Steganographic method with misguiding function of controllable secret key sequence
A steganography and sequence technology, applied in the field of information security, can solve the problems of large redundancy, no active misleading, misleading and so on
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
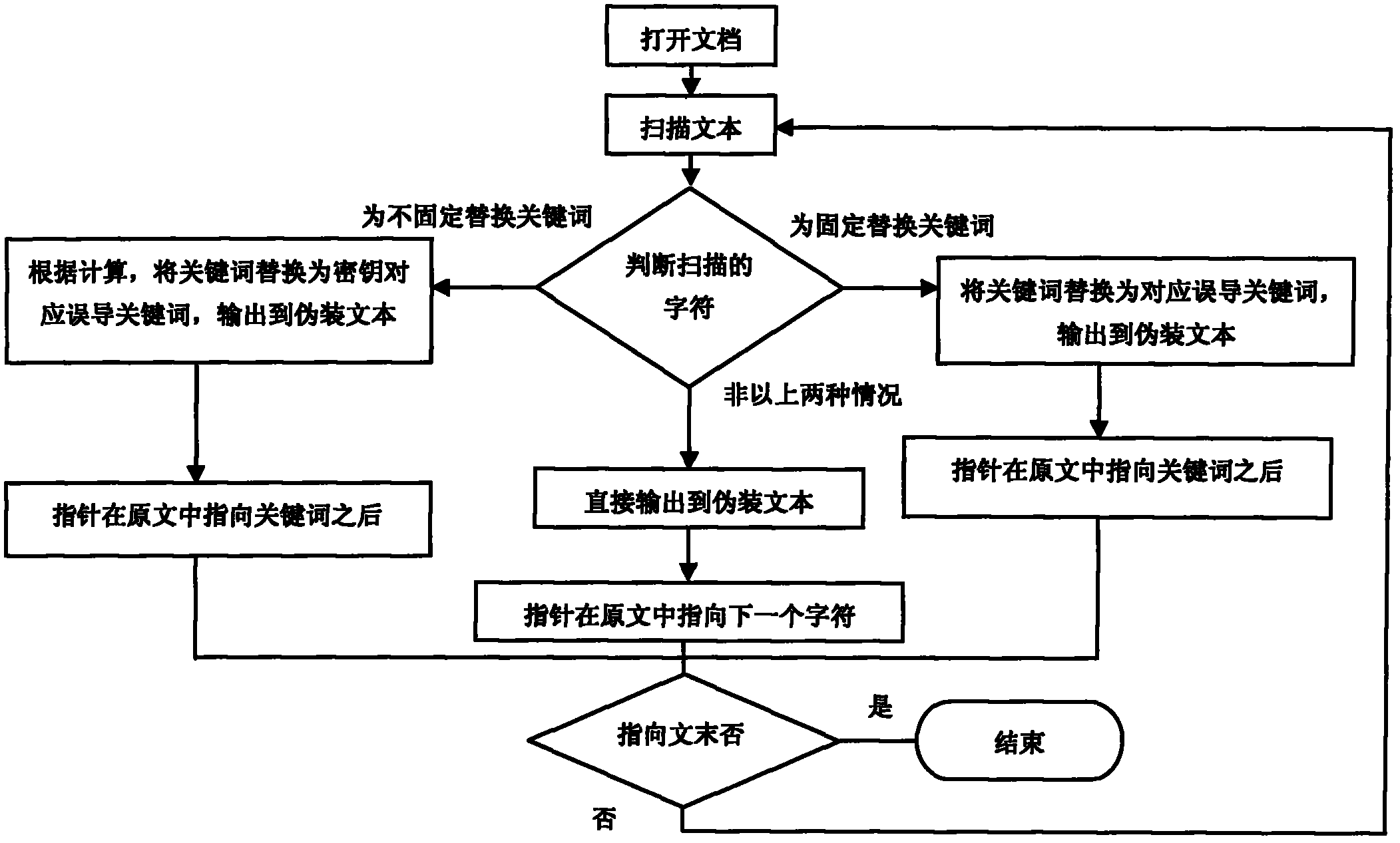
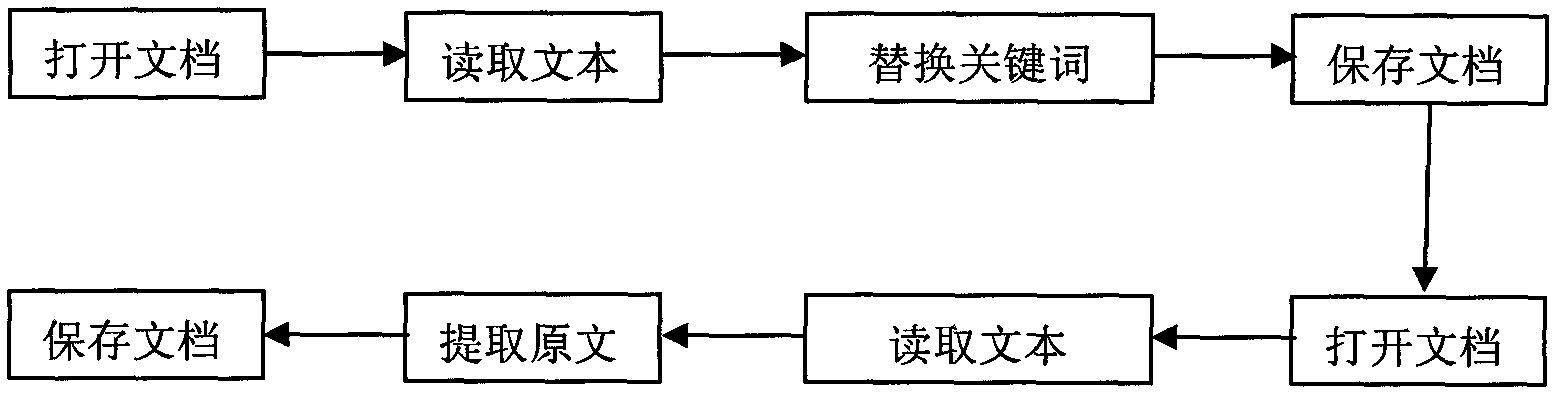
[0017] The following are examples of the present invention, however, the present invention is not limited to the examples.
[0018] When implementing it, it is necessary to consider the format of the file for steganography. Taking the format of the txt file as an example, first open the secret text with Notepad, and read the content of the text "she is a smart teacher, and her hometown is in Xinjiang". In the database, clever belongs to the keywords that are permanently replaced, replaced by stupid. Teachers, doctors, workers, farmers, and students are a group of non-fixed replacement keyword groups, which are numbered 0-4 in turn. 23 provinces and 4 municipalities belong to the non-fixed replacement keyword group, Xinjiang is among them, and they are They are numbered with 0-26 respectively, assuming Xinjiang is 8.
[0019] Select the algorithm for generating the key stream as a 256-bit stream cipher algorithm, and randomly generate 256 bits as the key K of the stream ciphe...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com