Novel low-resource efficient lightweight Surge block cipher implementation method
A technology of block cipher and implementation method, which is applied in the direction of encryption device with shift register/memory, etc., and can solve problems such as vulnerability to attack, low encryption performance, and low efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0061] The present invention will be further described below in conjunction with the accompanying drawings and embodiments.
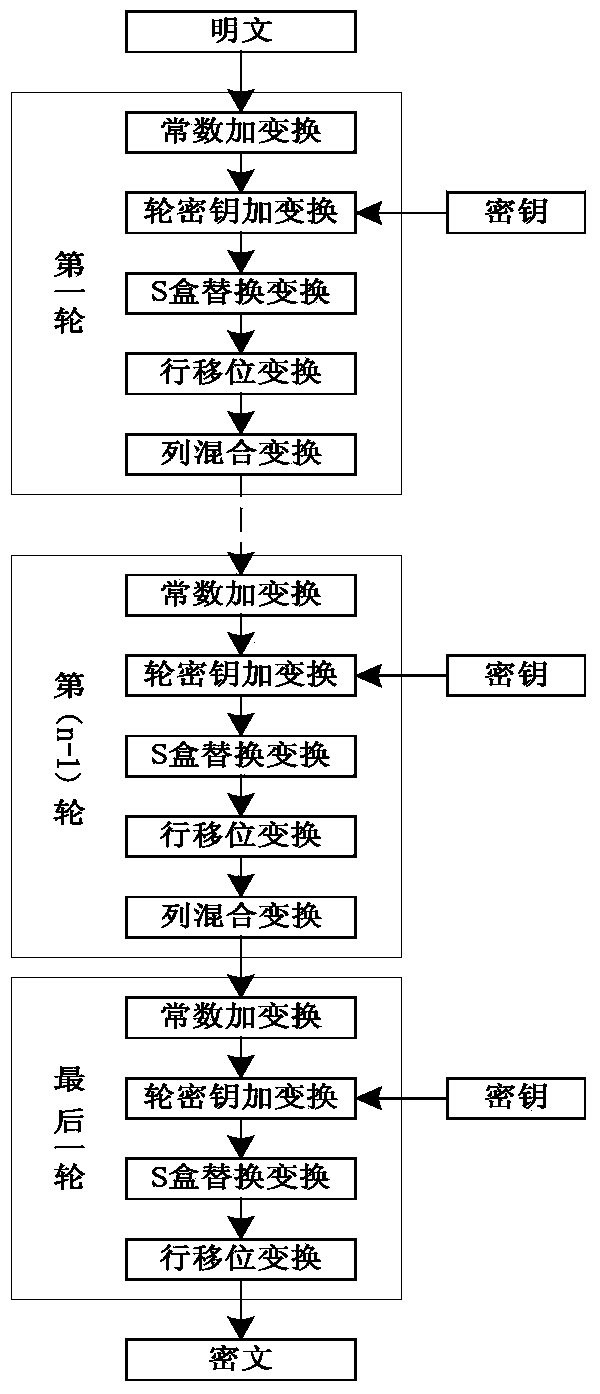
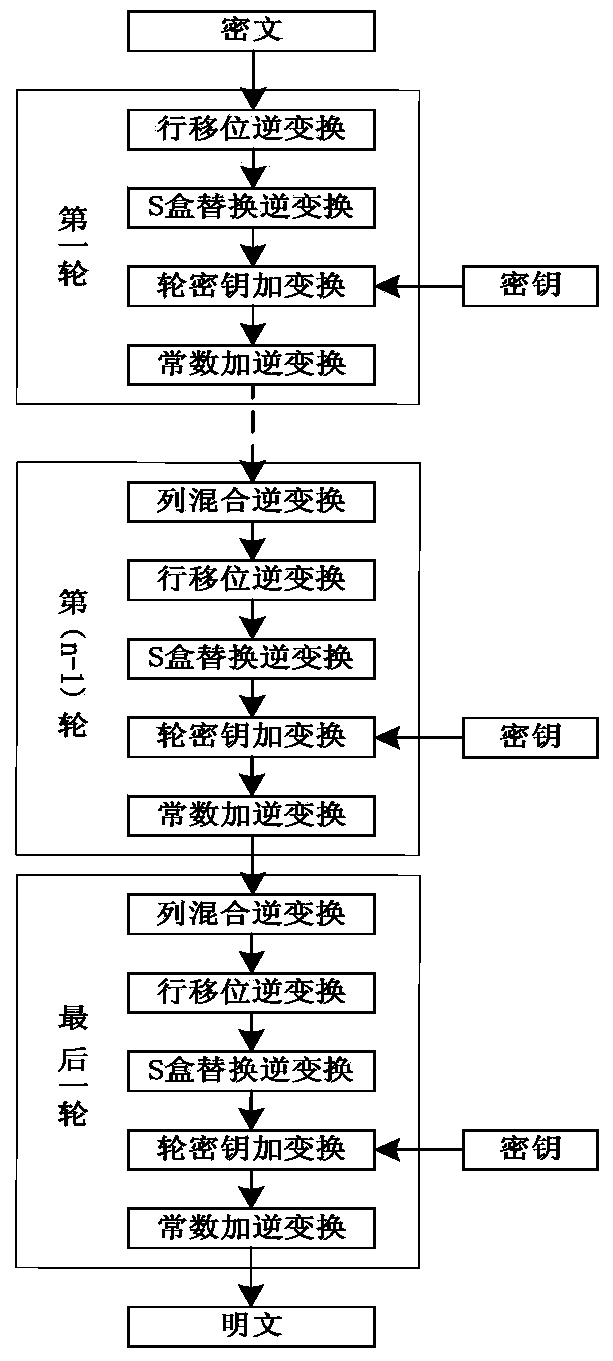
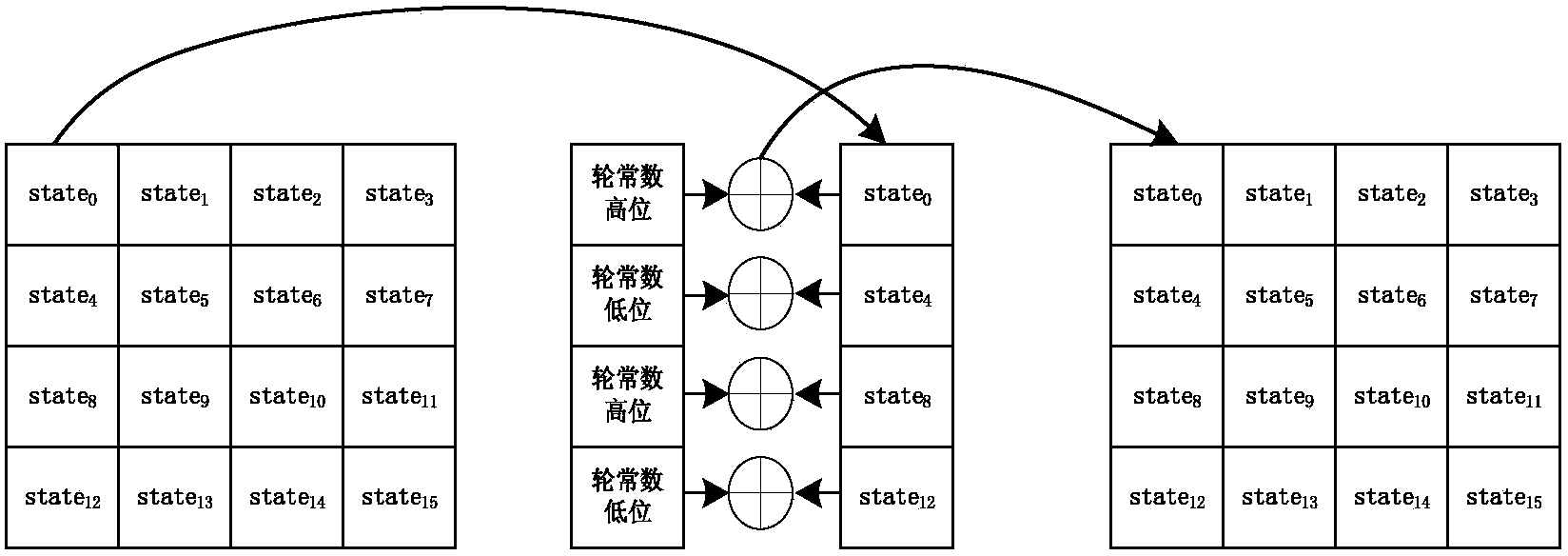
[0062] The implementation method of the Surge block cipher adopts the SPN structure, the block length is 64-bit, and the key length is designed to be 64-bit, 80-bit, and 128-bit, which are respectively recorded as Surge-64, Surge-80, and Surge-128 . Surge-64, Surge-80 and Surge-128 iteration rounds N R They are 32 rounds, 36 rounds and 40 rounds respectively. Surge encryption operation process is as follows: figure 1 As shown, the encryption round operation includes five modules: constant plus transformation (AddConstants), round key plus transformation (AddRoundKey), S-box replacement transformation (SubCells), row shift transformation (ShiftRows), and column mix transformation (MixColumns). The decryption operation flow is as follows figure 2 , the algorithm decryption round operation includes column mixing inverse transformation (InvMixColumns),...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com