Patents
Literature
66 results about "Image integrity" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
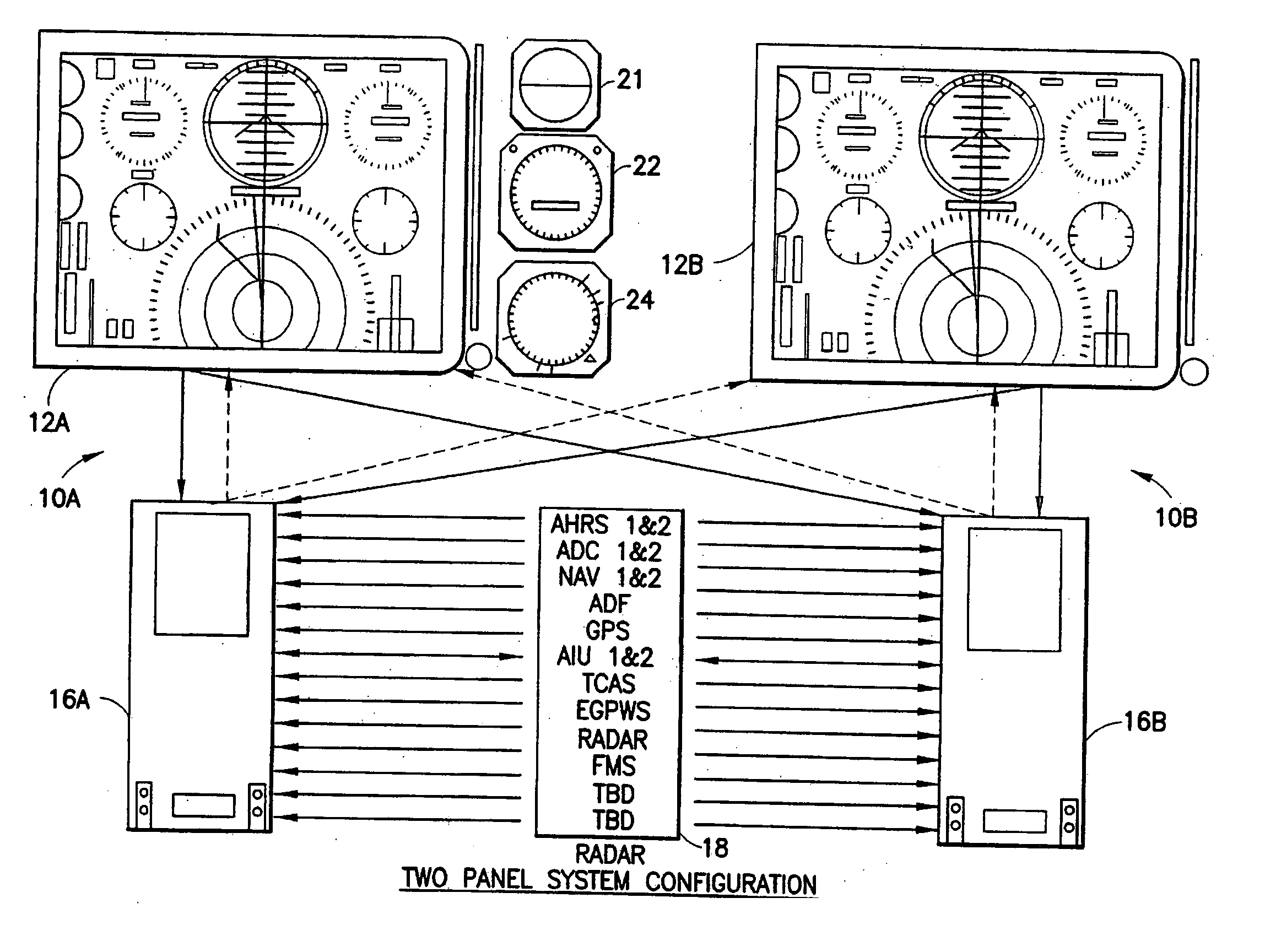
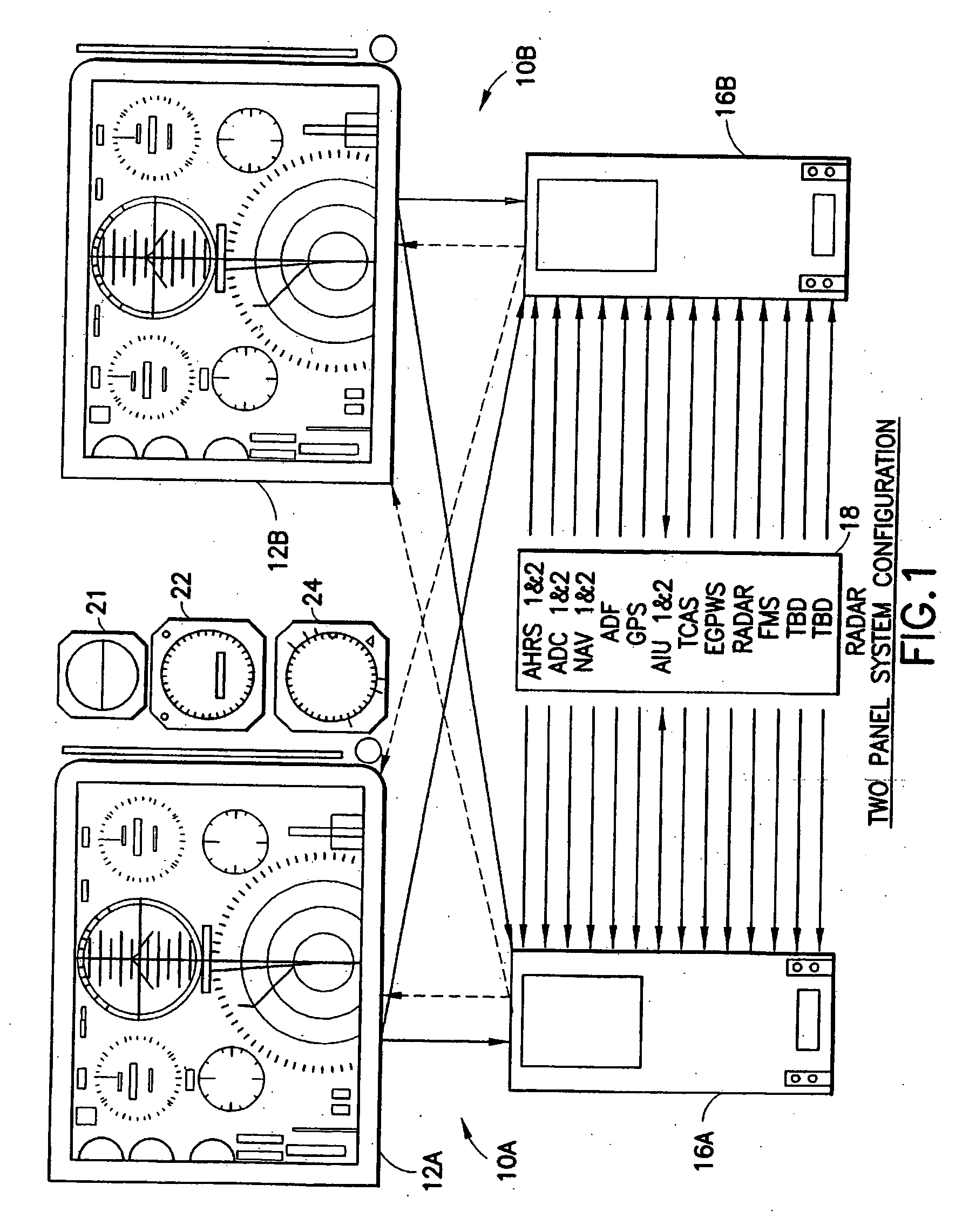
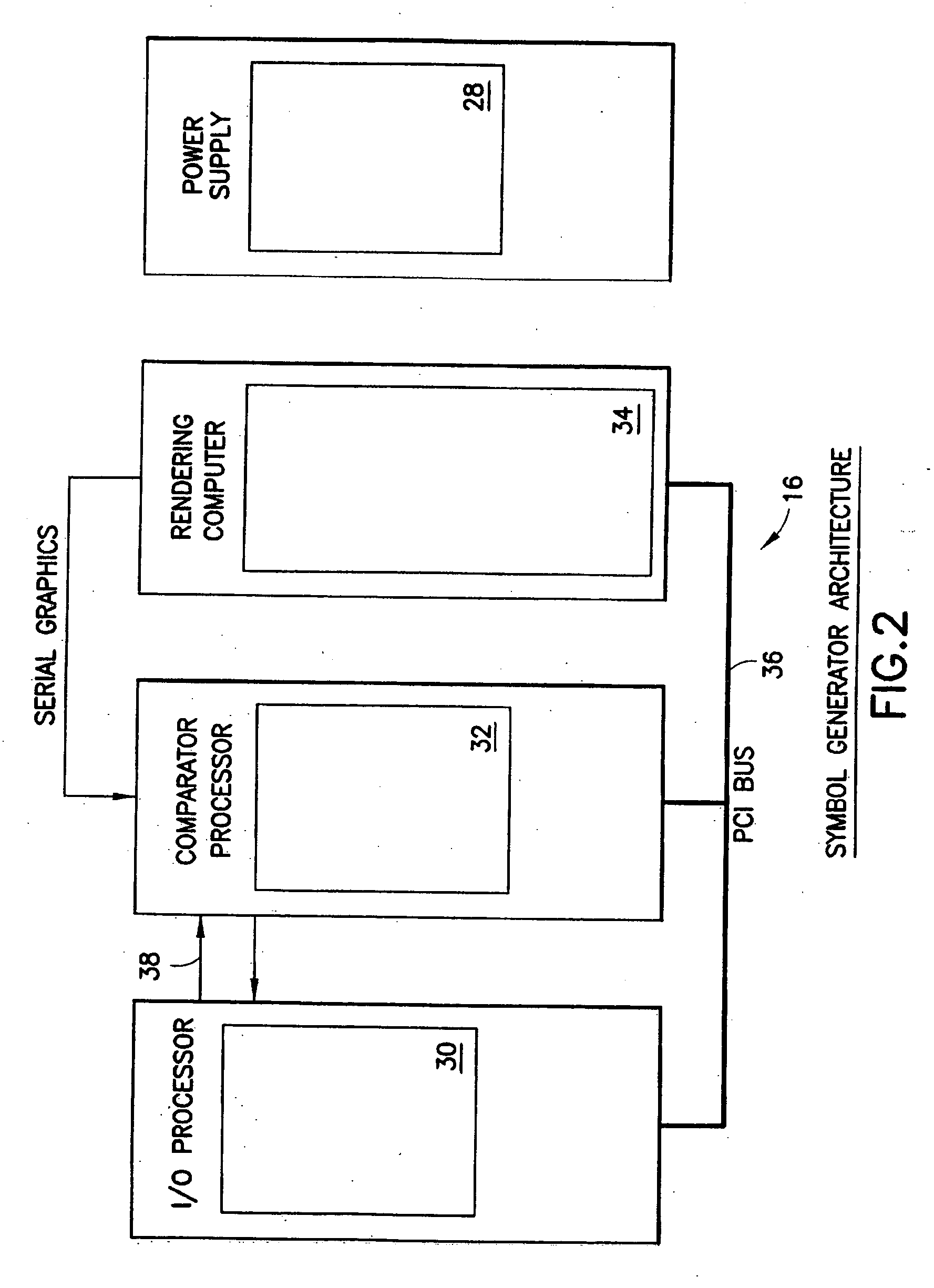
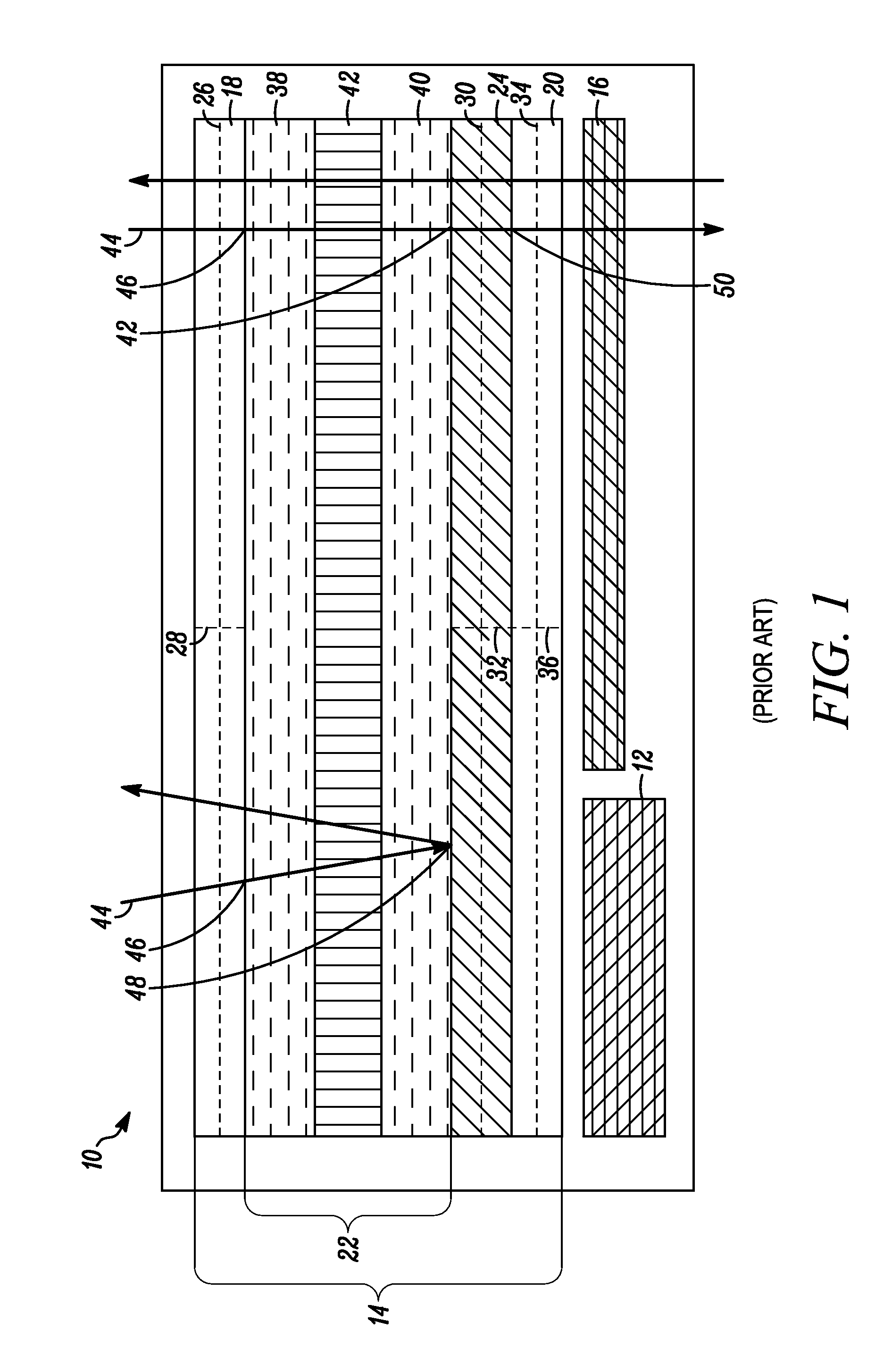
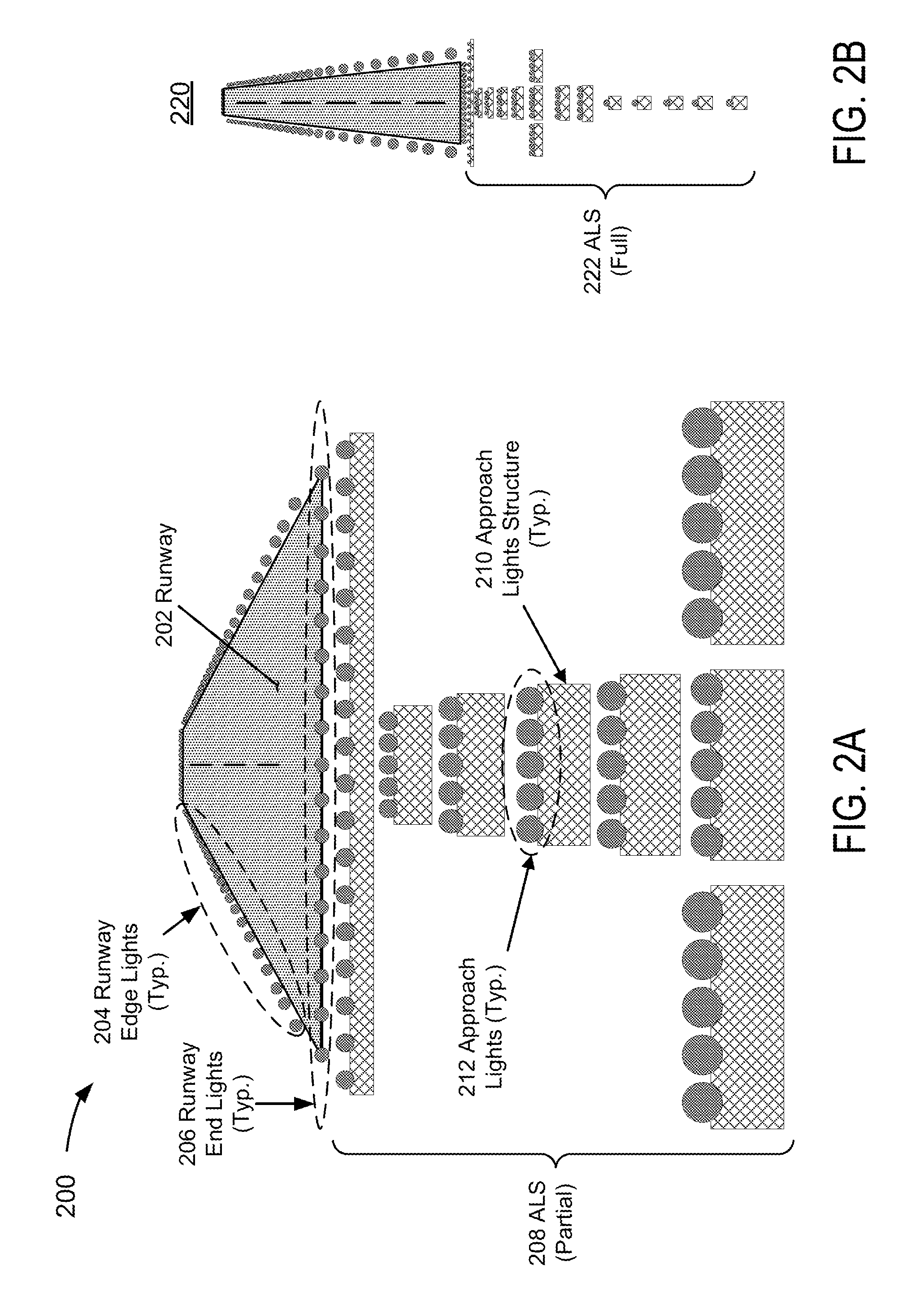
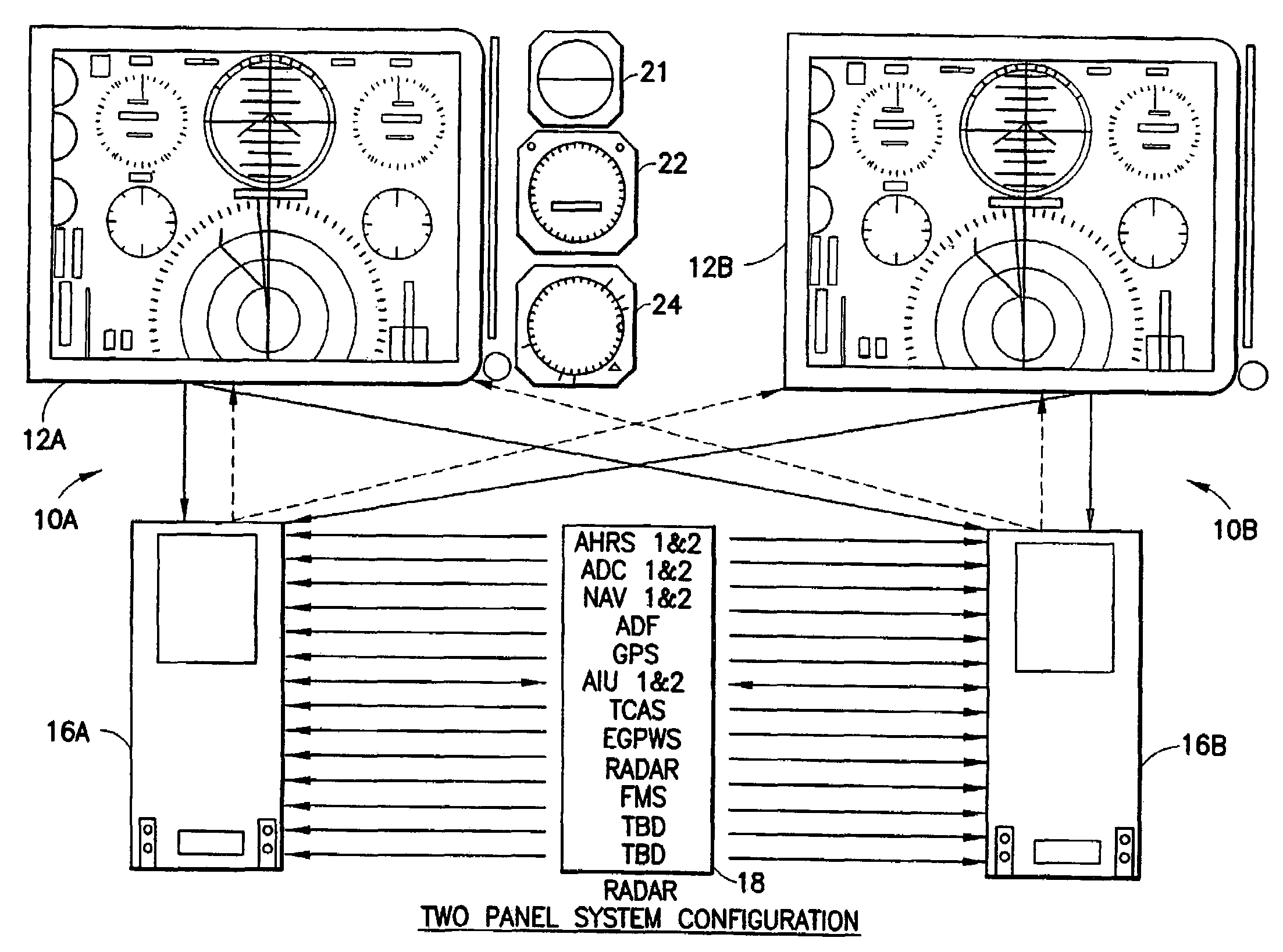
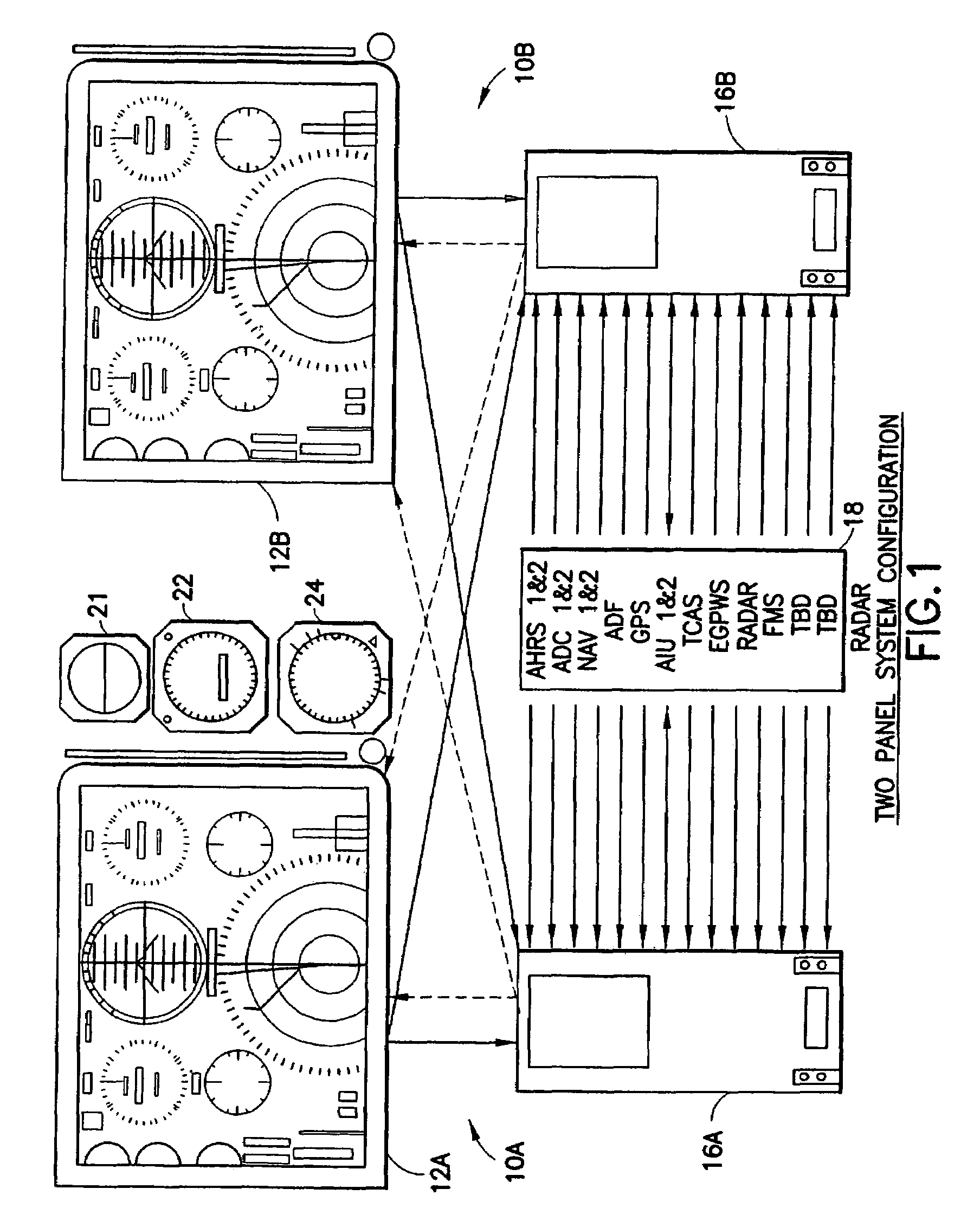
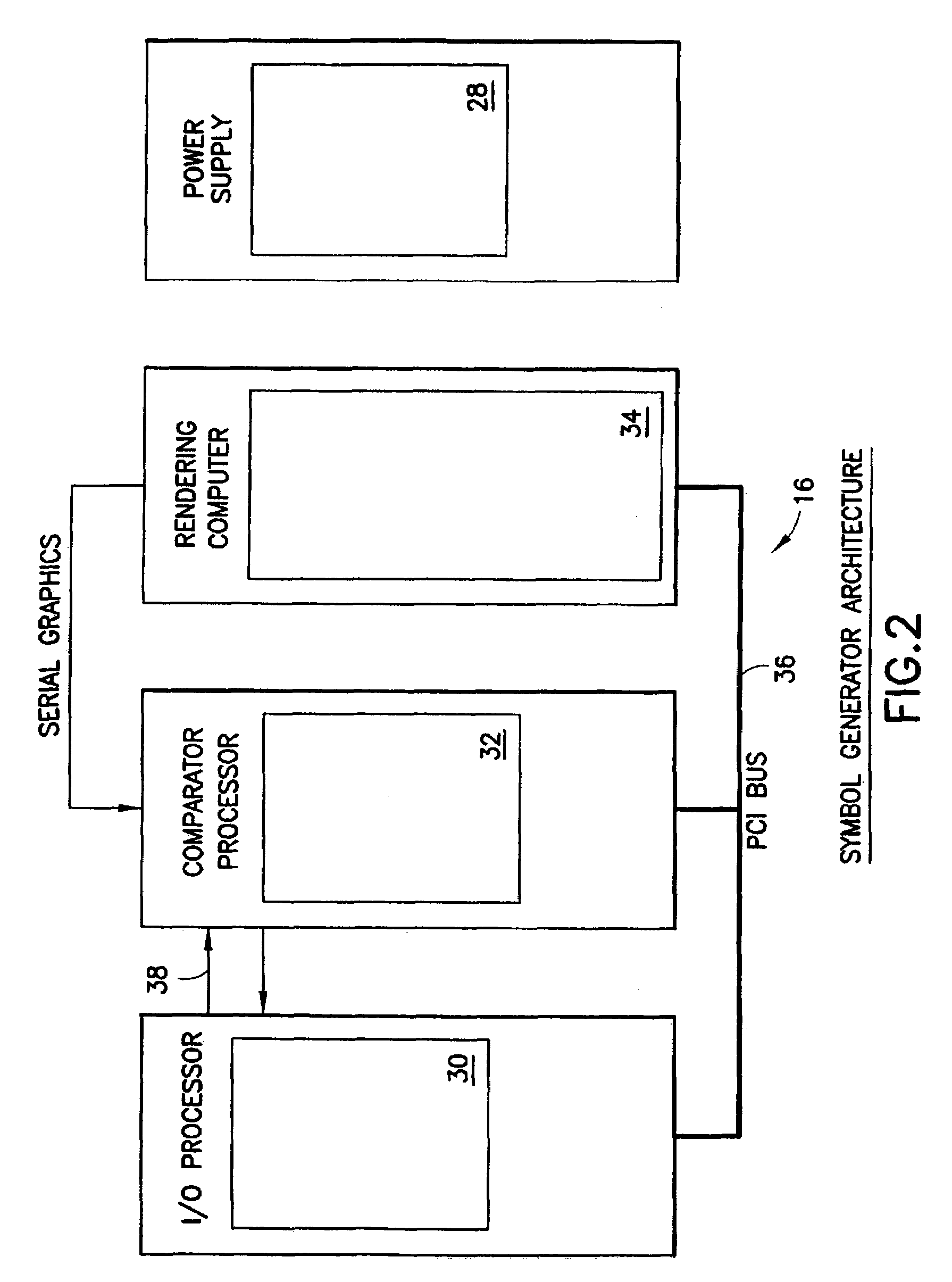
Aircraft flat panel display system with graphical image integrity
ActiveUS20070046670A1Enabling detectionDrawing from basic elementsDigital computer detailsGraphicsImage integrity
An improvement over prior art aircraft instrument flight display systems for imaging on a bit-mapped display formed of a multiplicity of individually addressable pixels at locations throughout the display and actuatable to create images on the display, employs a common processor operatively connected between a video graphics processor and the display system input of a common set of aircraft and environmental sensor data—to provide both an integrity checking function and a graphics rendering function in which the integrity checking function can directly check the images generated by the graphics rendering function without the need for comparator hardware. Separate processors may also be employed instead of a common processor. The integrity checking function uses the input information for generating a pixel verification map for checking the display based on pixel color and location. The system can also check for pitch and roll accuracy as well as check the integrity of complex images using statistical detection.
