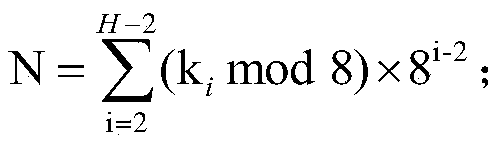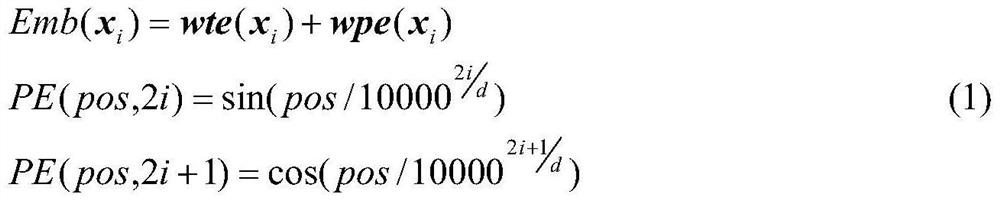Patents
Literature
56results about How to "Increase hidden capacity" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
H.264/AVC video information hiding method based on predictive mode
InactiveCN101621692AAchieve hiddenReduce the impact of objective qualityTelevision systemsDigital video signal modificationObjective qualityComputer architecture
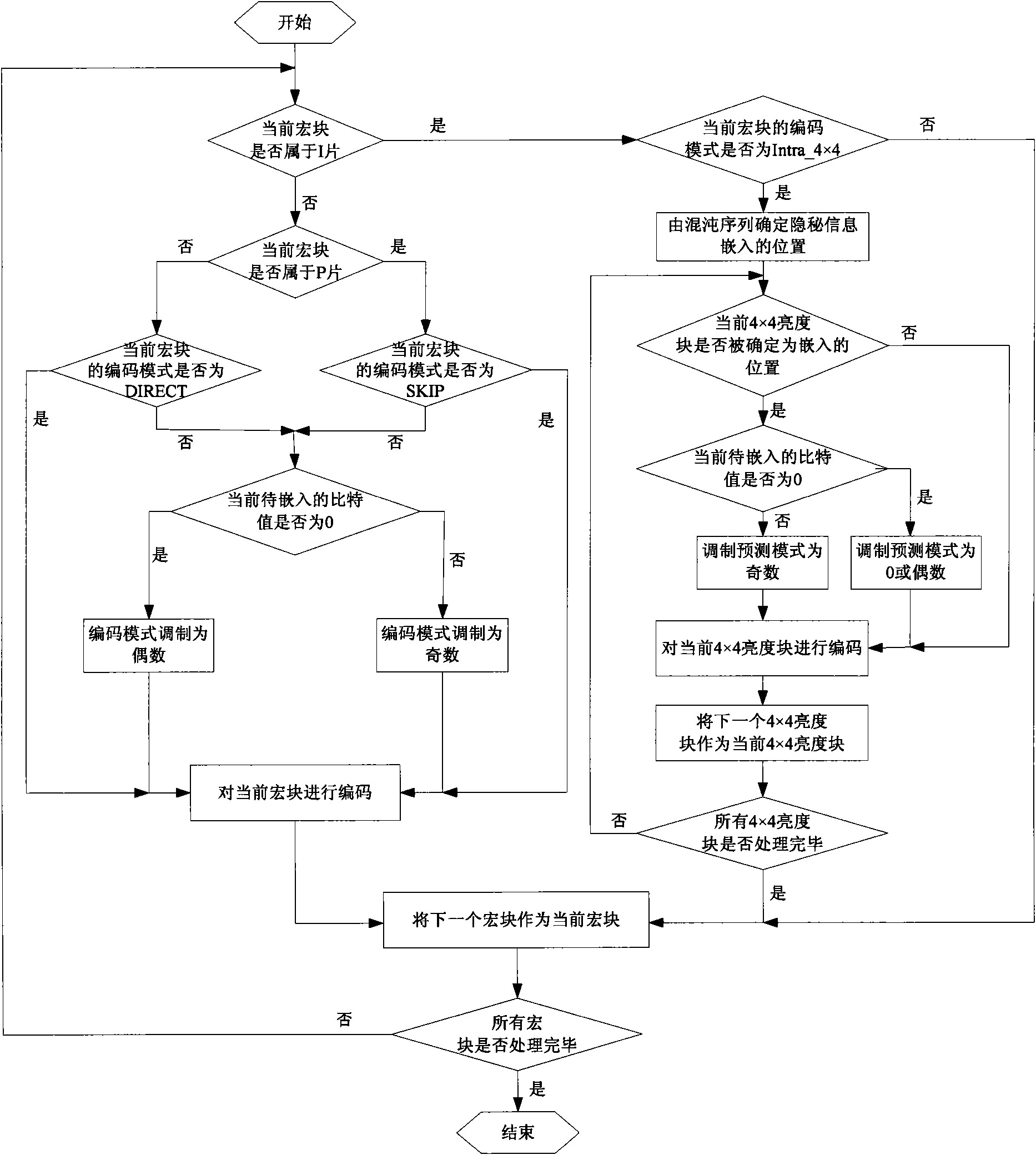
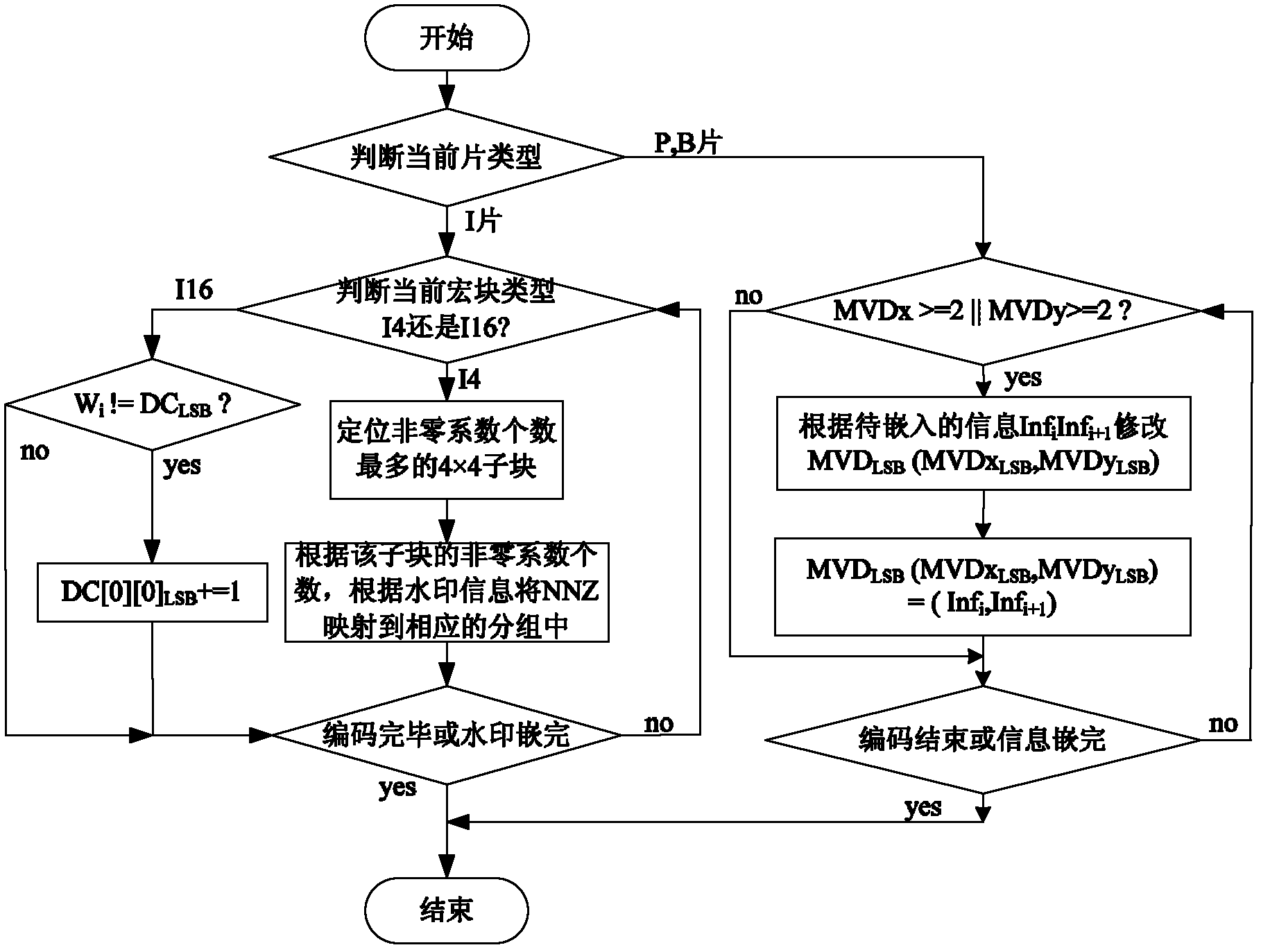
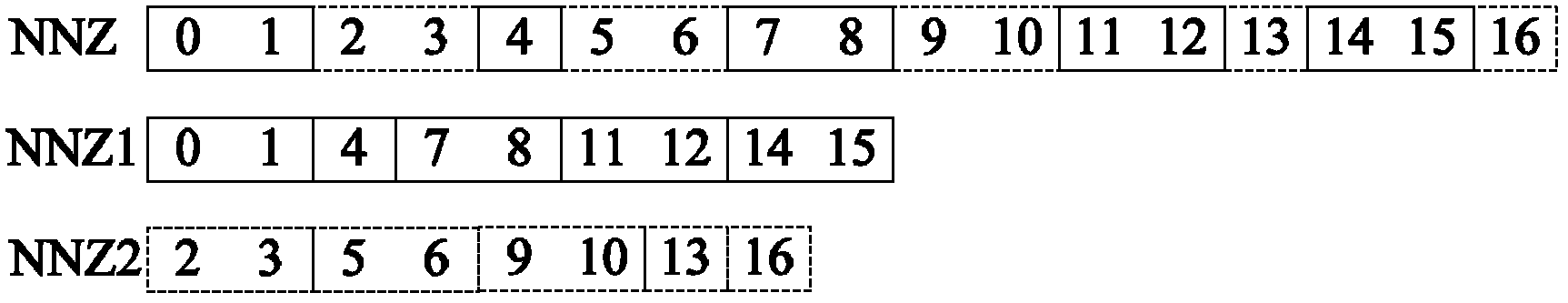
The invention discloses an H.264 / AVC video information hiding method based on a predictive mode. For a macro block whose coding mode is Intra_4*4 in an I chip, a predictive mode of a 4*4 luma block is modulated to a suboptimal predictive mode from an optimal predictive mode under the circumstance that the predictive mode of the 4*4 luma block needs to be changed, and for macro blocks whose coding modes are marked not by 0 in a P chip and a B chip, a coding mode of a macro block is modulated to a suboptimal predictive mode from an optimal predictive mode under the circumstance that the predictive mode of the macro block needs to be changed; the impact on the objective quality of a video, caused by the change of the predictive mode or the coding mode, can be reduced as much as possible under the circumstance of ensuring that the secret information can be effectively hidden at the same time; on the other hand, due to the fact that the secret information not only can be embedded in the macro block whose coding mode is Intra_4*4 in the I chip but also can be embedded in the macro blocks whose coding modes are marked not by 0 in the P chip and the B chip, the higher hiding capacity can be obtained.
Owner:NINGBO UNIV
Considerable information hide method using JPEG2000 compression image as carrier
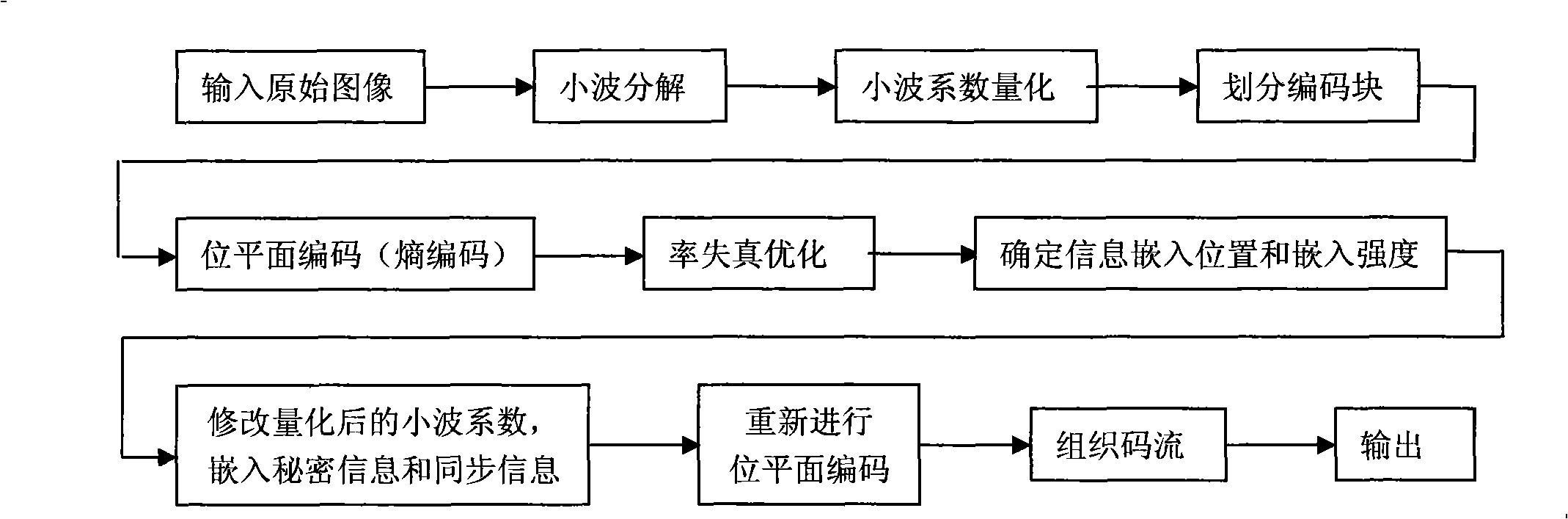
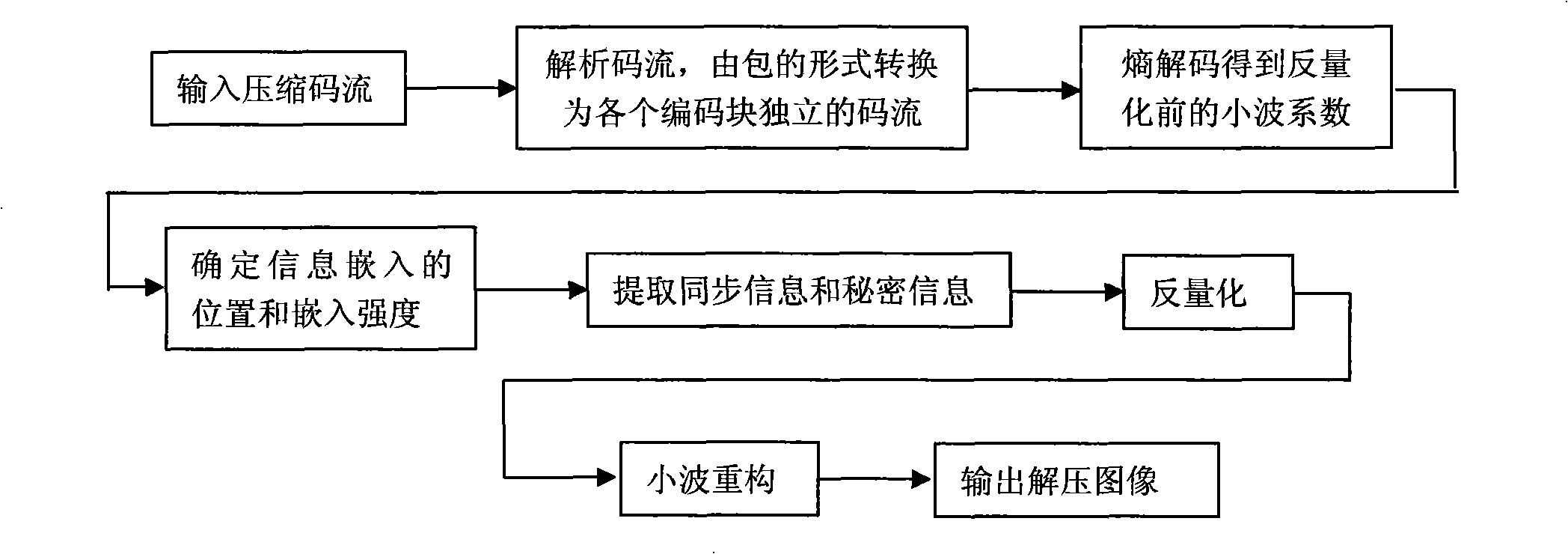
InactiveCN101304522AIncrease hidden capacityNormal decodingPulse modulation television signal transmissionImage codingCoding blockRate distortion
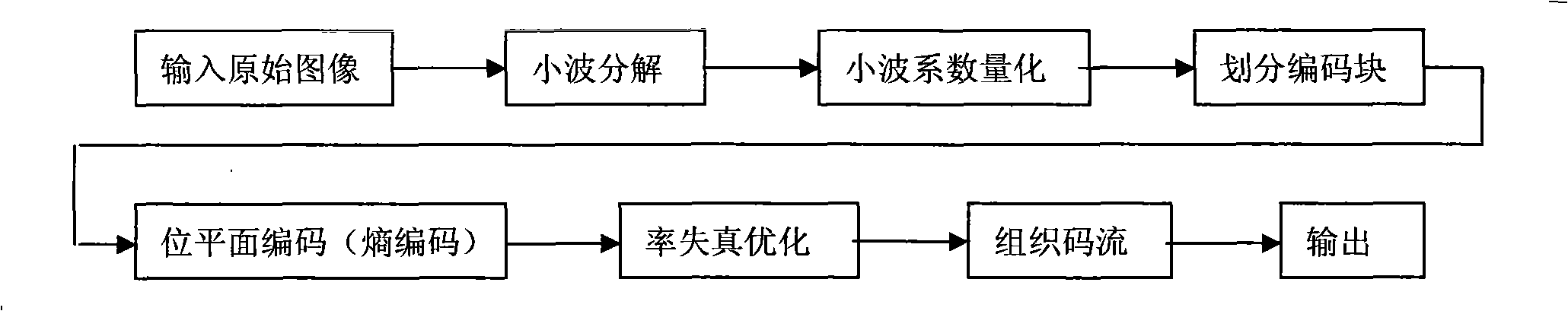
The invention relates to a high capacity information hiding method using JPEG2000 compressing images as the carrier. The operation steps are: applying wavelet decomposition, wavelet coefficients quantification and bit-plane coding to images, and determining the truncation position of the code flow of all coding blocks and the lowest bit-plane of the embeddable information by rate-distortion optimization; primarily choosing a wavelet coefficient which is more than the threshold value as the embedding point, and making a redundancy estimation and adjusting the embedding point and the embedding strength; embedding the synchronous information and the hidden information into the quantified wavelet coefficient in an order of the bit plane from the lowest to the highest starting from the lowest embeddable bit-plane; making a second bit-plane coding and organizing the code flow after embedding the information. The high capacity information hiding method is based on a second coding strategy to determine the embedding position and improves the information hiding volume by self-adaptively choosing the embedding point and adjusting the embedding strength, The high capacity information hiding method has the advantages of being transparent completely for the standard JPEG2000 decoders and being able to be conveniently integrated in the JPEG2000 coders. Meanwhile, the code flow still can decode normally after being embedded with hiding information.
