Safe and active image tampering detection method and device
An active, image technology, applied in the direction of image communication, electrical components, transmission systems, etc., can solve the problem that the receiving end device cannot detect that the original image has been tampered with, cannot accurately detect whether the image has been tampered with, and erroneous detection results. Guarantee image integrity and image authenticity, ensure image authenticity, and avoid the effect of detection results
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
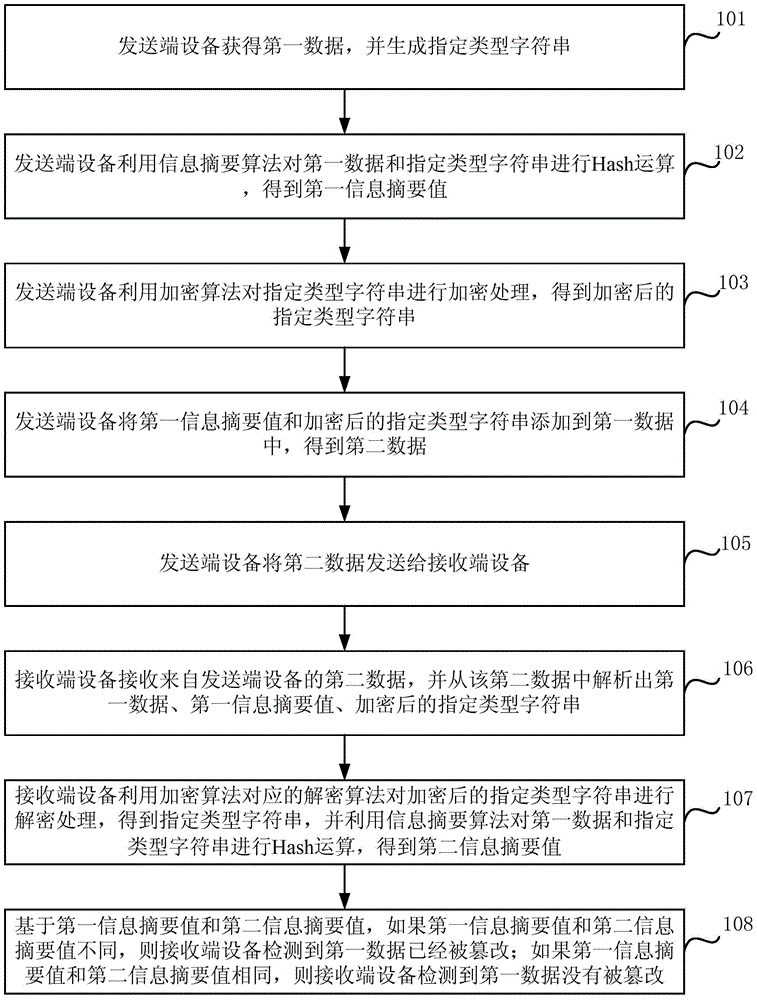
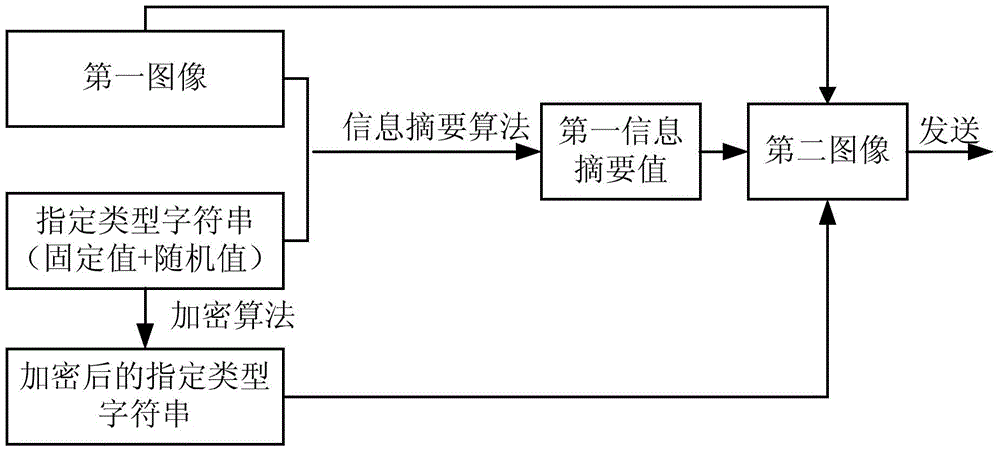
[0049] Aiming at the problems existing in the prior art, Embodiment 1 of the present invention proposes a safe active image tampering detection method, which is applied to a system including a sending-end device and a receiving-end device. Wherein, the sending-end device refers to a device that sends an image, and the receiving-end device refers to a device that receives an image and performs an integrity check on the image. In a specific application scenario, the sending end device may be a terminal device, and the receiving end device may be an application server. The images referred to in the embodiments of the present invention specifically include but are not limited to images generated by sensing applications of terminal devices, for example, reporting images generated by environmental pollution reporting applications, management images generated by public place management applications, and taking pictures of emergencies Photo images produced by forensic applications, et...
