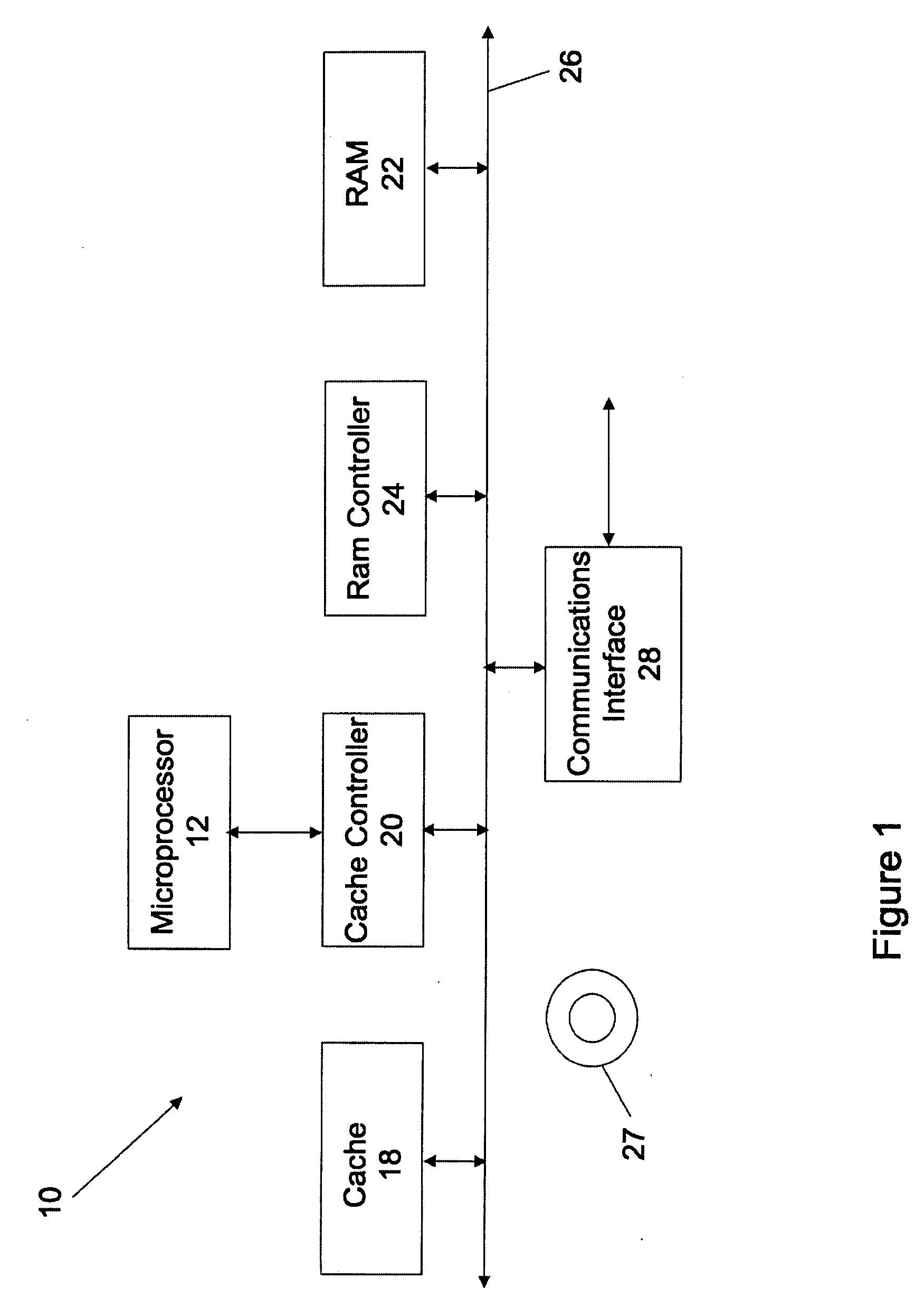
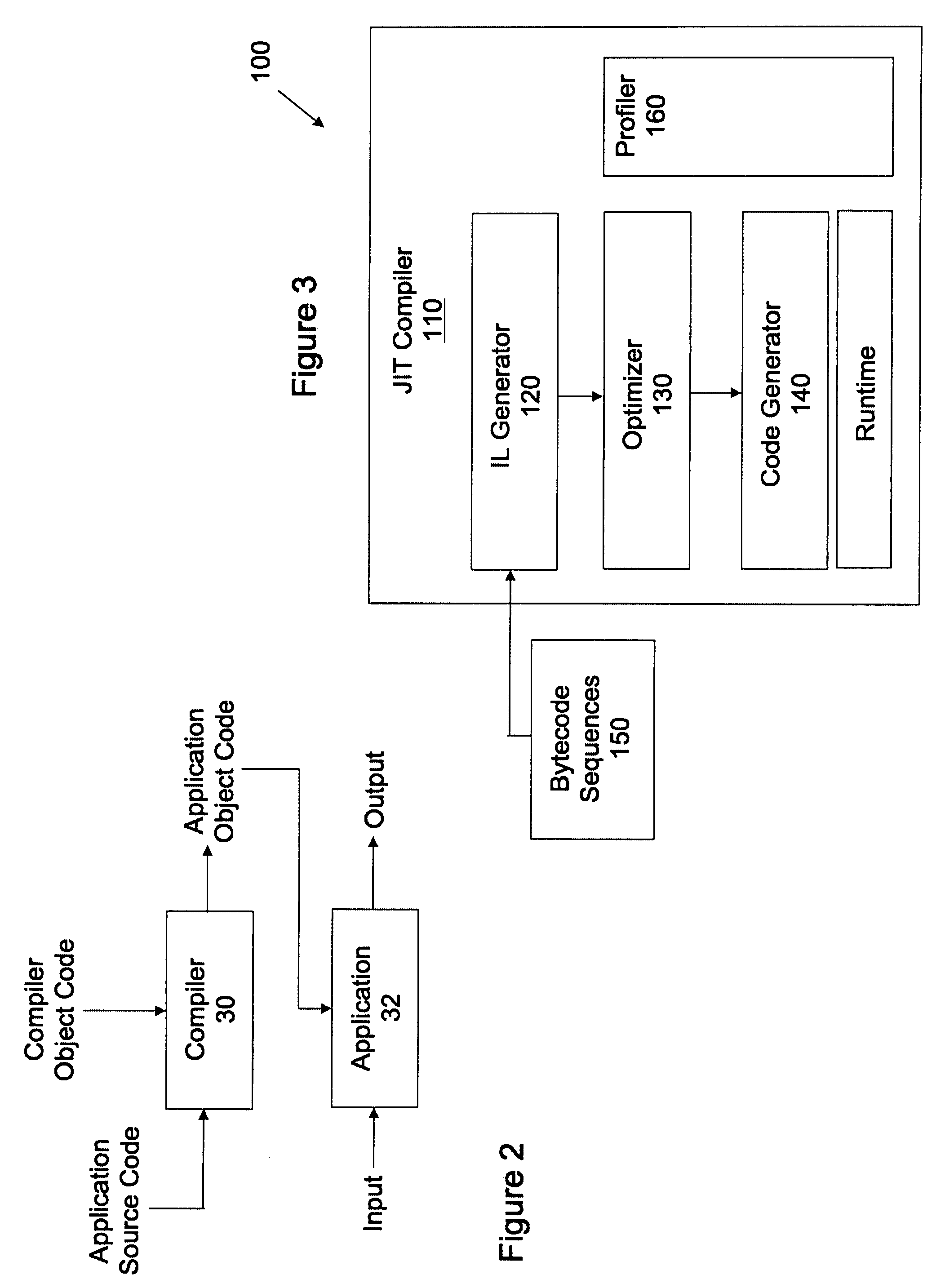
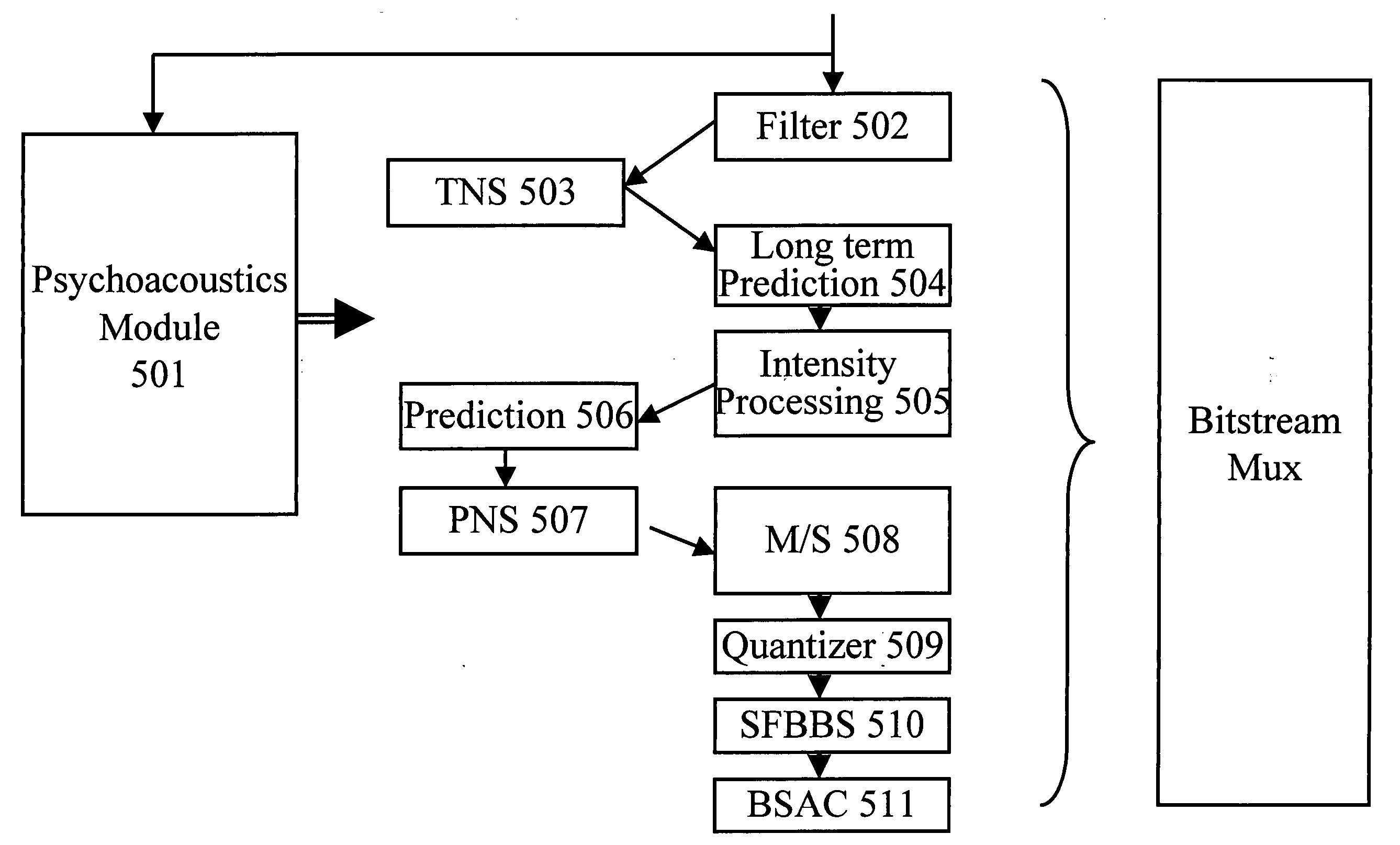
Patents
Literature
83 results about "Method Code" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
A coded value specifying a means, manner of procedure, or systematic course of actions that have to be performed in order to accomplish a particular goal.
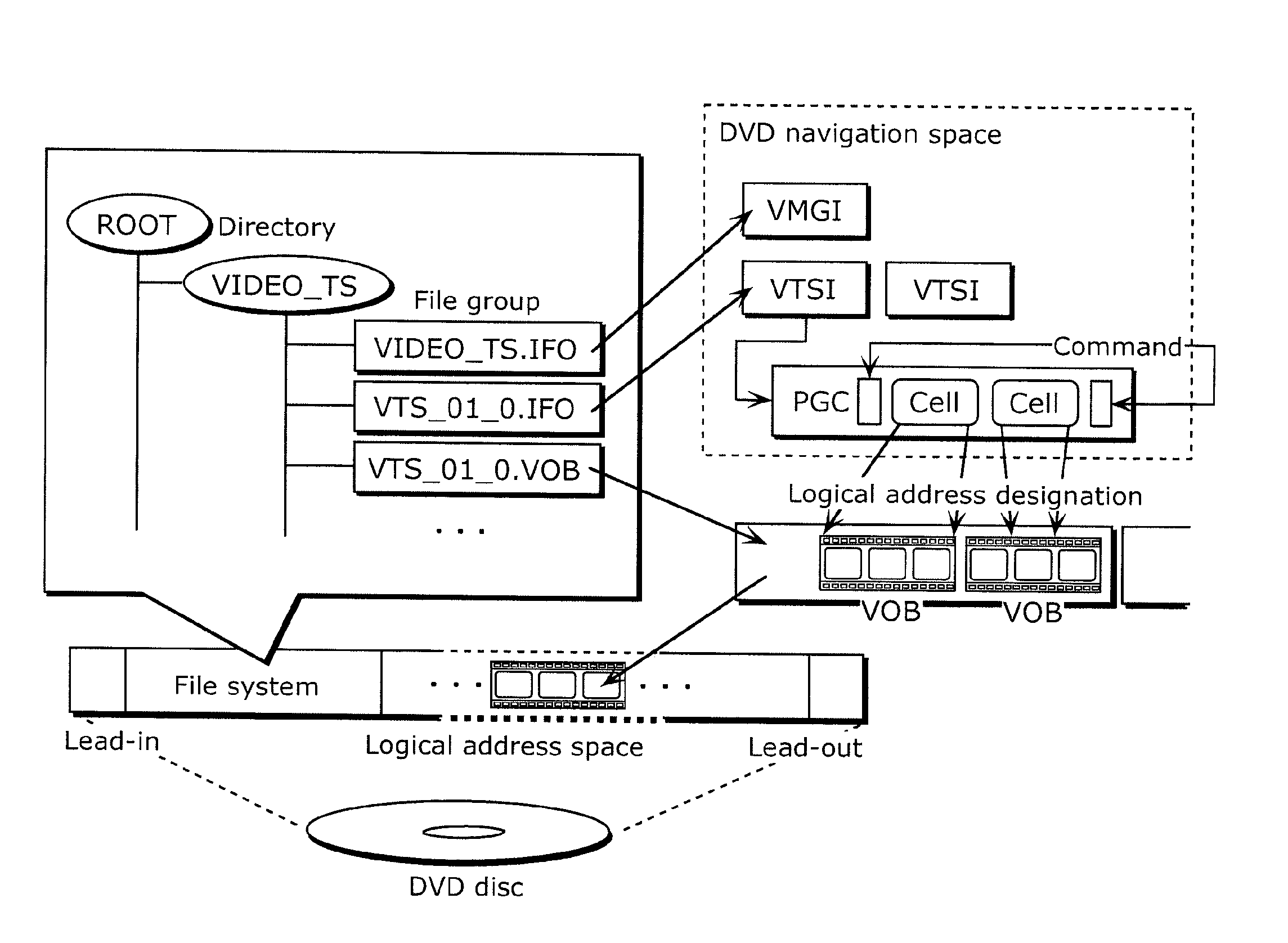
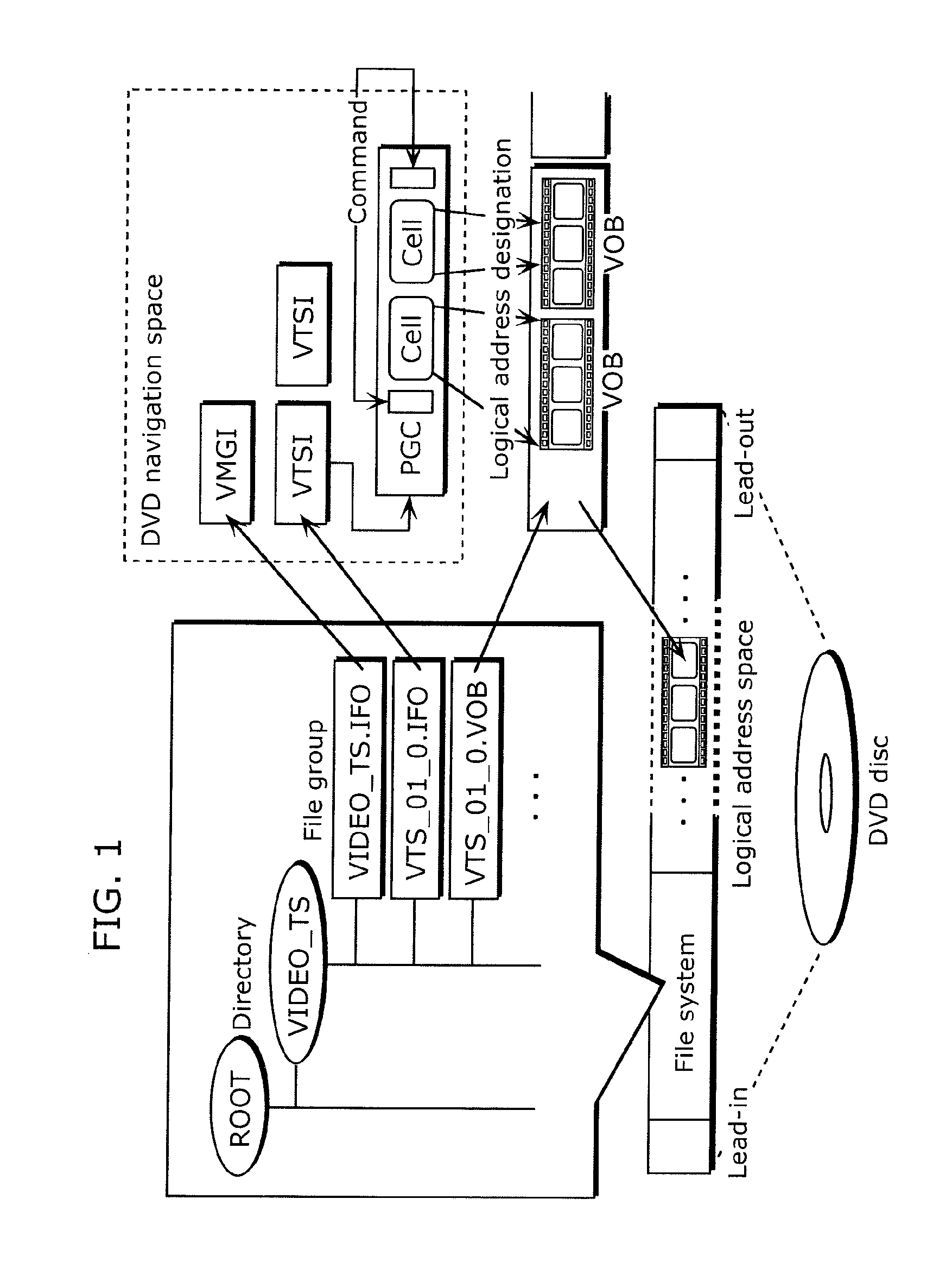
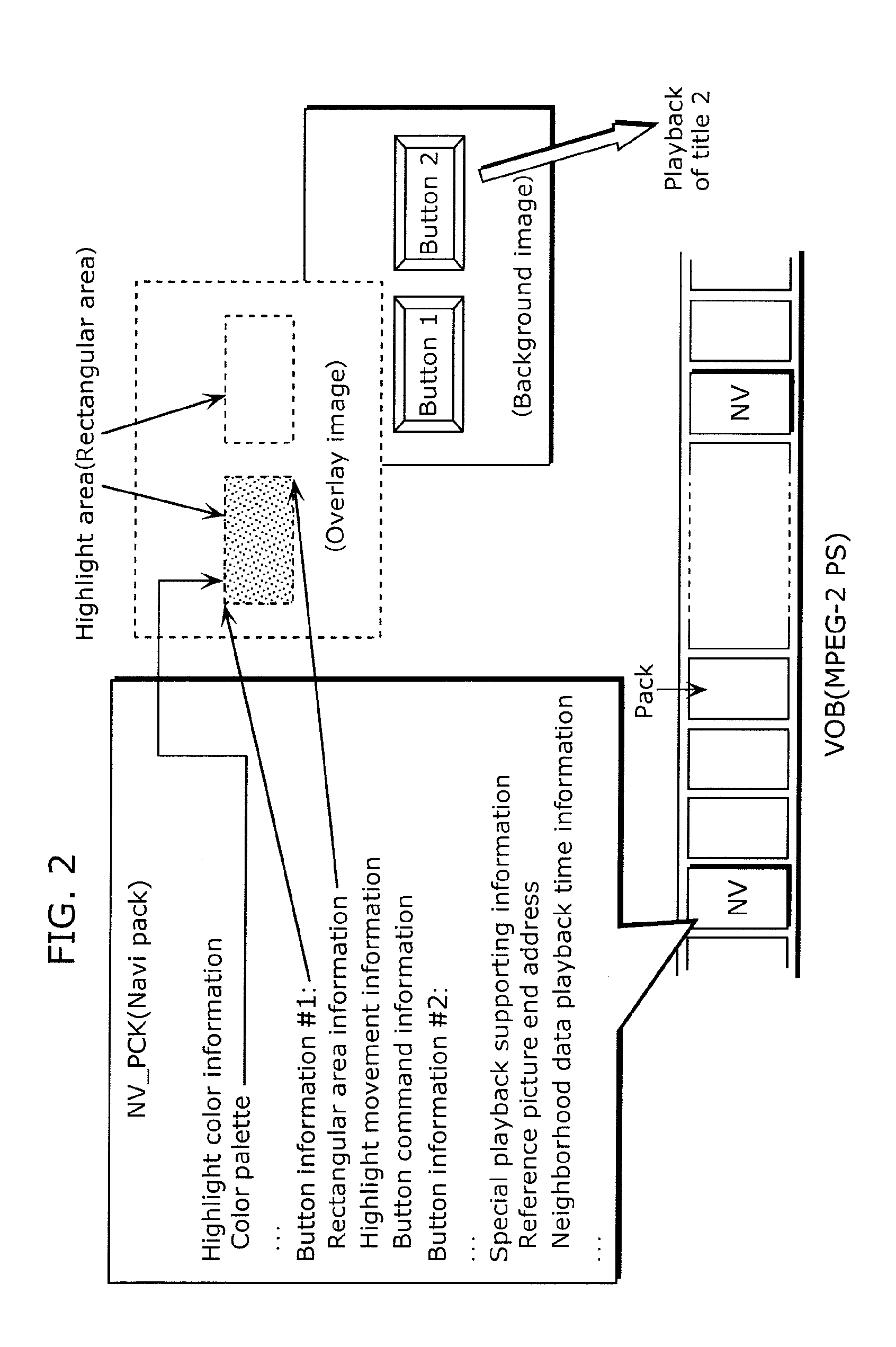
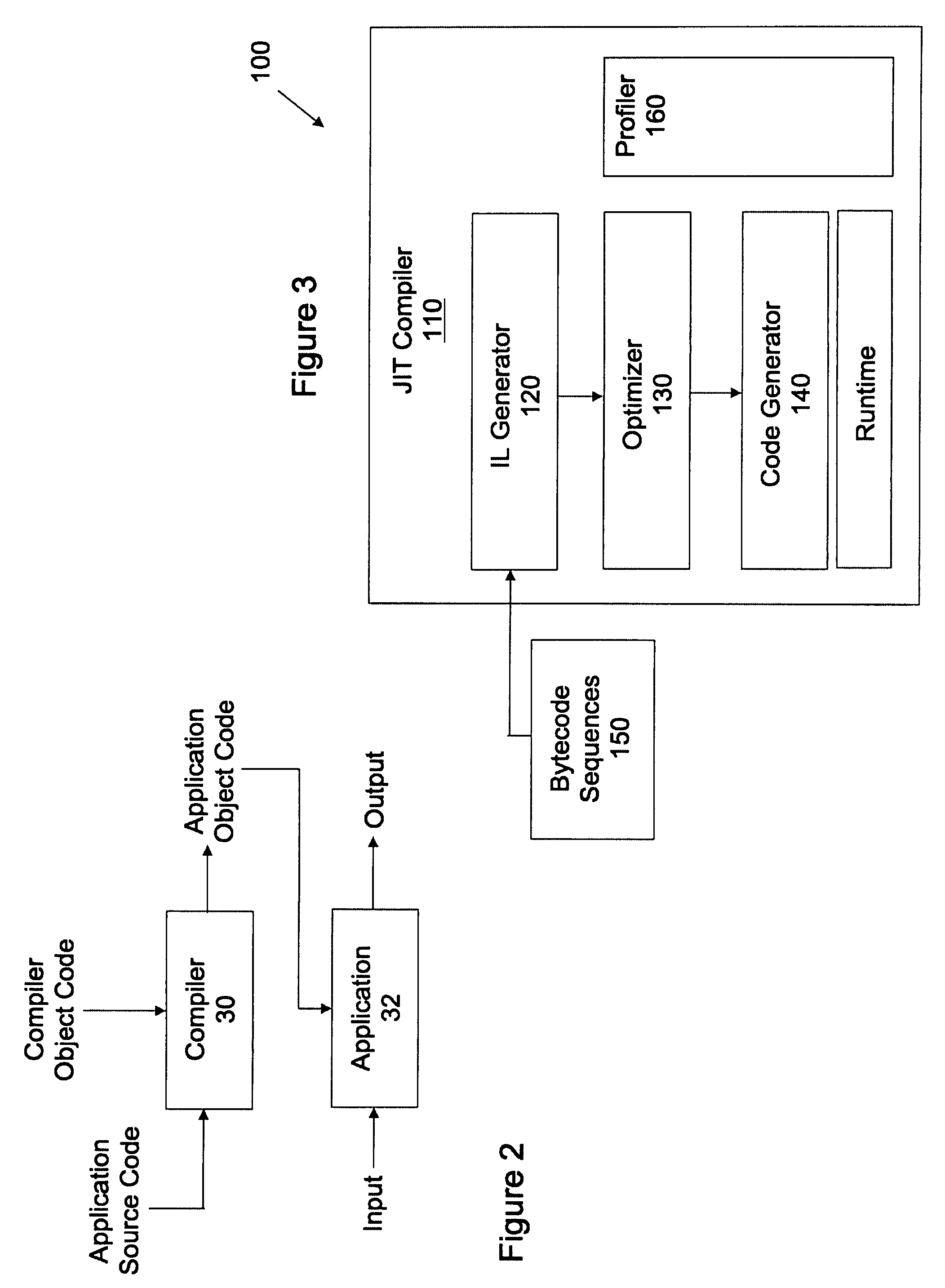
Moving image coding method, moving image coding device, moving image recording method, recording medium, moving image playback method, moving image playback device, and moving image playback system
ActiveUS20100040351A1Reduce processing loadImprove packaging qualityTelevision system detailsRecording carrier detailsComputer hardwareImage recording
A moving image coding method that can prevent playback discontinuity without an increase in processing load during playback is provided.The moving image coding method codes a video stream that includes a first moving image and a second moving image to be overlaid on the first moving image. The moving image coding method includes: a step of determining a continuous playback section that is a group of partial sections and is subject to continuous playback, in the video stream (S5301 to S5303); a step of coding the first and second moving images in the partial sections constituting the continuous playback section, under a constraint that prevents a threshold from being changed in the continuous playback section, the threshold being used for a transparency process by a luminance key in the overlaying (S5304); and a step of generating management information including flag information which indicates that the threshold is fixed in the continuous playback section (S5305).
