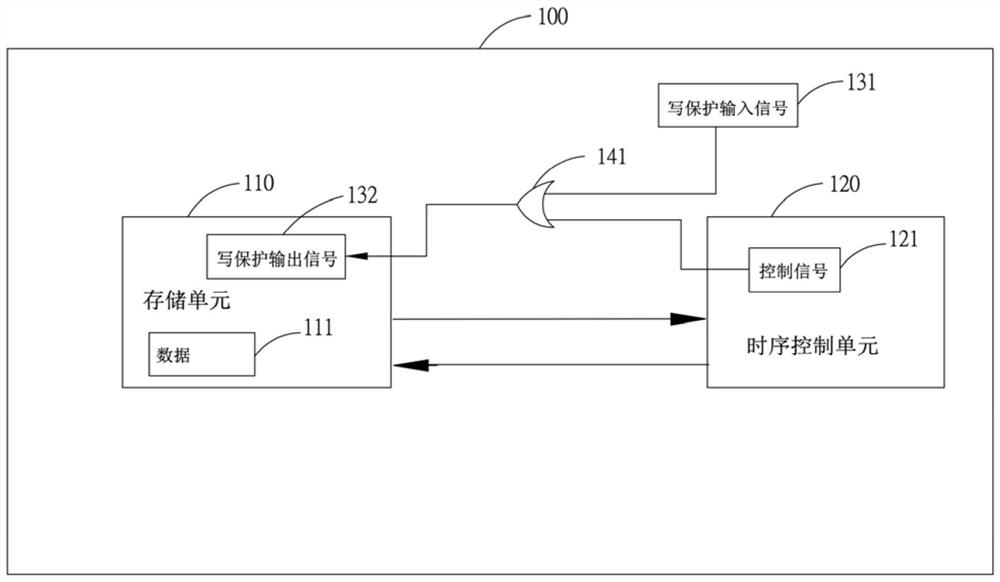
Data protection method in display panel and display device thereof
ActiveCN109446851BPrevent rewritingAvoid display screen anomaliesStatic indicating devicesInternal/peripheral component protectionWrite protectionControl signal
The present application relates to a method for protecting data in a display panel and a display device thereof. The display device includes: a display panel; a timing control unit arranged in the display panel and outputting a control signal; a judgment unit arranged in the In the display panel, a write protection input signal and the control signal are received, and when it is determined that at least one of the write protection input signal and the control signal is at a high level, a write protection output signal is output to a storage unit; and the storage unit, arranged on a drive board in the display panel, used to store the data of the timing control unit, and enter the read-only mode after receiving the write protection output signal; wherein, the The write protection output signal is at a high level; after the storage unit enters the read-only mode, the timing control unit reads the data in the storage unit.
Owner:HKC CORP LTD
programmable logic controller
ActiveCN104428782BPrevent rewritingDigital data protectionInternal/peripheral component protectionProgrammable logic controllerEngineering
It has: a device (2), which stores data; an authentication information storage unit (4), which stores authentication information; an authentication function unit (5), which performs user authentication based on the authentication information; and an encryption filter (3), which has multiple One of the encryption modes (311~31n), one of which is preset by the user for encryption processing, the authentication function part (5) performs user authentication when requesting to write data to the device from an external device, and the user authentication succeeds In this case, for the data written to the device (2), the encryption filter (3) is encrypted using the encryption mode (311~31n) set in advance by the user, and then written to the device (2). When the authentication fails, the encryption filter (3) encrypts the data written in the device (2) using an encryption mode (311 to 31n) different from the encryption mode set in advance by the user, and sends the encrypted data to the device (2). (2) Write.
Owner:MITSUBISHI ELECTRIC CORP
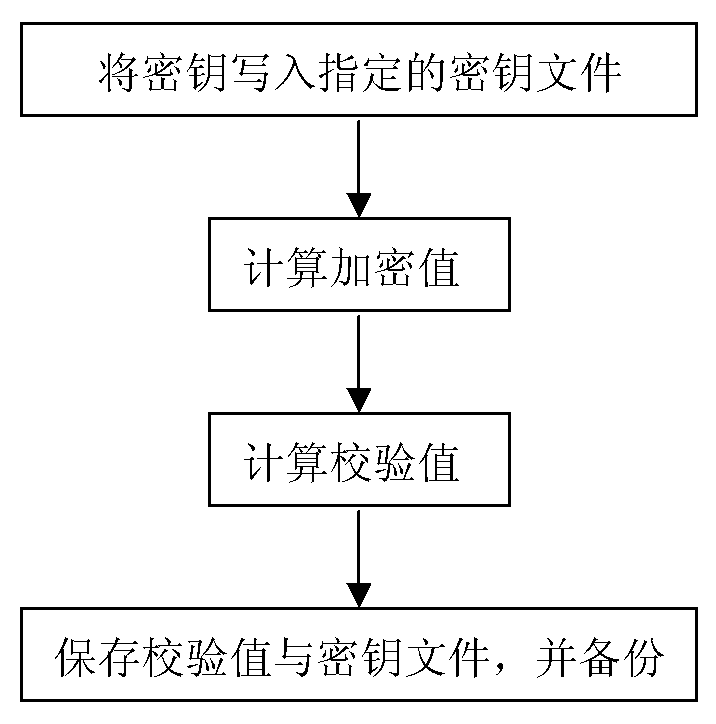
Key protection method in psam card
ActiveCN102542319BPrevent keys from being overwrittenEffective protectionRecord carriers used with machinesData valueCheck valve
The invention discloses a key protection method in a PSAM card. The key is written into a specified key file, a specified encryption algorithm is adopted, and the key value is used as the data of the specified encryption algorithm, which is also used as the encryption algorithm. Encryption key, calculate the encryption value; group the obtained encryption value by 4 bytes, and use the packet data to get a 4-byte verification value; save the verification value and the key file together, and back up the key and check value at the specified location on the PSAM card. The invention can effectively prevent the key from being rewritten and effectively protect the key.