Owner:CIVIL AVIATION UNIV OF CHINA
Information hiding method facing to H.264/AVC (automatic volume control) video
InactiveCN102223540AEnsure safetyIncrease hidden capacityTelevision systemsDigital video signal modificationAutomatic controlMotion vector
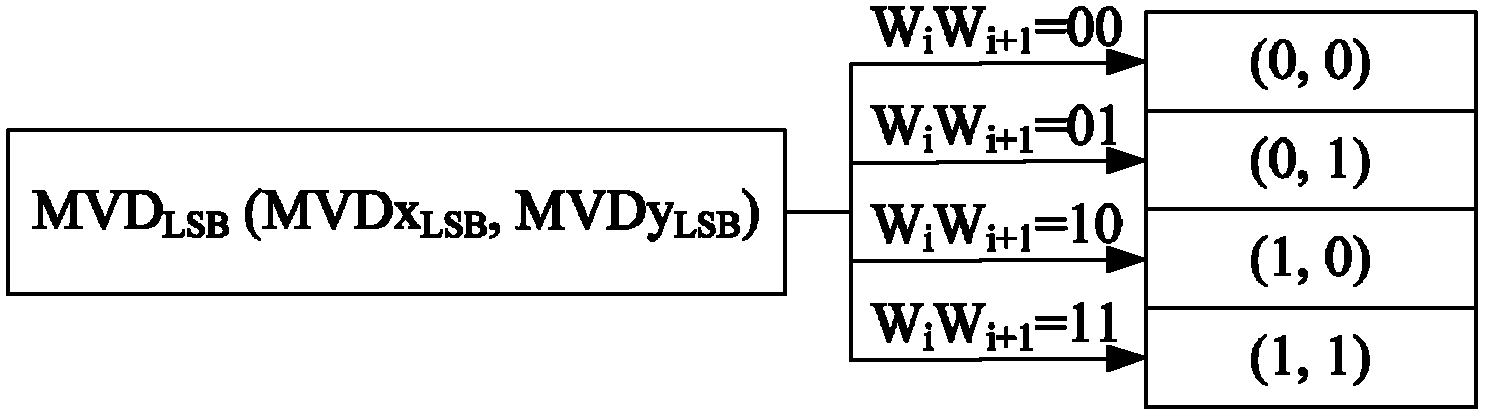
The invention discloses an information hiding method facing to an H.264 / AVC (automatic volume control) video. The embedding of watermark information is realized through modifying a data communication terminal (DCT) coefficient of a frame I, but for a frame B and a frame P, the embedding of the hiding information is realized through modifying motion vector data (MVD), thus on one hand, the embedded watermark information can be used for authenticating the integrity of the content of the video streaming, and on the other hand, whether the video is attacked is judged, and whether the extracted information is credible and the like at an information detection end according to the integrity of the extracted watermark information, thus ensuring the safety of the private information; as the frame P and frame B in a video sequence are divided into a motion subblocks from the size range of 16*16 to 4*4; the smaller subblock division provides a large amount of MVD data which can provide for hiding the private information, thus the video has larger information hiding capacity; and the process extracting the information is simple and rapid, does not need an original video file for reference, and only needs to decode the DCT coefficient of the frame I and the MVD data of the frame B and frame P, thereby effectively improving the instantaneity and the practicability.
Owner:NINGBO UNIV
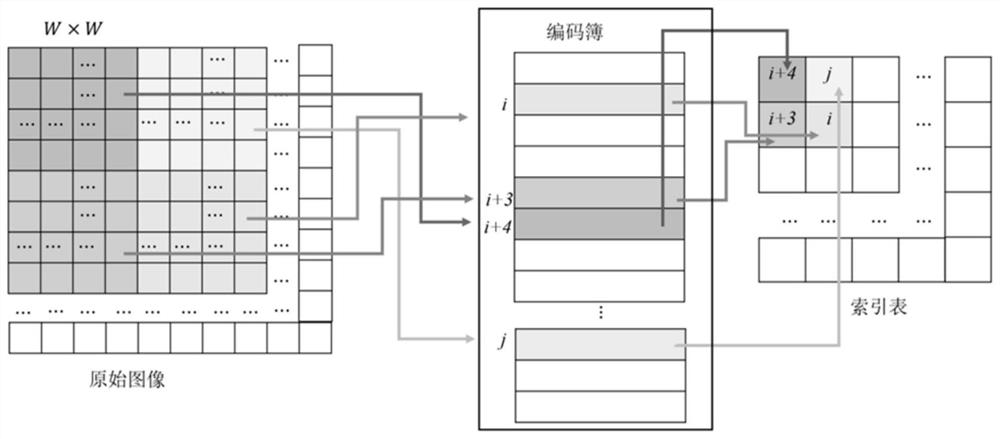
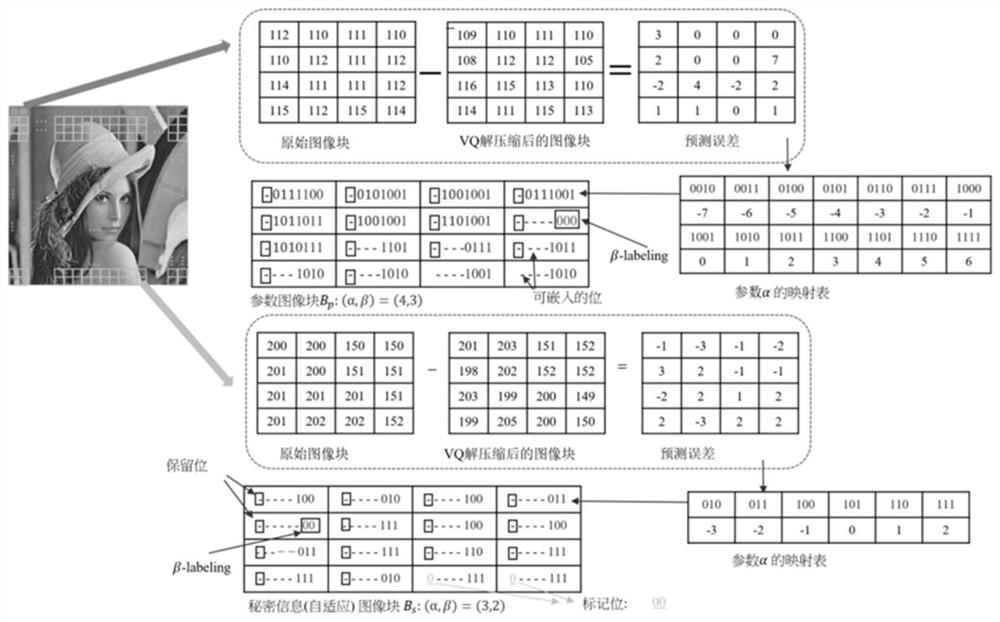
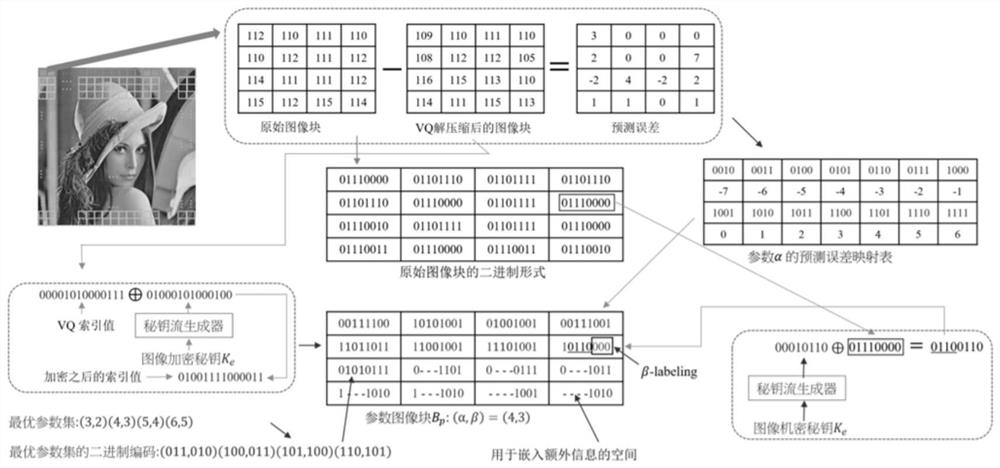
Reversible information hiding method of encryption image based on coding compression
ActiveCN107493405AEasy to compressIncrease hidden capacityPictoral communicationImage basedLossless compression
The invention discloses a reversible information hiding method of an encryption image based on coding compression. The method comprises steps of dividing an original image into a prediction region and a non-prediction region before encryption, calculating a pixel prediction vale of the prediction region so as to obtain a prediction difference value and carrying out lossless compression on the prediction difference value to obtain compression data; and randomly generating carrier data and carrying out image encryption and reconstruction on non-precision pixels, the compression data and the carrier data. In order to correctly restore the original image, code table hidden information should be determined and by hiding the code table information and the secret information in the carrier data, reversible hiding is achieved. For the carrier image, secret information is extracted in the carrier data; then, the non-prediction pixels and the compression data are decrypted; according to the code table information, the compression data is decompressed so that the prediction difference value is obtained; and finally, according to the non-prediction pixels and the prediction difference value, the original image is restored in a lossless manner. Compared with the prior art, the provided method has quite big hiding capacity; reversible hiding can be completely achieved; and the method has high actual application value.
Owner:GUANGXI NORMAL UNIV
Adaptive image encryption domain reversible hiding method based on hybrid encryption mechanism
ActiveCN108566500AReduce management difficultyAvoid elevationKey distribution for secure communicationPictoral communicationSelf adaptivePixel classification
The invention discloses an adaptive image encryption domain reversible hiding method based on a hybrid encryption mechanism. A user performs sequential prediction on a digital image to be encrypted toobtain the pixel type identification matrix of an original image, and adaptively selects an optimal block size of the pixel type identification matrix to generate an optimal block type identificationmatrix; a random number is taken as a secret key to combine the block type identification matrix, and 'xor plus pixel classification scrambling' is used for generating an encrypted image of the original image; the random number is taken as a secret key to encrypt partial information of the block type identification matrix, the public key of a receiver uses an asymmetric encryption algorithm to encrypt 'the random number, the residual block type identification matrix information and the optimal block size', which are then serially embedded into a variable pixel of the encrypted image; the receiver uses a private key to decrypt the extracted key information and can obtain a decrypted image the same as the original image and a plaintext image with additional information through sequence recovery. The method reduces the difficulty of secret key management, improves the security of image transmission, and brings convenience for cloud management.
Owner:SOUTHWEST JIAOTONG UNIV
Text carrier-free information hiding method based on tag model
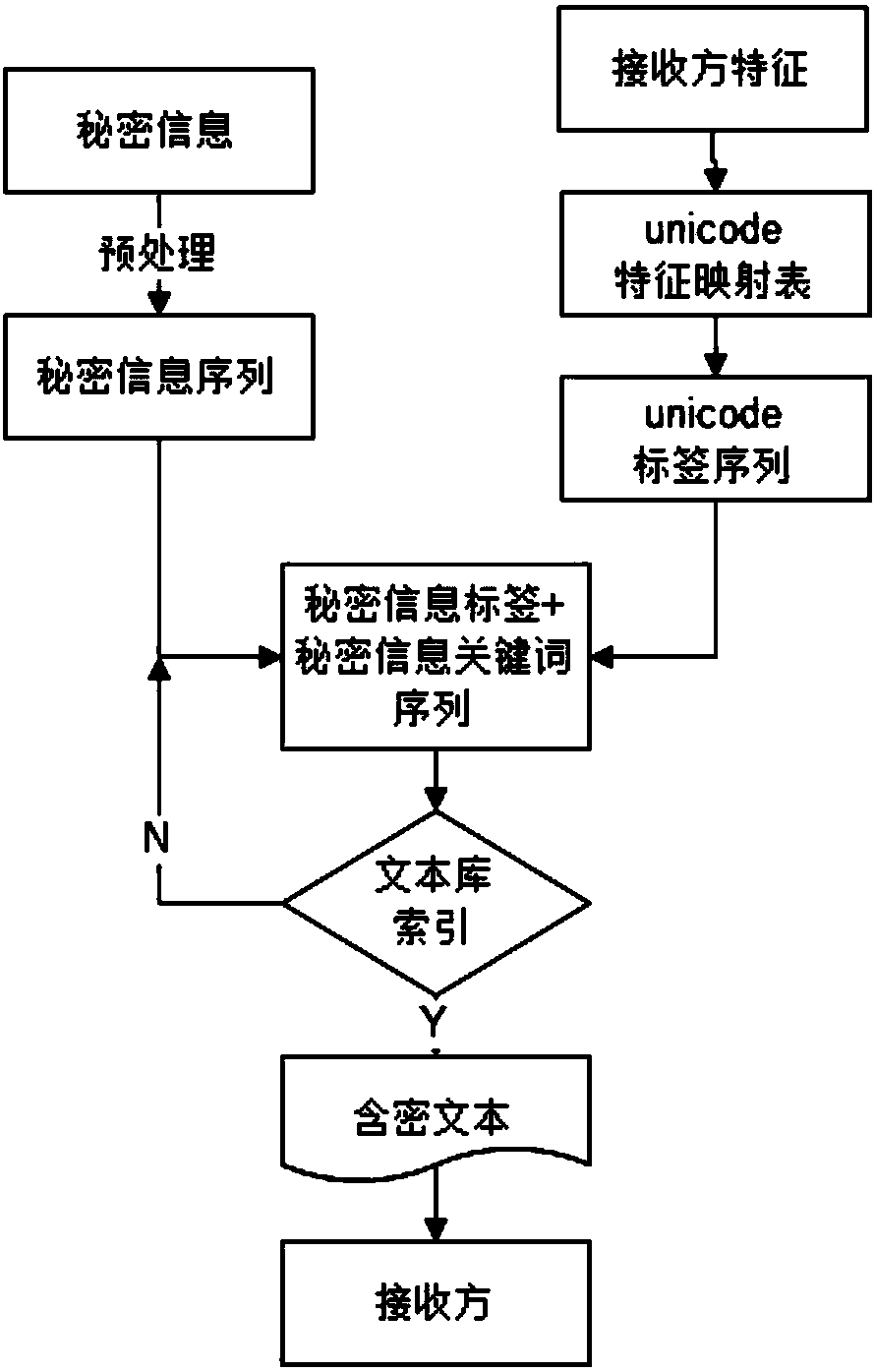
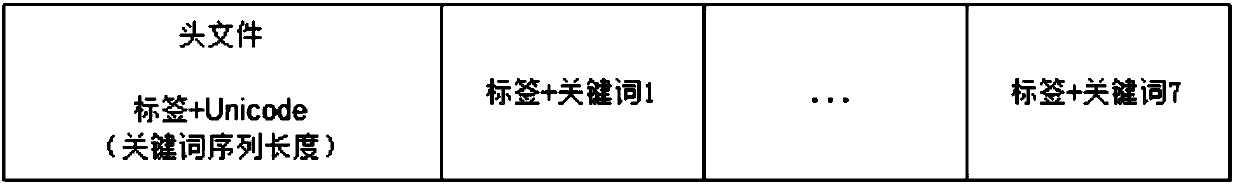
ActiveCN107609356AGuaranteed success rateIncrease hidden capacityTransmissionProgram/content distribution protectionChinese charactersTheoretical computer science
The invention provides a text carrier-free information hiding method based on a tag model. The method comprises the following steps that: collecting texts, and establishing indexes; hiding secret information: preprocessing the secret information to obtain the keyword sequence of the secret information; using the Unicode of Chinese characters as a secret information tag, and carrying out calculation according to the corresponding features of a receiver to obtain a secret information tag sequence; constructing a header file and a cipher containing text; through text index entries, selecting target text information corresponding to the header file and the cipher containing text one by one from a text library; and arranging all target text information in sequence, and sending the target text information to the receiver as a hidden text. By use of the method, while a hiding success rate is guaranteed, hiding capacity is improved.