Owner:INNOVATIVE SOLUTIONS & SUPPORT
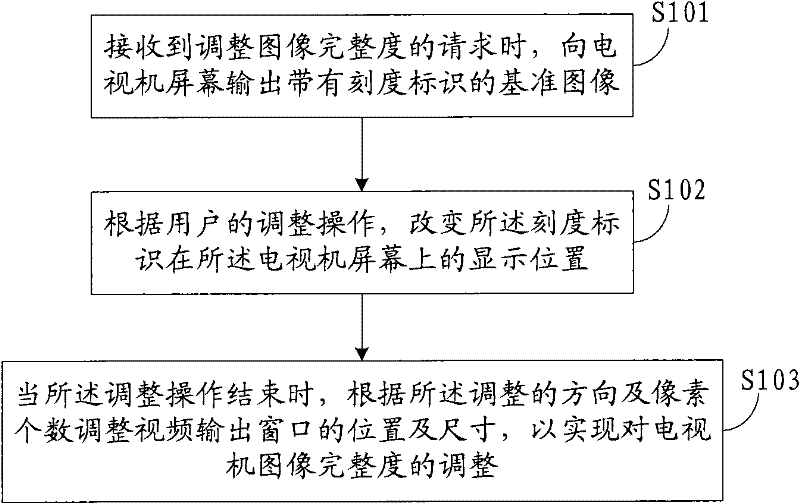
Method and device for adjusting image integrity of television
ActiveCN102244745AAdjust completenessPerformance is not affectedTelevision system detailsColor television detailsImage integrityTelevision screen
The invention discloses a method and device for adjusting image integrity of a television. The method comprises the following steps of: when receiving a request of adjusting the image integrity, outputting a reference image with a scale mark to a television screen; according to the adjusting operation of a user, modifying the display position of the scale mark on the television screen; when the adjusting operation is finished, recording the adjusting direction and the number of pixels, and adjusting the position and the size of a video output window according to the direction and the number of the pixels to adjust the image integrity of the television in real time. With the method and the device, the user can adjust the television image integrity according to the requirement per se, and other performances of the television can not be influenced in the adjusting process.
Owner:STARTIMES SOFTWARE TECH CO LTD
Damage-free digital watermarking based image tampering detection and positioning method
InactiveCN101236645ADoes not affect correct extractionImage data processing detailsImage integrityRegioselectivity
The invention discloses a detection and location method for image tampering based on no damage to digital watermarks in the image integrity authentication technical field. At first, an authentication area is selected from an image and is made a multi-layer division, then an authentication code of image data in each layer of subarea is calculated, the description information of the authentication area and the authentication information of each subarea are added into a watermark load to be embedded into the image by adopting a method which has area selectivity and has no damage to digital watermarks; when the tampering is detected and located, the description information of the authentication area is read form the watermark load, an authentication area is reconstructed on the restored image and is made a multi-layer division, an authentication code of the image data in each layer of subarea is calculated, the authentication code is compared with the authentication code of the corresponding subarea extracted from the watermark load to determine the tampered area. Any tampering in a non-embedding area in the invention has no effluence on the correct extraction of the watermark information.
Owner:SHANGHAI JIAO TONG UNIV
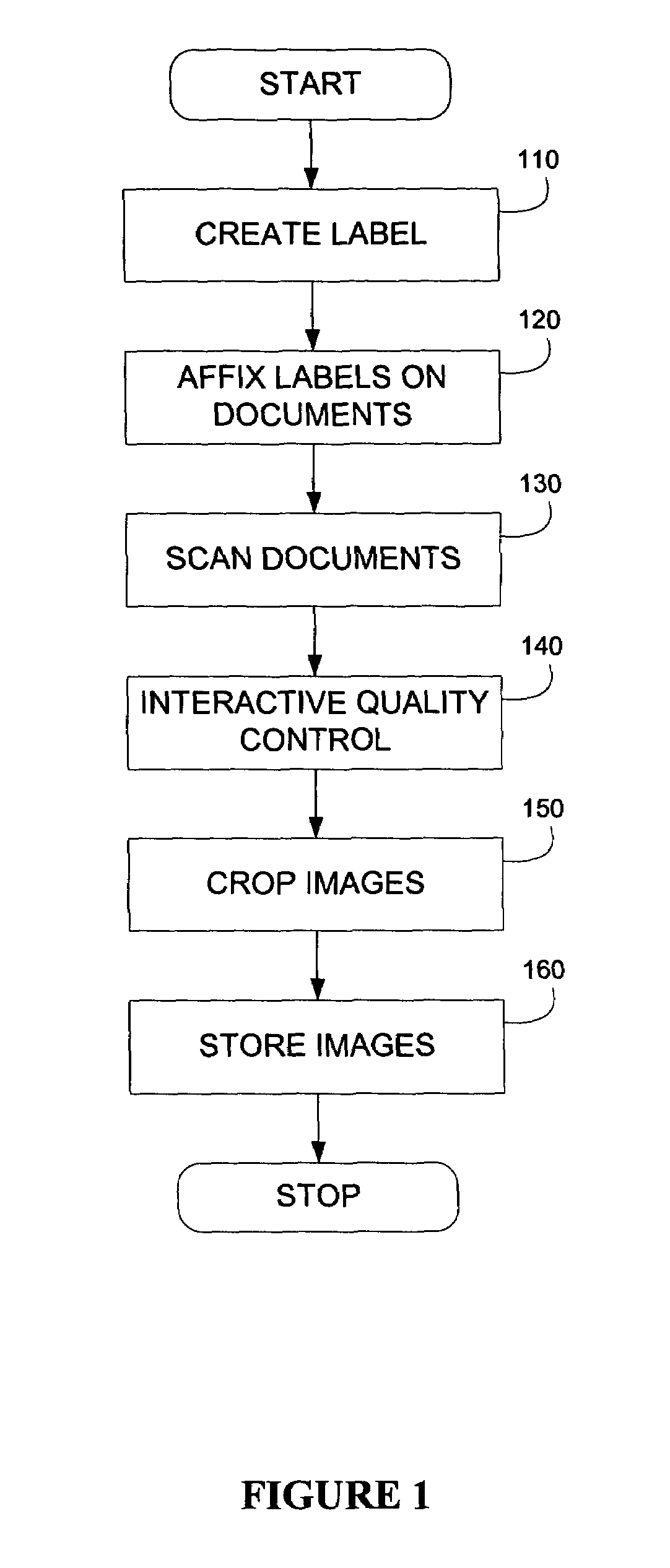
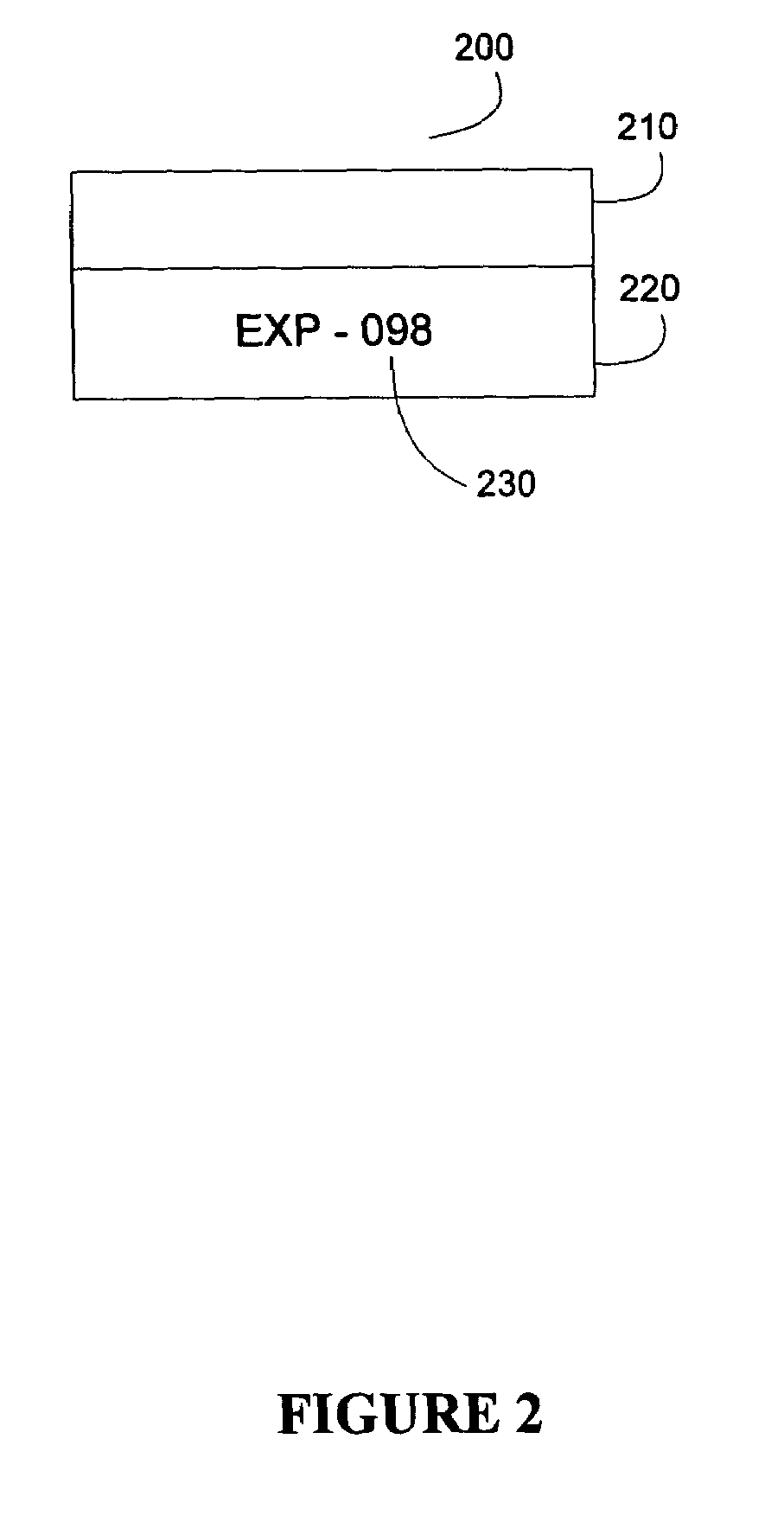
Labeling system and methodology
ActiveUS20050040642A1High level of assuranceHigh levelOther printing matterCharacter and pattern recognitionImage integrityQuality control
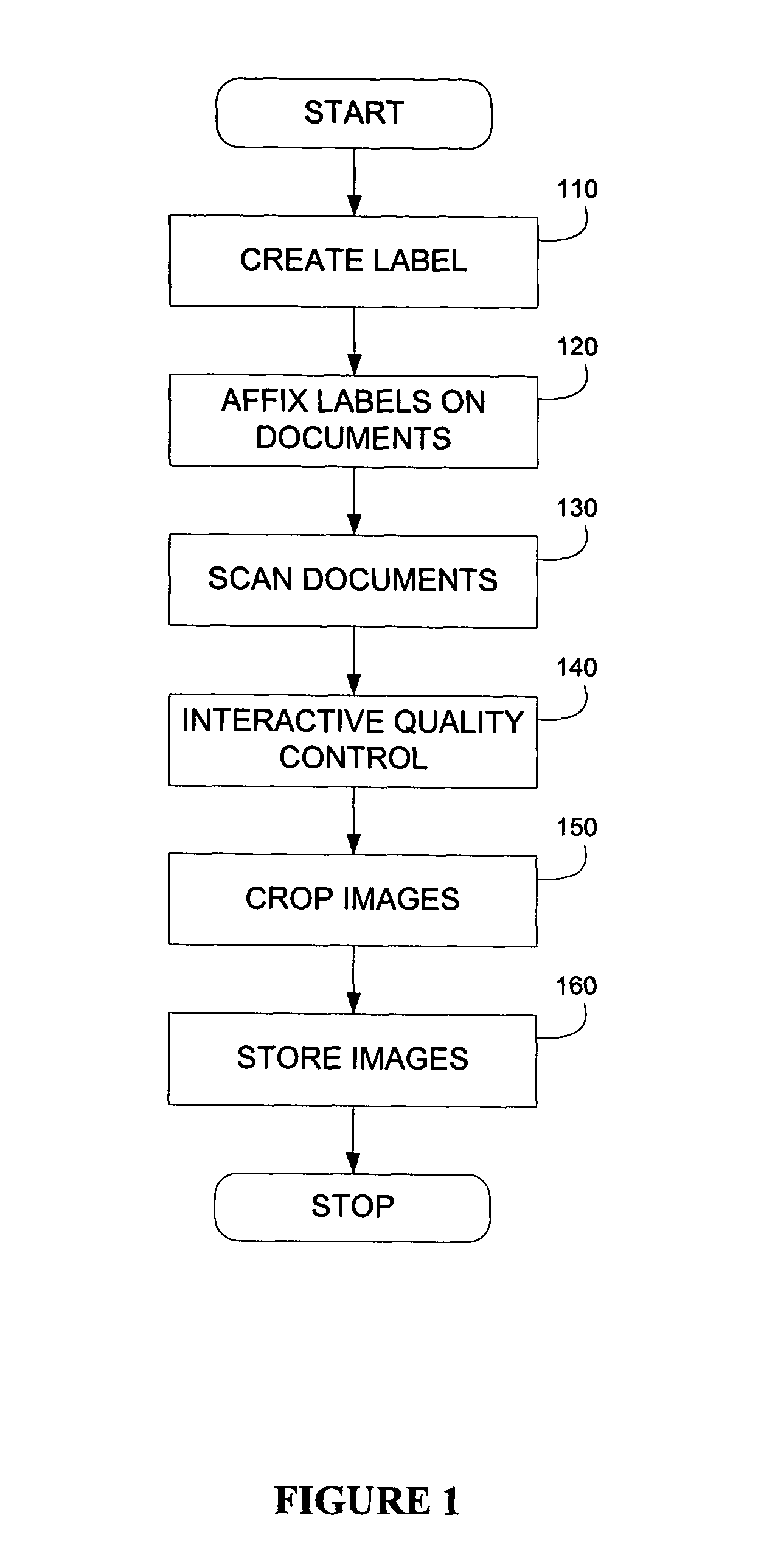
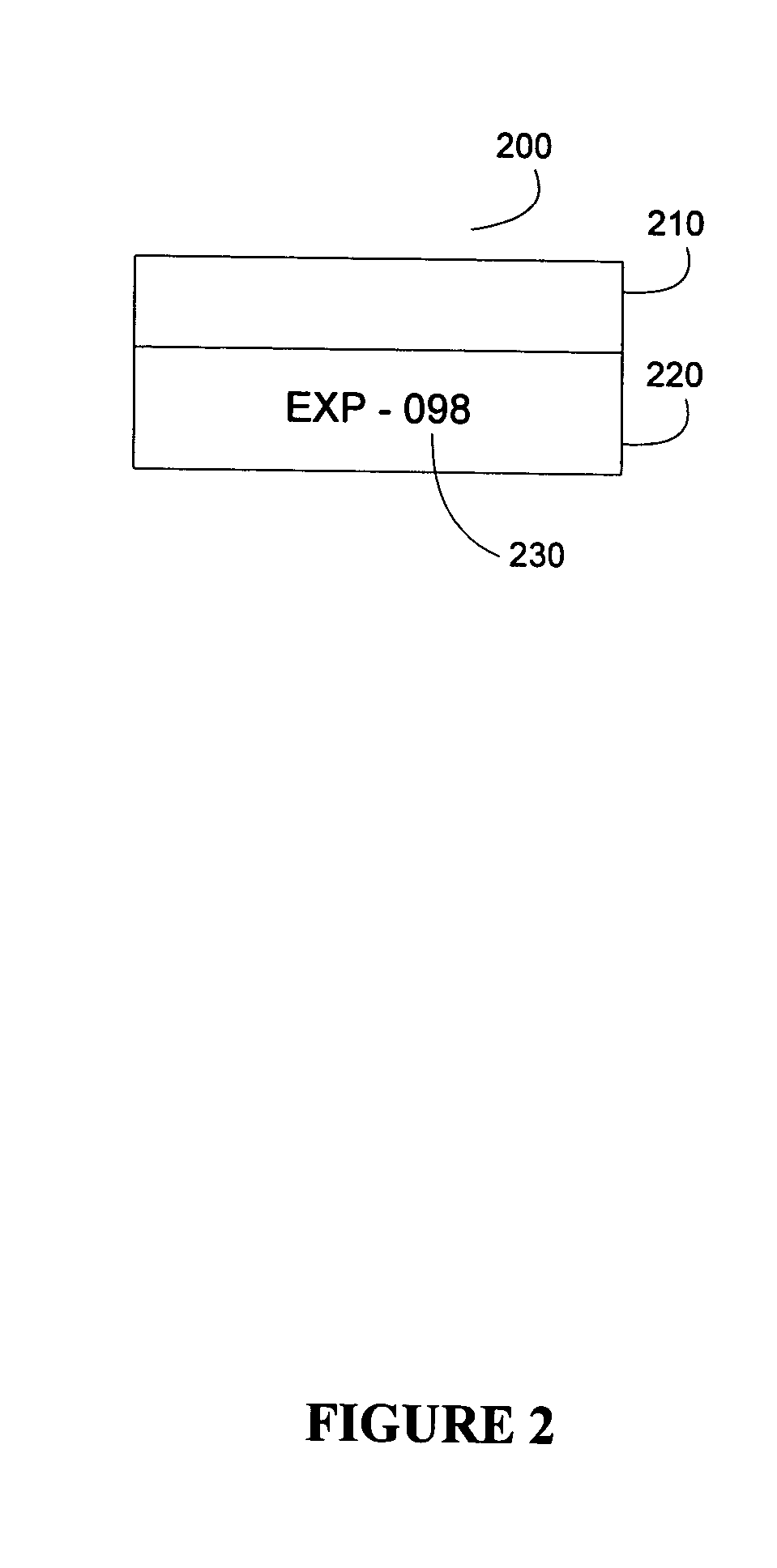
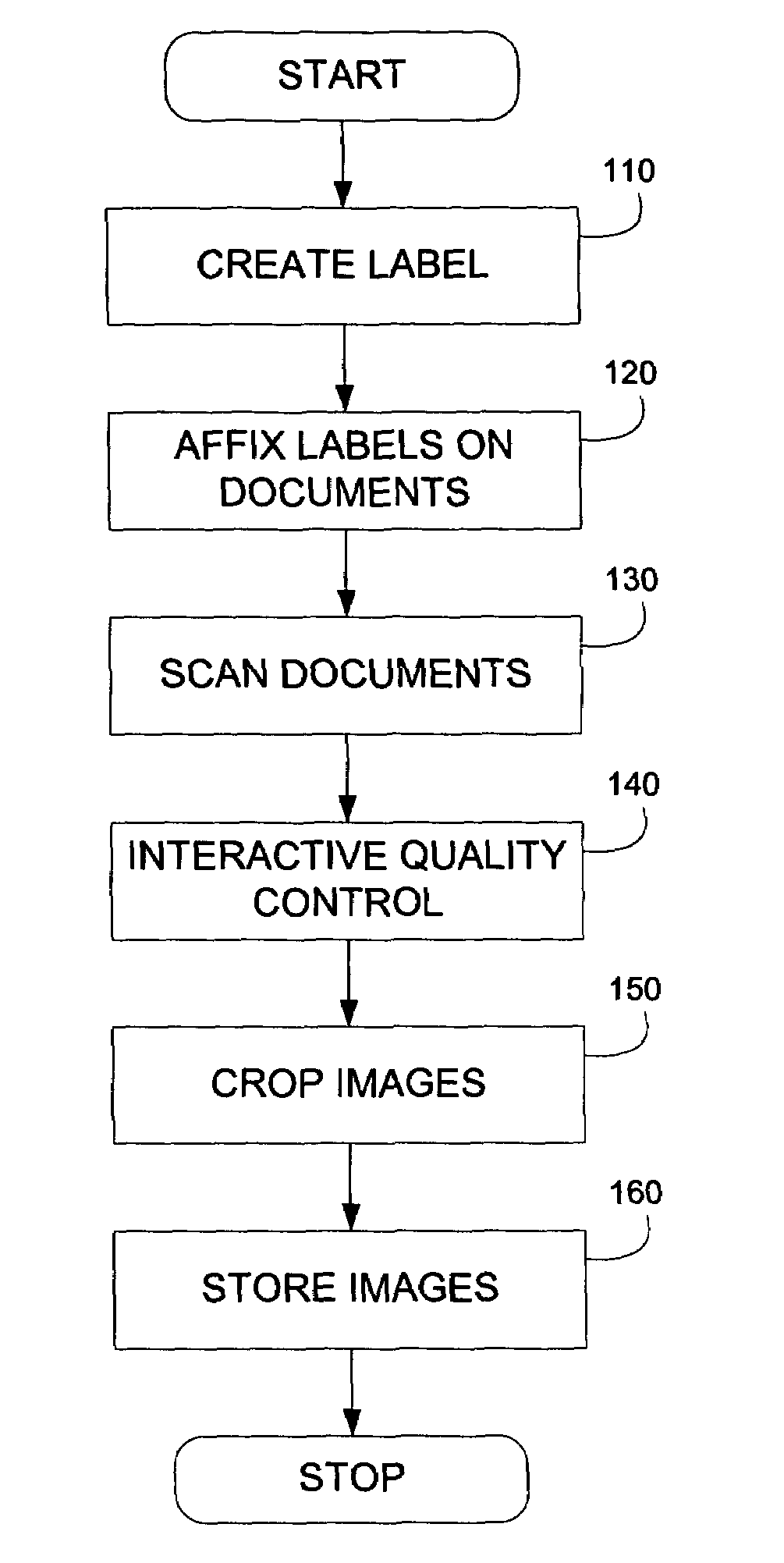
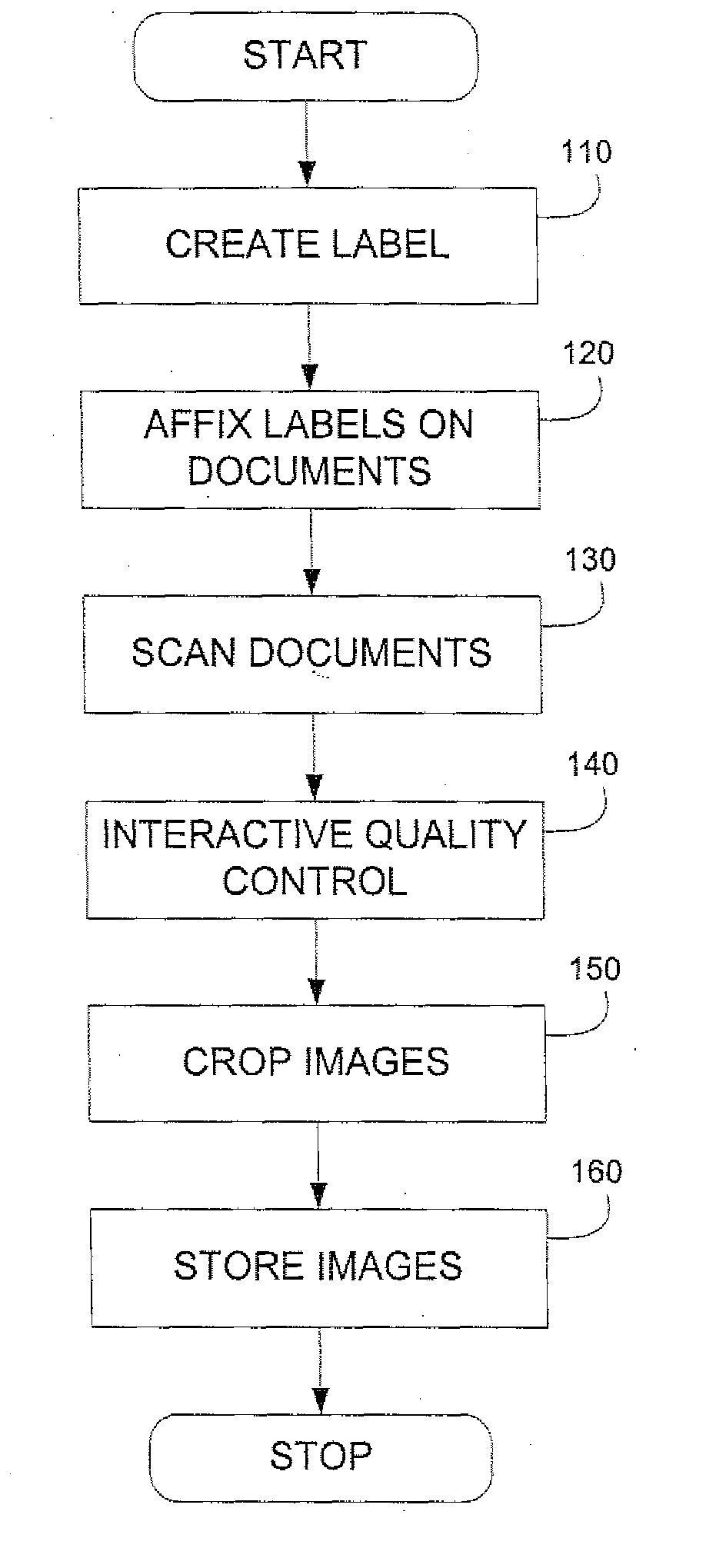
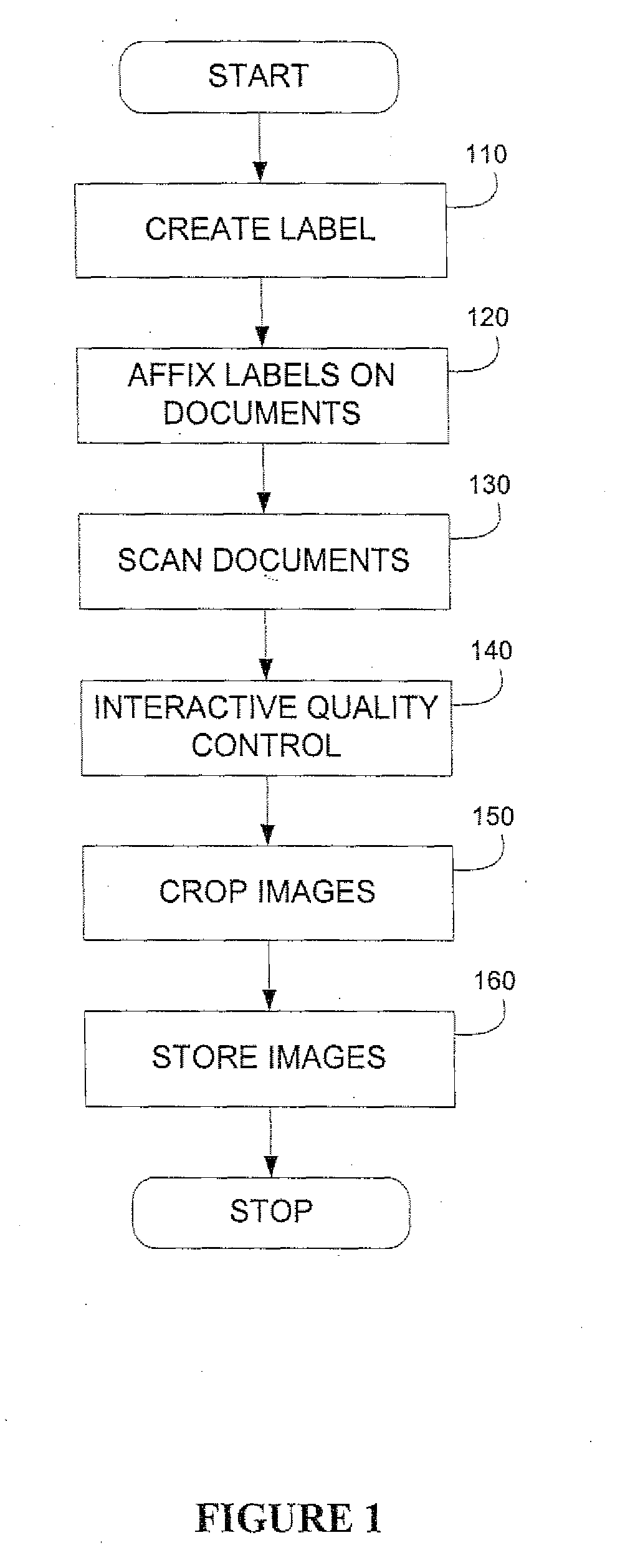
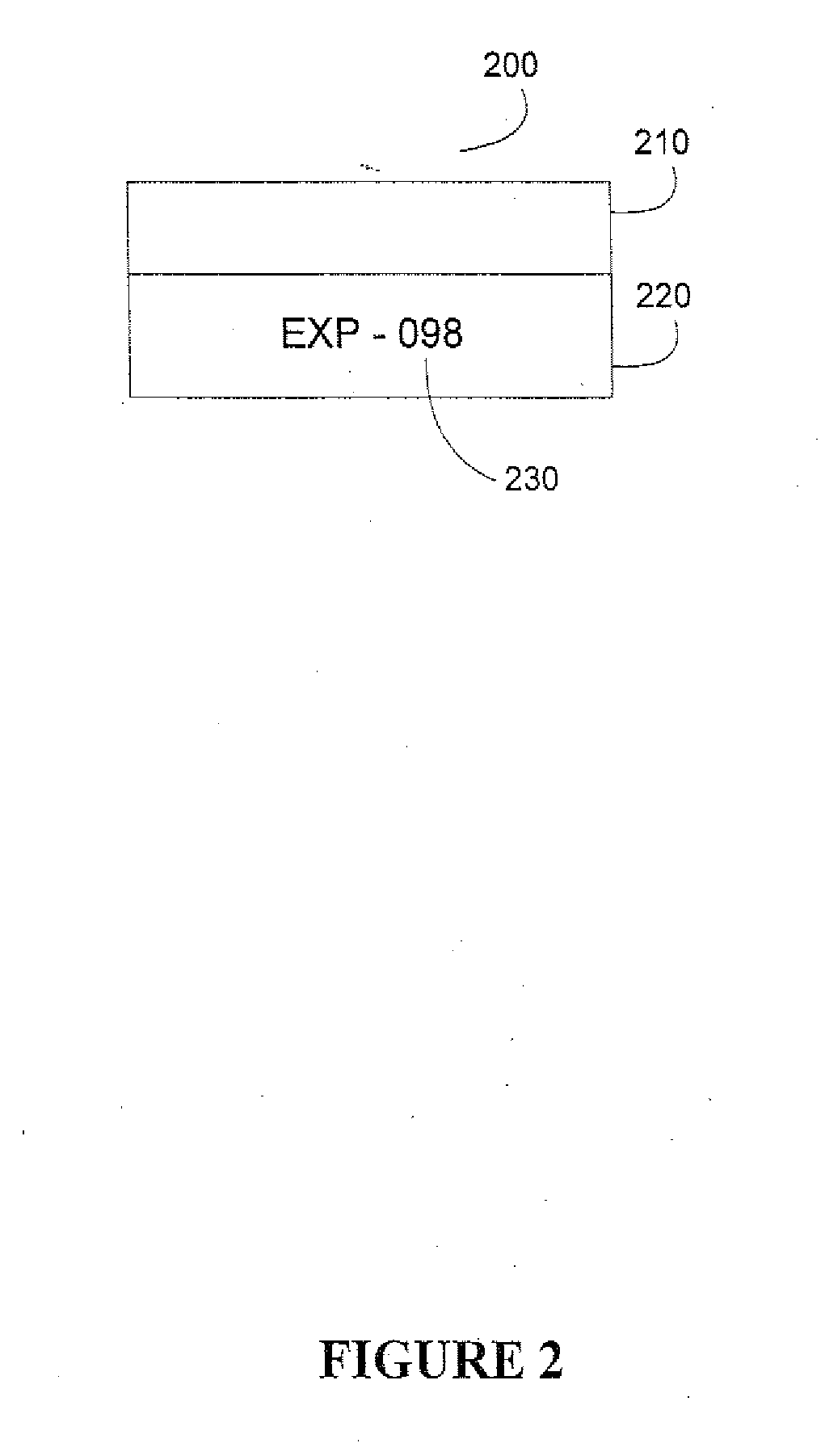
A digitization process and system which involves the use of a novel label, labeling system and labeling methodology. According to the teachings of the present invention, the label is comprised of two parts one of which is transparent and the other of which is opaque. Bates numbers or other identifiers according to some sequential numbering or ordering scheme are placed on the opaque portion of the label. The labels are placed on document edges prior to scanning and removed after scanning. Following scanning, an interactive quality control process is carried out in order to ensure image integrity against the original document sequence and integrity. After the sequence and integrity of the images is verified, the images are cropped so as to remove the ordering information and then the document may be stored possibly for later retrieval via its unique identifier. In this way, document integrity can be assured and stored document images reflect the actual document appearance rather than as modified by a label or stamped identifier. Labels may easily be removed from the original hard copy documents so that these documents may also be returned to their original form.