Owner:SHANGHAI HUAHONG INTEGRATED CIRCUIT
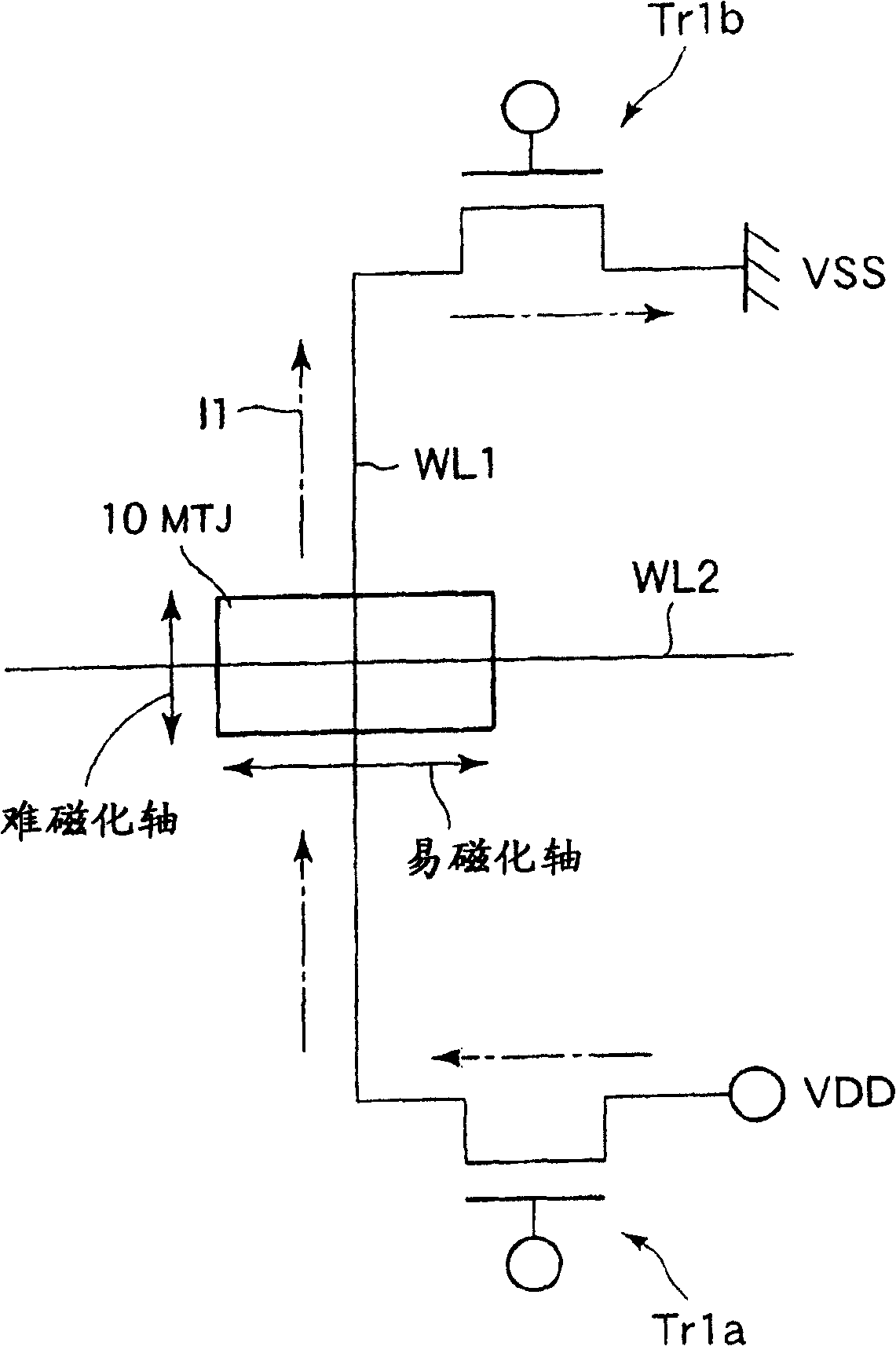
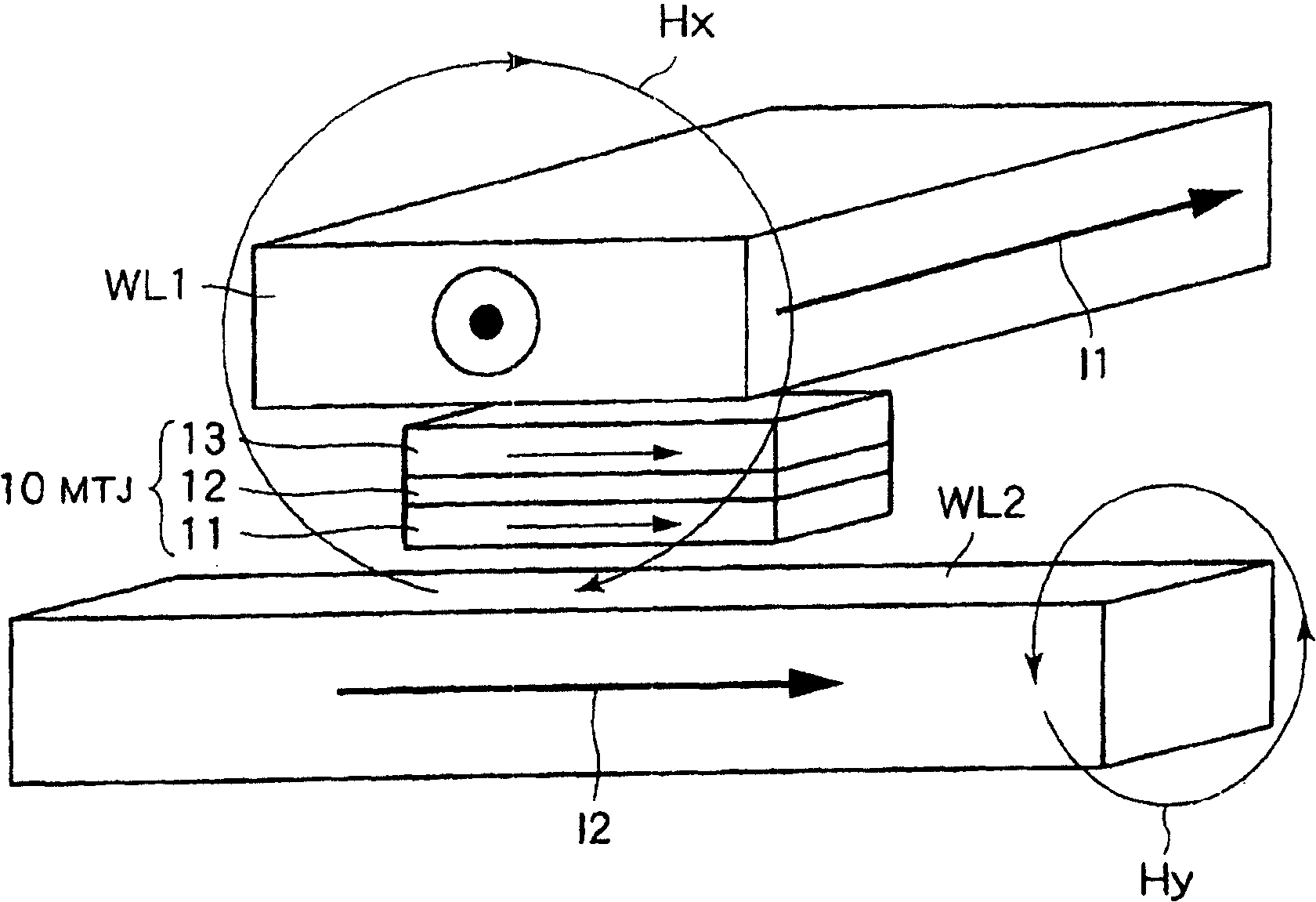
Semiconductor device and data writing method therefor
InactiveCN100431042CPrevent rewritingNanomagnetismSemiconductor/solid-state device detailsMagnetizationComputer science
A semiconductor device includes a memory portion in which a plurality of magneto-resistance effect elements each having a hard-axis of magnetization and an easy-axis of magnetization are arranged and one of binary data is written in all the magneto-resistance effect elements, and a circuit portion to which a write current is supplied to write only the other one of the binary data in only a selected magneto-resistance effect element selected from the magneto-resistance effect elements.