Owner:PANASONIC CORP
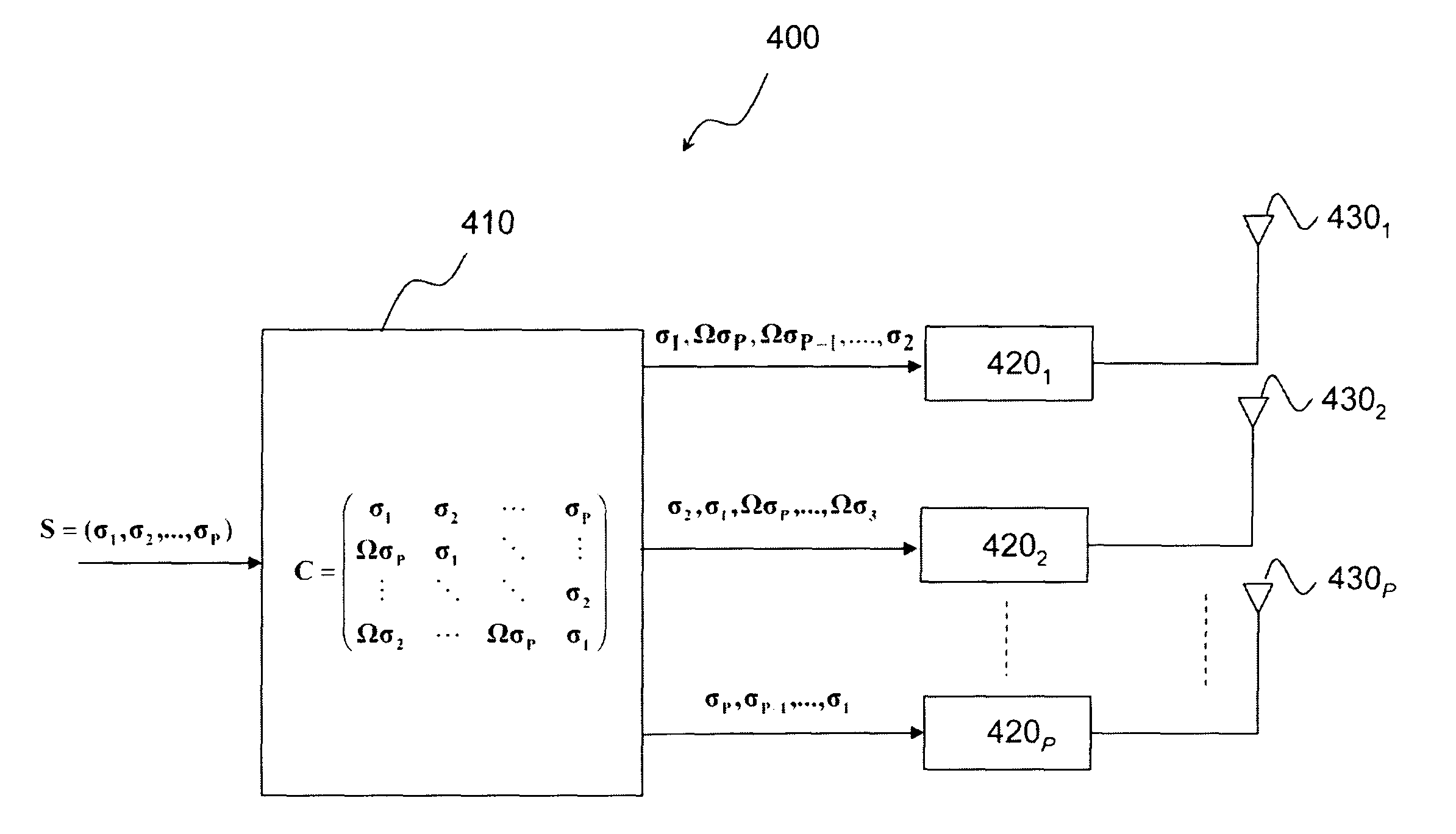
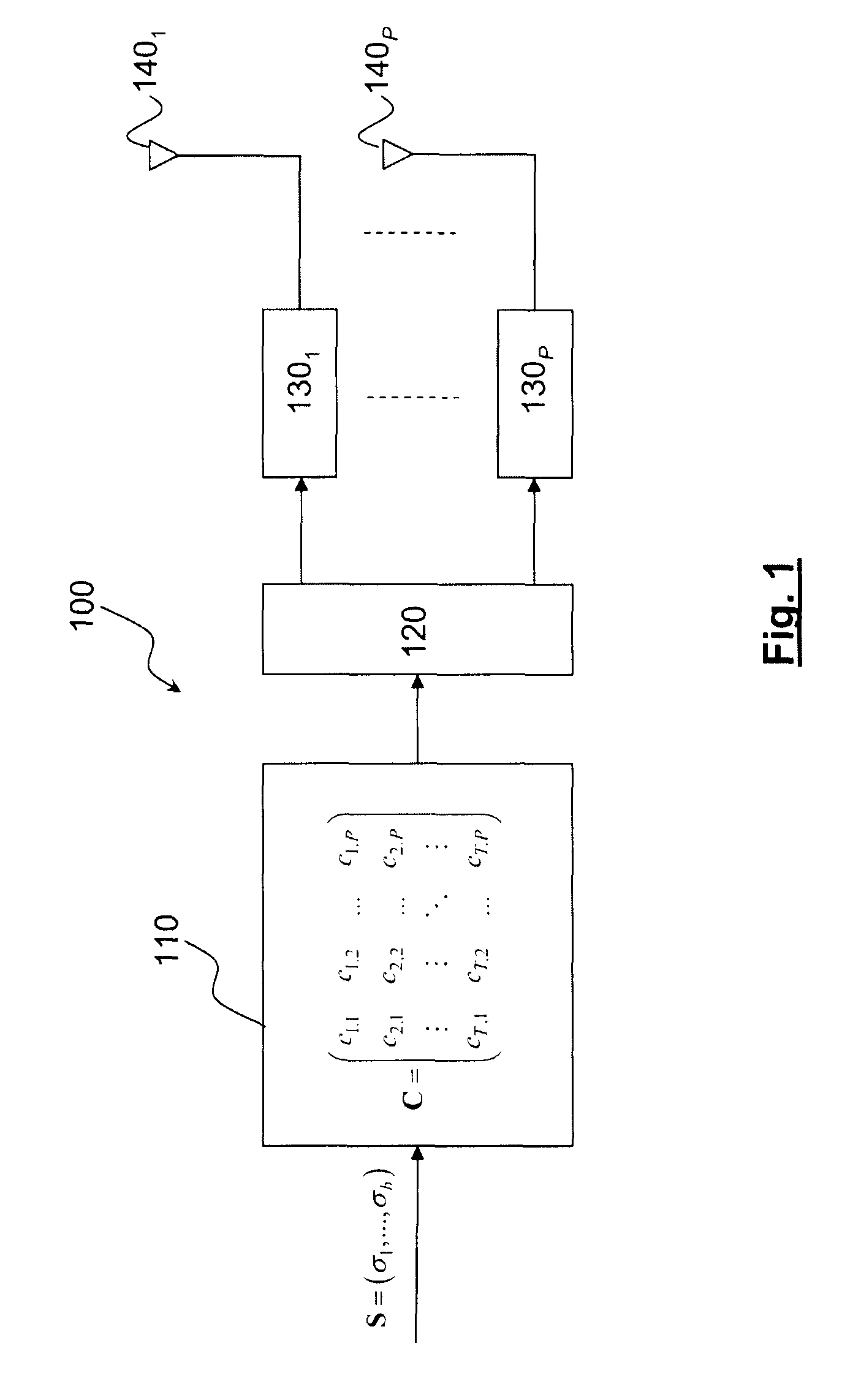
Method of space time coding with low papr for multiple antenna communication system of the UWB pulse type
InactiveUS8218670B2Polarisation/directional diversityFrequency/rate-modulated pulse demodulationCommunications systemTransmission channel
A method of space time coding for UWB transmission system including a plurality of radiative elements, the method coding a block of information symbols S=(σ1, σ2, . . . , σP) belonging to a M-PPM-M′-PAM modulation alphabet, as a sequence of vectors obtained from elements of the matrix:C=(σ1σ2…σPΩσPσ1⋱⋮⋮⋱⋱σ2Ωσ2…ΩσPσ1)a row of the matrix corresponding to a use of the transmission channel and a column of the matrix corresponding to a radiative element, the matrix C being defined to within a permutation of its rows and / or its columns and Ω being defined as the combination of a permutation (ω) of the modulation positions of the M-PPM alphabet and a symmetry operation (π) of the M′-PAM modulation alphabet for one of the modulation positions (m±).
Owner:COMMISSARIAT A LENERGIE ATOMIQUE ET AUX ENERGIES ALTERNATIVES
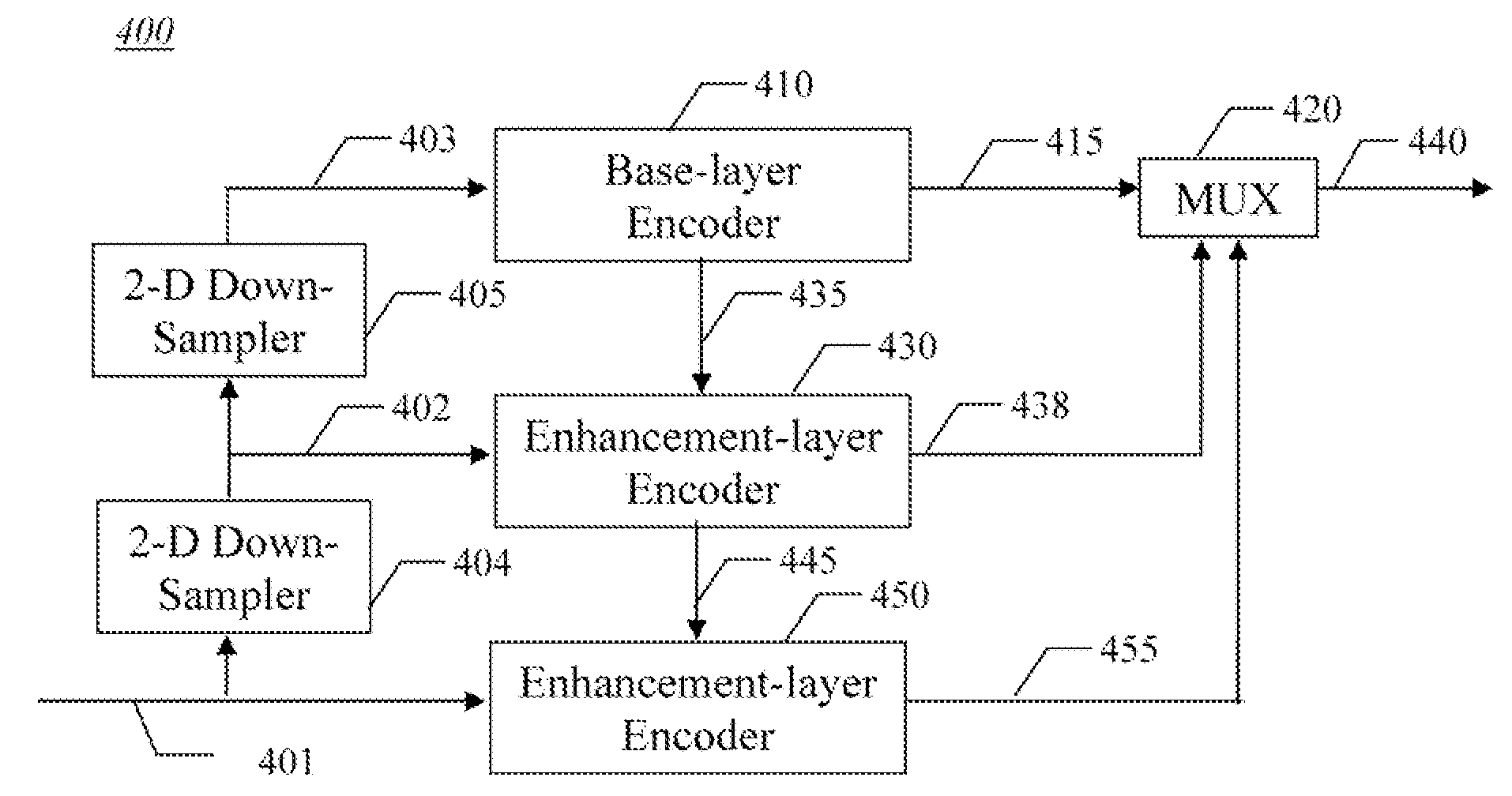
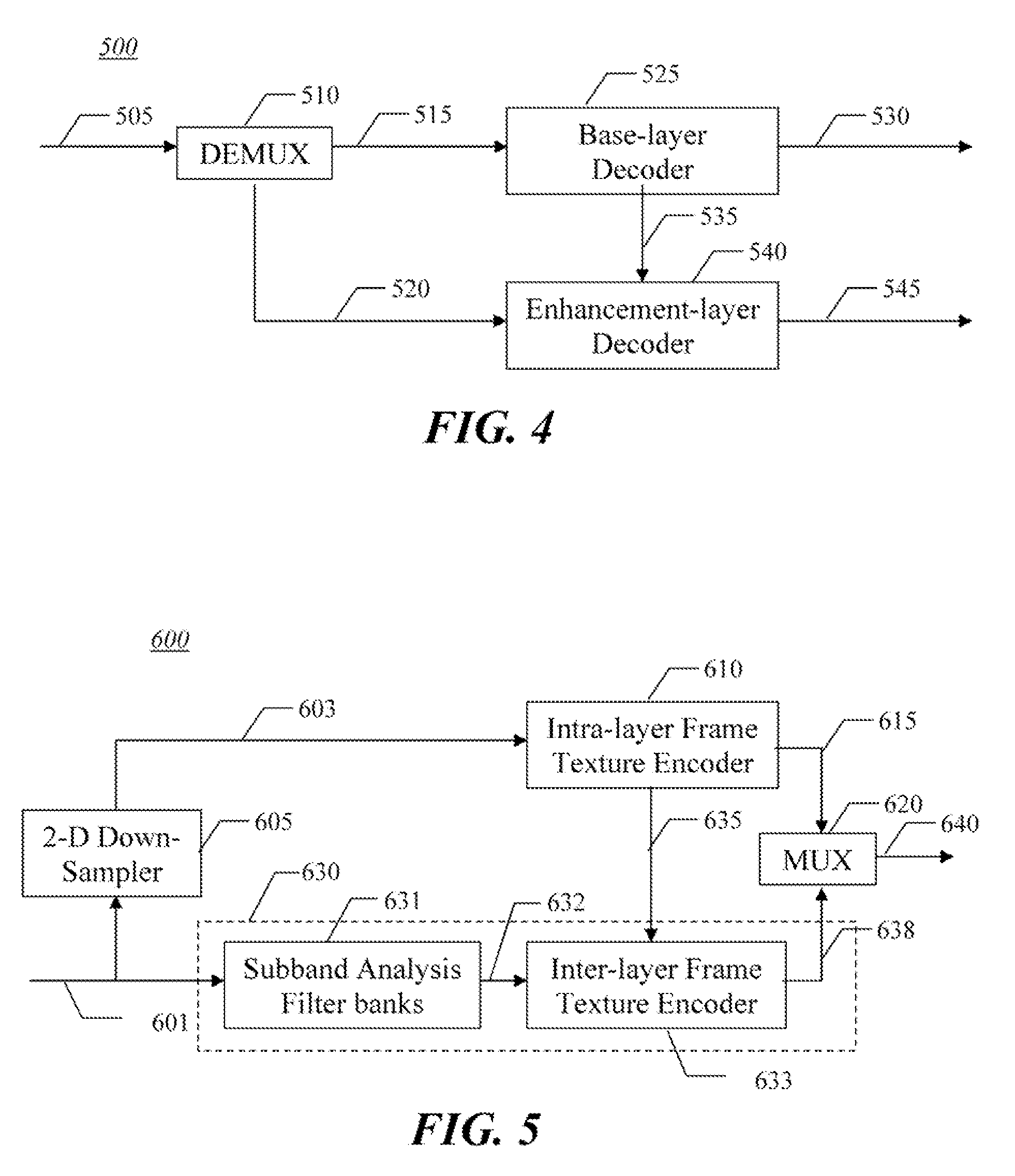
Method and apparatus for intra-frame spatial scalable video coding
InactiveUS20080095235A1Color television with pulse code modulationColor television with bandwidth reductionVideo bitstreamVideo encoding
An apparatus and method are for intra-frame spatial scalable video encoding. The method codes a low resolution base layer video bitstream from low resolution base layer video using a single layer encoder, and codes an enhancement layer in which individual videos frames are represented by wavelet coefficients for an LL residual sub-band, an HL sub-band, an LH sub-band; and an HH sub-band. The LL residual sub-band is generated as a difference of an LL sub-band and a recovered version of the base layer video bitstream.
Owner:MOTOROLA MOBILITY LLC
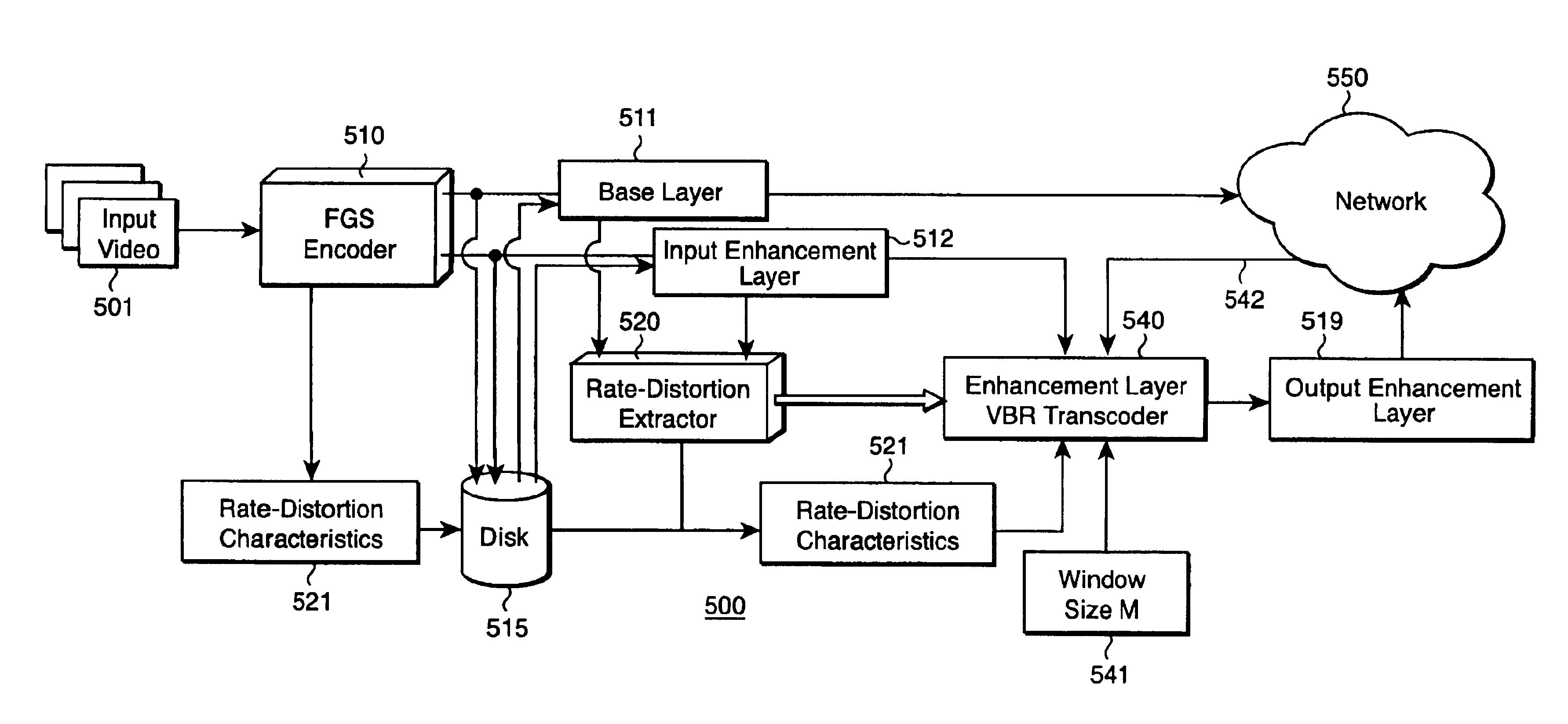
Transcoder for scalable multi-layer constant quality video bitstreams
InactiveUS6925120B2Minimize changesOptimal rate allocationPulse modulation television signal transmissionPicture reproducers using cathode ray tubesVideo bitstreamInput enhancement
A method codes an output bitstream of an input video so the decoded output bitstream has a constant perceived quality. A base layer bitstream having a constant bit-rate is generated from the input video, and an input enhancement layer bitstream is generated from a difference between the input video and the base layer bitstream. Rate and distortion characteristics are extracted from the base layer bitstream and the input enhancement layer bitstream, and an output enhancement layer bitstream having a variable bit-rate is generated from the input enhancement layer bitstream according to the rate and distortion characteristics. The base layer bitstream and the output enhancement layer bitstream, in combination, form an output bitstream having a variable bit-rate and a constant distortion.
Owner:MITSUBISHI ELECTRIC RES LAB INC
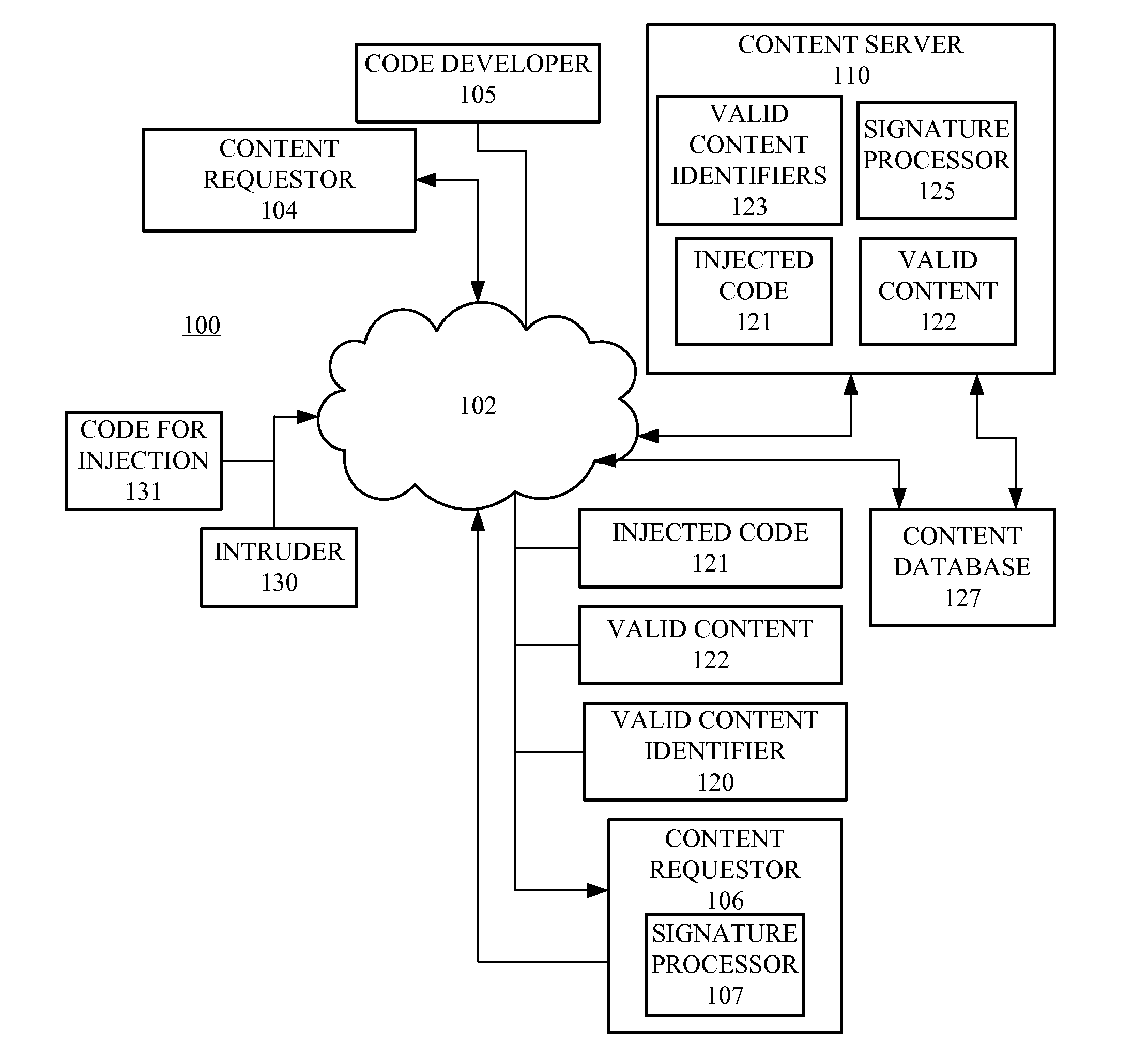
Detecting code injections through cryptographic methods
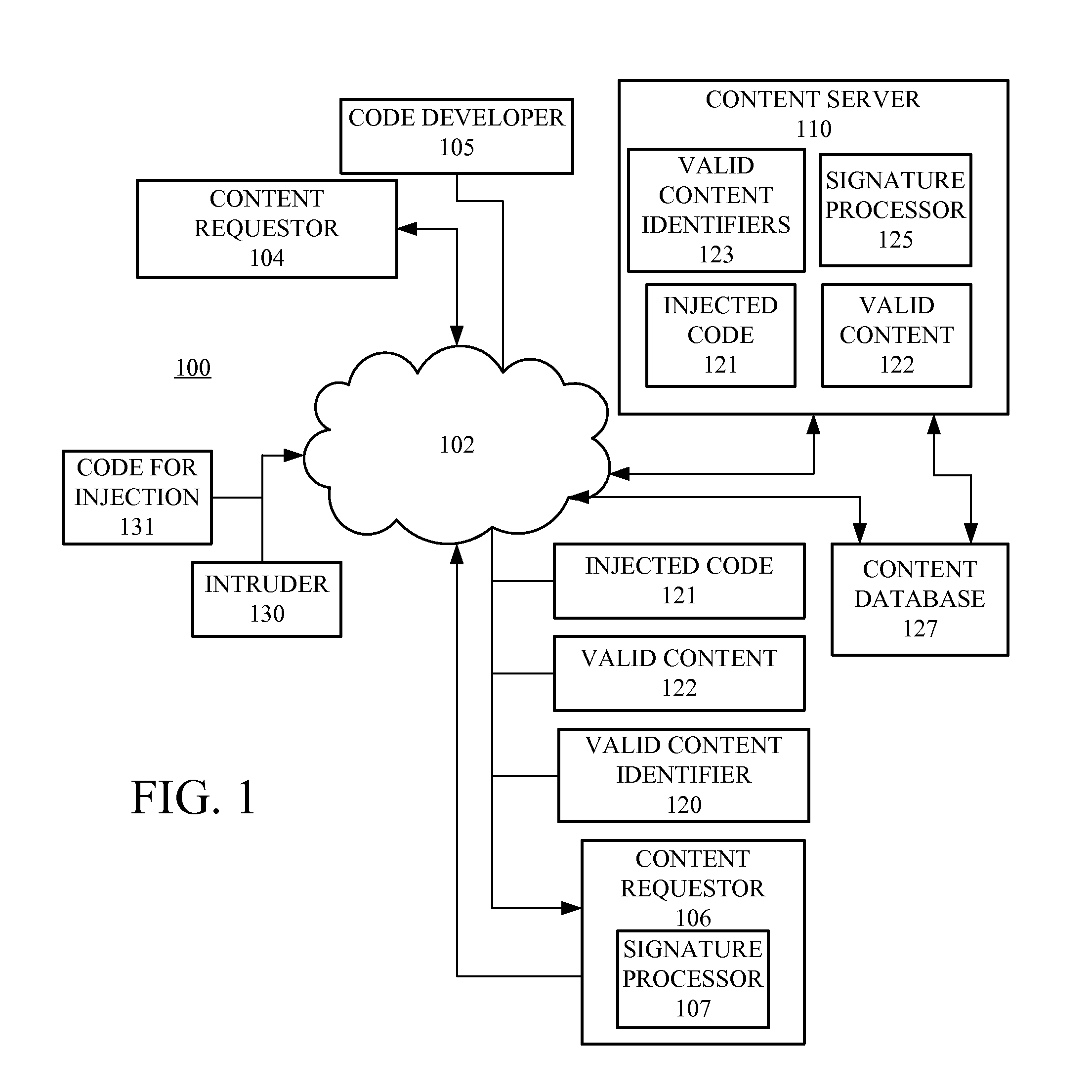
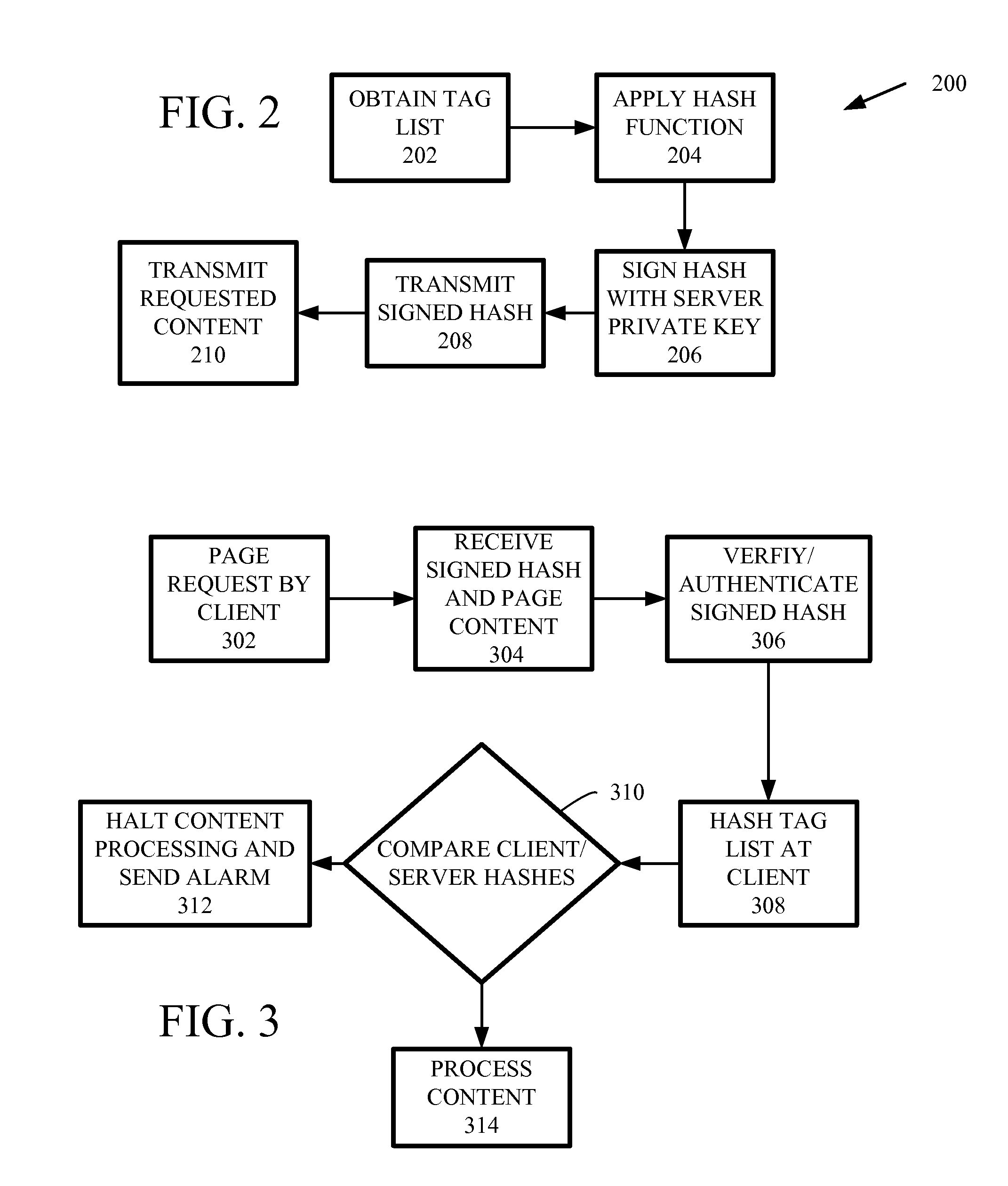
ActiveUS20120255027A1Digital data processing detailsAnalogue secracy/subscription systemsComputer hardwareCode injection
Code injection is detected based on code digests associated with hashes of selected portions of content supplied to clients by a server. A client receives the content and generates a corresponding code digest, and based upon a comparison with the code digest received from the server, determines if the received content has been corrupted. The code digest can be signed or supplied with a digital certification for verification that the code digest originated from the server providing the content.
