Constructive information hiding method based on automatic contour generation
An information hiding and automatic generation technology, applied in the field of information security, can solve the problems of small hidden capacity and difficulty in extracting secret information, and achieve the effects of high extraction accuracy, reduced training pressure, and easy extraction
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0030] The drawings constituting a part of the present invention are used to provide a further understanding of the present invention, and the schematic embodiments and descriptions of the present invention are used to explain the present invention, and do not constitute an improper limitation of the present invention.
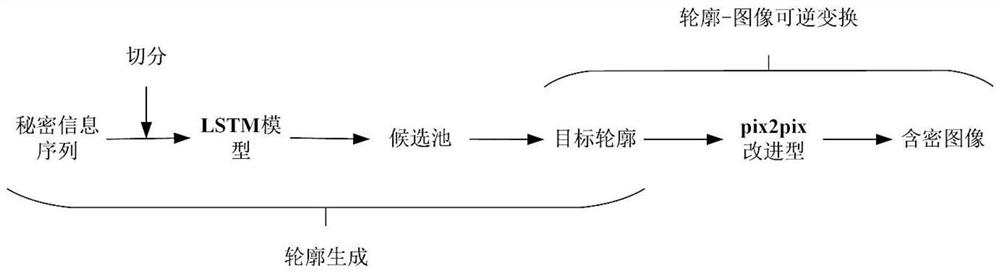
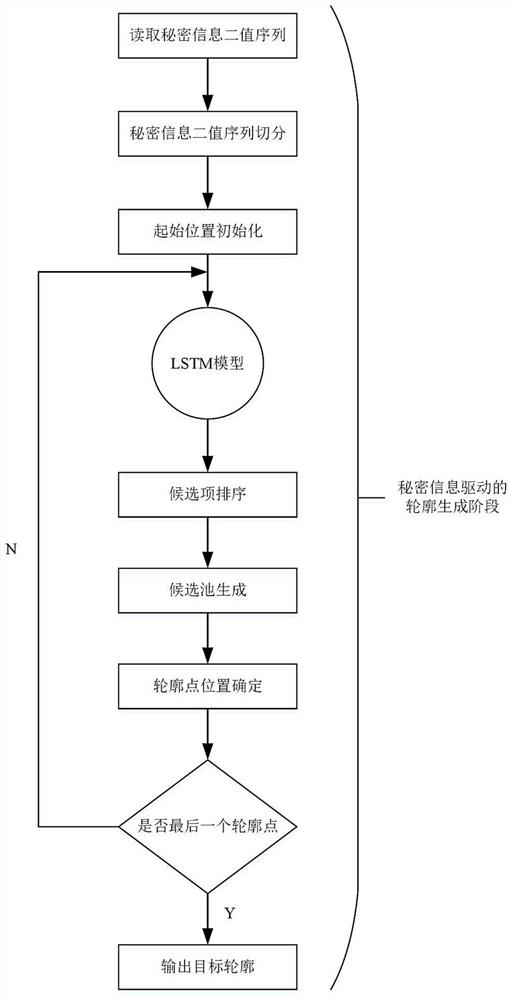
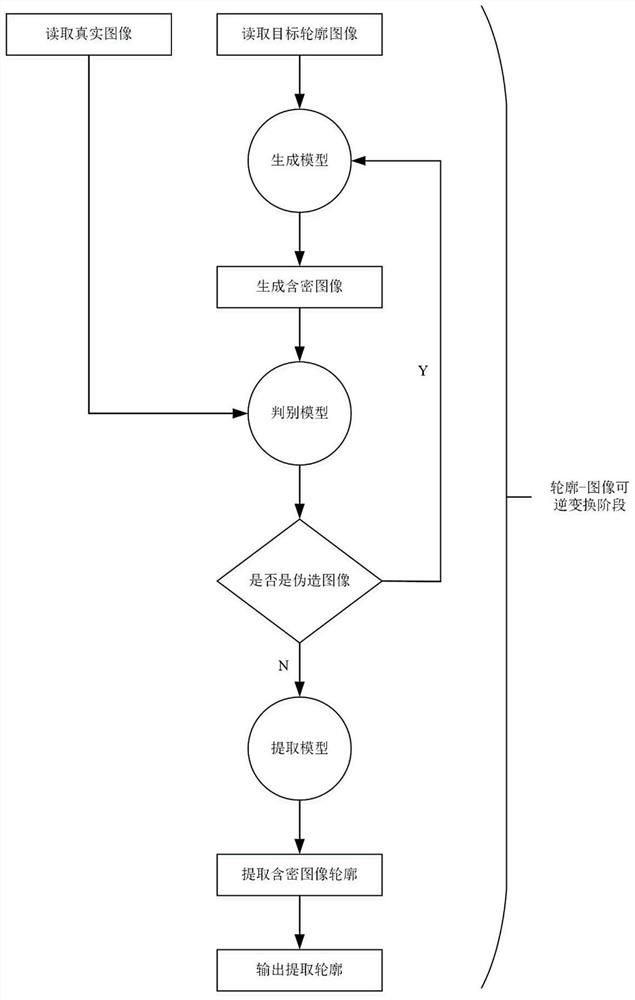
[0031] Such as figure 1As shown, this embodiment provides a constructive information hiding method based on automatic contour generation: in the contour generation stage, the secret information binary sequence is segmented, and the segmented sequence segments are input into the LSTM network segment by segment to obtain candidate pools , determine the position of the contour point according to the decimal value of the next sequence segment, and obtain the target contour image. In the contour-image reversible transformation stage, the target contour image is sent to the contour-image reversible transformation model. When training the contour-image reversible tra...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com