Code obfuscation method and code running method and device
A code obfuscation and object file technology, applied in the fields of code obfuscation method, code operation method and device, can solve the problem of low code obfuscation rate in Java layer
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0036] According to the embodiment of the present application, an embodiment of a code running method is also provided. It should be noted that the steps shown in the flow chart of the accompanying drawings can be executed in a computer system such as a set of computer-executable instructions, and, Although a logical order is shown in the flowcharts, in some cases the steps shown or described may be performed in an order different from that shown or described herein.
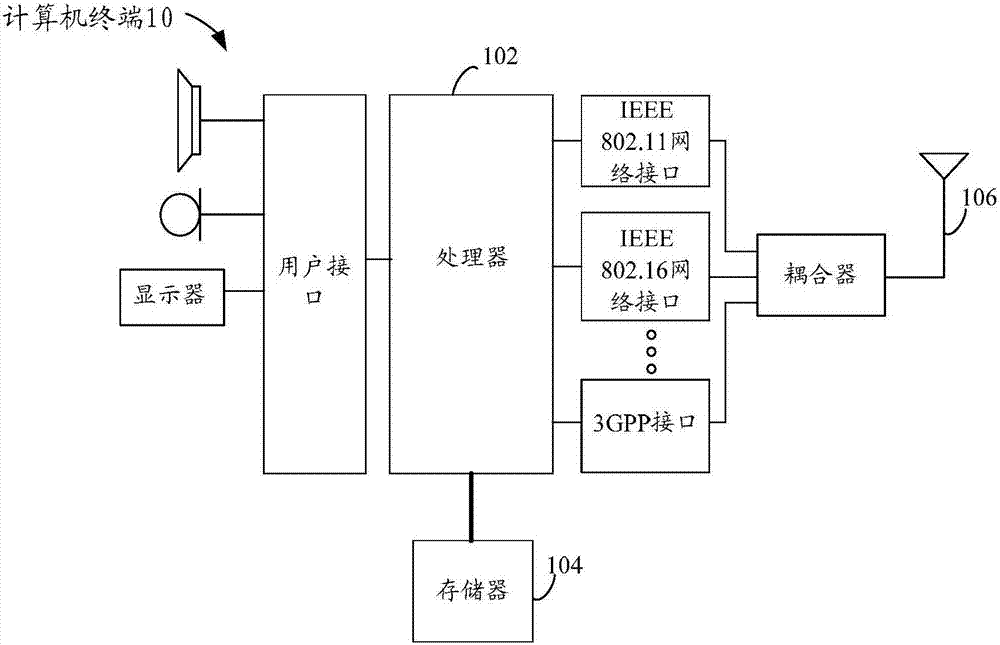
[0037] The method embodiment provided in Embodiment 1 of the present application may be executed in a mobile terminal, a computer terminal, or a similar computing device. Take running on a computer terminal as an example, figure 1 It is a block diagram of the hardware structure of a computer terminal of a code running method in the embodiment of the present application. Such as figure 1 As shown, the computer terminal 10 may include one or more (only one is shown in the figure) processors 102 (the processors 102...
Embodiment 2
[0051] According to the embodiment of the present application, an embodiment of a code obfuscation method is also provided. It should be noted that the steps shown in the flow chart of the accompanying drawings can be executed in a computer system such as a set of computer-executable instructions, and, Although a logical order is shown in the flowcharts, in some cases the steps shown or described may be performed in an order different from that shown or described herein.
[0052] The method embodiment provided in Embodiment 2 of the present application can still be executed in a mobile terminal, a computer terminal or a similar computing device. It should be noted here that the method embodiment provided in Embodiment 2 can still run on figure 1 on the computer terminal shown.