Owner:KK TOSHIBA
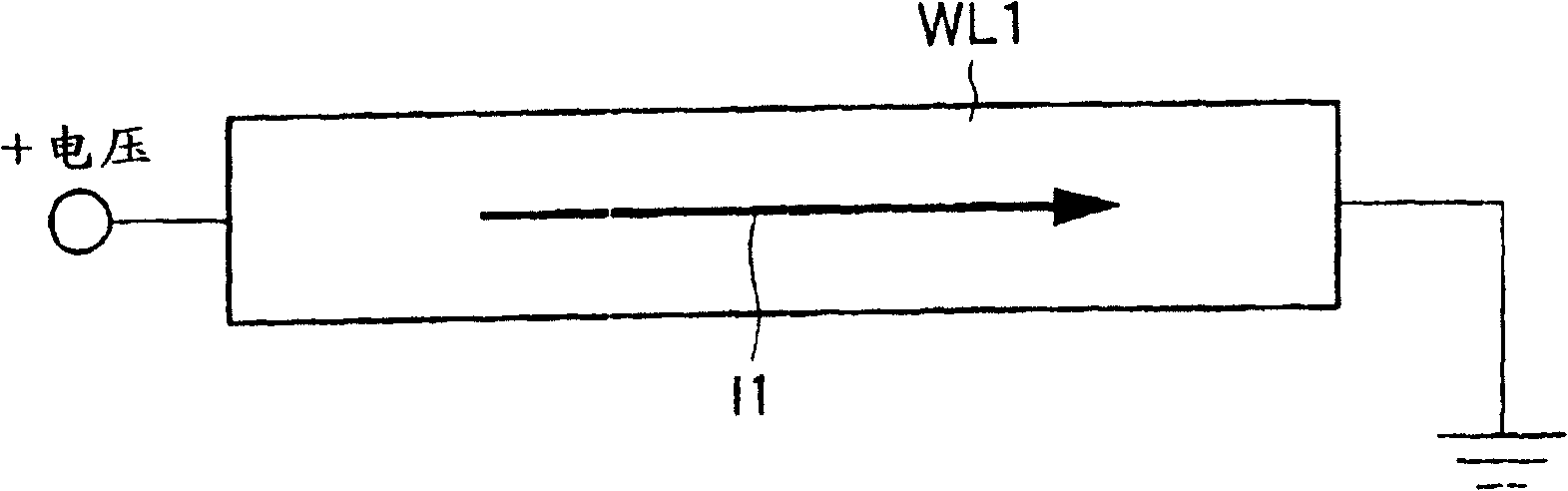
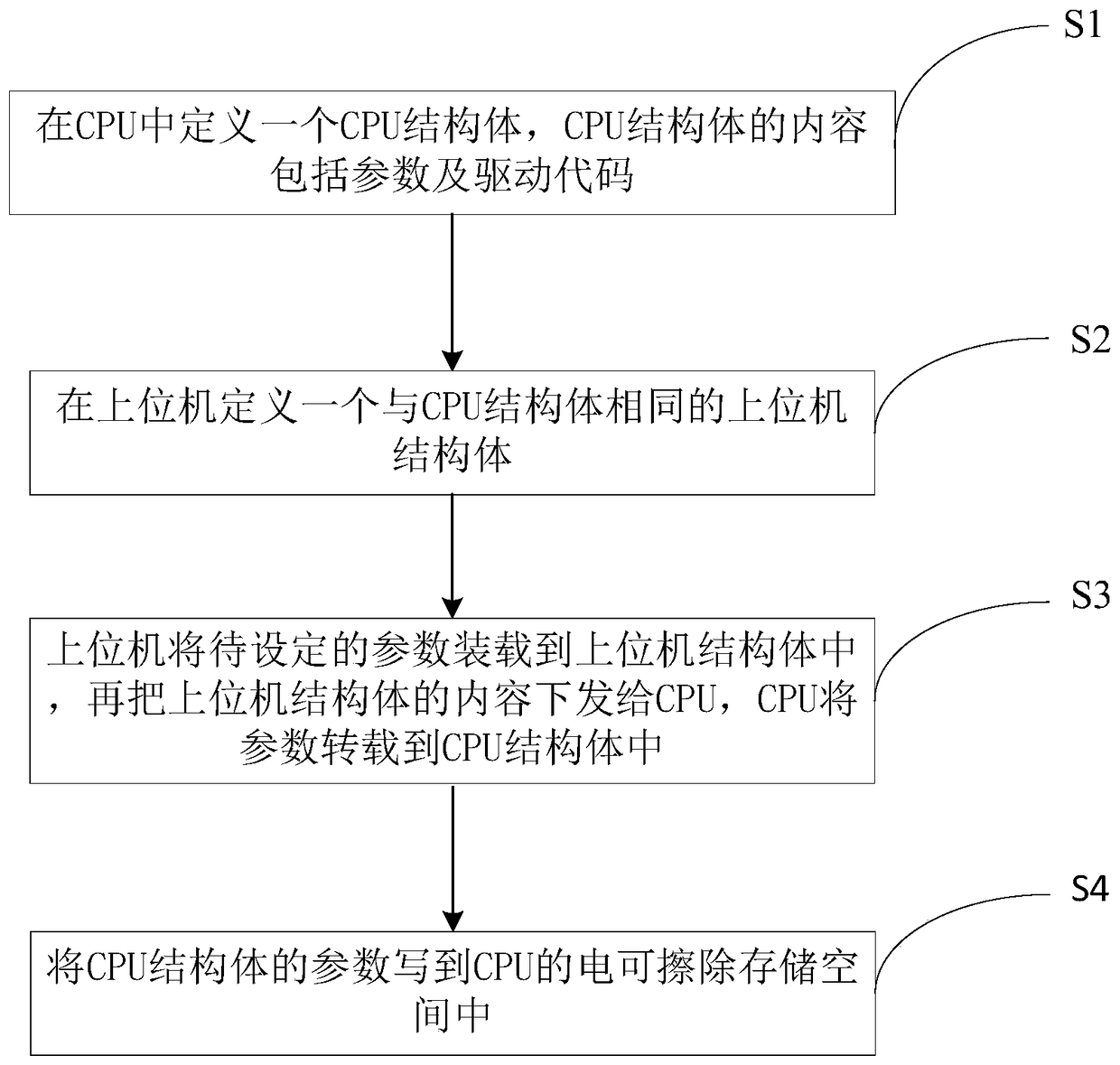
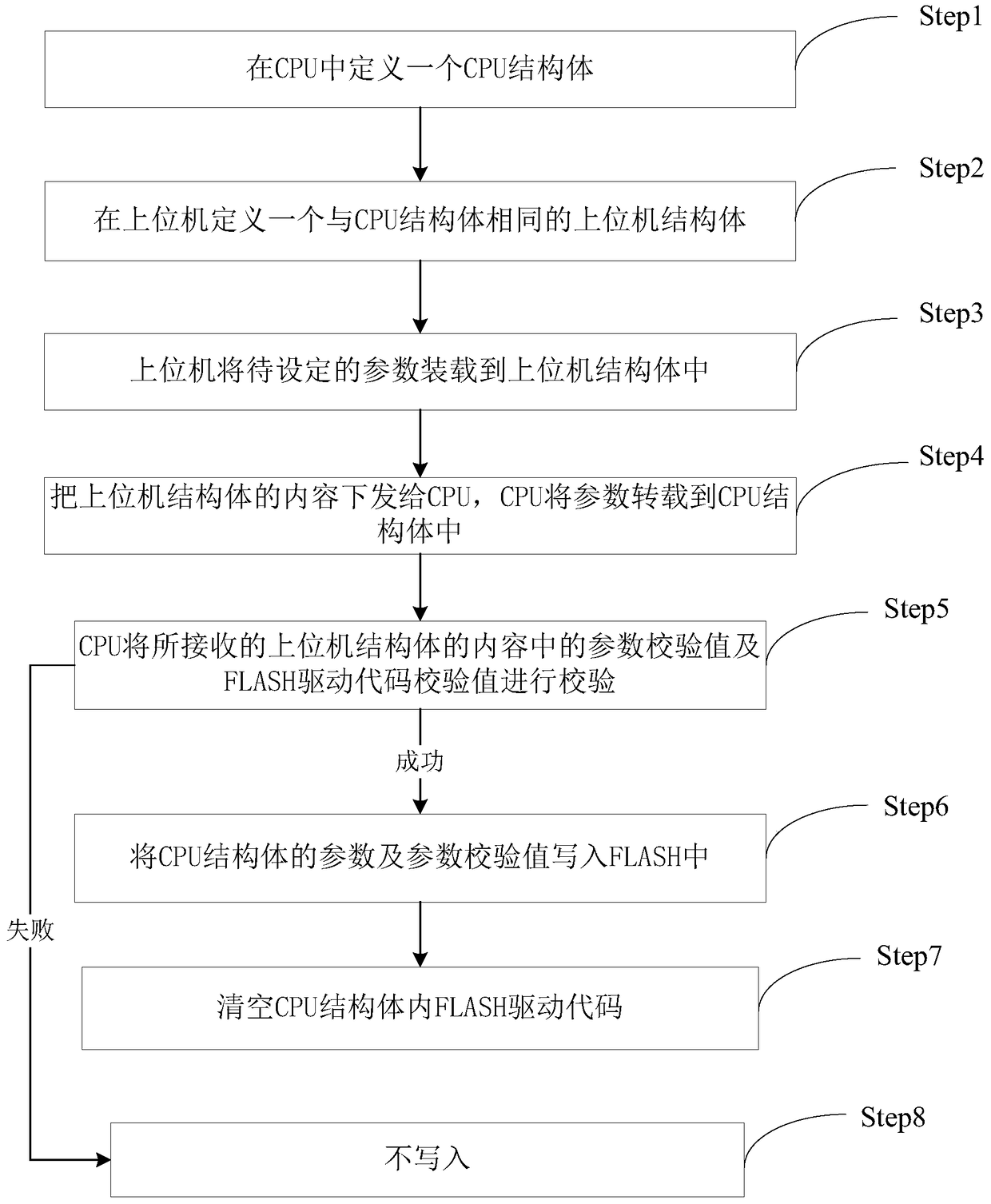
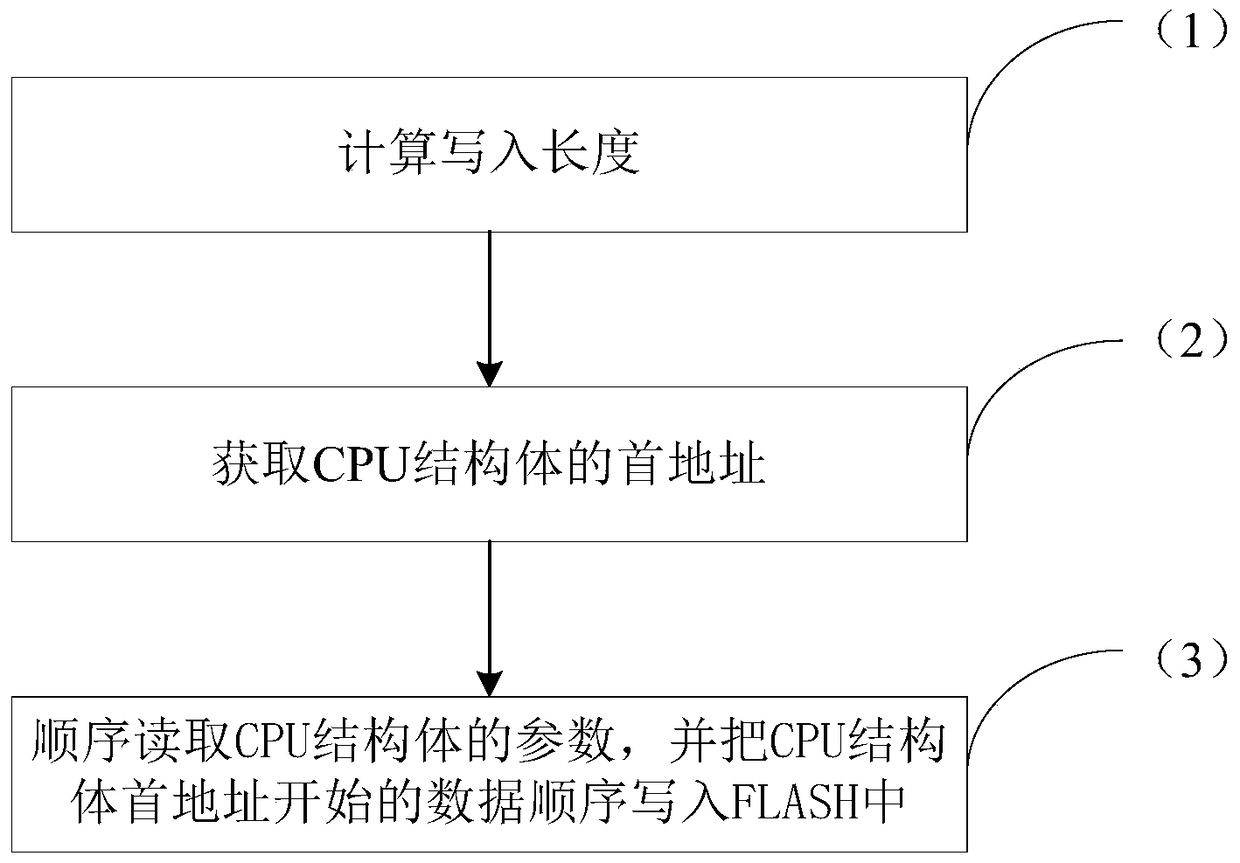
The method of storing parameters through the internal storage space of the cpu
ActiveCN105677502BPrevent rewritingImprove reliabilityFault response safety measuresElectricitySystem parameters
