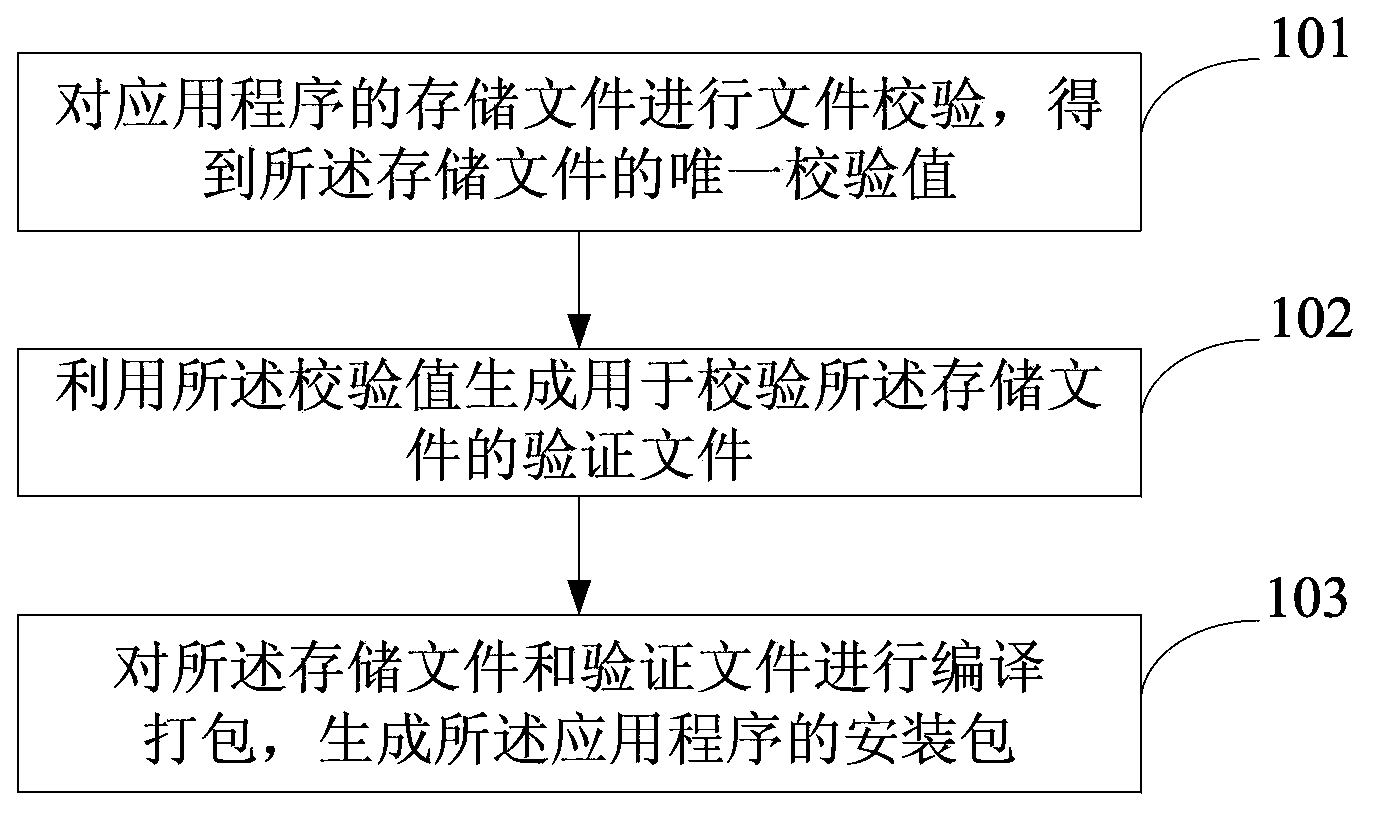
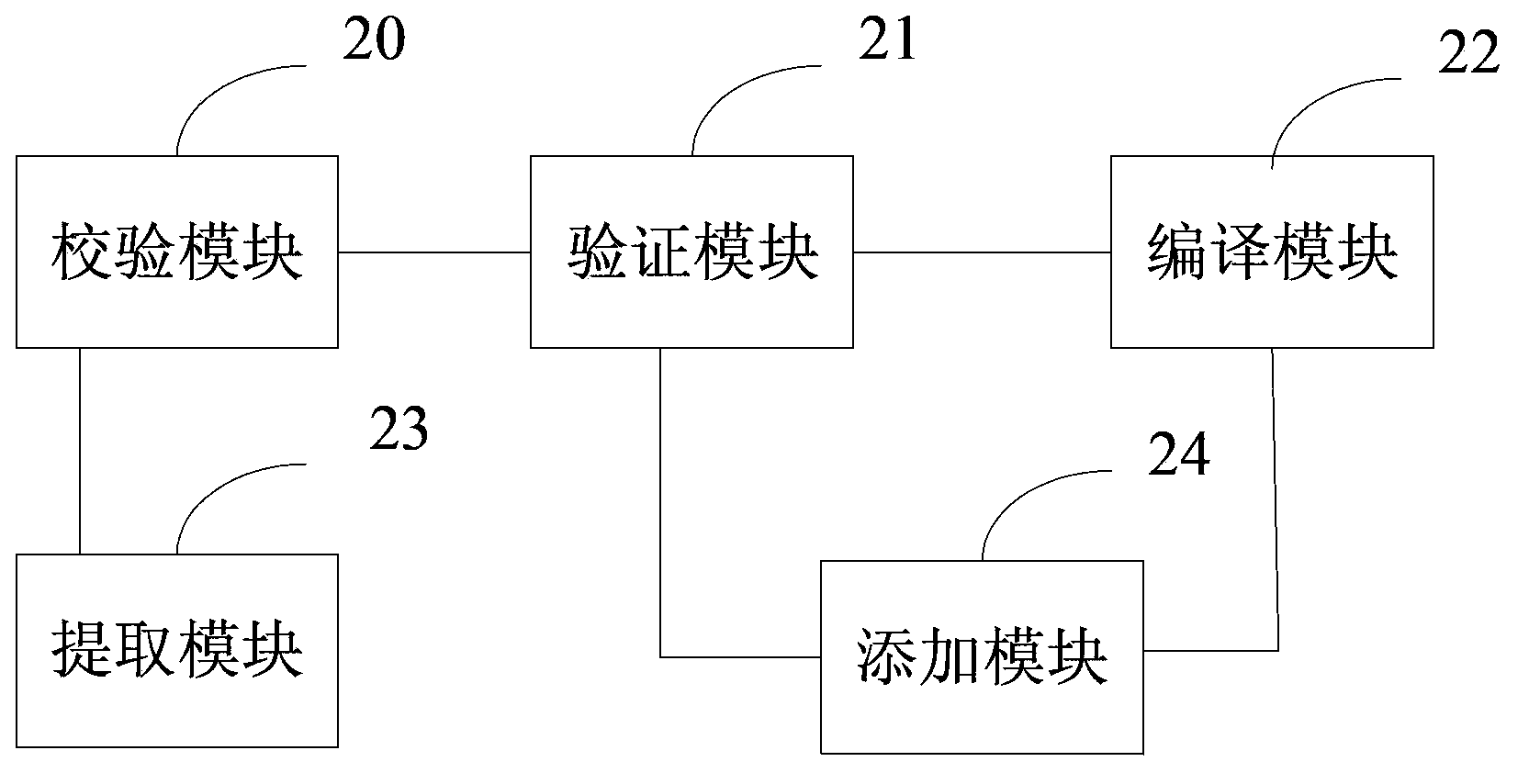
Method and device for preventing application program from being tampered
An application program and a technology that has been tampered with, applied in computer security devices, program/content distribution protection, instruments, etc., can solve problems such as increased difficulty in code reading, and achieve the effect of increasing security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0076] Generally, the malicious tampering of the application program is realized by modifying the java language code in the application program. Hackers can achieve malicious purposes by adding malicious codes such as advertisements and viruses to the original code, or deleting some verification-related codes. So as long as the code is prevented from being modified, the application can be fundamentally prevented from being maliciously tampered with.
