Secure data mirroring method with key negotiation function
A technology for key negotiation and secure data, applied in key distribution, can solve problems such as poor platform compatibility, poor real-time performance, and leakage of sensitive information, and achieve the effects of secure data synchronization, data synchronization, and data leakage avoidance
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0052] Below in conjunction with accompanying drawing and specific embodiment the present invention is described in further detail:
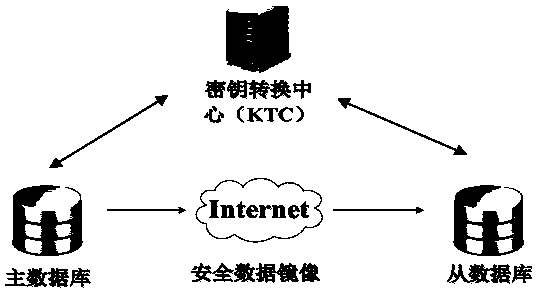
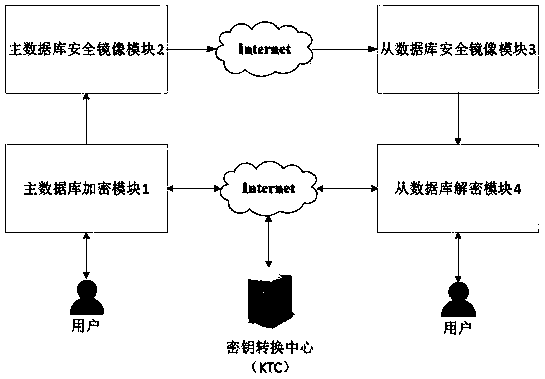
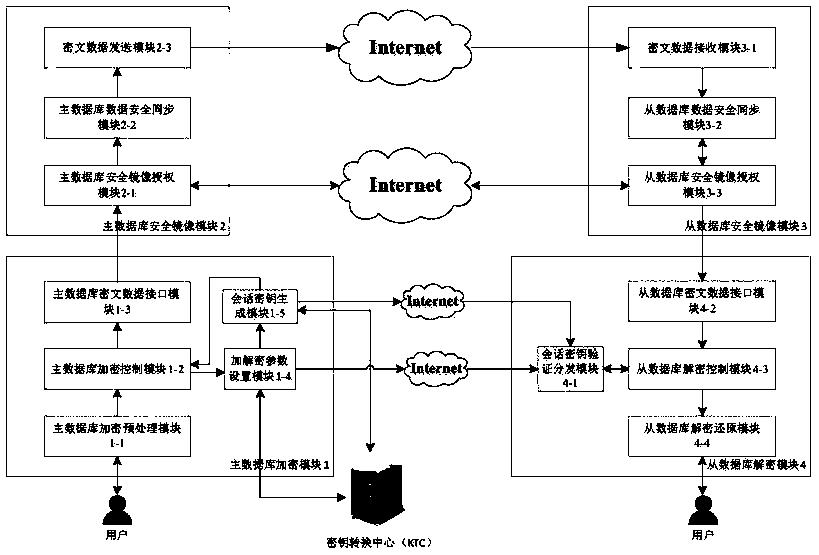
[0053] Based on the data encryption technology of the trusted third-party key forwarding center and the synchronization technology based on log files, the present invention provides a secure data mirroring method with a key negotiation function; the method uses the trusted third-party key forwarding center Complete the identity authentication of the master database and the slave database, and provide a customized one-time pad scheme to enable the master and slave databases to share session keys to ensure the security of key distribution, and complete the mirror authorization and data encryption of the master and slave databases through encryption. Transmission, based on a customized one-time pad scheme to achieve secure data synchronization and avoid data leakage; this method is based on log file synchronization data, whenever the user completes ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com