Owner:JIANG HUBIN
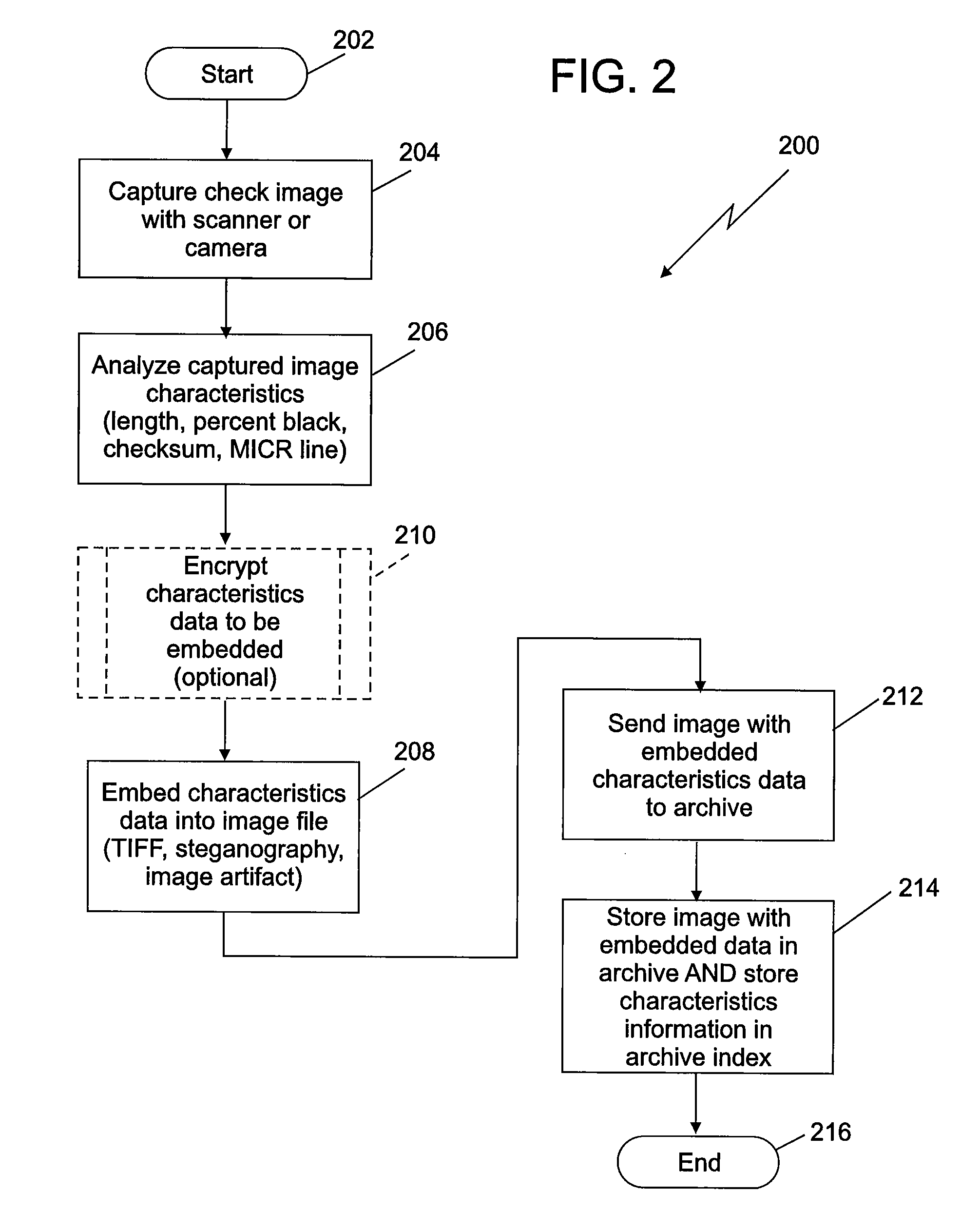
Ensuring image integrity using document characteristics
ActiveUS8639062B2Digital data information retrievalUser identity/authority verificationTagged Image File FormatImaging analysis
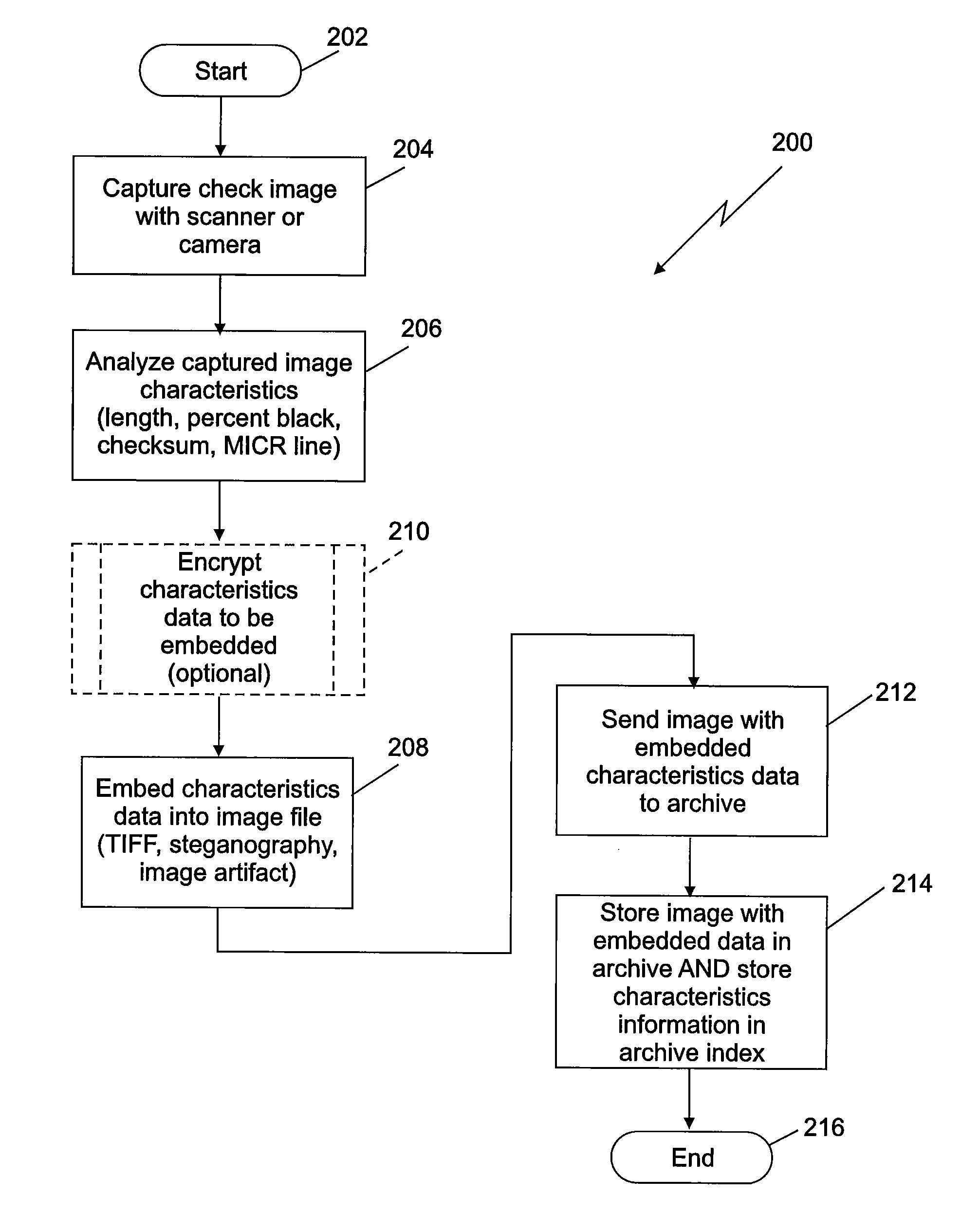
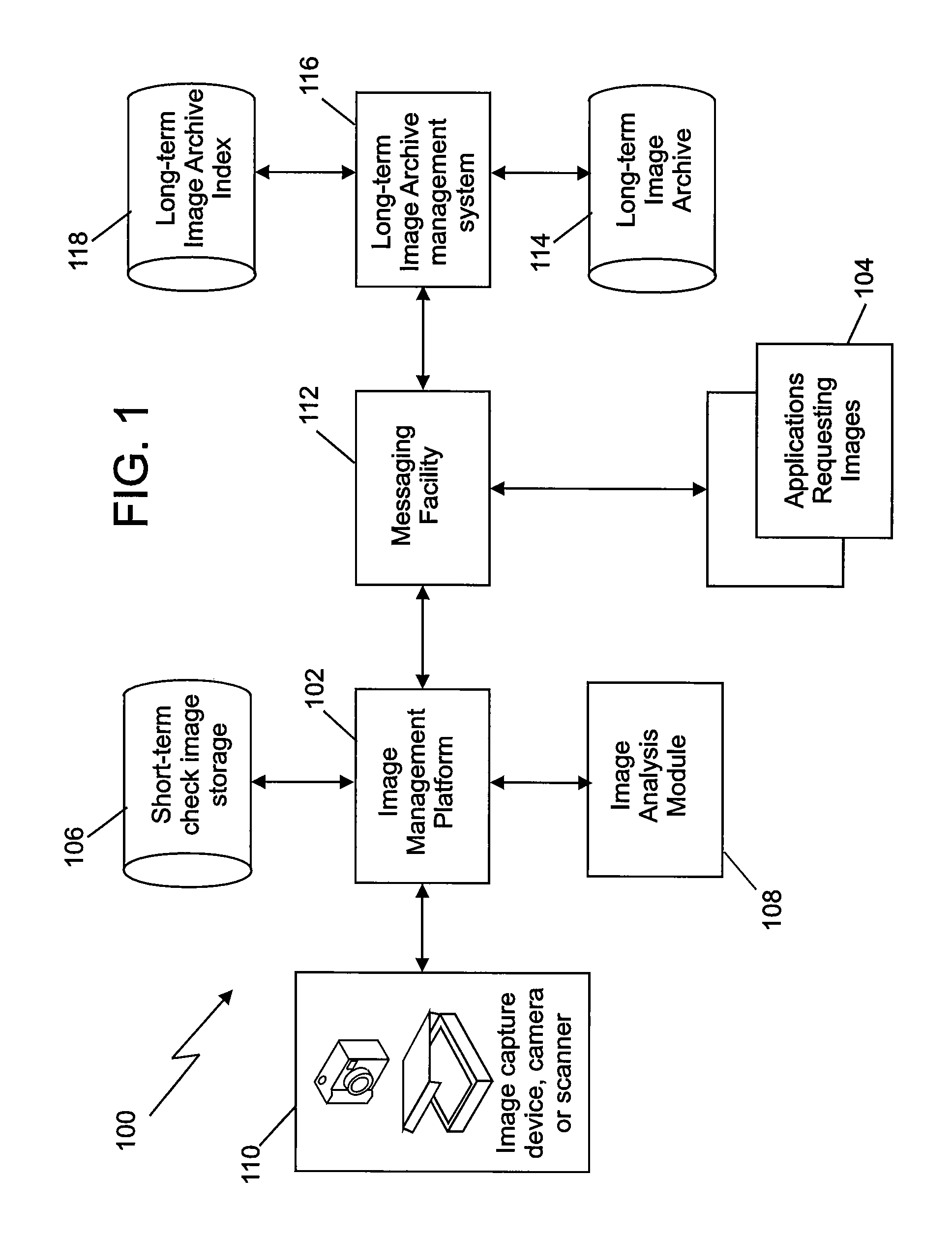
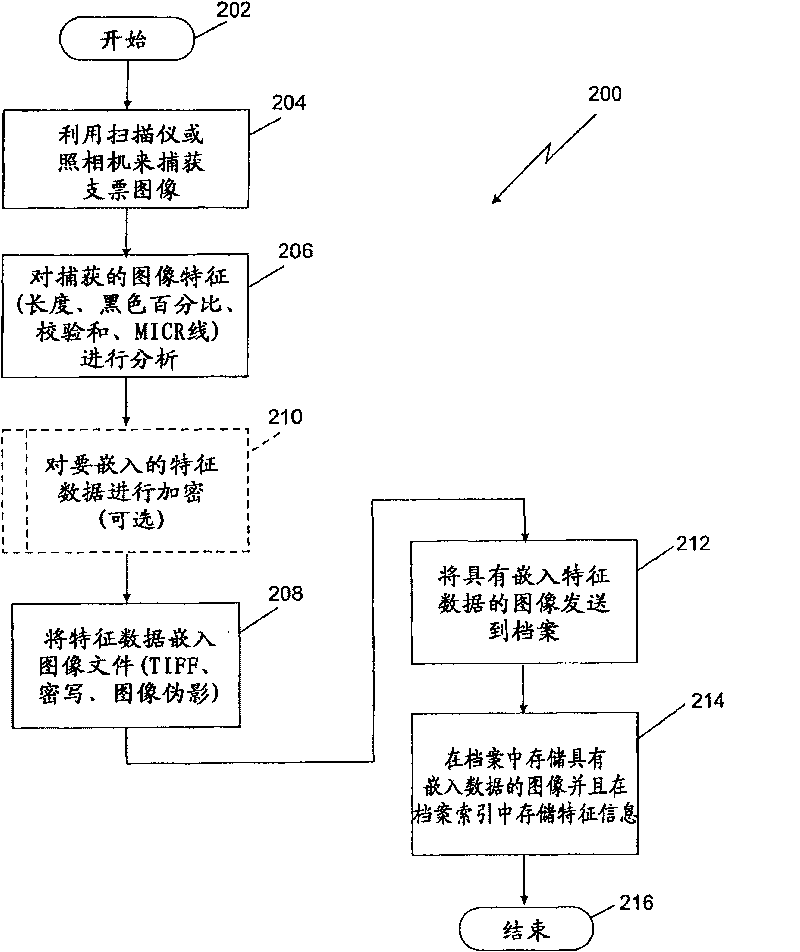
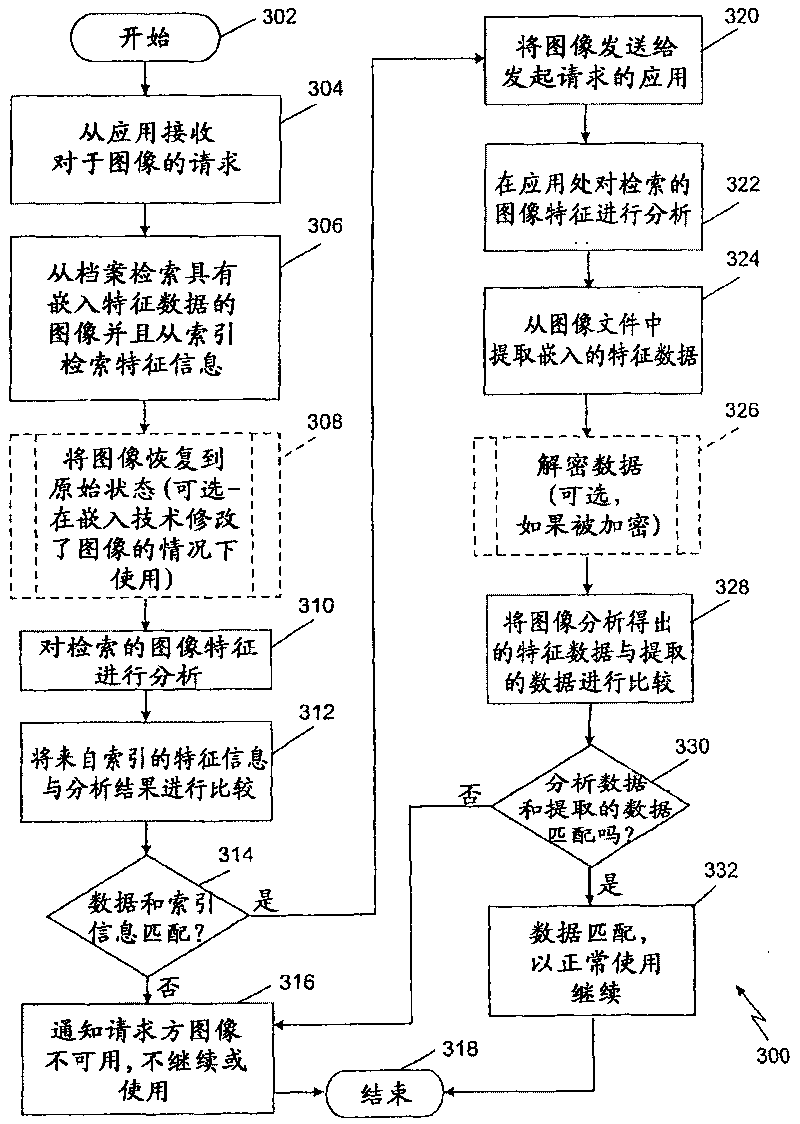
Image integrity in an archive can be verified using document characteristics. Embodiments of the invention provide a way to verify the integrity of a stored document image by determining document characteristics, which can also be embedded in the image file. Before allowing access to the image file by an application, the characteristics data from an image analysis can be compared to either or both of, characteristics information otherwise stored, or embedded characteristics data. The embedded data can optionally be encrypted. In example embodiments the data can include a result of an optical character recognition of contents of the document, a length of data describing the image, a percentage of a specified color of pixels in the image, or a checksum. Example embedding techniques can include those making use of a tagged image file format (TIFF) header, a steganographic watermark, or an image artifact.
Owner:BANK OF AMERICA CORP
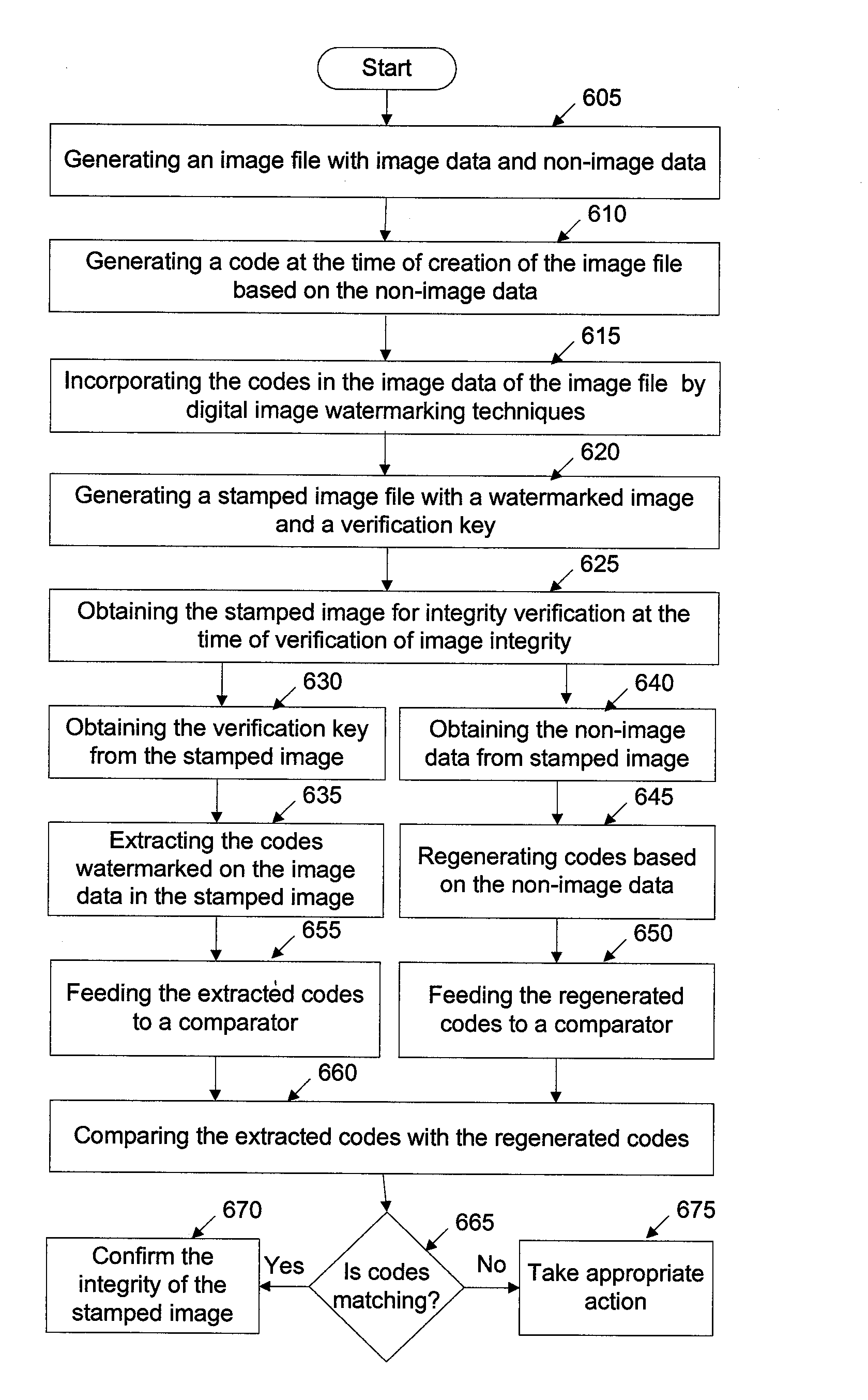
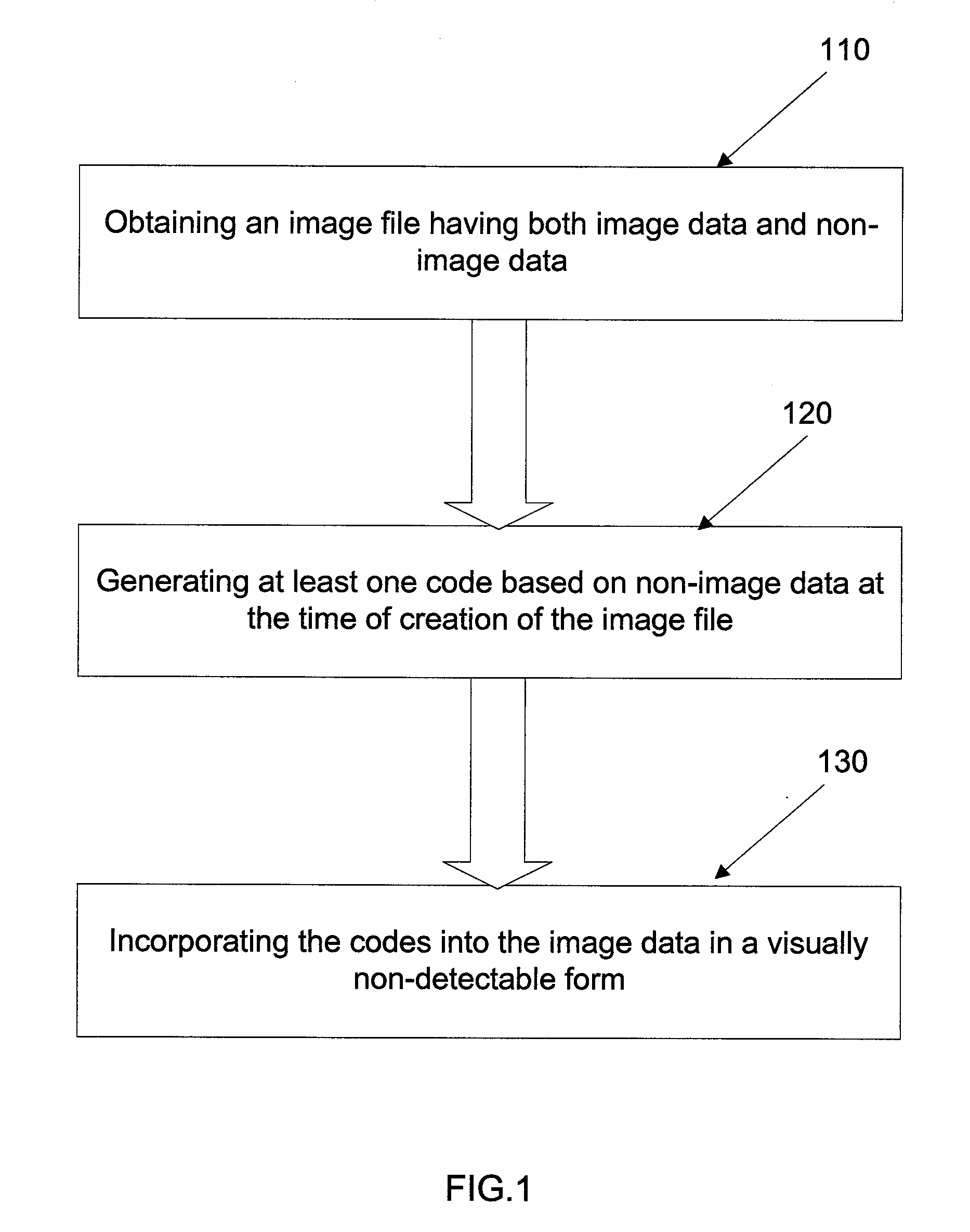
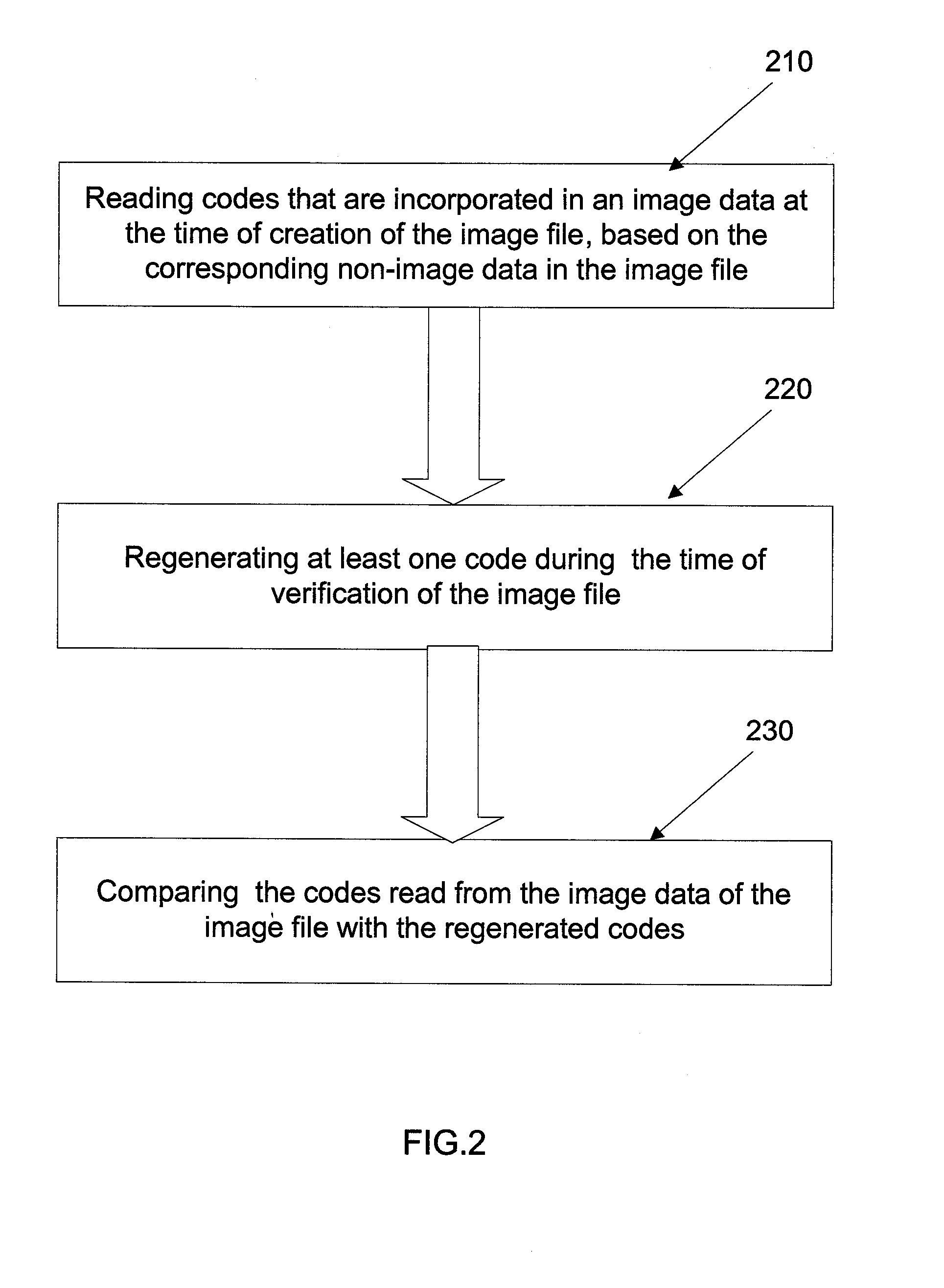
Method and system for image integrity determination
ActiveUS20090067667A1Character and pattern recognitionDigital data protectionImage integrityComputer vision
A method and system for determining integrity of images is disclosed herein. The method includes determining the integrity of a non-image data of an image file. The method of protecting images comprises: obtaining an image file having both image data and non-image data and generating at least one code based on the non-image data at the time of creation of the image file. The code is incorporated into the image data of the image file in a visually non-detectable format. In an example, a digital watermarking technique is used to incorporate the code into the image data.