Owner:HUIZHOU BNET TECH CO LTD
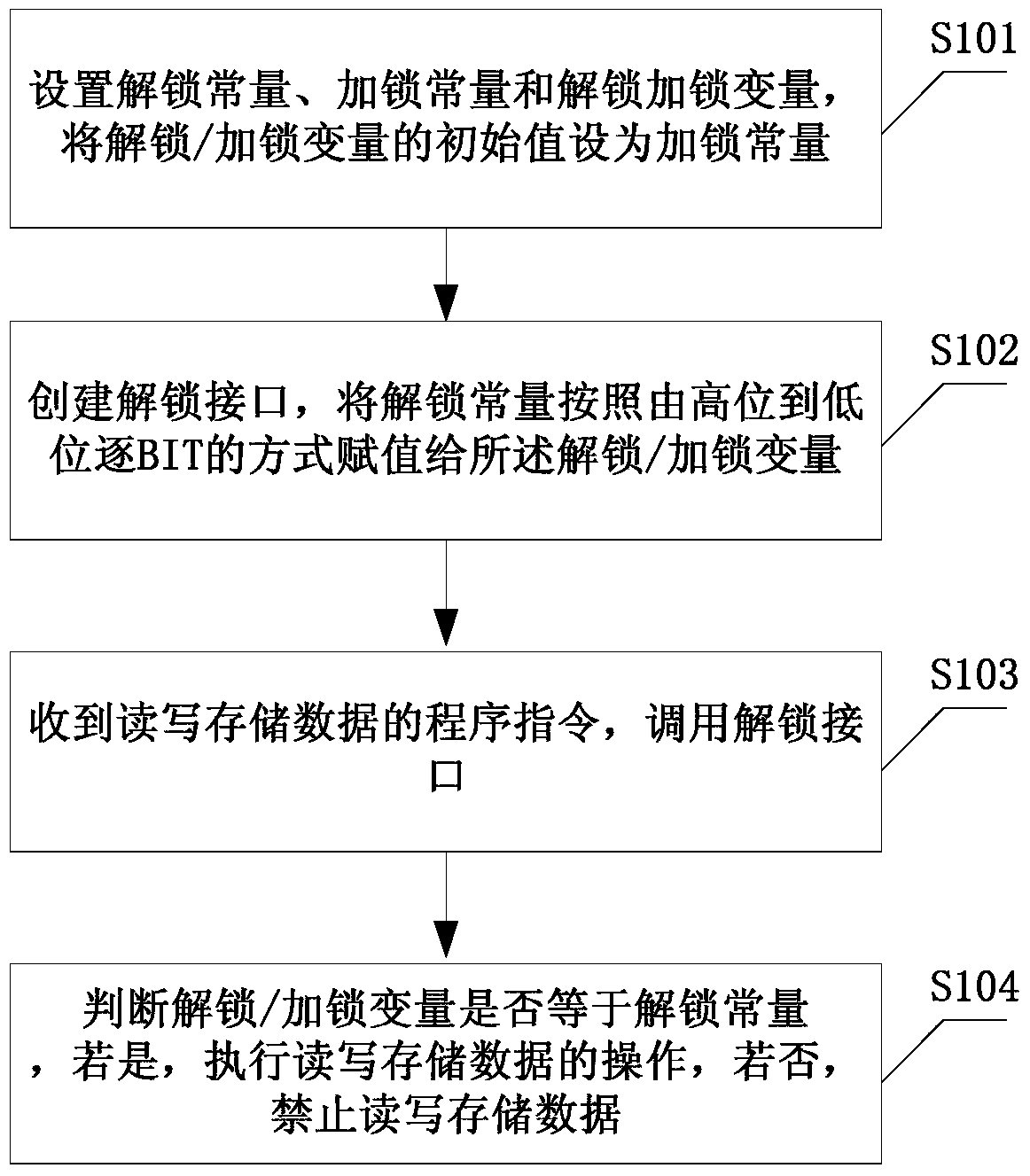
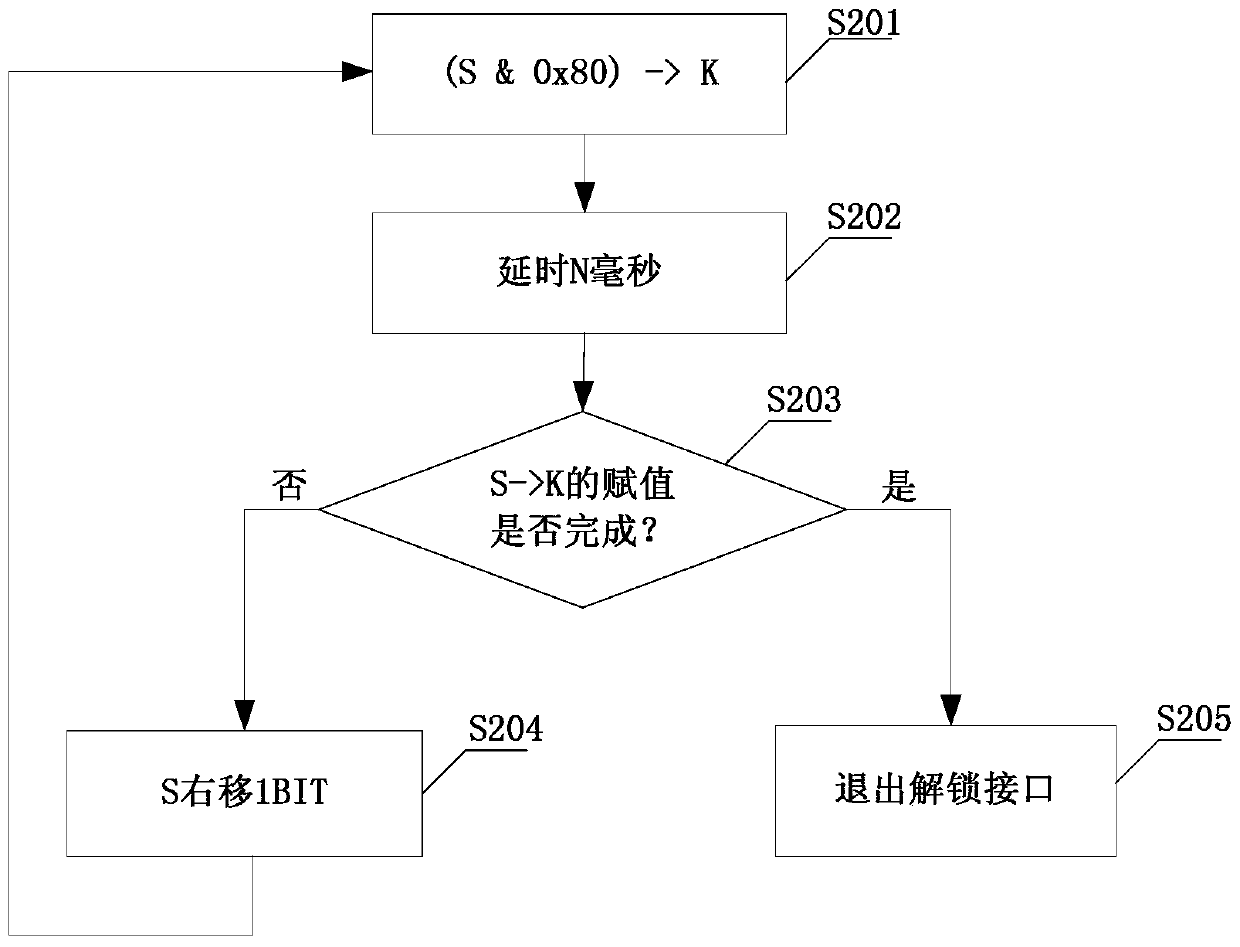
A read-write protection method for stored data
The invention discloses a storage data reading and writing protection method. The method comprises setting unlocking constants, locking constants and unlocking / locking variables, setting the initial value of the unlocking constants as the locking constants; creating an unlocking interface, and assigning the unlocking constants to the unlocking / locking constants in a high-to-low bit-by-bit mode; receiving a program command for reading / writing storage data and calling the unlocking interface; determining whether the unlocking / locking variables are equal to the unlocking constants, if so, calling the reading and writing interface of the storage data and executing the operation of storage data reading and writing, and if not, inhibiting the storage data reading and writing. The storage data reading and writing protection method can avoid rewriting data inside a storage device due to program running disorder during power interruption.