Embodiment 2
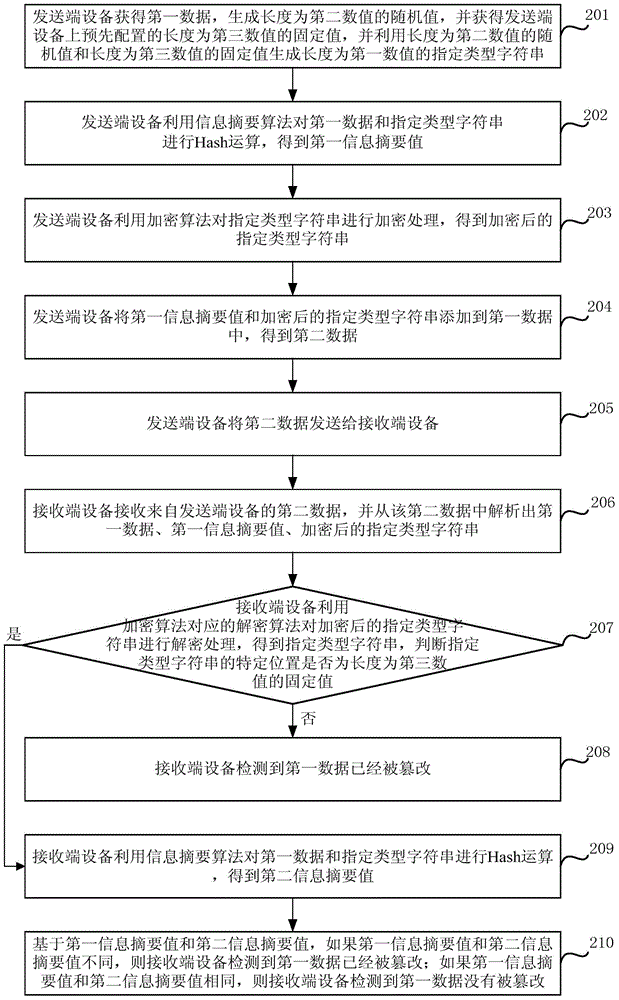
[0070] Embodiment 2 of the present invention proposes a safe active image tampering detection method, which can be applied to a system including a sending-end device and a receiving-end device. Wherein, the sending-end device refers to a device that sends an image, and the receiving-end device refers to a device that receives an image and performs an integrity check on the image. In a specific application scenario, the sending end device may be a terminal device, and the receiving end device may be an application server.
[0071] The images referred to in the embodiments of the present invention specifically include but are not limited to images generated by sensing applications of terminal devices, for example, reporting images generated by environmental pollution reporting applications, management images generated by public place management applications, and taking pictures of emergencies Photo images produced by forensic applications, etc.
[0072] It should be noted that ...
Embodiment 3
[0100] Embodiment 3 of the present invention proposes a safe active image tampering detection method, which can be applied to a system including a sending end device and a receiving end device. Wherein, the sending-end device refers to a device that sends an image, and the receiving-end device refers to a device that receives an image and performs an integrity check on the image. In a specific application scenario, the sending end device may be a terminal device, and the receiving end device may be an application server.
[0101] The images referred to in the embodiments of the present invention specifically include but are not limited to images generated by sensing applications of terminal devices, for example, reporting images generated by environmental pollution reporting applications, management images generated by public place management applications, and taking pictures of emergencies Photo images produced by forensic applications, etc.
[0102] It should be noted that ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com