Owner:GENERAL ELECTRIC CO
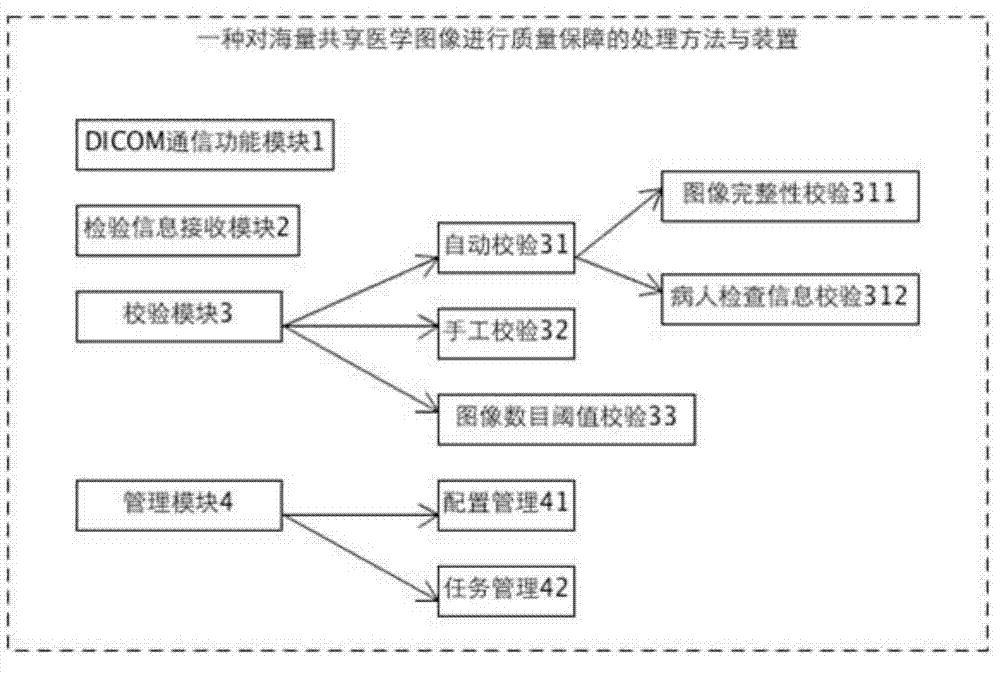
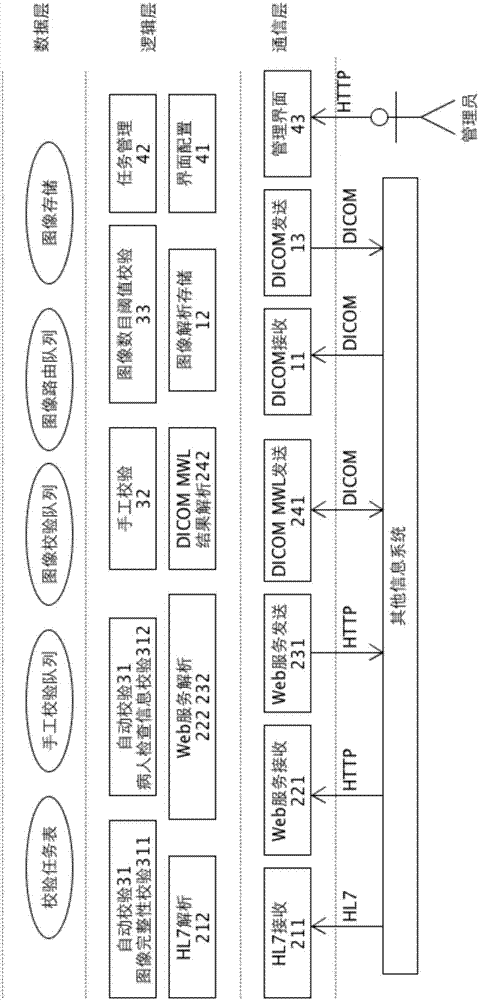
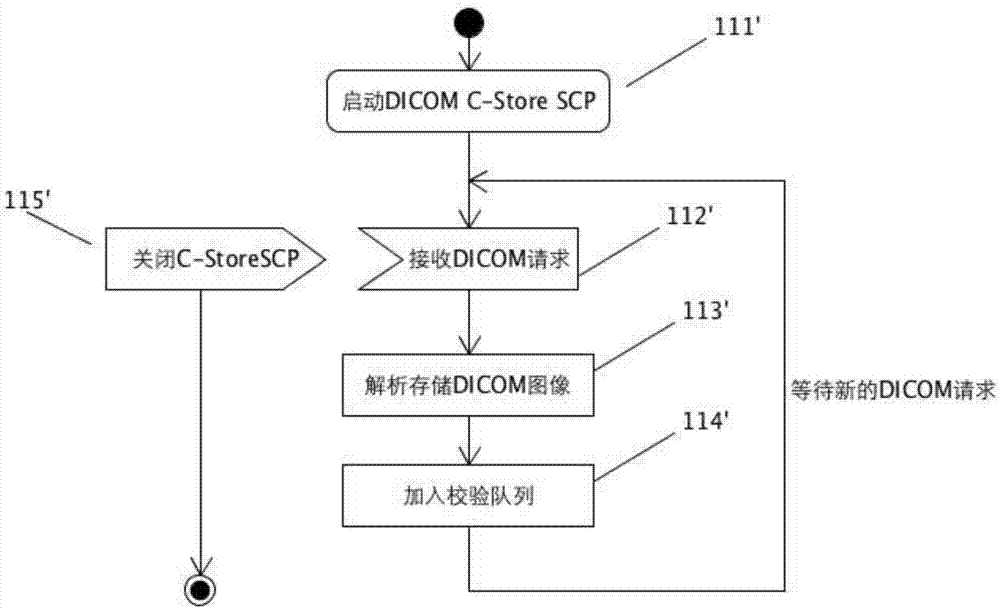
Processing method and device for conducting quality assurance on mass shared medical images
ActiveCN107292117AIntegrity guaranteedGuaranteed correctnessSpecial data processing applicationsImage integrityQuality assurance
The invention relates to a processing method and device for conducting quality assurance on mass shared medical images. The device has the function of according with DICOM standard communication, further comprises an image index information quality verification module and an image control module, can define image index information verification values and image number thresholds by itself, can conduct image integrity verification, can obtain patient verification information from a hospital information system or region information system, conducts automatic and manual verification on the provided verification information, updates DICOM label values corresponding to the images after the verification is completed, can further control whether to send the thresholds to other information systems or not according to the image number threshold definition, and accordingly guarantees the uniformity, integrity and correctness of the patient check information on the images and other information systems. The processing method and device can be applied to a sharing platform of a hospital and a region, solve the problems that the patient information of the hospital information system or region sharing collaboration platform is inconsistent with that of an image information system, and provides quality assurance for sharing of the mass medical images.
Owner:SHANGHAI INST OF TECHNICAL PHYSICS - CHINESE ACAD OF SCI
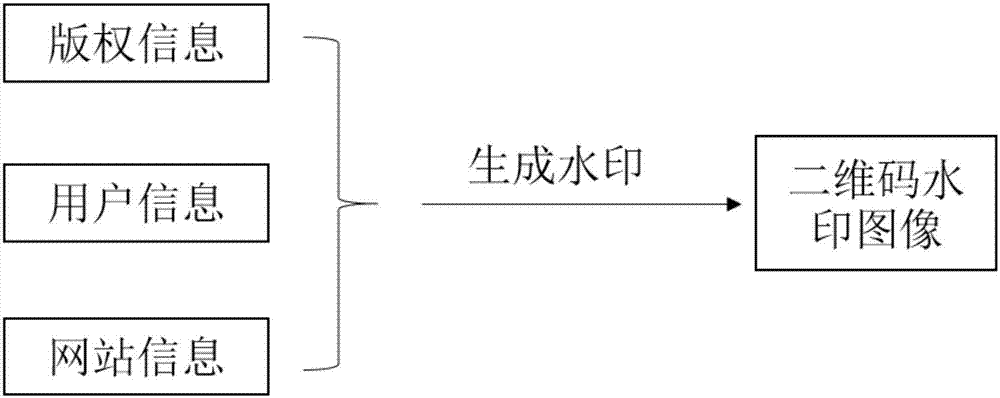
Semi-fragile unique image watermark embedding method for integrity protection and semi-fragile unique image watermark extraction method for integrity protection
InactiveCN107103577AImprove integrityIdentify illegal tamperingImage data processing detailsRecord carriers used with machinesImage integrityDigital image
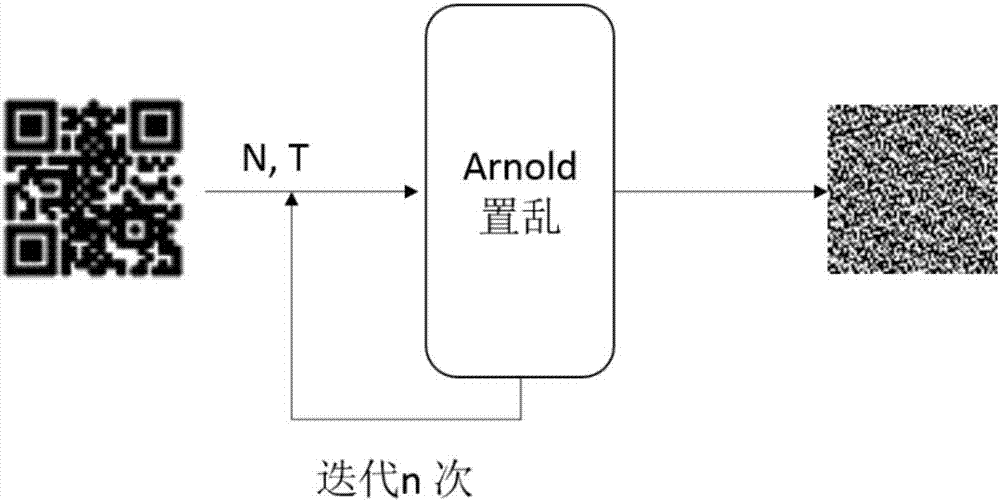
The present invention provides a semi-fragile unique image watermark embedding method for integrity protection from the semi-fragile watermark of an image. The method comprises the following steps: 1) generating a two-dimensional code image watermark according to the watermark information of a carrier image; 2) performing scrambling processing of the two-dimensional code image watermark, and obtaining a safety watermark; 3) embedding the safety watermark into the wavelet transform domain of the carrier image, obtaining an image embedded with the watermark, and generating an extraction watermark secret key; and 4) distributing the image embedded with the watermark and the extraction watermark secret key at the same time. The present invention provides an extraction method aiming at the embedding method mentioned above. The semi-fragile unique image watermark embedding method for integrity protection and the semi-fragile unique image watermark extraction method for integrity protection are effective and feasible and can authenticate the image integrity, the scheme is concise and efficient, many defects of a current image semi-fragile watermark are overcome, and the semi-fragile unique image watermark embedding method for integrity protection and the semi-fragile unique image watermark extraction method for integrity protection have important meanings for the integrity protection of digital images.
Owner:INST OF INFORMATION ENG CHINESE ACAD OF SCI
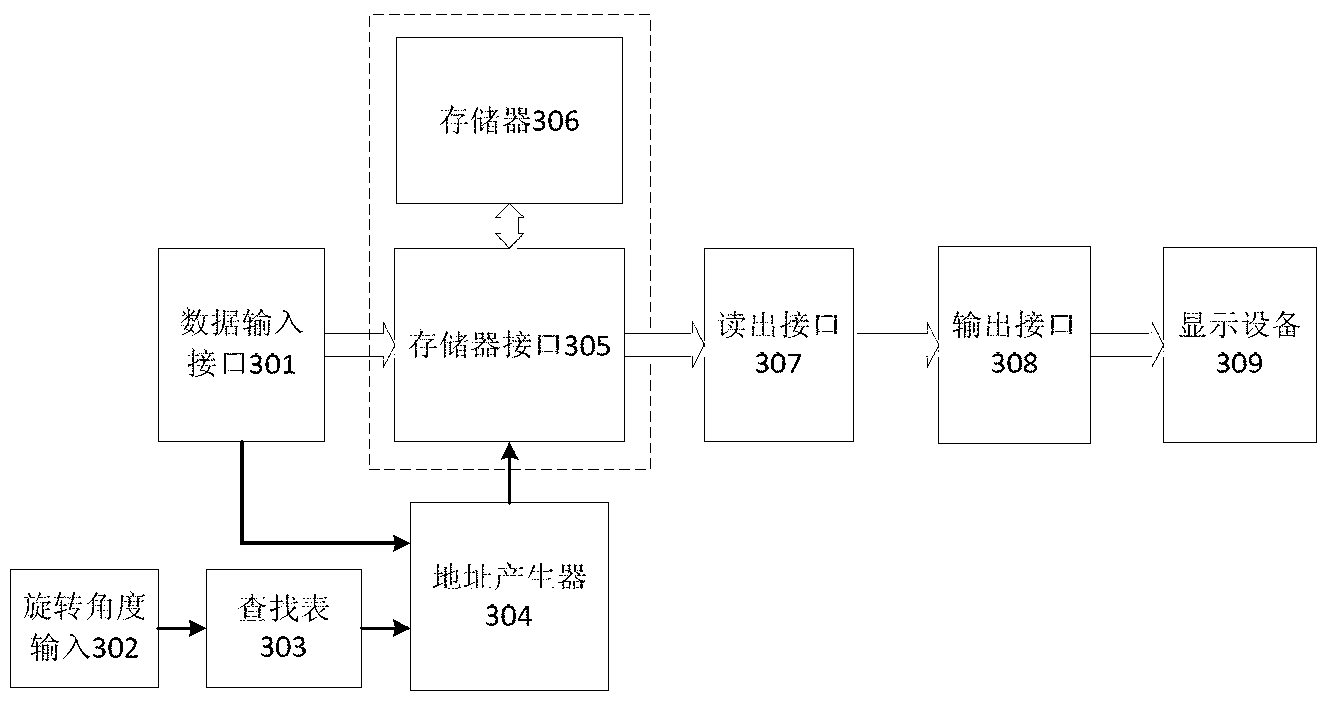
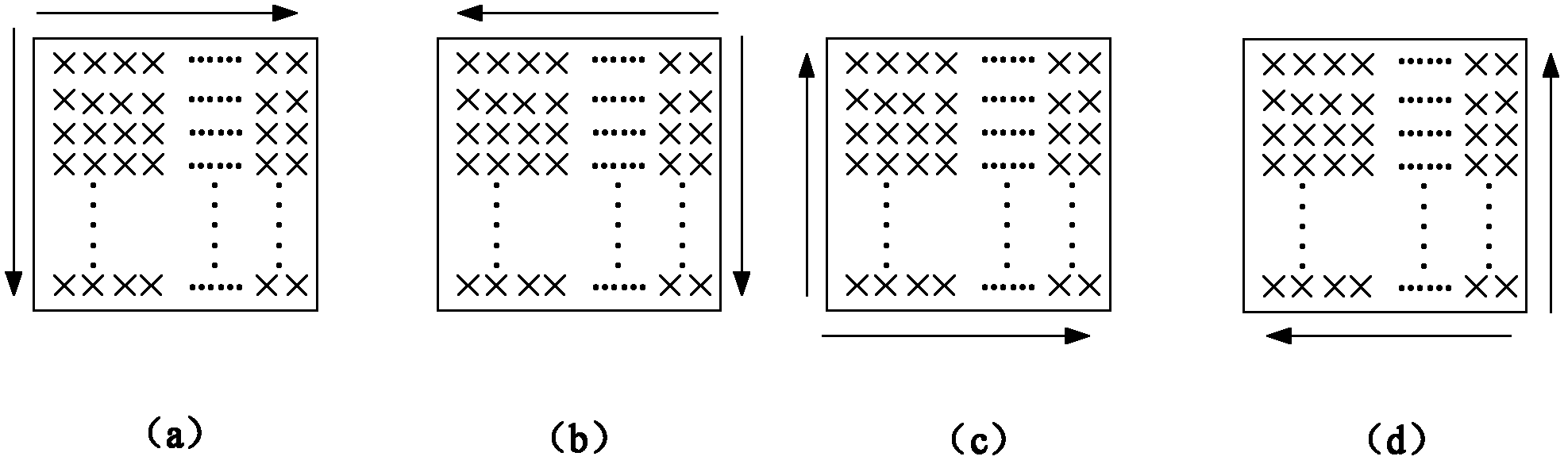
Image rotation method and device for dot matrix display equipment
InactiveCN103226807AAvoid the interpolation processCalculation speedGeometric image transformationImaging processingFast algorithm
The invention relates to the field of image processing and display and provides an image rotation method and device for dot matrix display equipment. According to the method, the pixel value of an original image is fully utilized in the process of rotating the image and corresponds to the pixels of the rotated image one to one, the image integrity is ensured, and the problem that the operational efficiency is low because of interpolation operation and multiplication is eliminated; and meanwhile, the rapid algorithm is combined with the image storage mechanism and then is applied to the real-time display process of the video image, which is suitable for hardware implementation. Therefore, according to the technical scheme, the image rotation method used for dot matrix display equipment comprises the following steps: decomposing the image rotation process into three steps, translating the horizontal coordinates of partial pixels for integer units after the first transform, translating the vertical coordinates of the partial pixels for integer units after the second transform, and translating the horizontal coordinates of the partial pixels for integer units after the third transform. The method is mainly applied to image processing.
Owner:TIANJIN UNIV
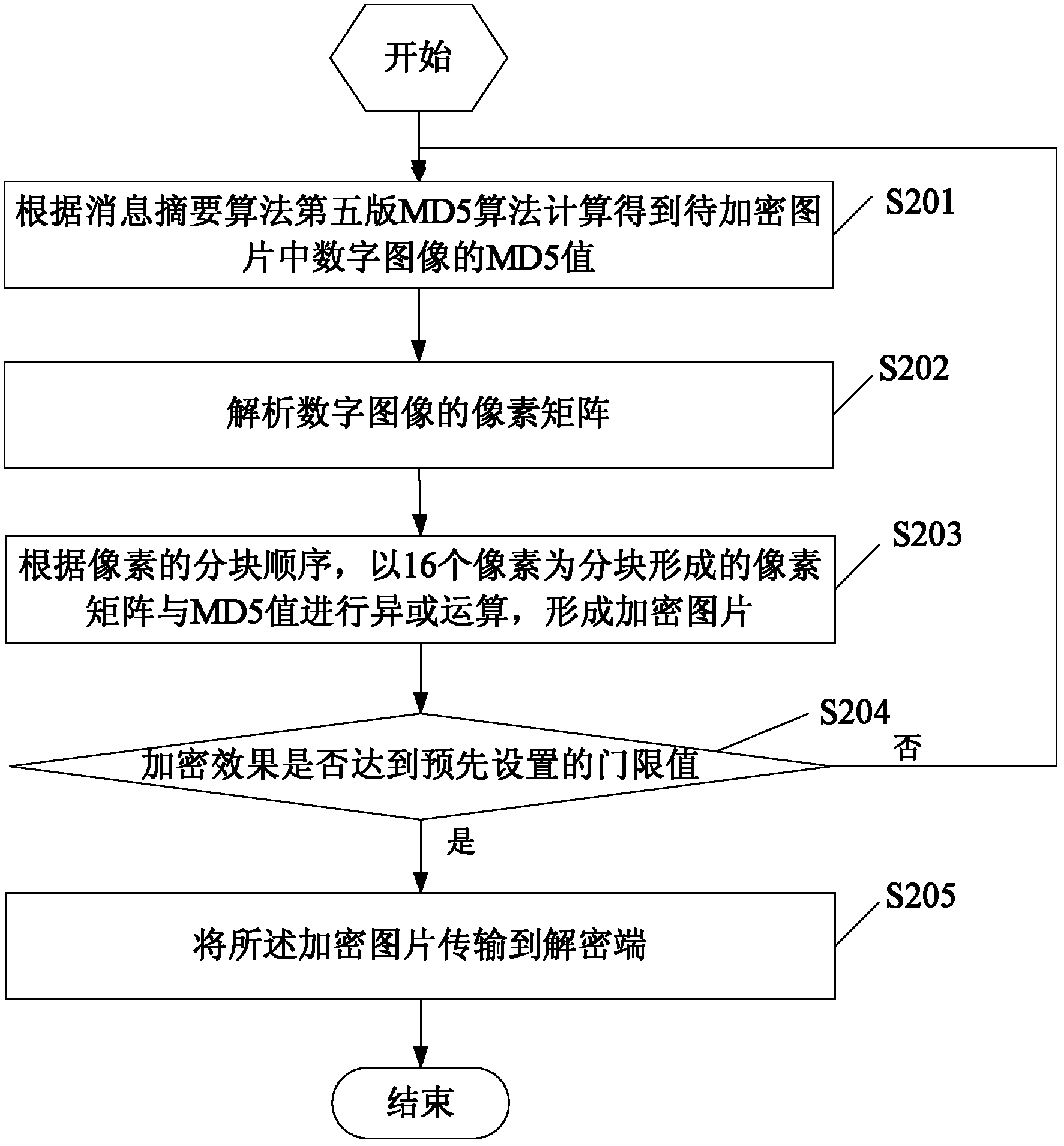
Encryption/decryption method and system based on image transmission
InactiveCN102625025ATo achieve the purpose of safe transmissionSecure Transport AuthenticationPictoral communicationImage integrityEncryption decryption
The embodiment of the invention discloses an encryption method based on image transmission. The method comprises the steps as follows: the MD5 value of the digital image of a picture to be encrypted is calculated and obtained according to the fifth edition of message abstract algorithm; the pixel array of the digital image is analyzed; according to the block sequence of the pixel, XOR operation of the pixel array formed by blocks including 16 pixels and the MD5 value is carried out, and an encryption image is formed; and the encryption image is transmitted to a decryption end. The invention also discloses a decryption method and an encryption / decryption system based on image transmission, by implementing the embodiment of the invention, the algorithm is easy to achieve, the algorithm load is low, the application is variable, the effect is good, the completeness function of the verification image is achieved, and at the same time, safe transmission of the image is ensured.