Owner:NANJING UNIV OF INFORMATION SCI & TECH
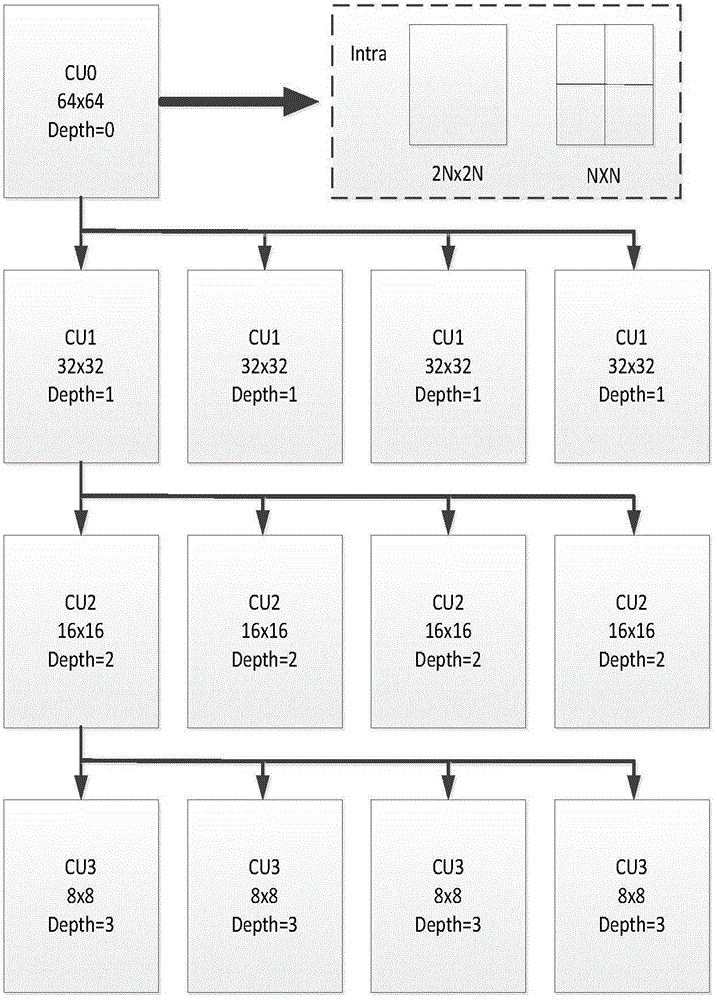
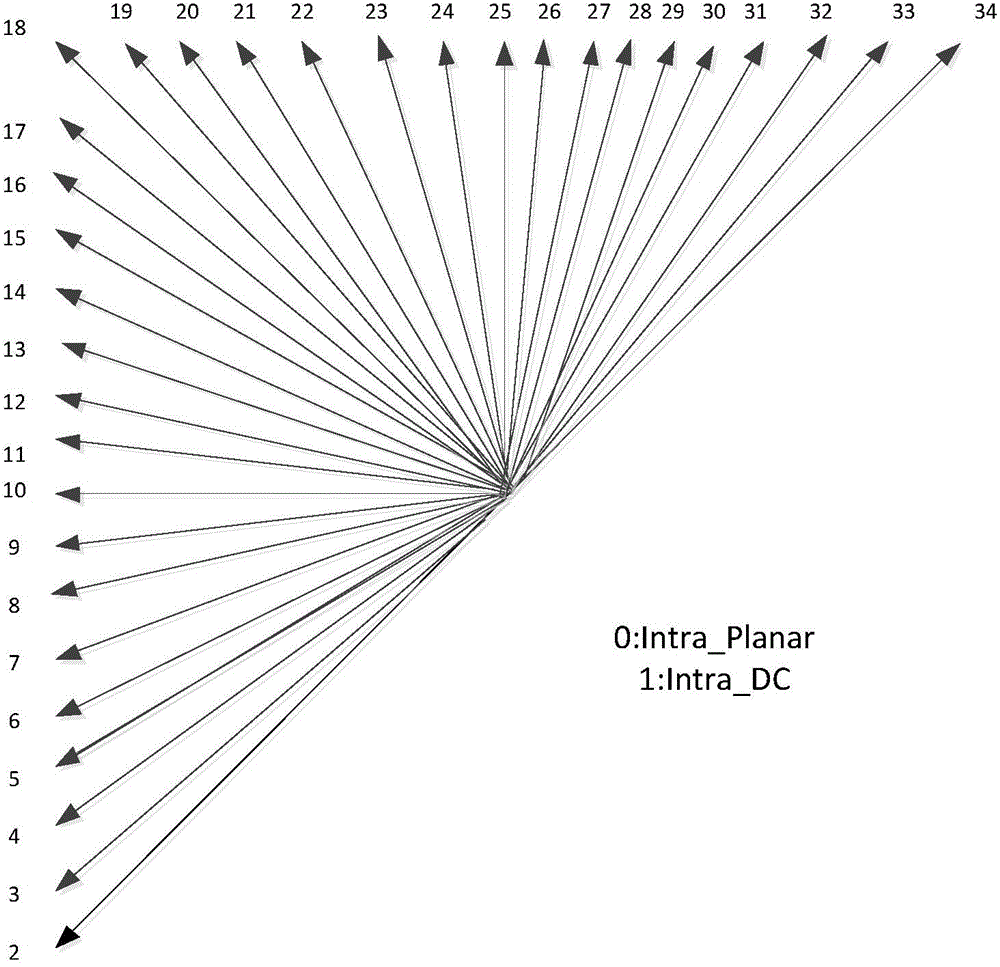
HEVC video information hiding method based on intra-frame prediction mode difference
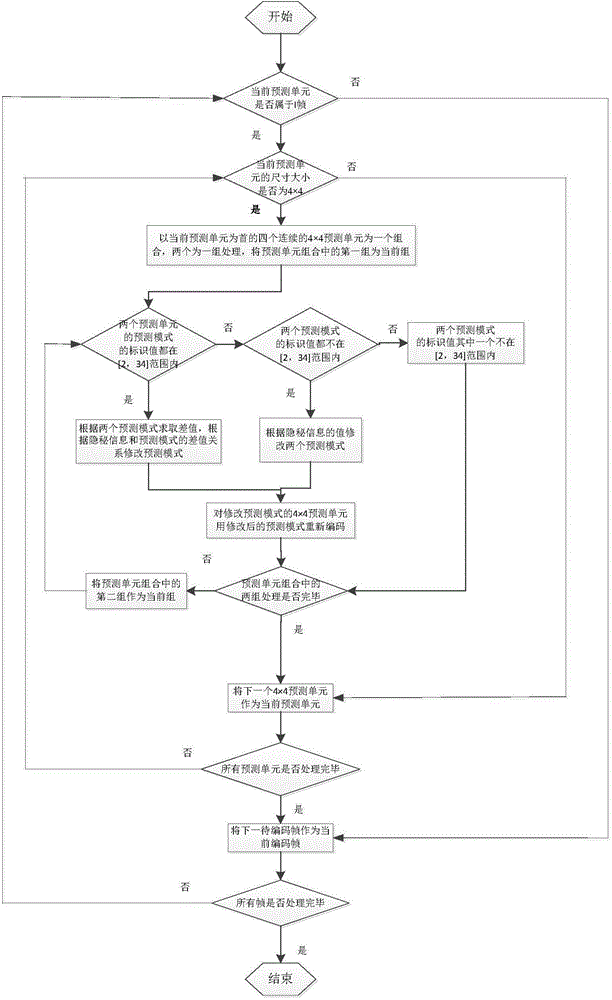
InactiveCN104602016AIncrease hidden capacitySubjective and objective quality declineDigital video signal modificationVideo qualityAlgorithm
The invention discloses an HEVC video information hiding method based on intra-frame prediction mode difference. The HEVC video information hiding method based on the intra-frame prediction mode difference includes that modulating a prediction mode and embedding secret information in an intra-frame prediction coding process for a 4*4 prediction unit through analyzing an HEVC coding and decoding structure, and using the difference between prediction modes of two continuous 4*4 prediction units to embed two-bit or three-bit secret information according to different mapping rules to improve the hiding capacity. Because the prediction mode correction greatly influences the subjective and objective quality of the video after embedding the secret information, the HEVC video information hiding method based on the intra-frame prediction mode difference embeds the two-bit secret information for two prediction units with prediction modes 0 or 1 according to the parity modification prediction mode of the secret information and embeds the three-bit secret information for two prediction units with directional prediction modes through the difference between the prediction modes of two prediction units, and the secret information is not embedded under the other situations; the HEVC video information hiding method based on the intra-frame prediction mode difference lowers the video quality reduction due to embedding secret information.
Owner:NINGBO UNIV
Text information hiding method resistant to statistic analysis
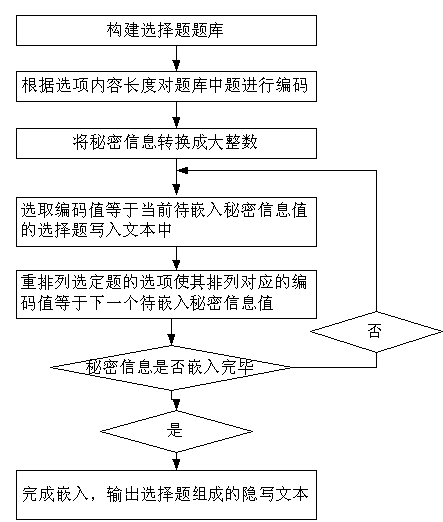
InactiveCN103294959ADoes not affect statistical propertiesIncrease hidden capacityDigital data protectionSubject specificMachine learning
The invention provides a text information hiding method resistant to statistic analysis. The text information hiding method includes that a sender collects a large number of choice questions with the same theme and establishes a question bank which is not required to be shared with a receiver; the sender has the choice questions of the question bank coded based on length of option contents, and selects the choice questions with specified coded values according to secret information and a vivid steganographic text is automatically generated, meanwhile, inserts extra secret information into option arrangement orders of the choice questions of the steganographic text, and rectification of the option display order cannot affect concrete content and various statistical characteristics of the choice questions. Extraction of the secret information can be acquired by calculating the coded values of each question of the steganographic text based on the length of the option contents and the option arrangement orders. The text information hiding method resistant to the statistic analysis is good in hiding performance, large in hiding capacity and strong in resistance to the statistic analysis.
Owner:NANJING UNIV OF INFORMATION SCI & TECH
Data hiding method based on image set
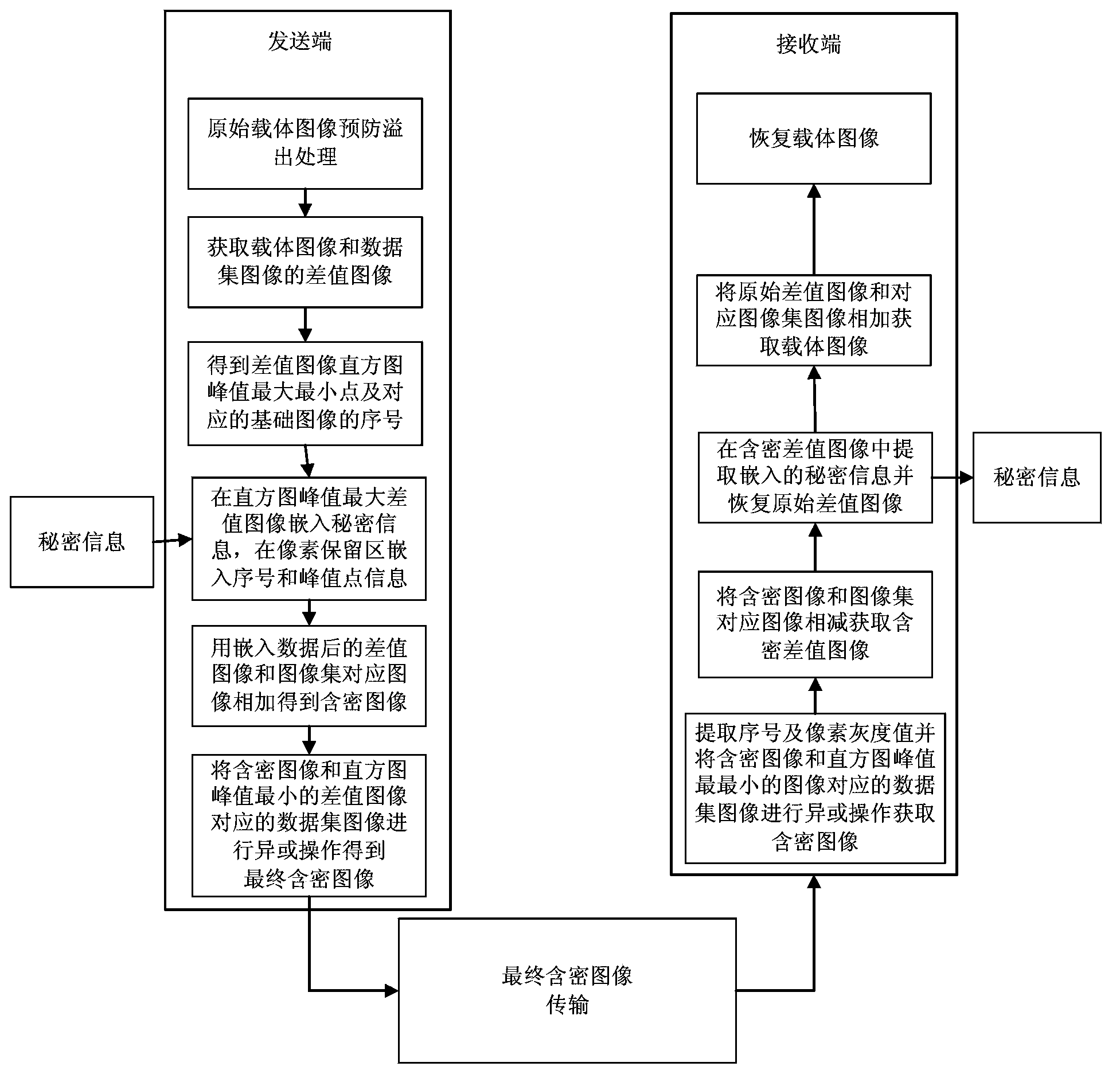
ActiveCN103414840AExcellent hidden capacityExcellent qualityImage enhancementPictoral communicationImage extractionHidden data
The invention discloses a data hiding method based on an image set. The data hiding method comprises the step of carrying out anti-overflow process on an original carrier image, the step of developing a reserved pixel area, the step of generating a carrier image, the step of respectively carrying out subtraction on the carrier image and a basic image in the built image set to obtain difference images and histogram information, the step of regarding the difference image which has largest peak value of a histogram as a carrier and hiding data based on the information hiding method of the histogram, the step of hiding label information corresponding the difference image which has the largest peak value of the histogram and the difference image which has the lowest peak value of the histogram based on the reserved pixel area serving as the carrier, the step of adding a secret containing difference image and the corresponding image in the image set to obtain a secret containing image, the step of carrying out xor operation on the secret containing image and the basic image corresponding to the lowest histogram peak value to obtain a secret containing carrier image to be transmitted, and the step of extracting label information from the secret containing carrier image through a receiving terminal, carrying out the information hiding inverse process and recovering hidden data and hidden carrier images. The capacity of information hiding is improved through the image set, and safer lossless data hiding is achieved.
Owner:XIAN INSTITUE OF SPACE RADIO TECH
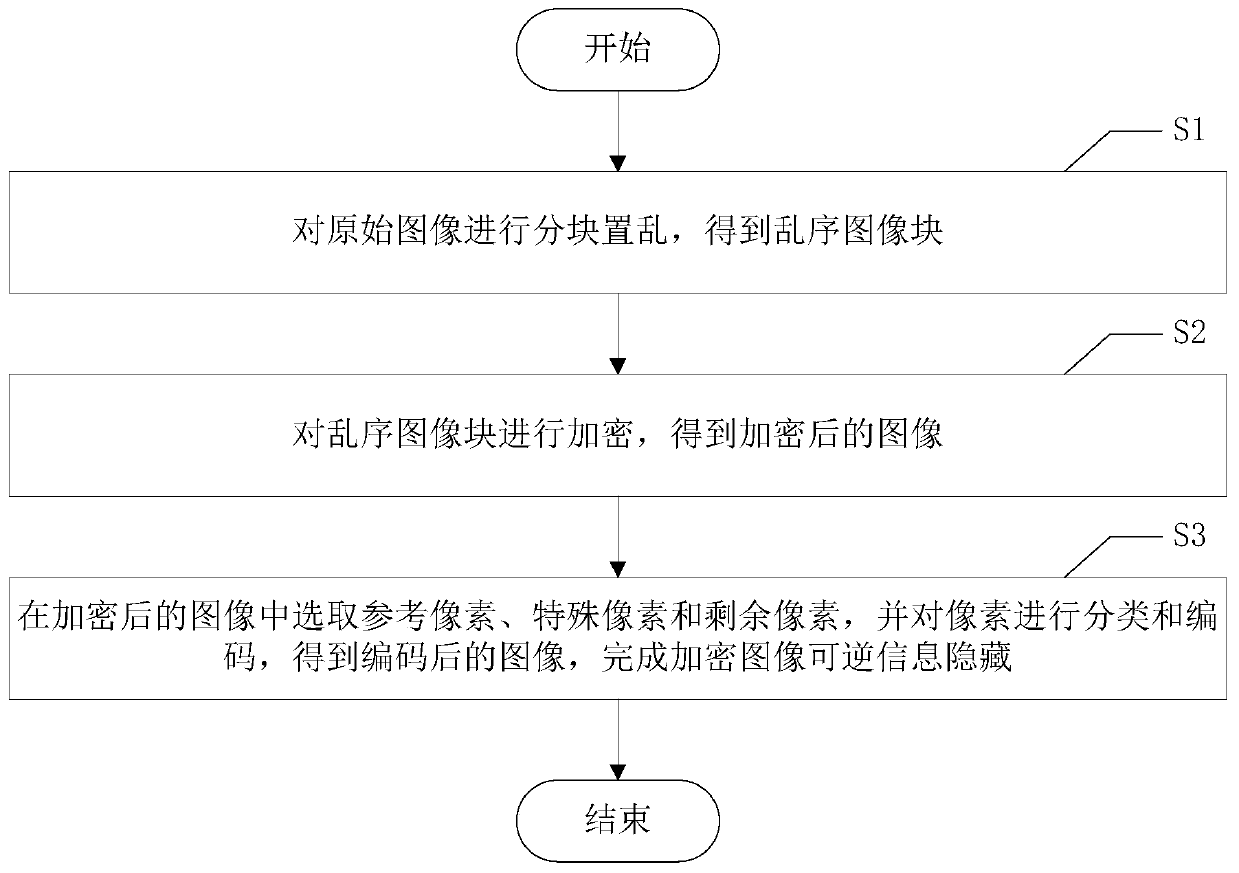
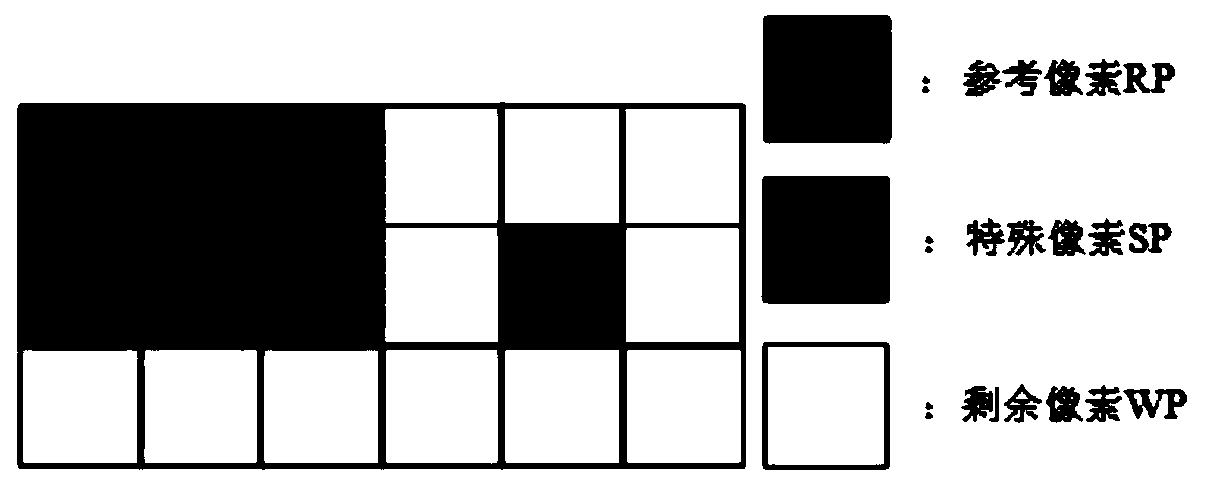
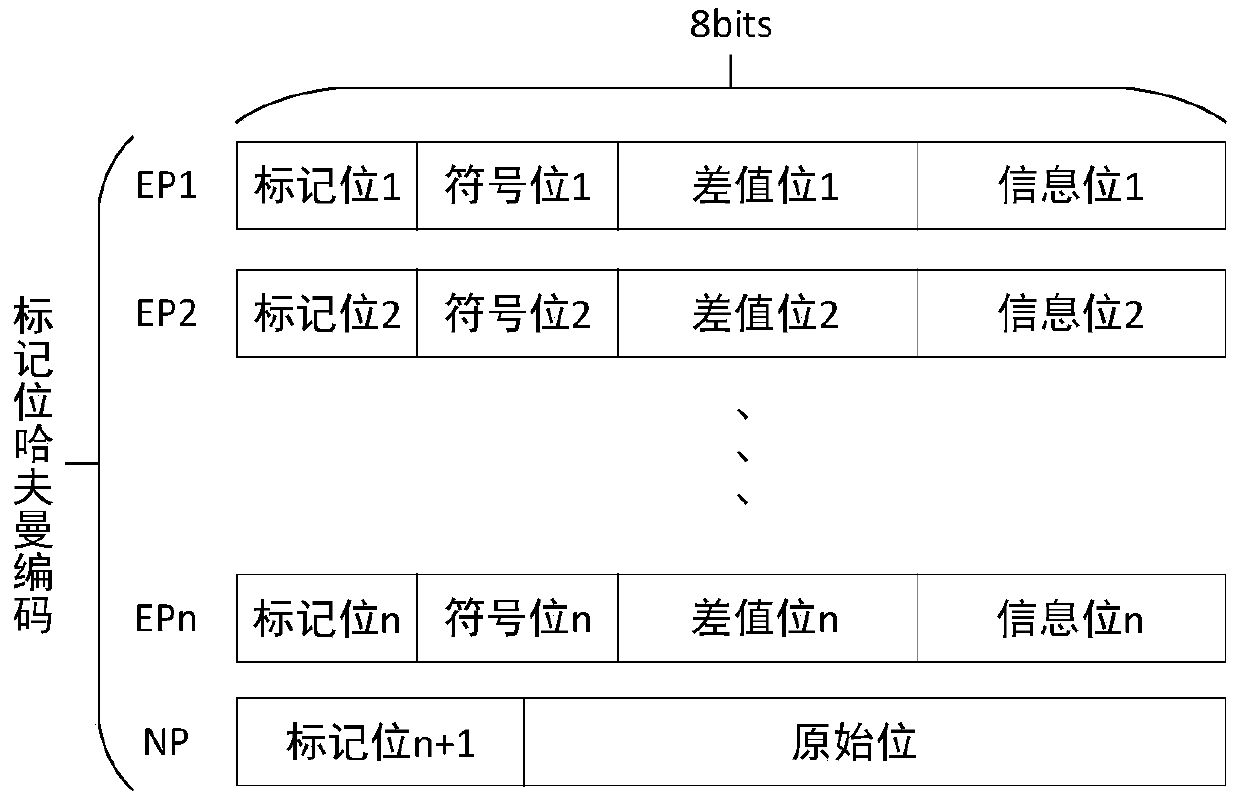
Encrypted image reversible information hiding method
ActiveCN110913092AIncrease hidden capacityGood buffPictoral communicationPattern recognitionEmbedding rate
The invention discloses an encrypted image reversible information hiding method, which comprises the following steps of S1, performing block scrambling on an original image to obtain out-of-order image blocks; S2, encrypting the out-of-order image blocks to obtain an encrypted image; and S3, selecting a reference pixel, a special pixel and residual pixels from the encrypted image, and classifyingand encoding the pixels to obtain an encoded image, thereby completing reversible information hiding of the encrypted image. According to the method, the image redundancy characteristic can be fully utilized by the adaptive coding method, compared with an existing related coding method, higher information hiding capacity can be achieved, and especially for a smooth image, the gain effect of the embedding rate is particularly remarkable.