Owner:INFOSYS LTD
Synchronization detection device and its method
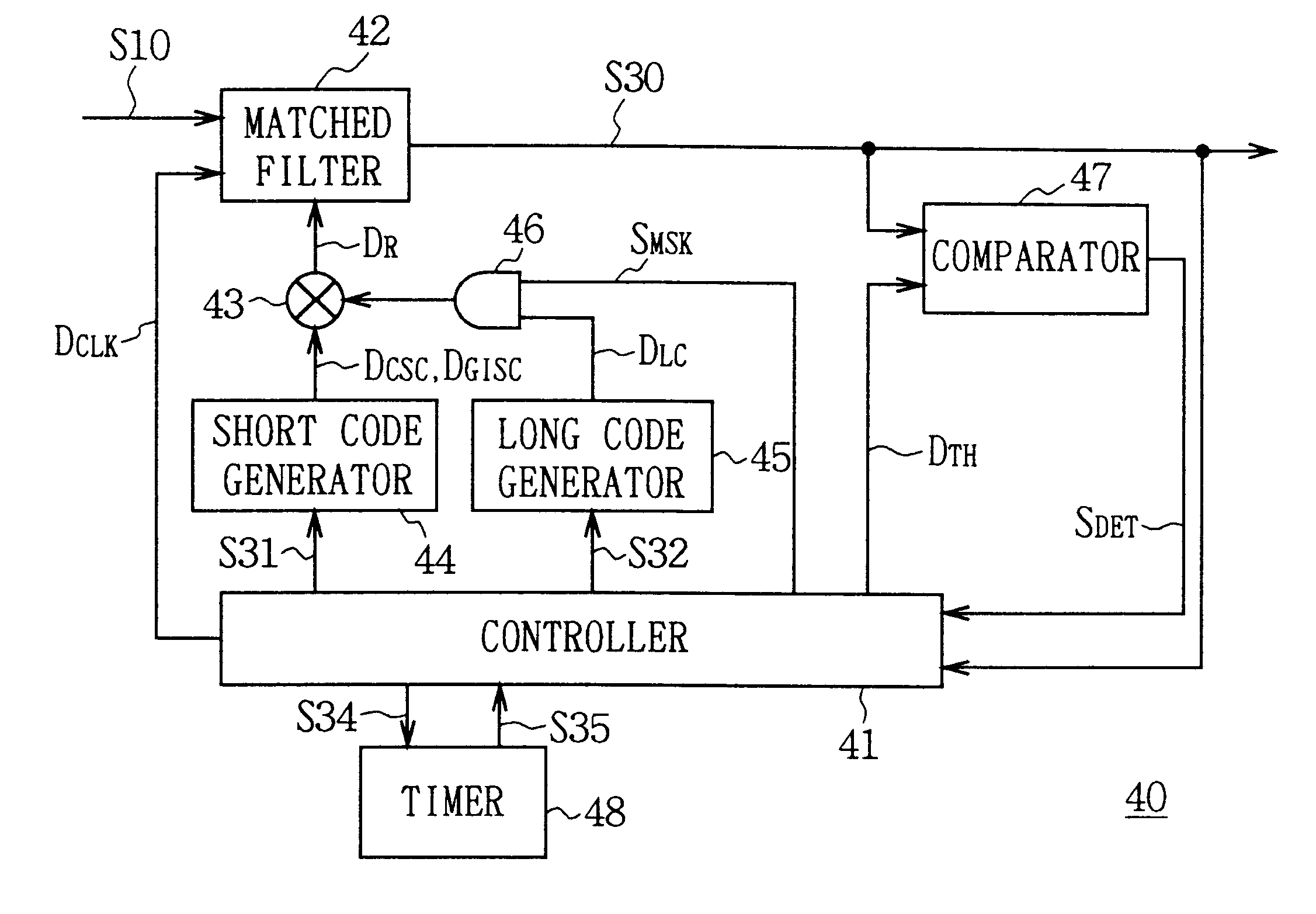
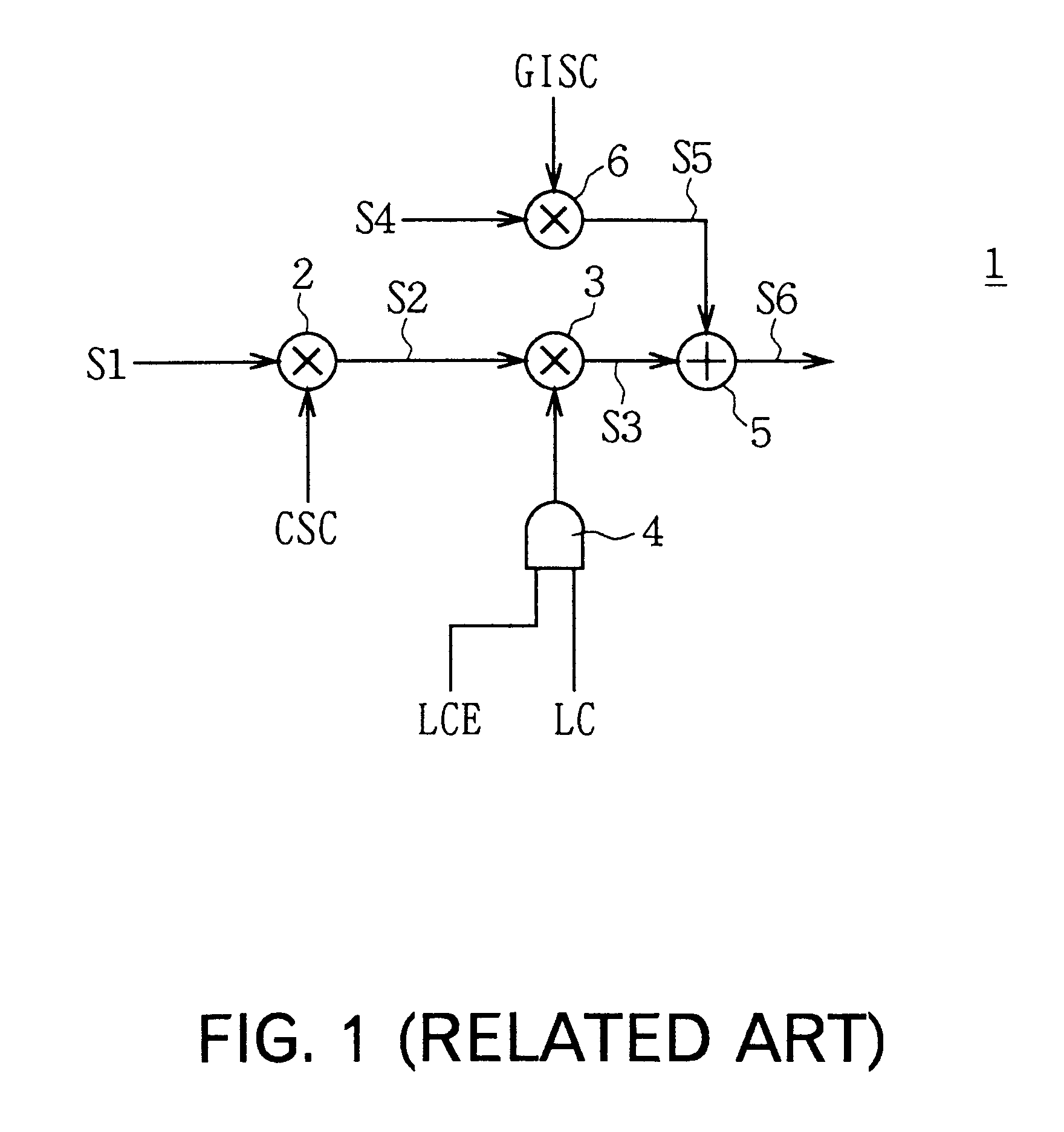
InactiveUS6385232B1Synchronisation arrangementTime-division multiplexCorrelation coefficientSynchronous detection
Codes to be detected can be identified at high speed. The supply of the data shift clock (DCLK1) to be given to the matched filter (82) is stopped at desired timing to hold the received signal (S10) and replica code generated at the correlation coefficient generator (83) is switched to the first, second or third replica code at desired timing to detect the correlation value of that time. Thereby, the second code, the third code and the first code are detected in order to detect the timing and the code type of the first code. Therefore, each correlation detection can be conducted at the same timing since the matched filter conducts the correlation detection at high speed holding the received signal and thus, the first code included in the received signal can be identified at higher speed than before.
Owner:SONY CORP
Reinforcement protection method, sever and system for android app
ActiveCN104462959AReduce reverse analysisAvoid gettingPlatform integrity maintainanceProgram controlReverse analysisAndroid app
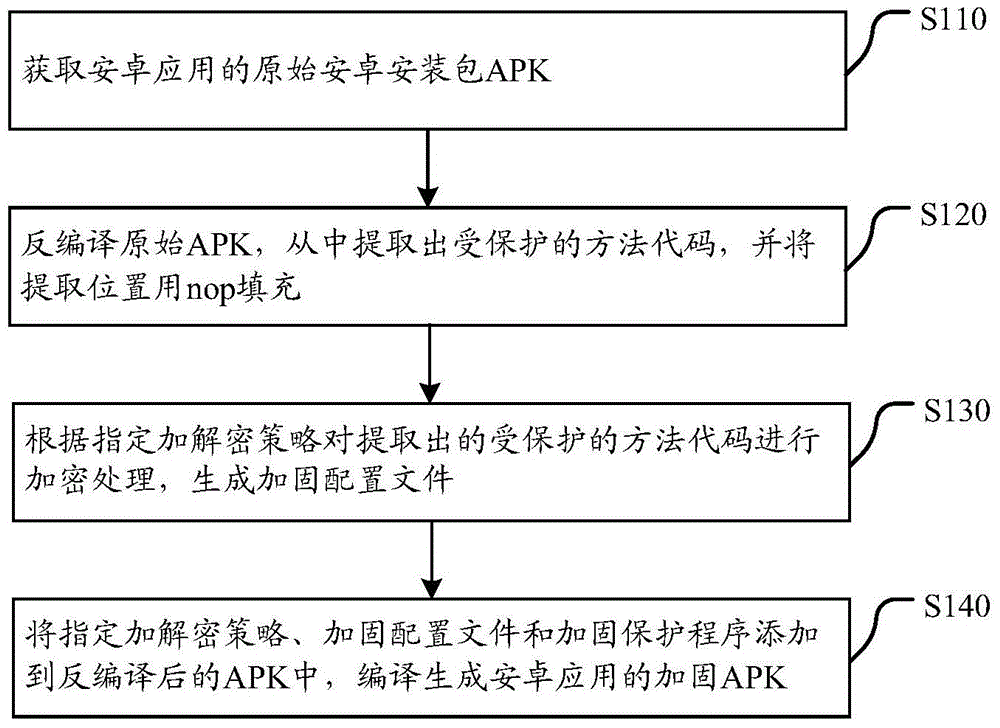
The invention discloses a reinforcement protection method, sever and system for android app. The method comprises the following steps: obtaining an initial android package APK of the android app; decompiling the initial APK, extracting protected method codes from the initial APK, and filling an extraction position with nop; encrypting the extracted protected method codes according to an appointed encryption and decryption strategy to generate a reinforcement configuration file; adding the appointed encryption and decryption strategy, the reinforcement configuration file and a reinforcement protection program into the decompiled APK, and compiling to generate a reinforcement APK of the android app. According to the technical scheme provided by the invention, protected methods can be dynamically encrypted and decrypted, and complete dex mapping does not exist in a memory at any moment, so that a complete dex file is prevented from being obtained in a memory dump manner and the probability of repacking and redistribution of the android app due to reverse analysis is greatly reduced.
Owner:BEIJING QIHOO TECH CO LTD
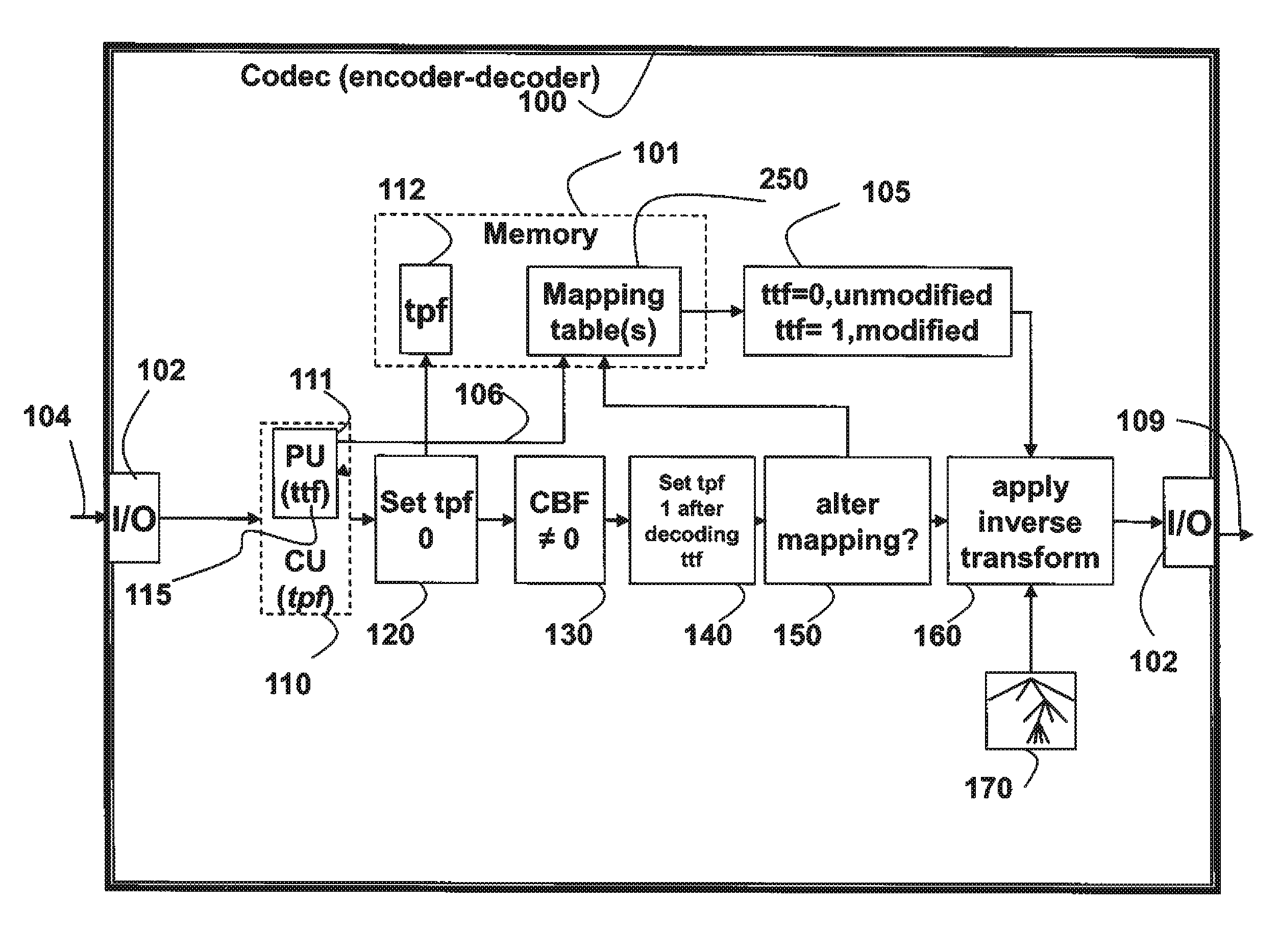
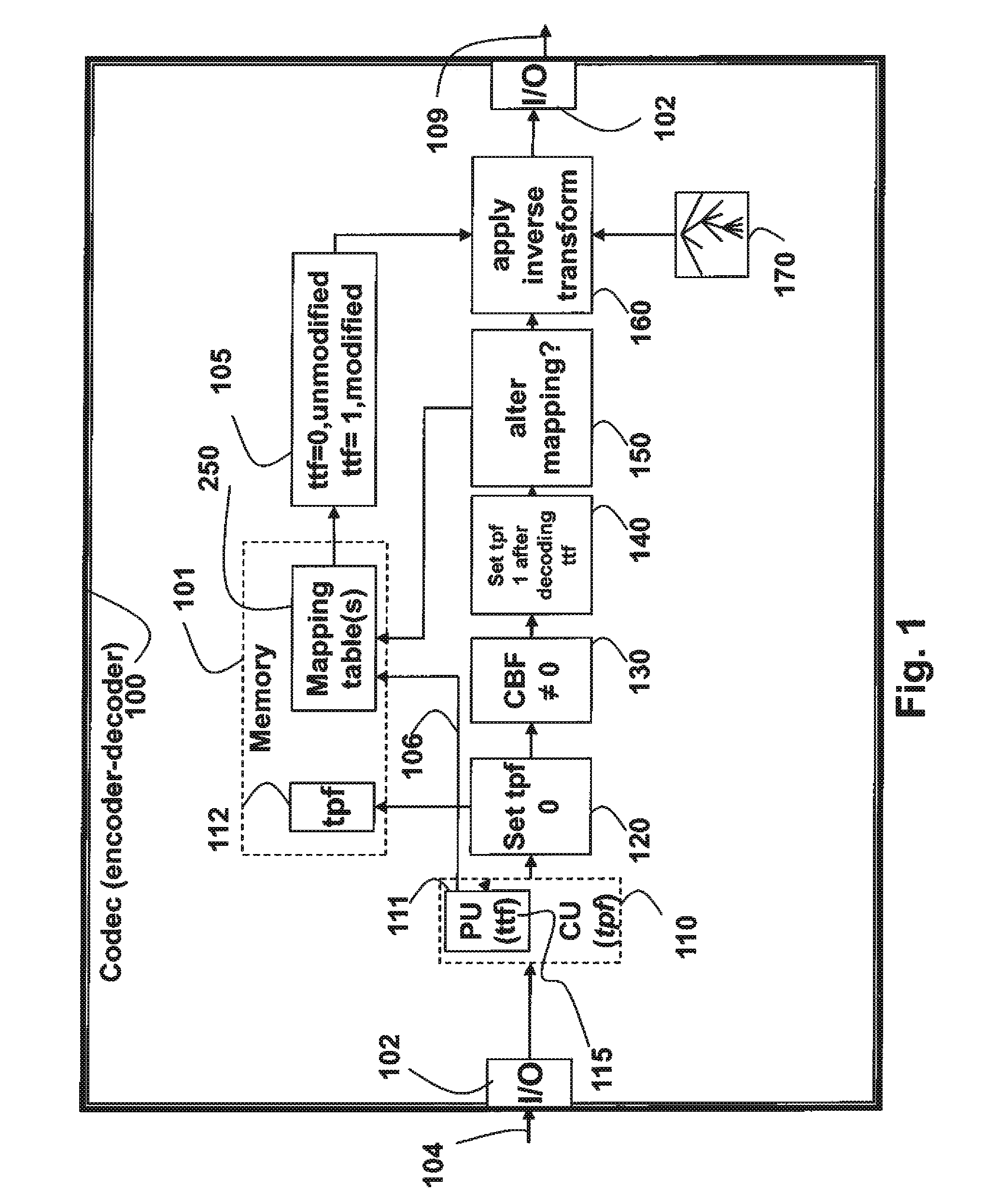
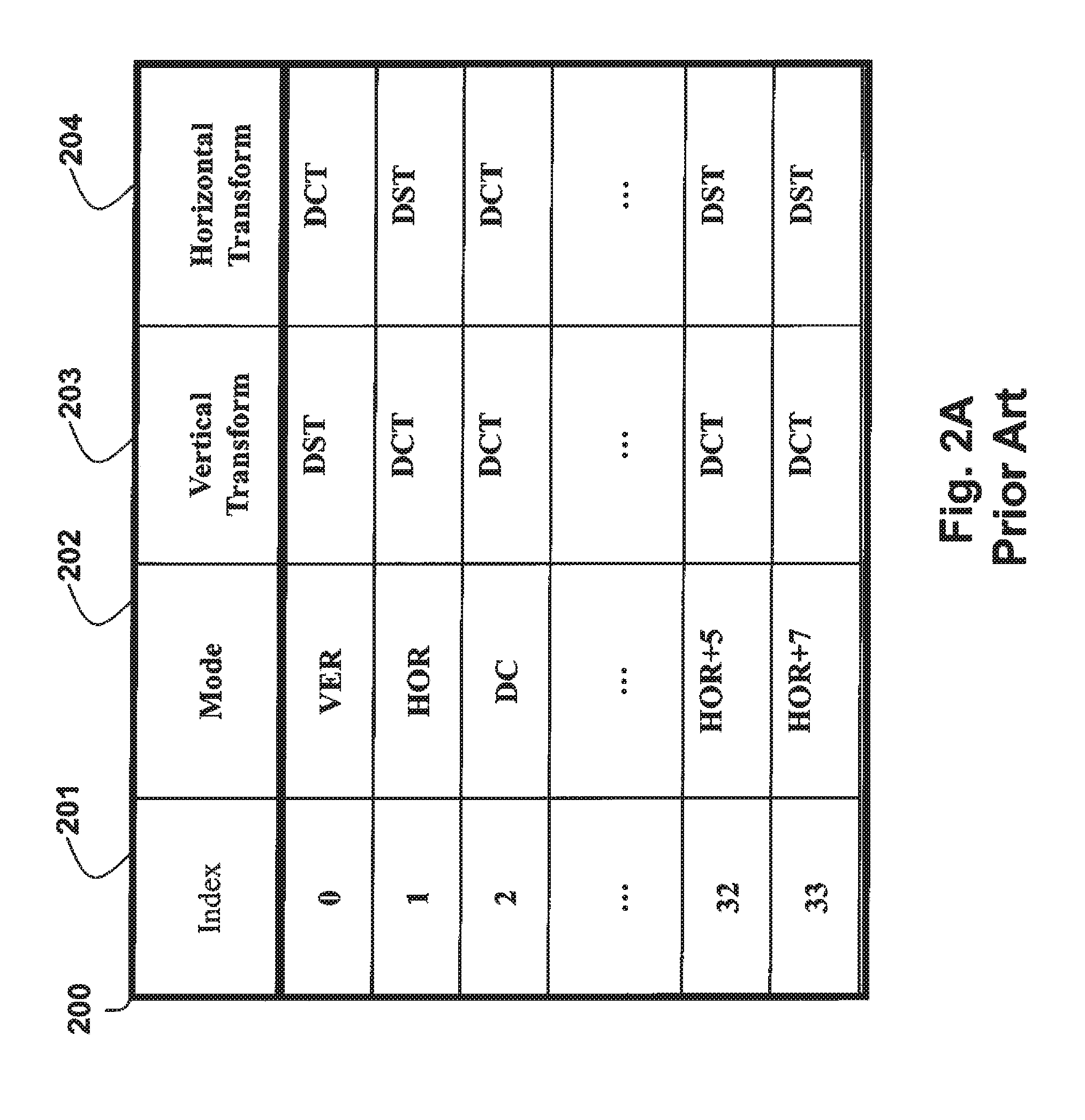
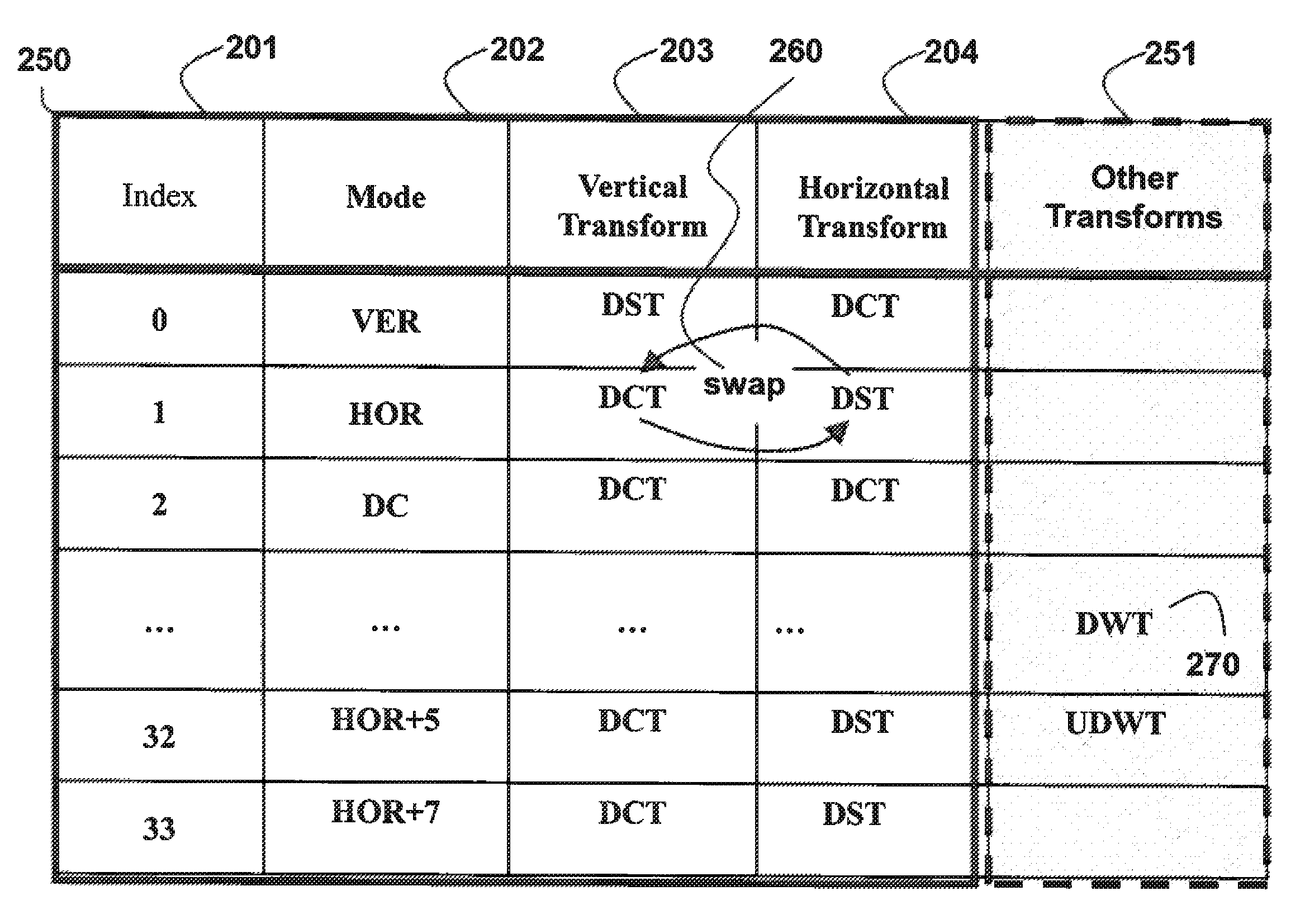
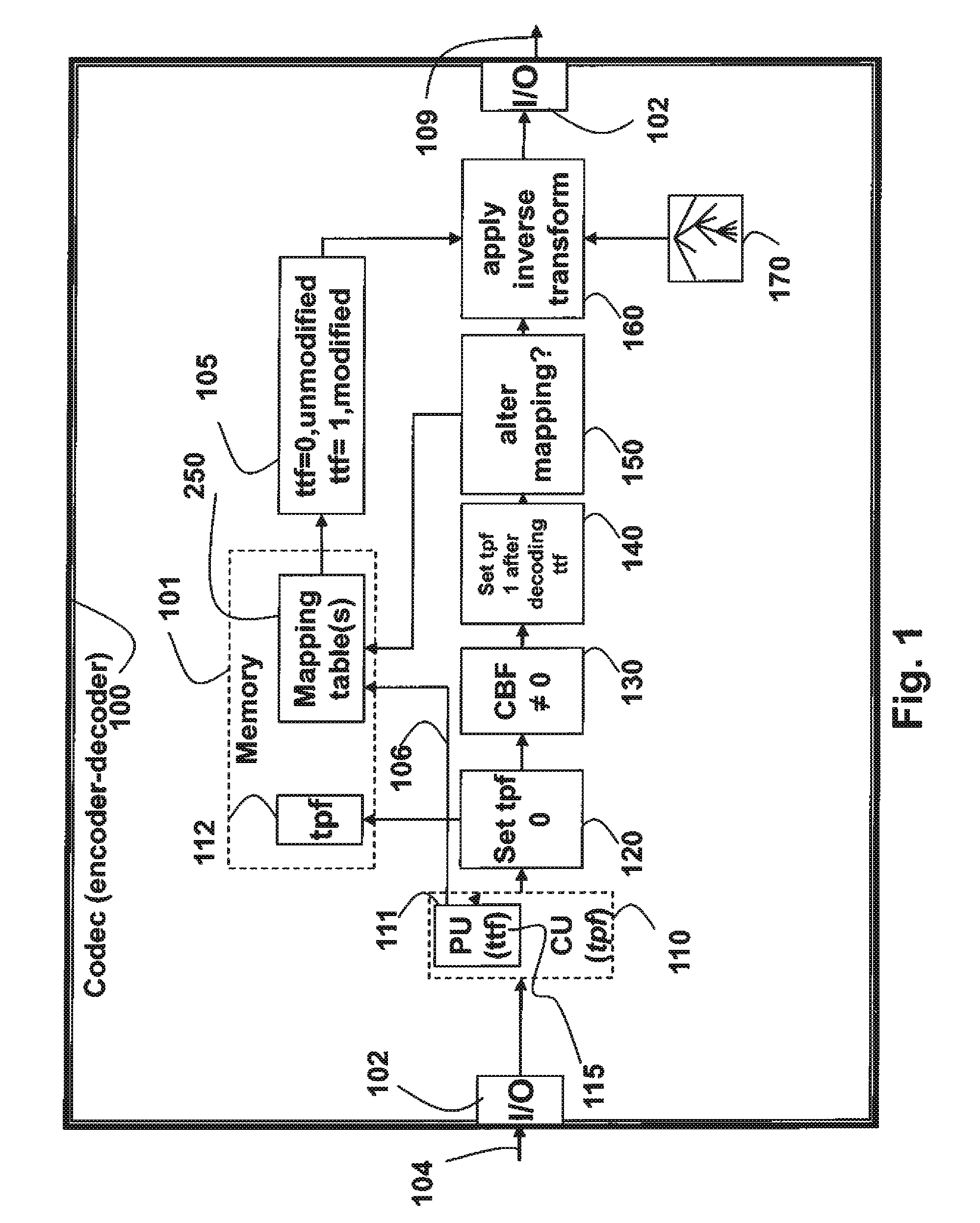
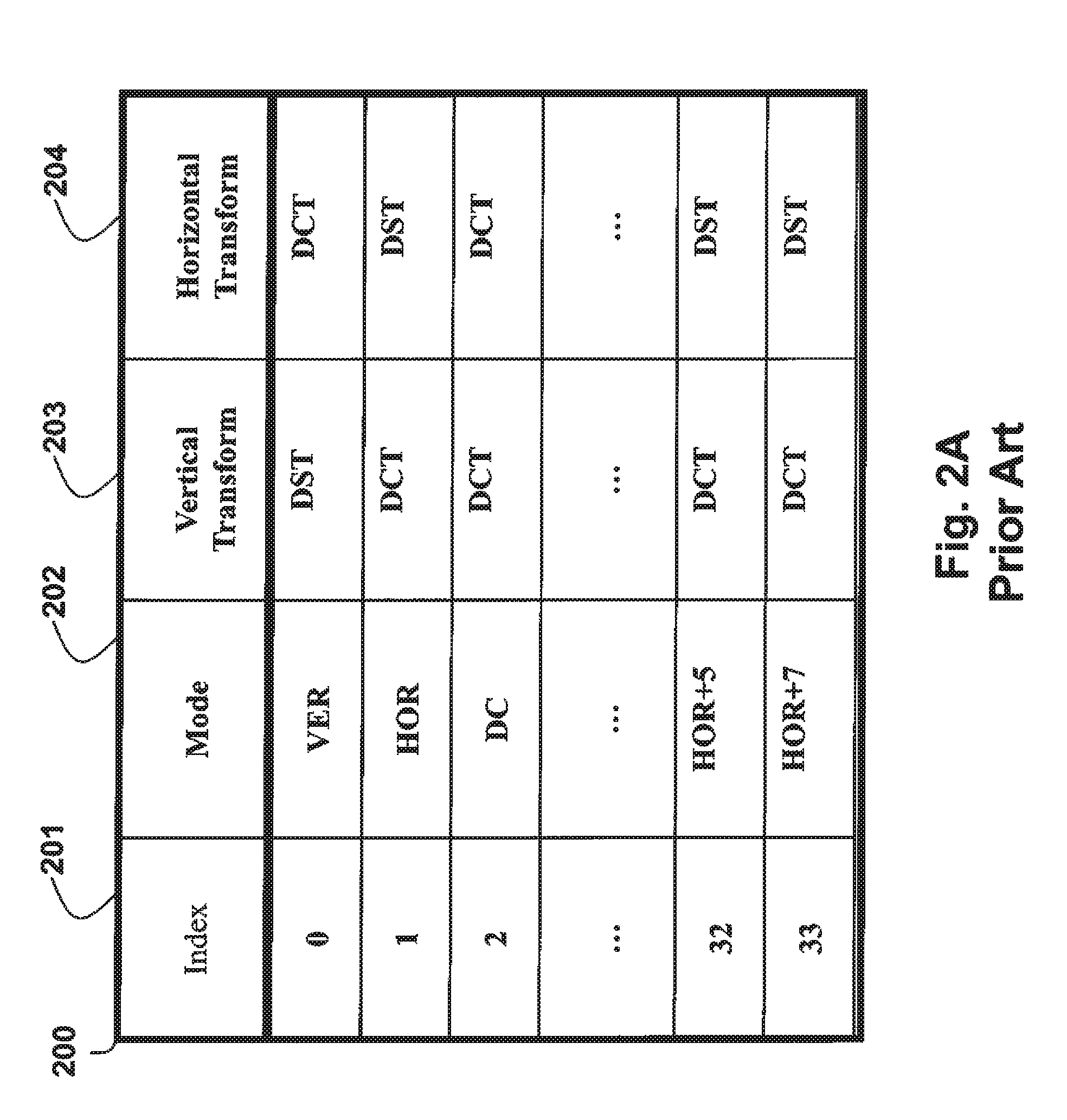
Method for Selecting Transform Types From Mapping Table for Prediction Modes
InactiveUS20130003828A1Color television with pulse code modulationPulse modulation television signal transmissionData miningData application
A method codes pictures in a bitstream, wherein the bitstream includes coded pictures to obtain data for associated TUs and data for generating a transform tree, and a partitioning of coding units (CUs) into Prediction Units (PUs), and data for obtaining prediction modes or directions associated with each PU. One or more mapping tables are defined, wherein each row of each table has an associated index and a first set of transform types to be used for applying an inverse transformation to the data in TU. The first set of transform types is selected according to an index, and then a second set of transform types is applied as the inverse transformation to the data, wherein the second set of transform types is determined according to the first set of transform types and a transform-toggle flag (ttf) to obtain a reconstructed prediction residual.