Owner:SUN YAT SEN UNIV
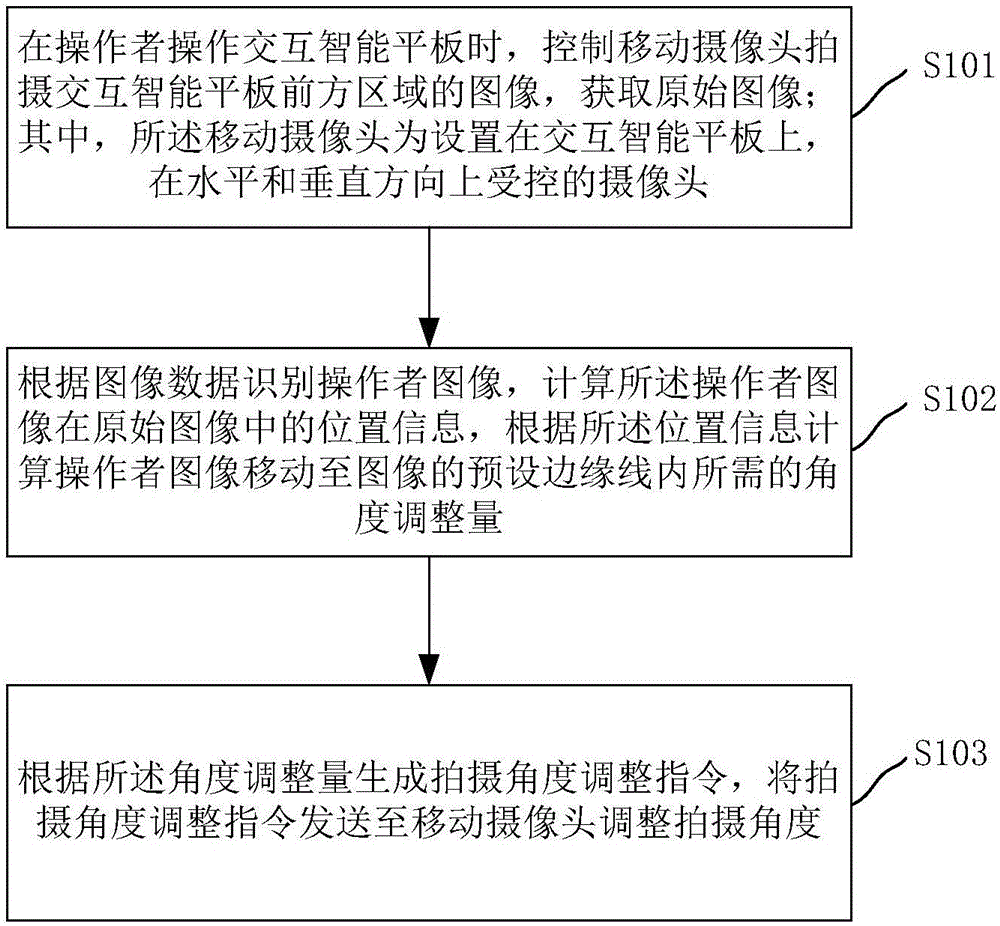
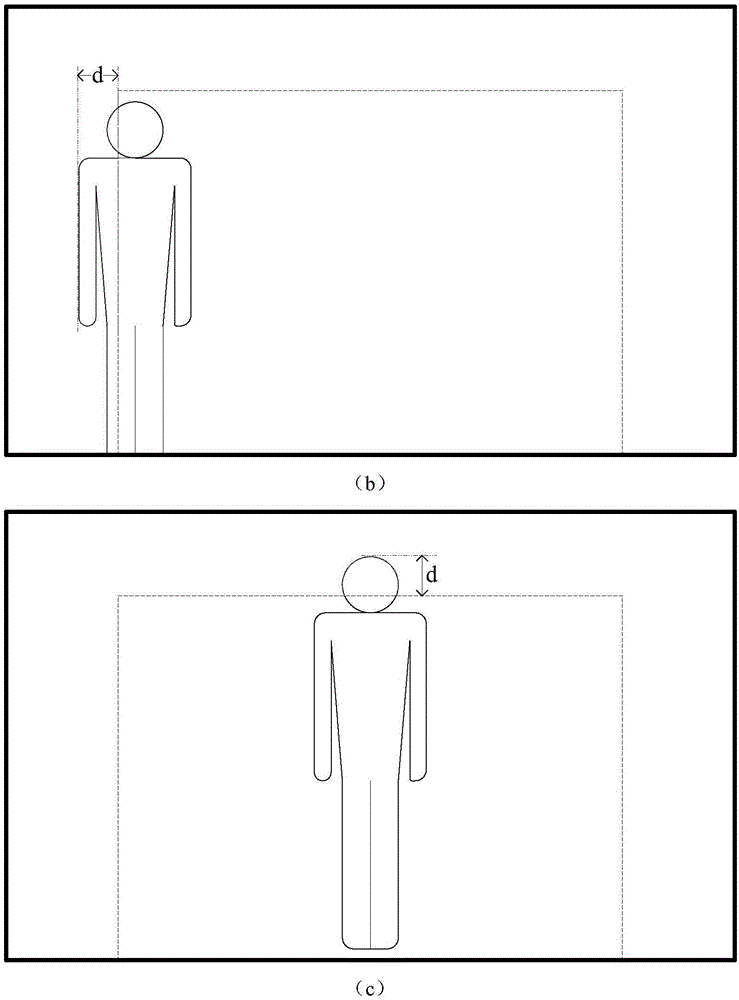
Camera shooting control method and system and interactive intelligent integrated tablet computer
InactiveCN106713749AIntegrity guaranteedAdapt to shooting needsTelevision system detailsImage analysisTablet computerMobile camera
The invention relates to a camera shooting control method and system and an interactive intelligent integrated tablet computer. The camera shooting control method comprises the steps of when an operator operates an interactive intelligent tablet computer, controlling mobile cameras to shoot an area in front of the interactive intelligent tablet computer so as to acquire an original image, wherein the mobile cameras are cameras which are arranged on the interactive intelligent tablet computer and controlled in the horizontal and vertical directions; recognizing an operator image according to image data, calculating location information of the operator image in the original image, and calculating the angle adjustment amount required by the operator image to move into a preset edge line of the image according to the location information; and generating a camera shooting angle adjustment instruction according to the angle adjustment amount, an sending the camera shooting angle adjustment instruction to the mobile cameras so as to adjust the camera shooting angle. According to the technical scheme, the camera shooting angle can be adjusted according to different scenes, the integrity of the operator image is ensured, and the camera shooting method can adapt to camera shooting requirements of difference scenes.
Owner:GUANGZHOU SHIYUAN ELECTRONICS CO LTD +1
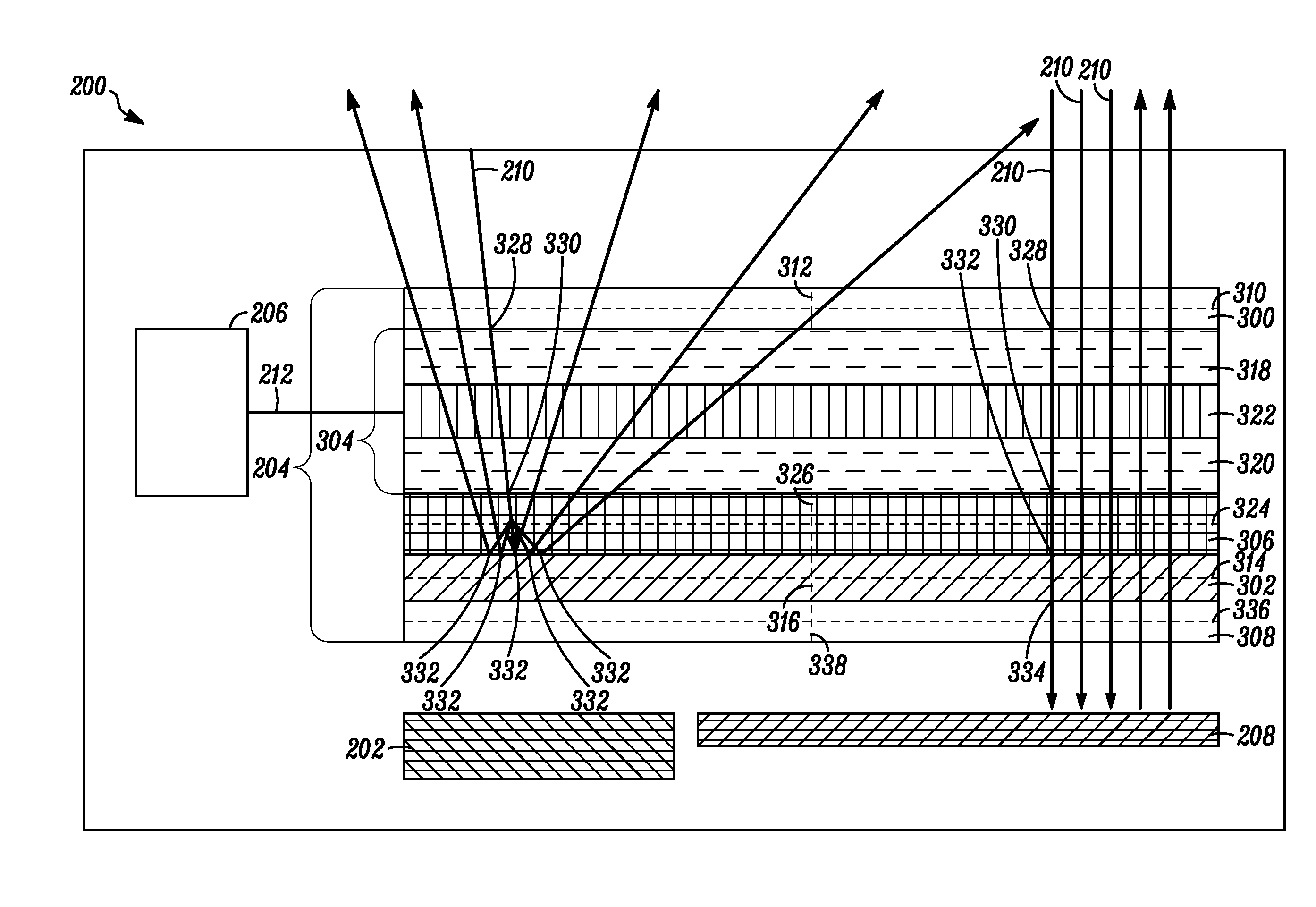
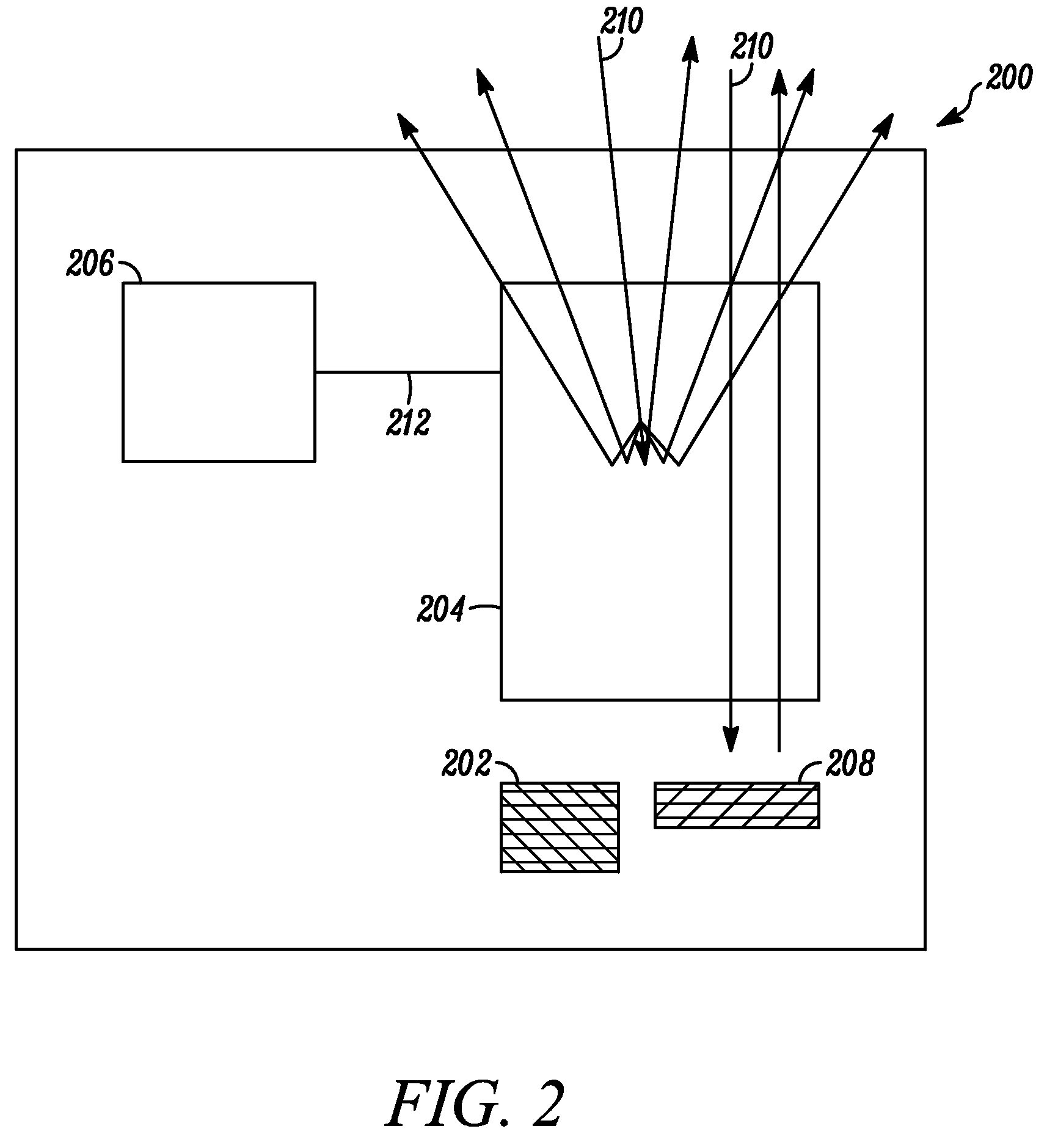
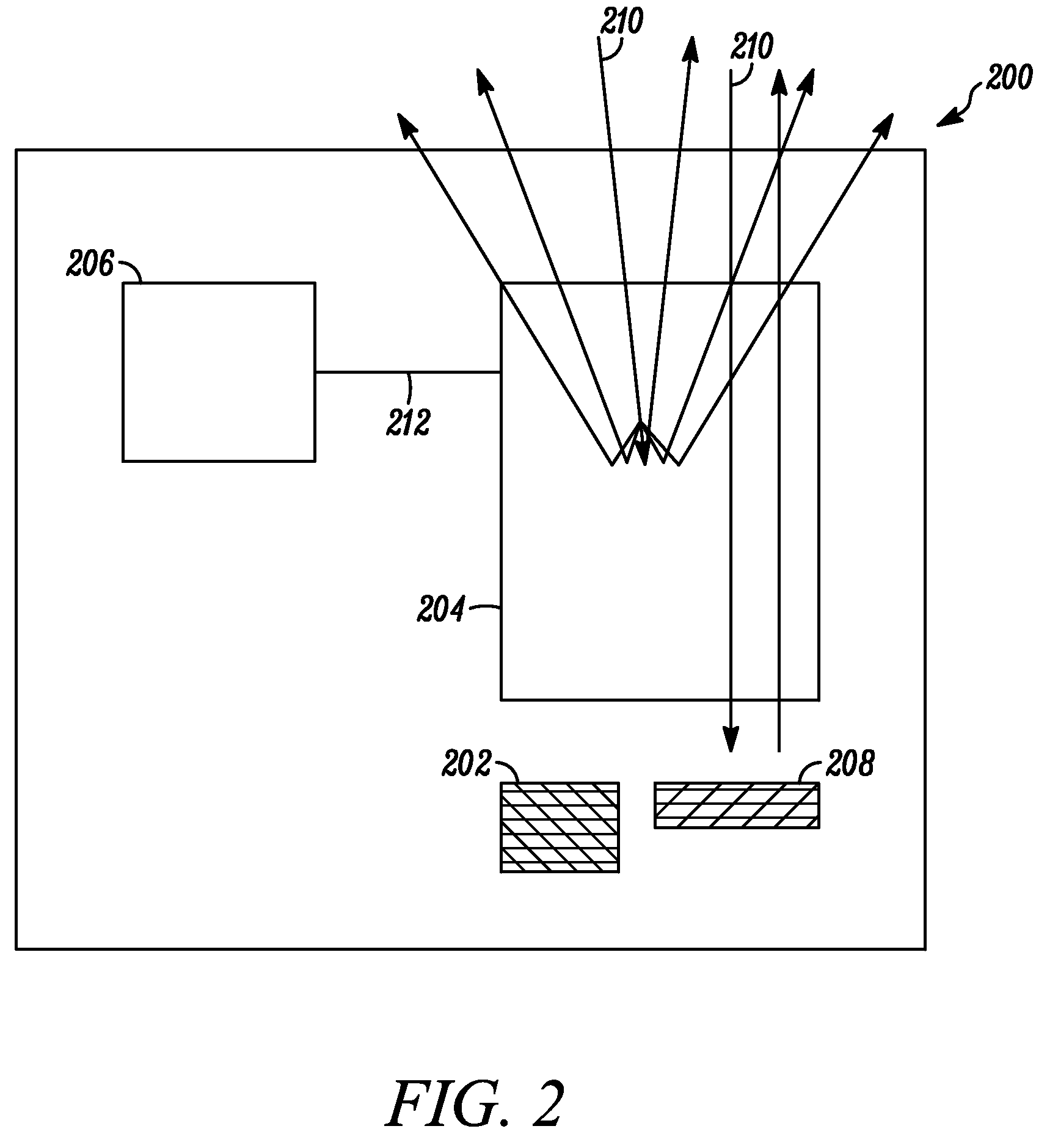
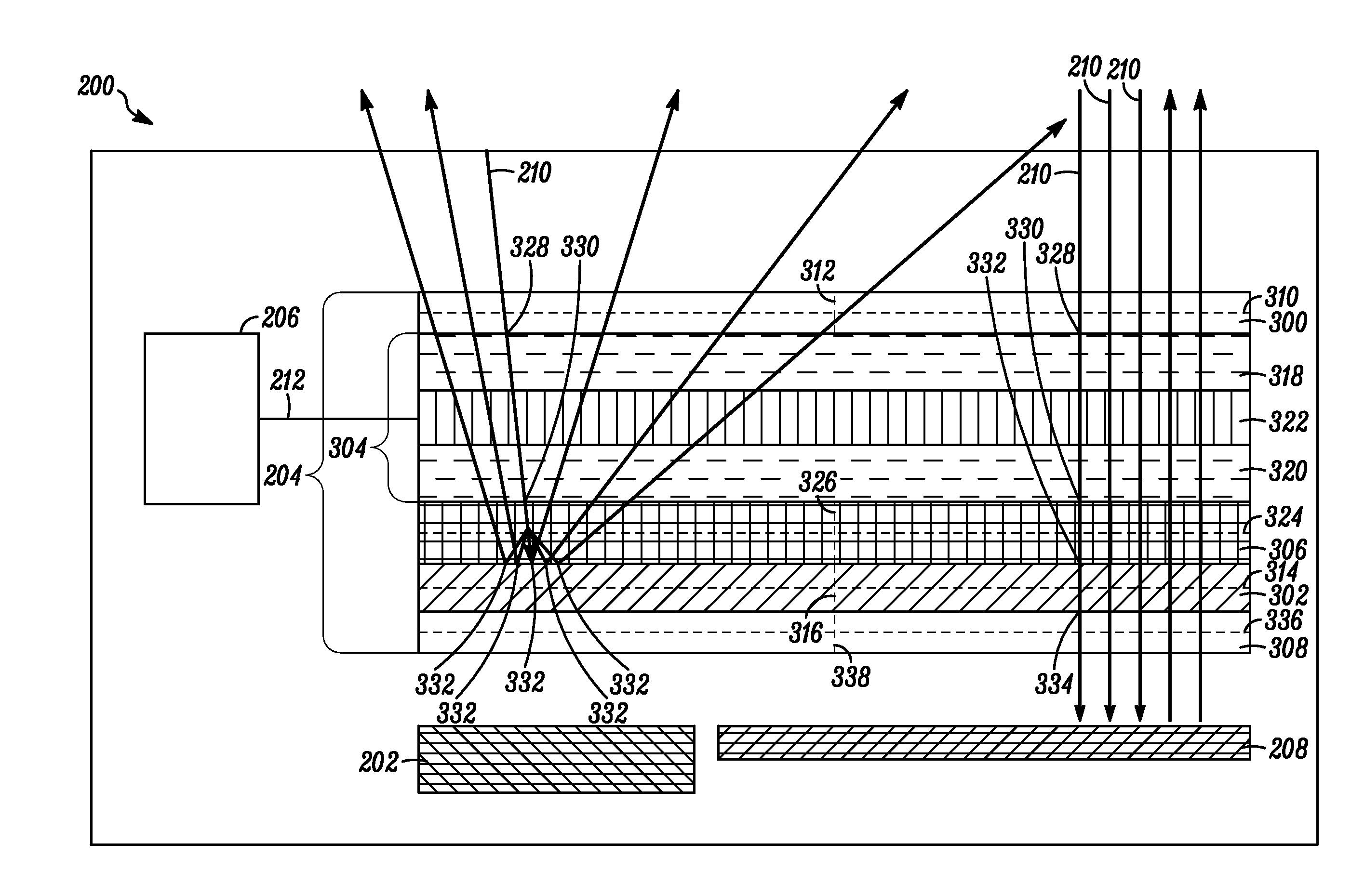
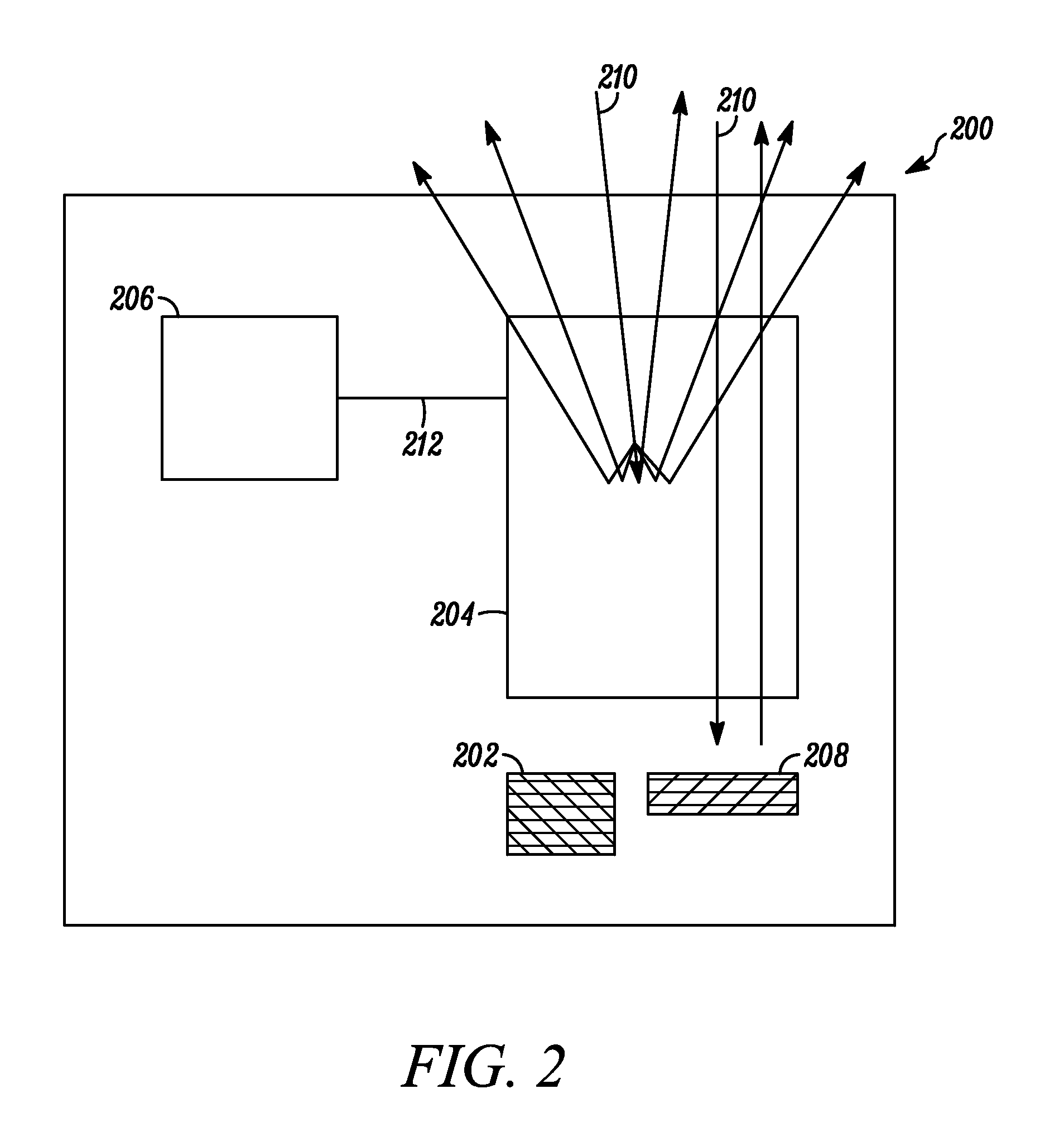
Electronic device and lc shutter with diffusive reflective polarizer
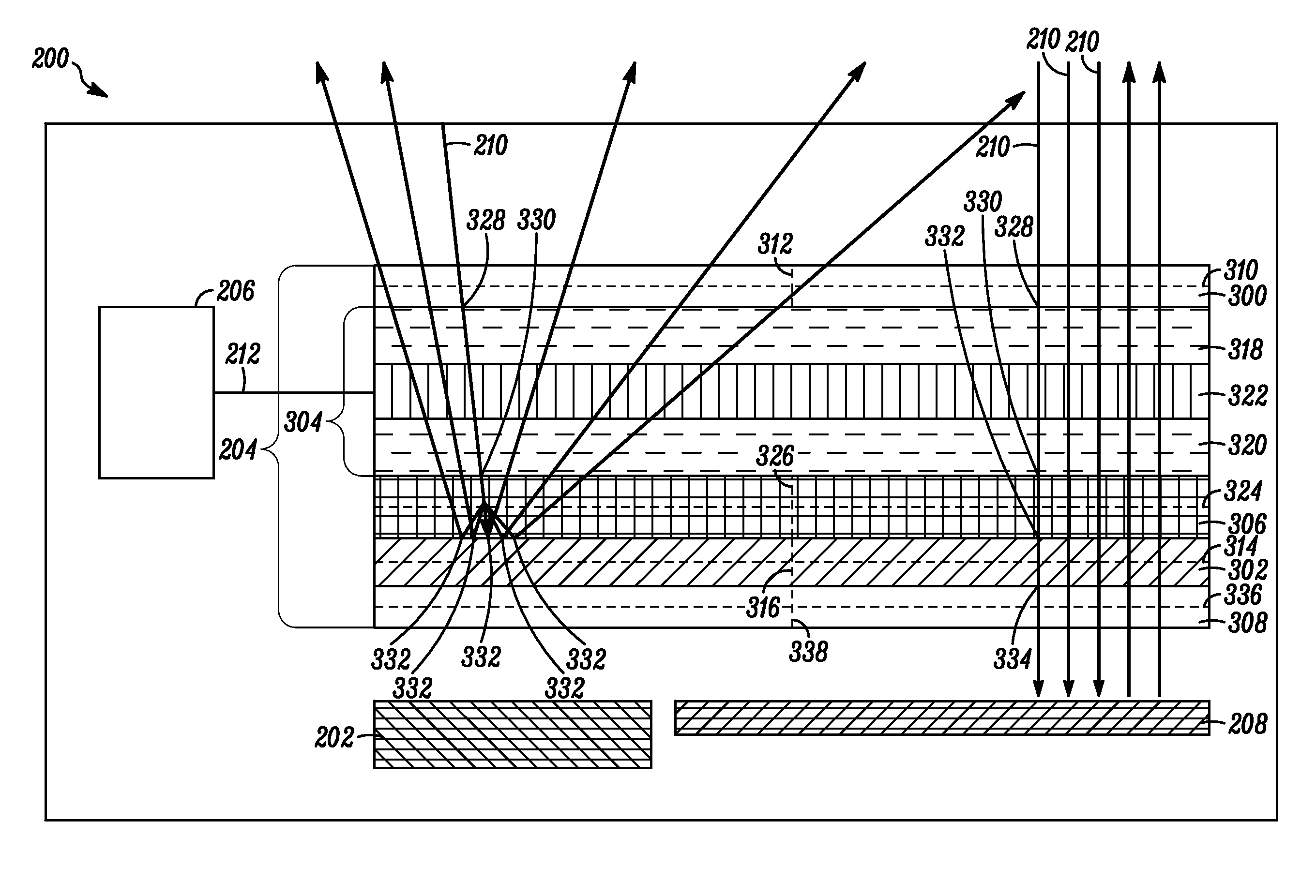
An electronic device (200) includes a display (202) and an LC shutter (204), at least a portion of which is operatively positioned over the display (202). The LC shutter (204) provides switching between a transparent state and a diffusive state with high image integrity, and high transmission in the transparent state. In one embodiment, the electronic device (200) further includes control logic (206) operatively coupled to the LC shutter (204) to provide control signals (212) to the LC shutter (204) to effect the transparent state. The LC shutter (204) includes a first dichroic polarizer (300), such as a broadband dichroic polarizer, an LC cell (304), and a diffusive reflective polarizer (307). The LC cell (304) is interposed between the first dichroic polarizer (300) and the diffusive reflective polarizer (307). Related methods are also set forth.