Owner:四川中油优途电子商务有限责任公司
Carrier-free information hiding method for big data Chinese text
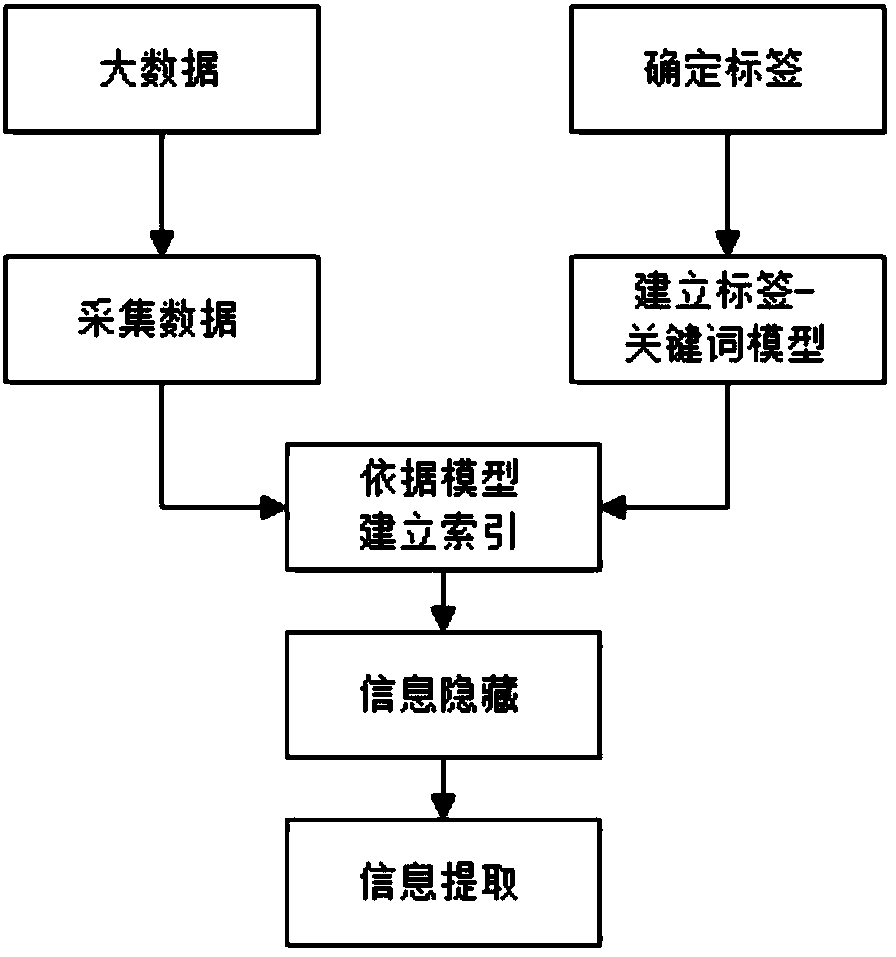
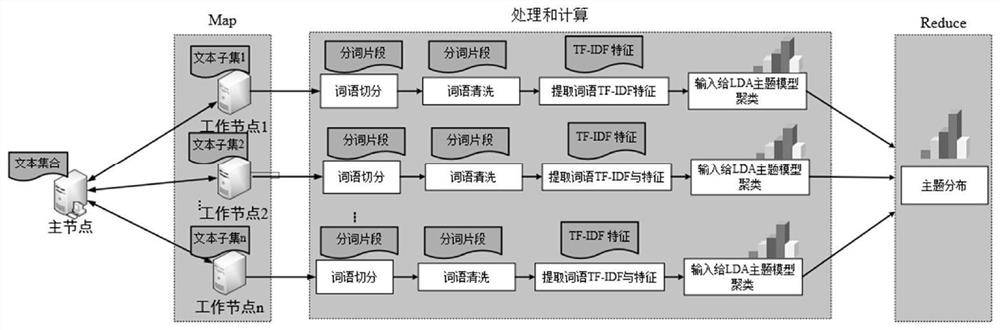
PendingCN111797409AEnsure safetyImprove concealmentDigital data protectionNatural language data processingPattern recognitionInformation hiding
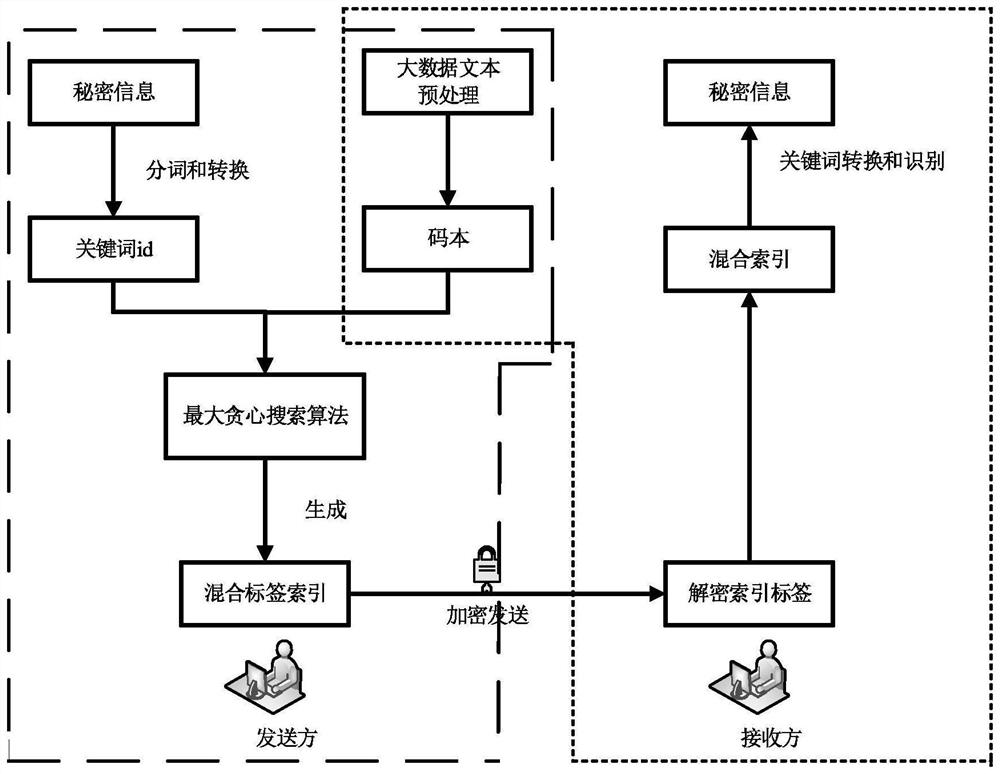
The invention discloses a carrier-free information hiding method for a big data Chinese text, and the method comprises: firstly carrying out preprocessing of the big data Chinese text, and mainly comprises word segmentation of the text, calculation of the word frequency and TF-IDF feature information of words after word segmentation, and LDA topic model clustering of the text; then, the sender segments the secret information, converts the secret information into keyword IDs through a word index table, and searches a text containing secret information keywords in the big data text; and, secondly, the searched text is used as an index label according to theme distribution of the corresponding text and TF-IDF characteristics of keywords in the corresponding text, meanwhile, a random number isintroduced to control the sequence of the secret information keywords, and finally, the random number and the index are used as labels together to be encrypted and sent to a receiver. Experiments show that the method improves the concealment and security of secret information while improving the concealment capacity.
Owner:CENTRAL SOUTH UNIVERSITY OF FORESTRY AND TECHNOLOGY
Reversible watermarking method based on image topological structure
ActiveCN108805788AIncrease hidden capacityKeep topological invarianceImage data processing detailsVisual perceptionHistogram
A reversible watermarking method based on an image topological structure belongs to the field of multimedia information security. The invention relates to a binary image reversible watermarking methodbased on the image topological structure. According to the reversible watermarking method, the image topological structure is used for replacing image pixel values to serve as horizontal coordinatesof a histogram, so that the invariance of the topological structure is guaranteed; and the statistical histogram is generated and embedded with watermark information. The method is suitable for a binary image; the visual quality of the watermark-containing binary image is improved; and double-layer watermark information can be embedded in combination with an existing gray image reversible watermarking algorithm, so that the hidden capacity of an existing algorithm is expanded and the universality of the algorithm is improved.
Owner:NANKAI UNIV
High-order airspace hiding method for resisting sample pair analysis
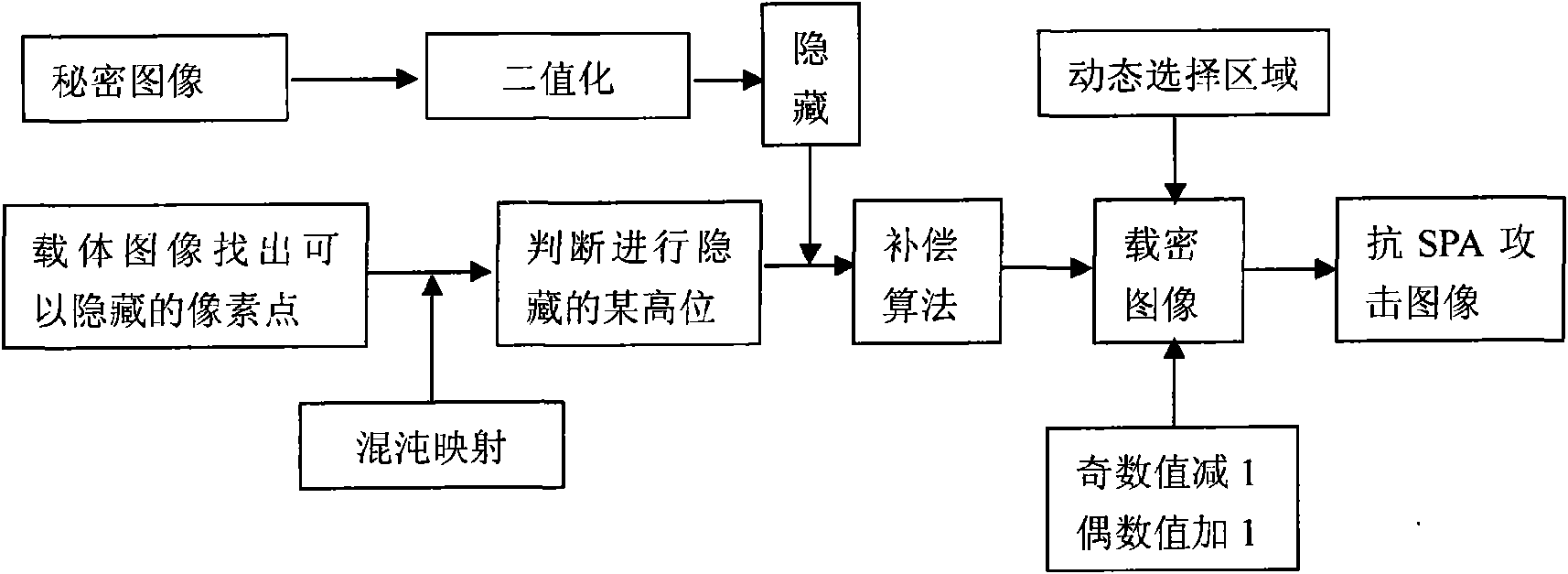
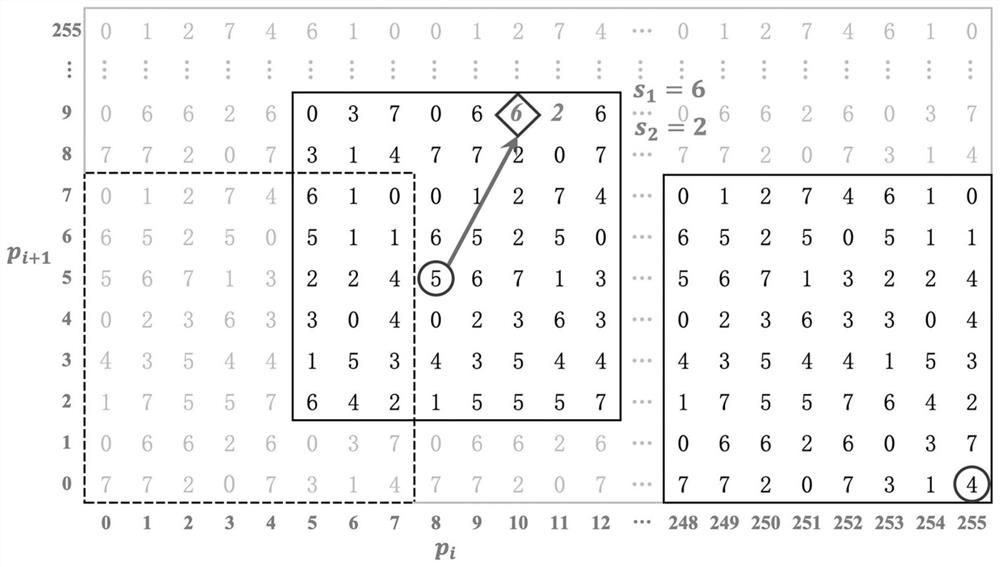
InactiveCN101561922AGuaranteed ability to resist attacksIncrease hidden capacityImage data processing detailsBinary informationComputer vision
The invention relates to a high-order airspace hiding method for resisting sample pair analysis. The information hiding technology is a new research topic in the information security field in recent years. The technology is to hide secret information in other carriers to go beyond the awareness of people so as to ensure the security of secret information. The high-order airspace hiding method for resistable sample pair analysis comprises the following steps: finding a pixel point capable of performing high-order hiding in a carrier gray level image with a size of N1xN2, converting the to-be-hidden secret image with a size of M1xM2 into binary information stream, determining on which position of the carrier image the binary information stream is hidden through Logistic chaos mapping, the Logistic chaos mapping formula being Z(n+1)=4Zn(1-Zn), wherein Zn belonging to (0,1); if the secret information is identical to the bit information, substitution is not performed, and otherwise, substitution is performed, then necessary compensation algorithm is performed to control the variation range of the pixel points within four pixels, then repeating the process till all information is hidden. The invention is used for information hiding technology.
Owner:HARBIN UNIV OF SCI & TECH
Reversible information hiding method for code groups
ActiveCN105430228AIncrease hidden capacityImprove applicabilityPictoral communicationRelationship extractionInformation hiding
The invention discloses a reversible information hiding method for code groups. 2bit in hidden information bit stream is converted into a decimal digit as a unit, 16 kinds of different codes in the converted decimal information are grouped, a hiding algorithm for each group of codes is established, and a one-to-one corresponding relation between code groups and carrier information is obtained. When information is hidden, statistics on the occurrence frequency of hidden information code groups is collected, the hidden information code groups are ranked, and the code groups occurring high frequently are hidden into the carrier information needing a few carriers, so that the hiding capacity is improved. When secret information is extracted, the code groups can be extracted according to the corresponding relation and decoded to obtain hidden information, and the carrier information is restored. The reversible information hiding method achieves high hiding capacity.