Owner:MITSUBISHI ELECTRIC RES LAB INC
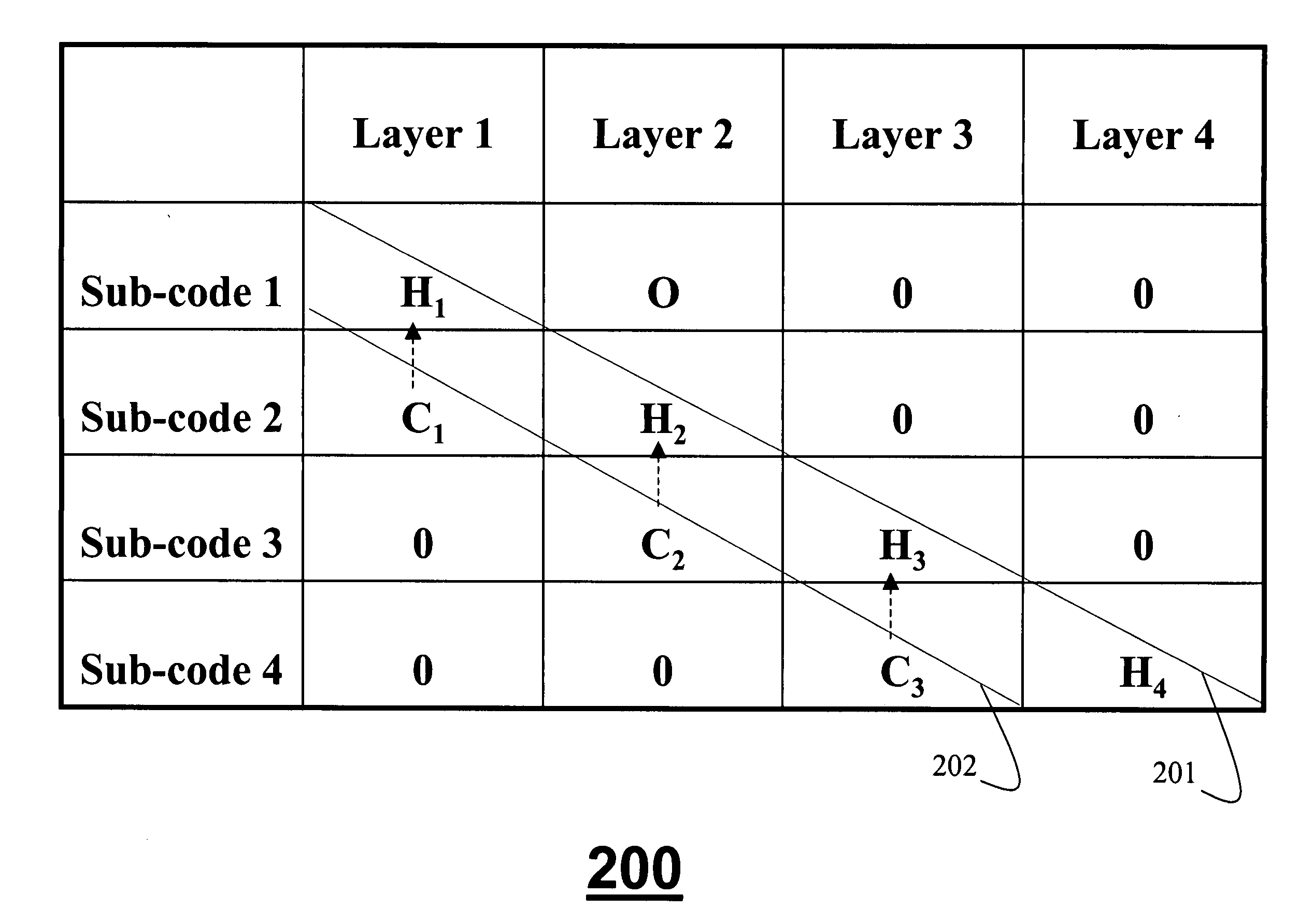
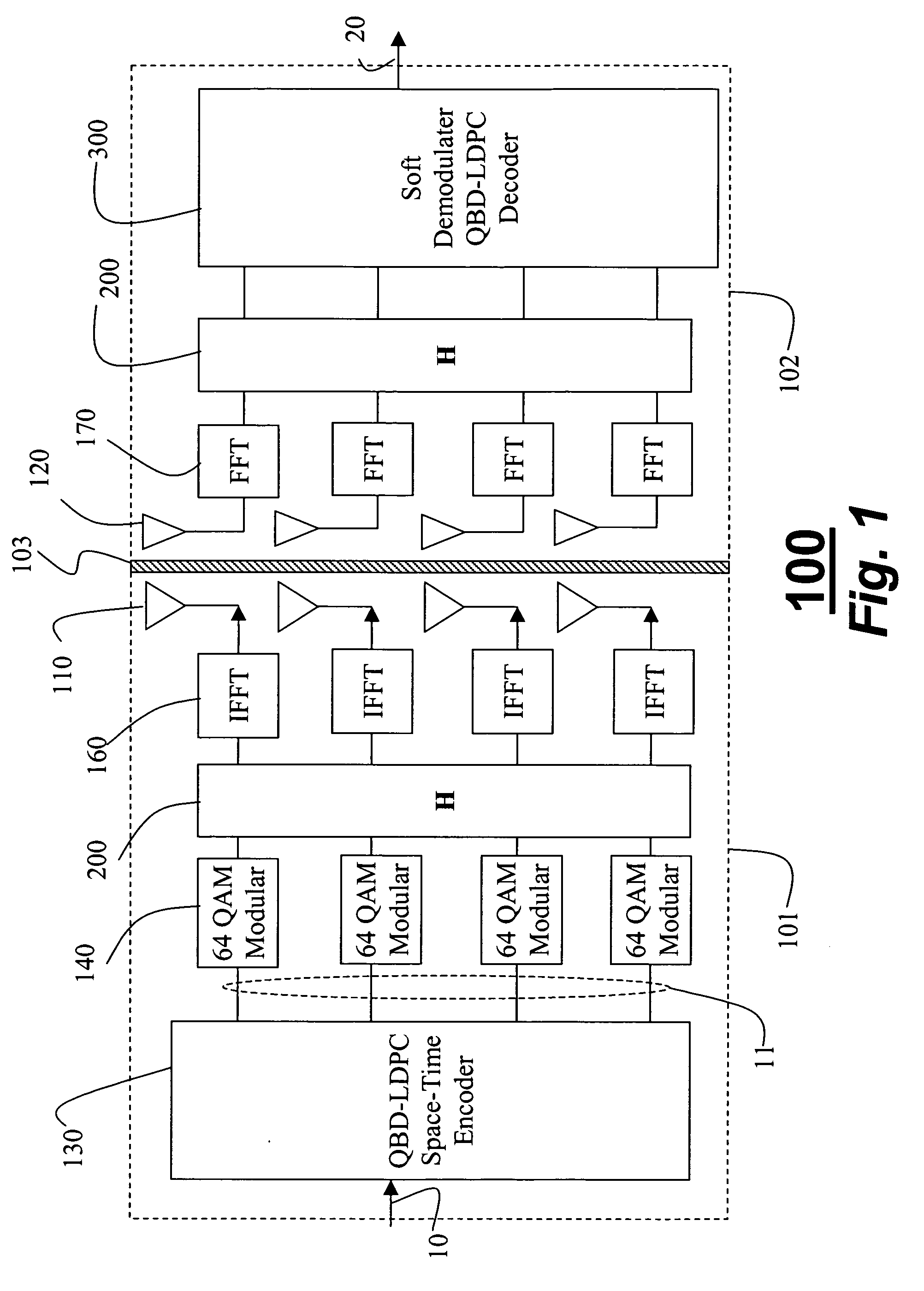
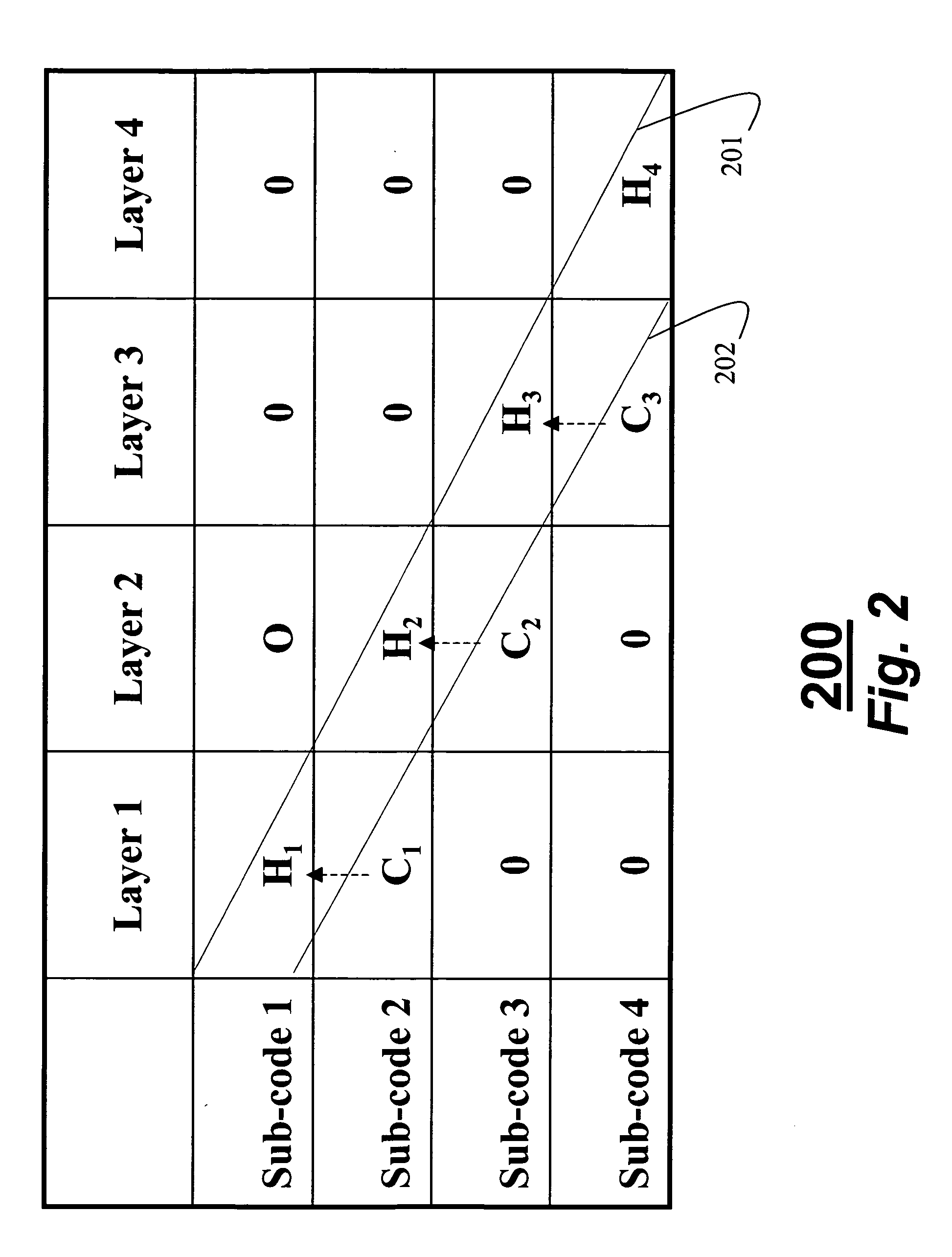
Quasi-block diagonal low-density parity-check code for MIMO systems
InactiveUS20050268202A1Easy to detectReduce error propagationMultiplex communicationCode conversionData streamCommunications system
A method codes multiple data streams in multiple-input, multiple-output communications systems. In a transmitter, an input bitstream is encoded as codewords b in multiple layers. Each layer is modulated. A quasi-block diagonal, low-density parity-check code is applied to each layer, the quasi-block diagonal, parity-check code being a matrix H, the matrix H including one row of blocks for each subcode, and one row of blocks for each layer such that Hb=0 for any valid codeword. The layers are then forwarded to transmit antennas as a transmitted signal x.
Owner:MITSUBISHI ELECTRIC RES LAB INC
Method for protecting JAVA application programs in Android system
ActiveCN102708322APrevent piracyProgram/content distribution protectionSpecific program execution arrangementsApplication softwareJava classes
The invention relates to the field of computer safety, in particular to a method for protecting application programs in an Android system. By carrying out encryption transformation on a plurality of method instruction codes of JAVA objects to be protected, encrypted method codes are subjected to real-time decryption operation according to the calling requirement when the programs operate, so that the application programs are difficult to subject to decompilation and static analysis, and therefore, the effective protection on the JAVA programs in the Android system is implemented.
Owner:BEIJING SENSESHIELD TECH
Data processing method coded and decoded by FEC, and relative device
ActiveCN103534971ADoes not reduce data transfer bandwidthGuaranteed interoperabilityRedundant data error correctionTransmission link error control systemComputer hardwareMultiplexing
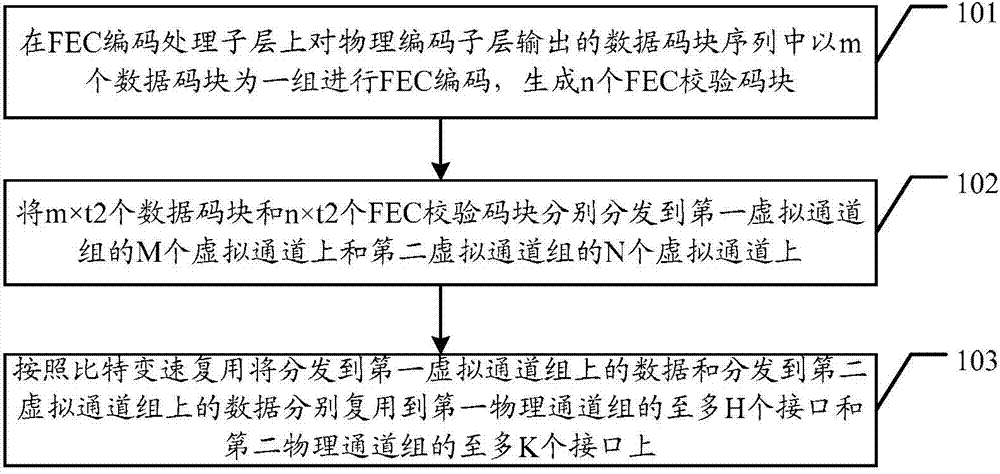
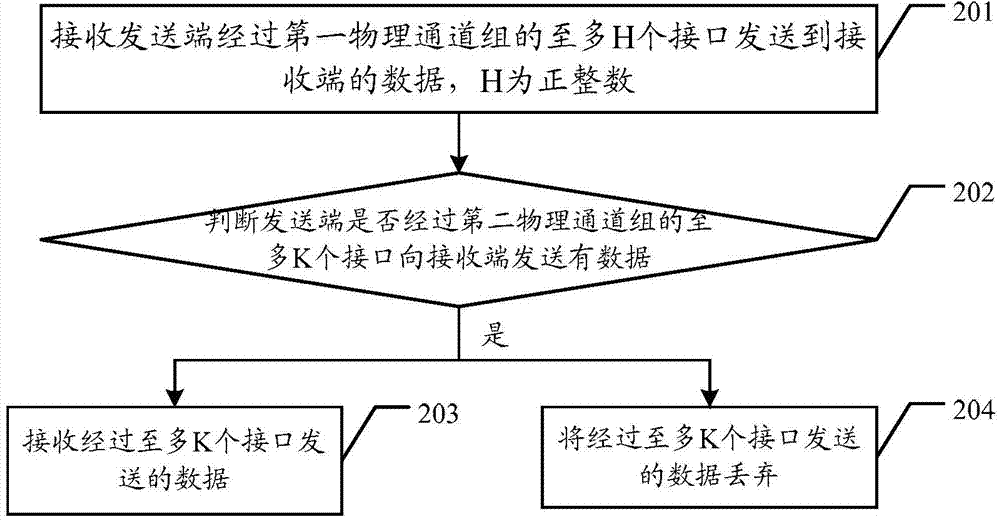
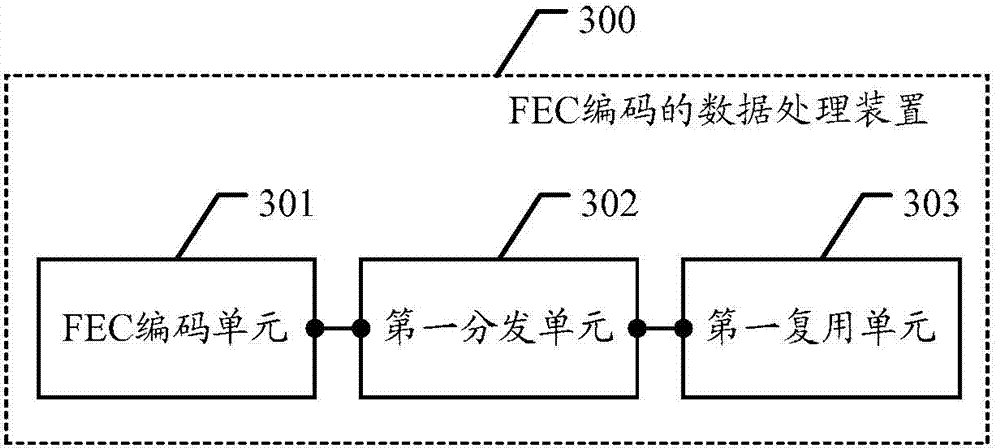
The invention provides a data processing method coded and decoded by FEC, and a relative device. The method comprises: carrying out FEC coding on a FEC code processing sub-layer for a data code block sequence which is output by a physical code sub-layer and uses m data code blocks as a group, to generate n FEC check code blocks; respecitively distributing m*t2 data code blocks and n*t2 FEC check code blocks to M virtual channels of a first virtual channel group and N virtual channels of a second virtual channel group, wherein m*t2 is less than or equal to m_max, m_max is t1 times of M, n is less than or equal to n_max, n_max is t1 times of N, and m, n, t1 and t2 are positive integers; and respectively multiplexing data distributed to the first virtual channel group and the second virtual channel group onto at most H interfaces of a fisrt physical channel group and at most K interfaces of a second physical channel group according to bit speed-changing multiplexing, wherein M is integral multiple times of H, and N is integral multiple times of K.
Owner:HUAWEI TECH CO LTD
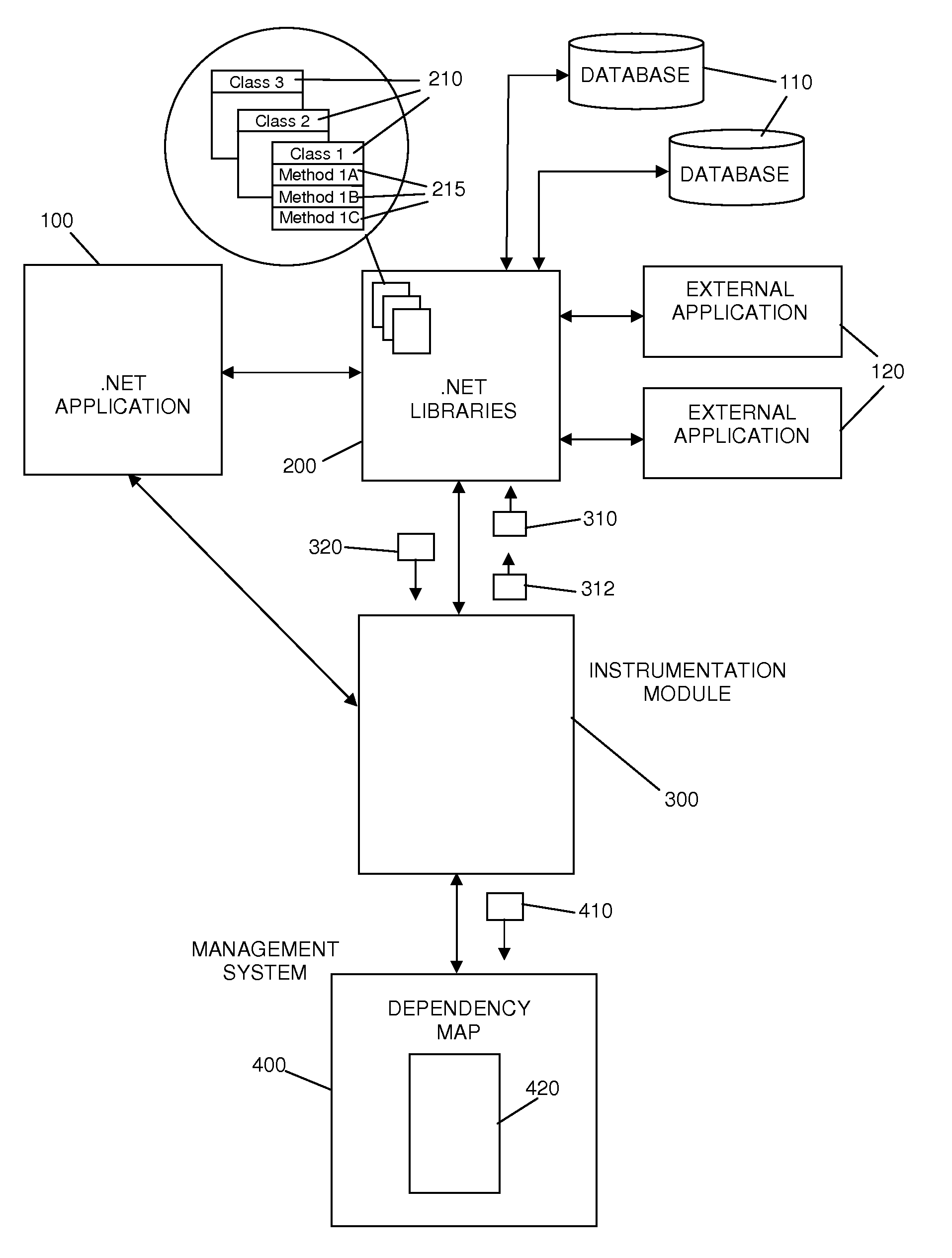
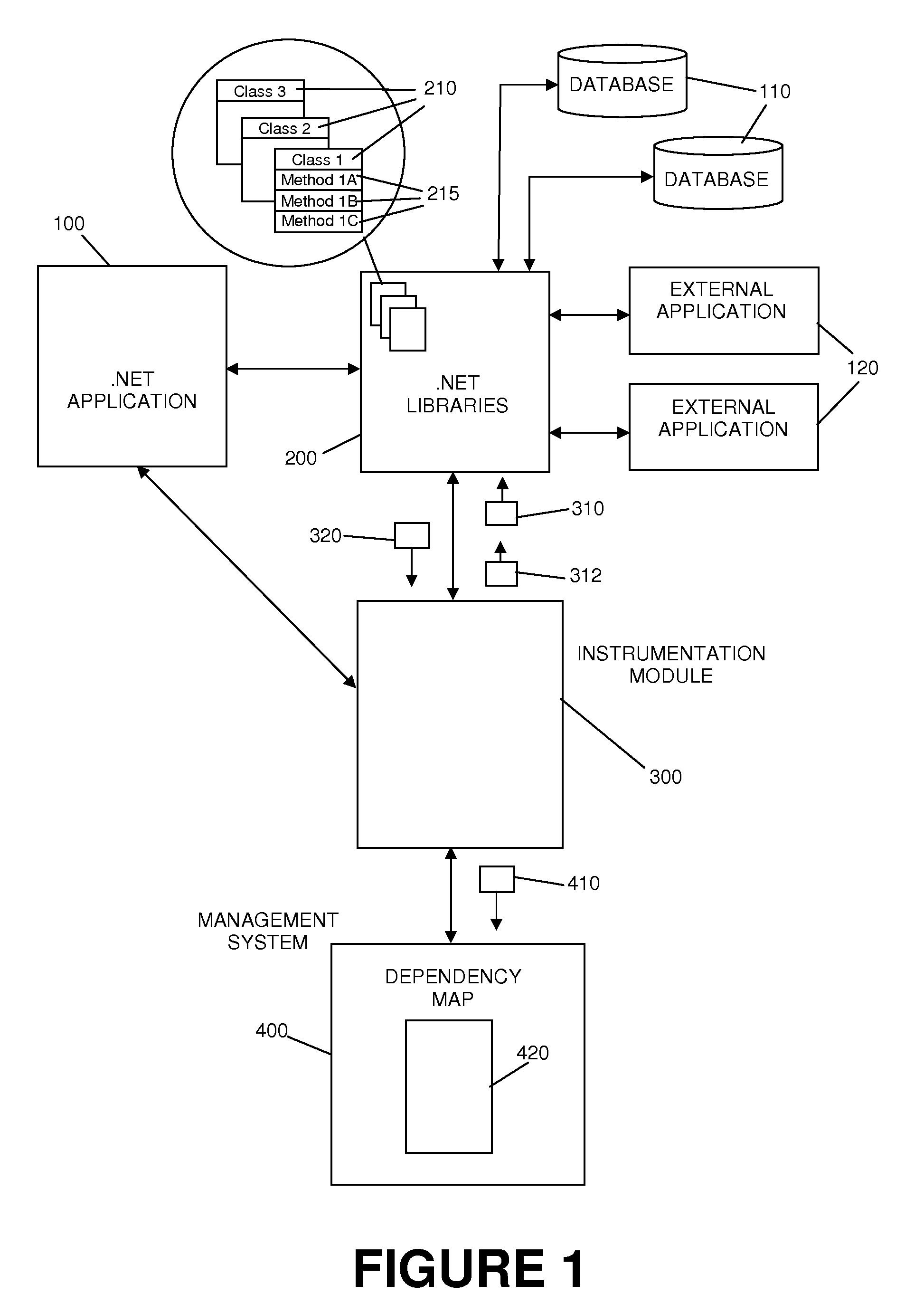
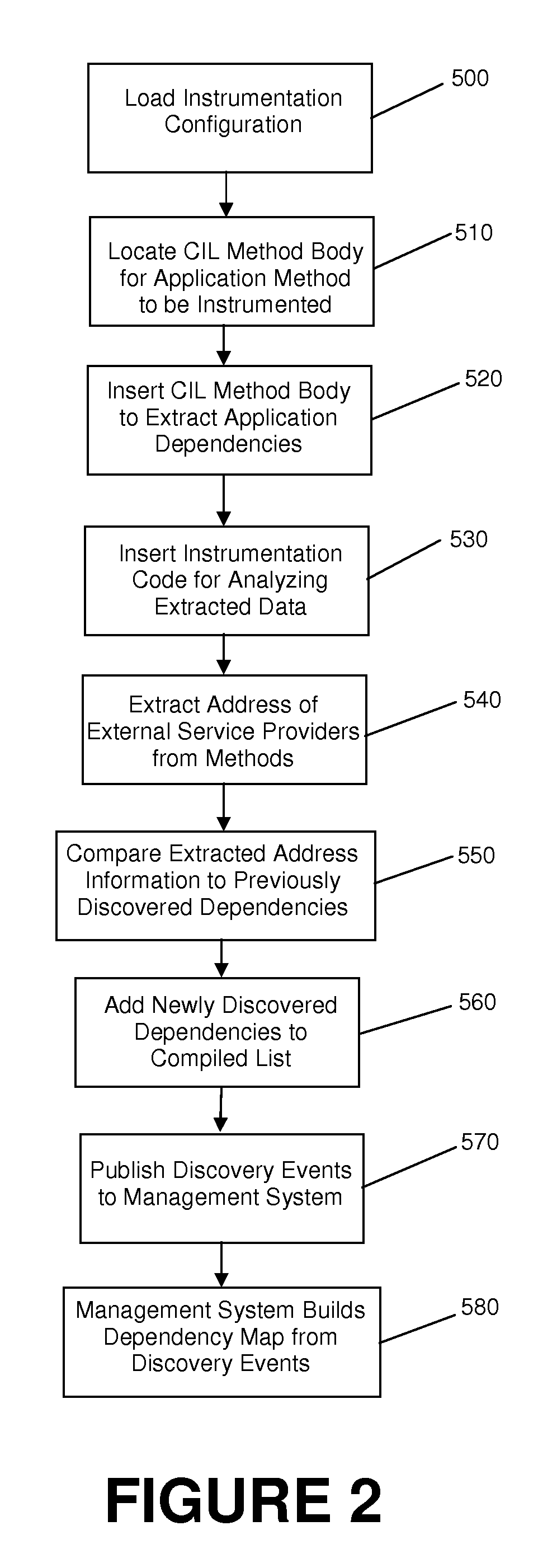
Automatic incremental application dependency discovery through code instrumentation
ActiveUS20100037211A1Error detection/correctionSpecific program execution arrangementsCall tracingMethod body
Disclosed is a method allowing the automatic discovery of application component dependencies by tracing application calls to dependant resources. The call tracing is embedded dynamically in an application at runtime using Common Intermediate Language (“CIL”) code instrumentation at compile time or runtime. Such a method reads an instrumentation configuration file to determine an address extraction code portion that is to be instrumented to an application method code, locates the CIL method body for the application method that is to be instrumented, instruments the application method by inserting the address extraction code portion into the appropriate .NET Application or .NET library at either compile time or at run time, extracts the address of one or more external service providers from the designated .NET library methods responsible for communication during execution of the application method that was instrumented, publishes any newly discovered dependencies to a management system in the form of the discovery event, and causes the management system to build an application dependency map based on the resource address information obtained.