Owner:GOOGLE TECH HLDG LLC
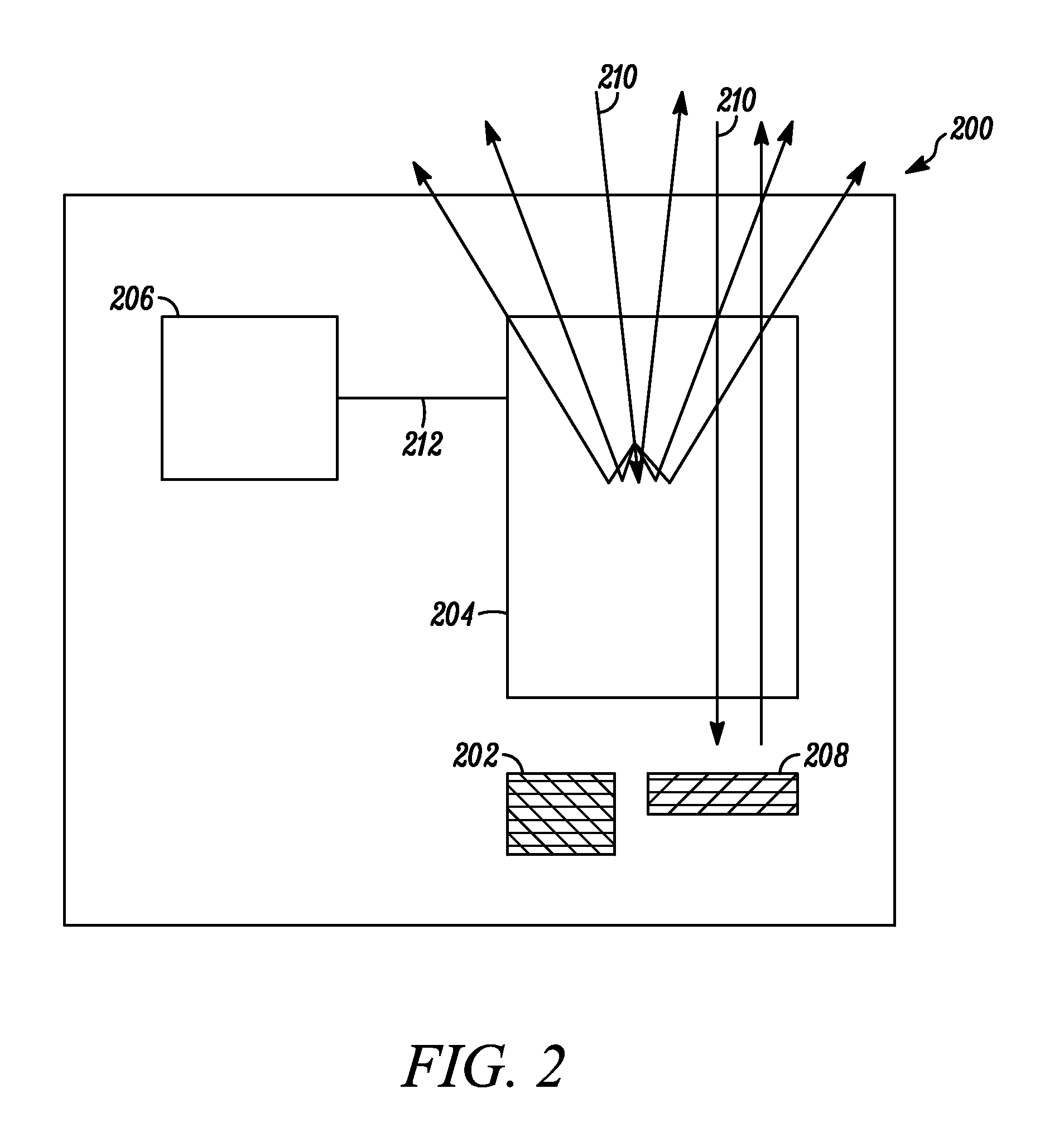
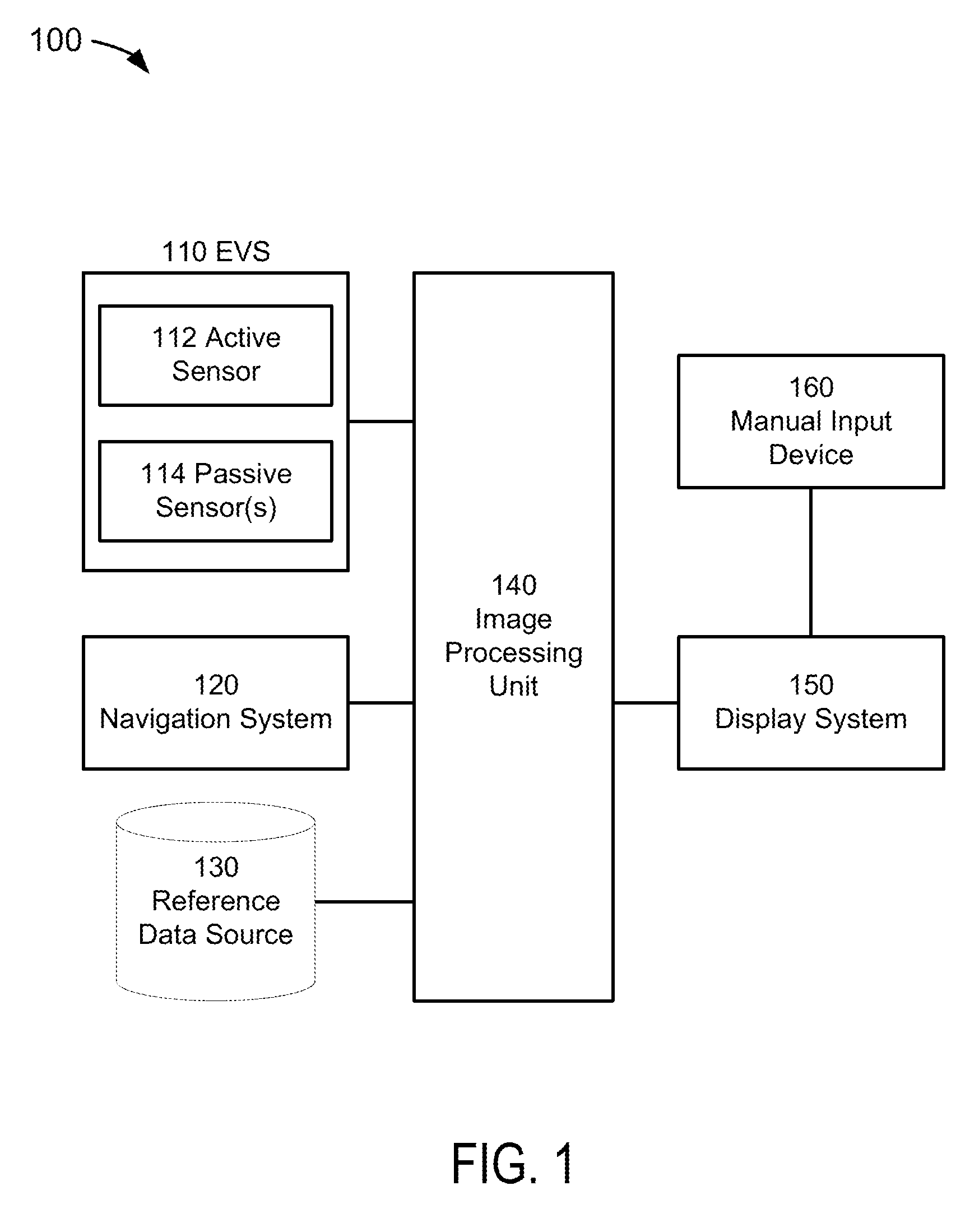
Sensor-based image(s) integrity determination system, device, and method
A system, device, and method for determining the integrity of sensor-based image(s) are disclosed. The integrity determination system may include one or more sources of passive sensor-based image data, one or more sources of an active sensor-based image data, and an image processing unit (“IPU”). The IPU may receive passive sensor-based image data; receive active sensor-based image data; and (1) determine the integrity of at least the passive sensor-based image data by comparison of the passive sensor-based image data with the active sensor-based image data, and / or (2) combine the passive sensor-based image data with the active sensor-based image data to produce third image data from which a pilot may manually determine the integrity of the first image data.
Owner:ROCKWELL COLLINS INC
Aircraft flat panel display system with graphical image integrity
ActiveUS7589735B2Enabling detectionDrawing from basic elementsDigital computer detailsGraphicsImage integrity
Owner:INNOVATIVE SOLUTIONS & SUPPORT
Image processing method and apparatus, storage medium, and mobile terminal
ActiveCN108551552AIntegrity guaranteedQuality improvementTelevision system detailsColor television detailsImaging processingImage integrity
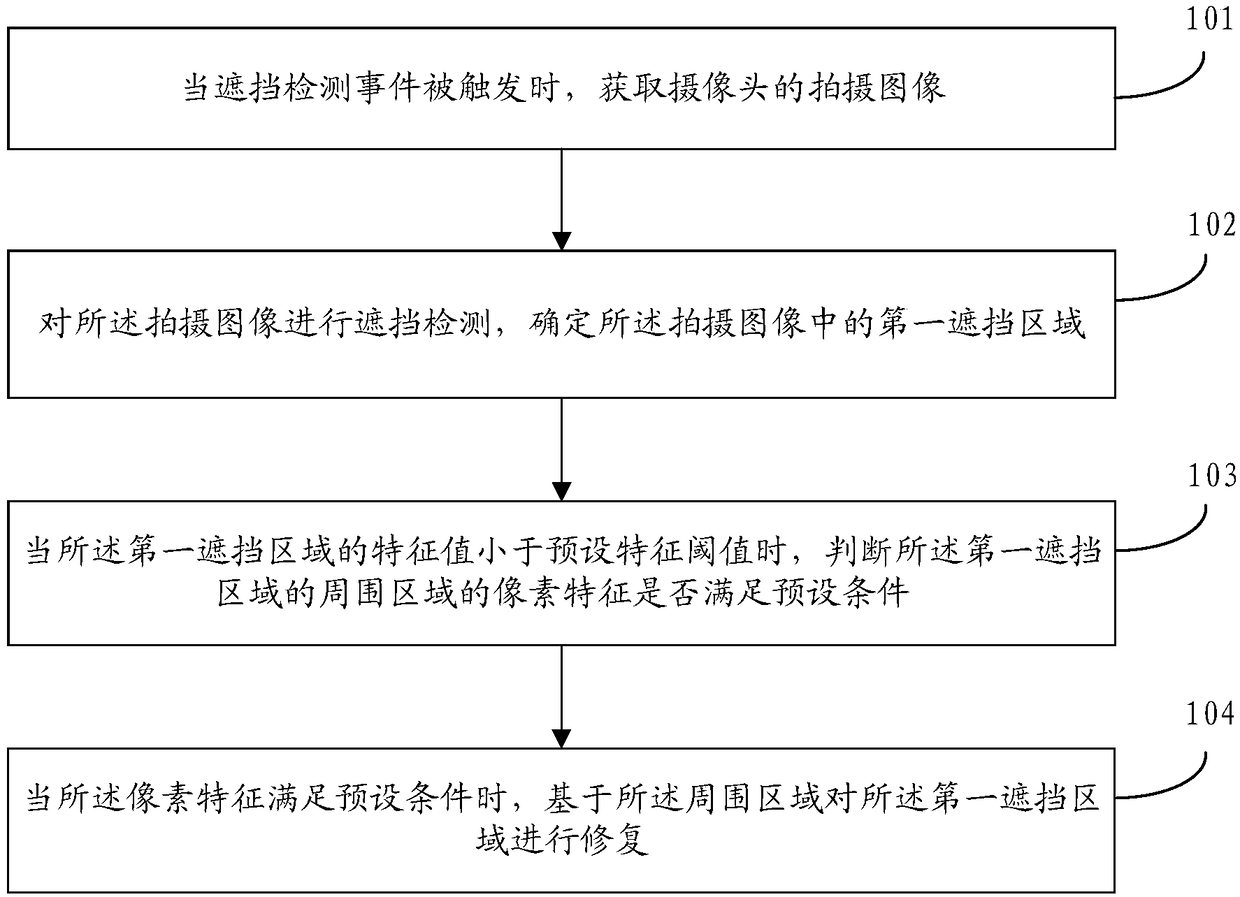
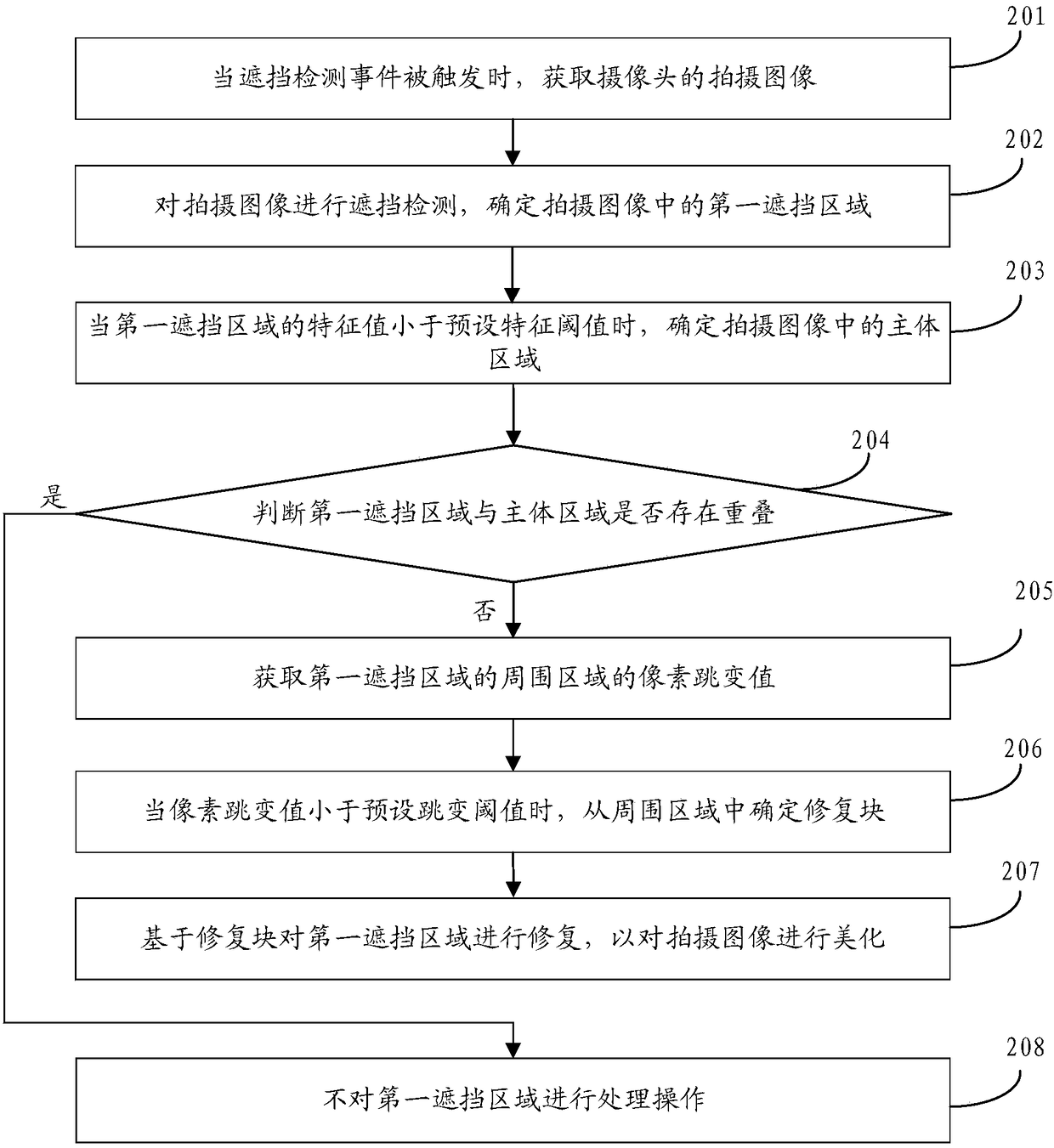
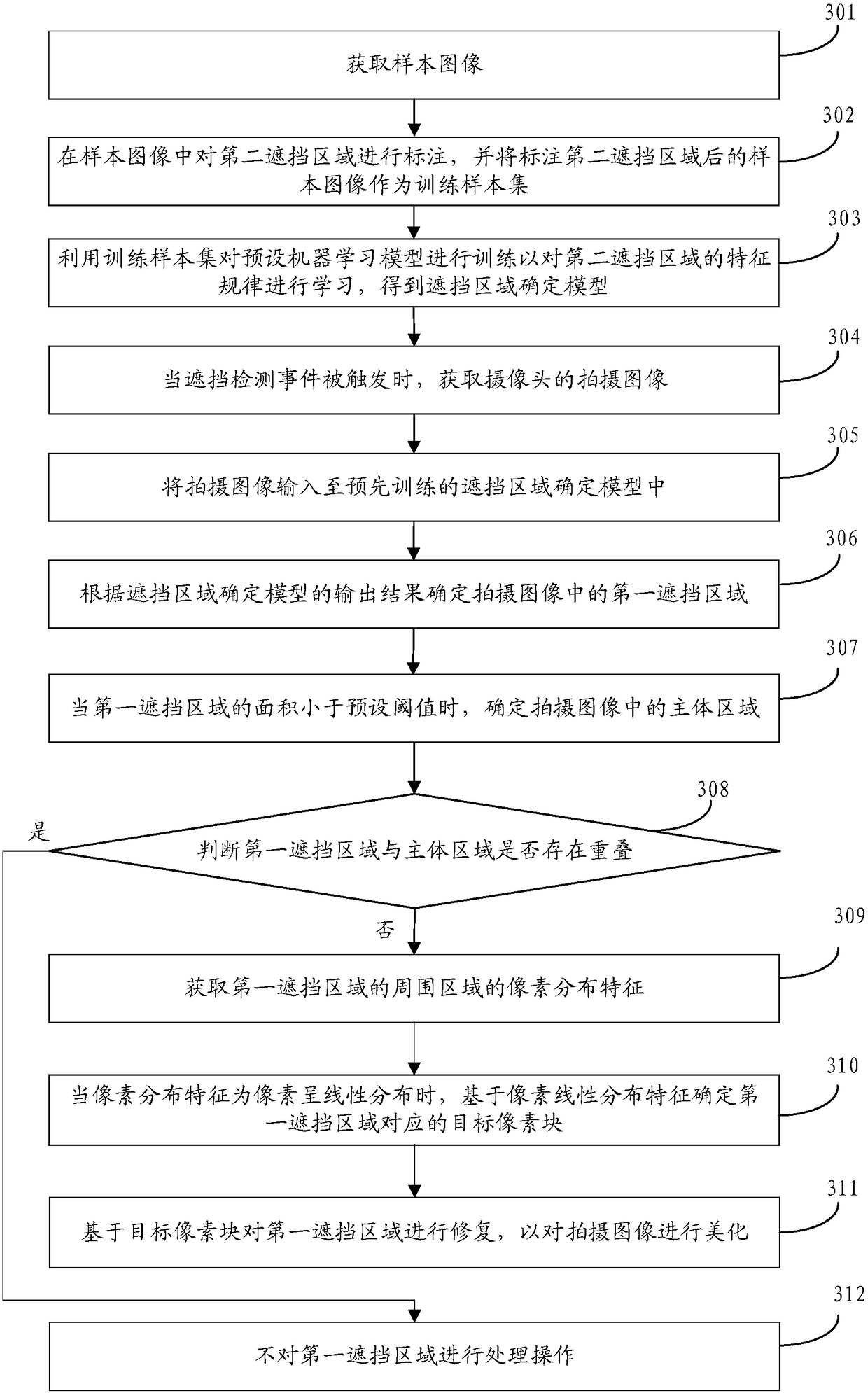
The embodiment of the invention discloses an image processing method and apparatus, a storage medium, and a mobile terminal. The method comprises the following steps: when an occlusion detection eventis triggered, obtaining a shot image of a camera; performing occlusion detection on the shot image to determine a first occlusion area in the shot image; when the feature value of the first occlusionarea is less than a preset feature threshold, judging whether a pixel feature of a surrounding area of the first occlusion area satisfies a preset condition, wherein the feature value of the first occlusion area comprises at least one of an area of the first occlusion area, a total number of pixels of the first occlusion area, and the proportion of the first occlusion area in the shot image; andwhen the pixel feature satisfies the preset condition, repairing the first occlusion area based on the surrounding area. By adoption the above technical scheme provided by the embodiment of the invention, on the premise of ensuring the integrity of the shot image, the shot image can not only be closer to the image shot when the camera is not shielded, and the quality of the shot image can also beeffectively improved.
Owner:GUANGDONG OPPO MOBILE TELECOMM CORP LTD
Priority constraint colorful image sparse expression restoration method
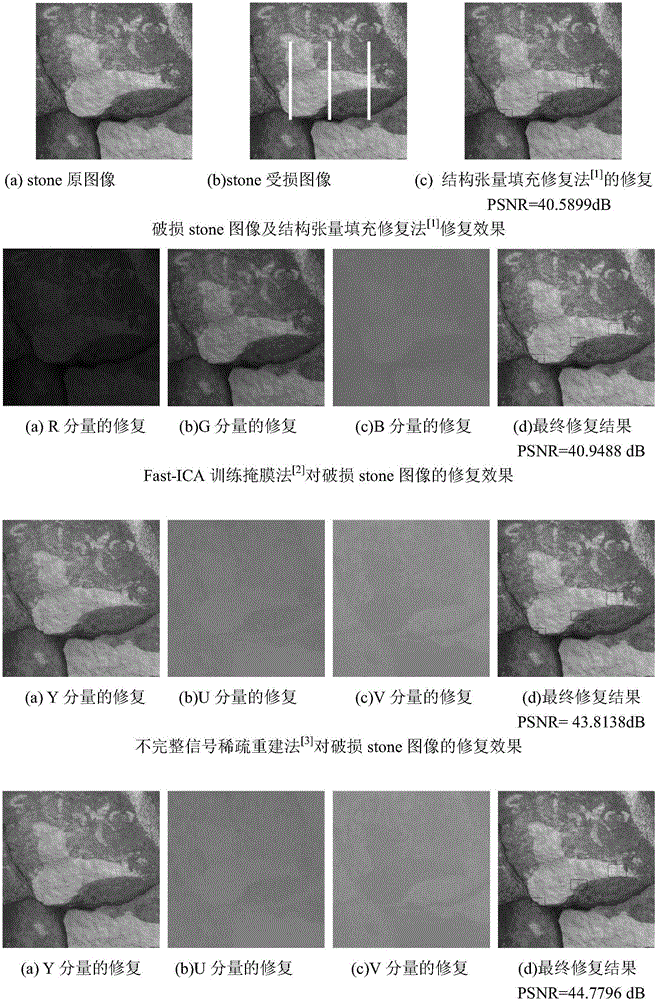
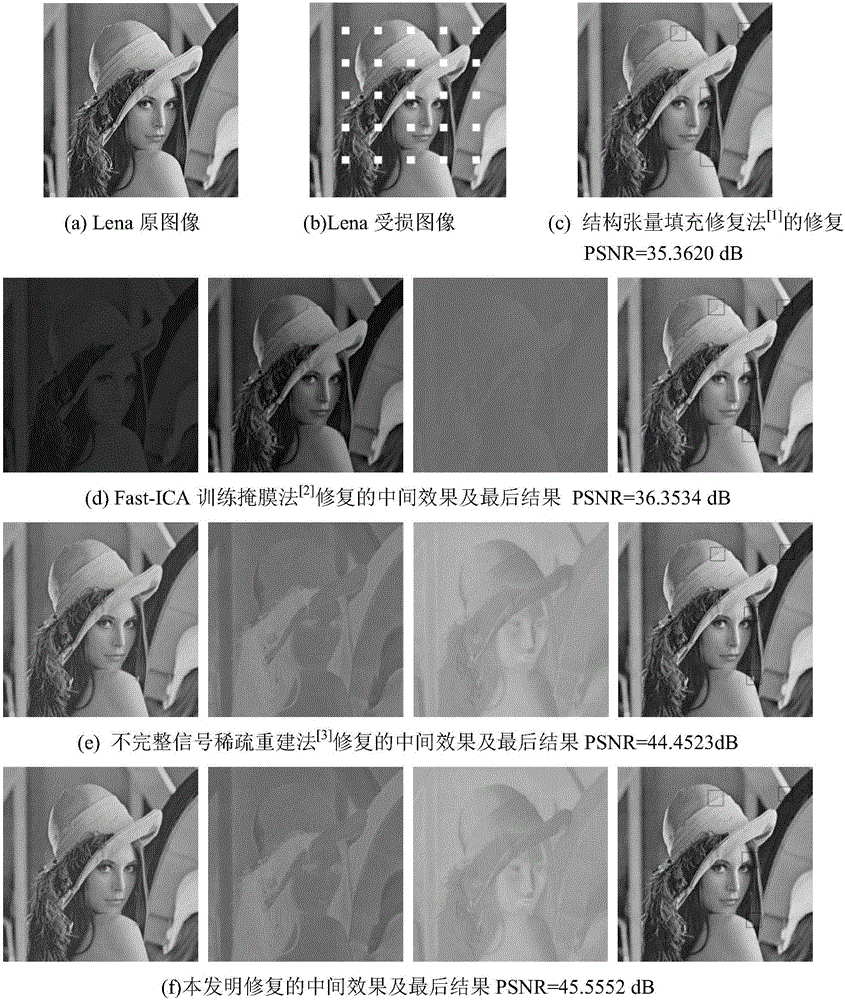
The invention discloses a priority constraint colorful image sparse expression restoration method. The method comprises steps that step 1, a colorful image is mapped from an RGB color space to a YUV color space, and three-layer component restoration is respectively carried out; step 2, a Fast-ICA algorithm is utilized for training to acquire a complete dictionary; step 3, priority of all edge points of a broken area of a to-be-restored image is calculated, and the restoration priority sequence is determined; step 4, in combination with an SL0 algorithm, sparse reconstruction of the broken block is carried out; and step 5, edge update is carried out, and the step 3 and the step 4 are repeated till image restoration is accomplished. The method is advantaged in that image restoration quality is high, the edge structure after image restoration has relatively good continuity, and image integrity is further kept.
Owner:HANGZHOU DIANZI UNIV
Image scaling method for keeping visual quality of sensitive target
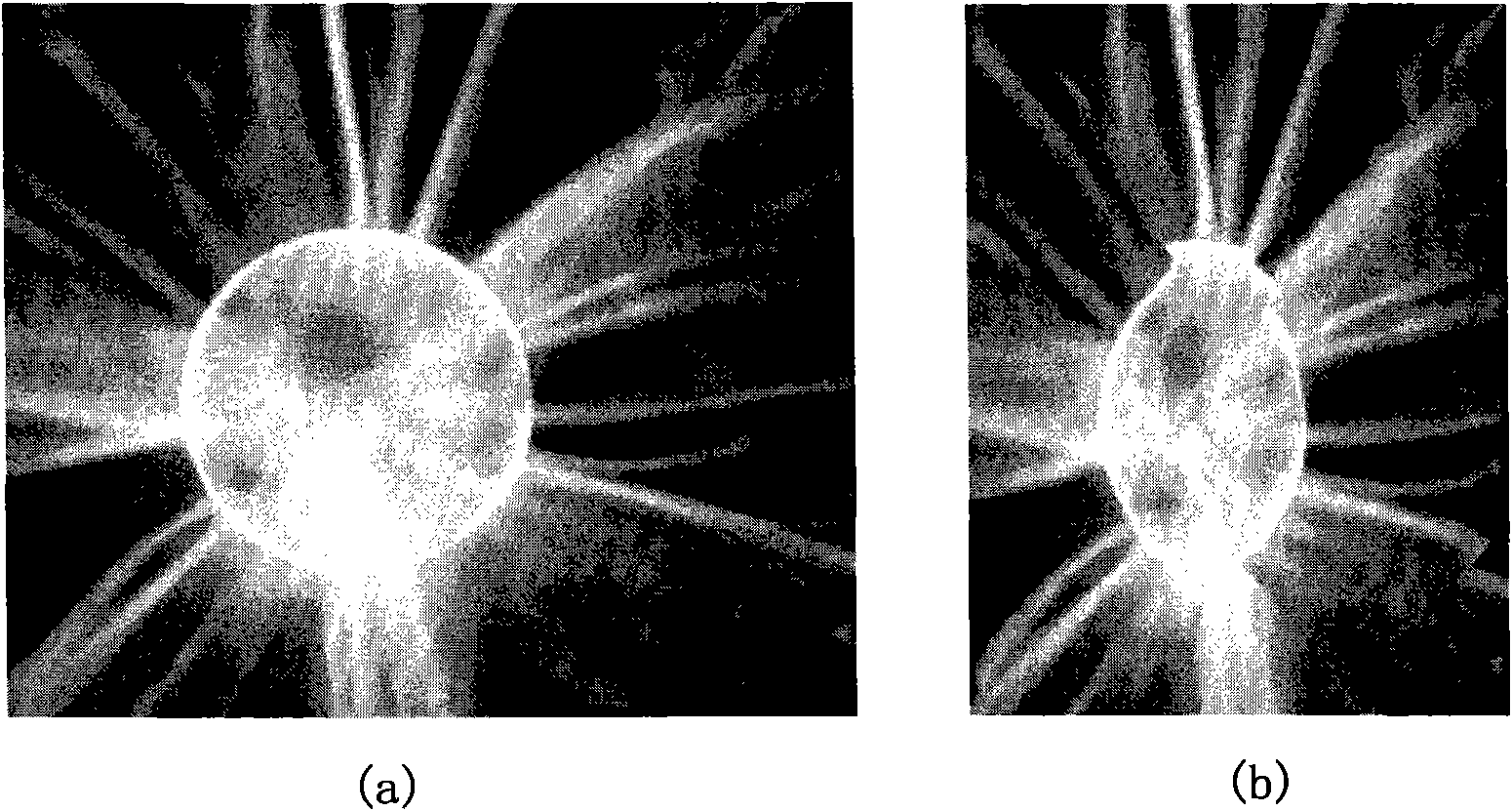
InactiveCN101872468AReduce distortionImprove scalabilityGeometric image transformationPictoral communicationImage integrityImage scale
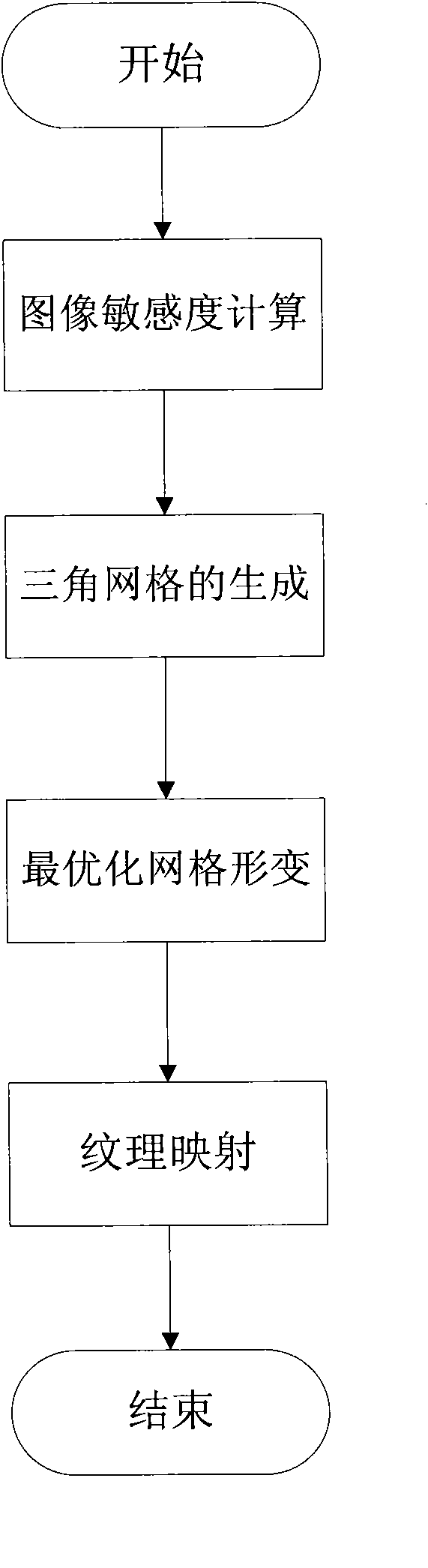
The invention discloses an image scaling method for keeping visual quality of a sensitive target, which comprises the following steps of: calculating the sensitivity of a pixel point in an image by using four characteristics comprising color, gradient, brightness and center distance of the pixel point in the image to obtain an image sensitivity graph in accordance with the primary image, then generating a triangle mesh covering the primary image by adopting Delaunay triangulation according to the image sensitivity graph, establishing a visual loss function of the image on the basis, obtaining a target mesh with the same size as a target image by solving the optimization problem of the minimum value of the visual loss function under integrity constraint of the image, and finally generating a final result image in a texture mapping mode.