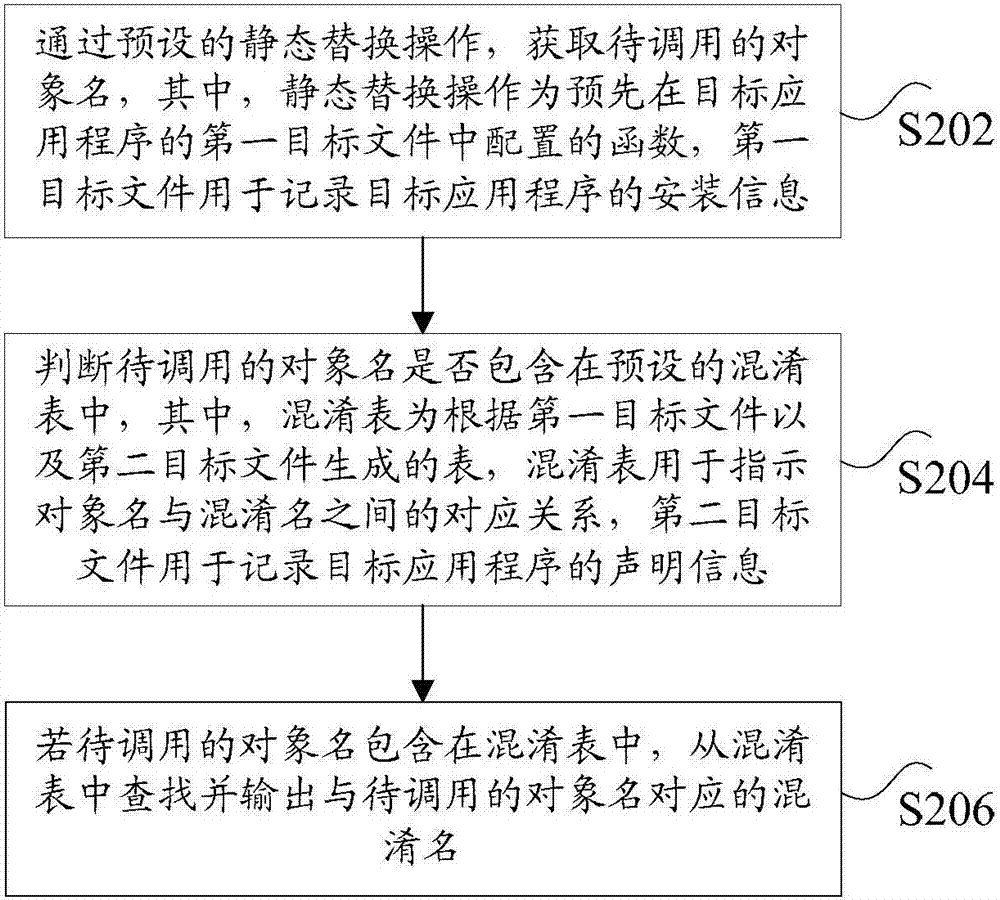
[0053] Under the above operating environment, this application provides such image 3 The code obfuscation method shown, image 3 is a schematic flowchart of a code obfuscation method according to E...
Embodiment 3
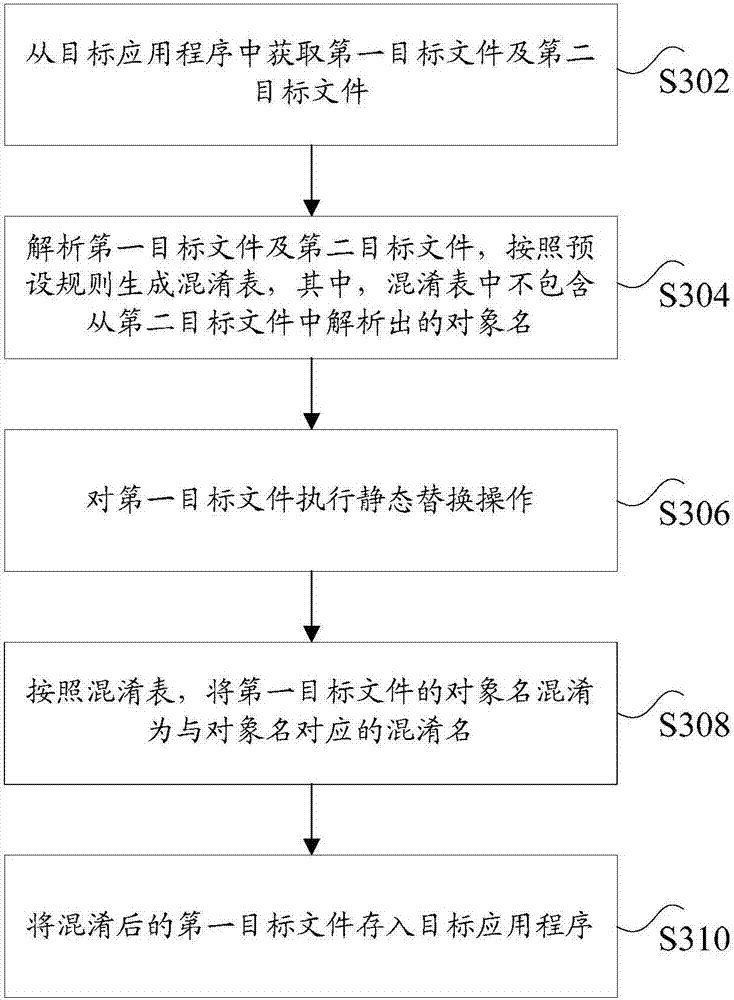
[0117] According to an embodiment of the present application, a code running device for implementing the above code running method is also provided, such as Figure 10 As shown, the apparatus may include: a first acquiring unit 1001 , a judging unit 1003 , and a first processing unit 1005 .
[0118]Wherein, the first obtaining unit 1001 is configured to obtain the name of the object to be called through a preset static replacement operation, wherein the static replacement operation is a function pre-configured in the first target file of the target application, and the first target file It is used to record the installation information of the target application program; the judging unit 1003 is used to judge whether the object name to be called is included in the preset confusion table, wherein the confusion table is a table generated according to the first target file and the second target file , the confusion table is used to indicate the correspondence between the object na...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com