Owner:MICROSOFT TECH LICENSING LLC
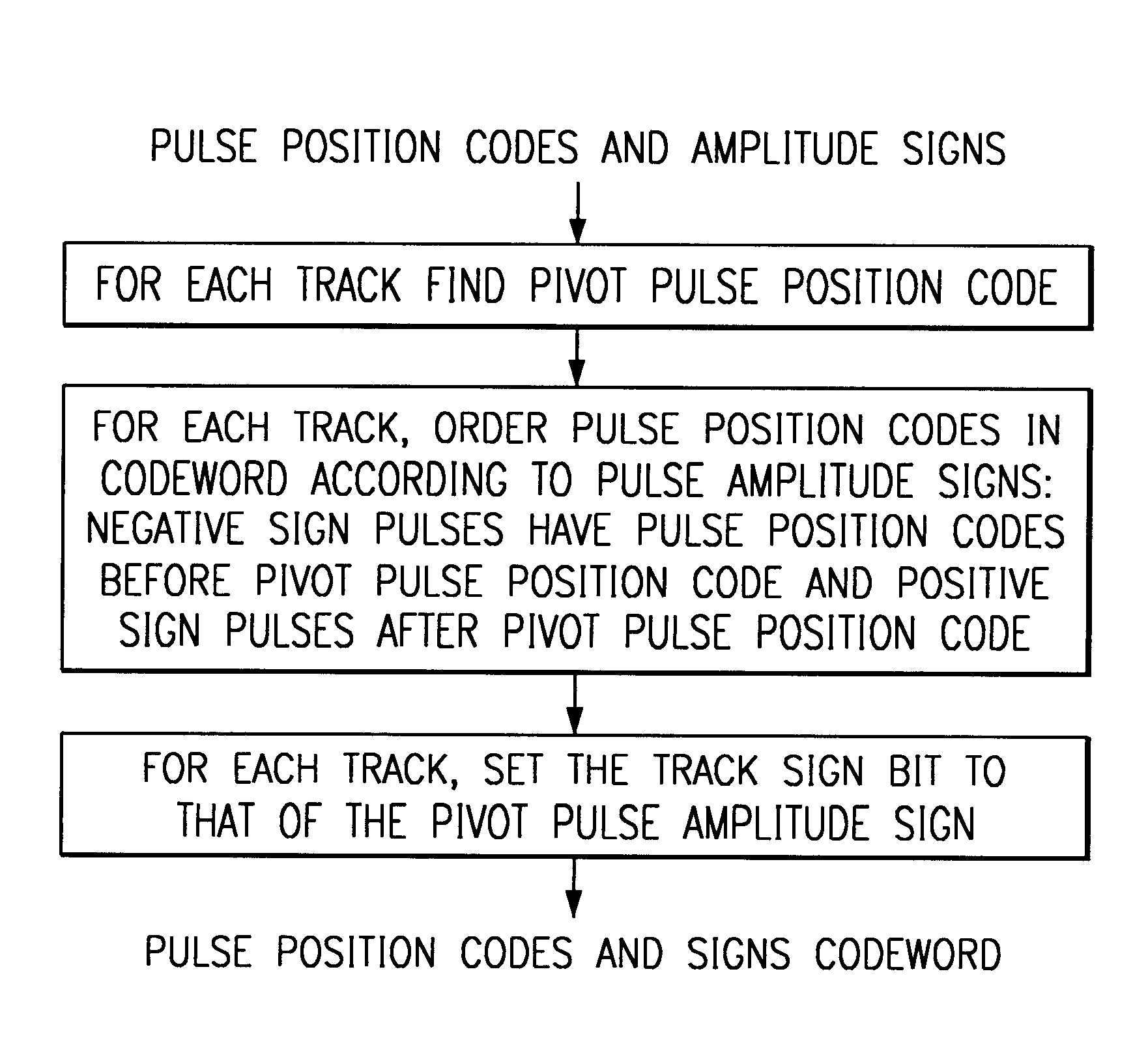
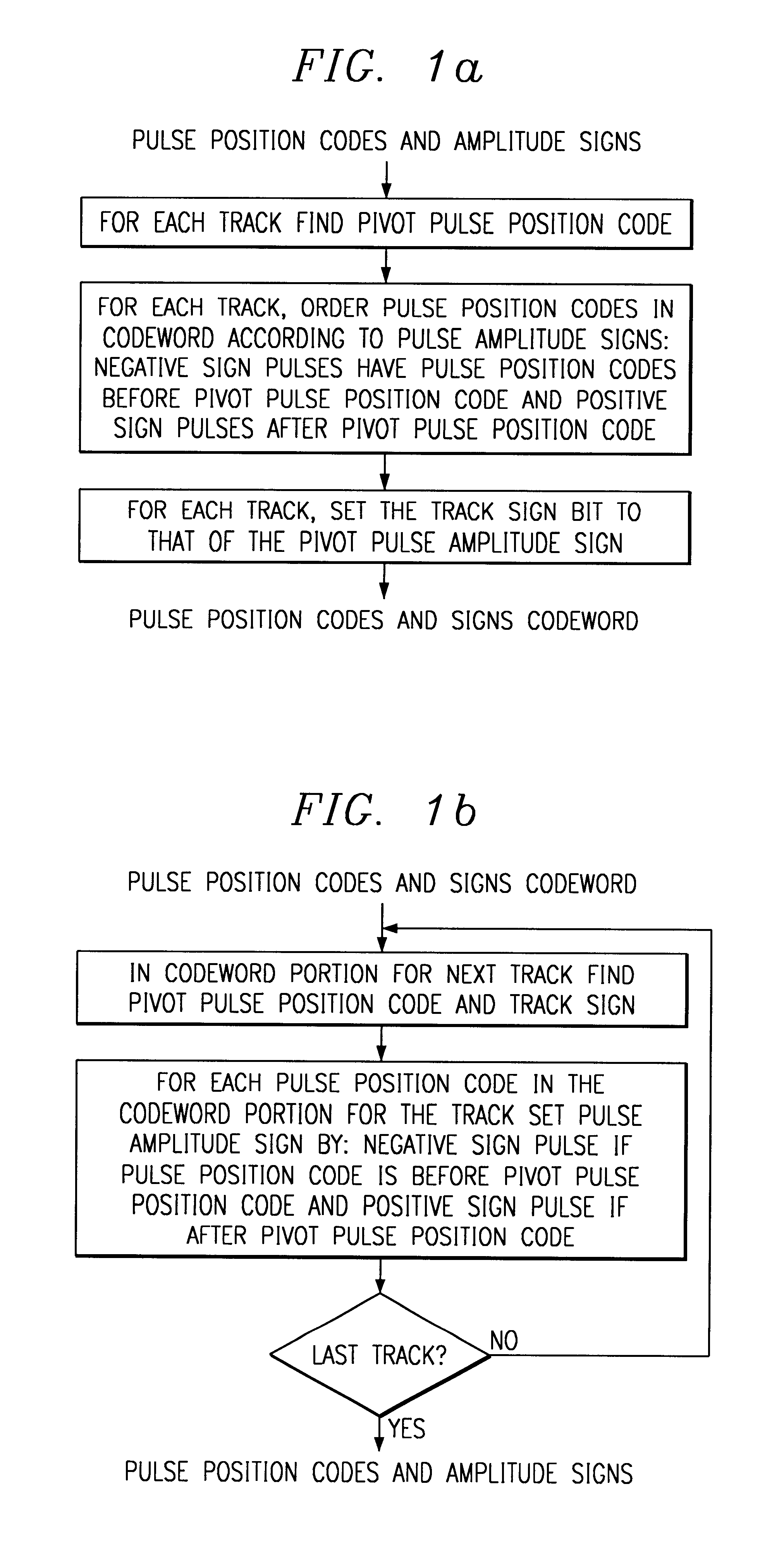
Algebraic codebook system and method
Code-excited linear prediction speech encoders / decoders with excitation including an algebraic codebook contribution encoded with a single sign bit for each track of pulses by inferring pulse amplitude signs from the pulse position code ordering within a codeword.
Owner:TEXAS INSTR INC
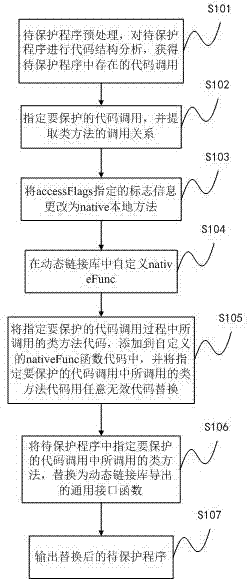
Code protecting method and system based on hook technology in JAVA
InactiveCN103902859AImprove protectionChange call flowProgram/content distribution protectionDead codeStructure of Management Information
The invention provides a code protecting method and system based on a hook technology in JAVA. The code protecting method mainly comprises the steps that a JNI mechanism is mainly used, class calling is changed by modifying class mark information to native, and a nativeFunc is customized in a dynamic link library; class method codes which are called in the calling process of codes assigned to be protected are added to codes of the customized nativeFunc, and the class method codes which are called in the calling process of the codes assigned to the protected are replaced with arbitrary invalid codes; a class method called in the calling process of the codes assigned to be protected in a program to be protected is replaced with a general interface function exported by the dynamic link library; finally, the replaced program to be protected is output. The invention further correspondingly provides a corresponding system structure. By means of the method, calling of the function can be hidden in a dynamic link library file which is compiled into binary machine instructions, and thus the difficulty of reversing the calling is greatly increased.
Owner:WUHAN ANTIY MOBILE SECURITY
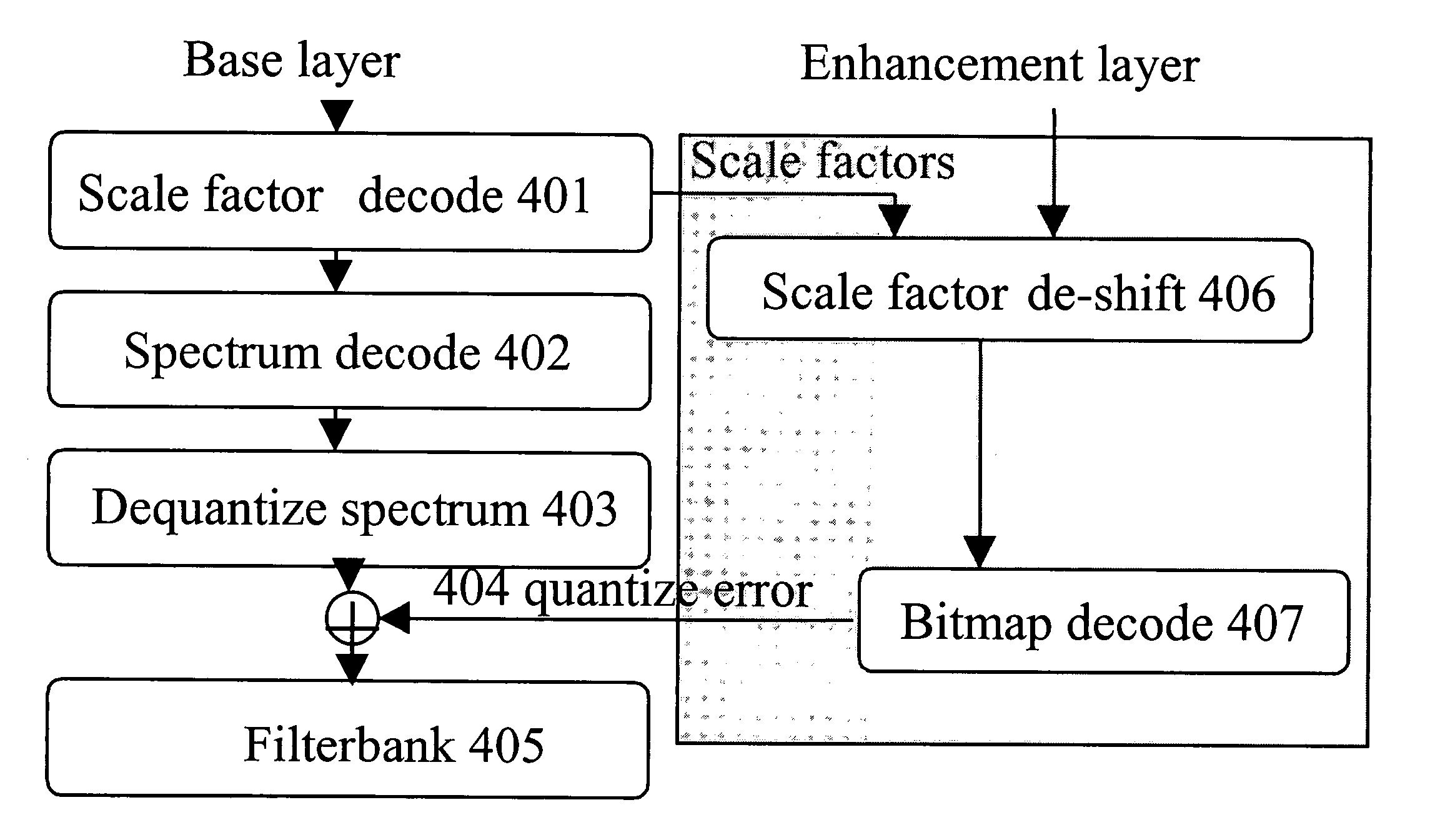
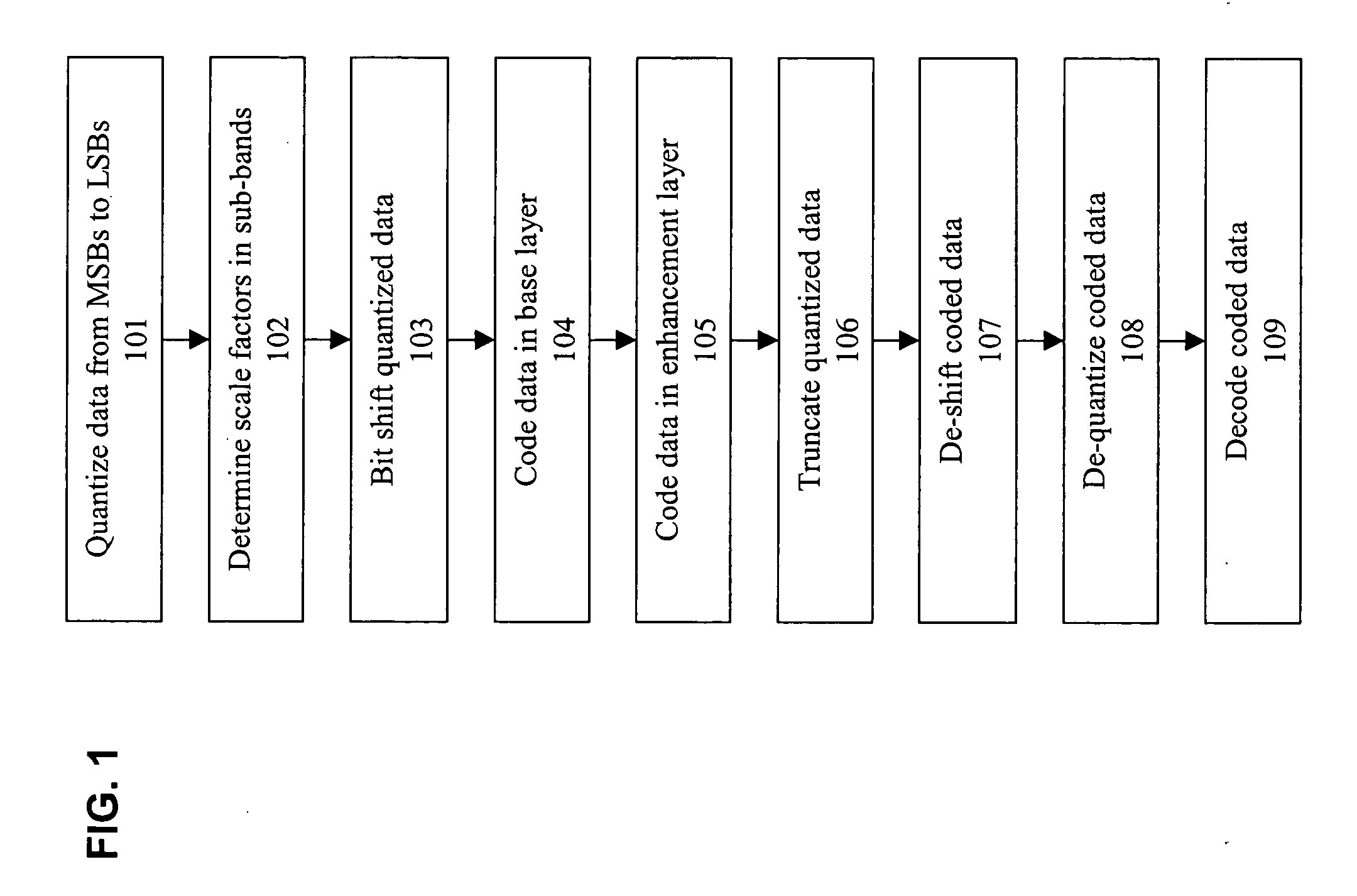
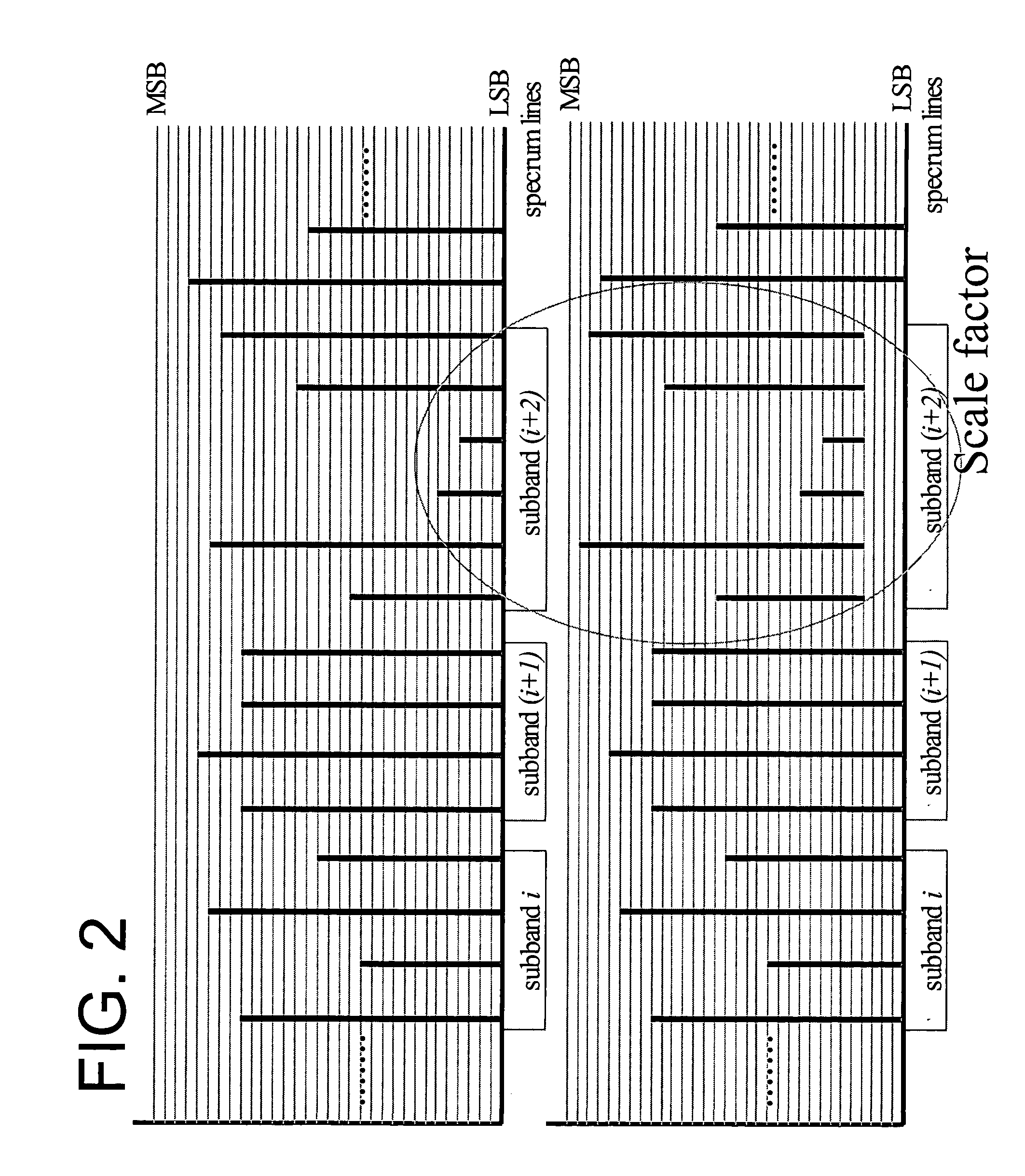
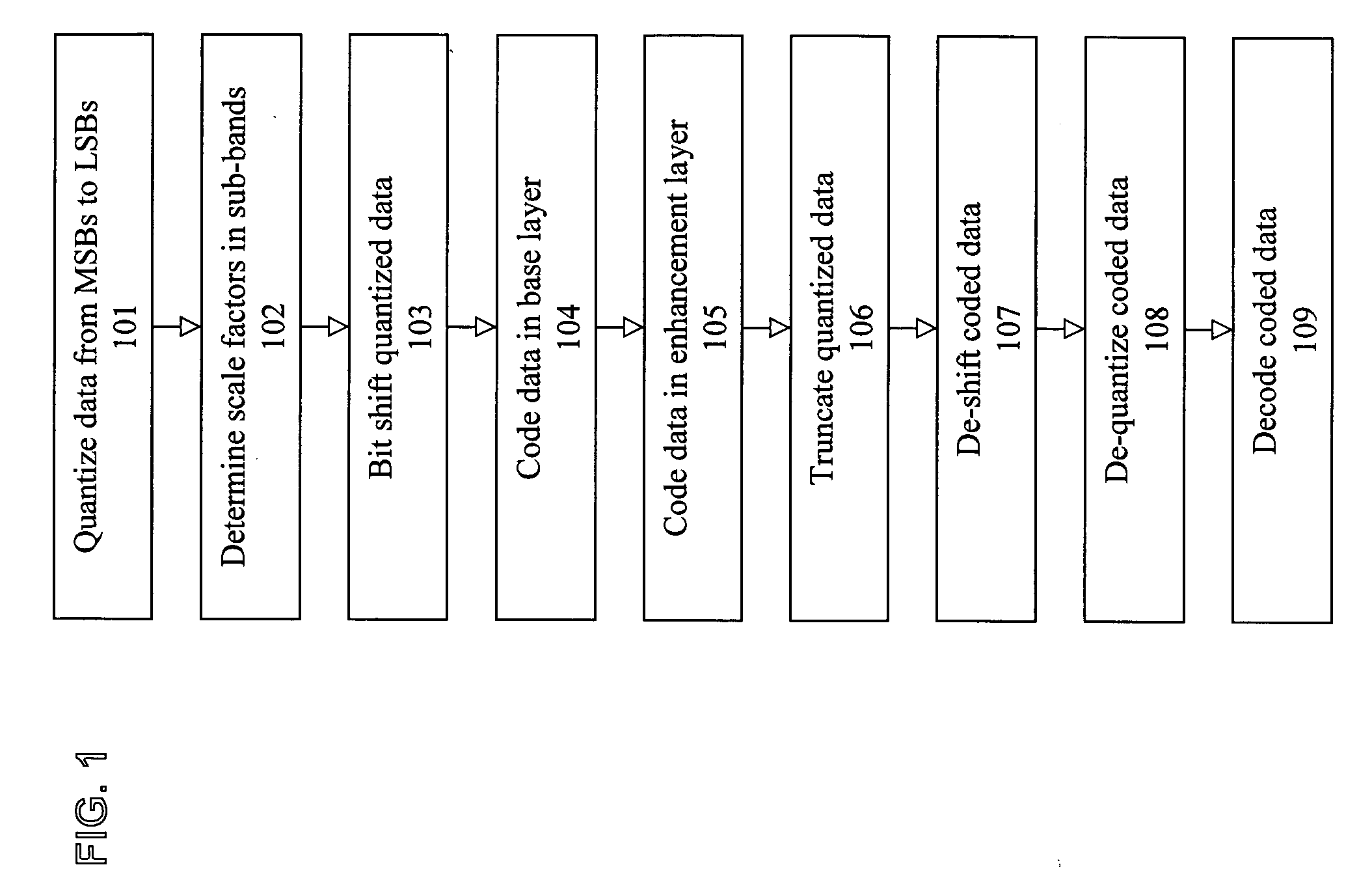
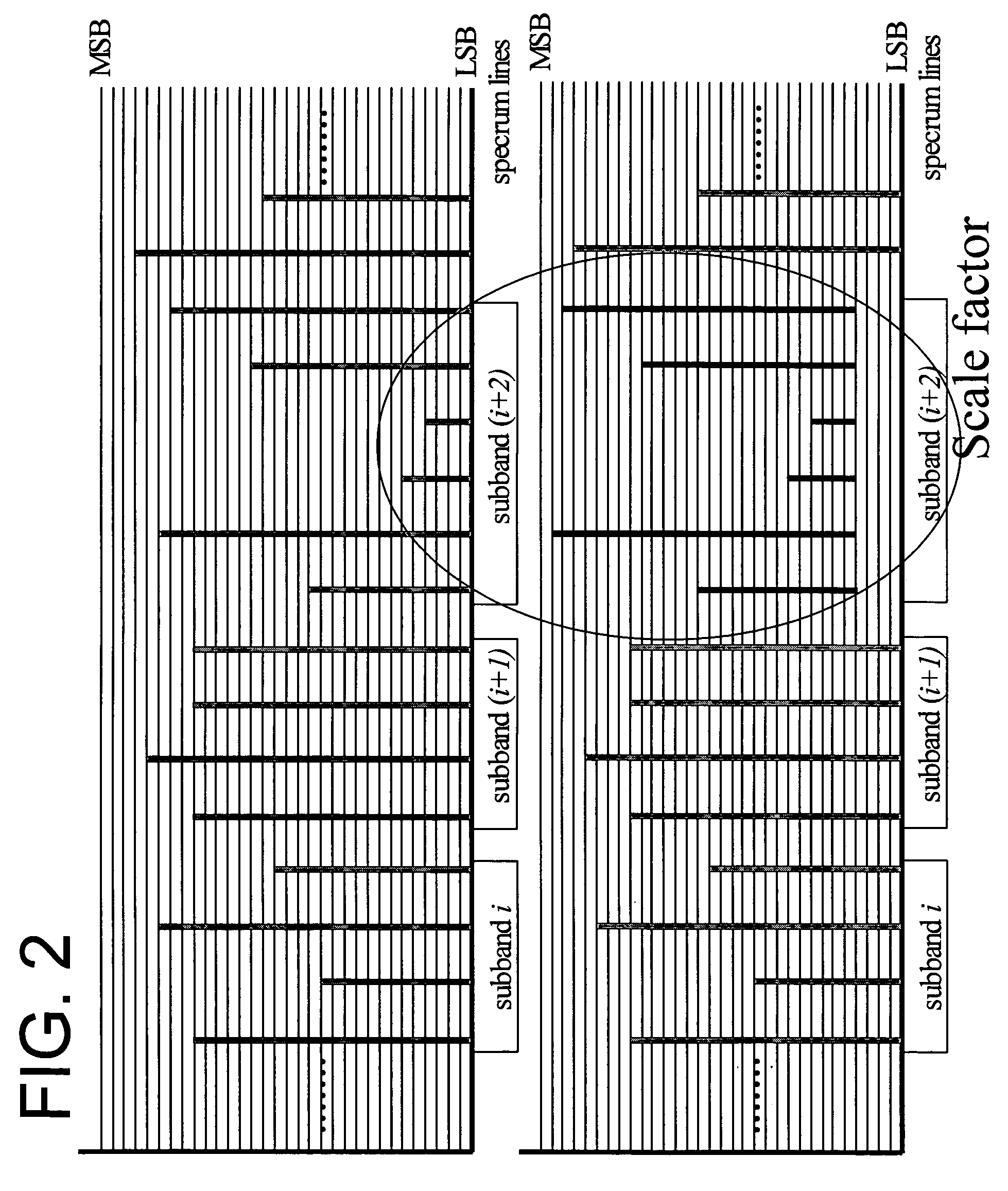
Scale factor based bit shifting in fine granularity scalability audio coding
InactiveUS20050010396A1Bandwidth issue and additionalIssue and additional overheadSpeech analysisFrequency spectrumGranularity
One embodiment of the present invention provides a method coding audio signals in a base layer and an enhancement layer comprising the steps of quantizing the audio signals in spectral lines into quantized data in a plurality of sub-bands in an order of most significant bits (MSBs) to least significant bits (LSBs), determining a plurality of scale factors corresponding to each of the sub-bands according to respective noise tolerance of each of the sub-bands, bit shifting the quantized data in the sub-bands by the respective scale factor if they exceed a threshold value, coding the quantized data in the base layer, coding the quantized data in the enhancement layer, truncating the quantized data in the enhancement layer up to respective layer size limits, de-shifting the coded data wit the respective scale factors, de-quantizing the coded data, and decoding the coded data.
