Login verification method and system based on SM3 algorithm and random challenge code
A login verification and random challenge technology, applied in the field of information security, can solve problems such as low randomness of data, short digits of summary information, security risks, etc., achieve high randomness of data, improve randomness and one-time, and secure sex high effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0044] The present invention will be further explained and described below in conjunction with the accompanying drawings and specific embodiments of the description. For the step numbers in the embodiment of the present invention, it is only set for the convenience of explanation and description, and there is no limitation on the order of the steps. The execution order of each step in the embodiment can be carried out according to the understanding of those skilled in the art Adaptive adjustment.
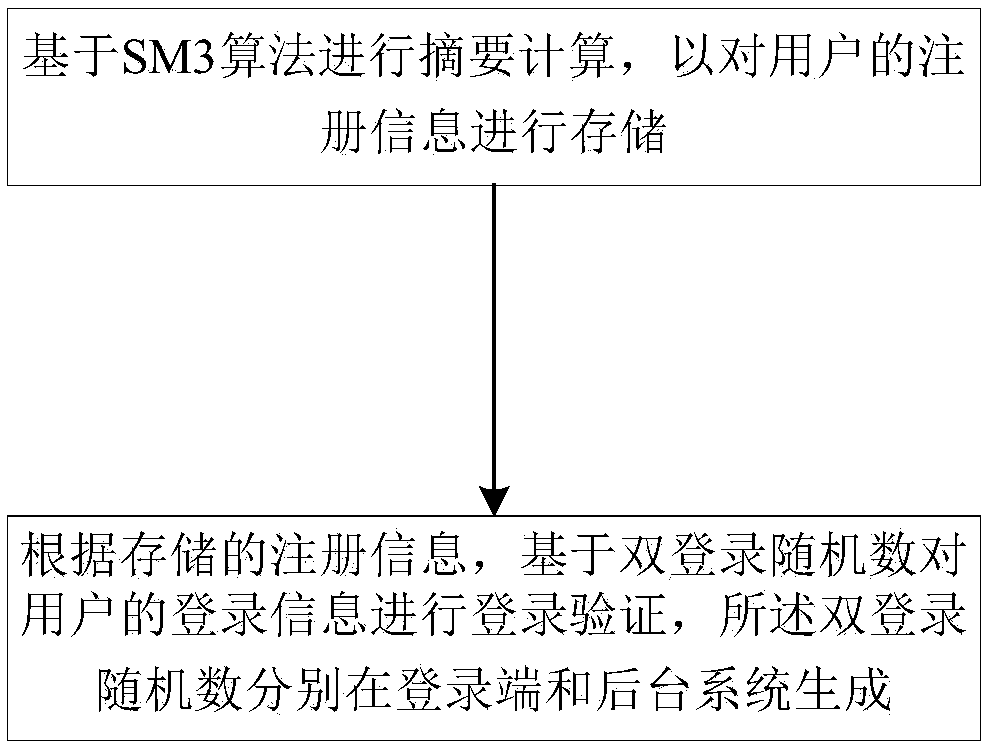
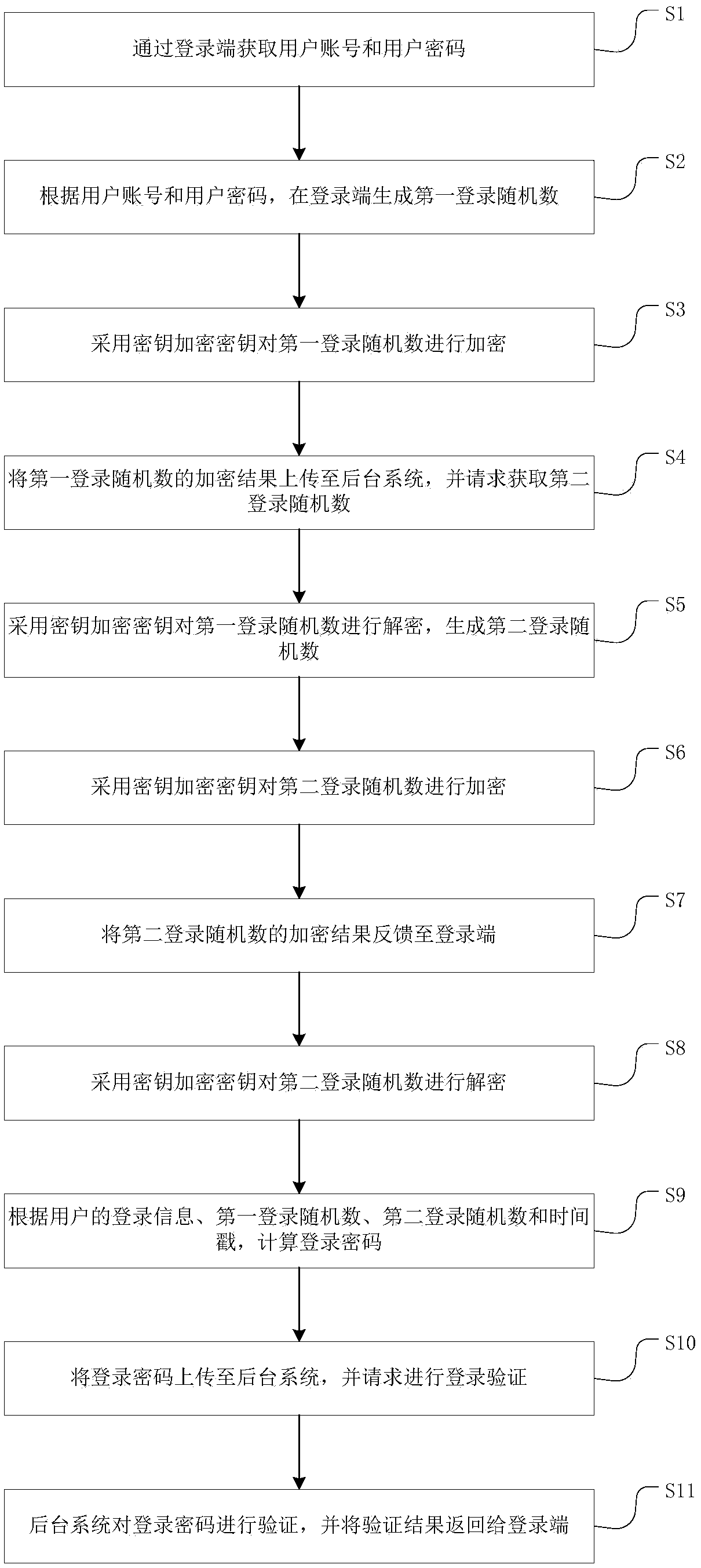
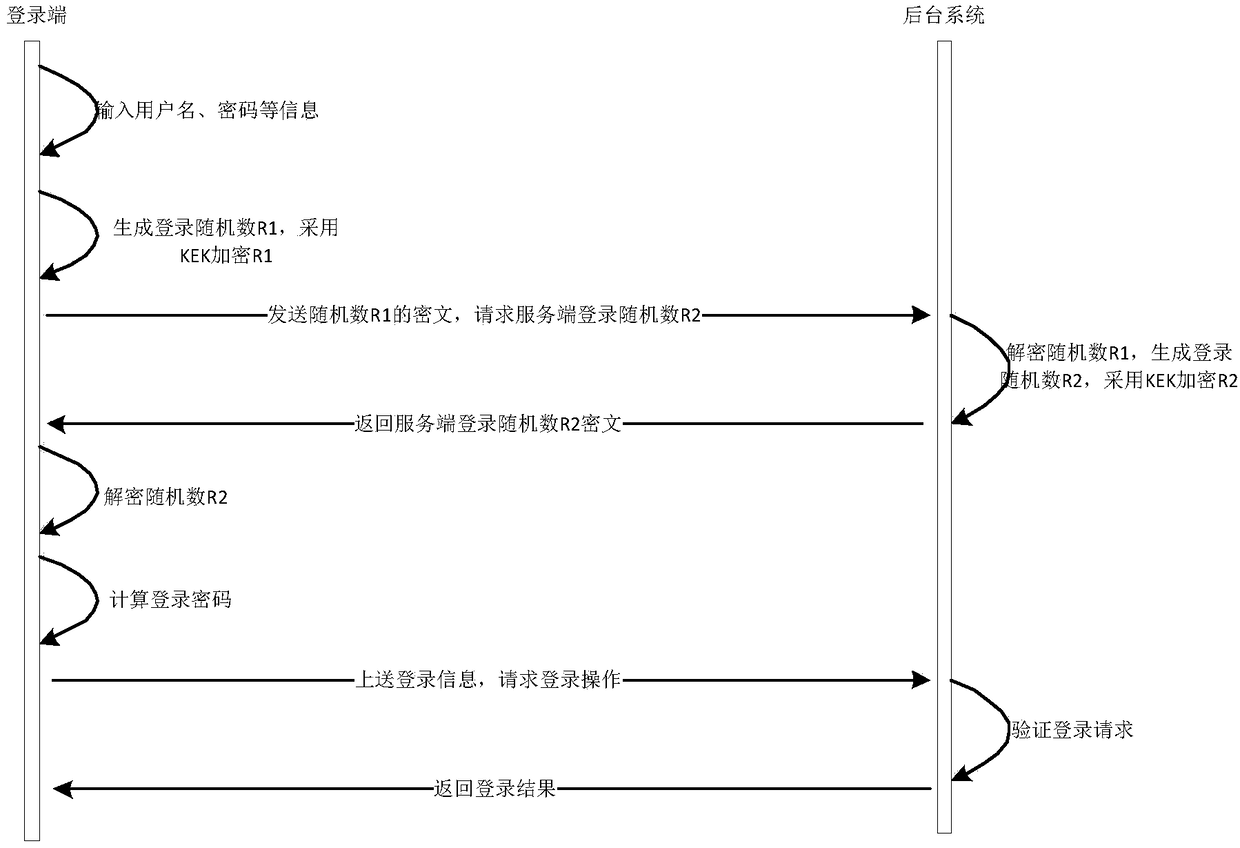
[0045] refer to figure 1 , the present invention is based on SM3 algorithm and the login verification method of random challenge code, comprises the following steps:
[0046] Abstract calculation based on SM3 algorithm to store user registration information;
[0047] According to the stored registration information, login verification is performed on the user's login information based on the double login random number generated at the login terminal and the background system respe...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com