File verification method and a related device
A verification method and file technology, which is applied in the field of file verification, can solve the problems of occupying large hardware resources and wasting resources, and achieve the effects of improving efficiency, improving hardware performance, and reducing resource utilization
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
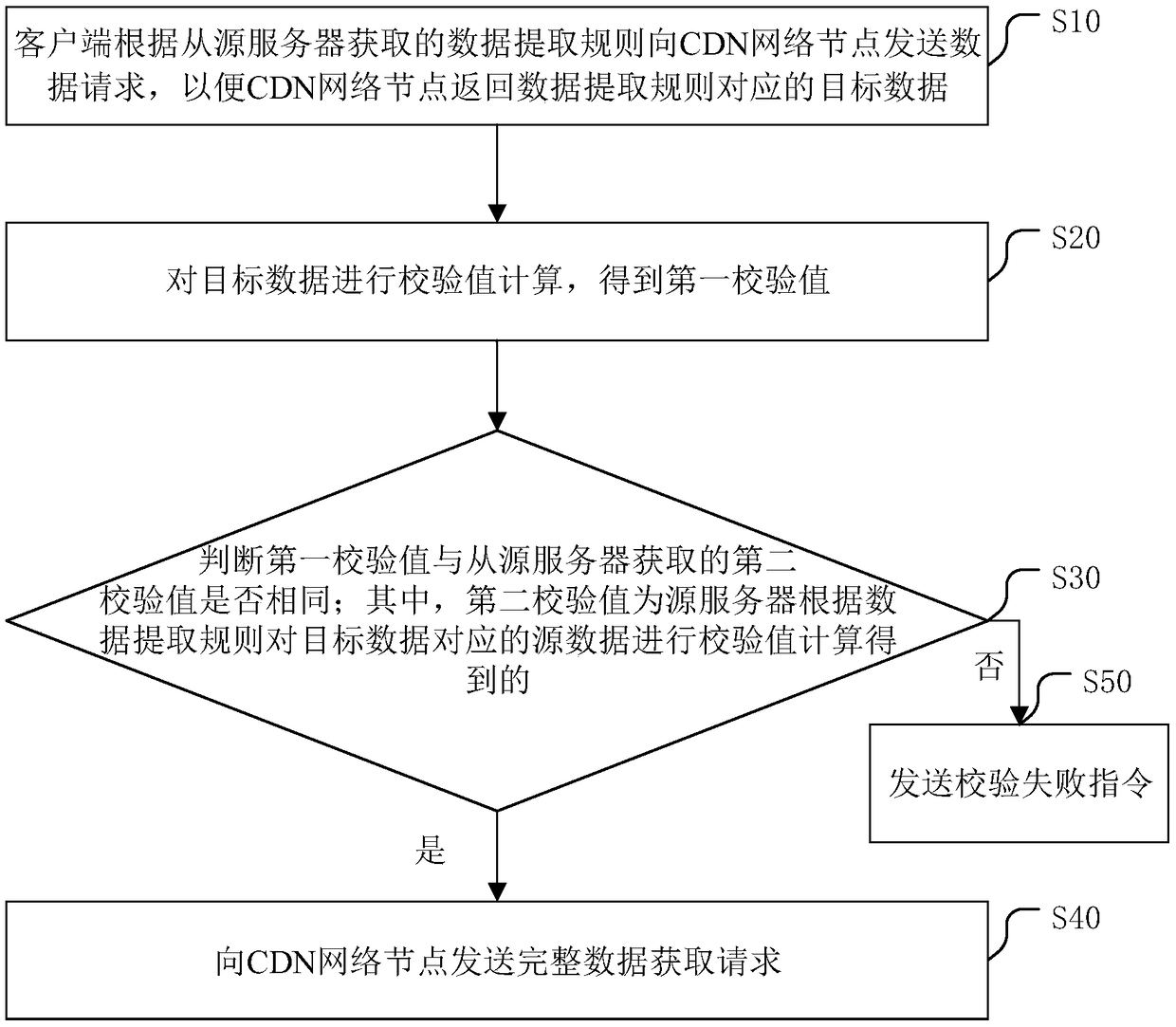
[0045] In a first embodiment, the method may include:
[0046] S10, the client sends a data request to the CDN network node according to the data extraction rule obtained from the source server, so that the CDN network node returns the target data corresponding to the data extraction rule;
[0047] In this step, the client first obtains the data extraction rules from the source server, receives the data extraction rules returned by the source server, and then sends data requests to the nodes of the CDN network and the index server according to the data extraction rules, so that the CDN network nodes can extract data according to the data extraction rules. The rule sends the target data to be extracted from the complete data to the client.
[0048]First, the application environment of this embodiment needs to be described, and this embodiment is mainly applied in a CDN (ContentDelivery Network) network. The process of downloading data before using the CDN network is that the s...