Owner:IND TECH RES INST
Method and system for dynamic loop transfer by populating split variables
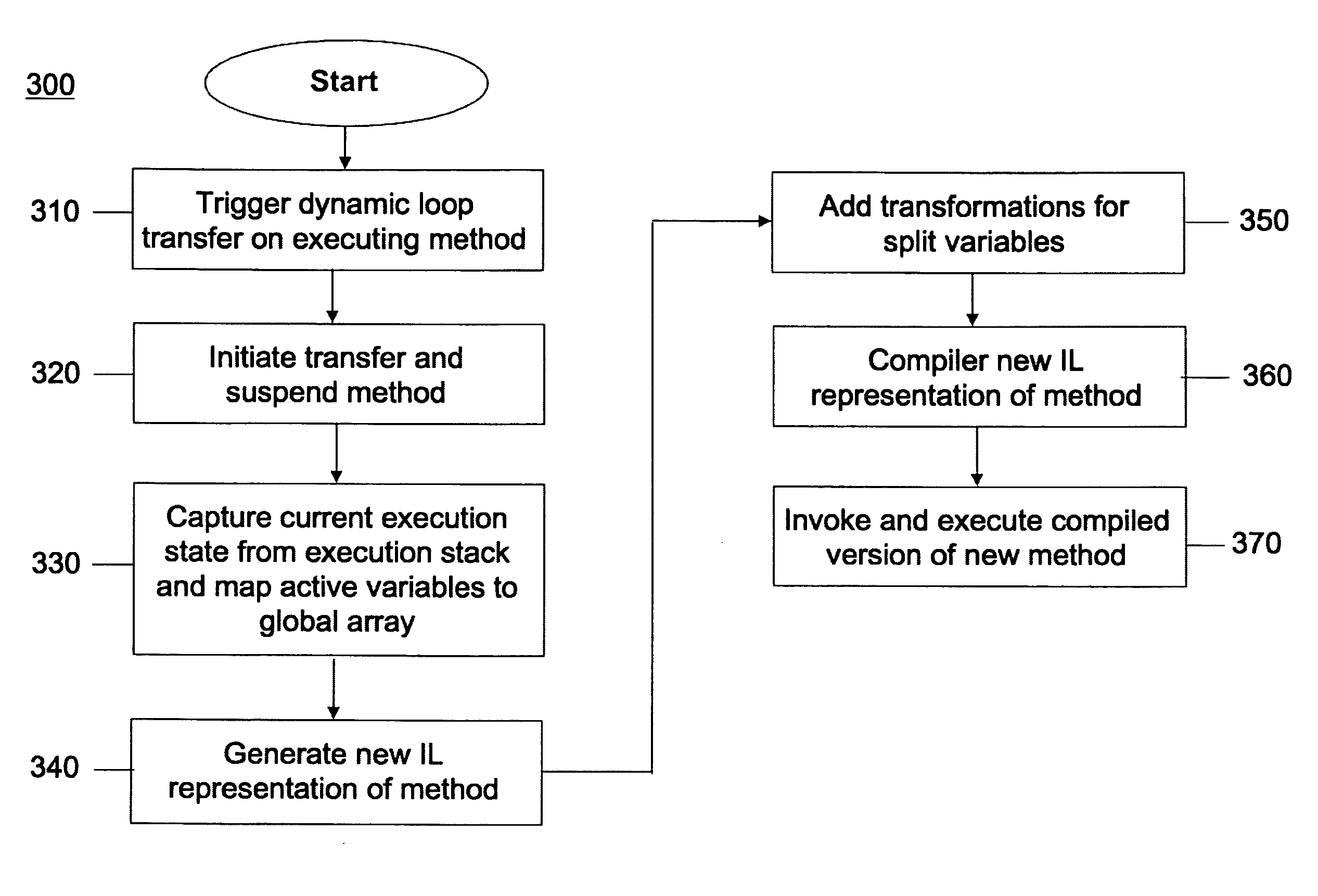
InactiveUS20090064113A1Performing codeIncrease flexibilitySoftware engineeringProgram controlLocal variableParallel computing
A method that provides for dynamic loop transfer for a method having a first set of instructions being executed by an interpreter is provided. An execution stack includes slots for storing a value of each local variable known to each subroutine while the subroutine is active. The method comprises suspending execution at a point for which a current execution state can be captured from the execution stack; assigning the value in each slot of the execution stack to a corresponding slot of an array of values; scanning the first set of instructions to identify a data type for local variable that is not known in the current execution state and shares a slot in the execution stack with a local variable that is known; and generating a second set of instructions for the method coded to be initially executed to declare each local variable that is known in the current execution state and each local variable for which a data type was identified, assign each declared variable with the value assigned to the slot in the array that corresponds to the slot of the execution stack in which the value of the variable is stored during execution of the first set of instructions, and branch to a target point in the second set of instructions that corresponds to the point at which execution was suspended.
Owner:IBM CORP
Scale factor based bit shifting in fine granularity scalability audio coding
ActiveUS20050010395A1Avoiding bandwidth issueAvoiding additional overheadPulse modulation television signal transmissionSpeech analysisMethod CodeSpeech recognition
One embodiment of the present invention provides a method coding audio signals in a base layer and an enhancement layer comprising the steps of quantizing the audio signals in spectral lines into quantized data in a plurality of sub-bands in an order of most significant bits (MSBs) to least significant bits (LSBs), determining a plurality of scale factors corresponding to each of the sub-bands according to respective noise tolerance of each of the sub-bands, bit shifting the quantized data in the sub-bands by the respective scale factor if they exceed a threshold value, coding the quantized data in the base layer, coding the quantized data in the enhancement layer, truncating the quantized data in the enhancement layer up to respective layer size limits, de-shifting the coded data wit the respective scale factors, de-quantizing the coded data, and decoding the coded data.
Owner:IND TECH RES INST
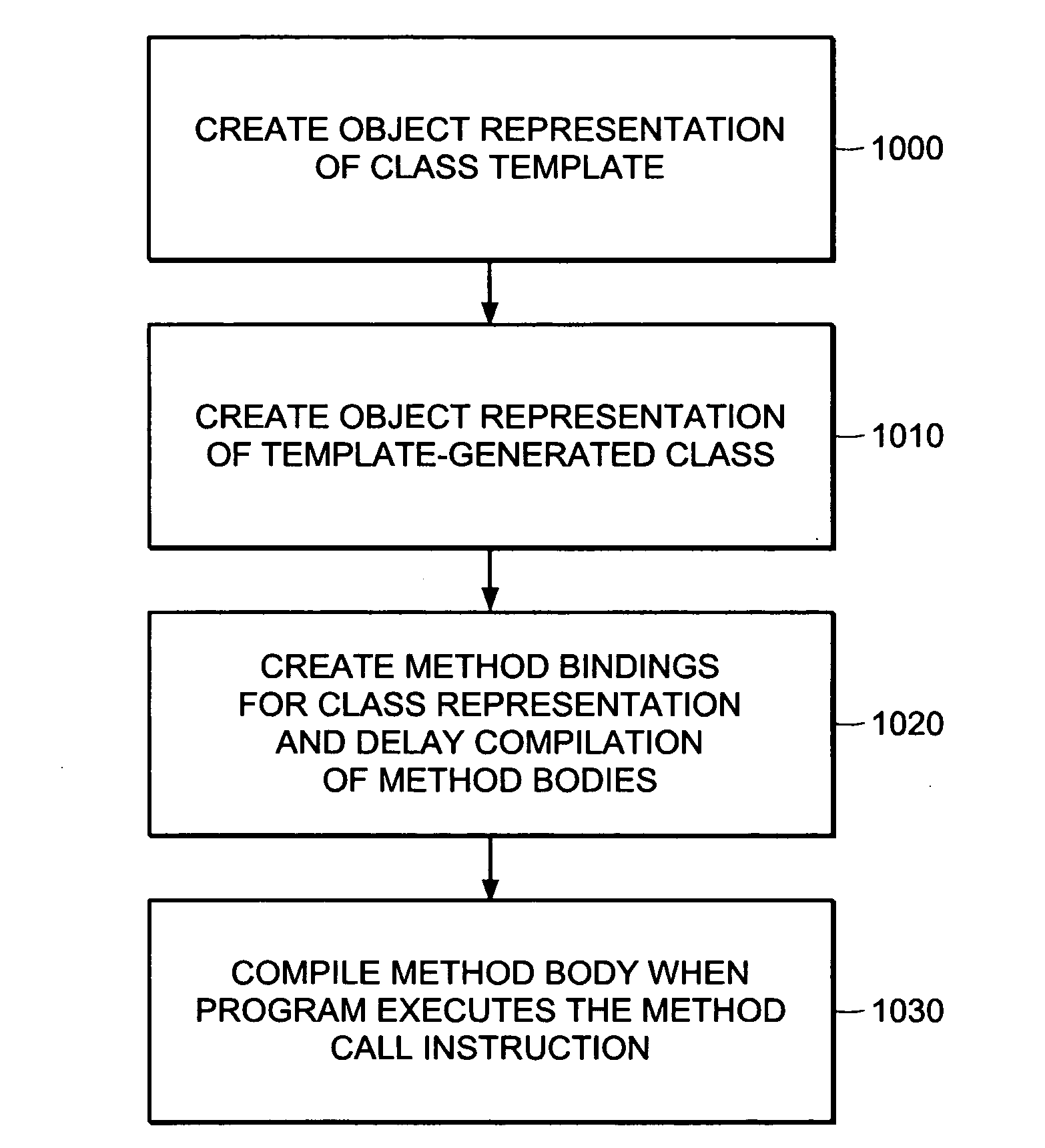
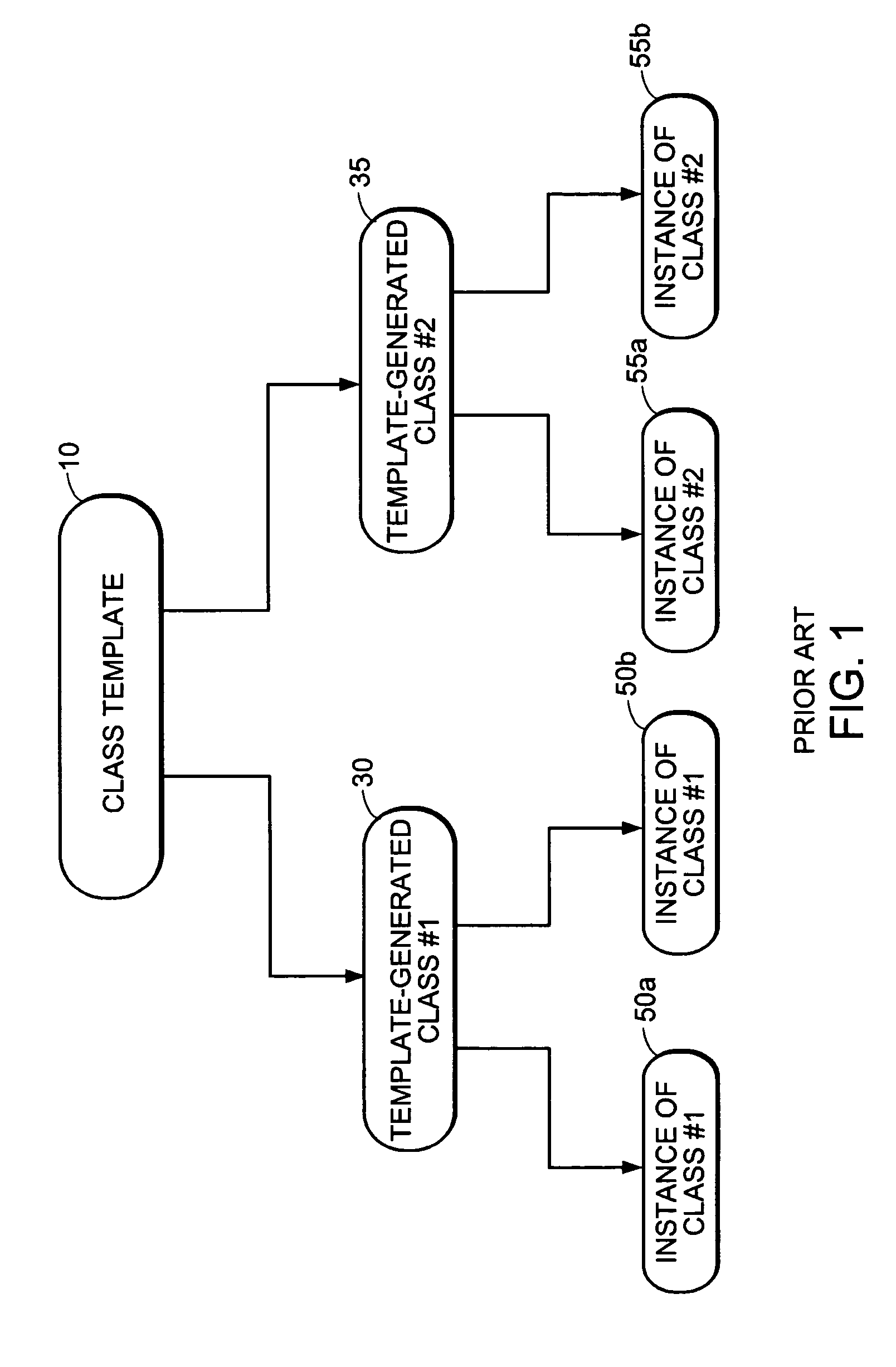
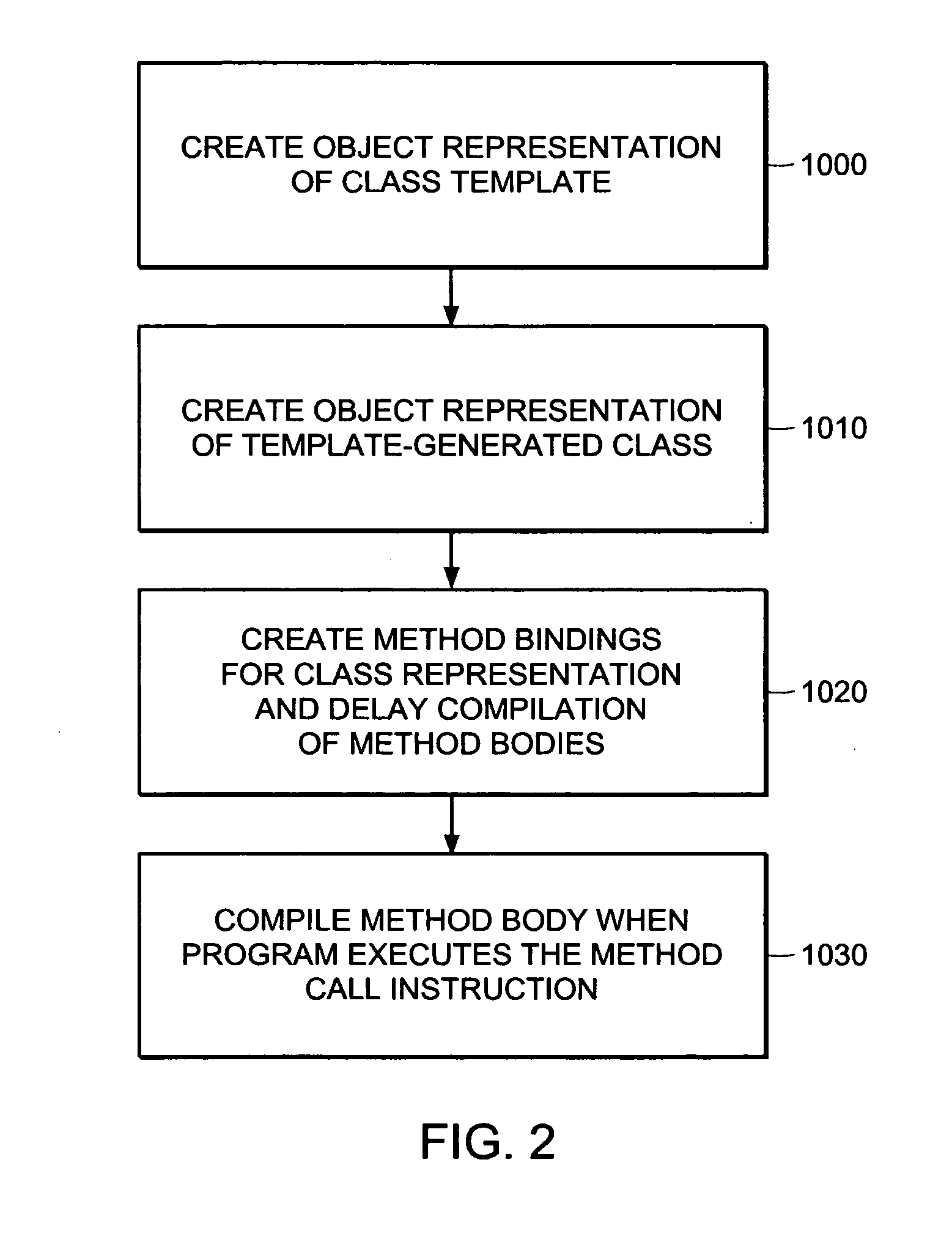
Lazy compilation of template-generated classes in dynamic compilation execution environments
InactiveUS20050060695A1Reduce the amount of codeShorten the timeProgram loading/initiatingExecution paradigmsDynamic compilationProgramming language
Template-generated classes in program code are compiled efficiently through a process of lazy compilation resulting in improved compilation times. Lazy compilation includes the generation of objects representing a class template and a template-generated class as well as the selective compilation of class methods that are invoked in the program code. Code sharing is a further enhancement for increasing compilation speed by providing a system and method for sharing executable object code for compatible methods among different classes generated from the same class template.
Owner:SCSK CORP
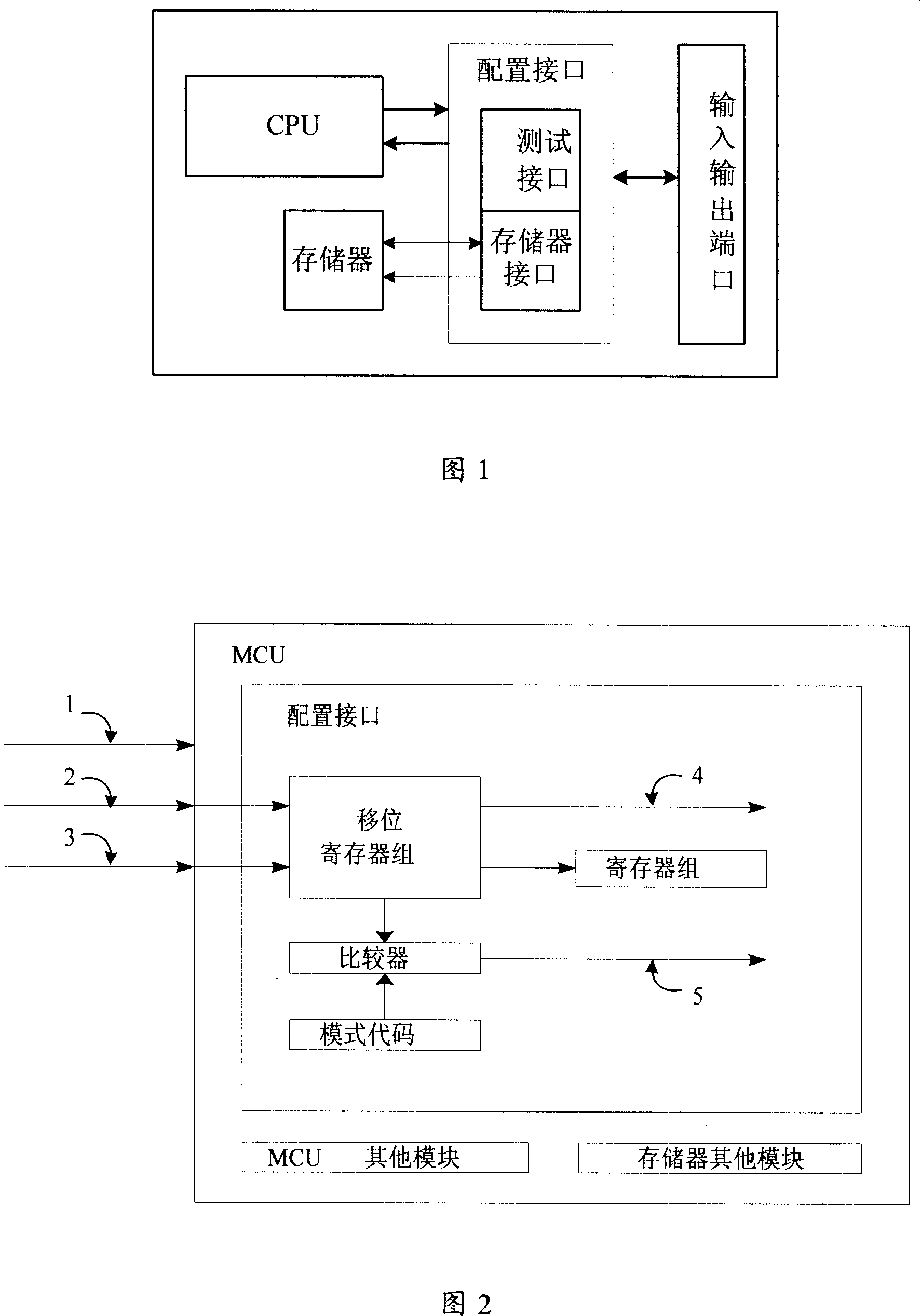
Operating method for configured interface of microcontroller
InactiveCN101154207AThe testing process is simpleSimple methodUnauthorized memory use protectionFunctional testingMicrocontrollerFunctional testing
The invention relates to an operation method of a configuration interface of a microcontroller, comprising the follow steps: when a high level is input into a testing port, a serial clock and a serial data are input through an I / O port, the serial data is compared with an operation method code which is internally set, a corresponding operation method can be accessed through the comparison of the effect. The invention also comprises a function testing operation method, a DC parameter testing operation method, a digit / analog conversion testing operation method, a program storage testing operation method, a parallel programming mode operation method and a serial programming mode operation method. The configuration interface operation method of the invention can be scalable, and can access a plurality of testing operation methods and working methods, the access of a chip to different testing or working operation methods becomes more easy.
Owner:SHANGHAI EASTSOFT MICROELECTRONICS
Method and device for coding video data and method and device for decoding video data
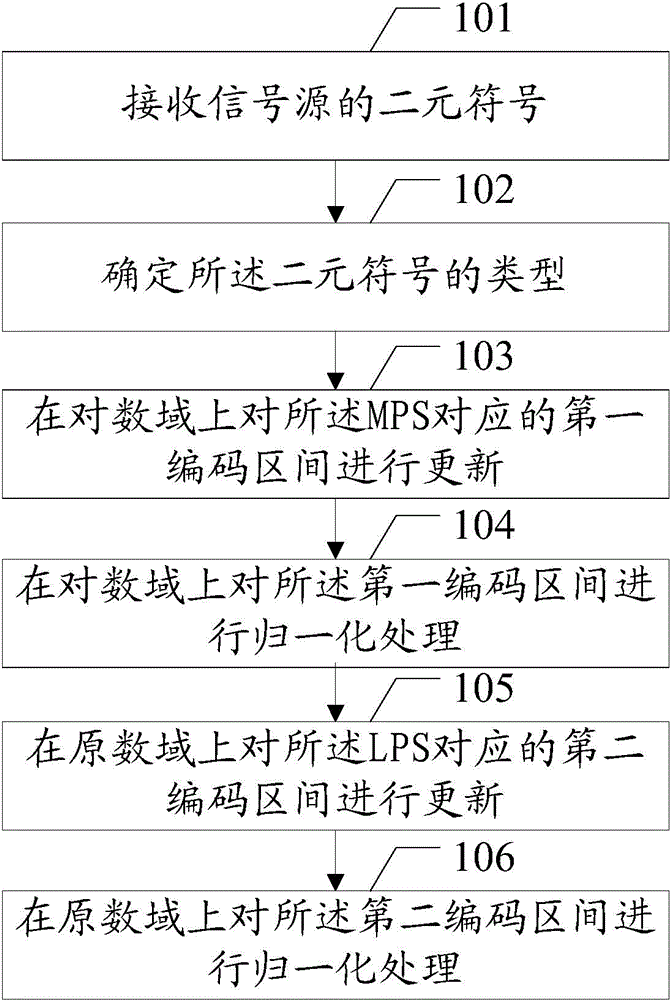
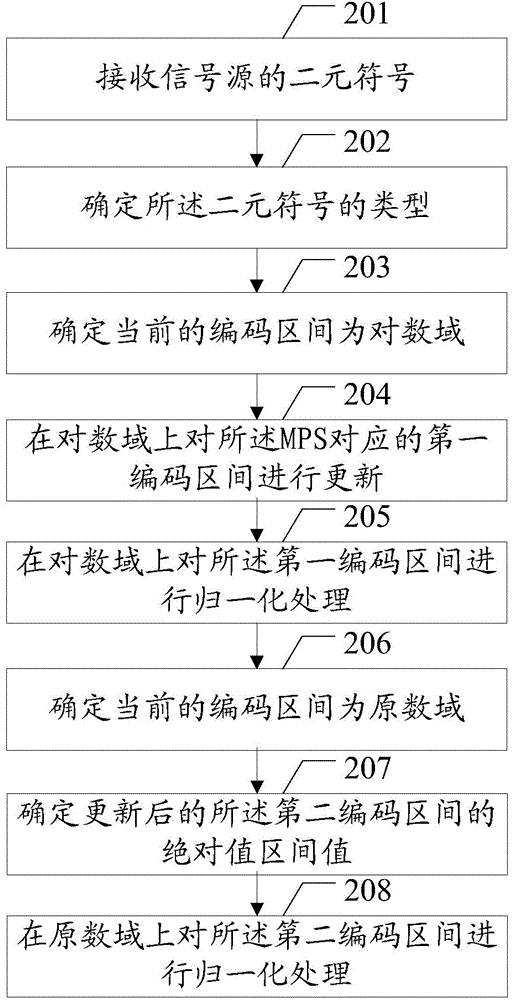
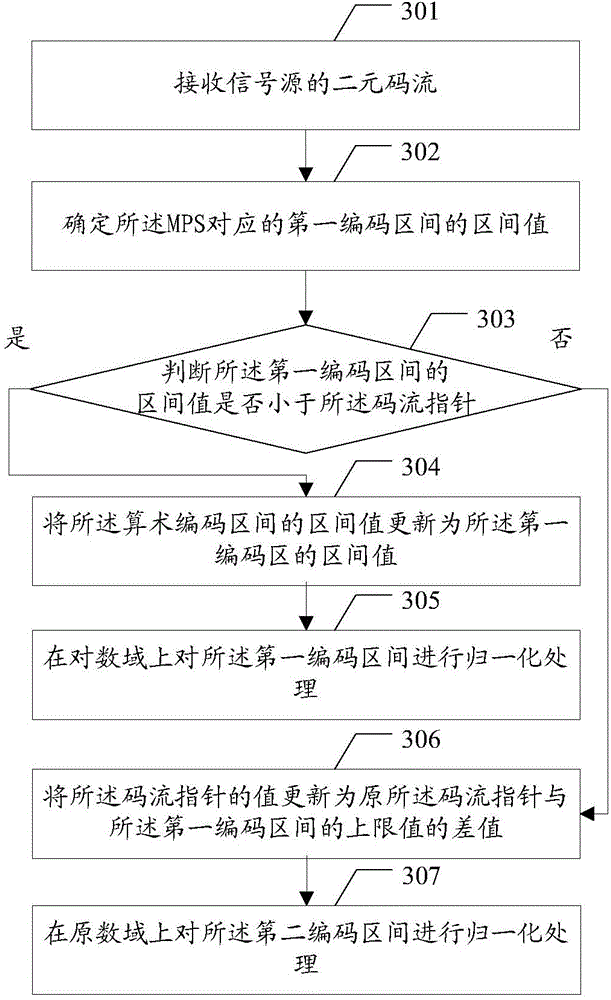
ActiveCN104394418AEasy to implementSpecify the maximum number of normalizationsCode conversionDigital video signal modificationComputer hardwareArithmetic coding
The embodiment of the invention discloses a method and device for coding video data and a method and device for decoding video data for conveniently performing data coding and decoding on video data. The method coding video data of the embodiment of the invention comprises: performing algorithm coding, the algorithm coding comprising: obtaining a binary symbol of image data; if the binary symbol is a more probable symbol (MPS), updating a first coding section corresponding to the MPS on a logarithm domain; if updated coding section less than a preset range of the algorithm coding section, performing a normalization process on the first coding section on the logarithm domain; if the binary symbol is a less probable symbol (LPS), updating a second coding section corresponding to the LPS on a primitive number domain, and performing a normalization process on the second coding section on the primitive number domain.
