Method for protecting JAVA application programs in Android system
An application program and Android system technology, applied in the field of computer security, can solve the problems of software piracy, weak application software protection ability, restricting the development of the Android system software market, etc., and achieve the effect of preventing piracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
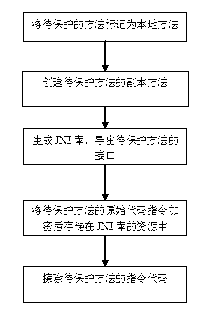
[0029] The specific implementation manner of the present invention is illustrated by examples below.
[0030] For example, to protect the common method M of the class ClassA (i.e., a functional unit that realizes a specific function), according to an embodiment of the present invention, the following steps are performed:
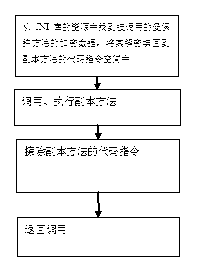
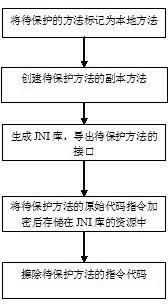
[0031] 1. Locate ClassA.M in the JAVA program file (source file). According to a specific embodiment of the present invention, the location is to first find the ClassA class, and then find the M method in ClassA. Locating by code form is ClassA test=new ClassA(); test.M method can be obtained. Change the method ClassA.M (i.e. the normal method M of the class ClassA to be protected) to a local method. Change the normal method to a native method through the keyword native, and it is a native method after the change.
[0032]2. Create a new common method M1 for class ClassA (M1 is the copy unit corresponding to the above functional unit M). According to an ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com