File integrity verification method and file processor
An integrity verification and file processing technology, applied in the field of communication, can solve the problems of inapplicability and time-consuming, and achieve the effect of shortening the detection process, the time of file check value extraction and file integrity verification
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
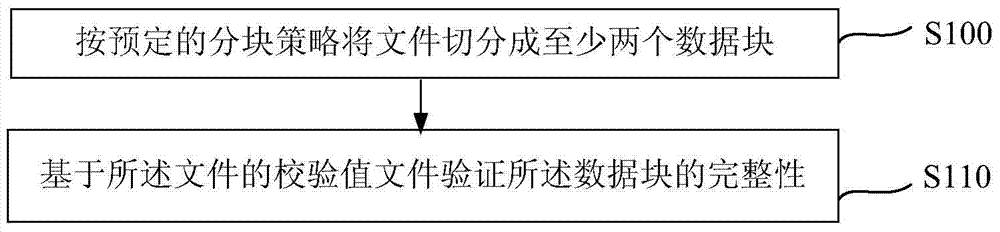
[0059] figure 1 A flowchart showing a file integrity verification method according to an embodiment of the present invention. Such as figure 1 As shown, the file integrity verification method may mainly include the following steps:
[0060] Step S100, dividing the file into at least two data blocks according to a predetermined block strategy; and
[0061] Step S110, verify the integrity of the data block based on the check value file of the file, wherein the check value file includes the respective check values of the at least two data blocks, if any of the data blocks determined to be incomplete, the document is determined to be incomplete and the verification is stopped.
[0062] Specifically, when a file is received, usually a check value file distributed with the file is also received, and the check value file is mainly used to verify the integrity of the file. In a possible implementation manner, the verification value file of the file can be generated by the foll...
Embodiment 2
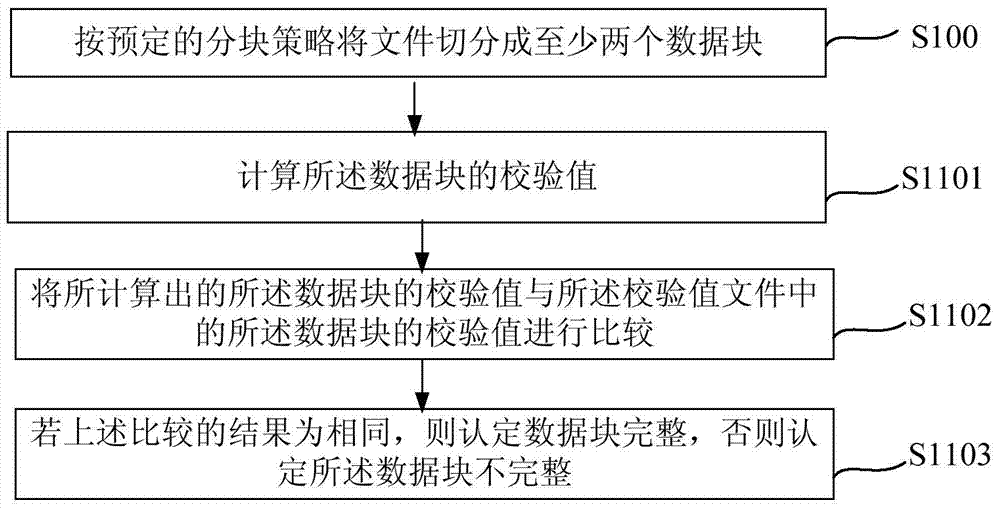
[0067] figure 2 A flowchart showing a file integrity verification method according to another embodiment of the present invention. figure 2 Winning mark and figure 1 Steps with the same numbers have the same functions, and for the sake of brevity, detailed descriptions of these steps are omitted.
[0068] Such as figure 2 as shown, figure 2 The file integrity verification method shown is the same as figure 1 The main difference between the shown file integrity verification methods is that the above step S110 may specifically include the following steps:
[0069] Step S1101, calculating the check value of the data block;
[0070] Step S1102, comparing the calculated check value of the data block with the check value of the data block in the check value file; and
[0071] Step S1103, if the result of the above comparison is the same, it is determined that the data block is complete, otherwise it is determined that the data block is incomplete.
[0072] Specifically,...
Embodiment 3
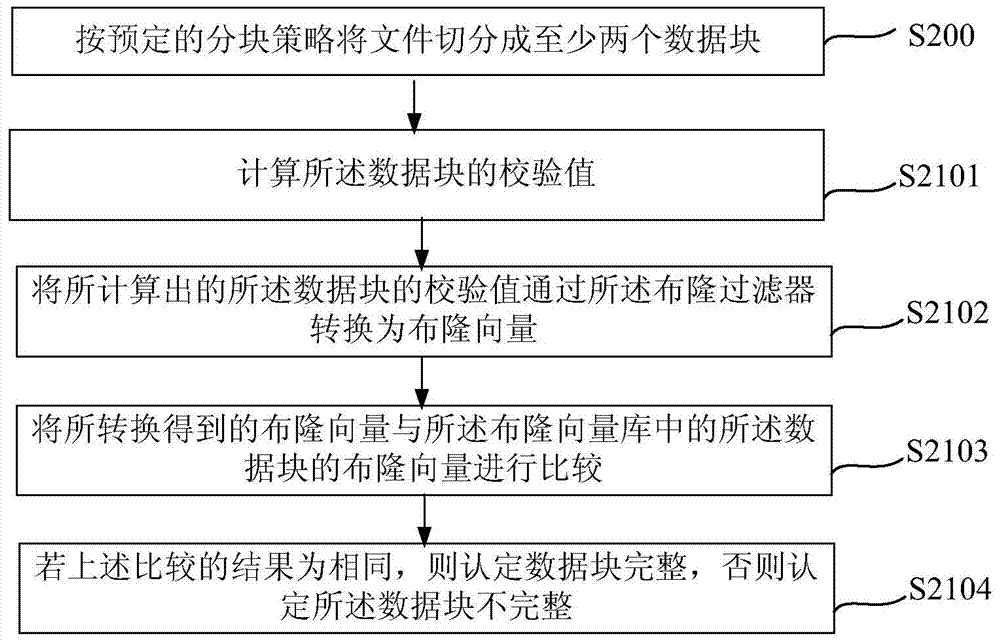
[0077] image 3 A flowchart showing a file integrity verification method according to another embodiment of the present invention. image 3 Winning mark and figure 1 , figure 2 The same steps have the same functions, and detailed descriptions of these steps are omitted for brevity.
[0078] The main difference between this embodiment of the present invention and the previous embodiment is that the check value file is a Bloom vector library, and the Bloom vector library includes the Bloom vectors of each of the data blocks, and the distribution of each of the data blocks The Bloom vector is obtained by passing the check value of each data block through a Bloom filter when the check value file is generated.
[0079] Specifically, such as Figure 4 As shown, after the file is divided into data blocks, in a possible implementation manner, each data block obtained after the division may be evenly distributed to different threads. Each thread directly generates the verificati...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com