Owner:TSINGHUA UNIV +1
Method and system for dynamic loop transfer by populating split variables
A method that provides for dynamic loop transfer for a method having a first set of instructions being executed by an interpreter is provided. An execution stack includes slots for storing a value of each local variable known to each subroutine while the subroutine is active. The method comprises suspending execution at a point for which a current execution state can be captured from the execution stack; assigning the value in each slot of the execution stack to a corresponding slot of an array of values; scanning the first set of instructions to identify a data type for local variable that is not known in the current execution state and shares a slot in the execution stack with a local variable that is known; and generating a second set of instructions for the method coded to be initially executed to declare each local variable that is known in the current execution state and each local variable for which a data type was identified, assign each declared variable with the value assigned to the slot in the array that corresponds to the slot of the execution stack in which the value of the variable is stored during execution of the first set of instructions, and branch to a target point in the second set of instructions that corresponds to the point at which execution was suspended.
Owner:INT BUSINESS MASCH CORP
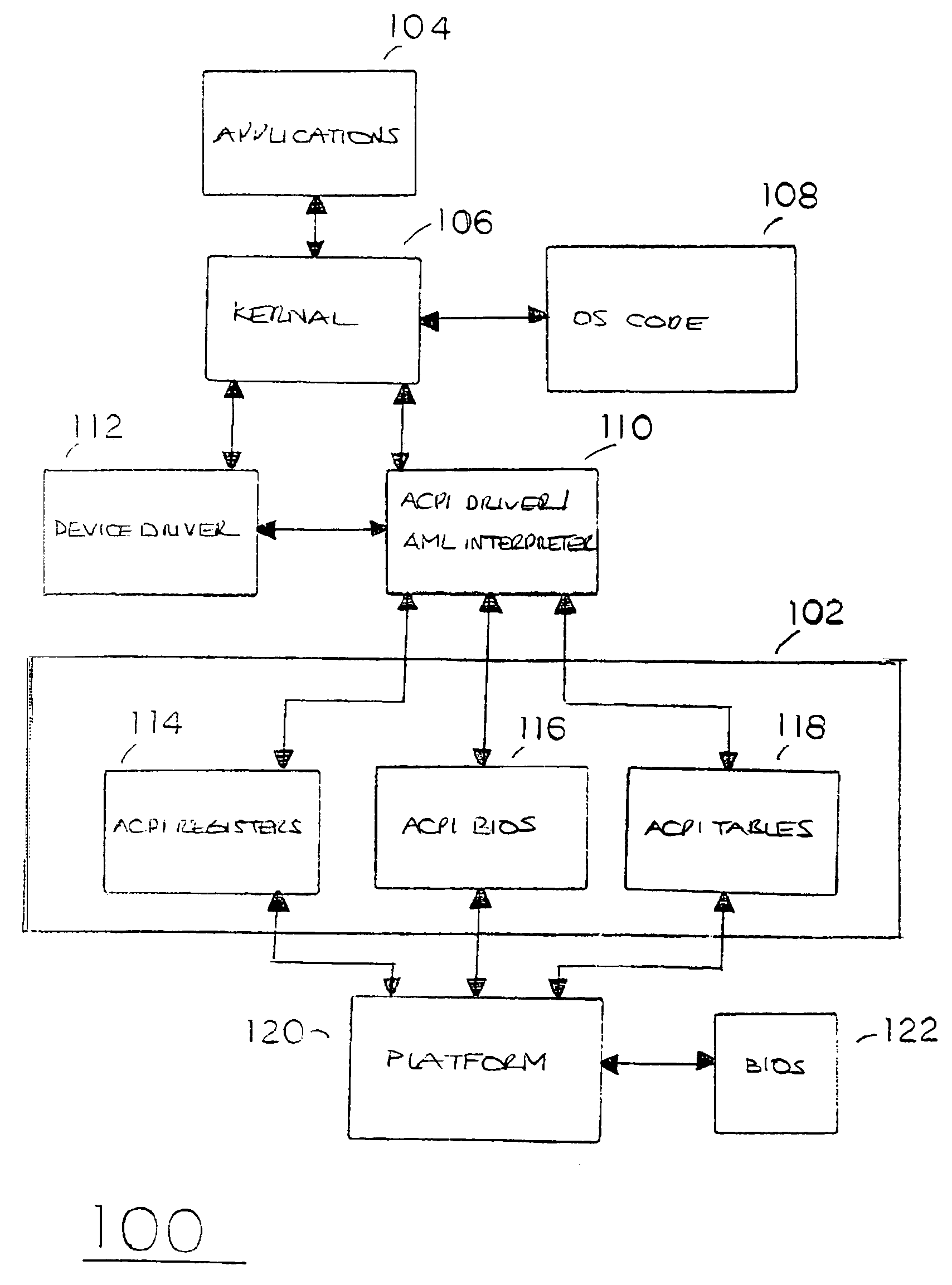
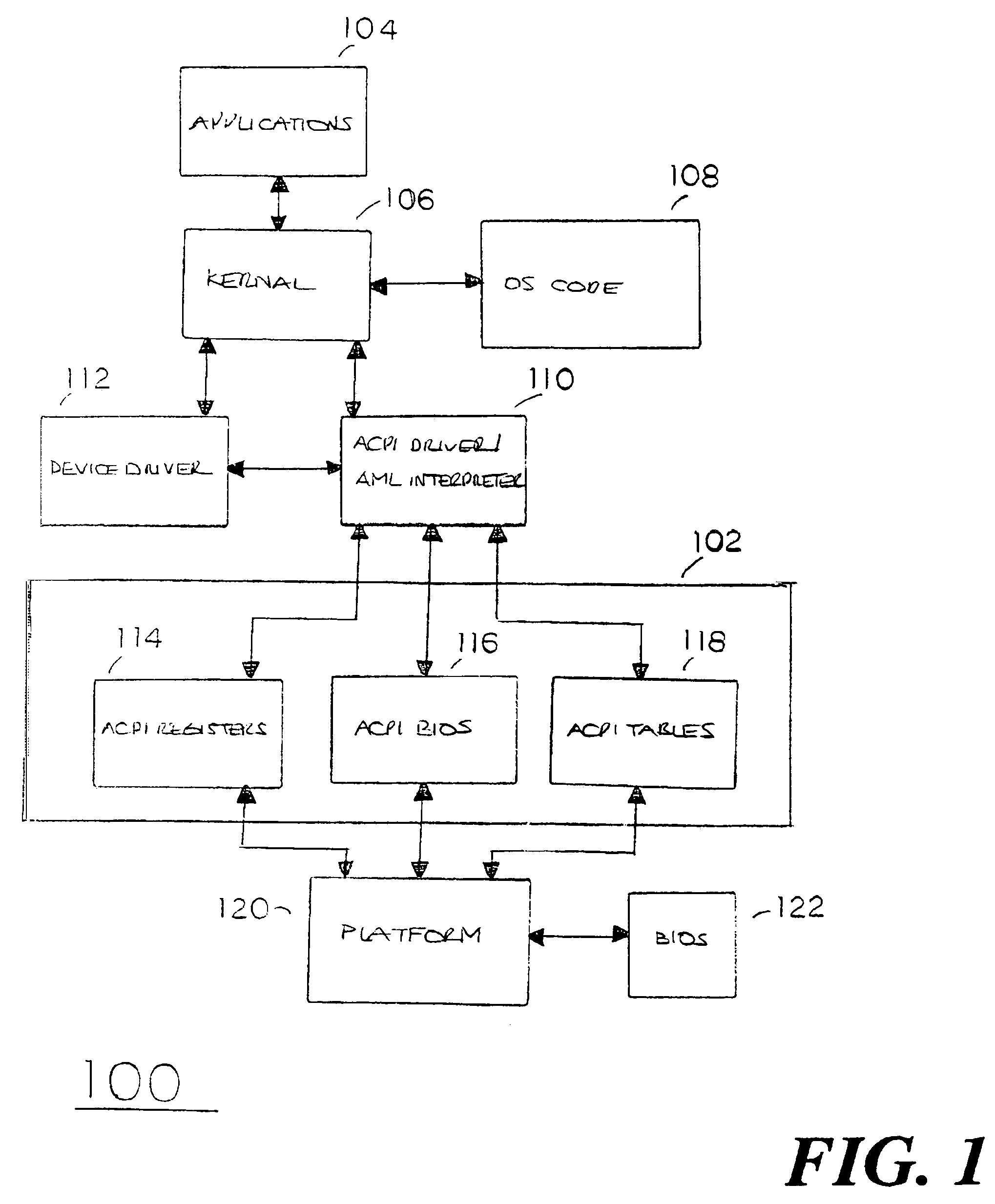
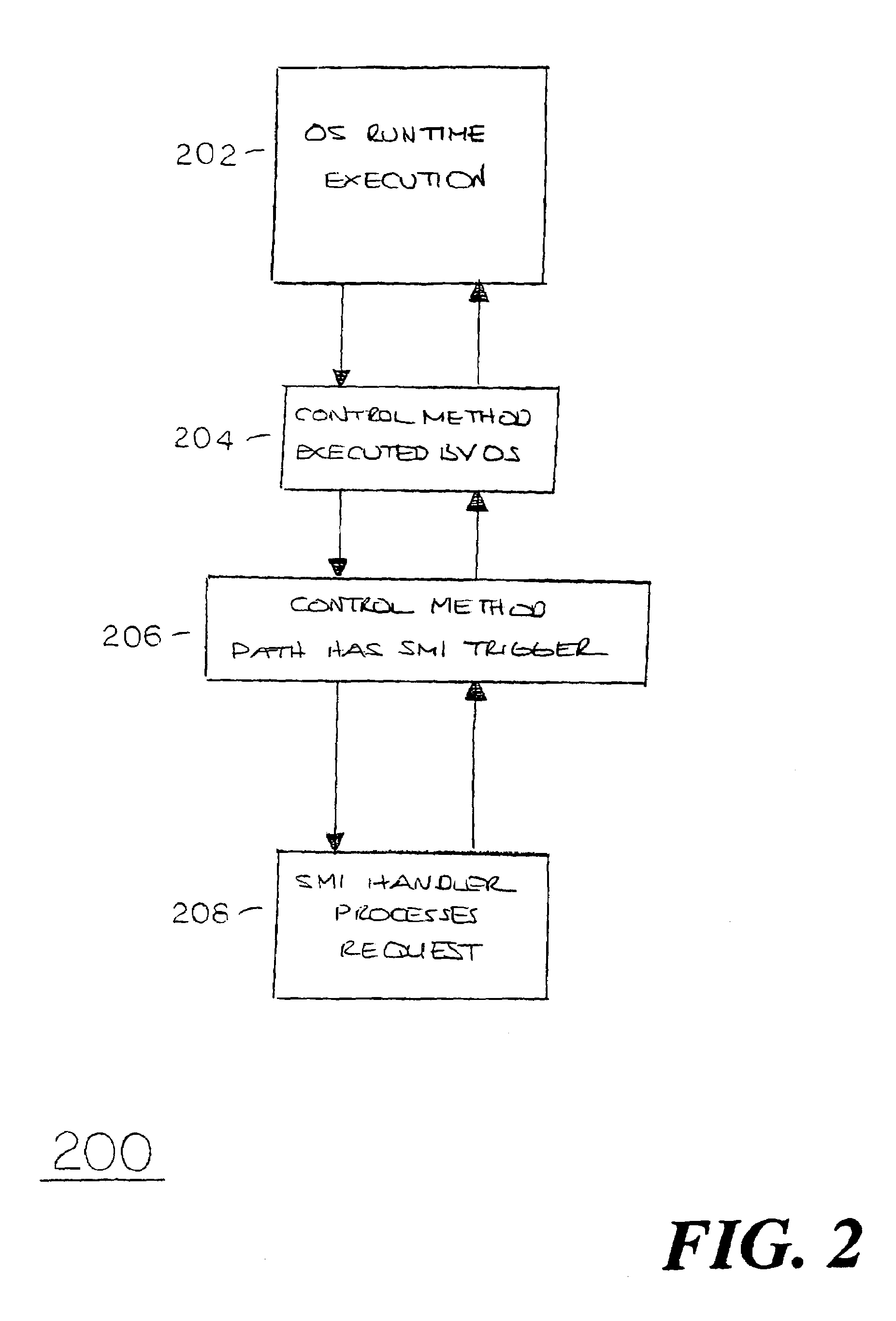
Method and apparatus for generating SMI from ACPI ASL control code to execute complex tasks
InactiveUS7325146B2Program initiation/switchingDigital data processing detailsMethod CodeMethod access
Embodiments of the present invention provide for generation of SMI from ACPI ASL control method code to execute complex tasks including, but not limited to, transferring or searching through large amounts of data dynamically. Instead of executing certain tasks using limited ASL functionality, an SMI is generated in an ASL code execution path to enable usage of a CPU instruction set accessible to the SMM handler. In particular, an ACPI operation region is defined for an I / O address location capable of triggering an SMI. An ACPI control method accesses the SMI generation I / O address location to generate an SMI during ASL code execution when a predefined complex task is encountered, thus enabling the SMI handler code to advantageously execute the complex task.
Owner:INTEL CORP
Method for selecting transform types from mapping table for prediction modes
InactiveUS8929455B2Color television with pulse code modulationPulse modulation television signal transmissionData miningData application
A method codes pictures in a bitstream, wherein the bitstream includes coded pictures to obtain data for associated TUs and data for generating a transform tree, and a partitioning of coding units (CUs) into Prediction Units (PUs), and data for obtaining prediction modes or directions associated with each PU. One or more mapping tables are defined, wherein each row of each table has an associated index and a first set of transform types to be used for applying an inverse transformation to the data in TU. The first set of transform types is selected according to an index, and then a second set of transform types is applied as the inverse transformation to the data, wherein the second set of transform types is determined according to the first set of transform types and a transform-toggle flag (ttf) to obtain a reconstructed prediction residual.
Owner:MITSUBISHI ELECTRIC RES LAB INC
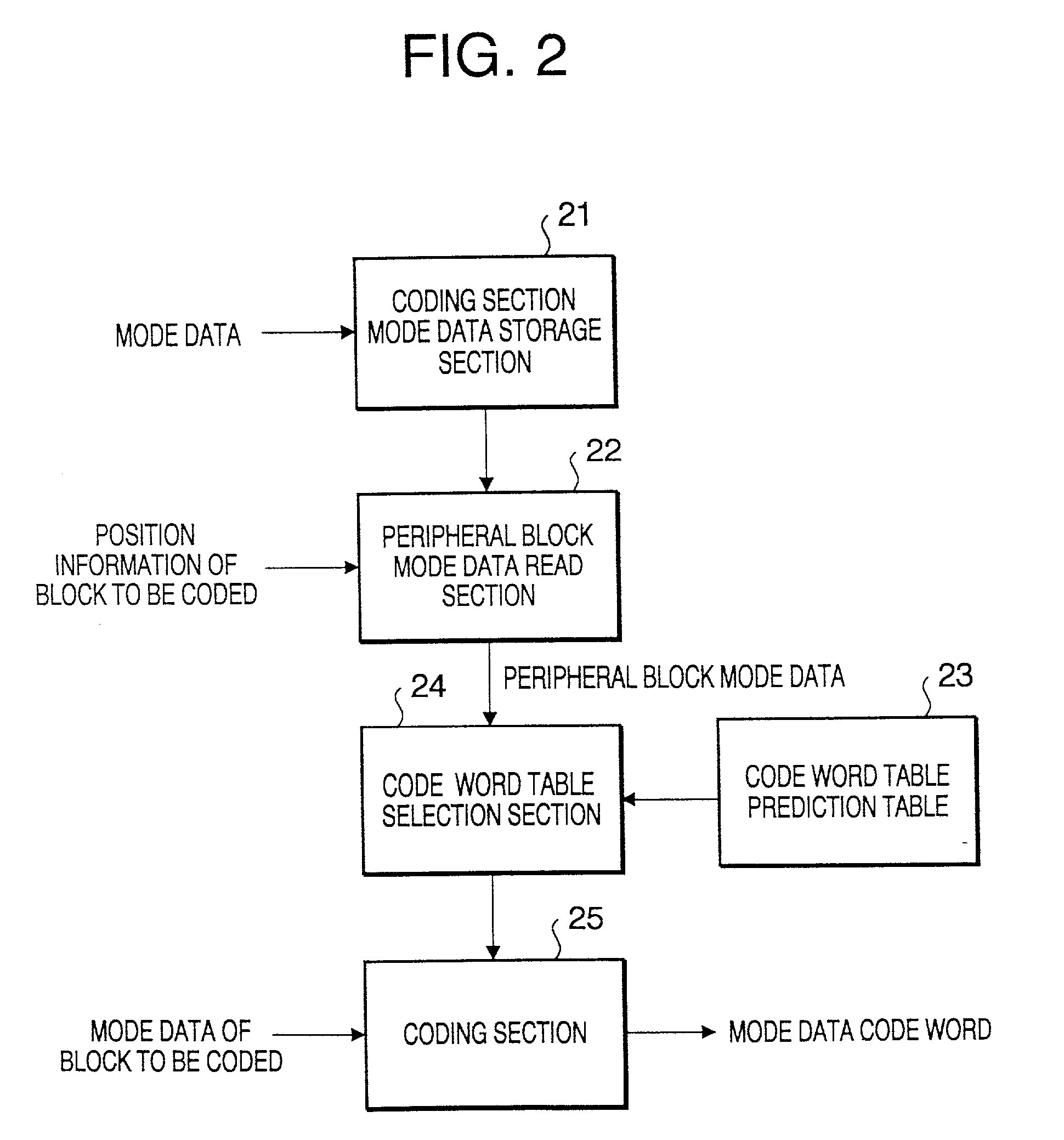
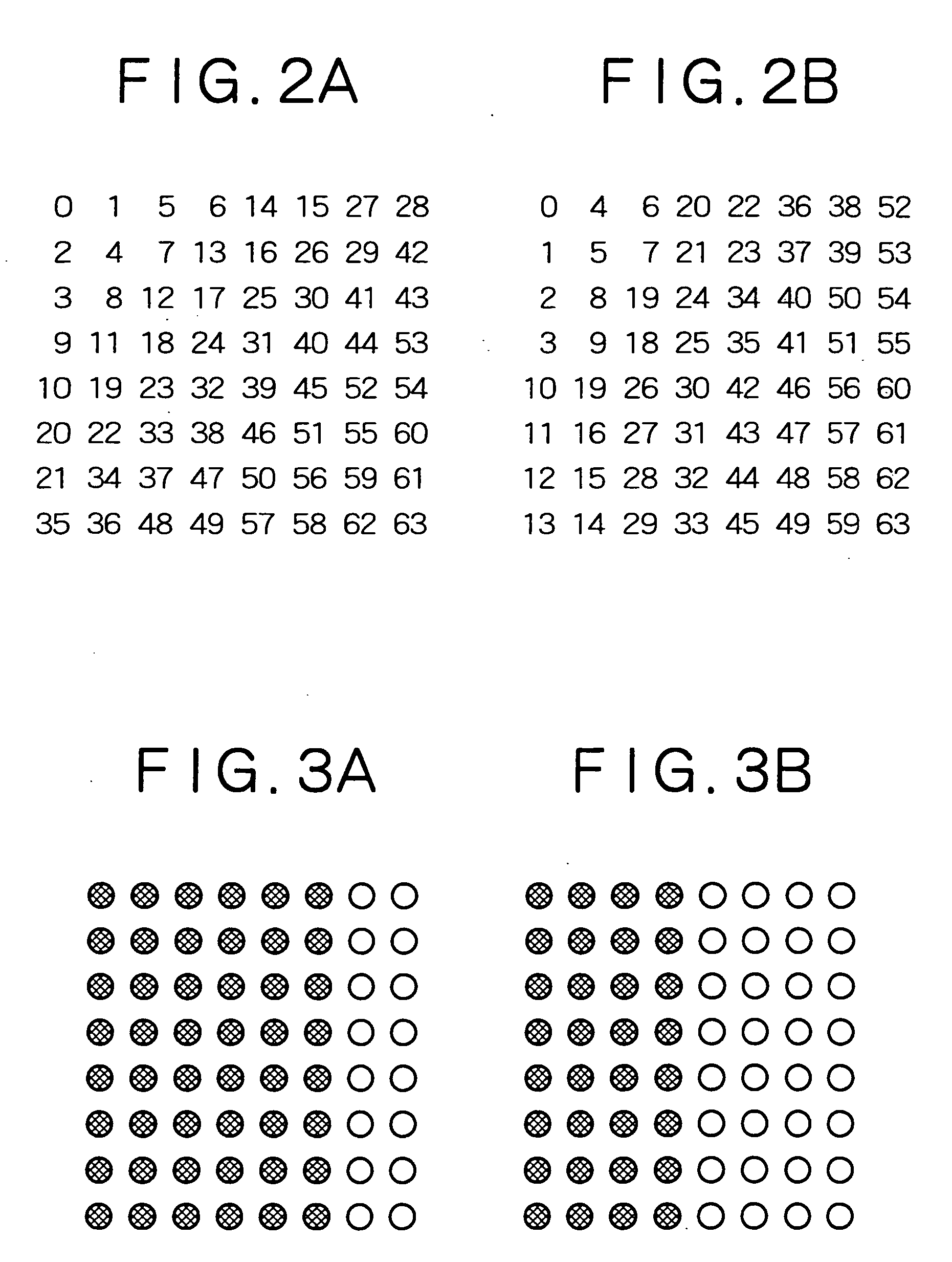
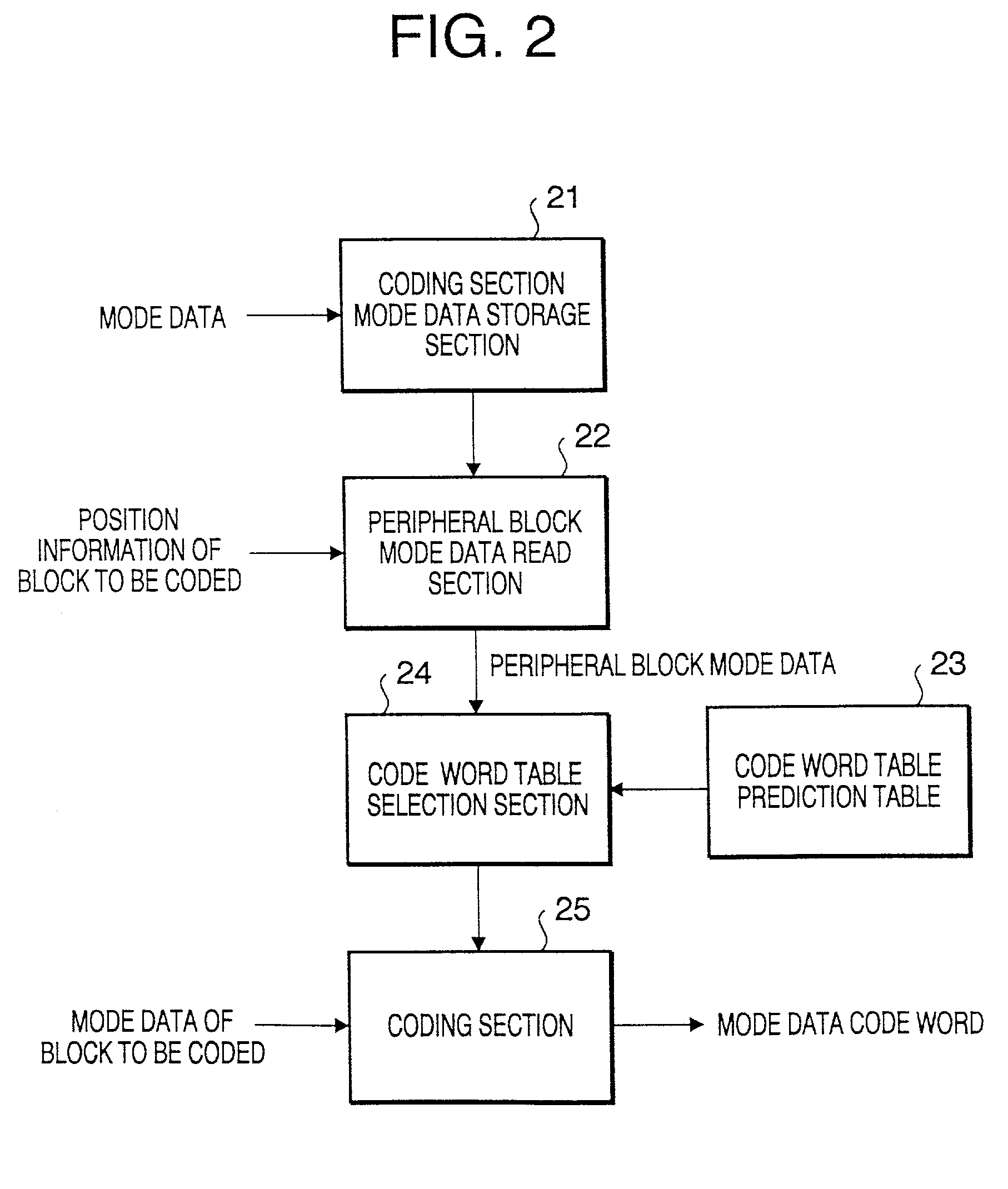
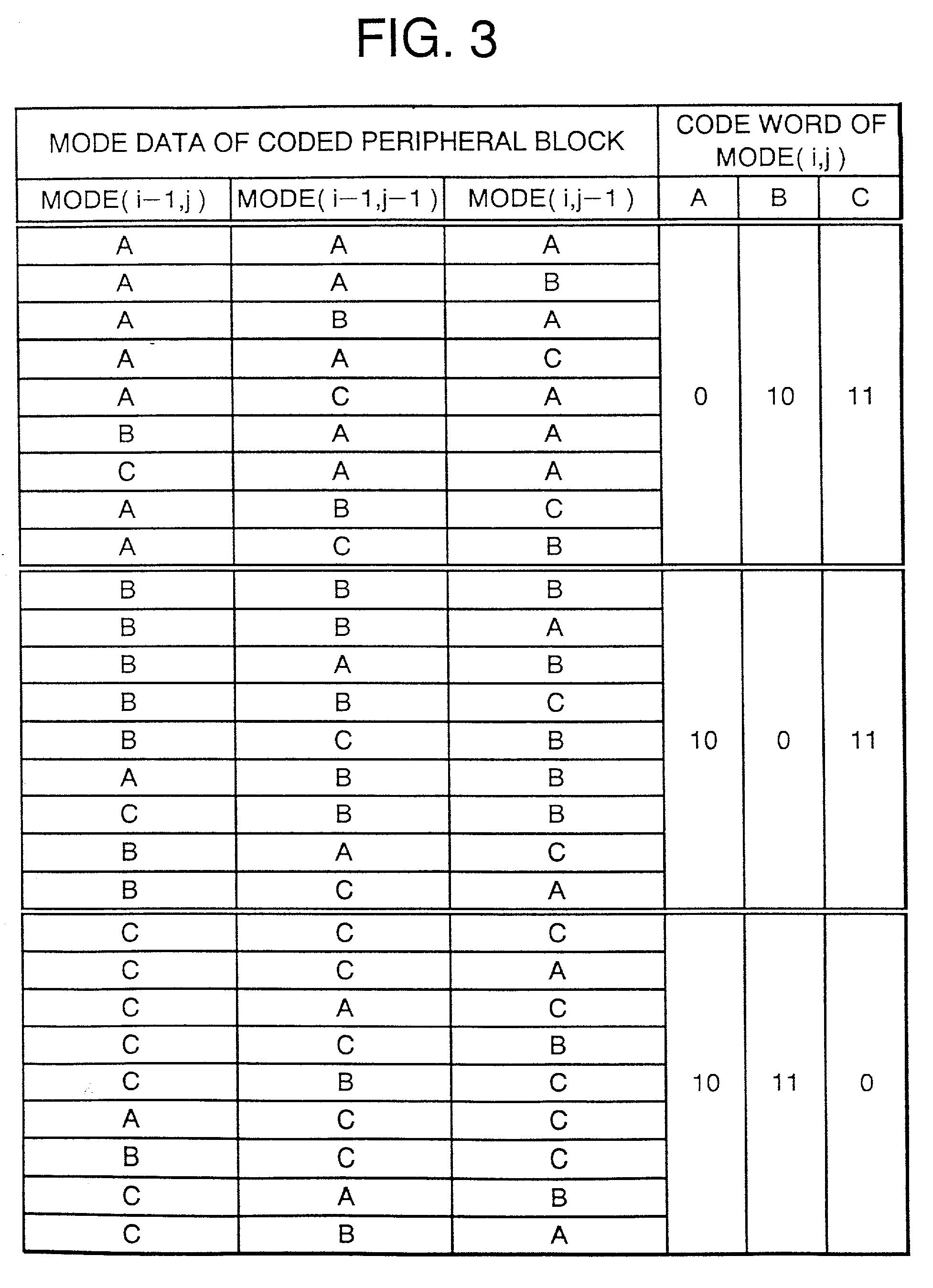
Image coding method and an image coding apparatus
InactiveUS20010022855A1Avoid efficiencyImprove coding efficiencyPulse modulation television signal transmissionCharacter and pattern recognitionComputer hardwareCoding block
An image coding method codes each block of a digital image divided into two-dimensional blocks, each block having a plurality of pixels. A coding mode for a target block is determined to output mode information of the target block. A codeword of the mode information of the target block is output, the codeword being determined based on a combination of the mode information of the target block and the mode information of previously coded blocks at a periphery of the target block, or a combination of the mode information of the target block and temporary mode information replacing the mode information of the blocks at the periphery of the target block when the blocks at the periphery are out of an image. Pixel data in the target block is coded according to the mode information of the target block.