Owner:贵州无聊科技服务有限公司
H.264/AVC video bitstream oriented large volume data hiding method
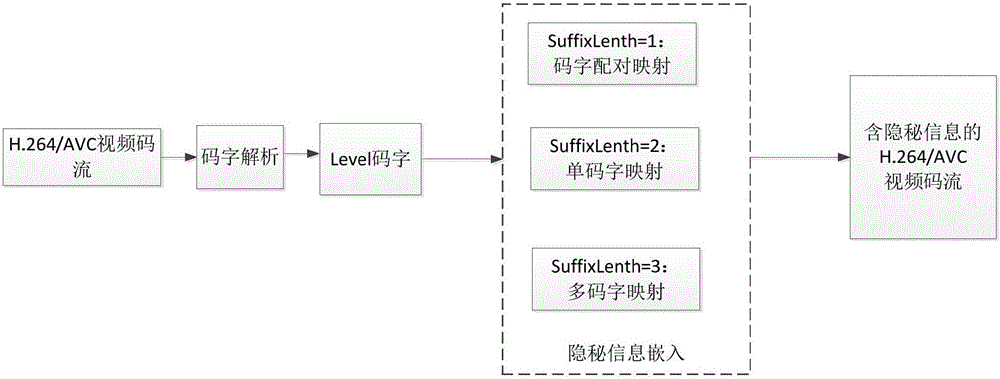
ActiveCN105141962AMeet application needsIncrease hidden capacityDigital video signal modificationDigital videoInformation extraction
The invention discloses an H.264 / AVC video bitstream oriented large volume data hiding method, which comprises hidden information embedding and hidden information extraction. The hidden information embedding and the hidden information extraction are directly carried out in an H.264 / AVC bitstream domain, and decoding or partial decoding is unnecessary for the H.264 / AVC bitstream, so that the H.264 / AVC video bitstream oriented large volume data hiding method can well satisfy an application demand of real-time videos. Classification is carried out based on a suffix length of a Level codeword, and information bits in the hidden information are embedded by respectively adopting codeword pairing, single-codeword mapping and multi-codeword mapping, so that data hiding volume of the method is much greater than that of an existing single-codeword mapping; the bitstream structure of the original H.264 / AVC video bitstream is unchanged after the hidden information is embedded by utilizing the method, so that the problems such as increase of a coding bit rate of the whole digital video and change of a file length, caused by the hiding operation, are avoided efficiently, and the hiding security of hidden data is ensured efficiently.
Owner:NINGBO UNIVERSITY OF TECHNOLOGY
Reversible data hiding method for high dynamic range image
ActiveCN104021518AIncrease hidden capacityImprove visual effectsImage data processing detailsPattern recognitionImaging quality
The invention discloses a reversible data hiding method for a high dynamic range image. The reversible data hiding method comprises a data embedding process and a data extracting process, wherein the data extracting process is inverse operation of the data embedding process, and the data embedding process comprises the following steps of converting a rgb image into an RGBE image, and dividing to-be-embedded data into three parts in sequence for embedding the three parts into rgb three channels corresponding to the RGBE image; dividing all pixels of a certain embedding channel of the rgb three channels into two types: S1 and S2, dividing the corresponding embedded data into two types corresponding to S1 and S2, wherein in an embedding process, one type of data is embedded to S1, and then the same process is repeated for embedding the other type of data to S2. The reversible data hiding method disclosed by the invention achieves a purpose of embedding more data by sacrificing least image quality. Compared with the existing reversible HDR (high dynamic range) image hiding algorithm, the hiding algorithm disclosed by the invention improves hiding capacity simultaneously when guaranteeing reversible hiding, and guarantees a better visual effect.
Owner:SHANDONG UNIV
Encryption domain three-dimensional model reversible information hiding method based on prediction error extension
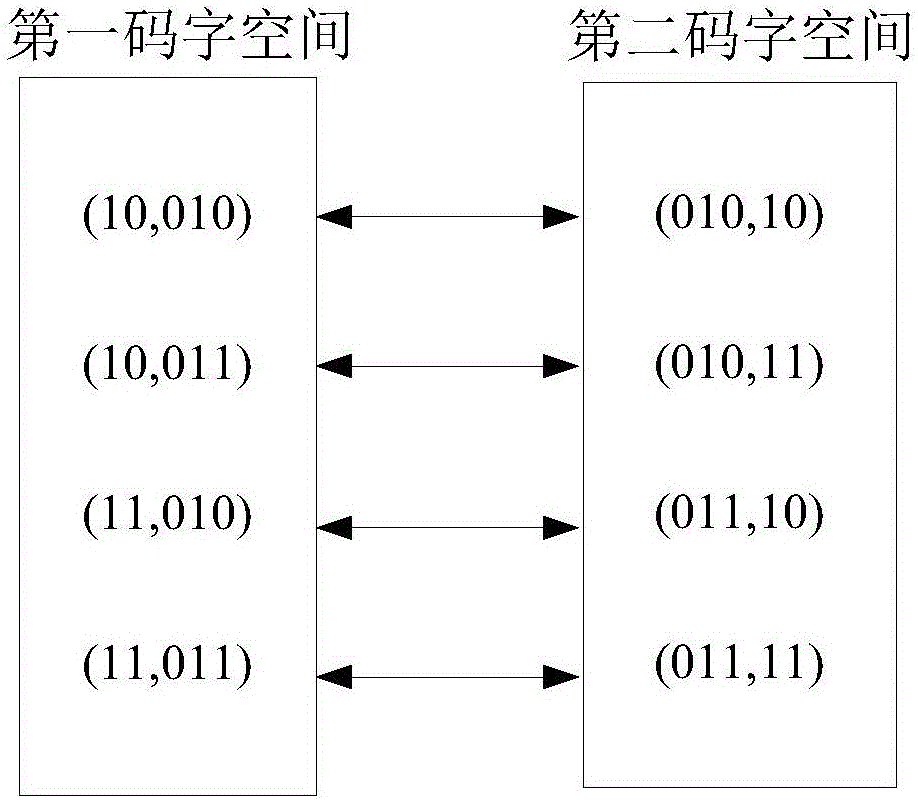
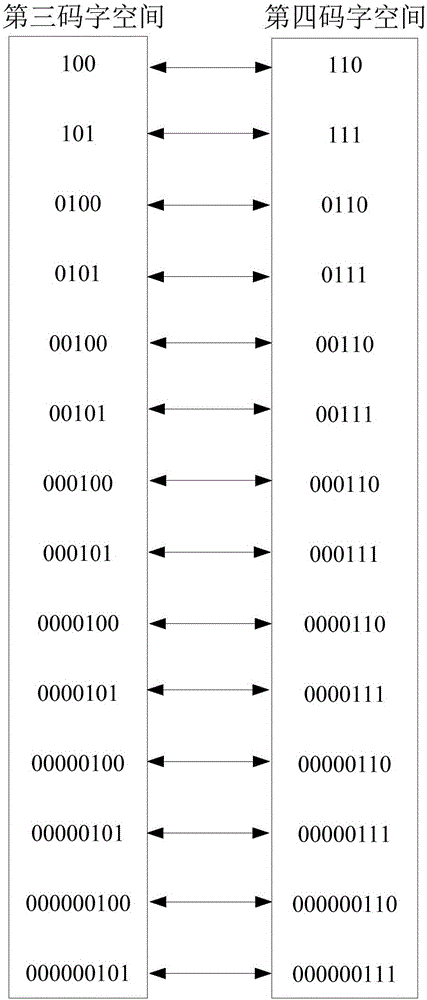
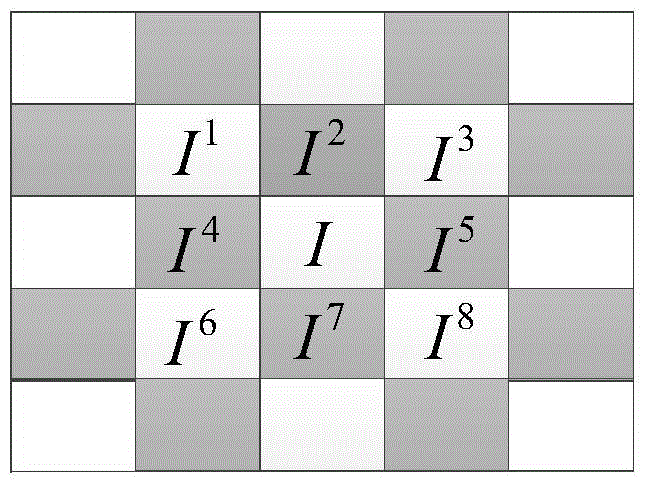
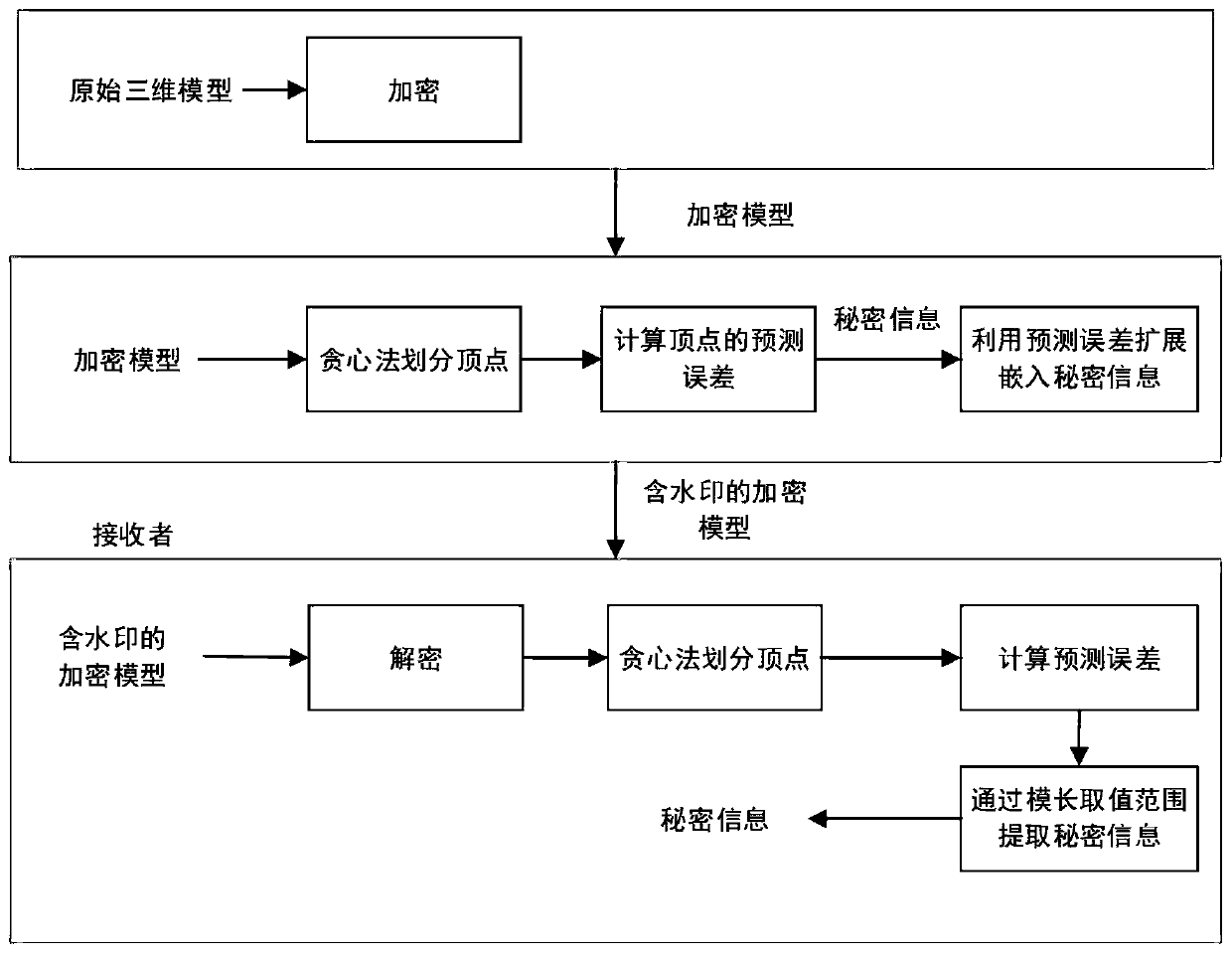
PendingCN111598766AImplement extractionAchieve recoveryDetails involving 3D image data3D modellingThree dimensional modelEncryption system
The invention discloses an encryption domain three-dimensional model reversible information hiding method based on prediction error extension. In a traditional method, due to invisibility of an encrypted three-dimensional model, data security protection of the three-dimensional model cannot be achieved. According to the method, a Paillier encryption system is used for encrypting the three-dimensional model, so that the privacy of the three-dimensional model is protected. The method comprises the following steps: firstly, dividing vertexes into an embedded vertex set and a reference vertex setby utilizing the characteristic that the vertexes of embedded information are not adjacent to each other; secondly, calculating a prediction error of the embedded vertex set by utilizing the referencevertex set; and finally, expanding the module length of the prediction error by utilizing the embedded secret key so as to embed secret information; at a receiving end, extracting secret informationby comparing the module length value ranges of the prediction errors, and recovering the original model by utilizing the reference vertex set. Compared with a traditional method, the method has the advantages that the bit error rate is low when the secret information is extracted, the directly decrypted model has less distortion, and the information hiding capacity is improved to a certain extent.
Owner:绍兴聚量数据技术有限公司
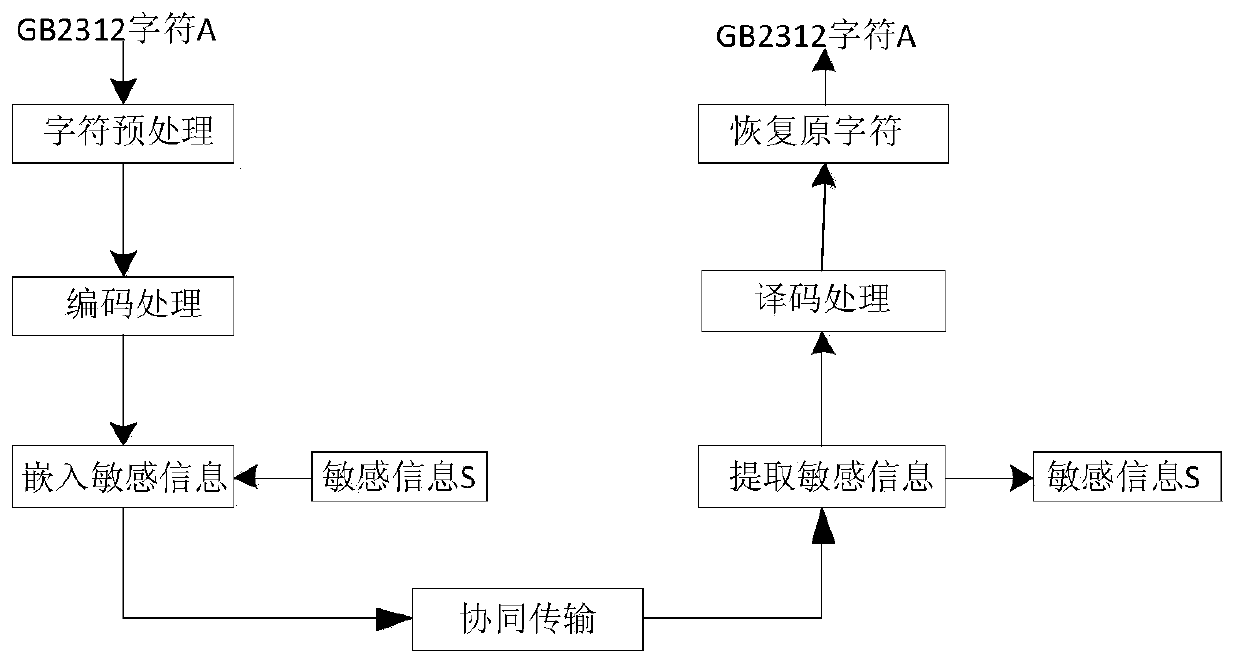
Satellite short message and information cooperative transmission method
ActiveCN110324795AIncrease hidden capacityDoes not increase the character byte countSource coding adaptationMessaging/mailboxes/announcementsDecoding methodsEmbedding rate
According to a satellite short message and information cooperative transmission method provided by the invention, information hiding processing is carried out in a navigation short message, and cooperative transmission of information and the short message is carried out by utilizing the characteristics of short message data. The method is applied to the framework of the national Chinese charactercoding standard GB2312. Through information preprocessing and encoding and decoding methods, the 3 / 16 lossless information hiding and embedding rate is realized, nearly 20% of characters can be hiddenand transmitted in any standard character by utilizing a short message transmission channel on the basis of not increasing the transmission data volume, the hidden character information and the original short message can be recovered in a lossless manner, and the security and confidentiality are realized. According to the method, the practicability of a satellite short message system is expanded,the application range of satellite communication and navigation satellite systems in China is expanded, and new value-added short message information service can be provided for millions and tens ofmillions of users.
Owner:XIAN INSTITUE OF SPACE RADIO TECH
Multi-image hiding method based on secret sharing
The invention discloses a multi-image hiding method based on secret sharing, and belongs to the field of information security. The invention provides a multi-image hiding method based on secret sharing in order to protect the safety of hidden image content, improve the algorithm robustness and expand the hiding capacity. The method comprises the following steps of: firstly, partitioning k carrierimages, scrambling image blocks by using two-dimensional Zig transform, and respectively mapping the scrambled image blocks from a spatial domain to a discrete cosine transform (DCT) domain; secondly,embedding the hidden image bits into k carrier images by using an additive spread spectrum algorithm or a multiplicative spread spectrum algorithm; and finally, mapping the disguised DCT coefficientsback to a spatial domain, performing scrambling recovery on the image blocks by using two-dimensional zigzag inverse transformation, and splicing the image blocks according to an original sequence toobtain k disguised images. Experiments show that the algorithm is efficient, good in embedding effect, large in hiding capacity, high in robustness and high in safety.