Owner:BEIHANG UNIV
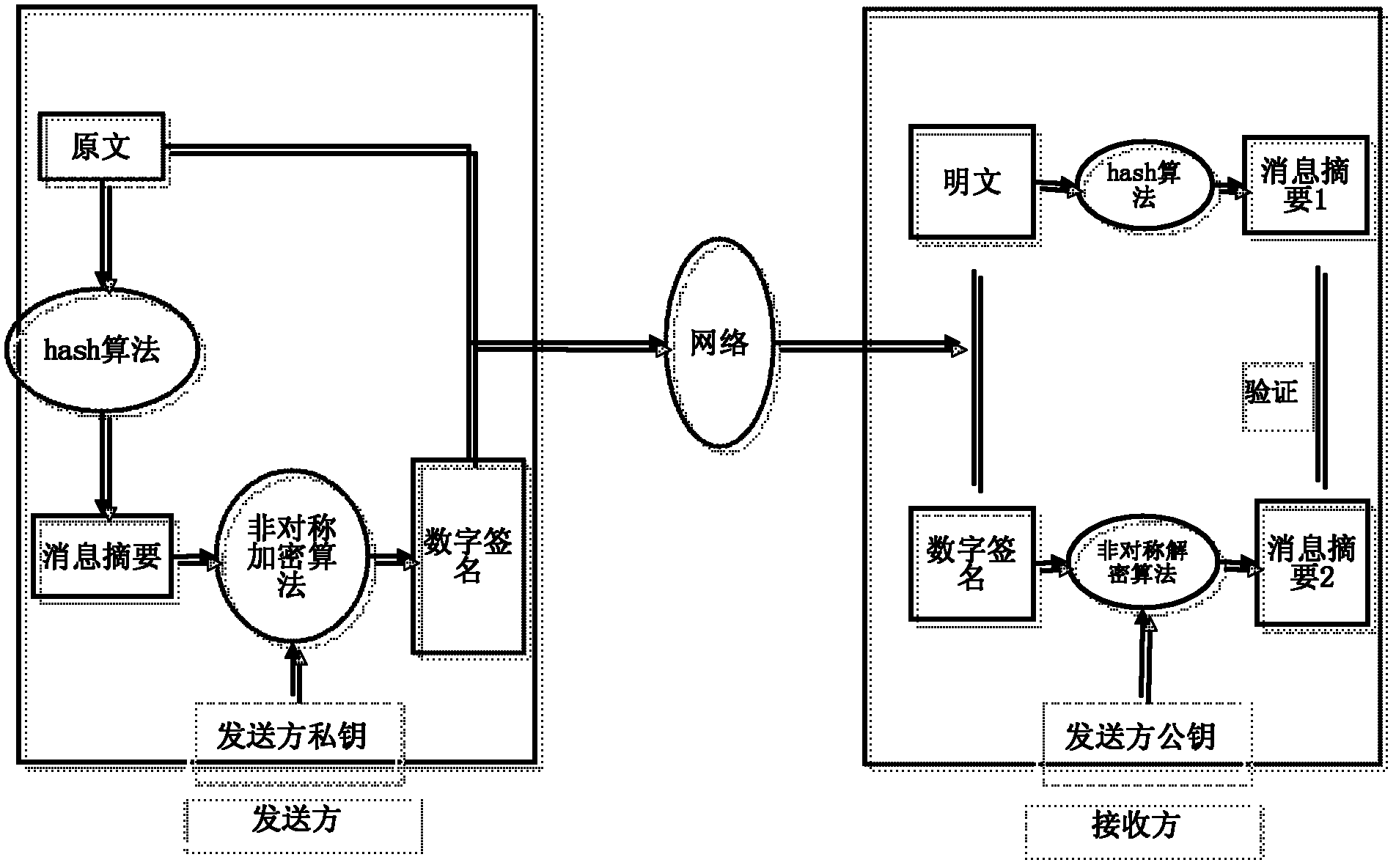
Safe and active image tampering detection method and device
ActiveCN104935783AIntegrity guaranteedAvoid False Detection ResultsTransmissionPictoral communicationPattern recognitionImage integrity
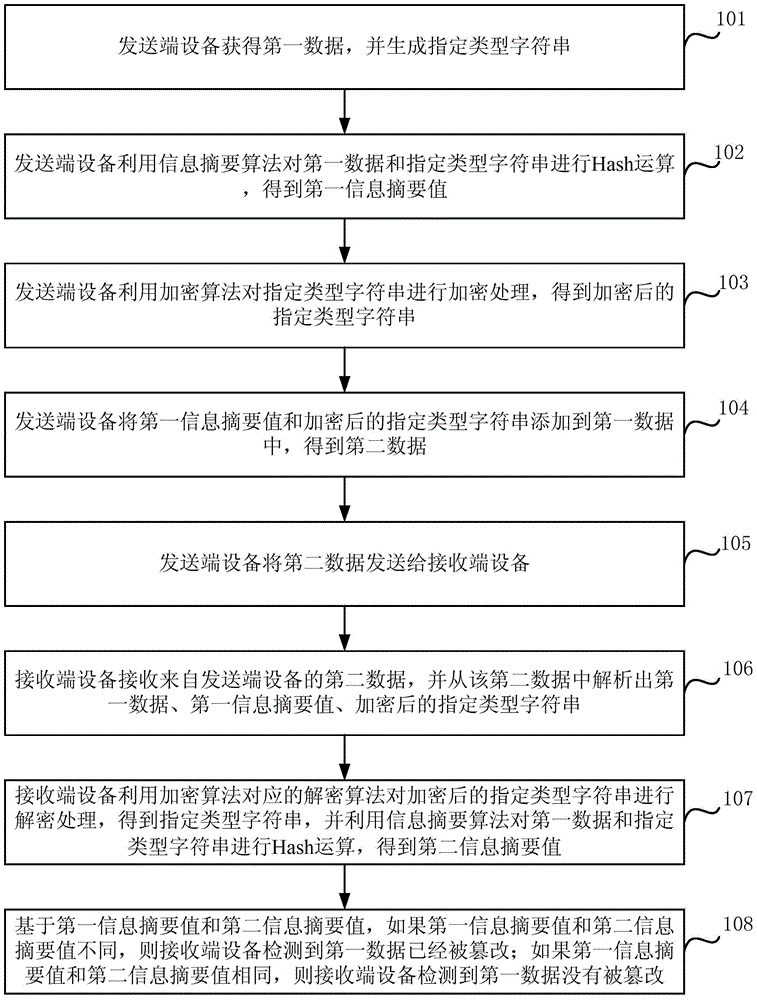
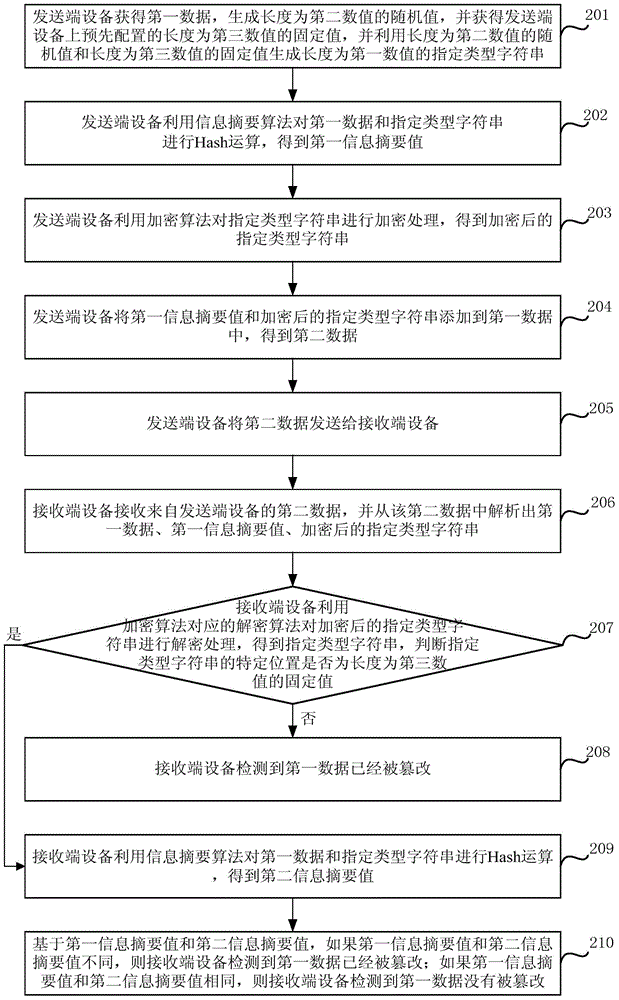
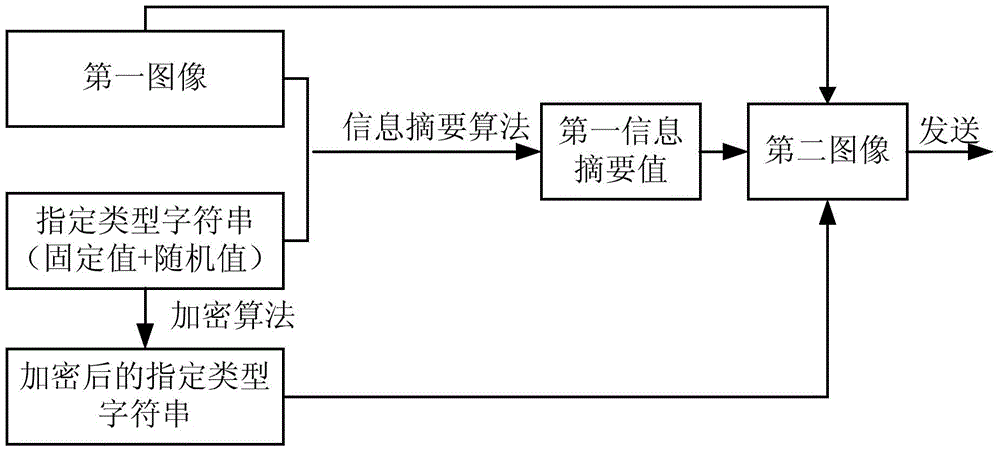
The embodiment of the present invention discloses a safe and active image tampering detection method and device. The method comprises: sending end equipment obtaining a first image, generating a random value of which the length is a second numerical value, obtaining a pre-configured fixed value of which the length is a third numerical value, and using the random value and the fixed value for generating a specified type character string of which the length is a first numerical value; performing Hash operation on the first image and the specified type character string by using an information digest algorithm to obtain a first information digest value; performing encryption processing on the specified type character string by using an encryption algorithm to obtain an encrypted specified type character string; adding the first information digest value and the encrypted specified type character string to the first image for obtaining a second image; sending the second image to receiving end equipment; and the receiving end equipment using the first information digest value and the encrypted specified type character string for detecting whether the first image is tampered or not. In the embodiment of the present invention, the image integrity and the image authenticity in the process of obtaining evidence for the images are ensured.
Owner:BEIJING UNIV OF POSTS & TELECOMM
Labeling system and methodology
ActiveUS7113656B2High levelEasy to disassembleOther printing matterCharacter and pattern recognitionImage integrityQuality control
A digitization process and system which involves the use of a novel label, labeling system and labeling methodology. According to the teachings of the present invention, the label is comprised of two parts one of which is transparent and the other of which is opaque. Bates numbers or other identifiers according to some sequential numbering or ordering scheme are placed on the opaque portion of the label. The labels are placed on document edges prior to scanning and removed after scanning. Following scanning, an interactive quality control process is carried out in order to ensure image integrity against the original document sequence and integrity. After the sequence and integrity of the images is verified, the images are cropped so as to remove the ordering information and then the document may be stored possibly for later retrieval via its unique identifier. In this way, document integrity can be assured and stored document images reflect the actual document appearance rather than as modified by a label or stamped identifier. Labels may easily be removed from the original hard copy documents so that these documents may also be returned to their original form.
Owner:JIANG HUBIN
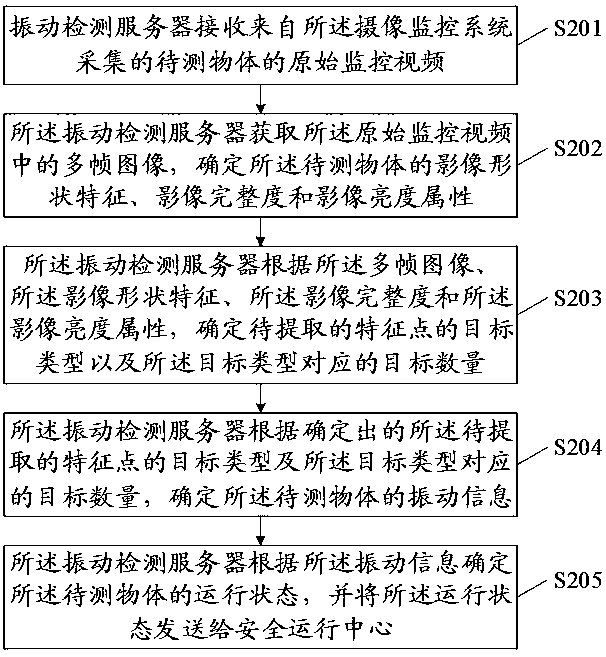
Intelligent vibration detection method and related products
ActiveCN110245650ARealize deep integrationImprove intelligenceCharacter and pattern recognitionClosed circuit television systemsPattern recognitionMultiple frame
The embodiment of the invention discloses an intelligent vibration detection method and a related product. The intelligent vibration detection method is applied to a vibration detection server. The vibration detection server is in communication connection with a camera monitoring system. The intelligent vibration detection method comprises the following steps: receiving an original monitoring video of a to-be-detected object collected by the camera monitoring system, obtaining a plurality of frames of images in the original monitoring video, determining image shape features, image integrity and image brightness attributes of the to-be-measured object; and then according to the multi-frame image, the image shape features, the image integrity and the image brightness attribute, determining the target type of the to-be-extracted feature point and the target number corresponding to the target type, further determining the vibration information of the to-be-detected object, finally determining the operation state of the to-be-detected object, and sending the operation state to a safe operation center. Therefore, the efficiency, accuracy and convenience of intelligent vibration detection can be improved.
Owner:SHENZHEN GUANGNING IND CO LTD +1
System and method of optical axis alignment monitor and feedback control for a spectrometer
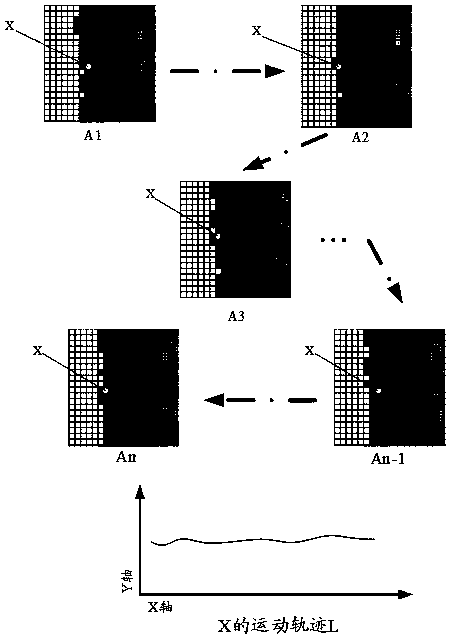
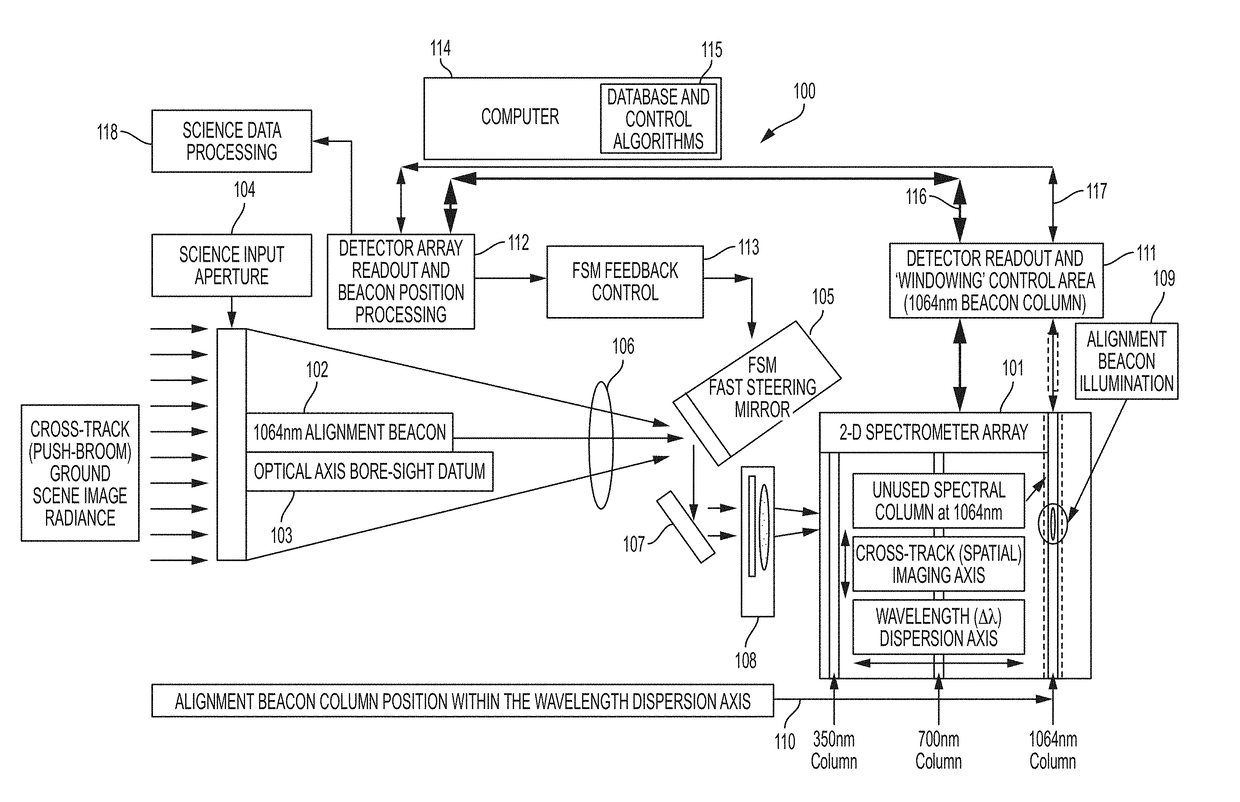
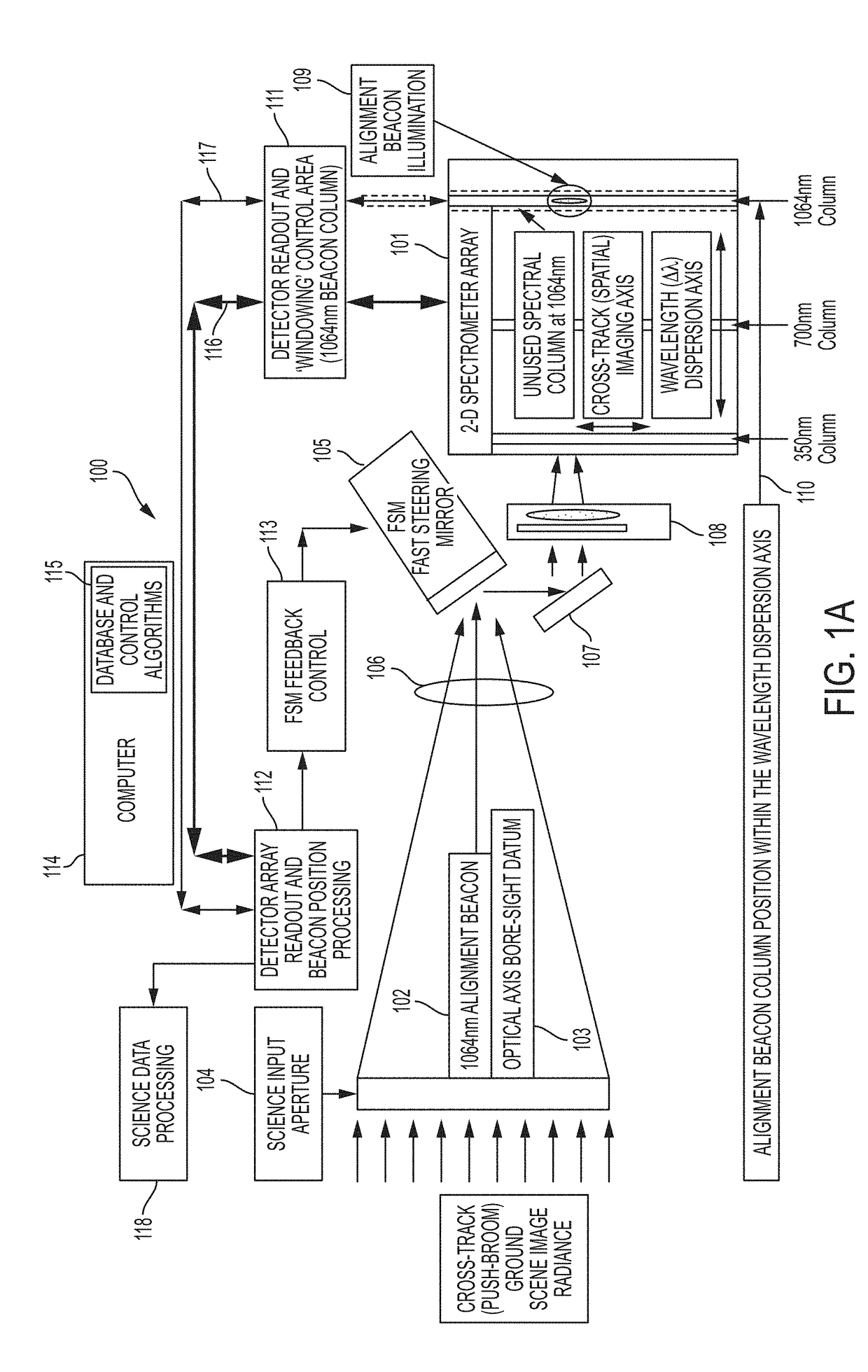
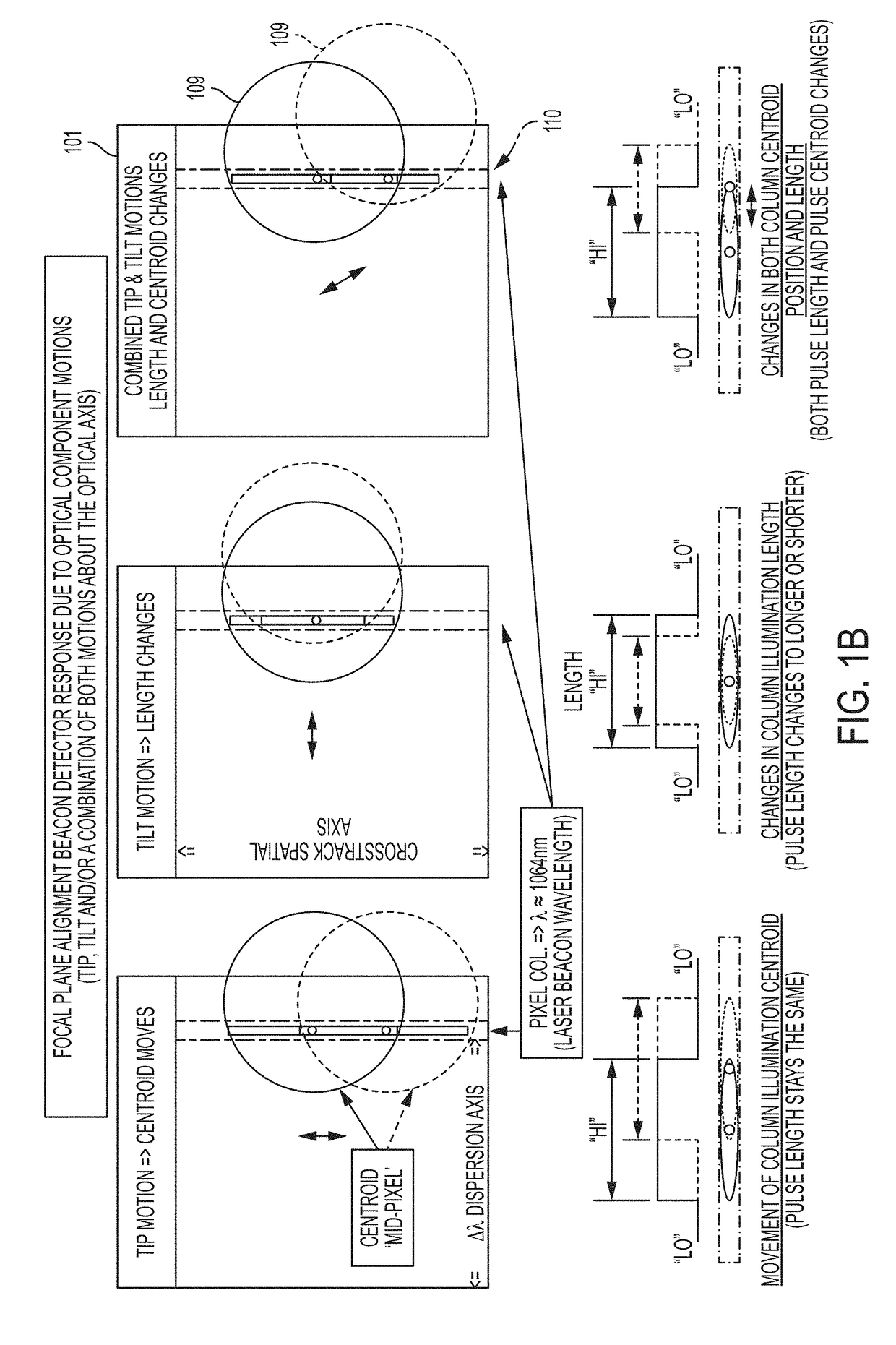
InactiveUS10113908B1Maximizing science image qualityDegraded image integrityRadiation pyrometrySpectrum investigationImage integrityImaging quality
The present invention relates to an apparatus and method of a real-time, monitoring and control feedback system for a 2-D spectrometer application, to correct for active optical axis pointing misalignments or jitter (i.e., tip, tilt), that result in degraded scientific image integrity, unwanted spatial crosstalk and image blurring artifacts which severely limit the applications for high resolution spectrometer image data. The present invention provides a unique system architecture which ensures the most direct optical axis motion detection and control capability that will enable sub-pixel image motion monitoring and boresight control stability, thus, maximizing the science image quality.
