A Text Steganography Method Based on Generative Adversarial Networks
A network and text technology, applied in the Internet field, can solve problems affecting the accuracy and fluency of text grammar, and achieve high-quality results
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0029] In order to deepen the understanding of the present invention, the present invention will be further described below in conjunction with the examples, which are only used to explain the present invention, and do not constitute a limitation to the protection scope of the present invention.
[0030] This embodiment discloses a text steganography method based on generating an adversarial network, which is characterized in that it includes:
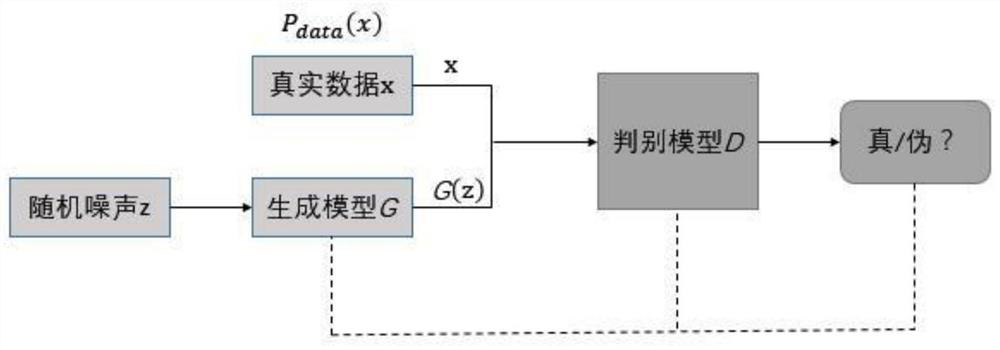
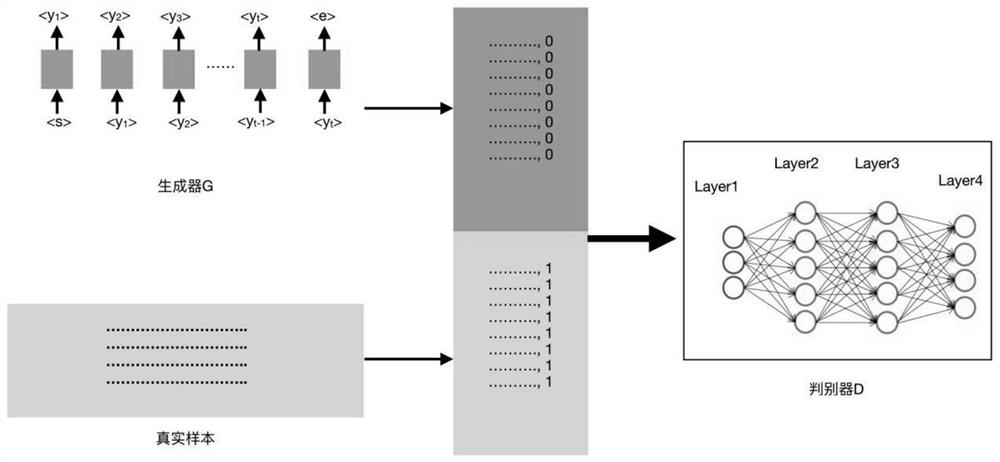
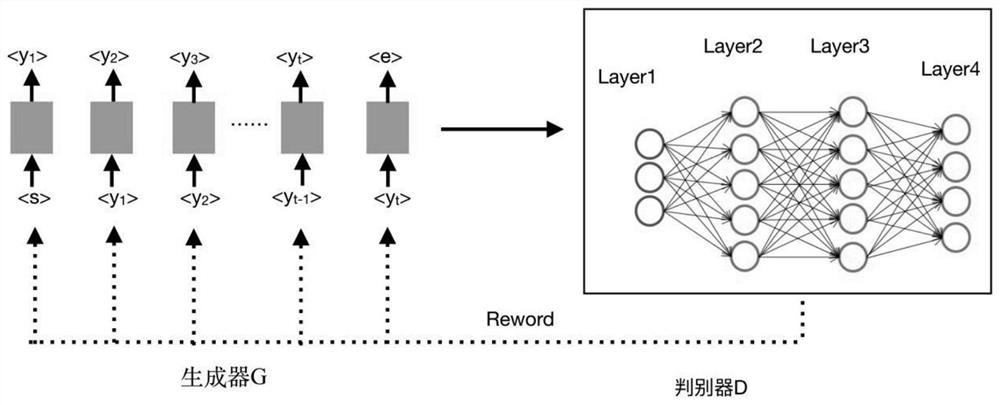
[0031] Text generation model based on Generative Adversarial Network (hereinafter referred to as GAN): Generative Adversarial Network consists of two parts, the first part is the raw network, the second part is the discriminant network, let the raw network and the discriminant network compete with each other, and generate false The confrontation network uses the discriminator to judge the authenticity of the data, and finally uses the data generated by the generation network to deceive the discriminator with the false ones;
[0032] Op...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com