Owner:CHINA UNIV OF MINING & TECH
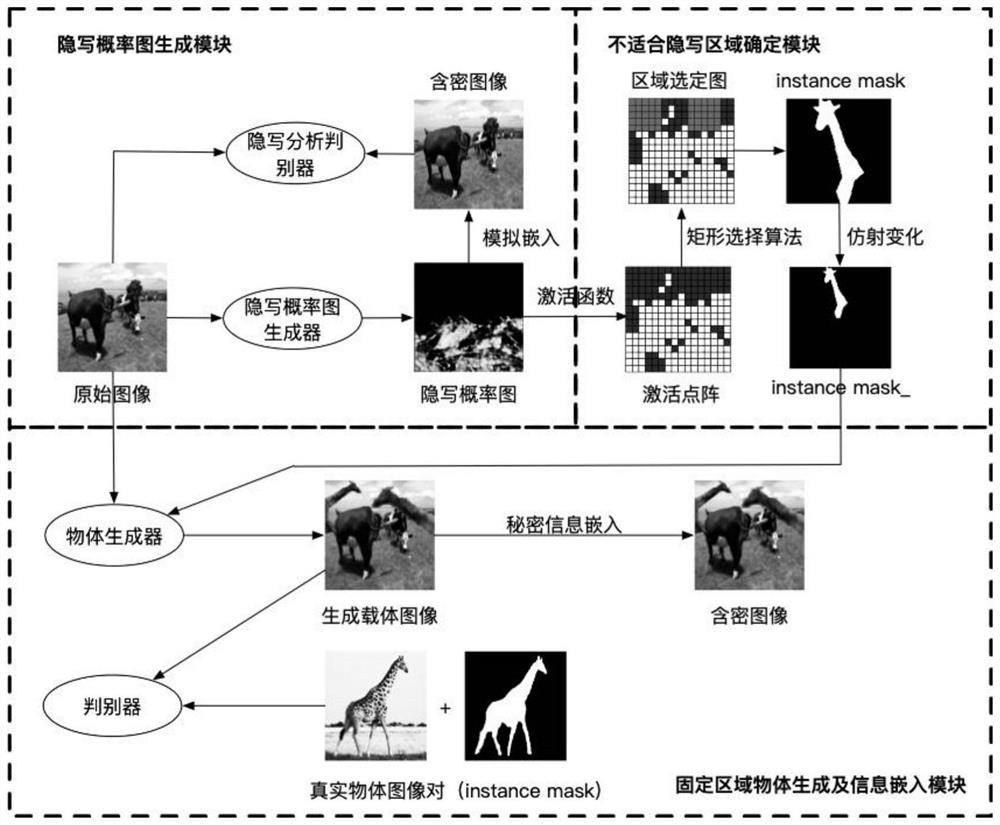
High-capacity data protection method based on GAN augmented image foreground object
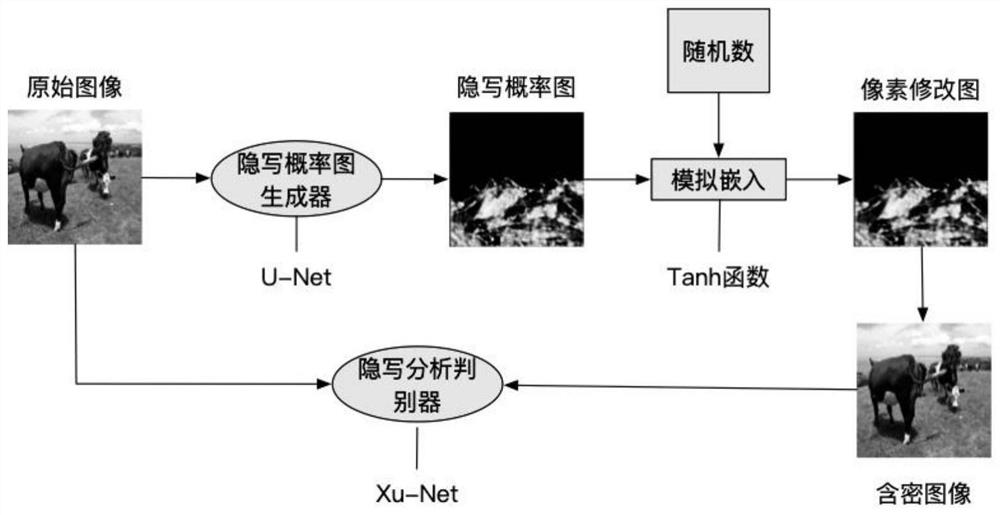
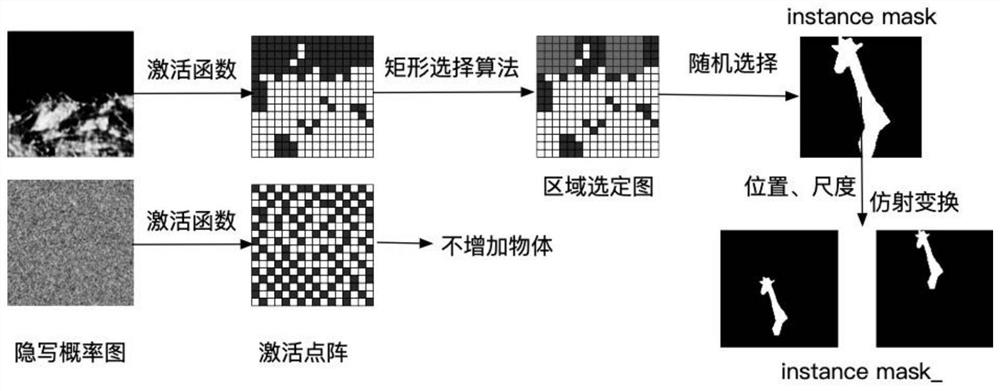
ActiveCN111768326AImprove securityIncrease hidden capacityImage enhancementImage analysisPattern recognitionInformation embedding
The invention discloses a high-capacity data protection method based on a GAN augmented image foreground object. By applying various GANs to information hiding, the high-capacity data protection method obtains an embedded distortion probability graph, calculates an unsuitable steganography area according to the embedded distortion probability graph, generates a foreground object in the unsuitablesteganography area through a fixed area object generation and information embedding module, and then hides the secret information in the generated graph. The high-capacity data protection method mainly comprises the following steps: (1) inputting an original image into a steganography probability graph generator; (2) calculating the steganography probability graph; (3) calculating the unsuitable steganography area; (4) adding a texture object into the original image; and (5) carrying out an information hiding algorithm to embed secret information. According to the high-capacity data protectionmethod, the unsuitable hidden area is calculated for the image in advance, so that the directional hiding capability of the unsuitable hidden area of the original image in information hiding is improved; and provided is a high-capacity data protection method which increases hiding capacity and has high security.
Owner:NANJING UNIV OF INFORMATION SCI & TECH
Image tampering detection positioning and self-recovery method based on fragile watermark
ActiveCN113014742AQuality improvementEnsure safetyEncryption apparatus with shift registers/memoriesPictoral communicationAlgorithmDigital watermarking
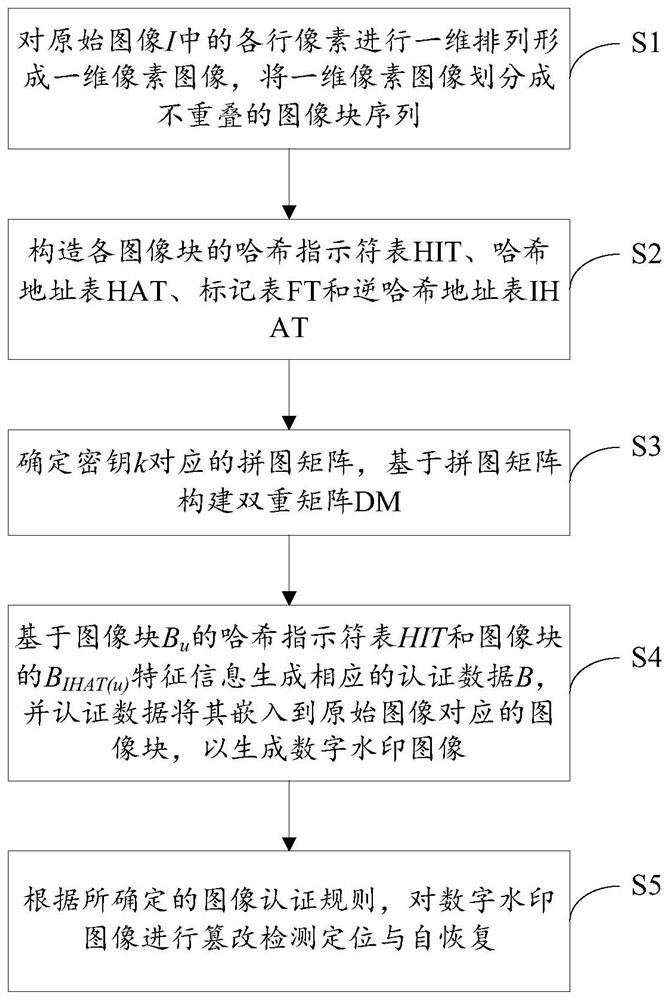
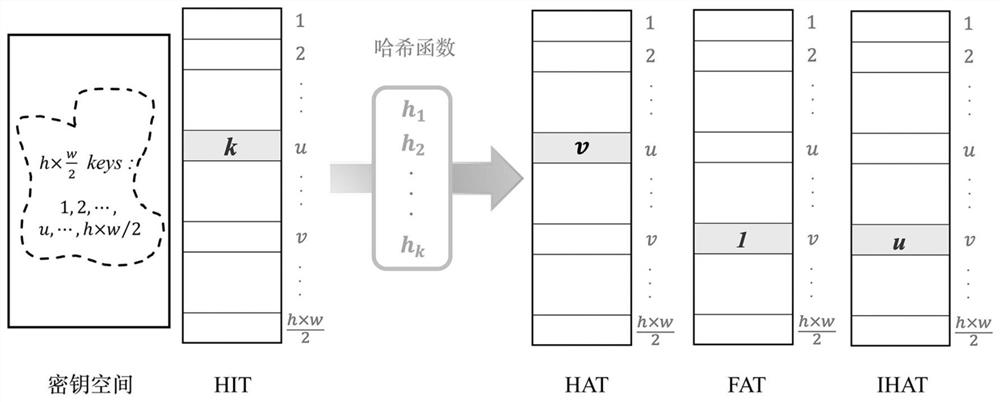
The invention discloses an image tampering detection positioning and self-recovery method for fragile watermarks, and the method comprises the steps: carrying out the one-dimensional arrangement of each row of pixels in an original image I to form a one-dimensional pixel image, dividing the one-dimensional pixel image into a non-overlapping image block sequence, and enabling each image block to comprise two continuous pixel points; constructing a Hash indicator table HIT, a Hash address table HAT, a tag table FT and an inverse Hash address table IHAT of each image block; determining a puzzle matrix corresponding to the key K, and constructing a dual matrix DM based on the puzzle matrix; generating authentication data B based on the Hash indicator table HIT of the image block Bu and the feature information of the image block BIHAT(u), and embedding the authentication data B into the image block Bu to generate a digital watermark image I '; and according to the determined image authentication rule, carrying out tampering detection positioning and self-recovery on the digital watermark image I'. According to the method, a perfect Hash model is used for generating authentication data, so that the authentication data has the self-recovery performance of a tampered area while a high tampering detection rate is obtained.
Owner:ANHUI NORMAL UNIV
High-order airspace hiding method for resisting differential detection
InactiveCN101561921ARobustIncrease hidden capacityImage data processing detailsComputer visionGray level image
The invention relates to a high-order airspace hiding method for resisting differential detection. As a necessary supplement of cryptology and a hot research topic in the information security field in recent years, the information hiding technology draws the attention of more and more people. The technology is to hide secret information in other carriers to go beyond the awareness of people so as to avoid the attack of attackers and ensure the security of secret information. The high-order airspace hiding method for resistable differential detection comprises the following steps: finding a pixel point capable of performing high-order hiding in a carrier gray level image with a size of N1xN2, converting the to-be-hidden secret image with a size of M1xM2 into binary information stream, determining on which position of the carrier image the binary information stream is hidden through Logistic chaos mapping, the Logistic chaos mapping formula being Z(n+1)=4Zn(1-Zn), wherein Zn belonging to (0,1); if the secret information is identical to the bit information, substitution is not performed, and otherwise, substitution is performed, then repeating the process till all information is hidden; in order to resist differential detection, interval size exchange is performed between the pixel points where information is hidden, i.e. + / -5 operation is performed. The invention is used for information hiding technology.
Owner:哈尔滨佳云科技有限公司
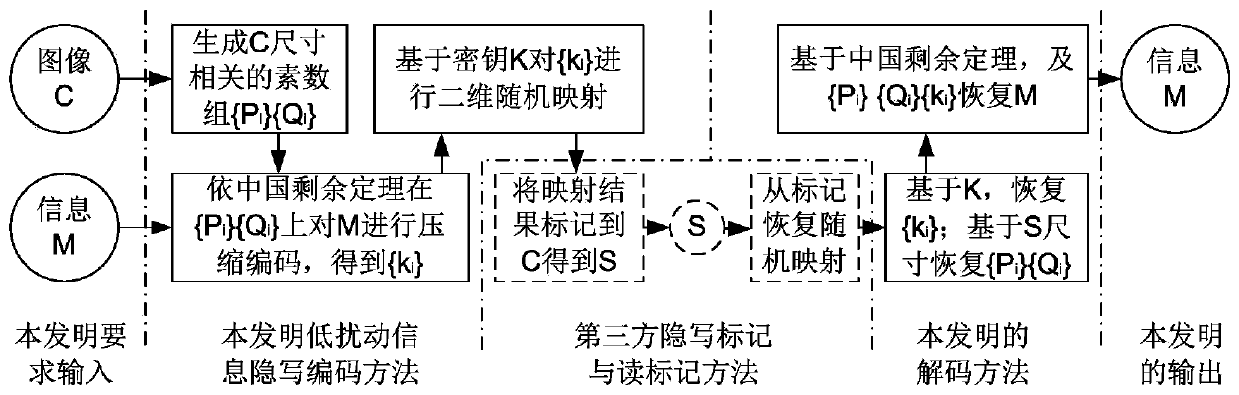
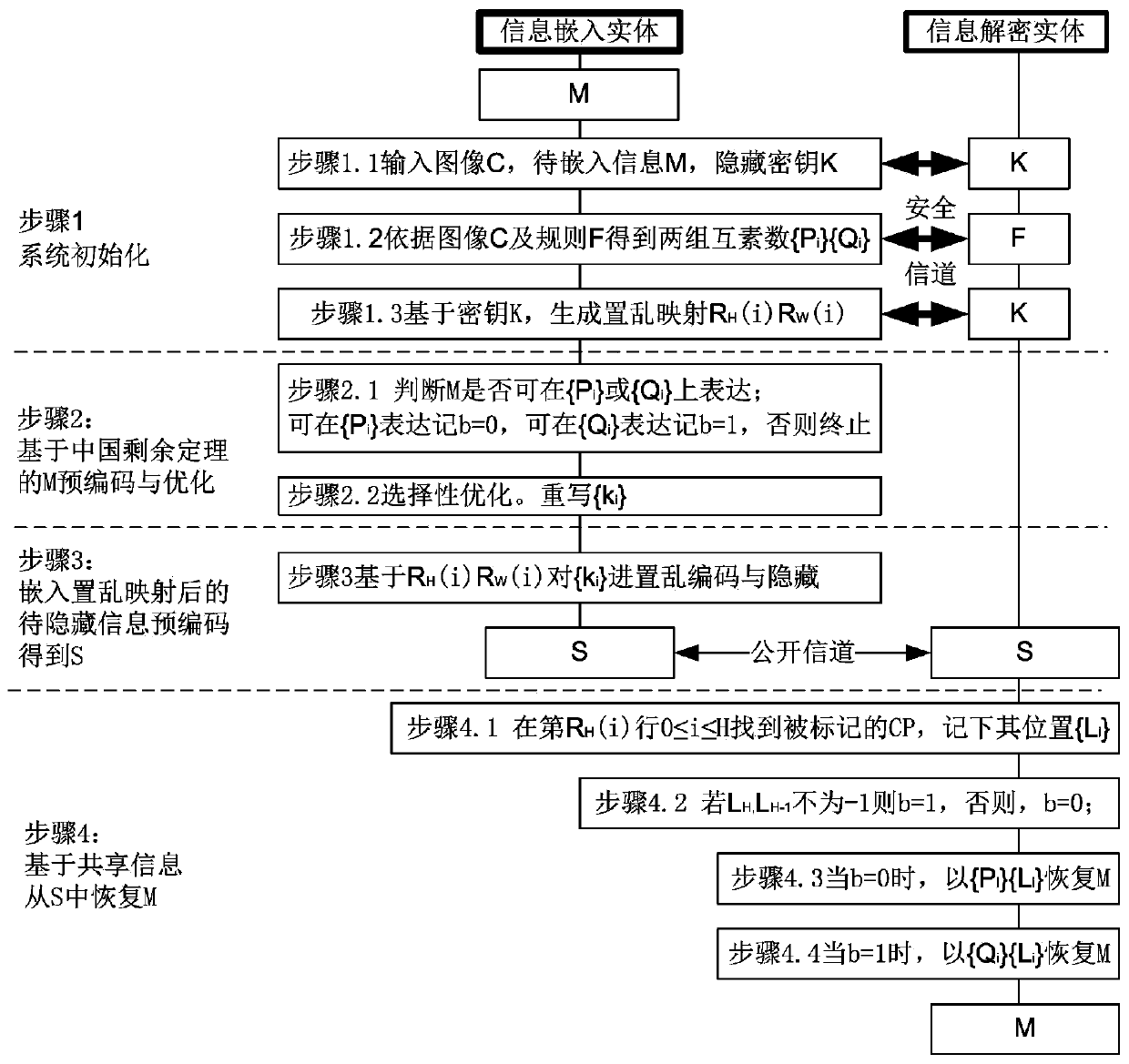
Low-disturbance information security steganography encoding method based on Chinese remainder theorem
ActiveCN110113505AII method smallImprove image qualityPictoral communicationDecoding methodsPattern recognition
The invention provides a low-disturbance information security steganography encoding and decoding method based on the Chinese remainder theorem. The coding comprises four steps: 1) initializing a system based on an image C, to-be-embedded information M and a hidden key K; 2) pre-coding the hidden information M based on the Chinese remainder theorem, and carrying out selective optimization; 3) pre-coding the scrambled and mapped information to be hidden in C to obtain S; and 4) recovering hidden information M from the S based on the shared information. According to the invention, the output result is marked in each line and each column of CPs, and at most only the LSB of one CP is marked, so that the marked S image quality can be obviously improved. At most one LSB is marked in each row andeach column of CPs, and with the increase of the C size, the improved gain of the image quality and the hidden capacity can be obtained at the same time. The hidden operation based on two-dimensionalrandom mapping can avoid the scanning attack aiming at the statistical characteristics of the LSB marking method.
