Database encryption and decryption method and device
An encryption method and database technology, applied in relational databases, database models, digital data protection, etc., can solve problems such as database file corruption and unusable tools, and achieve the effects of ensuring correctness, improving security, and avoiding damage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
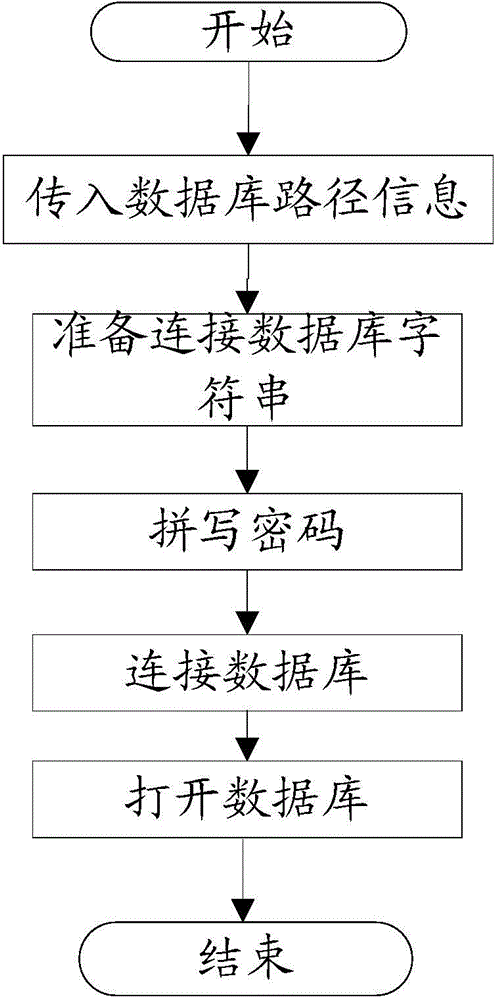
[0047] Please refer to Figure 5 , Figure 5 It is a flow chart of the method in Embodiment 1 of the present invention. Such as Figure 5 As shown, a database encryption method may include the following steps:
[0048] 101. Write file modification information to a preset location in the database to be encrypted.
[0049] Wherein, the database to be encrypted may be an Access database.
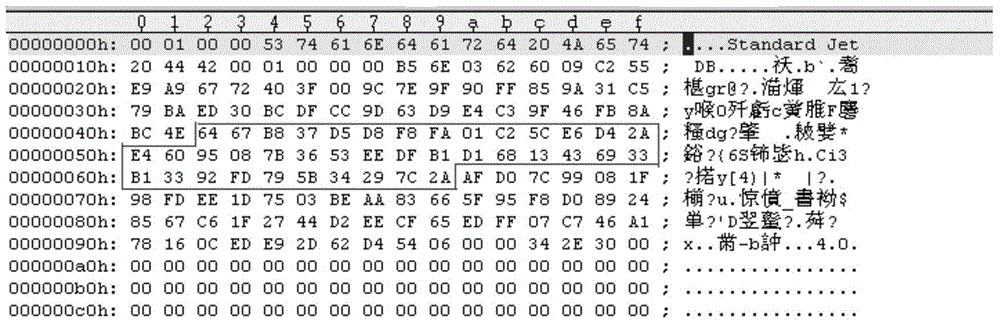
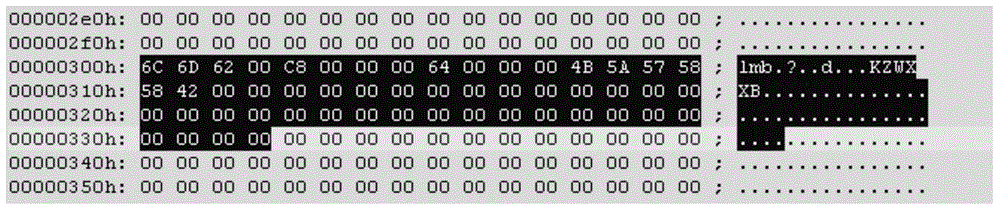
[0050] The file modification information includes: version information, flags and encryption algorithms corresponding to the database to be encrypted. In the embodiment of the present invention, the preset position is the data position starting from the 0x300th byte, and the data position of 0x300 does not participate in the verification of the database. Therefore, when the file modification information is written at this position, it can be ensured that the database file does not There will be crashes to ensure the normal operation of the database.
[0051] 102. Calculate an encryption p...
Embodiment 2
[0057] Please refer to Image 6 , Image 6 It is a flowchart of the encryption method in Embodiment 2 of the present invention. Such as Image 6 As shown, compared with Embodiment 1, the embodiment of the present invention also includes steps before writing the file modification information into the preset position in the database to be encrypted:
[0058] 201. Acquire verification code information of a database to be encrypted currently.
[0059] The check code information is used to identify the identity of the database and the version of the database. After the verification code information is obtained, the identifier of the database corresponding to the database to be encrypted and the version of the database can be obtained.
[0060] This embodiment may also include the steps of:
[0061] 202. Write the file modification information to a preset location in the database to be encrypted.
[0062] 203. Calculate an encryption password according to the version informati...
Embodiment 3
[0067] Correspondingly, the present invention also provides a database encryption device, please refer to Figure 7 , Figure 7 It is a schematic diagram of the device structure of the embodiment of the present invention. Such as Figure 7 As shown, the database encryption device may include:
[0068] The first writing unit 30 is configured to write file modification information into a preset location in the database to be encrypted, the file modification information including: version information corresponding to the database to be encrypted, a version flag and an encryption algorithm.
[0069] A calculating unit 31, configured to calculate an encryption password according to the version information and version flag corresponding to the database to be encrypted.
[0070] The second writing unit 32 is configured to write the encryption password into a password verification position in the database to be encrypted, and the password verification position is used to store a de...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com