Image tampering detection positioning and self-recovery method based on fragile watermark
A technology of tamper detection and fragile watermark, which is applied in image communication, encryption device with shift register/memory, digital transmission system, etc., can solve the problems of unable to realize original image self-recovery, image visual effect deterioration, etc., to achieve optimal Effect of watermarking on image quality, high tamper detection rate
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0049] The specific implementation of the present invention will be described in further detail below by describing the embodiments with reference to the accompanying drawings, so as to help those skilled in the art have a more complete, accurate and in-depth understanding of the inventive concepts and technical solutions of the present invention.
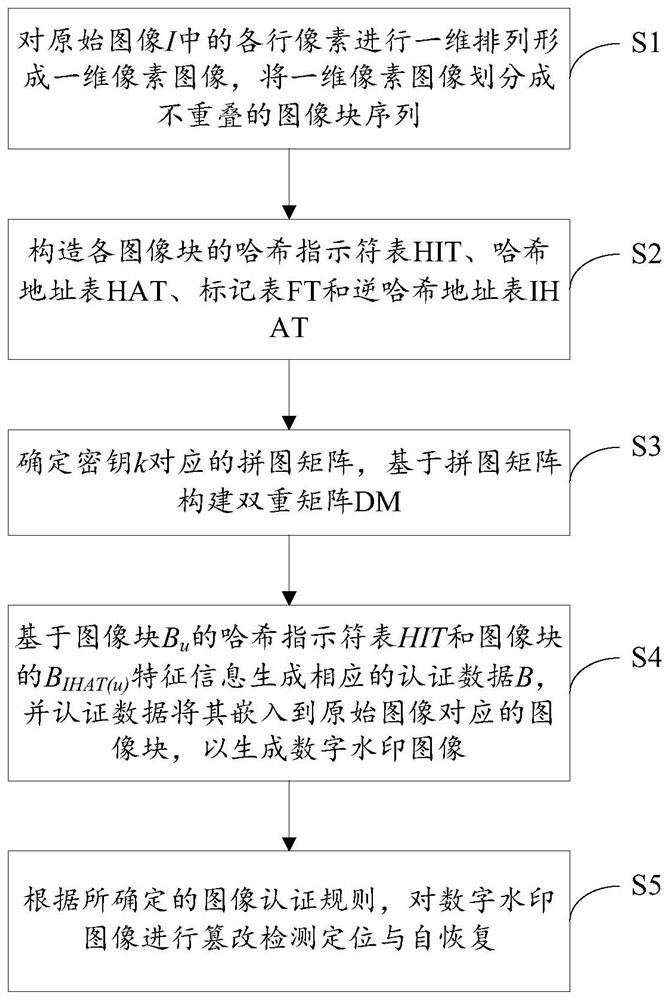
[0050] figure 1 It is a flow chart of the image tampering detection, positioning and self-recovery method of the fragile watermark provided by the embodiment of the present invention. The method specifically includes the following steps:
[0051] S1. Carry out one-dimensional arrangement of each row of pixels in the original image I having a size of h×w to form a one-dimensional pixel image, and divide the one-dimensional pixel image into non-overlapping image block sequences;
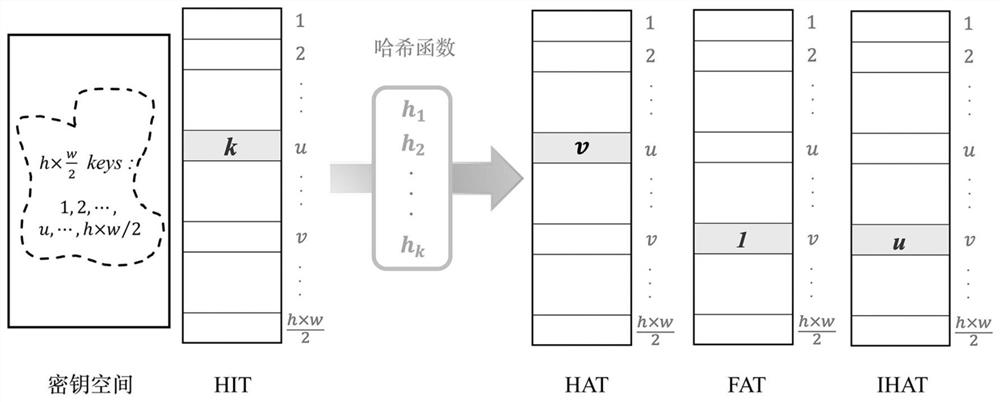
[0052] S2. Construct 7 random hash functions and a hash indicator table HIT according to the random number seed S;
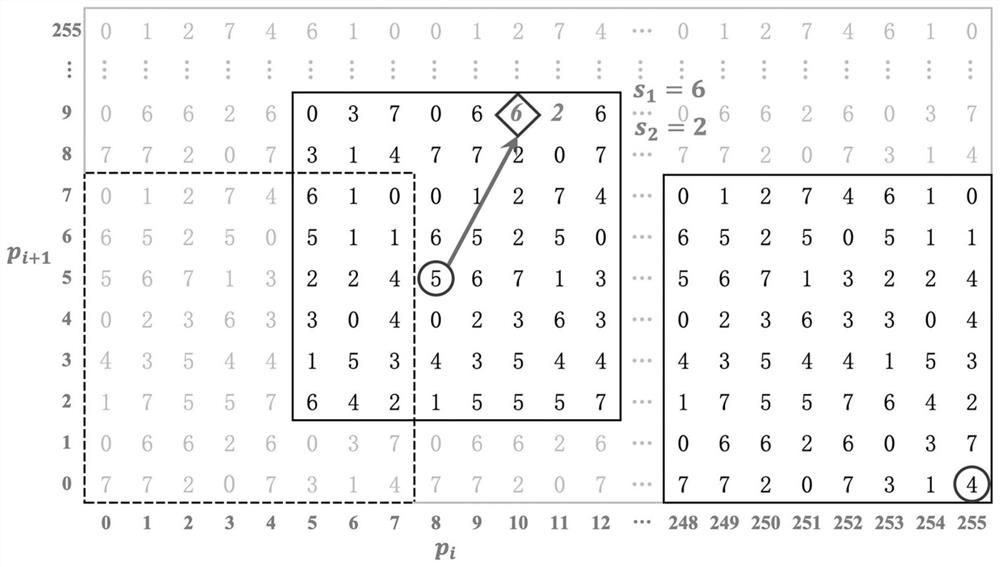
[0053] Use the random number seed S t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com