Owner:GK BRIDGE 1
Code quantity control apparatus, code quantity control method and picture information transformation method
InactiveUS20050276325A1Avoid it happening againAvoid large quantitiesColor television with pulse code modulationColor television with bandwidth reductionParallel computingImage compression
Code quantity control based on a virtual buffer is executed by using information extracted from picture compressed information conforming to a predetermined system. Thus, a reference quantization scale can be held at a fixed value throughout a frame. As a result, it is possible to generate picture compressed information having a smaller code quantity.
Owner:SONY CORP
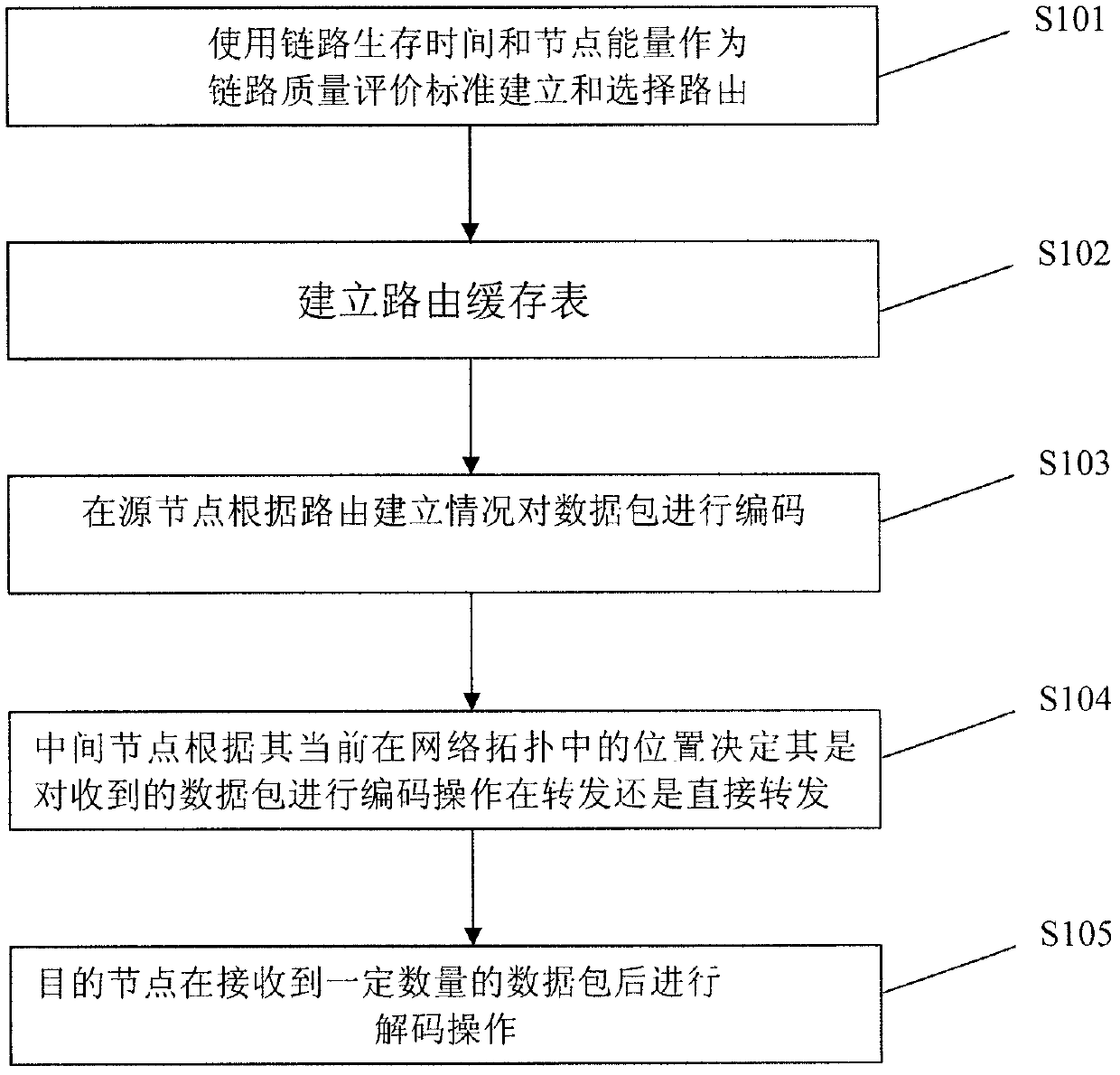
High-speed mobile ad hoc network data transmission method based on dynamic network codes
InactiveCN103297174AReliable transmissionEfficient and reliable transmissionError preventionNetwork topologiesNetwork codeData transmission
The invention discloses a high-speed mobile ad hoc network data transmission method based on dynamic network codes. The data transmission method comprises the following steps of using link survival time and node energy as a link quality evaluation criterion to establish and choose a route, establishing a route cache table, coding data packets at source nodes according to route establishing situations, and deciding that middle nodes code and transmit received data packets or directly transmit the received data packets according to the positions of the middle nodes in current network topology. The data transmission method can choose the most stable route to transmit data through a link quality prediction mechanism, and then whether the middle nodes are coded according to the real-time positions of the middle nodes in topology of a mobile ad hoc network is decided. Compared with a method coding all middle nodes, the data transmission method guarantees reliable data transmission, reduces time delay and total energy consumption and achieves high-efficiency data transmission in a high-speed mobile ad hoc network.
Owner:陈小虎 +1
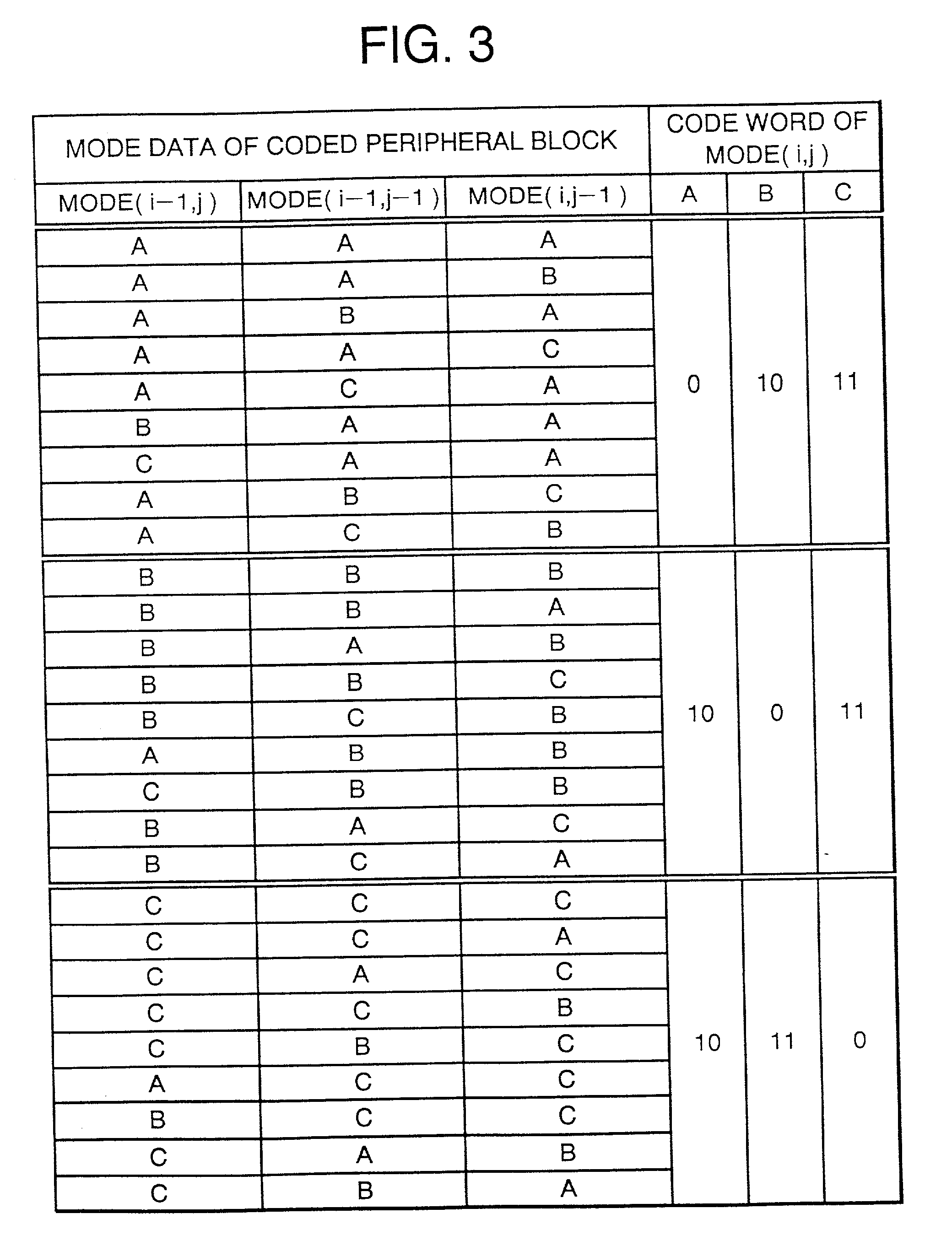
Image coding method and an image coding apparatus
InactiveUS20010022856A1Avoid efficiencyPulse modulation television signal transmissionImage codingCoding blockComputer hardware
An image coding method coding each block of a digital image divided into two-dimensional blocks, each block having a plurality of pixels. A coding mode for a target block is determined to output mode information of the target block. A codeword table is selected from a plurality of codeword tables based on a combination of the mode information of previously coded blocks at a periphery of the target block. The tables correspond to combinations of the mode information of the previously coded blocks at the periphery of the target block, and have codewords respectively corresponding to coding modes available for the target block. A codeword is assigned a shorter codeword length when the coding mode for the target block is numerically predominant among the coding modes for the blocks at the periphery of the target block than when the coding mode for the target block is numerically inferior among the coding modes for the blocks at the periphery. The code information for the target block is coded using the selected codeword table. The pixel data in the target block is coded according to the mode information of the target block.
Owner:GK BRIDGE 1
Supersonic movement detection method coding using reversing Golay dode
InactiveCN101149433AImprove SNRStrong penetrating powerAcoustic wave reradiationCode moduleSonification
This invention is a kind of ultrasonic movement test method which uses the reverse Golay code coding, uses the method that two coding module process two data path separately, when decoding the receiver signal of the receiver circuit, uses the original orthogonal Golay code module decode the first data path and superimpose it by the superimposed module; uses the reverse Golay code module decode the second data path and superimpose it by the superimposed module; at last processes the result of the first and second data path by bucking module, does a proper delay to the superimposed result of the second data path by delay module. The first data path in this invention can improve SNR and enhance the force of penetration, and at the same time remove the pseudo-image; the second data path will detect and enhance the movement display in B image, the enhanced area covered by a clean static image.
Owner:绵阳索尼克电子有限责任公司
Rate control method with region of interesting support
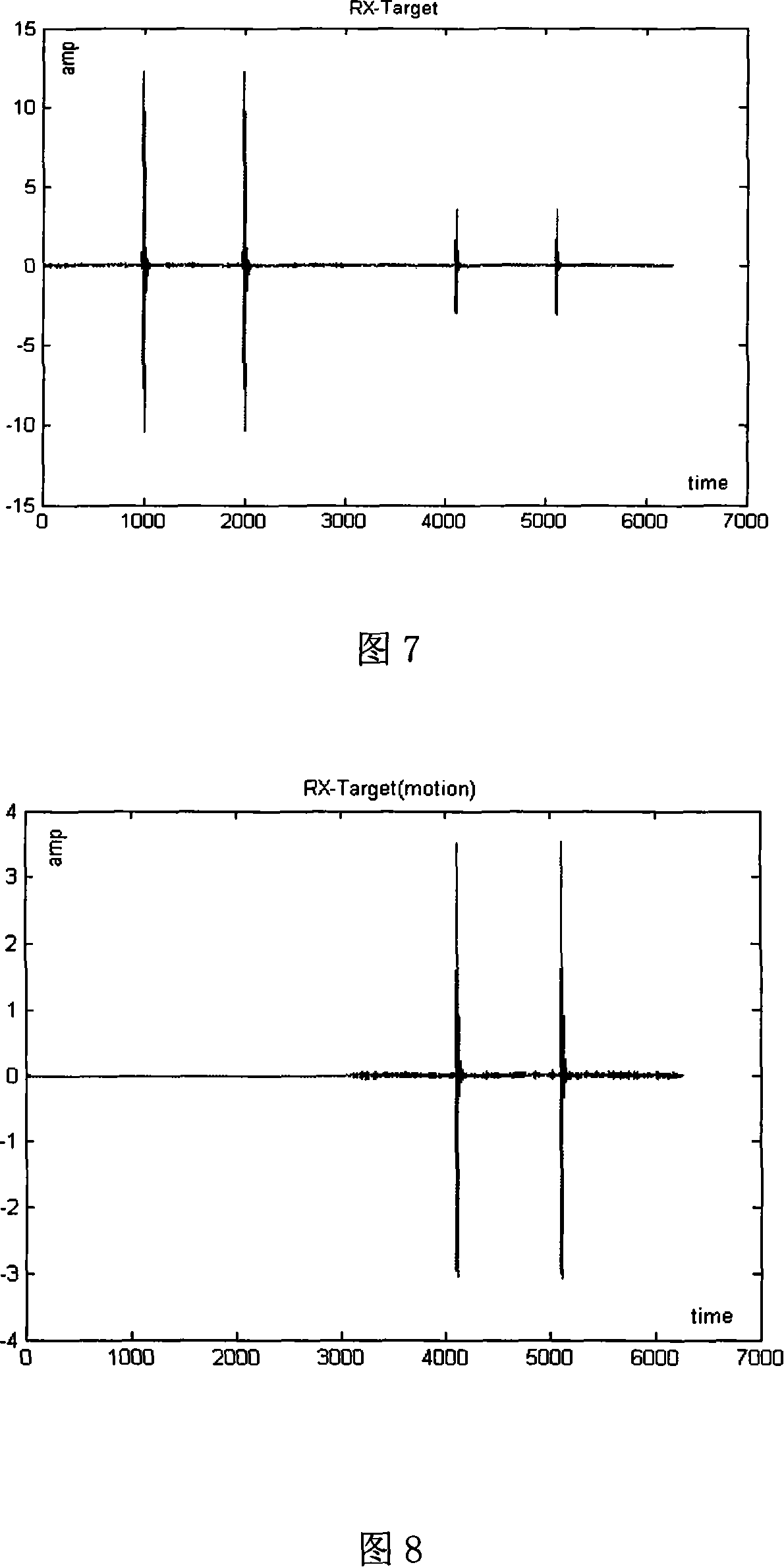
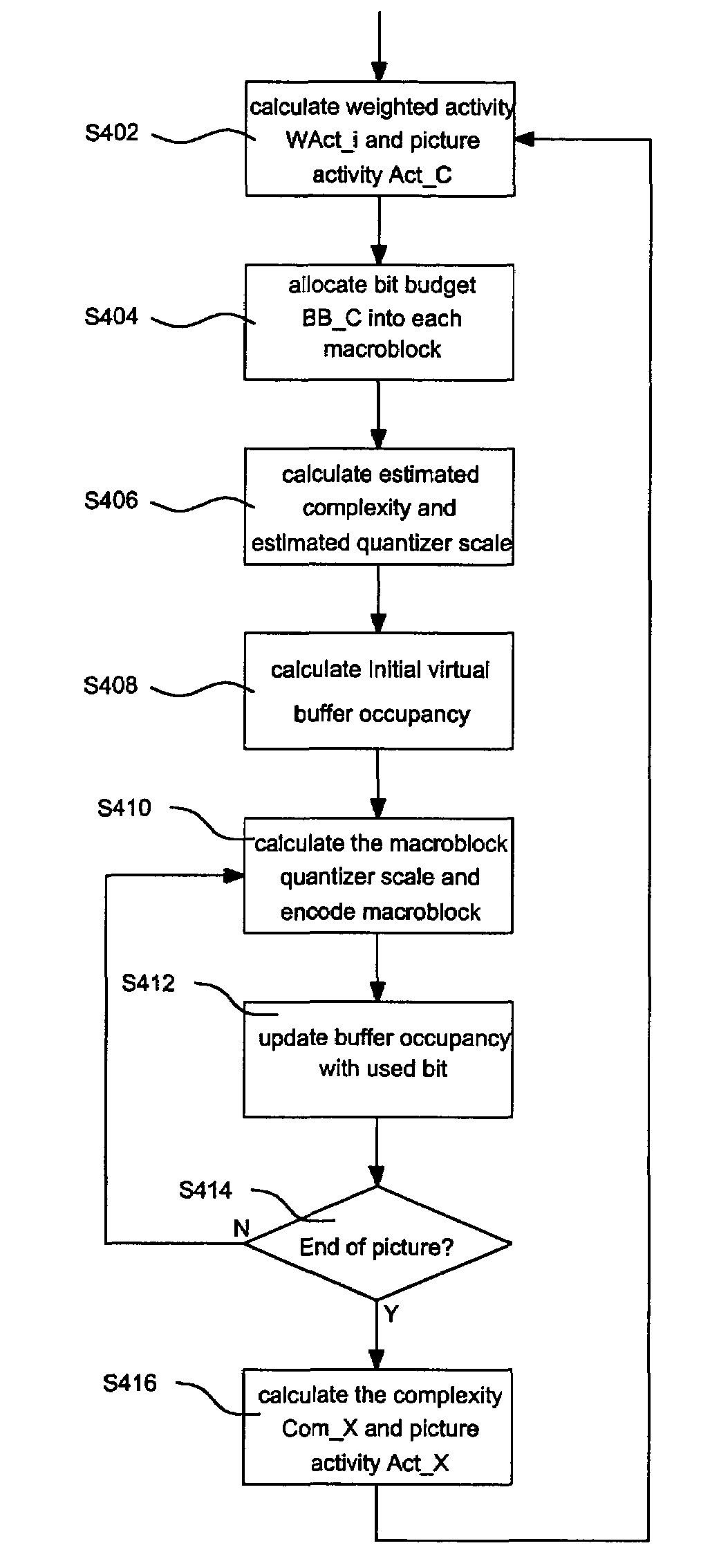
ActiveUS7194031B2Improve image qualityColor television with pulse code modulationColor television with bandwidth reductionMethod CodeRegion of support
A rate control method with region of interesting support, which coding macroblocks in a current picture with different priority. The rate control method calculates a weighted macroblock activity according to the priority and a macroblock activity and a picture activity for the current picture according to the weighted macroblock activity. Then, the method allocates a bit budget for each macroblock according to the priority and calculates an estimated complexity for the current picture according to a complexity of a previously coded picture, an activity of the previously coded picture and the weighted macroblock activity. The method also calculates an estimated quantizer scale according to the estimated complexity and the bit budget, an initial virtual buffer occupancy according to an reaction factor and the estimated quantizer scale and a macroblock quantizer scale according to a virtual buffer occupancy of a previously coded macroblock, the priority and the reaction factor. The method codes each macroblock according to the macroblock quantizer scale and updates a virtual buffer occupancy of the current coded macroblock according to a used bit of the coded macroblock, the virtual buffer occupancy of the previously coded macroblock and the bit budget of current coded macroblock.
Owner:SILICON INTEGRATED SYSTEMS
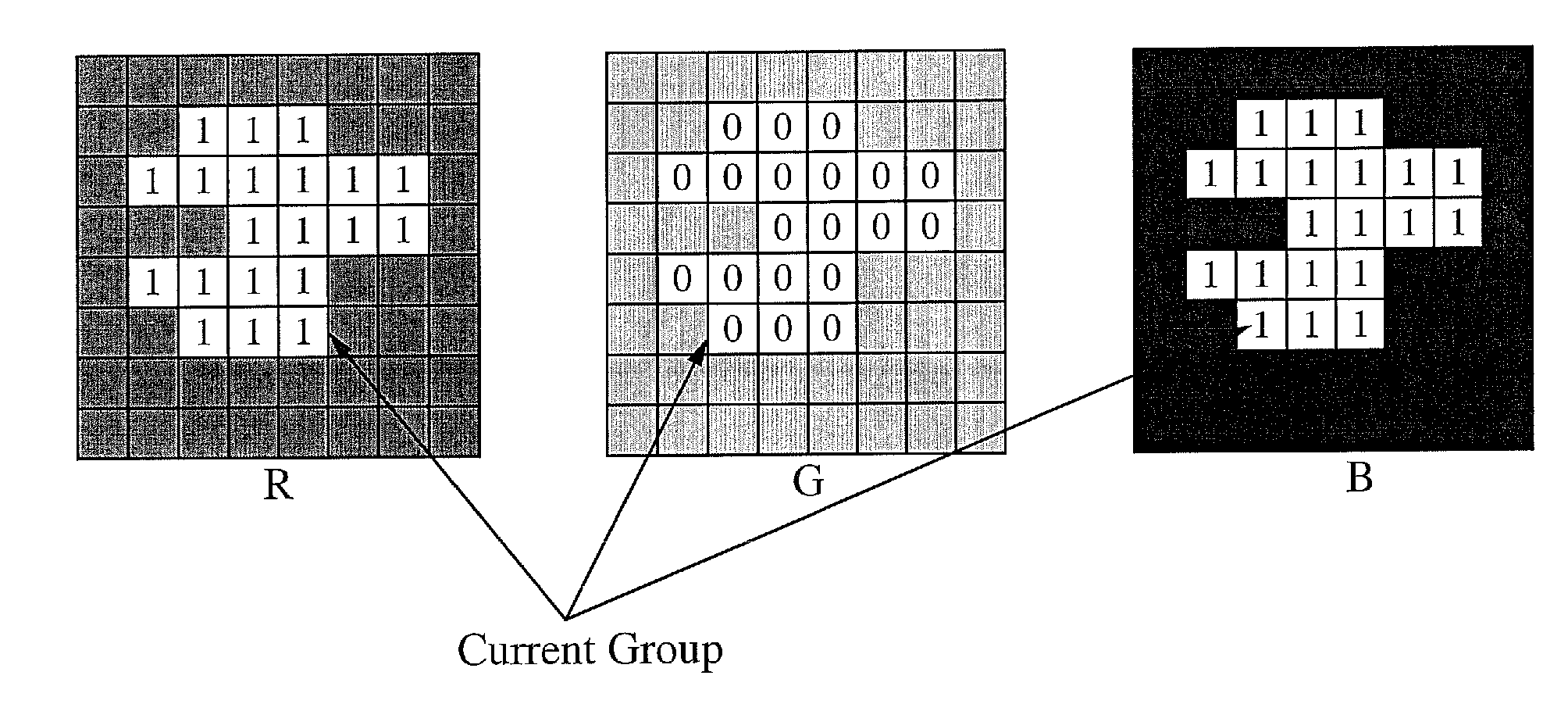
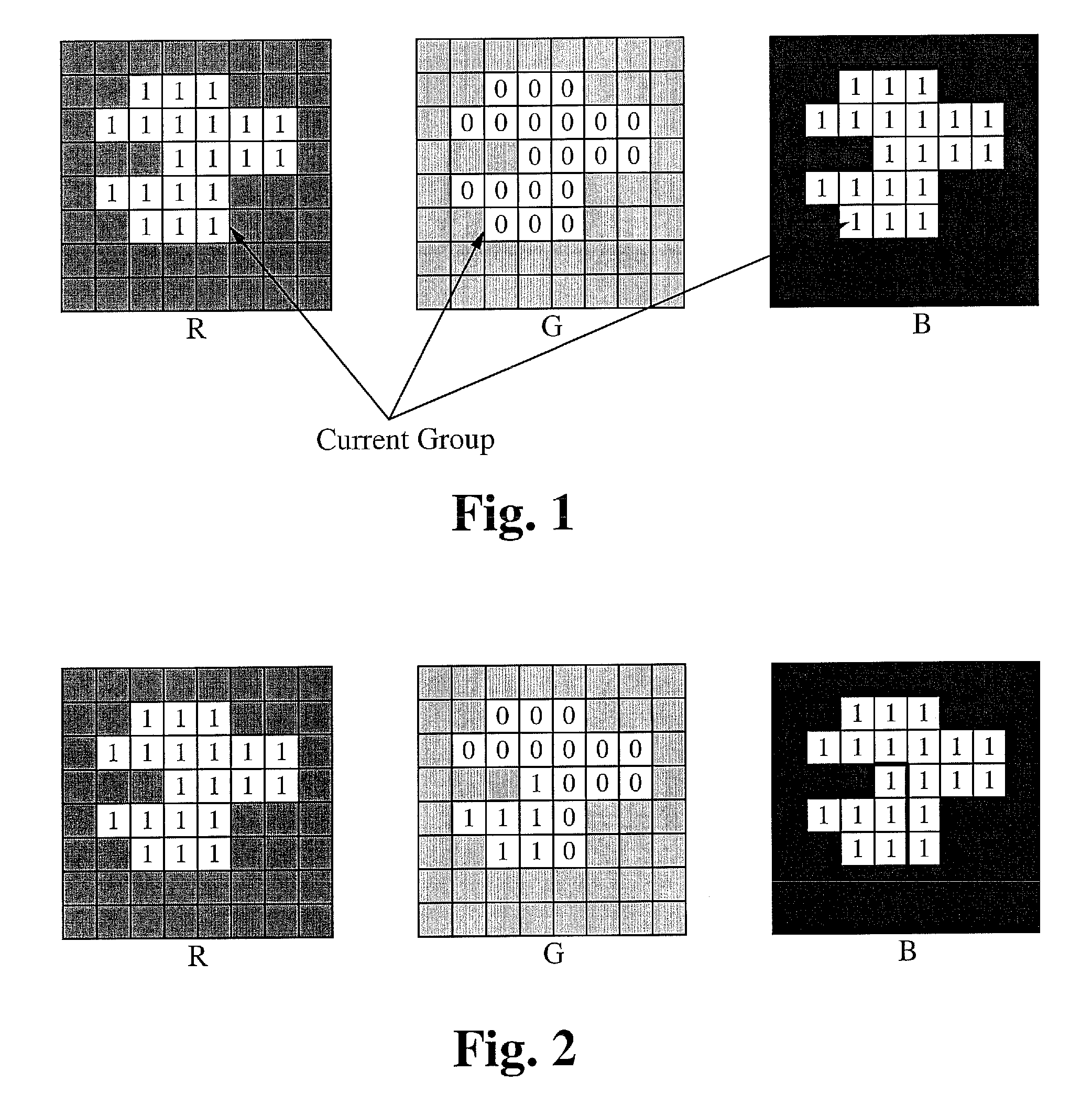
Vector embedded graphics coding
ActiveUS20110050959A1Television system detailsColor signal processing circuitsPattern recognitionGraphics
A method of coding High Definition (HD) color pictures is described. The method divides the HD picture into individual bit planes of the three colors. The method then interleaves the bit planes such that bit planes of the three colors having the same significance are coded together. The method codes a block of the picture based on the bit distribution in corresponding groups of the corresponding bit planes of the three colors. The method performs a first level grouping of bits in a bit plane of an image and a second level grouping of the first level grouping bits of different color components within a group.
Owner:SONY CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com