Hash algorithm based on complex dynamic network
A complex dynamic network and network technology, applied in the field of Hash algorithm, can solve the problems of many iterations and high algorithm complexity, and achieve the effect of low computational complexity, reduced algorithm complexity, and reduced computational complexity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
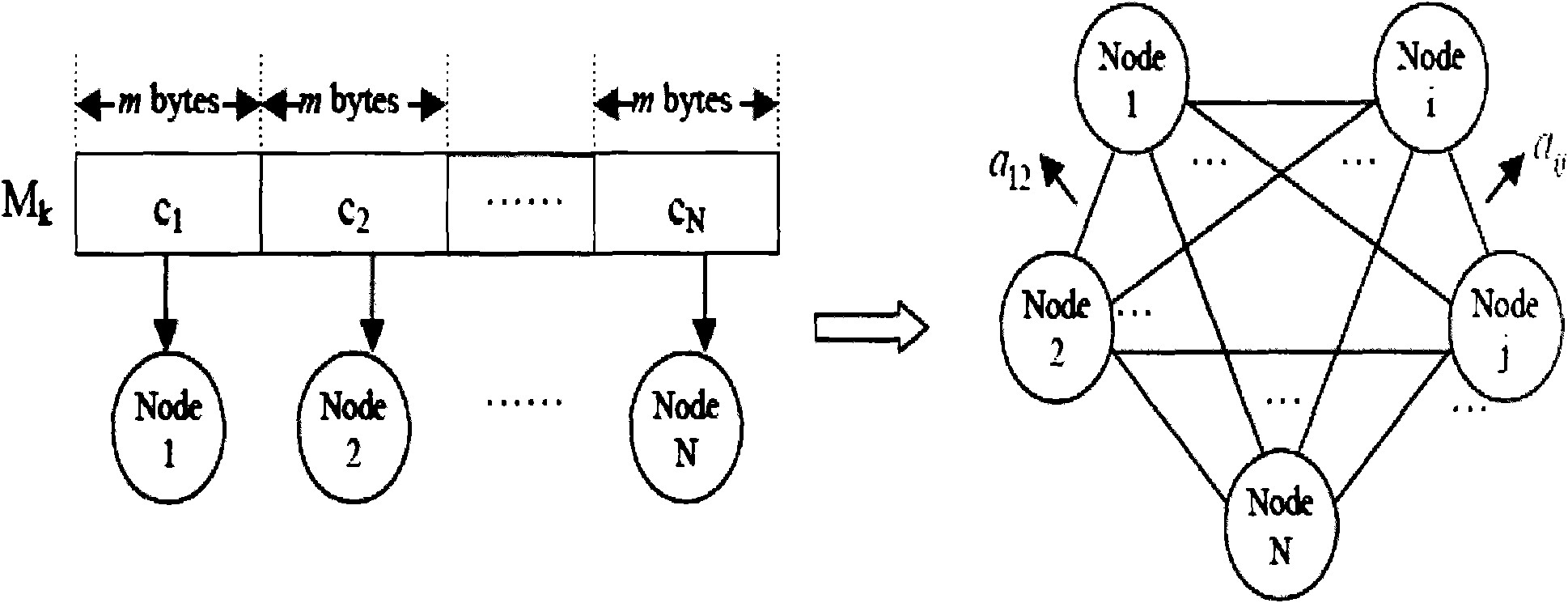
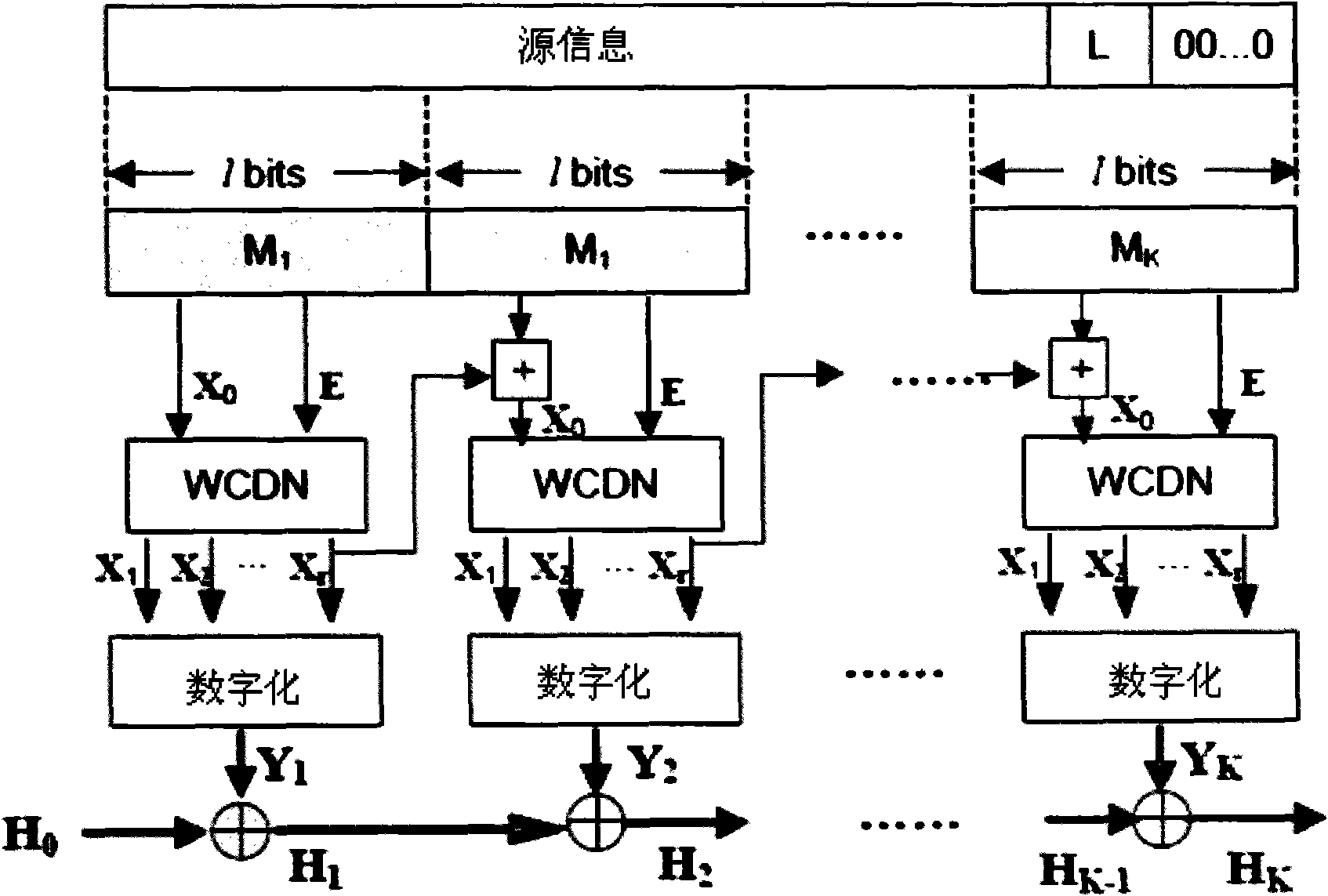
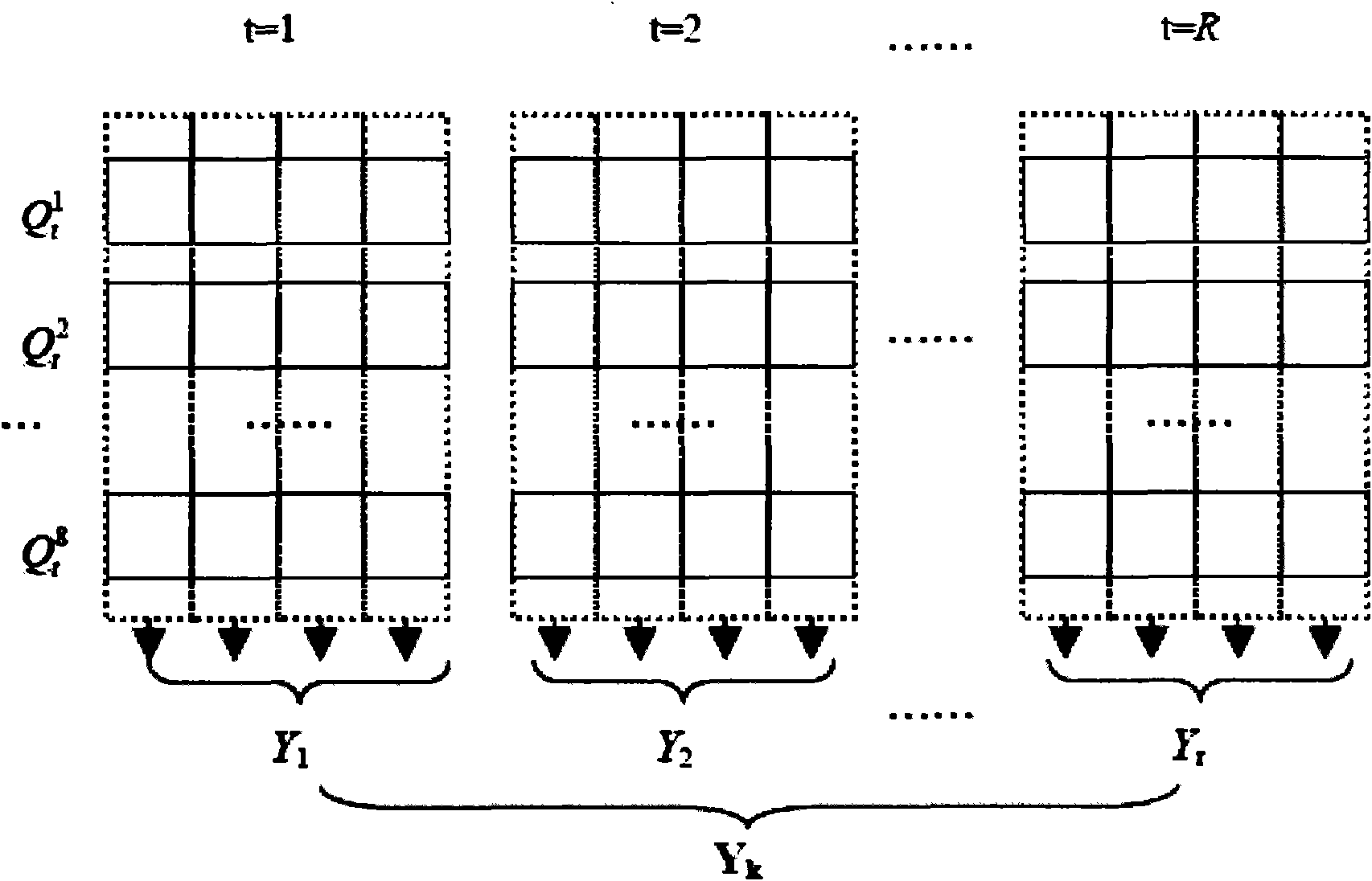
[0033] A Hash function construction algorithm based on a complex dynamic network according to the present invention, the method adopts a complex dynamic network based on a message, maps the network parameters to a chaotic coupling mapping network for iterative and quantitative processing, and obtains a Hash value, specifically including The following steps:
[0034] 1. Preprocess the original message
[0035] The original message M is first transformed as follows:
[0036] M'=M+string(|M|)+padding (1)
[0037] Its purpose is to make the transformed message M' can be divided into K message sub-blocks M with a length of Lbits k (k=1,...,K), k message block number, (1) where '+' represents the concatenation operation of strings, string(|M|) is the string form of the length of the original message M; padding It refers to the filling bits when the last block is less than Lbits to ensure that the last sub-block is also L bits;
[0038] 2. Initialize related parameters
[0039] ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com