Owner:SHENZHEN RAPOO TECH
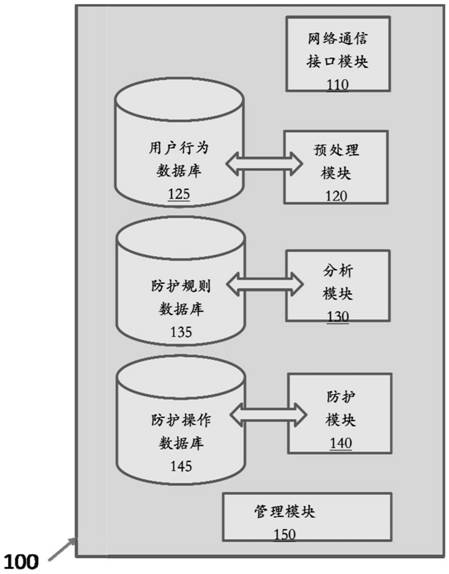
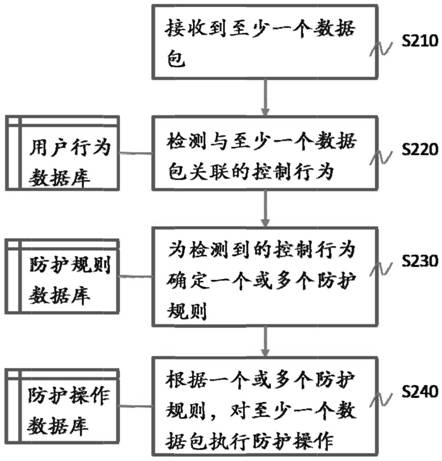
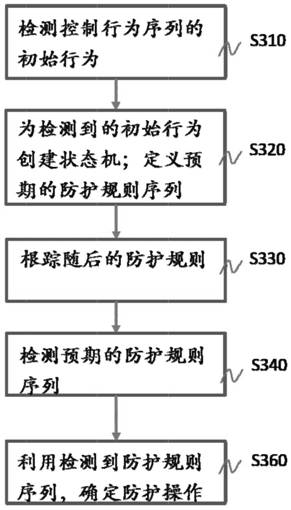
Industrial control system control behavior detection and protection method and system
ActiveCN111913430BPrevent rewritingProgramme control in sequence/logic controllersComputer networkNetwork on
The invention discloses a control behavior detection and protection method and system of an industrial control system. The detection and protection method includes receiving at least one data packet being transmitted on the communication network of the industrial control system; A control behavior associated with at least one data packet is detected by a plurality of characteristics; corresponding to at least one data packet being transmitted and the detected control behavior, at least one protection rule is determined; a protection operation is performed on the data packet, and the data packet is the corresponding One of several data packets of a protection rule, and the protection operation includes one or more of the following operations: allow data packet transmission, block data packet transmission, require user authentication, and record data packets. The invention can detect internal or external illegal operation attempts that violate the control behavior norms on the basis of the pre-established control behavior norms.
Owner:物耀安全科技(杭州)有限公司
WeChat platform information transmission encryption and decryption system
InactiveCN106162629ASecure transmissionPrevent rewritingSecurity arrangementApplication serverInformation transmission
The invention relates to a WeChat platform information transmission encryption and decryption system comprising terminal units, encryption units, an intermediate server unit and an application server unit. The charge and discharge interfaces of the multiple terminal units are plugged into the encryption units respectively. The multiple terminal units are connected to the intermediate server via a network. The intermediate server is connected with the other multiple terminal units or the application server unit via a network. The other multiple terminal units and the application server unit are equipped with encryption units. According to the invention, the terminal units can be mobile phones, tablets or other handheld devices and are equipped with mini USB interfaces, micro USB interfaces or lighting interfaces, and the interfaces appear in Windows phone modes, Android phone modes and Apple phone modes. Information is processed while being transmitted, so that information rewriting in a terminal unit or in a network is avoided, and the security of information transmission is ensured.
Owner:天津聚众德利科技有限公司
Method and device of protecting code segment in use for MIPS system
InactiveCN1916853BPrevent rewritingImprove robustnessSoftware testing/debuggingProgram loading/initiatingInternal memoryComputer architecture
A method for protecting code section used in MIPS system includes making addresses of code section and data section be both placed in region being able to be converted by internal memory management unit in MIPS system when host software is compiled and generated, making code section and data section be placed in said region in program address space of host software when host software is started up. The protection device for realizing said method is also disclosed.
Owner:HUAWEI TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com