Owner:NASA
Method and system for information handling system custom image manufacture
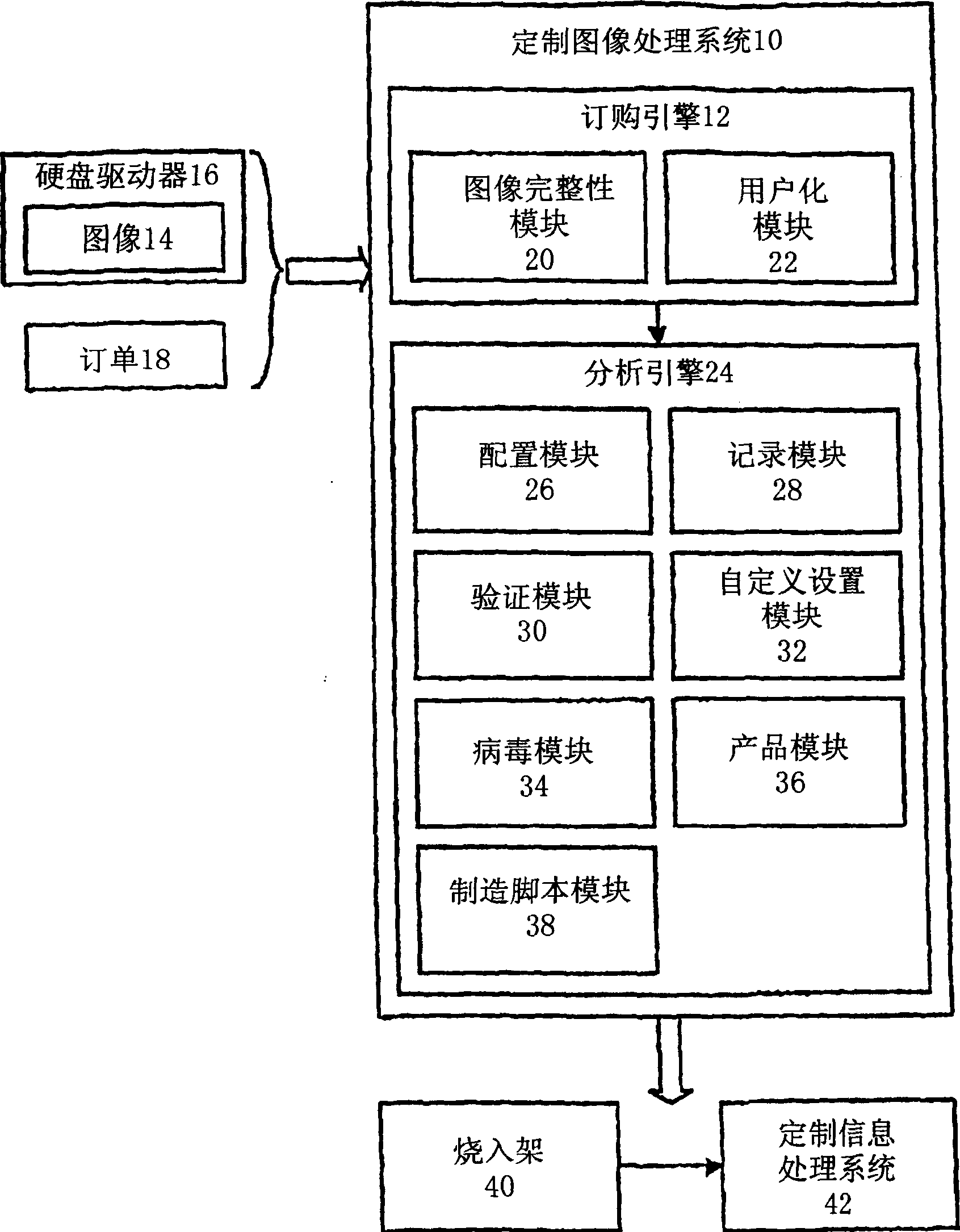
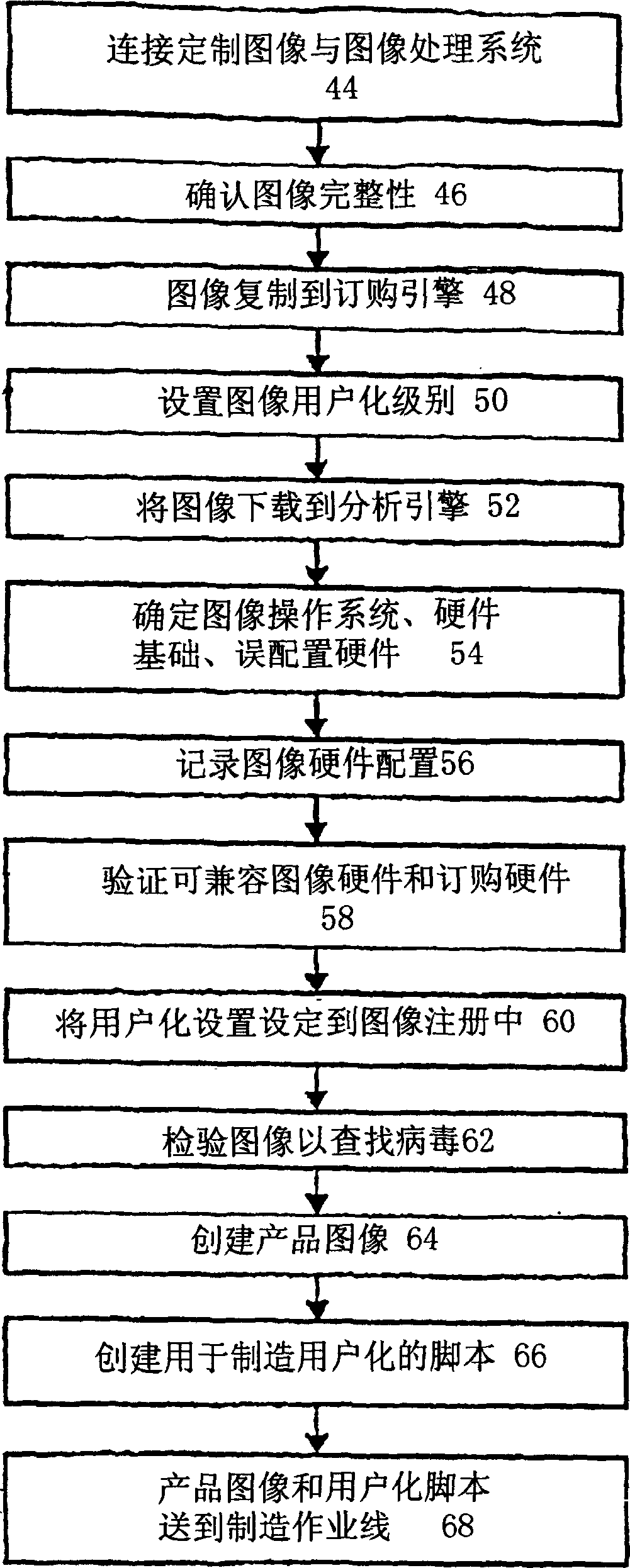
The present invention relates to a customized image processing system of product images, which is used in a treatment system that receives customized image order, automatically deals with the customized image order and produces manufacture information. An order engine (12) is used for receiving images (14) and orders. For example, with the connection with a hard disc drive (16), the order (18) designates the hardware configuration information of an information processing system that a customer needs and orders. The image integrity module (20) of the order engine (12) interacts with the hard disc drive (16), so as to detect whether the integrity of the images is destroyed in the transmission process and has a lost sector. The customization module (22) of the order engine (12) receives the customization information from the order (18) or a user interface so as to set the level of the customization information that can comprises the change of each image so as to build a unique SIDs or computer name.
Owner:DELL PROD LP
Fingerprint and palm print collection system
InactiveCN103198308ARealize acquisitionIntegrity guaranteedCharacter and pattern recognitionPalm printCollection system
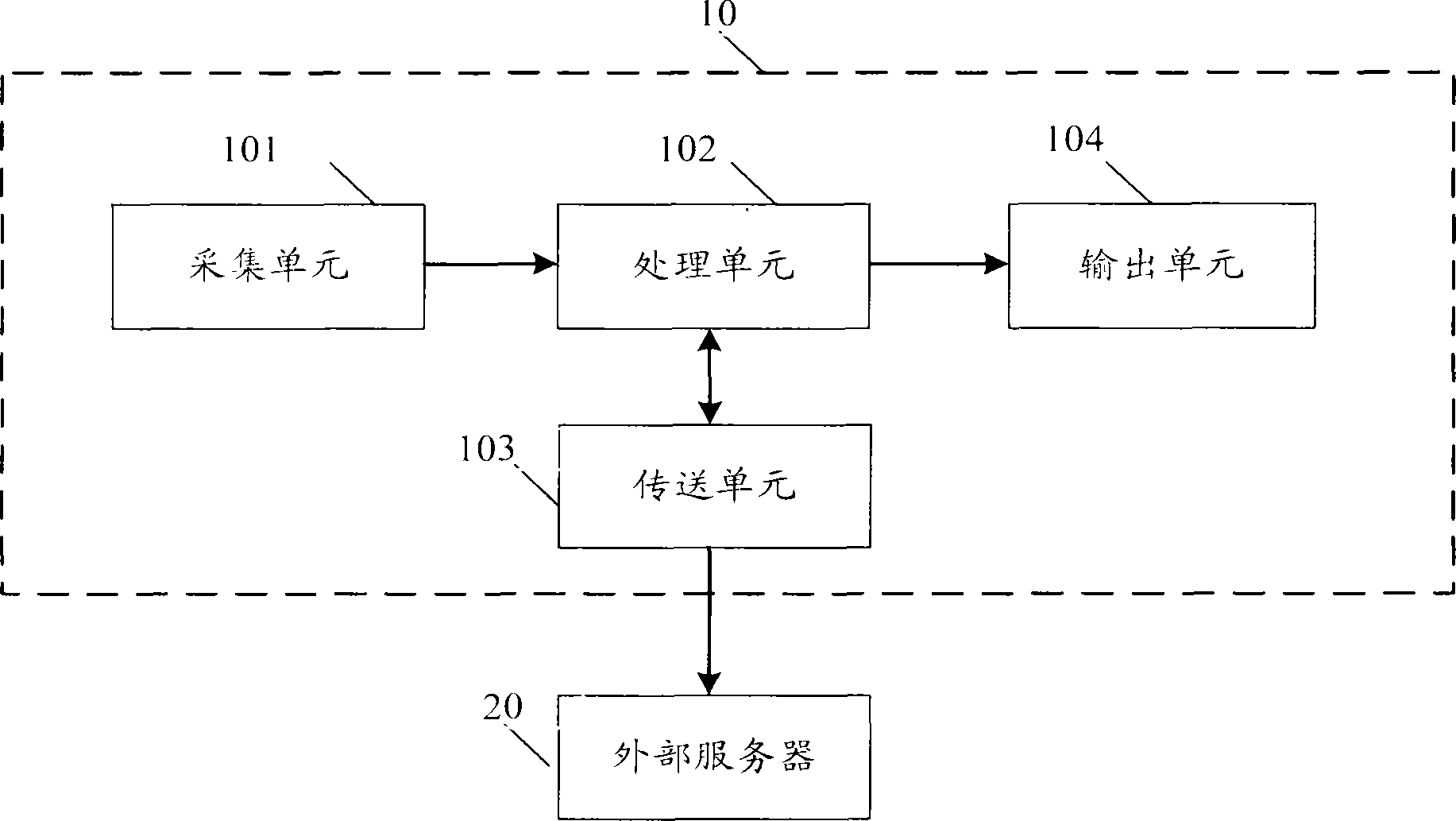
The invention discloses a fingerprint and palm print collection system which is connected with an external database and comprises a collecting unit, a processing unit, a transmitting unit and an output unit, wherein the collecting unit is coupled with the processing unit; the processing unit is coupled with the collecting unit, the transmitting unit and the output unit; the transmitting unit is coupled with the processing unit and the external database; and the output unit is coupled with the processing unit. The fingerprint and palm print collection system achieves the purposes of ensuring collection of complete palm print images without splicing and collection of clear fingerprints while ensuring the integrity of the palm print images.
Owner:BEIJING EASTERN GOLDEN FINGER TECH
Labeling system and methodology
InactiveUS20070076985A1High levelEasy to removeCharacter and pattern recognitionFiling appliancesComputer graphics (images)Image integrity
A digitization process and system which involves the use of a novel label, labeling system and labeling methodology. According to the teachings of the present invention, the label is comprised of two parts one of which is transparent and the other of which is opaque. Bates numbers or other identifiers according to some sequential numbering or ordering scheme are placed on the opaque portion of the label. The labels are placed on document edges prior to scanning and removed after scanning. Following scanning, an interactive quality control process is carried out in order to ensure image integrity against the original document sequence and integrity. After the sequence and integrity of the images is verified, the images are cropped so as to remove the ordering information and then the document may be stored possibly for later retrieval via its unique identifier. In this way, document integrity can be assured and stored document images reflect the actual document appearance rather than as modified by a label or stamped identifier. Labels may easily be removed from the original hard copy documents so that these documents may also be returned to their original form.
Owner:JIANG HUBIN
Method for ensuring image integrity by using file characteristics
InactiveCN101727572AFinanceCharacter and pattern recognitionEmbedded technologyTagged Image File Format
The invention relates to a method for verifying the image integrity in an archive by using file characteristics. The embodiment of the invention provides a method for verifying the integrity of a stored file image by confirming the file characteristics, and the file characteristics can also be embedded in an image file. Before an access image file is allowable to be applied, characteristic data from image analysis can be compared with one or both of stored characteristic information and embedded characteristic data. Optionally, the embedded data can be encrypted. In an example embodiment, the data can comprise an optical character identification result of document contents, the length of the data for describing the image and the percentage or check the sum of pixels of specific color in the image. The example embedded technology can comprise technologies for using tagged image file format (TIFF) preludes, steganographic watermarking or image artifacts.
Owner:BANK OF AMERICA CORP
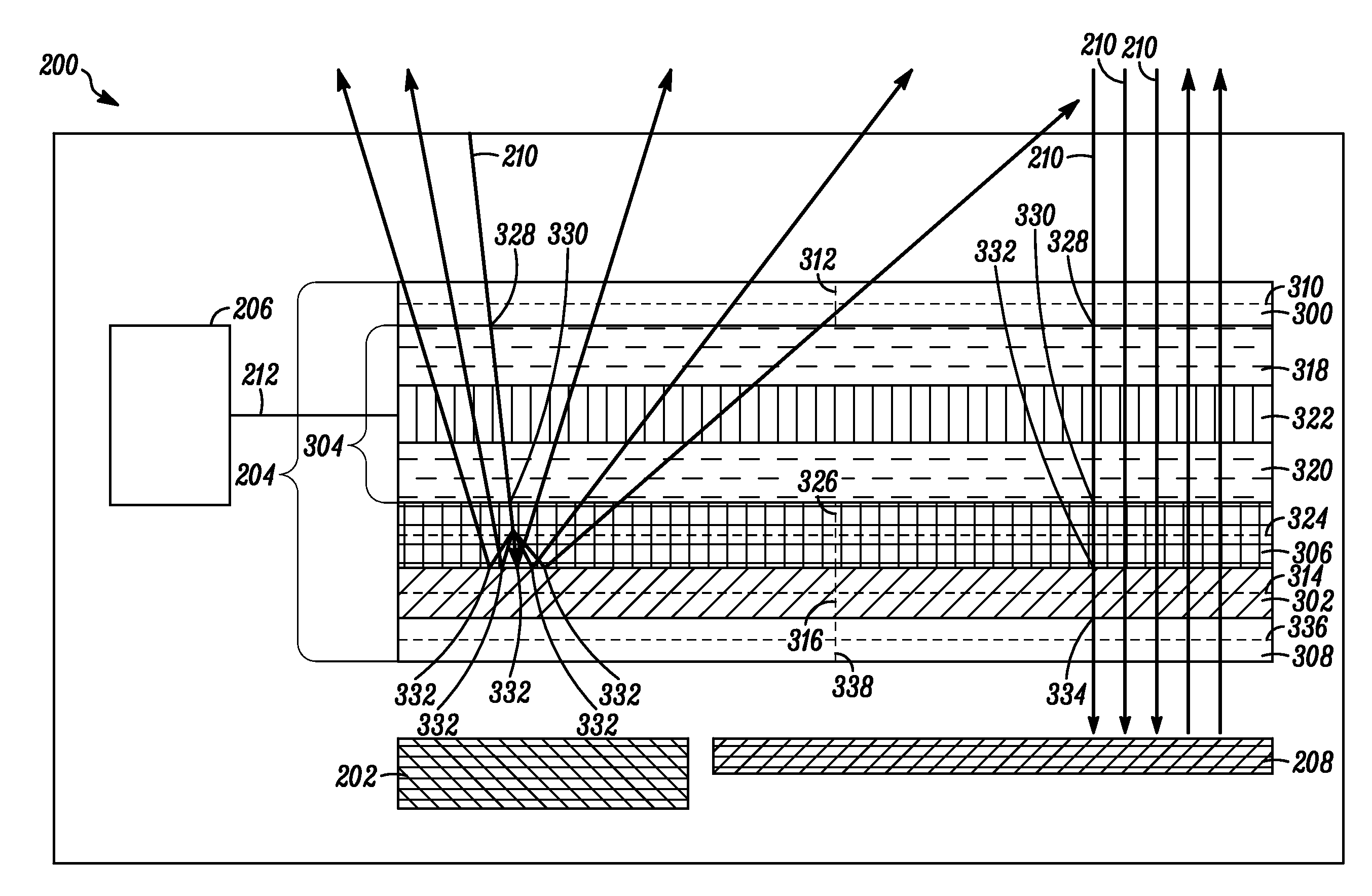
Electronic device and LC shutter for polarization-sensitive switching between transparent and diffusive states
An electronic device (200) includes a display (202) and an LC shutter (204), at least a portion of which is operatively positioned over the display (202). The LC shutter (204) provides switching between a transparent state and a diffusive state with high image integrity, and high transmission in the transparent state. In one embodiment, the electronic device (200) further includes control logic (206) operatively coupled to the LC shutter (204) to provide control signals (212) to the LC shutter (204) to effect the transparent state. The LC shutter (204) includes a first dichroic polarizer (300), such as a broadband dichroic polarizer, a specular reflective polarizer (302), such as a broadband reflective polarizer, an LC cell (304), and a diffusive reflective polarizer (306). The LC cell (304) is interposed between the first dichroic polarizer (300) and the specular reflective polarizer (302). The diffusive reflective polarizer (306) is interposed between the LC cell (304) and the specular reflective polarizer (302). Related methods are also set forth.
Owner:GOOGLE TECH HLDG LLC
Electronic device and lc shutter for polarization-sensitive switching between transparent and diffusive states
An electronic device (200) includes a display (202) and an LC shutter (204), at least a portion of which is operatively positioned over the display (202). The LC shutter (204) provides switching between a transparent state and a diffusive state with high image integrity, and high transmission in the transparent state. In one embodiment, the electronic device (200) further includes control logic (206) operatively coupled to the LC shutter (204) to provide control signals (212) to the LC shutter (204) to effect the transparent state. The LC shutter (204) includes a first dichroic polarizer (300), such as a broadband dichroic polarizer, a specular reflective polarizer (302), such as a broadband reflective polarizer, an LC cell (304), and a diffusive reflective polarizer (306). The LC cell (304) is interposed between the first dichroic polarizer (300) and the specular reflective polarizer (302). The diffusive reflective polarizer (306) is interposed between the LC cell (304) and the specular reflective polarizer (302). Related methods are also set forth.
Owner:GOOGLE TECH HLDG LLC
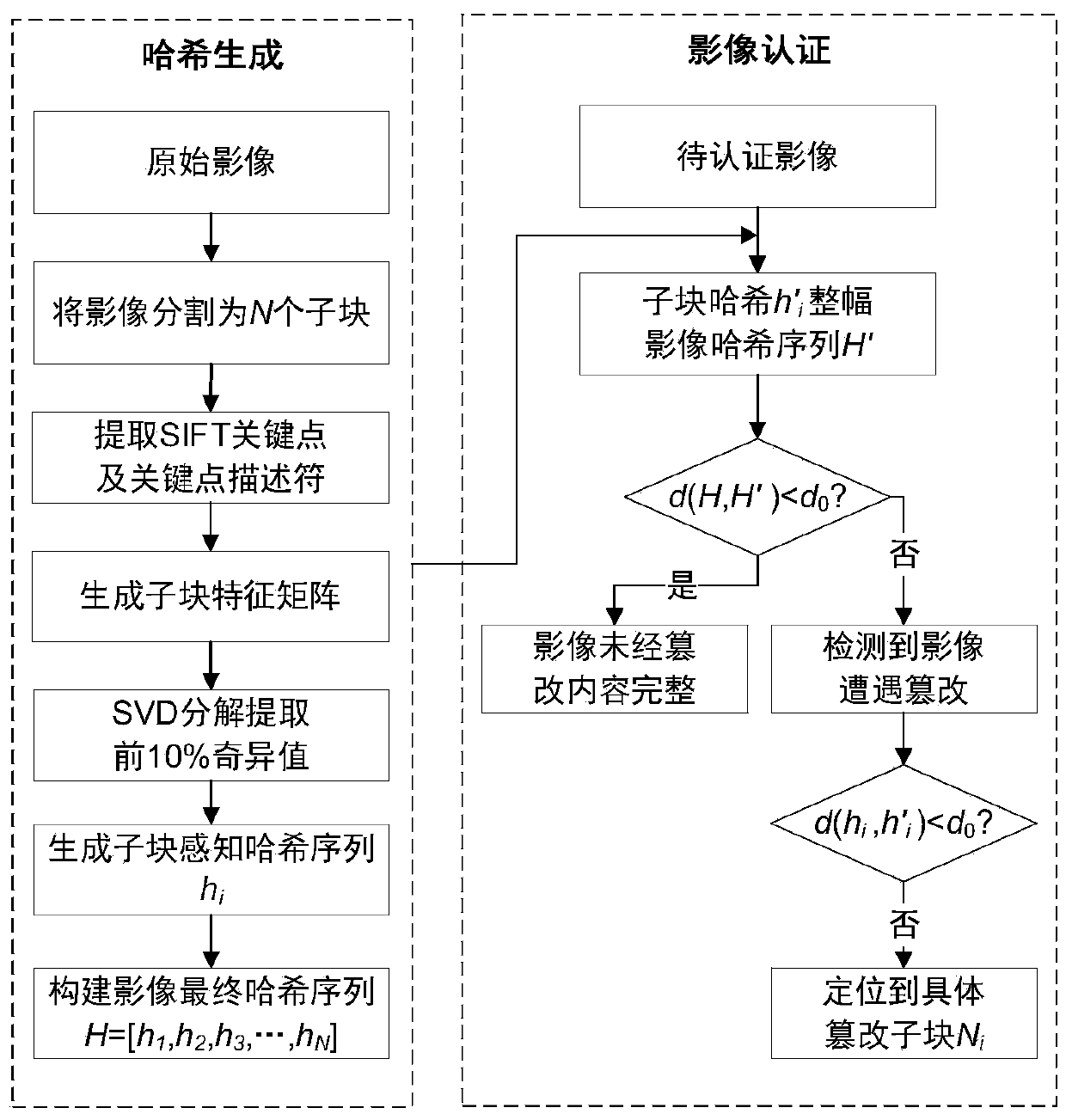
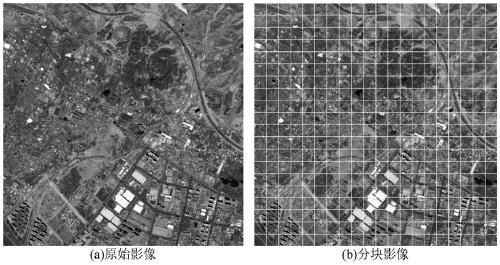
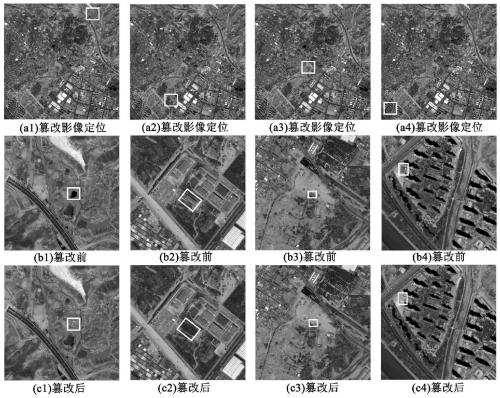
GF-2 image integrity authentication method using SIFT and SVD perceptual hash
The invention discloses a GF-2 image integrity authentication method using SIFT and SVD perceptual hash. The method comprises the steps of image perceptual hash sequence generation and image content integrity authentication, and the image hash sequence generation comprises the steps of constructing perceptual hash sequences of sub-blocks by using an SIFT operator and an SVD method after an image is subjected to block processing, and further connecting the perceptual hash sequences of all the sub-blocks in series to generate a perceptual hash sequence of a whole image. During image integrity authentication process, the detection of the image integrity is realized by measuring the degree of differentiation between the Euclidean distance between the perceptual hash sequences of the original image and the image to be authenticated and the initial threshold. And if the Euclidean distance between the two sub-blocks is smaller than an initial threshold value, a judgment is made that the imagecontent is complete, and if not, an image is detected to be tampered, thereby completing positioning of a local tampered region through difference measurement of perceptual hash between the sub-blocks. The invention has good robustness and is a GF-2 image content integrity authentication method with high practicability.
Owner:LANZHOU JIAOTONG UNIV
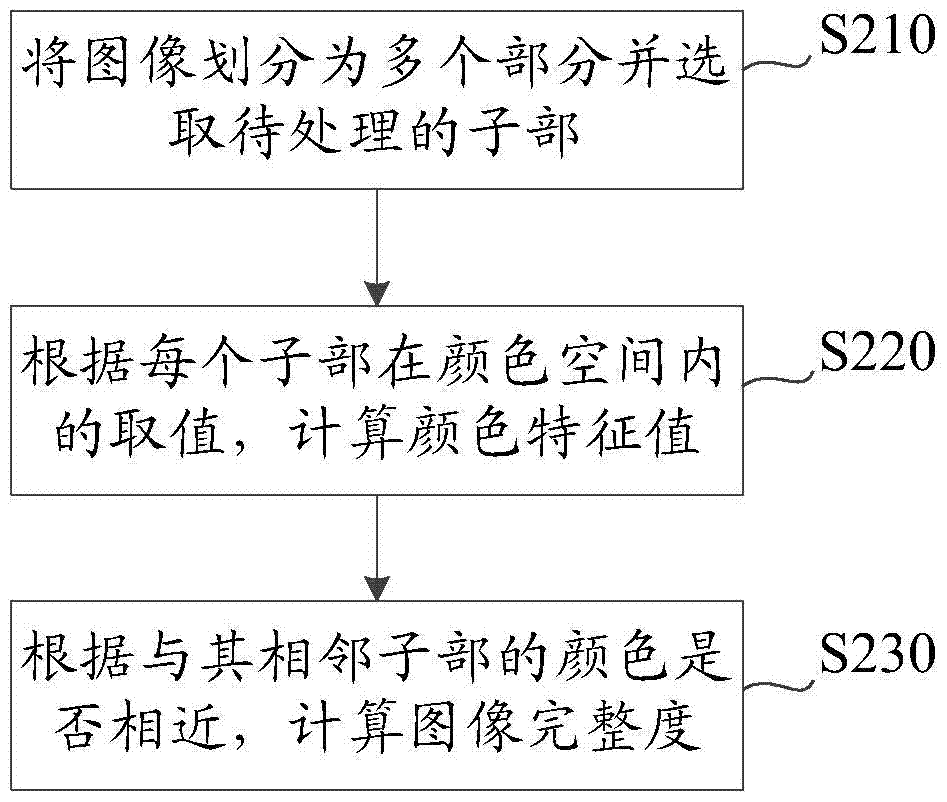
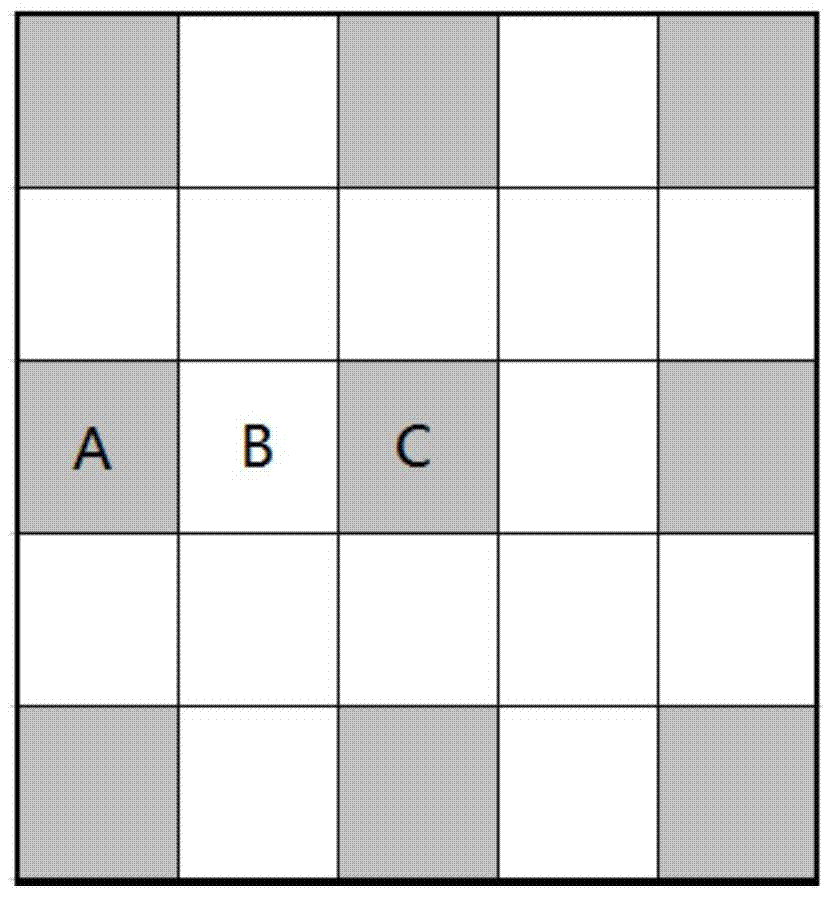
Method and device for judging image integrity and page loading degree and client device
ActiveCN106971386ADetermine loading statusImage enhancementImage analysisPattern recognitionImage integrity
The application discloses a method and device used for judging and calculating image integrity and a client device. The method includes dividing an image into a plurality of parts and selecting a plurality of or all of the plurality of parts as subparts to be processed; according to the value of each subpart in color space, calculating a color characteristic value of the subpart; and according to whether each subpart and a subpart adjacent thereto are close in color, calculating image integrity, and under the circumstance that difference of color characteristic values of the subpart and the subpart adjacent thereto is smaller than a first threshold value, judging that the subpart and the subpart adjacent thereto are close in color. The calculation of the image integrity can also introduce a bad block coefficient, and the calculated image integrity can be used for judging the page loading condition. Thus, a value irrelevant to content can be obtained through calculation of the color difference of regions of a picture and the value can be utilized to monitor a process (such as monitoring of page loading speed) and monitor problems (such as a white screen problem).
Owner:ALIBABA (CHINA) CO LTD
Electronic device and LC shutter with diffusive reflective polarizer
An electronic device (200) includes a display (202) and an LC shutter (204), at least a portion of which is operatively positioned over the display (202). The LC shutter (204) provides switching between a transparent state and a diffusive state with high image integrity, and high transmission in the transparent state. In one embodiment, the electronic device (200) further includes control logic (206) operatively coupled to the LC shutter (204) to provide control signals (212) to the LC shutter (204) to effect the transparent state. The LC shutter (204) includes a first dichroic polarizer (300), such as a broadband dichroic polarizer, an LC cell (304), and a diffusive reflective polarizer (307). The LC cell (304) is interposed between the first dichroic polarizer (300) and the diffusive reflective polarizer (307). Related methods are also set forth.
Owner:GOOGLE TECH HLDG LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com