Owner:HUBEI UNIV OF TECH
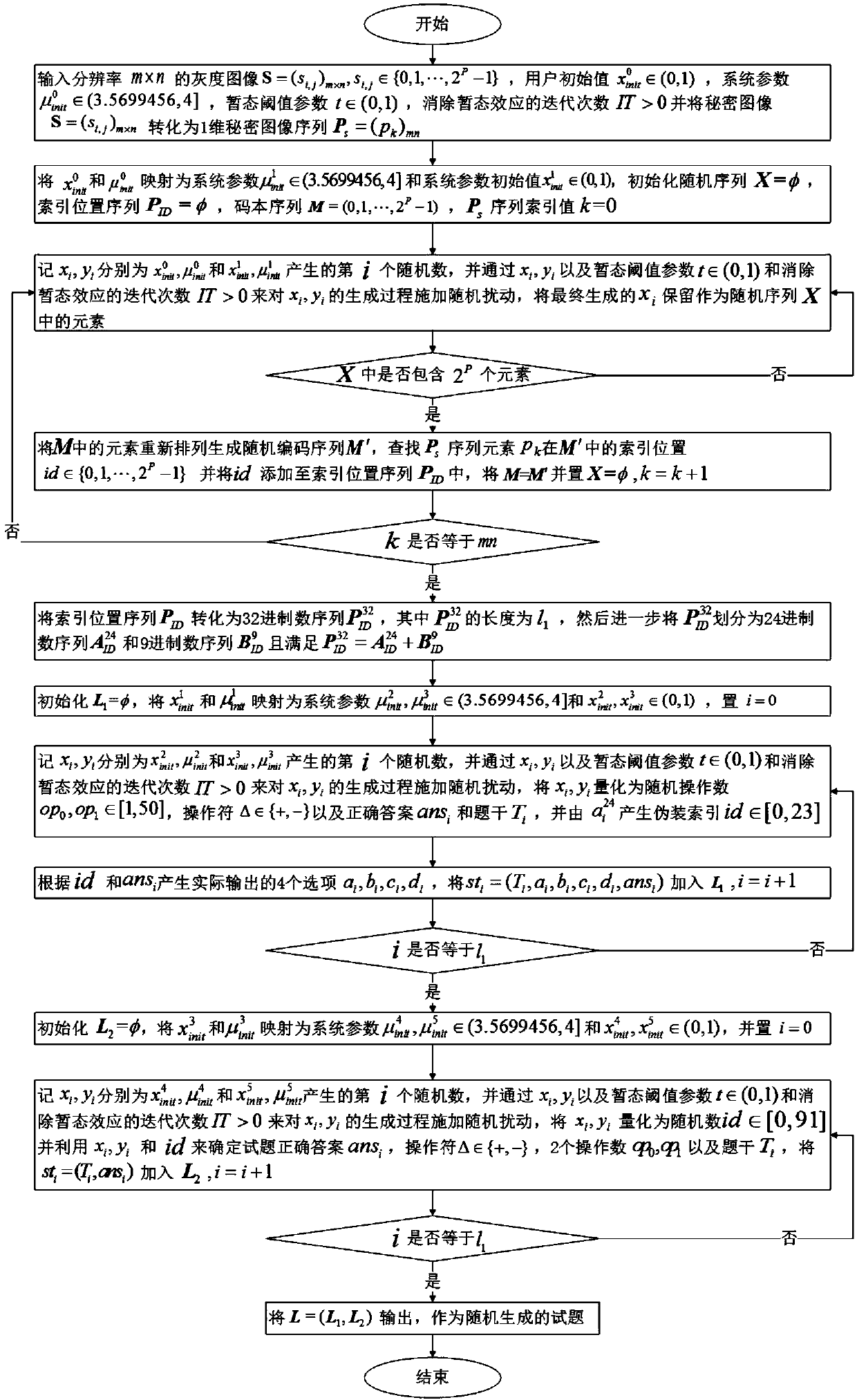
Password map carrier-free test question disguise method of non-direct transmission and random codebook
ActiveCN108156136ASearch heavyHeavy storageKey distribution for secure communicationImage data processing detailsPasswordTheoretical computer science
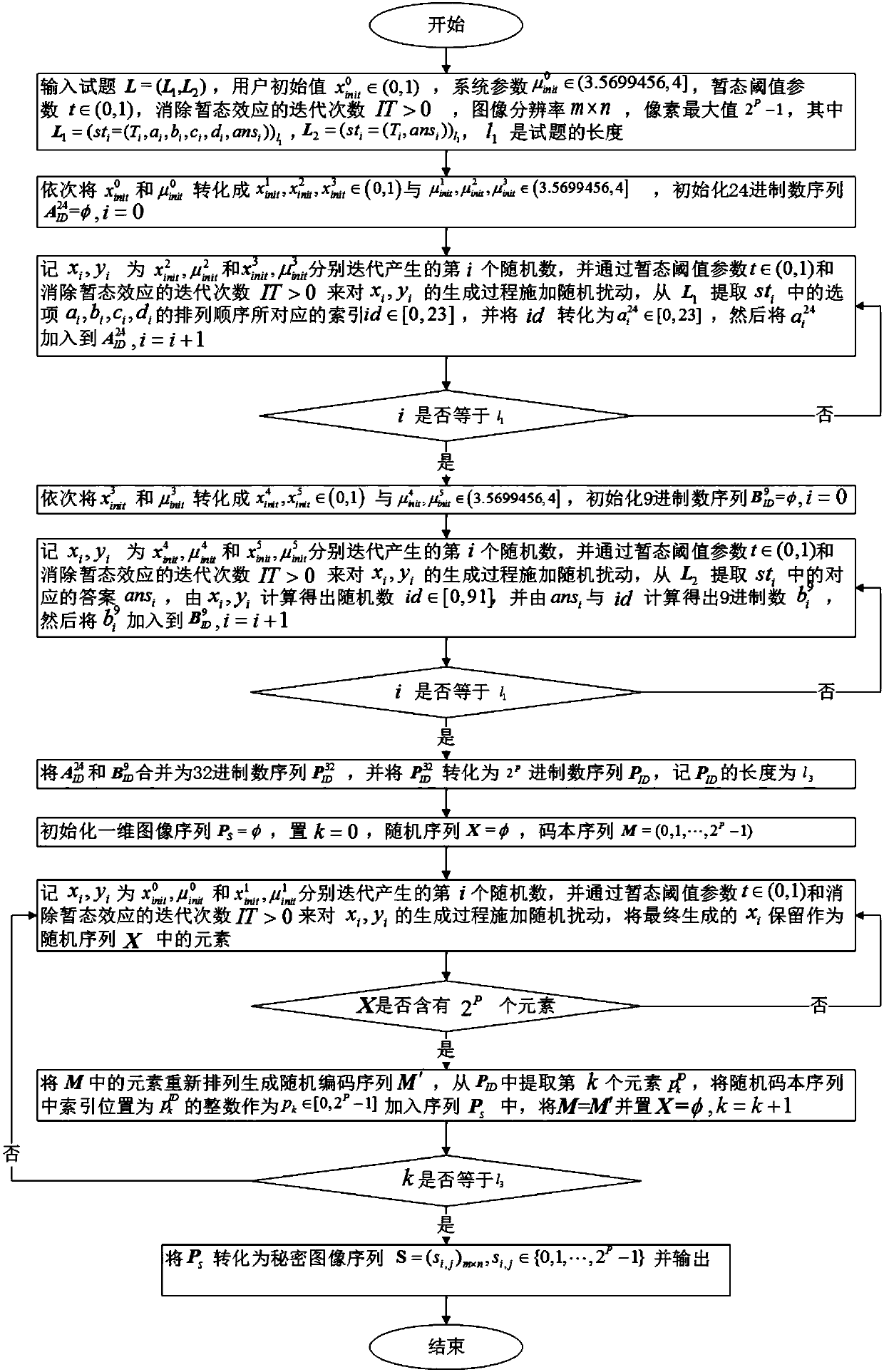
The invention provides a password map carrier-free test question disguise method of non-direct transmission and a random codebook. The method comprises the following steps: firstly, scrambling the codebook via a pseudo-random sequence, then, performing pseudo-random encoding on password map pixels by using the scrambled codebook index to avoid direct channel transmission of the password map; then,converting the encoded index location into a 32-ary sequence, and further expressing the same through 24-ary and 9-ary numbers; and finally, indirectly expressing choice question arrangement sequencenumbers and gap filling answers randomly generated by each 24-ary and 9-ary numbers in the sequence relative to a random offset to generate random test questions. Compared with the existing method, the method has the advantages of avoiding the direct channel transmission of the password map, the problems that the additional carrier is modified, the hiding capacity of the traditional non-embeddedcarrier-free information is small, a large text or image database needs to be constructed and maintained and that the search cost is high are avoided by using a password containing test question generation mode, and the password map is restored just by a correct key.
Owner:SHAANXI NORMAL UNIV
Reversible information hiding method for bit plane compressed encrypted image
PendingCN113382128AGive full play to the characteristicsFeatures are conducive to playPictoral communicationHigh level techniquesAlgorithmBlock code
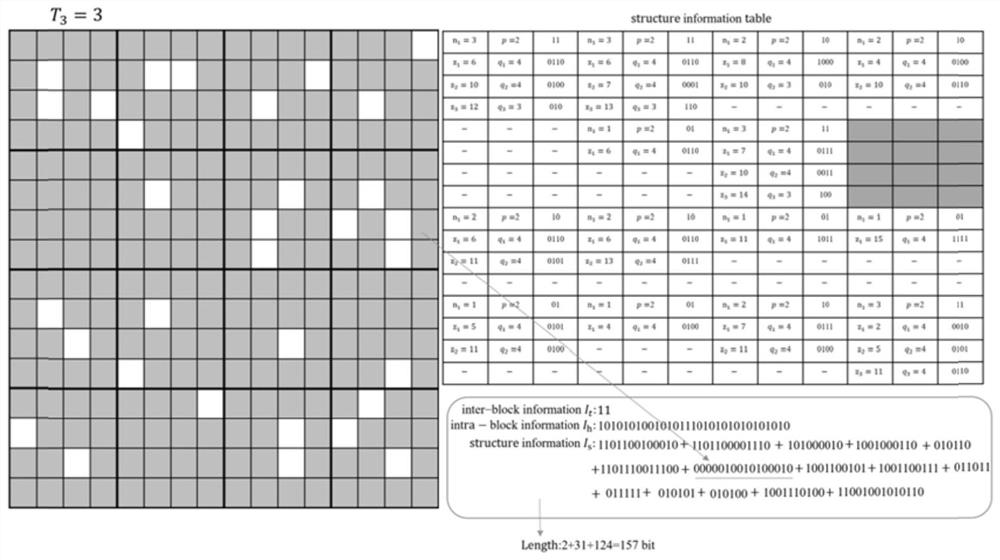
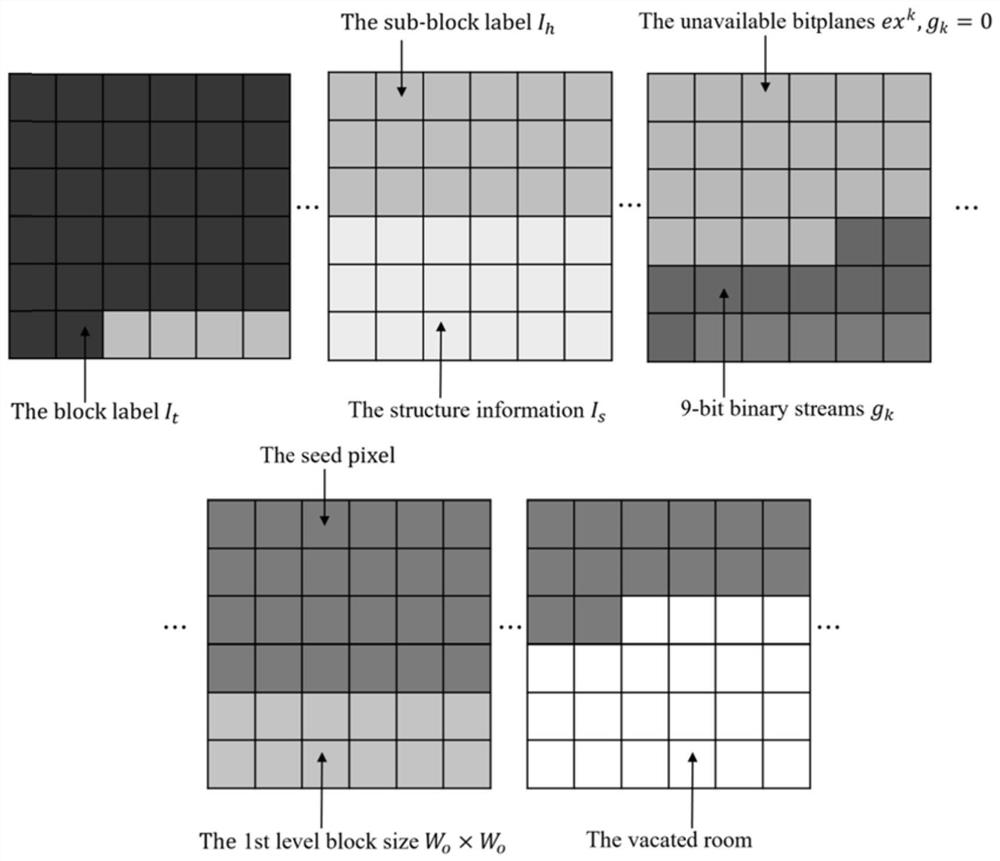
The invention provides an encrypted image reversible information hiding method based on bit plane compression. For an image owner, the method comprises the steps: firstly, performing median edge detection prediction on an original image to obtain a prediction error; secondly, calculating a bit plane compression space by using an adaptive selection method; thirdly, selecting an available bit plane to carry out self-adaptive variable-length block coding so as to code the image block; and finally, generating an encrypted connection information flow and sending the encrypted connection information flow to an information hider. For an information hiding person, the information hiding person encrypts secret information by using the hiding secret key and embeds the secret information into the vacated redundant space to obtain a secret-containing image. For the receiver, if the receiver has the encryption key, the original image can be obtained through decryption; if the mobile terminal has a hidden key, the mobile terminal can be used for decrypting and acquiring secret information; if the two secret keys are contained at the same time, the original image and the secret information can be decrypted at the same time. Compared with other existing related work, the scheme provided by the invention has relatively excellent performance in embedding capacity.
Owner:绍兴聚量数据技术有限公司
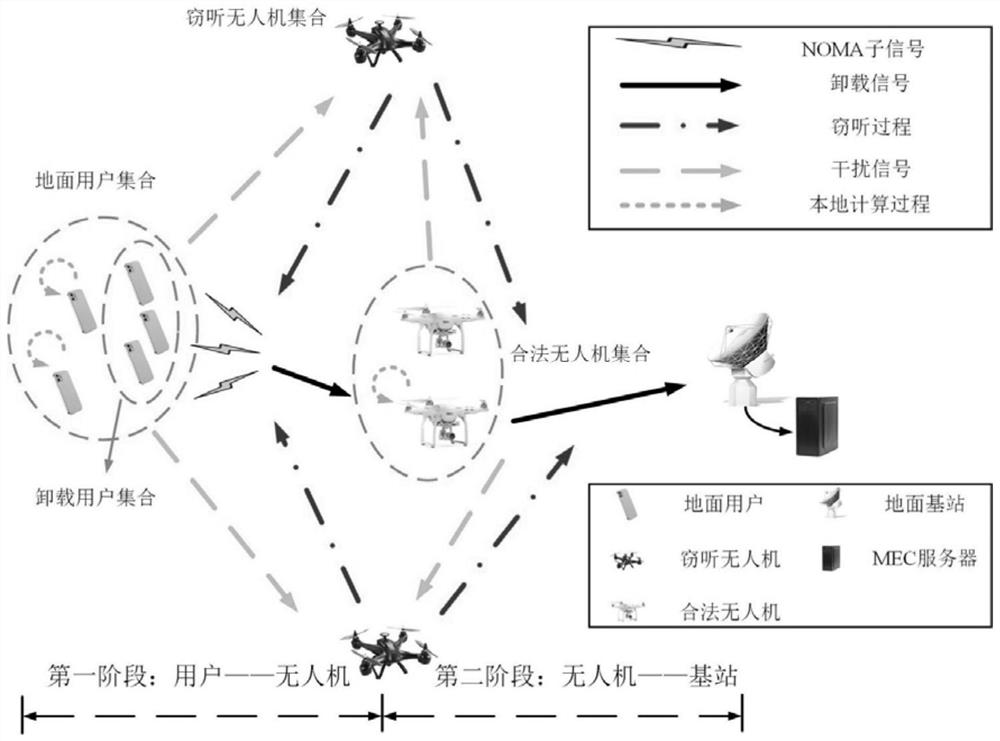
Two-stage mobile edge computing communication method based on NOMA and unmanned aerial vehicle assistance
ActiveCN113709728AImprove concealmentReduce transmission delayNetwork traffic/resource managementRadio transmissionCommunications systemSimulation
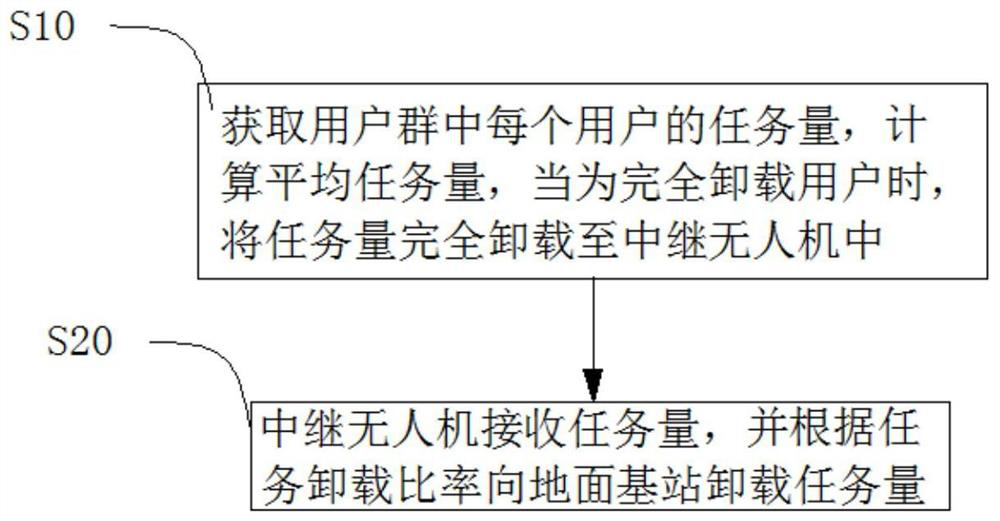
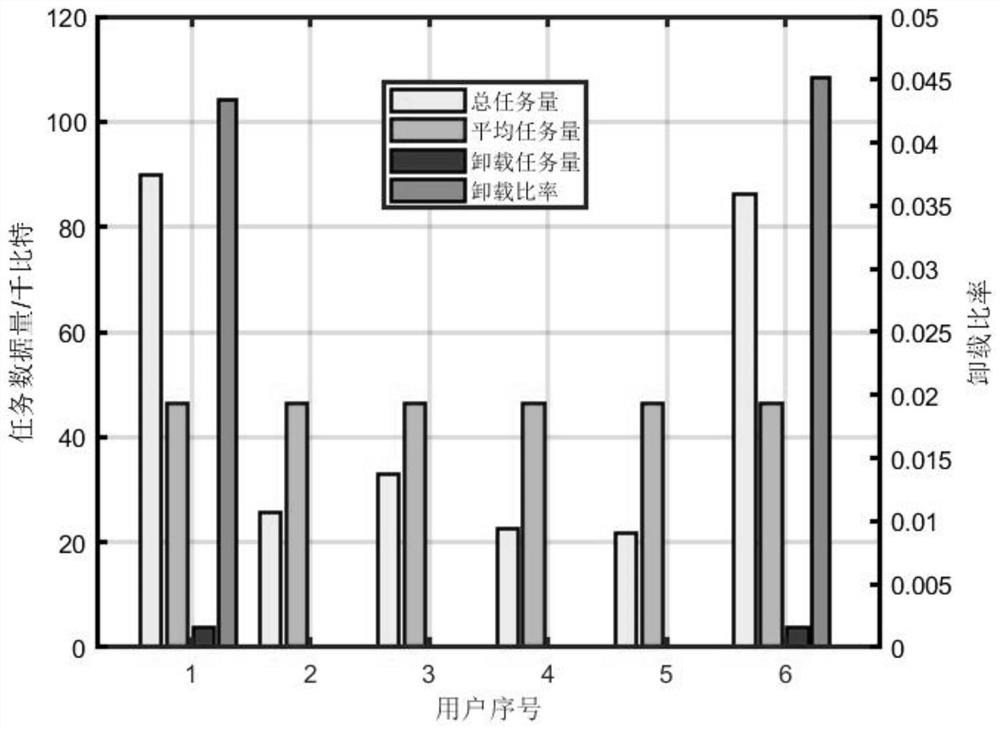
The invention discloses a two-stage mobile edge computing communication method based on NOMA and unmanned aerial vehicle assistance, which is applied to a communication system, the communication system comprises a user group, a relay unmanned aerial vehicle group and a ground base station, and the user group communicates with the ground base station through the relay unmanned aerial vehicle group. Each user in the user group executes the following steps that: the task load of each user in the user group is acquired, the average task load of the users in the user group is calculated, and when the task load of the user is greater than or equal to the average task load, the user is determined as a completely unloaded user; the complete unloading user completely unloads the task load to the relay unmanned aerial vehicle determined in the relay unmanned aerial vehicle group; the relay unmanned aerial vehicle receives the task amount sent by the complete unloading user and unloads a part of the received task amount to the ground base station according to the calculated task unloading ratio; user task data unloading is reasonably carried out in the communication system, and the performance of the communication system can be improved.
