Method for protecting wireless beep pager by encoding handset codes
A technology of a messenger and a mobile phone, applied in the field of wireless messengers, can solve the problems of inability to know the information received by the messenger 22, loss of the operator, and inability to know.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
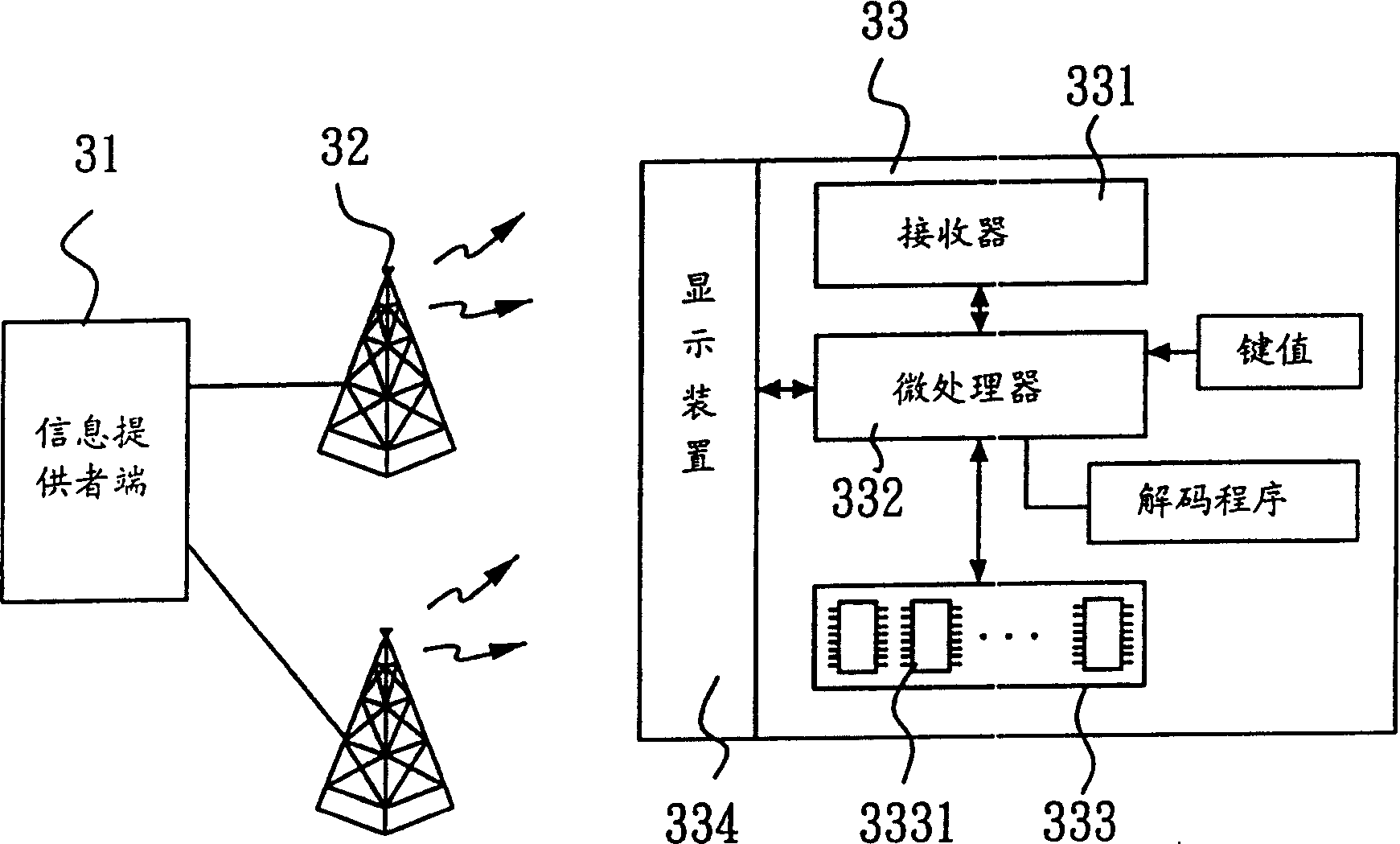
[0015] See first image 3 , which is an implementation state diagram of a preferred embodiment of the present invention, wherein the information provider terminal 31 transmits the information by the base station 32 in the form of wireless broadcast, and can be received by the communication machine 33, which has The receiver 331 , microprocessor 332 , memory 333 , and display device 334 are arranged so that the receiver 331 can receive wireless broadcast information, store it in the memory 333 and display it on the display device 334 . Wherein, the memory 333 also stores an encoded mobile phone code ciphertext, such as Figure 4 The shown mobile phone code ciphertext generation flow chart, this mobile phone code ciphertext is when the user uses the communication machine 33, the system operator executes an encoding program for the mobile phone code of the communication machine 33 with at least one key value (key) Gain, and store this mobile phone code cipher text in the memory ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com