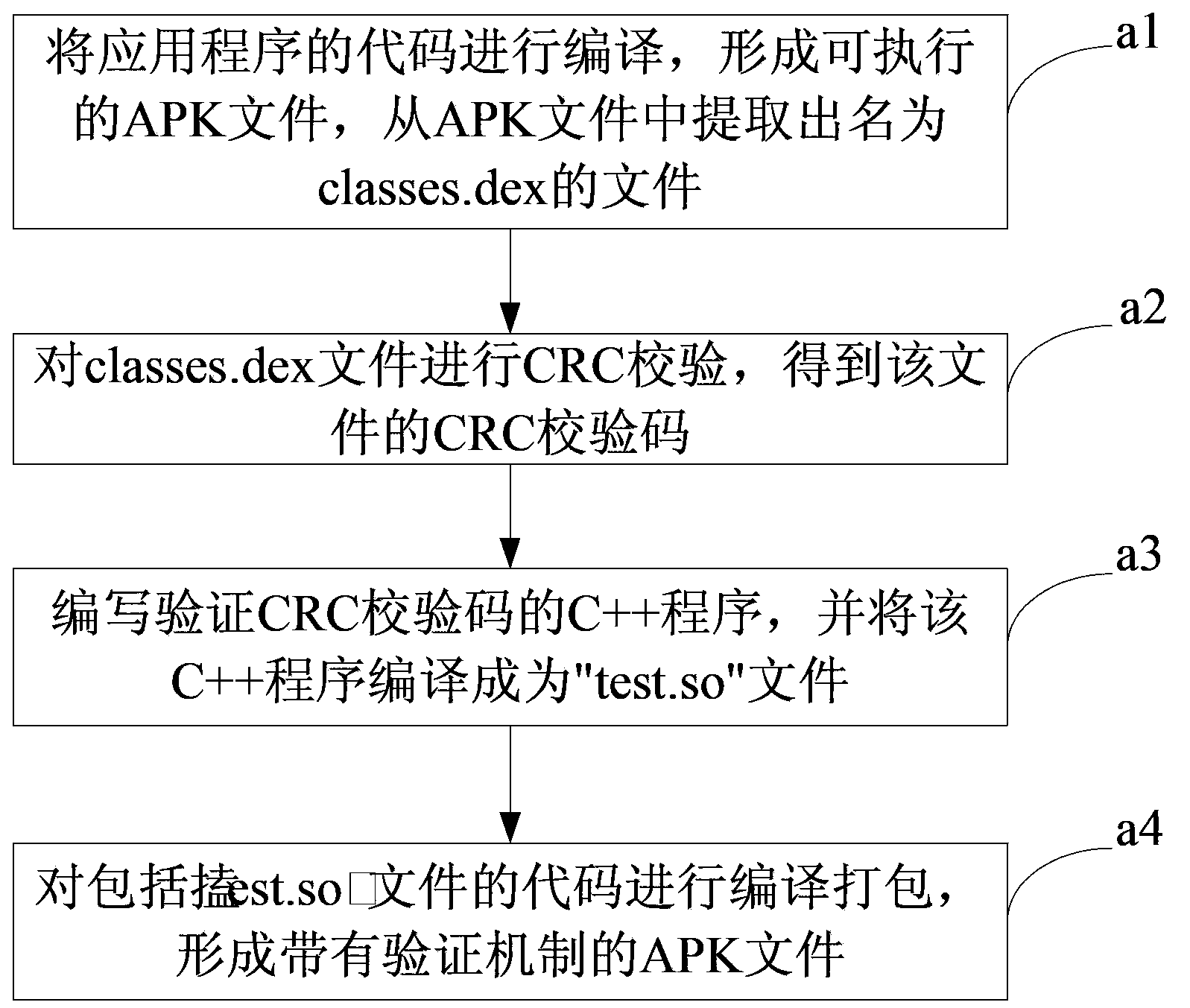
[0077] Such as image 3 As shown, this embodiment includes the following steps:
[0078] Step a1: After the application program is developed, the code of the application program is first compiled to form an executable APK file, and a file named classes.dex is extracted from the APK file.
[0079] Step a2: The classes.dex file includes all java language codes, and the file is verified using an existing file verification method, and a unique verification code of the file is obtained. For example, the file can be verified by usin...
Embodiment 2
[0086] Since the code calling the so format file is still written in Java language, some hackers can avoid verification by deleting the code calling the "test.so" file. Therefore, this embodiment adds preset executable codes in the "test.so" file. If the application program does not call the "test.so" file, the preset executable codes cannot run, and the application program obtains an error message to give the user relevant prompts , so as to prevent the application program from being modified maliciously.
[0087] Such as Figure 4 As shown, this embodiment includes the following steps:
[0088] Step b1: After the application program is developed, compile the code of the application program to form an executable APK file, and extract a file named classes.dex from the APK file.
[0089] Step b2: The classes.dex file includes all java language codes, and the file is verified using an existing file verification method, and a unique verification code of the file is obtained. F...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com