Owner:NORTHWESTERN POLYTECHNICAL UNIV
Information hiding method, device and system based on cavity space pyramid
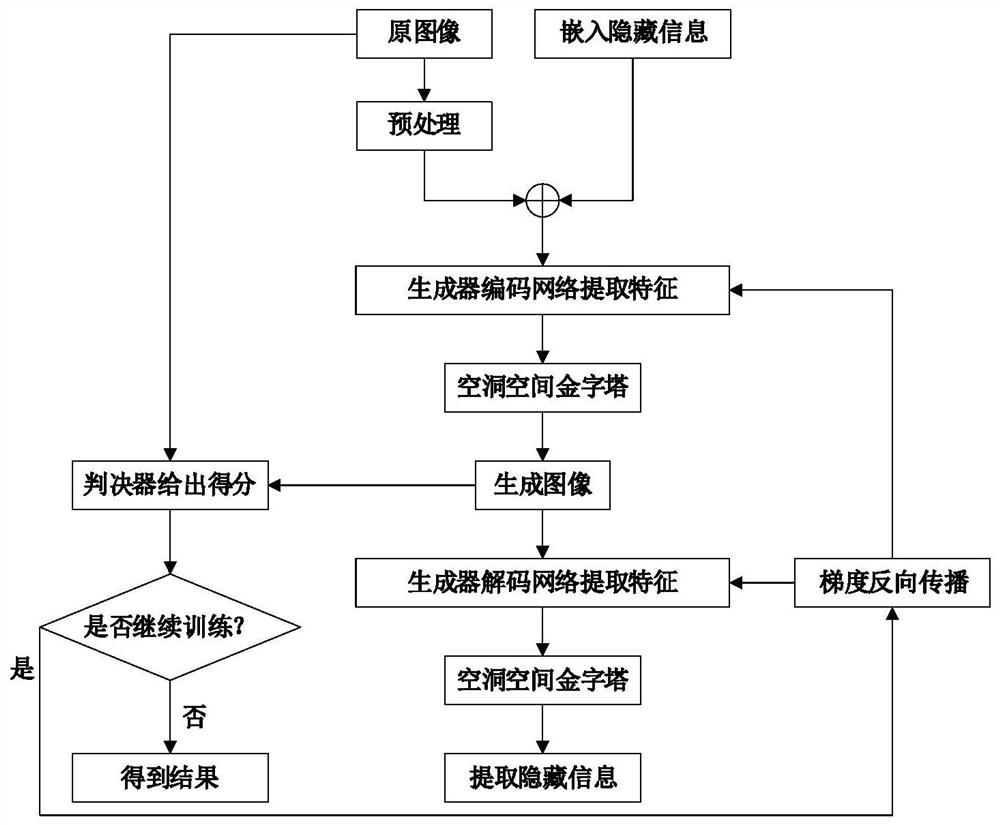
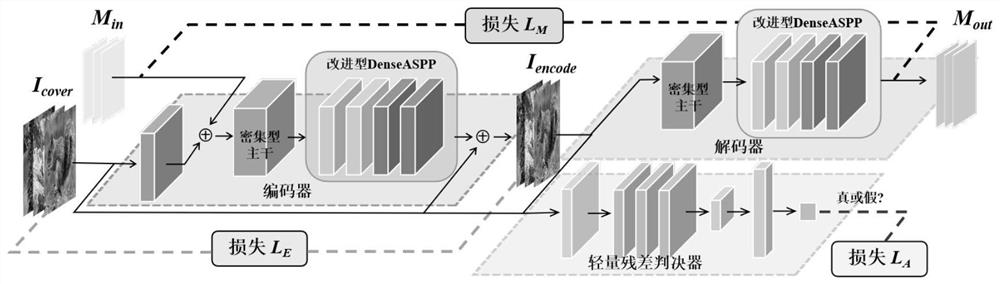
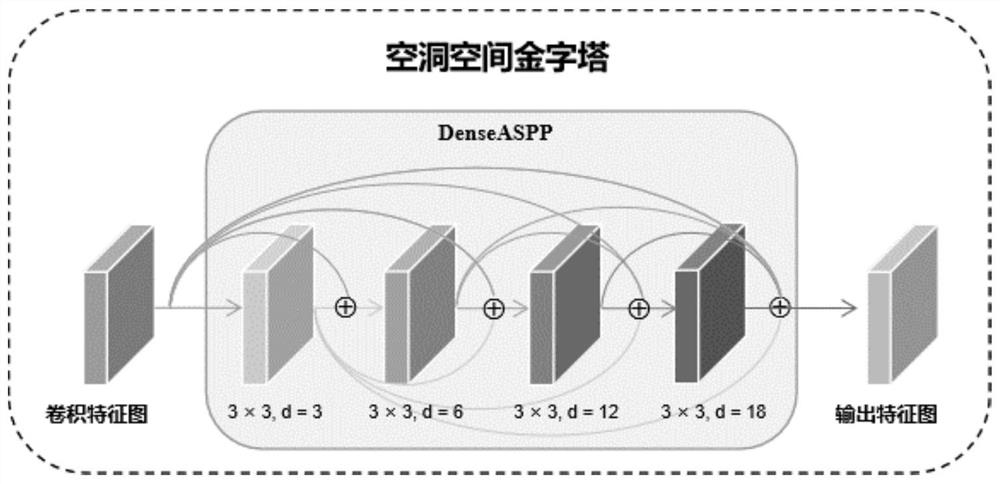
ActiveCN113254891ASolve the problem of low embeddable informationIncrease hidden capacityImage data processing detailsNeural architecturesData privacy protectionAlgorithm
In order to solve the problems of low image information hiding capacity and distortion in the aspect of data privacy protection, the invention provides an information hiding method, device and system based on a cavity spatial pyramid, which are used for embedding and extracting watermark information in a protected image to realize image version authentication and protection. According to the method, a cavity space pyramid module is built by adopting cascaded and parallel cavity convolution layers, the receptive field is expanded, the multi-scale and multi-cavity-rate characteristics are extracted, information is more accurately hidden in a semantic redundancy position, and the decoding capability of a network on embedded information is improved; meanwhile, the decoding accuracy is improved by using cross entropy loss; in addition, the quality of the generated image is improved through residual error and linear operation confrontation in the discrimination network; finally, in order to improve the network stability, updating of different scales, cosine annealing adjustment and an intensive connection strategy are used in training. According to the method, high-capacity information hiding is achieved, meanwhile, it is guaranteed that images are not distorted, and experiments prove that the method has high information hiding capacity.
Owner:SHANDONG UNIV
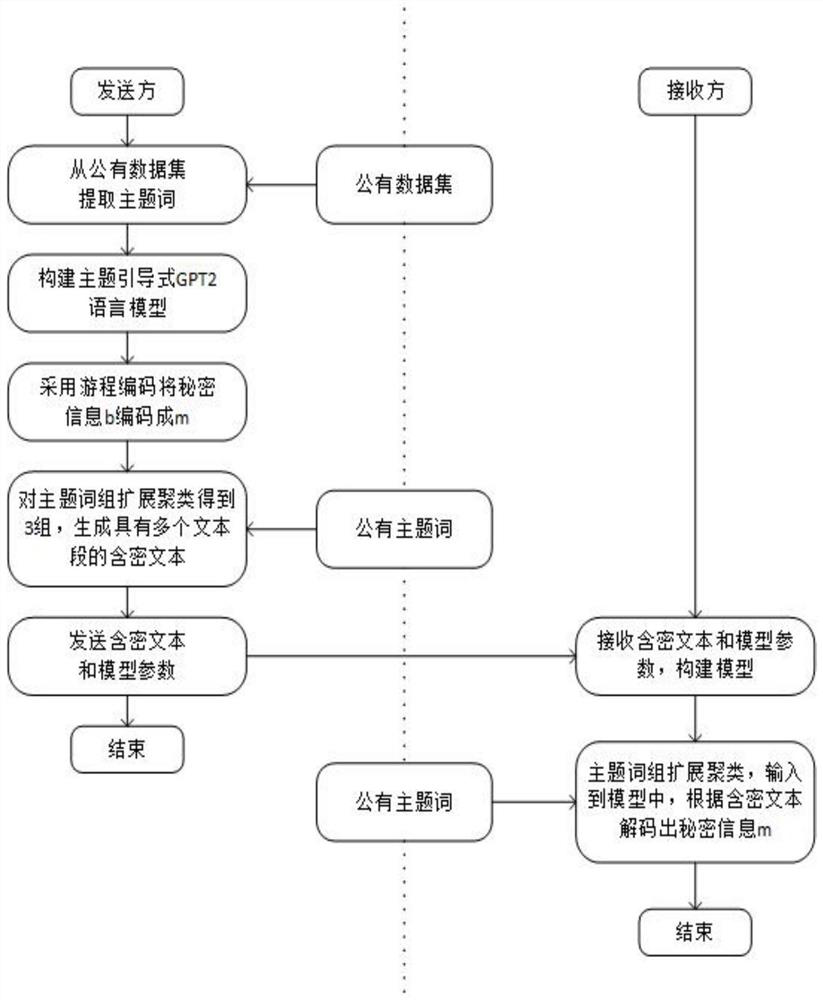
Generative text covert communication method based on theme guidance
ActiveCN113343250AIncrease hidden capacityQuality improvementDigital data protectionNatural language data processingAttention modelCovert communication
Disclosed is a generative text covert communication method based on theme guidance. The attention of a subject term is introduced into the GPT2 self-attention model, so that the model is controlled by the subject term at any time in the text generation process, and the generated long text is semantically and statistically fitted with a real text; the information hiding capacity is improved; a multi-paragraph text is generated by expanding a subject word group, so that redundant bits of hidden secret information are reduced, and the text quality is improved; in addition, run-length coding is adopted, so that the information hiding efficiency is improved on the premise of ensuring the text quality. The information hiding capacity is improved, the information hiding efficiency is improved, and the attack resistance of the text carrier is enhanced.
Owner:SHANGHAI UNIV
Encrypted image reversible information hiding method based on adaptive parameter binary tree marking
ActiveCN113079274AImprove performanceIncrease hidden capacityPictoral communicationInformation embeddingTheoretical computer science
Owner:绍兴图信物联科技有限公司
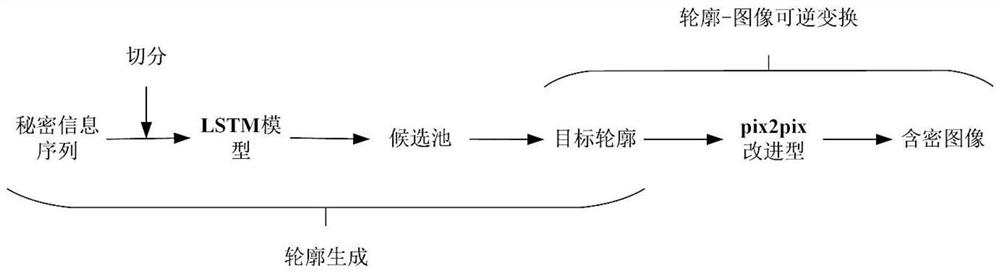
Constructive information hiding method based on automatic contour generation
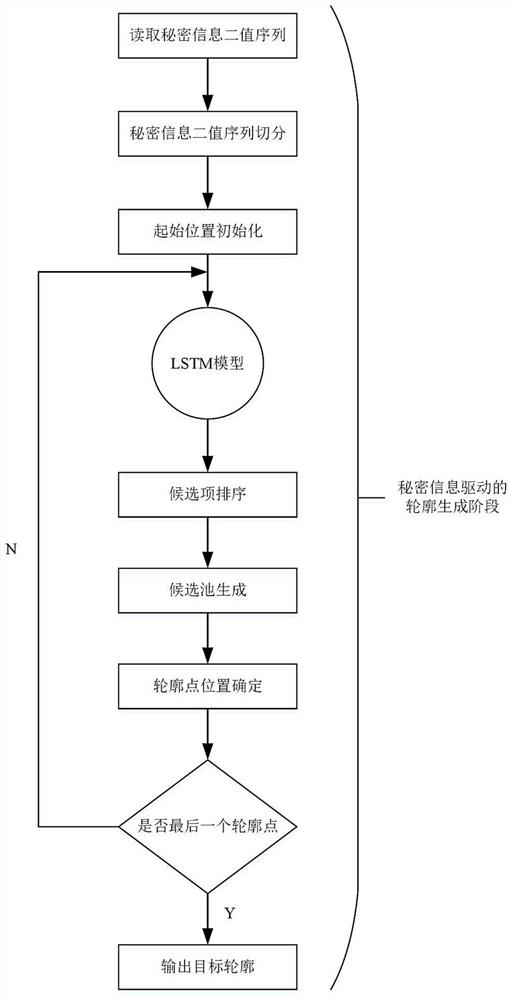
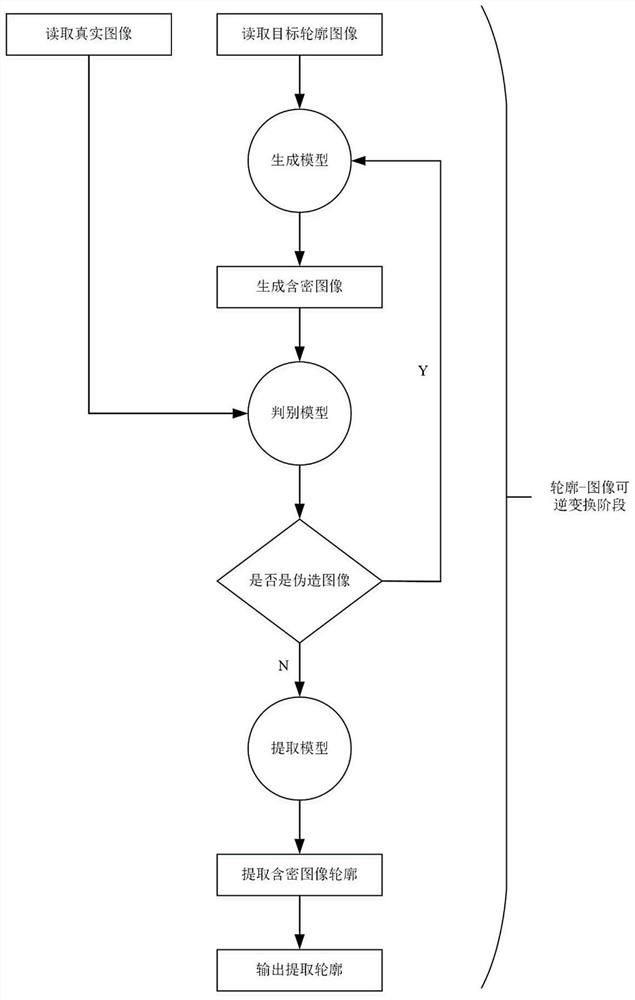
ActiveCN113610878AIncrease hidden capacityImprove extraction accuracyImage enhancementImage analysisPattern recognitionRadiology
The invention discloses a constructive information hiding method based on automatic contour generation. The method specifically comprises the following steps: segmenting a binary sequence S of secret information with the length of L into n binary sequences with the lengths of l; 2, constructing a target contour image; 3, constructing a contour-image reversible transformation model; and 4, inputting the target contour image into the trained contour-image reversible transformation model, generating a secret-containing image by the generation model according to the target contour image, and extracting the contour of the secret-containing image by the extraction model so as to hide the binary sequence of the secret information in the contour extracted by the extraction model. The generated secret-containing image is high in quality, and the visual effect is better.
Owner:NANJING UNIV OF INFORMATION SCI & TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com