no. 3 example
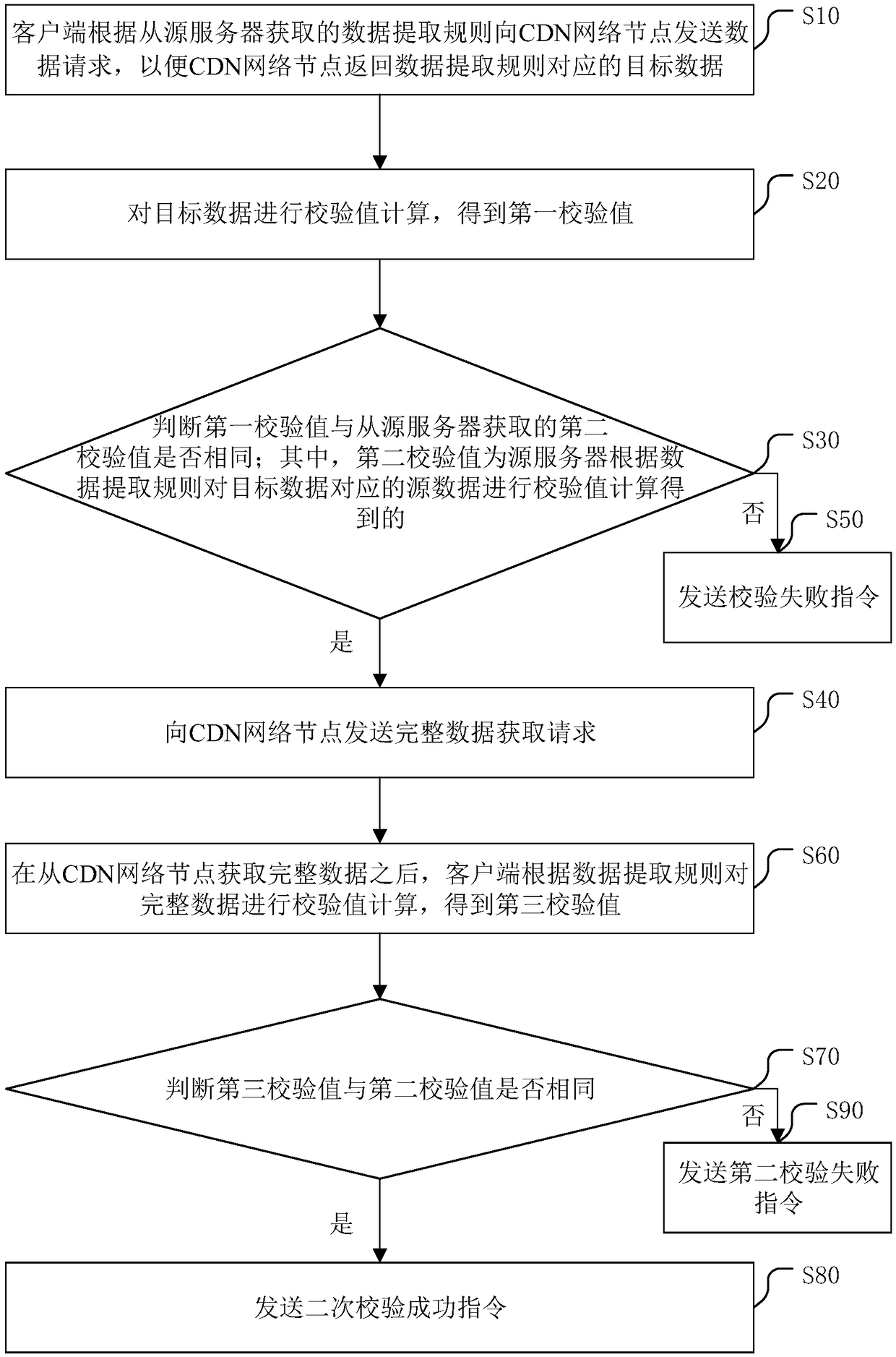
[0082] In a third embodiment, the method may include:
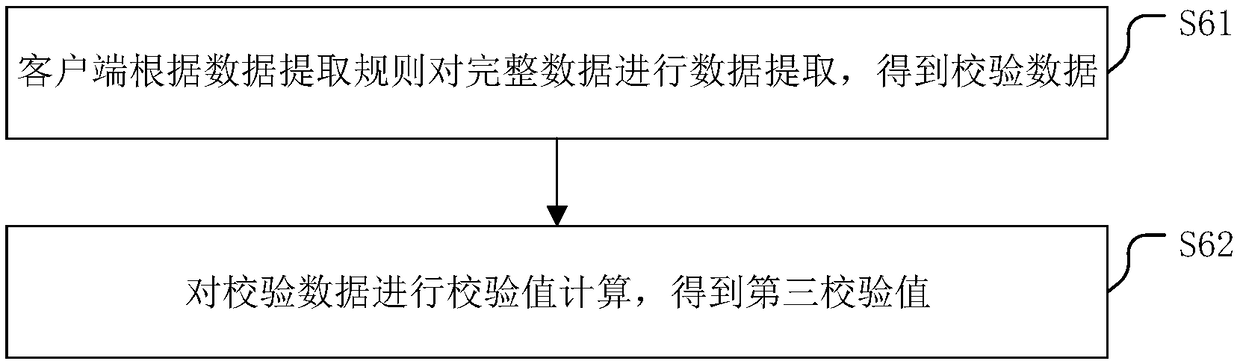
[0083] S61. The client performs data extraction on the complete data according to the data extraction rules to obtain verification data;
[0084] The purpose of this step is to perform data extraction on the complete data according to the data extraction rules to obtain verification data. In this step, the complete data is extracted according to the different data extraction rules. The data extraction rule can be to extract the data from the first address to a certain length of the complete data. For example, extract the data from the first address to 3MB ( MByte storage unit) position data; it can also determine multiple addresses in the complete data, and extract the data from each address to a certain length; it can also divide the complete data into multiple data, and extract each data The data of the preset length in; wherein, the complete data can be equally divided or not, and the preset length of the extracted da...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com