Authorization system based on oauth2 protocol enhancement and method thereof
An authorization system and protocol technology, applied in the field of authorization system enhanced based on the oauth2 protocol, can solve problems such as user information leakage, business access efficiency reduction, and data security risks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
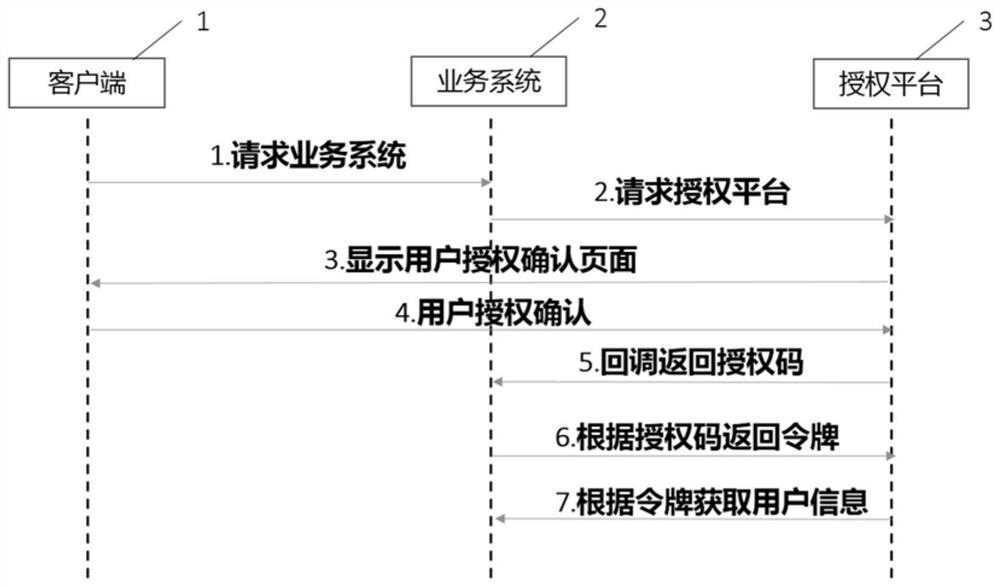
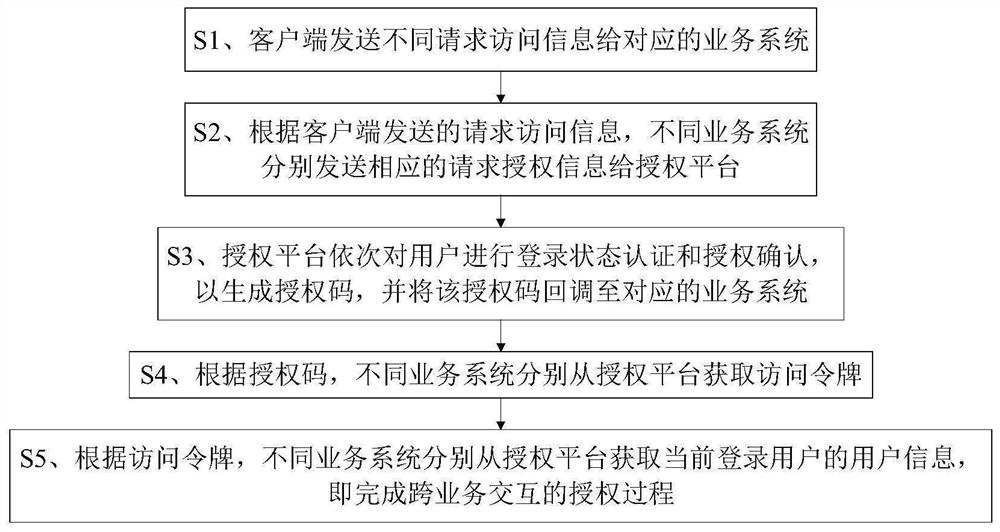
[0039] The purpose of the present invention is to realize a safe and efficient cross-service interactive authorization. Through multiple investigations and technology selection comparisons, it is finally decided to adopt an open authorization model based on the oauth2.0 protocol to solve these problems, but the original basic capabilities may It cannot meet the requirements, so it needs to be enhanced based on the oauth2 protocol.
[0040] The design principle takes the oauth2.0 protocol as the standard framework, and mainly solves the customer experience and data security problems caused by repeated authentication or passing customer parameters during the cross-platform jump interaction process. To put it simply, the platform can authorize its own personalized information to different business systems according to the wishes of customers.
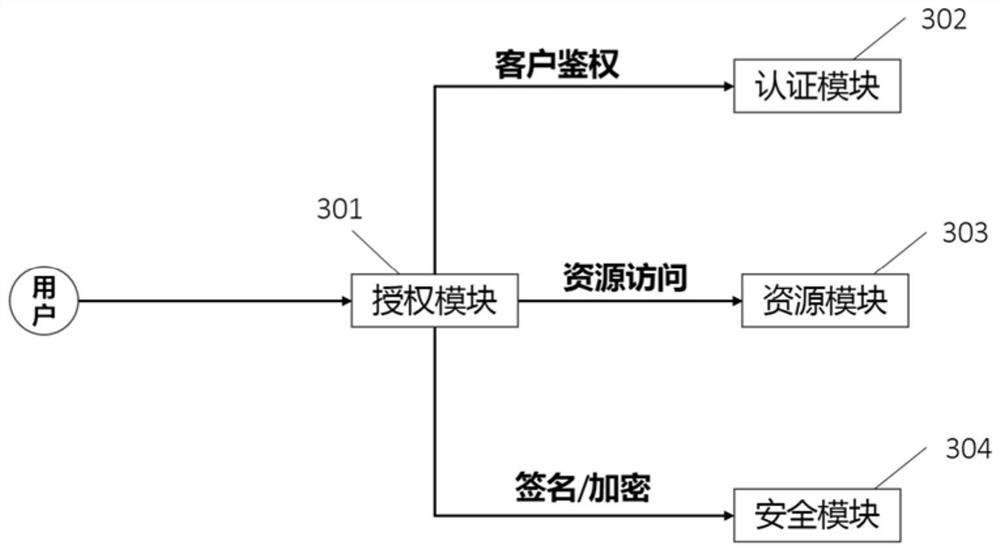
[0041] Such as figure 1 As shown, an authorization system enhanced based on the oauth2 protocol includes a client 1 and an authorization...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com